Linux Bible 9th Ed (2015)
Part IV. Becoming a Linux Server Administrator
Chapter 19. Configuring a Windows File Sharing (Samba) Server
IN THIS CHAPTER
1. Getting and installing Samba
2. Using Samba security features
3. Editing the smb.conf configuration file
4. Accessing Samba from Linux and Windows clients
5. Using Samba in the enterprise
Samba is the project that implements open source versions of protocols used to share files and printers, as well as authenticate users and restrict hosts, among Windows systems. Samba offers a number of ways to share files among Windows, Linux, and Mac OS/X systems that are well known and readily available to users of those systems.
This chapter steps you through the process of installing and configuring a Samba server. It describes security features you need to know to share your file and printer resources and describes how to access those resources from Linux and Windows systems.
Understanding Samba
Samba (www.samba.org) is a suite of programs that allows Linux, UNIX, and other systems to interoperate with Microsoft Windows file and printer sharing protocols. Windows, DOS, OS/2, Mac OS/X, and other client systems can access Samba servers to share files and printers in the same ways they would from Windows file and print servers.
With Samba, you can use standard TCP/IP networking to communicate with clients. For name service, Samba supports regular TCP/IP hostnames, as well as NetBIOS names. For that reason, Samba doesn't require the NetBEUI (Microsoft Raw NetBIOS frame) protocol. File sharing is done using the Common Internet File System (CIFS), which is an open implementation of the Server Message Block (SMB) protocol.
The Samba project has gone to great lengths to make its software secure and robust. In fact, many people prefer using Samba servers over Windows file servers because of the added security that is inherent in running Windows-style file sharing services on Linux or other UNIX-like operating systems.
Beyond all the technical mumbo-jumbo, however, the end result is that Samba makes it easy to share files and printers between Linux servers and Windows desktop systems. For the server, only a few configuration files and tools are needed to manage Samba. For the clients, shared resources just show up under the Network selection in the window manager or in the Network Neighborhood on older Windows systems.
Interfaces for managing Samba on a Linux server include the Samba Server Configuration window (system-config-samba) and the Samba SWAT (Samba Web Administration Tool) web-based interface. As an alternative, you can directly edit Samba configuration files (particularly smb.conf) and run a few commands to configure Samba.
Working with Samba SWAT
I do not cover this topic in this chapter, but many people prefer the Samba SWAT interface to directly editing configuration files. On some Linux distributions, Samba SWAT may be the only point-and-click interface available. Others, such as Fedora, no longer include it.
Here's a quick guide to getting Samba SWAT working on your RHEL 6 system:
1. Install the samba-swat and xinetd packages.
2. Edit the /etc/xinetd.d/swat file, and change the disable line to read disable = no.
3. Restart xinetd: service xinetd start ; chkconfig xinetd on.
4. Open your local web browser to this address: http://localhost:901.
The Samba Web Administration Tool screen that opens in your browser (after entering the root username and password) provides a different interface for configuring your Samba server, shared directories, and printers that are described in the rest of this chapter. By clicking around, you should be able to find how to plug that information into the SWAT interface.
To begin using Samba on your Linux system, you need to install a few software packages, as described in the next section.
Installing Samba
In Red Hat Enterprise Linux and Fedora, to configure a Samba file and print server, the only required packages are the samba and samba-common packages. Among other components, the samba package includes the Samba service daemon (/usr/sbin/smbd) and NetBIOS name server daemon (/usr/sbin/nmbd). The samba-common package contains server configuration files (smb.conf, lmhosts, and others) and commands for adding passwords and testing configuration files, along with other Samba features.
Features from other packages are referenced in this chapter, so I describe how to install those packages as well. Those packages include the following:
· samba-client package—Contains command-line tools such as smbclient (for connecting to Samba or Windows shares), nmblookup (for looking up host addresses), and findsmb (to find SMB hosts on the network).
· system-config-samba package—Contains a graphical interface for managing Samba.
· system-config-samba-docs package—Contains documentation associated with the system-config-samba graphical interface.
· samba-swat package—Contains a web-based interface for configuring a Samba server. (No longer in Fedora.)
· samba-winbind package—Includes components that allow your Samba server in Linux to become a complete member of a Windows domain, including using Windows user and group accounts in Linux.
To install all the packages just mentioned (samba-common is installed as a dependency of samba, so it doesn't need to be noted specifically), type the following as root from the command line in Fedora:
# yum install samba samba-client samba-winbind \
system-config-samba system-config-samba-docs
...
Dependencies Resolved
==================================================================
Package Arch Version Repository Size
==================================================================
Installing:
samba x86_64 2:4.1.15-1.fc21 updates 555 k
samba-client x86_64 2:4.1.15-1.fc21 updates 513 k
samba-winbind x86_64 2:4.1.15-1.fc21 updates 445 k
system-config-samba noarch 1.2.100-3.fc21 fedora 282 k
system-config-samba-docs noarch 1.0.9-7.fc21 fedora 274 k
Installing for dependencies:
libsmbclient x86_64 2:4.1.15-1.fc21 updates 112 k
samba-common x86_64 2:4.1.15-1.fc21 updates 685 k
samba-libs x86_64 2:4.1.15-1.fc21 updates 4.2 M
samba-winbind-modules x86_64 2:4.1.15-1.fc21 updates 93 k
Transaction Summary
====================================================================
Install 5 Packages (+4 Dependent packages)
Total download size: 7.1 M
Installed size: 25 M
Is this ok [y/d/N]: y
After you have installed the Samba packages, look at the configuration files in the samba-common package:
# rpm -qc samba-common
/etc/logrotate.d/samba
/etc/sysconfig/samba
/etc/samba/lmhosts
/etc/samba/smb.conf
The /etc/logrotate.d/samba and /etc/sysconfig/samba files are usually not modified. The first sets how files in /var/log/samba log files are rotated (copied to other files and removed) over time. The second is a file where you could put options that are passed to the smbd,nmbd, or winbindd daemons, so you could turn off features such as debugging.
Most configuration files you would modify for Samba are in the /etc/samba directory. The smb.conf file is the primary configuration file, where you put global settings for the Samba server as well as individual file and printer share information (more on that later). Thelmhosts file enables the Samba NetBIOS hostname to be mapped into IP addresses.
Although it doesn't exist by default, you can create a file named /etc/samba/smbusers to map Linux user names into Windows user names. As you configure your Samba server, you can refer to the smb.conf man page (man smb.conf). There are also man pages for Samba commands, such as smbpasswd (to change passwords), smbclient (to connect to a Samba server), and nmblookup (to look up NetBIOS information).
After you have installed Samba packages and completed a quick survey of what they contain, try starting up the Samba service and see what you get in a default configuration.
Starting and Stopping Samba
With samba and samba-common installed, you can start the server and investigate how it runs in the default configuration. Two main services are associated with a Samba server, each of which has its own service daemon. Those services include the following:
· smb—This service controls the smbd daemon process, which provides the file and print sharing services that can be accessed by Windows clients.
· nmb—This service controls the nmbd daemon. By providing NetBIOS name service name-to-address mapping, nmbd can map requests from Windows clients for NetBIOS names so they can be resolved into IP addresses.
To share files and printers with other Linux systems with Samba, only the smb service is required. The next section describes how to start and enable the smb service.
Starting the Samba (smb) service
The smb service is what starts the smbd server and makes files and printers available from your local system to other computers on the network. As usual, services are enabled and started differently on different Linux systems. For different Linux systems, you need to find the name of the service and the correct tool to start the smbd daemon.
In Fedora and RHEL 7, to enable Samba to start when the system boots and start Samba immediately, type the following from the command line as root:
# systemctl enable smb.service
# systemctl start smb.service
# systemctl status smb.service
smb.service - Samba SMB Daemon
Loaded: loaded (/usr/lib/systemd/system/smb.service; enabled)
Active: active (running) since Sun 2014-08-31 07:23:37 EDT; 6s ago
Main PID: 4838 (smbd)
CGroup: /system.slice/smb.service
![]() 4838 /usr/sbin/smbd
4838 /usr/sbin/smbd
![]() 4840 /usr/sbin/smbd
4840 /usr/sbin/smbd
The first systemctl command enables the service, the second starts it immediately, and the third shows the status. To investigate further, notice that the service file is located at /usr/lib/systemd/system/smb.service. Look at the contents of that file:
# cat /usr/lib/systemd/system/smb.service
[Unit]
Description=Samba SMB Daemon
After=syslog.target network.target nmb.service winbind.service
[Service]
Type=notify
NotifyAccess=all
PIDFile=/run/smbd.pid
LimitNOFILE=16384
EnvironmentFile=-/etc/sysconfig/samba
ExecStart=/usr/sbin/smbd $SMBDOPTIONS
ExecReload=/usr/bin/kill -HUP $MAINPID
[Install]
WantedBy=multi-user.target
The Samba daemon process (smbd) starts up after the syslog, network, nmb, and winbind services. The /etc/sysconfig/samba file contains variables that are passed as arguments to the /usr/sbin/smbd daemon when it starts. No options are set by default for the smbd daemon (none are set for nmbd or winbindd daemons either, which can also have options entered in that file). The WantedBy line indicates that smb.service should start when the system boots up into multi-user mode (multi-user.target), which it does by default.
In RHEL 6 and earlier, you can start the Samba service as follows:
# service smb start
Starting SMB services: [ OK ]
# chkconfig smb on
# service smb status
smbd (pid 28056) is running...
# chkconfig --list smb
smb 0:off 1:off 2:on 3:on 4:on 5:on 6:off
Whether you are running your Samba server on RHEL, Fedora, or another Linux system, you can check access to the Samba server using the smbclient command (from the samba-client package). You can get basic information from a Samba server using the following command:
# smbclient -L localhost
Enter root's password: <ENTER>
Anonymous login successful
Domain=[MYGROUP] OS=[Unix] Server=[Samba 4.1.15]
Sharename Type Comment
--------- ---- -------
IPC$ IPC IPC Service
(Samba Server Version 4.1.15)
DeskJet Printer DeskJet
Jeeves Printer HP Deskjet 3050 J610 series
deskjet-5550 Printer hp deskjet 5550
Anonymous login successful
Domain=[MYGROUP] OS=[Unix] Server=[Samba 4.1.15]
Server Comment
--------- -------
Workgroup Master
--------- -------
The smbclient output allows you to see what services are available from the server. By default, anonymous login is allowed when querying the server (so I just pressed Enter when prompted for a password).
You can discern a number of things about the default Samba server setup from this output:
· The default domain (this is a Windows domain and not a DNS domain) is set to MYGROUP.
· The default server name is set to the current version of Samba, in this case Samba 4.1.15.
· All printers that are shared via the CUPS server on your Linux system are, by default, also made available from the Samba server running on that same system.
· No directories are shared yet from the server.
· There is no NetBIOS name service running yet from the Samba server.
Next, you can decide whether you want to run the NetBIOS name service on your Samba server.
Starting the NetBIOS (nmbd) name server
If no Windows domain server is running on the network, as is the case here, you can start the nmb service on the Samba host to provide that service. To start the nmb service (nmbd daemon) in Fedora or RHEL 7, type the following:
# systemctl enable nmb.service
# systemctl start nmb.service
# systemctl status nmb.service
In RHEL 6 and earlier, you would type the following to start the nmb service:
# service nmb start
# service nmb status
# chkconfig nmb on
# chkconfig --list nmb
Regardless of how the NetBIOS service was started, the nmbd daemon should now be running and ready to serve NetBIOS name-to-address mapping. Run the smbclient -L command again, followed by the IP address of the server. This time, the last few lines of the output should show information obtained from the NetBIOS server now running on the server. In this case, the last few lines looked like this:
# smbclient -L localhost
...
Server Comment
--------- -------
FEDORA21 Samba Server Version 4.1.15
Workgroup Master
--------- -------
MYGROUP FEDORA21
You can see that the new NetBIOS server's name is FEDORA21 and that it is the master server for the workgroup. To query the nmbd server for the IP address of FEDORA21, you would type the following:
# nmblookup -U localhost FEDORA21
querying FEDORA21 on 127.0.0.1
192.168.0.101 FEDORA21<00>
You should be able to see your Samba server running from the local system now. The hostname assigned to the system (in this case FEDORA21) is assigned by default.
However, if you have a firewall configured or SELinux enabled, you may not be able to fully access the Samba server from a remote system yet. The next section should help you open Samba to systems outside the local system, as well as allow some Samba features that may be turned off by SELinux.
Stopping the Samba (smb) and NetBIOS (nmb) services
To stop the smb and nmb services in Fedora or RHEL 7, you can use the same systemctl command you used to start them. You can use the same command to disable the services as well, so they do not start up again when the system boots. Here are examples of how to immediately stop the smb and nmb services:
# systemctl stop smb.service
# systemctl stop nmb.service
In RHEL 6 and earlier, you would type the following to stop the smb and nmb services:
# service smb stop
# service nmb stop
To prevent the smb and nmb services from starting the next time the system reboots, type the following commands in Fedora or RHEL 7:
# systemctl disable smb.service
# systemctl disable nmb.service
In Red Hat Enterprise Linux 6, type the following commands to disable the smb and nmb services:
# chkconfig smb off
# chkconfig nmb off
Of course, you only want to stop or disable the smb and nmb services if you no longer want to use the Samba service. If you are ready to continue to configure your Samba service, you can continue on and begin to configure your Linux security features to allow the Samba service to become available to others on your network.
Securing Samba
If you cannot access your Samba server immediately after starting it, you probably have some security work to do. Because many default installations of Linux prevent, rather than allow, access to the system, dealing with security for a service such as Samba usually has more to do with making it available than making it secure.
Here are the security features you should be aware of when configuring your Samba system:
· Firewalls—The default firewall for Fedora, RHEL, and other Linux systems prevents any access to local services from outside systems. So, to allow users from other computers to access your Samba service, you must create firewall rules that open one or more ports for selected protocols (TCP in particular).
· SELinux—Many features of Samba are designated as potentially insecure by SELinux. Because the default SELinux Booleans (on/off switches for certain features) are set to provide the least access required, you need to turn Booleans on for features such as allowing users to access their own home directories with Samba. In other words, you can configure Samba to share user home directories, but SELinux prohibits someone trying to use that feature unless you explicitly configure SELinux to allow that feature.
· Host and user restrictions—Within the Samba configuration files themselves, you can indicate which hosts and users can have access to the Samba server as a whole or to particular shared directories.
The next sections describe how to set up the security features just mentioned for Samba.
Configuring firewalls for Samba
If an iptables or firewalld firewall is configured for your system when you first install it, the firewall typically allows any requests for services from local users, but none by outside users. That's why, at the end of the installation section of this chapter, you should have been able to test that Samba was working using the smbclient command from the local system. However, if the request originated from another system, it would have been rejected.
Configuring firewall rules for Samba consists mainly of opening up incoming ports that the smbd and nmbd daemons are listening on. These are the ports you should open to get a working Samba service on your Linux system:
· TCP port 445—This is the primary port the Samba smbd daemon listens on. Your firewall must support incoming packet requests on this port for Samba to work.
· TCP port 139—The smbd daemon also listens on TCP port 139, to handle sessions associated with NetBIOS hostnames. It is possible to use Samba over TCP without opening this port, but it is not recommended.
· UDP ports 137 and 138—The nmbd daemon uses these two ports for incoming NetBIOS requests. If you are using the nmbd daemon, these two ports must be open for new packet requests for NetBIOS name resolution.
For Fedora and RHEL 7, allowing incoming access to those four ports is easy. Simply open the Firewall Configuration window, and select the check boxes next to the samba and samba-client entries on the public zone, Services tab. Those ports become immediately accessible (no restart of the firewalld service is required).
For earlier Fedora and RHEL systems that use iptables directly instead of the firewalld service, opening the firewall is a more manual process. Consider a default firewall from Fedora that allows incoming packets from the local host, from established connections, and related to established connections, but denies all other incoming packets. The following example represents a set of firewall rules in the /etc/sysconfig/iptables file, with four new rules (highlighted in the example that follows) added to open ports for Samba:
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-I INPUT -m state --state NEW -m udp -p udp --dport 137 -j ACCEPT
-I INPUT -m state --state NEW -m udp -p udp --dport 138 -j ACCEPT
-I INPUT -m state --state NEW -m tcp -p tcp --dport 139 -j ACCEPT
-I INPUT -m state --state NEW -m tcp -p tcp --dport 445 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
Your firewall may include additional rules to allow incoming packet requests for other services, such as Secure Shell (sshd) or web (httpd) services. You can leave those in place. The main point is to have your Samba rules placed somewhere before the final REJECTrules.
If your iptables firewall is enabled, you can restart it to have the new rules take effect. To do that, type systemctl restart iptables.service (in older Fedora systems) or service restart iptables (in RHEL 6 or earlier). Try connecting to the Samba service by using thesmbclient command again, or by using other techniques described in the section “Accessing Samba Shares” later in this chapter.
See Chapter 25, “Securing Linux on a Network,” for more information on using iptables.
Configuring SELinux for Samba
There are both file context and Boolean considerations related to using Samba with SELinux in Enforcing mode. File contexts must be properly set on a directory that is shared by Samba. Booleans allow you to override the secure-by-default approach to certain Samba features.
You can find information on how SELinux confines Samba on the samba_selinux man page (man samba_selinux). You must install the selinux-policy-devel package to get that man page. For a deeper understanding of SELinux, refer to Chapter 24, “Enhancing Linux Security with SELinux.”
Setting SELinux Booleans for Samba
There are several ways to see the Booleans associated with Samba. In Fedora and RHEL, you could install the policycore-utils-gui package and run the system-config-selinux command. On the SELinux Administration window that appears, select Booleans from the left column and look for Booleans listed with the samba module.
Another way to list Booleans for Samba is to use the semanage command, as follows:
# semanage boolean -l | egrep "smb|samba"
The following is a list of SELinux Booleans that apply to Samba and their descriptions. The first Boolean allows you to leave SELinux in Enforcing mode, but prevents SELinux from restricting scripts the Samba server can run. All others set which files and directories the Samba server can read and write on behalf of Samba users:
· samba_run_unconfined—Allows samba to run unconfined scripts.
· smbd_anon_write—Allows Samba to let anonymous users modify public files used for public file transfer services. Files and directories must be labeled public_content_rw_t.
· samba_enable_home_dirs—Allows Samba to share users' home directories.
· samba_export_all_ro—Allows Samba to share any file and directory read-only.
· use_samba_home_dirs—Allows a remote Samba server to access home directories on the local machine.
· samba_create_home_dirs—Allows Samba to create new home directories (for example, via PAM).
· samba_export_all_rw—Allows Samba to share any file or directory read/write.
The following Booleans affect Samba's ability to share directories that are themselves mounted from other remote services (such as NFS) or to act as a Windows domain controller:
· samba_share_fusefs—Allows Samba to export ntfs/fusefs volumes.
· samba_share_nfs—Allows Samba to export NFS volumes.
· samba_domain_controller—Allows Samba to act as the domain controller, add users and groups, and change passwords.
The setsebool command is used to turn the SELinux Booleans on or off. Used with the -P option, setsebool sets the Boolean you indicate permanently. For example, to allow Samba to share any file or directory with read-only permission from the server, you could type the following from a shell as root user:
# setsebool -P samba_export_all_ro on
# getsebool samba_export_all_ro
samba_export_all_ro --> on
The setsebool command sets the Boolean, in this case to on. The getsebool lets you see the value of the Boolean.
Setting SELinux file contexts for Samba
SELinux confines the files that the Samba service can access. Instead of allowing any file with the proper read and write permission to be shared by the Samba server, SELinux (when in Enforcing mode) requires that files and directories have the correct file contexts set on them before the Samba service can even see that the files exist.
In order for the Samba service to function with SELinux immediately, some files and directories come preset with the proper file contexts. For example, Samba configuration files (/etc/samba/*), log files (/var/log/samba/*), and libraries (/var/lib/samba/*) have rules assigned to ensure they get the proper file contexts. To find files and directories associated with the Samba service and smbd daemon that have file contexts preset, run the following:
# semanage fcontext -l | grep -i samba
# semanage fcontext -l | grep -i smb
The file context portion that you are interested in ends with _t: for example, samba_etc_t, samba_log_t, and smbd_var_t, for the /etc/samba, /var/log/samba, and /var/lib/samba directories, respectively.
You may find that you need to change file contexts—for example, when you put files in nonstandard locations (such as moving the smb.conf file to /root/smb.conf) or when you want to share a directory (other than home directories, which can be turned on by setting a Boolean). Unlike the vsftpd (FTP) and httpd (web) servers that come with Linux, Samba has no default shared content directories (those just mentioned used /var/ftp and /var/www/html).
You can change a file context permanently by creating a new file context rule and then applying that rule to the file or directory for which it is intended. You can do that with the semanage command (to make the rule) and restorecon command (to apply the rule). For example, if you wanted to share a directory, /mystuff, you would create that directory with the proper permissions and run the following command to make it available for read/write access from Samba:
# semanage fcontext -a -t samba_share_t "/mystuff(/.*)?"
# restorecon -v /mystuff
After those commands are run, the /mystuff directory, along with any files and directories below that point, have the file context of samba_share_t. It is then up to you to assign the correct Linux ownership and file permissions to allow access to the users you choose. The section “Configuring Samba” provides an example of creating a share and shows you how to add permissions and ownership to a shared directory using standard Linux commands.
Configuring Samba host/user permissions
Within the smb.conf file itself, you can allow or restrict access to the entire Samba server or to specific shares based on the hosts or user trying to gain access. You can also restrict access to the Samba server by providing the service only on particular interfaces.
For example, if you have one network interface card connected to the Internet and another connected to the local network, you can tell Samba to serve requests only on the local network interface. The next section describes how to configure Samba, including how to identify which hosts, users, or network interfaces can access your Samba server.
Configuring Samba
Most Samba configuration is done in the /etc/samba/smb.conf file. As you configure your Samba server, you can also add host information to the lmhosts file.
To configure smb.conf, you can use a plain-text editor. However, Fedora has a graphical interface for configuring Samba (system-config-samba). The next sections step through how to use the graphical interfaces to configure Samba. After that, you look at the resultingsmb.conf file.
Using system-config-samba
On Fedora systems, you can install the system-config-samba package to use the Samba Server Configuration window to configure Samba. From that window, you can configure basic server settings, add shares, and set up user accounts so people can access those shares. If you have not already installed system-config-samba, type the following as root at the command line:
# yum install system-config-samba*
With system-config-samba and system-config-samba-docs packages installed, you can launch it from Fedora from the Applications page by double-clicking the Samba icon. Or you could just type the following from the shell:
# system-config-samba &
The Samba Server Configuration window should appear on your desktop. You can now configure your basic Samba server and begin adding shared directories.
Choosing Samba server settings
From the Samba Server Configuration window, you should first set your basic settings and the type of authentication you are using. Start by selecting Preferences ![]() Server Settings. The Server Settings pop-up window appears, as shown in Figure 19.1.
Server Settings. The Server Settings pop-up window appears, as shown in Figure 19.1.
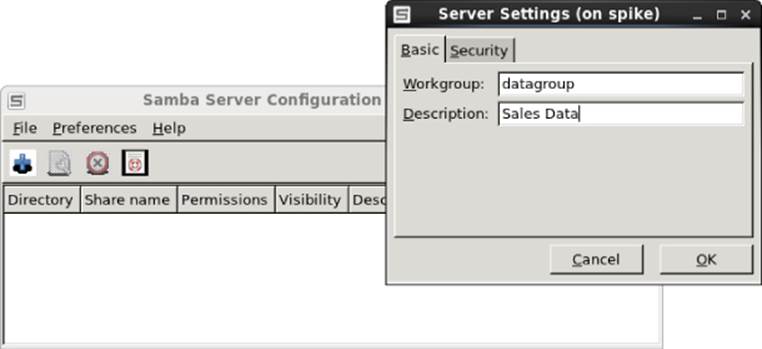
Figure 19.1 Choose basic Samba server settings.
In this example, the name of the Workgroup is changed to datagroup and Sales Data is set as the Description. Next, select the Security tab. The default Authentication mode is User, which means that Samba (Windows) usernames are mapped into real user accounts on the Linux system. No outside systems are contacted to authenticate users.
Encrypted passwords are used by default. Also by default, there is no guest account. If you would like to have an unauthenticated guest account that can access your Samba server, click the box that says No guest account, and choose which Linux user is assigned to the guest user. For example, if you assigned joe to the guest account, the user account joe would need to have access to a shared directory or file for a guest user to access it. Figure 19.2 shows an example of the Security settings.
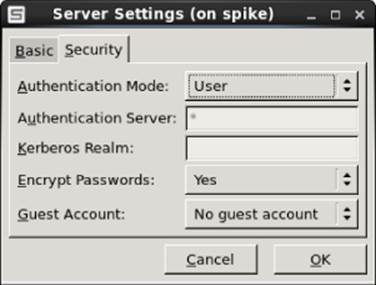
Figure 19.2 Choose Samba server security settings.
Configuring Samba user accounts
If you are using the default User type of authentication, as I am here, you can configure user accounts to access your Fedora system by selecting Preferences ![]() Samba Users. At first, there are no Samba users listed. To add a Samba user, select Add User from the Samba Users window.
Samba Users. At first, there are no Samba users listed. To add a Samba user, select Add User from the Samba Users window.
From the Create New Samba User screen that pops up, select the local Linux user account (UNIX Username) from the drop-down box. You can use the same name or a different one for the Windows Username. Then fill in the Samba password for that user, and select OK. Figure 19.3 shows you how to create a new Samba user named chris that has the same permission the Linux user chris has to access the system.
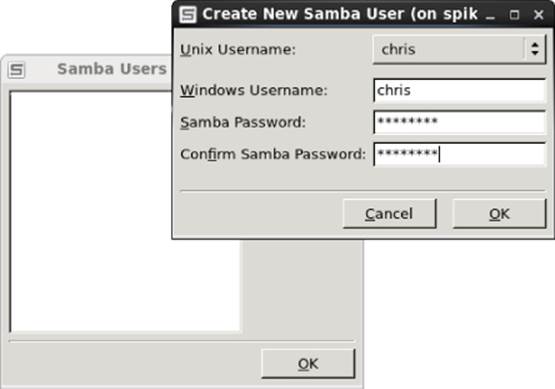
Figure 19.3 Add user accounts to your Samba server.
You can configure as many users as you like from your Linux user accounts to grant them access to files and directories via your Samba server. With the basic system and user settings in place, you can start creating shared directories.
Creating a Samba shared folder
Before you can create a shared folder, that folder (directory) must exist and have the proper permissions set. In this example, the /var/salesdata directory is shared. You want the data to be writable by the user named chris but visible to anyone on your network. To create that directory and set the proper permissions and SELinux file contexts, type the following as root user:
# mkdir /var/salesdata
# chmod 775 /var/salesdata
# chown chris:chris /var/salesdata
# semanage fcontext -a -t samba_share_t /var/salesdata
# restorecon -v /var/salesdata
Next, from the Samba Server Configuration window, select File ![]() Add Share. The Create Samba Share window appears. Start by filling in the folder name (select Choose to browse for it), a name to represent the share, and a description. Then you want to choose whether you want to let anyone write to it and whether you want the existence of the share to be visible to anyone. Figure 19.4 shows an example of this window.
Add Share. The Create Samba Share window appears. Start by filling in the folder name (select Choose to browse for it), a name to represent the share, and a description. Then you want to choose whether you want to let anyone write to it and whether you want the existence of the share to be visible to anyone. Figure 19.4 shows an example of this window.
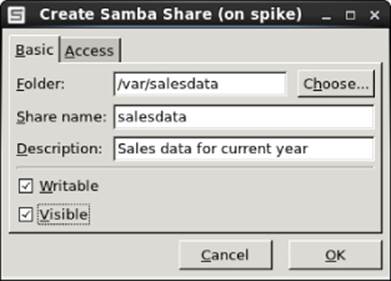
Figure 19.4 Choose the folder and name of the new share.
After filling in the Basic information, select the Access tab. Any Samba user you have created to this point appears in the Access tab. Put a check mark next to any user you want to allow to access this shared directory. Because I assigned ownership to chris and left read/write permissions open to chris, the user chris can read from and write to that directory via Samba. Figure 19.5 shows an example of the Access settings for the share.
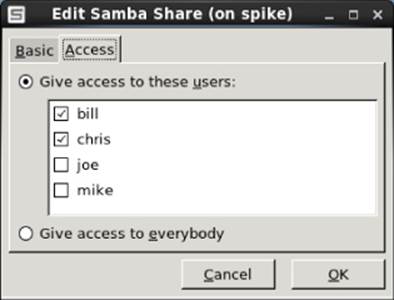
Figure 19.5 Set access to the new share.
Select OK when you are finished configuring the share. Next you want to test that the share is available.
Checking the Samba share
For the changes to your Samba configuration to take effect, you need to restart the smb service. After that is done, check that the Samba share you created is available and that any user you assigned to the share can access it. To do those things, type the following as root user from a shell on the Samba server:
# systemctl restart smb.service
# smbclient -L localhost
Enter root's password: <ENTER>
Anonymous login successful
Domain=[DATAGROUP] OS=[Unix] Server=[Samba 4.1.15]
Sharename Type Comment
--------- ---- -------
salesdata Disk Sales data for current year
IPC$ IPC IPC Service (Samba Server Version 4.1.15))
Anonymous login successful
Domain=[DATAGROUP] OS=[Unix] Server=[Samba 4.1.15]
...
Here you can see the share name (salesdata), the Domain set to the workgroup name DATAGROUP, and the description entered earlier (Sales data for current year). Next, a quick way to test access to the share is to use the smbclient command. You can use the hostname or IP address with smbclient to access the share. Because I am on the local system in this example, I just use the name localhost and the user I added (chris):
# smbclient -U chris //localhost/salesdata
Enter chris's password: ********
Domain=[DATAGROUP] OS=[Unix] Server=[Samba 4.1.15]
smb: \> lcd /etc
smb: \> put hosts
putting file hosts as \hosts (43.5 kb/s) (average 43.5 kb/s)
smb: \> ls
. D 0 Sun Oct 23 09:52:51 2014
.. D 0 Sun Oct 23 09:11:50 2014
hosts A 89 Sun Oct 23 09:52:51 2014
39941 blocks of size 524288. 28197 blocks available
smb: \> quit
A Samba share is in the form //host/share or \\host\share. However, when you identify a Samba share from a Linux shell in the latter case, backslashes need to be escaped. So, as an argument, the first example of the share would have to appear as\\\\localhost\\salesdata. So the first form is easier to use.
NOTE
Escaping a character that you type from the shell is done by putting a backslash (\) in front of that character. It tells the shell to use the character following the backslash literally, instead of giving the character a special meaning to the shell. (The * and ? characters are examples of characters with special meaning.) Because the backslash itself has special meaning to the shell, if you want to literally use a backslash, you need to precede it with a backslash. That is why, when you want to type a Samba address that includes two backslashes, you have to actually enter four backslashes.
When prompted, enter the Samba password for that user (it may be different from the Linux user's password). You see the smb: \> prompt after that.
At this point, you have a session open to the Samba host that is similar to an lftp session for traversing an FTP server. The lcd /etc command makes /etc the current directory on the local system. The put hosts command uploads the hosts file from the local system to the shared directory. Typing ls shows that the file exists on the server. The quit command ends the session.
Instead of configuring the server, users, and shares with the system-config-samba window, in some Linux systems you could use the samba-swat web-based interface or edit the smb.conf file directly. The next section shows you how to use the smb.conf file directly to configure Samba.
Configuring Samba in the smb.conf file
Inside the /etc/samba/smb.conf file are settings for configuring your Samba server, defining shared printers, configuring how authentication is done, and creating shared directories. The file consists of the following predefined sections:
· [global]—Settings that apply to the Samba server as a whole are placed in this section. This is where you set the server's description, its workgroup (domain), the location of log files, the default type of security, and other settings.
· [homes]—This section determines whether users with accounts on the Samba server can see their home directories (browseable) or write to them (writable).
· [printers]—In this section, settings tell Samba whether to make printers available through Samba that are configured for Linux printing (CUPS).
Inside the smb.conf file, many sections are commented out by the lines beginning with semicolons (;). Removing the semicolons enables you to quickly set up different kinds of shared information. The other information illustrated in the smb.conf file in the next sections reflects the same Samba configuration I added during the system-config-samba procedure.
Keep in mind that you don't have to use any graphical interface at all when configuring Samba. You can simply edit the smb.conf file directly, using the techniques described in this section. Editing smb.conf directly is the most common way to configure Samba on a Red Hat Enterprise Linux server that has no graphical desktop interface installed.
Configuring the [global] section
If you look at the [global] section of the smb.conf file, you can see that some settings were modified and others are commented out, ready for you to modify as you like:
[global]
workgroup = datagroup
server string = Sales Data
; netbios name = MYSERVER
; interfaces = lo eth0 192.168.12.2/24 192.168.13.2/24
; hosts allow = 127. 192.168.12. 192.168.13.
log file = /var/log/samba/log.%m
max log size = 50
security = user
cups options = raw
The workgroup (also used as the domain name) is set to datagroup in this example. When a client communicates with the Samba server, this name tells the client which workgroup the Samba server is in. Any value set for the server string is used later to fill in comment values presented next to IPC lines and in the printer comment box when that information is presented to client applications.
By default, your server's DNS hostname (type hostname to see what it is) is used as your Samba server's NetBIOS name as well. You can override that and set a separate NetBIOS name by uncommenting the netbios name line and adding the server name you want. For example: netbios name = myownhost. localhost is used as your NetBIOS name if it has not been otherwise set.
As the log file value is set, logs associated with Samba activity are written to /var/log/samba/log.%m, where %m represents the name or IP address of the system contacting the Samba server. This makes it easy to debug problems associated with requests from a particular system because each client is assigned its own log file.
The max log size limits the size of each log file to a set number of kilobytes (50KB by default). After that size is exceeded, Samba copies the file to a log file of the same name with a .old appended to it. The default security type is set to user (Samba usernames and passwords), and cups options lets you pass any options you like to the CUPS printers served by your Samba server. By default, only raw is set, which allows Windows clients to use their own print drivers. Printers on your Samba server print the pages they are presented in raw form.
Several options are commented out that you can consider setting. Setting the netbios name causes the name you set to be used as the hostname for the Samba service. If this is not set, the host portion of the system's fully qualified domain name is used as the hostname.
If you want to restrict access to the Samba server so it only responds on certain interfaces, you can uncomment the interfaces line and add either the IP address or name (lo, eth0, eth1, and so on) of the network interfaces you want.
You can restrict access to the Samba server to specific hosts as well. Uncomment the hosts allow line (remove the semicolon), and insert the IP addresses of the hosts you want to allow. To enter a range of addresses, simply end the subnetwork portion of the address, followed by a dot. For example, 127. is associated with IP addresses that point to the local host. The 192.168.12. entry matches all IP addresses from 192.168.12.1 to 192.168.12.254.
Configuring the [homes] section
The [homes] section is configured, by default, to allow any Samba user account to be able to access its own home directory via the Samba server. The browseable = no setting prevents the Samba server from displaying the availability of the shared home directories. Users who can provide their own Samba usernames and passwords can read and write in their own home directories (writable = yes). Here is what the default homes entry looks like:
[homes]
comment = Home Directories
browseable = no
writable = yes
; valid users = %S
; valid users = MYDOMAIN\%S
Notice that two examples of valid users entries are commented out. With this value not set (as it is by default), any valid users can log in to Samba. Setting it to %S substitutes the current service name, which allows any valid users of the service. You can also limit user access by indicating that only a particular workgroup (domain) name can be used to match users requesting this service.
If, after starting the smb service, you cannot log in using a valid user account, you may need to change some security features on your system. On Fedora and RHEL systems, in particular, SELinux features need to be changed to allow users to access their home directories if you are in SELinux Enforcing mode.
For example, if you tried to use smbclient to log in to your home directory, the login would succeed, but when you tried to list the contents of the home directory, you might see the following message:
NT_STATUS_ACCESS_DENIED listing \*
To tell SELinux to allow Samba users to access their home directories as Samba shares, turn on the samba_enable_home_dirs Boolean by typing the following as root from a shell:
# setsebool -P samba_enable_home_dirs on
The setsebool command turns on the capability of Samba to share home directories (which is off by default). The form for using the smbclient command to check access to the user's home directory, again for the user chris, would be the following (replacing the IP address with the name or address of your Samba server):
$ smbclient -U chris //192.168.0.119/chris
Enter chris's password:
Domain=[DATAGROUP] OS=[Unix] Server=[Samba 4.1.15]
smb: \> ls file.txt
file.txt 149946368 Sun Dec 7 09:28:53 2014
39941 blocks of size 524288. 28191 blocks available
The main point to remember is that, even though the share is not browseable, you can request it by giving the Samba server's hostname or IP address, followed by the user's name (here, chris), to access the user's home directory.
Configuring the [printers] section
Any printer that you configure for CUPS printing on your Linux system is automatically shared to others over Samba, based on the [printers] section that is added by default. The global cups options = raw setting makes all printers raw printers (meaning that the Windows client needs to provide the proper printer driver for each shared printer).
Here's what the default printers section looks like in the smb.conf file:
[printers]
comment = All Printers
path = /var/spool/samba
browseable = no
; guest ok = no
; writable = No
printable = yes
The printable = yes line causes all your CUPS printers on the local system to be shared by Samba. Printers are writable and allow guest printing by default. You can uncomment the guest ok = no line and the writable = No line, respectively, to change those settings.
To see that those printers are available, you could run the smbclient -L command from a Linux system, as shown earlier. On a Windows system, you can select Network from the Windows Explorer file manager window and select the icon representing your Samba server. All shared printers and folders appear in that window. (See the section “Accessing Samba Shares” later in this chapter for details on viewing and using shared printers.)
Creating custom shared directories
With the basic configuration of your Samba server in place, you can begin creating custom sections to share specific printers and folders and secure them as you choose. For the first example, here is what the share created in the system-config-samba demonstration earlier in this chapter (called salesdata) looks like in the smb.conf file:
[salesdata]
comment = Sales data for current year
path = /var/salesdata
read only = no
; browseable = yes
valid users = chris
Before creating this share, the /var/salesdata directory was created, with chris assigned as the user and group, and the directory was set to be readable and writable by chris. (The SELinux file context must also be set, if SELinux is in Enforcing mode.) The Samba username chris must be presented along with the associated password to access the share. After chris is connected to the share, chris has read and write access to it (read only = no).
Now that you have seen default settings for Samba and an example of a simple shared directory (folder), read the next few sections to see how to further configure shares. In particular, the examples demonstrate how to make shares available to particular users, hosts, and network interfaces.
Restricting Samba access by network interface
To restrict access to all your shares, you can set the global interfaces setting in the smb.conf file. Samba is designed more for local file sharing than sharing over wide area networks. If your computer has a network interface connected to a local network and one connected to the Internet, consider allowing access only to the local network.
To set which interfaces Samba listens on, uncomment the interfaces line in the [global] section of the smb.conf file. Then add the interface names or IP address ranges of those computers you want to allow access to your computer. Here is an example:
interfaces = lo 192.168.22.15/24
This interfaces entry allows access to the Samba service to all users on the local system (lo). It also allows access to any systems on the 192.168.22 network. See the smb.conf man page's description of different ways of identifying hosts and network interfaces.
Restricting Samba access by host
Host access to the Samba server can be set for the entire service or for single shares. The syntax used is similar to that of the hosts.allow and hosts.deny files in the TCP wrappers feature. Here, however, hosts allow and hosts deny entries are added directly to thesmb.conf file.
Here are some examples of hosts allow and hosts deny entries:
hosts allow = 192.168.22. EXCEPT 192.168.22.99
hosts allow = 192.168.5.0/255.255.255.0
hosts allow = .example.com market.example.net
hosts deny = evil.example.org 192.168.99.
These entries can be put in the [global] section or in any shared directory section. The first example allows access to any host in the 192.168.22. network, except for 192.168.22.99, which is denied. Note that a dot is required at the end of the network number. The 192.168.5.0/255.255.255.0 example uses netmask notation to identify 192.168.5 as the set of addresses that are allowed.
In the third line of the sample code, any host from the .example.com network is allowed, as is the individual host market.example.net. The hosts deny example shows that you can use the same form to identify names and IP addresses to prevent access from certain hosts.
Restricting Samba access by user
Particular Samba users and groups can be allowed access to specific Samba shares by identifying those users and groups within a share in the smb.conf file. Aside from guest users, which you may or may not allow, the default user authentication for Samba requires you to add a Samba (Windows) user account that maps into a local Linux user account.
To allow a user to access the Samba server, you need to create a password for the user. Here is an example of how to add a Samba password for the user jim:
# smbpasswd -a jim
New SMB password: *******
Retype new SMB password: *******
After running that smbpasswd command, jim can use that username and password to access the Samba server. The /var/lib/samba/private/passdb.tdb file holds the password just entered for jim. After that, the user jim can change the password by simply typing smbpasswdwhen he is logged in. The root user can change the password by rerunning the command shown in the example, but dropping the -a option.
If you wanted to give jim access to a share, you could add a valid users line to that shared block in the smb.conf file. For example, to provide both chris and jim access to a share, you could add the following line:
valid users = jim, chris
If the read only option is set to no for the share, both users could potentially write files to the share (depending on file permissions). If read only is set to yes, you could still allow access to jim and chris to write files by adding a write list line as follows:
write list = jim, chris
The write list can contain groups (that is, Linux groups contained in the /etc/group file) to allow write permission to any Linux user that belongs to a particular Linux group. You can add write permission for a group by putting a plus (+) character in front of a name. For example, the following adds write access for the market group to the share with which this line is associated:
write list = jim, chris, +market
There are many ways to change and extend the features of your shared Samba resources. For further information on configuring Samba, be sure to examine the smb.conf file itself (which includes many useful comments) and the smb.conf man page.
Accessing Samba Shares
After you have created some shared directories in Samba, many client tools are available in both Linux and Windows for accessing those shares. Command-line tools in Linux include the smbclient command, demonstrated earlier in this chapter. For graphical means of accessing shares, you can use the file managers available in both Windows (Windows Explorer) and Linux (Nautilus, with the GNOME desktop).
Accessing Samba shares in Linux
Opening a file manager in Linux can provide you access to the shared directories from Linux (Samba) and Windows (SMB). How you access the file manager is different on different Linux desktops. In GNOME 3, you can click the Files icon. In other desktops, open the Home folder.
With the Nautilus window manager displayed, look for a Connect to Server selection in the left pane or (in some versions of Nautilus) select File ![]() Connect to Server. In Fedora 21, the Connect to Server window should appear as shown in Figure 19.6.
Connect to Server. In Fedora 21, the Connect to Server window should appear as shown in Figure 19.6.
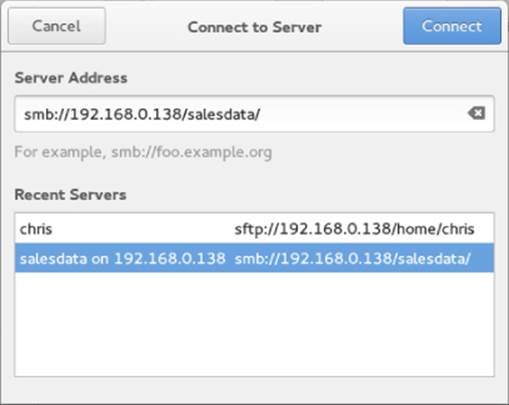
Figure 19.6 Identify a Samba share from the Nautilus Connect to Server window.
Fill in the address of a Samba share you want to access and click Connect. In the example, the salesdata share was chosen. If required, you are prompted for a username, domain, and password. Enter that information and click Connect.
If the user and password are accepted, you should see the contents of the remote directory. If you have write access to the share, you can open another Nautilus window and drag and drop files between the two systems. Figure 19.7 shows an example of the Nautilus window after I have connected to the salesdata share.
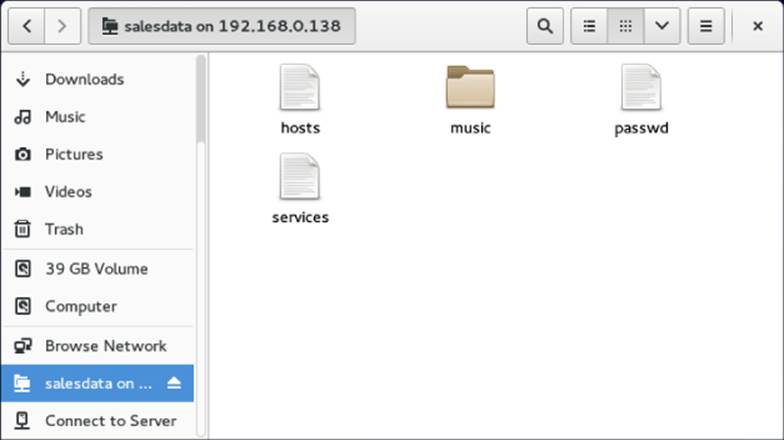
Figure 19.7 Opening Samba shares from Connect to Server in Nautilus.
Because a Samba shared directory can be viewed as a remote filesystem, you can use common Linux tools to connect a Samba share (temporarily or permanently) to your Linux system. Using the standard mount command, you can mount a remote Samba share as a CIFS filesystem in Linux. This example mounts the salesdata share from the host at IP address 192.168.0.119 on the local directory /mnt/sales:
# mkdir /mnt/sales
# mount -t cifs -o user=chris,password=mypass \
//192.168.0.119/salesdata /mnt/sales
Password: *******
# ls /mnt/sales
hosts services
When prompted, enter the Samba password for chris. Given that the user chris in this example has read-write permission to the shared directory, users on your system should be able to read and write to the mounted directory. Regardless of who saves files on the shared directory, on the server those files are owned by the user chris. This mount lasts until the system is rebooted or you run the umount command on the directory. If you want the share to be mounted permanently (that is, every time the system boots up) in the same location, you can do some additional configuration. First, open the /etc/fstab file and add an entry similar to the following:
//192.168.0.119/salesdata /mnt/sales cifs credentials=/root/
cif.txt 0 0
Next, create a credentials file (in this example, /root/cif.txt). In that file, put the name of the user and the user's password you want to present when the system tries to mount the filesystem. Here is an example of the contents of that file:
user=chris
pass=mypass
Before you reboot to check that the entry is correct, try mounting it from the command line. A mount -a command tries to mount any filesystem listed in the /etc/fstab file that is not already mounted. The df command shows information about disk space for the mounted directory. For example:
# mount -a
# df -h /mnt/sales
Filesystem Size Used Avail Ues% Mounted on
//192.168.0.119/salesdata 20G 5.7G 14G 30% /mnt/sales
You should now be able to use the shared Samba directory as you do any directory on the local system.
Accessing Samba shares in Windows
As with Linux, you can access Samba shares from the file manager window, in this case Windows Explorer. To do this, open any folder in Windows, and select Network from the left panel. An icon representing the Samba server should appear on the screen. Click that icon, and enter a password if prompted for one. You should see all shared printers and folders from that server (see Figure 19.8).
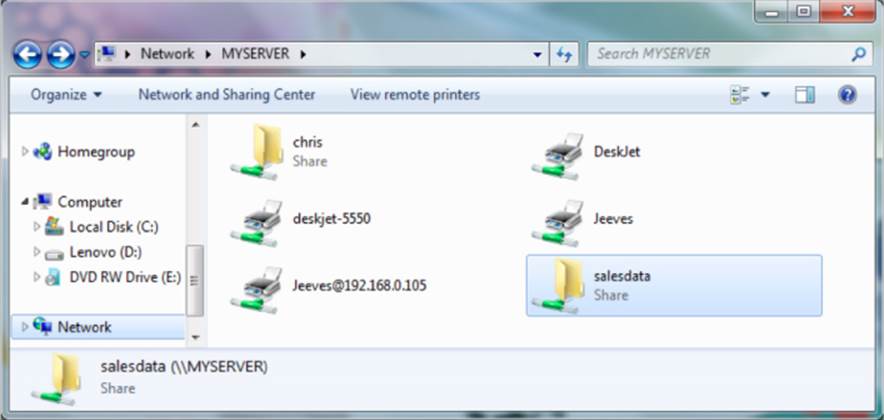
Figure 19.8 Accessing Samba shares from Windows.
In Figure 19.8, you can see that there are two shared folders (directories): chris and salesdata. There are also several shared printers. To use the folders, double-click them and enter the required authentication information. Because printers are set up to use raw drivers by default, you need to obtain Windows drivers to use any of the Samba printers.
Using Samba in the Enterprise
Although beyond the scope of this book, Windows file and printer sharing via Samba servers is a very popular application in large enterprises. Despite the fact that Linux has made huge inroads in the enterprise-quality server market, Microsoft Windows systems are still the predominant systems used on the desktop.
The major features needed to integrate Samba servers into a large enterprise with many Microsoft Windows desktops are related to authentication. Most large enterprises use Microsoft Active Directory Services (ADS) servers for authentication. On the Linux side, that means configuring Kerberos on the Linux system and using ADS (instead of user) for the type of security in the smb.conf file.
The advantage of central authentication is that users have to remember only one set of credentials throughout the enterprise, and system administrators need to manage fewer user accounts and passwords. If you are interested in investigating this subject further, I recommend you read the Samba & Active Directory page on the wiki at Samba.org:
http://wiki.samba.org/index.php/Samba_&_Active_Directory
Summary
Because of the popularity of Windows desktops, Samba servers have become popular for sharing files and printers among Windows and Linux systems. Samba provides a way to interoperate with Windows systems by implementing the Server Message Block (SMB) or Common Internet File (CIFS) protocol for sharing resources over a network.
This chapter stepped through the process of installing, starting, securing, configuring, and accessing Samba servers on a Linux system. Both graphical and command-line tools can be used to both set up a Samba server and get to it from Linux and Windows systems.
The next chapter describes the Network File System (NFS) facility. NFS is the native Linux facility for sharing and mounting filesystems over networks with other Linux and UNIX systems.
Exercises
The exercises in this section describe tasks related to setting up a Samba server in Linux and accessing that server using a Samba client. As usual, there are often several ways to accomplish some of the tasks here. So don't worry if you don't go about the exercises in exactly the same way as shown in the answers, as long as you get the same results. See Appendix B for suggested solutions.
Don't do these exercises on a Linux system running a Samba server because they will almost certainly interfere with that server. These exercises were tested on a Fedora system. Some of the steps might be slightly different on another Linux system.
1. Install the samba and samba-client packages.
2. Start and enable the smb and nmb services.
3. Set the Samba server's workgroup to TESTGROUP, the netbios name to MYTEST, and the server string to Samba Test System.
4. Add a Linux user named phil to your system, and add a Linux password and Samba password for phil.
5. Set the [homes] section so that home directories are browseable (yes) and writable (yes), and phil is the only valid user.
6. Set any SELinux Boolean that is necessary to make it so phil can access his home directory via a Samba client.
7. From the local system, use the smbclient command to list that the homes share is available.
8. From a Nautilus (file manager) window on the local system, connect to the homes share for the user phil on the local Samba server in a way that allows you to drag and drop files to that folder.
9. Open up the firewall so anyone who has access to the server can access the Samba service (smbd and nmbd daemons).
10.From another system on your network (Windows or Linux), try to open the homes share again as the user phil and again make sure you can drag and drop files to it.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2025 All site design rights belong to S.Y.A.