A practical guide to Fedora and Red Hat Enterprise Linux, 7th Edition (2014)
Part IV: Using Clients and Setting Up Servers
Chapter 23. Samba: Linux and Windows File and Printer Sharing
In This Chapter
Introduction to Samba
smbpasswd and pdbedit: Work with Samba Users and Passwords
Running Samba Clients
Setting Up a Samba Server
JumpStart: Configuring a Samba Server Using system-config-samba (Fedora)
smb.conf: Manually Configuring a Samba Server
Troubleshooting
Objectives
After reading this chapter you should be able to:
![]() Describe the use, history, and components of Samba
Describe the use, history, and components of Samba
![]() List capabilities of the Samba server
List capabilities of the Samba server
![]() Use a variety of Samba client tools
Use a variety of Samba client tools
![]() Describe Samba authentication methods
Describe Samba authentication methods
![]() Configure a Samba share for local accounts
Configure a Samba share for local accounts
![]() Troubleshoot Samba connections
Troubleshoot Samba connections
Samba is a suite of programs that enables UNIX-like operating systems, including Linux, Solaris, FreeBSD, and Mac OS X, to share files and printers with other operating systems, such as OS/2 and Windows, as both a server and a client.
As a server, Samba shares Linux files and printers with Windows systems. As a client, Samba gives Linux users access to files and printers on Windows systems. Its ability to share files across operating systems makes Samba an ideal tool in a heterogeneous computing environment.
Refer to pages 574 and 576 for information about printing to and from a Windows machine using CUPS and Samba.
Introduction to Samba
This chapter starts by providing a list of Samba tools followed by some basic information about Samba. The section on Samba clients explains how to use Samba to work with files and printers on a remote system. The next section describes three ways to configure a Samba server. First, a JumpStart section explains how to use the system-config-samba GUI (Fedora only) to set up a Samba server. The next sections cover using a text editor to edit Samba configuration files. The final section, “Troubleshooting” on page 846, offers tips on what to do when Samba does not work properly.
Table 23-1 lists some of the utilities and daemons that make up the Samba suite of programs. See the samba man page for a complete list.
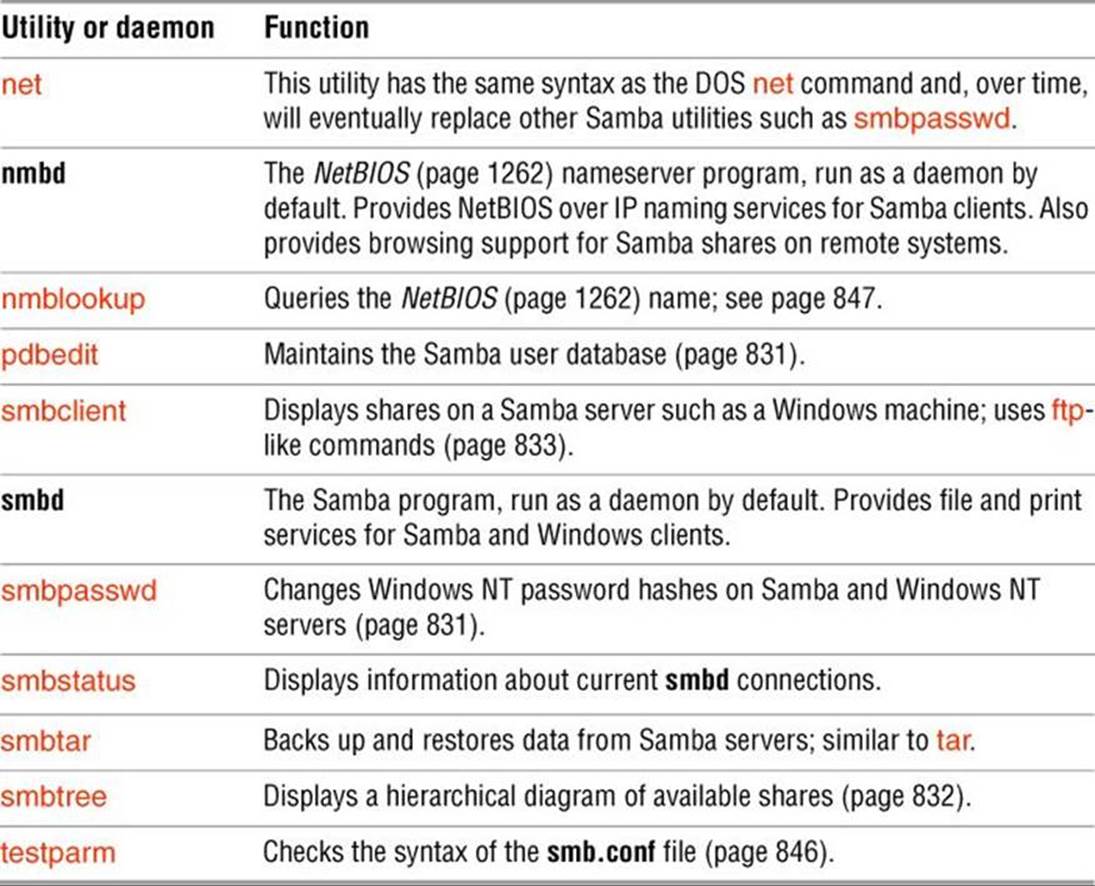
Table 23-1 Samba utilities and daemons
More Information
Web
Samba: www.samba.org (mailing lists, documentation, downloads, and more)
HOWTO
Unofficial Samba HOWTO: www.oregontechsupport.com/samba.
Notes
Client firewall
The Samba clients normally use UDP ports 137 and 138. If the client is running a firewall or is behind a firewall, you need to open these ports. Give the following commands to open the ports each time the system boots (permanently) and on the running system; see page 906 for information on firewall-cmd.
# firewall-cmd --add-port=137/udp
# firewall-cmd --permanent --add-port=137/udp
# firewall-cmd --add-port=138/udp
# firewall-cmd --permanent --add-port=138/udp
Share
Under Samba and Windows, an exported directory hierarchy is called a share.
Mapping a share
The Samba/Windows term mapping a share is equivalent to the Linux term mounting a directory hierarchy.
Samba
The name Samba is derived from SMB (page 1273), the protocol that is the native method of file and printer sharing for Windows. Also CIFS (next).
CIFS
CIFS (page 1242) is an Internet filesystem protocol based on SMB (previous). The terms SMB and CIFS are used interchangeably.
Printing
Using CUPS to print on a printer connected to a Linux system is easier and can be made more secure than using Samba to print from Windows. For more information refer to “Printing from Windows” on page 574.
Troubleshooting
If the server does not work properly, see “Troubleshooting” on page 846.
Samba Users, User Maps, and Passwords
Authentication
For a Windows user to access Samba services on a Linux system, the user must provide a Windows username and a Samba password. In some cases, Windows supplies the username and password for you. Alternately, you can log in as the user named guest (the Anonymous user; next page). It is also possible to authenticate using other methods. For example, Samba can use LDAP (page 1257) or PAM (page 476) instead of the default password file. Refer to the Samba documentation for more information on authentication methods.
Windows users
The username supplied by Windows must be the same as a Linux username or must map to a Linux username (see “User maps,” below).
Samba users
A Samba user must have the same name as a Linux user (the username must appear in /etc/passwd). You can use pdbedit (page 831) to display Samba users.
Samba passwords
By default, under Fedora/RHEL Samba uses Samba passwords to authenticate users. As installed, no Samba passwords exist. You can use smbpasswd (page 831) to work with Samba passwords. Each Samba user, except for nobody, must have a Samba password. See the next page for more information.
Linux passwords
By default, Linux passwords are different from Samba passwords.
No password
By default, a Windows user logging in without a password logs in as the Samba/Linux user nobody (the Anonymous user); you do not have to add this user as a Samba user. You need to add users and passwords for all other users who want to access shares on the Samba server
The user named guest
When the guest ok (page 845) parameter in the smb.conf configuration file (page 839) is set to YES and guest account (page 842) is set to nobody (default), Samba gives a Windows user logging in as guest the privileges of the Linux user named nobody. This user does not need to supply a password. The Samba user named nobody does not need to exist, but the user named nobody must appear in the /etc/passwd file. This user is referred to as the Anonymous user.
User maps
You can create a file, called a user map, that maps Windows usernames to Linux usernames. The username map (page 843) parameter in the smb.conf configuration file (page 839) specifies the location of this file. The default Samba configuration does not specify a user map. See page 838for a sample username map parameter.
A user map can map Windows usernames to Linux usernames and/or map multiple Windows usernames to a single Linux username to facilitate file sharing. Each line in a user map file starts with a server (Linux) username, followed by a SPACE, an equal sign, another SPACE, and one or moreSPACE-separated client (Windows) usernames. An asterisk (*) on the client side matches any client username. Following is an example file:
$ cat /etc/samba/smbusers
# Unix_name = SMB_name1 SMB_name2 ...
root = administrator admin
nobody = guest pcguest smbguest
The first entry maps the two Windows usernames (administrator and admin) to the Linux username root. The second entry maps three Windows usernames to the Linux username nobody.
Add the following line to the file the username map parameter points to, creating the file if necessary, to map the Windows username sam to the Linux username sls:
sls = sam
After you add a user to this file, you must give the user a password using smbpasswd (next). When Sam logs in as sam, Samba now maps sam to sls and looks up sls in the Samba password database. Assuming Sam provides the correct password, he logs in on the Samba server as sls.
smbpasswd and pdbedit: Work with Samba Users and Passwords
Samba passwords
Samba can use Linux passwords or Samba passwords to authenticate users. The passdb backend (page 842) parameter in the smb.conf (page 839) configuration file controls which type of passwords Samba uses. Setting passdb backend to tdbsam (default) causes Samba to use Samba passwords. Samba stores the passwords in a Trivial Database (tdb.sourceforge.net). Setting passdb backend to smbpasswd causes Samba to use Linux passwords that are stored in the text file named /etc/samba/smbpasswd. This section discusses how to use smbpasswd to work with Samba passwords and how to use pdbedit to display Samba users.
pdbedit
With the –L option, pdbedit displays a list of Samba users; when you install Samba, no Samba users are defined:
# pdbedit -L
#
The Samba user named nobody does not have to exist for the Windows user named guest to log in as the Anonymous user. See “The user named guest” in the preceding section for more information.
Adding a Samba user and password
As installed, no users have Samba passwords (there are no Samba users). You can add Samba users and optionally passwords only for users listed in /etc/passwd. Working with root privileges, use smbpasswd with the –a option to add a Samba user and password for a Linux user (a user listed in /etc/passwd):
# smbpasswd -a sam
New SMB password:
Retype new SMB password:
Added user sam.
The pdbedit utility shows the Samba user you just added, although it does not display password information:
# pdbedit -L
sam:1000:Sam the Great
Changing your own Samba password
Once a user has a Samba password, he can use smbpasswd without any arguments to change his password. The smbpasswd utility will display a nondescriptive error message if the new password is too simple or if the two passwords you enter do not match.
$ smbpasswd
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user sam
If a user has different usernames on the Linux and Windows systems, you must map the Windows username to a Linux username (see “User maps” on page 830). Except for the Windows user specified by the guest account (page 842), make sure all Linux users who will log in using Samba have Samba passwords.
Running Samba Clients
To run a Samba client under Linux you need to install a package and open a couple of ports on the client firewall. No Samba daemon runs on a client. Samba clients run on Linux and Windows. Under Linux you can use smbtree (page 832) to display shares, smbclient (page 833) to connect to shares in a manner similar to ftp, browse shares using Nautilus (page 833), and mount shares (page 834). Under Windows you can browse (page 835) and map (mount; page 835) shares.
Prerequisites
Install the following packages:
• samba-client (installed by default)
• samba-common (installed by default)
The samba-client package has no daemon, and therefore you do not have to run chkconfig or service when you install it.
Firewall
Open the client firewall as explained on page 829.
Usernames and passwords
You might have to set up a user and password on the server. For more information refer to “Samba Users, User Maps, and Passwords” on page 829.
Working with Shares from Linux
Samba enables you to view and work with files on a server system from a Linux system (client). This section discusses several ways of accessing Windows files from Linux.
smbtree: Displays Shares
The smbtree utility displays a hierarchical diagram of available shares. Unless you use the –N option, smbtree prompts you for a password; use the –N option or do not enter a password (just press RETURN) if you want to browse shares that are visible to the Anonymous user (browseable). The password allows you to view restricted shares, such as a user’s home directory in the [homes] share. Following is sample output from smbtree:
$ smbtree -N
MGS
\\PLUM Samba Server Version 4.0.6
\\PLUM\HL-2140-series Brother HL-2140 series
\\PLUM\tmp Temporary directory
\\PLUM\IPC$ IPC Service (Samba Server Version 4.0.6)
In the preceding output, MGS is the name of the workgroup and PLUM is the name of the Samba server. Workgroup and machine names are always shown in uppercase letters. If smbtree does not display output, set the workgroup (page 841) and wins server (page 845) parameters insmb.conf. Refer to the smbtree man page for more information.
smbclient: Connects to Shares
The smbclient utility functions similarly to ftp (page 713) and connects to a share. However, smbclient uses Linux-style forward slashes (/) as path separators rather than Windows-style backslashes (\). As with smbtree, entering a password allows you to view restricted shares. The –Noption prevents smbclient from requesting a password. The next example connects to a restricted share on PLUM:
$ smbclient //plum/sam
Enter sam's password: password RETURN
Domain=[MGS] OS=[Unix] Server=[Samba 4.0.6]
smb: \> ls
. D 0 Thu Jun 27 15:19:19 2013
.. D 0 Fri Jun 21 05:52:24 2013
.bashrc H 124 Mon Mar 11 12:53:01 2013
.config DH 0 Mon Jun 17 13:24:13 2013
.bash_profile H 193 Mon Mar 11 12:53:01 2013
...
.local DH 0 Tue Jun 11 19:30:00 2013
.mozilla DH 0 Tue Jun 4 19:28:00 2013
37645 blocks of size 1048576. 31993 blocks available
smb: \>
You can use most ftp commands from smbclient. Refer to “Tutorial Session” on page 717 for examples of ftp commands. Alternately, give the command help to display a list of commands or help followed by a command for information on a specific command:
smb: \> help history
HELP history:
displays the command history
Browsing Shares
Browsing shares using smbtree and smbclient is quite awkward compared with the ease of browsing a network from Windows; GNOME provides a more user-friendly alternative. Display a Nautilus File Browser window by entering nautilus from a terminal emulator or an Enter a Command window (ALT-F2). Select Connect to Server (on the left) to display a Connect to Server window. Enter smb:// followed by the name or IP address of the server in the text box labeled Server Address and click Connect to display Windows shares on the server. Or, follow the server name with the name of a user (e.g., smb://plum/sam) and click Connect. Nautilus displays a window that allows you to enter a domain (workgroup) and password for the user. Enter that information and click Connect to display that user’s directory.
Nautilus uses virtual filesystem add-ons, which are part of the desktop environment and not part of the native Linux system. As a consequence, only native GNOME applications can open files on remote shares; normal Linux programs cannot. For example, gedit can open files on remote shares; LibreOffice, mplayer, and xedit cannot.
![]() Mounting Shares
Mounting Shares
The mount utility (page 520) with a –t cifs option mounts a share as if it were a Linux directory hierarchy. See page 1242 for more information on the CIFS protocol. When you mount a share, you can write to the files on the share; you cannot write to files on a share using smbclient.
A mount command that mounts a share has the following syntax (you must run this command with root privileges):
mount -t cifs //host/share dir
where host is the name of the system the share is on, share is the name of the share you want to mount, and dir is the absolute pathname of the Linux directory you are mounting the share on (the mount point).
The following command, when run with root privileges, mounts on the /plum.sam directory the sam share on plum:
# mount -t cifs //plum/sam /plum.sam -o username=sam
Password for sam@//plum/sam: ****** RETURN
# ls /plum.sam
Desktop Documents Downloads Music Pictures Public ...
Omit the username argument and provide a blank password to mount shares that are visible to an anonymous user.
Use the uid, file_mode, and dir_mode mount options with type cifs filesystems to establish ownership and permissions of mounted files:
# mount -t cifs //plum/sam /plum.sam -o username=sam,uid=sam,file_mode=0644,dir_mode=0755
Permissions must be expressed as octal numbers preceded by a zero. For more information refer to the mount.cifs man page.
Credentials file
You can also store the username, password, and optionally the workgroup (domain) in a credentials file. To prevent another user from mounting this share, a credentials file should be owned by root and readable and writable only by a user working with root privileges (600 permissions). When you specify the credentials file in fstab (page 524), the share can be mounted automatically when the system is booted. Following is the credentials file for the share in the preceding example:
# cat /etc/plum.sam.credentials
username=sam
password=password
domain=MGS
# ls -l /etc/plum.sam.credentials
-rw-------. 1 root root 40 06-27 17:38 /etc/plum.sam.credentials
The following command mounts this share using the credentials file:
# mount -t cifs //plum/sam /plum.sam -o credentials=/etc/plum.sam.credentials
The following line in /etc/fstab would cause the share to be mounted when the system boots:
//plum/sam /plum.sam cifs defaults,credentials=/etc/plum.sam.credentials
Each share must have its own credentials file unless it uses the same login information as another share, in which case the files can use the same credentials file.
Working with Shares from Windows
This section describes how to access Linux (or Windows) directories from a Windows machine. You do not need to set up a Linux client to browse or map Linux shares from a Windows machine.
Browsing Shares
To access a share on a Samba server from Windows, open My Computer or Explorer on the Windows system, and in the text box labeled Address, enter \\ followed by the NetBIOS name (or just the hostname if you have not assigned a different NetBIOS name) of the Samba server. Windows then displays the share names of the directories the remote system is sharing. To view the shares on the Linux system named plum, for example, enter \\plum. From this window, you can view and, if permitted, browse the shares available on the remote system. If you set a share on the server so it is not browseable, you need to enter the path of the share using the format \\servername\sharename to display the share.
Mapping a Share
Another way to access a share on a Samba server from a Windows machine is by mapping (mounting) a share. Open My Computer or Explorer on the Windows system and click Map network drive at the top of the window or from one of the drop-down lists on the menubar (found on theTools menu on many Windows machines). Windows displays the Map Network Drive window. Select an unused Windows drive letter from the list box labeled Drive and enter the Windows path to the share you want to map in the text box labeled Folder. (When you use system-config-samba [Fedora only] to create a share, the share has the same name as the name of the directory you are sharing.) The format of the windows path is \\hostname\sharename. For example, to map /tmp on plum to Windows drive J, assuming the share is named tmp, select J in the list box labeled Drive, enter \\plum\tmp in the text box labeled Folder, and click Finish. After supplying a username and password, you should be able to access the /tmp directory from plum as J (tmp) on the Windows machine. If you cannot map the drive, refer to “Troubleshooting” on page 846.
Setting Up a Samba Server
This section describes how to install and configure a Samba server using the system-config-samba GUI (Fedora only) and an editor to edit the configuration files.
Prerequisites
Install the following packages:
• samba
• system-config-samba (optional; Fedora only)
• samba-common (installed with samba)
Enable and start smb
Run systemctl to cause the smb service (smbd daemon) to start each time the system enters multiuser mode and then start the xxxxxxxx service. Use the systemctl status command to make sure the service is running.
# systemctl enable smb.service
# systemctl start smb.service
Although it is not usually necessary, after modifying smb configuration files, you can give the second command again, replacing start with reload to cause smb to reread those files.
Enable and start nmb
Run systemctl to cause the nmb service (nmbd daemon) to start each time the system enters multiuser mode and then start the nmb service. Use the systemctl status command to make sure the service is running.
# systemctl enable nmb.service
# systemctl start nmb.service
Although it is not usually necessary, after modifying nmb configuration files, you can give the second command again, replacing start with reload to cause nmb to reread those files.
Server firewall
The Samba server uses UDP ports 137 and 138 and TCP ports 139 and 445. If the server is running a firewall or is behind a firewall, you need to open these ports. Give the following commands to open the ports each time the system boots (permanently) and on the running system; see page906 for information on firewall-cmd.
# firewall-cmd --add-port=137/udp
# firewall-cmd --permanent --add-port=137/udp
# firewall-cmd --add-port=138/udp
# firewall-cmd --permanent --add-port=138/udp
# firewall-cmd --add-port=139/tcp
# firewall-cmd --permanent --add-port=139/tcp
# firewall-cmd --add-port=445/tcp
# firewall-cmd --permanent --add-port=445/tcp
SELinux
When SELinux is set to use a targeted policy, Samba is protected by SELinux. You can use system-config-selinux (page 475) to disable this protection if necessary. If you want to allow users to share their home directories, see “SELinux” on page 840. The smb.conf file has extensive notes on setting up SELinux for Samba.
Printers
The default smb.conf configuration file shares printers on the Samba server; no configuration is necessary.
Home directories
The default smb.conf configuration file shares home directories of users on the Samba server; no configuration is necessary.
Configuration
The /etc/sysconfig/samba file causes smbd and nmbd each to start with the –D option, causing the smbd and nmbd processes to run as daemons.
JumpStart: Configuring a Samba Server Using system-config-samba (Fedora)
The system-config-samba utility, which is not available under RHEL, can set up only basic features of a Samba server. It is, however, the best tool to use if you are not familiar with Samba and you want to set up a simple Samba server quickly. The system-config-samba utility performs three basic functions: configuring the server, configuring users, and setting up shares (directory hierarchies) that are exported to Windows machines.
To display the Samba Server Configuration window (Figure 23-1), enter system-config-samba from a terminal emulator or an Enter a Command window (ALT-F2).
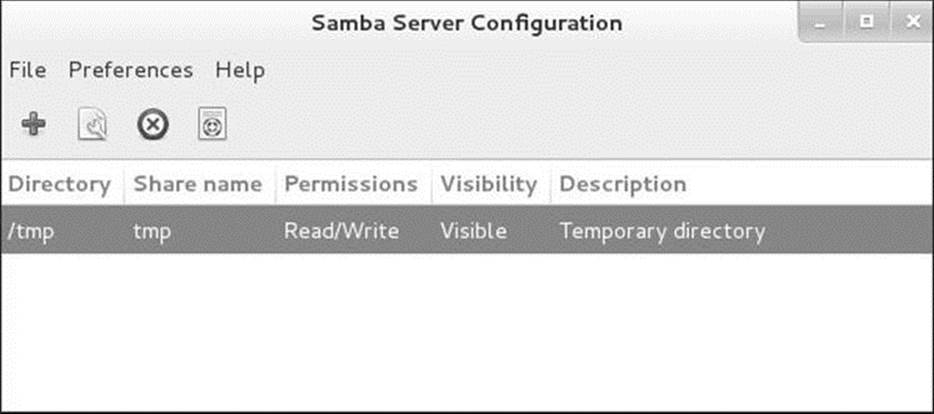
Figure 23-1 Samba Server Configuration window
Configure the server
Select menubar: Preferences![]() Server Settings to display the Server Settings window Basic tab (Figure 23-2). Change the workgroup to the one in use on the Windows machines. Change the description of the server if you like. Click the Security tab and make sure Authentication Mode is set to User; you do not need to specify an Authentication Server or a Kerberos Realm. If you are using Windows 98 or later, set Encrypt Passwords to Yes. When you specify a username in the Guest Account, anyone logging in on the Samba server as guest maps to that user’s ID. Click OK.
Server Settings to display the Server Settings window Basic tab (Figure 23-2). Change the workgroup to the one in use on the Windows machines. Change the description of the server if you like. Click the Security tab and make sure Authentication Mode is set to User; you do not need to specify an Authentication Server or a Kerberos Realm. If you are using Windows 98 or later, set Encrypt Passwords to Yes. When you specify a username in the Guest Account, anyone logging in on the Samba server as guest maps to that user’s ID. Click OK.
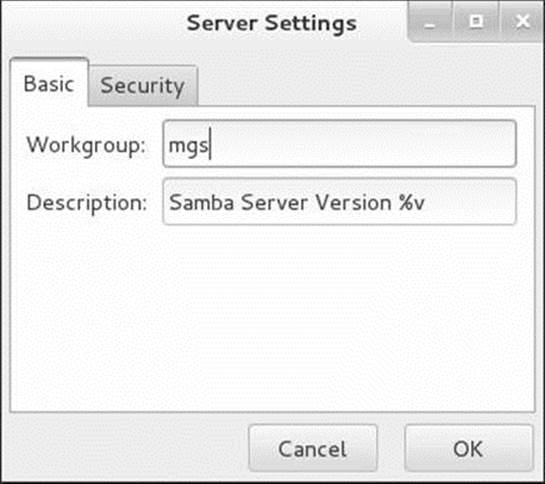
Figure 23-2 Server Settings window, Basic tab
Add or modify Samba users
Select menubar: Preferences![]() Samba Users to display the Samba Users window (Figure 23-3). If the user you want to log in as is not listed in this window, click Add User. When you have the proper permissions, the Create New Samba User window displays a combo box labeled Unix Username that allows you to select a Linux user; otherwise, your username is displayed as the Unix Username. The Windows Username is the Windows username that you want to map to the specified Linux (UNIX) username. The Samba Password is the password this user or Windows enters to gain access to the Samba server.
Samba Users to display the Samba Users window (Figure 23-3). If the user you want to log in as is not listed in this window, click Add User. When you have the proper permissions, the Create New Samba User window displays a combo box labeled Unix Username that allows you to select a Linux user; otherwise, your username is displayed as the Unix Username. The Windows Username is the Windows username that you want to map to the specified Linux (UNIX) username. The Samba Password is the password this user or Windows enters to gain access to the Samba server.
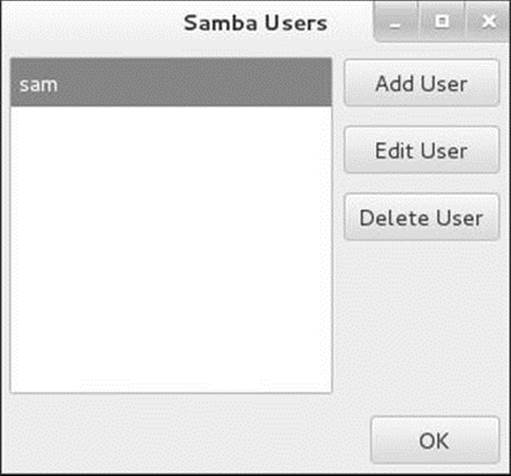
Figure 23-3 Samba Users window
If Sam’s username is sam on both the Linux and Windows systems, you would select sam from the Unix Username combo box and enter sam in the Windows Username text box. If his username were sls under Linux and sam under Windows, you would select sls from the Unix Username combo box and enter sam in the Windows Username text box. Finally you would enter Sam’s Windows password in the two Samba Password text boxes. Click OK to close the Create New Samba User window, then click OK to close the Samba Users window.
User map
If you are mapping a Windows username to a different Linux username, you must add the following username map (page 843) parameter to the [global] section of /etc/samba/smb.conf (page 839):
username map = /etc/samba/smbusers
Without this line in smb.conf, Samba will not consult the user map file.
Linux shares
Next you need to add a share, which is the directory hierarchy you export from the server (Linux) system to the client (Windows) system. Click the plus sign (+) on the toolbar to display the Basic tab of the Create Samba Share window (Figure 23-4). In the text box labeled Folder, enter the absolute pathname of the directory you want to share (/tmp is an easy directory to practice with). Enter a description if you like. It can be useful to enter the Linux hostname and the pathname of the directory you are sharing here. Put a tick in the check box labeled Writable if you want to be able to write to the directory from the client machine; putting a tick in the check box labeled Visible allows the share to be seen (browsed) from the client machine. Click the Access tab and specify whether you want to limit access to specified users or whether you want to allow anyone to access this share. Click OK. Close the Samba Server Configuration window.
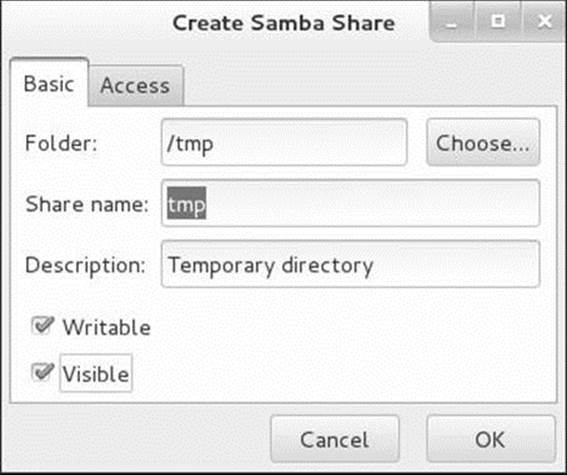
Figure 23-4 Create Samba Share window, Basic tab
You should now be able to access the share from a Windows machine (page 835). There is no need to start or restart the Samba server.
Troubleshooting
If the server does not work properly, see “Troubleshooting” on page 846.
Tip: You do not need to restart Samba when you change smb.conf
Samba rereads its configuration files each time a client connects. Unless you change the security parameter (page 843), you do not need to restart Samba when you change smb.conf.
smb.conf: Manually Configuring a Samba Server
The /etc/samba/smb.conf file controls most aspects of how Samba works and is divided into sections. Each section begins with a line that holds some text between brackets ([...]). The text within the brackets identifies the section. Typical sections are

smb.conf comments
As installed under Fedora/RHEL, the smb.conf sample configuration file contains extensive comments and commented-out examples. Comment lines start with either a hashmark (#) or a semicolon (;). The sample file uses hashmarks to begin lines that are intended to remain as comments. Semicolons begin lines you might want to mimic or use as is by removing the semicolons.
Basic smb.conf file
Following is a basic smb.conf file. It depends on default values for many parameters. To make the code clearer, important default values are written as comments beginning with a semicolon as they are in the default smb.conf file. To make the system more secure, change the default server string to eliminate the Samba version number; this value might aid hackers in penetrating the system. The hosts allow and hosts deny parameters are not required. When included, they prevent systems other than those listed from contacting the Samba server. If you uncomment these lines, replace 192.168.206.180 with the IP address of the system you want to allow to connect to the Samba server. You must open the firewall (page 836) and start the smb and nmb services (page 836) before a client can contact the server.
$ cat /etc/samba/smb.conf
[global]
workgroup = MGS
server string = Samba Server Version %v
log file = /var/log/samba/log.%m
max log size = 50
; hosts allow = 127.0.0.1, 192.168.206.180
; hosts deny = ALL
; security = user
; encrypt passwords = YES
; guest ok = NO
; guest account = nobody
[homes]
comment = Home Directories
read only = NO
browseable = NO
[tmp]
comment = Temporary Directory
path = /tmp
read only = NO
guest ok = YES
; available = YES
; browseable = YES
The [homes] share
The sample smb.conf file includes the [homes] share, which allows users to share their Linux home directories with a Windows machine. The default smb.conf file includes the same share. This share causes each user’s home directory to be shared with the specified parameters. The pathname of the share is /username; Sam’s share on plum would be /plum/sam. The default settings, which are used in the file shown above, prevent users other than the owners from browsing or accessing home directories while allowing logged-in owners full access.
SELinux
If the system is running SELinux with a targeted policy and you want to allow users to share their home directories as explained in this section, you must modify the SELinux policy to allow this access. You can use system-config-selinux (page 475) to allow this access: In the Boolean tab,samba module, put a tick mark adjacent to Allow samba to share users home directories.
Defining a share
The tmp share in the preceding smb.conf file enables a user on a Windows system to be able to read from and write to the /tmp directory on the server. The name of the share under Windows is tmp; the path under Linux is /tmp. Any Windows user who can log in on Samba, including guest, can read from and write to this directory, assuming the user’s Linux permissions allow it. To allow a user to log in on Samba, you must run smbpasswd (page 831). The browseable parameter, which defaults to YES, causes the share to appear as a share on the server. The Linux permissions that apply to a Windows user using Samba are the same permissions that apply to the Linux user that the Windows user logs in as or maps to.
Troubleshooting
Follow the steps in “Prerequisites” on page 836 and add users and passwords as necessary (page 831). From a Windows machine, you should now be able to access the share you just created (page 835). If the server does not work properly, see “Troubleshooting” on page 846.
Parameters in the smbd.conf File
The smb.conf man page lists all the parameters you can set in smb.conf. The following sections identify some of the parameters you might need to change.
Global Parameters
interfaces
A SPACE-separated list of networks Samba listens on. Specify as interface names (such as lo and eth0) or as IP address/net mask pairs (page 483).
Default: all active interfaces except 127.0.0.1
server string
The string the client (Windows) machine displays in various places. Within the string, Samba replaces %v with the Samba version number and %h with the hostname of the server. To make the system more secure, eliminate the Samba version number; this value might aid hackers in penetrating the system.
Default: Samba %v
Fedora/RHEL: Samba Server Version %v
workgroup
The workgroup the server belongs to. Set to the same workgroup as the Windows clients that use the server. This parameter controls the domain name that Samba uses when security (page 843) is set to DOMAIN.
Default: WORKGROUP
Fedora/RHEL: MYGROUP
Security Parameters
encrypt passwords
YES accepts only encrypted passwords from clients. Windows 98 and Windows NT 4.0 Service Pack 3 and later use encrypted passwords by default. This parameter uses smbpasswd to authenticate passwords unless you set security to SERVER or DOMAIN, in which case Samba authenticates using another server.
Default: YES
guest account
The username that is assigned to users logging in as guest or mapped to guest; applicable only when guest ok (page 845) is set to YES. This username should be present in /etc/passwd but should not be able to log in on the system. Typically guest account is assigned a value of nobodybecause the user nobody can access only files that any user can access. If you are using the nobody account for other purposes on the server system, set this parameter to a name other than nobody. See page 830 for more information.
Default: nobody
hosts allow
Analogous to the /etc/hosts.allow file (page 485); specifies hosts that are allowed to connect to the server. Overrides hosts specified in hosts deny. A good strategy is to specify ALL in hosts deny and to specify the hosts you want to grant access to in this file. Specify hosts in the same manner as in the hosts.allow file.
Default: none (all hosts permitted access)
hosts deny
Analogous to the /etc/hosts.deny file (page 485); specifies hosts that are not allowed to connect to the server. Overridden by hosts specified in hosts allow. If you specify ALL in this parameter, remember to include the local system (127.0.0.1) in hosts allow. Specify hosts in the same manner as in the hosts.deny file.
Default: none (no hosts excluded)
invalid users
Lists users who are not allowed to log in using Samba.
Default: none (all users are permitted to log in)
map to guest
Defines when a failed login is mapped to the guest account. Useful only when security (next page) is not set to SHARE or SERVER.
Never: Allows guest to log in only when the user explicitly provides guest as the username and a blank password.
Bad User: Treats any attempt to log in as a user who does not exist as a guest login. This parameter is a security risk because it allows a malicious user to retrieve a list of users on the system quickly.
Bad Password: Silently logs in as guest any user who incorrectly enters her password. This parameter might confuse a user when she mistypes her password and is unknowingly logged in as guest because she will suddenly see fewer shares than she is used to seeing.
Default: never
passdb backend
Specifies how Samba stores passwords. Set to ldapsam for LDAP, smbpasswd for Samba, or tdbsam for TDB (Trivial Database) password storage. See page 831 for instructions on using smbpasswd to change or add Samba passwords.
Default: tdbsam
passwd chat
The chat script Samba uses to converse with the program defined by passwd program (next). If this script is not followed, Samba does not change the password. Used only when unix password sync (page 843) is set to YES.
Default: *new*password* %n\n*new*password* %n\n *changed*
passwd program
The program Samba uses to set Linux passwords. Samba replaces %u with the user’s username.
Default: none
security
Specifies if and how clients transfer user and password information to the server. Choose one of the following:
USER: Causes Samba to require a username and password from Windows users when logging in on the Samba server. With this setting you can use
• username map (below) to map Samba usernames to Linux usernames
• encrypt passwords (page 841) to encrypt passwords (recommended)
• guest account (previous page) to map users to the guest account
SHARE: Causes Samba not to authenticate clients on a per-user basis. Instead, Samba uses the Windows 9x setup, in which each share can have an individual password for either read or full access. This option is not compatible with recent versions of Windows.
SERVER: Causes Samba to use another SMB server to validate usernames and passwords. If the remote validation fails, the local Samba server tries to validate usernames and passwords as though security were set to USER.
DOMAIN: Samba passes an encrypted password to a Windows NT domain controller for validation. The workgroup parameter (page 841) must be properly set in smb.conf for DOMAIN to work.
ADS: Instructs Samba to use an Active Directory server for authentication, allowing a Samba server to participate as a native Active Directory member. (Active Directory is the centralized information system that Windows 2000 and later use. It replaces Windows Domains, which was used by Windows NT and earlier.)
Default: USER
unix password sync
YES causes Samba to change a user’s Linux password when the associated user changes the encrypted Samba password.
Default: NO
username map
Points to a user map file that maps Windows usernames to Linux usernames. See “User maps” on page 830 for more information.
Default: no map
Logging Parameters
log file
The name of the Samba log file. Samba replaces %m with the name of the client system, allowing you to generate a separate log file for each client.
Default: none
Fedora/RHEL: /var/log/samba/log.%m
log level
Sets the log level, with 0 (zero) being off and higher numbers being more verbose.
Default: 0 (off)
max log size
An integer specifying the maximum size of the log file in kilobytes. A 0 (zero) specifies no limit. When a file reaches this size, Samba appends .old to the filename and starts a new log, deleting any old log file.
Default: 5000
Fedora/RHEL: 50
Browser Parameters
The domain master browser is the system responsible for maintaining the list of machines on a network used when browsing. SMB (page 1273) uses weighted elections every 11–15 minutes to determine which machine is the domain master browser.
Whether a Samba server wins this election depends on two parameters:
• Setting domain master to YES instructs the Samba server to enter the election.
• The os level determines how much weight the Samba server’s vote receives. The maximum setting for os level is 255, although setting it to 65 should ensure that the Samba server wins. NT Server series domain controllers—including Windows 2000, XP, and 2003—use an os level of 32.
domain master
YES causes nmbd to attempt to be the domain master browser. If a domain master browser exists, then local master browsers will forward copies of their browse lists to it. If there is no domain master browser, then browse queries might not be able to cross subnet boundaries. A Windows PDC (primary domain controller) will always try to become the domain master and might behave in unexpected ways if it fails. Refer to the preceding discussion for more information.
Default: AUTO
local master
YES causes nmbd to enter elections for the local master browser on a subnet. A local master browser stores a cache of the NetBIOS (page 1262) names of entities on the local subnet, allowing browsing. Windows machines automatically enter elections; for browsing to work, the network must have at least one Windows machine or one Samba server with local master set to YES. It is poor practice to set local master to NO. If you do not want a computer to act as a local master, set its os level to a lower number, allowing it to be used as the local master if all else fails.
Default: YES
os level
An integer that controls how much Samba advertises itself for browser elections and how likely nmbd is to become the local master browser for its workgroup. A higher number increases the chances of the local server becoming the local master browser. Refer to the discussion at the beginning of this section for more information.
Default: 20
preferred master
YES forces nmbd to hold an election for local master and enters the local system with a slight advantage. With domain master set to YES, this parameter helps ensure the local Samba server becomes the domain master. Setting this parameter to YES on more than one server causes the servers to compete to become master, generating a lot of network traffic and sometimes leading to unpredictable results. A Windows PDC automatically acts as if this parameter is set to YES.
Default: AUTO
Communication Parameters
dns proxy
When acting as a WINS server (page 1281), YES causes nmbd to use DNS if NetBIOS (page 1262) resolution fails.
Default: YES
socket options
Tunes the network parameters used when exchanging data with a client.
Default: TCP_NODELAY
wins server
The IP address of the WINS server nmbd should register with.
Default: not enabled
wins support
YES specifies nmbd is to act as a WINS server.
Default: NO
Share Parameters
Each of the following parameters can appear many times in smb.conf, once in each share definition.
available
YES specifies the share as active. Set this parameter to NO to disable the share but continue logging requests for it.
Default: YES
browseable
Determines whether the share can be browsed, for example, in Windows My Network Places.
Default: YES
Fedora/RHEL: varies
comment
A description of the share, shown when browsing the network from Windows.
Default: none
Fedora/RHEL: varies
guest ok
Allows a user who logs in as guest to access this share.
Default: NO
Fedora/RHEL: varies
path
The path of the directory being shared.
Default: none
Fedora/RHEL: various
read only
Does not allow write access. Use writable to allow read-write access.
Default: YES
Fedora/RHEL: various
Troubleshooting
Samba and Windows provide tools that can help troubleshoot a connection. This section discusses these tools and suggests other techniques that can help narrow down the problem when you cannot get Samba to work.
1. Restart the Samba daemons. Normally you do not need to restart these daemons after changing the smb.conf file. Make sure smbd and nmbd are running.
# systemctl reload smb
# systemctl reload nmb
# systemctl status smb
...
# systemctl status nmb
...
testparm
2. Run testparm to confirm that the smb.conf file is syntactically correct:
$ testparm
Load smb config files from /etc/samba/smb.conf
Processing section "[homes]"
Processing section "[printers]"
Processing section "[tmp]"
Loaded services file OK.
Server role: ROLE_STANDALONE
Press enter to see a dump of your service definitions
...
You can ignore an error message about rlimit_max. If you misspell a keyword in smb.conf, you get an error such as the following:
$ testparm
Load smb config files from /etc/samba/smb.conf
Unknown parameter encountered: "workgruop"
Ignoring unknown parameter "workgruop"
...
Log files
3. Check the log files in /var/log/samba (page 843).
ping
4. Use ping (page 305) from both sides of the connection to make sure the network is up.
Firewall
5. Confirm the firewall on the server is not blocking the Samba connection on either the server or the client (page 836). The command firewall-cmd ––list-ports displays the open ports on the local system.
User
6. Make sure the user who is trying to log in exists as a Samba user. See pdbedit on page 831.
Password
7. Make sure you have set up a password for the Samba user who is trying to log in. See smbpasswd on page 831.
SELinux
8. You might need to modify the SELinux policy. See pages 836 and 840.
hosts allow
9. If you specify a value for hosts deny, be sure to specify values for hosts allow, including 127.0.0.1 so you can access Samba from the local system. See page 842 for more information.
net view
10. From a Windows command prompt, use net view to display a list of shares available from the server (plum in this example):
C:>net view \\plum
Shared resources at \\plum
Samba Server Version 4.0.6
Share name Type Used as Comment
--------------------------------------------------------------
sam Disk Home Directories
tmp Disk Temporary Directory
The command completed successfully.
net use
11. Try to map (mount) the drive from a Windows command prompt. The following command attempts to mount the share named sam on plum as drive X:
C:>net use x: \\plum\sam
Enter the user name for 'plum': sam
Enter the password for plum:
The command completed successfully.
nmblookup
12. From the Samba server, use nmblookup (samba-client package) to query the nmbd server, using the special name __SAMBA__ for the server’s NetBIOS name. The –d 2 option turns the debugger on at level 2, which generates a moderate amount of output. The –B option specifies the server you are querying.
$ nmblookup -d 2 -B 127.0.0.1 __SAMBA__
...
querying __SAMBA__ on 127.0.0.1
Got a positive name query response from 127.0.0.1 ( 192.168.206.181 )
192.168.206.181 __SAMBA__<00>
The next example uses nmblookup, without setting the debug level, to query the local system for all NetBIOS names.
$ nmblookup -B 127.0.0.1 \*
querying * on 127.0.0.1
192.168.206.181 *<00>
To query for the master browser from the local server, run nmblookup with the –A option followed localhost or the name of the server:
$ nmblookup -A 127.0.0.1
Looking up status of 127.0.0.1
PLUM <00> - B <ACTIVE>
PLUM <03> - B <ACTIVE>
PLUM <20> - B <ACTIVE>
MGS <00> - <GROUP> B <ACTIVE>
MGS <1e> - <GROUP> B <ACTIVE>
MAC Address = 00-00-00-00-00-00
smbclient
13. From the Samba server, use smbclient (samba-client package) with the –L option followed by the name of the server to generate a list of shares offered by the server. When you do not enter a password, smbclient displays shares available to the Anonymous user. When you enter a password, it also displays restricted shares including the [homes] share for the user.
$ smbclient -L localhost
Enter sam's password: RETURN (do not enter a password)
Anonymous login successful
Domain=[MGS] OS=[Unix] Server=[Samba 4.0.6]
Sharename Type Comment
--------- ---- -------
tmp Disk Temporary Directory
IPC$ IPC IPC Service (Samba Server Version 4.0.6)
Anonymous login successful
Domain=[MGS] OS=[Unix] Server=[Samba 4.0.6]
Server Comment
--------- -------
PEACH
PLUM Samba Server Version 4.0.6
Workgroup Master
--------- -------
MGS PEACH
Chapter Summary
Samba is a suite of programs that enables a server to share directory hierarchies and printers with a client. Typically the server is a Linux system and the client is a Windows machine. A directory hierarchy or printer that Samba shares between server and client systems is called a share. To access a share on a Linux system, a Windows user must supply a username and password. Usernames must correspond to Linux usernames either directly or as mapped by the file that is pointed to by the username map parameter in smb.conf, often /etc/samba/smbusers. Samba passwords are generated by smbpasswd and kept in a Trivial Database named tdbsam. The main Samba configuration file is /etc/samba/smb.conf, which you can edit using system-config-samba (Fedora only) or a text editor.
From a Windows machine, you can access a share on a Samba server by opening a directory or Explorer window and, in the location text box near the top of the window, entering \\ followed by the name of the server. In response, Windows displays the shares on the server. You can work with these shares as though they were Windows files.
From a Linux system, you can use any of several Samba tools to access shares. These tools include smbtree (displays shares), smbclient (similar to ftp), and mount with the –t cifs option (mounts shares). In addition, you can enter nautilus from a terminal emulator or an Enter a Command window (ALT-F2) to browse shares.
Exercises
1. Which two daemons are part of the Samba suite? What does each do?
2. What steps are required for mapping a Windows user to a Linux user?
3. How can a system administrator add a Samba password for a new user?
4. What is the purpose of the [homes] share? Should this share be browseable? Why?
Advanced Exercises
5. Describe how Samba’s handling of users differs from that of NFS.
6. Which configuration changes would you need to apply to routers if you wanted to allow SMB/CIFS browsing across multiple subnets without configuring master browsers?
7. WINS resolution allows hosts to define their own names. Suggest a way to use Samba to assign names from a centralized list.