CompTIA Network+ N10-006 Cert Guide (2015)
Chapter 12. Network Security
Upon completion of this chapter, you will be able to answer the following questions:
![]() What are the goals of network security, and what sorts of attacks do you need to defend against?
What are the goals of network security, and what sorts of attacks do you need to defend against?
![]() What best practices can be implemented to defend against security threats?
What best practices can be implemented to defend against security threats?
![]() What are the characteristics of various remote-access security technologies?
What are the characteristics of various remote-access security technologies?
![]() How can firewalls be used to protect an organization’s internal network, while allowing connectivity to an untrusted network, such as the Internet?
How can firewalls be used to protect an organization’s internal network, while allowing connectivity to an untrusted network, such as the Internet?
![]() How can virtual private networks (VPNs) be used to secure traffic as that traffic flows over an untrusted network?
How can virtual private networks (VPNs) be used to secure traffic as that traffic flows over an untrusted network?
![]() What is the difference between intrusion prevention and intrusion detection systems, and how do they protect an organization from common security threats?
What is the difference between intrusion prevention and intrusion detection systems, and how do they protect an organization from common security threats?
Today’s networks are increasingly dependent on connectivity with other networks. However, connecting an organization’s trusted network to untrusted networks, such as the Internet, introduces security risks. Security risks even exist within an organization.
To protect your organization’s data from malicious users, you need to understand the types of threats against which you might have to defend. Then you need to know the options you have for defending your network. A key security concept to understand is that you need multiple layers of security for your network, not just a single solution, such as a firewall. Rather, you might combine user training, security policies, remote-access security protocols, firewalls, VPNs, and intrusion prevention systems. Combined, these solutions offer overlapping layers of network protection.
This chapter begins by introducing you to the fundamentals of security, which includes a discussion of common network attacks. Then the discussion turns to how to defend against those attacks. Remote-access security options are also reviewed, along with the functions and deployment considerations of dedicated security solutions, including firewalls, VPNs, and intrusion detection/prevention systems.
Foundation Topics
Security Fundamentals
Security is a vast topic, and to begin our discussion, this section introduces the goals that security can help you meet. Then, to better understand what you are defending against, this section identifies several categories of network attacks.
Network Security Goals
For most of today’s corporate networks, the demands of e-commerce and customer contact require connectivity between internal corporate networks and the outside world. Two basic assumptions, from a security standpoint, about modern corporate networks are the following:
![]() Today’s corporate networks are large, interconnect with other networks, and run both standards-based and proprietary protocols.
Today’s corporate networks are large, interconnect with other networks, and run both standards-based and proprietary protocols.
![]() The devices and applications connecting to and using corporate networks are continually increasing in complexity.
The devices and applications connecting to and using corporate networks are continually increasing in complexity.
Because almost all (if not all) corporate networks require network security, consider the three primary goals of network security:

![]() Confidentiality
Confidentiality
![]() Integrity
Integrity
![]() Availability
Availability
The following sections explain these goals in more detail.
Confidentiality
Data confidentiality implies keeping data private. This privacy could entail physically or logically restricting access to sensitive data or encrypting traffic traversing a network. A network that provides confidentiality would, as a few examples:
![]() Use network-security mechanisms (for example, firewalls and access control lists [ACLs]) to prevent unauthorized access to network resources.
Use network-security mechanisms (for example, firewalls and access control lists [ACLs]) to prevent unauthorized access to network resources.
![]() Require appropriate credentials (such as usernames and passwords) to access specific network resources.
Require appropriate credentials (such as usernames and passwords) to access specific network resources.
![]() Encrypt traffic such that any traffic captured off of the network by an attacker could not be deciphered by the attacker.
Encrypt traffic such that any traffic captured off of the network by an attacker could not be deciphered by the attacker.
Confidentiality can be provided by encryption. Encryption allows a packet to be encoded in such a way that it can be decoded by an intended party. However, if a malicious user intercepted an encrypted packet in transit, he would not be able to decrypt the packet. The way most modern encryption algorithms prevent decryption by a third party is through the use of a key. Because the encryption or decryption algorithm uses a key in its mathematical calculation, a third party who does not possess the key cannot interpret encrypted data that he intercepts.
Encryption has two basic forms: symmetric encryption and asymmetric encryption.
Symmetric Encryption
Symmetric encryption is fast in comparison to asymmetric encryption. The word symmetric in symmetric encryption implies that the same key is used by both the sender and the receiver to encrypt or decrypt a packet. Examples of symmetric encryption algorithms include the following:

![]() DES: Data Encryption Standard (DES) is an older encryption algorithm (developed in the mid 1970s) using a 56-bit key. It is considered weak by today’s standards.
DES: Data Encryption Standard (DES) is an older encryption algorithm (developed in the mid 1970s) using a 56-bit key. It is considered weak by today’s standards.
![]() 3DES: Triple DES (3DES), developed in the late 1990s, uses three 56-bit DES keys (for a total of 168 bits) and is usually considered a strong encryption algorithm. However, the security of 3DES varies based on the way it is implemented. Specifically, 3DES has three keying options, where all three keys are different (keying option 1), two of the three keys are the same (keying option 2), or all three keys are the same (keying option 3) to maintain backward compatibility with DES.
3DES: Triple DES (3DES), developed in the late 1990s, uses three 56-bit DES keys (for a total of 168 bits) and is usually considered a strong encryption algorithm. However, the security of 3DES varies based on the way it is implemented. Specifically, 3DES has three keying options, where all three keys are different (keying option 1), two of the three keys are the same (keying option 2), or all three keys are the same (keying option 3) to maintain backward compatibility with DES.
![]() AES: Advanced Encryption Standard (AES), released in 2001, is typically considered the preferred symmetric encryption algorithm. AES is available in 128-bit key, 192-bit key, and 256-bit key versions.
AES: Advanced Encryption Standard (AES), released in 2001, is typically considered the preferred symmetric encryption algorithm. AES is available in 128-bit key, 192-bit key, and 256-bit key versions.
Figure 12-1 illustrates an example of symmetric encryption, where both parties have a shared key to be used during a session (called a session key).
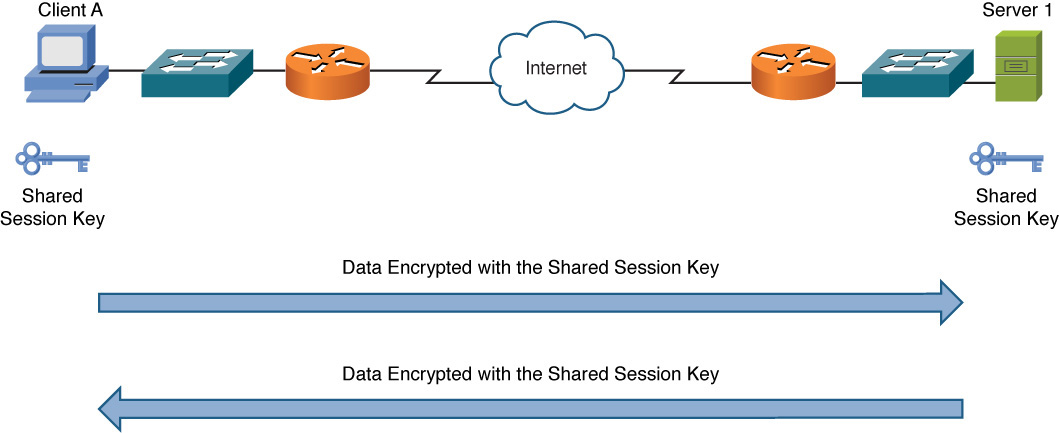
Figure 12-1 Symmetric Encryption Example
Note
Another widely deployed asymmetric encryption algorithm is pretty good privacy (PGP), which is often used to encrypt e-mail traffic. A free variant of PGP is GNU Privacy Guard (GPC).
Asymmetric Encryption
Asymmetric encryption is slow in comparison to symmetric encryption but balances this slowness with higher security. As its name suggests, asymmetric encryption uses asymmetric (different) keys for the sender and the receiver of a packet. Because of its speed, asymmetric encryption algorithms are not typically used to encrypt large quantities of real-time data. Rather, asymmetric encryption might be used to encrypt a small chunk of data used, for example, to authenticate the other party in a conversation or to exchange a shared key to be used during a session (after which the parties in the conversation could start using symmetric encryption). One of the most popular asymmetric encryption algorithms in use today is RSA; its name comes from the last initials of its inventors: Ronald L. Rivest, Adi Shamir, and Leonard M. Adleman.
RSA is commonly used as part of a public key infrastructure (PKI) system. Specifically, PKI uses digital certificates and a certificate authority (CA) to authentication and encryption services.
For example, when client A wants to communicate securely with server 1, as illustrated in Figure 12-2, the following steps occur (which are outlined in the following list).

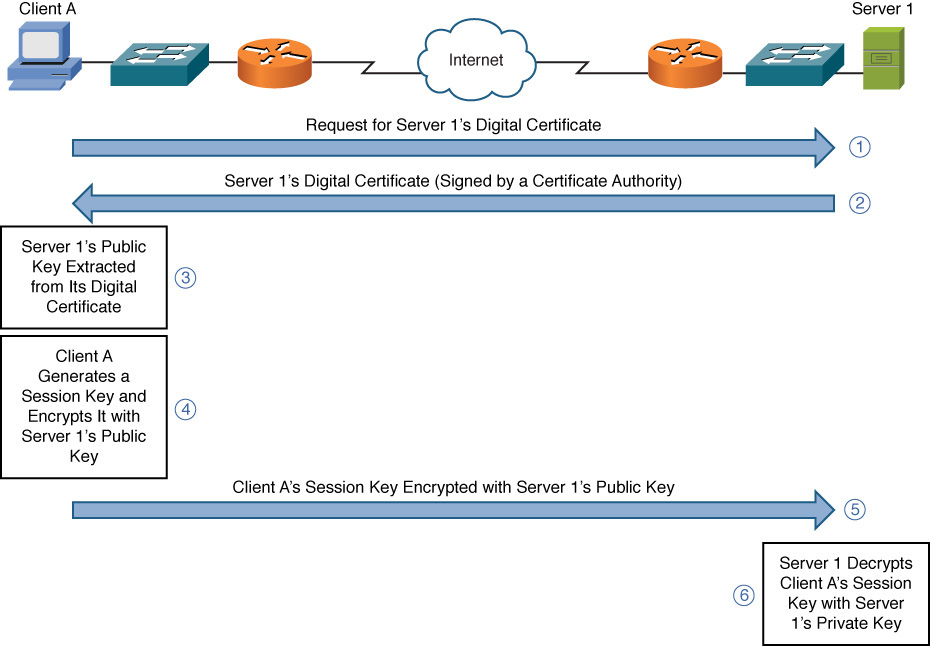
Figure 12-2 Asymmetric Encryption Example
Step 1. Client A requests server 1’s digital certificate.
Step 2. Server 1 sends its digital certificate, and client A knows the received certificate is really from server 1 because the certificate has been authenticated (signed) by a trusted third party, called a certificate authority.
Step 3. Client A extracts server 1’s public key from server 1’s digital certificate. Data encrypted using server 1’s public key can only be decrypted with server 1’s private key, which only server 1 has.
Step 4. Client A generates a random string of data called a session key.
Step 5. The session key is then encrypted using server 1’s public key and sent to server 1.
Step 6. Server 1 decrypts the session key using its private key.
At this point, both client A and server 1 know the session key, which can be used to symmetrically encrypt traffic during the session.
Integrity
Data integrity ensures that data has not been modified in transit. Also, a data integrity solution might perform origin authentication to verify that traffic is originating from the source that should send the traffic.
Examples of integrity violations include the following:
Note
Challenge-Response Authentication Mechanism Message Digest 5 (CRAM-MD5) is a common variant of HMAC frequently used in e-mail systems.

![]() Modifying the appearance of a corporate website
Modifying the appearance of a corporate website
![]() Intercepting and altering an e-commerce transaction
Intercepting and altering an e-commerce transaction
![]() Modifying financial records that are stored electronically
Modifying financial records that are stored electronically
Hashing is one approach to providing integrity to data transmissions crossing a network. Specifically, hashing takes a string of data (such as a password) and runs it through an algorithm. The result of the algorithm is called a hash or a hash digest. If the sender of that data runs a hashing algorithm on the data and sends the hash digest along with the data, when the recipient receives the data, she can also run the data through the same hashing algorithm. If the recipient calculates the same hash digest, she might conclude that the data has not been modified in transit (that is, she has confirmed the integrity of the data). Note that a hashing algorithm produces hash digests of the same length regardless of the size of the data being hashed.
Two of the most common hashing algorithms are the following:
![]() Message digest 5 (MD5): Creates 128-bit hash digests
Message digest 5 (MD5): Creates 128-bit hash digests
![]() Secure Hash Algorithm 1 (SHA-1): Creates 160-bit hash digests
Secure Hash Algorithm 1 (SHA-1): Creates 160-bit hash digests
Hashing by itself, however, does not guarantee data integrity because an attacker could intercept a string of data, manipulate it, and recalculate the hash value based on the manipulated data. The victim would then determine that the hash was valid based on the data.
To overcome this limitation of pure hashing, hash-based message authentication code (HMAC) uses an additional secret key in the calculation of a hash value. So an attacker would not be able to create a valid hash value because he would not know the secret key. Other variants of hashing algorithms exist that involve longer digests, such as SHA-256. In cryptography, bigger implies better security.
Availability
The availability of data is a measure of the data’s accessibility. For example, if a server was down only 5 minutes per year, the server would have an availability of 99.999 percent (that is, the five nines of availability).
A couple of examples of how an attacker could attempt to compromise the availability of a network are as follows:
![]() Send improperly formatted data to a networked device, resulting in an unhandled exception error.
Send improperly formatted data to a networked device, resulting in an unhandled exception error.
![]() Flood a network system with an excessive amount of traffic or requests, which would consume a system’s processing resources and prevent the system from responding to many legitimate requests. This type of attack is referred to as a denial-of-service (DoS) attack.
Flood a network system with an excessive amount of traffic or requests, which would consume a system’s processing resources and prevent the system from responding to many legitimate requests. This type of attack is referred to as a denial-of-service (DoS) attack.
The topic of availability was elaborated on in Chapter 9, “Network Optimization.”
Categories of Network Attacks
The previous discussion identified confidentiality, integrity, and availability as the three primary goals of network security. Therefore, we need to better understand the types of attacks that attempt to compromise these areas.
Confidentiality Attacks
A confidentiality attack attempts to make confidential data (for example, personnel records, usernames, passwords, credit card numbers, or e-mails) viewable by an attacker. Because an attacker often makes a copy of the data, rather than trying to manipulate the data or crash a system, confidentiality attacks often go undetected. Even if auditing software to track file access were in place, if no one suspected an issue, the audit logs might never be examined.
Figure 12-3 illustrates a confidentiality attack.
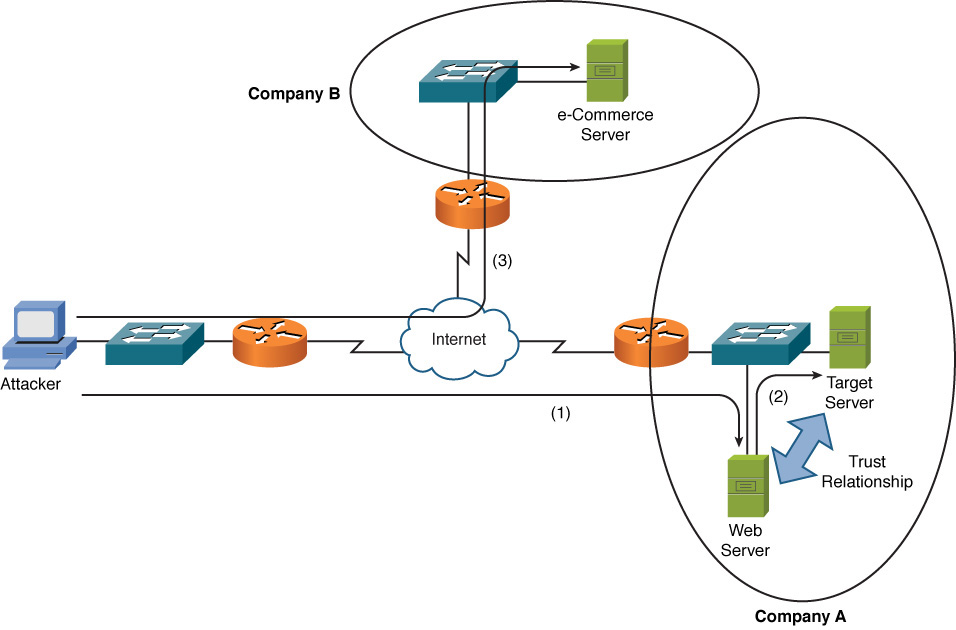
Figure 12-3 Confidentiality Attack Example
In Figure 12-3, a web server and a database server have a mutual trust relationship. The database server houses confidential customer information, such as customer credit card information. As a result, company A decided to protect the database server (for example, patching known software vulnerabilities) better than the web server. However, the attacker leverages the trust relationship between the two servers to obtain customer credit card information and then make a purchase from company B using the stolen credit card information. The procedure is as follows:
Step 1. The attacker exploits a vulnerability in company A’s web server and gains control of that server.
Step 2. The attacker uses the trust relationship between the web server and the database server to obtain customer credit card information from the database server.
Step 3. The attacker uses the stolen credit card information to make a purchase from company B.
Table 12-1 identifies several methods that attackers might use in a confidentiality attack.

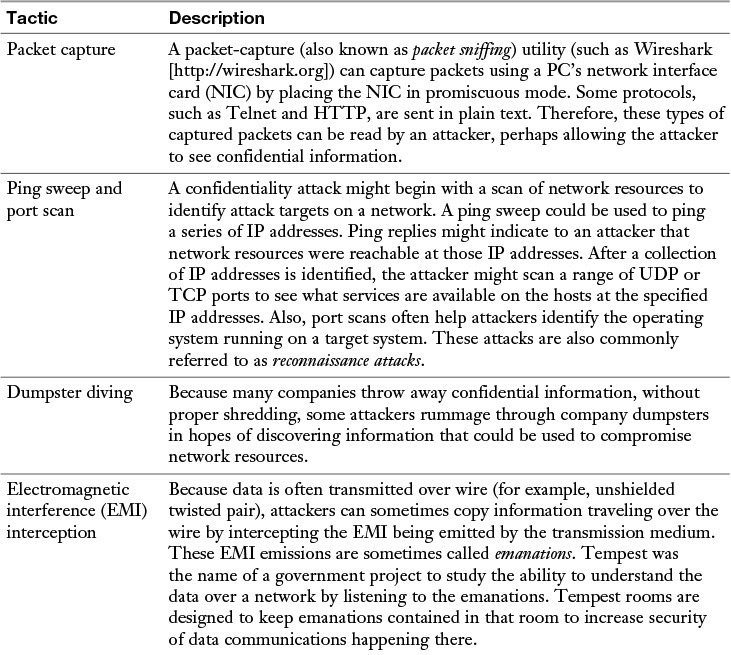
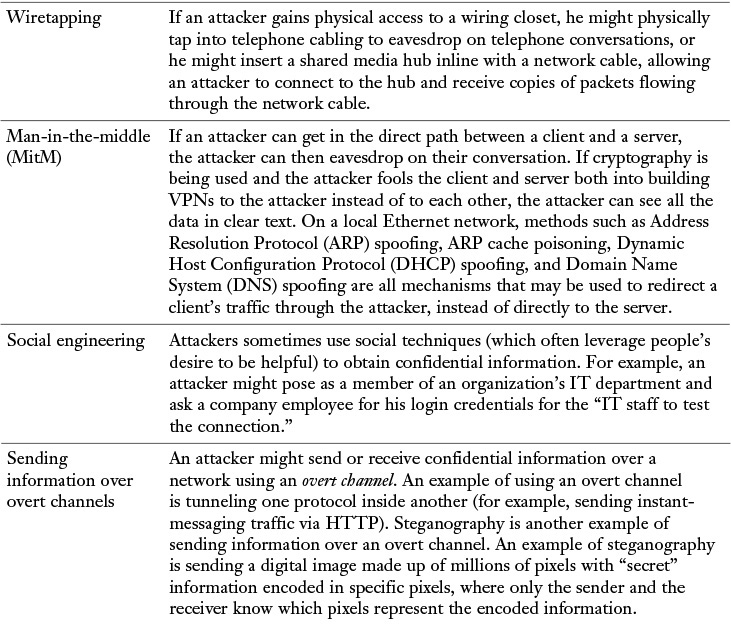
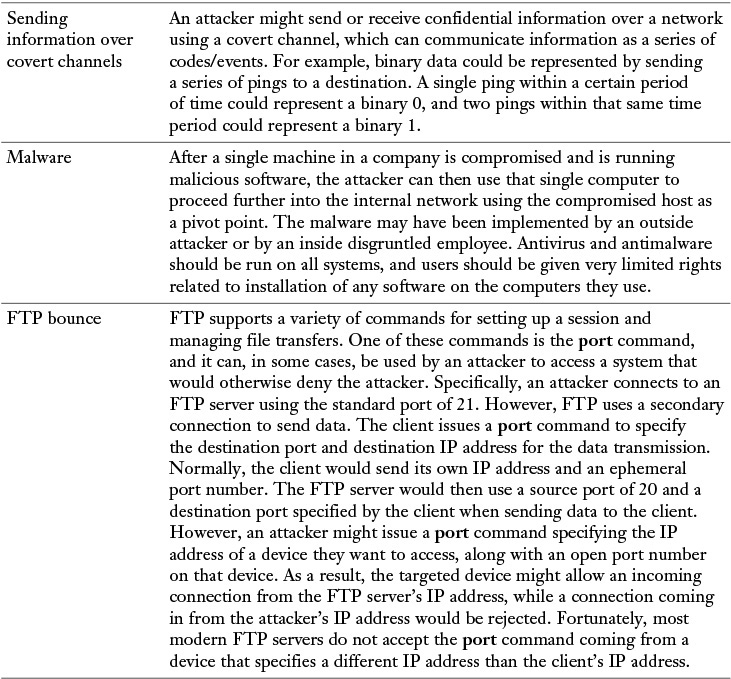
Table 12-1 Confidentiality Attack Tactics
Note
Attack types listed in this book are a partial list. New attacks and even new categories of attacks are being created all the time.
Integrity Attacks
Integrity attacks attempt to alter data (compromise the integrity of the data). Figure 12-4 shows an example of an integrity attack.
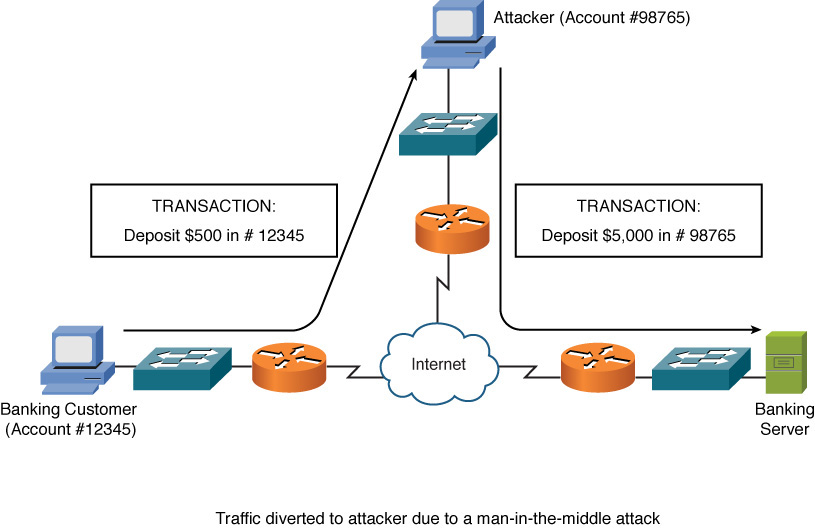
Figure 12-4 Integrity Attack
In Figure 12-4, an MitM attack has been launched by an attacker. This attack causes data flowing between the banking customer and the banking server to be sent via the attacker’s computer. The attacker can then not only intercept but also manipulate the data. In the figure, notice that the banking customer attempts to deposit $500 into her account. However, the attacker intercepts and changes the details of the transaction, such that the instruction to the banking server is to deposit $5,000 into the attacker’s account. The MitM attack can compromise both confidentiality and data integrity, and that is why it is covered twice here, once in each section.
The following list identifies multiple methods attackers might use to conduct an integrity attack:
![]() Salami attack: A salami attack is a collection of small attacks that result in a larger attack when combined. For example, if an attacker has a collection of stolen credit card numbers, the attacker could withdraw small amounts of money from each credit card (possibly unnoticed by the credit card holders). Although each withdrawal is small, the combination of the multiple withdrawals results in a significant sum for the attacker.
Salami attack: A salami attack is a collection of small attacks that result in a larger attack when combined. For example, if an attacker has a collection of stolen credit card numbers, the attacker could withdraw small amounts of money from each credit card (possibly unnoticed by the credit card holders). Although each withdrawal is small, the combination of the multiple withdrawals results in a significant sum for the attacker.
![]() Data diddling: The process of data diddling changes data before it is stored in a computing system. Malicious code in an input application or a virus could perform data diddling. For example, a virus, Trojan horse, or worm could be written to intercept keyboard input, and while displaying the appropriate characters onscreen (so that the user does not see an issue), manipulated characters could be entered into a database application or sent over a network.
Data diddling: The process of data diddling changes data before it is stored in a computing system. Malicious code in an input application or a virus could perform data diddling. For example, a virus, Trojan horse, or worm could be written to intercept keyboard input, and while displaying the appropriate characters onscreen (so that the user does not see an issue), manipulated characters could be entered into a database application or sent over a network.
Note
For the Network+ exam, you need to understand the difference between a virus, a worm, and a Trojan horse. A virus is a piece of code (for example, a program or a script) that an end user executes. A worm, however, can infect a system or propagate to other systems without intervention from the end user. Finally, a Trojan horse is a program that appears to be for one purpose (for example, a game) but secretly performs another task (such as collecting a list of contacts from an end user’s e-mail program).
![]() Trust relationship exploitation: Different devices in a network might have a trust relationship between themselves. For example, a certain host might be trusted to communicate through a firewall using specific ports, while other hosts are denied passage through the firewall using those same ports. If an attacker were able to compromise the host that had a trust relationship with the firewall, the attacker could use the compromised host to pass normally denied data through a firewall. Another example of a trust relationship is a web server and a database server mutually trusting one another. In that case, if an attacker gained control of the web server, he might be able to leverage that trust relationship to compromise the database server.
Trust relationship exploitation: Different devices in a network might have a trust relationship between themselves. For example, a certain host might be trusted to communicate through a firewall using specific ports, while other hosts are denied passage through the firewall using those same ports. If an attacker were able to compromise the host that had a trust relationship with the firewall, the attacker could use the compromised host to pass normally denied data through a firewall. Another example of a trust relationship is a web server and a database server mutually trusting one another. In that case, if an attacker gained control of the web server, he might be able to leverage that trust relationship to compromise the database server.
![]() Password attack: A password attack, as its name suggests, attempts to determine the password of a user. Once the attacker gains the username and password credentials, he can attempt to log in to a system as that user and inherit that user’s set of permissions. Various approaches are available to determine passwords, including the following:
Password attack: A password attack, as its name suggests, attempts to determine the password of a user. Once the attacker gains the username and password credentials, he can attempt to log in to a system as that user and inherit that user’s set of permissions. Various approaches are available to determine passwords, including the following:
![]() Trojan horse: A Trojan horse is a program that appears to be a useful application but might capture a user’s password and then make it available to the attacker.
Trojan horse: A Trojan horse is a program that appears to be a useful application but might capture a user’s password and then make it available to the attacker.
![]() Packet capture: A packet-capture utility can capture packets seen on a PC’s NIC. Therefore, if the PC can see a copy of a plain-text password being sent over a link, the packet-capture utility can be used to glean the password.
Packet capture: A packet-capture utility can capture packets seen on a PC’s NIC. Therefore, if the PC can see a copy of a plain-text password being sent over a link, the packet-capture utility can be used to glean the password.
![]() Keylogger: A program that runs in a computer’s background and logs keystrokes that a user makes. After a user enters a password, the password is stored in the log created by the keylogger. An attacker can then retrieve the log of keystrokes to determine the user’s password.
Keylogger: A program that runs in a computer’s background and logs keystrokes that a user makes. After a user enters a password, the password is stored in the log created by the keylogger. An attacker can then retrieve the log of keystrokes to determine the user’s password.
![]() Brute force: This attack tries all possible password combinations until a match is made. For example, the brute-force attack might start with the letter a and go through the letter z. Then the letters aa through zz are attempted, until the password is determined. Therefore, using a mixture of upper- and lowercase, in addition to special characters and numbers, can help mitigate a brute-force attack.
Brute force: This attack tries all possible password combinations until a match is made. For example, the brute-force attack might start with the letter a and go through the letter z. Then the letters aa through zz are attempted, until the password is determined. Therefore, using a mixture of upper- and lowercase, in addition to special characters and numbers, can help mitigate a brute-force attack.
![]() Dictionary attack: Similar to a brute-force attack, in that multiple password guesses are attempted. However, the dictionary attack is based on a dictionary of commonly used words, rather than the brute-force method of trying all possible combinations. Picking a password that is not a common word helps mitigate a dictionary attack.
Dictionary attack: Similar to a brute-force attack, in that multiple password guesses are attempted. However, the dictionary attack is based on a dictionary of commonly used words, rather than the brute-force method of trying all possible combinations. Picking a password that is not a common word helps mitigate a dictionary attack.
![]() Botnet: A software robot is typically thought of as an application on a machine that can be controlled remotely (for example, a Trojan horse or a backdoor in a system). If a collection of computers is infected with such software robots, called bots, this collection of computers (each of which is known as a zombie) is called a botnet. Because of the potentially large size of a botnet, it might compromise the integrity of a large amount of data.
Botnet: A software robot is typically thought of as an application on a machine that can be controlled remotely (for example, a Trojan horse or a backdoor in a system). If a collection of computers is infected with such software robots, called bots, this collection of computers (each of which is known as a zombie) is called a botnet. Because of the potentially large size of a botnet, it might compromise the integrity of a large amount of data.
![]() Hijacking a session: An attacker could hijack a TCP session, for example, by completing the third step in the three-way TCP handshake process between an authorized client and a protected server. If an attacker successfully hijacked a session of an authorized device, he might be able to maliciously manipulate data on the protected server.
Hijacking a session: An attacker could hijack a TCP session, for example, by completing the third step in the three-way TCP handshake process between an authorized client and a protected server. If an attacker successfully hijacked a session of an authorized device, he might be able to maliciously manipulate data on the protected server.
Availability Attacks
Availability attacks attempt to limit the accessibility and usability of a system. For example, if an attacker were able to consume the processor or memory resources on a target system, that system might be unavailable to legitimate users.
Availability attacks vary widely, from consuming the resources of a target system to doing physical damage to that system. The following sections describe various availability attacks that might be employed by attackers.
Denial of Service
An attacker can launch a denial-of-service (DoS) attack on a system by sending the target system a flood of data or requests that consume the target system’s resources. Alternatively, some operating systems and applications crash when they receive specific strings of improperly formatted data, and the attacker can leverage such OS/application vulnerabilities to render a system or application inoperable. The attacker often uses IP spoofing to conceal his identity when launching a DoS attack, as illustrated in Figure 12-5.
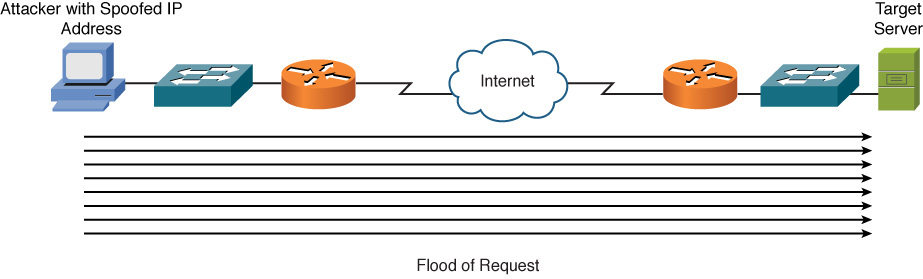
Figure 12-5 DoS Attack
Distributed Denial of Service
Distributed denial-of-service (DDoS) attacks can increase the amount of traffic flooded to a target system. This is a coordinated attack. Specifically, an attacker compromises multiple systems, and those compromised systems, called zombies or botnets, can be instructed by the attacker to simultaneously launch a DDoS attack against a target system. A significant traffic spike (as compared to the baseline) could provide an early indication that an attack is in place. An intrusion prevention system (IPS) is designed to recognize and alert when attacks or malicious traffic is present on the network.
TCP SYN Flood
One variant of a DoS attack is for an attacker to initiate multiple TCP sessions by sending SYN segments but then never complete the three-way TCP handshake. As illustrated in Figure 12-6, the attack can send multiple SYN segments to a target system with false source IP addresses in the header of the SYN segments. Because many servers limit the number of TCP sessions they can have open simultaneously, a SYN flood can render a target system incapable of opening a TCP session with a legitimate user.
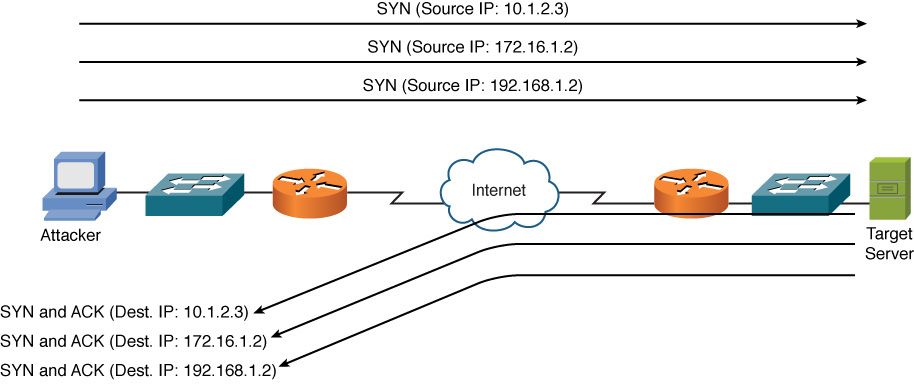
Figure 12-6 TCP SYN Flood Attack Example
Buffer Overflow
Consider a computer program that has been given a dedicated area of memory to which it can write. This area of memory is called a buffer. However, if the program attempts to write more information than the buffer can accommodate, a buffer overflow can occur. If permitted to do so, the program can fill up its buffer and then have its output spill over into the memory area being used for a different program. This can potentially cause the other program to crash. Some programs are known to have this vulnerability (that is, the characteristic of overrunning their memory buffers) and can be exploited by attackers.
ICMP Attacks
Many networks permit the use of Internet Control Message Protocol (ICMP) traffic (for example, ping traffic) because pings can be useful for network troubleshooting. However, attackers can use ICMP for DoS attacks. One ICMP DoS attack variant is called the ping of death, which uses ICMP packets that are too big. Another variant sends ICMP traffic as a series of fragments in an attempt to overflow the fragment reassembly buffers on the target device. Also, a Smurf attack can use ICMP traffic directed to a subnet to flood a target system with ping replies, as illustrated in Figure 12-7. Notice in the figure that the attacker sends a ping to the subnet broadcast address of 172.16.0.0/16. This collection of pings instructs devices on that subnet to send their ping replies to the target system at IP address 10.2.2.2, thus flooding the target system’s bandwidth and processing resources.
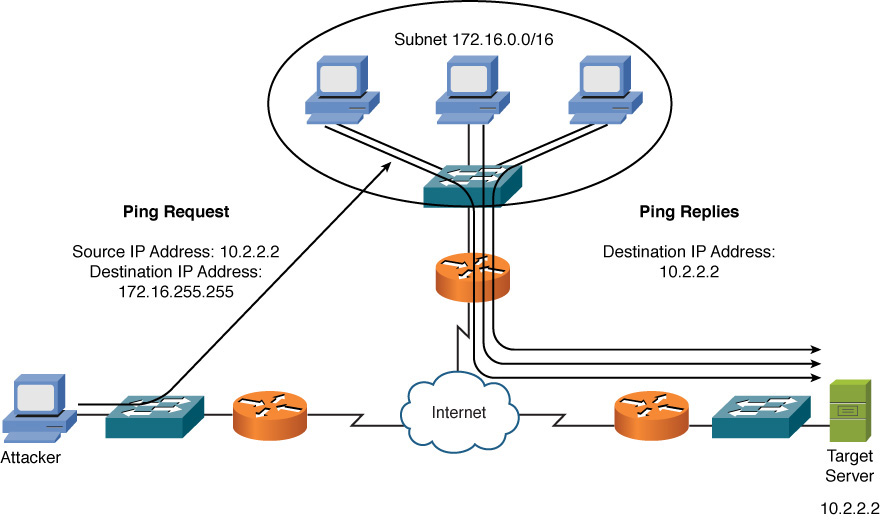
Figure 12-7 Smurf Attack Example
Note
For illustrative purposes, Figure 12-7 only shows three systems in the subnet being used for the Smurf attack. However, realize that thousands of systems could potentially be involved and send ping replies to the target system. This is an example of an amplification attack, which begins small and then is increased as additional devices (often unaware) contribute to the attack. Common protocols such as Domain Name Service (DNS) and Network Time Protocol (NTP) can also be used as part of an amplification attack.
Electrical Disturbances
At a physical level, an attacker could launch an availability attack by interrupting or interfering with the electrical service available to a system. For example, if an attacker gained physical access to a data center’s electrical system, he might be able to cause a variety of electrical disturbances, such as the following:
![]() Power spikes: Excess power for a brief period of time
Power spikes: Excess power for a brief period of time
![]() Electrical surges: Excess power for an extended period of time
Electrical surges: Excess power for an extended period of time
![]() Power fault: A brief electrical outage
Power fault: A brief electrical outage
![]() Blackout: An extended electrical outage
Blackout: An extended electrical outage
![]() Power sag: A brief reduction in power
Power sag: A brief reduction in power
![]() Brownout: An extended reduction in power
Brownout: An extended reduction in power
Note
A standby power supply (SPS) is a lower-end version of an uninterruptible power supply (UPS). Although it is less expensive than a traditional UPS, an SPS’s battery is not inline with the electricity coming from a wall outlet. Instead, an SPS’s battery operates in parallel with the wall power, standing by in the event that the wall power is lost. Because of this configuration, a brief period of time lapses between a power outage and the SPS taking over, which could result in the attached equipment shutting down.
To combat such electrical threats, you might want to install UPS and generator backups for strategic devices in your network. Also, you need to routinely test the UPS and generator backups.
Attacks on a System’s Physical Environment
Attackers could also intentionally damage computing equipment by influencing the equipment’s physical environment. For example, attackers could attempt to manipulate such environmental factors as the following:
![]() Temperature: Because computing equipment generates heat (for example, in data centers or server farms), if an attacker interferes with the operation of an air-conditioning system, the computing equipment could overheat.
Temperature: Because computing equipment generates heat (for example, in data centers or server farms), if an attacker interferes with the operation of an air-conditioning system, the computing equipment could overheat.
![]() Humidity: Because computing equipment is intolerant of moisture, an attacker could, over time, cause physical damage to computing equipment by creating a high level of humidity in a computing environment.
Humidity: Because computing equipment is intolerant of moisture, an attacker could, over time, cause physical damage to computing equipment by creating a high level of humidity in a computing environment.
![]() Gas: Because gas is often flammable, if an attacker injects gas into a computing environment, small sparks in that environment could cause a fire.
Gas: Because gas is often flammable, if an attacker injects gas into a computing environment, small sparks in that environment could cause a fire.
Consider the following recommendations to mitigate such environmental threats:
![]() Computing facilities should be locked (and not accessible via a drop ceiling, a raised floor, or any other way other than a monitored point of access).
Computing facilities should be locked (and not accessible via a drop ceiling, a raised floor, or any other way other than a monitored point of access).
![]() Access should require access credentials (for example, via a card swipe or a biometric scan).
Access should require access credentials (for example, via a card swipe or a biometric scan).
![]() Access points should be visually monitored (for example, via local security personnel or remotely via a camera system).
Access points should be visually monitored (for example, via local security personnel or remotely via a camera system).
![]() Climate control systems should maintain temperature and humidity and send alerts if specified temperature or humidity thresholds are exceeded.
Climate control systems should maintain temperature and humidity and send alerts if specified temperature or humidity thresholds are exceeded.
![]() The fire detection and suppression systems should be designed not to damage electronic equipment.
The fire detection and suppression systems should be designed not to damage electronic equipment.
A business should have a disaster recovery (DR) and business continuity (BC) plan in place so that, in the event of any type of downtime (due to an attack or natural disaster), the company can be back up and running to maintain its business. DR focuses on getting critical applications back online, and BC focuses on the tasks carried out by an organization to ensure that critical business functions continue to operate during and after a disaster. These plans should include training, identification, and roles of the first responders as well as practice drills to confirm the plans are functional. A company without these plans in place could be victims of a permanent denial-of-service (DoS), which could ultimately destroy their business if an attacker has damaged the hardware (by reflashing firmware) with corrupt or defective images to such a point that it is no longer usable.
With this understanding of the three primary targets of an attack (that is, confidentiality, integrity, and availability) and examples of common attacks, the next section presents you with strategies for defending against such attacks.
Physical Controls
To reduce unauthorized access, physical control can and should also be used. Mantraps only allow a single person through a door or entry at a time, requiring every person to authenticate. Authentication could be done via badge readers, biometrics, key fobs, keypads with unique codes for each user, or even a physical security guard checking each user’s ID. Intermediate Distribution Frames (IDFs) and wiring closets should be locked. Monitored closed-circuit TVs (CCTV) can act as a deterrent to unauthorized physical access.
Defending Against Attacks
Upcoming sections in this chapter address how to defend against security threats using network devices (that is, switches, routers, firewalls, VPN concentrators, and IDS/IPS sensors). However, this section presents a collection of best practices for defending a network against attacks.
User Training
Many attacks require user intervention to be carried out. For example, a user needs to execute an application containing a virus before the virus takes any action. Similarly, social engineering requires a user to give sensitive information (such as username and password credentials) to an attacker in order for the attacker to access the user’s account. As a result, several potential attacks can be thwarted through effective user training. For instance, users could be trained on using policies such as the following:
![]() Never give out your password to anyone, even if that person claims to be from IT.
Never give out your password to anyone, even if that person claims to be from IT.
![]() Do not open e-mail attachments from unknown sources.
Do not open e-mail attachments from unknown sources.
![]() Select strong passwords, consisting of at least eight characters and containing a mixture of alphabetic (upper- and lowercase), numeric, and special characters.
Select strong passwords, consisting of at least eight characters and containing a mixture of alphabetic (upper- and lowercase), numeric, and special characters.
![]() Do not visit unauthorized websites.
Do not visit unauthorized websites.
![]() Report suspicious activity.
Report suspicious activity.
![]() Do not run or install any applications not provided directly by the company.
Do not run or install any applications not provided directly by the company.
![]() Change your passwords monthly.
Change your passwords monthly.
This list is only an example, and you should develop a collection of best practices for your users based on your network’s specific circumstances. Users should also know who to contact in the event of a suspected data breach or compromise of the computers and systems the user is responsible for. The users should also know never to run penetration testing tools or other network discovery tools that may cause an unintentional DoS or other harm to the network and its devices. Technical controls such as web/content filtering, port filtering, IP filtering, and access control lists (ACLs) that deny specific traffic can be used to assist in the enforcement of the policies agreed to by the users.
As part of user training and for the safety of human life, emergency procedures should also be communicated and verified with each user, including the building layout, fire-escape plan, safety and emergency exits, doors that automatically fail closed or fail open based on their purpose to contain or allow access, emergency alert systems, fire suppression systems, and HVAC operations and emergency shutoff procedures.
In the data center, procedures for safety related to electrostatic discharge (ESD), grounding, rack installation, lifting, tool safety, and the correct placement of devices should also be planned, communicated, and verified. If there are dangerous substances in or near the work area, a material safety data sheet (MSDS) should be created to identify procedures for handling and working with those substances.
Patching
Some attacks are directed at vulnerabilities known to exist in various operating systems and applications. As these vulnerabilities are discovered, the vendors of the operating systems or applications often respond by releasing a patch. A patch is designed to correct a known bug or fix a known vulnerability in a piece of software. Therefore, network administrators should have a plan for implementing patches as they become available. Network and host-based vulnerability scanning should be done, with proper management authorization, to verify that well-known vulnerabilities are not present on the network. Penetration testing can be done as well to verify that the security measures in place are working as expected.
Note
A patch differs from an update, which, in addition to fixing a known bug or vulnerability, adds one or more features to the software being updated.
Security Policies
One of the main reasons security breaches occur within an organization is the lack of a security policy or, if a security policy is in place, the lack of effectively communicating/enforcing that security policy to all concerned. A security policy is a continually changing document that dictates a set of guidelines for network use. These guidelines complement organizational objectives by specifying rules for how a network is used.
The main purpose of a security policy is to protect the assets of an organization. An organization’s assets include more than just tangible items. Assets also entail things such as intellectual property, processes and procedures, sensitive customer data, and specific server functions (for example, e-mail or web functions).
Aside from protecting an organization’s assets, a security policy serves other purposes, such as the following:
![]() Making employees aware of their obligations in regard to security practices
Making employees aware of their obligations in regard to security practices
![]() Identifying specific security solutions required to meet the goals of a security policy
Identifying specific security solutions required to meet the goals of a security policy
![]() Acting as a baseline for ongoing security monitoring
Acting as a baseline for ongoing security monitoring
One of the more well-known components of a security policy is an acceptable use policy (AUP), also known as an appropriate use policy. An AUP identifies what users of a network are and are not allowed to do on a network. For example, retrieving sports scores during working hours via an organization’s Internet connection might be deemed inappropriate by an AUP.
Because an organization’s security policy applies to various categories of employees (such as management, technical staff, and end users), a single document might not be sufficient. For example, managerial personnel might not be concerned with the technical intricacies of a security policy. However, the technical personnel might be less concerned with why a policy is in place, while end users might be more likely to comply with the policy if they did understand the reasoning behind the rules. Therefore, a security policy might be a collection of congruent, yet separate, documents. Figure 12-8 offers a high-level overview of these complementary documents.
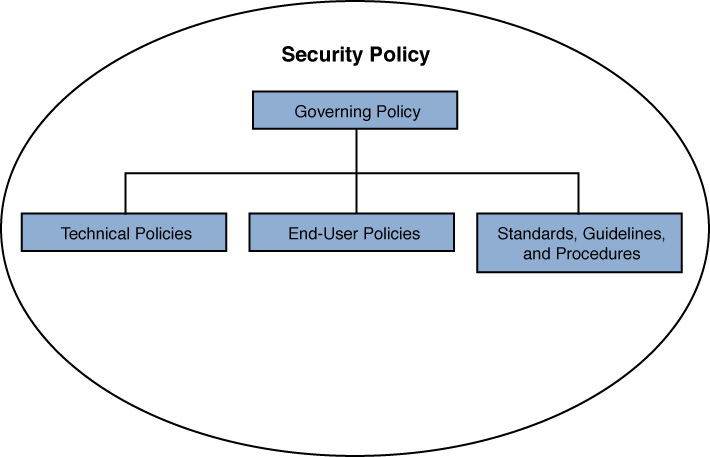
Figure 12-8 Components of a Security Policy
Governing Policy
At a very high level, a governing policy addresses security concepts deemed important to an organization. The governing policy is primarily targeted toward managerial and technical employees. The following are typical elements of a governing policy:
![]() Identification of the issue addressed by the policy
Identification of the issue addressed by the policy
![]() Discussion of the organization’s view of the issue
Discussion of the organization’s view of the issue
![]() Examination of the relevance of the policy to the work environment
Examination of the relevance of the policy to the work environment
![]() Explanation of how employees are to comply with the policy
Explanation of how employees are to comply with the policy
![]() Enumeration of appropriate activities, actions, and processes
Enumeration of appropriate activities, actions, and processes
![]() Explanation of the consequences of noncompliance
Explanation of the consequences of noncompliance
You might want to consult with your company’s legal counsel when formulating a governing policy.
Technical Policies
Technical policies provide a more detailed treatment of an organization’s security policy, as opposed to the governing policy. Typical components of technical policies include specific duties of the security and IT staff in areas such as the following:
![]() E-mail
E-mail
![]() Wireless networks
Wireless networks
![]() Bring your own device (BYOD)
Bring your own device (BYOD)
![]() Remote access
Remote access
Security and IT personnel are the intended target of these technical policies, and these personnel use these policies in performing their day-to-day tasks.
BYOD also allows users to bring their own device’s vulnerabilities if allowed on the network. Devices with Bluetooth capability have the vulnerability of the following attacks:
![]() Bluejacking: The sending of unauthorized messages over a Bluetooth connection to a device
Bluejacking: The sending of unauthorized messages over a Bluetooth connection to a device
![]() Bluesnarfing: Provides unauthorized access from a wireless device through a Bluetooth connection
Bluesnarfing: Provides unauthorized access from a wireless device through a Bluetooth connection
![]() Bluebugging: Creates unauthorized backdoor access to connect a Bluetooth device back to the attacker
Bluebugging: Creates unauthorized backdoor access to connect a Bluetooth device back to the attacker
End-User Policies
End-user policies address security issues and procedures relevant to end users. For example, an end user might be asked to sign an AUP for Internet access. That AUP might state that Internet access is only for business purposes. Then, if an end user is found using the Internet for personal reasons, she could face the consequences outlined in the governing policy. The AUP should include the consent to have monitored the user’s system, e-mail, and digital communications from company devices.
More Detailed Documents
Because the governing policy, technical policies, and end-user policies each target a relatively large population of personnel, these policies tend to be general in nature. However, a comprehensive security policy requires a highly granular treatment of an organization’s procedures. Therefore, more detailed documents, such as the following, are often contained in a security policy:
![]() Standards: Standards support consistency within a network. For example, a standard might specify a limited number of operating systems to be supported in the organization because it would be impractical for the IT staff to support any OS that a user happened to select. Also, standards could apply to configuring devices, such as routers (for example, having a standardized routing protocol).
Standards: Standards support consistency within a network. For example, a standard might specify a limited number of operating systems to be supported in the organization because it would be impractical for the IT staff to support any OS that a user happened to select. Also, standards could apply to configuring devices, such as routers (for example, having a standardized routing protocol).
![]() Guidelines: Standards tend to be mandatory practices, but guidelines tend to be suggestions. For example, a series of best practices might constitute a security policy’s guidelines.
Guidelines: Standards tend to be mandatory practices, but guidelines tend to be suggestions. For example, a series of best practices might constitute a security policy’s guidelines.
![]() Procedures: To support consistency in a network, and as dictated by the previously mentioned standards, a security policy might include a collection of procedures. These procedures are detailed documents that provide step-by-step instructions for completing specific tasks (for example, steps for configuring port security on an Ethernet switch that include manual assignments of access ports to avoid VLAN hopping by malicious hosts connected to a port, port security to limit the number of MAC addresses learned on a port, DHCP snooping to deny a device that is attempting a DHCP-based attack by acting as a DHCP server, MAC address filtering to only allow specific MAC addresses on the port, and dynamic ARP inspection to prevent MAC spoofing from the device connected to the switch port).
Procedures: To support consistency in a network, and as dictated by the previously mentioned standards, a security policy might include a collection of procedures. These procedures are detailed documents that provide step-by-step instructions for completing specific tasks (for example, steps for configuring port security on an Ethernet switch that include manual assignments of access ports to avoid VLAN hopping by malicious hosts connected to a port, port security to limit the number of MAC addresses learned on a port, DHCP snooping to deny a device that is attempting a DHCP-based attack by acting as a DHCP server, MAC address filtering to only allow specific MAC addresses on the port, and dynamic ARP inspection to prevent MAC spoofing from the device connected to the switch port).
Keep in mind that this list is not comprehensive and that you need to create a set of documents to match the security needs of your company.
Incident Response
How an organization reacts to a security violation is called its incident response. Many deterrent controls display warnings such as, “Violators will be prosecuted to the fullest extent of the law.” However, to successfully prosecute an attacker, litigators typically require the following elements to present an effective argument:
![]() Motive: A motive describes why the attacker committed the act. For example, was the attacker a disgruntled employee? Also, potential motives can be valuable to define during an investigation. Specifically, an investigation might begin with those that had a motive to carry out the attack.
Motive: A motive describes why the attacker committed the act. For example, was the attacker a disgruntled employee? Also, potential motives can be valuable to define during an investigation. Specifically, an investigation might begin with those that had a motive to carry out the attack.
![]() Means: With all the security controls in place to protect data or computer systems, you need to determine whether the accused had the means (for example, the technical skills) to carry out the attack.
Means: With all the security controls in place to protect data or computer systems, you need to determine whether the accused had the means (for example, the technical skills) to carry out the attack.
![]() Opportunity: The question of whether the accused had the opportunity to commit an attack asks whether the accused was available to commit the attack. For example, if the accused claims to have been at a ball game at the time of the attack, and if there are witnesses to verify her assertion, it is less likely that the accused indeed committed the attack.
Opportunity: The question of whether the accused had the opportunity to commit an attack asks whether the accused was available to commit the attack. For example, if the accused claims to have been at a ball game at the time of the attack, and if there are witnesses to verify her assertion, it is less likely that the accused indeed committed the attack.
Computer forensics is about legal evidence found in computers and digital storage devices. Another challenge with prosecuting computer-based crime stems from the fragility of data. A time stamp can easily be changed on a file without detection. To prevent such evidence tampering, strict policies and procedures for data handling must be followed. For example, before any investigative work is done on a computer system, a policy might require that multiple copies of a hard drive be made. One or more master copies could be locked up, and copies could be given to the defense and prosecution for their investigation.
Also, to verify the integrity of data since a security incident occurred, you need to be able to show a chain of custody. A chain of custody documents who has been in possession of the data (evidence) since a security breach occurred. A well-prepared organization will have process and procedures that are used when an incident occurs. A plan should include first responders securing the area and then escalating to senior management and authorities when required by policy or law. The chain of custody also includes documentation of the scene, collection of evidence, and maintenance, e-discovery (which is the electronic aspect of identifying, collecting, and producing electronically stored information), transportation of data, forensics reporting, and a process to preserve all forms of evidence and data when litigation is expected. The preservation of the evidence, data, and details is referred to as legal hold.
Vulnerability Scanners
After you deploy your network security solution, components of that solution might not behave as expected. In addition, you might not be aware of some of the vulnerabilities in your network devices. Therefore, you should periodically test your network for weaknesses. Such a test can be performed using applications designed to check for a variety of known weaknesses. These applications are known as vulnerability scanners. These can assist in identifying unnecessary running services, open ports, or unpatched or legacy systems. Examples of these vulnerability scanners include Nessus and Nmap (network mapper).
Nessus
Tenable Network Security has a vulnerability scanning product called Nessus, which is available from http://www.tenable.com/products/nessus. A few of the product features include the following:
![]() Performing audits on systems without requiring an agent to be installed on the systems
Performing audits on systems without requiring an agent to be installed on the systems
![]() Checking system configurations for compliance with an organization’s policy
Checking system configurations for compliance with an organization’s policy
![]() Auditing systems for specific content (for example, credit card information or adult content)
Auditing systems for specific content (for example, credit card information or adult content)
![]() Performing continuous scanning, thus reducing the time required to identify a network vulnerability
Performing continuous scanning, thus reducing the time required to identify a network vulnerability
![]() Scheduling scans to run once, daily, weekly, or monthly
Scheduling scans to run once, daily, weekly, or monthly
Tenable Network Security offers a variety of products for home and business use. Figure 12-9 shows an example of a Nessus scan result.
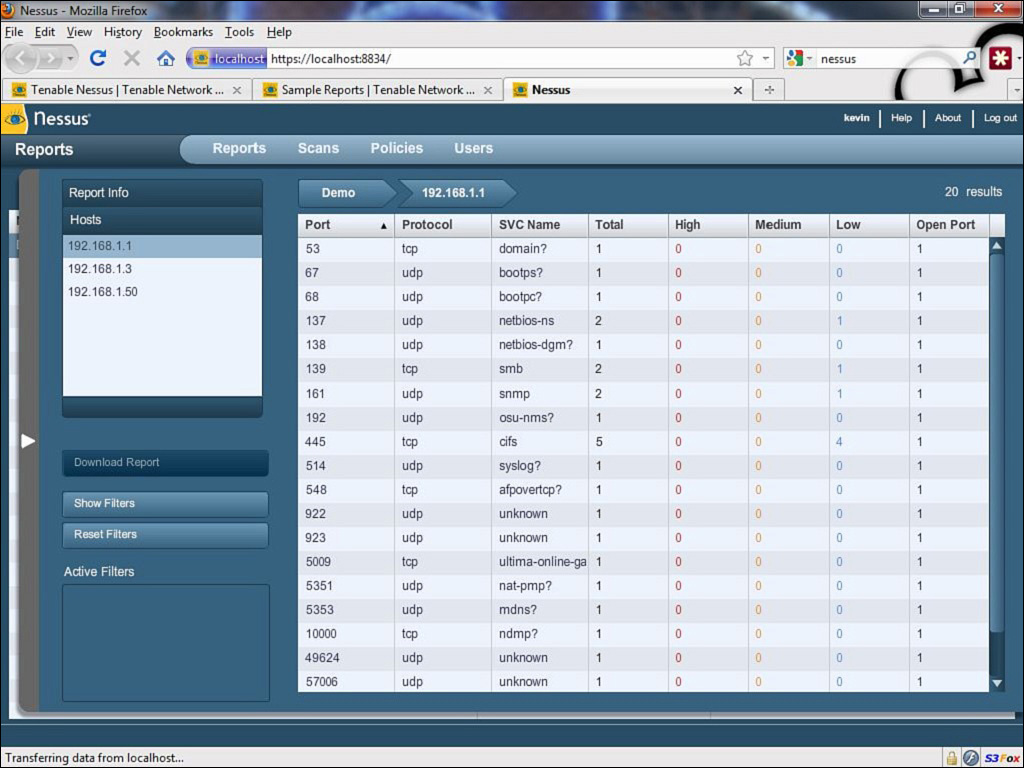
Figure 12-9 Nessus
Nmap
As another example of a vulnerability scanner, consider the Nmap utility. Nmap is a publicly available scanner that can be downloaded from http://nmap.org. Nmap offers features such as the following:
![]() Scanning and sweeping features that identify services running on systems in a specified range of IP addresses
Scanning and sweeping features that identify services running on systems in a specified range of IP addresses
![]() Using a stealth approach to scanning and sweeping, making the scanning and sweeping less detectible by hosts and IPS technology
Using a stealth approach to scanning and sweeping, making the scanning and sweeping less detectible by hosts and IPS technology
![]() Using OS fingerprinting technology to identify an OS running on a target system (including a percentage of confidence that the OS was correctly detected)
Using OS fingerprinting technology to identify an OS running on a target system (including a percentage of confidence that the OS was correctly detected)
Figure 12-10 illustrates a GUI version of Nmap, where a collection of host IP addresses are scanned for open ports, in addition to a variety of other fingerprinting operations.
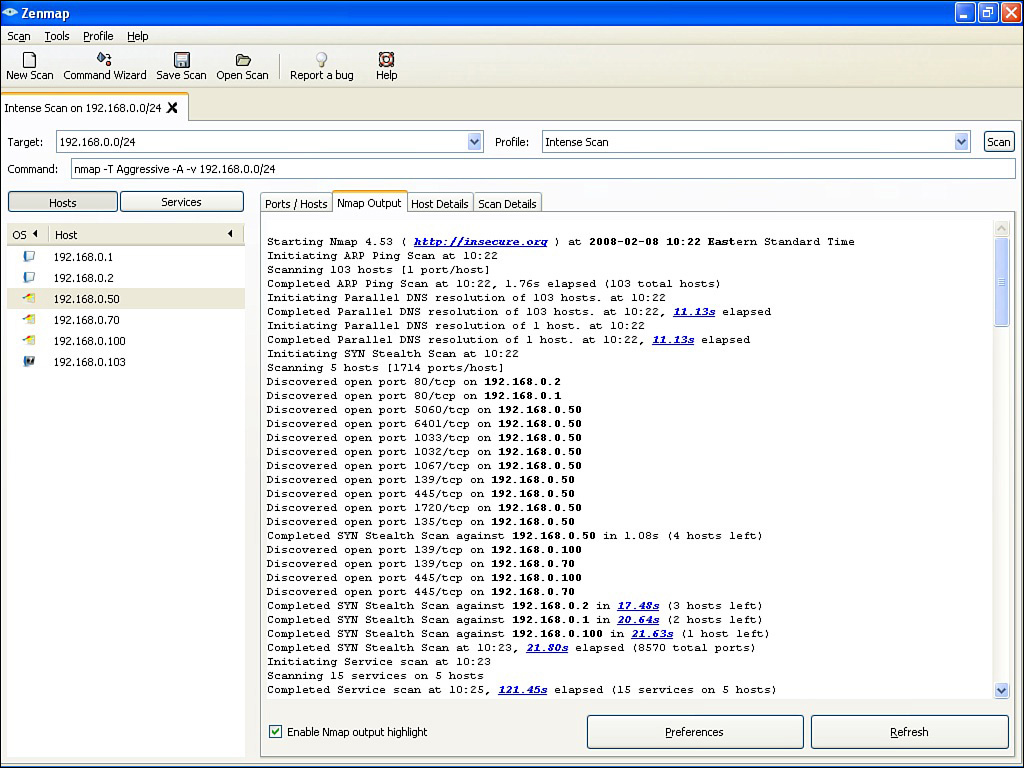
Figure 12-10 Nmap
Note
For larger networks, a network administrator might deploy multiple honey pots, forming a honey net.
Honey Pots and Honey Nets
A honey pot acts as a distracter. Specifically, a system designated as a honey pot appears to be an attractive attack target. One school of thought on the use of a honey pot is to place one or more honey pot systems in a network to entice attackers into thinking a system is real. The attackers then use their resources attacking the honey pot, the end result of which is that the attackers leave the real servers alone.
Another use of a honey pot is as a system that is extensively monitored to learn what an attacker is attempting to do on the system. A honey pot could, as an example, be a UNIX system configured with a weak password. After an attacker logs in, surveillance software could log what the attacker does on the system. This knowledge could then be used to protect real servers in the network.
Access Control Lists
Access control lists (ACLs) are rules usually applied to router interfaces that specify permitted and denied traffic. Although ACL features can vary by router vendor, examples of filtering criteria include IP addresses (source or destination), port number (source or destination), and MAC addresses (source or destination).
Consider Figure 12-11, for example, which shows an ACL being applied to an interface on a Cisco IOS router.

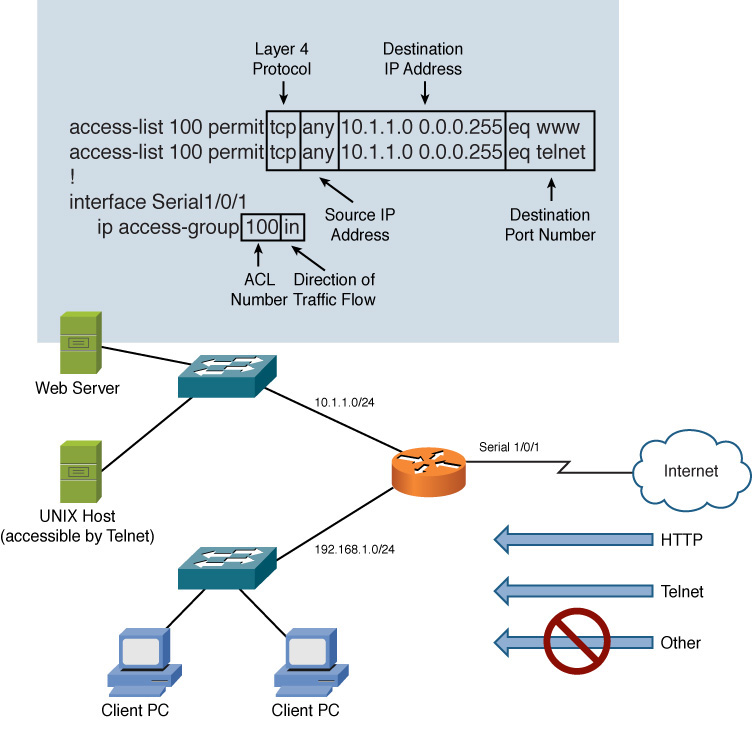
Figure 12-11 ACL Example
This syntax tells the router interface of Serial 1/0/1 to permit incoming Telnet and HTTP traffic from any source and destined for a network of 10.1.1.0/24. However, you might be curious about all the other traffic that attempts to enter interface Serial 1/0/1. Because there is no deny instruction seen in the syntax, is that traffic permitted? Actually, in the case of Cisco IOS routers, ACLs have an implicit (and invisible) deny all instruction. Therefore, any traffic not explicitly permitted is rejected.
Remote-Access Security
Although ACLs can be used to permit or deny specific connections flowing through a router (or switch), you also need to control connections to network devices (for example, routers, switches, or servers). Many of these remote-access security methods have been introduced in preceding chapters. However, as a review, Table 12-2 provides a summary of these protocols and procedures.

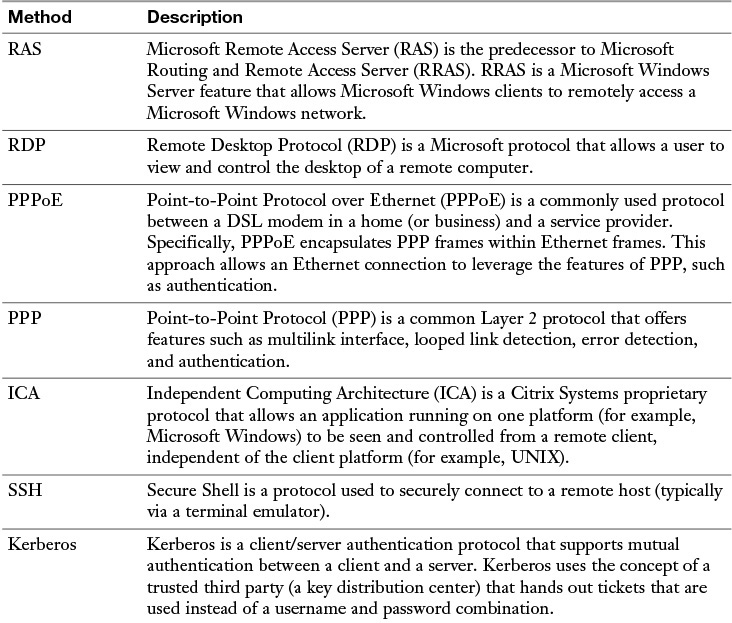

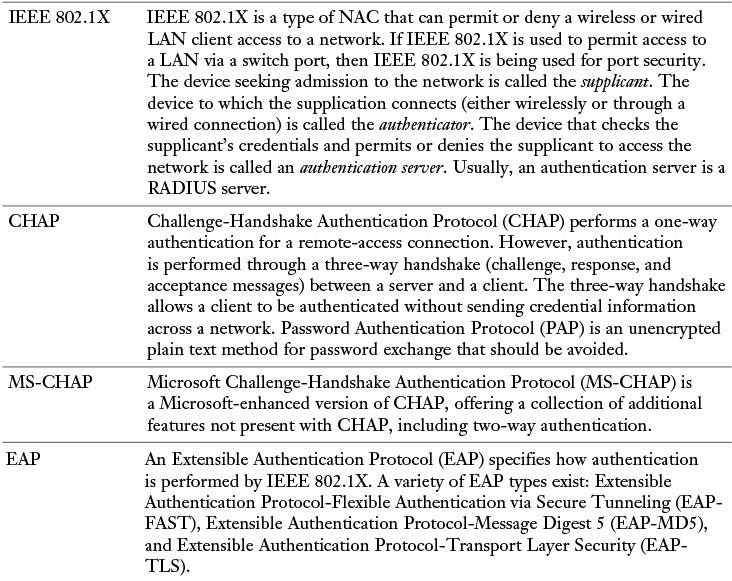
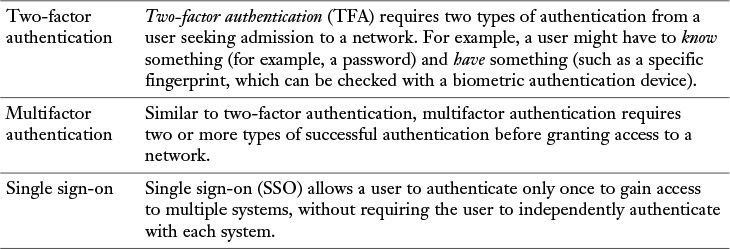
Table 12-2 Remote-Access Security Methods
Firewalls
At this point, this chapter has introduced you to various security threats, along with best practices to protect your network from those threats. In addition, you reviewed a collection of remote-access security methods. In the remainder of this chapter, you are introduced to three additional layers of security that can be applied to a network, often in the form of a dedicated security appliance. These additional layers consist of firewalls, virtual private networks, and intrusion detection and prevention systems. This section focuses on firewalls.
Firewall Types

A firewall defines a set of rules to dictate which types of traffic are permitted or denied as that traffic enters or exits a firewall interface. The actual firewall devices can be either a software firewall or a hardware firewall:
![]() Software firewall: A computer running firewall software that can protect the computer itself (for example, preventing incoming connections to the computer). This is referred to as a host-based firewall. Alternatively, a software firewall could be a computer with more than one network interface card (NIC) running firewall software. This type of software firewall could filter traffic attempting to pass through the computer (that is, coming in one of the NICs and leaving via a different NIC). A firewall that is filtering traffic that is being routed through the firewall is known as a network-based firewall.
Software firewall: A computer running firewall software that can protect the computer itself (for example, preventing incoming connections to the computer). This is referred to as a host-based firewall. Alternatively, a software firewall could be a computer with more than one network interface card (NIC) running firewall software. This type of software firewall could filter traffic attempting to pass through the computer (that is, coming in one of the NICs and leaving via a different NIC). A firewall that is filtering traffic that is being routed through the firewall is known as a network-based firewall.
![]() Hardware firewall: A network appliance that acts as a firewall. This appliance can have multiple interfaces for connecting to areas of a network that require varying levels of security. Hardware-based firewalls usually have higher capacity than software-based firewalls. However, for a small office or home office firewall, the price and performance requirement may be better met with a software-based firewall.
Hardware firewall: A network appliance that acts as a firewall. This appliance can have multiple interfaces for connecting to areas of a network that require varying levels of security. Hardware-based firewalls usually have higher capacity than software-based firewalls. However, for a small office or home office firewall, the price and performance requirement may be better met with a software-based firewall.
As traffic flows into or out of a firewall, the firewall checks the traffic against a set of firewall rules, which might permit or deny the traffic. In addition, many firewalls perform Network Address Translation (NAT) or Port Address Translation (PAT), described in Chapter 6, “Routing IP Packets.” Some firewalls may include a content filtering service that can deny packets through the firewall based on the type of content being requested. An example is a company policy restricting access to gaming websites, and the firewall checking before allowing traffic to a site identified as a gaming website.
Firewall Inspection Types
Some firewalls inspect traffic based solely on a packet’s header. This type of firewall is called a packet-filtering firewall. Other firewalls, however, can recognize that a packet is part of a session that might have originated inside the local network or outside the local network. This type of firewall is called a stateful firewall.
Packet-Filtering Firewall
Earlier, this chapter described the function of ACLs. An ACL can decide whether a packet should be permitted or denied based on the contents of its header (for example, based on source and destination IP address information or source and destination port number information).
A device that filters traffic based on ACL-like rules is a packet filtering firewall. However, a packet-filtering firewall lacks flexibility. For example, in Figure 12-12, a router is acting as a firewall. The ACL applied to interface Serial 1/0/1 permits all traffic from the inside network to go out to the Internet. However, all traffic coming from the Internet is blocked as it attempts to enter the router. Although this might seem like a reasonable ACL, it can prevent a session from being set up between a client on the inside network with a host on the Internet, even if the session originated from the inside client.

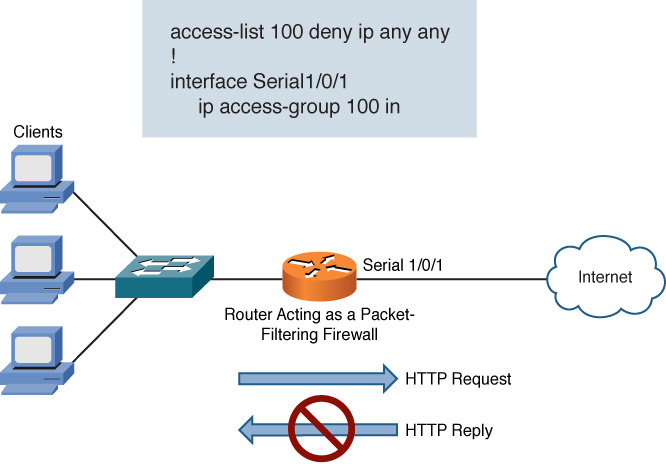
Figure 12-12 Packet-Filtering Firewall
For example, imagine that an inside client running a web browser attempts to contact a web server on the Internet. Although the outgoing HTTP request is permitted, the returning HTTP reply is blocked by the incoming ACL applied to interface Serial 1/0/1. As a result, the HTTP session cannot be established.
Stateful Firewall
Unlike a packet-filtering firewall, a stateful firewall inspects traffic leaving the inside network as it goes out to the Internet. Then, when returning traffic from the same session (as identified by source and destination IP addresses and port numbers) attempts to enter the inside network, the stateful firewall permits that traffic. The process of inspecting traffic to identify unique sessions is called stateful inspection.
As an example, consider Figure 12-13, where a stateful firewall allows return traffic from the Internet for a Telnet session initiated from the inside network (session A). However, Telnet traffic coming from the Internet is blocked if the Telnet session is initiated from a device on the Internet (session B).

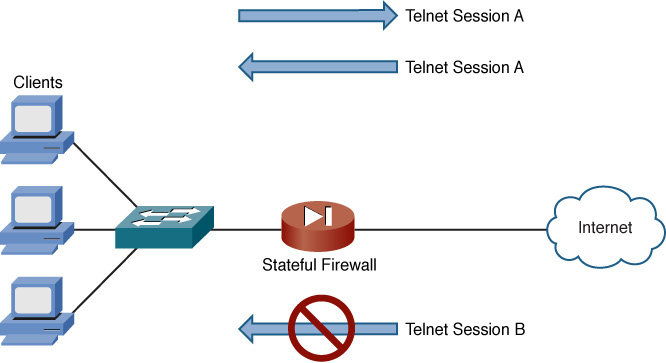
Figure 12-13 Stateful Firewall
Firewall Zones
A firewall’s interfaces can be defined as belonging to different firewall zones. After you define which interfaces belong to which zones, you can set up rules saying what types of traffic are permitted to flow between zones. Consider Figure 12-14, for example. The firewall interface connecting to the inside network (trusted network) is configured as belonging to the INSIDE zone. The firewall interface connecting to the Internet (an untrusted network) is configured as belonging to the OUTSIDE zone. In this example, a rule has been applied to the firewall stating that the traffic source from the INSIDE zone is allowed to go to the OUTSIDE zone. Return traffic from sessions originating in the INSIDE zone is also permitted to come back into the INSIDE zone from the OUTSIDE zone thanks to stateful inspection. However, traffic from sessions originating in the OUTSIDE zone is not permitted to come into the INSIDE zone.

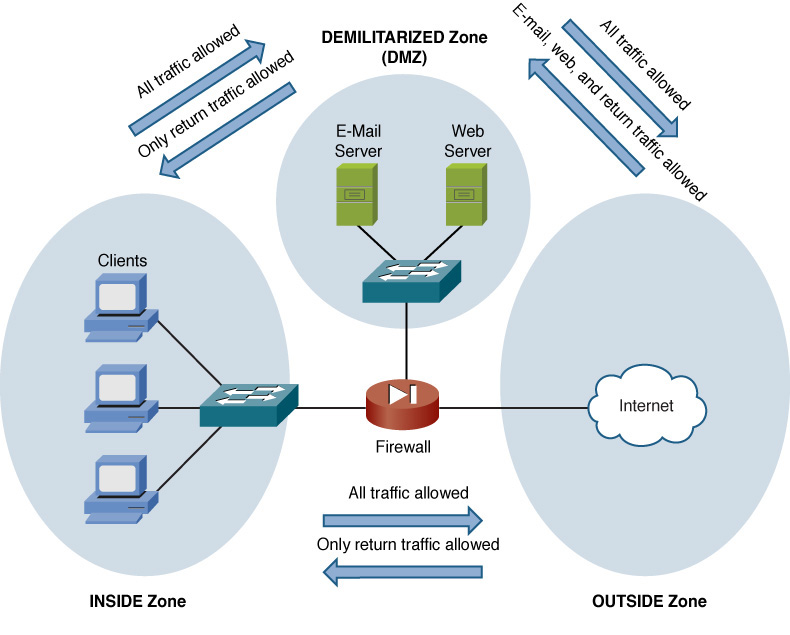
Figure 12-14 Firewall Zone Example
Notice the DEMILITARIZED zone (DMZ). A DMZ often contains servers that should be accessible from the public Internet. This approach would, in this example, allow users on the Internet to initiate an e-mail or a web session coming into an organization’s e-mail or web server. However, other protocols would be blocked.
Unified Threat Management Firewalls
A unified threat management (UTM) firewall or gateway is a device that attempts to bundle multiple security functions into a single physical or logical device. Features of an ideal UTM could include a network intrusion prevention system (IPS), network-based antivirus/antimalware, URL and content filtering, antispam, data-loss prevention (DLP), regulatory compliance checking, stateful filtering, VPN services, multiple interfaces for DMZs, load balancing, user-based access control and filtering, Network Address Translation (NAT), transparent or routed implementation, Secure Sockets Layer (SSL) interception, application layer content analysis, posture assessment for a connecting computer, and more.
A device that is performing posture assessment against a client system usually involves an agent running on the client computer or mobile device, which can be queried from the UTM during the posture assessment to verify that required elements such as security updates or antimalware packages are installed before allowing the client to connect through a VPN to the UTM device. If a client does not meet the requirements, it can be given limited access to a remediation or quarantine area of the network so that the required components can be updated on the client computer before it tries to obtain full access from the UTM system. A UTM could also provide guest network access based on the authentication of the user. An agent running on the client computer could be a persistent agent that is running all the time or a temporary one that is installed/run only during an attempt by the client computer to connect to the UTM.
Depending on the vendor, these may be referred to as UTM, next-generation firewalls (NGFs) or some other marketing term to imply an all-inclusive network security device. As an alternative to purchasing their own UTM device to provide these services, many companies are turning to cloud-based services, where the service provider implements and maintains the system at the service provider location, and the customer purchases these cloud-based services from the provider.
A misconfigured firewall of any type could allow vulnerabilities to be exposed that allow attackers to exploit the firewall itself or the internal and DMZ devices the firewall was intended to protect. Leaving a default password on a firewall and permitting all traffic through the firewall from the outside untrusted network are two examples of a misconfigured firewall.
Virtual Private Networks
Much of today’s workforce (approximately 40 percent, according to Cisco Systems) is located outside of a corporate headquarters location. Some employees work in remote offices, and others telecommute. These remote employees can connect to their main corporate network by using a variety of WAN technologies (such as leased lines and private virtual circuits (PVCs), found in Frame Relay/ATM networks). However, these WAN technologies typically cost more than widely available broadband technologies, such as digital subscriber line (DSL) and cable, which might also offer faster speeds. Fortunately, virtual private networks (VPNs) support secure communication between two sites over an untrusted network (for example, the Internet). The two primary categories of VPNs are site-to-site and client-to-site VPNs:

![]() Site-to-site VPN: A site-to-site VPN interconnects two sites, as an alternative to a leased line, at a reduced cost. Figure 12-15 shows an example of a site-to-site VPN.
Site-to-site VPN: A site-to-site VPN interconnects two sites, as an alternative to a leased line, at a reduced cost. Figure 12-15 shows an example of a site-to-site VPN.
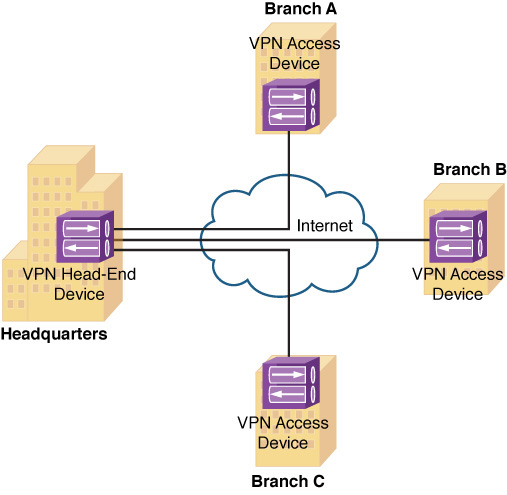
Figure 12-15 Site-to-Site VPN
![]() Client-to-site VPN: A client-to-site VPN (also known as a remote-access VPN) interconnects a remote user with a site, as an alternative to dial-up or ISDN connectivity, at a reduced cost. Figure 12-16 shows an example of a client-to-site VPN.
Client-to-site VPN: A client-to-site VPN (also known as a remote-access VPN) interconnects a remote user with a site, as an alternative to dial-up or ISDN connectivity, at a reduced cost. Figure 12-16 shows an example of a client-to-site VPN.
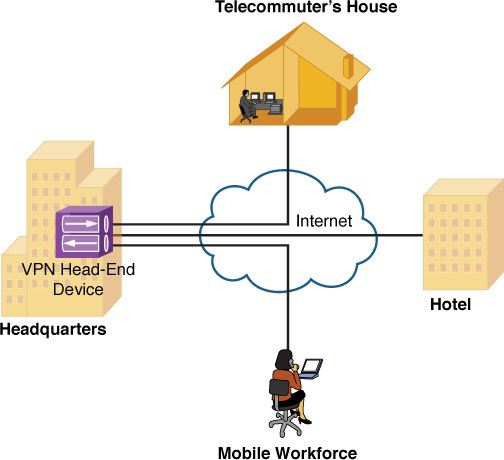
Figure 12-16 Client-to-Site VPN
Although a VPN tunnel might physically pass through multiple service provider routers, the tunnel appears to be a single router hop from the perspective of the routers at each end of the tunnel.
A client-to-site VPN allows a user with software on his client computer to connect to a centralized VPN termination device, and a site-to-site VPN interconnects two sites without requiring the computers at those sites to have any specialized VPN software installed. Client-to-site VPNs could be implemented using a VPN-compatible device, such as a router, firewall, or special-purpose device called a VPN concentrator that is purpose built for handling remote-access client-to-site VPN connections. It is also possible (using the correct software) for two computers to connect to each other directly using a host-to-host IPsec VPN connection.
Overview of IPsec with IKEv1
Broadband technologies, such as cable and DSL, in addition to other VPN transport mechanisms, often traverse an untrusted network, such as the Internet. Therefore, a primary concern with using a broadband technology as a VPN transport is security.
Although different VPN technologies (for example, IP Security [IPsec], generic routing encapsulation [GRE], Layer 2 Transport Protocol [L2TP], and Layer 2 Forwarding [L2F]) offer a variety of features, IPsec VPNs offer strong security features. Specifically, IPsec offers the following protections for VPN traffic:
![]() Confidentiality: Data confidentiality is provided by encrypting data. If a third party intercepts the encrypted data, he would not be able to interpret the data.
Confidentiality: Data confidentiality is provided by encrypting data. If a third party intercepts the encrypted data, he would not be able to interpret the data.
![]() Integrity: Data integrity ensures that data is not modified in transit. For example, routers at each end of a tunnel can calculate a checksum value or a hash value for the data, and if both routers calculate the same value, the data has most likely not been modified in transit.
Integrity: Data integrity ensures that data is not modified in transit. For example, routers at each end of a tunnel can calculate a checksum value or a hash value for the data, and if both routers calculate the same value, the data has most likely not been modified in transit.
![]() Authentication: Data authentication allows parties involved in a conversation to verify that the other party is the party they claim to be.
Authentication: Data authentication allows parties involved in a conversation to verify that the other party is the party they claim to be.
IPsec also scales to a wide range of networks. IPsec operates at Layer 3 of the OSI model (the network layer). As a result, IPsec is transparent to applications, which means that applications do not require any sort of integrated IPsec support.
IKE Modes and Phases
IPsec uses a collection of protocols to provide its features. One of the primary protocols that IPsec uses is Internet Key Exchange (IKE). Specifically, IPsec can provide encryption between authenticated peers using encryption keys, which are periodically changed. IKE, however, allows an administrator to manually configure keys.
IKE can use the three modes of operation to set up a secure communicate path between IPsec peers. These modes are explained in Table 12-3.
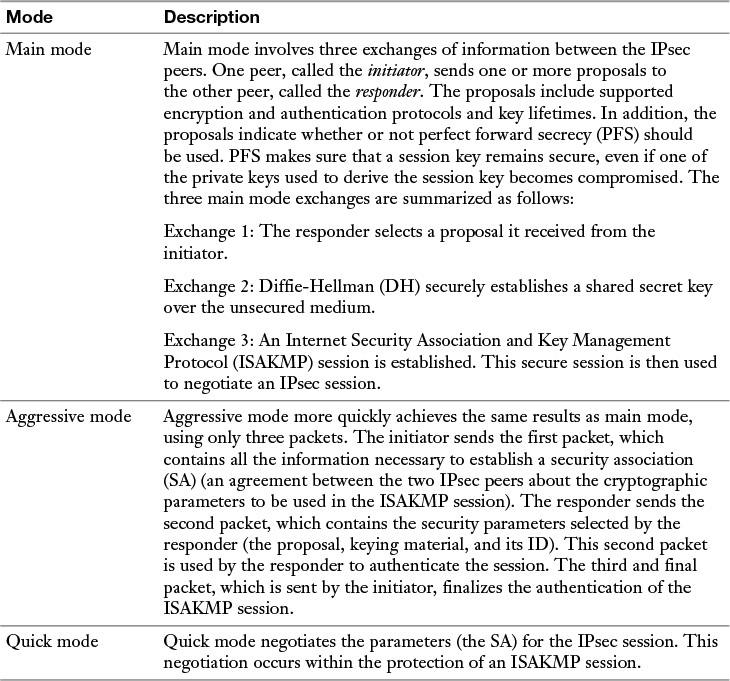
Table 12-3 IKEv1 Modes
The IKEv1 modes reflect the two primary phases of establishing an IPsec tunnel. For example, during IKE Phase 1, a secure ISAKMP session is established using either main mode or aggressive mode. During IKE Phase 1, the IPsec endpoints establish transform sets (which are a collection of encryption and authentication protocols), hash methods, and other parameters needed to establish a secure ISAKMP session (sometimes called an ISAKMP tunnel or an IKE Phase 1 tunnel). As a reminder, this collection of parameters is called a security association (SA). With IKE Phase 1, the SA is bidirectional, which means that the same key exchange is used for data flowing across the tunnel in either direction.
IKE Phase 2 occurs within the protection of an IKE Phase 1 tunnel, using the previously described quick mode of parameter negotiation. A session formed during IKE Phase 2 is sometimes called an IKE Phase 2 tunnel or simply an IPsec tunnel. However, unlike IKE Phase 1, IKE Phase 2 performs unidirectional SA negotiations, which means that each data flow uses a separate key exchange.
Although an IPsec tunnel can be established using just IKE Phase 1 and IKE Phase 2, an optional IKE Phase 1.5 can be used. IKE Phase 1.5 uses the Extended Authentication (XAUTH) protocol to perform user authentication of IPsec tunnels. Like IKE Phase 2, IKE Phase 1.5 is performed within the protection of an IKE Phase 1 tunnel. The user authentication provided by this phase adds a layer of authentication for VPN clients. Also, parameters such as IP, WINS, and DNS server information can be provided to a VPN client during this optional phase. A newer version called IKEv2 combines many of the same functions of IKEv1 and uses an initial IKEv2 tunnel (instead of IKEv1 phase 1) and children security associations (SAs/tunnels) for the IPsec tunnels instead of calling them IKE Phase 2 tunnels.
Authentication Header and Encapsulating Security Payload
In addition to IKE, which establishes the IPsec tunnel, IPsec relies on either the Authentication Header (AH) protocol (IP protocol number 51) or the Encapsulating Security Payload (ESP) protocol (IP protocol number 50). Both AH and ESP offer origin authentication and integrity services, which ensure that IPsec peers are who they claim to be and that the data was not modified in transit.
However, the main distinction between AH and ESP is encryption support. ESP encrypts the original packet, while AH does not offer encryption. As a result, ESP is much more popular on today’s networks.
Both AH and ESP can operate in one of two modes: transport mode or tunnel mode. Figure 12-17 illustrates the structure of an ESP transport mode packet versus an ESP tunnel mode packet.

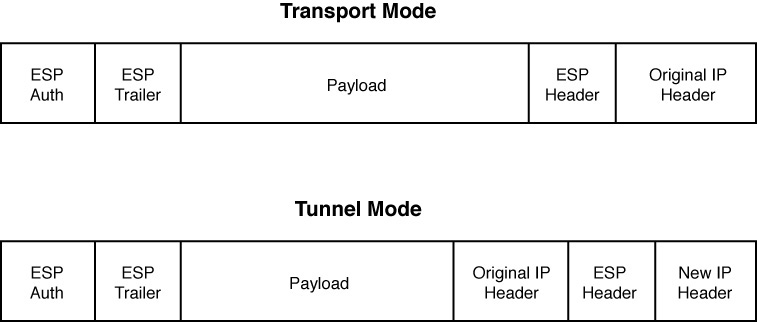
Figure 12-17 Transport Mode Versus Tunnel Mode
Note
You might be concerned that transport mode allows the IP address of the IPsec peers to remain visible during transit, because the original packet’s IP header is used to route a packet. However, IPsec is often used in conjunction with the generic routing encapsulation (GRE) tunneling protocol. In such a scenario, the original IP packet is encapsulated inside of a GRE tunnel packet, which adds a new GRE tunnel header. The GRE packet is then sent over an IPsec tunnel. Even if the IPsec tunnel were running in transport mode, the original packet’s IP header would still not be visible. Instead, the GRE packet’s header would be visible.
Following is a detailed description of these two modes:
![]() Transport mode: Uses a packet’s original IP header, as opposed to adding an additional tunnel header. This approach works well in networks where increasing a packet’s size might cause an issue. Also, transport mode is often used for client-to-site VPNs, where a PC running VPN client software connects back to a VPN termination device at a headquarters location.
Transport mode: Uses a packet’s original IP header, as opposed to adding an additional tunnel header. This approach works well in networks where increasing a packet’s size might cause an issue. Also, transport mode is often used for client-to-site VPNs, where a PC running VPN client software connects back to a VPN termination device at a headquarters location.
![]() Tunnel mode: Unlike transport mode, tunnel mode encapsulates an entire packet. As a result, the encapsulated packet has a new header (an IPsec header). This new header has source and destination IP address information that reflects the two VPN termination devices at different sites. Therefore, tunnel mode is often used in an IPsec site-to-site VPN.
Tunnel mode: Unlike transport mode, tunnel mode encapsulates an entire packet. As a result, the encapsulated packet has a new header (an IPsec header). This new header has source and destination IP address information that reflects the two VPN termination devices at different sites. Therefore, tunnel mode is often used in an IPsec site-to-site VPN.
One reason a GRE tunnel might be used with an IPsec tunnel is a limitation on the part of IPsec. Specifically, an IPsec tunnel can only transmit unicast IP packets. The challenge is that large enterprise networks might have a significant amount of broadcast or multicast traffic (for example, routing protocol traffic). GRE can take any traffic type and encapsulate the traffic in a GRE tunnel packet, which is a unicast IP packet that can then be sent over an IPsec tunnel. Take, for example, a multicast packet used by a routing protocol. Although IPsec cannot directly transport the multicast packet, if the packet is first encapsulated by GRE, the GRE packet can then be sent over an IPsec tunnel, thereby securing the transmission of the multicast packet.
The Five Steps in Setting Up and Tearing Down an IPsec Site-to-Site VPN Using IKEv1
The process of establishing, maintaining, and tearing down an IPsec site-to-site VPN consists of five primary steps. These steps are illustrated in Figure 12-18 and described in detail in the following list.

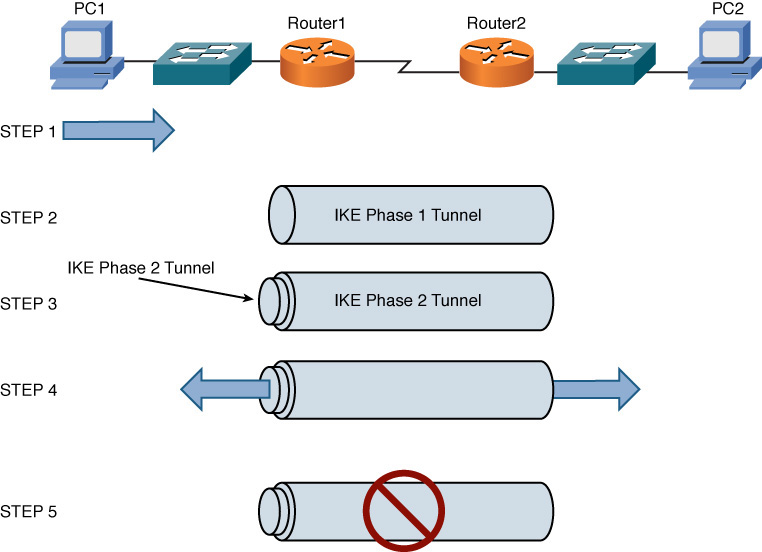
Figure 12-18 IPsec VPN Steps
Step 1. PC1 sends traffic destined for PC2. Router1 classifies the traffic as “interesting” traffic, which initiates the creation of an IPsec tunnel.
Step 2. Router1 and Router2 negotiate a security association (SA) used to form an IKE Phase 1 tunnel, which is also known as an ISAKMP tunnel.
Step 3. Within the protection of the IKE Phase 1 tunnel, an IKE Phase 2 tunnel is negotiated and set up. An IKE Phase 2 tunnel is also known as an IPsec tunnel.
Step 4. After the IPsec tunnel is established, interesting traffic (for example, traffic classified by an ACL) flows through the protected IPsec tunnel. Note that traffic not deemed interesting can still be sent between PC1 and PC2. However, the noninteresting traffic is transmitted outside of the protection of the IPsec tunnel.
Step 5. After no interesting traffic is seen for a specified amount of time the IPsec tunnel is torn down, and the IPsec SA is deleted.
The previous example described an IPsec site-to-site VPN, but the procedure is similar for a client-to-site VPN. IPsec is typically deployed using IKEv1, with its two phases (Phase 1 and Phase 2). There is another IKE version called IKEv2. IKEv2 uses a few less packets in setting up the SAs between VPN peers and does not use the terms Phase 1 and Phase 2. Instead, the initial tunnel is called the IKEv2 SA, and the IPsec SA is referred to as a child tunnel (instead of calling it an IKE Phase 2 tunnel). Additional features that are integrated into IKEv2 include EAP, NAT traversal (the ability to detect NAT in the path between the peers), and the ability to validate the tunnel is still up and active. IKEv1 required additional configuration and vendor add-ons to implement similar types of features.
Other VPN Technologies
Although IPsec VPNs are popular for securely interconnecting sites or connecting a remote client to a site, you need to be aware of other VPN protocols, examples of which are provided in Table 12-4.

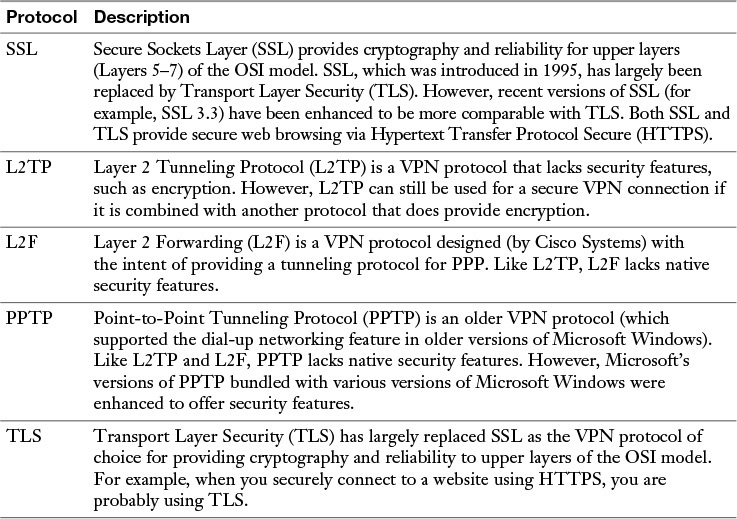
Table 12-4 Examples of VPN Protocols
Intrusion Detection and Prevention
When an attacker launches an attack against a network, intrusion detection system (IDS) and intrusion prevention system (IPS) technologies are often able to recognize the attack and respond appropriately. Attacks might be recognizable by comparing incoming data streams against a database of well-known attack signatures. Other mechanisms for detecting attacks include policy-based and anomaly-based approaches. In addition to dedicated network-based intrusion prevention system (NIPS) sensors, IPS software can be installed on a host to provide a host-based intrusion prevention system (HIPS) or host-based intrusion detection system (HIDS) solution.
IDS Versus IPS
Both IDS and IPS devices can recognize network attacks; they differ primarily in their network placement. Specifically, whereas an IDS device receives a copy of traffic to be analyzed, an IPS device resides inline with the traffic, as illustrated in Figure 12-19.

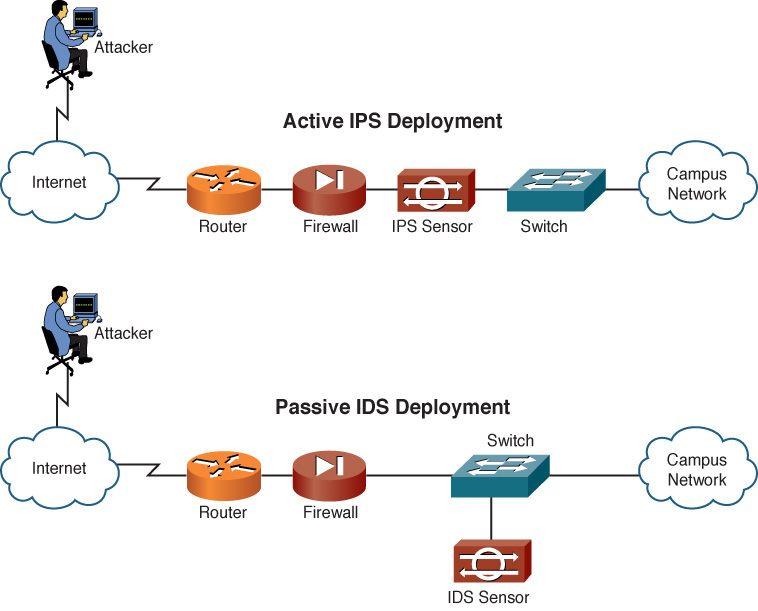
Figure 12-19 IDS and IPS Network Placement
Because the analyzed traffic does not flow through the IDS device, the IDS device is considered to be passive, and the IPS device is considered to be active. Both the IDS and the IPS devices can send alerts to, for example, a management station. Although an IDS device can also communicate with a security appliance or a router to prevent subsequent attack packets, the initially offending traffic reaches its destination. Conversely, an IPS device can drop the traffic inline, thus preventing even the first malicious packet from reaching its intended target.
The previous discussion of IDS versus IPS devices might seem to suggest that IPS devices should always be used instead of IDS devices. However, in some network environments, these two solutions complement one another. For example, an IDS device can add value to a network that already employs an IPS device by verifying that the IPS device is still operational. The IDS device might also identify suspicious traffic and send alerts about that traffic without having the IPS device drop the traffic.
IDS and IPS Device Categories
IDS and IPS devices can be categorized based on how they detect malicious traffic. Alternatively, IPS devices can be categorized based on whether they run on a network device or on a host.
Detection Methods
Consider the following approaches for detecting malicious traffic:

![]() Signature-based detection
Signature-based detection
![]() Policy-based detection
Policy-based detection
![]() Anomaly-based detection
Anomaly-based detection
The following is a detailed discussion of each method.
Signature-Based Detection
The primary method used to detect and prevent attacks using IDS or IPS technologies is signature based. A signature could be a string of bytes, in a certain context, that triggers detection.
For example, attacks against a web server typically take the form of URLs. Therefore, URLs could be searched for a certain string that would identify an attack against a web server.
As another example, the IDS or IPS device could search for a pattern in the MIME header of an e-mail message. However, because signature-based IDS/IPS is, as its name suggests, based on signatures, the administrator needs to routinely update those signature files.
Policy-Based Detection
Another approach to IDS/IPS detection is policy based. With a policy-based approach, the IDS/IPS device needs a specific declaration of the security policy. For example, you could write a network access policy that identified which networks could communicate with other networks. The IDS/IPS device could then recognize out-of-profile traffic that does not conform to the policy, and then report that activity. A policy-based detection could also identify unencrypted channels and clear text credentials and unsecure protocols such as Telnet, SNMPv1, HTTP, FTP, SLIP and TFTP. Secure protocols such as SSH, SNMPv3, TLS/SSL, HTTPS, SFTP, and IPsec should be used when possible to protect the confidentiality of the data flows on the network.
Anomaly-Based Detection
A third approach to detecting or preventing malicious traffic is anomaly based. This approach is prone to false positives because a normal condition is difficult to measurably define. However, there are a couple of options for detecting anomalies:
![]() Statistical anomaly detection: This approach watches network-traffic patterns over a period of time and dynamically builds a baseline. Then, if traffic patterns significantly vary from the baseline, an alarm can be triggered.
Statistical anomaly detection: This approach watches network-traffic patterns over a period of time and dynamically builds a baseline. Then, if traffic patterns significantly vary from the baseline, an alarm can be triggered.
![]() Nonstatistical anomaly detection: This approach allows an administrator to define what traffic patterns are supposed to look like. However, imagine that Microsoft released a large service pack for its Windows 7 OS, and your company has hundreds of computers that are configured to automatically download that service pack. If multiple employees turn on their computers at approximately the same time tomorrow morning, and multiple copies of the service pack simultaneously start to download from http://www.microsoft.com, the IDS/IPS device might consider that traffic pattern to be significantly outside of the baseline. As a result, the nonstatistical anomaly detection approach could lead to a false positive (an alarm being triggered in the absence of malicious traffic). A zero-day attack is one that exploits a previously unknown vulnerability. An anomaly-based IPS may be able to indicate abnormal behavior, compared to the baseline of normal activity, which could assist you in discovering a new type of attack that is being used against your network.
Nonstatistical anomaly detection: This approach allows an administrator to define what traffic patterns are supposed to look like. However, imagine that Microsoft released a large service pack for its Windows 7 OS, and your company has hundreds of computers that are configured to automatically download that service pack. If multiple employees turn on their computers at approximately the same time tomorrow morning, and multiple copies of the service pack simultaneously start to download from http://www.microsoft.com, the IDS/IPS device might consider that traffic pattern to be significantly outside of the baseline. As a result, the nonstatistical anomaly detection approach could lead to a false positive (an alarm being triggered in the absence of malicious traffic). A zero-day attack is one that exploits a previously unknown vulnerability. An anomaly-based IPS may be able to indicate abnormal behavior, compared to the baseline of normal activity, which could assist you in discovering a new type of attack that is being used against your network.
Note
Anomaly-based detection is also known as behavior-based detection.
Deploying Network-Based and Host-Based Solutions
NIPS and HIPS solutions can work in tandem. For example, although a NIPS solution can inspect traffic flowing through the network, what if a host had an SSL connection to a server, and the malicious traffic traveled over the SSL connection? In that instance, the NIPS hardware would be unable to analyze the malicious traffic because it would be encrypted inside of the SSL connection. However, a HIPS software solution could analyze the malicious traffic after the traffic was decrypted on the host. Similarly, a NIPS device might be able to prevent a DoS attack or recognize network reconnaissance patterns, and a HIPS solution could focus on the protection of applications and host resources.
Figure 12-20 illustrates the deployment of network-based IDS (NIDS), NIPS, and HIPS technologies in the same network. Notice the sensors are strategically deployed at network boundaries (that is, coming into the network from the Internet and going into the DMZ). As previously discussed, both NIDS and NIPS devices complement the functions of one another. In addition, HIPS software is deployed on strategic hosts, which are the HTTP, DNS, and e-mail hosts in this example. The NIDS, NIPS, and HIPS devices can send any alarms triggered on their respective devices to a management console. Using input from these diverse sources, the management console software might be able to perform event correlation to recognize broader network attack patterns, rather than just examining a single attack against a single device.

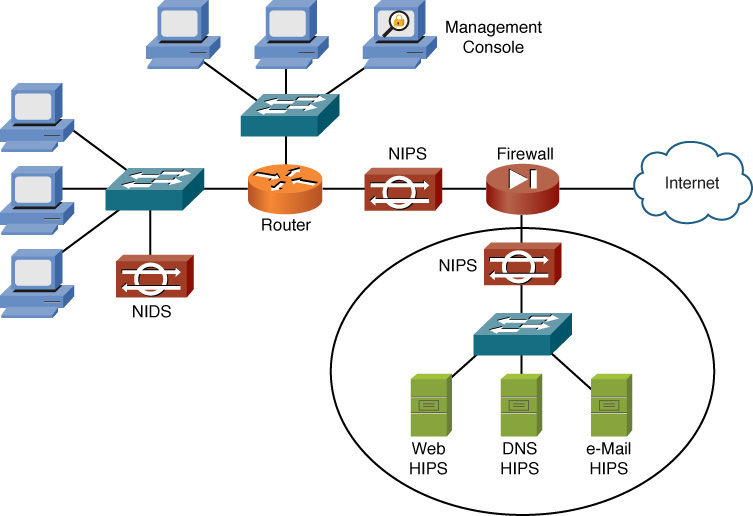
Figure 12-20 NIDS, NIPS, and HIPS Deployment Example
Real-World Case Study
Acme Inc. has decided to use a centralized RADIUS server for the authentication authorization and accounting on its network. This server will interact with Microsoft Active Directory (AD) to verify existing usernames and passwords that are already in AD. When users log in to their local computers, Active Directory using Kerberos will authenticate those users. For wireless network access, 802.11i/WPA2 enterprise is being used, leveraging the same RADIUS server.
When users access the Internet, the firewall will implement controls based on user. By implementing a unified threat management (UTM) system such as Check Point, the UTM can integrate with both the RADIUS server and Active Directory. Features such as intrusion prevention, stateful firewall, antimalware, VPN, application layer inspection, and URL filtering can all be integrated as part of their network-based UTM solution. The interaction between the UTM, wireless security, and Microsoft AD assists in not having to re-create the same user account in multiple different places.
In addition to the network protection provided by the UTM, critical servers will run a host-based intrusion prevention system as an extra precaution.
Traffic sent between the headquarters location and any of the branch offices over the WAN will have confidentiality and data integrity by implementing a site-to-site VPN using IPsec. The AES encryption will provide the confidentiality, and the SHA or HMAC hashing will provide the data integrity. The VPN also provides the ability to authenticate the peer on the other side of the VPN to avoid a man-in-the-middle attack.
For remote users who need to connect over the Internet to either the branch or the headquarters office, remote-access VPNs will be used for the authentication, confidentiality, and data integrity that the VPNs can provide.
ACME’s public-facing web servers will enroll with a certificate authority and request identity certificates. Using server-side identity certificates, ACME can implement SSL/TLS/HTTPS and provide secure connectivity for customers who are connecting to these web servers. The servers will be running as virtualized systems in VMware’s vSphere.
Policies have been created and communicated to all employees, including user awareness training, about the responsibilities of users on the network. Limited rights have been given to users on their local computers. This will help reduce malicious software being installed on those computers. Each of the computers is also running host-based antivirus and antimalware software.
The company has authorized a third-party vendor to perform periodic vulnerability scans in addition to specifically controlled penetration testing on Acme’s network. Acme has decided to internally manage its updates and patch management for its local systems, including virtualized servers and workstations that are on premise.
Acme is working on a bring your own device (BYOD) policy that would allow users to have access to corporate data on their personal devices. However, until they determine a safe and best practice for BYOD, the current policy is that no company data may be accessed or stored on any device that is not company issued.
On the switch ports, the features of DHCP snooping, port security, dynamic ARP inspection, 802.1X, and MAC address filtering have been configured to reduce the risk of attack coming in on one of the switch ports.
Accounting logs and user account activity are periodically reviewed, which can assist in identifying malicious or unauthorized activity on the network.
Summary
The main topics covered in this chapter are the following:
![]() Security fundamentals were discussed. Specifically, you were introduced to the security goals of confidentiality, integrity, and availability. Then you were presented with several examples of common network threats.
Security fundamentals were discussed. Specifically, you were introduced to the security goals of confidentiality, integrity, and availability. Then you were presented with several examples of common network threats.
![]() You reviewed best practice recommendations for defending against threats to network security. These recommendations included such things as user training, patching, having a security policy, having an incident response policy, testing your own network with vulnerability scanners, distracting attackers with honey pots, and blocking unwanted traffic with access control lists.
You reviewed best practice recommendations for defending against threats to network security. These recommendations included such things as user training, patching, having a security policy, having an incident response policy, testing your own network with vulnerability scanners, distracting attackers with honey pots, and blocking unwanted traffic with access control lists.
![]() A collection of remote-access security technologies was presented (for example, SSH, AAA, and NAC).
A collection of remote-access security technologies was presented (for example, SSH, AAA, and NAC).
![]() Firewalls were discussed, along with firewall types, inspection types, and firewall zones.
Firewalls were discussed, along with firewall types, inspection types, and firewall zones.
![]() Virtual private networks were introduced, along with various VPN protocols. However, the primary focus was on IPsec, and you saw a detailed explanation of how an IPsec tunnel is established.
Virtual private networks were introduced, along with various VPN protocols. However, the primary focus was on IPsec, and you saw a detailed explanation of how an IPsec tunnel is established.
![]() You saw how to defend your network against well-known attacks using IDS and IPS sensors.
You saw how to defend your network against well-known attacks using IDS and IPS sensors.
Exam Preparation Tasks
Review All the Key Topics
Review the most important topics from inside the chapter, noted with the Key Topic icon in the outer margin of the page. Table 12-5 lists these key topics and the page numbers where each is found.
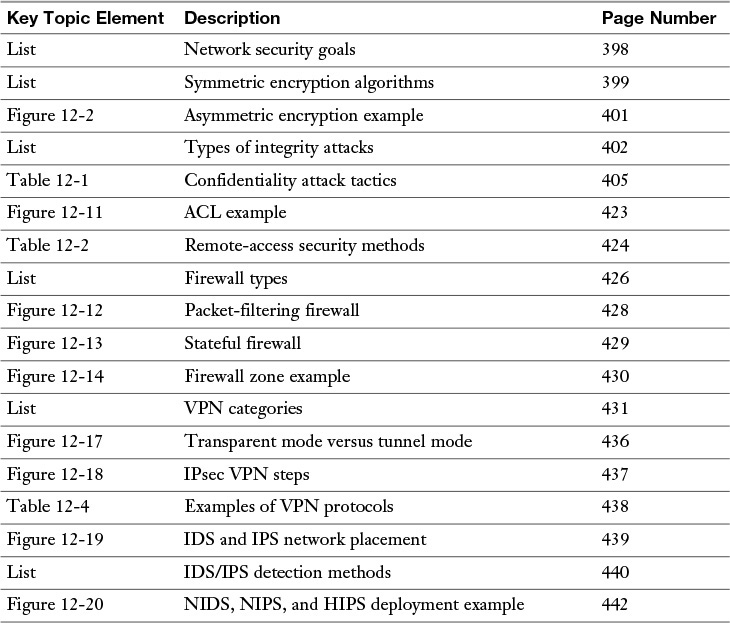
Table 12-5 Key Topics for Chapter 12
Complete Tables and Lists from Memory
Print a copy of Appendix D, “Memory Tables” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix E, “Memory Table Answer Key,” also on the DVD, includes the completed tables and lists so you can check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the Glossary:
symmetric encryption
asymmetric encryption
Advanced Encryption Standard (AES)
RSA
pretty good privacy (PGP)
GNU Privacy Guard (GPC)
public key infrastructure (PKI)
Challenge-Response Authentication Mechanism Message Digest 5 (CRAM-MD5)
denial of service (DoS)
social engineering
FTP bounce
distributed denial of service (DDoS)
buffer overflow
security policy
acceptable use policy (AUP)
Nessus
Nmap
honey pot
honey net
access control list (ACL)
Kerberos
Remote Authentication Dial-In User Service (RADIUS)
Terminal Access Controller Access-Control System Plus (TACACS+)
two-factor authentication
multifactor authentication
single sign-on (SSO)
software firewall
hardware firewall
stateful firewall
unified threat management (UTM)
demilitarized zone (DMZ)
virtual private network (VPN)
site-to-site VPN
client-to-site
remote-access VPN
IP security (IPsec)
Internet Key Exchange (IKE)
Internet Security Association and Key Management Protocol (ISAKMP)
security association (SA)
Authentication Header (AH)
Encapsulating Security Payload (ESP)
Secure Sockets Layer (SSL)
Layer 2 Tunneling Protocol (L2TP)
Layer 2 Forwarding (L2F)
Point-to-Point Tunneling Protocol (PPTP)
intrusion detection system (IDS)
intrusion prevention system (IDS)
network-based IDS (NIDS)
network-based IPS (NIPS)
host-based IPS (HIPS)
Complete Chapter 12 Hands-On Lab in Network+ Simulator Lite
![]() Security Appliance Terminology and Methods
Security Appliance Terminology and Methods
Review Questions
The answers to these review questions are in Appendix A, “Answers to Review Questions.”
1. Which of the following is a symmetric encryption algorithm available in 128-bit, 192-bit, and 256-bit key versions?
a. RSA
b. 3DES
c. AES
d. TKIP
2. In what type of attack does the attacker compromise multiple systems and then instruct those compromised systems, called zombies, to simultaneously flood a target system with traffic?
a. DoS
b. TCP SYN flood
c. Buffer overflow
d. DDoS
3. Which of the following is a continually changing document that dictates a set of guidelines for network use?
a. Security policy
b. Post-mortem report
c. Syslog report
d. QoS policy
4. What type of software application should network administrators routinely use to verify the security of their network and check for any weaknesses?
a. Honey pot
b. Posture monitor
c. Profile scanner
d. Vulnerability scanner
5. Which of the following are characteristics of RADIUS? (Choose two.)
a. TCP based
b. UDP based
c. Encrypts an entire authentication packet
d. Only encrypts the password in an authentication packet
6. What feature allows a firewall to permit traffic to flow from a trusted network (for example, a corporate intranet) to an untrusted network (for example, the Internet) and then allow return traffic for that session, while blocking sessions initiated on the untrusted network?
a. Packet filtering
b. Stateful inspection
c. Demilitarized zone
d. Implicit deny all instruction
7. Which of the following is an IPsec protocol that provides authentication and integrity services but does not support encryption?
a. IKE Phase I
b. IKE Phase II
c. AH
d. ESP
8. Which of the following protocols are most commonly used to provide security for an HTTPS connection? (Choose two.)
a. L2TP
b. SSL
c. PPTP
d. TLS
9. Which of the following security solutions consists of software running on a host to protect that host against a collection of well-known attacks?
a. HIPS
b. NIDS
c. L2F
d. NIPS
10. From the following list, identify the detection methods commonly used by IPS sensors. (Choose three.)
a. Signature based
b. Distribution based
c. Policy based
d. Behavior based
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.