CEH Certified Ethical Hacker Practice Exams Second Edition (2014)
Reconnaissance: Information Gathering for the Ethical Hacker
This chapter includes questions from the following topics:
• Define active and passive footprinting
• Identify methods and procedures in information gathering
• Understand the use of whois, ARIN, and nslookup
• Describe DNS record types
• Define and describe Google hacking
• Use Google hacking in footprinting
![]()
Criminology (the study of the nature, causes, control, and prevention of criminal behavior) is a fascinating subject, and while we’re concentrating on the virtual world in this book, it’s amazing how much footprinting is done in the physical criminal world as well. Most of us have already heard a million times the standard things we’re supposed to do to make our homes less desirable as a target for the bad guys. Things such as keeping your house well lit, installing timers on lights and TVs to make the house appear “lived in” all the time, and installing a good alarm system are so common in these discussions that we tend to nod off in boredom when a security expert starts talking about them. But did you know most common burglars prefer to work during the daytime, when it’s most likely you’re not at home at all? Did you know most don’t give a rip about your alarm system because they plan on being inside for eight to ten minutes or less? And did you know that most timer systems for lights don’t change a thing in the bad guy’s mind because there’s usually sound associated with people being home?
For the sake of example, take an imaginary ride with me around my subdivision here in Satellite Beach, Florida, and we’ll try thinking like a criminal footprinting a neighborhood for targets. Maybe we’ll start by just driving around the neighborhood to ascertain who the nosy neighbors are and what houses make the most promising opportunities. This house on our right is in a cul de sac and provides more privacy and less police patrol traffic than those on the main drag. That house over there? Yeah, it looks like the yard hasn’t been mowed for a while, so maybe they aren’t home or they just don’t pay as close attention to home details as the other houses do. The owners of that two-story over there have a dog, so we’ll probably avoid that one. But look here: This house has a giant box leaned against the garbage can showing the brand-new 65-inch LED TV the owner has just purchased. We should probably write this address down for a closer look later. And the house across the pond there with the sliding glass door? It definitely has potential.
As fascinating as footprinting a building might seem, were you aware that you, as a person, could be footprinted in the physical world as well? According to several studies on the matter, criminals are good at sensing weakness based just on the way you walk. In one such study, 47 inmates at a maximum-security prison were surveyed, and the findings showed that social predators are very good at picking victims based on their gait, posture, and stride. The study provided the inmates with a film of 12 people (eight women and four men, some of whom had been attacked before) walking down a street and asked them to rate each person as a potential victim. The ratings were then compared against each person’s actual history. Surprisingly (or maybe not so surprisingly), the people who the criminals picked as likely victims were usually the same ones who had been victimized in the past. Inmates described the men and women they saw as targets as “walking like an easy target...slow, with short strides.” What distinguished the likely victims from the rest of the pedestrians? Things like posture, body language, pace, length of stride, and awareness of their environment. Nonverbal communication works wonderfully well, and a person’s level of self-confidence can be identified just by the style of walk. Walk with your head down at a slow or unorganized, meandering pace, and you’re screaming to the world you lack self-confidence. Walk fast, fluidly, and with a purpose, and you’re less likely to be a target.
I could go on and on here (I really like this subject and could chat about it forever), but this book is about the virtual world, and I’m prepping you to be an ethical hacker, not a policeman working a beat. This chapter is also all about reconnaissance and footprinting—in the virtual world—and is all about the methods and tools to gather information about your targets before you even try to attack them.
![]()
 STUDY TIPS There are tons of questions from this particular segment of hacking, namely because it’s so important to gather good intelligence before starting an attack. Sure, you can sometimes get lucky and strike quickly, but oftentimes he who puts in the work during footprinting reaps the biggest rewards.
STUDY TIPS There are tons of questions from this particular segment of hacking, namely because it’s so important to gather good intelligence before starting an attack. Sure, you can sometimes get lucky and strike quickly, but oftentimes he who puts in the work during footprinting reaps the biggest rewards.
The biggest area of focus you’ll probably see on your actual exam will revolve around DNS. Know your record types like the back of your hand, play with whois so you know what you’re looking at, and get really familiar with nslookup. The biggest area to trip you up will most likely come in the form of active versus passive reconnaissance. I can’t help you much there other than to remind you that sometimes the exam and the real world are at opposites.
You’ll see a few questions on the other stuff too. Know your e-mail headers well, and by all means start practicing your Google hacking right now—you’ll definitely need it. Most Google hacking questions will require you to know exact syntax, so be careful in your study and practice.
1. The result of a whois search on a target is listed here:
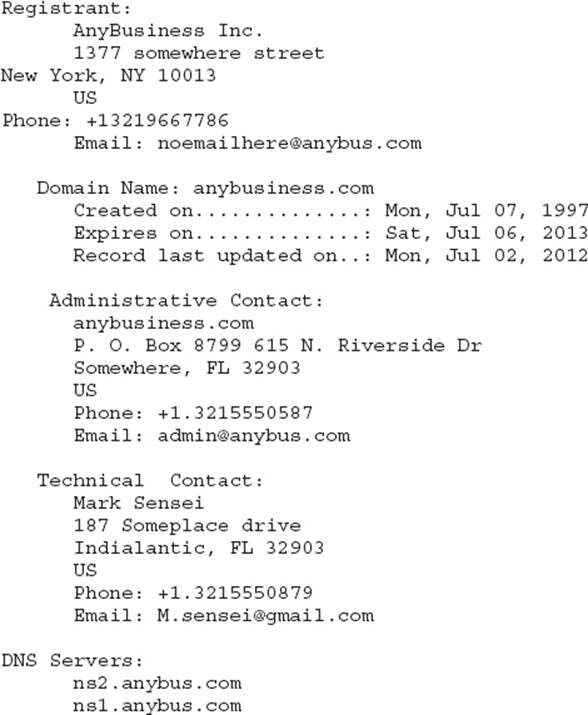
Which of the following is a true statement regarding this output?
A. Anybusiness.com was registered using GoDaddy.com.
B. The technical contact for this website may have entered personal information at registration.
C. There is no information within this output useful for a zone transfer.
D. The administrative and technical contacts are the same.
2. A pen test team member sends an e-mail to an address that she knows is not valid inside an organization. Which of the following is the best explanation for why she took this action?
A. To possibly gather information about internal hosts used in the organization’s e-mail system
B. To start a denial-of-service attack
C. To determine an e-mail administrator’s contact information
D. To gather information about how e-mail systems deal with invalid addressed messages
3. From the partial e-mail header provided, which of the following represents the true originator of the e-mail message?
Return-path: <SOMEONE@anybiz.com>
Delivery-date: Wed, 13 Apr 2011 00:31:13 +0200
Received: from mailexchanger.anotherbiz.com([220.15.10.254])
by mailserver.anotherbiz.com running ExIM with esmtp
id xxxxxx-xxxxxx-xxx; Wed, 13 Apr 2011 01:39:23 +0200
Received: from mailserver.anybiz.com ([158.190.50.254] helo=mailserver.
anybiz.com)
by mailexchanger.anotherbiz.com with esmtp id xxxxxx-xxxxxx-xx
for USERJOE@anotherbiz.com; Wed, 13 Apr 2011 01:39:23 +0200
Received: from SOMEONEComputer [217.88.53.154]
(helo=[SOMEONEcomputer])
by mailserver.anybiz.com with esmtpa (Exim x.xx)
(envelope-from <SOMEONE@anybiz.com) id xxxxx-xxxxxx-xxxx
for USERJOE@anotherbiz.com; Tue, 12 Apr 2011 20:36:08 -0100
Message-ID: <xxxxxxxx.xxxxxxxx@anybiz.com>
Date: Tue, 12 Apr 2011 20:36:01 -0100
X-Mailer: Mail Client
From: SOMEONE Name <SOMEONE@anybiz.com>
To: USERJOE Name <USERJOE@anotherbiz.com>
Subject: Something to consider
...
A. 220.15.10.254.
B. 158.190.50.254.
C. 217.88.53.154.
D. The e-mail header does not show this information.
4. You are looking for files with the terms CEH and V8 in their titles. Which Google hack is the appropriate one?
A. inurl:CEHinurl:V7
B. allintitle:CEH V7
C. intitle:CEHinurl:V7
D. allinurl:CEH V7
5. You’ve just kicked off a penetration test against a target organization and have decided to perform a little passive footprinting. One of the first sites you visit is a job board, where the company has listed various openings. What is the primary useful footprinting information to be gained through this particular search?
A. Insight into the HR processes of the company
B. Insight into the operating systems, hardware, and applications in use
C. Insight into corporate security policy
D. None of the above
6. Which of the following activities is not considered passive footprinting?
A. Dumpster diving
B. Reviewing financial sites for company information
C. Clicking links within the company’s public website
D. Calling the company’s help desk line
7. Examine the following command sequence:
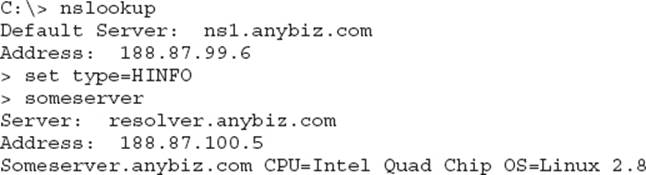
Which of the following best describes the intent of the command sequence?
A. The operator is enumerating a system named someserver.
B. The operator is attempting DNS poisoning.
C. The operator is attempting a zone transfer.
D. The operator is attempting to find a name server.
8. You are footprinting information for a pen test. Social engineering is part of your reconnaissance efforts, and some of it will be active in nature. You take steps to ensure that if the social engineering efforts are discovered at this early stage, any trace efforts point to another organization. Which of the following terms best describes what you are participating in?
A. Anonymous footprinting
B. Pseudonymous footprinting
C. Passive footprinting
D. Redirective footprinting
9. You are setting up DNS for your enterprise. Server A is both a web server and an FTP server. You want to advertise both services for this machine as name references your customers can use. Which DNS record type would you use to accomplish this?
A. NS
B. SOA
C. MX
D. PTR
E. CNAME
10. A company has a publicly facing web application. Its internal intranet-facing servers are separated and protected by a firewall. Which of the following choices would be helpful in protecting against unwanted enumeration?
A. Allowing zone transfers to any
B. Ensuring there are no A records for internal hosts on the public-facing name server
C. Changing the preference number on all MX records to zero
D. Not allowing any DNS query to the public-facing name server
11. Within the DNS system a primary server (SOA) holds and maintains all records for the zone. Secondary servers will periodically ask the primary if there have been any updates, and if updates have occurred, they will ask for a zone transfer to update their own copies. Under what conditions will the secondary name server request a zone transfer from a primary?
A. When the primary SOA record serial number is higher than the secondary’s
B. When the secondary SOA record serial number is higher than the primary’s
C. Only when the secondary reboots or restarts services
D. Only when manually prompted to do so
12. Examine the following SOA record:
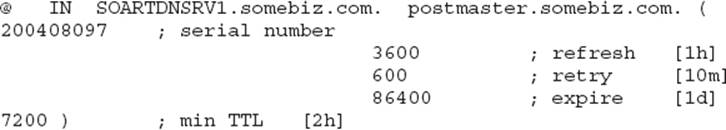
If a secondary server in the enterprise is unable to check in for a zone update within an hour, what happens to the zone copy on the secondary?
A. The zone copy is dumped.
B. The zone copy is unchanged.
C. The serial number of the zone copy is decremented.
D. The serial number of the zone copy is incremented.
13. Which protocol and port number combination is used by default for DNS zone transfers?
A. UDP 53
B. UDP 161
C. TCP 53
D. TCP 22
14. Examine the following command-line entry:
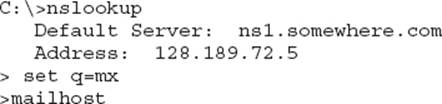
Which two statements are true regarding this command sequence? (Choose two.)
A. Nslookup is in noninteractive mode.
B. Nslookup is in interactive mode.
C. The output will show all mail servers in the zone somewhere.com.
D. The output will show all name servers in the zone somewhere.com.
15. Joe accesses the company website, www.anybusi.com, from his home computer and is presented with a defaced site containing disturbing images. He calls the IT department to report the website hack and is told they do not see any problem with the site—no files have been changed, and when accessed from their terminals (inside the company), the site appears normally. Joe connects over VPN into the company website and notices the site appears normally. Which of the following might explain the issue?
A. DNS poisoning
B. Route poisoning
C. SQL injection
D. ARP poisoning
16. One way to mitigate against DNS poisoning is to restrict or limit the amount of time records can stay in cache before they’re updated. Which DNS record type allows you to set this restriction?
A. NS
B. PTR
C. MX
D. CNAME
E. SOA
17. Which of the following may be a security concern for an organization?
A. The internal network uses private IP addresses registered to an Active Directory–integrated DNS server.
B. An external DNS server is Active Directory integrated.
C. All external name resolution requests are accomplished by an ISP.
D. None of the above.
18. Which of the following is a good footprinting tool for discovering information on a publicly traded company’s founding, history, and financial status?
A. SpiderFoot
B. EDGAR Database
C. Sam Spade
D. Pipl.com
19. What method does traceroute use to map routes traveled by a packet?
A. By carrying a hello packet in the payload, forcing the host to respond
B. By using DNS queries at each hop
C. By manipulating the time to live (TTL) parameter
D. By using ICMP Type 5, code 0 packets
20. Brad is auditing an organization and is asked to provide suggestions on improving DNS security. Which of the following would be valid options to recommend? (Choose all that apply.)
A. Implementing split-horizon operation
B. Restricting zone transfers
C. Obfuscating DNS by using the same server for other applications and functions
D. Blocking all access to the server on port 53
21. A zone file consists of which records? (Choose all that apply.)
A. PTR
B. MX
C. SN
D. SOA
E. DNS
F. A
G. AX
22. Examine the following SOA record:

How long will the secondary server wait before asking for an update to the zone file?
A. 1 hour
B. 2 hours
C. 10 minutes
D. 1 day
23. A colleague enters the following into a Google search string:
![]()
Which of the following is most correct concerning this attempt?
A. The search engine will not respond with any result because you cannot combine Google hacks in one line.
B. The search engine will respond with all pages having the word intranet in their title and human resources in the URL.
C. The search engine will respond with all pages having the word intranet in the title and in the URL.
D. The search engine will respond with only those pages having the word intranet in the title and URL and with human resources in the text.
24. Amanda works as senior security analyst and overhears a colleague discussing confidential corporate information being posted on an external website. When questioned on it, he claims about a month ago he tried random URLs on the company’s website and found confidential information. Amanda visits the same URLs but finds nothing. Where can Amanda go to see past versions and pages of a website?
A. Search.com
B. Google cache
C. Pasthash.com
D. Archive.org
25. Which of the following is a primary service of the U.S. Computer Security Incident Response Team (CSIRT)?
A. CSIRT provides an incident response service to enable a reliable and trusted single point of contact for reporting computer security incidents worldwide.
B. CSIRT provides a computer security surveillance service to supply a government with important intelligence information on individuals traveling abroad.
C. CSIRT provides a penetration testing service to support exception reporting on incidents worldwide by individuals and multinational corporations.
D. CSIRT provides a vulnerability assessment service to assist law enforcement agencies with profiling an individual’s property or company’s asset.
26. Your client’s business is headquartered in Japan. Which regional registry would be the best place to look for footprinting information?
A. APNIC
B. RIPE
C. ASIANIC
D. ARIN
E. LACNIC
![]()
1. B
2. A
3. C
4. B
5. B
6. D
7. A
8. B
9. E
10. B
11. A
12. B
13. C
14. B, C
15. A
16. E
17. B
18. B
19. C
20. A, B
21. A, B, D, F
22. A
23. D
24. D
25. A
26. A
1. The result of a whois search on a target is listed here:
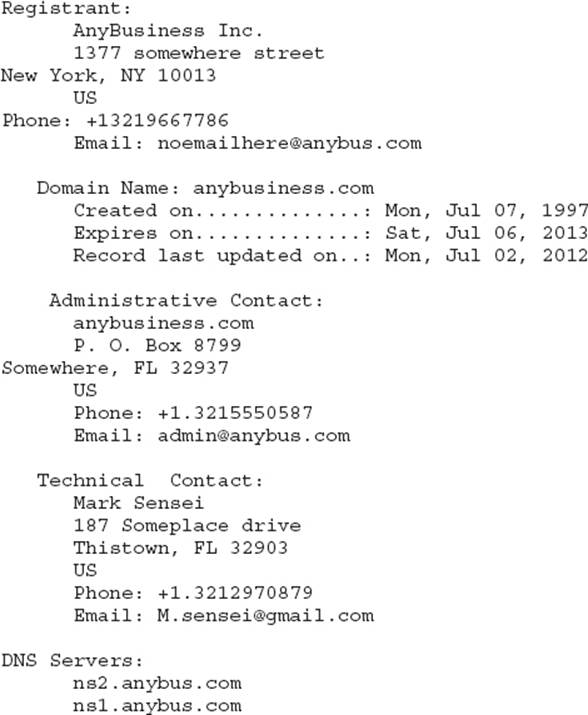
Which of the following is a true statement regarding this output?
A. Anybusiness.com was registered using GoDaddy.com.
B. The technical contact for this website may have entered personal information at registration.
C. There is no information within this output useful for a zone transfer.
D. The administrative and technical contacts are the same.
![]() B. The Technical Contact listing displays the technical contact’s name, as well as what may be their personal phone number. The address? It’s probably where they work, but you never know. This could turn out to be nothing, but it might provide you with an “in” for social engineering efforts later.
B. The Technical Contact listing displays the technical contact’s name, as well as what may be their personal phone number. The address? It’s probably where they work, but you never know. This could turn out to be nothing, but it might provide you with an “in” for social engineering efforts later.
![]() A is incorrect because the registrant is clearly listed as Anybusiness.com. You’ll find these whois searches to be hit-and-miss sometimes. Every once in a while there is a ton of information. Sometimes it’s bare-bones basics. Had this been registered with GoDaddy.com, it would look something like this:
A is incorrect because the registrant is clearly listed as Anybusiness.com. You’ll find these whois searches to be hit-and-miss sometimes. Every once in a while there is a ton of information. Sometimes it’s bare-bones basics. Had this been registered with GoDaddy.com, it would look something like this:

![]() C is incorrect because the target’s DNS servers are listed right there at the bottom. If you’re going to pull a zone transfer, you’ll need to know the DNS servers holding the proper information.
C is incorrect because the target’s DNS servers are listed right there at the bottom. If you’re going to pull a zone transfer, you’ll need to know the DNS servers holding the proper information.
![]() D is incorrect because both are clearly different. The administrative contact is listed as a business name—smart idea. The technical contact, however, may be personal in nature.
D is incorrect because both are clearly different. The administrative contact is listed as a business name—smart idea. The technical contact, however, may be personal in nature.
2. A pen test team member sends an e-mail to an address that she knows is not valid inside an organization. Which of the following is the best explanation for why she took this action?
A. To possibly gather information about internal hosts used in the organization’s e-mail system.
B. To start a denial-of-service attack
C. To determine an e-mail administrator’s contact information
D. To gather information about how e-mail systems deal with invalid addressed messages
![]() A. The thought process behind this is a lot like banner grabbing or any of a hundred different forced error situations in hacking: Lots of information can be gleaned from responses to an error situation. A bogus internal address has the potential to provide more information about the internal servers used in the organization, including IP addresses and other pertinent details.
A. The thought process behind this is a lot like banner grabbing or any of a hundred different forced error situations in hacking: Lots of information can be gleaned from responses to an error situation. A bogus internal address has the potential to provide more information about the internal servers used in the organization, including IP addresses and other pertinent details.
![]() B is incorrect because a bogus e-mail doesn’t necessarily indicate the beginning of a DoS attack.
B is incorrect because a bogus e-mail doesn’t necessarily indicate the beginning of a DoS attack.
![]() C is incorrect because the e-mail administrator’s contact information is not sent on invalid e-mail responses.
C is incorrect because the e-mail administrator’s contact information is not sent on invalid e-mail responses.
![]() D is incorrect because we already know how systems deal with bogus e-mail addresses—what we don’t know is what servers inside this particular organization carry out those steps.
D is incorrect because we already know how systems deal with bogus e-mail addresses—what we don’t know is what servers inside this particular organization carry out those steps.
3. From the partial e-mail header provided, which of the following represents the true originator of the e-mail message?
Return-path: <SOMEONE@anybiz.com>
Delivery-date: Wed, 13 Apr 2011 00:31:13 +0200
Received: from mailexchanger.anotherbiz.com([220.15.10.254])
by mailserver.anotherbiz.com running ExIM with esmtp
id xxxxxx-xxxxxx-xxx; Wed, 13 Apr 2011 01:39:23 +0200
Received: from mailserver.anybiz.com ([158.190.50.254] helo=mailserver.
anybiz.com)
by mailexchanger.anotherbiz.com with esmtp id xxxxxx-xxxxxx-xx
for USERJOE@anotherbiz.com; Wed, 13 Apr 2011 01:39:23 +0200
Received: from SOMEONEComputer [217.88.53.154]
(helo=[SOMEONEcomputer])
by mailserver.anybiz.com with esmtpa (Exim x.xx)
(envelope-from <SOMEONE@anybiz.com) id xxxxx-xxxxxx-xxxx
for USERJOE@anotherbiz.com; Tue, 12 Apr 2011 20:36:08 -0100
Message-ID: <xxxxxxxx.xxxxxxxx@anybiz.com>
Date: Tue, 12 Apr 2011 20:36:01 -0100
X-Mailer: Mail Client
From: SOMEONE Name <SOMEONE@anybiz.com>
To: USERJOE Name <USERJOE@anotherbiz.com>
Subject: Something to consider
...
A. 220.15.10.254.
B. 158.190.50.254.
C. 217.88.53.154.
D. The e-mail header does not show this information.
![]() C. E-mail headers are packed with information showing the entire route the message has taken, and I can guarantee you’ll see at least one question on your exam about them. You’ll most likely be asked to identify the true originator—the machine (person) who sent it in the first place (even though in the real world with proxies and whatnot to hide behind it may be impossible). This is clearly shown in line 9: Received: from SOMEONEComputer [217.88.53.154] (helo=[SOMEONEcomputer]). But don’t just study and rely on that one section. Watch the entire trek the message takes and make note of the IPs along the way.
C. E-mail headers are packed with information showing the entire route the message has taken, and I can guarantee you’ll see at least one question on your exam about them. You’ll most likely be asked to identify the true originator—the machine (person) who sent it in the first place (even though in the real world with proxies and whatnot to hide behind it may be impossible). This is clearly shown in line 9: Received: from SOMEONEComputer [217.88.53.154] (helo=[SOMEONEcomputer]). But don’t just study and rely on that one section. Watch the entire trek the message takes and make note of the IPs along the way.
![]() A and B are incorrect because these IPs do not represent the true originator of the message. They show e-mail servers that are passing/handling the message.
A and B are incorrect because these IPs do not represent the true originator of the message. They show e-mail servers that are passing/handling the message.
![]() D is incorrect because the e-mail header definitely shows the true originator.
D is incorrect because the e-mail header definitely shows the true originator.
4. You are looking for files with the terms CEH and V8 in their titles. Which Google hack is the appropriate one?
A. inurl:CEHinurl:V7
B. allintitle:CEH V7
C. intitle:CEHinurl:V7
D. allinurl:CEH V7
![]() B. The Google search operator allintitle searches for pages that contain the string, or strings, you specify. It also allows for the combination of strings in the title, so you can search for more than one term within the title of a page.
B. The Google search operator allintitle searches for pages that contain the string, or strings, you specify. It also allows for the combination of strings in the title, so you can search for more than one term within the title of a page.
![]() A is incorrect because the operator inurl looks only in the URL of the site, not the page title. In this example, the search might bring you to a page like this: http://anyplace.com/apache_Version/pdfs.html.
A is incorrect because the operator inurl looks only in the URL of the site, not the page title. In this example, the search might bring you to a page like this: http://anyplace.com/apache_Version/pdfs.html.
![]() C is incorrect because the inurl operator isn’t looking in the page title. Yes, you can combine operators, but these two just won’t get this job done.
C is incorrect because the inurl operator isn’t looking in the page title. Yes, you can combine operators, but these two just won’t get this job done.
![]() D is incorrect because allinurl does not look at page titles; it’s concerned only with the URL itself. As with the title searches, this allinurl operator allows you to combine search strings.
D is incorrect because allinurl does not look at page titles; it’s concerned only with the URL itself. As with the title searches, this allinurl operator allows you to combine search strings.
5. You’ve just kicked off a penetration test against a target organization and have decided to perform a little passive footprinting. One of the first sites you visit is a job board, where the company has listed various openings. What is the primary useful footprinting information to be gained through this particular search?
A. Insight into the HR processes of the company
B. Insight into the operating systems, hardware, and applications in use
C. Insight into corporate security policy
D. None of the above
![]() B. Jobs boards are great sources of information. You probably wouldn’t get much of a response if you called the business up and said, “Hi! I’ll be attempting a hack into your network. Would you be so kind as to tell me your server infrastructure and if you’re using Microsoft Exchange for your e-mail?” However, go to a job board, and the listing will provide all that for you anyway. If they’re asking for system administrator experience on Linux RHEL 8, you’re already ahead of the game. Job postings list the set of skills, technical knowledge, and system experience required, so why not use them in preparation?
B. Jobs boards are great sources of information. You probably wouldn’t get much of a response if you called the business up and said, “Hi! I’ll be attempting a hack into your network. Would you be so kind as to tell me your server infrastructure and if you’re using Microsoft Exchange for your e-mail?” However, go to a job board, and the listing will provide all that for you anyway. If they’re asking for system administrator experience on Linux RHEL 8, you’re already ahead of the game. Job postings list the set of skills, technical knowledge, and system experience required, so why not use them in preparation?
![]() A is incorrect because while the HR process may be usable in a long-term attack—for social engineering purposes—you’re probably not going to get too much actual policy/process information here, and, frankly, that’s not what you’d be looking for.
A is incorrect because while the HR process may be usable in a long-term attack—for social engineering purposes—you’re probably not going to get too much actual policy/process information here, and, frankly, that’s not what you’d be looking for.
![]() C is incorrect because that type of information simply isn’t put in a job listing. If it is, they have serious problems a pen test simply isn’t going to fix.
C is incorrect because that type of information simply isn’t put in a job listing. If it is, they have serious problems a pen test simply isn’t going to fix.
![]() D is incorrect because ignoring job listings as part of your reconnaissance effort is folly. Why ignore such a gold mine of easily obtainable information? Depending on how deeply they go into describing job duties and knowledge requirements, you might be able to build a pretty good picture of your attack before even leaving the living room (or wherever you do your recon from).
D is incorrect because ignoring job listings as part of your reconnaissance effort is folly. Why ignore such a gold mine of easily obtainable information? Depending on how deeply they go into describing job duties and knowledge requirements, you might be able to build a pretty good picture of your attack before even leaving the living room (or wherever you do your recon from).
6. Which of the following activities is not considered passive footprinting?
A. Dumpster diving
B. Reviewing financial sites for company information
C. Clicking links within the company’s public website
D. Calling the company’s help desk line
![]() D. This one may be a little tricky, but it’s pretty easy if you think about it. Remember active and passive footprinting can be defined by two things: what you touch and how much discovery risk you put yourself in. Social engineering in and of itself is not all passive or active in nature. In the case of dumpster diving, it’s considered passive. Pick up a phone and call someone inside the company or talk to people in the parking lot, however, and you’ve exposed yourself to discovery and are now practicing active footprinting.
D. This one may be a little tricky, but it’s pretty easy if you think about it. Remember active and passive footprinting can be defined by two things: what you touch and how much discovery risk you put yourself in. Social engineering in and of itself is not all passive or active in nature. In the case of dumpster diving, it’s considered passive. Pick up a phone and call someone inside the company or talk to people in the parking lot, however, and you’ve exposed yourself to discovery and are now practicing active footprinting.
![]() A is incorrect because digging through the trash for useful information is passive footprinting: According to EC-Council and this exam, your discovery risk is negligible, and you’re not touching the company’s network or personnel. Now, in the real world, rummaging through someone’s trash on private property with no authorization and in full view of security personnel is probably going to get you caught and is about as passive as a Tasmanian Devil, but for your exam, ditch your hold on the real world and please remember it’s passive.
A is incorrect because digging through the trash for useful information is passive footprinting: According to EC-Council and this exam, your discovery risk is negligible, and you’re not touching the company’s network or personnel. Now, in the real world, rummaging through someone’s trash on private property with no authorization and in full view of security personnel is probably going to get you caught and is about as passive as a Tasmanian Devil, but for your exam, ditch your hold on the real world and please remember it’s passive.
![]() B is incorrect because reviewing financial sites for company information is a method of gaining competitive intelligence. As we know, competitive intelligence refers to the information gathered by a business entity about their competitor’s customers, products, and marketing. Most of this information is readily available and can be acquired through a host of different means.
B is incorrect because reviewing financial sites for company information is a method of gaining competitive intelligence. As we know, competitive intelligence refers to the information gathered by a business entity about their competitor’s customers, products, and marketing. Most of this information is readily available and can be acquired through a host of different means.
![]() C is incorrect because while you are actively participating in moving around inside the company’s website, you are not necessarily putting yourself at discovery risk or touching anything the company doesn’t want you to. The public website is placed there for people to use, and the odds of someone picking up your clicks out of the thousands they receive every day anyway are minimal. Granted, if you keep digging through their site and get deep enough (for example, you dig your way to an admin portal on a SAP site), you can, and should, be detected.
C is incorrect because while you are actively participating in moving around inside the company’s website, you are not necessarily putting yourself at discovery risk or touching anything the company doesn’t want you to. The public website is placed there for people to use, and the odds of someone picking up your clicks out of the thousands they receive every day anyway are minimal. Granted, if you keep digging through their site and get deep enough (for example, you dig your way to an admin portal on a SAP site), you can, and should, be detected.
7. Examine the following command sequence:

Which of the following best describes the intent of the command sequence?
A. The operator is enumerating a system named someserver.
B. The operator is attempting DNS poisoning.
C. The operator is attempting a zone transfer.
D. The operator is attempting to find a name server.
![]() A. The HINFO record type is one of those really great ideas that was designed to make life easier on everyone yet turned out to be a horrible idea. Defined in RFC 1035, Host Information (HINFO) DNS records were originally intended to provide the type of computer and operating system a host uses (back in the day, you could also put things in like room numbers and other descriptions in the record, too). However, to avoid publicly advertising that information (for obvious reasons), they’re simply not used much anymore. And if you find one on a public-facing machine, it’s a sure sign of incompetence on the part of the server administrators. In this example, the type is set to HINFO, and a machine name—someserver—is provided.
A. The HINFO record type is one of those really great ideas that was designed to make life easier on everyone yet turned out to be a horrible idea. Defined in RFC 1035, Host Information (HINFO) DNS records were originally intended to provide the type of computer and operating system a host uses (back in the day, you could also put things in like room numbers and other descriptions in the record, too). However, to avoid publicly advertising that information (for obvious reasons), they’re simply not used much anymore. And if you find one on a public-facing machine, it’s a sure sign of incompetence on the part of the server administrators. In this example, the type is set to HINFO, and a machine name—someserver—is provided.
![]() B is incorrect because DNS poisoning is not carried out this way. In this command sequence, the operator is asking for information, not pushing up false entries to a name server.
B is incorrect because DNS poisoning is not carried out this way. In this command sequence, the operator is asking for information, not pushing up false entries to a name server.
![]() C is incorrect because this is not how nslookup is used to perform a zone transfer. To do that, you would use the set type=any command and then ls –d anybiz.com. You’ll more than likely see that on your exam, too.
C is incorrect because this is not how nslookup is used to perform a zone transfer. To do that, you would use the set type=any command and then ls –d anybiz.com. You’ll more than likely see that on your exam, too.
![]() D is incorrect because checking for name servers in the domain would require the set type=NS command.
D is incorrect because checking for name servers in the domain would require the set type=NS command.
8. You are footprinting information for a pen test. Social engineering is part of your reconnaissance efforts, and some of it will be active in nature. You take steps to ensure that if the social engineering efforts are discovered at this early stage, any trace efforts point to another organization. Which of the following terms best describes what you are participating in?
A. Anonymous footprinting
B. Pseudonymous footprinting
C. Passive footprinting
D. Redirective footprinting
![]() B. Pseudonymous footprinting is a relatively new term in the CEH realm, so you’ll probably see it on your exam. It refers to obfuscating your foot-printing efforts in such a way that anyone trying to trace it back to you would instead be pointed to a different person (usually to look like a competitor’s business). I understand there’s probably a large segment out there (like my tech editor) screaming at the page that this word sounds fabricated and shouldn’t be here. I won’t argue for or against: All I’ll say is it’s on your exam, so you better memorize it. As a side note for those of you getting ready for a real-world job in pen testing, the scenario presented here may sound like a great idea, but you better be careful in practicing this. In many ways this could be illegal: Pointing to another organization without authorization could make you liable both criminally or civilly.
B. Pseudonymous footprinting is a relatively new term in the CEH realm, so you’ll probably see it on your exam. It refers to obfuscating your foot-printing efforts in such a way that anyone trying to trace it back to you would instead be pointed to a different person (usually to look like a competitor’s business). I understand there’s probably a large segment out there (like my tech editor) screaming at the page that this word sounds fabricated and shouldn’t be here. I won’t argue for or against: All I’ll say is it’s on your exam, so you better memorize it. As a side note for those of you getting ready for a real-world job in pen testing, the scenario presented here may sound like a great idea, but you better be careful in practicing this. In many ways this could be illegal: Pointing to another organization without authorization could make you liable both criminally or civilly.
![]() A is incorrect because anonymous footprinting refers to footprinting efforts that can’t be traced back to you. These don’t redirect a search to someone else; they’re just efforts to hide your footprinting in the first place.
A is incorrect because anonymous footprinting refers to footprinting efforts that can’t be traced back to you. These don’t redirect a search to someone else; they’re just efforts to hide your footprinting in the first place.
![]() C is incorrect because passive footprinting is generally gathering competitive intelligence and doesn’t put you at risk of discovery anyway.
C is incorrect because passive footprinting is generally gathering competitive intelligence and doesn’t put you at risk of discovery anyway.
![]() D is incorrect because this term simply doesn’t exist. It’s here purely as a distractor.
D is incorrect because this term simply doesn’t exist. It’s here purely as a distractor.
9. You are setting up DNS for your enterprise. Server A is both a web server and an FTP server. You want to advertise both services for this machine as name references your customers can use. Which DNS record type would you use to accomplish this?
A. NS
B. SOA
C. MX
D. PTR
E. CNAME
![]() E. We all know—or should know by now—that a hostname can be mapped to an IP using an A record within DNS. CNAME records provide for aliases within the zone on that name. For instance, your server might be named mattserver1.matt.com. A sample DNS zone entry to provide HTTP and FTP access might look like this:
E. We all know—or should know by now—that a hostname can be mapped to an IP using an A record within DNS. CNAME records provide for aliases within the zone on that name. For instance, your server might be named mattserver1.matt.com. A sample DNS zone entry to provide HTTP and FTP access might look like this:
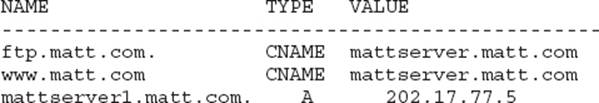
![]() A is incorrect because a name server (NS) record shows the name servers within your zone. These servers are the ones that respond to your client’s requests for name resolution.
A is incorrect because a name server (NS) record shows the name servers within your zone. These servers are the ones that respond to your client’s requests for name resolution.
![]() B is incorrect because the Start of Authority (SOA) entry identifies the primary name server for the zone. The SOA record contains the hostname of the server responsible for all DNS records within the namespace, as well as the basic properties of the domain.
B is incorrect because the Start of Authority (SOA) entry identifies the primary name server for the zone. The SOA record contains the hostname of the server responsible for all DNS records within the namespace, as well as the basic properties of the domain.
![]() C is incorrect because the Mail Exchange (MX) record identifies the e-mail servers within your domain.
C is incorrect because the Mail Exchange (MX) record identifies the e-mail servers within your domain.
![]() D is incorrect because a pointer record (PTR) works opposite to an A record. The pointer maps an IP address to a hostname and is generally used for reverse lookups.
D is incorrect because a pointer record (PTR) works opposite to an A record. The pointer maps an IP address to a hostname and is generally used for reverse lookups.
10. A company has a publicly facing web application. Its internal intranet-facing servers are separated and protected by a firewall. Which of the following choices would be helpful in protecting against unwanted enumeration?
A. Allowing zone transfers to any
B. Ensuring there are no A records for internal hosts on the public-facing name server
C. Changing the preference number on all MX records to zero
D. Not allowing any DNS query to the public-facing name server
![]() B. If your company has a publicly facing website, it follows that a name server somewhere has to answer lookups in order for your customers to find the site. That name server, however, does not need to provide lookup information to internal machines. Of the choices provides, as silly as it seems to point out, ensuring there are no A records (those used to map hostnames to an IP address) on the external name server is a good start.
B. If your company has a publicly facing website, it follows that a name server somewhere has to answer lookups in order for your customers to find the site. That name server, however, does not need to provide lookup information to internal machines. Of the choices provides, as silly as it seems to point out, ensuring there are no A records (those used to map hostnames to an IP address) on the external name server is a good start.
![]() A is incorrect because allowing a zone transfer to anyone asking for it is just plain dumb. It may or may not help an attacker enumerate your internal network (maybe you don’t have anything in there to worry about), but it’s just a horrendously bad idea.
A is incorrect because allowing a zone transfer to anyone asking for it is just plain dumb. It may or may not help an attacker enumerate your internal network (maybe you don’t have anything in there to worry about), but it’s just a horrendously bad idea.
![]() C is incorrect because changing the preference number on an MX record doesn’t have a thing to do with enumeration. The preference number (a lower number means first used) determines only which server handles e-mail first.
C is incorrect because changing the preference number on an MX record doesn’t have a thing to do with enumeration. The preference number (a lower number means first used) determines only which server handles e-mail first.
![]() D is incorrect because if your customers can’t query for the IP associated with the hostname, how are they supposed to find your website?
D is incorrect because if your customers can’t query for the IP associated with the hostname, how are they supposed to find your website?
11. Within the DNS system a primary server (SOA) holds and maintains all records for the zone. Secondary servers will periodically ask the primary if there have been any updates, and if updates have occurred, they will ask for a zone transfer to update their own copies. Under what conditions will the secondary name server request a zone transfer from a primary?
A. When the primary SOA record serial number is higher than the secondary’s
B. When the secondary SOA record serial number is higher than the primary’s
C. Only when the secondary reboots or restarts services
D. Only when manually prompted to do so
![]() A. Occasionally you’ll get a question like this. It’s not necessarily hacking in nature but more about how the DNS system works in general. The serial number on an SOA record is incremented each time the zone file is changed. So, when the secondary checks in with the primary, if the serial number is higher than its own, the secondary knows there has been a change and asks for a full zone transfer.
A. Occasionally you’ll get a question like this. It’s not necessarily hacking in nature but more about how the DNS system works in general. The serial number on an SOA record is incremented each time the zone file is changed. So, when the secondary checks in with the primary, if the serial number is higher than its own, the secondary knows there has been a change and asks for a full zone transfer.
![]() B is incorrect because the serial number increments with each change, not decrements. If the secondary checked in and the numbers were reversed—in other words, the secondary had a serial number higher than the primary—it would either leave its own record unchanged or most likely dump the zone altogether.
B is incorrect because the serial number increments with each change, not decrements. If the secondary checked in and the numbers were reversed—in other words, the secondary had a serial number higher than the primary—it would either leave its own record unchanged or most likely dump the zone altogether.
![]() C is incorrect because a zone transfer does not occur on startup. Additionally, and this is a free test-taking tip here, any time you see the word “only” in an answer, it’s usually wrong. In this case, that’s definitely true because the servers are configured to check in with each other on occasion to ensure the zone is consistent across the enterprise.
C is incorrect because a zone transfer does not occur on startup. Additionally, and this is a free test-taking tip here, any time you see the word “only” in an answer, it’s usually wrong. In this case, that’s definitely true because the servers are configured to check in with each other on occasion to ensure the zone is consistent across the enterprise.
![]() D is incorrect because this is just a ridiculous answer. Could you imagine having to manually update every DNS server? I can think of worse jobs, but this one would definitely stink.
D is incorrect because this is just a ridiculous answer. Could you imagine having to manually update every DNS server? I can think of worse jobs, but this one would definitely stink.
12. Examine the following SOA record:

If a secondary server in the enterprise is unable to check in for a zone update within an hour, what happens to the zone copy on the secondary?
A. The zone copy is dumped.
B. The zone copy is unchanged.
C. The serial number of the zone copy is decremented.
D. The serial number of the zone copy is incremented.
![]() B. You will definitely see questions about the SOA record. In this question, the key portion you’re looking for is the time to live (TTL) at the bottom, currently set to 2 hours (7,200 seconds). This sets the time a secondary server has to verify its records are good. If it can’t check in, this TTL for zone records will expire, and they’ll all be dumped. Considering, though, this TTL is set to 2 hours and the question states it’s been only one hour since update, the zone copy on the secondary will remain unchanged.
B. You will definitely see questions about the SOA record. In this question, the key portion you’re looking for is the time to live (TTL) at the bottom, currently set to 2 hours (7,200 seconds). This sets the time a secondary server has to verify its records are good. If it can’t check in, this TTL for zone records will expire, and they’ll all be dumped. Considering, though, this TTL is set to 2 hours and the question states it’s been only one hour since update, the zone copy on the secondary will remain unchanged.
![]() A is incorrect because the secondary is still well within its window for verifying the zone copy it holds. It dumps the records only when TTL is exceeded.
A is incorrect because the secondary is still well within its window for verifying the zone copy it holds. It dumps the records only when TTL is exceeded.
![]() C is incorrect because, first, serial numbers are never decremented; they’re always incremented. Second, the serial number of the zone copy is changed only when a connection to the primary occurs and a copy is updated.
C is incorrect because, first, serial numbers are never decremented; they’re always incremented. Second, the serial number of the zone copy is changed only when a connection to the primary occurs and a copy is updated.
![]() D is incorrect because while serial numbers are incremented on changes (the secondary copies the number from the primary’s copy when transferring records), the serial number of the zone copy is changed only when a connection to the primary occurs and a copy is updated. That has not occurred here.
D is incorrect because while serial numbers are incremented on changes (the secondary copies the number from the primary’s copy when transferring records), the serial number of the zone copy is changed only when a connection to the primary occurs and a copy is updated. That has not occurred here.
13. Which protocol and port number combination is used by default for DNS zone transfers?
A. UDP 53
B. UDP 161
C. TCP 53
D. TCP 22
![]() C. TCP 53 is the default protocol and port number for zone transfers. DNS actually uses both TCP and UDP to get its job done, and if you think about what it’s doing, they make sense in particular circumstances. A name resolution request and reply? Small and quick, so use port 53 on UDP. A zone transfer, which could potentially be large and requires some insurance it all gets there? Port 53 on TCP is the answer.
C. TCP 53 is the default protocol and port number for zone transfers. DNS actually uses both TCP and UDP to get its job done, and if you think about what it’s doing, they make sense in particular circumstances. A name resolution request and reply? Small and quick, so use port 53 on UDP. A zone transfer, which could potentially be large and requires some insurance it all gets there? Port 53 on TCP is the answer.
![]() A, B, and C are incorrect because they do not represent the default port and protocol combination for a zone transfer.
A, B, and C are incorrect because they do not represent the default port and protocol combination for a zone transfer.
14. Examine the following command-line entry:

Which two statements are true regarding the following command sequence? (Choose two.)
A. Nslookup is in noninteractive mode.
B. Nslookup is in interactive mode.
C. The output will show all mail servers in the zone somewhere.com.
D. The output will show all name servers in the zone somewhere.com.
![]() B and C. Nslookup runs in one of two modes—interactive and noninteractive. Noninteractive mode is simply the use of the command followed by an output. For example, nslookup www.google.com will return the IP address your server can find for Google. Interactive mode is started by simply typing nslookup and pressing ENTER. Your default server name will display, along with its IP address, and a carrot ( > ) will await entry of your next command. In this scenario we’ve entered interactive mode and set the type to MX, which we all know means “Please provide me with all the mail exchange servers you know about.”
B and C. Nslookup runs in one of two modes—interactive and noninteractive. Noninteractive mode is simply the use of the command followed by an output. For example, nslookup www.google.com will return the IP address your server can find for Google. Interactive mode is started by simply typing nslookup and pressing ENTER. Your default server name will display, along with its IP address, and a carrot ( > ) will await entry of your next command. In this scenario we’ve entered interactive mode and set the type to MX, which we all know means “Please provide me with all the mail exchange servers you know about.”
![]() A is incorrect because we are definitely in interactive mode.
A is incorrect because we are definitely in interactive mode.
![]() D is incorrect because type was set to MX, not NS.
D is incorrect because type was set to MX, not NS.
15. Joe accesses the company website, www.anybusi.com, from his home computer and is presented with a defaced site containing disturbing images. He calls the IT department to report the website hack and is told they do not see any problem with the site—no files have been changed, and when accessed from their terminals (inside the company), the site appears normally. Joe connects over VPN into the company website and notices the site appears normally. Which of the following might explain the issue?
A. DNS poisoning
B. Route poisoning
C. SQL injection
D. ARP poisoning
![]() A. DNS poisoning makes the most sense here. Joe’s connection from home uses a different DNS server for lookups than that of the business network. It’s entirely possible someone has changed the cache entries in his local server to point to a different IP than the one hosting the real website—one that the hackers have set up to provide the defaced version. The fact the web files haven’t changed and it seems to be displaying just fine from inside the network also bears this out. Also, for those of you paying close attention, in a case like this, it’s important to note VPN access. If it turns out Joe’s DNS modification is the only one in place, there is a strong likelihood that Joe is being specifically targeted for exploitation—something Joe should take very seriously.
A. DNS poisoning makes the most sense here. Joe’s connection from home uses a different DNS server for lookups than that of the business network. It’s entirely possible someone has changed the cache entries in his local server to point to a different IP than the one hosting the real website—one that the hackers have set up to provide the defaced version. The fact the web files haven’t changed and it seems to be displaying just fine from inside the network also bears this out. Also, for those of you paying close attention, in a case like this, it’s important to note VPN access. If it turns out Joe’s DNS modification is the only one in place, there is a strong likelihood that Joe is being specifically targeted for exploitation—something Joe should take very seriously.
![]() B is incorrect because route poisoning has nothing to do with this. Route poisoning is used in distance vector routing protocols to prevent route loops in routing tables.
B is incorrect because route poisoning has nothing to do with this. Route poisoning is used in distance vector routing protocols to prevent route loops in routing tables.
![]() C is incorrect because while SQL injection is, indeed, a hacking attack, it’s not relevant here. The fact the website files remain intact and unchanged prove that access to the site through an SQL weakness isn’t what occurred here.
C is incorrect because while SQL injection is, indeed, a hacking attack, it’s not relevant here. The fact the website files remain intact and unchanged prove that access to the site through an SQL weakness isn’t what occurred here.
![]() D is incorrect because ARP poisoning is relevant inside a particular subnet, not outside it (granted, you can have ARP forwarded by a router configured to do so, but it simply isn’t the case for this question). ARP poisoning will redirect a request from one machine to another inside the same subnet and has little to do with the scenario described here.
D is incorrect because ARP poisoning is relevant inside a particular subnet, not outside it (granted, you can have ARP forwarded by a router configured to do so, but it simply isn’t the case for this question). ARP poisoning will redirect a request from one machine to another inside the same subnet and has little to do with the scenario described here.
16. One way to mitigate against DNS poisoning is to restrict or limit the amount of time records can stay in cache before they’re updated. Which DNS record type allows you to set this restriction?
A. NS
B. PTR
C. MX
D. CNAME
E. SOA
![]() E. The SOA record holds all sorts of information, and when it comes to DNS poisoning, the TTL is of primary interest. The shorter the TTL, the less time records are held in cache. While it won’t prevent DNS poisoning altogether, it can limit the problems a successful cache poisoning attack causes.
E. The SOA record holds all sorts of information, and when it comes to DNS poisoning, the TTL is of primary interest. The shorter the TTL, the less time records are held in cache. While it won’t prevent DNS poisoning altogether, it can limit the problems a successful cache poisoning attack causes.
![]() A is incorrect because an NS record shows the name servers found in the domain.
A is incorrect because an NS record shows the name servers found in the domain.
![]() B is incorrect because a PTR record provides for reverse lookup capability—an IP address to hostname mapping.
B is incorrect because a PTR record provides for reverse lookup capability—an IP address to hostname mapping.
![]() C is incorrect because an MX record shows the mail exchange servers in the zone.
C is incorrect because an MX record shows the mail exchange servers in the zone.
![]() D is incorrect because a CNAME record is used to provide alias entries for your zone (usually for multiple services or sites on one IP address).
D is incorrect because a CNAME record is used to provide alias entries for your zone (usually for multiple services or sites on one IP address).
17. Which of the following may be a security concern for an organization?
A. The internal network uses private IP addresses registered to an Active Directory–integrated DNS server.
B. An external DNS server is Active Directory integrated.
C. All external name resolution requests are accomplished by an ISP.
D. None of the above.
![]() B. If you have a Windows Active Directory (AD) network, having AD-integrated DNS servers has some great advantages. For example (and directly from Microsoft, I might add), “with directory-integrated storage, dynamic updates to DNS are conducted based upon a multimaster update model. In this model, any authoritative DNS server, such as a domain controller running a DNS server, is designated as a primary source for the zone. Because the master copy of the zone is maintained in the Active Directory database, which is fully replicated to all domain controllers, the zone can be updated by the DNS servers operating at any domain controller for the domain.” Zones are also replicated and synchronized to new domain controllers automatically whenever a new one is added to an Active Directory domain, and directory replication is faster and more efficient than standard DNS replication. But having an Active Directory server facing externally is a horrible idea.
B. If you have a Windows Active Directory (AD) network, having AD-integrated DNS servers has some great advantages. For example (and directly from Microsoft, I might add), “with directory-integrated storage, dynamic updates to DNS are conducted based upon a multimaster update model. In this model, any authoritative DNS server, such as a domain controller running a DNS server, is designated as a primary source for the zone. Because the master copy of the zone is maintained in the Active Directory database, which is fully replicated to all domain controllers, the zone can be updated by the DNS servers operating at any domain controller for the domain.” Zones are also replicated and synchronized to new domain controllers automatically whenever a new one is added to an Active Directory domain, and directory replication is faster and more efficient than standard DNS replication. But having an Active Directory server facing externally is a horrible idea.
![]() A is incorrect because having AD-integrated DNS servers inside your network, with all private IP addresses, is just fine. Actually, it’s a pretty good idea if you think about it for a bit.
A is incorrect because having AD-integrated DNS servers inside your network, with all private IP addresses, is just fine. Actually, it’s a pretty good idea if you think about it for a bit.
![]() C is incorrect because having an external ISP answer all name resolution requests for your public-facing servers isn’t a bad idea at all. Even if the ISP’s DNS is subject to attack, nothing is there but the public-facing hosts anyway.
C is incorrect because having an external ISP answer all name resolution requests for your public-facing servers isn’t a bad idea at all. Even if the ISP’s DNS is subject to attack, nothing is there but the public-facing hosts anyway.
![]() D is incorrect because there is a correct answer provided.
D is incorrect because there is a correct answer provided.
18. Which of the following is a good footprinting tool for discovering information on a publicly traded company’s founding, history, and financial status?
A. SpiderFoot
B. EDGAR Database
C. Sam Spade
D. Pipl.com
![]() B. The EDGAR Database—www.sec.gov/edgar.shtml—holds all sorts of competitive intelligence information on businesses and is an old favorite of EC-Council. From the website, “All companies, foreign and domestic, are required to file registration statements, periodic reports, and other forms electronically through EDGAR. Anyone can access and download this information for free. Here you’ll find links to a complete list of filings available through EDGAR and instructions for searching the EDGAR database.” Finally, one more note on EDGAR and the SEC: They have purview only over publicly traded companies. Privately held companies are not regulated or obligated to put information in EDGAR. Additionally, even publicly traded companies might not provide information about privately owned subsidiaries, so be careful and diligent.
B. The EDGAR Database—www.sec.gov/edgar.shtml—holds all sorts of competitive intelligence information on businesses and is an old favorite of EC-Council. From the website, “All companies, foreign and domestic, are required to file registration statements, periodic reports, and other forms electronically through EDGAR. Anyone can access and download this information for free. Here you’ll find links to a complete list of filings available through EDGAR and instructions for searching the EDGAR database.” Finally, one more note on EDGAR and the SEC: They have purview only over publicly traded companies. Privately held companies are not regulated or obligated to put information in EDGAR. Additionally, even publicly traded companies might not provide information about privately owned subsidiaries, so be careful and diligent.
![]() A is incorrect because SpiderFoot is a free, open source, domain footprinting tool. From the site, “it will scrape the websites on that domain, as well as search Google, Netcraft, Whois and DNS to build up information.”
A is incorrect because SpiderFoot is a free, open source, domain footprinting tool. From the site, “it will scrape the websites on that domain, as well as search Google, Netcraft, Whois and DNS to build up information.”
![]() C is incorrect because Sam Spade is a DNS footprinting tool.
C is incorrect because Sam Spade is a DNS footprinting tool.
![]() D is incorrect because pipl.com is a site used for “people search.” When footprinting, pipl.com can use so-called deep web searching for loads of information you can use. From the site, “Also known as ‘invisible web,’ the term ‘deep web’ refers to a vast repository of underlying content, such as documents in online databases that general-purpose web crawlers cannot reach. The deep web content is estimated at 500 times that of the surface web, yet has remained mostly untapped due to the limitations of traditional search engines.”
D is incorrect because pipl.com is a site used for “people search.” When footprinting, pipl.com can use so-called deep web searching for loads of information you can use. From the site, “Also known as ‘invisible web,’ the term ‘deep web’ refers to a vast repository of underlying content, such as documents in online databases that general-purpose web crawlers cannot reach. The deep web content is estimated at 500 times that of the surface web, yet has remained mostly untapped due to the limitations of traditional search engines.”
19. What method does traceroute use to map routes traveled by a packet?
A. By carrying a hello packet in the payload, forcing the host to respond
B. By using DNS queries at each hop
C. By manipulating the time to live (TTL) parameter
D. By using ICMP Type 5, code 0 packets
![]() C. Traceroute tracks a packet across the Internet by incrementing the TTL on each packet it sends by one after each hop is hit and returns, ensuring the response comes back explicitly from that hop and returns its name and IP address. This provides route path and transit times. It accomplishes this by using ICMP ECHO packets to report information on each “hop” (router) from the source to destination.
C. Traceroute tracks a packet across the Internet by incrementing the TTL on each packet it sends by one after each hop is hit and returns, ensuring the response comes back explicitly from that hop and returns its name and IP address. This provides route path and transit times. It accomplishes this by using ICMP ECHO packets to report information on each “hop” (router) from the source to destination.
![]() A is incorrect because ICMP simply doesn’t work that way. A hello packet is generally used between clients and servers as a check-in/health mechanism, not a route tracing method.
A is incorrect because ICMP simply doesn’t work that way. A hello packet is generally used between clients and servers as a check-in/health mechanism, not a route tracing method.
![]() B is incorrect because a DNS lookup at each hop is pointless and does you no good. DNS isn’t for route tracing; it’s for matching hostnames and IP addresses.
B is incorrect because a DNS lookup at each hop is pointless and does you no good. DNS isn’t for route tracing; it’s for matching hostnames and IP addresses.
![]() D is incorrect because an ICMP Type 5, code 0 packet is all about message redirection and not about a ping request (Type 8).
D is incorrect because an ICMP Type 5, code 0 packet is all about message redirection and not about a ping request (Type 8).
20. Brad is auditing an organization and is asked to provide suggestions on improving DNS security. Which of the following would be valid options to recommend? (Choose all that apply.)
A. Implementing split-horizon operation
B. Restricting zone transfers
C. Obfuscating DNS by using the same server for other applications and functions
D. Blocking all access to the server on port 53
![]() A and B. Split-horizon DNS (also known as split-view or split DNS) is a method of providing different answers to DNS queries based on the source address of the DNS request. It can be accomplished with hardware or software solutions and provides one more step of separation between you and the bad guys. Restricting zone transfers to only those systems you desire to have them is always a good idea. If you leave it open for anyone to grab, you’re just asking for trouble.
A and B. Split-horizon DNS (also known as split-view or split DNS) is a method of providing different answers to DNS queries based on the source address of the DNS request. It can be accomplished with hardware or software solutions and provides one more step of separation between you and the bad guys. Restricting zone transfers to only those systems you desire to have them is always a good idea. If you leave it open for anyone to grab, you’re just asking for trouble.
![]() C is incorrect because you generally should not put DNS services on a machine performing other tasks or applications. Does it happen in the real world? Sure, it does, and just like it’s not too far-fetched to find a stray Windows 2000 machine in any given organization’s network, it’s probably more common than we’d like to guess.
C is incorrect because you generally should not put DNS services on a machine performing other tasks or applications. Does it happen in the real world? Sure, it does, and just like it’s not too far-fetched to find a stray Windows 2000 machine in any given organization’s network, it’s probably more common than we’d like to guess.
![]() D is incorrect because restricting all port 53 access to the server means it’s not acting as a DNS server anymore: No one can query for name lookups, and no zone transfers are going to happen. I guess in some weird way the DNS side of it is really secure, but its functionality has dropped to nothing.
D is incorrect because restricting all port 53 access to the server means it’s not acting as a DNS server anymore: No one can query for name lookups, and no zone transfers are going to happen. I guess in some weird way the DNS side of it is really secure, but its functionality has dropped to nothing.
21. A zone file consists of which records? (Choose all that apply.)
A. PTR
B. MX
C. SN
D. SOA
E. DNS
F. A
G. AX
![]() A, B, D, and F. A zone file contains a list of all the resource records in the namespace zone. Valid resource records are as follows:
A, B, D, and F. A zone file contains a list of all the resource records in the namespace zone. Valid resource records are as follows:
|
SRV |
Service This record defines the hostname and port number of servers providing specific services, such as a Directory Services server. |
|
SOA |
Start of Authority This record identifies the primary name server for the zone. The SOA record contains the hostname of the server responsible for all DNS records within the namespace, as well as the basic properties of the domain. |
|
PTR |
Pointer This record maps an IP address to a hostname (providing for reverse DNS lookups). You don’t absolutely need a PTR record for every entry in your DNS namespace, but PTR records are usually associated with e-mail server records. |
|
NS |
Name Server This record defines the name servers within your namespace. These servers are the ones that respond to your client’s requests for name resolution. |
|
MX |
Mail Exchange This record identifies your e-mail servers within your domain. |
|
CNAME |
Canonical Name This record provides for domain name aliases within your zone. For example, you may have an FTP server and a web service running on the same IP address. CNAME records could be used to list both within DNS for you. |
|
A |
Address This record maps an IP address to a hostname and is used most often for DNS lookups. |
![]() C, E, and G are incorrect because they are not valid DNS resource records.
C, E, and G are incorrect because they are not valid DNS resource records.
22. Examine the following SOA record:
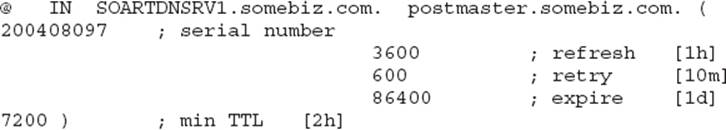
How long will the secondary server wait before asking for an update to the zone file?
A. 1 hour
B. 2 hours
C. 10 minutes
D. 1 day
![]() A. The refresh interval defines the amount of time a secondary will wait before checking in to see whether it needs a zone update.
A. The refresh interval defines the amount of time a secondary will wait before checking in to see whether it needs a zone update.
![]() B is incorrect because the refresh interval is set to 3,600 seconds (1 hour). If you chose this because the TTL interval appealed to you, note that the TTL interval is the minimum time to live for all records in the zone (if it’s not updated by a zone transfer, the records will perish).
B is incorrect because the refresh interval is set to 3,600 seconds (1 hour). If you chose this because the TTL interval appealed to you, note that the TTL interval is the minimum time to live for all records in the zone (if it’s not updated by a zone transfer, the records will perish).
![]() C is incorrect because the refresh interval is set to 3,600 seconds (1 hour). If you chose this because the retry interval appealed to you, note that the retry interval is the amount of time a secondary server will wait to retry if the zone transfer fails.
C is incorrect because the refresh interval is set to 3,600 seconds (1 hour). If you chose this because the retry interval appealed to you, note that the retry interval is the amount of time a secondary server will wait to retry if the zone transfer fails.
![]() D is incorrect because the refresh interval is set to 3,600 seconds (1 hour). If you chose this because the expire interval appealed to you, note the expire interval is the maximum amount of time a secondary server will spend trying to complete a zone transfer.
D is incorrect because the refresh interval is set to 3,600 seconds (1 hour). If you chose this because the expire interval appealed to you, note the expire interval is the maximum amount of time a secondary server will spend trying to complete a zone transfer.
23. A colleague enters the following into a Google search string:
![]()
Which of the following is most correct concerning this attempt?
A. The search engine will not respond with any result because you cannot combine Google hacks in one line.
B. The search engine will respond with all pages having the word intranet in their title and finance in the URL.
C. The search engine will respond with all pages having the word intranet in the title and in the URL.
D. The search engine will respond with only those pages having the word intranet in the title and URL and with finance in the text.
![]() D. This is a great Google hack that’s listed on several websites providing Google hacking examples. Think about what you’re looking for here—an internal page (intranet in title and URL) possibly containing finance data. Don’t you think that would be valuable? This example shows the beauty of combining Google hacks to really burrow down to what you want to grab. Granted, an Intranet being available from the Internet, indexed by Google and open enough for you to touch it, is unlikely, but these are questions concerning syntax, not reality.
D. This is a great Google hack that’s listed on several websites providing Google hacking examples. Think about what you’re looking for here—an internal page (intranet in title and URL) possibly containing finance data. Don’t you think that would be valuable? This example shows the beauty of combining Google hacks to really burrow down to what you want to grab. Granted, an Intranet being available from the Internet, indexed by Google and open enough for you to touch it, is unlikely, but these are questions concerning syntax, not reality.
![]() A is incorrect because Google hack operators can be combined. In fact, once you get used to them, you’ll spend more time combining them to narrow an attack than launching them one by one.
A is incorrect because Google hack operators can be combined. In fact, once you get used to them, you’ll spend more time combining them to narrow an attack than launching them one by one.
![]() B is incorrect because the operator does not say to look for human resources in the URL. It specifically states that should be looked for in the text of the page.
B is incorrect because the operator does not say to look for human resources in the URL. It specifically states that should be looked for in the text of the page.
![]() C is incorrect because there is more to the operation string than just intranet in the URL and title. Don’t just glaze over the intext:”human resources” operator—it makes Answer D more correct.
C is incorrect because there is more to the operation string than just intranet in the URL and title. Don’t just glaze over the intext:”human resources” operator—it makes Answer D more correct.
24. Amanda works as a senior security analyst and overhears a colleague discussing confidential corporate information being posted on an external website. When questioned on it, he claims about a month ago he tried random URLs on the company’s website and found confidential information. Amanda visits the same URLs but finds nothing. Where can Amanda go to see past versions and pages of a website?
A. Search.com
B. Google cache
C. Pasthash.com
D. Archive.org
![]() D. The Internet Archive (http://archive.org) is a nonprofit organization “dedicated to build an Internet library. Its purposes include offering permanent access for researchers, historians, scholars, people with disabilities, and the general public to historical collections that exist in digital format.” The good-old Wayback Machine has been used for a long time to pull up old copies of websites, for good and maybe not-so-good purposes. Archive.orgincludes “snapshots of the World Wide Web,” which are archived copies of pages taken at various points in time dating back to 1996.
D. The Internet Archive (http://archive.org) is a nonprofit organization “dedicated to build an Internet library. Its purposes include offering permanent access for researchers, historians, scholars, people with disabilities, and the general public to historical collections that exist in digital format.” The good-old Wayback Machine has been used for a long time to pull up old copies of websites, for good and maybe not-so-good purposes. Archive.orgincludes “snapshots of the World Wide Web,” which are archived copies of pages taken at various points in time dating back to 1996.
![]() A is incorrect because Search.com is simply another search engine at your disposal. It does not hold archived copies.
A is incorrect because Search.com is simply another search engine at your disposal. It does not hold archived copies.
![]() B is incorrect because Google cache holds a copy of the site only from the latest “crawl”—usually nothing older than a couple to few days.
B is incorrect because Google cache holds a copy of the site only from the latest “crawl”—usually nothing older than a couple to few days.
![]() C is incorrect because, as far as I know, Pasthash.com doesn’t even exist.
C is incorrect because, as far as I know, Pasthash.com doesn’t even exist.
25. Which of the following is a primary service of the U.S. Computer Security Incident Response Team (CSIRT)?
A. CSIRT provides an incident response service to enable a reliable and trusted single point of contact for reporting computer security incidents worldwide.
B. CSIRT provides computer security surveillance to governments, supplying important intelligence information on individuals traveling abroad.
C. CSIRT provides pen testing services to individuals and multinational corporations.
D. CSIRT provides vulnerability assessment services to law enforcement agencies.
![]() A. EC-Council loves CSIRT, and I promise you’ll see it mentioned somewhere on the exam. The Computer Security Incident Response Team (CSIRT; www.csirt.org/) “provides 24x7 Computer Security Incident Response Services to any user, company, government agency or organization. CSIRT provides a reliable and trusted single point of contact for reporting computer security incidents worldwide. CSIRT provides the means for reporting incidents and for disseminating important incident-related information.” A privately held company that started in 2001, CSIRT seeks “to raise awareness among its customers of computer security issues, and provides information for secure protection of critical computing infrastructure and equipment against potential organized computer attacks.”
A. EC-Council loves CSIRT, and I promise you’ll see it mentioned somewhere on the exam. The Computer Security Incident Response Team (CSIRT; www.csirt.org/) “provides 24x7 Computer Security Incident Response Services to any user, company, government agency or organization. CSIRT provides a reliable and trusted single point of contact for reporting computer security incidents worldwide. CSIRT provides the means for reporting incidents and for disseminating important incident-related information.” A privately held company that started in 2001, CSIRT seeks “to raise awareness among its customers of computer security issues, and provides information for secure protection of critical computing infrastructure and equipment against potential organized computer attacks.”
![]() B, C, and D are incorrect because these statements do not match CSIRT’s purpose or actions.
B, C, and D are incorrect because these statements do not match CSIRT’s purpose or actions.
26. Your client’s business is headquartered in Japan. Which regional registry would be the best place to look for footprinting information?
A. APNIC
B. RIPE
C. ASIANIC
D. ARIN
E. LACNIC
![]() A. This one is easy as pie and should be a free one if you see it on the test. There are five regional Internet registries that provide overall management of the public IP address space within a given geographic region. APNIC handles Asia and Pacific realms.
A. This one is easy as pie and should be a free one if you see it on the test. There are five regional Internet registries that provide overall management of the public IP address space within a given geographic region. APNIC handles Asia and Pacific realms.
![]() B is incorrect because RIPE handles Europe, Middle East, and parts of Central Asia/Northern Africa. If you’re wondering, the name is French and stands for Réseaux IP Européens.
B is incorrect because RIPE handles Europe, Middle East, and parts of Central Asia/Northern Africa. If you’re wondering, the name is French and stands for Réseaux IP Européens.
![]() C is incorrect because ASIANIC is not a regional registry. It’s purely a distractor here.
C is incorrect because ASIANIC is not a regional registry. It’s purely a distractor here.
![]() D is incorrect because the ARIN service region includes Canada, many Caribbean and North Atlantic islands, and the United States. Caribbean islands falling under ARIN include Puerto Rico, the Bahamas, Antigua, American and British Virgin Islands, Turks and Caicos Islands, and the Cayman Islands (among others).
D is incorrect because the ARIN service region includes Canada, many Caribbean and North Atlantic islands, and the United States. Caribbean islands falling under ARIN include Puerto Rico, the Bahamas, Antigua, American and British Virgin Islands, Turks and Caicos Islands, and the Cayman Islands (among others).
![]() E is incorrect because LACNIC handles Latin America and parts of the Caribbean. It stands for Latin America and Caribbean Network Information Center. LACNIC coverage includes most of South America, Guatemala, French Guiana, Dominican Republic, and Cuba (among others). This one and ARIN most often get confused.
E is incorrect because LACNIC handles Latin America and parts of the Caribbean. It stands for Latin America and Caribbean Network Information Center. LACNIC coverage includes most of South America, Guatemala, French Guiana, Dominican Republic, and Cuba (among others). This one and ARIN most often get confused.