Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
11
Chapter
Investigating Child Pornography
Objectives
After completing this chapter, you should be able to:
• Define child pornography
• Understand people’s motives behind child pornography
• Know what kinds of people are involved in child pornography
• Understand the role of the Internet in promoting child pornography
• Describe the effects of child pornography on children
• Describe the measures to prevent dissemination of child pornography
• Understand the challenges in controlling child pornography
• Enumerate the steps for investigating child pornography cases
• Understand the sources of digital evidence
• Understand the techniques to reduce the problem of child pornography
• Understand the guidelines to avoid child pornography
• Understand the laws against child pornography
• List the anti-child-pornography/organizations
• Know how to report on child pornography
Key Terms
Child pornography an obscene visual depiction of any kind involving a minor engaging in, or
appearing to engage in, sexually explicit conduct, graphic bestiality, sadistic or masochistic abuse, or sexual intercourse of any kind; child pornography also includes the production, distribution, and possession of pornographic material
11-1
11-2
Chapter 11
Introduction to Investigating Child Pornography
Child pornography is a serious crime. There are a growing number of children who access the Internet all over the world. Rapidly expanding computer technology and the Internet have facilitated the production and distribution of child pornography. Child pornography is an obscene visual depiction of any kind involving a minor engaging in, or appearing to engage in, sexually explicit conduct, graphic bestiality, sadistic or masochistic abuse, or sexual intercourse of any kind. Child pornography also includes the production, distribution, and possession of pornographic material.
As children spend more and more of their time on the Internet, they are increasingly falling prey to child abusers and pornographers. Child pornography begins with the production of pornographic materials such as images and videos. Offenders enter into correspondence with children through online instant messaging or chat rooms. They emotionally attract the prospective victim and befriend him or her. After establishing a steady relationship, they introduce children to pornography by providing images and videos that have sexually explicit material. Pornographers also make use of poor children, disabled minors, and sometimes neighborhood children for sexual exploitation. Even infants have become victims of these activities.
Distribution of porn material is also a serious crime. The Internet has made the distribution of illegal material easy. Pornographers resort to newsgroups, Internet Relay Chat (IRC), Web-based groups, e-mail, Webcams, and peer-to-peer technology to distribute pornographic material. Downloading these materials is also considered a crime.
This chapter focuses on child pornography and the steps involved in investigating child pornography cases.
People’s Motives Behind Child Pornography
Criminals involved in pornographic cases tend to be unmarried, separated, divorced, or widowed. They become involved with child pornography because of various factors. These factors could range from mere moneymaking to sexual perversion. They draw children into pornographic activities by using the following tactics:
• Seduction: They offer children something enticing.
• Coercion: They force children into sexual activities or threaten them with dire consequences.
• Payment: They offer monetary benefits to attract children.
• Solicitation: They request a sexual relationship with the children.
• Blackmailing: The offenders lure or force children or teenagers into offensive activities and make videos and images of them. Later, they blackmail the victims or their parents by threatening to expose the images or videos.
Voyeurism is another motive behind child pornography. This involves people who derive sexual pleasure by secretly watching sexual activities or others in the nude.
Offenders often sell pornographic material to make easy money. They also build their own Web sites that provide pornographic materials for money.
People Involved in Child Pornography
People involved in child pornography either directly or indirectly are also involved with child abuse. It involves people who enter into online relationships with children. These people attract victims for sexual activities or send pornographic materials to children as part of the grooming process. They contact children using online messaging or chat rooms. This is considered direct abuse of children. For such people, the main intention is to satisfy their sexual curiosity. They also make pornographic images or videos for their own satisfaction.
Production of pornographic material is also a serious crime. A person who produces pornographic images or records the sexual activities of children is considered a pornographer. A person who provides sources of child pornography is also included in such an offense. Such offenses are indirect abuse of children. These people may distribute pornographic materials through e-mail, Webcams, or chat rooms.
People who intentionally download pornographic material from the Internet and save it to their computer also fall into the category of pornographer. They may not have any intention of abuse and may not be related to other offenders; they download it for pleasure. Parents or guardians who allow their children to engage in pornographic activity are also considered offenders.
Measures to Prevent Dissemination of Child Pornography
11-3
Role of the Internet in Child Pornography
The Internet is a fast communication vehicle providing a number of online services. This growing facility helps children learn. Yet, with the increase in access, there has been a rise in Internet crimes. The Internet plays an important role in child pornography cases.
Through the Internet, it is easy to access a huge quantity of pornographic material. The Internet provides complete anonymity and privacy. It reduces the cost of production and distribution of such material. The offender distributes the material easily with Web services such as e-mail, newsgroups, and Webcams. An offender can create his or her own Web site and upload the pornographic material, so that others can easily download it. Using an Internet facility such as a Webcam, he or she can send real-time pornographic pictures or video.
The most frequent source for distributing pornographic material is e-mail. Offenders can send images or videos as attachments. Offenders can also use e-mail for grooming or seduction purposes.
The Internet is the least-expensive method for transferring pornographic materials. The most advantageous factor about the Internet is that the offenders can access pornographic material anytime and anywhere. The Internet enables them to send the images or videos in any format. These files can be stored easily on any digital device, such as a mobile phone or a PDA.
Effects of Child Pornography on Children
Child pornography affects children physically, socially, and psychologically. Molestation can cause physical injuries such as genital bruising and lacerations. In many cases, teenagers may experience negative effects later in life due to inappropriate early sexual experiences. Child pornography also gives rise to sexually transmitted diseases.
Child pornographic victims also suffer from psychological trauma, such as depression, anger, and schizo-phrenia. Female victims may suffer from higher rates of nightmares, back pain, headaches, pelvic pain, and other similar symptoms in their adult age. Pornography may cause sexual addiction, which may further result in prostitution or teenage pregnancy. A victim may also lose his or her mental balance and become suicidal.
Measures to Prevent Dissemination of Child Pornography
Computer Industry Self-Regulation (Role of ISP)
An ISP (Internet service provider) plays an important role in reducing the problem of child pornography. It is necessary for an ISP to take some self-regulatory actions, including the following:
• Block illegal sites: It is important that various ISP associations come together and make a decision to block illegal sites.
• Use browser filters and search engines for safe search: ISPs can use browser filters to help block sites containing words related to pornography and use filters on search engines so that they will not search illegal sites or images.
• Establish complaint sites: ISPs should open sites that will help people complain about pornography hosted on the ISPs servers. The ISPs may deal directly with the police or any other authority.
Legislative Regulation
It should be mandatory for ISPs to inform the police about illegal sites. ISPs should have to verify the identities of people who access the Internet. ISPs should confirm the age of the account holder and restrict children from opening an account without adult supervision. Advertisers should not advertise illegal sites.
Citizens’ Committee
A citizens’ committee can help control child pornography. This is an organization that creates awareness among the public about such issues and provides community members with a forum in which to voice their complaints about such activities. The committee may provide information to parents and teachers through their sites or publications about the problem of child pornography and how to tackle the issue.
11-4
Chapter 11
Parental Strategies
Parents play an important role in protecting children from child pornography. They should restrict their children from accessing such materials. They should use filtering software to protect their children from any indecent material.
Law Enforcement Responses (Role of Police)
Police play a crucial role in investigating pornographic sites. The police may use computer forensic tools and techniques to investigate such sites. They may scan the ISP’s servers and request the ISP to remove illegal sites.
The police may perform sting operations to investigate suspected offenders. They may make contact with suspects through chat rooms, newsgroups, or other electronic means and disguise themselves as teenagers.
Police may also use honeytrap sites to find offenders. These sites contain pornographic material, but they note the IP address or the credit card number of a criminal who tries to download pornographic material from these sites.
Challenges in Controlling Child Pornography
The following are some of the challenges involved in controlling child pornography:
• Large amount of Internet traffic: The Internet is the network of networks; it provides a fast and easy way for disseminating information. If an ISP blocks a site, there may be other ways to reach the site or another site may spring up containing the same pornographic material.
• Unclear jurisdiction due to anonymity of offenders: Criminals from any corner of the world can send or use pornographic material. Laws differ from country to country, which adds to the difficulty of tracking the offender. For example, in the United States, a child is defined as a person who is younger than 18 years of age, but in Australia, a child is defined as a person who is younger than 16 years of age.
An offender may produce the pornographic material in one country and distribute it in another country.
This raises questions about who will investigate the crime and under which country’s laws the offender will be prosecuted.
• Lack of laws and regulations: Another challenge in controlling child pornography is the lack of laws and regulations in certain countries. In most countries, there are no laws against child pornography, so offenders can easily produce the pornographic material in those countries and distribute it through the Internet all over the world.
• Sophistication and use of Internet technology by offenders: Due to sophisticated Internet technologies, it is difficult to track offenders. Offenders use various techniques such as e-mail, Webcams, chat rooms, and newsgroups to distribute the materials. With the Internet, it is easy to access a number of pornographic materials. The Internet provides complete anonymity and privacy, which causes a problem during investigation.
Precautions Before Investigating Child Pornography Cases
Investigators should take the following precautions before investigating a child pornography case:
• Ensure that they have authorization to investigate the child pornography case.
• Be familiar with local laws related to child pornography.
• Document each step of the investigation in detail.
• Request assistance from at least two authorized persons.
Steps for Investigating Child Pornography
The following are the steps an investigator should follow when investigating child pornography cases: 1. Search and seize all computers and media devices.
2. Check authenticated login sessions.
Steps for Investigating Child Pornography
11-5
3. Search hard disks for pornographic material.
4. Recover deleted files and folders.
5. Check metadata of files and folders related to pornography.
6. Check and recover browser information.
7. Check ISP logs.
Step 1: Search and Seize All Computers
and Media Devices
The following are the steps an investigator should follow to search the files on computers and media devices for evidence:
1. Search the files and folders of the suspect’s system for pornographic material.
2. Look for pornographic material on media devices such as USB drives, CD-ROMs, and DVDs.
3. Document and seize the collected evidence carefully.
Step 2: Check Authenticated Login Sessions
The following are the steps an investigator should take when checking authenticated login sessions: 1. Check the login information, as user accounts are password protected.
2. Check under which account the pornographic material was accessed.
3. Check whether the user who accessed the pornographic material is an authenticated user, a guest, or an administrator.
Step 3: Search Hard Disks for Pornographic Material
The investigator should do a thorough search for pornographic material on suspects’ hard disks. The following are areas the investigator should look in:
• Files and folders
• Applications
• Temporary Internet files
• Recycle Bin
Tools like SurfRecon scan systems for pornographic material (on hard disks as well as in the
browser cache).
Step 4: Recover Deleted Files and Folders
The suspect may have deleted the pornographic material from the system. To recover files and folders, even when they have been deleted from the Recycle Bin, an investigator can use tools such as the following:
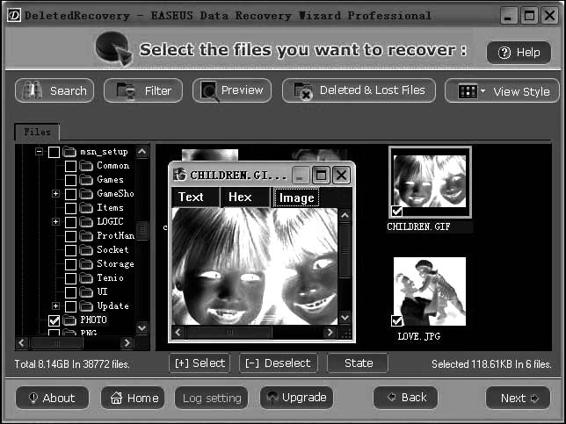
• File Recover
• Data Recovery Wizard (Figure 11-1)
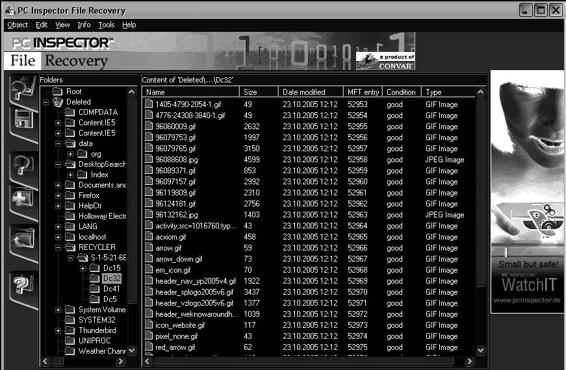
• PC Inspector File Recovery (Figure 11-2)
Step 5: Check Metadata of Files and Folders
Related to Pornography
The metadata associated with files and folders is the information concerning when the file was created, modified, or deleted. This information allows the investigator to know when the material was accessed. The investigator should do the following:
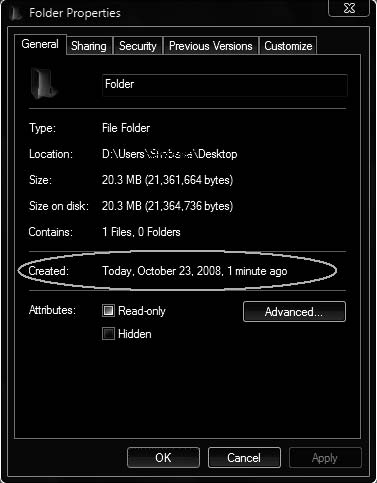
• Check the metadata of files and folders that contain pornographic material, as shown in Figure 11-3.
• Check the metadata of files and folders in the Recycle Bin.
11-6
Chapter 11
Figure 11-1 Data Recovery Wizard allows investigators to recover files a suspect
has deleted.
Figure 11-2 PC Inspector File Recovery can recover deleted files, even when the
suspect has emptied the Recycle Bin.
Steps for Investigating Child Pornography
11-7
Figure 11-3 Investigators should look at the metadata
for a suspect folder, including the folder’s creation date.
Step 6: Check and Recover Browser Information
The investigator should check and recover the browser information, which includes the following:
• Browsing history
• Download history
• Cache
• Cookies
• Offline Web site data
• Saved passwords
• Authenticated sessions
• Saved forms
• Search history
Browsing History, Saved Forms, and Search History
Most browsers allow users to access the browsing history. In most browsers, a user accesses the browsing history by pressing ctrl+H. The investigator should check the browsing history for any sites that contain pornographic materials. The search bar in browsers often has an automatic completion feature, so an investigator can start typing in key words and phrases relating to child pornography to see if the suspect searched for these terms.
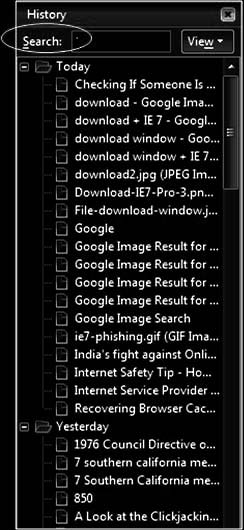
The investigator can also search the history itself, as shown in Figure 11-4. Many browsers also offer a URL
suggestion feature, so the investigator can start typing in a suspected URL to see if the suspect visited that site.
Once a site is found, the investigator can check to see if the suspect saved any form data for that site. This will let the investigator know that the suspect used that particular site.
11-8
Chapter 11
Figure 11-4 Investigators can search
Figure 11-5 Investigators can look at the
the browser history on a suspect
download history in a suspect’s browser to
computer to see if the suspect has
see if he or she has downloaded any child
visited any child pornography sites.
pornography.
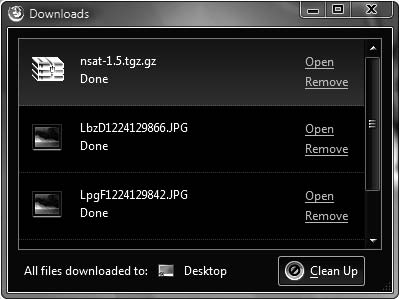
Download History
Download history is one of the features of most Internet browsers. It shows what files were downloaded and where the downloaded files were saved. To view the download history in Firefox on a Windows system, a user can either select Tools and then Downloads, or just press Ctrl+J. Though users tend to clear the download history regularly, any files that do show up in the list could be useful as evidence. Figure 11-5 shows the download history window in Firefox.
Cache
The browser cache is a collection of Web page copies stored on the system’s hard disk or in its volatile memory.
Most browsers allow the user to specify the size of the cache. The user can also manually clear the cache. The investigator can search for information in the browser cache. If the cache has been cleared, the investigator can use tools to view the files in which the browser cache is stored to see if there are any traces of important information.
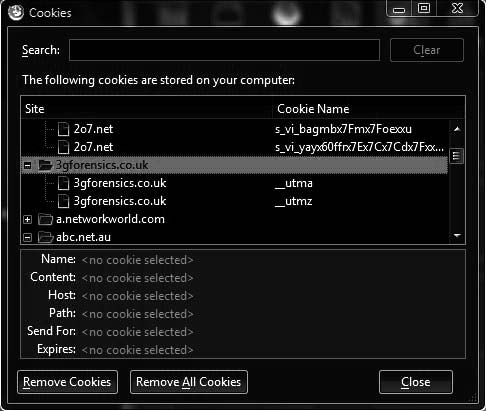
Cookies
A cookie is a piece of information that a Web site stores on a user’s system. Most browsers allow users to view these cookies. Figure 11-6 shows the button in Firefox that allows users to view cookies. Viewing the cookies allows the investigator to see what sites have stored cookies on the system. These are sites that the suspect has visited, possibly frequently. Figure 11-7 shows the cookie viewer in Firefox.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Steps for Investigating Child Pornography
11-9
Figure 11-6 Users can view the cookies that Web sites have stored on their computers.
Figure 11-7 Investigators can use cookies to see what sites a suspect has visited.
11-10
Chapter 11
Saved Passwords
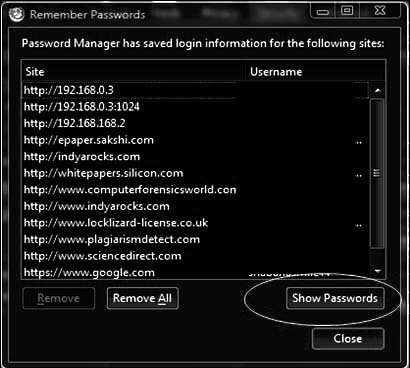
Most modern browsers give users the option to store passwords used on Web sites. Viewing these
passwords allows the investigator to see the URLs of the sites, usernames and passwords, as shown in Figure 11-8.
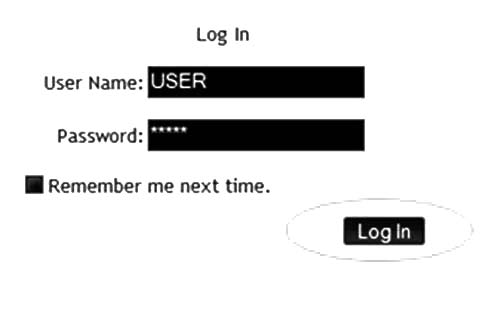
Authenticated Sessions
An authenticated session is the use of the correct username and password for a particular site. Sites often allow users to save their login information for future visits. If an investigator visits a suspected site, he or she can see that the suspect has been there before if the authentication information has been saved. Figure 11-9 shows a site that allows a user to save login information.
Figure 11-8 Many browsers allow users to save passwords, giving
investigators evidence they can use during an investigation.
Figure 11-9 Many sites allow users to save their
authentication information for future visits.
Guidelines to Avoid Child Pornography on the Web
11-11
Step 7: Check ISP Logs
ISP logs contain all Internet activity information that Internet service providers save. They are the logs of the users’ visited Web pages. It can be difficult for an investigator to extract information from these logs for the following reasons:
• Some ISPs refuse to show their logs in order to maintain user privacy.
• Even when ISPs release their logs, investigators may find it difficult to extract the required information from the huge amount of log data.
ISP logs can reveal whether any users that the ISP serves have visited a site that police have identified as a child pornography site.
Sources of Digital Evidence
The following are some of the sources of evidence that play an important role during an investigation:
• Offender’s computer: The offender’s computer is the main source of evidence during the investigation of child pornography cases. Any pornographic material stored on the offender’s computer is important evidence for the investigation. Log files show detailed information about who logged on to the computer and when. Web browser history shows the online activities of the criminal. E-mail and chat logs constitute an online communication record of the offender.
• Handheld devices: Offenders may also use handheld devices for child pornography. They may use devices such as PDAs and mobile phones with digital cameras to record offensive pictures and transmit digital images. Therefore, these devices are also important in an investigation.
• Servers: Servers may also play an important role in an investigation. For example, an ISP authentication server records a customer’s information, including the IP address that can be used to identify the user. FTP and Web servers are generally used for uploading and downloading files; these servers record details about what files are uploaded or downloaded, and they also keep track of the IP addresses of users who connect to the servers.
Citizens’ Responsibility in Fighting Against Child Pornography
Citizens have a responsibility to act against child pornography to try to eradicate it completely. The following are some ways that citizens can fight against child pornography:
• Protest against child pornography Web sites.
• Provide information about the impact of pornography on children.
• Take initiatives to cease child pornography on the Web.
• Report to anti-child-pornography organizations about any child pornography sites.
• Block credit card transactions that are requested for child pornography.
• Ask ISPs to block the content or URL of a child pornography site.
Guidelines to Avoid Child Pornography on the Web
There are many child pornography sites on the Web. The following are some guidelines for avoiding child pornography on the Web:
• Use Internet filters that filter unwanted content on the system: Internet filters are pieces of software that are installed on a system in order to block unwanted content, such as child pornography sites or gambling sites.
• Make use of search engines that have built-in filters: Search engines that have built-in filters help a user search safely, as they filter results. For instance, Google’s Safe Search feature filters out any sexually explicit or otherwise unsafe images.
11-12
Chapter 11
• Avoid guesswork for URLs: Many users have a habit of taking a guess about a site’s URL. An incorrect guess can take a user to a pornographic site.
• Use proper and appropriate keywords during research: Using inappropriate keywords while doing research can lead users to sites containing child pornography or other inappropriate content.
• Avoid clicking on questionable URLs or banners: These may take a user to an unwelcome site.
Guidelines for Parents to Reduce the Risk of Their Children
Being Exposed to Child Pornography
Parental guidance is the best way to keep children away from child pornography. The following are some guidelines for parents to reduce the risk to their children:
• Form a friendly, trusting relationship with the child: If the child is afraid of his or her parents, it is unlikely that he or she will ask for or accept help. The child may also be hesitant about reporting any pornographic sites he or she finds to his or her parents.
• Guide the child while he or she is browsing: Parents should teach children how to safely browse the Internet. This includes teaching them about sites to avoid and about how to perform safe searches.
• Install filtering software that blocks pornographic sites: There are various Internet filters available that parents can use to block children from accessing the Web sites that parents wish to block.
• Promote the use of search engines with safe search: Parents should promote the use of search engines with safe search (such as Google) to keep children away from potentially dangerous sites.
• Make the child aware of the prevalence of child pornography on the Internet: Parents should explain to their children in detail about how easy it is to be exposed to child pornography on the Internet, even accidentally. Parents may even want to familiarize their children with the laws concerning
child pornography.
• Assist the child with various anti-child-pornography organizations: It is the duty of parents to inform their children about whom to approach and how to report illegal sites that children might come across.
• Use monitoring software: Parents should use software that monitors and records all Web sites visited by the child, captures and logs the chat conversations of the child, monitors their e-mails, and so on.
Tool: Reveal
Reveal allows parents to quickly evaluate the files on a system for the presence of child pornography. It works by comparing each word inside text files against special dictionaries of words commonly used by pedophiles, child pornographers, and other types of criminals. It also searches for image, video, and audio files on a system so parents can review those files for objectionable content.
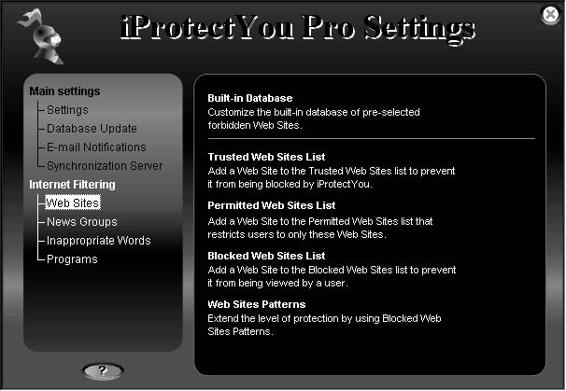
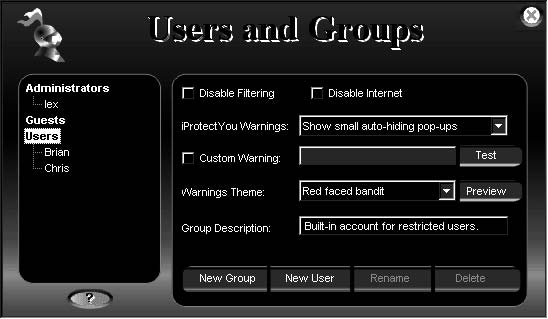
Tool: iProtectYou
iProtectYou is an Internet filtering and monitoring program that enables users to control when the Internet can be used and which Web sites can be accessed through the computer. iProtectYou is designed for parents who are concerned about the possible detrimental effects of the Internet on the development of their children. iProtectYou is also designed for schools and libraries, so that they can control what is being viewed in public spaces.
iProtectYou gives parents several methods for blocking their children’s access to child pornography over the Internet, including the following:
• Porn block by word filtering: Parents can prevent access to Web sites that contain certain words or phrases. Parents can either create a list of words or use the list included with the program.
Tool: Web Control for Parents
11-13
Source: http://www.softforyou.com/articles tutorials/porn blockers.html. Accessed 2/2007.
Figure 11-10 Parents can use iProtectYou to control which Web sites their children
can visit.
• Porn block by URL filtering: Parents can block individual Web sites based on their URLs.
• Porn block by using the bad-site list: This constantly updated list is made up of thousands of Web sites that contain undesirable content such as pornography. This list is provided with the program.
The following are some of the features of iProtectYou:
• Restricts family members from visiting Web sites (Figure 11-10) and newsgroups that may contain pernicious information
• Blocks e-mails, chat sessions, instant messages, and P2P connections if they contain
inappropriate words
• Prevents private information from being sent over the Internet
• Allows a parent to set a schedule of days and times when online activity is allowed
• Limits Internet traffic to a specified amount of data that can be sent or received per user, per day
• Allows parents to control the list of programs that can have access to the Internet
• Sends notification e-mails with full descriptions of blocked operations and an attached screenshot of the child’s computer
• Allows parents to set different levels of restrictions for every member of the family based on maturity, interest, habits, and parental control needs (Figure 11-11)
Tool: Web Control for Parents
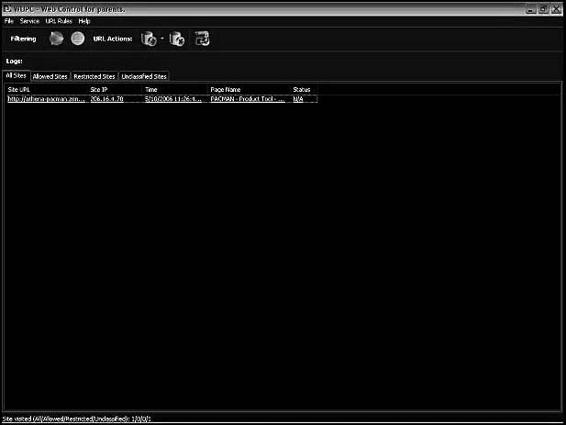
Web Control for Parents is a parental control tool, developed specially for protecting children from forbidden materials such as pornography, online gambling, and online drug information. It allows parents to view what Web sites their children visited and block any that the parents find objectionable. Figure 11-12 shows a screenshot from Web Control for Parents.
11-14
Chapter 11
Source: http://www.softforyou.com/articles tutorials/porn blockers.html. Accessed 2/2007.
Figure 11-11 Parents can create users or groups and then assign different
restrictions for each user or group.
Source: http://www.download.com/WUPC-Web-Control-for-Parents/3000-2311 4-10529193.html. Accessed 2/2007.
Figure 11-12 Web Control for Parents allows parents to view what Web sites their
children visited.
Tool: ChatGuard
11-15
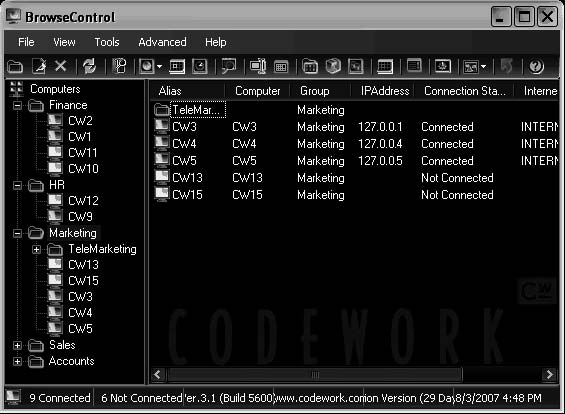
Tool: BrowseControl
BrowseControl controls access to the Internet and blocks the usage of certain applications. Parents can also use it to block access to floppy disks, CD drives, and USB drives.
The following are some of the features of BrowseControl:
• It can completely block Internet access.
• It allows access only to Web sites parents specify.
• It allows parents to schedule times when children can access the Internet.
• It can block the use of different protocols and ports.
Figure 11-13 shows a screenshot from BrowseControl.
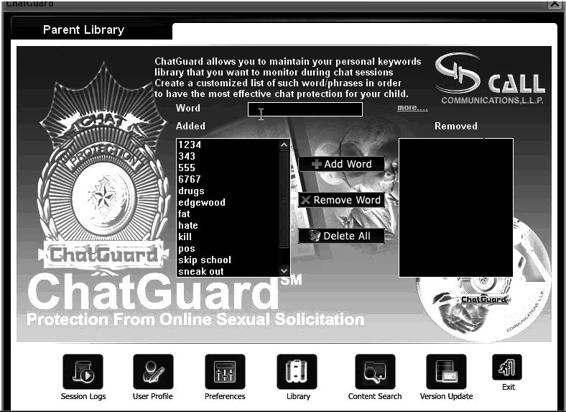
Tool: ChatGuard
ChatGuard is software developed to protect children from online sexual solicitation. It monitors the following:
• Internet activity, including the following:
• Chat sessions
• Sites visited
• E-mails
• Games and audio
• Desktop enhancements
Figures 11-14 and 11-15 show screenshots from ChatGuard.
Source: http://www.browsecontrol.com/overview.html. Accessed 2/2007.
Figure 11-13 BrowseControl allows a user to monitor and control access to
the Internet.

11-16
Chapter 11
Source: http://www.chatprotection.com/. Accessed 2/2007.
Figure 11-14 ChatGuard allows parents to view logs of their children’s chat sessions.
Source: http://www.chatprotection.com/. Accessed 2/2007.
Figure 11-15 Using ChatGuard, parents can maintain a list of keywords that they
want to watch for in chat sessions.
Child Pornography Legislation Survey
11-17
Tool: Child Exploitation Tracking System (CETS)
CETS was developed jointly by Microsoft Canada, the Royal Canadian Mounted Police (RCMP), and the Toronto Police Service. CETS is a software solution that allows different law-enforcement agencies to collaborate.
It also provides investigators with a set of software tools they can use when investigating child pornography.
The tracking system serves as a repository of information. The software enables police agencies to capture, share, and search information. The following are some of the features of CETS:
• CETS enables agencies to avoid duplicating effort. Sharing information over a secure network, officers can match up investigations that reference the same people or online identities.
• CETS links and connects criminal behavior online that is difficult for the human eye to see.
• Using CETS, police agencies can manage and analyze huge volumes of information in different ways, such as cross-referencing obscure data relationships and using social-network analysis to identify communities of offenders.
Child Pornography Legislation Survey
Table 11-1 shows the results of a survey of various countries concerning legislation against child pornography.
This table shows that some countries such as Afghanistan, Albania, Bangladesh, India, Pakistan, Thailand, Singapore, and Egypt do not have any laws against child pornography, while countries such as Argentina, Austria, Belgium, Brazil, Canada, France, Germany, Hong Kong, Italy, Japan, New Zealand, Russia, South Africa, the United Kingdom, and the United States have well-defined laws against child pornography.
Country
Legislation
Child
Includes
Includes Simple
Includes ISP
Specific to Child
Pornography
Computer-
Possession?
Reporting?
Pornography?
Defined?
Facilitated
Offenses?
Afghanistan
✕
✕
✕
✕
✕
Albania
✕
✕
✕
✕
✕
Algeria
✕
✕
✕
✕
✕
Andorra
✓
✕
✕
✓
✕
Angola
✕
✕
✕
✕
✕
Antigua & Barbuda
✕
✕
✕
✕
✕
Argentina
✓
✕
✕
✕
✕
Armenia
✓
✕
✓
✕
✕
Aruba
✓
✕
✓
✓
✕
Australia
✓
✓
✓
✓
✓
Austria
✓
✓
✓
✓
✕
Azerbaijan
✕
✕
✕
✕
✕
Table 11-1 This table shows what types of legislation, if any, concerning child pornography that countries around the world have
( continues)
11-18
Chapter 11
Country
Legislation
Child
Includes
Includes Simple
Includes ISP
Specific to Child
Pornography
Computer-
Possession?
Reporting?
Pornography?
Defined?
Facilitated
Offenses?
Bahamas
✕
✕
✕
✕
✕
Bahrain
✕
✕
✕
✕
✕
Bangladesh
✕
✕
✕
✕
✕
Barbados
✓
✕
✕
✓
✕
Belarus
✓
✕
✕
✕
✕
Belgium
✓
✓
✓
✓
✓
Belize
✕
✕
✕
✕
✕
Benin
✕
✕
✕
✕
✕
Bhutan
✓
x
✓
x
x
Bolivia
✕
✕
✕
✕
✕
Bosnia-
✓
✕
✓
✓
✕
Herzegovina
Botswana
✕
✕
✕
✕
✕
Brazil
✓
✕
✓
✕
✕
Brunei
✓
✕
✓
✕
✕
Bulgaria
✓
✕
✓
✓
✕
Burkina-Faso
✕
✕
✕
✕
✕
Burundi
✕
✕
✕
✕
✕
Cambodia
✕
✕
✕
✕
✕
Cameroon
✕
✕
✕
✕
✕
Canada
✓
✓
✓
✓
✕
Cape Verde
✓
✕
✕
✕
✕
Central African
✕
✕
✕
✕
✕
Republic
Chad
✕
✕
✕
✕
✕
Chile
✓
✓
✓
✕
✕
China
✓
✕
✓
✕
✕
Colombia
✓
✓
✓
✕
✓
Comoros
✕
✕
✕
✕
✕
Congo
✕
✕
✕
✕
✕
Costa Rica
✓
✓
✕
✕
✕
Côte d’Ivoire
✕
✕
✕
✕
✕
Croatia
✓
✕
✓
✓
✕
Cuba
✕
✕
✕
✕
✕
Cyprus
✓
✕
✓
✓
✕
Czech Republic
✓
✕
✓
✕
✕
Democratic
✕
✕
✕
✕
✕
Republic of Congo
Denmark
✓
✓
✓
✓
✕
Table 11-1 This table shows what types of legislation, if any, concerning child pornography that countries around the world have
Child Pornography Legislation Survey
11-19
Country
Legislation
Child
Includes
Includes Simple
Includes ISP
Specific to Child
Pornography
Computer-
Possession?
Reporting?
Pornography?
Defined?
Facilitated
Offenses?
Djibouti
✕
✕
✕
✕
✕
Dominica
✕
✕
✕
✕
✕
Dominican
✓
✕
✕
✕
✕
Republic
Ecuador
✓
✕
✕
✕
✕
Egypt
✕
✕
✕
✕
✕
El Salvador
✓
✕
✓
✓
✕
Equatorial Guinea
✕
✕
✕
✕
✕
Eritrea
✕
✕
✕
✕
✕
Estonia
✓
✕
✓
✓
✕
Ethiopia
✕
✕
✕
✕
✕
Fiji
✕
✕
✕
✕
✕
Finland
✓
✓
✓
✓
✕
France
✓
✓
✓
✓
✓
Gabon
✕
✕
✕
✕
✕
Gambia
✓
✕
✕
✕
✕
Georgia
✓
✓
✕
✕
✕
Germany
✓
✓
✓
✓
✕
Ghana
✕
✕
✕
✕
✕
Greece
✓
✓
✓
✓
✕
Grenada
✕
✕
✕
✕
✕
Guatemala
✓
✕
✕
✕
✕
Guinea
✕
✕
✕
✕
✕
Guinea Bissau
✕
✕
✕
✕
✕
Guyana
✕
✕
✕
✕
✕
Haiti
✕
✕
✕
✕
✕
Honduras
✓
✓
✓
✓
✕
Hong Kong
✓
✓
✓
✓
✕
Hungary
✓
✓
✓
✓
✕
Iceland
✓
✕
✓
✓
✕
India
✕
✕
✕
✕
✕
Indonesia
✕
✕
✕
✕
✕
Iran
✕
✕
✕
✕
✕
Iraq
✕
✕
✕
✕
✕
Ireland
✓
✓
✓
✓
✕
Israel
✓
✓
✓
✓
✕
Italy
✓
✓
✓
✓
✕
Jamaica
✕
✕
✕
✕
✕
Table 11-1 This table shows what types of legislation, if any, concerning child pornography that countries around the world have
( continues)
11-20
Chapter 11
Country
Legislation
Child
Includes
Includes Simple
Includes ISP
Specific to Child
Pornography
Computer-
Possession?
Reporting?
Pornography?
Defined?
Facilitated
Offenses?
Japan
✓
✓
✓
✕
✕
Jordan
✕
✕
✕
✕
✕
Kazakhstan
✓
✕
✕
✕
✕
Kenya
✕
✕
✕
✕
✕
Korea
✓
✓
✓
✕
✕
Kuwait
✕
✕
✕
✕
✕
Kyrgyzstan
✓
✕
✕
✕
✕
Laos
✕
✕
✕
✕
✕
Latvia
✓
✕
✓
✕
✕
Lebanon
✕
✕
✕
✕
✕
Lesotho
✕
✕
✕
✕
✕
Liberia
✕
✕
✕
✕
✕
Libya
✕
✕
✕
✕
✕
Liechtenstein
✓
✕
✓
✓
✕
Lithuania
✓
✕
✕
✓
✕
Luxembourg
✓
✕
✓
✓
✕
Macedonia
✓
✕
✓
✕
✕
Madagascar
✓
✕
✓
✕
✕
Malawi
✕
✕
✕
✕
✕
Malaysia
✕
✕
✕
✕
✕
Maldives
✕
✕
✕
✕
✕
Mali
✓
✕
✕
✕
✕
Malta
✓
✕
✓
✓
✕
Marshall Islands
✕
✕
✕
✕
✕
Mauritania
✕
✕
✕
✕
✕
Mauritius
✓
✕
✓
✕
✕
Mexico
✓
✓
✓
✕
✕
Moldova
✕
✕
✕
✕
✕
Monaco
✕
✕
✕
✕
✕
Mongolia
✕
✕
✕
✕
✕
Morocco
✓
✕
✕
✓
✕
Mozambique
✕
✕
✕
✕
✕
Myanmar
✓
✕
✕
✕
✕
Namibia
✕
✕
✕
✕
✕
Nauru
✕
✕
✕
✕
✕
Nepal
✓
✕
✕
✕
✕
Netherlands
✓
✓
✓
✓
✕
Table 11-1 This table shows what types of legislation, if any, concerning child pornography that countries around the world have
Child Pornography Legislation Survey
11-21
Country
Legislation
Child
Includes
Includes Simple
Includes ISP
Specific to Child
Pornography
Computer-
Possession?
Reporting?
Pornography?
Defined?
Facilitated
Offenses?
Netherlands
✕
✕
✕
✕
✕
Antilles
New Zealand
✓
✓
✓
✓
✕
Nicaragua
✕
✕
✕
✕
✕
Niger
✕
✕
✕
✕
✕
Nigeria
✕
✕
✕
✕
✕
Norway
✓
✓
✓
✓
✕
Oman
✕
✕
✕
✕
✕
Pakistan
✕
✕
✕
✕
✕
Panama
✓
✓
✓
✓
✕
Papua New Guinea
✓
✕
✕
✓
✕
Paraguay
✓
✕
✕
✓
✕
Peru
✓
✓
✓
✓
✕
Philippines
✓
✕
✕
✕
✕
Poland
✓
✕
✕
✓
✕
Portugal
✓
✕
✓
✕
✕
Qatar
✓
✕
✓
✕
✕
Romania
✓
✓
✓
✓
✕
Russia
✓
✕
✕
✕
✕
Rwanda
✕
✕
✕
✕
✕
St. Kitts & Nevis
✕
✕
✕
✕
✕
St. Lucia
✕
✕
✕
✕
✕
St. Vincent & the
✕
✕
✕
✕
✕
Grenadines
Sao Tome &
✕
✕
✕
✕
✕
Principe
Saudi Arabia
✕
✕
✕
✕
✕
Senegal
✕
✕
✕
✕
✕
Serbia &
✓
✕
✓
✕
✕
Montenegro
Seychelles
✕
✕
✕
✕
✕
Sierra Leone
✕
✕
✕
✕
✕
Singapore
✕
✕
✕
✕
✕
Slovak Republic
✓
✓
✓
✓
✕
Slovenia
✓
✓
✓
✕
✕
Somalia
✕
✕
✕
✕
✕
South Africa
✓
✓
✓
✓
✓
Spain
✓
✕
✓
✓
✕
Sri Lanka
✓
✕
✕
✓
✕
Table 11-1 This table shows what types of legislation, if any, concerning child pornography that countries around the world have
( continues)
11-22
Chapter 11
Country
Legislation
Child
Includes
Includes Simple
Includes ISP
Specific to Child
Pornography
Computer-
Possession?
Reporting?
Pornography?
Defined?
Facilitated
Offenses?
Sudan
✕
✕
✕
✕
✕
Suriname
✕
✕
✕
✕
✕
Swaziland
✕
✕
✕
✕
✕
Sweden
✓
✕
✓
✓
✕
Switzerland
✓
✓
✓
✓
✕
Syria
✕
✕
✕
✕
✕
Tajikistan
✓
✕
✕
✕
✕
Tanzania
✓
✕
✕
✕
✕
Thailand
✕
✕
✕
✕
✕
Timor-Leste
✕
✕
✕
✕
✕
Togo
✕
✕
✕
✕
✕
Tonga
✓
✓
✓
✓
✕
Trinidad & Tobago
✕
✕
✕
✕
✕
Tunisia
✓
✕
✓
✕
✕
Turkey
✓
✕
✕
✓
✕
Turkmenistan
✕
✕
✕
✕
✕
Uganda
✕
✕
✕
✕
✕
Ukraine
✓
✕
✓
✕
✕
United Arab Emirates ✕
✕
✕
✕
✕
United Kingdom
✓
✓
✓
✓
✕
United States
✓
✓
✓
✓
✓
Uruguay
✓
✕
✓
✕
✕
Uzbekistan
✕
✕
✕
✕
✕
Venezuela
✓
✓
✓
✕
✕
Vietnam
✕
✕
✕
✕
✕
Yemen
✕
✕
✕
✕
✕
Zambia
✕
✕
✕
✕
✕
Zimbabwe
✕
✕
✕
✕
✕
Table 11-1 This table shows what types of legislation, if any, concerning child pornography that countries around the world have continued
U.S. Laws Against Child Pornography
There are several U.S. laws concerning child pornography. The following sections describe some of these laws.
§ 18 U.S.C. 1466A
This law involves the prohibition of the production, distribution, reception, and possession of child pornography. It also defines child pornography under U.S. law as any obscene visual representation of a minor engaging in sexually explicit conduct that lacks serious literary, artistic, political, or scientific value. This law also prohibits the transportation and transmittal of child pornography.
Belgian Laws Against Child Pornography
11-23
§ 18 U.S.C. 2251
The focus of this law is preventing the sexual exploitation of children. It prohibits using, persuading, enticing, or coercing a minor to engage in sexually explicit conduct for the purpose of producing child pornography. It also prohibits parents and legal guardians from knowingly permitting minors to engage in sexually explicit conduct for the purpose of producing child pornography. This law also covers printing, receiving, buying, producing, or exchanging child pornography or advertisements for child pornography.
§ 18 U.S.C. 2252
This law prohibits transporting child pornography by any means, including through electronic media or the postal system. It also prohibits knowingly receiving such material. The law also prohibits selling or possessing any child pornography that has been transported.
§ 42 U.S.C. 13032
The purpose of this law is to spell out the duties of ISPs in reporting child pornography. It also specifies the hefty fines that an ISP must pay if it knowingly and willfully fails to report such a discovery of child pornography.
State Laws: Michigan Laws Against Child Pornography
The Child Abuse and Neglect Prevention Act establishes the state Child Abuse and Neglect Prevention Board.
It also describes the powers and duties of this board.
Australian Laws Against Child Pornography
There are several laws in Australia dealing with child pornography. The following sections describe a pair of laws concerning child pornography sent over computer networks.
Criminal Code Act 1995 Section 474.19
This law prohibits a person from using a computer network to access, transmit, publish, distribute or make available child pornography material. The penalty for violating this law is imprisonment for 10 years.
Criminal Code Act 1995 Section 474.20
This law prohibits a person from possessing, producing, supplying, or obtaining child pornography material for use through a computer network. The penalty for violating this law is imprisonment for 10 years.
Austrian Laws Against Child Pornography
One of the major laws concerning child pornography in Austria is Austrian Penal Code § 207a. This law states that anyone who produces, imports, exports, offers, procures, transfers, or makes available child pornography will be sentenced to up to 3 years’ imprisonment. It also spells out further punishments for those who violate the law for financial gain or who violate the law in a way that causes harm to the minor involved. The law also provides a punishment of 1 to 2 years in prison for anyone who possesses child pornography.
Belgian Laws Against Child Pornography
The following two sections describe two laws against child pornography in Belgium.
Article 383bis of the Penal Code
This law prohibits the display, sale, rental, distribution, manufacture, possession, or import of child pornography. Penalties for violating this law include fines, imprisonment for a month to a year, and forced labor for 10 to 15 years.
Article 380ter of the Penal Code
This law prohibits a person from publishing or distributing an offer of services of a sexual nature with a direct or indirect profit-making objective, when the publicity is either specifically addressed to minors or when the 11-24
Chapter 11
services involve minors. It also specifically makes note of this occurring over a telecommunications medium.
Those who respond to such advertisements will also be punished.
Cypriot Laws Against Child Pornography
There are two major laws against child pornography in Cyprus, and these are covered in the following two sections.
The Convention on Cybercrime, Law 22(III)/2004
This law prohibits the following:
• Producing child pornography for the purpose of its distribution through a computer system
• Offering or making available child pornography through a computer system
• Distributing or transmitting child pornography through a computer system
• Procuring child pornography through a computer system
• Possessing child pornography in a computer system or on a computer data storage medium
Combating Trafficking in Human Beings and Sexual Abuse
of Minors Law 3(1)/2000
This law states that anyone who makes, possesses, carries, imports, exports, publishes, or distributes child pornography will be imprisoned for up to 10 years.
Japanese Laws Against Child Pornography
The Law for Punishing Acts Related to Child Prostitution and Child Pornography and for Protecting Children is the major law concerning child pornography in Japan. Article 2 of this law defines child pornography as a visual depiction of the following:
• A child posed in such a way that it appears that the child is engaging in sexual intercourse or an act similar to sexual intercourse
• A child touching his or her genital organs or the genital organs of another person in order to arouse the viewer’s sexual desire
• A child who is naked totally or partially in order to arouse the viewer’s sexual desire
Article 7 of this law prohibits the distribution, sale, lending, or display of child pornography. It also prohibits the production, possession, transportation, import, and export of child pornography.
South African Laws Against Child Pornography
There are several South African laws concerning child pornography. These are described in the
following sections.
Child Care Amendment Act
This act prohibits the commercial sexual exploitation of children. It also establishes secure care facilities for children. Section 50A of this act says that anyone who participates or is involved in the commercial sexual exploitation of a child will be punished. This section also says that any person who is an owner, lessor, manager, tenant, or occupier of a property where the sexual exploitation of a child occurs and who learns of this occurrence must report it to the police or else that person will also be punished.
Amendment of Section 2 of Act 65 of 1996
This amendment prohibits the creation, production, possession, and distribution of child pornography. It specifically mentions the Internet as a prohibited distribution medium.
Scottish Laws Against Child Pornography
11-25
Amendment of Section 27 of Act 65 of 1996
This amendment prohibits the creation, production, import, and possession of child pornography.
U.K. Laws Against Child Pornography
The Sex Offences Act 2003 is the major piece of legislation concerning child pornography in the U.K. The following sections describe sections of this law that deal with child pornography.
Section 15
This section concerns meeting a child following sexual grooming. A person violates this law if he or she has communicated with a minor at least twice and then meets or intends to meet with that minor to engage in sexual activity.
Section 16
This section concerns inappropriate touching. A person violates this law if he or she intentionally touches a minor in a sexual manner.
Section 17
This section states that a person violates this law if he or she causes or incites a minor to engage in sexual activity.
Section 18
This section states that a person violates this law if he or she knowingly engages in sexual activity in the presence of a minor.
Section 19
This section states that a person violates this law if he or she forces a minor to watch sexual activity.
Section 47
This section states that a person violates this law if he or she pays for the sexual services of a minor.
Section 48
This section states that a person violates this law if he or she causes or incites child prostitution or child pornography.
Section 49
This section states that a person violates this law if he or she controls the action of a minor involved in child prostitution or child pornography.
Section 50
This section states that a person violates this law if he or she arranges or facilitates child prostitution or child pornography.
English and Welsh Laws Against Child Pornography
The Protection of Children Act 1978 states that it is an offense for a person to take, or permit to be taken, or to make an indecent photograph of a child. It is also an offense under this law to possess, distribute, publish, or display such photographs.
Scottish Laws Against Child Pornography
The Civic Government (Scotland) Act 1982 deals with child pornography. The act prohibits the creation, distribution, possession, publishing, and display of indecent photographs of children.
11-26
Chapter 11
Philippine Laws Against Child Pornography
Republic Act 7610—known as the Special Protection of Children against Child Abuse, Exploitation, and Discrimination Act—deals with child prostitution and other sexual abuse. It states that children who are influenced by an adult, syndicate, or group to engage in sexual intercourse for the monetary or profitable gain of the adult, syndicate, or group are deemed to be victims of child prostitution and other sexual abuse. Those who engage in this exploitation are punished under the law. This includes those who coerce the child into performing the sexual activity and those who engage in the sexual activity with the child.
Children’s Internet Protection Act (CIPA)
The Children’s Internet Protection Act (CIPA) is a federal law that addresses concerns about access to offensive content over the Internet on school and library computers. CIPA imposes certain types of requirements on any school or library that receives funding for Internet access or internal connections from the E-rate program—a program that makes certain communications technology more affordable for eligible schools and libraries.
The following are the requirements of CIPA:
• Schools and libraries subject to CIPA may not receive the discounts offered by the E-rate program unless they certify that they have an Internet safety policy and technology protection measures in place. This Internet safety policy must block or filter access to images that are obscene, are child pornography, or are otherwise harmful to minors.
• Schools subject to CIPA are required to adopt and enforce a policy to monitor the online activities of minors.
• Schools and libraries subject to CIPA are required to adopt and implement a policy addressing access by minors to inappropriate material on the Internet, the safety and security of minors who engage in electronic communications over the Internet, unauthorized access and other unlawful activities by minors online, unauthorized disclosure of personal information regarding minors, and restricting minors’ access to harmful materials online.
Anti-Child-Pornography Organizations
Anti-child-pornography organizations are nonprofit organizations established to eradicate child pornography so children can live in a better environment. They accept anonymous and online abuse reports to maintain the privacy of individuals. The following are some of the various anti-child-pornography organizations:
• Project Safe Childhood (PSC)
• Innocent Images National Initiative (IINI)
• Internet Crimes Against Children (ICAC)
• Anti-Child Porn Organization (ACPO)
• Child Exploitation and Online Protection Centre (CEOP)
• Think U Know
• Virtual Global Taskforce (VGT)
• Internet Watch Foundation (IWF)
• International Centre for Missing & Exploited Children (ICMEC)
• National Center for Missing & Exploited Children (NCMEC)
• CyberTipline
• Child Victim Identification Program (CVIP)
• Financial Coalition Against Child Pornography (FCACP)
• Perverted Justice
• National Society for the Prevention of Cruelty to Children (NSPCC)
• Canadian Centre for Child Protection (CCCP)
• Cybertip.ca
Anti-Child-Pornography Organizations
11-27
• Association of Sites Advocating Child Protection (ASACP)
• Web Sites Against Child Porn (WSACP)
• Report Child Porn
• Child Focus
• StopChildPorno.be
Project Safe Childhood
Project Safe Childhood (PSC) aims to combat technology-facilitated sexual exploitation crimes against children.
Its goals are to investigate and prosecute vigorously, and to protect and assist the victimized children. The organization recognizes the need for a broad, community-based effort to protect children.
PSC creates, on a national platform, locally designed partnerships of federal, state, local, and tribal law enforcement officers in each federal judicial district to investigate and prosecute Internet-based crimes against children. With the U.S. Attorney as the convener, each local community is able to design and implement programs that are uniquely tailored to its needs, while maximizing the impact of national resources and expertise.
The PSC partnerships in every district aim to address the five major components of the initiative, as follows: 1. Integrated federal, state, and local efforts to investigate and prosecute child exploitation cases, and to identify and rescue child victims: U.S. Attorneys coordinate the investigation and prosecution of child exploitation crimes, and the efforts to identify and rescue victims.
2. Participation of PSC partners in coordinated national initiatives: Child pornography cases are often initiated by law enforcement agents uncovering a peer-to-peer network, server, or Web site. Such national operations may be conducted by the FBI’s Innocent Images Unit, ICE’s Cyber Crime Center, USPIS’s Child Exploitation Task Forces, ICAC task forces, or others. These investigations can lead to hundreds or thousands of leads in communities throughout the country.
3. Increased federal involvement in child pornography and enticement cases: All states have laws in place to respond to child exploitation and abuse, and some states have very significant criminal laws and penalty provisions for child pornography offenders and online sexual predators that parallel or exceed those provided by federal law. However, federal law has some advantages over state law, so PSC strives to get federal prosecutors more involved in these types of cases.
4. Training of federal, state, and local law enforcement: Computer-based crimes present unique challenges for law enforcement. Investigators must be trained and have the necessary equipment to investigate and perform computer forensic analysis of targeted equipment. A key component of PSC is to ensure that federal, state, local, and tribal officers are properly instructed.
5. Community awareness and educational programs: PSC aims to enhance existing efforts to generate awareness and to educate the public about the threats to children and the ways to prevent online exploitation. It partners with existing national programs to raise awareness about the threat of online sexual predators and provide the tools and information to parents and children seeking to report possible violations.
Innocent Images National Initiative
The Innocent Images National Initiative (IINI), a component of the FBI’s Cyber Crimes Program, combats child pornography and child sexual exploitation facilitated by an online computer. It provides centralized coordina-tion with state, local, and international governments. It also provides analysis of case information.
The following are the main goals of the IINI:
• To reduce the vulnerability of children to acts of sexual exploitation and abuse that are facilitated through the use of computers
• To identify and rescue witting and unwitting child victims
• To investigate and prosecute sexual predators who use the Internet and other online services to sexually exploit children for personal or financial gain
• To strengthen the capabilities of federal, state, local, and international law enforcement through training programs and investigative assistance
The FBI’s Innocent Images National Initiative focuses on the following:
• Online organizations, enterprises, and communities that exploit children for profit or personal gain
• Producers of child pornography
11-28
Chapter 11
• Individuals who travel, or indicate a willingness to travel, for the purpose of engaging in sexual activity with a minor
• Major distributors of child pornography
• Possessors of child pornography
The following are some of the areas of the Internet that the IINI investigates:
• Internet Web sites that post child pornography
• Internet newsgroups
• Internet Relay Chat (IRC) channels
• File servers
• Online groups and organizations
• Peer-to-peer (P2P) file-sharing programs
• Bulletin board systems and other online forums
Internet Crimes Against Children
The Internet Crimes Against Children Task Force (ICAC) investigates and prosecutes individuals who use the Internet to exploit children. It comprises regional task forces that assist state and local law enforcement develop an effective response to computer-related crimes against children, including child pornography. The following are some of the things the ICAC provides to law enforcement agencies:
• Proactive investigations
• Forensic and investigative components
• Training and technical assistance
• Effective prosecutions
• Victim services
• Community education
The following are some of the components of the task force’s mission:
• To intervene and stop individuals who use the Internet to entice a child to meet with them for sexual purposes
• To investigate and prosecute those who possess, create, or distribute child pornography
• To educate the public about the dangers that exist for minors on the Internet
Anti-Child Porn Organization
The Anti-Child Porn Organization (ACPO) is an organization whose mission is to stop the sexual exploitation of the world’s children. Composed of volunteers from all over the world, ACPO focuses on the issues of child pornography production and distribution via the Internet, as well as the predatory use of the Internet for the sexual abuse of children.
The organization’s main goal is to protect children from becoming victims of child pornography and to keep it from spreading over the Internet. Its secondary goal is educating individuals and organizations about the Internet and its associated risks. The ACPO feels it is key to educate both politicians and the public about the danger that child pornographers pose to the collective social interest. The organization also counsels law enforcement agencies on gathering information and evidence related to the Internet.
The following are some of the ACPO’s other goals:
• To provide a massive amount of information to law enforcement authorities, including activity hot spots on the Internet and the results of the ACPO’s own investigations of the activities of online child pornographers
• To halt sensationalism and hype regarding the Internet while promoting quality investigative journalism on pedophile pornography
• To create enough public pressure to bring authorities to the point of action
• To form a cooperative with other Internet groups with similar goals that will benefit them all and increase their impact
Anti-Child-Pornography Organizations
11-29
How to Report to the Anti-Child Porn Organization About Child Pornography Cases
The following is the procedure for reporting child pornography cases to the Anti-Child Porn Organization: 1.
Go
to
http://www.antichildporn.org.
2.
Click
Report! and then Report Child Porn.
3. A form titled “Anonymous Submission” will appear (Figure 11-16).
4. Give the appropriate Web address or FTP address of the pornographic sites.
5. Write details about those sites.
6.
Click
Submit.
Child Exploitation and Online Protection Centre
Child Exploitation and Online Protection (CEOP) Centre is a U.K.-based anti-child-pornography organization.
It focuses on protecting children from sexual abuse. It targets, tracks, and brings offenders or perpetrators to the court of law with the help of local or international forces. Teams consist of police officers, staff members from or sponsored by corporations, and government and corporate experts.
Think U Know
Think U Know is the education program of the Child Exploitation and Online Protection Centre aimed at young people. It encourages safe Internet browsing and is based around the following three themes:
1. How to safely have fun
2. How to stay in control
3. How to report a problem
Source: http://www.antichildporn.org. Accessed 2/2007.
Figure 11-16 Users can use this form to report sites containing child pornography.

11-30
Chapter 11
The Web site divides users into the following groups:
• Children between 5 and 7
• Children between 8 and 10
• Children between 11 and 16
• Parents or caregivers
• Teachers or trainers
Figure 11-17 shows the Web site for Think U Know.
Virtual Global Taskforce
The Virtual Global Taskforce (VGT) is a group of law enforcement agencies from around the world working together to fight child abuse online. The following are some of the objectives of the VGT:
• To make the Internet a safer place
• To identify, locate, and help children at risk
• To hold perpetrators appropriately to account
The VGT is made up of the following agencies:
• Australian Federal Police
• CEOP Centre in the U.K.
• Italian Postal and Communication Police Service
• Royal Canadian Mounted Police
• U.S. Department of Homeland Security
• Interpol
The VGT allows users to report abuse online. The user just needs to click the icon Report Abuse, fill in the details, and submit the report. Figure 11-18 shows a screenshot from the VGT Web site.
Source: http://www.thinkuknow.co.uk/. Accessed 2/2007.
Figure 11-17 The Think U Know Web site divides content into different areas for
different groups of people.
Anti-Child-Pornography Organizations
11-31
Source: http://www.virtualglobaltaskforce.com/. Accessed 2/2007.
Figure 11-18 Users can report abuse on the VGT Web site by clicking the Report
Abuse icon.
Internet Watch Foundation
The Internet Watch Foundation (IWF) is the U.K. hotline for reporting illegal content, specifically acting upon child sexual abuse hosted worldwide, and content, hosted in the U.K., that is criminally obscene or incites racial hatred.
Following are the features of the Internet Watch Foundation (IWF) Web site:
• Online reporting form: It can be reached from any page of the Web site by clicking on the Report Illegal Content Click Here icon on every page (Figure 11-19).
• Links to relevant Web sites: These are shown on every page where needed; this section shows links to the relevant Web sites and document downloads for that page.
• Communications: This section is shown on every page; it provides IWF contact details as well as links to the newsletter registration page, the Web site feedback page, IWF literature, and the materials page.
• News ticker: It is shown on every page; these scrolling links allow users to access the most recent IWF
news stories.
• Search function: It is shown on every page; this function allows users to search the IWF Web site using key words and phrases.
International Centre for Missing & Exploited Children
The International Centre for Missing & Exploited Children (ICMEC) was founded in 1998. It works to identify and coordinate a global network of organizations fighting the sexual exploitation and abduction of children.
It lets people report sites containing child pornography. ICMEC’s work helps children and families by doing the following:
• Establishing a global resource to find missing children and prevent the sexual exploitation of children (Figure 11-20)
• Creating national centers and affiliates worldwide
• Building an international network to disseminate images of and information about missing and
exploited children

11-32
Chapter 11
Source: http://www.iwf.org.uk/. Accessed 2/2007.
Figure 11-19 The IWF Web site features a Report Illegal Content Click Here icon on every page to allow users to report illegal Web site content.
Source: http://www.icmec.org/. Accessed 2/2007.
Figure 11-20 One of the goals of the ICMEC is to find missing children.
• Providing training to law enforcement, prosecutors, judges, legal professionals, nongovernmental organizations, and government officials
• Advocating and proposing legislative changes in laws, treaties, and systems to protect children worldwide
Anti-Child-Pornography Organizations
11-33
• Conducting international expert conferences to build awareness, and encourage and increase cooperation and collaboration between and among countries
• Working alongside financial industry and law enforcement to combat commercial sexual exploitation of children
National Center for Missing & Exploited Children
The National Center for Missing & Exploited Children (NCMEC) is a nonprofit anti-child-pornography organization. It helps people report through the CyberTipline about missing children or about sites that are offering child pornography. Figure 11-21 shows the NCMEC’s Web site.
CyberTipline
CyberTipline is a reporting mechanism for cases of child sexual exploitation, including child pornography, online enticement of children for sex acts, molestation of children outside the family, sex tourism of children, child victims of prostitution, and unsolicited obscene material sent to a child. Reports may be made 24 hours per day, 7 days per week, online or over the phone. Figure 11-22 shows the CyberTipline Web site.
Child Victim Identification Program
The Child Victim Identification Program (CVIP) provides domestic and international agencies with information concerning child pornography cases. It is also the central point of contact for victim identification.
CVIP assists law enforcement and prosecution teams with child-pornography evidence reviews in order to help them learn the full range of crimes committed in each case, maximize sentences available for each charge, and attempt to identify the location of unidentified child sexual exploitation victims. It is maintained by the Child Exploitation and Obscenity Section of the U.S. Department of Justice and the National Center for Missing & Exploited Children (NCMEC). Figure 11-23 shows a Web site concerning CVIP.
Financial Coalition Against Child Pornography
The Financial Coalition Against Child Pornography (FCACP) is a coalition of credit card issuers, Internet services companies, and other financial and technological organizations that seek to eliminate commercial child pornography by taking action on the payment systems used to fund these illegal operations. The International Centre for Missing & Exploited Children (ICMEC) and National Center for Missing & Exploited Children (NCMEC) formed the coalition. As of 2009, thirty-one companies had joined the coalition. Coalition members proactively look for and report child pornography.
Source: http://www.missingkids.com/. Accessed 2/2007.
Figure 11-21 The NCMEC searches for missing children in the United States.
11-34
Chapter 11
Source: http://www.missingkids.com/cybertip/. Accessed 2/2007.
Figure 11-22 The CyberTipline Web site allows people to report child sexual
exploitation online.
Source: http://www.missingkids.com/. Accessed 2/2007.
Figure 11-23 CVIP is the central point of contact for victim identification.
Anti-Child-Pornography Organizations
11-35
Perverted Justice
Perverted Justice is a California-based nonprofit organization for investigating, identifying, and publicizing users in chat rooms with predatory tendencies toward children. Its methods are controversial, and a number of critics have termed these actions as harassment.
It recruits volunteer contributors who do the following:
• Pose as underage children in chat rooms
• Use a fake online screen name
• Wait for predators to initiate conversations with them
National Society for the Prevention of Cruelty to Children
The National Society for the Prevention of Cruelty to Children (NSPCC) protects children from cruelty, supports vulnerable families, campaigns for changes to the law, and raises awareness about abuse. Its aim is to have a society where all children are loved, valued, and able to fulfill their potential. It runs the Child Protection Helpline and the ChildLine in the U.K. and the Channel Islands.
Most of its work is with children, young people, and their families. It also works to achieve cultural, social, and political change by influencing legislation, policy, practice, public attitudes, and behaviors.
ChildLine is a service provided by NSPCC that is the U.K.’s free, 24-hour help line for children in distress or danger. Trained volunteer counselors comfort, advise, and protect children and young people who may feel they have nowhere else to turn.
NSPCC has set the following four objectives:
1. To mobilize everyone to take action to end child cruelty
2. To give children the help, support, and environment they need to stay safe from cruelty
3. To find ways of working with communities to keep children safe from cruelty
4. To be, and be seen as, someone to turn to for children and young people
Canadian Centre for Child Protection
The Canadian Centre for Child Protection (CCCP) is a charitable organization whose goal is to reduce child victimization by providing programs and services to Canadians. The following describe the mission of the Canadian Centre for Child Protection:
• To reduce the incidence of missing and sexually exploited children
• To educate the public on child personal safety and sexual exploitation
• To assist in finding the location of missing children
• To advocate for and increase awareness about issues relating to child sexual exploitation
The Canadian Centre for Child Protection does the following:
• Delivers programs to increase the personal safety of children and reduce their risk of
sexual exploitation
• Prevents harm to children through education and prevention programs for children, families, schools, and communities
• Receives and addresses reports of child pornography, online luring, child sex tourism, and children exploited through prostitution
• Maintains comprehensive data on the latest trends in child victimization and develops training and programs to address the risks
• Accepts tips from the public and assists in locating missing children
• Advocates on issues relating to child victimization and protection
• Researches better practices on how to keep children safer
• Coordinates national efforts in the area of child protection through collaboration with nonprofit agencies, government, industry, law enforcement, educators, and families
Figure 11-24 shows the CCCP Web site.
11-36
Chapter 11
Source: http://www.protectchildren.ca/app/en/. Accessed 2/2007.
Figure 11-24 The CCCP educates the public about child exploitation on the Internet.
Source: http://www.cybertip.ca/. Accessed 2/2007.
Figure 11-25 Cybertip.ca allows people to report the online sexual exploitation
of children.
Cybertip.ca
Cybertip.ca is Canada’s national tip line for reporting the online sexual exploitation of children. The following is the procedure for reporting about child pornography on Cybertip.ca:
1.
Go
to
http://cybertip.ca.
2.
Click
on
Click here to report (Figure 11-25).
Anti-Child-Pornography Organizations
11-37
3. Write details about the site.
4. Submit the report.
Association of Sites Advocating Child Protection
The Association of Sites Advocating Child Protection (ASACP) is a nonprofit organization dedicated to eliminating child pornography from the Internet. It battles child pornography through its reporting hotline and by organizing the efforts of online organizations to combat the sexual abuse of children. It also works to help parents prevent children from viewing age-inappropriate material online. Figure 11-26 shows the ASACP Web site.
Web Sites Against Child Porn
Web Sites Against Child Porn (WSACP) is an anti-child-pornography organization. Its goal is to stop as many child pornography Web sites as possible and make the Internet a better place for everyone. It provides feedback on all reports submitted with a valid e-mail address. When a user submits a suspect site online, the staff of WSACP will inform the user if the suspect site has been reported to the authorities or not, if they were unable to report the suspect site to the authorities, and any reasons why they were unable to report the site.
Report Child Porn
Report Child Porn is a hotline for Webmasters and surfers to report suspected child pornography. It offers the following:
• A way to report child pornography
• An avenue to discuss problems related to child pornography
Figure 11-27 shows the Report Child Porn Web site.
Child Focus
The European Centre for Missing and Sexually Exploited Children, operating under the name of Child Focus, is a foundation under Belgian law. It acts on an independent basis and only in the interest of children.
Source: http://www.asacp.org/. Accessed 2/2007.
Figure 11-26 ASACP is dedicated to eliminating child pornography from the
Internet.

11-38
Chapter 11
Source: http://www.reportchildporn.com/. Accessed 2/2007.
Figure 11-27 Report Child Porn allows people to report child pornography Web sites.
Source: http://www.childfocus.be/en/index.php. Accessed 2/2007.
Figure 11-28 Child Focus is a Belgian organization that fights child exploitation.
The following are the features of Child Focus:
• It provides active support in the investigation of the disappearance, abduction, or sexual exploitation of children.
• It supports and encourages investigations and legal measures.
• It ensures follow-up to the cases that are entrusted to it and participates in the counseling of victims.
Figure 11-28 shows the Child Focus Web site.
Chapter Summary
11-39
Source: http://www.stopchildporno.be/index.php?language=en. Accessed 2/2007.
Figure 11-29 StopChildPorno.be is a Belgian Web site for reporting child
pornography images.
StopChildPorno.be
StopChildPorno.be is the Belgian civil hotline for reporting child abuse images found on the Internet. It informs citizens about the problem of child pornography on the Internet, Belgian legislation concerning this matter, different possibilities to report, procedures, and addresses of other hotlines abroad.
The following steps explain how to report a Web site:
1.
Go
to
http://www.stopchildporno.be/index.php?language=en. The Web site is shown in Figure 11-29.
2.
Click
on
Report a Site.
3.
Check
either
I want to be anonymous or I want to be informed and click Continue.
4. Indicate which type of report to submit.
5. Copy and paste the URL of the Web site.
6. Submit the report.
Chapter Summary
■ Child pornography is defined as any work that centers on activities involving the sexual behavior of children. Such works include drawings, cartoons, sculptures, paintings, photography, films, videos, images, and pictures, whether made or produced by electronic, mechanical, or other means. It also includes distribution and possession of pornographic materials.
■ Criminals involved in pornographic cases are generally unmarried, separated, divorced, or widowed.
Motives of people can range from mere money making to sexual perversion. Child pornographers at-
tract children by coercion, seduction, payment, blackmail, and solicitation.
11-40
Chapter 11
■ The Internet provides easy access to a number of pornographic materials and reduces the cost of production and distribution of such materials. An offender can easily distribute the materials through e-mails, newsgroups, and webcams.
■ Child pornography affects children physically, socially, and psychologically.
■ ISPs (Internet service providers) play an important role in reducing the problem of child pornography.
They can block illegal sites, apply filters to browsers and search engines, and create complaint sites.
■ The police play a crucial role in investigating pornographic sites. They may use computer forensic tools and techniques to investigate such sites. They may also use honeytrap sites to find offenders.
■ The challenges in controlling child pornography include the large amount of Internet traffic, a lack of rules and regulations in certain countries, and the advanced techniques offenders use.
■ An offender’s computer, handheld devices, and servers are the main sources of evidence for an investigation.
■ There are many anti-child-pornography organizations around the globe that seek to stop the sexual exploitation of children; these organizations offer reporting capabilities, education, training, and other services.
Review Questions
1. What are the motives of people involved in child pornography?
_______________________________________________________________________________________________
_______________________________________________________________________________________________
2. Explain the role of the Internet in promoting child pornography.
_______________________________________________________________________________________________
_______________________________________________________________________________________________
3. What are the effects of child pornography on children?
_______________________________________________________________________________________________
_______________________________________________________________________________________________
4. How can the dissemination of child pornography be prevented?
_______________________________________________________________________________________________
_______________________________________________________________________________________________
5. What are the challenges involved in controlling child pornography?
_______________________________________________________________________________________________
_______________________________________________________________________________________________
6. List the guidelines for investigating child pornography cases.
_______________________________________________________________________________________________
_______________________________________________________________________________________________
7. List the sources of digital evidence during an investigation.
_______________________________________________________________________________________________
_______________________________________________________________________________________________
8. List the guidelines for parents to reduce the risk of their children becoming exposed to child pornography.
_______________________________________________________________________________________________
_______________________________________________________________________________________________

Hands-On Projects
11-41
9. Describe four tools that parents can use to protect their children from accessing pornography.
_________________________________________________________________________________________________
_________________________________________________________________________________________________
10. Describe the various anti-child-pornography organizations.
_________________________________________________________________________________________________
_________________________________________________________________________________________________
Hands-On Projects
1. Perform the following steps:
■ Go to the National Child Exploitation Coordination Centre (NCECC) Web site at http://
www.ncecc.ca.
■ Click on the Reporting child exploitation link.
■ Read “How to Report Internet Pornography or Internet Luring Related to Children.”
2. Perform the following steps:
■ Go to the Project Safe Childhood (PSC) Web site at http://www.projectsafechildhood.gov.
■ Click
on
PSC Media Fact Sheet and read about Project Safe Childhood’s initiatives.
3. Perform the following steps:
■ Navigate to Chapter 11 of the Student Resource Center.
■ Install and launch iProtectYou.
■ Explore the various options.
This page intentionally left blank

Index
18 U.S.C. § 2252A/B, 7-27
BillSniff, 2-27, 2-28
investigation steps, 11-4–11-11
A
BrowseControl, 11-15
investigation tools for, 11-12–11-16
Buffer overflow attacks, 3-6–3-7, 5-4
Japanese laws against, 11-24
Abuse.Net, 7-5
legislation survey, 11-17–11-22,
Acceptable level of loss, 8-5
C
11-17–11-22
AccessDiver, 3-26, 3-27
Cache, 11-8
Michigan laws against, 11-23
ActiveWhois, 3-44, 3-45
Cache poisoning, 2-8–2-9
people involved in, 11-2
Activeworx Security Center, 1-17, 1-18
CallerIP, 3-47
people’s motives behind, 11-2
Activity Monitor, 8-8–8-9
Canadian Centre for Child Protection
Philippine laws against, 11-26
(CCCP), 11-35, 11-36
Activity profiling, 5-8
precaution before investigating, 11-4
Canadian laws, for trademarks and
Acunetix Web Vulnerability Scanner,
copyright, 9-38
preventing dissemination of, 11-3–11-4
3-24–3-25
CAN-SPAM Act, 7-26
reducing risk for exposure to, 11-12
Adaptive Security Analyzer (ASA) Pro,
1-14–1-15, 1-16
CenterTrack method, 5-14
Scottish laws against, 11-25
Admin’s Server Monitor, 5-17, 5-18
Centralized binary logging, 1-7–1-8
sources of digital evidence, 11-11
AlterWind Log Analyzer, 3-22
CentralOps.net, 6-12–6-13
South African laws against, 11-24–11-25
Analog (tool), 3-16, 3-18
CERT Coordination Center/SEI Study
U.K. laws against, 11-25
on insider threats, 8-7
AnalogX PacketMon, 2-26, 2-28
U.S. laws against, 11-22–11-23
Chain of custody, 1-7, 4-6
Anti-Child Porn Organization (ACPO),
Children’s Internet Protection
11-28–11-29
ChatGuard, 11-15, 11-16
Act (CIPA), 11-26
AOL, viewing and copying e-mail
Chat rooms, 7-7
Child Victim Identification Program (CVIP),
headers in, 7-10
11-33, 11-34
CHECK, 9-14
Apache logs, investigating, 3-12–3-13
Child Exploitation and Online Protection
Chinese laws
Application layer, of main protocols, 2-4–2-5
(CEOP), 11-29
on sexual harassment, 10-12
AppScan, 3-26, 3-27
Child Exploitation Tracking
for trademarks and copyright, 9-38
System (CETS), 11-17
ARP table, evidence gathering from, 2-9
Cisco NetFlow, for DoS attack detection, 5-9
Child Focus, 11-37–11-38
Association of Sites Advocating Child
Civil Rights Act (1964), Title VII, 10-10
Protection (ASACP), 11-37
Child pornography
Civil Rights Act (1991), 10-10
Atelier Web Ports Traffic Analyzer, 2-30, 2-31
anti-child-pornography organizations,
11-26–11-39
Code injection attacks, 3-5
Attacks, types of, 2-6
Australian laws against, 11-23
Colasoft Capsa Network Analyzer, 2-24, 2-26
Audit logs, 1-8
Austrian laws against, 11-23
Colasoft EtherLook, 2-26, 2-27
Australian laws
Belgian laws against, 11-23–11-24
Common headers, 7-13–7-15
against child pornography, 11-23
Children’s Internet Protection
Common law torts, 10-11
on sexual harassment, 10-11–10-12
Act (CIPA), 11-26
CommView, 2-14–2-15
for trademarks and copyright, 9-35–9-37
citizen responsibility in fighting, 11-11
Computer times, synchronizing, 1-21–1-28
Austrian laws, against child pornography, 11-23
control challenges of, 11-4
Control channel detection, 5-14–5-15
Authentication hijacking, 3-7, 3-8
Cypriot laws against, 11-24
Cookie poisoning, 3-5–3-6
AWStats, 3-19, 3-20
defined, 11-2
Cookies, 11-8, 11-9
B
effects of, on children, 11-3
Cookie snooping, 3-7
Backscatter traceback, 5-11–5-13
English and Welsh laws against, 11-25
Cookie Viewer, 6-15, 6-17
Belgian laws
guidelines to avoiding, 11-11–11-12
CopyCatch, 9-12, 9-13
against child pornography, 11-23–11-24
Internet role in, 11-3
Copy Protection System (COPS),
for trademarks and copyright, 9-39
introduction, 11-2
9-12–9-13, 9-14
I-1
I-2
Index
Copyright Act (1968), 9-36–9-37
D
E
Copyright Management Business Law
Data link layer
(4.2.2.3) (2000), 9-35
evidence gathering from, 2-10
specialized forensic tools for, 7-17–7-26
Copyrights
of main protocols, 2-4
tracing, 7-22–7-24
Australian laws for, 9-35–9-37
of OSI model, 2-5
E-mail addresses, tracing, 6-22–6-25
Belgian laws for, 9-39
Data Recovery Wizard, 11-5, 11-6
E-mail crime
Canadian laws for, 9-38
DDoS attacks, 5-5–5-7
investigating, 7-8–7-17, 7-18, 7-19
Chinese laws for, 9-38
Deep Log Analyzer, 3-18–3-19
overview, 7-4–7-7
enforcement of, 9-10–9-11
Denial-of-service (DoS) attacks, 4-4
RCW 19.190.020, 7-27
Indian laws for, 9-33–9-34
DDoS attacks, 5-5–5-7
types of, 7-4–7-7
introduction, 9-1–9-2
defined, 5-2
U.S. laws against (CAN-SPAM Act),
Japanese laws for, 9-34–9-35
7-26–7-27
detection techniques, 5-8–5-9
length of, 9-9–9-10
E-Mail Detective, 7-20
indications of, 5-2
plagiarism, 9-11–9-23
Email Dossier, 7-16
introduction, 5-2
South African laws for, 9-38
E-Mail Examiner by Paraben, 7-21, 7-22
investigating, 5-9–5-15
South Korean laws for, 9-39
E-mail headers
investigation challenges, 5-16
status investigation, 9-9
common, 7-13–7-15
investigation tools for, 5-16–5-20
U.K. laws for, 9-37–9-38
examining, 7-11–7-15
modes of, 5-7–5-8
U.S. laws for, 9-30–9-33
“received”, 7-13
types of, 5-2–5-4
Corporate espionage
viewing and copying in AOL, 7-10
DHCP database, evidence gathering
defenses against, 8-4–8-5
from, 2-10
viewing and copying in Gmail, 7-10–7-11
defined, 8-1–8-2
Digital evidence, 11-11
viewing and copying in Hotmail, 7-10
information sought by spies, 8-2–8-3
Digital Millennium Copyright Act (DMCA)
viewing and copying in Microsoft
insider/outsider threat, 8-3
(1998), 9-30–9-31
Outlook, 7-9
introduction, 8-1–8-2
Digital rights management (DRM),
viewing and copying in Yahoo! Mail,
9-26–9-29
7-11, 7-12
motives behind, 8-2
Directory reversals, 3-9
E-mails
prevention steps, 8-5–8-7
Diskinternals Outlook Recovery,
chain messages, 7-8
spying techniques, 8-3–8-4
7-22, 7-23
copying messages, 7-9
threat due to aggregate of
Distinct Network Monitor, 2-23
information, 8-3
examining messages, 7-9
Distributed denial-of-service (DDoS) attacks,
CounterSpy, 8-16, 8-17
5-5–5-7
investigating crimes and violations,
7-8–7-17, 7-18, 7-19
CounterStorm-1, 3-49
DMZ protocol attacks, 3-7
obtaining bit-by-bit image
CountryWhois, 3-46
DNS (Domain Name Service)
information, 7-9
CPU utilization, for DoS attack
poisoning techniques, 2-7–2-9
online programs, 7-15
detection, 5-9
Web page defacement using, 3-14
personal address book, 7-15
Critical assets, 8-5
DNS root name servers, 6-7
printing messages, 7-9
Cross-site request forgery (CSRF), 3-3–3-4
Documentation, of evidence gathered on
spoofing, 7-8
Cross-site scripting (XSS) attacks, 3-2–3-3
network, 2-45–2-46
systems, 7-2–7-4
Cryptographic interceptions, 3-9
Domain name infringement, 9-25
tracking and investigating crimes, 7-2
Cyberbullying, 10-2
Domain Name System (DNS), Internet crimes
and, 6-6–6-8
viewing and copying e-mail headers in
Cyberstalking, 10-6
AOL, 7-10
DoSHTTP, 5-20
Cybertip.ca, 11-36–11-37
eMailTrackerPro, 7-24, 7-25
dotDefender, 3-25, 3-26
CyperTipline, 11-33, 11-34
Employee-monitoring policies, writing
Dupli Checker, 9-21, 9-22
guidelines, 8-19–8-20
Cypriot laws, against child pornography,
11-24
Dynamic IP addresses, investigating, 3-16
Employee responsibilities, 10-7
Index
I-3
Emsa Web Monitor, 3-28
G
Industry self-regulation (ISP), 11-3
End-to-end forensic investigation, 1-3
General Packet Radio Service (GPRS),
InfiniStream, 2-38–2-39, 2-40
English laws, against child pornography, 11-25
2-35–2-36
Innocent Images National Initiative (IINI),
11-27–11-28
Enterprise IP-Address Manager, 3-42, 3-43
German laws, on sexual harassment, 10-12
Insider threats, 8-3, 8-7
Ephemeral, 6-4
GFI EventsManager, 1-15–1-17
Intellectual property, 9-25–9-26, 9-39
Equal Protection Clause of 14th
Give Me Too, 2-33, 2-34
Amendment, 10-11
Glatt, 9-21
IntelliProtector, 9-28, 9-29
EtherApe, 2-24, 2-25
Gmail, viewing and copying e-mail headers
Intermediate System to Intermediate System
(IS-IS), 4-4
EtherDetect Packet Sniffer, 2-18–2-19
in, 7-10–7-11
International Centre for Missing & Exploited
Ethernets
GPRS Network Sniffer- Nokia LIG, 2-35–2-36
Children (ICMEC), 11-31–11-33
shared, 2-6–2-7
Grab-a-Site, 6-18–6-19
Internet, role in child pornography, 11-3
switched, 2-7
Grooming, 6-3
Internet Assigned Numbers Authority
EtherScan Analyzer, 2-29
H
(IANA), 6-6
EtherSnoop, 2-35
Internet crimes
Haihaisoft Media DRM Platform, 9-28
eTrust Network Forensics, 2-39–2-41
Internet forensics, 6-4
Hash-based IP tracebacks, 5-13
EVE2 (Essay Verification Engine), 9-19, 9-21
introduction, 6-2
Hide Real IP, 3-40, 3-41
investigation goals, 6-4
EventLog Analyzer, 1-20–1-21
Hit-and-run attacks, 4-5
investigation steps, 6-4–6-8
EventReporter, 1-20
Honeypots, 8-5–8-6
investigation tools for, 6-8–6-27
Evidence
Honeytokens, 8-5–8-6
types of, 6-2–6-3
log files as, 1-3–1-8
Hong Kong laws, for intellectual
property, 9-39
Internet Crimes Against Children Task Force
looking for, 1-3
(ICAC), 11-28
Hop-by-Hop IP traceback, 5-10–5-11
multiple logs as, 1-5
Internet DNS spoofing (remote network), 2-8
Hostlie work environment harassment,
at physical layer, 2-6–2-7
10-3–10-4
Internet Service provider (ISP), 6-6
eWebLog Analyzer, 3-23, 3-24
Hotmail, viewing and copying e-mail headers
Internet Spy Filter, 8-12, 8-13
Exchange Message Tracking Center,
in, 7-10
Internet Watch Foundation, 11-31
7-16, 7-17
HP WebInspect, 3-30
Internetwork addressing, 2-2–2-3
Exploit-Me, 3-34
HTTP Sniffer, 2-16, 2-18
Intranet DNS spoofing (local network), 2-8
F
I
Intrusion detection, 1-5, 3-15
Fair Use Doctrine, 9-31–9-32
ICMP traceback, 5-10
Intrusion detection system (IDS), evidence
Falcove Web Vulnerability Scanner, 3-28
gathering from, 2-10
Identity theft, 7-8
Intrusion process, 1-2
FINALeMAIL, 7-20
ID Protect, 7-26
IP2country, 3-46
Financial Coalition Against Child
IDS (intrusion detection system), evidence
Pornography (FCACP), 11-33
gathering from, 2-10
IP addresses
Firefox, 6-15, 6-16, 6-18, 6-22
IDS Policy Manager, 2-45, 2-46
examining the origin of, 7-16
Firewall Analyzer, 1-13–1-14, 1-15
IE HTTP Analyzer, 2-29
Internet crimes and, 6-5–6-6
Forensic Linguistics Institute, 9-22–9-23
IISLogger, 1-8, 1-9
investigating, 3-16
Forensics, vs. router forensics, 4-5
IIS logs, 1-5–1-6
locating, 5-15
Forensic Toolkit (FTK), 7-19–7-20
investigating, 3-12
IP Address Locator, 6-12, 6-13
Fourteenth Amendment, 10-11
IMAP (Internet Message Access Protocol), 7-4
IP.com, 9-24–9-25
Fraggle attacks, 5-3–5-4
iMonitorPC, 8-17, 8-19
IP Detective Suite, 3-40, 3-41
Friendly Pinger, 5-16–5-17
Impersonation attacks, 3-10
IPgrab, 2-32
FTP compromises, 3-11
Indian laws
IPHost Network Monitor, 5-17, 5-18
FTP logs, investigating, 3-11–3-12
on sexual harassment, 10-12
iProtectYou, 11-12–11-13
FTP servers, investigating, 3-12
for trademarks and copyright, 9-33–9-34
IPSec, 5-13
I-4
Index
IP Sniffer, 2-30, 2-31
Mail user agent (MUA), 7-2
Network Probe, 2-43
Iris Network Traffic Analyzer,
Malaysian penal code, on sexual
Network protocols, overview, 2-3–2-5
2-19–2-20, 2-21
harassment, 10-12
Network Time Protocol (NTP),
IS-IS (Intermediate System to Intermediate
Mapper, 3-32
1-21–1-27
System), 4-4
McAfee Visual Trace, 3-37, 3-38
Network traffic
iThenticate, 9-20, 9-21
Media Access Control (MAC) address, 2-2
data link layer of OSI model, 2-5
J
Michigan laws, against child
DNS poisoning techniques, 2-7–2-9
pornography, 11-23
Japanese laws
documenting evidence, 2-45–2-46
Microsoft Log Parser, 1-12–1-13, 1-14
against child pornography, 11-24
evidence gathering at data link layer-
Microsoft Outlook, 7-15
DHCP database, 2-10
for trademarks and copyright, 9-34–9-35
viewing and copying e-mail headers in, 7-9
evidence gathering at physical layer,
JavaScript, 6-17–6-18
2-6–2-7
Moles, detecting, 8-6
JPlag, 9-15
evidence gathering from ARP table, 2-9
Monitoring, 8-6
K
evidence gathering from IDS, 2-10
Multiple logs, 1-5
keepNI, 3-31–3-32
introduction, 2-2
My Offline Browser, 6-19–6-20
Kiwi Syslog Daemon, 1-12, 1-13
investigation tools for, 2-10–2-45
N
L
network addressing, 2-2–2-3
Nagios, 2-33
network layer of OSI model, 2-5–2-6
LAN addressing, 2-2
National Center for Missing & Exploited
OSI reference model, 2-3
LAND attacks, 5-3
Children (NCMEC), 11-33
physical layer of OSI model, 2-5
Lanham (Trademark) Act, 9-31–9-32
National Society for the Prevention of Cruelty
to Children (NSPCC), 11-35
protocols overview, 2-3–2-5
LanWhoIs, 3-45
NeoTrace (McAfee Visual Trace), 6-25, 6-26
reasons for investigating, 2-6
Link Logger, 4-17–4-18
NETGEAR router logs, 4-13–4-14, 4-15
reconstructing evidence for investigation,
Linux, process accounting, 1-18–1-19
2-46–2-47
NetIntercept, 2-12, 2-13
Local area network (LAN), 2-2
transport layer of OSI model, 2-6
NetResident, 2-38
LOCIS, 9-9, 9-10
types of attacks, 2-6
NetScan Tools, 6-26, 6-27
LockLizard, 9-28, 9-29
NIC (network interface card), 2-2
NetSetMan, 2-21–2-22
Log files
NIDS (Network Intrusion Detection System),
Netspionage, 8-7
authenticity of, 1-7
for DoS attack detection, 5-9
NetVizor, 8-11
as evidence, 1-3–1-8
Nmap, 5-16
NetWitness, 2-37
missing, 1-7
Nokia LIG, 2-35–2-36
Network Abuse Clearinghouse, 7-5
multiple, 1-5
Nslookup, 3-34, 3-36, 6-8–6-9
Network E-Mail Examiner by Paraben, 7-22
tampering with, 3-8
N-Stalker, 3-33
Network forensics
Log-input, tracing with, 5-14
N-Stealth, 3-23, 3-24
data analysis, 1-2
Logs, investigating
ntop, 2-24, 2-25
end-to-end, 1-3
introduction, 1-2
NTP (Network Time Protocol), 1-21–1-27
introduction, 1-2
log files as evidence, 1-3–1-8
NTsyslog, 1-19–1-20
intrusion process, 1-2–1-3
tools for, 1-8–1-21
Nuke attacks, 5-4
looking for evidence, 1-3
LoPe, 7-24, 7-25
NTP, 1-21–1-28
O
M
Network Intrusion Detection System (NIDS),
ODBC logging, 1-8
MaaTec Network Analyzer, 2-23, 2-24
for DoS attack detection, 5-9
OmniPeek, 2-19
MAC (Media Access Control) address, 2-2
Network interface card (NIC), 2-2
Online Copyright Infringement Liability
Mail bombing, 7-6–7-7
Network layer
Limitation Act, 9-32–9-33
MailDetective, 7-16–7-17, 7-18
of main protocols, 2-4
OOB attacks, 5-4
Mail storm, 7-7
of OSI model, 2-5–2-6
Open Shortest Path First (OSPF), 4-4
Index
I-5
OSI reference model
Project Safe Childhood (PSC), 11-27
Sexual harassment
overview, 2-3
Promiscuous attacks, 2-7
Australian laws on, 10-11–10-12
routers on, 4-2
Protocols, overview, 2-3–2-5
Chinese laws on, 10-12
OSPF (Open Shortest Path First), 4-4
Proxy servers, DNS poisoning on, 2-8, 2-9
complaint procedures, 10-7–10-8
Outsider threats, 8-3
Q
consequences of, 10-4
P
defined, 10-2
Quid pro quo harassment, 10-3
dos and don’ts for employees, 10-5
P2 Enterprise Shuttle, 2-41
R
employee responsibilities, 10-7
Packet marking, 5-14
“Received” headers, 7-13
German laws on, 10-12
Packet-mistreating attacks, 4-5
Recover My Email for Microsoft
Indian laws on, 10-12
Pandora FMS, 3-49
Outlook, 7-22
Paper mills, 9-11
introduction, 10-2
Reflected attacks, 5-4
Parameter tampering, 3-5
investigation process, 10-8–10-9
Reliance party, 9-10
Paros, 3-29–3-30
Malaysian penal code on, 10-12
Remote logging, 1-9–1-10
Patents, 9-23–9-25
policies, 10-9
Report Child Porn, 11-37, 11-38
infringement, 9-24
preventive steps, 10-9–10-10
Reveal, 11-12
introduction, 9-23
stalking, 10-5–10-6
R-Mail, 7-20, 7-21
search for, 9-24
stalking laws, 10-15
Router Audit Tool (RAT), 4-16–4-17
types of, 9-23–9-24
statistics, 10-4
Router forensics
Patents (Amendment) Act (1999), 9-33
supervisors responsibilities, 10-7
definition of router, 4-2
Path identification (Pi) method, 5-15
types of, 10-2–10-4
functions of a router, 4-2–4-4
PC Inspector File Recovery, 11-5, 11-6
U.K. laws on, 10-12
introduction, 4-2
Persistent attacks, 4-5
U.S. laws on, 10-10–10-11
investigating router attacks, 4-6–4-16
Perverted Justice, 11-35
Sherlock, 9-17, 9-19
router attacks, 4-4–4-5
Philippine laws, against child
Show Traffic, 2-42
router vulnerabilities, 4-4
pornography, 11-26
Siemens Monitoring Center, 2-36–2-37
tools for, 4-16–4-18
Phishing, 7-8, 7-17, 7-18
Signature analysis, 8-6–8-7
vs. traditional forensics, 4-5
Physical layer, of OSI model, 2-5
Simple Mail Transfer Protocol (SMTP), 7-3
Ping of death attacks, 5-2
Router logs, 4-12–4-13
SIM (Software Similarity Tester), 9-16, 9-17
Plagiarism
Routing Information Protocol (RIP),
4-3–4-4
SmartSniff, 2-21, 2-22
detection factors, 9-11–9-12
Routing table, 4-3–4-4
SmartWhois, 3-44
detection tools, 9-12–9-23
Routing table poisoning, 4-5
SMTP (Simple Mail Transfer Protocol), 7-3
prevention steps, 9-11
Smurf attacks, 5-3
types of, 9-11
S
Sniff-O-Matic, 2-33, 2-34
PlagiarismDetect.com, 9-21, 9-22
SafeAssignment, 9-19, 9-20
Sniphere, 2-29–2-30
PLAGUE, 9-16–9-17
Sample complaint form, 10-12–10-14
Snork attacks, 5-4
POP3 (Post Office Protocol version 3), 7-3–7-4
Samspade, 6-12
Snort Intrusion Detection System, 2-43–2-44
Post Office Protocol version 3 (POP3), 7-3–7-4
Sawmill, 4-18
Socklog, 1-10–1-11
PRAISE, 9-19, 9-20
Scottish laws, against child pornography, 11-25
SoftPerfect Network Protocol Analyzer,
Presentation layer, of main protocols, 2-4–2-5
Scrawlr, 3-34
2-15–2-16, 2-17
Privatefirewall, 8-11–8-12
Search warrants, 6-4–6-5, 7-8–7-9
South African laws
Probabilistic packet monitoring (PPM), 5-14
Security, for Web applications, 3-15
against child pornography, 11-24–11-25
Process accounting, 1-18–1-19
Sequential change-point detection, 5-8
for trademarks and copyright, 9-38
ProDiscover Investigator, 2-41, 2-42
Server Log Analysis (tool), 3-20
South Korean laws, for trademarks and
Profiling, 8-6
Session layer, of main protocols, 2-4–2-5
copyright, 9-39
I-6
Index
Spam Arrest, 7-6, 7-7
South African laws for, 9-38
Web attacks
Spamming, 7-5–7-6
South Korean laws for, 9-39
indications of, 3-2
SPAM Punisher, 7-5–7-6
trade dress and, 9-2
introduction, 3-1
Spector CNE, 8-9
U.K. laws for, 9-37–9-38
intrusion detection, 3-15
SPlaT, 9-17, 9-18
U.S. laws for, 9-30–9-33
investigating, 3-11–3-13
Spybot-Search & Destroy, 8-12, 8-13
Trade Marks Act (1995), 9-35–9-36
investigating static and dynamic IP
addresses, 3-16
SpyBuddy, 8-10–8-11
Trade Marks Act (1999), 9-33–9-34
investigation tools for, 3-16–3-34, 3-47–3-49
SpyCop, 8-12–8-13, 8-14
Trademarks Act (TMA) (1994), 9-37–9-38
overview of web logs, 3-10–3-11
Spy Sweeper, 8-14, 8-16
Transport layer
security strategies for Web applications, 3-15
Spyware Terminator, 8-14, 8-15
of main protocols, 2-4
SQL injection attacks, 3-4–3-5
statistics, 3-16
of OSI model, 2-6
SQL Inject-Me, 3-34, 3-35
tools for locating IP addresses, 3-34–3-47
Turnitin, 9-12, 9-13
Stalking, 10-5–10-6, 10-15
types of, 3-2–3-10
U
Stanford Copy Analysis Mechanism (SCAM),
web page defacement, 3-13–3-15
9-14, 9-15
Uniform Resource Locator (URL), 3-5
Web security checklist, 3-16
Static IP addresses, investigating, 3-16
United Kingdom laws
Web Control for Parents, 11-13, 11-14
Status2k, 5-19
against child pornography, 11-25
WebLog Expert, 3-20–3-21
StopChildPorno.be, 11-39
on sexual harassment, 10-12
Web logs, 3-10–3-11
Stratum levels, 1-22–1-27
for trademarks and copyright, 9-37–9-38
Web page defacement, 3-13–3-15
SUPERAntiSpyware, 8-17, 8-18
United States laws
Web pages, recovering information from, 6-22
Supervisors responsibilities, 10-7
against child pornography, 11-22–11-23
Web Sites Against Child Porn (WSACP), 11-37
SurfOffline, 6-19, 6-20
for trademarks and copyright, 9-30–9-33
WebWatchBot, 3-29
SYN flooding, 5-3
United States Patent and Trademark Office
Welsh laws, against child pornography, 11-25
(USPTO), 9-2
Syslog, 1-8–1-9
WHOIS, 3-38–3-40, 6-9–6-12
Urkund, 9-19
Syslog-ng, 1-10, 1-11
Whois Lookup, 3-42, 3-43
URL interpretation attacks, 3-9
T
Whois.Net, 3-47, 3-48
URL redirection, 6-15, 6-17
Tail4Win, 5-18, 5-19
Wikto, 3-32
URL (Uniform Resource Locator), 3-5
Tcpdump, 2-10, 2-11
Windows-based servers, investigating attacks
U.S. Copyright Office, 9-10
in, 3-13
Teardrop attacks, 5-3
U.S. Secret Service, 8-7
Windows logging, 1-19
Think U Know, 11-29–11-30
UTC time, 1-6
Windows Media Digital Rights Management
Three-way handshake, 5-3
UV Uptime Website Defacement
(DRM), 9-26, 9-27
Title VII of Civil Rights Act (1964), 10-10
Detector, 3-49
Windows time service, 1-27–1-28
Traceroute, 3-36–3-37, 6-13–6-14
V
WinDump, 2-11–2-12
Track4Win, 8-9, 8-10
Wireshark, 2-13–2-14
VAST, 9-15–9-16
Trademarks
Www.whatismyip.com, 3-40, 3-41
Victim, interviewing, 6-5
Australian laws for, 9-35–9-37
Virtual Global Taskforce (VGT), 11-30
X
Belgian laws for, 9-39
VisualRoute, 6-22, 6-23
XoftSpySE, 8-14, 8-15
Canadian laws for, 9-38
Volatile evidence, 4-9–4-11
XSS-Me, 3-34, 3-35
Chinese laws for, 9-38
Indian laws for, 9-33–9-34
W
Y
infringement, 9-3–9-9
Wavelet-based signal analysis, 5-9
Yahoo! Mail, viewing and copying e-mail
headers in, 7-11, 7-12
introduction, 9-1
Wayback Machine, 6-21
Japanese laws for, 9-34–9-35
WCopyfind, 9-20
Z
registration eligibility and benefits, 9-2
WebAgain, 3-47, 3-48
Zero-day attacks, 3-7
vs. service mark, 9-2
Webalizer, 3-22, 3-23
Zombies, 5-5
This page intentionally left blank
General Notice
The EC-Council | Press Series’ mission is to educate, introduce and demonstrate Information Security related tools and techniques for internal security analysis purposes only. You will not use the newly acquired skills for illegal or malicious attacks and you will not use such tools in an attempt to compromise any computer system, and you shall indemnify EC-Council and its partners from all liability with respect to the use or misuse of these tools, regardless of intent.
EC-Council provides the hacking skills and tools presented throughout the EC-Council | Press for educational use. The hacking tools are not authored by EC-Council, and in many cases are submitted by the security community. EC-Council will not be held accountable for any damages caused by the proper or improper usage of these materials, and makes no guarantee in regards to their operation or suitability for any specific purpose.
The hacking tools used in the EC-Council | Press programs are meant for research and educational purposes only. The primary intent of these tools is to provide the user with hard to find content for research or self education relevant to network security and various protection methods and their intrinsic flaws by demonstrating exploitation methods and techniques used to circumvent them. We hope that you become more aware of the dangers that lurk in society today and learn how to protect yourself from them with the knowledge you are about to learn. In order to continue you must accept that you are going to use this information only for educational and research purposes only.
While possession of information or programs included in this training violates no laws, actually using or implementing some of the programs or content may violate U.S. Federal and other laws. For this reason, the user is instructed not to use any programs or content contained in this training which may violate any laws or infringe on the rights, including intellectual property rights, of others. We provide them for research and educational purposes only.
· Front Cover
· Title Page
· Copyright
· Brief Table of Contents
· Table of Contents
· Preface
· CHAPTER 1: Network Forensics and Investigating Logs
o Objectives
o Key Terms
o Case Example
o Introduction to Network Forensics and Investigating Logs
o Network Forensics
§ Analyzing Network Data
§ The Intrusion Process
§ Looking for Evidence
§ End-To-End Forensic Investigation
o Log Files as Evidence
§ Legality of Using Logs
§ Examining Intrusion and Security Events
§ Using Multiple Logs as Evidence
§ Maintaining Credible IIS Log Files
§ Importance of Audit Logs
§ Syslog
§ Tool: Syslog-ng
§ Tool: Socklog
§ Tool: Kiwi Syslog Daemon
§ Tool: Microsoft Log Parser
§ Tool: Firewall Analyzer
§ Tool: Adaptive Security Analyzer (ASA) Pro
§ Tool: GFI EventsManager
§ Tool: Activeworx Security Center
§ Linux Process Accounting
§ Configuring Windows Logging
§ Tool: NTsyslog
§ Tool: EventReporter
§ Tool: EventLog Analyzer
o Why Synchronize Computer Times?
§ What Is NTP?
§ Configuring the Windows Time Service
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 2: Investigating Network Traffic
o Objectives
o Key Terms
o Case Example
o Introduction to Investigating Network Traffic
o Network Addressing Schemes
§ LAN Addressing
§ Internetwork Addressing
o OSI Reference Model
o Overview of Network Protocols
§ Data Link Layer
§ Network Layer
§ Transport Layer
§ Session Layer, Presentation Layer, and Application Layer
o Overview of Physical and Data Link Layers of the OSI Model
§ The Physical Layer
§ The Data Link Layer
o Overview of Network and Transport Layers of the OSI Model
§ The Network Layer
§ The Transport Layer
o Types of Network Attacks
o Why Investigate Network Traffic?
o Evidence Gathering at the Physical Layer
§ Shared Ethernet
§ Switched Ethernet
o DNS Poisoning Techniques
§ Intranet DNS Spoofing (Local Network).
§ Internet DNS Spoofing (Remote Network)
§ Proxy Server DNS Poisoning
§ DNS Cache Poisoning
o Evidence Gathering from ARP Table
o Evidence Gathering at the Data Link Layer: DHCP Database
o Gathering Evidence from an IDS
o Tool: Tcpdump
o Tool: WinDump
o Tool: NetIntercept
o Tool: Wireshark
o Tool: CommView
o Tool: SoftPerfect Network Protocol Analyzer
o Tool: HTTP Sniffer
o Tool: EtherDetect Packet Sniffer
o Tool: OmniPeek
o Tool: Iris Network Traffic Analyzer
o Tool: SmartSniff
o Tool: NetSetMan
o Tool: Distinct Network Monitor
o Tool: MaaTec Network Analyzer
o Tool: ntop
o Tool: EtherApe
o Tool: Colasoft Capsa Network Analyzer
o Tool: Colasoft EtherLook
o Tool: AnalogX PacketMon
o Tool: BillSniff
o Tool: IE HTTP Analyzer
o Tool: EtherScan Analyzer
o Tool: Sniphere
o Tool: IP Sniffer
o Tool: Atelier Web Ports Traffic Analyzer
o Tool: IPgrab
o Tool: Nagios
o Tool: Give Me Too
o Tool: Sniff-O-Matic
o Tool: EtherSnoop
o Tool: GPRS Network Sniffer: Nokia LIG
o Tool: Siemens Monitoring Center
o Tool: NetWitness
o Tool: NetResident
o Tool: InfiniStream
o Tool: eTrust Network Forensics
o Tool: ProDiscover Investigator
o Tool: P2 Enterprise Shuttle
o Tool: Show Traffic
o Tool: Network Probe
o Tool: Snort Intrusion Detection System
§ Snort Rules
o Tool: IDS Policy Manager
o Documenting the Evidence Gathered on a Network
o Evidence Reconstruction for Investigation
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 3: Investigating Web Attacks
o Objectives
o Key Terms
o Introduction to Investigating Web Attacks
o Indications of a Web Attack
o Types of Web Attacks
§ Cross-Site Scripting (XSS)
§ Cross-Site Request Forgery (CSRF)
§ SQL Injection Attacks
§ Code Injection Attack
§ Parameter Tampering
§ Cookie Poisoning
§ Buffer Overflow
§ Cookie Snooping
§ DMZ Protocol Attack
§ Zero-Day Attack
§ Authentication Hijacking
§ Log Tampering
§ Directory Traversal
§ Cryptographic Interception
§ URL Interpretation Attack
§ Impersonation Attack
o Overview of Web Logs
§ Log Security
§ Log File Information
o Investigating a Web Attack
§ Example of FTP Compromise
§ Investigating FTP Logs
o Investigating FTP Servers
o Investigating IIS Logs
o Investigating Apache Logs
o Investigating Web Attacks in Windows-Based Servers
o Web Page Defacement
§ Defacement Using DNS Compromise
o Intrusion Detection
o Security Strategies for Web Applications
o Investigating Static and Dynamic IP Addresses
o Checklist for Web Security
o Statistics
o Tools for Web Attack Investigations
§ Analog
§ Deep Log Analyzer
§ AWStats
§ Server Log Analysis
§ WebLog Expert
§ AlterWind Log Analyzer
§ Webalizer
§ eWebLog Analyzer
§ N-Stealth
§ Acunetix Web Vulnerability Scanner
§ dotDefender
§ AppScan
§ AccessDiver
§ Falcove Web Vulnerability Scanner
§ Emsa Web Monitor
§ WebWatchBot
§ Paros
§ HP WebInspect
§ keepNI
§ Wikto
§ Mapper
§ N-Stalker Web Application Security Scanner
§ Scrawlr
§ Exploit-Me
o Tools for Locating IP Addresses
§ Nslookup
§ Traceroute
§ McAfee Visual Trace
§ WHOIS
§ Hide Real IP
§ www.whatismyip.com
§ IP Detective Suite
§ Enterprise IP-Address Manager
§ Whois Lookup
§ SmartWhois
§ ActiveWhois
§ LanWhoIs
§ CountryWhois
§ IP2country
§ CallerIP
§ Whois.Net
o Other Tools
§ WebAgain
§ Pandora FMS
§ UV Uptime Website Defacement Detector
§ CounterStorm-1
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 4: Router Forensics
o Objectives
o Key Terms
o Introduction to Router Forensics
o Functions of a Router
§ A Router in the OSI Model
§ Router Architecture
§ The Routing Table and Its Components
o Router Vulnerabilities
o Router Attacks
§ Types of Router Attacks
o Router Forensics Versus Traditional Forensics
o Investigating Router Attacks
§ Investigation Steps
o Tools
§ Router Audit Tool (RAT)
§ Link Logger
§ Sawmill
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 5: Investigating DoS Attacks
o Objectives
o Key Terms
o Introduction to Investigating DoS Attacks
o Indications of a DoS/DDoS Attack
o Types of DoS Attacks
§ Ping of Death Attack
§ Teardrop Attack
§ SYN Flooding Attack
§ LAND Attack
§ Smurf Attack
§ Fraggle Attack
§ Snork Attack
§ OOB Attack
§ Buffer Overflow Attack
§ Nuke Attack
§ Reflected Attack
o DDoS Attack
§ Working of a DDoS Attack
§ Classification of a DDoS Attack
o DoS Attack Modes
§ Network Connectivity
§ Misuse of Internal Resources
§ Bandwidth Consumption
§ Consumption of Other Resources
§ Destruction or Alteration of Configuration Information
o Techniques to Detect DoS Attacks
§ Activity Profiling
§ Sequential Change-Point Detection
§ Wavelet-Based Signal Analysis
§ Monitoring CPU Utilization to Detect DoS Attacks
§ Detecting DoS Attacks Using Cisco NetFlow
§ Detecting DoS Attacks Using a Network Intrusion Detection System (NIDS)
o Investigating DoS Attacks
§ ICMP Traceback
§ Hop-by-Hop IP Traceback
§ Backscatter Traceback
§ Hash-Based (Single-Packet) IP Traceback
§ IP Traceback with IPSec
§ CenterTrack Method
§ Packet Marking
§ Check Domain Name System (DNS) Logs
§ Tracing with �log-input�
§ Control Channel Detection
§ Correlation and Integration
§ Path Identification (Pi) Method
§ Packet Traffic Monitoring Tools
§ Tools for Locating IP Addresses
o Challenges in Investigating DoS Attacks
o Tool: Nmap
o Tool: Friendly Pinger
o Tool: IPHost Network Monitor
o Tool: Admin�s Server Monitor
o Tool: Tail4Win
o Tool: Status2k
o Tool: DoSHTTP
o Chapter Summary
o Review Questions
· CHAPTER 6: Investigating Internet Crime
o Objectives
o Key Terms
o Case Example
o Introduction to Investigating Internet Crime
o Internet Crimes
o Internet Forensics
§ Why Internet Forensics?.
o Goals of Investigation
o Steps for Investigating Internet Crime
§ Obtain a Search Warrant
§ Interview the Victim
§ Prepare Bit-Stream Copies
§ Check the Logs
§ Identify the Source of the Attack
§ IP Addresses
§ Trace the IP Address of the Attacker Computer
§ Domain Name System (DNS)
§ Analysis of WHOIS Information
§ Collect the Evidence
§ URL Redirection
§ Embedded JavaScript
§ Downloading a Single Page or an Entire Web Site
§ Recovering Information from Web Pages
§ Trace the E-Mail Addresses
§ Tool: NeoTrace (now McAfee Visual Trace)
§ Tool: NetScan Tools
§ Generate a Report
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 7: Tracking E-Mails and Investigating E-Mail Crime
o Objectives
o Key Terms
o Introduction to Tracking E-Mails and Investigating E-Mail Crime
o E-Mail Systems
§ E-Mail Client
§ E-Mail Server
o E-Mail Crime
§ Spamming
§ Mail Bombing
§ Mail Storm
o Identity Theft
o Chain E-Mails
o Phishing
o E-Mail Spoofing
o Investigating E-Mail Crimes and Violations
§ Obtaining a Search Warrant and Seizing the Computer and E-Mail Account
§ Examining E-Mail Messages
§ Copying an E-Mail Message
§ Printing an E-Mail Message
§ Obtaining a Bit-By-Bit Image of E-Mail Information
§ Viewing and Copying E-Mail Headers in Microsoft
§ Viewing and Copying E-Mail Headers in AOL
§ Viewing and Copying E-Mail Headers in Hotmail
§ Viewing and Copying E-Mail Headers in Gmail
§ Viewing and Copying E-Mail Headers in Yahoo!
§ Examining an E-Mail Header
§ Examining Additional Files
§ Examine the Originating IP Address
§ Examine Phishing
o Using Specialized E-Mail Forensic Tools
§ Tool: Forensic Toolkit (FTK)
§ Tool: FINALeMAIL
§ Tool: R-Mail
§ Tool: E-Mail Detective
§ Tool: E-mail Examiner by Paraben
§ Tool: Network E-mail Examiner by Paraben
§ Tool: Recover My Email for Microsoft Outlook
§ Tool: Diskinternals Outlook Recovery
§ Trace the E-Mail
§ Tool: LoPe
§ Tool: eMailTrackerPro
§ Tool: ID Protect
o U.S. Laws against E-Mail Crime: CAN-SPAM Act
o U.S. Law: 18 U.S.C. � 2252A
o U.S. Law: 18 U.S.C. � 2252B
o E-Mail Crime Law in Washington: RCW 19.190.020
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 8: Investigating Corporate Espionage
o Objectives
o Key Terms
o Introduction to Investigating Corporate Espionage
o Motives Behind Spying
o Information That Corporate Spies Seek
o Corporate Espionage: Insider/Outsider Threat
o Corporate Espionage Threat Due to Aggregation of Information
o Techniques of Spying
o Defense Against Corporate Spying
o Steps to Prevent Corporate Espionage
§ Understand and Prioritize Critical Assets
§ Define Acceptable Level of Loss
§ Control Access
§ Bait: Honeypots and Honeytokens
§ Detect Moles
§ Perform Profiling
§ Perform Monitoring
§ Analyze Signatures
o Key Findings from U.S. Secret Service and CERT Coordination Center/SEI Study on Insider Threats
o Netspionage
o Investigating Corporate Espionage Cases
o Tool: Activity Monitor
o Tool: Spector CNE
o Tool: Track4Win
o Tool: SpyBuddy
o Tool: NetVizor
o Tool: Privatefirewall
o Tool: Internet Spy Filter
o Tool: Spybot�Search & Destroy
o Tool: SpyCop
o Tool: Spyware Terminator
o Tool: XoftSpySE
o Tool: Spy Sweeper
o Tool: CounterSpy
o Tool: SUPERAntiSpyware
o Tool: iMonitorPC
o Guidelines for Writing Employee-Monitoring Policies
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 9: Investigating Trademark and Copyright Infringement
o Objectives
o Key Terms
o Introduction to Investigating Trademark and Copyright Infringement
o Trademarks
§ Trademark Eligibility and Benefits of Registering It
§ Service Mark and Trade Dress
o Trademark Infringement
§ Monitoring Trademark Infringements
§ Key Considerations Before Investigating Trademark Infringements
§ Steps for Investigating Trademark Infringements
o Copyright
§ Investigating Copyright
§ How Long Does a Copyright Last?
§ U.S. Copyright Office
§ How Are Copyrights Enforced?
§ Plagiarism
o Patent
§ Patent Infringement
§ Patent Search
§ Tool: http://www.ip.com
o Domain Name Infringement
§ How to Check for Domain Name Infringement
o Intellectual Property
§ Investigating Intellectual Property Theft
o Digital Rights Management (DRM)
§ Tool: Windows Media Digital Rights Management
§ Tool: Haihaisoft Media DRM Platform
§ Tool: LockLizard
§ Tool: IntelliProtector
o U.S. Laws for Trademarks and Copyright
§ The Digital Millennium Copyright Act (DMCA) of 1998
§ The Lanham (Trademark) Act (15 USC �� 1051�1127)
§ Online Copyright Infringement Liability Limitation Act
o Indian Laws for Trademarks and Copyright
§ The Patents (Amendment) Act, 1999
§ Trade Marks Act, 1999
o Japanese Laws for Trademarks and Copyright
§ Trademark Law
§ Copyright Management Business Law (4.2.2.3 of 2000)
o Australian Laws for Trademarks and Copyright
§ The Trade Marks Act 1995
§ The Copyright Act 1968: Section 132
o U.K. Laws for Trademarks and Copyright
§ The Copyright, etc. and Trade Marks (Offences and Enforcement) Act 2002
§ Trademarks Act 1994 (TMA)
o Chinese Laws for Trademarks and Copyrights
§ Copyright Law of People�s Republic of China (Amendments on October 27, 2001)
§ Trademark Law of the People�s Republic of China (Amendments on October 27, 2001)
o Canadian Laws for Trademarks and Copyrights
§ Copyright Act (R.S., 1985, c. C-42)
§ Trademark Law
o South African Laws for Trademarks and Copyright
§ Trademarks Act 194 of 1993
§ Copyright Act of 1978
§ Patents Act No. 57 of 1978
o South Korean Laws for Trademarks and Copyright
§ Copyright Law Act No. 3916
§ Industrial Design Protection Act
o Belgian Laws for Trademarks and Copyright
§ Copyright Law, 30/06/1994
§ Trademark Law, 30/06/1969
o Hong Kong Laws for Intellectual Property
§ Article 139 of the Basic Law
§ Article 140 of the Basic Law
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 10: Investigating Sexual Harassment Incidents
o Objectives
o Key Terms
o Case Example 1
o Case Example 2
o Case Example 3
o Introduction to Investigating Sexual Harassment Incidents
o Types of Sexual Harassment
§ Quid Pro Quo Harassment
§ Hostile Work Environment Harassment
o Consequences of Sexual Harassment
o Sexual Harassment Statistics
o The Dos and Don�ts if an Employee Is Being Sexually Harassed
o Stalking
§ Stalking Behaviors
§ Stalking Effects
§ Guidelines for Stalking Victims
o Responsibilities of Supervisors
o Responsibilities of Employees
o Complaint Procedures
o Investigation Process
§ Sexual Harassment Investigations
o Sexual Harassment Policy
o Preventive Steps
o U.S. Laws on Sexual Harassment
§ Title VII of the Civil Rights Act of 1964
§ The Civil Rights Act of 1991
§ Equal Protection Clause of the 14th Amendment
§ Common Law Torts
§ State and Municipal Laws
o Australian Laws on Sexual Harassment
§ Sex Discrimination Act 1984
§ Equal Opportunity for Women in the Workplace Act 1999
§ Anti-Discrimination Act 1991
§ Workplace Relations Act 1996
o Indian Law: Sexual Harassment of Women at Workplace (Prevention, Prohibition, and Redressal) Bill, 2006
o German Law: Protection of Employees Act
o U.K. Law: The Employment Equality (Sex Discrimination) Regulations 2005
o Law of the People�s Republic of China on the Protection of Rights and Interests of Women
o Malaysian Penal Code, Section 509
o Sample Complaint Form
o Laws against Stalking
o Chapter Summary
o Review Questions
o Hands-On Projects
· CHAPTER 11: Investigating Child Pornography
o Objectives
o Key Terms
o Introduction to Investigating Child Pornography
o People�s Motives Behind Child Pornography
o People Involved in Child Pornography
o Role of the Internet in Child Pornography
o Effects of Child Pornography on Children
o Measures to Prevent Dissemination of Child Pornography
§ Computer Industry Self-Regulation (Role of ISP)
§ Legislative Regulation
§ Citizens� Committee
§ Parental Strategies
§ Law Enforcement Responses (Role of Police)
o Challenges in Controlling Child Pornography
o Precautions Before Investigating Child Pornography Cases
o Steps for Investigating Child Pornography
§ Step 1: Search and Seize All Computers and Media Devices
§ Step 2: Check Authenticated Login Sessions
§ Step 3: Search Hard Disks for Pornographic Material
§ Step 4: Recover Deleted Files and Folders
§ Step 5: Check Metadata of Files and Folders Related to Pornography
§ Step 6: Check and Recover Browser Information
§ Step 7: Check ISP Logs.
o Sources of Digital Evidence
o Citizens� Responsibility in Fighting Against Child Pornography
o Guidelines to Avoid Child Pornography on the Web
o Guidelines for Parents to Reduce the Risk of Their Children Being Exposed to Child Pornography
o Tool: Reveal
o Tool: iProtectYou
o Tool: Web Control for Parents
o Tool: BrowseControl
o Tool: ChatGuard
o Tool: Child Exploitation Tracking System (CETS)
o Child Pornography Legislation Survey
o U.S. Laws Against Child Pornography
§ � 18 U.S.C. 1466A
§ � 18 U.S.C. 2251
§ � 18 U.S.C. 2252
§ � 42 U.S.C. 13032
o State Laws: Michigan Laws Against Child Pornography
o Australian Laws Against Child Pornography
§ Criminal Code Act 1995 Section 474.19
§ Criminal Code Act 1995 Section 474.20
o Austrian Laws Against Child Pornography
o Belgian Laws Against Child Pornography
§ Article 383bis of the Penal Code
§ Article 380ter of the Penal Code
o Cypriot Laws Against Child Pornography
§ The Convention on Cybercrime, Law 22(III)/2004
§ Combating Trafficking in Human Beings and Sexual Abuse of Minors Law 3(1)/2000
o Japanese Laws Against Child Pornography
o South African Laws Against Child Pornography
§ Child Care Amendment Act
§ Amendment of Section 2 of Act 65 of 1996
§ Amendment of Section 27 of Act 65 of 1996
o U.K. Laws Against Child Pornography
§ Section 15
§ Section 16
§ Section 17
§ Section 18
§ Section 19
§ Section 47
§ Section 48
§ Section 49
§ Section 50
o English and Welsh Laws Against Child Pornography
o Scottish Laws Against Child Pornography
o Philippine Laws Against Child Pornography
o Children�s Internet Protection Act (CIPA)
o Anti-Child-Pornography Organizations
§ Project Safe Childhood
§ Innocent Images National Initiative
§ Internet Crimes Against Children
§ Anti-Child Porn Organization
§ Child Exploitation and Online Protection Centre
§ Think U Know
§ Virtual Global Taskforce
§ Internet Watch Foundation
§ International Centre for Missing & Exploited Children
§ National Center for Missing & Exploited Children
§ Financial Coalition Against Child Pornography
§ Perverted Justice
§ National Society for the Prevention of Cruelty to Children
§ Canadian Centre for Child Protection
§ Cybertip.ca
§ Association of Sites Advocating Child Protection
§ Web Sites Against Child Porn
§ Report Child Porn
§ Child Focus
§ StopChildPorno.be
o Chapter Summary
o Review Questions
o Hands-On Projects
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.