Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
4
Chapter
Router Forensics
Objectives
After completing this chapter, you should be able to:
• Understand router architecture
• Understand the use of Routing Information Protocol (RIP)
• List the different types of router attacks
• Differentiate router forensics from traditional forensics
• List the steps for investigating router attacks
• Conduct an incident response
• Read router logs
• List various router auditing tools
Key Terms
Chain of custody a record of the seizure, custody, control, transfer, analysis, and disposition of physical and electronic evidence
Intermediate System to Intermediate System (IS-IS) a link-state routing protocol that converges faster, supports much larger internetworks, and is less susceptible to routing loops than OSPF
Open Shortest Path First (OSPF) a link-state routing protocol used to manage router information based on the state (i.e., speed, bandwidth, congestion, and distance) of the various links between the source and destination
Router a network-layer device or software application that determines the next network point to which a data packet should be forwarded
Router log a log that provides information about a router’s activities
Routing Information Protocol (RIP) a distance-vector routing protocol used to manage router
information based on the number of hops between the source and destination
Routing table a database that stores the most efficient routes to particular network destinations Volatile evidence evidence that can easily be lost during the course of a normal investigation
4-1
4-2
Chapter 4
Introduction to Router Forensics
A router is a network-layer device or software application that determines the next network point to which a data packet should be forwarded in a packet-switched network. A router decides where to send information packets based on its current understanding of the state of the networks it is connected to, as well as the network portion of the Internet Protocol (IP) address.
As a hardware device, a router can execute specific tasks just like a switch. The only difference is that routers are more sophisticated. They have access to network-layer (layer 3 of the OSI model) addresses and contain software that enables them to determine which of several possible paths between those addresses is most suitable for a particular transmission.
Routers use headers and forwarding tables to determine the best path for sending data packets. Protocols such as ICMP, RIP, and OSPF are employed for communication and configuration of the best route between any two hosts.
Functions of a Router
The basic functions of a router are as follows:
• Forwarding packets
• Sharing routing information
• Packet filtering
• Network address translation (NAT)
• Encrypting or decrypting packets in the case of virtual private networks (VPNs)
The router is the backbone of a network and performs significant network functions. It determines the subsequent destination for a message on the path to its final destination based on the most effective path. It transfers link-state data, such as position, and the accessibility of servers and the connections between the servers. This is done within and amid routing groups.
A router also has the additional responsibility of protocol interpretation. This responsibility becomes easier for the router if it is supported with suitable hardware and software.
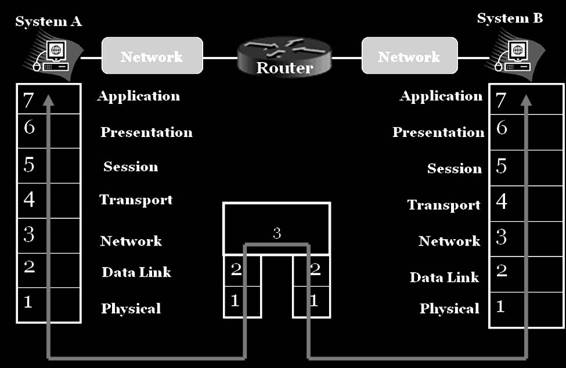
A Router in the OSI Model
Routers operate at the network layer of the OSI model (Figure 4-1). They relay packets among multiple interconnected networks.
If there is no single router connected to both the sending and receiving networks, the sending router transfers the packet across one of its connected networks to the next router in the direction of the ultimate destination.
The router forwards the packets to the next router on the path until the destination is reached. Each of these transfers is called a hop.
Once the best route is identified, the router generally sends the packets through that particular route. The router searches for the destination address and chooses the shortest path to reach it.
Router Architecture
The router’s physical architecture consists of the following three components:
• Memory
• Hardware
• IOS
Memory
This includes the NVRAM, which contains the startup configurations, and the SRAM/DRAM, which consists of the existing internetwork operating system and the routing tables.
Hardware
This includes the motherboard, the central processing unit (CPU), and the input/output peripherals.
![]()
Functions of a Router
4-3
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 4-1 Routers operate in the physical, data link, and network layers of the
OSI model.
IOS (Internetwork Operating System)
This is the software part of the router. IOS indicates the software version used in the router to make it operable.
The Routing Table and Its Components
A routing table is a database that stores the most efficient routes to particular network destinations. A router can only connect to a limited number of local area networks at startup. However, it can identify which network it is connected to by examining its own logical addresses. These data are sufficient for structuring a routing table.
Components of a Routing Table
A routing table consists of the following:
• An address prefix specifying the address of the final destination of the packet
• The interface on which the packets corresponding to the address prefix are transmitted
• A next hop address specifying the address of the router to which a packet must be delivered en route to its final destination
• A preference value for choosing between several routes with similar prefixes
• Route duration
• A specification showing whether the route is advertised in a routing advertisement
• A specification on how the route is aged
• Route type
Routing Information Protocol (RIP)
Routing Information Protocol (RIP) is a protocol used to manage router information within a self-contained network. RIP depends on an algorithm that uses distance vectors to find the best and shortest path for a packet to reach its destination. The distance between the source and destination network is calculated with the help of a hop-count metric (single-routing metric). Each hop on the way from the source to the destination is given 4-4
Chapter 4
a hop-count value. When a new network enters the topology, RIP sends a new, updated routing message to the router. When the router gets the updated destination network address, it changes its router table.
RIP is limited in that it allows only 15 hops in the path from source to destination. If a 16th hop is required, the network destination is then indicated as unreachable. The routing protocols OSPF (Open Shortest Path First) and IS-IS (Intermediate System to Intermediate System) can be used when RIP is not practical. OSPF
is a link-state routing protocol used to manage router information based on the state (i.e., speed, bandwidth, congestion, and distance) of the various links between the source and destination. IS-IS is a link-state routing protocol that converges faster, supports much larger internetworks, and is less susceptible to routing loops than OSPF.
Router Vulnerabilities
The following common router vulnerabilities are likely avenues for attack:
• HTTP authentication vulnerability: With the aid of http://router.address/level/$NUMBER/exec/....,
where $NUMBER is an integer between 16 and 99, it is possible for a remote user to gain full administrative access to a router.
• NTP vulnerability: By sending a crafted NTP control packet, it is possible to trigger a buffer overflow in the NTP daemon.
• SNMP parsing vulnerability: Malformed SNMP messages received by affected systems can cause various parsing and processing functions to fail, which results in a system crash and reloading. In some cases, access-list statements on the SNMP service do not protect the device.
Router Attacks
An intruder that takes control of a router can perform many different attacks on a network. They can gain knowledge of all possible vulnerabilities in a network once the router has been accessed.
An attacker who has gained access to a router can interrupt communication, disable the router, stop communication between compromised networks, as well as observe and record logs on both incoming and outgoing traffic. By compromising a router, attackers can avoid firewalls and intrusion detection systems (IDS), and can transmit any kind of traffic to a chosen network.
Types of Router Attacks
There are many types of router attacks. The following are the most common:
• Denial-of-service attacks
• Packet-mistreating attacks
• Routing table poisoning
• Hit-and-run attacks
• Persistent attacks
Denial-Of-Service (DoS) Attacks
A denial-of-service (DoS) attack renders a router unusable for network traffic by overloading the router’s resources so that no one can access it. An attacker that cannot gain access to a router can simply crash it by sending the router more packets than it can handle. A DoS attack is carried out with the following three goals:
• Destruction: These attacks damage the ability of the router to operate.
• Resource utilization: These attacks are achieved by overflowing the router with numerous requests to open connections at the same time.
• Bandwidth consumption: These attacks utilize the bandwidth capacity of a router’s network. An attacker who has successfully carried out a DoS attack can then modify configuration information and carry out an attack on any network the router is connected to.
Router Forensics Versus Traditional Forensics
4-5
Packet-Mistreating Attacks
In these types of attacks the compromised router mishandles or mistreats packets, resulting in congestion. These attacks are difficult to detect. They have limited effectiveness when compared to routing table poisoning and DoS attacks because the attacks are confined to only a part of the network rather than the whole network.
Attackers carrying out packet-mistreating attacks often acquire an actual data packet and mistreat it. The mistreated packet could invoke the following problems:
• Denial of service: This can be caused indirectly by directing an irrepressible number of packets to the victim’s address, thus rendering the victim router and its network inaccessible for regular traffic.
• Congestion: This is caused by misrouting packets to heavily loaded links of a network.
• Lowering of connection throughput: The attacker carrying out a packet-mistreating attack can decrease throughput by preventing TCP packets from broadcasting further. The victim router, sensing congestion, would lower the sending speed, resulting in a decrease in connection throughput.
Routing Table Poisoning
Routing table poisoning is one of the most prominent types of attacks. When an attacker maliciously alters, or poisons, a routing table, the routing-data update packets are also maliciously modified. These routing-data packets are needed by some routing protocols to broadcast their IP packets. Misconfigured packets produce false entries in the routing table, such as a false destination address. This leads to a breakdown of one or more systems on a network and the following problems:
• Suboptimal routing: This attack affects real-time applications on the Internet.
• Congestion: This attack can lead to artificial congestion, which cannot be eliminated using conventional congestion control methodologies.
• Partition: Due to the presence of false entries in the routing table, artificial partitions are created in the network.
• Overwhelmed host: The compromised router can be used as a tool for DoS attacks.
• Unauthorized access to data: The attacker can access the data present in the compromised network.
Hit-and-Run Attacks
Hit-and-run attacks occur when an attacker injects a small number of bad packets into the router to exploit the network.
This type of attack is similar to a test attack because the attacker gains knowledge of whether the network is online and functioning. This kind of test attack, however, can cause long-term damage and is hard to detect.
Persistent Attacks
In a persistent attack, the attacker continuously injects bad packets into the router and exploits the vulnerabilities that are revealed during the course of the injection process.
These attacks can cause significant damage because the router can get flooded with packets and cease functioning due to the constant injection of packets. These attacks are comparatively easy to detect.
Router Forensics Versus Traditional Forensics
Router forensics does not differ much from traditional forensics except in some particular steps taken during investigations. During router investigations, the system needs to be online, whereas in traditional forensic investigations, the system needs to be powered off. The system must be online so the forensic investigator can have exact knowledge of what type of traffic flows through the router.
In traditional forensics, the system is powered off because data may get erased or modified by the intruder and the forensic investigator may be unable to discover what kind of data has been modified. Data remains constant, unchanged, and ineffective during router investigations because it is prohibited for any other person to handle or read the data.
In traditional forensics, a copy of the data to be investigated should be made for examinations, since the data is most likely to be modified or erased.
4-6
Chapter 4
Investigating Router Attacks
An attack must be investigated to establish countermeasures that could possibly prevent the success of future attacks. An investigator must keep in mind that the router to be investigated can be in any state and must be returned to its preattack state. The following guidelines should be kept in mind during a router investigation:
• Start with a security policy and develop a plan that includes collecting and defining data.
• Create a reconnaissance methodology that provides information about the target.
• Perform an analysis check to identify incidents and review default passwords and
default information.
• Develop an attack strategy for analyzing commands to access the network, access control lists, firewalls, and protocols.
• The investigator must be careful while accessing the router, as valuable evidence can be lost if the router is mishandled.
• Intrusion analysis is vital to identifying the attacker and preventing the success of future attacks.
Investigation Steps
The following steps should be carried out during the investigation of a router attack:
1. Seize the router and maintain the chain of custody.
2. Perform incident response and session recording.
3. Access the router.
4. Gather volatile evidence.
5. Identify the router configuration.
6. Examine and analyze.
7. Generate a report.
Seize the Router and Maintain the Chain of Custody
Before starting the investigation process, the investigator should seize the router so that nobody can change its configuration. Chain of custody must be maintained throughout an investigation. Chain of custody is a record of the seizure, custody, control, transfer, analysis, and disposition of physical and electronic evidence.
It is essential to maintain the chain of custody to prevent mishandling of evidence. Doing so also prevents the individual who collected and handled the evidence from being confused while giving testimony during a trial.
This record must be handled carefully to avoid claims of corruption or misconduct during a trial. These claims could possibly compromise a case.
The chain of custody must document the following:
• The source of any evidence
• When evidence was received
• The individuals who provided the evidence
• The methods applied to gain the evidence
• The reasons for seizing the evidence
• The evidence handlers
A chain of custody form should include the conditions under which the evidence was collected, who actually handled the evidence, the time of collection, the duration of custody, the security conditions while the evidence was handled and stored, and how the evidence was transferred. A sample chain of custody form can be seen in Figure 4-2.


![]()
Investigating Router Attacks
4-7
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 4-2 Chain of custody forms document the evidence-gathering phase of
an investigation.
Perform Incident Response and Session Recording
The first steps taken by an investigator when an incident has occurred constitute the incident response. The following rules should be followed during the incident response phase of an investigation:
• The router should not be rebooted unless absolutely necessary, according to the rules of router forensics.
If the router is rebooted, valuable information can be lost.
• All information and evidence acquired must be recorded.
• No modifications should be made to the information and evidence acquired.

4-8
Chapter 4
The following incidents should be handled in specific ways:
• Direct-compromise incidents
• Routing table manipulation
• Theft of information
• Denial of service
Direct-Compromise Incidents After denial of service, a direct-compromise incident is one of the most common incidents. The investigator must actually assume the role of the perpetrator while investigating these incidents in order to accurately assess vulnerabilities.
The investigator must make use of listening services, which in turn reveal possible vulnerabilities and attack points. With the consent of the network administrator these attack points can be closed, countermeasures for the vulnerabilities can be provided, or the vulnerabilities can be left alone.
During the next step, the router must be rebooted so that the investigator can acquire access to the console.
The session must be recorded as soon as the investigator gains console access. The investigator may also access the modem if there was an improper logoff.
Passwords are important during investigations. As previously mentioned, the forensic investigator must step into the shoes of the perpetrator to find out how the attacker cracked the passwords. Attackers can crack passwords by using password-cracking tools; stealing them from configuration files; acquiring them by sniffing user protocols such as SNMP, telnet, HTTP, or TFTP; or by simply guessing them.
Trivial File Transfer Protocol (TFTP) is a useful protocol for discovering what an attacker did while attacking a router. The protocol stores and reloads configuration files. An attacker can scan a network for a router and the TFTP server. The attacker can use this protocol to acquire the configuration file and enumerate all possible passwords to access the router.
Routing Table Manipulation The routing table must be reviewed by using the command show ip route.
This will reveal the IP to which the attack was directed and exactly how it was carried out.
Theft of Information The network topology and access control lists must be examined thoroughly in a theft-of-information incident. These are contained in the router. The access control lists play a vital role in router investigations.
Denial of Service Denial-of-service incidents are one of the most common incidents, and the investigator must behave in a clinical manner while handling them. The router must be restarted for conducting investigations into denial-of-service incidents.
Recording the Session Every step taken during a router investigation must be recorded (Figure 4-3). The investigation session must be recorded beginning from the time of router login. The time that each step is taken must be recorded. To show the current time, the investigator can use the command show clock detail.
Figure 4-3 Every step an investigator takes must be recorded.
Investigating Router Attacks
4-9
Access the Router
A router needs to be accessed to acquire information and evidence related to the incident. An investigator must be careful while accessing the router because critical information can be lost if the router is not accessed properly. There are certain points that should be kept in mind while accessing the router.
The following guidelines should be followed:
• The router must be accessed through the console. It must be not be accessed through the network.
• Record the entire console session.
• Record the actual time and the router time.
• Only show commands should be executed. Configuration commands must not be executed, as they may change the state of the router and complicate issues for the investigator.
• Volatile information must be given priority over persistent data, as volatile information is temporary in nature and can be destroyed easily.
Gather Volatile Evidence
Volatile evidence is evidence that can easily be lost during the course of a normal investigation. It must be given priority while accessing a router for investigative purposes. It is temporary in nature and can be lost at any time.
Therefore, the investigator should take steps to gather it at the earliest opportunity.
The following items are considered volatile evidence:
• Current configuration
• Access list
• Time
• Log files
Volatile evidence can be collected in the following two ways:
• Direct access
• Indirect access
Direct Access Direct access is carried out using show commands. The router is accessed directly through the router console. Some of the show commands (along with accompanying output for some) are as follows:
• show clock detail
10:27:46.089 PST Wed Dec 25 2004
• show version
Cisco Internetwork Operating System Software
IOS (tm) 7000 Software (C7000-JS-M), Version 11.2(21), RELEASE
SOFTWARE (fc1)
Copyright (c) 1986-1999 by cisco Systems, Inc.
Compiled Wed 15-Dec-99 23:44 by ccai
Image text-base: 0x00001000, data-base: 0x008F86E8
ROM: System Bootstrap, Version 11.2(3), SOFTWARE
ROM: 7000 Software (C7000-AJSV-M), Version 11.2(3), RELEASE SOFTWARE (fc2)
Router uptime is 1 hour, 38 minutes
System restarted by power-on at 15:19:36 MEST Tue Apr 25 2000
System image file is “c7000-js-mz _ 112-21.bin”, booted via tftp
from 172.17.240.250
cisco RP1 (68040) processor (revision C0) with 65536K bytes of memory.
Processor board ID 0025A50A
G.703/E1 software, Version 1.0.
SuperLAT software copyright 1990 by Meridian Technology Corp.
4-10
Chapter 4
Bridging software.
X.25 software, Version 2.0, NET2, BFE and GOSIP compliant.
TN3270 Emulation software.
1 Switch Processor
1 EIP controller (6 Ethernet).
1 TRIP controller (4 Token Ring).
1 AIP controller (1 ATM).
6 Ethernet/IEEE 802.3 interface(s)
4 Token Ring/IEEE 802.5 interface(s)
1 ATM network interface(s)
128K bytes of non-volatile configuration memory.
4096K bytes of flash memory sized on embedded flash.
Configuration register is 0x2102
• show running-config
Building configuration...
Current configuration:
!
version 12.0
service timestamps debug datetime localtime
service timestamps log datetime localtime
no service password-encryption
!
hostname Router
!
boot buffersize 126968
boot system flash slot0:halley
boot bootldr bootflash:c6msfc-boot-mz.120-6.5T.XE1.0.83.bin
enable password lab
!
clock timezone Pacific Ϫ8
clock summer-time Daylight recurring
redundancy
main-cpu
auto-sync standard
!
ip subnet-zero
!
ip multicast-routing
ip dvmrp route-limit 20000
ip cef
mls flow ip destination
mls flow ipx destination
cns event-service server
!
spanning-tree portfast bpdu-guard
spanning-tree uplinkfast
spanning-tree vlan 200 forward-time 21
port-channel load-balance sdip
Investigating Router Attacks
4-11
!
!
!
interface Port-channel2
no ip address
switchport
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/1
no ip address
no ip directed-broadcast
sync-restart-delay 600
shutdown
!
!
.
.
.
• show startup-config
• show ip route
• show ip arp
• show users
• show logging
• show ip interface
• show ip sockets
• show ip cache flow
• show snmp user
Indirect Access Indirect access can be carried out only if the attacker has changed the passwords. It can be carried out by port-scanning every router IP.
For example, if the router is named X, then the syntax for performing the port scan would be
the following:
nmap -v -sS -P0 -p 1- X
nmap -v -sU -P0 -p 1- X
nmap -v -sR -P0 -p 1- X
Indirect access can also be carried out by SNMP-scanning every router IP.
For example, if the router is named X, the syntax would be the following:
snmpwalk –v1 Router.domain.com public
snmpwalk –v1 Router.domain.com private
Identify the Router Configuration
There are two router configurations:
• Stored configuration: This is a nonvolatile configuration stored in the nonvolatile RAM (NVRAM).
• Current configuration: This is a volatile configuration that is kept in RAM.
4-12
Chapter 4
The following are the steps the investigator must take to acquire the router configurations:
1. Establish a connection to the router to retrieve the RAM and NVRAM.
2. Use the encrypted protocol secure shell to remotely access the router if a direct connection is not possible.
3. Log entire session with HyperTerminal.
4. Capture and save the volatile and nonvolatile router configurations for documentation purposes.
Examine and Analyze
Once the volatile evidence has been secured and the configuration has been obtained, the investigator can begin to analyze the retrieved information. The following router components should be examined and analyzed during this phase:
• Router configuration
• Routing table
• Access control list
• Router logs
Router Configuration Compare the startup configuration with the running configuration of the router. The following are the commands used for this purpose:
• show startup-config
• show running-config
Routing Table The routing table contains information regarding how the router forwards packets. Routing tables can be shown using the show ip route command. The investigator should search for a convert channel that diverts packets using an unauthorized path.
Access Control List The access control list is shown using the command show access list. The investigator should examine the access control list of the router to attempt to identify the attacker. An attacker may have entered the network from a trusted network address.
Router Logs Router logs provide information about the router’s activities. They show detailed information about the people on the network and what they are doing within the network.
Router logs help investigations in the following ways:
• Provide detailed information about what happens on the routers
• Enable the investigator to find out where the data is coming from and determine if it is a threat to the network
• Show details about the IP addresses of senders and receivers of packets
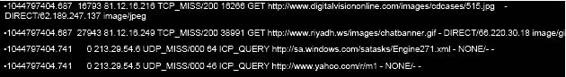
Figure 4-4 depicts part of a router log file.
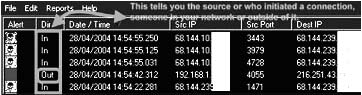
Because a router log shows the IP address of both the sender and the receiver, the ping or nslookup commands can be used from the command line to determine the host’s name (Figure 4-5).
The following types of router logs have different and important functions:
• Syslog log: Log messages are received and stored in the syslog server. The investigator must examine the syslog server for these log messages.
• Log buffer: The router log buffer stores the log messages. These log messages must be identified by the investigator. The command to check the log messages in the log buffer is show logging. This command reveals the contents of the router log buffer.
• Console log: Console sessions are recorded in this type of logging. This logging reveals who logged onto the console during a specific period of time.
• Terminal log: This logging is exactly the opposite of console logging. All of the nonconsole sessions are recorded, and the investigator can view these nonconsole log messages.

Investigating Router Attacks
4-13
Source: http:// www.worldstart.com/tips/tips/.php/1510. Accessed 2/2007.
Figure 4-4 Router log files can tell an investigator where a connection originated.
Source: http:// www.worldstart.com/tips/tips/.php/1510. Accessed 2/2007.
Figure 4-5 The ping command can be used to find a host name.
• SNMP log: This type of logging accepts all SNMP traps and records them.
• ACL violation log: Access control lists play an important role in investigating routers. They can be configured to log packets that match their rules. A router’s log buffer and the syslog server both receive and store these log messages in this type of logging.
NETGEAR Router Logs NETGEAR router logs can be used for monitoring network activities for specific types of attacks and reporting those attacks to a security monitoring program (Figure 4-6).

4-14
Chapter 4
Figure 4-6 NETGEAR router logs allow the user to apply various firewall rules.
NETGEAR router logs can be used to perform the following tasks:
• Alert when someone on a LAN has tried to access a blocked WAN address
• Alert when someone on the Internet has tried to access a blocked address in a LAN
• Identify port scans, attacks, and administrative logins
• Collect statistics on outgoing traffic for administrative purposes
• Assess whether keyword-blocking rules are excluding an undesired IP address
NETGEAR router logs include the following features:
• On many NETGEAR routers, the main purpose of logging is to collect information about traffic coming into a LAN.
• On models that limit the stored log to 128 entries, a complete record of activity can be sent by e-mail when the log is full.
• If logging is used with firewall rules and many entries are logged, the router’s regular traffic throughput can be reduced.
• Routers can send up to 120 e-mail notifications an hour. Half this many causes performance degradation.
• In some NETGEAR routers, certain logging functions are always turned on (NTP, for example).
The following examples are of log entries that indicate an attack:
• Example 1:
Multiple entries in the logs indicating suspicious data being dropped are an indication of attack (Figure 4-7). In most cases, the same ports or source IP addresses are indicated in each log entry.
• Example 2:
NETGEAR *Security Alert* [15:c9:11]
TCP Packet - Source:84.92.8.225,1261 Destination:84.92.37.165,3127 - [DOS]
A single message of this type may just indicate a random packet; however, several messages indicate a probable attack.

Investigating Router Attacks
4-15
Source: http:// kb.netgear.com/app/answers/detail/a_id/1014. Accessed 2/2007.
Figure 4-7 Entries indicating suspicious data being dropped are a possible
indication of an attack.
Real-Time Forensics An investigator should use the router to monitor the network, after removing or collecting the data from the compromised router. To do so, the investigator can turn logging on if it was not already activated, by using the following commands:
config terminal
service timestamps log datatime msec localtime show-timezone
no logging console
logging on
logging buffered 32000
logging buffered informational
logging facility local6
logging trap informational
logging Syslog-server.domain.com
AAA (authentication, authorization, and accounting) logging gathers the following information when a user connects to the network:
• Login time: The time when a user logs in to the network
• Logout time: The time when a user logs out of the network
• HTTP accesses: All the HTTP accesses a user made
• Privilege level changes: Any change made to an account’s privilege level
• Commands executed: All commands executed by users
AAA log entries are transferred to the authentication server through the following protocols:
• TACACSϩ (Terminal Access Controller Access Control System) protocol: This protocol provides access control to routers, network access servers, and other devices. It provides different AAA services.
• RADIUS (Remote Access Dial-In User Service): RADIUS is a client-server protocol that provides AAA services.
To enable AAA logging, an investigator can use the following commands:
config terminal
aaa accounting exec default start-stop group tacacsϩ
aaa accounting system default stop-only group tacacsϩ
aaa accounting connection default start-stop group tacacsϩ
aaa accounting network default start-stop group tacacsϩ

4-16
Chapter 4
Access control lists play an important role in investigating routers and checking log messages. They count packets and log specific events. A router’s log buffer and the syslog server both receive and store the log messages in this type of logging. Real-time monitoring can also be performed by configuring syslog logging and analyzing syslog files.
Generate a Report
The following steps must be performed whenever generating a router forensic report:
1. Note the name of the investigator.
2. List the router evidence.
3. Document the evidence and other supporting items.
4. Provide a list of tools used for the investigation.
5. List the devices and setup used in the examination.
6. Give a brief description of the examination steps.
7. Provide the following details about the findings:
a. Information about the files
b.
Internet-related
evidence
c. Data and image analysis
8. Provide conclusions for the investigation.
Tools
Router Audit Tool (RAT)
The Router Audit Tool (RAT) (Figure 4-8) downloads configurations of devices to be audited and then checks them against the settings defined in the benchmark. For each configuration examined, RAT produces a report listing the following items:
• A list of each rule checked with a pass/fail score
• A raw overall score
• A weighted overall score (1–10)
• A list of IOS/PIX commands that will correct the identified problems
Source: http:// www.cisecurity.org/bench_cisco.html. Accessed 2/2007.
Figure 4-8 The RAT tool checks devices against settings in a benchmark.


Tools
4-17
In addition, RAT produces a composite report listing the rules (settings) checked on each device as well as an overall score.
The Router Audit Tool (RAT) includes the following features:
• Ability to score Cisco router IOS
• Ability to score Cisco PIX firewalls
• Includes benchmark documents (PDF) for both Cisco IOS and Cisco PIX security settings
• Consolidates the following four Perl programs:
• snarf: Downloads configurations and generates reports
• ncat (Network Config Audit Tool): Reads rules and configurations and writes CSV-like output
• ncat_report: Reads CSV-like files and writes HTML
• ncat_config: Performs localization of the rule base
Link Logger
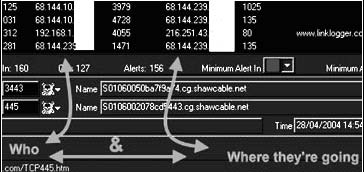
Link Logger (Figure 4-9) enables users to see and learn about Internet security and their network traffic. Link Logger is designed to take the logging information sent out from a router or firewall, process it, and then display it in a fashion that allows the user to see what is happening at the router or firewall. This allows the user to see how many scans and attacks are occurring, when and where they are coming from, and what kinds of scans and attacks they are. It also provides a link to further information concerning the details of a scan or attack.
Link Logger allows users to see when new scans or attacks are released, their effects on the Internet, and if they are a threat to a network.
Figure 4-9 Link Logger allows users to see and analyze
firewall traffic.
4-18
Chapter 4
Field
Internal Name
date/time
date_time
day of week
day_of_week
hour of day
hour_of_day
source host
source_host
destination host
destination_host
source port
source_port
destination port
destination_port
Table 4-1 Sawmill stores these nonnumerical fields in its Linksys
router database
Link Logger can perform the following functions:
• Monitor and administer the systems on a LAN to ensure that they are being used appropriately on the Internet
• Display traffic in real time and produce reports and graphs on a network level or on an individual system
• Retrieve and review the details behind the reports quickly and easily
Sawmill
Sawmill is a Linksys router log analyzer. Sawmill processes router log files, analyzes them, and then generates a report based on the analysis.
Sawmill stores the nonnumerical fields seen in Table 4-1 in its Linksys router database, generates reports for each field, and allows dynamic filtering on any combination of fields.
Sawmill includes the following features:
• Extensive documentation
• Live reports and graphs
• Analysis toolset
• Attractive statistics
• Advanced user tracking by WebNibbler
• Works with a variety of platforms
Chapter Summary
■ A router is a computer networking device that forwards data packets across networks.
■ A router decides the most effective path for a packet to reach its final destination.
■ A routing table is a database that stores the most efficient routes to particular network destinations.
■ The types of router attacks are: denial-of-service attacks, packet-mistreating attacks, routing table poisoning, hit-and-run attacks, and persistent attacks.
■ RIP sends routing update messages when the network topology changes.
■ A router log shows whether anyone has been trying to get into a network.
■ Investigators must be careful while accessing a router.
Review Questions
4-19
Review Questions
1. List the three components that comprise a router’s architecture.
__________________________________________________________________________________________
__________________________________________________________________________________________
2. List the types of router attacks.
__________________________________________________________________________________________
__________________________________________________________________________________________
3. List the steps necessary to investigate a router attack.
__________________________________________________________________________________________
__________________________________________________________________________________________
4. What are the basic functions of a router?
__________________________________________________________________________________________
__________________________________________________________________________________________
5. Describe the purpose of RIP.
__________________________________________________________________________________________
__________________________________________________________________________________________
6. What is routing table poisoning?
__________________________________________________________________________________________
__________________________________________________________________________________________
7. What is chain of custody?
__________________________________________________________________________________________
__________________________________________________________________________________________
8. Name four essential guidelines when accessing a router.
__________________________________________________________________________________________
__________________________________________________________________________________________
9. What is the difference between direct and indirect access of a router?
__________________________________________________________________________________________
__________________________________________________________________________________________
10. Name three types of router logs and their functions.
__________________________________________________________________________________________
__________________________________________________________________________________________


4-20
Chapter 4
Hands-On Projects
1. Use Link Logger to monitor Internet security and network traffic:
■ Navigate to Chapter 4 of the Student Resource Center.
■ Install and launch the Link Logger program.
■ Check various monitoring options of Link Logger (Figure 4-10).
Figure 4-10 Check the various monitoring options of Link Logger.

All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.