Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
5
Chapter
Investigating DoS Attacks
Objectives
After completing this chapter, you should be able to:
• Understand DoS attacks
• Recognize the indications of a DoS/DDoS attack
• Understand the different types of DoS attacks
• Understand DDoS attacks
• Understand the working of a DDoS attack
• Understand the classification of a DDoS attack
• Detect DoS attacks using Cisco NetFlow
• Investigate DoS attacks
• Understand the challenges in investigating DoS attacks
Key Terms
Buffer overflow attack a type of attack that sends excessive data to an application that either brings down the application or forces the data being sent to the application to be run on the host system
Denial-of-service attack an attack that overloads a system’s resources, either making the system unusable or significantly slowing it down
SYN flood occurs when the intruder sends SYN packets (requests) to the host system faster than
the system can handle.
Three-way handshake a common connection method on a network; first, a SYN packet is sent
to a host server. The host sends back an SYN-ACK packet to the source. The source then sends a
response ACK packet to complete the connection.
Zombie a slave computer in a distributed denial-of-service attack
5-1
5-2
Chapter 5
Introduction to Investigating DoS Attacks
In denial-of-service attacks, or DoS attacks, attackers attempt to prevent legitimate users of a service from using it by flooding the network with traffic or disrupting connections. The attacker may target a particular server application (HTTP, FTP, ICMP, TCP, etc.) or the network as a whole.
There may also be an effort to interrupt the connection between two machines, preventing or disturbing access to a particular system or individual. Improper use of resources may also create a DoS. For example, an intruder may use an unidentified FTP area to store large amounts of data, using disk space and producing network traffic problems.
In such an attack, a user or organization is deprived of the services of a resource that they would normally expect to have. In general, for certain network services, failure might mean the loss of a service such as e-mail or a Web server. DoS attacks are a kind of security breach that does not generally result in the theft of information or in any other type of security loss, but these attacks can harm the target in terms of time and resources.
Indications of a DoS/DDoS Attack
Indications of a DoS/DDoS attack are as follows:
• Unusual slowdown of network services: Most low- and medium-risk DoS attacks only slow down network services. They do not completely prevent access; they just make it more difficult.
• Unavailability of a particular Web site: When a DoS attack occurs against a poorly protected system or network server for any site, it can make the site impossible to reach.
• Dramatic increase in the volume of spam: Spam e-mails are sometimes used to generate huge amounts of bogus traffic over the network, causing a DoS.
Types of DoS Attacks
The main types of DoS attacks are as follows:
• Ping of death: Sending a malformed or otherwise malicious ping to a computer
• Teardrop: Forging fragmented packets designed to overlap each other when the receiving hosts defragment them
• SYN flooding: Sending TCP connection requests to a target host faster than it can process them
• LAND: Sending a data packet to a targeted machine with the same host and port names for the source and the destination
• Smurf: Using spoofed IP addresses to send broadcast ping messages to a large number of hosts in a network to flood the system
• Fraggle: Using UDP packets to flood a network
• Snork: Targeted against Windows NT RPC services
• OOB attack: Exploiting a bug in Microsoft’s implementation of its IP stack
• Buffer overflow attack: Sending more information to a program than it is allocated to handle
• Nuke attack: Repeatedly sending fragmented or invalid ICMP packets to the target computer
• Reflected attack: Sending false requests to a large number of computers, which respond to those requests
Ping of Death Attack
In the ping of death attack, an attacker deliberately sends an ICMP (Internet Control Message Protocol) echo packet of more than 65,536 bytes, the largest size acceptable by the IP protocol. Fragmentation is one of the features of TCP/IP, requiring that a large IP packet be broken down into smaller segments. Many operating systems do not know what to do when they receive an oversized packet, so they freeze, crash, or reboot.
Ping of death attacks are dangerous since the identity of the attacker sending the huge packet could simply be spoofed. Also, the attacker does not have to know anything about the target except its IP address. Several Web sites block ICMP ping messages at their firewalls to avoid this type of DoS attack.
Types of DoS Attacks
5-3
Teardrop Attack
A Teardrop attack occurs when an attacker sends fragments with overlapping values in their offset fields, which then cause the target system to crash when it attempts to reassemble the data. It affects systems that run Windows NT 4.0, Windows 95, and Linux up to 2.0.32, causing them to hang, crash, or reboot.
As stated earlier, TCP/IP will fragment a packet that is too large into smaller packets, no larger than 64 kilo-bytes. The fragment packets identify an offset from the beginning of the original packet that enables the entire original packet to be reassembled by the receiving system. In the Teardrop attack, the attacker manipulates the offset value of the second or latter fragments to overlap with a previous fragment. Since older operating systems are not equipped for this situation, it can cause them to crash.
SYN Flooding Attack
SYN flooding occurs when the intruder sends SYN packets (requests) to the host system faster than the system can handle them.
A connection is established through a TCP three-way handshake, in which the following occurs: 1. Host A sends a SYN request to Host B.
2. Host B receives the SYN request and replies to the request with a SYN-ACK to Host A.
3. Host A receives the SYN-ACK and responds with an ACK packet, establishing the connection.
When Host B receives the SYN request from Host A, it makes use of the partially open connections that are available on the listed line for at least 75 seconds.
The intruder transmits large numbers of such SYN requests, producing a TCP SYN flooding attack. This attack works by filling the table reserved for half-open TCP connections in the operating system’s TCP/IP stack.
When the table becomes full, new connections cannot be opened until some entries are removed from the table due to a handshake timeout. This attack can be carried out using fake IP addresses, making it difficult to trace the source. The table of connections can be filled without spoofing the source IP address. Normally, the space existing for fixed tables, such as a half-open TCP connection table, is less than the total.
LAND Attack
In a LAND attack, an attacker sends a fake TCP SYN packet with the same source and destination IP addresses and ports to a host computer. The IP address used is the host’s IP address. For this to work, the victim’s network must be unprotected against packets coming from outside with their own IP addresses. When the target machine receives the packet, the machine considers that it is sending the message to itself, and that may cause the machine to crash.
The symptoms of a LAND attack depend upon the operating system running on the targeted machine.
On a Windows NT machine, this attack just slows the machine down for 60 seconds, while Windows 95 or 98 machines may crash or lock up. UNIX machines also crash or hang and require a reboot.
Because LAND uses spoofed packets to attack, only blocking spoofed packets can prevent it. Still, with current IP technology, it is not possible to completely filter spoofed packets.
Smurf Attack
The smurf attack, named after the program used to carry it out, is a network-level attack against hosts. The attacker sends a large amount of ICMP echo (ping) traffic to IP broadcast addresses using a spoofed source address matching that of the victim. Smurf attacks generate a large number of echo responses from a single request, which results in a huge network traffic jam, causing the network to crash. If the routing device delivering traffic to those broadcast addresses accepts the IP broadcast, hosts on that IP network will take the ICMP
echo request and reply to each echo, exponentially increasing the replies.
On a multiaccess broadcast network, there could potentially be hundreds of machines replying to each packet, ensuring that the spoofed host may no longer be able to receive or distinguish real traffic.
Fraggle Attack
The fraggle attack is a UDP variant of the Smurf attack. In Fraggle attacks, an attacker sends a large number of UDP ping packets, instead of ICMP echo reply packets, to a list of IP addresses using a spoofed IP address.
All of the addressed hosts then send an ICMP echo reply, which may crash the targeted system. Fraggle attacks 5-4
Chapter 5
target networks where UDP ports are open and allow unrestricted UDP traffic to bypass firewalls. Fraggle is considered a medium-risk attack and can be easily carried out by slightly tweaking Smurf code.
Fraggle attacks affect network management consoles by bypassing the installed firewall by having the internal system try to respond to external echo requests. These attacks prevent the network from receiving UDP
traffic. A network administrator may not be able to distinguish between an inner system fault and an attack, due to missing syslog messages or SNMP trap alerts.
Snork Attack
In a Snork attack, a UDP packet sent by an attacker consumes 100% of CPU usage on a remote Windows NT
machine. If there are several Snork-infected NT systems in a network, they can send echoes to each other, generating enough network traffic to consume all available bandwidth.
Windows NT 4.0 workstations and servers with service packs up to and including SP4 RC 1.99 are vulnerable to Snork attacks. Network administrators can easily detect these attacks by adding a filter in their firewalls with the following specifications:
• Name: Snork
• Protocol: UDP
• Source Address: Any
• Source Port: 135 (additional rules for ports 7 and 19, if desired)
• Destination Address: Any
• Destination Port: 135
OOB Attack
The OOB attack exploits a bug in Microsoft’s implementation of its IP stack, causing a Windows system to crash. Windows NT (server and workstation versions up through 4.0), Windows 95, and Windows for Workgroups 3.11 platforms are the most vulnerable to these kinds of attacks.
RPC port 135, also known as the NetBIOS Session Service port, is the most susceptible port for these kinds of attacks. When a Windows system receives a data packet with an URGENT flag on, it assumes that the packet will have data with it, but in OOB attacks a virus file has an URGENT flag with no data.
The best way to prevent such attacks is to configure firewalls and routers so that they allow only trusted hosts to get in, and in some cases NetBIOS Session Service ports can be blocked altogether to secure systems.
Buffer Overflow Attack
A buffer overflow attack is a type of attack that sends excessive data to an application that either brings down the application or forces the data being sent to the application to be run on the host system. This can allow the attacker to run malicious code on the target system. Sending e-mail messages that have 256-character file names is one common way to cause a buffer overflow.
There are two types of buffer overflow attacks: heap based and stack based. In a heap-based buffer overflow attack, memory space that is reserved for a program is filled with useless data and can allow malicious code to overflow and be written into adjacent memory space. In a stack-based buffer overflow attack, the program stores the user’s input in a memory object together with local variables on the program’s stack. This causes the return address to be overwritten and redirects the flow to allow a malicious user to execute arbitrary code.
Nuke Attack
In a nuke attack, the attacker repeatedly sends fragmented or invalid ICMP packets to the target computer using a ping utility. This significantly slows the target computer.
Reflected Attack
A reflected attack involves sending huge amounts of SYN packets, spoofed with the victim’s IP address, to a large number of computers that then respond to those requests. Requested computers reply to the IP address of the target’s system, which results in flooding.
![]()
DDoS Attack
5-5
DDoS Attack
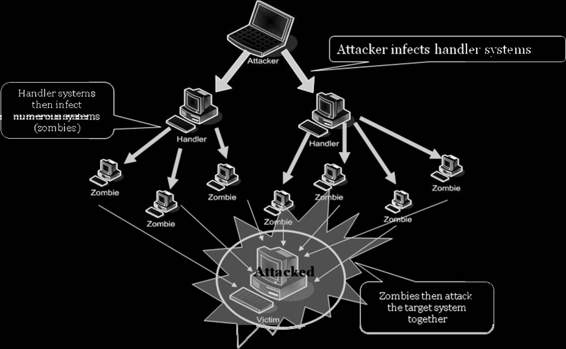
A distributed denial-of-service (DDoS) attack is a DoS attack where a large number of compromised systems attack a single target. In a DDoS attack, attackers first infect multiple systems, called zombies, which are then used to attack a particular target.
The services under attack are those of the primary victim, while the compromised systems used to launch the attack are often called the secondary victims. The use of secondary victims in performing a DDoS attack provides the attacker with the ability to wage a much larger and more disruptive attack, while at the same time making it more difficult to track down the original attacker.
Distributed denial-of-service attacks have become increasingly popular due to their readily available exploit plans and their ease of execution; however, these attacks can be the most dangerous because they can, in a relatively short amount of time, compromise even the largest Internet servers.
Working of a DDoS Attack
The first step in a DDoS attack is to build a network of computers that can be used to flood the target network. Attackers look out for poorly secured systems over the Internet that can be easily infected, and install malicious programs in these zombie systems. Attackers can remotely control these programs to carry out attacks as required. Systems without updated antivirus programs and firewalls are easy targets for the attackers to build an attack network.
There are many tools that automate this process. Self-propagating programs are used to automatically scan networks for vulnerable systems and install the necessary programs. This enables the attacker to build a large attack network within a short span of time. Attack networks are generally spread across different geographical locations and time zones to make it more difficult to track the source.
Once the attack network is ready, attackers can tell the malicious programs in the infected systems to launch an attack on a target or a number of targets. The zombies generate massive amounts of bogus network traffic that consumes the bandwidth of the target networks and prevents legitimate users from accessing network services. Attackers use IP spoofing to hide the origin of the traffic and avoid detection.
Figure 5-1 depicts how a DDoS attack works.
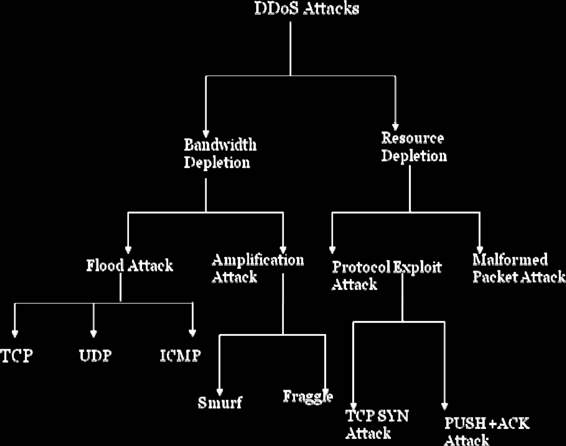
Classification of a DDoS Attack
DDoS attacks can be classified according to the degree of automation, the propagation mechanism, the vulnerability being exploited, the rate of attack, and the final impact. Figure 5-2 shows a taxonomy of DDoS attacks.
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 5-1 In a DDoS attack, the attacker first corrupts handlers, which then
corrupt zombies, which then attack the victim.
![]()
5-6
Chapter 5
DDoS Attacks
Bandwidth
Resource
Depletion
Depletion
Flood Attack
Amplification Protool Exploit
Malformed
Attack
Attack
Packet Attack
TCP
UDP
ICMP
Smurf
Fraggle
TCP SYN
PUSH+ACK
Attack
Attack
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 5-2 DDoS attacks are classified based on various criteria.
Degree of Automation
• Manual attacks: Attackers scan remote machines manually for vulnerabilities to infect the machine.
• Semiautomatic attacks: The attacker deploys automated, self-propagating programs to scan and infect vulnerable systems by installing malicious attack code. An attacker can remotely instruct these programs to launch an attack by manually specifying the attack type, target, time of attack, and code to be executed on the target. Most present-day DDoS attacks belong to this category.
• Attacks by direct communication: The malicious programs installed in the infected systems directly communicate with the attacker’s master system. For this purpose, the IP address of the attacker’s system needs to be hard-coded into the agent’s program.
• Attacks by indirect communication: The attacker’s system does not communicate with the agent directly; instead, the attacker uses IRC channels to direct agent programs. This ensures the
anonymity of the attacker.
• Automatic attacks: All instructions of the time of the attack, attack type, duration, and the victim’s address are encoded in the attacking program itself. This method ensures complete anonymity for
the attacker.
• Attacks using random scanning: Each zombie scans random addresses in the IP address space, generating a huge amount of network traffic.
• Attacks using hit-list scanning attacks: An infected zombie machine scans all addresses from an externally supplied list.
• Attacks using topology scanning: Zombies use information on the compromised host to select new targets for scanning.
• Attacks using permutation scanning: All infected zombie machines share a common pseudorandom permutation of the IP address space; every IP address is mapped to an index in this permutation.
• Attacks using local subnet scanning: Each infected machine scans the systems on the same subnet.
DoS Attack Modes
5-7
Propagation Mechanism
• Attacks using central source propagation: The attack code remains on a central server or set of servers and is downloaded to a target machine after successful infection.
• Attacks using back-chaining propagation: The attack code is downloaded from the attacker’s machine to the infected machine, and then the program in the infected machine is used for further propagation.
• Attacks using autonomous propagation: The malicious program is directly inserted into the target machine by the attacker.
Exploited Vulnerability
• Protocol attacks: Attackers exploit the vulnerabilities present in the communication protocol implementations in target machines. The TCP SYN attack, the CGI request attack, and the authentication server attack are a few examples of protocol attacks.
• Brute-force attacks: Attackers generate huge amounts of seemingly legitimate transactions that the target system cannot handle.
• Filterable attacks generate bogus traffic that can be filtered by most firewalls.
• Nonfilterable attacks use legitimate packets from the infected target to flood the network and cannot be filtered.
Attack-Rate Dynamics
• Continuous-rate attacks: The rate of propagation of attacking code is continuous and static.
• Variable-rate attacks: The rate of propagation of attacking code varies throughout propagation.
• Increasing-rate attacks: The rate of propagation of attacking code increases with time.
• Fluctuating-rate attacks: The rate of propagation of attacking code fluctuates with time.
Impact
• Disruptive attacks completely prevent legitimate users from using network services.
• Degrading attacks degrade the quality of services available to legitimate network users.
DoS Attack Modes
A DoS attack is known as an asymmetric attack when an attacker with limited resources attacks a large and advanced site. An attacker who is using a consumer-grade computer and a comparatively slow Internet connection may successfully attack powerful servers.
Denial-of-service attacks come in a variety of forms and target a variety of services. The attacks may cause the following:
• Consumption of resources
• Destruction or alteration of information regarding the configuration of the network
• Destruction of programming and files in a computer system
Network Connectivity
Denial-of-service attacks are most commonly executed against network connectivity. The goal is to stop hosts or networks from communicating on the network or to disrupt network traffic. An example of this type of attack is the SYN flood, where an attacker begins the process of establishing a connection to the victim’s machine, but does it in a way that ultimately prevents completion of the connection. An analogy would be to think of someone dialing your telephone and every time you answered, he or she would hang up and dial again. No one would ever be able to call you. Now automate it. In this case, an intruder uses the kernel data structures used in building a network connection, the three-way handshake of a TCP/IP connection model. This vulnerability enables an attack using a slower connection against a machine on a fast network.
5-8
Chapter 5
Misuse of Internal Resources
In a Fraggle attack, or UDP flood attack, forged UDP packets are used to connect the echo service on one machine to the character generator on another machine. This results in the consumption of the available network bandwidth between them, possibly affecting network connectivity for all machines.
Bandwidth Consumption
Generation of a large number of packets can cause the consumption of all the bandwidth on the network. Typically, these packets are ICMP echo packets. The attacker may also coordinate with many machines to achieve the same results. In this case, the attacker can control all the machines and instruct them to direct traffic to the target system.
Consumption of Other Resources
In addition to consuming network bandwidth, attackers may be able to consume other resources that systems need to operate. For example, an intruder may attempt to consume disk space by generating excessive e-mail messages or by placing files in anonymous FTP areas or network shares. Many sites will lock an account after a certain number of failed login attempts. An intruder may use this to prevent legitimate users from logging in.
Even privileged accounts, such as root or administrator, may be subjected to this type of attack.
Destruction or Alteration of Configuration Information
Alteration of the configuration of a computer or the components in a network may disrupt the normal functioning of a system. For instance, changing information stored in a router can disable a network, and making modifications to the registry of a Windows machine can disable certain services.
Techniques to Detect DoS Attacks
Detecting a DoS attack is a tricky job. A DoS attack traffic detector needs to distinguish between a genuine and a bogus data packet, which is not always possible; the techniques employed for this purpose are not perfect.
There is always a chance of confusion between traffic generated by a legitimate network user and traffic generated by a DoS attack.
One problem in filtering bogus traffic from legitimate traffic is the volume of traffic. It is impossible to scan each and every data packet to ensure security from a DoS attack.
All the detection techniques used today define an attack as an abnormal and noticeable deviation in network traffic characteristics. These techniques involve statistical analysis of deviations to categorize malicious and genuine traffic.
Activity Profiling
An activity profile is defined as the average packet rate of data packets with similar packet header information. Packet header information includes the destination and sender IP addresses, ports, and transport protocols used.
A flow’s average packet rate or activity level is higher the less time there is between consecutive matching packets. Randomness in average packet rate or activity level can indicate suspicious activity. The entropy calculation method is used to measure randomness in activity levels. Entropy of network activity levels will increase if the network is attacked.
One of the major hurdles for an activity profiling method is the volume of the traffic. This problem can be overcome by clustering packet flows with similar characteristics. DoS attacks generate a large number of data packets that are very similar, so an increase in average packet rate or an increase in the diversity of packets could indicate a DoS attack.
Sequential Change-Point Detection
The sequential change-point detection technique filters network traffic by IP addresses, targeted port numbers, and communication protocols used, and stores the traffic flow data in a graph that shows traffic flow rate versus time. Sequential change-point detection algorithms highlight any change in traffic flow rate. If there is a drastic change in traffic flow rate, a DoS attack may be occurring.
Investigating DoS Attacks
5-9
Wavelet-Based Signal Analysis
The wavelet analysis technique analyzes network traffic in terms of spectral components. It divides incoming signals into various frequencies and analyzes different frequency components separately. These techniques check for certain frequency components present at a specific time and provide a description of those components. Presence of an unfamiliar frequency indicates suspicious network activity.
A network signal consists of a time-localized data packet flow signal and background noise. Wavelet-based signal analysis filters out the anomalous traffic flow input signals from background noise. Normal network traffic is generally low-frequency traffic. During an attack, the high-frequency components of a signal increase.
Monitoring CPU Utilization to Detect DoS Attacks
High CPU utilization and a high number of packets are common symptoms that can be seen during a DoS
attack. Logging into perimeter routers, firewalls, and examining the CPU utilization can help identify a DoS attack.
For example, an administrator can determine the CPU utilization on a Cisco router using the show process cpu command. This command shows the average CPU utilization over the past five seconds, one minute, and five minutes. If all three of these values are at high percentages and are close to each other, there may be a DoS attack.
Monitoring CPU utilization at the time of a DoS attack and comparing it to the CPU utilization baselines captured at normal traffic conditions can show the severity of an attack. If the CPU utilization is 75% or less, then the condition of the router is normal, but if the CPU utilization is closer to 100%, then the DoS attack is severe and the router must be rebooted. Periodic gathering of statistical information about the router, along with CPU utilization and bandwidth utilization, helps identify any kind of attack on the router.
Detecting DoS Attacks Using Cisco NetFlow
NetFlow is a major service in Cisco routers that monitors and exports IP traffic-flow data. It checks the flow with a target IP destination and rings an alarm when the destination is reached. NetFlow sampling includes the following:
• Source and destination IP address
• Source and destination TCP/UDP ports
• Port utilization numbers
• Packet counts and bytes per packet
• Start time and stop time of data-gathering events and sampling windows
• Type of service (TOS)
• Type of protocol
• TCP flags
Detecting DoS Attacks Using a Network Intrusion Detection System (NIDS)
A network intrusion detection system monitors network traffic for suspicious activity. The NIDS server can be placed on a network to monitor traffic for a particular server, switch, gateway, or router. In order to monitor incoming and outgoing traffic, the NIDS server scans system files to identify unauthorized activity and monitor data and file integrity. The NIDS server can also identify changes in the server backbone components and scan log files to identify suspicious network activity, usage patterns, or remote hacking attempts. The NIDS server scans local firewalls or network servers and monitors live traffic. It is not limited to monitoring only incoming network traffic; it can be set to either monitor one machine’s traffic or all network traffic.
Investigating DoS Attacks
The first step in investigating a DoS attack is to identify the DNS logs that are used by an attacker to trace the IP address of the target system before launching an attack. If this is performed automatically by using an attack tool, the time of the DNS query and the time of the attack might be close to each other. The attacker’s DNS resolver could be determined by looking at the DNS queries during the start of the attack. Using DNS
![]()
5-10
Chapter 5
Copyright © by
All rights reserved. Reproduction is strictly prohibited
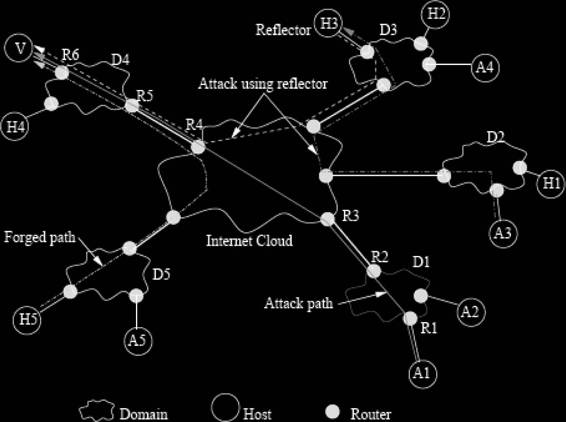
Figure 5-3 This reverse trace can identify an attacker, even when using reflectors.
logs, an investigator can identify the various attacks that are generated by the attacker. An investigator can trace packets to follow the appropriate path of a packet. It includes reconfiguration of routers and verifying log information.
ICMP Traceback
ICMP traceback messages are used to find the source of an attack. The messages contain the following:
• Router’s next and earlier hops addresses
• Time stamp
• Role of the traced packet
• Authentication information
While passing packets through the network path from the attacker to the victim, routers within the network path will test some packets and then send ICMP traceback messages to the destination. The victim may hold sufficient messages to trace the network path from the attacker to the victim. The disadvantage of this aspect is that the attacker can send fake messages to misguide the victim.
Modification should be involved in the ICMP traceback message when reflectors are introduced to deal with DDoS attacks. According to Figure 5-3, attacker A3 will send TCP SYN segments to the reflector H3 specifying V as the source address. In response, H3 will send SYN ACK segments to the victim V. This reverse trace allows the victim to identify an attacking agent from trace packets. This method depends on attacking agents and not on reflectors.
Hop-by-Hop IP Traceback
Hop-by-hop IP traceback is a basic method for tracking and tracing attacks. This method is available for tracing large, continuous packet flows that are currently in progress, such as those generated by ongoing DoS packet flood attacks. In a DoS flood attack, the source IP addresses are typically spoofed, so tracing is required to find the true origin of the attack.
For example, assume that the victim of a flood attack has just reported the attack to his or her ISP. First, an ISP administrator identifies the ISP’s router closest to the victim’s machine. Using the diagnostic, debugging, or Investigating DoS Attacks
5-11
logging features available on many routers, the administrator can characterize the nature of the traffic and determine the input link on which the attack is arriving. The administrator then moves on to the upstream router.
The administrator repeats the diagnostic procedure on this upstream router, and continues to trace back-ward, hop-by-hop, until the source of the attack is found inside the ISP’s administrative domain of control (such as the IP address of another customer of the ISP) or, more likely, until the entry point of the attack into the ISP’s network is identified. The entry point is typically an input link on a router that borders another provider’s network. Once the entry point into the ISP’s network is identified, the bordering provider carrying the attack traffic must be notified and asked to continue the hop-by-hop traceback. Unfortunately, there often is little or no economic incentive for such cooperation between ISPs.
Limitations of Hop-by-Hop IP Traceback
Hop-by-hop IP traceback has several limitations, such as the following:
• Traceback to the origin of an attack fails if cooperation is not provided at every hop or if a router along the way lacks sufficient diagnostic capabilities or resources.
• If the attack stops before the trace is completed, the trace fails.
• Hop-by-hop traceback is a labor-intensive, technical process, and since attack packets often cross administrative, jurisdictional, and national boundaries, cooperation can be difficult to obtain.
• Partial traceback can be useful, since packet filters can be put in place to limit the DoS flood.
• How anomalous the attack packets are and how well they can be characterized determines how
restrictive the filters have to be.
• Overly restrictive filters can contribute to the negative effects of a DoS attack.
Hop-by-hop traceback can be considered to be the baseline from which all proposed improvements in tracking and tracing are judged. It is the most basic method for tracing large packet flows with spoofed source addresses, but it has many limitations and drawbacks. DDoS attacks are difficult, if not impossible, to trace via this process, since there are multiple sources of attack packets, multiple paths through the Internet, and a relatively small number of packets coming from each source.
Backscatter Traceback
Backscatter traceback is a technique for tracing a flood of packets that are targeting the victim of a DDoS attack.
The backscatter traceback technique relies entirely on the standard characteristics of existing Internet routing protocols, and although some special router configurations are used, there is no custom modification of protocols or equipment that is outside of current Internet standards.
In a typical DDoS attack, a victim’s system is put out of service by a flood of malicious attack packets originating from a large number of zombie machines compromised by the attacker. The destination address field of each attack packet contains the IP address of the victim. The source IP address of each packet is typically spoofed. In contemporary DDoS attacks, the spoofed source address is typically chosen at random from the universe of all possible IP addresses.
How the Backscatter Traceback Works
1.
The attack is reported to an ISP: The victim of a DDoS attack reports the problem to his or her ISP.
The flood of attack packets has made the victim’s Internet connection unusable, putting the victim out of service.
2.
The ISP configures all of its routers to reject all packets destined for the victim: The ISP uses a standard routing control protocol to quickly configure all of its routers to reject packets that are targeted to the victim. By rejecting all packets that have the source address of the victim, benign packets carrying legitimate traffic will also be lost; however, the overwhelming number of packets heading for the victim will be attack packets. If the technique is successful, the total blockade of packets destined for the victim will only be in place for a short period of time.
3.
Rejected packets are “returned to sender” : When a router rejects a packet with the destination address of the victim, it sends an Internet Control Message Protocol (ICMP) “destination unreachable” error message packet back to the source IP address contained in the rejected packet. While some of the “return to sender” ICMP error messages will be sent to legitimate users whose benign packets have been rejected along with the malicious ones, most of the packets destined for the victim are malicious attack packets.
![]()
5-12
Chapter 5
Copyright © by
All rights reserved. Reproduction is strictly prohibited
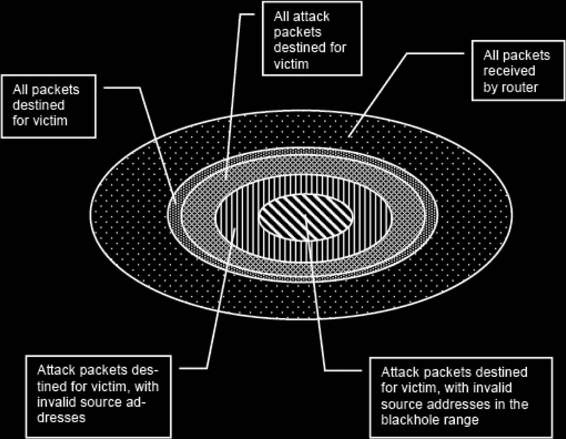
Figure 5-4 After applying the correct filters, only a fraction of packets will be
caught by the blackhole system.
Each ICMP “return to sender” error message packet contains, in its source IP address field, the address of the router (controlled and configured by the ISP) that rejected the packet heading for the victim. The router is also the machine that is generating the ICMP message. In its destination IP address field, the ICMP
“return to sender” error message packet contains the source IP address found in the rejected packet that had been heading for the victim. These ICMP error packets are the “backscatter” or “noise” that enables the ISP to trace the attack packets back to their ingress point into the ISP’s network.
4.
The ISP configures all of its routers to route for capture, or blackhole, many of the ICMP error packets (the backscatter) with illegitimate destination IP addresses: The Internet Address Naming Authority (IANA) has yet to allocate several large blocks of IP addresses for global routing. No one should ever see a legitimate packet containing an IP source address from this unallocated address space entering a domain from an external network. The next step in backscatter traceback is for an ISP to select a large range of IP addresses unallocated by IANA and to configure all of the ISP’s routers to send packets destined for these invalid addresses to a specific blackhole machine for analysis. The centermost region in Figure 5-4
represents the fraction of the overall packets arriving at an ISP’s router that are blackholed for analysis.
Since packets with these invalid destination addresses cannot have been routed into the ISP’s network from an external source, these packets can only be some of the ICMP “destination unreachable” error message packets generated internally by the ISP’s routers, which have been configured to reject all packets destined for the victim.
5.
Analysis by the blackhole machine quickly traces the attack to one or more routers at the outermost boundary of the ISP’s network: A human or program at the blackhole machine looks at the source address of each ICMP error packet to determine the address of the router that sent it. Typically, only a single router, or a small number of routers, will be identified as the entry point of the attack into the ISP’s network.
Investigating DoS Attacks
5-13
6.
The ISP removes the filter blocking the victim’s IP address from all routers except those serving as the entry points for the DDoS attack: The ISP leaves the blocking filter in place at those routers that have been traced as the entry points of the attack into the ISP’s network and removes the blocking filter at all other routers. The DDoS attack remains blocked, but most of the flow of the legitimate traffic to the victim is restored. The entire backscatter traceback process can typically be executed within a minute.
Only that portion of the inbound legitimate traffic that passes through the same entry points as the DDoS
attack and is intended for the victim’s IP address will remain blocked. Further analysis can identify specific characteristics of the attack packets that would allow the blocking filter on the attack entry-point routers to be refined in order to be more permissive of the benign traffic that has followed the same path as the attack packets, restoring an even higher level of service to the victim.
7.
The ISP asks neighboring ISPs, upstream of the attack, to continue the trace: The ISP further identifies the specific router interfaces through which the attack is entering the ISP’s network and notifies the neighboring ISPs directly upstream of the entry points. The neighboring ISPs will hopefully continue to trace the attack closer to its ultimate source, using the backscatter traceback technique or any alternative tracking method.
Hash-Based (Single-Packet) IP Traceback
Hash-based IP traceback, also known as single-packet IP traceback, offers the possibility of making the traceback of single IP packets feasible. The fundamental idea is to store highly compact representations of each packet rather than the full packets themselves. These compact representations are called packet digests and are created using mathematical functions called hash functions. The complete original packets cannot be restored from the packet digests.
A hash function is a mathematical function that maps values from a large domain into a smaller range, and that reduces a long message into a message digest or hash value that is small enough to be input into a digital signature algorithm.
Hash functions play a significant role in cryptography. The only aspect of hash functions of importance for this traceback application, however, is the ability to create highly compact digests of packets in order to greatly reduce the storage requirements at each router. A bloom filter provides reduction in the storage requirements needed to uniquely identify each packet. The hash functions and bloom filter reduce the storage requirement to 0.5% of the link capacity per unit of time, making single-packet IP traceback technically feasible with respect to the storage requirements. In addition, this approach addresses the obvious privacy issues posed by the universal logging of Internet traffic, since only the packet digests are stored at each router and not the actual packet contents. In general, a victim or an intrusion detection system submits a query by presenting the actual contents of the attack packet, and not the digest; however, for particularly sensitive cases, a victim will be able to submit a query without revealing the actual packet contents, at the cost of significant additional computational resources.
IP Traceback with IPSec
IPSec uses cryptographic security services for securing communications over IP networks. It supports the following:
• Network-level peer authentication
• Data origin authentication
• Data integrity
• Data confidentiality (encryption)
• Replay protection
IPSec tunnels are used by IP traceback systems such as DECIDUOUS (Decentralized Source Identification for Network-Based Intrusion). The analysis is processed by introducing IPSec tunnels between an arbitrary router and the victim. The attack may occur behind the router when the attack packets are established by the security association (SA). Otherwise, the attacker is established between the router and the victim. In that case, another SA is established closer to the victim, again and again until the source is found.
5-14
Chapter 5
CenterTrack Method
An overlay network is a supplemental or auxiliary network that is created when a collection of nodes from an existing network are joined together using new physical or logical connections to form a network on top of the existing one. The first step in the CenterTrack approach is to create an overlay network, using IP tunnels to connect the edge routers in an ISP’s network to special-purpose tracking routers that are optimized for analysis and tracking. The overlay network is also designed to further simplify hop-by-hop tracing by having only a small number of hops between the edge routers. In the event of a DoS flood attack, the ISP diverts the flow of attack packets from the existing ISP network onto the overlay tracking network containing the special-purpose tracking routers. The attack packets can be easily traced back, hop-by-hop, through the overlay network, from the edge router closest to the victim, back to the entry point of the packet flood into the ISP’s network.
Packet Marking
In packet marking, packets are marked to identify their traffic class. Once the type of traffic is identified, it can be marked, or “colored,” within the packet’s IP header. Packets are colored by marking the IP precedence or the DSCP field to divide them into groups so that end-to-end quality of service (QoS) policies can be applied.
In deterministic packet marking, the router shows all the packets, while in probabilistic packet marking, the path information is divided into small packets.
Probabilistic Packet Marking (PPM)
In packet marking, tracking information is placed into rarely used header fields inside the IP packets themselves.
The tracking information is collected and correlated at the destination of the packets, and if there is a sufficiently large packet flow, there will be enough tracking information embedded in the packets to successfully complete the trace.
An attacker can tamper with, or spoof, the tracking information. This method is enhanced by adding authentication to the embedded encodings of tracking information. All of the probabilistic traceback approaches depend on auditing very sparse samples of large packet flows and thus are well suited for attacks that generate massive packet flows, such as DDoS floods. These approaches are not useful for tracking attacks that employ only a small number of packets.
Check Domain Name System (DNS) Logs
The attacker uses DNS to find the actual IP address of the target computer before the attack is introduced. If an attacker uses an attack tool to determine the IP address, then the DNS query closest to the attack could help to identify the attacker’s DNS resolver. It can be useful to compare DNS logs of different systems that are under attack. Using DNS logs, an investigator can identify the different attacks carried out within the same individual or group. Sawmill DNS log analyzer can help view and analyze DNS log files.
Tracing with “log-input”
The following are the steps an investigator should take to trace an attack passing through a router using “log-input”:
1. Make an access list entry that goes with the attack traffic.
2. Attach the log-input keyword to it.
3. Use the access list outbound on the interface through which the attack stream is sent toward
the destination.
Log entries produced by the access list discover the router interface from which the traffic arrives and, if the interface is a multipoint connection, provide the layer 2 address of the device from where it is received. Use the layer 2 address to identify the next router in the chain, using show ip arp mac-address.
Control Channel Detection
A large volume of control channel traffic indicates that the actual attacker or coordinator of the attack is close to the detector. The control channel function provides facilities to define, monitor, and control channels. An investigator can use a threshold-based detector to determine the particular number of control channel detectors Investigating DoS Attacks
5-15
within a specific time period, and also to provide a clear way into the network and geographical location of the attacker.
Correlation and Integration
The attack detector tool can find the location of the attacker by integrating its results with other packet spoofing tools. An investigator can integrate it with other tools in order to identify spoofed packets and to find out the location of an attacker. Also, the investigator can correlate data from control channel detectors and flood detectors to identify which control channel established which flood and to observe spoofed signals from hop to hop or from the attacker to the server.
Path Identification (Pi) Method
The major part of the Pi method is to determine the path of each packet and filter out the packets that have the attack path. It can be used to identify the attack packets with filtering techniques and to analyze their path. It suggests routers to mark information on packets toward the victim. Pi is better than traceback mechanisms if the following are true:
• The victim can filter the packet independently from other upstream routers.
• The victim decides whether to drop or receive each packet.
• It is easier to determine the packet’s source.
Pi considers the following four factors of marking to mark a path between the attackers and the victim: 1. Which part of the router’s IP address to mark
2. Where to write the IP address in each packet’s ID field
3. How to neglect the unnecessary nodes in the path
4. How to differentiate the paths
Packet Traffic Monitoring Tools
The source of the attack can be identified by monitoring network traffic. The following are some useful traffic monitoring tools:
• Ethereal
• Dude Sniffer
• Tcpdump
• EffeTech
• SmartSniff
• EtherApe
• MaaTec Network Analyzer
Tools for Locating IP Addresses
After getting the IP address of the attacker’s system, an investigator can use the following IP address-locating tools to give details about the attacker:
• Traceroute
• NeoTrace
• Whois
• Whois Lookup
• SmartWhois
• CountryWhois
• WhereIsIp
5-16
Chapter 5
Challenges in Investigating DoS Attacks
The following are a few challenges that an investigator could face in investigating a DoS attack:
• The attacker will only attack for a limited time.
• An attack may come from multiple sources.
• Anonymizers protect privacy and impede tracing.
• Attackers may destroy logs and other audit data.
• The attacker may compromise the victim’s computer.
• Communication problems slow the tracing process.
• It can be difficult to detect and distinguish malicious packet traffic from legitimate packet traffic, particularly at such a high volume.
• There can be false positives, missed detections, and delayed detections, all preventing a timely and successful investigation.
• There may not be skilled network operators available the moment an attack takes place.
• Legal issues can impede investigations.
Tool: Nmap
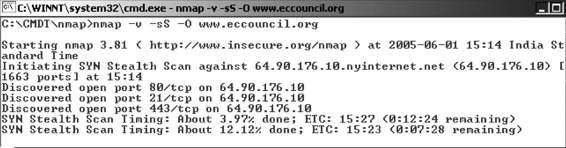
Nmap, short for “Network Mapper,” is an open-source utility for network exploration or security auditing. It was designed to rapidly scan large networks, although it works against single hosts.
Nmap uses raw IP packets to determine what hosts are available on the network, what services and ports they are offering, what operating system they are running, what type of packet filters and firewalls are in use, and dozens of other characteristics.
Figure 5-5 is a screenshot from Nmap.
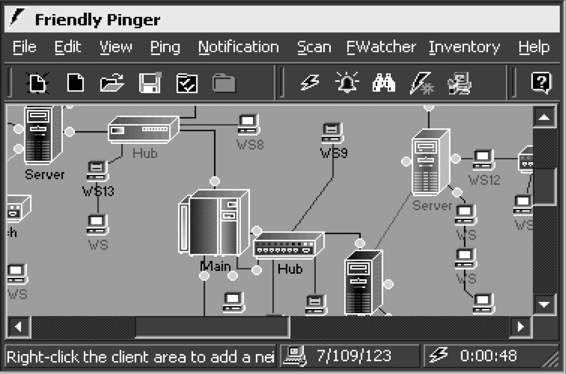
Tool: Friendly Pinger
Friendly Pinger is an application for network administration, monitoring, and inventory. It performs the following tasks:
• Visualization of a computer network, as shown in Figure 5-6
• Monitoring network device availability
• Notification when any server wakes up or goes down
• Ping of all devices in parallel at once
• Audit software and hardware components installed on computers over the network
• Tracking user access and files opened on a computer via the network
• Assignment of external commands (like telnet, tracert, and net) to devices
• Search of HTTP, FTP, e-mail, and other network services
Figure 5-5 Nmap runs from the command line.
Tool: Admin’s Server Monitor
5-17
Figure 5-6 Friendly Pinger will show a visual map of the network.
• Graphical Traceroute
• Opening of computers in Explorer, in Total Commander, or in FAR
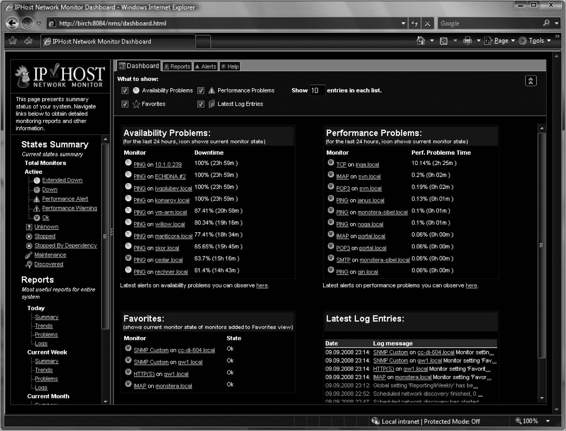
Tool: IPHost Network Monitor
IPHost Network Monitor allows availability and performance monitoring of mail, database, and other servers; Web sites; applications; and various other network resources using the following:
• SNMP
• WMI
• HTTP/HTTPS
• FTP
• SMTP
• POP3
• IMAP
• ODBC
• PING
It can create reports that can be read using a Web browser, as shown in Figure 5-7.
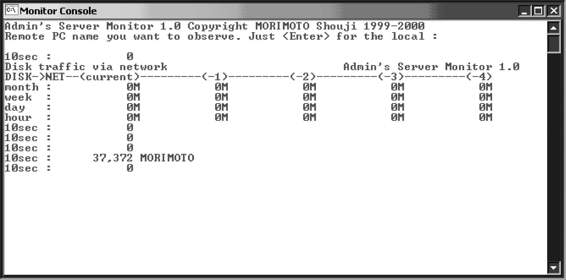
Tool: Admin’s Server Monitor
Admin’s Server Monitor is a tool to monitor server disk traffic loaded over a network. It gathers data for ranges from ten seconds to a full month and displays it in real time, as shown in Figure 5-8. It can show data from a remote PC with its console program.
5-18
Chapter 5
Figure 5-7 IPHost Network Monitor creates Web-based output reports.
Figure 5-8 Admin’s Server Monitor gives real-time reports on disk usage.
Tool: Tail4Win
Tail4Win, a Windows version of the UNIX tail -f command, is a real-time log monitor and viewer that can be used to view the end of a growing log file. Users can watch multiple files at once and monitor their changes in real time, as shown in Figure 5-9, but cannot make any changes to those files. Using Tail4Win is significantly faster than loading an entire log file because it is only concerned with the last part of the log, so users can monitor changes to logs as they occur and watch for suspicious behavior.
Tool: Status2k
5-19
Figure 5-9 Tail4Win can view multiple log files in real time.
Figure 5-10 Status2k shows real-time server information.
Tool: Status2k
Status2k provides server information in an easy-to-read format, with live load, uptime, and memory usage. The administration page displays a number of system statistics such as logs, port connections, users logged into SSH, and more. The whole administration page is in real time, showing how many connections there are to HTTP, SSH, POP3, MySQL, and the current top processes, as shown in Figure 5-10. Status2k can be viewed remotely from a Web browser.
5-20
Chapter 5
Figure 5-11 This is a screenshot of DoSHTTP.
Tool: DoSHTTP
DoSHTTP is an HTTP flood DoS testing tool for Windows. DoSHTTP includes URL verification, HTTP redirection, port designation, performance monitoring and enhanced reporting. DoSHTTP uses multiple asynchro-nous sockets to perform an effective HTTP flood. DoSHTTP can be used simultaneously on multiple clients to emulate a DDoS attack. A screenshot of the tool is shown in Figure 5-11.
Chapter Summary
■ A DoS attack is type of network attack intended to make a computer resource inaccessible to its legitimate and authorized users by flooding the network with bogus traffic or disrupting connections.
■ The attacker may target a particular server application (HTTP, FTP, ICMP, TCP, etc.) or the network as a whole.
■ The ping of death attack uses an abnormal ICMP (Internet Control Message Protocol) data packet that contains large amounts of data that causes TCP/IP to crash or behave irregularly. The attacker sends an illegal ping request that is larger than, the largest size acceptable by the IP protocol, to the target computer.
■ A distributed denial-of-service (DDoS) attack is a DoS attack where a large number of compromised systems attack a single target, thereby causing a denial of service for users of the targeted system. In a DDoS attack, attackers first infect multiple systems called zombies, which are then used to attack a particular target.
■ An activity profile is defined as the average packet rate for a network flow for the traffic that consists of data packets with similar packet header information.
■ The sequential change-point detection technique filters network traffic by IP addresses, targeted port numbers, and communication protocols used, and stores the traffic flow data in a traffic-flow-rate-versus-time graph.
■ The wavelet analysis technique analyzes network traffic in terms of spectral components. It divides incoming signals into various frequencies and analyzes different frequency components separately.
Review Questions
5-21
Review Questions
1. Describe the ping of death attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
2. Describe the Teardrop attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
3. Describe the SYN flooding attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
4. Describe the LAND attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
5. Describe the Smurf attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
6. Describe the Fraggle attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
7. Describe the Snork attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
8. Describe the OOB attack.
_____________________________________________________________________________________________
_____________________________________________________________________________________________
This page intentionally left blank

All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.