Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
6
Chapter
Investigating Internet Crime
Objectives
After completing this chapter, you should be able to:
• Understand Internet crimes
• Understand Internet forensics
• Understand DNS record manipulation
• Examine information in cookies
• Switch URL redirection
• Download a single page or an entire Web site
• Understand e-mail header forging
• Understand and read HTTP headers
Key Terms
DNS root name servers a series of 13 name servers strategically located around the world to
provide the names and IP addresses of all authoritative top-level domains
Ephemeral something that is transient or short lived in nature, as in network evidence, or
ephemeral ports (ports above the well-known ports [0–1023] that are temporarily assigned for
application communication)
Grooming the act of trying to build a relationship with children to gain their trust for
illicit purposes
Case Example
A Kelowna, British Columbia, man was arrested after a two-year investigation into an international Internet fraud case. The Calgary Police Service and Royal Canadian Mounted Police conducted
the investigation. The victims were defrauded for millions of dollars through Internet auctions for vintage automobiles. The investigation shows that these Internet frauds were part of a larger scheme where victims were attracted into bidding on Internet auctions for vintage automobiles.
6-1
6-2
Chapter 6
The victims sent tens of thousands of dollars through online transfer to bank accounts held in Calgary.
But they would either fail to receive the purchased vehicle or receive a vehicle that was not the same as the item purchased. The money that was sent by the victims to the holding company bank accounts was then directed elsewhere.
Introduction to Investigating Internet Crime
This chapter focuses on investigating Internet crimes. It starts by describing the different types of Internet crimes. It then discusses the different forensic methods and tools investigators use when investigating Internet crimes.
Internet Crimes
Internet crimes are crimes committed over the Internet or by using the Internet. The executor or perpetrator commits criminal acts and carries out wrongful activities on the Web in a variety of ways.
The following are some of the different types of Internet crimes:
• Phishing: Phishing is an e-mail fraud method in which the perpetrator sends out official-looking e-mail to the possible victims, pretending to be from their ISP, bank, or retail establishment, to collect personal and financial information. It is also known as “brand spoofing,” which is a trick to steal valuable information such as passwords, credit card numbers, Social Security numbers, and bank account
numbers that the authorized organization already has. During this process, users are asked by e-mail to visit a Web site to update their personal information.
• Identity theft: Identity theft is a crime where a person’s identity is stolen. The perpetrator then uses the victim’s personal data—such as Social Security number, bank accounts, or credit card numbers—to
commit fraud. Identity thieves obtain the names, addresses, and birth dates of victims, and may apply for loans in the name of their victims. In other instances, attackers acquire information such as usernames and passwords to login and steal valuable information and e-mails. Multiple methods are used to commit these frauds, such as purse or wallet theft, or posing as fake marketing executives. The Internet is the easiest and most effective way to carry out identity theft. It is simple for criminals to use a person’s credit card information to make purchases because transactions over the Internet occur quickly and without prior personal interaction. It is quite easy for any person to get another’s personal details if a victim is careless. Shoulder surfing is a method by which a thief looks over a person’s shoulder to see the person’s password or PIN. Identity thieves also use phishing to acquire personal information.
• Credit card fraud: In credit card fraud, attackers illegally use another’s credit card for purchasing goods and other services over the Internet. Attackers can steal personal details using different techniques such as phishing, eavesdropping on a user’s transactions over the Internet, or using social engineering techniques. In social engineering, an attacker extracts personal details from a user through
social interactions.
• Illegal downloading: Illegal downloading is an offense under the cyber laws. Downloading from an authorized Web site is acceptable; however, an unauthorized organization or individual cannot sell any product that is copyright protected. Illegal downloading affects the sales of that product. This type of crime is rampant because of the availability of tools for cracking software. Different types of services are provided for customer satisfaction but are misused. There are many issues that lead to illegal downloading. These include:
• Getting products at low cost or for free
• No personal information required
• Readily available throughout the world
The following are the types of items downloaded illegally most often:
• Music
• Movies
• Software
• Confidential or defense information
Internet Crimes
6-3
• Corporate espionage: Espionage means collecting information about an enemy or a competitor through spies. Corporate espionage is all about collecting information such as client lists to perpetrate frauds and scams in order to affect a rival financially. For this reason, companies focus specifically on such crimes and take special care to prevent such situations. Experts have sketched out a two-pronged strategy for overcoming this situation as follows:
• Knowledge of employees: Conducting background checks on new employees, and keeping a check on employees who have been assigned sensitive projects is crucial.
• Access control: Information about the business that is critical or important should not be stored on a computer that is connected to a network. Data that is highly critical should be encrypted.
• Child pornography: Child pornography is any work that focuses on children in a sexual manner.
The global community has realized that children are at risk and can suffer from negative effects because of pornographic exploitation. Rapidly expanding computer technology has given access to the production and distribution of child pornography. Not only girls and boys but also infants are becoming victims of such offensive activity. Pornographers make use of poor children, disabled minors, and sometimes neighborhood children for sexual exploitation. Children who are sexually exploited through pornography suffer from mental depression, emotional withdrawal, mood swings, fear, and anxiety.
• Luring children via chat rooms: Kidnappers often use chat rooms to turn children into victims. A kidnapper tries to build a relationship with children by showing them cartoons, interesting art clips, and offering them sweets. This is known as grooming. With many people of different ages, including children and youth, having access to the Internet, children are easily trapped and kidnapped because of their innocence and trust.
• Scams: The Internet is globally uniform and serves as the best-known market to promote businesses and services for customers around the world. Yet it is difficult to track and differentiate between legal and fake sellers on the Internet. Fake sellers cheat people by using various options available on the Internet, such as e-mail, chat rooms, and e-commerce sites.
• Cyber terrorism: Cyber terrorism is committed using computer and electronic attacks. Cyber terrorists can sit on one system and carry out attacks on computers worldwide.
• Creation and distribution of viruses and spam: A virus is a program that spreads from machine to machine, usually causing damage to each system. These are some forms of viruses:
• A polymorphic virus is one that produces varied but operational copies of itself.
• A stealth virus is one that, while active, hides the modifications it has made to files or boot records.
• A fast infector infects programs not just when they are run, but also when they are simply accessed.
• A slow infector will only infect files when they are created or modified.
The following are some of the reasons individuals create viruses:
• It is a way of attracting attention.
• Virus writers gain a sense of fulfillment from creating something that impacts a vast number
of people.
• It is motivated by financial gain.
• Virus writers may get excited about every bit of junk e-mail they get as a result of their virus.
The following are some of the forms in which a virus can be distributed:
• Removable disks: This includes floppy disks, CD-ROMs, and USB drives.
• Crack sites: These are sites that provide information on how to crack different applications and software.
• Unsecured sites: These are Web sites that do not use the HTTPS protocol.
• Flash greetings: This is the most common way of spreading a virus. This is a Flash animation or video that hides a virus.
• E-mail attachments: Users should not open attachments from unknown persons or Web sites.
• Downloading: Users should check Web sites to make sure they are legitimate before downloading.
6-4
Chapter 6
Internet Forensics
Internet forensics is the application of scientific and legally sound methods for the investigation of Internet crimes, whose focus ranges from an individual system to the Internet at large. The computer forensics expert works on a different level than the person he or she is investigating. Internet forensics experts use different tools and engage in the same set of activities as the person he or she is investigating. Internet forensics experts use a combination of advanced computing techniques and human intuition to uncover clues about people and computers involved in Internet crime. In Internet forensics, it is usually the case that forensics experts go through the same level of education and training as the hacker, but the difference is one of morals, not skill. Computer forensics deals with physical things, while Internet forensics deals with ephemeral factors. Something that is
ephemeral is transient or short lived in nature, as in network evidence, or ephemeral ports (ports above the well-known ports [0–1023] that are temporarily assigned for application communication).
Why Internet Forensics?
The large-scale and unregulated nature of the Internet provides a breeding ground for all kinds of scams and schemes. The purpose of Internet forensics is to uncover the origins of the spammers, con artists, and identity thieves that plague the Internet. Internet forensics techniques aid in unearthing the information that lies hidden in every e-mail message, Web page, and Web server on the Internet.
Internet forensics procedures are necessary because underlying Internet protocols were not designed to address the problems that complicate the process of identifying real sources of Internet crime. It is difficult to verify the source of a message or the operator of a Web site. Electronic evidence is fragile in nature and requires expert handling.
Goals of Investigation
The following are the goals of Internet forensic investigations:
• To ensure that all applicable logs and evidence are preserved
• To understand how the intruder is entering the system
• To discover why the intruder has chosen the target machine
• To gather as much evidence of the intrusion as possible
• To obtain information that may narrow the list of suspects
• To document the damage caused by the intruder
• To gather enough information to decide if law enforcement should be involved
Steps for Investigating Internet Crime
The following are the steps involved in investigating Internet crime:
1. Obtain a search warrant and seize the victim’s equipment.
2. Interview the victim.
3. Prepare bit-stream copies.
4. Identify the victim’s configuration.
5. Acquire the evidence.
6. Examine and analyze the evidence.
7. Generate a report.
Obtain a Search Warrant
The search warrant application should describe clearly that the investigators are to perform an on-site examination of the computer and network devices. The warrant needs to permit the seizure of all devices suspected to have been used in the crime, including the following:
• Victim’s equipment
• Router
Steps for Investigating Internet Crime
6-5
• Webcam
• Switch
• Other network device
Investigators should perform forensic examinations on all equipment permitted in the search warrant.
Interview the Victim
Investigators need to interview the victim about the incident. While interviewing the victim, the investigator should ask the following questions:
• What incident occurred?
• How did the intruder get into the network?
• What was the purpose of the attack?
• What are the major losses from this incident?
Prepare Bit-Stream Copies
Investigators need to prepare bit-stream copies of all storage devices attached to the affected computer, using a tool such as SafeBack. Investigators should never directly work on original copies of evidence.
Check the Logs
Investigators need to remember to do the following when checking logs:
• Check the offsite or remote logs.
• Check the system, e-mail and Web server, and firewall log files.
• Check log files of chat sessions if the attacker monitored or had conversations with the victim through IRC services.
Identify the Source of the Attack
Investigators need to trace the source of the attack. The following are some of the possible initial sources:
• Web site
• E-mail address
IP Addresses
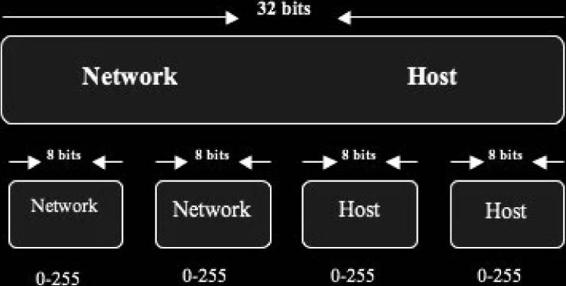
Each computer on the Internet has a unique IP address. Information is transmitted using the TCP/IP protocol suite. An IP address is a 32-bit integer value that is divided into four 8-bit integers separated by periods, as depicted in Figure 6-1. Each number is in the range from 0 to 255; these numbers can be used in different ways to identify the particular network and particular host on that network. An example of an IP address is 255.21.168.5.
The Internet Assigned Numbers Authority (IANA) allocates blocks of addresses to Regional Internet Registries (RIRs). The following are the five RIRs in the world:
• ARIN (American Registry for Internet Numbers)
• APNIC (Asia Pacific Network Information Centre)
• RIPE NCC (Réseaux IP Européens Network Coordination Centre)
• LACNIC (Latin American and Caribbean Internet Addresses Registry)
• AfriNIC (African Region Internet Registry)
Each of these RIRs doles out subblocks of IP addresses to the national registries and Internet service providers (ISP). They assign smaller blocks of addresses to smaller ISPs and single IP addresses to personal computers.
The following are the four different classes of IP addresses:
1.
Class A: This class is for large networks with many devices. It supports 16 million computers on each of 126 networks. The class A address range is from 10.0.0.0 to 10.255.255.255.
![]()
![]()
6-6
Chapter 6
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 6-1 An IP address is made up of four 8-bit integers.
2.
Class B: This is for medium-sized networks. It supports 65,000 computers on each of 16,000 networks.
The class B address range is from 172.16.0.0 to 172.31.255.255.
3.
Class C: This class is for small networks (fewer than 256 devices) on each of 2 million networks. The class C address range is from 192.168.0.0 to 192.168.255.255.
4.
Class D: These addresses are the multicast addresses. Class D ranges from 224.0.0.0 to 239.255.255.255.
Internet Assigned Numbers Authority (IANA)
The Internet Assigned Numbers Authority (IANA) plays an important role in the functioning of the Internet. It is responsible for coordinating one of the key elements that makes the Internet work.
IANA is the entity that oversees global IP address allocation, DNS root zone management, media types, and other Internet protocol assignments. IANA actively participates in regular meetings with Regional Internet Registries, top-level domain operators, and other relevant communities.
Internet Service Provider (ISP)
Internet service providers are the commercial vendors that provide Internet service in a region or a country. An ISP provides its users with e-mail accounts that allow them to communicate with other users by sending and receiving electronic messages through the ISP’s servers. ISPs can reserve blocks of IP addresses that they can assign to their users.
Trace the IP Address of the Attacker Computer
The steps to trace the IP address of an attacker computer are as follows:
1. Examine the e-mail header, and get the IP address of the attacker’s system.
2. Access a Web site that allows users to find out IP address information.
3. Use an IP address locating tool, such as WhoisIP, to find out the location of the attacker.
Domain Name System (DNS)
A domain name system translates the host name of a computer into an IP address. When a user enters a host name into a browser as a URL, the browser translates that name into its corresponding IP address. It uses that IP address to communicate with a Web server. The DNS server looks for the name in its database and gives the numeric address to the browser. For example, the domain name www.exampass.com might translate into 198.105.232.4.
A DNS server contains two tables of data and the software required to query them. The first table consists of a list of host names and their corresponding IP addresses. The second table consists of a list of IP addresses and
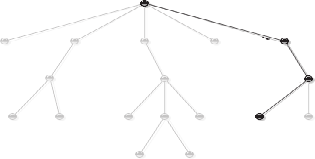
Steps for Investigating Internet Crime
6-7
'' ''
com
net
org
edu
it
sourceforge
openbsd
kernel-panic
users
dev
www
ca
de
www
www
ftp
Source: http://www.kernel-panic.it/openbsd/dns/dns2.html. Accessed 2/2007.
Figure 6-2 A domain name is made up of different hierarchical parts.
the host names to which they map. It is not possible to store the IP address of every computer on each server, so DNS distributes this data among a number of servers around the world. If a browser sends a request for a host name to the server, and if the server does not carry data for it, then that server forwards that request to other servers until it gets a response.
There is a series of 13 name servers strategically located around the world to provide the names and IP
addresses of all authoritative top-level domains. These servers are called the DNS root name servers. These servers implement the root namespace domain for the Internet.
Figure 6-2 is an example of a domain name. It is made up of the sequence www, kernel-panic, it, and the root’s null label, and is therefore written as www.kernel-panic.it.
DNS Records
DNS records are stored in zone files. Zone files are ASCII text files. A zone file contains full source information on a zone, including the domain name’s name server and mail server information, and is stored on the primary DNS server for the zone. For constructing zone files, two types of control entries are used, which simplifies constructing the file and standard resource records. The resource records describe the domain data present in the zone file. There are various types of standard resource records, but only the following two control statements:
• $INCLUDE <file name>: It identifies the data present in the zone file.
• $ORIGIN <domain name>: It is used to put more than one domain name in the zone file.
Resource Records The set of resource information associated with a particular name is composed of separate resource records (RRs). The order of RRs in a set is not significant and need not be preserved by name servers, resolvers, or other parts of the DNS.
A specific RR contains the following information:
• Owner: The domain name where the RR is found
• Type: an encoded 16-bit value that specifies the type of the resource in this resource record. Types refer to abstract resources. The following are the different types:
• A: A host address
• CNAME: Identifies the canonical name of an alias
• HINFO: Identifies the CPU and OS used by a host
• MX: Identifies a mail exchange for the domain
• NS: The authoritative name server for the domain
• PTR: For reverse lookup
• SOA: Identifies the start of a zone of authority
• SRV: Identifies hosts providing specific network services (like an Active Directory domain controller) 6-8
Chapter 6
• Class: an encoded 16-bit value that identifies a protocol family or instance of a protocol
• IN: The Internet system
• CH: The Chaos system
• TTL: The time to live of the RR. The TTL describes how long a RR can be cached before it should be discarded.
• RDATA: The type-dependent and sometimes class-dependent data that describes the resource
DNS Queries There are five types of queries that can be carried out on a WHOIS database: 1.
Registrar: Displays specific registrar information and associated WHOIS servers. It provides details about the potential domains that correlate to the target.
2.
Organizational: Displays all information related to a particular organization. This query can list all known instances associated with the particular target and the number of domains associated with
the organization.
3.
Domain: Provides information about a specific domain. A domain query arises from information gathered from an organizational query. An attacker can use a domain query to find the address, domain name, phone number of the administrator, and the system domain servers of the company.
4.
Network: Provides information about a network with one IP address. Network enumeration can help ascertain the network block assigned or allotted to the domain.
5.
Point of contact (POC): Displays information about personnel that deal with administrative, technical, or billing accounts.
If an organization is a high-security organization, it can opt to register a domain in the name of a third party, as long as that party agrees to accept responsibility. The organization must also take care to keep its public data updated and relevant for faster resolution of any administrative or technical issues. The public data is available only to the organization that is performing the registration, and that entity is responsible for keeping it current.
DNS Record Manipulation DNS servers cache recent data for fast retrieval. DNS poisoning involves damag-ing a server’s DNS table. Using this technique, an attacker replaces the IP address of a system with the address of a system owned by the attacker. Then, worms, viruses, and other malware programs can be downloaded onto the user’s system, or the attacker can steal the user’s personal information.
Defending against DNS Attacks The first line of defense for any target system is proper configuration and implementation of its DNS. The system must refuse inappropriate queries, thereby blocking crucial information leakage.
Another best practice is to use more than one DNS, where one DNS caters to the external interface, and the other to the internal interface. This lets the internal DNS act like a proxy server, thus shielding the internal servers from leaking information to the outside.
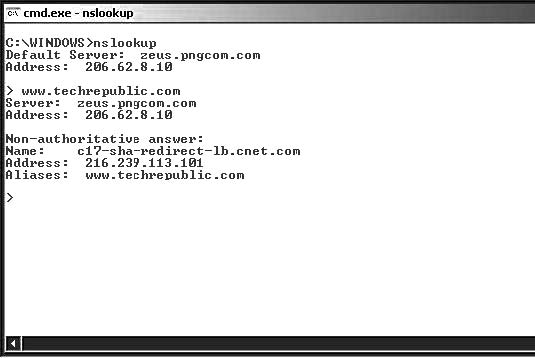
Tool: Nslookup
Nslookup is a valuable tool for querying DNS information for host name resolution. It is bundled with both UNIX and Windows and is accessed from the command prompt. When a user runs Nslookup, it shows the host name and IP address of the DNS server that is configured for the local system, and then it displays a command prompt for further queries. This is the interactive mode. Interactive mode allows the user to query name servers for information about various hosts and domains or to print a list of hosts in a domain.
When an IP address or host name is appended to the Nslookup command, it acts in noninteractive mode.
Noninteractive mode is used to print the name and requested information for a host or domain.
Nslookup allows the local machine to use a DNS server that is different from the default one by invoking the server command. By typing server <name> (where <name> is the host name or IP address of the server the user wants to use for future lookups), the system uses the given DNS server. The following is an example of Nslookup:
nslookup
Default Server: cracker.com
Address: 10.11.122.133
Server 10.12.133.144
Steps for Investigating Internet Crime
6-9
Host
Type
Value
google.com
NS
ns2.google.com
google.com
NS
ns1.google.com
google.com
NS
ns3.google.com
google.com
NS
ns4.google.com
google.com
MX
20 smtp2.google.com
google.com
MX
40 smtp3.google.com
google.com
MX
10 smtp1.google.com
google.com
NS
ns2.google.com
google.com
NS
ns1.google.com
google.com
NS
ns3.google.com
google.com
NS
ns4.google.com
ns2.google.com
A
216.239.34.10
ns1.google.com
A
216.239.32.10
ns3.google.com
A
216.239.36.10
ns4.google.com
A
216.239.38.10
smtp2.google.com
A
216.239.37.25
smtp3.google.com
A
216.239.33.26
smtp1.google.com
A
216.239.33.25
Table 6-1 These are the results of an Nslookup query for
google.com
Default Server: ns.targetcompany.com
Address 10.12.133.144
set type؍any
ls -d target.com
systemA 1DINA
10.12.133.147
1DINHINFO “Exchange MailServer”
1DINMX 10 mail1
geekL 1DINA
10.12.133.151
1DINTXT
“RH6.0”
Domain Name Delegation Nslookup employs the domain name delegation method when used on the local domain. For instance, typing hr.targetcompany.com queries for that particular name, and if it is not found, Nslookup will go up one level to find targetcompany.com. To query a host name outside the domain, a fully qualified domain name (FQDN) must be typed. This can be easily obtained from a WHOIS database query.
Table 6-1 shows the results of querying google.com. Figure 6-3 shows a screenshot of Nslookup.
Analysis of WHOIS Information
The WHOIS database contains information about Internet hosts, including the physical address, telephone number, and other contact information for the owner of the host.
Several operating systems provide a WHOIS utility. The following is the format to conduct a query from the command line:
whois -h <host name> <query string>
The user can specify several flags in the same query, though he or she can include only one flag from each query type. The following sections list some of the flags, by type.
6-10
Chapter 6
Figure 6-3 In interactive mode, Nslookup accepts host names and displays
information about those hosts.
Query by Record Type
n Network address space
a Autonomous systems
p Points of contact
o Organizations
c End-user customers
Query by Attribute
@ <domain name>
Searches for matches by the domain portion of an e-mail address
! <handle>
Searches for matches by handle or ID
. <name>
Searches for matches by name
Display Flags
؉ Shows detailed information for each match
Shows a summary only, even if there is only a single match
WHOIS Example
The following shows the results of a query for Google:
Domain Name: GOOGLE.COM
Registrar: ALLDOMAINS.COM INC.
Whois Server: whois.alldomains.com
Referral URL: http://www.alldomains.com
Name Server: NS2.GOOGLE.COM
Name Server: NS1.GOOGLE.COM
Name Server: NS3.GOOGLE.COM
Steps for Investigating Internet Crime
6-11
Name Server: NS4.GOOGLE.COM
Status: REGISTRAR-LOCK
Updated Date: 03-oct-2002
Creation Date: 15-sep-1997
Expiration Date: 14-sep-2011
The following shows the results of querying WHOIS for registrar ALLDOMAINS.COM INC:
Registrar Name: ALLDOMAINS.COM INC.
Address: 2261 Morello Ave, Suite C, Pleasant Hill, CA 94523, US
Phone Number: 925-685-9600
Email: registrar@alldomains.com
Whois Server: whois.alldomains.com
Referral URL: www.alldomains.com
Admin Contact: Chris J. Bura
Phone Number: 925-685-9600
Email: registrar@alldomains.com
Admin Contact: Scott Messing
Phone Number: 925-685-9600
Email: scott@alldomains.com
Billing Contact: Chris J. Bura
Phone Number: 925-685-9600
Email: registrar@alldomains.com
Billing Contact: Joe Nikolaou
Phone Number: 925-685-9600
Email: accounting@alldomains.com
Technical Contact: Eric Lofaso
Phone Number: 925-685-9600
Email: eric@alldomains.com
Technical Contact: Chris Sessions
Phone Number: 925-685-9600
Email: chris.sessions@alldomains.com
Technical Contact: Justin Siu
Phone Number: 925-685-9600
Email: justin.siu@alldomains.com
The following shows the results of querying WHOIS for name server NS2.GOOGLE.COM:
Server Name: NS2.GOOGLE.COM
IP Address: 216.239.34.10
Registrar: ALLDOMAINS.COM INC.
Whois Server: whois.alldomains.com
Referral URL: http://www.alldomains.com
As shown in the example, a normal query will give a user a lot of information, including contact information, name of ISP, and name servers, which can be resolved further into specific IP addresses.
6-12
Chapter 6
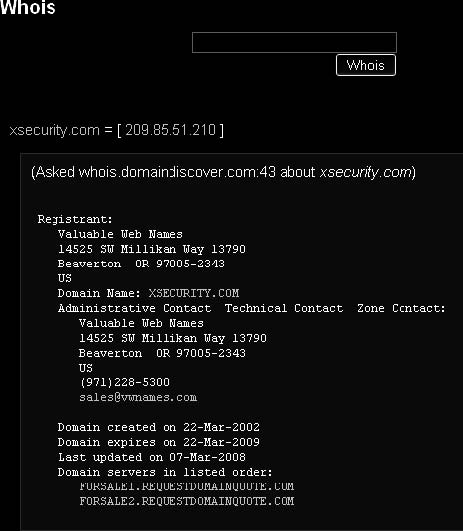
Source: http://www.samspade.org. Accessed 2/2007.
Figure 6-4 Samspade is a Web-based utility that shows the WHOIS information
for a given host.
Tool: Samspade
Samspade is a Web-based WHOIS query tool. Figure 6-4 shows a screenshot of the results of a Samspade query.
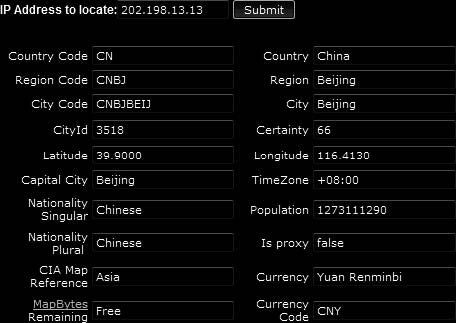
Tool: IP Address Locator
IP Address Locator allows a user to locate the geographical location of an IP address, as shown in Figure 6-5.
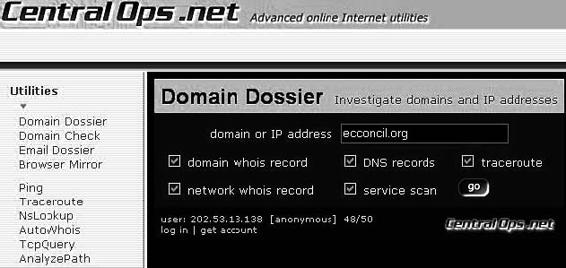
Tool: CentralOps.net
CentralOps.net is a Web-based collection of Internet utilities. The following are some of the tools included in the suite:
• Domain Dossier: Used to investigate domains and IP addresses
• Domain Check: Sees if a domain is available
• Email Dossier: Validates and investigates e-mail addresses
• Browser Mirror: Shows what a user’s browser reveals
• Ping: Sees if a host is reachable
• Traceroute: Traces the path from one server to another
• NsLookup: Looks up domain resource records
Steps for Investigating Internet Crime
6-13
Figure 6-5 IP Address Locator displays geographical information about an
IP address.
Figure 6-6 CentralOps.net contains a variety of tools that provide Internet information.
• AutoWhois: Gets WHOIS records for domains worldwide
• TcpQuery: Grabs Web pages, looks up domains, and more
• AnalyzePath: Does a simple, graphical Traceroute
Figure 6-6 shows a screenshot from CentralOps.net.
Tool: Traceroute
The Traceroute utility displays the path IP packets travel between two systems. It can trace the number of routers the packets travel through, calculate the round-trip transit time between two routers and, if the routers have DNS entries, display the names of the routers and their network affiliation and geographic location. Traceroute
6-14
Chapter 6
works by exploiting an IP feature called time to live (TTL). The TTL field indicates the maximum number of routers a packet may transit. Each router that handles a packet will decrement the TTL count field in the ICMP
header by one. When the count reaches zero, the packet will be discarded and an error message will be transmitted to the originator of the packet.
Traceroute sends out a packet destined for a user-specified destination. It sets the TTL field in the packet to one. The first router in the path receives the packet, decrements the TTL value by one, discards the packet, and sends a message back to the originating host to inform it that the packet has been discarded. Traceroute records the IP address and DNS name of that router, and sends out another packet with a TTL value of two.
This packet makes it through the first router and then times out at the next router in the path. This second router also sends an error message back to the originating host. Traceroute continues to do this, recording the IP address and name of each router until a packet finally reaches the target host or until it decides that the host is unreachable. A host may be unreachable for many reasons, including the presence of a packet-filtering device such as a firewall.
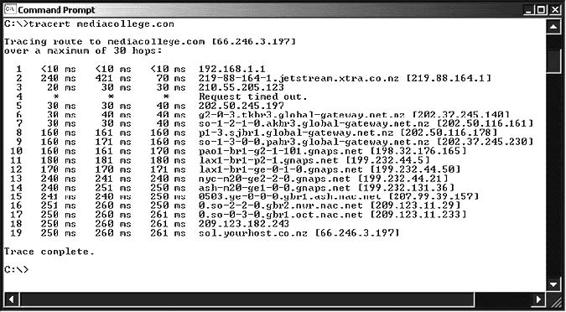
In the process, Traceroute records the round-trip transit time for each packet. The following example shows the results of running the tracert 216.239.36.10 command at the Windows command prompt:
Tracing route to ns3.google.com [216.239.36.10] over a maximum of 30 hops:
1
1262 ms
186 ms
124 ms
195.229.252.10
2
2796 ms
3061 ms
3436 ms
195.229.252.130
3
155 ms
217 ms
155 ms
195.229.252.114
4
2171 ms
1405 ms
1530 ms
194.170.2.57
5
2685 ms
1280 ms
655 ms
dxb-emix-ra.ge6303.emix.ae [195.229.31.99]
6
202 ms
530 ms
999 ms
dxb-emix-rb.so100.emix.ae [195.229.0.230]
7
609 ms
1124 ms
1748 ms
iar1-so-3-2-0.Thamesside.cw.net [166.63.214.65]
8
1622 ms
2377 ms
2061 ms
eqixva-google-gige.google.com [206.223.115.21]
9
2498 ms
968 ms
593 ms
216.239.48.193
10
3546 ms
3686 ms
3030 ms
216.239.48.89
11
1806 ms
1529 ms
812 ms
216.33.98.154
12
1108 ms
1683 ms
2062 ms
ns3.google.com [216.239.36.10]
Trace complete.
Figure 6-7 shows a screenshot from Traceroute.
Figure 6-7 Traceroute shows the route that packets travel over a network.
Steps for Investigating Internet Crime
6-15
Collect the Evidence
The investigator can gather the evidence using the following resources:
• Volatile and other important sources of evidence on live systems:
• Running processes (ps or the proc file system)
• Active network connections (netstat)
• ARP cache (arp)
• List of open files (lsof)
• Virtual and physical memory (/dev/mem, /dev/kmem)
• Computer forensic tools for data collection, including:
• Guidance Software’s EnCase ( www.guidancesoftware.com)
• AccessData’s Forensic Toolkit ( www.accessdata.com)
Examining Information in Cookies
Web sites use cookies to authenticate, track, and maintain specific information about users.
The following is the syntax of a Set-Cookie header:
Set-Cookie: <NAME>ϭ<CONTENT>; expiresϭ<TIMESTAMP>;
pathϭ<PATH>; domainϭ<DOMAIN>;
• Name: Identifies cookie
• Content: Contains a string of information that has some specific meaning to the server; the content is often encoded in some way
• Timestamp: Denotes the date, time, and duration of a cookie
• Path: Denotes the directory on the target site
• Domain: Defines hosts within a domain that the cookie applies to
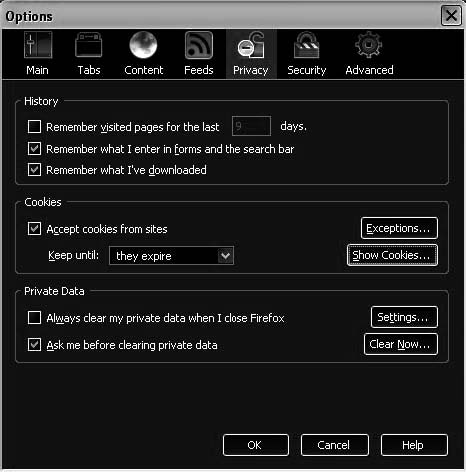
Viewing Cookies in Firefox The following are the steps for viewing cookies in Firefox: 1.
Go
to
Tools and then Options (Figure 6-8).
2.
Click
on
Show Cookies (Figure 6-9).
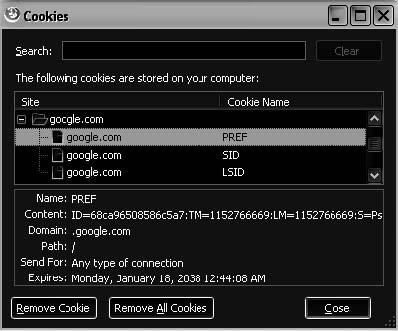
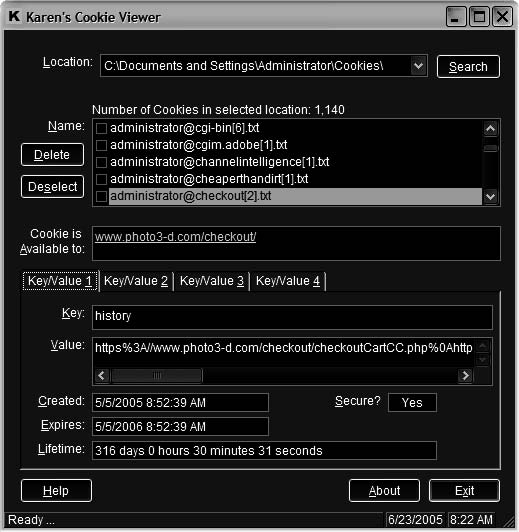
Tool: Cookie Viewer Cookie Viewer scans a system, looking for the cookies created by Internet Explorer, Netscape Navigator, and Firefox. It displays the data stored in each cookie. It can also delete any unwanted cookies stored by these browsers. Figure 6-10 shows a screenshot from Cookie Viewer.
URL Redirection
URL redirection is a technique where many URLs point to a single Web page. It is done by posting the address of one site and redirecting the traffic it receives to a target address. It can be done in two basic ways: 1.
Page-based redirection: In this method, the administrator inserts a special tag in a Web page on the proxy site that tells the browser to go to the target. The administrator first creates a Web page and then inserts a META tag into the HEAD section of the proxy site’s main page. The following is an example of this page:
• <meta http-equivϭ“refresh” contentϭ“0; URLϭhttp://www.craic.com”>
2.
Server-based redirection: In this method, the administrator adds a line to the Web server configuration file to intercept the request for a specific page and tell the browser to fetch it from the target location. The following are some of the ways an administrator can accomplish this:
• Adding a one-line Redirect directive to the file and restarting the server; the following is the syntax of this directive:
Redirect <old url> <new url>
6-16
Chapter 6
Figure 6-8 The Options window in Firefox allows a user
to look at cookies.
Figure 6-9 Firefox organizes cookies by the site they come from.
Steps for Investigating Internet Crime
6-17
Source: http.//www.karenware.com/powertools/ptcookie.asp. Accessed 2/2007.
Figure 6-10 Cookie Viewer allows a viewer to see the contents of a cookie.
• Creating a Web page from a server-side script (generally in Perl or PHP) and including a
Location header. This method is widely used by phishing Web sites. The following is an example
of this header:
Location:
http://www.google.com
Sample JavaScript for Page-Based Redirection
var version ϭ navigator.appVersion; // sets variable ϭ browser version
if (version.indexOf(“MSIE”) >ϭ -1) // checks to see if using IE
{
window.location.hrefϭ“ie.htm” /* If using IE, it shows this page replace ie.htm
with page name */
}
else window.open(“other.htm”, targetϭ“ _ self”) /* else open other page replace
other.html with page name */
Embedded JavaScript
JavaScript is an object-oriented dynamic scripting language. It is used in millions of Web pages and server applications to perform specific tasks such as opening pop-up windows or submitting form information.
6-18
Chapter 6
A developer can insert JavaScript into a Web page using the following syntax:
<SCRIPT
LANGUAGEϭ“JavaScript”>
<!—comment about script
[code to perform some action]
// end script hiding -->
</SCRIPT>
The following are some of the ways attackers use embedded JavaScript:
• Hide source HTML for a page: The escape command hides HTML and/or JavaScript from other people.
The following is an example:
<script
languageϭ“javascript”>
document.write( escape( ‘HTML file name’ ) );
</script>
• Manipulate the URL displayed in the status bar and browser history.
Downloading a Single Page or an Entire Web Site
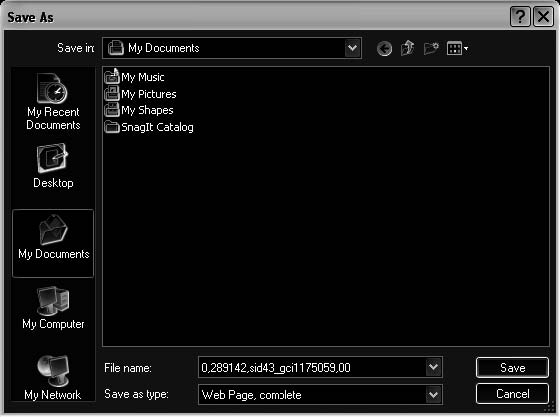
To save a page from Firefox, a user needs to choose File and then Save Page As, which brings up the window shown in Figure 6-11.
The following tools are available for saving an entire Web site:
• Grab-a-Site
• SurfOffline
• My Offline Browser
Tool: Grab-a-Site
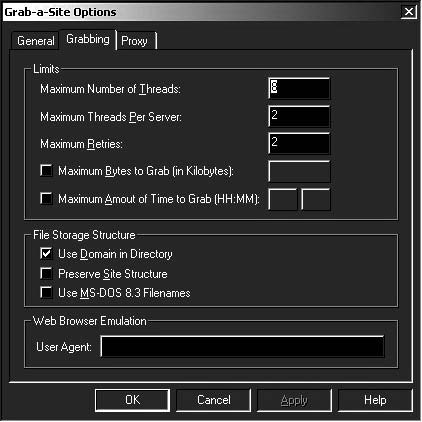
Grab-a-Site is a file-based offline browser that allows a user to grab complete sections of the World Wide Web.
When a user grabs a site, it is downloaded onto the user’s hard drive. The user can tell Grab-a-Site specifically which sites to grab and which sites to exclude, using filters.
The following are some of the features of Grab-a-Site:
• Grabs every movie (MOV, AVI), picture (JPG), document (PDF), program (EXE), or archive (ZIP) file from a site
Figure 6-11 A user can save a Web page in Firefox using this
Save As dialog.
Steps for Investigating Internet Crime
6-19
• Grabs from multiple Web sites at the same time
• Exports a Web site to burn it to a CD with Nero, Easy CD Creator, or some other CD-burning software
• Generates files so that CDs of Web sites will automatically run when inserted into a CD drive
• Stores files just like on a Web server, except the user will not need Web access to view the files Figure 6-12 shows a screenshot from Grab-a-Site.
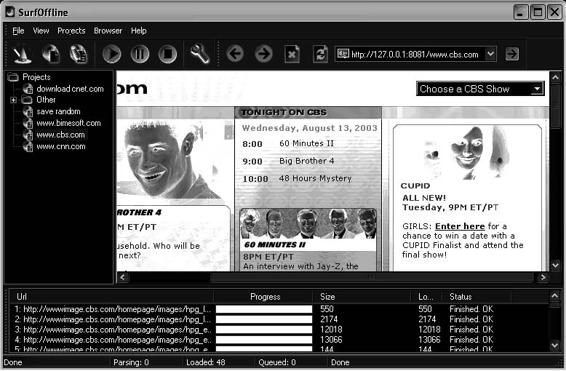
Tool: SurfOffline
SurfOffline is an offline browser that is capable of downloading up to 100 files simultaneously. The software can save a partial or complete copy of a Web site to a user’s hard drive in just a few minutes. Another important feature is a wizardlike interface that enables users to quickly set up downloading rules. The program supports HTTP, SSL (HTTPS), FTP, proxy servers, CSS, Macromedia Flash, and JavaScript parsing.
The following are some of the features of SurfOffline:
• Can download up to 100 files simultaneously
• Can download up to 200,000 files in one project
• Downloads entire Web sites (including images, video, audio)
• Prepares downloaded Web sites for writing to a CD or DVD
• Downloads password-protected Web pages and password-protected Web sites
Figure 6-13 shows a screenshot from SurfOffline.
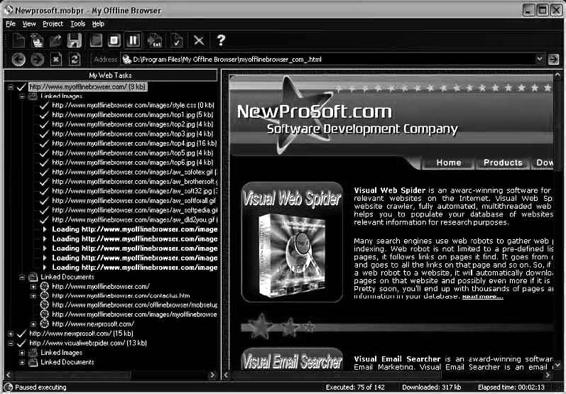
Tool: My Offline Browser
My Offline Browser is an offline browser that allows a user to automatically download and save entire Web sites, including all pages, images, Flash, and other files to the user’s hard disk. My Offline Browser changes all the links in the HTML code to relative local links, so a user can browse the downloaded Web sites offline using a regular Web browser or the built-in browser.
My Offline Browser is a bot that downloads a page and then goes to all the links on that page. It continues following links on the linked pages until it runs out of links.
Source: http://www.bluesquirrel.com/products/grabasite/. Accessed 2/2007.
Figure 6-12 A user can limit how much data Grab-a-Site
acquires from a site.
6-20
Chapter 6
Source: http://www.surfoffline.com/. Accessed 2/2007.
Figure 6-13 SurfOffline allows a user to view the Web pages that have been
downloaded from a site.
Source: http://www.newprosoft.com/offline-browser.htm. Accessed 2/2007.
Figure 6-14 My Offline Browser allows users to view Web pages without an
Internet connection.
The following are some of the features of My Offline Browser:
• Supports multithreaded downloading (up to 50 threads)
• Automatically reexecutes any task
• Supports proxy servers
• Limits downloading by URL filter, maximum crawling depth, and maximum file size
• Exports all URLs into a text file or an Excel file
Figure 6-14 shows a screenshot from My Offline Browser.
Steps for Investigating Internet Crime
6-21
Tool: Wayback Machine
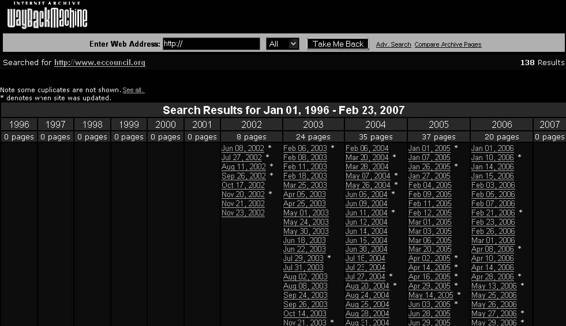
The Wayback Machine is a Web-based utility that allows users to browse through 85 billion Web pages archived from 1996 to just a few months ago.
To view the history of a Web site, perform the following steps:
1.
Go
to
www.archive.org.
2. Type in the Web address of a site or page.
3. Press Enter or click on Take Me Back.
4. Click on the desired date from the archive dates (Figure 6-15) available.
The resulting pages point to other archived pages at as close a date as possible.
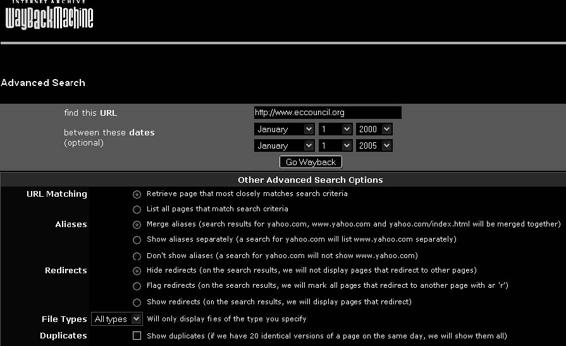
The Wayback Machine offers many advanced search options, as shown in Figure 6-16.
Figure 6-15 The Wayback Machine displays a list of archived Web pages by date
that a user can pick from.
Figure 6-16 The Wayback Machine provides a lot of different search options so
users can find the exact archived Web pages they want.
6-22
Chapter 6
Figure 6-17 A user can view the source of a Web page using Firefox and
a text editor.
Recovering Information from Web Pages
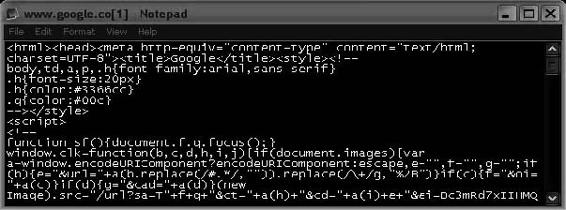
To recover the source code of a Web page, an investigator can do one of the following, depending on the browser (other browsers may have slightly different ways of doing this):
• Click View and select Source in Internet Explorer.
• Click View and select Page Source in Firefox.
Figure 6-17 shows the source of a page being viewed in Notepad.
Trace the E-Mail Addresses
The investigator needs to trace the e-mail addresses to determine the source of any e-mails involved in the investigation. Investigators can use this technique to find the source of spam e-mails or phishing e-mails, among other things. The following are some of the tools available for tracing e-mail addresses:
• Samspade ( www.samspade.org)
• VisualRoute ( http://visualroute.visualware.com)
• CentralOps.net ( www.centralops.net)
• Abika ( www.abika.com)
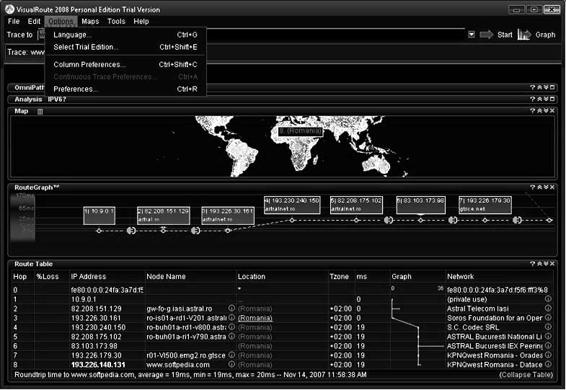
Tool: VisualRoute
VisualRoute is a graphical tool that determines where and how virtual traffic is flowing on the route between the desired destination and the location from which the user is trying to access it. It provides a geographical map of the route and performance information about each portion of that route.
VisualRoute has the ability to identify the geographical location of routers, servers, and other IP devices. This is valuable information for identifying the source of network intrusions and Internet abusers. It helps in establishing the identity of the originating network, identifying the Web software that a server is running, detecting routing loops, and identifying hosts.
VisualRoute provides WHOIS information about any host, including the site owner’s name, telephone number, and e-mail address, providing instant contact information for problem reporting.
Figure 6-18 shows a screenshot from VisualRoute.
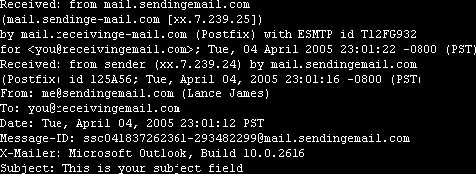
E-Mail Headers
Headers give the following information about an e-mail:
• Source
• Destination
• Subject of the e-mail
![]()
Steps for Investigating Internet Crime
6-23
• Date
• Route
Figure 6-19 shows part of an e-mail header.
E-Mail Header Forging The following are the steps to forge e-mail headers:
1. Open a command prompt.
2.
Find out the name of the ISP’s mail server from the e-mail client settings (for example, mail.isp.com or smtp.isp.com).
3. Connect to the ISP, and type SMTP commands after the mail server responds.
Source: http://www.visualware.com. Accessed 2/2007.
Figure 6-18 VisualRoute shows a graphical representation of the route a packet
takes through the network.
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 6-19 E-mail headers contain information that allows an investigator to trace the source of the e-mail.
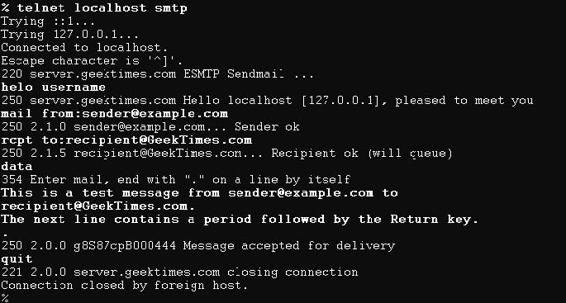
![]()
6-24
Chapter 6
4.
Continue with the fake address the mail will say it comes from. For example, to forge mail from XYZ@
abc.com, type mail from: XYZ@abc.com.
5.
Specify the recipient of the e-mail. For example, to send mail to your enemy, type rcpt to: yourenemy@
isp.com.
6.
Type
data and press Enter.
7. On the first line, type the subject (for example, subject: your subject) and press Enter twice.
8. Type the content of the message.
9. Type a period (.) and press Enter.
The server should respond, “Message accepted for delivery.”
Figure 6-20 shows a transcript of a telnet session where a user is forging e-mail headers.
HTTP Headers
The following are some of the different types of HTTP headers:
• Entity: Meta information about an entity body or resource
• General: Applicable for use both in request and in response messages
• Request: Sent by a browser or other client to a server
• Response: Sent by a server in response to a request
The following are some of the types of information headers include:
• Accept: Specifies which Internet media types are acceptable for the response and assigns preferences to them
• Accept-Charset [Request]: Specifies which character encodings are acceptable for the response and assigns preferences to them
• Accept-Encoding [Request]: Specifies the data format transformations, called content encodings
• Accept-Ranges [Response]: Indicates the server’s acceptance of range requests for a resource
• Age [Response]: Gives the sender’s estimate of the amount of time since the response (or its revalidation) was generated at the origin server
• Allow [Entity]: Lists the set of methods supported by the resource identified by the Request-URI Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 6-20 A user can forge e-mail headers by connecting directly to the
mail server and issuing SMTP commands.
Steps for Investigating Internet Crime
6-25
Figure 6-21 A user can view HTTP header information by
looking at the Page Info window in Firefox.
• Authorization [Request]: Consists of credentials containing the authentication information of the client for the realm of the resource being requested
• Cache-Control [General]: Specifies directives that must be obeyed by all caching mechanisms along the request/response chain
• Connection [General]: Specifies options that are desired for the particular connection and must not be communicated by proxies over further connections
• Content-Encoding [Entity]: Used as a modifier to the media type
• Content-Language [Entity]: Specifies the natural language(s) of the intended audience for the enclosed entity
• Content-Length [Entity]: Indicates the size of the entity body that is sent or that would have been sent if it had been requested
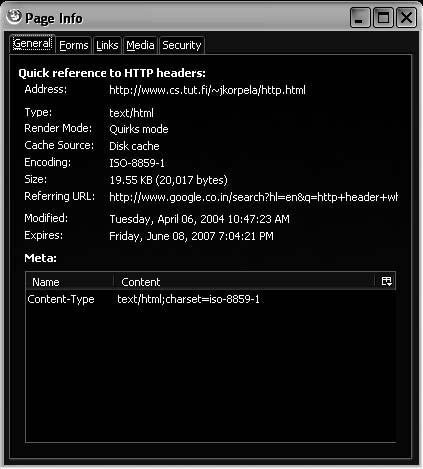
Viewing Header Information In Mozilla Firefox, an investigator can view header information by going to Tools and selecting Page Info (Figure 6-21).
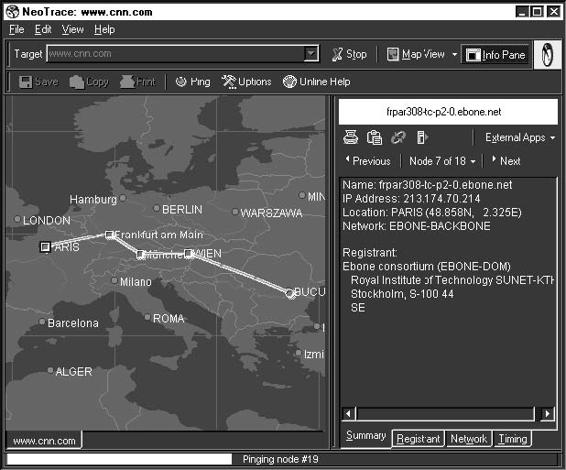
Tool: NeoTrace (now McAfee Visual Trace)
NeoTrace is a diagnostic and investigative tool that traces the network path across the Internet from the host system to a target system. Automatic retrieval of data includes registration details for the owner of each computer on the route (address, phone number, and e-mail address) and the network to which each node IP is registered.
Views of the data include a world map showing the locations of nodes along the route, a graph showing the relative response time of each node along the path, and a configurable list of node data. Figure 6-22 shows a screenshot from NeoTrace.
6-26
Chapter 6
Figure 6-22 NeoTrace shows the path of a packet using geographic visuals.
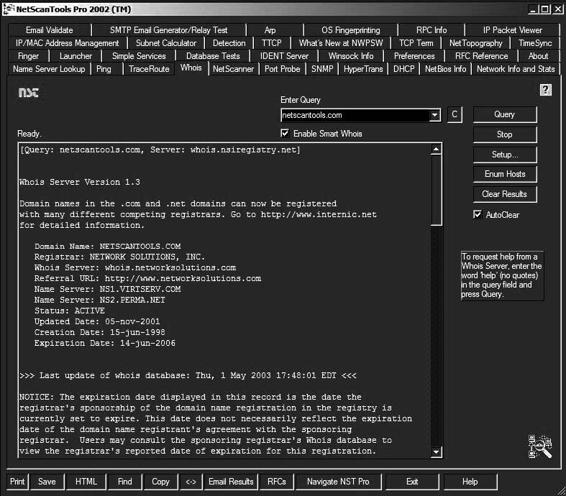
Tool: NetScan Tools
NetScan Tools is an advanced Internet information-gathering program for Windows. An investigator can use it to research IP addresses, host names, domain names, e-mail addresses, and URLs automatically or with manual tools.
The following are some of the benefits of NetScan Tools:
• Requires less time to gather information about Internet or local LAN users, network devices, IP addresses, ports, and many other network specifics
• Removes guesswork from Internet investigation by automating research requiring multiple network tools
• Produces clear, concise result reports in HTML or CSV format
Figure 6-23 shows a screenshot from NetScan Tools.
Generate a Report
The generated report must at least contain the following information:
• Name of the investigator
• List of router evidence
• Documents of the evidence and other supporting items
• List of tools used for investigation
• List of devices and setups used in the examination
Chapter Summary
6-27
Source: http://www.netscantools.com/. Accessed 2/2007.
Figure 6-23 The different tabs in NetScan Tools represent different Internet
utilities that a user can utilize to find information.
• Brief description of the examination steps
• Details about the findings:
• Information about the files
• Internet-related evidences
• Data and image analysis
• Conclusion of the investigation
Chapter Summary
■ Internet crimes are crimes committed over the Internet or by using the Internet.
■ Internet forensics is the application of scientific and legally sound methods for the investigation of Internet crimes.
■ URL redirection is a technique where many URLs point to a single Web page.
■ Attackers use embedded JavaScript to cover their tracks.
■ Cookies are used for authenticating, tracking, and maintaining specific information about users.
■ Nslookup is a process that converts a unique IP address into a domain name and is frequently used by Webmasters to research listings contained in server log files.

6-28
Chapter 6
Review Questions
1. What is the purpose of IANA?
___________________________________________________________________________________________
___________________________________________________________________________________________
2. What is an RIR?
___________________________________________________________________________________________
___________________________________________________________________________________________
3. What is URL redirection?
___________________________________________________________________________________________
___________________________________________________________________________________________
4. Describe the different types of DNS queries a user can make.
___________________________________________________________________________________________
___________________________________________________________________________________________
5. Describe the steps involved in forging e-mail headers.
___________________________________________________________________________________________
___________________________________________________________________________________________
6. What is embedded JavaScript, and how do attackers use it?
___________________________________________________________________________________________
___________________________________________________________________________________________
7. Describe the different classes of IP addresses.
___________________________________________________________________________________________
___________________________________________________________________________________________
8. What is the purpose of DNS?
___________________________________________________________________________________________
___________________________________________________________________________________________
Hands-On Projects
1. Visit the U.S. Department of Justice Web site ( www.usdoj.gov) and read about laws concerning Internet crimes.
2. Visit the National Conference for State Legislatures’ Web site and read about laws concerning Internet crimes at www.ncsl.org/programs/lis/cip/ciphome.htm.
3. Perform the following steps:
■ Navigate to Chapter 6 of the Student Resource Center.
■ Install and launch the Grab-a-Site program.
■ Pick a site to grab and download that site. Use various combinations of filters to see
the effects.

All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.