Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
7
Chapter
Tracking E-Mails and Investigating
E-Mail Crime
Objectives
After completing this chapter, you should be able to:
• Understand e-mail systems
• Understand e-mail clients
• Understand e-mail servers
• Understand e-mail crime
• Understand spamming
• Understand identity theft and chain e-mails
• Investigate e-mail crimes and violations
• Enumerate common e-mail headers
• Understand Microsoft Outlook
• Trace an e-mail message
• Understand U.S. laws against e-mail crime
Key Terms
Identity theft the willful act of stealing someone’s identity for monetary benefits
Internet Message Access Protocol (IMAP) an Internet protocol designed for accessing e-mail on a mail server
Mail bombing the intentional act of sending multiple copies of identical content to the same
recipient in order to hinder the functions of the recipient’s mail server
Mail storm a large flurry of e-mail sent through automated processes, often without
malicious intent
Mail user agent (MUA) a computer application used to manage e-mail; also called an
e-mail client
Post Office Protocol version 3 (POP3) an Internet protocol used to retrieve e-mail from a
mail server
7-1
![]()
7-2
Chapter 7
Simple Mail Transfer Protocol (SMTP) an Internet protocol for transmitting e-mail over IP networks Spam unsolicited commercial e-mail that is sent to a large number of e-mail addresses at the same time
Introduction to Tracking E-Mails and Investigating E-Mail Crime
The focus of this chapter is on how to investigate e-mail crimes and what countermeasures a user can take to prevent them. The chapter covers the different parts of an e-mail system before diving into a discussion of the different kinds of e-mail crimes. The chapter also discusses the U.S. laws concerning e-mail crime.
E-Mail Systems
E-mail is a term derived from the phrase electronic mail. Users can send and receive messages over an electronic communication system, such as the Internet.
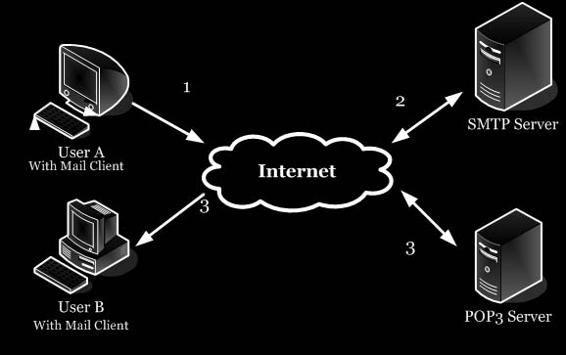
An e-mail system consists of both the servers that send and receive e-mails on the network and the e-mail clients that allow users to view and compose messages. Figure 7-1 is a simple depiction of an e-mail system.
An e-mail system works in the following way:
1.
A user—let’s call her Jane—composes a message using her mail user agent (MUA) and writes the e-mail address of her correspondent—Peter, in this example—and hits the Send button.
2.
Jane’s MUA formats the message in the Internet e-mail format and uses SMTP to send the message to the local mail transfer agent (MTA).
3. The MTA looks at the destination address provided in SMTP.
4.
The MTA looks for this domain name in the Domain Name System to find the mail exchange servers accepting messages for Peter’s domain.
5. The DNS server responds with a mail exchange record for Peter’s domain.
6. Jane’s SMTP server sends the message to the mail exchange server of Peter’s domain.
7.
Peter presses the Get Mail button in his MUA, which picks up the message using the Post Office Protocol (POP3). Peter then reads the message in his MUA.
E-Mail Client
An e-mail client, also known as a mail user agent (MUA), is a computer program for reading and sending e-mail.
There are a number of standalone e-mail clients, including the following:
• Microsoft Outlook
• Microsoft Outlook Express
• Eudora
• Pegasus
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 7-1 An e-mail system is made up of mail
servers and the clients that connect to them.
E-Mail Systems
7-3
• The Bat!
• Mozilla Thunderbird
There are also a number of Web-based e-mail clients, including the following:
• Hotmail
• Yahoo!
• Gmail
E-mail clients perform the following common functions:
• They display all the messages in a user’s inbox. The message header typically shows the date, time, subject of the mail, who sent the mail, and the mail’s size.
• A user can select a message and read the data in the message.
• A user can create e-mails and send them to others.
• A user can add a file attachment to a message and can also save any attachments received in other messages.
E-Mail Server
An e-mail server connects to and serves several e-mail clients. An e-mail server works in the following way:
• An e-mail server has a number of e-mail accounts; each person typically has one account.
• The server contains a text file for each account. This text file contains all the messages for that account.
• When a user presses the Send button in his or her e-mail client, the client connects to the e-mail server and passes the message and its accompanying information (including the sender and receiver) to the server.
• The server formats that information and attaches it to the bottom of the receiving user’s file. The server also saves the time, date of receipt, and subject line into the file.
• If the receiving user wants to see the message in an e-mail client, then he or she has to send a request to the server via the e-mail client.
SMTP Server
Simple Mail Transfer Protocol (SMTP) is an Internet protocol for transmitting e-mail over IP networks.
An SMTP server listens on port 25 and handles all outgoing e-mail. When a user sends an e-mail, the SMTP
server from that user’s host interacts with the receiving host’s SMTP server.
Consider an example where a user has an account with myicc.com, and he or she wants to send a mail to
john@mybird.com through a client such as Outlook Express.
The procedure works as follows:
• When the user clicks on the Send button, Outlook Express connects to the server of myicc.com at port 25.
• This client tells the SMTP server about the sender’s address, recipient’s address, and body of the message.
• The SMTP server breaks the recipient’s address into the following parts:
• The recipient’s name (john)
• The domain name ( mybird.com)
• This SMTP server contacts the DNS (Domain Name Service) server and asks about the IP address of the SMTP server for mybird.com.
• The SMTP server from myicc.com connects to the SMTP server for mybird.com using port 25 and sends the message to it. The SMTP server at mybird.com gets the message and transfers it to the POP3 server.
POP3 Servers
Post Office Protocol version 3 (POP3) is an Internet protocol used to retrieve e-mail from a mail server. A POP3
server handles incoming mails. The server contains one text file for each e-mail account. The POP3 server acts as an intermediary between the e-mail client and this text file. When a message comes in, the POP3 server attaches that message to the bottom of the recipient’s file. POP3 servers require usernames and passwords. An e-mail client connects with a POP3 server via port 110. The server opens the text file and permits the user to

7-4
Chapter 7
access it. It then deletes the messages from the server. A POP3 server can understand simple commands such as the following:
• USER: accept a user ID
• PASS: accept a password
• QUIT: quit the POP3 server
• LIST: list the messages and their sizes
• RETR: retrieve a message
• DELE: delete a message
IMAP Servers
Internet Message Access Protocol (IMAP) is an Internet protocol designed for accessing e-mail on a mail server.
IMAP servers are similar to POP3 servers. Like POP3, IMAP handles incoming mails. An e-mail client connects to an IMAP server via port 143. Unlike POP3, this protocol keeps e-mails on the server after a user has downloaded them. A user can also arrange e-mails into folders and store the folders on the server.
Importance of Electronic Records Management
Electronic records management is the field of management responsible for the efficient and systematic control of the creation, receipt, maintenance, use, and disposition of electronic records, including the processes for capturing and maintaining evidence of and information for legal, fiscal, administrative, and other business purposes.
The importance of electronic records management is as follows:
• It helps in the investigation and prosecution of e-mail crimes.
• It acts as a deterrent for abusive and indecent materials in e-mail messages.
• It helps in nonrepudiation of electronic communication so that someone cannot deny being the
source of a particular communication.
E-Mail Crime
E-mail crime is a serious offense. Over the past few years, e-mail has become the most preferred method of communication because of its ease of use and speed. But these advantages have made e-mail a powerful tool for criminals.
E-mail crimes and violations are identified by the cyber laws created by the government of the place from where the e-mail originates. For example, spamming is a crime in Washington State, but not in other states.
E-mail crime can be categorized in two ways: crimes committed by sending e-mails and crimes supported by e-mails.
The following are examples of crimes committed by sending e-mails:
• Spamming
• Fake e-mails
• Mail bombing
• Mail storms
The following are examples of crimes supported by e-mail:
• Selling narcotics
• Stalking
![]()
E-Mail Crime
7-5
Copyright © by
All rights reserved. Reproduction is strictly prohibited
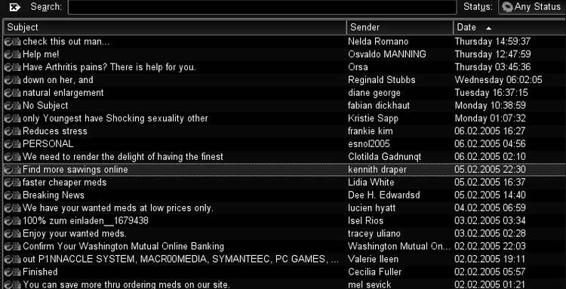
Figure 7-2 Spam mail often has a misleading subject line.
• Fraud
• Child pornography
• Child abduction
Spamming
Unsolicited commercial e-mail (UCE), or junk e-mail, can be defined as spam. Spam mail involves sending the same content to a large number of addresses at the same time. Spammers often obtain these addresses from Usenet postings, DNS listings, and Web pages. Spam mail fills mailboxes and often prevents users from accessing their regular e-mails. These regular e-mails start bouncing because the user exceeds his or her mail server quota.
Spammers hide their identities by forging e-mail headers. To avoid getting annoyed responses, spammers provide misleading information in the “From” and “Reply-To” fields. Figure 7-2 shows a list of spam e-mails.
Handling Spam
When a user receives spam, he or she can send a short notice to the domain administrator of the sender’s ISP to take immediate action and stop the nuisance. The user can also send a copy of the spam to the ISP.
If the spamming persists, the user can report it to the Federal Trade Commission (FTC). The user can send a copy of the spam message to spam@uce.gov. The FTC refers the spam mails stored in its database to law enforcement to pursue action against spammers. The FTC’s online complaint form is available at www.ftc.gov.
Any complaint should include the e-mail header. The header information is important for consumer protection agencies to follow up on spam complaints.
Network Abuse Clearinghouse at Abuse.Net The Network Abuse Clearinghouse is a mail-forwarding service that forwards abuse complaints to the system administrator for action. It is not a blacklist or spam analysis service. A domain name listed in abuse.net does not mean that the domain is involved in abusive activity.
The Network Abuse Clearinghouse contact database has contact addresses for more than 200,000 domains.
Responsible providers and domain managers submitted the domain contacts voluntarily, and abuse.net forwards messages to the listed addresses.
A user can utilize e-mail forwarding only if he or she has registered with the service. To register, a user sends
a mail to new@abuse.net and accepts the terms and conditions. After registration, mail can be sent to domain-
name@abuse.net, where domain-name is the name of the source responsible for the abuse. The Network Abuse
Clearinghouse automatically e-mails the message back to the best reporting addresses for that domain, and proper action can then be taken against the abusive domain.
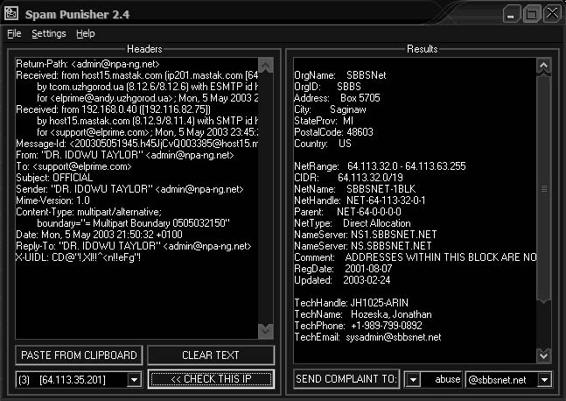
Tool: SPAM Punisher
This antispam tool makes the search for a spammer’s ISP address easy. It automatically detects forged addresses. SPAM Punisher supports various e-mail client programs such as Microsoft Outlook, AOL,
7-6
Chapter 7
Figure 7-3 SPAM Punisher can generate an e-mail complaint about spam and send
it to a spammer’s ISP.
Hotmail, and Eudora. SPAM Punisher generates and sends complaints to the ISP regarding spamming, as shown in Figure 7-3.
Tool: Spam Arrest
Spam Arrest protects accounts against spam. It uses challenge/response antispam technology. It allows a user to access his or her e-mail from any Web browser, without having to install any additional software. Spam Arrest works with a user’s existing e-mail address, including AOL, Hotmail, and Yahoo!. A user can also use Spam Arrest with Eudora, Thunderbird, and other standalone e-mail clients.
The following are some of the features of Spam Arrest:
• Supports POP3/IMAP
• Supports SMTP with autoauthorization
• Provides 1 GB of e-mail storage
• Provides multiple whitelist options, including authorizing incoming messages based on sender e-mail, sender domain, recipient e-mail, mailing list e-mail, and more
• Allows a user to create an unlimited number of disposable addresses to help control and categorize e-mail
• Provides antivirus protection
• Provides antiphishing protection
• Allows a user to forward his or her Spam Arrest inbox to another e-mail account or wireless device
• Provides e-mail delivery confirmation
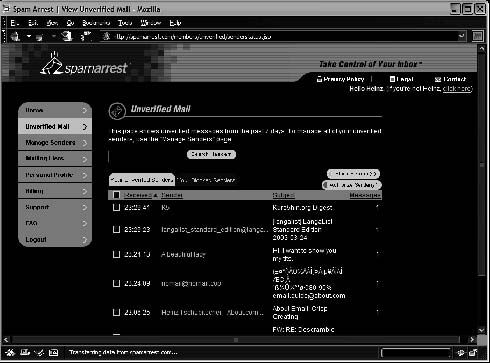
Figure 7-4 shows a screenshot from Spam Arrest.
Mail Bombing
Mail bombing is the intentional act of sending multiple copies of identical content to the same recipient. The primary objective behind mail bombing is to overload the e-mail server and degrade the communication system by making it unserviceable. Usually, a mail bomber and the victim are known to each other in some way. Mail

E-Mail Crime
7-7
Figure 7-4 Users can look through a Spam Arrest inbox to verify whether an e-mail
is spam or legitimate.
bombers also attack users whose newsgroup and forum postings do not agree with the mail bomber’s opinions.
The target for a mail bomber can be either a specific machine or a particular person. Mail bombing is more abusive than spamming because it not only sends mails in excessive amounts to a particular person, but it also prevents other users using the same server from accessing their e-mails.
Mail Storm
A mail storm occurs when computers start communicating without human intervention. The flurry of junk mail, often sent by accident, is a mail storm. Usage of mailing lists, autoforwarding e-mails, automated response, and the presence of more than one e-mail address are the various causes for a mail storm. Malicious software code, such as the “Melissa, I-Love-u” message, is also written to create mail storms. Mail storms hinder communication systems and also make them inoperable.
Crime via Chat Rooms
A chat room is a Web site or part of a Web site where a number of users, often with common interests, can communicate in real time.
Online instant messaging and chat rooms have benefited children, but they are also potential sources of sexual abuse. Pedophiles use chat rooms to sexually abuse children by establishing online relationships with them. After establishing a steady relationship, they introduce children to pornography by providing images and videos that have sexually explicit material. Pedophiles exploit children for cybersex, which may lead to physical abuse.
7-8
Chapter 7
Identity Theft
Identity theft is the willful act of stealing someone’s identity for monetary benefits. Criminals obtain personal information about a person and misuse it, causing heavy financial loss to the victim. False shopping sites and spam mails that contain irresistible offers are common means used to obtain a victim’s credit card numbers. Criminals not only withdraw huge amounts from the victim’s bank accounts but can also make the victim bankrupt.
Chain E-Mails
A chain e-mail is a message that is sent successively to several e-mail users. It directs the recipients to circulate multiple copies of the e-mail, often promising rewards for this compliance, such as a blessing or good luck.
A chain e-mail can be in the form of sympathy or threats.
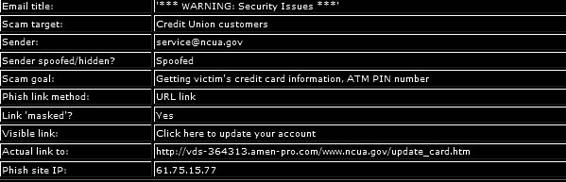
Phishing
Phishing has emerged as an effective method to steal the personal and confidential data of users. It is an Internet scam that tricks users into divulging their personal and confidential information by making false statements and enticing offers. Phishers can attack users through mass mailings to millions of e-mail addresses around the world.
A successful phishing attack deceives and convinces users with fake technical content and social engineering practices. The major task for phishers is to make the victims believe in the phishing sites. Most phishing attacks are initiated through e-mails, where the user gets an e-mail that prompts him or her to follow a link given in the e-mail. This link leads to a phishing Web site, though the e-mail says otherwise. The e-mail may contain a message stating that a particular transaction has taken place on the user’s account, and a link is provided to check his or her balance. Or the e-mail may contain a link to perform a security check on the user’s account.
E-Mail Spoofing
E-mail spoofing is the process of altering e-mail headers so that an e-mail appears to be from someone or somewhere other than the original source. Spammers and phishers use this technique to conceal the origin of their email messages. The following are the e-mail header fields that are most often changed during e-mail spoofing:
• From
• Return-Path
• Reply-To
Investigating E-Mail Crimes and Violations
The steps involved in investigating e-mail crimes and violations are as follows:
1. Examine an e-mail message.
2. Copy the e-mail message.
3. Print the e-mail message.
4. View the e-mail headers.
5. Examine any attachments.
6. Trace the e-mail.
Obtaining a Search Warrant and Seizing the Computer and E-Mail Account
A search warrant application should include the proper language to perform on-site examination of the suspect’s computer and the e-mail server used to send the e-mails under investigation. The investigator should seize all Investigating E-Mail Crimes and Violations
7-9
computers and e-mail accounts suspected to be involved in the crime. Investigators can seize e-mail accounts by just changing the existing password of the e-mail account either by asking the suspect his or her password or from the mail server.
Examining E-Mail Messages
After it is established that an e-mail crime has been committed, investigators require evidence to prove the crime.
To obtain evidence, investigators need access to the victim’s computer so they can examine the e-mail that the victim received. As with all forensic investigations, analysis should not be done on the original data. The investigator should image the victim’s computer first. Then, the investigator should physically access the victim’s computer and use the same e-mail program the victim used to read the e-mail. If required, the investigator can get the username and password from the victim and log on to the e-mail server. If physical access to a victim’s computer is not feasible, the investigator should instruct the victim to open and print a copy of an offending message, including the header. The header of the e-mail message has a key role to play in e-mail tracing because it contains the unique IP address of the server that sent the message.
Copying an E-Mail Message
An e-mail investigation can be started as soon as the offending e-mail message is copied and printed. Any e-mail client will allow an investigator to copy e-mail messages from the inbox folder to a floppy disk.
The following are the steps to copy an e-mail message using Microsoft Outlook or Outlook Express: 1. Insert a formatted floppy disk into the floppy disk drive.
2. Navigate to My Computer or Windows Explorer to view the floppy disk.
3. Start Microsoft Outlook or Outlook Express.
4. Click the folder that contains the offending message, keeping the Folders list open.
5. Resize the Outlook window to see both the message to be copied and the floppy disk contents.
6. Drag the message from the Outlook window to the floppy disk.
E-mail programs, such as Pine, that run from the command line have a command to copy an e-mail message.
Printing an E-Mail Message
The next step after copying the e-mail message is to print it. The following steps provide guidelines for printing an e-mail message in Outlook Express:
1. Go to My Computer or Windows Explorer and get the copy of the e-mail message received by
the victim.
2. Open the message in the e-mail program.
3. Go to the File menu and click Print.
4. After selecting the settings for printing in the dialog box, click the Print button.
For command line e-mail clients, an investigator can open the e-mail message and select the print option.
Obtaining a Bit-By-Bit Image of E-Mail Information
Investigators should make a bit-by-bit image of all the folders, settings, and configuration for the e-mail account for further investigation. They should then use MD5 hashing on the image to maintain integrity of the evidence.
Viewing and Copying E-Mail Headers in Microsoft Outlook
The procedure to view and copy headers in Microsoft Outlook is as follows:
1. Launch Outlook and open the copied e-mail message.
2. Right-click on the message and click on Options.
3. Right-click in the Internet Headers box and choose Select All.
4. Copy the header text and paste it into any text editor.
5. Save the text file.
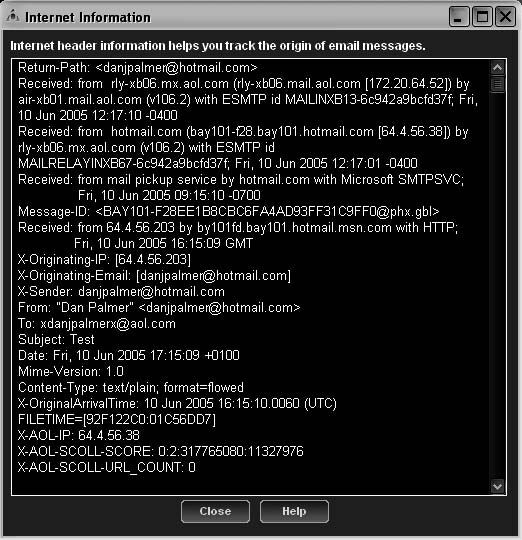
7-10
Chapter 7
Figure 7-5 This window shows the headers for an AOL e-mail.
Viewing and Copying E-Mail Headers in AOL
The procedure to view and copy headers in AOL is as follows:
1. Launch the program.
2. Open the received message.
3. Click the DETAILS link. This brings up the window in Figure 7-5.
4. Select the header text and copy it.
5. Paste the text into any text editor and save the file.
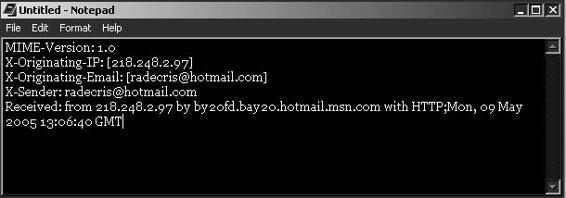
Viewing and Copying E-Mail Headers in Hotmail
The procedure to view and copy headers in Hotmail is as follows:
1. Logon to Hotmail.
2. Right-click on the received message.
3. Click View message source.
4. Select the header text and copy it.
5. Paste the text into any text editor (Figure 7-6) and save the file.
Viewing and Copying E-Mail Headers in Gmail
The procedure to view and copy headers in Gmail is as follows:
1. Logon to Gmail.
2. Open the received mail.
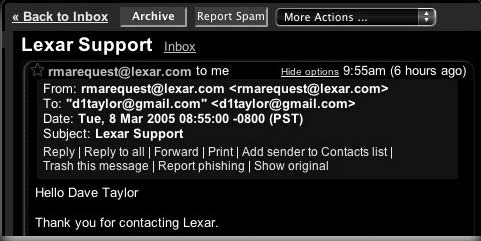
Investigating E-Mail Crimes and Violations
7-11
Figure 7-6 An investigator can copy Hotmail e-mail headers to a text file.
Figure 7-7 Showing the original e-mail in Gmail displays the headers.
3. Click on the More option.
4. Click on Show original (Figure 7-7).
5. Select the header text and copy it.
6. Paste the text into any text editor and save the file.
Viewing and Copying E-Mail Headers in Yahoo! Mail
The procedure to view and copy headers in Yahoo! Mail is as follows:
1. Logon to Yahoo! Mail.
2. Open the received mail.
3. Click on Full Header.
4. Select the header text and copy it (Figure 7-8).
5. Paste the text into any text editor and save the file.
Examining an E-Mail Header
An investigator can acquire the IP address of the sender of an e-mail by examining the e-mail header. The e-mail header also provides additional information like the date and time the message was sent and any attachments included with the message.
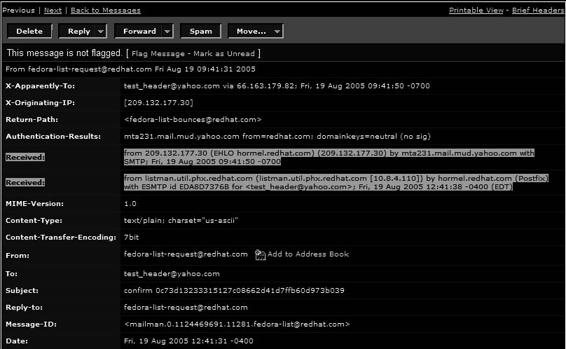
7-12
Chapter 7
Figure 7-8 Copying the headers from Yahoo! Mail is a simple task.
Mail originated from this IP address
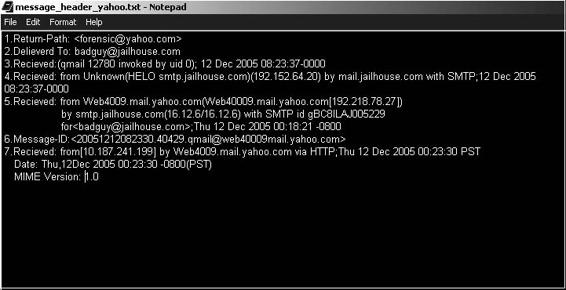
Figure 7-9 Line 7 shows the address of the originating e-mail server.
The message header can provide significant information if examined properly. Figure 7-9 shows a sample message header with added line numbers to explain the different parts of the header. This header was generated by qmail, a UNIX mail system.
Information about the e-mail’s origin is contained in lines 1, 3, 4, and 5. The return path for sending a reply is indicated in line 1. The return path information is not reliable because it can be faked easily.
The recipient’s e-mail address is specified in line 2. The e-mail service provider can verify the e-mail address.
An investigator can authenticate the victim’s address by cross-checking it with the bill or log provided by the service provider.
Line 3 displays a header identifying it as a qmail header followed by an identifier.
Line 4 indicates the IP address of the e-mail server that was used to send the offending message.
Line 5 contains the name and IP address of the e-mail server exploited to connect to the victim’s e-mail server.
The piece of information crucial for tracing the origin of the e-mail origin is contained in lines 6 and 7. Line 6
illustrates a unique message ID that is assigned by the sending server. Line 7 shows the IP address of the e-mail server along with the date and time. Line 7 also specifies the protocol used to send the e-mail.
Investigating E-Mail Crimes and Violations
7-13
If a message has an attachment, the name of the attachment is shown in the header itself. Attachments serve as supporting evidence in an investigation. An investigator should search for the attachment on the victim’s hard drive. After retrieving the file, the investigator can copy it to preserve the evidence.
“Received” Headers
“Received” headers provide a detailed log of a message’s history, and they make it possible to draw some conclusions about the origin of an e-mail, even when other headers have been forged.
If, for instance, the machine turmeric.com, whose IP address is 104.128.23.115, sends a message to mail.
bieberdorf.edu, but falsely says HELO galangal.org, the resultant “Received” line might start like this: Received: from galangal.org ([104.128.23.115]) by mail.bieberdorf.edu (8.8.5)...
Forging “Received” Headers A common trick e-mail forgers use is to add spurious “Received” headers before sending the offending mail. This means that the hypothetical e-mail sent from turmeric.com might have
“Received” lines that look something like this:
Received: from galangal.org ([104.128.23.115]) by mail.bieberdorf.edu (8.8.5)...
Received: from nowhere by outer space (8.8.3/8.7.2)...
Received: This is a header. Move along.
The last two lines are complete nonsense, written by the sender and attached to the message before it was sent. Since the sender has no control over the message once it leaves turmeric.com, and “Received” headers are always added at the top, the forged lines have to appear at the bottom of the list.
This means that someone reading the lines from top to bottom, tracing the history of the message, can safely throw out anything after the first forged line; even if the “Received” lines after that point look plausible, they are guaranteed to be forgeries.
Common Headers
The following is a list of some common headers:
• Content-Transfer-Encoding: This header relates to MIME, a standard way of enclosing nontext content in e-mail. It has no direct relevance to the delivery of mail, but it affects how MIME-compliant mail programs interpret the content of the message.
• Content-Type: This is another MIME header, telling MIME-compliant mail programs what type of content to expect in the message.
• Date: This header specifies a date, normally the date the message was composed and sent. If the sender’s computer omits this header, it might conceivably be added by a mail server or even by some other machine along the route.
• Errors-To: This header specifies an address for mailer-generated errors, such as bounce messages, to go to (instead of the sender’s address). This is not a particularly common header, as the sender usually wants to receive any errors at the sending address, which is what most mail server software does by default.
• From: This is whom the message is from.
• Apparently-to: Messages with many recipients sometimes have a long list of headers of the form
“Apparently-to: rth@bieberdorf.edu” in them. These headers are unusual in legitimate mail; they are normally a sign of a mailing list, and in recent times mailing lists have generally used software sophisticated enough not to generate a giant pile of headers.
• Bcc: This stands for “blind carbon copy.” If this header appears in incoming mail, something is wrong.
This header is used to send copies of e-mails to people who might not want to receive replies or to appear in the headers. Blind carbon copies are popular with spammers, since they confuse many
inexperienced users who get e-mail that does not appear to be addressed to them.
• Cc: This stands for “carbon copy.” This header specifies additional recipients beyond those listed in a
“To” header. The difference between “To” and “Cc” is essentially connotative; some mailers also deal with them differently in generating replies.
• Comments: This is a nonstandard, free-form header field. Some mailers add this header to identify the sender; however, spammers often add it by hand (with false information).
7-14
Chapter 7
• Message-Id: This header specifies a more-or-less unique identifier assigned to each message, usually by the first mail server it encounters. Conventionally, it is of the form “foo@mailserv.com,” where the
“foo” part could be absolutely anything and the second part is the name of the machine that assigned the ID. Sometimes, but not often, the “foo” part includes the sender’s username. Any e-mail in which the message ID is malformed (e.g., an empty string or no @ sign) or in which the site in the message ID
is not the real site of origin is probably a forgery.
• In-Reply-To: A Usenet header that occasionally appears in mail, the “In-Reply-To” header gives the message ID of the message to which it is replying. It is unusual for this header to appear except in e-mail directly related to Usenet; spammers have been known to use it, probably in an attempt to evade filtration programs.
• MIME-Version: Another MIME header, this one specifies the version of the MIME protocol that was used by the sender.
• Newsgroups: This header appears only in e-mail that is connected with Usenet—either e-mail copies of Usenet postings or e-mail replies to postings. In the first case, it specifies the newsgroup(s) to which the message was posted; in the second, it specifies the newsgroup(s) in which the message being replied to was posted.
• Organization: This is a completely free-form header that normally contains the name of the organization through which the sender of the message has net access. The sender can generally control this header, and silly entries are commonplace.
• Priority: This is an essentially free-form header that assigns a priority to the mail. Most software ignores it. It is often used by spammers in an attempt to get their messages read.
• References: The “References” header is rare in e-mail except for copies of Usenet postings. Its use on Usenet is to identify the upstream posts to which a message is a response; when it appears in e-mail, it is usually just a copy of a Usenet header. It may also appear in e-mail responses to Usenet postings, giving the message ID of the post being responded to as well as the references from that post.
• Reply-To: This header specifies an address for replies to go to. Though this header has many legitimate uses, it is also widely used by spammers to deflect criticism. Occasionally, a naive spammer will actually solicit responses by e-mail and use the “Reply-To” header to collect them, but more often the address specified in junk e-mail is either invalid or an innocent victim.
• Sender: This header is unusual in e-mail (“X-Sender” is usually used instead), but appears occasionally, especially in copies of Usenet posts. It should identify the sender; in the case of Usenet posts, it is a more reliable identifier than the “From” line.
• Subject: This is a completely free-form field specified by the sender to describe the subject of the message.
• To: This header specifies whom the message is to. Note that the “To” header does not always contain the recipient’s address.
X-headers is the generic term for headers starting with a capital X and a hyphen. The convention is that X-headers are nonstandard and provided for information only, and that, conversely, any nonstandard informative header should be given a name starting with X-. This convention is frequently violated. The following are some common X-headers:
• X-Confirm-Reading-To: This header requests an automated confirmation notice when the message is received or read. It is typically ignored, though some software acts on it.
• X-Distribution: In response to problems with spammers using his software, the author of Pegasus added this header. Any message sent with Pegasus to a sufficiently large number of recipients has a header added that says “X-Distribution: bulk.” It is explicitly intended as something for recipients to filter against.
• X-Errors-To: Like “Errors-To,” this header specifies an address for errors to be sent to.
• X-Mailer: This is a free-form header field intended for the mail software used by the sender to identify itself (as advertising or whatever). Since much junk e-mail is sent with mailers invented for that purpose, this field can provide much useful fodder for filters.
• X-PMFLAGS: This is a header added by Pegasus; its semantics are nonobvious. It appears in any message sent with Pegasus, so it doesn’t obviously convey any information to the recipient.
Investigating E-Mail Crimes and Violations
7-15
Figure 7-10 The Outlook directory contains a user’s e-mail database.
• X-Priority: This is another priority field, used notably by Eudora to assign a priority (which appears as a graphical notation on the message).
• X-Sender: The usual e-mail analogue to the Sender: header in Usenet news, this header identifies the sender with greater reliability than the “From” header. In fact, it is nearly as easy to forge and should therefore be viewed with the same sort of suspicion as the “From” header.
• X-UIDL: This is a unique identifier used by POP for retrieving mail from a server. It is normally added between the recipient’s mail server and the recipient’s mail client; if mail arrives at the mail server with an “X-UIDL” header, it is probably junk.
Examining Additional Files
E-mail storage depends on the state of the client and server computers. Some e-mail programs permit the user to store e-mail on a server and some on the client computer. Various e-mail clients allow the user to save all his or her e-mail messages in a separate folder that can later be accessed from anywhere without logging on to the user’s e-mail client.
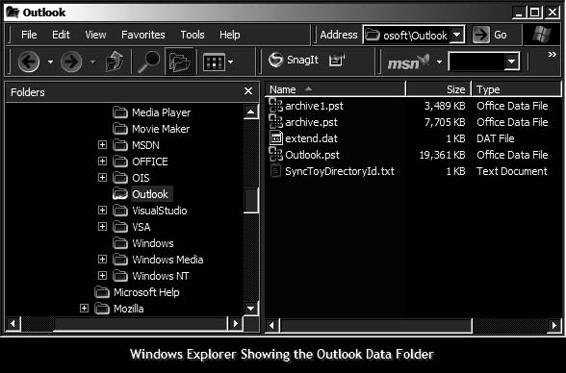
Microsoft Outlook
Microsoft Outlook acts like a personal information manager, maintaining all information related to e-mail.
The e-mail database is usually located in the <user home>\Local Settings\Application Data\Microsoft\Outlook directory. These are typically hidden files. Figure 7-10 shows the contents of this directory.
Microsoft Outlook gives the user the advantage to save all e-mail messages in the following two file locations:
• Personal e-mail file (.pst)
• Offline e-mail file (.ost)
Online E-Mail Programs
Online e-mail programs such as AOL, Hotmail, and Yahoo! leave the files containing e-mail messages on the computer. These files are stored in different folders such as History, Cookies, Temp, Cache, and Temporary Internet Folder. Investigators can use forensic tools to retrieve the folder for the respective e-mail client. Once the folder is retrieved, the investigator can open the files to find information about the suspect e-mails.
Personal Address Book
Another feature of e-mail programs that can prove to be useful is the personal address book. A suspect’s personal address book can become supporting evidence that can indicate the suspect’s involvement in a crime.

7-16
Chapter 7
Source: http://www.centralops.net. Accessed 2/2007.
Figure 7-11 This screenshot shows e-mail validation results from Email Dossier.
Examine the Originating IP Address
The following are the steps involved in examining the originating IP address:
1. Collect the IP address of the sender from the header of the received mail.
2. Search for the IP in the WHOIS database.
3. Look for the geographic address of the sender in the WHOIS database.
Tool: Email Dossier
Email Dossier is part of the CentralOps.net suite of online network utilities. It is a scanning tool that an investigator can use to check the validity of an e-mail address. It provides information about the e-mail address, including the mail exchange records of the e-mail address. This tool initiates SMTP sessions to check address acceptance, but it never actually sends e-mail. Figure 7-11 shows a screenshot from Email Dossier.
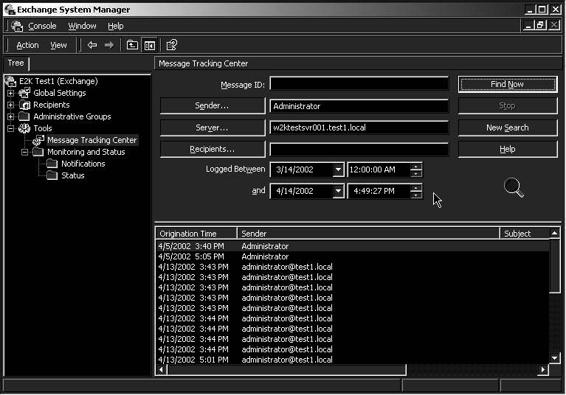
Tool: Exchange Message Tracking Center
This tool can help an investigator track a message’s path between servers, as well as determine when the user sent the message, to whom the user sent the message, and other important pieces of information.
Using the Exchange Message Tracking Center is fairly straightforward and is similar to searching through Active Directory. Most administrators should have no problem quickly finding messages they are looking for, provided that their logs date back far enough to support finding the message in question.
Figure 7-12 shows a screenshot from Exchange Message Tracking Center.
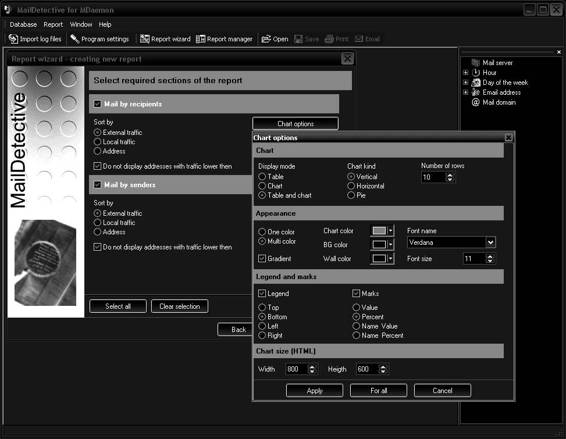
Tool: MailDetective
MailDetective is an effective tool for monitoring corporate e-mail usage in Microsoft Exchange Server. The following are some of the uses of MailDetective:
• Monitors e-mail usage to check for employees who use e-mail services for non-work-related communications
• Helps management cut down on costs incurred due to misuse of bandwidth
• Monitors mail server log files and gives detailed reports about business and private e-mails going to and from the corporate network
• Gives a report of the traffic distribution by users and e-mail addresses
Using Specialized E-Mail Forensic Tools
7-17
Figure 7-12 Exchange Message Tracking Center allows an administrator to search
for messages based on a number of criteria.
The following are some of the features of MailDetective:
• Built-in HTML browser
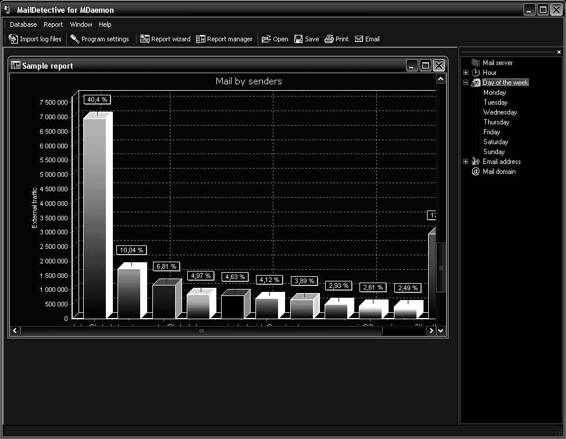
• Charts (Figures 7-13 and 7-14)
• Ability to export reports to HTML
• Ability to print reports directly from the built-in browser
• Ability to export reports to Microsoft Excel format
• Tools for automatic log file import and report creation
• Ability to send reports through e-mail
Examine Phishing
The following are the steps involved in examining phishing:
1. Search for any e-mails received that contain malicious links to Web sites.
2. Check the link in the phishing archive in the Honeytrap database tool (Figures 7-15 and 7-16).
Using Specialized E-Mail Forensic Tools
During e-mail investigation, an e-mail administrator has a key role to play in providing information such as log files and retrieving deleted files. An investigator also relies on forensic tools. Sophisticated forensic tools, such as AccessData’s Forensic Toolkit (FTK) and EnCase, are specially designed for data recovery from hard drives, while tools like FINALeMAIL and Sawmill are specifically built for e-mail recovery, including attachments recovery.
An investigator can use data recovery tools such as FTK and EnCase to locate log files, mail database files, personal e-mail files, and offline storage files. These data recovery tools extract the data from the mail server and permit the investigator to see the evidence on the machine itself. A text editor or special viewer program
7-18
Chapter 7
Source: http://www.advsoft.info/products/maildetective/. Accessed 2/2007.
Figure 7-13 MailDetective allows users to specify different options for
chart displays.
Source: http://www.advsoft.info/products/maildetective/. Accessed 2/2007.
Figure 7-14 MailDetective can display data as charts.
![]()
Using Specialized E-Mail Forensic Tools
7-19
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 7-15 This is information about a particular phishing attempt.
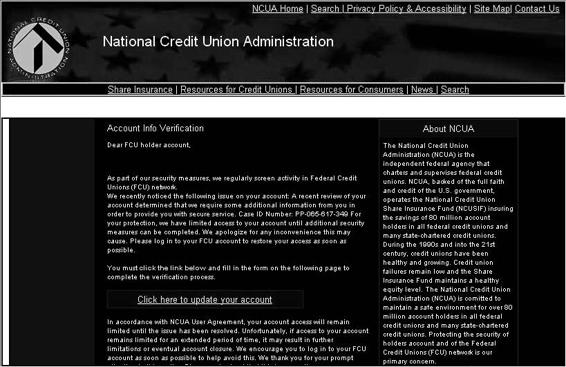
Figure 7-16 This is the Web site that is linked to in the phishing attempt described
by Figure 7-15.
can open the recovered files. This e-mail log information can be compared with the victim’s e-mail message, and once it is verified, this information can serve as evidence.
Tool: Forensic Toolkit (FTK)
FTK has file-filtering and search functionality. FTK’s customizable filters allow investigators to sort through thousands of files to quickly find the evidence they need.
FTK has the following features:
• Supports Outlook, Outlook Express, AOL, Earthlink, Netscape, Yahoo!, Eudora, Hotmail,
Thunderbird, and MSN e-mail
• Generates audit logs and case reports
• Provides full text indexing that yields instant text search results
• Provides advanced searches for JPEG images and Internet text
• Locates binary patterns
7-20
Chapter 7
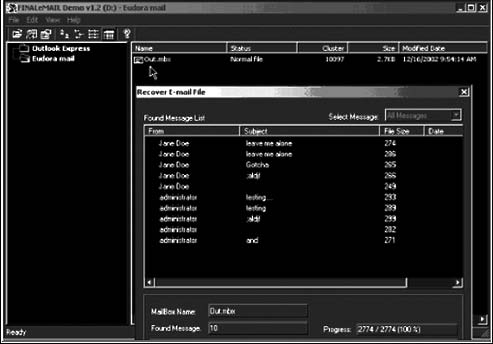
Figure 7-17 FINALeMAIL recovers e-mails deleted from Outlook Express
and Eudora.
• Automatically recovers deleted files and partitions
• Targets key files quickly by creating custom file filters
• Supports NTFS, FAT12, FAT16, FAT32, ext2, ext3, HFS, HFSϩ, and Reiser FS 3 file systems
• Supports EnCase, SnapBack, Safeback (up to but not including version 3), Expert Witness, ICS, and Linux DD image file formats
• Allows an investigator to view, search, print, and export e-mail messages and attachments
• Recovers deleted and partially deleted e-mails
• Automatically extracts data from PKZIP, WinZip, WinRAR, GZIP, and TAR compressed files
Tool: FINALeMAIL
FINALeMAIL can scan e-mail databases to locate deleted e-mails that do not have any data location information. This tool can recover e-mails lost through virus infection, accidental deletion, and disk formatting.
FINALeMAIL not only restores single messages to their original state but also has the capability to restore whole database files. FINALeMAIL supports Outlook Express and Eudora. Figure 7-17 shows a screenshot from FINALeMAIL.
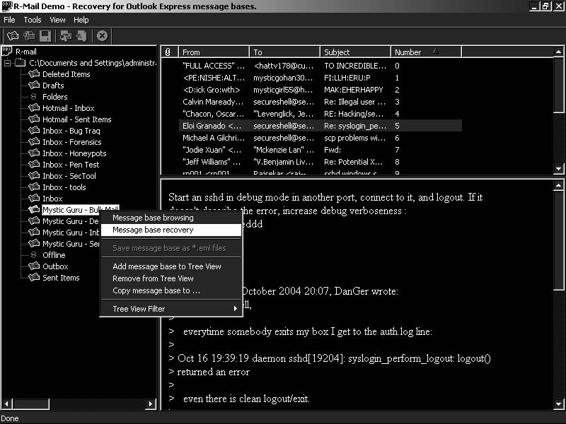
Tool: R-Mail
R-Mail is an e-mail recovery tool. It restores deleted Outlook and Outlook Express e-mail messages. R-Mail can also recover Outlook and Outlook Express data files if they have been damaged. Recovered data are stored in .eml, .pst, or .msg format so they can be imported into Outlook or Outlook Express.
An investigator can also view recovered messages within R-Mail. This tool is of vital importance if a suspect has deleted e-mail messages intentionally. Figure 7-18 shows a screenshot from R-Mail.
Tool: E-Mail Detective
E-Mail Detective allows investigators to extract all e-mail contents (including graphics) from cached AOL
e-mails stored on a user’s disk drive. An investigator can run E-Mail Detective from a USB jump drive for field investigations.
Using Specialized E-Mail Forensic Tools
7-21
Source: http://www.outlook-mail-recovery.com/. Accessed 2/2007.
Figure 7-18 An investigator can browse recovered e-mails in R-Mail.
Figure 7-19 E-mail Examiner allows investigators to view recovered e-mails.
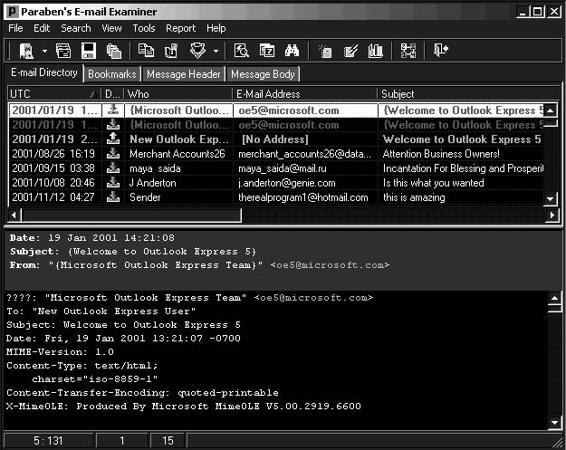
Tool: E-mail Examiner by Paraben
E-mail Examiner allows investigators to recover deleted e-mail messages. It can even recover deleted messages that have been removed from the Deleted Items folder. E-mail Examiner supports over 15 different mail types, including AOL, Microsoft Outlook, Eudora, Mozilla, MSN, and Pegasus. Figure 7-19 shows a screenshot from E-mail Examiner.
7-22
Chapter 7
Figure 7-20 Network E-mail Examiner can show all information associated with a
particular e-mail.
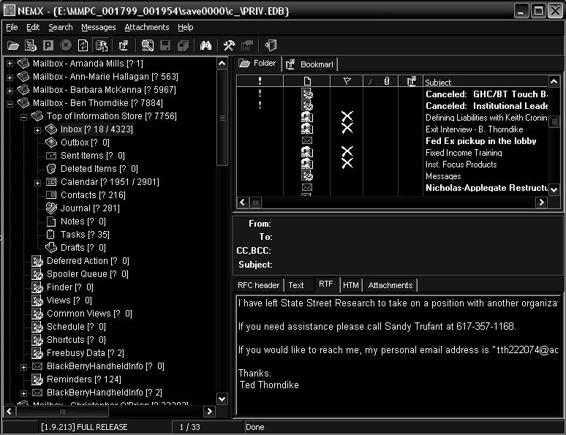
Tool: Network E-mail Examiner by Paraben
Network E-mail Examiner allows an investigator to examine a variety of network e-mail archives. This tool views all the individual e-mail accounts in e-mail stores and the associated metadata. Network E-mail Examiner reads Microsoft Exchange, Lotus Notes, and Novell GroupWise e-mail stores.
Network E-mail Examiner is designed to work with E-mail Examiner. The outputs are compatible, so an investigator can load one tool’s output into the other tool for further analysis. Figure 7-20 shows a screenshot from Network E-mail Examiner.
Tool: Recover My Email for Microsoft Outlook
Recover My Email for Microsoft Outlook is an e-mail recovery tool. The following are some of its features:
• Recovers individual e-mail messages and attachments deleted from a Microsoft Outlook e-mail file
• Scans an Outlook .pst file to see what e-mail can be recovered
• Saves deleted messages and attachments into a new .pst file
• Converts .pst files to .ost files
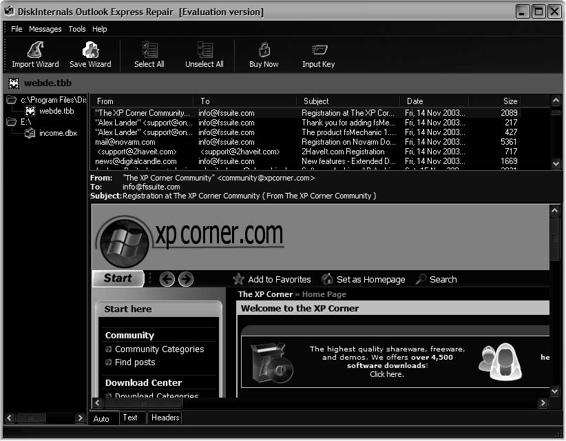
Tool: Diskinternals Outlook Recovery
Outlook Recovery restores messages and attachments that have been deleted from the Deleted Items folder in Outlook. It also repairs damaged .pst and .ost files for all versions of Outlook. Outlook Recovery can scan an entire hard drive for damaged Outlook database files. It can often even restore files on damaged hard drives.
Figure 7-21 shows a screenshot from Outlook Recovery.
Trace the E-Mail
Tracing e-mail begins with looking at the message header. All e-mail header information can be faked except the “Received” portion referencing the victim’s computer (the last received).
Using Specialized E-Mail Forensic Tools
7-23
Figure 7-21 Users can view recovered e-mails using Outlook Recovery’s
internal viewer.
Once it is confirmed that the header information is correct, the investigator can use the originating e-mail server as the primary source. The investigator can get a court order served by law enforcement or a civil complaint filed by attorneys. The investigator can use the court order to obtain the log files from the server in order to determine the sender. After getting contact information about the suspect, the investigator can take punitive steps against the suspect.
Validating Header Information
Once it is established that a crime has been committed, the investigator can use the IP address of the originating source to track down the owner of the e-mail address. The suspect can provide fake information. An investigator should always validate the information first. The following are some acceptable sites that an investigator can use to find the person owning a domain name:
• www.arin.net: This site employs the American Registry for Internet Numbers (ARIN) to match a domain name with an IP address. It also provides the point of contact for the domain name.
• www.internic.com: It provides the same information given by www.arin.net.
• www.freeality.com: This site provides various types of searches, including those for e-mail addresses, physical addresses, phone numbers, and names. An investigator can do a reverse e-mail search, which could reveal a suspect’s real name.
• www.google.com: An investigator can use this all-purpose search engine to find many different types of information. The investigator can search both Web sources and newsgroup sources.
These Web sites can assist in tracing an e-mail message by providing essential pieces of information, such as a suspect’s contact information.
Tracing Web-Based E-Mail
It can be difficult to trace the sender of Web-based e-mail. A user can read and send this type of e-mail from any computer and from any part of the world. Web-based e-mail accounts are free, and no authentic information 7-24
Chapter 7
is required for creating an e-mail account. Criminals exploit this advantage and create e-mail accounts using false identities.
In case a Web-based e-mail account is used for sending offending messages, an investigator can contact the provider of the account to find the IP address of the user who connected to the Web site to send the mail. After performing IP address authentication, the investigator can get the sender’s information.
Searching E-Mail Addresses
After getting the suspect’s contact information, such as e-mail address, name, and phone number, the investigator can use various Internet search engines to find more information about the suspect.
The following search engines are used for searching for e-mail addresses:
• http://www.dogpile.com: This site searches all the most popular engines and then provides more comprehensive and relevant results. The site provides a comprehensive background report that has all the information about a suspect, including age, current and previous addresses, phone number,
occupation, bankruptcies, tax liens and judgments, and property ownership.
• http://www.searchscout.com: This is a powerful tool that assists in tracing an offender by delivering relevant search results for keyword queries and giving ample search options to investigators. This search site provides investigators with the option to look up e-mail addresses and trace e-mails back to the source. It has powerful lookup tools, an e-mail directory, and an in-depth guide for advanced searching so an investigator can find names connected to street addresses, phone numbers, and e-mail addresses.
• http://www.altavista.com: This site allows an investigator to search for a suspect based on various criteria, including name, phone number, and e-mail address.
• http://www.mamma.com: This is a metasearch engine, which concurrently searches a variety of engines and directories and provides the most relevant results after eliminating duplicate information. It provides various options to allow an investigator to refine the search.
• http://www.infospace.com: This site has a reverse lookup option that makes tracing e-mails easy and quick. An investigator can refer to e-mail directories and public records while investigating a suspect.
• http://www.emailaddresses.com: This is a free e-mail address directory. It provides a wide range of search criteria, such as reverse lookup and search by city, state, and business. Any single piece of information can be used to retrieve a suspect’s information.
• http://www.google.com: This search engine serves as a convenient way for tracing e-mails. The people search has two criteria: phone number and e-mail address. An investigator can also perform an instant background check. Many popular e-mail search sites use this search engine.
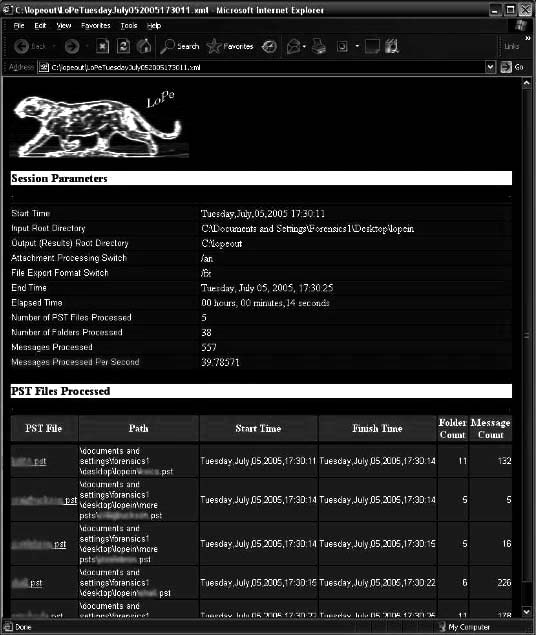
Tool: LoPe
LoPe (Figure 7-22) is an e-mail forensic tool that has the following features:
• It extracts all e-mail messages and attachments from multiple .pst files.
• It recreates the internal .pst folder structure.
• It extracts all message headers and properties.
• Files are exported in MSG, EML, or XML format.
• It hashes every message and attachment.
• It offers a command-line interface so it can be easily batch scripted.
• LoPe allows a user to customize XML output format using XSL style sheets.
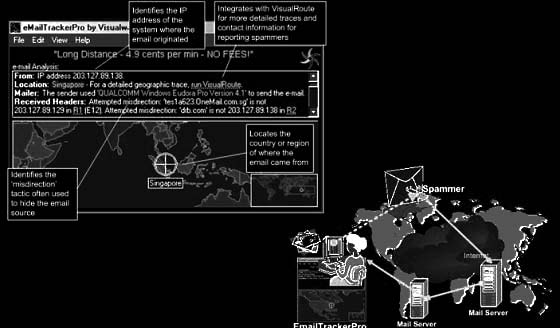
Tool: eMailTrackerPro
eMailTrackerPro analyzes e-mail headers and provides the IP address of the machine that sent the e-mail. It also provides the graphical location of that IP address so an investigator can track down the sender (Figure 7-23).
eMailTrackerPro also protects users from spam by blocking mail that comes from blacklisted sites. Users can also easily report e-mail abuse. eMailTrackerPro can create a report and send it to the offending user’s ISP.
Using Specialized E-Mail Forensic Tools
7-25
Source: http://www.evidencetalks.com/. Accessed 2/2007.
Figure 7-22 LoPe can extract e-mails from multiple .pst files.
Figure 7-23 eMailTrackerPro analyzes e-mail headers.
7-26
Chapter 7
Tool: ID Protect
ID Protect protects a domain owner’s contact information from becoming public. The WHOIS database contains a domain owner’s address, phone number, and other private information. ID Protect’s dynamic e-mail system constantly changes the e-mail address visible in the WHOIS database, so any spammer that harvests the address will get an invalid address. A user’s private information is held in confidentiality and protected by the Domain Privacy Protection Service. The Domain Privacy Protection Service secures and maintains the user’s real e-mail address on file so he or she receives important information regarding his or her domain.
A domain name with ID Protect can shield a user from the following:
• Domain-related spam
• Identity theft
• Data mining
• Name hijackers
U.S. Laws against E-Mail Crime: CAN-SPAM Act
The CAN-SPAM Act of 2003 (Controlling the Assault of Non-Solicited Pornography and Marketing Act of 2003) does the following:
• Establishes requirements for individuals and organizations that send commercial e-mail
• Details the penalties for violating the law
• Gives consumers the right to request that spammers stop contacting them
The law pertains to e-mail whose primary purpose is advertising or promoting a commercial product or service, including content on a Web site.
The following are the main provisions of this act:
• Header information must be accurate. The sender and recipient e-mail addresses must be correct.
• Subject lines must not be misleading. The subject of the message must relate to the content of the message.
• E-mail recipients must be given a way to opt out of receiving further messages. This method must be spelled out in each e-mail message.
• Any commercial e-mail must identify itself as an advertisement or solicitation. It must also include the individual or organization’s physical address.
The following are the penalties for violating the provisions of this act:
• Each violation is subject to fines of up to $11,000. Commercial e-mail is also subject to laws banning false or misleading advertising.
• Commercial e-mailers who also do the following are subject to additional fines:
• Harvest e-mail addresses from Web sites that have posted a notice prohibiting the transfer of e-mail addresses
• Generate e-mail addresses using a dictionary attack
• Use automated methods to register for multiple e-mail accounts to send commercial e-mail
• Relay e-mails through a computer or network without permission
The law allows the Department of Justice to seek criminal penalties for commercial e-mailers who do the following:
• Use someone else’s computer without authorization and send commercial e-mail from it
• Use a computer to relay or retransmit multiple commercial e-mail messages in an attempt to mislead recipients about the origin of the message
• Falsify header information in multiple e-mail messages and send those messages
• Register for multiple e-mail accounts or domain names using false identification information
Chapter Summary
7-27
U.S. Law: 18 U.S.C. § 2252A
This law pertains to child pornography. The following are the provisions of the law:
• A person cannot knowingly transport by any means, including but not limited to through the mail or through a computer, child pornography.
• A person cannot knowingly receive or distribute child pornography that has been transported by any means, including but not limited to through the mail or through a computer.
• A person cannot knowingly reproduce any child pornography for distribution by any means, including but not limited to through the mail or through a computer.
• A person cannot advertise, promote, present, distribute, or solicit child pornography.
• A person cannot knowingly possess or sell child pornography in any form, including books, magazines, films, and digital media.
The penalties for violating this law are fines and a prison sentence of between 5 and 20 years.
U.S. Law: 18 U.S.C. § 2252B
This law pertains to misleading domain names on the Internet. The following are the provisions of this law:
• A person cannot knowingly use a misleading domain name on the Internet with the intent to deceive a person into viewing obscene material. This does not include using a domain name containing sexual terms that indicate the sexual content of the site. The penalty for violating this provision is a fine, imprisonment for no longer than 2 years, or both.
• A person cannot knowingly use a misleading domain name on the Internet with the intent to deceive a minor into viewing material that is harmful to minors. The penalty for violating this provision is a fine, imprisonment for no longer than 4 years, or both.
E-Mail Crime Law in Washington: RCW 19.190.020
This law prohibits unpermitted or misleading e-mail. The provision of this law is that a person cannot knowingly send a commercial e-mail from a computer located in Washington or to an e-mail address held by a Washington resident that does one of the following:
• Uses someone else’s Internet domain name without permission or otherwise tries to hide the origin of the e-mail or the path the e-mail took
• Contains a false or misleading subject line
Chapter Summary
■ E-mail crimes are those crimes that use e-mail to perpetrate the crime or that are supported by e-mail.
■ Spammers obtain e-mail addresses by harvesting addresses from Usenet postings, DNS listings, and Web pages.
■ Chat rooms can also be used as a social engineering tool to collect information for committing crimes.
■ Phishers use fake Web sites to obtain users’ personal information.
■ E-mail spoofing is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source.

7-28
Chapter 7
Review Questions
1. What is spam?
___________________________________________________________________________________________
___________________________________________________________________________________________
2. Describe the differences between IMAP and POP3.
___________________________________________________________________________________________
___________________________________________________________________________________________
3. List six examples of e-mail crimes.
___________________________________________________________________________________________
___________________________________________________________________________________________
4. List the steps involved in investigating e-mail crimes.
___________________________________________________________________________________________
___________________________________________________________________________________________
5. What is the purpose of examining e-mail headers? What can they tell an investigator?
___________________________________________________________________________________________
___________________________________________________________________________________________
6. What is phishing?
___________________________________________________________________________________________
___________________________________________________________________________________________
7. What are the steps involved in tracing an e-mail?
___________________________________________________________________________________________
___________________________________________________________________________________________
8. Name four common headers and their purposes.
___________________________________________________________________________________________
___________________________________________________________________________________________
9. Describe the provisions of the CAN-SPAM Act of 2003.
___________________________________________________________________________________________
___________________________________________________________________________________________
Hands-On Projects
1. Perform the following steps:
■ Navigate to Chapter 7 of the Student Resource Center.
■ Install and launch FINALeMAIL.
■ Explore the various options of this program.
Hands-On Projects
7-29
2. Perform the following steps:
■ Navigate to Chapter 7 of the Student Resource Center.
■ Install and launch E-Mail Detective.
■ Explore the various options of this program.
3. Perform the following steps:
■ Navigate to Chapter 7 of the Student Resource Center.
■ Install and launch Spam Arrest.
■ Track an e-mail address.
This page intentionally left blank

All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.