Computer Forensics: Investigating Network Intrusions and Cybercrime (CHFI) (2016)
9
Chapter
Investigating Trademark
and Copyright Infringement
Objectives
After completing this chapter, you should be able to:
• Understand trademarks and their characteristics
• Understand service marks and trade dress
• Recognize and investigate trademark infringement
• Understand copyright
• Investigate copyright status
• Understand how copyrights are enforced
• Understand plagiarism
• Use plagiarism detection tools
• Understand patent infringement
• Understand domain name infringement
• Investigate intellectual property theft
• Understand digital rights management
Key Terms
Reliance party an individual or business that used a work when it was in the public domain,
prior to the Uruguay Round Agreements Act
Introduction to Investigating Trademark
and Copyright Infringement
This chapter discusses copyrights, trademarks, and patents. It covers what constitutes infringement, and how that infringement can be investigated. For reference, the texts of some international trademark laws are included.
9-1
9-2
Chapter 9
Trademarks
According to the United States Patent and Trademark Office (USPTO), “A trademark is a word, phrase, symbol or design, or a combination of words, phrases, symbols or designs, which identifies and distinguishes the source of the goods of one party from those of others.” Brand names, symbols, slogans, designs, words, smells, colors, or a combination of any of these that distinguishes a particular product or service from others of the same trade classify as trademarks. There are three types of trademarks, as defined by the USPTO:
1. Service mark: “A service mark is any word, name, symbol, device, or any combination, used, or intended to be used, in commerce, to identify and distinguish the services of one provider from services provided by others, and to indicate the source of the services.” Some consider service marks to be separate from trademarks.
2. Collective mark: “A collective mark is a trademark or service mark used or intended to be used, in commerce, by the members of a cooperative, an association, or other collective group or organization, including a mark, which indicates membership in a union, an association, or other organization.”
3. Certification mark: “Certification mark is any word, name, symbol, device, or any combination, used, or intended to be used, in commerce with the owner’s permission by someone other than its owner, to certify regional or other geographic origin, material, mode of manufacture, quality, accuracy, or other characteristics of someone’s goods or services, or that the work or labor on the goods or services was performed by members of a union or other organization.”
Trademark Eligibility and Benefits of Registering It
An individual or business unit intending to use a unique identifier to categorize its goods or services can register that identifier as a trademark. The trademark should be unique and not misleading. To own a trademark, the individual or business unit must file a trademark application form at the USPTO.
The application form must include the following to be accepted by the USPTO:
• Applicant’s name
• Applicant’s address for correspondence
• A depiction of the mark
• A list of the goods or services provided
• The application filing fee
Registering the trademark provides several benefits, including the following:
• Protection of an organization’s name and logo
• Exclusive rights of the mark and protection against trademark infringement
• More visibility of the product versus other products in the same trade
• Inclusion in the trademark search database, which helps to discourage other applicants from filing a similar kind of trademark
• The ability to, in the event of trademark infringement, ask the infringer to pay for damages and the attorneys’ fees that the plaintiff incurred while filing the lawsuit
• A base for filing the registration for that particular trademark in a foreign country
Service Mark and Trade Dress
There is a thin line of difference between a trademark and a service mark, so some consider them to be in the same category. A trademark differentiates products of the same trade, while a service mark differentiates services of the same trade. The symbol SM is for an unregistered service mark, and the symbol TM represents an unregistered trademark.
Trade dress is the distinctive packaging of a product that differentiates it from other products of the same trade. Color, pattern, shape, design, arrangement of letters and words, packaging style, and graphical presentation all constitute trade dress. Previously, trade dress referred to the way in which a product was packaged to be launched in a market, but now even the product design is an element of trade dress. Elements of trade dress do not affect the way in which the product is used. Federal law for trademark also applies to trade dress. There is no distinction between trade dress and trademark; the Lanham Act, also known as the Trademark Act of 1946, does not provide any distinction between the two.
Trademark Infringement
9-3
Trademark Infringement
An infringement is the encroachment on another’s right or privilege. In the legal field, this term is often used when referring to intellectual property rights, such as patents, copyrights, and trademarks. A party that owns the rights to a particular trademark can sue other parties for trademark infringement based on the standard likelihood of confusion.
The Trademark Act of 1946 section 1114 and 1125 specify trademark infringement. The full text of these sections follows:
TITLE VI REMEDIES
§ 32 (15 U.S.C. § 1114). Remedies; infringement; innocent infringers
(1) Any person who shall, without the consent of the registrant—
a) Use in commerce any reproduction, counterfeit, copy, or colorable imitation of a registered mark in connection with the sale, offering for sale, distribution, or advertising of any goods or services on or in connection with which such use is likely to cause confusion, or to cause mistake, or to deceive; or
b)
Reproduce, counterfeit, copy or colorably imitate a registered mark and apply such repro-
duction, counterfeit, copy or colorable imitation to labels, signs, prints, packages, wrappers, receptacles or advertisements intended to be used in commerce upon or in connection with
the sale, offering for sale, distribution, or advertising of goods or services on or in connection with which such use is likely to cause confusion, or to cause mistake, or to deceive, shall be liable in a civil action by the registrant for the remedies hereinafter provided. Under subsection (b) hereof, the registrant shall not be entitled to recover profits or damages unless the acts have been committed with knowledge that such imitation is intended to be used to cause
confusion, or to cause mistake, or to deceive.
As used in this paragraph, the term “any person” includes the United States, all agencies and instrumentalities thereof, and all individuals, firms, corporations, or other persons acting for the United States and with the authorization and consent of the United States, and any State, any instrumentality of a State, and any officer or employee of a State or instrumentality of a State acting in his or her official capacity. The United States, all agencies and instrumentalities thereof, and all individuals, firms, corporations, other persons acting for the United States and with the authorization and consent of the United States, and any State, and any such instrumentality, officer, or employee, shall be subject to the provisions of this Act in the same manner and to the same extent as any nongovernmental entity.
(2) Notwithstanding any other provision of this Act, the remedies given to the owner of a right infringed under this Act or to a person bringing an action under section 43(a) or (d) shall be limited as follows:
a) Where an infringer or violator is engaged solely in the business of printing the mark or violating matter for others and establishes that he or she was an innocent infringer or innocent violator, the owner of the right infringed or person bringing the action under section 43(a) shall be entitled as against such infringer or violator only to an injunction against future printing.
b) Where the infringement or violation complained of is contained in or is part of paid advertising matter in a newspaper, magazine, or other similar periodical or in an electronic com-
munication as defined in section 2510(12) of title 18, United States Code, the remedies of
the owner of the right infringed or person bringing the action under section 43(a) as against the publisher or distributor of such newspaper, magazine, or other similar periodical or
electronic communication shall be limited to an injunction against the presentation of such
advertising matter in future issues of such newspapers, magazines, or other similar periodi-
cals or in future transmissions of such electronic communications. The limitations of this
subparagraph shall apply only to innocent infringers and innocent violators.
c) Injunctive relief shall not be available to the owner of the right infringed or person bringing the action under section 43(a) with respect to an issue of a newspaper, magazine, or other
similar periodical or an electronic communication containing infringing matter or violating
9-4
Chapter 9
matter where restraining the dissemination of such infringing matter or violating matter in
any particular issue of such periodical or in an electronic communication would delay the
delivery of such issue or transmission of such electronic communication after the regular
time for such delivery or transmission, and such delay would be due to the method by which
publication and distribution of such periodical or transmission of such electronic commu-
nication is customarily conducted in accordance with sound business practice, and not due
to any method or device adopted to evade this section or to prevent or delay the issuance of an injunction or restraining order with respect to such infringing matter or violating matter.
d)(i)(I) A domain name registrar, a domain name registry, or other domain name registration authority that takes any action described under clause (ii) affecting a domain name shall not be liable for monetary relief or, except as provided in subclause (II), for injunctive relief, to any person for such action, regardless of whether the domain name is finally determined to infringe or dilute the mark.
(II) A domain name registrar, domain name registry, or other domain name registration authority described in subclause (I) may be subject to injunctive relief only if such registrar, registry, or other registration authority has—
(aa) not expeditiously deposited with a court, in which an action has been filed regarding the disposition of the domain name, documents sufficient for the court to establish the
court’s control and authority regarding the disposition of the registration and use of
the domain name;
(bb) transferred, suspended, or otherwise modified the domain name during the pendency
of the action, except upon order of the court; or
(cc) willfully failed to comply with any such court order.
(ii) An action referred to under clause (i)(I) is any action of refusing to register, removing from registration, transferring, temporarily disabling, or permanently canceling a domain name—
(I) In compliance with a court order under section 43(d); or
(II) In the implementation of a reasonable policy by such registrar, registry, or authority prohibiting the registration of a domain name that is identical to, confusingly similar to, or dilutive of another’s mark.
(iii) A domain name registrar, a domain name registry, or other domain name registration authority shall not be liable for damages under this section for the registration or maintenance of a domain name for another absent a showing of bad faith intent to profit from such registration or maintenance of the domain name.
(iv) If a registrar, registry, or other registration authority takes an action described under clause (ii) based on a knowing and material misrepresentation by any other person that a domain name is
identical to, confusingly similar to, or dilutive of a mark, the person making the knowing and material misrepresentation shall be liable for any damages, including costs and attorney’s fees, incurred by the domain name registrant as a result of such action. The court may also grant
injunctive relief to the domain name registrant, including the reactivation of the domain name or the transfer of the domain name to the domain name registrant.
(v) A domain name registrant whose domain name has been suspended, disabled, or transferred under a policy described under clause (ii)(II) may, upon notice to the mark owner, file a civil action to establish that the registration or use of the domain name by such registrant is not unlawful under this Act. The court may grant injunctive relief to the domain name registrant, including the reactivation of the domain name or transfer of the domain name to the domain
name registrant.
e) As used in this paragraph—(i) the term “violator” means a person who violates section 43(a); and (ii) The term “violating matter” means matter that is the subject of a violation under
section 43(a).
(Amended Oct. 9, 1962, 76 Stat. 773; Nov. 16, 1988, 102 Stat. 3943; Oct. 27, 1992, 106 Stat.
3567; Oct. 30, 1998, 112 Stat. 3069; Aug. 5, 1999, 113 Stat. 218; Nov. 29, 1999, 113 Stat.
1501A-549.)
Trademark Infringement
9-5
TITLE VIII FALSE DESIGNATIONS OF ORIGIN,
FALSE DESCRIPTIONS, AND DILUTION FORBIDDEN
§ 43 (15 U.S.C. § 1125). False designations of origin; false description or representation a)(1) Any person who, on or in connection with any goods or services, or any container for goods, uses in commerce any word, term, name, symbol, or device, or any combination thereof, or
any false designation of origin, false or misleading description of fact, or false or misleading representation of fact, which—
(A) Is likely to cause confusion, or to cause mistake, or to deceive as to the affiliation, connection, or association of such person with another person, or as to the origin, sponsorship,
or approval of his or her goods, services, or commercial activities by another person, or
(B) In commercial advertising or promotion, misrepresents the nature, characteristics, qualities, or geographic origin of his or her or another person’s goods, services, or commercial
activities, Shall be liable in a civil action by any person who believes that he or she is or is likely to be damaged by such act
(2) As used in this subsection, the term “any person” includes any State, instrumentality of a State or employee of a State or instrumentality of a State acting in his or her official capacity. Any State, and any such instrumentality, officer, or employee, shall be subject to the provisions of this Act in the same manner and to the same extent as any nongovernmental entity.
(3) In a civil action for trade dress infringement under this Act for trade dress not registered on the principal register, the person who asserts trade dress protection has the burden of proving that the matter sought to be protected is not functional.
b) Any goods marked or labeled in contravention of the provisions of this section shall not be imported into the United States or admitted to entry at any customhouse of the United States. The owner, importer, or consignee of goods refused entry at any customhouse under this section may have any recourse by protest or appeal that is given under the customs revenue laws or may have the remedy given by this Act in cases involving goods refused entry or seized.
c)(1) T.he owner of a famous mark shall be entitled, subject to the principles of equity and upon such terms as the court deems reasonable, to an injunction against another person’s commercial use in commerce of a mark or trade name, if such use begins after the mark has become famous
and causes dilution of the distinctive quality of the mark, and to obtain such other relief as is provided in this subsection. In determining whether a mark is distinctive and famous, a court may consider factors such as, but not limited to—
(A) The degree of inherent or acquired distinctiveness of the mark;
(B) The duration and extent of use of the mark in connection with the goods or services with which the mark is used;
(C) The duration and extent of advertising and publicity of the mark;
(D) The geographical extent of the trading area in which the mark is used;
(E) The channels of trade for the goods or services with which the mark is used;
(F) The degree of recognition of the mark in the trading areas and channels of trade used by the mark’s owner and the person against whom the injunction is sought;
(G) The nature and extent of use of the same or similar marks by third parties; and
(H) Whether the mark was registered under the Act of March 3, 1881, or the Act of February 20, 1905, or on the principal register.
(2) In an action brought under this subsection, the owner of the famous mark shall be entitled only to injunctive relief as set forth in section 34 unless the person against whom the injunction is sought willfully intended to trade on the owner’s reputation or to cause dilution of the famous mark. If such willful intent is proven, the owner of the famous mark shall also
be entitled to the remedies set forth in sections 35(a) and 36, subject to the discretion of the court and the principles of equity.
(3) The ownership by a person of a valid registration under the Act of March 3, 1881, or the Act of February 20, 1905, or on the principal register shall be a complete bar to an action against 9-6
Chapter 9
that person, with respect to the mark, that is brought by another person under the common
law or a statute of a State and that seeks to prevent dilution of the distinctiveness of a mark, label or form or advertisement.
(4) The following shall not be actionable under this section:
(A) Fair use of a famous mark by another person in comparative commercial advertising or
promotion to identify the competing goods or services of the owner of the famous mark.
(B) Noncommercial use of a mark.
(C) All forms of news reporting and news commentary.
(D)(1) (A) A person shall be liable in a civil action by the owner of a mark, including a personal name which is protected as a mark under this section, if, without regard to the goods or
services of the parties, that person—
(i) Has a bad faith intent to profit from that mark, including a personal name which is
protected as a mark under this section; and
(ii) Registers, traffics in, or uses a domain name that—
(I) In the case of a mark that is distinctive at the time of registration of the domain
name, is identical or confusingly similar to that mark;
(II) In the case of a famous mark that is famous at the time of registration of the do-
main name, is identical or confusingly similar to or dilutive of that mark; or
(III) Is a trademark, word, or name protected by reason of section 706 of title 18,
United States Code, or section 220506 of title 36, United States Code.
(B) (i) In determining whether a person has a bad faith intent described under subpara-
graph (A), a court may consider factors such as, but not limited to—
(I) The trademark or other intellectual property rights of the person, if any, in the
domain name;
(II) The extent to which the domain name consists of the legal name
of the person or a name that is otherwise commonly used to identify
that person;
(III) The person’s prior use, if any, of the domain name in connection with the
bona fide offering of any goods or services;
(IV) The person’s bona fide noncommercial or fair use of the mark in a site
accessible under the domain name;
(V) The person’s intent to divert consumers from the mark owner’s online loca-
tion to a site accessible under the domain name that could harm the good-
will represented by the mark, either for commercial gain or with the intent
to tarnish or disparage the mark, by creating a likelihood of confusion as to
the source, sponsorship, affiliation, or endorsement of the site;
(VI) The person’s offer to transfer, sell, or otherwise assign the domain name to
the mark owner or any third party for financial gain without having used,
or having an intent to use, the domain name in the bona fide offering of
any goods or services, or the person’s prior conduct indicating a pattern of
such conduct;
(VII) The person’s provision of material and misleading false contact informa-
tion when applying for the registration of the domain name, the person’s
intentional failure to maintain accurate contact information, or the person’s
prior conduct indicating a pattern of such conduct;
(VIII) The person’s registration or acquisition of multiple domain names which
the person knows are identical or confusingly similar to marks of others
that are distinctive at the time of registration of such domain names, or
dilutive of famous marks of others that are famous at the time of registra-
tion of such domain names, without regard to the goods or services of the
parties; and
Trademark Infringement
9-7
(IX) The extent to which the mark incorporated in the person’s domain name
registration is or is not distinctive and famous within the meaning of subsec-
tion (c)(1) of section 43.
(ii) Bad faith intent described under subparagraph (A) shall not be found in any case in
which the court determines that the person believed and had reasonable grounds
to believe that the use of the domain name was a fair use or otherwise lawful.
(C) In any civil action involving the registration, trafficking, or use of a domain name under this paragraph, a court may order the forfeiture or cancellation of the domain name or
the transfer of the domain name to the owner of the mark.
(D) A person shall be liable for using a domain name under subparagraph (A) only if that
person is the domain name registrant or that registrant’s authorized licensee.
(E) As used in this paragraph, the term “traffics in” refers to transactions that include, but are not limited to, sales, purchases, loans, pledges, licenses, exchanges of currency, and
any other transfer for consideration or receipt in exchange for consideration.
(2)(A) The owner of a mark may file an in rem civil action against a domain name in the judicial district in which the domain name registrar, domain name registry, or other domain
name authority that registered or assigned the domain name is located if—
(i) The domain name violates any right of the owner of a mark registered in the Patent
and Trademark Office, or protected under subsection (a) or (c); and
(ii) The court finds that the owner—
(I) Is not able to obtain in personam jurisdiction over a person who would have been
a defendant in a civil action under paragraph (1); or
(II) Through due diligence was not able to find a person who would have been a
defendant in a civil action under paragraph (1) by—
(aa) sending a notice of the alleged violation and intent to proceed under this
paragraph to the registrant of the domain name at the postal and e-mail ad-
dress provided by the registrant to the registrar; and
(bb) publishing notice of the action as the court may direct promptly after filing
the action.
(B) The actions under subparagraph (A)(ii) shall constitute service of process.
(C) In an in rem action under this paragraph, a domain name shall be deemed to have its sites in the judicial district in which—
(i) The domain name registrar, registry, or other domain name authority that registered
or assigned the d omain name is located; or
(ii) Documents sufficient to establish control and authority regarding the disposition of
the registration and use of the domain name are deposited with the court.
(D) (i) The remedies in an in rem action under this paragraph shall be limited to a court order for the forfeiture or cancellation of the domain name or the transfer of the domain name to the owner of the mark. Upon receipt of written notification of a filed,
stamped copy of a complaint filed by the owner of a mark in a United States district
court under this paragraph, the domain name registrar, domain name registry, or
other domain name authority shall—
(I) Expeditiously deposit with the court documents sufficient to establish the court’s
control and authority regarding the disposition of the registration and use of the
domain name to the court; and
(II) Not transfer, suspend, or otherwise modify the domain name during the pen-
dency of the action, except upon order of the court.
(ii) The domain name registrar or registry or other domain name authority shall not be
liable for injunctive or monetary relief under this paragraph except in the case of bad
faith or reckless disregard, which includes a willful failure to comply with any such
court order.
9-8
Chapter 9
(3) The civil action established under paragraph (1) and the in rem action established under paragraph (2), and any remedy available under either such action, shall be in addition to
any other civil action or remedy otherwise applicable.
(4) The in rem jurisdiction established under paragraph (2) shall be in addition to any other jurisdiction that otherwise exists, whether in rem or in personam.
(Amended Nov. 16, 1988, 102 Stat. 3946; Oct. 27, 1992, 106 Stat. 3567; Jan. 16, 1996,
109 Stat. 985; Aug. 5, 1999, 113 Stat. 218; Nov. 29, 1999, 113 Stat. 1501A-545)
Monitoring Trademark Infringements
Trademark infringement is a threat to any successful product or brand. It not only affects the direct revenue of the branded product, but it also defames the product by confusing the customer with products of inferior quality.
It is necessary for the holder of a trademark to monitor infringements, following these guidelines:
• Check whether the infringement has been done by a distributor, employee, or customer.
• Check any third party who is involved in the infringement process.
• Ask for government authorities to identify a problem in third-party trademark application filings and domain name registrations.
• Stay up to date with news, articles, and consumers’ comments through which infringement can be prevented in its initial stages.
• Analyze infringement with the use of search engines.
• Make use of trademark infringement monitoring services such as CyberAlert and AdGooroo for detailed monitoring.
For example, say an organization trademarks a successful product called “WEED EATER” and another organization trademarks a different, inferior product called “weedeater.” A consumer may wish to buy a
“WEED EATER,” but could end up with a “weedeater” by mistake, costing the original organization a sale and tarnishing its name with a product of lesser quality.
Key Considerations Before Investigating Trademark Infringements
Before investigating trademark infringements, an investigator must do the following:
• Check if the trademark owner has registered or applied for registration in the country where the infringement has occurred.
• Check if the country is a member of the Paris Convention or the Madrid Protocol.
• Check the laws addressing this kind of infringement.
• Look for availability of adequate and strong enforcement mechanisms.
• Check whether the trademark is in use in the relevant country or is vulnerable to cancellation.
Steps for Investigating Trademark Infringements
When investigating illegal trademark infringement, follow these steps:
1. Check the type of infringement.
2. Investigate the infringement.
a. Check if the trademark owner has the necessary rights within the scope of the infringement.
b. If the owner has prior rights, seek a settlement or pursue court proceedings.
c.
Obtain photographs and video footage outside the infringement location, i.e., property, area, build-ings, signs, and so on.
d.
Obtain any available literature, brochures, business cards, and printouts from any sales software available.
e. Document any promotional programs that are in use.
f. Maintain a record of conversations with the business owner or employees.
g.
Do background research on the subject’s entity—local, county, state, and federal business registrations and licenses.
h. Obtain video footage on location using hidden cameras.
Copyright
9-9
3. Search for any article or advertisement related to the issue that was published in a newspaper or magazine.
4. Obtain civil, criminal, and family background on the business or its owners.
5. Document the intellectual property of the business or owner.
6. Investigate the history of the registration and license for filing in court.
7. Check conversations with neighboring businesses or residents.
8. Document pending changes that are noted during the investigation.
9. Document and investigate new locations.
10. Keep an updated record of changes in promotional programs to present as evidence in court.
11. Monitor changes after the proceedings in court.
Copyright
According to the USPTO, “Copyright is a form of protection provided to the authors of ‘original works of authorship’ including literary, dramatic, musical, artistic, and certain other intellectual works, both published and unpublished.” The 1976 Copyright Act empowers the owner of a copyright to reproduce and distribute the copyrighted work as well as derivatives of the work. It also gives the owner of the copyright the right to show-case the copyrighted work in public, sell it, and give rights related to it to others. The owner is also allowed to transfer the copyrighted work to a publication house and charge royalties.
A copyright notice for visually perceptible copies should have the word “Copyright” followed by the symbol ©, the published date, and the name of the owner. Works published before March 1989 require a valid copyright notice in order to be protected under the laws governing copyright. Works published after March 1, 1989, do not need to have a written copyright notice to be protected by copyright law, but it is still advisable.
Investigating Copyright Status
The following are the three basic ways by which an investigator can investigate the copyright status of a particular work:
1. Examine the copy of the work to find elements that need to be included in the copyright notice. Because works published after March 1, 1989, do not need to have a copyright notice along with the copyrighted work, the investigator has to do extensive research by using tools such as search engines to check the status of the copyrighted work.
2. Search the database of the U.S. Copyright Office ( http://www.copyright.gov/records). This search method is recommended for users who search the database only occasionally. For an advanced search, the investigator should use the Library of Congress Information System (LOCIS). The LOCIS usage guide should be read before connecting to LOCIS.
3. Approach the U.S. Copyright Office to do a search for the requested category. After the request is made for a copyright search, the U.S. copyright officials will search the records for a fee of $75 per hour. A typewritten or oral report will be sent at the investigator’s request.
The status changes made under the Copyright Act of 1976, the Berne Convention Implementation Act of 1988, the Copyright Renewal Act of 1992, and the Sonny Bono Copyright Term Extension Act of 1998 must be considered. It is important that the investigator has a clear understanding of these laws.
Tool: LOCIS
The Library of Congress Information System (LOCIS) is an online utility that helps an investigator search for copyright records. LOCIS runs on a command prompt. There is a link on the Library of Congress’s Web page to connect to LOCIS. Figure 9-1 shows a screenshot from LOCIS.
An investigator should follow the on-screen instructions to search the LOCIS database. Typing help at the command prompt shows the help screen at any point during the session. Information related to copyright and federal legislation can be obtained from the database.
How Long Does a Copyright Last?
The duration of a copyright is different for joint works, anonymous works, works under pseudonyms, and works-for-hire. In general, copyrights for works that are published after 1977 are valid for the life span of the author plus another 70 years. Works published before 1923 in the United States are in the public domain. Copyrights for works published between 1923 and 1977 have a validity of 95 years from the date of first publication.
9-10
Chapter 9
Figure 9-1 This is the LOCIS interface using HyperTerminal.
Works done by two or more authors are called joint works. Validity of the copyright for these works is until the death of the last surviving author of that particular work plus the next 70 years.
The copyright for anonymous, pseudonymous, or made-for-hire works lasts for the shorter of a period of 95 years from the year when the work was published or for a period of 120 years from the year when the work was created. Copyrights for works-for-hire can be renewed and extended for a term of 67 years by owner request.
U.S. Copyright Office
Article 1, Section 8 of the U.S. Constitution empowers Congress “to promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries.”
The objectives of the U.S. Copyright Office are as follows:
• To govern copyright law
• To create and maintain the public record
• To impart technical support to Congress
• To offer information service to the public
• To serve as a resource to international and domestic communities
• To provide support to the Library of Congress
How Are Copyrights Enforced?
President Bill Clinton signed the Uruguay Round Agreements Act (URAA) on December 8, 1994. This agreement created the Notice of Intent to Enforce (NIE). According to URAA, the owner of a restored work should notify any reliance parties if there is a plan to enforce copyrights for the particular work. A reliance party is an individual or business who used the work when the status of the work was in the public domain, prior to the URAA agreement.
The URAA directs the owner of a restored work to confront the reliance party either directly or by providing a constructive notice via filing a Notice of Intent to Enforce with the U.S. Copyright Office.
A lawsuit can be filed against anyone who has violated the rights of the copyright owner. Infringers who violate the fair use doctrine and try to commercialize the work of copyrighted owners or portray it as their own will often have to face a lawsuit from the owners of the copyrighted work.
Copyright
9-11
In this case, the copyright owner can do the following:
• Issue orders to prevent escalation of copyrights
• Ask for compensation from the infringer for the damage already done
• Ask the infringer to pay attorneys’ fees
Plagiarism
Plagiarism is when someone takes someone else’s words or ideas and presents them as his or her own. Plagiarism can prove costly, especially to students. Copying or even paraphrasing original ideas without quoting the source is an act of plagiarism. Examining the writing style, layout, formatting style, and references can help determine if students have plagiarized their work.
Paper Mills
Paper mills are Web sites that provide students with research works, essays, and so on. Some are advertiser supported and available for free. The following are a few paper mills:
• http://www.cheathouse.com
• http://www.essaysonfile.com
• http://www.gradesaver.com
• http://www.mightystudents.com
Types of Plagiarism
Plagiarism is categorized into various types depending upon its nature:
• Sources not cited
• Ghostwriting: taking the entire work directly from one source, without altering key words or phrases
• Poor masking: changing the appearance of information by altering key words or phrases
• Photocopying: copying a few portions of information directly from one source without any alteration
• Potlucking: using phrases from many sources, tweaking the sentences so as to fit them together but retaining most of the original phrasing
• Laziness: rewording or paraphrasing without concentrating on original work
• Self-plagiarizing: copying information from the creator’s previous work
• Sources cited
• Omitting or misattributing source: not citing, or misguiding the user to the resource
• Perfect paraphrasing: citing the source and avoiding quotation marks for directly copied information
Steps for Plagiarism Prevention
To prevent plagiarism, follow these steps:
1. Know in detail the types of plagiarism.
2. Understand facts and myths about plagiarism.
3. Cite the source, if the information is directly taken from it.
4. Quote the information if it cannot be reworded.
5. Learn to paraphrase, as it avoids plagiarism to an extent.
6. Be aware of detection tools.
7. Be aware of policies and procedures.
8. Be aware of legal penalties.
Plagiarism Detection Factors
An investigator should look for the following when detecting plagiarism:
• Change of vocabulary: The vocabulary used by the author in one portion of the text is inconsistent with the rest of the text.
9-12
Chapter 9
• Incoherent text: The text is not in the proper style and appears to be written by many people.
• Punctuation: The punctuation marks used in one text are the same as in another text. It is not likely for two different authors to use the same punctuation marks while writing the text.
• Dependence on certain words and phrases: Certain words and phrases are used by one author as well as by another author. Different authors tend to have different word preferences.
• Amount of similarity between texts: Two texts written by two different authors share large amounts of similar text.
• Long sequences of common text: Long sequences of common words or phrases are in the text.
• Similarity in the order of text: Two texts have the same order of words and phrases.
• Frequency of words: Two texts contain the same frequency of words.
• Common spelling mistakes: An independent author makes the same spelling mistakes repetitively as another author.
• Distribution of words: The distribution of word usage by an independent author appears in the same fashion throughout the document as another’s work.
• Syntactic structure of the text: Two texts written by different authors have similar syntactic structure.
Different authors often use different syntactic rules.
• Preference for the use of long or short sentences: If a sentence is long and shows no meaning in the text, it is possible that the author has combined sentences copied from another text.
• Readability of written text: The same readability is found in the works of two different authors.
• Inadequate references: References appear only in the text, but not in the bibliography.
Plagiarism Detection Tools
The following are the three categories of plagiarism detection tools:
1. Tools to detect plagiarism in text, such as Sumbit.ac.uk and CopyCatch, are helpful in checking plagiarism in works submitted in Microsoft Word, Corel WordPerfect, and text formats.
2. Tools to detect plagiarism in source code, such as JPlag and CodeMatch, help in finding similar source code from multiple sets.
3. Tools such as BOSS from Warwick University’s computer science department assist in the process of data collection.
Tool: Turnitin Turnitin is an online plagiarism detection tool primarily for educators and students. Turnitin detects plagiarism by comparing the submitted work to pages available on the Internet and in its database.
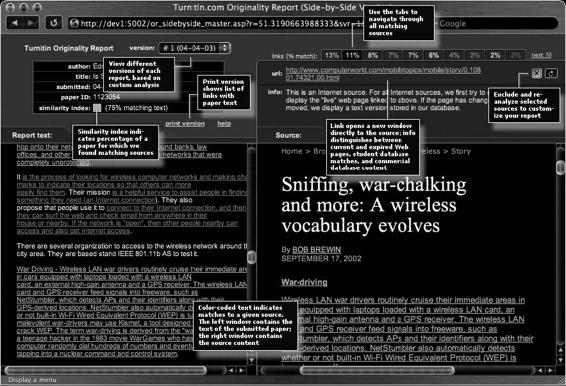
Figure 9-2 shows a screenshot from Turnitin.
The following are the key features of Turnitin:
• Plagiarism prevention: It helps identify the plagiarized work of students and also acts as a deterrent, stopping plagiarism before it starts.
• Peer review: It helps students review each other’s work.
• Grademark: This tool helps instructors, without much hassle, in assessing works submitted by students.
Instructors can add comments to the submitted work without altering the formatting of the document.
• Gradebook: It is similar to a paper gradebook, where the instructor can manage assignments and grade students in a more organized manner.
• Digital portfolio: It is an online student record book, helping to track student records for academic purposes or for placements.
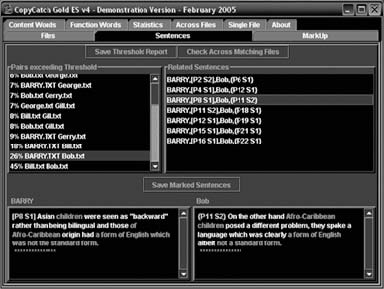
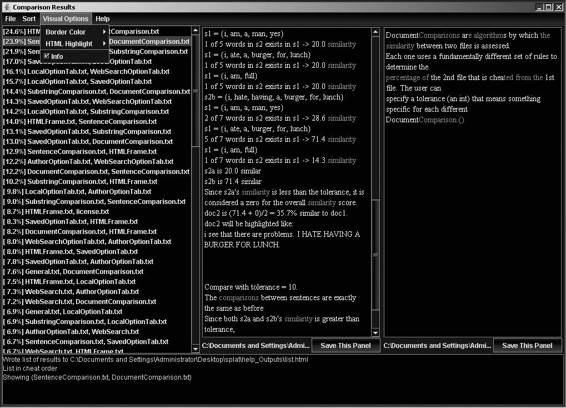
Tool: CopyCatch CopyCatch supports various formats such as Rich Text Format (RTF), Microsoft Word documents, and text. After checking documents for plagiarism, this utility highlights the changes on the screen and saves them in RTF format. It includes Web search comparison, zip archive submission, and course/module filtering. CopyCatch is shown in Figure 9-3.
Tool: Copy Protection System (COPS) The Copy Protection System (COPS) is an experimental working prototype of a copy detection system that can be used in a digital library. The COPS part of the project is to
Copyright
9-13
Figure 9-2 The Turnitin originality report shows the similarities
between documents.
Figure 9-3 CopyCatch compares sentences between documents.
detect exact or partial copies of documents in the library in TeX, DVI, and Troff formats. The system looks for documents with significant overlap as well as exact copies.
These documents are first converted into ASCII format. They are then divided into sentences called units, and these sentences are further grouped together to form a series of sentences called chunks. These sentences are stored in a registration server that is simply a large hash table using a standard hashing algorithm. These chunks are compared with the other documents to check whether there is overlapping. If the documents share a preset number of sentences, then a violation is flagged. Figure 9-4 shows the COPS architecture.
![]()
9-14
Chapter 9
Test to ASCII
DVI to ASCII
Troff to ASCII
Sentence Identification and Hashing
Document Processing
Query Processing
Database
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 9-4 COPS compares large amounts of documents for similarities.
Tool: Stanford Copy Analysis Mechanism (SCAM) The Stanford Copy Analysis Mechanism (SCAM) is another system designed for detecting plagiarism, copies, extracts, and strongly similar documents in digital libraries. The main difference between SCAM and COPS is that SCAM is a word-based scheme, whereas COPS is sentence-based. The problem with simply comparing sentences is that partial sentence overlaps are not detected. Figure 9-5 shows the functionality of SCAM.
The documents are divided into words (units) and these are grouped to form chunks. The chunks are inserted into the repository in an inverted index structure and are used to compare with new document arrivals. SCAM
uses words as chunks for comparison, allowing the system to detect partial sentence overlap. SCAM uses a derivative of the vector-space model to measure similarity between documents. This is a popular information retrieval (IR) technique and operates by storing the normalized frequency of words within the document as a vector. The vectors are then compared for similarity, using a measure such as the vector dot product or cosine-similarity measure and a resulting value. If this measure exceeds a predefined threshold, the document is flagged.
Tool: CHECK CHECK maintains a database for registered documents in order to compare them with the new document. With the help of the IR system, CHECK filters out the probable plagiarism candidates. Later, the IR
process is applied to sections, subsections, paragraphs, and finally individual sentences.
Comparison of two documents is mainly based on keywords because they identify the semantic meaning of the document. Computer programs are well structured and preserve the parse tree of the original program, even though changes were made to them. Finding plagiarism in a document is harder because the document protects the semantics of the original; however, it makes more changes when compared to a computer program.
CHECK merges the weighted words into the parse tree to capture a better representation that is resistant to simple document modifications. It identifies the LaTeX documents at the time of writing.
CHECK works in the following ways:
• Document recognition: The LaTeX recognizer parses the documents and creates a new document tree.
• Keyword extraction: IR techniques are used to extract the words. These words explain the semantics of the document. These words are classified into the following two classes:
• Open-class words consist of nouns, verbs, adjectives, and adverbs.
• Closed-class words consist of prepositions, pronouns, conjunctions, and interjections.
• Generating structural characteristics: For each and every document, a structural characteristic (SC) must be generated. It looks like a document that is mixed with an extracted set of keywords.
![]()
Copyright
9-15
Web Server
Postscript,
HTML, Word
Mail Server
Chunker
Parser
Copy Detection
Bulk Loader
Mailing Lists, Web Pages
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 9-5 SCAM compares words to other documents in a database.
Figure 9-6 JPlag compares code files and displays results graphically.
Tool: JPlag JPlag detects software plagiarism by identifying the similarities between multiple sets of code files. It does not compare the bytes of the text, but it compares the programming language syntax and program structure in order to distinguish the similarities between plagiarized files.
JPlag supports programming languages like Java, C, and C++. It also supports Scheme and natural language texts. Results are displayed in a graphical interface, shown in Figure 9-6.
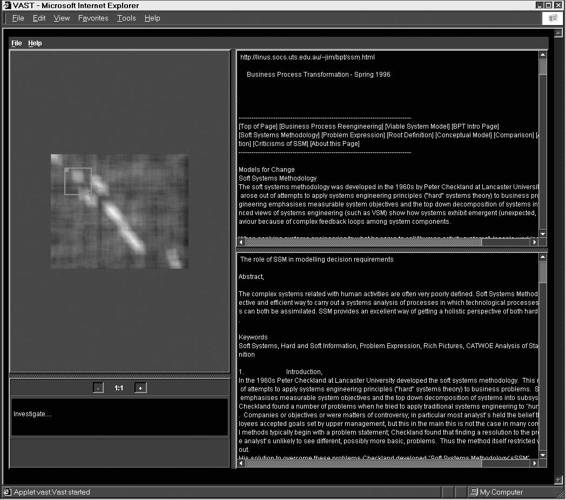
Tool: VAST The Visual Analysis of Similarity Tool (VAST) offers an interactive visualization of two different documents and highlights the areas that are plagiarized. It is used to investigate the extent and similarity of the text that is detected by tools like PRAISE (mentioned later).
In Figure 9-7, the upper document was downloaded from the Web and the lower document was an assignment submitted by a computing student.
Once two documents have been pasted, the type of image can be selected, and pressing the Create Image button will start the generation of the image. The default image type is unsequenced, which ignores the sequence in which words common to both documents appear. The alternative is sequenced, which includes this information; however, the sequenced option takes significantly longer to prepare.
9-16
Chapter 9
Figure 9-7 VAST displays documents graphically, highlighting similarities.
Two totally identical documents would generate a square image with a single dark band along the prime upper-left, lower-right diagonal.
Figure 9-7 indicates that the start of both documents is similar; following that, there is some original material in the lower document. The two areas mirrored across the diagonal suggest some simple rearrangement of the Web upper document in the lower document, following which there is a long similar section. The document ends with some original material in the lower document before another small similar section.
Projecting the dark areas onto a horizontal line indicates how much of the upper document appears in the lower one. Likewise, a vertical projection indicates how much of the lower document appears in the upper.
Tool: SIM SIM, or Software Similarity Tester, is used to detect the similarity between two computer programs.
It examines the correctness, style, and uniqueness of the program.
Each input C source file is passed to the lexical analyzer to generate a compact structure in terms of streams of integers known as tokens. Each token symbolizes either arithmetical or logical operations like a punctuation symbol, a C macro, a keyword, a numeric or string constant, a comment, or an identifier.
After the two source files get tokenized, the token stream of the second program is divided into sections. Each section represents a module of the original program, and each module gets compared with the token stream of the first program separately. This technique enables SIM to detect similarities even if the positions in the module are changed.
When the tokens are compared, their alignment is scored as follows:
• A match involving two identifier tokens scores 2; other matches score 1.
• A gap scores –2.
• A mismatch involving two identifiers scores 0; other mismatches score –2.
The total alignment score is calculated from the individual score for each block, and then it is normalized.
This process is shown in Figure 9-8.
Tool: PLAGUE PLAGUE, or Plagiarism in University Environments, is an open repository of resources assist-ing students and academics in detecting plagiarism in software code and protecting themselves against it.
![]()
Copyright
9-17
File1
Token
Program
Source
Tokens
Scanner
Alignment
Sigma
Block
Tokens
Source
Function
File2
Function
Block
Token
Normalized
Score
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 9-8 SIM compares computer programs.
PLAGUE compares all of the following:
• Comments and layout
• Case
• Identifier replacement
• Program output variations
• String/character constant variations
• Order of functions and classes
• Order of case/if-else branches
• Redundant syntax
• Lexical token streams
• Artificial bias resulting from tight specifications or reusable exercise templates
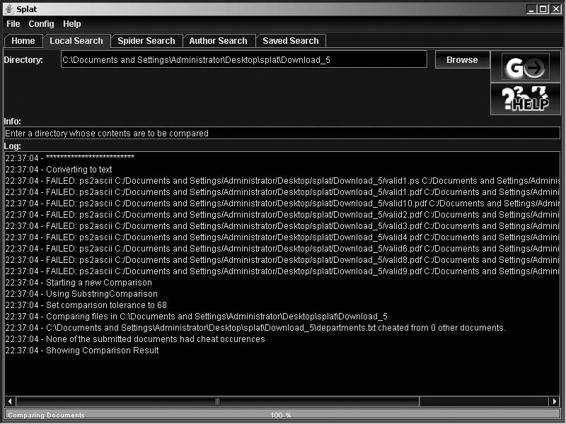
Tool: SPlaT SPlaT checks documents for any similarity between them. It functions in the following four modes:
• Web spider mode: SplaT crawls through the Web sites of any department in the organization and downloads research papers to search for plagiarism.
• Reviewer’s workbench mode: SPlaT compares a paper under review to a record of the author’s previously published articles extracted from Web sites and online article repositories.
• Author mode: SPlaT allows authors, who are wary of committing self-plagiarism by accident, to check a new paper against their previous publications.
• Local search: SPlaT compares files already downloaded to a directory.
Figure 9-9 shows SPlaT running. The results show a list of all comparisons that had nonzero overlap, sorted alphabetically or by cheat amount. Clicking on any entry will show the two files side by side with the overlaps highlighted, as shown in Figure 9-10.
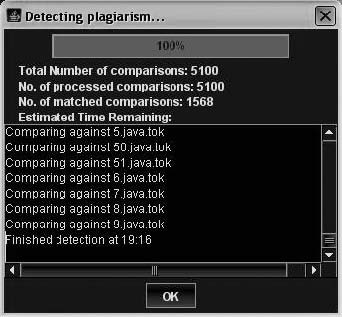
Tool: Sherlock Sherlock is a command-line program that finds the similarities between textual documents. It uses digital signatures for finding similar pieces of text in the documents. It works with text files, source code files, and assignments that are in digital form. It works with tar files, but not other compressed files. Sherlock is shown in action in Figure 9-11.
9-18
Chapter 9
Figure 9-9 SPlaT compares documents for similarities.
Figure 9-10 SPlaT highlights the similarities between files.
Copyright
9-19
Figure 9-11 Sherlock detects plagiarism between
text documents.
The following are some example Sherlock commands:
• Sherlock *.txt
This compares the text files in the directory and produces a list of files that are similar.
• Sherlock *.java
This compares the Java source files in the directory.
• Sherlock *.java > results.txt
This compares the Java source files in the directory and outputs the results to a file called results.txt.
Tool: Urkund Urkund checks documents against Web pages, published material, and other documents. After checking the documents, it sends an overview via e-mail. It exempts quotations from comparison and handles 300 different file types.
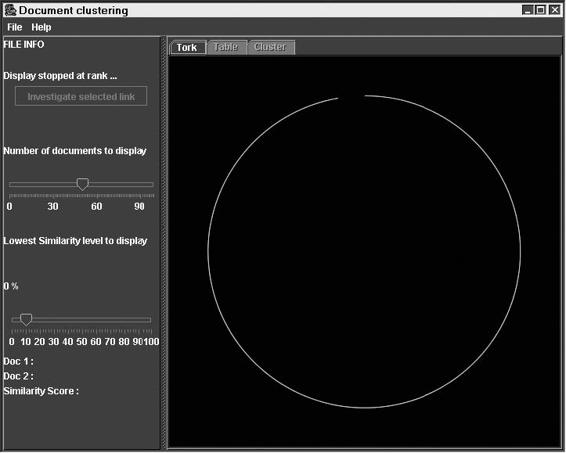
Tool: PRAISE Plotted Ring of Analyzed Information for Similarity Exploration (PRAISE) examines all the documents that are collected and plots them on a torc in a sequence determined by gross nonoriginality. A group of documents that are associated with a particular document are highlighted. A pair of documents can be selected for further investigation in VAST.
It works with plain text files, Microsoft Word documents, and HTML documents. The PRAISE interface is shown in Figure 9-12.
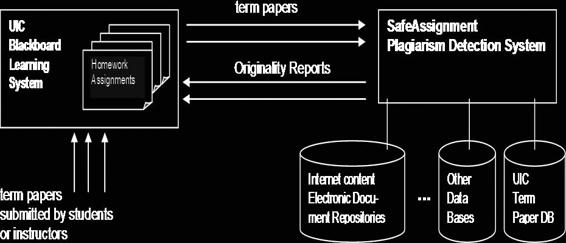
Tool: SafeAssignment SafeAssignment analyzes any text, sentence by sentence, in order to determine whether the sentences are taken from the Internet or from its databases. It creates convenient and easy-to-read reports where all the unoriginal content is highlighted. Its process is shown in Figure 9-13.
The originality detection process is simple and entirely automatic once the parameters of plagiarism-checked assignments have been set. It can detect even inexact matching. This is geared specifically toward teachers and may have limited usage in a corporate environment.
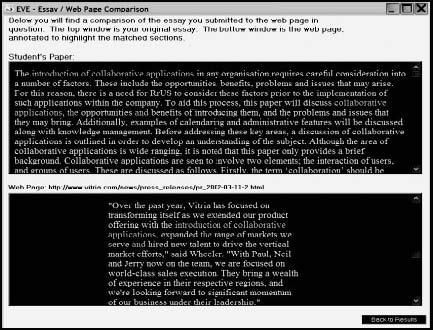
Tool: EVE2 (Essay Verification Engine) EVE2 determines if information is plagiarized from the World Wide Web. It accepts essays in plain text, Microsoft Word, or Corel WordPerfect format, and returns links to Web pages from which material may have originated, without too many false positives. Once the search is completed, a full report, including the percentage of the essay plagiarized and an annotated copy of the paper showing plagiarism highlighted in red, is presented. A report is shown in Figure 9-14.
![]()
9-20
Chapter 9
Figure 9-12 PRAISE clusters documents and plots them according
to their similarity.
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 9-13 SafeAssignment compares text, sentence by sentence, with its
own databases.
Tool: WCopyfind WCopyfind extracts the text portions of a collection of document files. It then searches them for matching words in phrases of a specified minimum length. If WCopyfind finds two files that share enough words in those phrases, it generates a report in HTML format. The report contains the text of both documents with the matching phrases underlined. It can handle text, HTML, and some older word processor files.
Tool: iThenticate iThenticate compares documents to a publications database comprising more than 10,000 major newspapers, magazines, and journals. It is designed to provide service for corporate organizations. Its interface is pictured in Figure 9-15.

Copyright
9-21
Figure 9-14 EVE2 compares documents to Web sites.
Figure 9-15 iThenticate checks against newspapers, magazines, and journals
for plagiarism.
Tool: Glatt The Glatt Plagiarism Screening Program (GPSP) is a comprehensive computer software program specifically designed for detecting plagiarism.
Tool: Dupli Checker Dupli Checker ( http://www.duplichecker.com) is a freeware online plagiarism detection tool, shown in Figure 9-16.
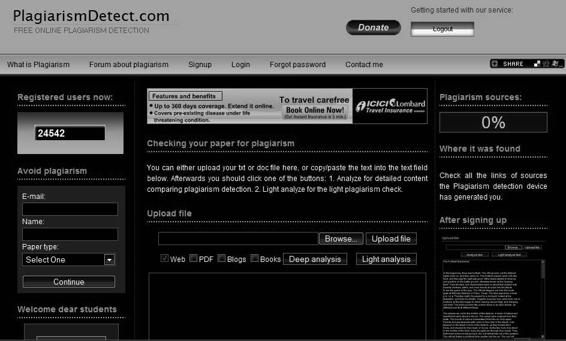
Tool: PlagiarismDetect.com PlagiarismDetect.com is another freeware online plagiarism detection tool, shown in Figure 9-17.
9-22
Chapter 9
Figure 9-16 Dupli Checker uses search engines to check text for plagiarism.
Figure 9-17 PlagiarismDetect.com is freeware.
Tool: Forensic Linguistics Institute The Forensic Linguistics Institute, whose antiplagiarism Web site is shown in Figure 9-18, is mainly aimed at researchers, and performs the following tasks on a submitted work:
• Does a brief study of the work’s field of research
• Compares the work’s research aims and the current research profile of the field
Patent
9-23
Figure 9-18 The Web site of the Forensic Linguistics Institute ( http://
plagiarism.org.uk) is one of the longest running antiplagiarism sites.
• Compares the work’s conclusions with what is already publicly available on the Internet
• Offers search for collocations of keywords
• Checks to see that important quotes have been properly referenced
• Reports on any extent to which the work appears to infringe on existing works
• Issues a certificate reporting on the work done by the Web site
Patent
A patent is a property right granted to the inventor by the USPTO to keep others from making, using, or selling the invention without authorization. A patent is effective for up to 20 years from the date it is filed. According to patent law, a patent is granted on the new and unique article. Any article, process, or manufacture that claims patent is required to prove its usefulness.
Patent law says that an invention cannot be patented if the invention already existed and was known or used by others prior to the applicant’s invention. Also, an invention cannot be patented if it has already been patented or if it has been sold or used publicly for at least a year.
There are three types of patents:
1. Utility patents are granted to individuals who discover or invent new machines, processes, useful composi-tions of matter, or manufactured items, such as the following:
• Machine: motorcycle, car
• Process: fraction distillation of petroleum
• Composition of matter: alloys, drugs
• Manufactured item: paper, calculator
9-24
Chapter 9
2. Design patents are granted to individuals who invent new original designs for an article to be manufactured. It protects the appearance of an article. Examples include a computer cabinet or a container.
3. Plant patents are granted to individuals who invent, discover, or asexually reproduce new varieties of plants.
Patent Infringement
According to the USPTO, “Patent infringement is unauthorized making, using, offering to sell, selling or import-ing into the United States any patented invention.” Infringement can be classified as one of the following:
• Direct infringement is selling, using, or making a patented creation. It can be classified as the following:
• Literal infringement occurs with each limitation in the asserted claims present in the accused device.
• Infringement under the doctrine of equivalents occurs when the difference between the patented device and the accused device becomes insubstantial.
• Indirect infringement is instigating another person to sell, make, or use a patented invention.
• Contributory infringement is participating in the making or supplying of products that are meant for a patented invention.
Resolving patent infringement is a two-step process involving the following:
1. Analyzing the claims by going through all patented documents
2. Verifying the claim for its authenticity
Patent Search
The following is the seven-step strategy proposed by the USPTO for a patent search:
1. Index to the U.S. Patent Classification: It is an alphabetical index in which someone can view the general terms depicting the invention and its function, effect, end product, structure, and use. A person can note class and subclass numbers and can then refer to the Manual of Classification.
2. Manual of Classification: Class and subclass numbers noted down earlier can be referenced to find out where the terms fall within the U.S. Patent Classification System. Search the entire class and give importance to the dot indent.
3. Classification Definitions: Go through the definitions to establish the relevancy of classes and subclasses to the search. The definitions comprise important search notes and suggestions that can be referred to in further searches.
4. Browse Patent Titles and Abstracts: Inspect whether the search is in the right direction or not. If not, redirect the search and find out lists of patents and published applications containing the right keywords to initiate the search again.
5. Retrieve Subclass Listing: Retrieve a list of all patent numbers (granted from 1790 to the present) once the relevant classes or subclasses are identified.
6. Official Gazette—Patent Section: Refer to the Gazette section and find out ideal claims and a representative drawing for all patents on the lists. This step will eliminate unrelated patents. Published applications can be viewed online.
7. Complete Patent Document: Examine the complete text and drawings of relevant patents and compare it with the invention. This will help in determining similarities and dissimilarities in the invention and published patents.
Tool: http://www.ip.com
The IP.com Prior Art Database provides companies with a way to publish their innovations in a publicly searchable, library-indexed collection of prior art. It allows a company to easily provide evidence in the event of a patent dispute.
Intellectual Property
9-25
How IP.com Works
1. Prepare a disclosure using normal business software, such as Microsoft Word.
2. Upload the files, along with some bibliographic information about the file, to the servers at IP.com.
3. Files are scanned and digital fingerprints are generated. Fingerprints provide a digital signature of a file’s contents.
4. The primary file is automatically scanned for searchable text content, which gets extracted from the document in order to make it searchable.
5. Additional IP.com-generated information is bundled with the document into a single Zip file.
6. The newly generated package is assigned a permanent IP.com number. IP.com numbers are assigned to uniquely identify protected files at IP.com.
7. The new disclosure is published and available online via the IP.com site.
Domain Name Infringement
Anyone can register a domain name, but if it conflicts with an existing trademark, it constitutes domain name infringement. Responsibility lies with the domain name registrant to comply with trademark laws. Domain name infringement can be avoided if the domain name registrant checks whether their trademark is infringing upon another’s trademark before registering. If not, he or she can register a trademark. Consulting an attorney familiar with the Internet, trademarks, and related laws prior to domain name registration is another way to prevent domain name infringement.
How to Check for Domain Name Infringement
A potential domain name proprietor can avoid the risk of trademark infringement by conducting a thorough investigation before registering a trademark. In order to minimize the chances of litigation, follow these five steps:
1. Use search engines such as Google to find out whether a domain name is already in use or not. Thoroughly examine all the links that could contain domain names identical to the desired name. This search can display all the businesses or services that have similar domain names. If the desired domain name is already registered, seek another domain name.
2. Search Whois.net to find out if any other businesses contain text identical to the desired domain name.
Domain Surfer can also be utilized for a text string search. Domain Surfer is a Web site dedicated to help trademark owners and prospective domain name owners do a quick search to determine if a domain name is already registered.
3. Examine the Trademark Electronic Search System (TESS). This database contains trademarks and service marks that are all federally registered. It also contains dead or dumped trademarks and service marks, and all pending applications for trademark registration.
4. Engage an efficient search firm to do a national trademark, service mark, and domain name search. Search firms such as Thomson & Thomson do a comprehensive search and provide all results in a written report.
5. Appoint a trademark attorney to perform all activities described in the above steps. Domain name registration requires an attorney’s skills and knowledge to interpret trademark laws, give answers to questions such as whether a desired domain name will infringe upon another’s trademark, and so on.
Intellectual Property
Intellectual property is the product of intellect that includes copyrights and trademarks for commercial use. It is protected through various copyright, trademark, and patent laws. It is broadly classified into two types, which are as follows:
• Copyright: a product of intellect that includes literary and artistic works
• Industrial property: a product of intellect that includes patents, trademarks, industrial designs, and geographic indications of the source
9-26
Chapter 9
Investigating Intellectual Property Theft
Intellectual property theft includes the theft of the following:
• Unregistered trade secrets
• Copyrighted, patented, or registered works
• Trademark violations
• Confidential proposals
• Confidential work papers
• Technical notes
• Strategic business planning
• Gray-market distributions
• Counterfeiting
• Illegal distributions
• Unauthorized product diversions
• Trade names or partials
Steps for Investigating Intellectual Property Theft
The following are the steps involved in investigating intellectual property theft:
1. Check the type of theft.
2. Look for clues that indicate theft of intellectual property by:
a. Performing a plagiarism check
b. Checking whether the theft is from a single source or more than one
c. Checking if there is a lack of reference or quoting for referred information
d. Checking if the information is directly taken from the source
3. Search and find the source of the theft.
4. Use detection tools or various plagiarism detection tools to find the source.
5. Check for unauthorized sharing of software.
6. Document all the information for further reference.
Digital Rights Management (DRM)
Digital rights management (DRM) is access-control technology used by manufacturers, publishers, and copyright holders to limit the usage of digital devices or information. It describes the technology that prevents unauthorized distribution and usage of content, media, or devices. It has been adopted by the entertainment industry, most online music stores, and e-book publishers.
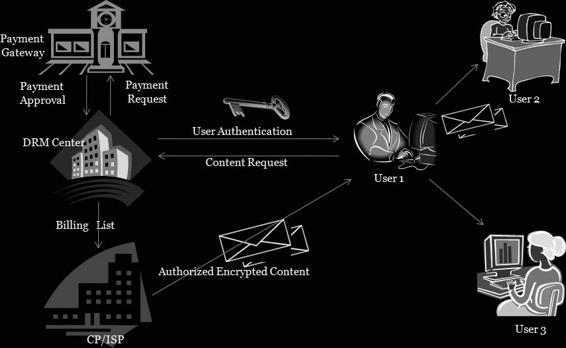
DRM involves the following:
• Users pay for the content and gain it through their provider.
• The content provider or Internet service provider (ISP) takes the billing list from the DRM center and sends authorized or encrypted content to the user.
• The payment gateway takes payment requests from the DRM center and sends an approval of payment to it.
• The DRM center takes content requests from the user after payment approval and then sends the billing list to the content providers or ISPs and authentication to the user.
This process is shown in Figure 9-19.
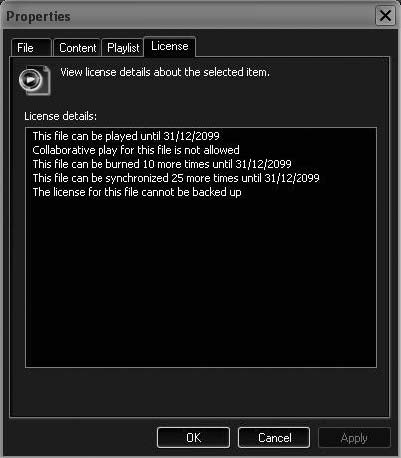
Tool: Windows Media Digital Rights Management
Windows Media Digital Rights Management (DRM) is a DRM solution included with Windows and is shown in Figure 9-20.
![]()
Digital Rights Management (DRM)
9-27
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 9-19 DRM allows the user to use protected content.
Figure 9-20 Windows Media Digital Rights Management is
included with Windows.
9-28
Chapter 9
Tool: Haihaisoft Media DRM Platform
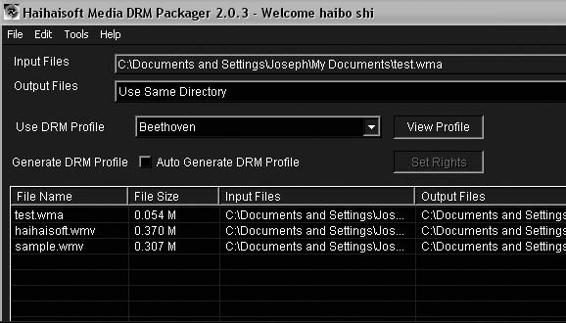
The Haihaisoft Media DRM Platform enables the secure deployment of digital audio and video media. It provides a media DRM packager and an online management account. The packager is pictured in Figure 9-21.
Tool: LockLizard
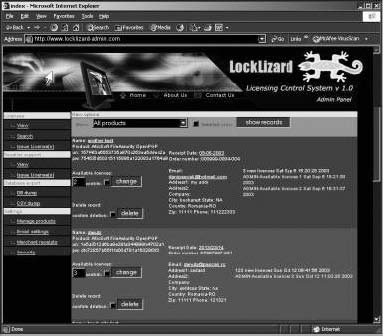
LockLizard is a document security and copy-protection program for PDF files, Flash files, e-books, and Web-based content. It protects information with strong encryption and DRM controls to ensure complete protection against copyright infringement. It can stop copying, prevent printing, disable Print Screen, expire content, and instantly revoke access to information. It provides copyright protection without the use of passwords to ensure maximum security, and to protect information, documents, and Web content from unauthorized use no matter where it resides. LockLizard’s Web interface is shown in Figure 9-22.
Tool: IntelliProtector
IntelliProtector is a software activation service with a Web-based control panel that helps reduce a form of piracy known as casual copying. Casual copying is when people share software in a way that infringes on the software’s end-user license agreement (EULA).
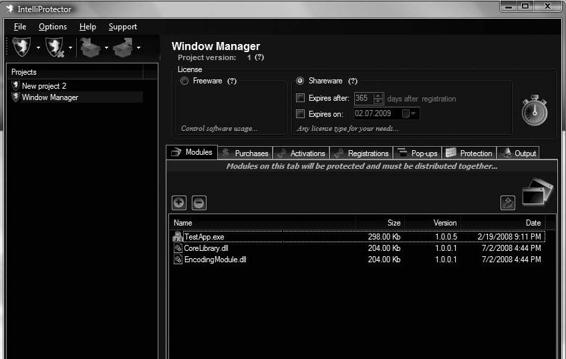
IntelliProtector enables distribution of software securely over the Internet, on CD-ROM, and on DVD. It ensures that users comply with the license terms associated with the product. This includes not sharing the product or using it simultaneously on more than one computer. The service provides reporting features, detailed statistics, and automatic license-key management. Its Window Manager is shown in Figure 9-23.
IntelliProtector includes the following features:
• Protection against piracy
• Creates time-limited and feature-limited trials
• Blocks license violators automatically
• Integration with all popular payment processors
• Automatic delayed delivery of the license code
• Powerful reporting and statistics
Figure 9-21 Haihaisoft Media DRM Packager adds DRM to media files.
Digital Rights Management (DRM)
9-29
Figure 9-22 LockLizard provides real-time licensing control for documents.
Figure 9-23 IntelliProtector provides several options for protecting software.
9-30
Chapter 9
U.S. Laws for Trademarks and Copyright
The following sections discuss U.S. laws concerning trademarks and copyright.
The Digital Millennium Copyright Act (DMCA) of 1998
This act was signed into law and passed on October 28, 1998, by President Clinton. It is subdivided into five titles:
• WIPO (World Intellectual Property Organization) Copyright and Performances and Phonograms Treaties Implementation Act of 1998 implements the WIPO treaties.
Article 11 of the WCT (WIPO Copyright Treaty) states:
Contracting Parties shall provide adequate legal protection and effective legal remedies against the circumvention of effective technological measures that are used by authors in connection with the exercise of their rights under this Treaty or the Berne Convention and that restrict acts, in respect of their works, which are not authorized by the authors concerned or permitted by law.
Article 12 of the WCT provides the relevant part:
Contracting Parties shall provide adequate and effective legal remedies against any person knowingly performing any of the following acts, or with respect to civil remedies having reasonable grounds to know, that it will induce, enable, facilitate or conceal an infringement of any right covered by this Treaty or the Berne Convention:
(i) to remove or alter any electronic rights management information without authority;
(ii) to distribute, import for distribution, broadcast, or communicate to the public, without authority, works or copies of works knowing that electronic rights management information has been removed or altered without authority.
The new section 1202 is the provision implementing this obligation to protect the integrity of Copyright Management Information (CMI). The scope of the protection is set out in two separate paragraphs, the first dealing with false CMI and the second with removal or alteration of CMI.
Subsection (a) prohibits the knowing provision or distribution of false CMI, if done with the intent to induce, enable, facilitate, or conceal infringement.
Subsection (b) bars the intentional removal or alteration of CMI without authority, as well as the dissemination of CMI or copies of works, knowing that the CMI has been removed or altered without authority.
• Online Copyright Infringement Liability Limitation Act:
Title II of the DMCA adds a new section 512 to the Copyright Act3 to create four new limitations on liability for copyright infringement by online service providers. The limitations are based on the following four categories of conduct by a service provider:
1. Transitory communications;
2. System caching;
3. Storage of information on systems or networks at the direction of users; and
4. Information location tools.
• Computer Maintenance Competition Assurance Act:
Title III expands the existing exemption relating to computer programs in section 117 of the Copyright Act, which allows the owner of a copy of a program to make reproductions or adaptations when necessary to use the program in conjunction with a computer. The amendment permits the owner or lessee of a computer to make or authorize the making of a copy of a computer program in the course of maintaining or repairing that computer.
The exemption only permits a copy that is made automatically when a computer is activated, and only if the computer already lawfully contains an authorized copy of the program. The new copy cannot be used in any other manner and must be destroyed immediately after the maintenance or repair is completed.
U.S. Laws for Trademarks and Copyright
9-31
• Miscellaneous provisions:
Section 401(b) adds language to section 701 of the Copyright Act confirming the Copyright Office’s authority to continue to perform the policy and international functions that it has carried out for decades under its existing general authority.
• Vessel Hull Design Protection Act:
Title V of the DMCA, entitled the Vessel Hull Design Protection Act (VHDPA), adds a new chapter 13 to Title 17 of the U.S. Code. It creates a new system for protecting original designs of certain useful articles that make the article attractive or distinctive in appearance. For purposes of the VHDPA, “useful articles” are limited to the hulls (including the decks) of vessels no longer than 200 feet.
The Lanham (Trademark) Act (15 USC §§ 1051–1127)
This act was first passed on July 5, 1946, and was signed into law by President Harry Truman. It concerns activities like trademark infringement, trademark dilution, and false advertising, and is subdivided into four chapters, one of which is partially quoted below:
TITLE 15 – COMMERCE AND TRADE
CHAPTER 22 – TRADEMARKS
SUBCHAPTER III – GENERAL PROVISIONS
Sec. 1114. Remedies; Infringement; Innocent Infringement By Printers And Publishers
(1) Any person who shall, without the consent of the registrant —
a) use in commerce any reproduction, counterfeit, copy, or colorable imitation of a registered mark in connection with the sale, offering for sale, distribution, or advertising of any goods or services on or in connection with which such use is likely to cause confusion, or to cause mistake, or to deceive; or
b) reproduce, counterfeit, copy, or colorably imitate a registered mark and apply such reproduction, counterfeit, copy, or colorable imitation to labels, signs, prints, packages, wrappers, receptacles or advertisements intended to be used in commerce upon or in connection with
the sale, offering for sale, distribution, or advertising of goods or services
(2) Notwithstanding any other provision of this chapter, the remedies given to the owner of a right infringed under this chapter or to a person bringing an action under section 1125(a) of this title shall be limited as follows:
a) Where an infringer or violator is engaged solely in the business of printing the mark or violating matter for others and establishes that he or she was an innocent infringer or innocent violator, the owner of the right infringed or person bringing the action under section 1125(a) of this title shall be entitled as against such infringer
b) Where the infringement or violation complained of is contained in or is part of paid advertising matter in a newspaper, magazine, or other similar periodical or in an electronic com-
munication as defined in section 2510(12) of title 18
Doctrine of “Fair Use”
Section 107 of the Copyright Law mentions the doctrine of “fair use.” This doctrine is a result of a number of court decisions over the years. Reproduction of a particular work for criticism, news reporting, comment, teaching, scholarship, and research is considered as fair according to Section 107 of the Copyright Law. The copyright office does not give permission to use copyrighted works. It is advised to obtain permission from the owner of a particular copyrighted work.
Section 107 also sets out four factors to be considered in determining whether or not a particular use is fair:
• The purpose and character of the use, including whether such use is of commercial nature or is for nonprofit educational purposes;
• The nature of the copyrighted work;
9-32
Chapter 9
• Amount and substantiality of the portion used in relation to the copyrighted work as a whole; and
• The effect of the use upon the potential market for or value of the copyrighted work.
One cannot easily differentiate between fair use and copyright infringement. There is no mention of the number of lines, words, and notes that one can take from a copyrighted work and still escape infringement.
Investigating Copyright Violations
Copyright violation can be investigated in the following ways:
1. Explanations of parties and third persons
2. Testimonial evidences
3. Written and material evidence
4. Audio and video records
5. Conclusions of experts
The following are the evidence of copyright violations:
• The documents received by law enforcement agencies during checks committed by them on their own initiative or by complaints of rights owners
• Record of examination of computer and software
• Record of examination of a tangible carrier where the installation of software products on the computer was performed
• Conclusion of expert performing examination of the seized computer and tangible carriers with software
• Delivery note or cash memo for the purchased computer
• Warranty statement on the purchased computer
• Explanations of the employees of the seller company, explanations of the customer
• Copies of statutory documents of a legal entity (statute and foundation agreement)
• Job functions of the organization directly related to selling computer facilities and software
• Advertising materials and price lists evidencing that accused person carried out entrepreneurial activity
• Other documents related to the software's illegal sale or distribution in any form
Counterfeit samples of software, the production or use of which involves copyright violations, are also referred to as evidence of copyright violation. Advertising materials, price lists, documents on goods, and other materials evidencing copyright violation are also regarded as evidence along with counterfeit samples.
During investigation, it is necessary to establish, at least approximately, the volume of the obtained revenue from the violation of copyright and adjacent rights.
The following accounting documents should be analyzed and attached to the file:
• Reports of different checks and inspections;
• Delivery notes, charge tickets, other documents reflecting transaction of products and payment;
• Financial statements (reports delivered to tax office);
• Agreements reflecting facts of criminal activity (transportation of products, issuance of goods to distributors, storing products at some place in some amount, etc.)
• U.S. laws for trademarks and copyright
Online Copyright Infringement Liability Limitation Act
Sec. 512. Limitations on liability relating to material online
a) LIMITATION– Notwithstanding the provisions of section 106, a provider shall not be liable for—
(1) Direct infringement, based solely on the intermediate storage and transmission of material over that provider’s system or network, if—
(A) The transmission was initiated by another person;
(B) The storage and transmission is carried out through an automatic technological process, without any selection of that material by the provider; and
Indian Laws for Trademarks and Copyright
9-33
(C) Any copy made of the material is not retained longer than necessary for the purpose of carrying out that transmission;
(2) Monetary relief under section 504 or 505 for contributory infringement or vicarious liability, based solely on conduct described in paragraph (1); or
(3) Monetary relief under section 504 or 505 for contributory infringement or vicarious liability, based solely on transmitting or providing access to material over that provider’s system or network, other than conduct described in paragraph (1), if the provider—
(A) Does not know and is not aware of information indicating that the material is infringing; and (B) Does not receive a financial benefit directly attributable to the infringing activity.
b) PROTECTION OF PRIVACY—Nothing in subsection (a) shall authorize or obligate a provider
to access material that the provider is prohibited by law from accessing, or impose an affirmative obligation to monitor or otherwise seek information indicating infringement.
c) LIMITATION BASED UPON REMOVING OR DISABLING ACCESS TO INFRINGING
MATERIAL—A provider shall not be liable for any claim based on that provider’s removing or disabling online access to material, in response to knowledge or information indicating that the material is infringing, whether or not the material is infringing.
d) OTHER DEFENSES NOT AFFECTED—Removing or disabling access to material which a pro-
vider transmits online or to which a provider provides online access, or the failure to do so, shall not adversely bear upon the consideration by a court of a defense to infringement asserted by that provider on the basis of section 107 or any other provision of law.
e) MISREPRESENTATIONS—Any person who knowingly materially misrepresents that material
online is infringing shall be liable for any damages, including costs and attorneys’ fees, incurred by the alleged infringer or by any copyright owner or copyright owner’s authorized licensee who is injured by such misrepresentation, or by any provider who relies upon such misrepresentation in removing or disabling access to the material claimed to be infringing.
Indian Laws for Trademarks and Copyright
The Patents (Amendment) Act, 1999
(1) This Act may be called the Patents (Amendment) Act, 1999.
(2) It shall be deemed to have come into force on the 1st day of January, 1995.
24B. (1) Where a claim for patent covered under subsection (2) of section 5 has been made and the applicant has—
a) where an invention has been made whether in India or in a country other than India and
before filing such a claim, filed an application for the same invention claiming identical
article or substances in a convention country on or after the 1st day of January, 1995
and the patent and the approval to sell or distribute the article or substance on the basis
of approval tests conducted on or after the 1st day of January, 1995, in that country has
been granted on or after the date of making a claim for patent covered under subsection
(2) of section 5; or
b) where an invention has been made in India and before filing such a claim, made a claim for patent on or after the 1st day of January, 1995 for method or process of manufacture for
that invention relating to identical article or substance and has been granted in India the
patent therefore on or after the date of making a claim for patent covered under subsection
(2) of section 5, and has received the approval to sell or distribute the article or substance from the authority specified in this behalf by the Central Government
Trade Marks Act, 1999
This act was signed into law and was passed on December 23, 1999, by the Indian parliament. This law repealed and replaced the Trade and Merchandise Marks Act. This law provides the registration of trademarks relating to goods and services.
9-34
Chapter 9
This law states that it is considered an offense if, a person who-
a) Falsifying and falsely applying trademarks
b)
Without the assent of the proprietor of the trademark makes that trademark or a deceptively similar mark; or c) Falsifies any genuine trademark, whether by alteration, addition, effacement or otherwise.
(2) A person shall be deemed to falsely apply to goods or services a trademark who, without the assent of the proprietor of the trademark,
a)
applies such trademark or a deceptively similar mark to goods or services or any package containing goods; b)
Uses any package bearing a mark which is identical with or deceptively similar to the trademark of such proprietor, for the purpose of packing, filling or wrapping therein any goods other than the genuine goods of the proprietor of the trademark.
(4) In any prosecution for falsifying a trademark or falsely applying a trademark to goods or services, the burden of proving the assent of the proprietor shall lie on the accused.
And who selling goods or providing services to which false trademark or false trade description is applied.
Any person who-
Causes any of things above-mentioned in this section to be done,
Shall, unless he proves that he acted, without intent to defraud, be punishable with imprisonment for a term which shall not be less than six months but which may extend to three years and with fine which shall not be less than fifty thousand rupees but which may extend to two lakh rupees:
PROVIDED that the court may, for adequate and special reasons to be mentioned in the judgment, impose a sentence of imprisonment for a term of less than six months or a fine of less than fifty thousand rupees.
Source: http://www.indialawinfo.com/bareacts/cpr.html
The Copyright Act, 1957:
This Act may be called the Copyright Act, 1957; it extends to the whole of India.
This law states that, it is an offense when -
Any person who knowingly infringes or abets the infringement of-
a) the copyright in a work, or
b) any other right conferred by this Act, [except the right conferred by section 53A],
shall be punishable with imprisonment for a term which shall not be less than six months but which may extend to three years and with fine which shall not be less than fifty thousand rupees but which may extend to two lakh rupees:
PROVIDED that [where the infringement has not been made for gain in the course of trade
or business] the court may, for adequate and special reasons to be mentioned in the judgment, impose a sentence of imprisonment for a term of less than six months or a fine of less than fifty thousand rupees.
Any person who knowingly makes use on a computer of an infringing copy of a computer pro-
gram shall be punishable with imprisonment for a term which shall not be less than seven days but which may extend to three years and with fine which shall not be less than fifty thousand rupees but which may extend to two lakh rupees.
Possession of plates for purpose of making infringing copies
Any person who knowingly makes, or has in his possession, any plate for the purpose of making infringing copies of any work in which copyright subsists shall be punishable with imprisonment which may extend to two years and shall also be liable to fine.
Japanese Laws for Trademarks and Copyright
Trademark Law
The Trademark Law that was promulgated in Japan on June 12, 1996, entered into effect on April 1, 1997. The following are the principal changes that were effected by the law:
• Three-dimensional trademarks consisting of the shape of goods or their packaging may be registered, provided they are distinguishable and are not indispensable to secure the function of the goods or their packaging.
• Collective trademarks may be registered.
Australian Laws for Trademarks and Copyright
9-35
• Associated trademarks registered or pending on April 1, 1997, are deemed to be independent trademarks.
• Applications for trademarks that are held to be identical or similar to a well-known trademark filed with an unjust purpose will be rejected, irrespective of whether there is a likelihood of confusion between the respective goods and/or services.
• A single application may cover several classes of goods and/or services. However, applications for the same mark filed on the same date in more than one class prior to April 1, 1997, may not be consolidated into one application.
• It is no longer necessary to submit evidence of use to support renewals of trademark registrations.
Belated renewals may be filed six months following the expiration date of the registration, subject to payment of additional fees.
• It is no longer necessary to publish a Notice of Assignment of a registered trademark.
• A general Power of Attorney is now accepted.
• Any person may file a cancellation action based on nonuse of a registered trademark for more than three consecutive years.
• Use of a registered trademark by the owner or licensee within three months prior to the date of filing of a cancellation action will not be considered legitimate use, provided that the petitioner in the cancellation action can prove that the trademark owner or licensee commenced such use upon becoming aware of the prospective cancellation action.
• If a cancellation action is successful, the trademark registration is deemed to have been cancelled retro-actively as of the date of filing of the cancellation action.
• A postregistration opposition procedure replaces the current preregistration opposition system. An opposition may be filed by any interested party within two months following the date of publication of a registered mark.
• Japan adopted the International Classification system on April 1, 1992. Under the new trademark law, the goods covered by those registered trademarks that were filed on or before March 31, 1992, in accordance with the four versions of the earlier Japanese classifications (of 1899, 1909, 1921, and 1959) will be reclassified in accordance with the International Classification system upon renewal.
The reclassification will commence with trademark registrations that expire on or after
October 1, 1998.
Copyright Management Business Law (4.2.2.3 of 2000)
In November 2000, the Copyright Management Business Law (4.2.2.3) was enacted. Its main purpose is to facilitate the establishment of new copyright management businesses, in order to “respond to the development of digital technologies and communication networks.”
Australian Laws for Trademarks and Copyright
The Trade Marks Act 1995
Section 145
(1) A person is guilty of an offense if the person falsifies or unlawfully removes a trademark that: a) has been applied to any goods that are being, or are to be, dealt with or provided in the course of trade; or
b) has been applied in relation to any goods or services that are being, or are to be, dealt with or provided in the course of trade;
Knowing that the trademark is registered or regardless of whether or not the trademark is
registered.
(2) A person falsifies a registered trademark if the person:
a) alters or defaces it; or
b) makes any addition to it; or
9-36
Chapter 9
c) partly removes, erases, or obliterates it;
without the permission of the registered owner, or an authorized user, of the trademark, Section 148
A person is guilty of an offense if the person intentionally:
a) sells goods; or
b) exposes goods for sale; or
c) has goods in his or her possession for the purpose of trade or manufacture; or
d) imports goods into Australia for the purpose of trade or manufacture; knowing that, or regardless of whether or not:
e) a falsified registered trademark is applied to them or in relation to them; or
f) a registered trademark has been unlawfully removed from them; or
g) a registered trademark is falsely applied to them or in relation to them.
Penalty for offense under section 145, 148
A person guilty of an offense under section 145, 146, 147 or 148 is punishable on conviction by: a) a fine not exceeding 500 penalty units; or
b) imprisonment for a period not exceeding 2 years; or
c) by both a fine and a term of imprisonment.
False representations regarding trademarks is also considered as the offense.
The Copyright Act 1968: Section 132
According to this law, following are the offenses:
Offenses relating to infringing copies
(1) A person shall not, at a time when copyright subsists in a work:
a) make an article for sale or hire or with the intention of obtaining a commercial advantage or profit;
b) sell or let for hire, or by way of trade, or with the intention of obtaining a commercial advantage or profit, offer or expose for sale or hire, an article;
c) import an article into Australia for the purpose of:
i. selling, letting for hire, or by way of trade, or with the intention of obtaining a commercial advantage or profit, offering or exposing for sale or hire, the article;
If the person knows, or ought reasonably to know, the article to be an infringing copy of the work.
(2) A person shall not, at a time when copyright subsists in a work, distribute:
a) for the purpose of trade or with the intention of obtaining a commercial advantage or profit; or b) for any other purpose to an extent that affects prejudicially the owner of the copyright; (3) A person shall not, at a time when copyright subsists in a work, make or have in his or her possession a device that the person knows, or ought reasonably to know, is to be used for making infringing copies of the work.
(4) The preceding provisions of this section apply in relation to copyright subsisting in any subject matter by virtue of Part IV in like manner as they apply in relation to copyright subsisting in a work by virtue of Part III.
Offense relating to infringing public performances of literary, dramatic or musical works
(5) A person shall not cause a literary, dramatic or musical work to be performed in public at a place of public entertainment, if the person knows, or ought reasonably to know, that copyright subsists in the work and that the performance constitutes an infringement of the copyright.
(5C) A person commits an offense if:
a) copyright subsists in a work or other subject matter; and
U.K. Laws for Trademarks and Copyright
9-37
b) either:
i. the person removes, from a copy of the work or subject matter, any electronic rights management information that relates to the work or subject matter; or
ii.
the person alters any electronic rights management information that relates to the work
or subject matter; and
c) the person does so without the permission of the owner or exclusive licensee of the copyright; and d) the person is reckless as to whether the removal or alteration will induce, enable, facilitate or conceal an infringement of the copyright.
U.K. Laws for Trademarks and Copyright
The Copyright, etc. and Trade Marks (Offences and Enforcement) Act 2002
This act was signed into law and passed on July 24, 2002, by the Department of Trade and Industry. This Act amends the criminal provisions in intellectual property law, more specifically the law relating to copyright, rights in performances, fraudulent reception of conditional access transmissions by use of unauthorized decod-ers, and trademarks.
The Copyright, etc. and Trade Marks (Offences and Enforcement) Act has three main powers. It:
• Increases the penalties for the offense of copyright theft to 10 years to match trademark law so it is no longer a low risk option for organized crime
• Strengthens search warrant provisions to make it easier to expose counterfeiting and piracy
• Gives greater powers to allow rights to owners to obtain forfeiture of infringing material to reduce the current potential return for criminals
Counterfeiting and piracy is now regularly included in the NCIS National Threat Assessment Report. It was clear that a stronger deterrent was needed, particularly as counterfeiting and piracy are increasingly linked with organized crime. Greater penalties provide that deterrent.
Trademarks Act 1994 (TMA)
This act was signed into law and passed on July 1, 1995. This law amends the registration of trademarks and protection of registered trademarks.
This law states that:
(1) A person commits an offense who, with a view to gain for himself or another, or with intent to cause loss to another, and without the consent of the proprietor-a) applies to goods or their packaging a sign identical to, or likely to be mistaken for, a registered trademark, or
b) sells or lets for hire, offers or exposes for sale or hire, or distributes goods which bear, or the packaging of which bears, such a sign, or
(2) A person commits an offense who, with a view to gain for himself or another, or with intent to cause loss to another, and without the consent of the proprietor -
a) applies a sign identical to, or likely to be mistaken for, a registered trademark to material intended to be used-i. for labeling or packaging goods,
ii. as a business paper in relation to goods, or
iii. for advertising goods, or
b) uses in the course of a business material bearing such a sign for labeling or packaging goods, as a business paper in relation to goods, or for advertising goods
(3) A person commits an offense who, with a view to gain for himself or another, or with intent to cause loss to another, and without the consent of the proprietor -
a) makes an article specifically designed or adapted for making copies of a sign identical to, or likely to be mistaken for, a registered trademark, or
9-38
Chapter 9
b) has such an article in his possession, custody, or control in the course of a business knowing or having reason to believe that is has been, or is to be, used to produce goods or
material for labeling or packaging goods, as a business paper in relation to goods, or for
advertising goods.
Chinese Laws for Trademarks and Copyrights
Copyright Law of People’s Republic of China (Amendments on
October 27, 2001)
• Article 1: The purpose of protecting the copyright of authors in their literary, artistic, and scientific works and the copyright-related rights and interests.
• Article 2: Works of Chinese citizens, legal entities, or other organizations, whether published or not, shall enjoy copyright in accordance with this Law.
Trademark Law of the People’s Republic of China (Amendments on
October 27, 2001)
This law was enacted for the purposes of improving the administration of trademarks, protecting the exclusive right to use trademarks, and of encouraging producers and operators to guarantee the quality of their goods and services and maintaining the reputation of their trademarks, with a view to protecting the interests of consumers, producers, and operators, and to promoting the development of the socialist market economy.
Canadian Laws for Trademarks and Copyrights
Copyright Act (R.S., 1985, c. C-42)
This act grants protection to an architectural work, artistic work, Berne convention country, commission, book, broadcaster, choreographic work, cinematographic work, collective society, work, or combination of these, used by traders on their goods and services to indicate their origin.
Trademark Law
This law states that if a mark is used by a person as a trademark for any of the purposes or in any of the manners, it shall not be held invalid merely on the ground that the person or a predecessor in title uses it or has used it for any other of those purposes or in any other of those manners.
South African Laws for Trademarks and Copyright
Trademarks Act 194 of 1993
This act provides the registration of trademarks, certification trademarks, and collective trademarks.
Copyright Act of 1978
This act regulates copyright and provides for matters incidental thereto.
Patents Act No. 57 of 1978
This act provides for the registration and granting of letters patent for inventions and for matters connected therewith.
Chapter Summary
9-39
South Korean Laws for Trademarks and Copyright
Copyright Law Act No. 3916
The purpose of this act is to protect the rights of authors and the rights neighboring on them and to promote fair use of works in order to contribute to the improvement and development of culture.
Industrial Design Protection Act
The purpose of this act is to encourage the creation of designs by ensuring their protection and utilization so as to contribute to the development of industry.
Belgian Laws for Trademarks and Copyright
Copyright Law, 30/06/1994
The purpose of the act is to protect literary and artistic works from unauthorized usage. The author of a work alone shall have the right to reproduce his or her work or to have it reproduced in any manner or form whatsoever.
Trademark Law, 30/06/1969
This law approves the Benelux Convention Concerning Trademarks and Annex, signed in Brussels on March 19, 1962. The high contracting parties shall incorporate into their domestic legislation, in one or both of the original texts, the Benelux Uniform Law on Trade Marks annexed to this Convention and shall establish an administration common to their countries under the name Benelux Trade Marks Bureau.
Hong Kong Laws for Intellectual Property
Hong Kong’s IP laws are based on constitutional or basic law provisions.
Article 139 of the Basic Law
Government shall formulate policies on science and technology and protect achievements in scientific research.
Article 140 of the Basic Law
This law protects the rights of authors in their literary and artistic creations.
Chapter Summary
■ A trademark is a word, phrase, symbol, or design that identifies and distinguishes the goods of one party from those of others.
■ Copyright is a form of protection provided to the owners of original works.
■ Plagiarism is using others’ ideas and words without clearly acknowledging the source of that information.
■ According to the USPTO, “A patent is a property right granted to the inventor by the USPTO to keep others from making, using, or selling the invention without authorization.”
■ Intellectual property is a product of intellect that includes copyrights and trademarks for commercial use.
■ DRM is access control technology used by manufacturers, publishers, and copyright holders to limit the usage of digital devices or information.

9-40
Chapter 9
Review Questions
1. Explain fair use.
__________________________________________________________________________________________
__________________________________________________________________________________________
2. How do you investigate the copyright status of a work?
__________________________________________________________________________________________
__________________________________________________________________________________________
3. What is a service mark?
__________________________________________________________________________________________
__________________________________________________________________________________________
4. What is a patent?
__________________________________________________________________________________________
__________________________________________________________________________________________
5. What is plagiarism?
__________________________________________________________________________________________
__________________________________________________________________________________________
6. What tools are available for detecting plagiarism?
__________________________________________________________________________________________
__________________________________________________________________________________________
7. What are paper mills?
__________________________________________________________________________________________
__________________________________________________________________________________________
8. Explain digital rights management (DRM).
__________________________________________________________________________________________
__________________________________________________________________________________________
Hands-On Projects
1. Search for a trademark at the USPTO.
■ Visit http://www.uspto.gov.
■ Click Trademark search.
■ Type CEH in the search field.
2. Research the SCO vs. IBM copyright claim.
■ Visit http://www.groklaw.net.
■ Read various articles related to SCO and IBM with respect to the lawsuit.
Hands-On Projects
9-41
3.
Investigate
plagiarism.
■ Visit http://www.turnitin.com.
■ Explore the various services provided by this site.
4. Use the CopyCatch program to find plagiarism in a given file.
■ Navigate to Chapter 9 of the Student Resource Center.
■ Install and launch CopyCatch.
■ Explore the program’s various options.
5. Use the SPlaT program to find plagiarism in a given file.
■ Navigate to Chapter 9 of the Student Resource Center.
■ Install and launch the SPlaT program.
■ Explore the program’s various options.
This page intentionally left blank

All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.