Building an Information Security Awareness Program: Defending Against Social Engineering and Technical Threats, First Edition (2014)
CHAPTER 8. Physical Security
Valerie Thomas Securicon, Lorton, VA, USA
Abstract
When someone mentions physical security, often visions of fences and security guards come to mind. While those are components, there are many other elements that create a physical security program. In this chapter, we'll discuss building security, data center security, physical security assessments, and what physical security means to the employee.
Keywords
Physical security
Natural threats
Unintentional threats
Human threats
Red team
Reconnaissance
What is Physical Security?
Physical security describes security measures that are designed to control access to a building, facility, or resource from unauthorized personnel. Unauthorized personnel include attackers who wish to cause harm to the protected environment and accidental intruders, such as employees who may not be aware of the restricted area [1]. Physical security can be divided into three basic levels: outer perimeter security, inner perimeter security, and interior security.
Outer Perimeter Security
The property lines define the outer perimeter. For some organizations, this includes one building; for others, it is a campus of multiple buildings and parking facilities. The goal of securing the outer perimeter is to control who can walk or drive onto the property [2].
Inner Perimeter Security
The inner perimeter consists of outside-facing doors, windows, and walls of your building(s). Controlling who enters and exits the building (and when) is the goal of securing the inner perimeter.
Interior Security
The inside of the building(s) forms the interior security level. The goal of interior security is to only provide appropriate access to portions of the building(s) to authorized employees. This is implemented not only for security but also for employee safety in environments that contain hazardous chemicals or working conditions.
Physical Security Layers
The physical security layers incorporate various methods and tools to support their purpose. Portions of these layers will be included in all three levels of physical security discussed above.
Deterrence
The deterrence layer includes environmental structures that can impede or stop an attack from occurring. Examples of these are as follows:
■ Fences
■ Gates
■ Razor wire
■ Speed bumps
■ Checkpoints
■ Vehicle barriers
■ Vehicle height restrictions
■ Trenches
■ Lighting
■ Warning signs
These structures can be combined to funnel the number of entry and exit points of the outer perimeter and create multiple checkpoints.
Control
Physical security control refers to capabilities that limit access to restricted areas. Control features are utilized at all levels of security. Controls can be mechanical, procedural, or electronic. Examples include the following:
■ Turnstiles or mantraps
■ Electronic card systems
■ Mechanical keys
■ Combination safes and doors
■ Authorization by guard force
■ Sign-in book
■ Access via security escort
In addition to access control, many of these items provide accountability. Electronic or paper sign-in and sign-out logs can be used as proof of admittance into the controlled building or room.
Detection
Detection and alert systems trigger a response when unauthorized access is detected. The goal of detection devices is to alert physical security personnel of a possible intrusion. Some examples include the following:
■ Motion sensors for alarm system or lights
■ Alarm functionality of electronic card systems
■ Glass break detectors
If your organization employs a guard force, these devices will alert them to the area of concern for further investigation. Some organizations do not have a guard force and rely on police response to alarm systems.
Identification
The identification layer focuses on video monitoring. Although video cameras can be used as a deterrent and detection device, their primary purpose if for historical analysis. If a detection device alerts, a video camera can be used to verify activity in the area. If an attack has already occurred, video footage can be used to identify the attacker and the damage caused by their attack.
Threats to Physical Security
Attackers are not the only threat to physical security. The three main types of physical security threats are as follows:
■ External—Often referred to as natural threats. This includes fire, flooding, earthquakes, hurricanes, and tornados.
■ Internal—This category includes unintentional acts of destruction such as bad plumbing or wiring, spilled drinks, operator error, and dropped equipment.
■ Human—Considered intentional acts of destruction. These threats include theft, vandalism, sabotage, and espionage. Hacking can incorporate one or more of these threats depending on the goals of the attacker [3].
Why Physical Security is Important to an Awareness Program
Physical security is often managed separately from cyber security; however, both divisions are protecting the same mission: critical items, corporate infrastructure, and intellectual property. While both divisions protect the same assets, cyber security is perceived as the more specialized career path. This perception creates a split personality of security, as depicted in Figure 8.1.
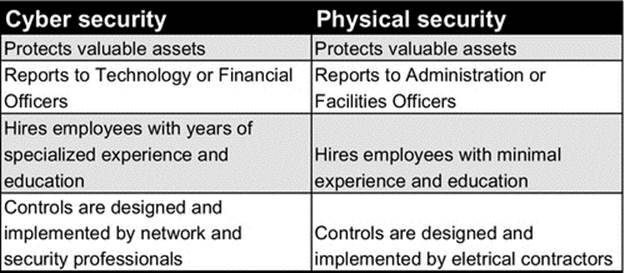
FIGURE 8.1 The split personality of security.
An organization can have a multimillion-dollar cyber security program with the latest technology and specialized staff, but if an attacker can simply walk into their building and obtain network access, the security implementation is flawed. As mentioned inChapter 7, physical security breaches and social engineering go hand in hand. Employee awareness of physical security is crucial to the success of protecting the organization's information and employee safety. In order to properly educate your employees on physical attacks, we've detailed the typical steps that a Red Team, or physical assessment team, would follow to obtain unauthorized access to a building or campus.
How Physical Attacks Work
Organizations often hire security companies to perform a physical penetration assessment. Physical penetration testing evaluates a target facility's controls for prevention of entry, delay of entry, and in some cases response time of security forces. The assessment objectives may vary depending on the organization's largest physical security concerns. Some sample objectives include the following:
■ Gaining access to the interior perimeter
■ Gaining access to any or all portions of a building
■ Obtaining access to the data center or other high-profile target
■ Obtaining sensitive information through technical or nontechnical means
■ Gaining network and/or computer access
The basic process for physical security assessments has three phases: reconnaissance, attack planning, and attack execution. Similar to social engineering attacks, most of the assessment team's time is spent in the reconnaissance and planning phases.
Reconnaissance
Quality reconnaissance is crucial to the success of a physical attack. Put yourself in the assessment team member's shoes. If you were going to walk into a building unauthorized, wouldn't you want to have as much information as possible before the attack? It is most likely that the assessment team is not physically located within close proximity of the target facility. Most organizations will not fund several weeks of travel for an assessment team to perform reconnaissance, thus creating the need for off-site and on-site reconnaissance.
Off-Site Reconnaissance
A large amount of information can be obtained about an organization utilizing various Internet resources. Gathering as much information as possible on the target's location, physical surroundings, floor plan, day-to-day operations, and security controls in this phase will increase the assessment team's chances of success. The primary areas of off-site reconnaissance are discussed below.
Maps
The first course of action in off-site reconnaissance is getting the lay of the land. Thanks to Google and Bing maps, this is easier than ever (Figure 8.2). Both map programs offer an aerial and, in most cases, street view of locations in the United States.

FIGURE 8.2 Aerial image from Google Maps.
Understanding the target facility and surrounding area is the main focus of the off-site reconnaissance phase. Online maps and street-level images are used to
■ identify perimeter security mechanisms including fences, gates, and checkpoints
■ locate building parking lots or garages
■ identify potential entry points including doors, loading dock, and underground parking
■ identify location of dumpsters
■ view the surrounding area
The age-old real estate saying “location, location, location” also applies to the physical assessment world. A target's surrounding area plays a large role in the assessment dynamics. One of the most important goals of the off-site reconnaissance phase is to locate potential on-site reconnaissance areas. If the target is located in a heavily populated area surrounded by office buildings, coffee shops, and restaurants, the assessment team will have many on-site reconnaissance areas. However, if the target is located in a rural area, on-site reconnaissance options may be extremely limited. In some heavily populated areas, you may be able to view your target area near real time by utilizing Internet traffic and weather cameras (Figure 8.3). Google Maps provide a web camera option for select locations.
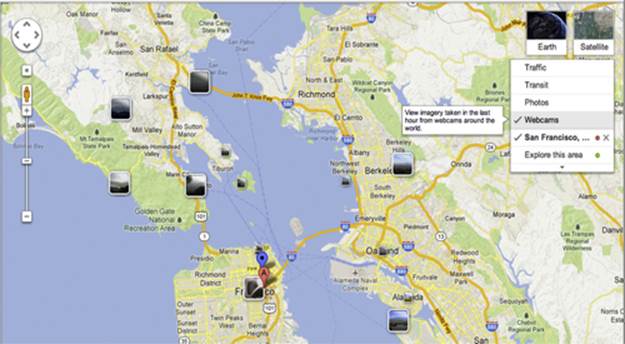
FIGURE 8.3 Camera locations via Google Maps.
In addition to Google Maps, searching for city-sponsored traffic and weather cameras may also provide valuable results.
The Company Website
While information listed on the company website may be considered mundane, it can provide a wealth of information to a physical assessment team. The key pieces of information from the company website include the following:
■ Operating hours—Often listed with customer service and public relations phone numbers, the operating hours provide insight as to when the target building may be empty or have minimal employees present. If the company website indicates that 24/7 customer service is available, then call center staff may be on-site throughout the night.
■ Address specifics—It is doubtful that the physical assessment team will gain access to a floor plan during this phase. However, by examining mailing address or employee directory details, the team may be able to create a route estimate of a floor map. For example, if the address for customer service is listed as 145 East Main Street, 2nd floor, the assessment team can begin creating a rough building floor plan.
■ Information from photos—Photos can be a valuable source of information for the assessment team. Companies often include photos of their building lobby area, fitness center, sundry shop, and other common areas of the building. These photos can be combined to provide the assessment team a basic layout of what is behind the building's front door. Additionally, information can be gathered on the security posture of the organization by locating security cameras, alarm panels, ID card readers, and employee ID cards in the background of company photos.
Additional Sources
The company website and map programs are not the only useful sources of information for attackers. Often, information can be obtained from real estate companies, construction permits, and social media:
■ Tax records—Analyze the tax records of the target building to determine if the property is owned by the company or by a real estate company. In addition to ownership, details regarding total square footage and property lines may be obtained from tax records.
■ Real estate companies—If the target building is owned by a real estate company, their website may provide detailed information on the building's features including fitness center, underground parking, on-site security monitoring, and rental car service. Real estate companies often have multiple photos of the interior and exterior of the building to attract potential clients. These photos are analyzed for information similar to photos from the company website. Additionally, it may be possible to determine if the target organization leases the entire building or portions of it. A quick phone call to the real estate agent can confirm building availability. Assessment team members often approach real estate companies as a fictitious business that is interested in leasing space in the target building and schedule a tour of the available office space during their on-site reconnaissance phase.
■ Social media—Social media is utilized to provide the assessment team with a list of employees. Searching popular networking websites, such as LinkedIn, can provide team members with names, job titles, and photos of the target company's employees. Additionally, other social media websites are utilized to gather and analyze photos uploaded by employees that may provide ID card photos or other useful information.
Upon completing the off-site reconnaissance phase, the assessment team has an understanding of
■ what buildings are in scope of the assessment
■ building surroundings
■ potential locations to perform on-site reconnaissance
■ basic perimeter security knowledge
■ the ownership or lease of the building
■ operating hours
■ basic view of the lobby area
■ ID card readers in use
■ public events that could provide access to the building
■ street-level view of entrances
■ potential smoking areas
On-Site Reconnaissance
While the majority of the research occurs during off-site reconnaissance, on-site reconnaissance focuses on observing building operations and employee awareness. The goal of the on-site reconnaissance phase is to have gathered adequate information to plan the attack.
Surveillance
Upon arriving at the target location, team members will drive or walk past the building to observe the level of activity and time of observation. The objective is to determine the level of activity at various times throughout the day and night. Performing the initial drive by at night is preferred, as the building is not likely to be highly occupied. The goals for night surveillance include the following:
■ Identify if guard force is present.
■ Document if lights are on in specific areas of the building.
■ Determine if cleaning crew is present after hours.
■ Locate dumpster and assess security controls around it.
■ Document if employees enter or exit the building.
If the dumpster appears to be unguarded, the assessment team may perform a dumpster dive to retrieve discarded sensitive information.
Daytime surveillance can be performed in a number of locations throughout the day. Team members will distribute themselves in order to observe all sides of the building. Not all surveillance is performed in a car using binoculars. In highly populated areas, the best surveillance locations are often in public places such as coffee shops, restaurants, benches along the sidewalk, or circling the area on foot. Assessment team members often alter their appearance with clothing, hats, and accessories to avoid suspicion of a single person within close proximity of the building for an extended time. Daytime surveillance objectives include the following:
■ Identify smoking areas, as they are ideal locations for gathering information or tailgating into the building.
■ Document entry and exit observations for each entrance. Do employees hold the door open for each other?
■ Document when the majority of employees report for work in the morning and leave in the evening.
■ Determine if parking area is controlled via radio frequency identification (RFID) transponders.
■ If the building offers an hourly car rental service through companies such as Zipcar or Hertz, reserve the car and document if an RFID tag is present.
■ Obtain photographs of employee ID cards. Most employees wear them in public areas, such as a coffee shop.
■ Document if guard staff are present and their locations throughout the facility.
■ Document employee attire. If the team members plan to impersonate an employee, they need to dress accordingly.
As you can see, simply observing and documenting the activity around a building can provide an attacker with a plethora of information on its security posture.
Real Estate Meeting
If the assessment team was able to schedule a meeting with the building real estate agent prior to arrival, only one or two team members will attend the meeting to prevent raising suspicion. A guided tour of the building is the ideal opportunity for the team members to observe building operations and ask questions pertaining to the building and office space. If possible, the team will select an available office space on the same floor as the target company and an additional space on a separate floor. Some of the questions the assessment team will ask include the following:
■ Does the building require an access card for entry?
■ Do individual office spaces require the same access card or separate access card?
■ Is 24/7 access available?
■ Does the building have on-site guard staff?
■ Is office cleaning included in the monthly rent?
■ When does the cleaning crew access the office space?
■ Do the office spaces have alarm systems?
In addition to the listed questions, the team members should inquire about other details (nonsecurity-related) of the office space to avoid raising suspicion.
RFID Credential Stealing
Many organizations utilize RFID access systems to prevent unauthorized entry into their facilities. These access systems rely on ID cards and card readers to verify a person's access level. Most ID cards are proximity-based. When the ID card is held up to the reader, it receives power from the reader in order to verify its contents. Door controllers and servers then determine if the presented credentials are permitted into the secured area. Reading and reproducing the contents of the ID card can compromise some RFID access card systems. The two popular devices for RFID credential capture are the Proxmark3 and the Bishop Fox Long-range RFID Stealer. These devices can read and store the contents of RFID cards that are within read range. The two main challenges with these devices are getting close enough to the target person without raising suspicion and transporting the necessary power and antenna hardware. Some designs include attaching the hardware to the inside of a binder using Velcro. At first glance, the binder appears unmodified. However, compartments conceal the Proxmark3, power supply, and antenna (Figures 8.4–8.6).

FIGURE 8.4 Binder to conceal Proxmark3 hardware.

FIGURE 8.5 The Proxmark3 and power supply inside the binder.

FIGURE 8.6 The antenna inside the binder.
Another mobile design for the Proxmark3 includes securing the components to an organizer with elastic bands (Figure 8.7). The organizers are commercially available in a number of sizes.

FIGURE 8.7 Proxmark3 with organizer.
The organizer holds the required components and cables in place during movement. Assessment team members then insert the organizer into a basic laptop sleeve to carry without raising suspicion.
Although the Proxmark3 is easy to transport, the range at which it can read ID card contents is approximately 6 in. Positioning the disguised Proxmark3 within 6 in. of a person's ID card is fairly difficult, even in highly populated areas. To solve this problem, employees at Bishop Fox created a Long-range RFID Stealer [4]. The design utilizes a long-range RFID card reader, as shown in Figure 8.8.

FIGURE 8.8 Commercial long-range RFID reader.
The designers modified the device to include stand-alone power, data storage, and display features (Figure 8.9).
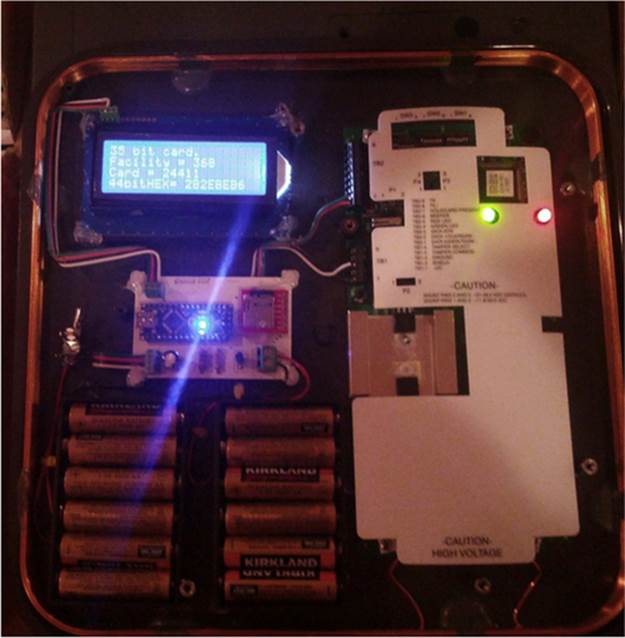
FIGURE 8.9 Bishop Fox Long-range RFID Stealer.
The modified card reader first reads the card contents, displays the data on the LCD, and then writes the card contents to a microSD card for analysis on a computer. The assessment team utilizes RFID credential stealing technology during on-site reconnaissance to collect ID card information. Once the card information is collected and analyzed, the team will write the appropriate electronic content to an ID card. Finally, the team members will create a fictitious ID card printout, including the team member's picture; attach it to the programmed ID card; and laminate the finished product. This process produces an ID card that will most likely pass basic visual inspection and access control systems.
Attack Planning
During the planning phase, the assessment team analyzes the collected data to determine the best course of action to execute the attack. Key decision points for planning the attack include the following:
■ When is the ideal time to attack?
■ During business hours
■ After business hours when cleaning crew is present
■ After business hours when the building is empty
■ What is the primary approach?
■ Masquerading as an employee
■ Accessing after business hours when a cover identity is not required
■ Claiming to be from a telecommunications provider or vendor
■ Masquerading as a cleaning crew employee
■ What is the secondary approach in case the primary approach fails?
■ What accessories do the team members need for their assigned duties?
■ Appropriate clothing (cleaning crew uniform or company polo shirt)
■ Tools associated with duties
■ ID cards
■ Business cards
■ Authorization letter from the target company in case of containment
Attack Execution
The attack execution phase is the shortest phase in the physical attack process. It is essential that assessment team members have contact with each other during the attack. If the primary attack fails, the team can execute the secondary attack immediately. Bluetooth headsets and handheld radios are the most popular communication mechanisms for assessment teams. Once the attack has succeeded and the team is inside, typical steps include the following:
■ Taking photographs to prove the team's success.
■ If the team is also performing a network penetration test, custom malicious backdoors will be uploaded to desktops of employees that have elevated access. These employees were discovered prior to the physical attack using social networking.
■ Obtaining access to the server room or data center.
■ Collecting sensitive data that are openly displayed on desks, under keyboards, and in file cabinets.
■ Obtaining access to senior management offices.
The assessment team is usually on-site for approximately 20 minutes, depending on the security-monitoring schedule. Generally, the assessment team spends as little time as possible on-site to avoid discovery.
Minimizing the Risk of Physical Attacks
As detailed above, physical attacks require intense and time-consuming research. However, most of the information utilized to plan the attack was publicly available. The most popular method for assessing your organization's risk of physical attack is to perform a physical security assessment, or physical penetration test. Typically performed by specialized consultants, a physical penetration test can highlight areas of potential weakness.
Preparing for a Physical Assessment
If you haven't performed a physical security assessment in the past, there are specific planning steps to be taken to ensure satisfactory results.
Set an Objective
A clear objective is one of the most crucial planning items for a physical security assessment. What areas of your physical security program concern you the most? Common objectives include the following:
■ Gaining access to a controlled area, such as the data center
■ Bypassing perimeter security controls
■ Evaluating electronic security controls
Some organizations elect to perform a zero-knowledge physical security assessment. This type of assessment provides the assessment team with no background information and allows the team to compromise any security control to gain access to as many facilities as possible.
Declare Off-Limits Areas
List specific areas that the assessment team is not authorized to enter. Some organizations work with hazardous material that could harm the assessment team. The company president's office is often declared an off-limits area for physical security assessment.
Schedule
Select a range of acceptable dates and time for the assessment team to perform the attack. Ensure that key personnel, such as the director of physical security and the CIO, are readily available to confirm the assessment team's objective and identify in case the assessment team is discovered.
Authorization Letter
Often referred to as a “get out of jail free card,” the authorization letter lists the team members by name along with a summary of their assessment objective. Employee names, such as the director of physical security, and phone numbers should be listed for guard forces to contact and verify the authorized activity.
A physical security assessment can be an eye-opening experience for even the most sophisticated of organizations. Above all, it is a practical learning experience that will provide valuable insight to improving your organization's physical security posture.
Can't Afford A Physical Security Assessment?
While physical security assessments provide value and insight into currently deployed defense mechanisms, they come at a price. If your organization can't afford a physical security assessment from an outside vendor, there are prevention steps that can be applied without outside assistance:
■ Perform your own reconnaissance—Your organization's cyber or physical security team can perform the steps listed in the reconnaissance phase. This nonintrusive evaluation can reveal several vulnerabilities in the physical security program.
■ Complete security walk-throughs—A security walk-through is another nonintrusive evaluation that involves reviewing the information that is left exposed on desks or public places. Locating several pieces of sensitive information that has been mishandled could point to a lack of employee awareness.
■ Watch the doors—Simply observing how employees enter and exit the building can provide valuable information on the status of physical security awareness. If employees are holding doors open for people behind them, enforcing a strict ID card scanning policy may eliminate tailgating.
Physical security is much more than fences and security guards. Incorporating physical security threats into your awareness program will improve overall security for your organization.
Notes
[1] Physical Security http://www.police.psu.edu/physical-security/what-is-physical-security.cfm [last accessed 25 May 2014].
[2] How to Secure Your Building and Property http://bizsecurity.about.com/od/physicalsecurity/a/What_is_physical_security.htm [last accessed 25 May 2014].
[3] Protecting Your System: Physical Security http://nces.ed.gov/pubs98/safetech/chapter5.asp [last accessed 29 April 2014].
[4] RFID Attack Tools http://www.bishopfox.com/resources/tools/rfid-hacking/attack-tools/ [last accessed 26 May 2014].