Information Security Management Handbook, Sixth Edition (2012)
DOMAIN 5: CRYPTOGRAPHY
Cryptographic Concepts, Methodologies, and Practices
Chapter 21. Pirating the Ultimate Killer App: Hacking Military Unmanned Aerial Vehicles
Sean P. McBride
Introduction
In late 2008, a U.S. Army commander in Iraq planned and ordered a combat operation based off intelligence that suggested the possible location of a known Shiite militant.1 To the assigned combat patrol, this action was a seemingly typical combat operation. As on most other days, the soldiers planned and rehearsed how they would storm the target location based on maps and digital imagery intercepted from Predator drones. The patrol traveled to the suspected location, stormed the building, and neutralized the target without significant resistance. After the soldiers subdued, disarmed, and tied up the insurgent, they searched his person and immediate surroundings for anything that could possibly yield actionable intelligence for future combat operations. Among other things, the soldiers found and cataloged a laptop computer.
The discovery of an enemy combatant’s laptop computer can often be extremely useful for coalition forces. Much like domestic police, the U.S. Army has trained experts in digital forensics who are able to extract actionable intelligence from laptops and other captured enemy electronics. Such actionable intelligence can include documents and digital communications between insurgent cells, which provides commanders and intelligence officers information on enemy personnel, weapons, and operational intent. When the Army digital forensics experts analyzed this laptop, they likely found many of these things. However, they also found something seemingly impossible: files containing the very Predator drone video feeds used to plan missions and assaults against insurgent forces. In the following months, other coalition commanders in Iraq and Afghanistan discovered other laptops containing similar collections of drone footage, demonstrating that the Predator possessed a serious vulnerability.
Approximately 1 year after the Department of Defense (DOD) learned that enemy insurgents possessed the ability to intercept drone footage, the Wall Street Journal published a front-page tell-all expose based on a series of anonymous military tips. To the eyes of the media and the public, this story raised grave concerns about military information security (InfoSec) policy, particularly involving unmanned aerial vehicles (UAVs) like the Predator. Media reports that the Predator drone transmitted real-time reconnaissance footage over an unencrypted satellite data link made the Pentagon appear foolish and short-sighted. With only a PC, a small satellite receiver, and a $26 piece of software called SkyGrabber, the enemy gained the MacGyver-like ability to access the exact same footage as coalition commanders.3 Watching the breaking news (perhaps on a satellite TV receiver), the viewers likely wondered how a military reconnaissance drone could possibly possess less encryption than Direct T.V.
This chapter seeks to examine the narrative of the Predator project to determine how the Pentagon allowed this crucial InfoSec vulnerability to develop, how insurgent forces learned to exploit this vulnerability, and how the Pentagon has responded. To understand the nature of this vulnerability, this chapter will examine how drone pilots near Las Vegas launch missiles at insurgents located thousands of miles away. This narrative will follow the Predator drone through design, deployment to the Balkans, to destructive use in Iraq, Afghanistan, and Pakistan. Next, this chapter will analyze the hardware and software that allowed enemy forces to intercept Predator drone feeds, including the theories for how insurgent cells received their equipment and training. By examining these portions of the Predator narrative, this chapter will then analyze the underlying security decisions that led to the 2008 Predator “hack” in terms of InfoSec threat analysis and risk management.
Development of UAVs
The wars of the future will not be fought on the battlefield or at sea. They will be fought in space, or possibly on top of a very tall mountain. In either case, most of the actual fighting will be done by small robots. And as you go forth today remember always your duty is clear: To build and maintain those robots.
—The Simpsons4
Despite recent attention by the media and military theorists, UAV technology dates back to 1896, when Dr. Samuel Pierpoint Langley launched the first unmanned aircraft over the Potomac River.5 Since this early date, UAVs have developed more or less alongside their manned counterparts. However, due to the elimination of risk to manned pilots, UAVs became associated with the most dull, dirty, and dangerous of missions. The earliest models of UAVs were the so-called “aerial torpedoes,” flying bombs designed to explode on impact. Although these projects were ultimately scrapped before being fielded during WWI, they laid the technical groundwork for the cruise missile platform, including the infamous German Vergeltungswaffe used extensively in the London Blitz. By WWII, B-movie actor Lee Dugmore Denny, inspired by his love of radio-controlled hobby aircraft, evangelized a new dangerous mission for UAVs: expendable aerial target drones used to train American pilots in mock dogfights.5
As improved communication technology allowed for a more reliable data link between the UAV and the remote operator, military theorists began to envision UAVs as the ideal platform for high-risk reconnaissance missions. However, many leaders within the defense establishment strongly resisted the idea that UAVs could replace small manned reconnaissance aircraft.6 The strongest resistance to the operational use of UAVs often came from pilots themselves, who considered UAVs a threat to manned flight hours and benefits such as flight pay. Following the creation of the Air Force as a separate military branch, these pilots gained the decision-making authority to effectively sideline the development and use of UAV technologies. The exception to this was the BQM-34 Frisbee, which successfully flew more than 34,000 clandestine surveillance missions over Cambodia and Laos, due to political restrictions over manned flight in those areas.5
Despite this aircraft’s tremendous track record, the Air Force terminated the Frisbee’s use as a reconnaissance platform following the end of conflict in Vietnam, and further American development in unmanned aerial technologies languished.
In contrast to the U.S. Air Force, the armed forces of the newly created state of Israel were quite willing to experiment with new and untested military technologies. Due to Israel’s severe sense of military insecurity brought about by close proximity to hostile neighbors, Israeli ground commanders demanded a technology that would allow effective “over-the-horizon” reconnaissance.6 Drawing from the lessons learned of the BQM-34 Frisbee’s operations in Vietnam, Israeli engineers created the Mastiff, a 13′9″ wingspan UAV built out of fiberglass and equipped with TV cameras and infrared sensors to provide 360° surveillance.6 Over the next few years, the Mastiff demonstrated the tremendous capabilities of unmanned aircraft, allowing the Israeli Air Force to spoof Egyptian air defenses into wasting their surface to air missiles prior to launching Israeli fighter-bombers during the Yom Kippur War,6 and enabling Israel to eliminate all radar systems in the Bekaa Valley in Lebanon, without losing a single pilot.6
Development of the Predator
The elimination of pilot life support systems and control interfaces allows for smaller, simpler aircraft [that] can be placed in flight ready storage for years, eliminating consumables, maintenance, and personnel requirements.6
—Rich Alldredge
Boeing Program Director
Due to Israel’s successful record at employing UAV technology during the Yom Kippur War, the U.S. military’s perception of UAVs began to shift. The excellent combat record of the Israeli Mastiff demonstrated that UAVs offer force projection without risk to human pilots, allowing the Air Force leaders to “breathe easier when making a combat decision.” 6 Furthermore, UAVs offered far more economical force projection than manned aircraft, which provided unmanned development considerable support in the austere post-Cold War era.7 Due to these factors, the U.S. military and the Central Intelligence Agency (CIA) began to fund Abraham Karem, a former chief aircraft designer of the Israeli Air Force turned U.S. citizen, to create a new UAV for the United States. His creation was the Predator, a prototype UAV (officially named the Gnat 750) that incorporated many of the lessons of the Israeli UAV program.5
After General Atomics won the contract to develop and manufacture Abraham Karem’s prototype in 1994, the testing and fielding of the Predator proceeded extremely quickly. Within a year, the Predators took part in the 1995 Roving Sands exercise, impressing the Air Force and Army leaders as a capable reconnaissance platform. Within 3 months of Roving Sands, the Air Force formed and trained its first Predator squadron: the 11th Reconnaissance Squadron. By July 1995, the pilots and UAVs of this squadron were deployed to the Balkans to provide aerial reconnaissance support for NATO operations.6 In total, this meant that the period of time from the awarding of the Predator contract to its first use in combat was around 2 years: a grueling development timeline that led to numerous technical and training shortcomings. During operations in Bosnia, 19 of 68 deployed Predators were lost, mostly due to poor weather conditions “including visible moisture such as rain, snow, ice, frost or fog” and operator error associated with the loss of “situational awareness that a normal pilot would have of where the ground is and where the attitude of this aircraft is.” 6 Despite these criticisms, the Predator proved highly capable of providing battlefield intelligence, earning praise from the Congress as one of the major military success stories of FY1996.5 Furthermore, the high loss rate of UAVs attracted little media attention relative to the shooting down of Captain Scott O’Grady, leading Major General Kenneth Israel to note that “when an F-16 pilot … was shot down, it was a crisis, but when a $2 million Predator UAV was shot down, it was a curiosity. Who is going to tell a parent that their child is not worth $2 million?” 7
Based on these successes, the Air Force dramatically increased support for UAVs. In addition to beginning development on newer unmanned aircraft (including the Global Hawk and the Reaper), the Air Force began a substantial upgrade program to install a larger turbocharged engine and deicing system to make the Predators more resilient in adverse weather conditions. While the Air Force undertook to improve the Predator as a reconnaissance platform, the CIA began development of a new offensive variant of the Predator that could be used to remotely fire munitions at enemy targets. Due to increased intelligence chatter, the CIA was particularly interested in using this weapon as a means to assassinate Osama Bin Laden, a man increasingly viewed as a major terrorist threat following the failed 1993 bombing of the World Trade Center. Although it proved difficult to find a warhead that could work with this small aircraft, by 16 February 2001, a specially modified Predator drone successfully destroyed a target at a testing facility, using an AGM-114 Hellfire missile. Ultimately, the CIA was unable to follow through with its operational intent to assassinate Bin Laden, as the Predator was still undergoing testing when Al-Qaeda terrorists destroyed the World Trade Center on 11 September 2001.
Shortly after the 9/11 attacks, President George W. Bush told the military that “the enemy who appeared on September 11 seeks to avoid our strengths and constantly searches for our weaknesses … so America is required once again to change the way our military thinks and fights.” 6Drawing on this exhortation, General John P. Jumper, the new Air Force Chief of Staff, ordered immediate coordination with the CIA to arm all Predators. Unlike other generals, John P. Jumper was a serious supporter of the UAV program. After working with Predator drones in Bosnia, he cooperated extensively with the CIA on the project to develop an offensive UAV, believing that arming the Predator would allow it to strike “fleeting, perishable targets that don’t require a big warhead that we can just go ahead and take care of.”6 After the start of Operation Enduring Freedom, armed Predator drones were some of the very first deployed assets, scoring their first kill on 4 November 2002, 100 miles east of the capital of Yemen, by blowing up an SUV carrying Al-Harthi, the head of Al-Qaeda in Yemen and the mastermind behind the suicide attack on the USS Cole, which killed 17 American sailors.6 Although 9/11 disrupted CIA plans to use the Predator to preemptively assassinate Osama Bin Laden, the Hellfire-equipped Predator quickly grew to become the quintessential weapon in the war against Al-Qaeda.
Predator Vulnerability
Global terrorism is extreme both in its lack of realistic goals and in its cynical exploitation of the vulnerability of complex systems.
—Jürgen Habermas8
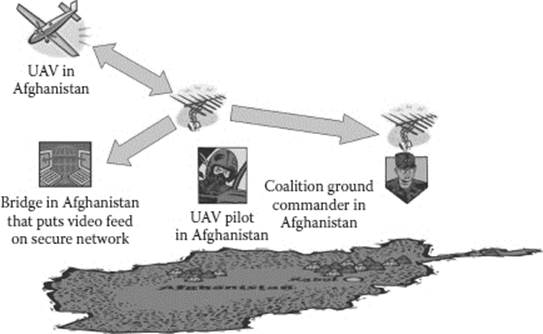
Figure 21.1 Line-of-sight.
The Predator UAV relies on highly complex data links to connect with operators and end users throughout the world. These data links occurs over two distinct wireless mediums. If the UAV is in line-of-sight proximity to its operator, it can transmit directly to its control van using the C-band, which then retransmits the live surveillance video feed onto the military network through numerous other network technologies (see Figure 21.1). However, this line-of-sight data link is rarely used, as drone pilots typically fly deployed UAVs remotely from military bases in the United States. In this case, where the operator and control equipment is out of theater, the UAV instead sends and receives all data over a satellite data link on the Ku band.5
These satellites, such as the INTELSAT 602, serve to simultaneously provide the UAV with three important connections (see Figure 21.2):
1. A link to the remote UAV control station that allows the drone pilot to fly the UAV from the United States
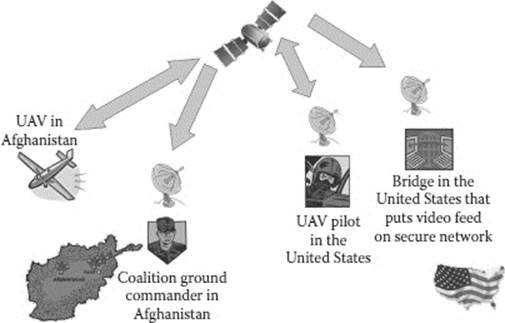
Figure 21.2 Non–line-of-sight.
2. A link to a communications station that rebroadcasts the data over the secure U.S. military network
3. A link to Trojan Spirit communications terminals (or equivalent) in theater for immediate dissemination of the video feed to American and coalition commanders5
Through these communications methods, a UAV has a duplex connection with its pilot and two distinct simplex connections: one to commanders in theater and one to a network bridge connected to the secure military network. The two simplex connections serve as the primary distribution methods for Predator surveillance video data.
The vulnerability of the Predator platform lies in the fact that it does not encrypt its surveillance video data as it does with its command and control (C2) data prior to transmission over the C or Ku bands. This means that secure video communications depend on the network encryption of the specific data link used. In the case of line-of-sight communications, this data is protected by encryption built into the military’s C-band transmission equipment, but when the Predator uses the satellite-based Ku data link, the surveillance video data is completely unprotected and widely vulnerable to interception.5 In practical terms, this means that any Ku band–compatible satellite dish within the broadcast area of the Predator’s geosynchronous satellite can intercept the Predator’s surveillance video downlink. Additionally, such a satellite dish can also access the Predator Joint Broadcast System, which is essentially a CNN-like broadcast that switches between various live video feeds designed to provide coalition troops in Afghanistan and Iraq simultaneous access to a “common picture of the battlefield.” 5
A key factor behind this InfoSec vulnerability is the speed with which the Predator drone was initially fielded. Throughout the Cold War, the arms race to develop the most sophisticated weapons systems, such as fighter jets, led the real unit production cost of combat aircraft to double around every 7 years (see Figure 21.3).10 As previously mentioned, one of the key reasons the DOD supported the development of the Predator UAV was because it offered force projection without the exponential cost increase of developing a new manned aircraft. In the years following the end of the Cold War, defense budgets fell precipitously throughout the world (see Figure 21.4). Given that the U.S. defense budget halved during the 1990s, the DOD began to rethink its operational requirements and weapons procurement model. Rather than seeking, what Defense Secretary Robert Gates called, “gold-plated” solutions to defense procurement, the Pentagon began to look for ways to pursue “75 percent solutions over a period of months.” 11 Predator procurement during the 1990s fit this model of producing rapidly scalable battlefield solutions within months and at minimal cost using as much commercial off-the-shelf (COTS) technology as possible, causing the Predator platform to exist, in the words of the Air Force director of UAV systems, “on the ragged edge … [seeking] to do just the absolute minimum needed to sustain the fight now, and accept the risks, while making fixes as you go along.” 11 Because of this procurement posture, the Pentagon judged the risk exposure associated with the myriad issues that could develop during the operational lifespan of the Predator to be less than the added utility of rushing the Predator into operational use, largely due to the elimination of risk to the pilot in the calculation of risk exposure.
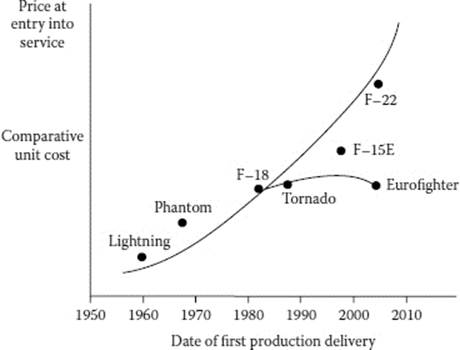
Figure 21.3 The exponential increase in jet fighter development cost. (From Sandler, T. and Hartley, K., eds., Handbook of Defense Economics: Volume 2 Defense in a Globalized World, Elsevier, London, p. 1153, 2007.)
Of particular interest to this case study was the Pentagon’s decision to lower costs by using COTS satellite technology based on the Ku band for the military data link of the Predator drones. As the Predator was undergoing development in 1996, the Undersecretary of Defense for Acquisition and Technology stated that “Hughes is the primary provider of direct (satellite) TV that you can buy in the United States, and that’s the technology we’re leveraging off of.” 9
By basing their data link on a television model, the Joint Broadcast System that displayed military reconnaissance footage developed as a sort of CNN for military reconnaissance videos. American and coalition commanders with the proper Trojan Spirit communications terminals could “tune” into the UAV “channel,” which greatly simplified data distribution by forgoing the need to share U.S. encryption codes with allies and coalition partners. Many Air Force leaders actually considered the use of unencrypted video downlinks to be a feature of the Predator system. For example, General David McKeirnan named this unencrypted data link as an important factor in “tripartite” cooperation between Pakistan, Afghanistan, and the International Security Assistance Force, allowing them to better “coordinate[] at various levels [by] exchange[ing] frequencies, … intelligence, [and] … Predator feed[s].” 12
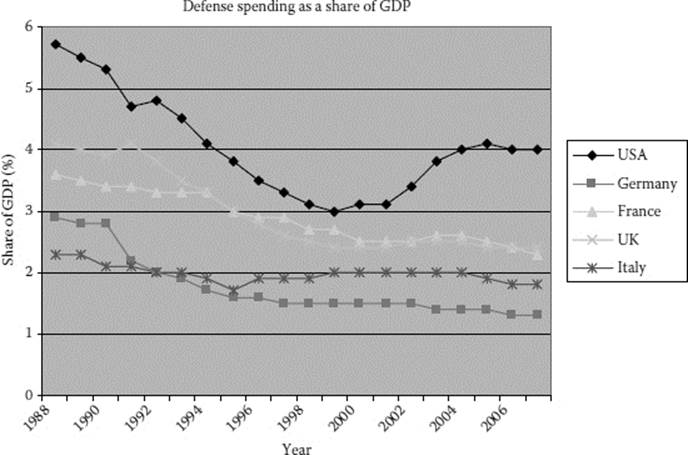
Figure 21.4 The precipitous drop of global defense spending post Cold War. (From SIPRI Yearbook 1990 and SIPRI Yearbook 2007. Solna, Sweden: Stockholm International Peace Research Institute [SIPRI].)
In 2002, a British satellite enthusiast named John Locker stumbled upon military reconnaissance footage from Kosovo when he accidently tuned into the Joint Broadcast System. Locker was shocked at the discovery that such footage was being transmitted over an open commercial satellite channel, leading him to contact the military with the concern that the ease of potential signal interception “may be compromising the troops on the ground, and, for that reason … we should either get it encrypted or get it switched off.” Ultimately, the U.S. military ignored Locker’s warnings with the explanation that:
1. The images need to remain unencrypted to allow NATO allies that lack proper decrypting equipment to see them.
2. The surveillance footage would be of no real value if intercepted by a potential adversary due to the absence of any meaningful operational context.
Media coverage of this event largely questioned this explanation, suggesting that enemy forces could systematically study intercepted surveillance footage to learn U.S. operational priorities and objectives. In an ironic premonition of things to come, a CBS reporter wrapped up this story with the comment that “even Al Qaeda reported terrorists are known to be in the area.” 13
Skygrabber Functionality and Exploit
Skygrabber is a piece of software designed to intercept unencrypted satellite data through the use of a digital satellite TV tuner card attached to a computer. In technical terms, Skygrabber is most accurately described as a sniffer for digital communications over a satellite data link. This makes the design, functionality, and usage of Skygrabber extremely similar to Kismet, an 802.11 sniffer that allows for the capture of data packets using NIC cards. Like Kismet and other sniffers, Skygrabber listens to the packets passed over the data link, intercepts them, and then reassembles them as files on a local machine.1 In Russia (where Skygrabber was developed), this offered users, which otherwise could not afford an expensive satellite Internet connection, the opportunity to gain limited access to digital media, including “new movie, best music, and funny pictures for free” [sic].14
By running the Skygrabber sniffer on a PC attached to a digital satellite TV tuner card, a user effectively piggybacks on the unencrypted downlink of legitimate satellite Internet users (see Figure 21.5). The software configures the TV tuner card to listen to and intercept different types of packets, which the PC then reassembles into usable files. This method only allows the user to tap into someone else’s downlink, due to the inability to transmit from a TV tuner card and the increased levels of authentication required for satellite uplink. This means that the Skygrabber user is at the mercy of the tastes of legitimate users, merely able to intercept all files that pass through the common satellite downlink. Nonetheless, Skygrabber users can exercise limited control over the files they intercept and download by applying software filters. While the sniffer is running, Skygrabber downloads all files that pass through the satellite data link meeting the defined filter criteria.6
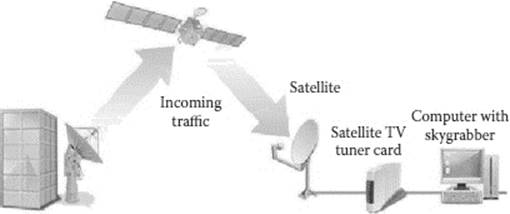
Figure 21.5 Skygrabber functionality.
Given the known Iranian affiliation of the Kata’ib Hezbollah militia originally caught possessing laptops filled with Predator intercepts, it is highly likely that Iranian Quds agents taught enemy combatants how to use SkyGrabber to intercept drone footage.16 The Iranian Quds agents themselves likely learned this system based off equipment seized from Iranian activists, as SkyGrabber is often used by dissidents to circumvent restrictions on information, such as those caused by the Iranian Firewall.1 By reverse engineering the Skygrabber software, Iranian experts were likely able to apply their previous experience tapping into the video downlink of geosynchronous satellites used by American drones in Iraq and Afghanistan to turn the Skygrabber package into an easy and user-friendly means of signal interception for Shiite militias in Iraq and Afghanistan. The ease with which the Skygrabber software could be modified to intercept drone footage reflects very poorly on the Pentagon’s decision to base its surveillance footage data link on COTS technology without additional encryption or security countermeasures. The common data link between the military’s Joint Broadcast System and the CNN network greatly aided low-cost signal interception techniques by ensuring that the techniques used to intercept satellite TV and Internet data could be easily reconfigured for military feeds, thereby enabling Quds agents to configure Skygrabber to emulate the technical settings of the Trojan Spirit communication terminals used by American and coalition forces to view Predator feeds.
Military Response
On 18 December 2009, Admiral Mike Mullen, the chairman of the Joint Chiefs of Staff, admitted that the Pentagon had been aware of the Predator’s data link weakness since 2004.17 In fact, further investigations demonstrated that the military knew about this vulnerability much earlier. As previously mentioned, John Locker contacted the Pentagon about Predator encryption in 2002, but the military had received similar reports as early as the 1996 Bosnia deployment, when it was reportedly easier for the Serbians to tap into military feeds than the Disney Channel.6
Indeed, a 1996 Air Force document very bluntly analyzed electromagnetic spectrum threats to the Predator platform as the following:
The Predator is designed to operate with unencrypted datalinks. Depending on the theater of operation and hostile electronic combat systems present, the threat to the UAVs could range from negligible with only a potential of signal intercept for detection purpose, to an active jamming effort made against an operating, unencrypted UAV. The link characteristics of the baseline Predator system could be vulnerable to corruption of downlink data or hostile data insertions.18
This candid assessment demonstrates that the military officials were quite aware of several electromagnetic threats associated with this data link vulnerability, but chose not to mitigate them for several reasons. The first reason was the belief at the Pentagon that enemy combatants lacked the technical sophistication to intercept these signals,1 making the subsequent fiasco akin to the military’s failure to anticipate sophisticated IEDs in their counterinsurgency strategy.17
This is demonstrated by the fact that early Pentagon risk analyses focused on the threat of Russia or China exploiting this unencrypted data link to manipulate the surveillance feed such that “a commander looking on a feed, [would see] nothing, and then [have] an enemy tank brigade come roaring into [his] command post.” 17 In contrast to Russia and China, Afghan and Iraqi insurgents were not even considered threat-sources. The second reason for not mitigating was the Air Force’s view that this data link vulnerability would eventually be fixed by phasing out the Predator platform and replacing it with DarkStar, a next-generation UAV platform designed with encryption and stealth characteristics. This argument, found in an Air Force officer’s thesis from the School of Advanced Airpower Studies, may have made sense when the military owned only 167 drones in 2001,19 but in light of the 5500 drones the military possessed in 2009 (nearly all of which were unencrypted), it seems doubtful that thousands of these craft would actually be retired in the near-term.11 The third reason for not mitigating was the military’s insistence that the interception of UAV footage by enemy combatants did little damage. Ultimately, this is impossible to judge, but it appears that intercepted drone footage assisted certain high-value enemy combatants evade capture.13 The final reason for not mitigating was the military’s perception of the unencrypted data link as a “feature” that helped the sharing of data with less-advanced coalition partners. Given the technical state of Iraqi and Afghan police and military units, this view is logical, but in many ways this view created a lowest-common denominator approach to InfoSec.
Despite Admiral Mike Mullen’s assurances that the drone “hack” caused no damage, the Pentagon promised to step up the effects to prevent drone footage from falling into the wrong hands by upgrading all Predators to encrypt video data before transmission.20 However, due to the age of the platform and its reliance on proprietary design, the military has warned that it may be quite some time until these changes are fully completed.1 Certain military analysts have suggested that these technical modifications will likely not be completed until 2014, and even then, this fix would not solve the larger problem of dependence on an unencrypted COTS satellite technology for the transmission of critical military data.21
Conclusion
The overarching narrative of the history, design, use, vulnerability, and exploitation of the Predator UAV is important, given the increasing military bullishness toward unmanned systems. Leaders such as Major General Kenneth Israel state that UAVs “will play an increasingly important role in many military missions beyond intelligence, surveillance and reconnaissance.” 5 Indeed, military policy documents seem to reflect this view. An Air Force study called the Unmanned Aircraft System Flight Plan envisions a future where unmanned aircraft carry out all types of aerial missions, including the hitherto sacrosanct areas of dog fighting and strategic bombing.22 Recent research and development is slowly making this a reality. In response to the success of the Predator as an armed weapons platform, General Atomics has been developing a new generation of UAVs: the MQ-9 Reaper. Unlike the Predator, the Reaper has been conceptually designed and built to optimize its performance as a hunter-killer, which allows it to carry 15 times the weapons payload and equips it to take over many of the ground-support missions previously tasked to fighter jets.1 Because of similar capabilities, full squadrons of F-16 pilots are being retrained to fly the MQ-9 Reaper. As P. W. Singer, a defense analyst at the Brookings Institution, notes, the Predators “are very much Model T Fords. These things will only get more advanced.” 11
In light of the very strong possibility that unmanned aircraft may eventually become the United States’ primary vehicle for air power, it is important to consider the implications of the Skygrabber fiasco. Throughout the process of designing, testing, and fielding the Predator, the U.S. Air Force demonstrated a troubling tendency to view InfoSec concerns as an afterthought, when, in fact, electronics warfare is becoming an ever more-important element of military power. In a military environment where pilots telecommute to UAV hunter-killers on the other side of the world, it is absolutely crucial that the data links that carry UAV control data is protected more than any other component of the aircraft. Initially, the Pentagon viewed UAV technologies as inherently less risky than manned aircraft due to the relative safety of the pilot, allowing UAV procurement to be “on the ragged edge,” but now that UAVs are offensive weapons platforms, this can no longer be the case. If an enemy were to electronically penetrate the command and control channel of these hunter-killer UAVs, they could potentially use American weapons against American soldiers. This is ultimately the biggest problem. Under the current system, the development of UAVs is managed by aircraft program managers and purchased by pilots.21 Although these parties may understand airframes, they know little about networking and InfoSec. Going forward, the Pentagon must drop its cavalier attitude toward the security of its data links and integrate communications engineering and networking throughout the UAV development cycle.
References
1. Gorman, S., Dreazen, Y. J., and Cole, A. Insurgents hack U.S. drones: $26 software is used to breach key weapons in Iraq; Iranian backing suspected. The Wall Street Journal, sec. A. p. 1, December 17, 2009. http://online.wsj.com/article/SB126102247889095011.html (accessed February 13, 2011).
2. Giordano, J. and Maciag, C. Cyber forensics: A military operations perspective. International Journal of Digital Evidence 1(2), 2002.
3. Gorman et al., Insurgents hack U.S. drones, The Wall Street Journal, 17 December 2009, sec. A. p. 1. Technical information for the Skygrabber program can be found at http://www.skygrabber.com/en/index.php.
4. Appel, R. The secret war of Lisa Simpson. The Simpsons archive, May 18, 1997. http://www.snpp.com/episodes/4F21 (accessed March 27, 2011).
5. McDavid, H. and Oliver, D. Smart Weapons: Top Secret History of Remote Controlled Airborne Weapons. Welcome Rain, New York, pp. 9, 10, 14, 34, 50, 104, 112, 113, 115, 1997.
6. Yenne, B. Attack of the Drones: A History of Unmanned Aerial Combat. Zenith Press, Saint Paul, MN, pp. 8, 11, 12, 19, 21, 35, 60, 66, 85, 86, 2004.
7. Siuru, W. D. Planes without Pilots: Advances in Unmanned Flight. Tab/Aero Books, Blue Ridge Summit, PA, pp. 1, 7, 1991.
8. Habermas, J., Derrida, J., and Borradori, G. Philosophy in a Time of Terror: Dialogues with Jurgen Habermas and Jacques Derrida. University of Chicago Press, Chicago, IL, p. 34, 2003.
9. McCullagh, D. U.S. was warned of predator drone hacking. CBSNews.com, December 17, 2009. http://www.cbsnews.com/8301-504383 162-5988978-504383.html?tag=mncol%3btxt (accessed March 22, 2011).
10. Sandler, T. and Hartley, K., eds. Handbook of Defense Economics, Volume 2: Defense in a Globalized World. Elsevier, London, p. 1153, 2007.
11. Drew, C. Drones are weapons of choice in fighting Al Qaeda. The New York Times, March 17, 2009. http://www.nytimes.com/2009/03/17/business/17uav.html (accessed February 13, 2011).
12. Hodge, N. U.S. sharing predator video with Afghanistan, Pakistan. Wired.com, November 19, 2008. http://www.wired.com/dangerroorn/2008111/in-a-presentati/ (accessed March 22, 2011).
13. Phillips, M. Military surveillance hack warning. 60 Minutes, December 17, 2009 (original broadcast in 2002). http://www.cbsnews.com/video/watch/?id=5990213n (accessed April 10, 2011).
14. Official Site for … Skygrabber. http://www.skygrabber.com/en/index.php (accessed April 10, 2011).
15. For a complete video tutorial of how to operate SkyGrabber, please visit the developer’s official Web site at http://www.skygrabber.com/en/videotutorials/main/skygrabber how to work.php.
16. Hoffman, M. Fixes on the way for nonsecure UAV links. Air Force Times, December 18, 2009. http://www.airforcetimes.com/news/2009/12/airforceuavhack121809w/ (accessed February 13, 2011).
17. Commanders discussed drone hacking in 2004. CBSNews.com, December 18, 2009. http://www.cbsnews.com/stories/2009112/18/world/main5993716.shtml (accessed March 22, 2011).
18. U.S. Air Force. Air Combat Command Concept of Operations for Endurance Unmanned Aerial Vehicles (Version 2), December 3, 1996. http://www.fas.org/irp/doddir/usaf/conopsuav/partOl.htm (accessed April 10, 2011).
19. Stephenson, J. L. The Air Refueling Receiver That Does Not Complain. Air University Press, Maxwell AFB, p. 10, 1999.
20. Mullen: Drone hack caused no damage. CBSNews.com, December 18, 2009. http://www.cbsnews.com/stories/2009112/18/national/main5994775.shtml (accessed February 13, 2011).
21. Hodge, N. Fixing drone data: A not-so-modest proposal. Wired.com, December 21, 2009. http://www.wired.com/dangerroom/2009112/fixing-drone-data-a-not-so-modest-proposal/ (accessed March 22, 2011).
22. Axe, D. Air Force plans for all-drone future. Wired.com, July 17, 2009. http://www.wired.com/dangerroom/2009/07/air-force-plans-for-all-drone-future/ (accessed March 22, 2011).
23. Hoffman, M. Troops use archived UAV feed downrange. Air Force Times, February 27, 2010. http://www.airforcetimes.com/news/2010/02/airforcevideobank022710w/ (accessed March 22, 2011).
24. Hoffman, M. AF looks to automation to help monitor UAVs. Air Force Times, August 27, 2010. http://www.airforcetimes.com/news/2010/08/air-force-automation-uav-0827101 (accessed March 22, 2011).
25. Iraq rebels ‘hack into video feeds from US drones’. BBC News, December 17, 2009. http://news.bbc.co.uk/2/hi/8419147.stm (accessed February 13, 2011).
26. Jelinek, P. Pentagon: Insurgents intercepted UAV videos. Air Force Times, December 17, 2009. http://www.airforcetimes.com/news/2009112/ap uav insurgents hacked 121709/ (accessed February 13, 2011).
27. Martin, M. J. Predator: The Remote-Control Air War over Iraq and Afghanistan: A Pilot’s Story. Zenith Press, Grand Rapids, MI, 2010.
28. Mount, M. and Quijano, E. Iraqi insurgents hacked Predator drone feeds, U.S. official indicates. CNN.com, December 17, 2009. http:l/articles.cnn.com/2009-12-17/us/drone.video.hacked1uav-systems-encryption-feeds?s=PM:US (accessed February 13, 2011).
29. Official site for programs SkyGrabber (accepting free to air satellite data by digital satellite TV tuner card (DVB-S/DVB-S2)), LanGrabber (save YouTube video), Tuner4PC (software for satellite internet). http://www.skygrabber.com/enlindex.php (accessed April 10, 2011).
30. Rolfsen, B. Unmanned a misnomer when it comes to UAVs. Air Force Times, June 11, 2010. http://www.airforcetimes.com/news/2010/06/airforceuavpersonnel061110w/ (accessed March 22, 2011).
31. Schneier, B. Insurgents intercepting predator video? No problem. Wired.com, December 23, 2009. http://www.wired.com/politics/security/commentary/securitymatters/2009112/securitym atters 1223 (accessed March 22, 2011).
32. Shachtman, N. Military faces bandwidth crunch. Wired.com, January 31, 2003. http://www.wired.com/techbizlit/news/2003/01/57420 (accessed March 22, 2011).
33. Shachtman, N. Not just drones: Militants can snoop on most U.S. warplanes. Wired.com, December 17, 2009. http://www.wired.com/dangerroom/2009112/not-just-drones-militants-can-snoop-on-most-us-warolanes/ (accessed March 22, 2011).
34. SkyGrabber and the curse of encryption. Strategypage.com, December 19, 2009. http://www.strategypage.comlhtmwlhtairfo/articles/20080811.aspx (accessed February 13, 2011).
35. Spoth, T. GAO: UAV surge leaves many shortfalls. Air Force Times, April 16, 2010. http://www.airforcetimes.com/news/2010/04/airforcegaouavs041610w/ (accessed March 22, 2011).
36. Taylor, J. W. R. and Munson, K. Jane’s Pocket Book of Remotely Piloted Vehicles: Robot Aircraft Today. Collier Books, New York, 1977.
37. U.S. Air Force. Unmanned Aircraft Systems Flight Plan 2009–2047. HSDL, Washington, DC, 2009. http://www.scribd.com/doc/17312080/United-States-Air-Force-Unmanned-Aircraft-Systems-Flight-Plan-20092047-Unclassified (accessed March 22, 2011).
38. U.S. House of Representatives, Committee on Oversight and Government Reform, Subcommittee on National Security and Foreign Affairs. Rise of the Drones: Unmanned Systems and the Future of War. HSDL, Washington, DC, 2010.
39. Warplanes: The rise of the droids. Strategypage.com, August 11, 2008. http://www.strategypage.com/htmwlhtairfo/articles/20080811.aspx (accessed February 13, 2011).