Untangle Network Security (2014)
Chapter 11. Untangle WAN Services
This chapter covers the services provided by Untangle to allow you to get the full utilization of multiple Internet connections. With Untangle WAN services, you can use multiple cheap ADSL lines instead of one expensive leased line, which, when goes down, will disconnect you from the Internet.
WAN Failover allows you to use multiple WAN interfaces and get a continuous Internet connection. It detects disconnected interfaces and redirects their traffic to another available interface. WAN Balancer allows you to maximize bandwidth utilization by distributing your network traffic among multiple WAN interfaces.
WAN Balancer has some dependencies on the WAN Failover; thus, Untangle offers WAN Failover with no additional charge for the purchases of the WAN Balancer.
To utilize the functionality of multiple WAN interfaces, your Untangle NGFW internal interface should be in addressed mode and not bridged mode.
A list of topics that will be covered in this chapter are as follows:
· Untangle WAN Failover
· Untangle WAN Balancer
WAN Failover
With Untangle WAN Failover, you can provide a redundant Internet connection to your network. Untangle WAN Failover runs connectivity tests on each WAN interface; you have to determine its status. If any test failed for a certain amount of time, the WAN interface will be considered to be down, and the traffic will be rerouted to the WAN interface with the lower ID.
Setting up interface tests
For Untangle Failover to work properly, you should configure the connectivity test for each WAN interface you have. Untangle NGFW provides different tests that could be used to determine WAN interface connectivity:
· Ping test: Untangle NGFW will ping a configured IP address
· ARP test: Untangle NGFW will request the MAC address of the interface's gateway using the Address Resolution Protocol (ARP)
· DNS test: Untangle NGFW will try to query the DNS server configured in the interface settings
· HTTP test: Untangle NGFW will try to create an HTTP connection to a specific site
You should select the test to be used carefully. For example, if you used an HTTP test and the website you're running your test against is down while your Internet connection is up, Untangle NGFW will consider the interface to be disconnected as the configured test will fail.
You can create a new test by pressing the Add button located under WAN Failover settings | Tests. You will need to configure the following settings:
· Interface: Select the interface you wish to run the test on.
· Description: Enter a suitable description for your test.
Note
Adding the description will help you identify the tests in the event logs.
· Testing Interval: The test will run based on the defined time interval. The default interval is 5 seconds.
· Time Out: This is the time that Untangle NGFW will wait for a response before it considers the test as a failed test. The default time-out is 2 seconds.
Note
It's important to select a time-out that is lower than the time interval.
· Failure Threshold: This is the number of failed tests (out of 10) to consider the interface to be down. The default value is 3 tests out of 10.
· Test Type: Select the test type you want to use (that is, Ping, ARP, DNS, and HTTP).
These settings are illustrated in the following screenshot:
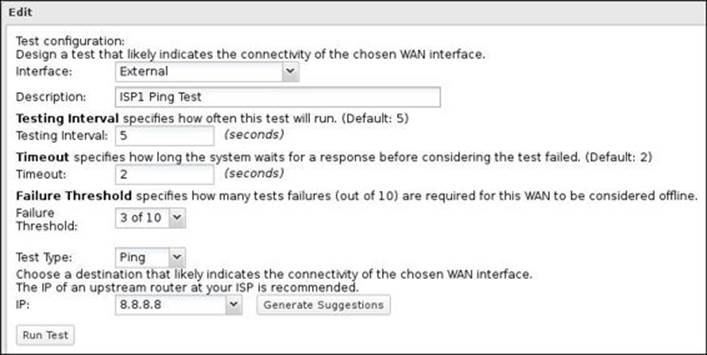
The default value for the Ping Test IP is 8.8.8.8, which is the Google's DNS server. You can use the default value as it represents a high available destination for your test. However, Untangle recommends the usage of an upstream router of your ISP, as when the router is down, your connection will probably be down.
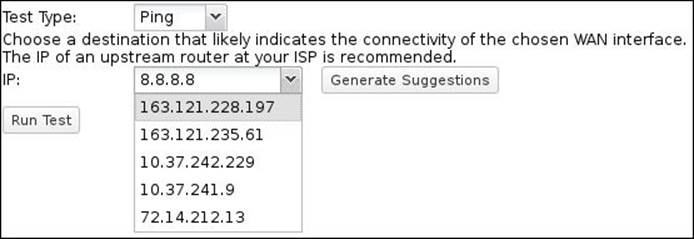
The Generate Suggestions button will perform a trace route to 8.8.8.8 that will return the routers between you and Google. Select an appropriate router from the IP drop-down menu. The higher the IP in the list, the closer the router is to you. The Run Test button could be used to test your settings and check whether the configured test would work properly or not:
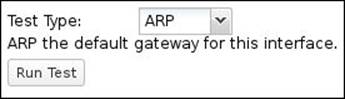
The ARP test will try to get the MAC address of the gateway configured in the interface settings. There is nothing to configure here.
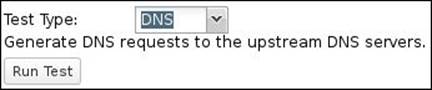
The DNS test will run a query using the DNS server configured in your interface settings. Also, there is nothing to configure here.
The HTTP test will try to connect to a website that you will configure. You can use a hostname or an IP address to complete this test. However, using an IP address is better as a DNS query would not be required.

Reviewing the WAN Failover events
You can review your WAN interface's connection status from different sources. The first place to achieve this is the WAN Failover application faceplate, which will provide you with the total number of current connected and disconnected WAN interfaces. In addition, it shows the total number of state changes, and whether a WAN interface state has changed from connected to disconnected or vice versa, as shown in the following screenshot:

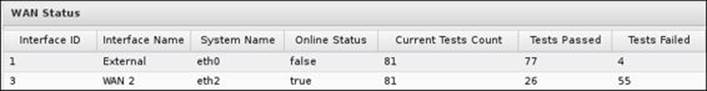
The second place to achieve this is under WAN Failover Settings | Status, which shows the different interfaces and their current status (online or offline), and the total number of tests that are completed and how many passed and failed:
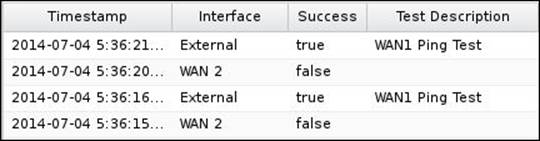
The third place is the WAN Failover application event logs. There are two different event logs. The test event log shows when individual tests were run and whether they failed or succeeded:
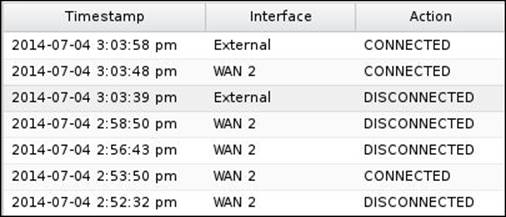
The event log shows the interface status change events:
The fourth place is the Reports application from which we can find the following summary reports:
· WAN Availability: This gives us a percentage of the number of times we were fully connected or partially connected or not connected to the Internet
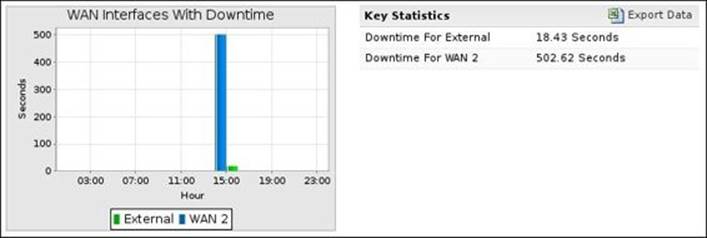
· WAN Interfaces With Downtime: This indicates for how long the interface was down
· WAN Interfaces With Failure: This indicates the number of times the interface was down
The following screenshot shows the WAN Interfaces With Downtime summary report:
WAN Balancer
With Untangle's WAN Balancer, you can distribute your traffic across multiple ISPs to provide a higher bandwidth for your network. Untangle NGFW will dynamically distribute the traffic to different WAN interfaces based on the set rules. Untangle NGFW distributes the traffic based on the number of sessions and not bytes.
Untangle's WAN Balancer will not increase the total available speed for one session, but it will increase the available bandwidth for your entire network. For example, if you have 1 Mbps and 2 Mbps connections, no individual session can use the 3 Mbps. Instead, a session can use the 2 Mbps connection and another session can use the 1 Mbps connection.
Configuring traffic allocation
You could set the weights of traffic to be directed to each WAN interface under the WAN Balancer Settings | Traffic Allocation tab. By default, Untangle will divide the load equally on the different interfaces. Thus, if you have two interfaces, each interface will get 50 percent of the traffic, as shown in the following screenshot:
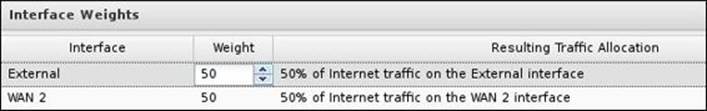
It's recommended to set the interfaces' weights based on their bandwidth. Thus, if you have 1.5 Mbps and 6 Mbps connections, you will set the weights as 15 and 60. The resulting traffic allocation ratio will automatically be changed to reflect the percentage of traffic that will be processed by each interface, as shown in the following screenshot:
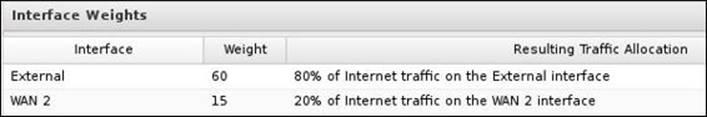
When a new connection is to take place, the WAN interface to be used is determined based on the weights assigned for each interface. Once the connection is established, Untangle NGFW will cache that route (the connection between two specific IPs is done through a specific interface). If any new session is to be established and there is a cached route for it, that cached route would be used (that is, the previously used interface will be used again). Thus, the weights are applied on new sessions with no cached routes. The preceding behavior is also known as sticky sessions, which are used to prevent SSL-enabled websites and some cloud services from breaking down.
Note
HTTPS sessions are sticky, while HTTP cloud services that are based on multiple load-balanced web servers need to use sticky sessions.
It is common for a web application to need to track a user's progress between pages. Some examples include keeping track of login information or the progress through a test with correct/incorrect totals, the items in a shopping cart, and so on.
The track is simple if the web application was using only one web server. When the application starts to use multiple load-balanced web servers, it is a must to use sticky sessions.
Sometimes, when a change is done on any of the connection endpoints, the session will break down and issues can occur. The cause of the changes in the endpoints could be that the load balancer was forced to shift users to a different server or because the user was using a WAN failover, or in the case that the user was using a WAN Balancer solution that does not support sticky sessions.
The resultant issues are related to the loss of user's session data; the effects of this will vary depending on the application and what the user was doing at that time. Perhaps, they can get booted back to a login prompt, or maybe they lose the contents of their shopping cart, or maybe they suddenly lose their place in the test and are forced back to the beginning. All of these cases make the application appear defective to the end user.
For more information, visit http://www.chaosincomputing.com/2012/05/sticky-sessions-are-evil/.
Setting Route Rules
Sometimes, you want certain traffic to always use a certain interface. For example, if you have an e-mail server and you have two connections, one of which is an ADSL line in which the outgoing SMTP traffic is blocked by ISP, you will set a rule that will make the internal e-mail server always use the other connection for outgoing SMTP traffic. Also, VOIP sessions need to be sticky to the same interface, or they will fail.
Route Rules are similar to other Untangle NGFW rules in that they are evaluated from above downward, and if a match is found, the rule will be applied. If no match is found or the rule is set to balance the traffic, the traffic will be randomly assigned to a WAN interface based on its weight. There are five matchers that could be used with Route Rule, which are as follows:
· Source Address
· Source Port
· Destination Address
· Destination Port
· Protocol
The following screenshot shows a route rule that will direct any outbound SMTP traffic to WAN 2 interface:
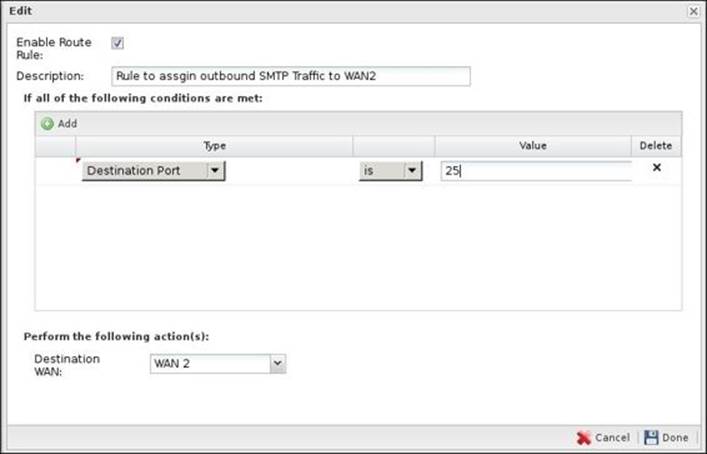
If the Routes configured under Config | Network | Routes are in conflict with the Route Rules, the Routes configured under Config | Network | Routes will always override any Route Rule. Also, if the interface selected in the Route Rules was detected to be down by the WAN Failover, WAN Balancer will assign the traffic to an interface based on the defined weights.
Note
WAN Failover is necessary for the WAN Balancer functionality as you won't distribute traffic to a failed-down interface.
As sessions are sticky, when the sessions interface goes down and a failover occurs, any new session will be processed by a new interface, but the old opened sessions will remain sticky to the down interface and won't change the interface; thus, the user of the computer that is running those individual sessions needs to reset them.
Reviewing the WAN Balancer status
As with all Untangle applications, we could review the status of the application from its faceplate, or from its status and event logs tab, and from the Reports application.
The WAN Balancer faceplate shows the total number of sessions processed by each WAN interface:

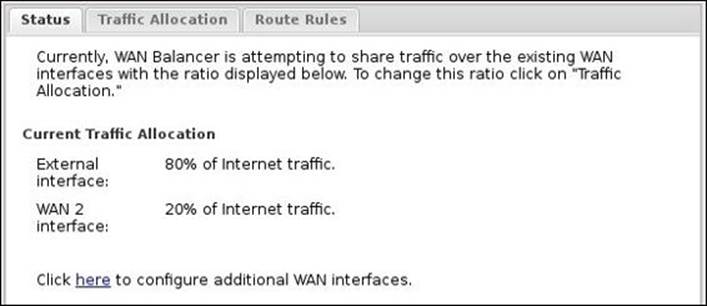
The Status tab shows the configured traffic allocation percentage and provides a link to Config | Network | Interface to allow you to configure any additional WAN interfaces.
The Reports application provides a summary report about the maximum and average bandwidth usage by each interface. Also, it provides many summary reports related to the sessions' activity on each WAN interface. The reports are as follows:
· Bandwidth Usage: This shows the maximum and the average bandwidth usage for each WAN interface in KB/sec
· Active Sessions: This shows the maximum number of sessions at any single time, and the average number of sessions during the day
· Sessions By WAN: This shows the maximum and the average number of sessions/hour for each WAN interface
· Traffic By WAN: This gives you the maximum and the average KB/hour for each WAN Interface
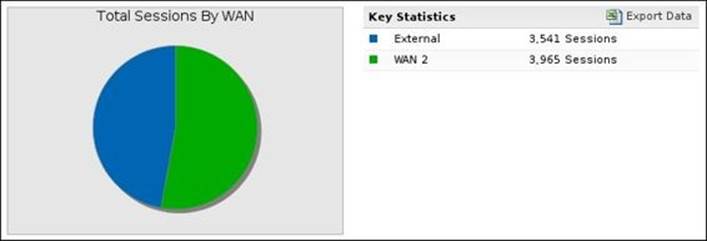
· Total Sessions By WAN: This shows the number of sessions processed by each WAN interface
· Bandwidth by a WAN interface: This gives you the amount of the bandwidth usage for each WAN interface
The following screenshot shows the Total Sessions By WAN summary report:
Troubleshooting
This troubleshooting part applies for both Untangle WAN Failover and Untangle WAN Balancer as the troubleshooting steps for both are similar. Besides the normal troubleshooting listed in Chapter 4, Untangle Advanced Configuration, if you have a problem with the WAN connection, you should do the following tasks:
· Check whether the modem/router is up.
· Check whether Untangle NGFW is able to reach the modem/router. Try to ping the modem/router from the Untangle NGFW administration console.
· Check whether the clients behind Untangle NGFW are able to reach the modem/router. Try to ping each of your modem routers from the clients.
· Make sure that each ISP's interface is configured to be a WAN interface under Config | Networking | Interfaces. Also, ensure that the interfaces have all of the required information properly entered.
· Verify that the WAN Failover has tests set up for each WAN connection.
· If you're only using WAN Failover, you'll need to disconnect your primary WAN to get traffic to flow over the secondary one.
· If you're using WAN Balancer, make sure your weights are set properly.
· You can test the WAN Balancer functionality by going to any of the show my IP sites.
· When you're using WAN Balancer beside WAN Failover and have connection problems, ensure that the WAN Balancer does not distribute traffic to a down interface as the WAN failover might be turned off or uninstalled.
Summary
In this chapter, we covered two Untangle applications related to WAN interfaces. The two applications allow us to utilize multiple WAN interfaces and get all the benefits from this setup. Untangle WAN Failover is used to provide a constant Internet connection by failing over all traffic from a down WAN interface to another interface. Untangle WAN Balancer is used to enhance network connection and bandwidth utilization by distributing your network traffic among multiple WAN interfaces.
The next chapter will cover the VPN solutions provided by Untangle NGFW. Open VPN is a free module using SSL-based VPN. OpenVPN is based on the well-known open source project (OpenVPN). Also, Untangle provides a paid IPsec VPN module that has some additional features over the OpenVPN module. Both the applications provide remote access (user-to-site) and site-to-site VPN connections.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.