Untangle Network Security (2014)
Chapter 5. Advanced Administration Settings
So far, we have our Untangle NGFW server up and running and its advanced networking settings have been configured. In this chapter, we will learn how to enhance the administration experience of Untangle NGFW.
We will cover how to manage the administrators' accounts, how administrators can remotely administrate Untangle NGFW, how to configure Untangle NGFW to be publicly available on the Internet, and how to configure Untangle NGFW regional settings. Furthermore, the chapter will cover how to make Untangle NGFW only parse certain protocols. Then, we will cover the support options available from Untangle, and how to change the administration console theme.
In addition, this chapter will cover the configuration of the digital certificates used by Untangle NGFW to provide secure access to its services such as the administration console, and to be used with the HTTPS inspector application. We will also learn how to configure Untangle NGFW to send e-mails and how to manage the spam quarantine.
Furthermore, the chapter will cover how to create local users on the Untangle NGFW that can be used to allow users to authenticate and apply different policies on them. The process of upgrading the Untangle NGFW and the backup and restore of the server will also be covered.
Eventually, the chapter will cover how you can monitor your Untangle NGFW and review the system information and the license details.
In this chapter, we will cover the following topics:
· Configuring the administration settings
· Managing Untangle SSL certificates
· Configuring Untangle NGFW e-mail settings
· Managing the Untangle NGFW local directory
· Exploring Untangle NGFW server upgrade
· Backing up and restoring Untangle
· Monitoring the Untangle NGFW server
· Looking at system information and license details
Configuring the administration settings
In this section, we will learn how to manage the administrator accounts, configure the remote administration options, configure the public address that will be used by the Untangle modules to give external users access to the services provided by these modules, configure the regional settings, specify which protocols Untangle will be able to understand and interact with, review the different support options available on Untangle NGFW, and finally, changing Untangle NGFW skins.
Managing the administrator accounts
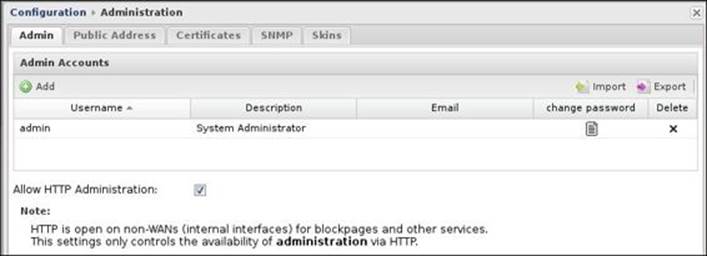
We can manage Untangle NGFW administrator accounts under Config | Administration | Admin. Under this tab, we can create additional administrator accounts, change the accounts' password, and assign e-mail addresses to the accounts.
By default, we have the admin account created during the initial configuration wizard. We can add an additional account that has administrative privileges over the Untangle NGFW server through the Add button, as shown in the following screenshot:
Configuring the remote administration settings
We can manage Untangle NGFW either through HTTP, HTTPS, or SSH. In this section, we will see how we can configure the different options related to the remote administration.
HTTP remote administration is allowed for the internal subnets only. You can't use HTTP to access Untangle NGFW from the external interfaces. You can disable/enable the HTTP remote administration from the Allow HTTP Administration checkbox located under Config |Administration | Admin.
Note
Disabling the HTTP administration is only related to the administration console. Any other HTTP-related services such as the captive portal will continue using HTTP as normal.
By default, HTTPS remote administration of Untangle NGFW is allowed for the internal interfaces and disabled for the external interfaces. You can allow the usage of HTTPS on the external interfaces by checking the Allow HTTPS on WANs checkbox located under Config |Network | Advanced | Input Filter Rules.
In addition, SSH remote administration is disabled by default. You can enable it by checking the Allow SSH checkbox located under Config | Network | Advanced | Input Filter Rules.
Note
Enabling SSH is not recommended by Untangle. However, if you want to enable it, ensure that you have a strong password for your administrator account.
Configuring the public address of Untangle NGFW
Some Untangle NGFW services need to be externally accessible. For example, the Quarantine Digest sends e-mails to the users. The e-mails include a link that refers back to the Untangle NGFW server. The address used in this link (that is, the public address) should be externally accessible. These settings could be configured under Config | Administration | Public Address.
The different options that can be used as the Untangle NGFW public address are as follows:
· IP address from External interface: This uses the IP address of the primary interface. This is recommended if Untangle NGFW has a routable public static IP address.
· Hostname: This will use the hostname configured in Chapter 4, Untangle Advanced Configuration. This option is recommended if the FQDN of the Untangle NGFW server is resolvable both internally and externally.
· Manually Specified Address: This option will use custom configured IP/hostname and port number. This option is suitable for Untangle NGFW servers installed on a transparent bridge mode behind another firewall. You can configure port forward on the other firewall (using the new custom port) to the Untangle NGFW server.
Configuring the regional settings
Regional settings include the time, time zone, and language settings. The regional settings can be configured under Config | System | Regional.
Using the correct time and time zone on your server are very important aspects as the events will use the server time as their timestamp, and the time-based policies will also use the server time.
Untangle NGFW uses Network Time Protocol (NTP) to automatically sync its time. The current time is shown under the Current Time part. If you noticed any time deviation between the server time and the real time, you can force time synchronization via the Synchronize Timebutton. In addition, you can modify your time zone from the Timezone drop-down list.
You can change the system language by selecting the desired language from the Language drop-down list. If you didn't find your language in the drop-down list, you can press the Download New Language Packs hyperlink, which will send you to pootle.Untangle.com where you can download or even create a new language pack. The downloaded language packs can be imported to Untangle NGFW under the Upload New language Pack part.
Configuring Untangle NGFW processing of protocols
Many of the Untangle NGFW applications depend on certain protocols such as HTTP, FTP, and SMTP. You can configure whether you want Untangle NGFW to process these protocols under Config | System | Protocols, as shown in the following screenshot:
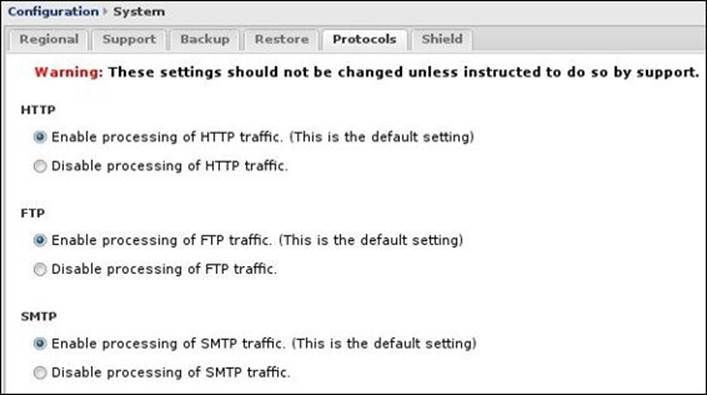
When the processing of a certain protocol is enabled, Untangle NGFW will be able to translate the sessions to the right format and forward them to the dependent applications. If the protocol processing is disabled, the sessions will still be treated as a binary stream but will not beparsed and unparsed and hence the dependent application functionality will be affected.
Note
You should not change these settings unless instructed to do so by support.
The available protocols and the visibility of the Protocols tab itself depends on the currently installed applications.
Understating the available support settings
Untangle offers different options for support purposes such as allowing Untangle's support team to access your server, and manually restart or shut down the server from the administration console. Furthermore, you can rerun the initial configuration wizard anytime you wish to reconfigure the Untangle NGFW server. The support settings can be accessed from Config | System | Support.
For support purposes, you can allow the Untangle support team to access your server by checking Allow secure access to your server for support purposes. No changes will be needed on any firewall in front of Untangle NGFW.
In addition, you can manually reboot or shutdown the server by pressing the Reboot or Shutdown buttons. Also, you can rerun the initial configuration wizard at any time by pressing the Setup Wizard button.
Changing Untangle NGFW skins
Skins control the look and feel of the administration interface. You can select a skin from the existing skins or upload a new custom skin under Config | Administration | Skins, as shown in the following screenshot:
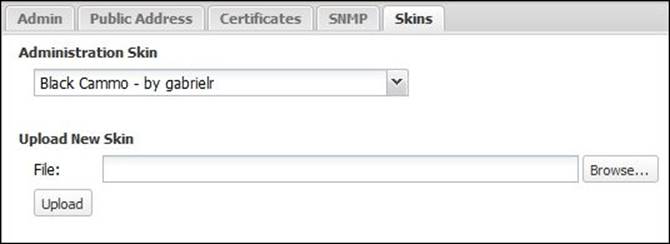
Creating custom skins requires extensive work and knowledge of HTML and CSS. You can download Untangle Skins Cookbook, which gives you instructions on creating custom skins, from http://wiki.untangle.com/images/c/c1/Untangle-Skin-Cookbook.zip.
The following screenshot shows the Dell skin designed by MikeTrike:

Managing Untangle SSL certificates
Untangle uses the digital certificates to provide secure access to the Administrative Console and Email Quarantine via SSL. In addition, digital certificates are also required for the HTTPS Inspector application. The Untangle NGFW certificates settings can be configured from Config |Administration | Certificates.
The certificate authority
A default certificate authority (CA) is automatically created during the server's initial installation. This CA is used to create and sign the imitation certificates used by the HTTPS Inspector application. It also generates the default server certificate that is used to securely access the administration console.
We can keep using the default CA, or we could create a new CA if we want to customize the information contained in the root certificate. To create a new CA, press the Generate Certificate Authority button; this will present a pop up in which we will need to enter the details to be included in the Subject DN of the new root certificate. The Common Name (CN) field is the only mandatory field; all other fields are optional. As this is not a server certificate, the CN field could be anything you like (for example, Untangle-CA).
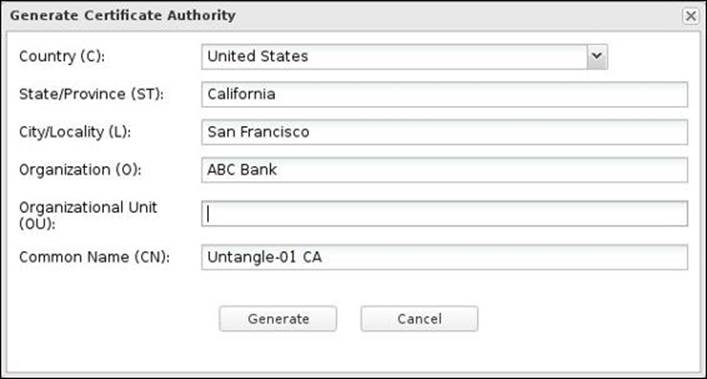
To eliminate the certificate security warnings on the client computers, you will need to add the Untangle CA root certificate to the clients' trusted root CA. We can get the Untangle root certificate by pressing the Download Root Certificate button to download the root_authority.crtcertificate file.
Tip
Adding the Untangle CA root certificate to the clients trusted root CA is covered in Chapter 8, Untangle Filters.
The server certificate
The Server Certificate is used with the SSL connections to the server such as the Administrative Console and the Email Quarantine pages. We can keep the default certificate or generate a new server certificate for the customization of the included information. The new certificate can be issued either by the server internal CA or by a third-party CA.
The server's internal CA is more suitable in cases where the HTTPS Inspector is enabled. The HTTPS Inspector only uses the internal CA. Thus, the internal CA root certificate will be already imported to the clients for the proper functionality of the HTTPS Inspector, and you will not need to do any additional configuration to the clients.
If you don't plan to use the HTTPS Inspector, it's more suitable to use an external CA that is already trusted by the client computers such as VeriSign, Thawte, or even Active Directory CA. So, you won't have to install the new root certificate on the different clients.
You can generate a new server certificate signed by the local CA by clicking on the Generate Server Certificate button. You will be presented with a pop up in which you could enter the server certificate's Subject DN details. The only mandatory field is the Common Name (CN) field, which should be the server name (for example, Untangle-01.ABC.local); all other fields are optional. Once created, the Untangle NGFW server will start to use the new server certificate immediately.
To generate a new server certificate issued by a third-party CA, we first need to have Certificate Signing Request (CSR). To create the CSR, press the Create Signature Signing Request button, which will open a pop up in which you will need to enter the Subject DN details to be included in the CSR. Once you have completed the form, click on Generate. A server_certificate.csr file will be downloaded to your computer.
The CA will use the CSR file to issue the new server certificate. You'll need to import the new certificate to the server so that it can start using it. This can be done via the Import Signed Server Certificate button.
Configuring the e-mail settings of Untangle NGFW
Some Untangle NGFW features such as Reports and Spam Blocker require Untangle NGFW to be able to send e-mails to administrators and end users. In this section, we will cover how to configure Untangle NGFW to send e-mails. In addition, this section will cover how to make Untangle NGFW trust particular senders such that it will not scan any e-mails coming from those senders by the Spam and Phish Blockers.
Furthermore, this section will cover how to manage Untangle NGFW quarantine, which is used to temporarily store spam e-mails instead of delivering them to the intended recipient and give that recipient the option to release or delete the spam messages. The e-mail settings can be configured under Config | Email.
Configuring the outgoing e-mail server
Untangle NGFW is able to send daily spam quarantine digest e-mails to the related users and daily server activities summary reports to the administrators. Thus, we will need to configure the way Untangle NGFW will use to send these e-mails. Untangle NGFW can send e-mails directly using the SMTP daemon or through SMTP relay. These settings are available under Config | Email | Outgoing Server.
If Send email directly is checked, Untangle NGFW will use the SMTP daemon to send the e-mails without relying on another e-mail server. Untangle NGFW will look up for the recipient domain MX record and will send the message to that address.
As many ISPs block port 25 to prevent spam, Untangle NGFW will not be able to send e-mails directly and the usage of SMTP relay will be required. To use SMTP relay, check the Send email using the specified SMTP Server option and provide the relay SMTP server IP address or hostname, the server port, and any authentication credentials, if required.
Note
You may have to configure the SMTP relay server to allow Untangle NGFW to relay e-mail through it.
The Email from Address section is the from e-mail addresses that will appear on all e-mails sent by the Untangle NGFW server except to the e-mails released from the quarantine.
The following figure shows the configurations used on Untangle-03 where Acme-EX01 is used as a SMTP relay for Untangle-03:
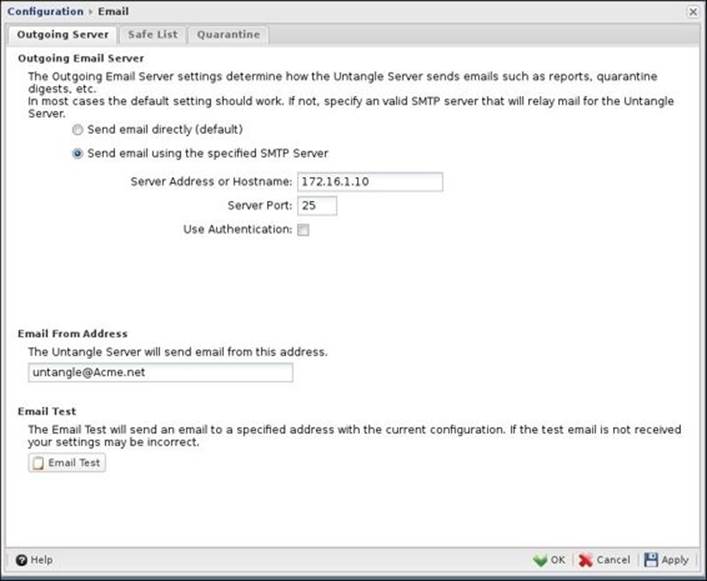
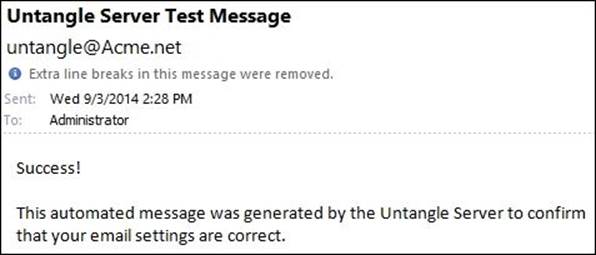
The Email Test button sends a test e-mail from the configured Email from Address section to validate the server configurations. You will need to define the recipient of that test e-mail. The following screenshot shows a test e-mail sent from Untangle-03 to Acme Administrator:
Configuring trusted senders
Safe lists are used by the Spam Blocker and Phish Blocker applications to define trusted sources whose e-mails will not be scanned in order to save resources and/or avoid false positives. These settings can be configured under Config | Email | Safe List.
· Global Safe List: This is applicable to all users. All e-mails from a listed address will not be scanned by Spam Blocker or Phish Blocker. You can add a single e-mail address or even an entire domain to the list using *@example.com.
· Per-User Safe List: Each user's e-mail address has its own safe list. Thus, e-mails from a certain address will not be scanned for this certain user, while it will be scanned for the remaining users. A user can add a single e-mail or an entire domain, or even disable the scanning of all the received e-mails by adding *. Users can edit their safe lists via the quarantine web application that is accessible via https://UNTANGLE_IP:HTTPS_PORT/quarantine/. In addition, administrators can access and control the users' safe lists from the administration console.
Managing the Untangle NGFW quarantine
When the Spam Blocker and Phish Blocker applications determine an e-mail as spam or phish, these applications should drop this e-mail. However, this could be a legitimate e-mail (that is, false positive) and the e-mail is important. So, instead of dropping the e-mails, they will be delivered to the user's quarantine. Then, the user has the option to review and release the e-mails to his or her inbox or completely delete them.
Daily quarantine digest e-mails will automatically be sent to users with new e-mails in their quarantine. In addition, the users can manually generate a Quarantine Digest from https://UNTANGLE_IP:HTTPS_PORT/quarantine/.
The quarantine settings can be configured under Config | Email | Quarantine. The different settings are as follows:
· Maximum Holding Time (days): This sets the duration an e-mail will be held on the quarantine before it is automatically deleted.
· Send Daily Quarantine Digest Emails: This configures whether to send the daily Quarantine Digest to the users or not.
· Quarantine Digest Sending Time: This configures when to send the daily digests.
· User Quarantines: This shows a list of the currently existing user quarantines. User quarantines are automatically created when an e-mail is quarantined for this user and will automatically be deleted when no more messages remain. We can release entire user quarantine via theRelease Selected button or delete the entire user quarantine via the Purge Selected button. Additionally, we can view the individual messages in a user quarantine via the Show Detail button. We also have the option to release or purge single messages.
· Quarantineable Addresses: The e-mail addresses on this list will have quarantines automatically created. All other e-mails will be marked and not quarantined. By default, an entry of * could be found, and it's advisable to not change any settings in this part.
· Quarantine Forwards: This is a list of e-mail addresses whose quarantine digest gets forwarded to another account. This is common for distribution lists where the whole list should not receive the digest; instead, the digest would be sent to an administrator who can manage the spam on the distribution list quarantine.
Accessing Untangle's quarantine web application
The users can manage their quarantines through the quarantine web app, which is accessible via https://UNTANGLE_IP:HTTPS_PORT/quarantine/ or through a link provided in the digest e-mails. The quarantine contains the following tabs:
· Quarantine Messages: This shows the currently quarantined messages. You can release and add the sender to the user's safe list or delete the messages
· Safe List: This configures the user's safe list
· Forward or Receive Quarantines: As discussed earlier, it's better to forward the digest e-mails to the distribution list admin instead of sending this e-mail to all users
o Forward Quarantined Messages To: This defines an e-mail address to forward the quarantined message to it
o Received Quarantined Messages From: This shows the other addresses that have forwarded quarantined messages to this quarantine
Note
Additional details on Untangle quarantine can be found in Chapter 6, Untangle Blockers.
Managing the local directory of Untangle NGFW
We can connect the Untangle NGFW server to different directories of users. Thus, we can apply different policies on different users. For example, we can define which users have access to the social network websites and which users don't have that right.
The directories of users could be the Active Directory, a local directory on the Untangle NGFW server, or a local directory on Radius servers. In this section, we will learn how to manage the Untangle NGFW local directory.
The Untangle NGFW local directory can be managed under Config | Local Directory. The created users are used for authentication and applying different policies. They don't have administrative privileges or have access to the admin console.
To add new users to the local directory, click on the Add button. This will open the Edit window in which you will need to supply a username, first name, last name, e-mail address, password, and expiration time, as shown in the following screenshot:
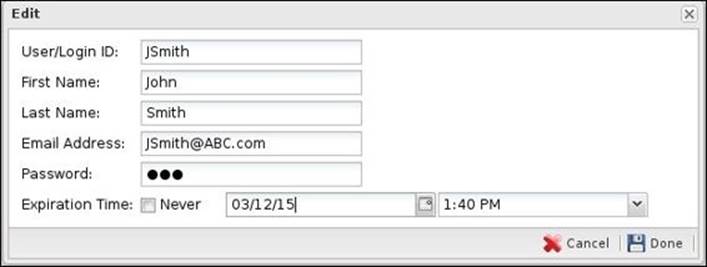
Only the User/Login ID, Email Address, and Password fields are required.
Note
A login ID can only have alphanumeric values. So, a login ID such as J.Doe is an invalid ID.
The password field can't be left empty. You have to enter at least one character password. Only the administrators have the right to set the user password.
In addition, an expiration date could be set for a specific user. Thus, that user would not authenticate after that date. The Cleanup expired users button removes the expired users from the local directory.
Upgrading Untangle
In this section, we will see how to configure Untangle NGFW to look for and install new updates. Upgrade settings are available under Config | Upgrade.
We have to perform all the possible upgrades before being able to download and install the different Untangle modules. We have two tabs under Upgrade: Upgrades and Upgrade Settings, as shown in the following screenshot:
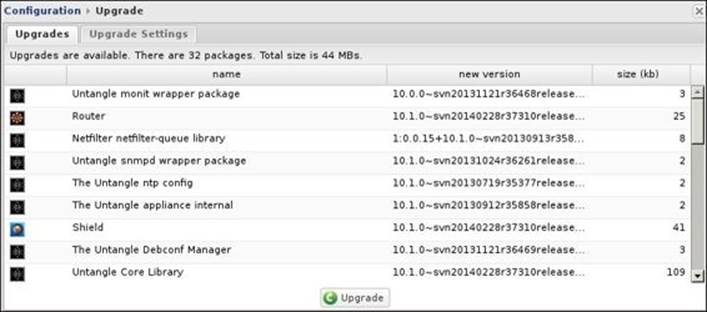
The Upgrades tab will only be shown if any upgrades are available to be downloaded. The upgrades will be listed as shown in the preceding screenshot. The upgrade process will download and install all the available upgrades and you cannot select to apply or reject individual updates. To start the upgrade process, press the Upgrade button at the bottom. The upgrade process will download the new packages and install them. During the process, do not reboot or power off the server. While the packages are being upgraded, the administration interface will lose connection to the server. The following screenshot shows the upgrade process of Untangle NGFW:
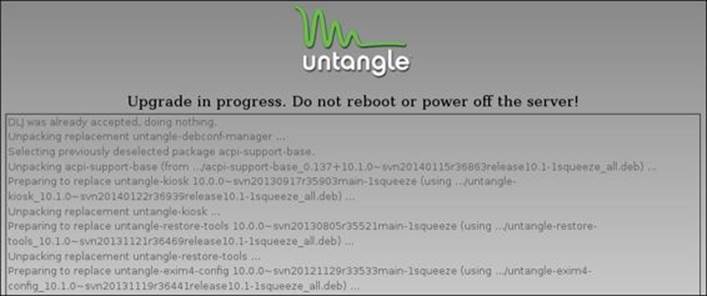
The Upgrade Settings tab configures when Untangle NGFW looks for and installs the new upgrades. If Automatically Install Upgrades is checked, Untangle will automatically look for new versions and upgrades as defined by Automatic Upgrade Schedule. In addition, you have the option to manually look for updates.
Backing up and restoring
In this section, we will cover how to back up and restore all Untangle NGFW configurations, and how to back up and restore individual settings.
Backing up and restoring all Untangle NGFW configurations
You can back up your Untangle NGFW configurations to be restored later in case of server failure or misconfiguration. In addition, the server backup can be restored to another server to simplify the configuration process of the other server by importing the already configured settings. Backup and restore settings are located under Config | System.
Backups will store the current Untangle NGFW server settings in the .backup file. The file will include the settings in Config and the Applications. It will not include the reporting data, the quarantine data, or any unique configuration such as the unique ID (UID) of the server.
After clicking on the Backup to File button located under Config | System | Backup, a backup will be created based on the current configuration. The .backup file can be saved to your local server or to the administration PC.
The Restore tab allows you to restore the Untangle configuration settings from the backup files, as shown in the following screenshot:
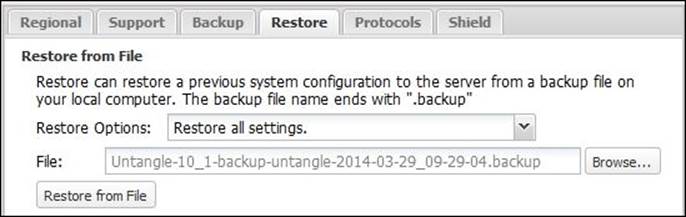
To restore from .backup file, we'll need to specify the desired restore options, which are as follows:
· Restore all settings: This is typically used to restore from failure cases as it will restore all the server configurations including the network settings
· Restore all except keep current network settings: This option is useful to maintain a standard configuration across the servers while each server has its unique network settings
After that, you will need to navigate to the desired .backup file location and select it. Then, you will need to press the Restore from File button to start uploading the restore file to the server and begin the restore process.
Note
The restore process will reset the server to same state when the backup was done. This means that if any programs have been removed after to the backup, it will be automatically installed again, and any newly installed programs will be removed.
Typically, the only supported versions of the restore process will be the current version of Untangle NGFW and the immediately prior major version. For example, 10.2 will restore 10.2 backups and 10.1 backups, but not 10.0.
After the beginning of the restore process, the Untangle NGFW processes will reboot and you will lose connection to the server. After reconnecting to the server, you will see the settings and configuration restored from the backup file.
Backing up and restoring individual settings
Different Untangle modules and configurations tabs include the Import and Export buttons, which allows you to back up and restore individual settings.
The following screenshot shows the Block File Types list of the Web Filter application. You can back up the configured list as a baseline and restore it to the same server when you need or you can restore it to another server to keep consistent configurations between your servers, as shown in the following screenshot:
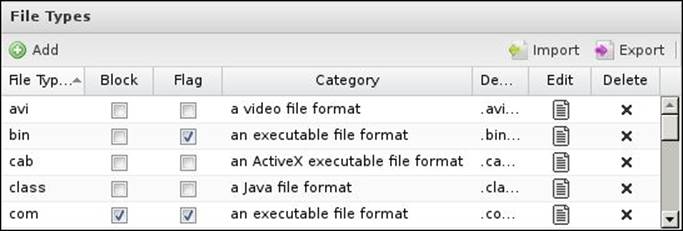
To back up the list, click on the Export button that allows you to export the settings as a JavaScript Object Notation (JSON) file. The Import button is used to restore the configurations. There are three different restore options:
· Replace current settings
· Prepend to current settings
· Append to current settings
Note
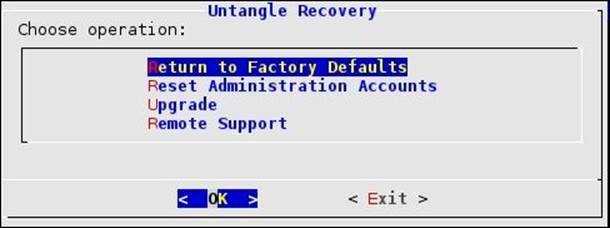
The recovery utility is used to reset the Untangle NGFW server to the factory defaults, rest the administrator credentials, perform/resume upgrades, and configure the remote support settings. The utility can be accessed from the (Recovery Utilities) button on the local administration console or by selecting the (recover mode) boot option. The following screenshot shows the recovery utility:
Monitoring your Untangle NGFW
Untangle provides you with many methods to monitor your server. The different methods include using Simple Network Management Protocol (SNMP), syslog, and summary reports.
Using SNMP
SNMP can be used to remotely query and monitor the current state of the Untangle NGFW server. SNMP has two modes: Get and Trap. Get is when the SNMP server queries the client (that is, the Untangle server) for its state, while Trap is when the client sends an alert to the SNMP server because of a high priority event (for example, high CPU usage for 5 minutes). The SNMP settings are located under Config | Administration | SNMP.
To start the SNMP service, check the Enable SNMP Monitoring checkbox. The following table shows the different options related to SNMP:
|
Description |
Options |
|
Community |
An SNMP community is the group to which devices and management stations running SNMP belong. The SNMP community defines where information is sent. The SNMP community acts as a password. The Untangle server will not respond to requests from a management system that does not belong to its community. |
|
System Contact |
The e-mail addresses of the system administrator that should receive SNMP messages. |
|
System Location |
This provides a description of the system's location. Simply use the default location if you don't want to specify a location. |
|
Enable Traps |
If checked, SNMP traps (events) will be sent to the configured host/port. |
|
Host |
This shows the hostname or IP address of the management system that is authorized to receive statistics from the Untangle server. |
|
Port |
The default port for SNMP traps is 162. |
Syslog and summary reports
Syslog is a method that allows network devices and *nix servers to send event messages to a logging server, usually known as a syslog server. Syslog is useful to keep the events in a centralized place. In addition, Untangle NGFW provides summary reports presented as charts and graphs, which simplify the process of reviewing the server usage. Syslog and reports are covered in Chapter 13, Untangle Administrative Services.
Reviewing system information and license details
This section will show you how to access the system information, get the license details, and review the license agreement. These details are available under Config | About.
Server information
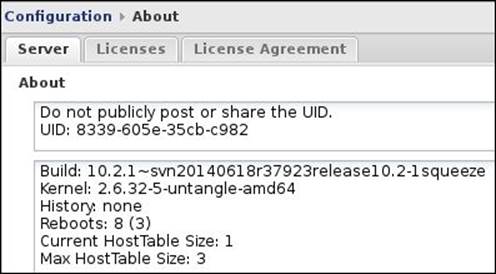
The Server tab shows the current information about the Untangle NGFW server. First, you will find your Untangle server's UID, which is automatically generated during the installation. The UID is a 16 alphanumeric characters code that uniquely identifies your server for licensing and tracking purposes. You should never share the UID of your server.
Note
Cloning your server after the installation will create two servers with identical UIDs, which will result in problems and licensing issues.
In the second field, you can find the Untangle NGFW server build and the kernel versions. The history and the number of reboots fields are used by Untangle support:
The Licenses tab
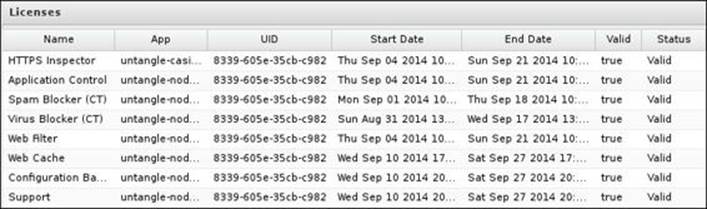
The Licenses tab shows the licensing state of your apps. The following information is listed for each app: the UID of the server that the app license is assigned to, the license validity period (start and end dates), and the current status of the license that is it valid or not:
License agreement
Under the License Agreement tab, you can find the View License button that opens the licensing and legal information of the Untangle NGFW server and its various applications and packages.
Summary
In this chapter, we learned how to configure the different settings related to the Untangle NGFW administration and its e-mail configurations. We also learned how to create local Untangle users and how to upgrade a server. In addition, we learned how to configure system-related settings. Finally, we reviewed the system information and license details.
In the next chapter, we will begin to deal with the Untangle NGFW apps. The next chapter will cover how we can utilize Untangle NGFW apps to protect our network against different threats such as malware, spam, phishing e-mails, adware, and tracking cookies.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.