COLLABORATIVE INTERNET OF THINGS (C-IOT). FOR FUTURE SMART CONNECTED LIFE AND BUSINESS (2015)
1
Introductions and Motivation
1.1 Introduction
This book will provide the reader with a quick overview of the Internet of Things (IoT) as the next technical revolution of the Internet and address its impact on digital life and business process empowered by emerging Cloud Services. The IOE – Internet of Everything is a DOT (Disruption of Things) and agent of change transforming from Internet of People to Internet of M2M (machine-to-machine) to IoT and IoE. Key benefits include improved business process efficiency, productivity, and quality of digital life. The market demand is moving from reactive on-demand remote monitoring and control (pull model) to more proactive services where the services will identify who you are and deliver what you want and when you want. Services will take on a new form empowered by insights driven from data collected in a given target applications.
This book is targeted to:
· Decision Makers, CEOs, CIOs, CTOs, and Senior Executives
· Communications and Networking System Architects
· Product and Marketing Managers
· Software and Hardware Engineers
· Consultants, Entrepreneurs, and Startups
· Service Providers of content, utility, security, entertainment, and other services
· Professors and Students
· Hobbyists.
1.2 The Book
1.2.1 Objectives
The objective of this book is to provide a simplified approach to comprehend the IoT innovative business model, value, and the impact it will have over our lives and businesses.
Hence, the objective will be analyzed from two aspects:
1. Improving quality of our lives
2. Improving business efficiencies.
Both (1) and (2) will contribute to having better insights that will lead to living in a smart environment and being part of a smart community/smart city.
This book will provide both a simplified and innovative business model for IoT and IoT domains and key applications. In addition, window of opportunities for IoT applications is rapidly growing and this book will address the need for a platform where diverse applications and solution can be developed. Finally, there is a need for system solution to collaborate for better insights and decision-making.
1.2.2 Benefits
It is the hope that this book will be a great reference and a tool for the reader and provide tangible benefits that include:
· Prepare the readers to embrace the revolution of Internet Technology with IOT that impact our lives, our business, and the environment we live in.
· Understand the evolution of IoT opportunities in terms of key applications that impact our lives, business, or the environment. Examples include Health & Fitness, Smart Building & Home, Video Surveillance, Track & Monitor, Smart Factor/Manufacturing, Smart Energy, and others.
· Comprehend the simplified approach to IoT Business Model consisted of Sensing, Gateway, and Services. Understand landscape of technologies and standards that enable creation of innovative time-to-market solutions and systems.
· Describe technologies and protocols that directly relate to IoT for IoT Architecture model (Physical, Virtual, and Cloud). Examples:
· Physical. Sensors, radio frequency identification (RFID), micro-electromechanical systems (MEMS), wireless sensor networks (WSN), global positioning system (GPS), ZigBee, near field communication (NFC), Wi-Fi, and 3G/4G
· Virtual. Software Defined anything (SDx), network functions virtualization (NFV), IPv4/IPv6, geographic information system (GIS), and body area network (BAN)/local area network (LAN)/wide area network (WAN) (body area network/local area network/wide area network)
· Cloud. Big Data/Analytics.
· Acquire deeper the understanding with series of requirements of key applications and how they are implemented.
· Leverage a smart IoT platform approach to facilitate the development of applications and enable communications among systems and solutions in a collaborative manner (C-IoT). Smart IoT as characterized by the 8A’s stand for Automated Remote Provisioning and Management, Augmented Reality, Awareness of Context and Location, Analyze, Take Action, Automate, Anticipate, Predict, Autonomous, and Attractive. The 7S’s stand for Simplicity, Security, Safety, Smart, Scalable, Sustainable, and Sleek Appeal.
· Acquire deeper understanding of Secured IoT products and systems. Provide examples and tips for do-it-yourself (DIY) IoT solution.
· Make the reader aware of future challenges facing IoT.
· Inspire the reader to think and innovate on unlimited IoT opportunities by sharing examples of future trends.
1.2.3 Organization
This chapter introduces a simple innovative model for Collaborative Internet of Things (C-IoT) and a new way of looking at the market via domains and applications. The book introduces simplified segmentation for C-IoT consisting of three domains: Individual, Industrial, and Infrastructure. Applications/Solutions/Systems can impact Individual, Industry, or Infrastructure or all. The C-IoT model in its simplest form consists of sensing, gateway, and services. Gaining insights from application/solution/system will result in driving better results in each domain. Spanning applications/solutions/systems to more than one domain create a higher value for a better strategic decision.
The core of this book will highlight a series of cases spanning from the requirements to the solution for present market and business opportunities and exploring future opportunities.
Chapter 2 describes the landscape of C-IoT and highlights relevant technologies and standards of the C-IoT model. In addition, it illustrates the application requirements by selecting some of the C-IoT applications spanning one or more of the three domains: Individual, Industry, and Infrastructure.
Chapter 3 describes the implementation of some C-IoT applications progressively from personal consumer to home to industrial (business) and smart city (infrastructure and communities) levels to deliver sustainable smart living and smart environment that help optimize business process efficiency and improve quality of life.
Chapter 4 describes the need for a unified smart C-IoT software platform that enables one to build and deploy smart C-IoT product, systems solutions, and services for different vertical markets in a quick time-to-market fashion. This will be described including the 4A’s and 4S’s that characterize smart C-IoT products. The 4A’s stand for Awareness of Context and Location, Analyze, and Take Action, Automate and Autonomous, and Anticipate. The 4S’s stand for Simplicity, Security, Smart, and Scalable. The chapter ends with covering the Secured IoT.
Chapter 5 provides examples of do it yourself (DIY) kits aimed on bringing the concept, approach to hands-on experience that will inspire innovative thinking in exploring untapped opportunities that will improve the quality of humanity, and business efficiency in general.
Chapter 6 addresses the emerging new wave of new devices and technologies such as wearable/mobile and cloud technology (local, public, and inter-cloud), analytics, and social media as key building blocks of C-IoT distributed intelligence. In addition, the chapter examines the C-IoT impact on our digital lives and businesses and some of the future challenges such as privacy and security.
Chapter 7 presents the readers with final remarks and tips to inspire them to innovate and deliver differentiated solution that contributes toward improving quality of lives and improves business processes.
1.2.4 Book Cover
1.2.4.1 Title of the Book
The title is carefully constructed that is depicted by the image on the front cover of this book as well as the brief text in the back cover.
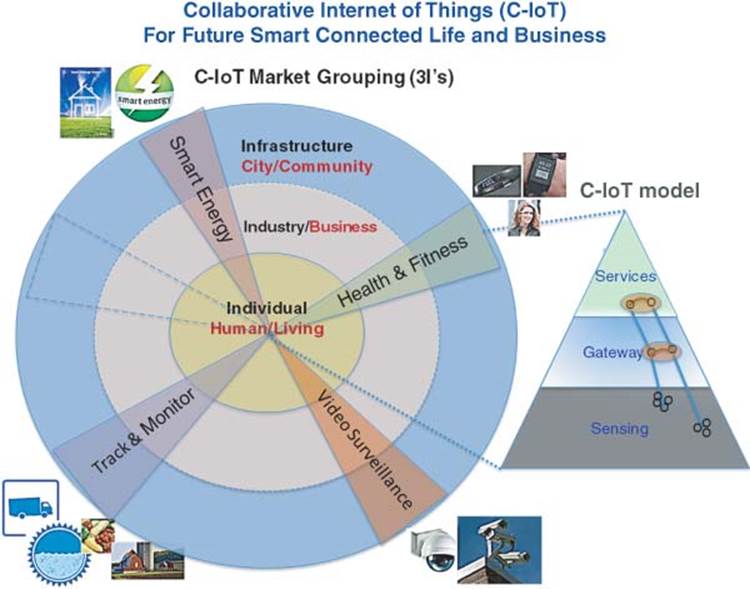
The title reflects the direction of the book focusing on the Future and addressing the need for a C-IoT that represents intelligently interacting and collaborating with current IoT solutions and systems to gain improvement and greater benefits that will have a positive impact on the quality of our lives and our business in terms of process efficiency.
The title can be depicted by two diagrams, which consists of:
· C-IoT domains and applications represented by the three circles (Individual, Industry, and Infrastructure) and examples of apps represented by triangles that cross the circles (examples of apps: Health & Fitness, Video Surveillance, Track & Monitor, and Smart Energy).
· IoT Model represented by the triangle with three functions (Sensing, Gateway, and Services).
The C-IoT in the title reflects the impact C-IoT has in breaking silos exist today in vertical markets by enabling communications and collaborations of solutions and systems within each market and across IoT domains: Individual (Human), Industry (Business), and Infrastructure (Government/smart city).
C-IoT impacts Individual, Industry, and Infrastructure and contributes in improving quality of life and/or improves business operational efficiencies.
· On the Individual C-IoT, a consumer is interested in buying a Nest thermostat because it saves energy without the hassle of constantly tweaking the thermostat by hand. A consumer is interested in fitness trackers such as Fitbit or Jawbone UP because visualizing the progress reinforces the behaviors that will make him or her fitter and view and act on video surveillance that is triggered by detecting a presence of a potential intruder.
· On the Industrial C-IoT, Internet solution providers (spearheaded by GE), focus on making industrial processes more efficient. For example, Industrial sensors for machines can be used to reduce the downtime, saving money. Business owner (referred here as CIO) can view information on the fly from anywhere using, for example, mobile device and conduct other queries and scenarios and then make a decision.
· On the Infrastructure IoT side, we see many initiatives on selling technology to city administrations that improves the operations of lighting, parking, water supply, garbage collection, and improve city data networks.
1.2.4.2 Walkthrough Example
C-IoT solution spans sensing, gateway, and services represented by the vertical line within the triangle (also referred to as a point solution). C-IoT is intelligently connecting two point solutions within the triangle. For example, connecting iWatch to not only manage health and fitness but also control remotely video surveillance at home or open/close garage door, or adjust temperature as person enter the home or car, and so on.
Imagine the following scenario: an elderly lady wearing an iWatch and she fell on the ground and broke her legs at home. She also had food being cooked on the stove but cannot reach it and shut it off. With C-IoT solution, automatic scan of video images and other sensors around her will generate multiple alerts that will be transmitted in real time to EMS (emergency medical services). EMS personnel will diagnose remotely the situation and based on assessment, other alert may be sent to fire department and police to protect the house from potential risk being caught on fire. With a severe condition of broken legs, EMS will send alert to a hospital closer to the home of the elderly. EMS, Police, and Fire vehicle will be dispatched finding the shortest path and interacting with smart street poles to reach the home of the elderly. With smart poles, First Responders will have access to change the traffic light, send messages to all vehicles on along the path to clear the road. And real time alert will be sent to the utility company to turn off the stove remotely.
We can see clearly from this example of a collaborative – IoT solution impacting three domains: Individual (elderly lady), Industry (Utility, surveillance alarms, hospital/medical services, and insurance), and Infrastructure (EMS, Police, and Fire). The end result is efficiency, faster services, which leads to an improved quality of livings, safety, and operational efficiency.
1.2.5 Impact of C-IoT
IoT is bringing a new level of coverage and information that were not possible before due to technological advancement and scalability DOT. IoT via variety of sensors will increase smartness and intelligence of information gathering that will impact a better decision and results.
We have embarked into the next era of technology evolution, after PC-era and post mobile-era. With the rapid evolution of mobile applications and generation of big data, there will be need for series of analysis to make sense of the data and present the user with factual and filtered information so that sound informed decision can be taken and communicated. This level of communicating quality results will open the window to a new level of smart communication that will lead to a collaborative networking supported by social media and break down barriers for global and effective and intelligent global communications.
IoT will enable convergence of several technologies and consequently will impact the overall architecture of the network so that we envision a common architecture platform for most of the vertical markets and adaptation and customization through applications and special devices to address the specific needs of a given market. This in turn will accelerate time-to-market of applications and services in many markets.
The impact is huge in terms of explosive growth of Internet traffic, increase of broadband speed, and the emergence of multimedia class of applications. This has led to the migration from client/server to cloud computing and services.
The future calls for a better insights not only through Compute engine for data processing, but also with analyzing workflows, advanced analytics, stream processing, and business intelligence that is GPS-based and visual analytics that is GIS-based. This helps in improving judgment and speed process of taking a better decision.
Security has become and remains to be a key challenge to secure access of content at anytime and anywhere.
We can see users equipped with remote access and control capabilities to manage the home environment (energy, safety, and security). This will contribute toward improve efficiency, reduce stress, and improve quality of life. In the area of health and wellness, consumer will have access to gadgets and devices that help track indicators about their physical condition and well-being so that a proper proactive course of action can be taken.
For example, when buy a car you have the option to activate smart services after purchase. Not sure if you want the model with the turbo? No problem, we offer a telematics service where additional muscle can be delivered to your vehicle when you need it and turned off when you do not. That is IoT meets cloud and mobile – the convergence of disruptive technologies doing what they do best: rewriting the traditional business rulebook.
Of course, it is easy to scoff at these examples, but are they really so crazy? Today there are real-world cases where savvy businesses are disrupting markets with practical applications in our connected world.
Take, for example, a UK company called Insurethebox. This business has developed a telematics device that can be fitted to a car to monitor driving behaviors. Insurethebox has wrapped the hardware with software and services that allow customers to purchase insurance according to the number of miles they expect to drive in a year and then monitor usage from a personal portal. Furthermore, if they drive safely they will be rewarded with bonus miles that help keep their premiums down. That is the IoT meets cloud meets gamification – again, highly disruptive.
What is exciting about examples such as Insurethebox is not so much the technology, but the opportunities created. The telematics hardware is only a means to an end, the real deal is the additional monitoring apps, APIs (application programming interfaces), and services, which when taken all together allow the company to deliver new and compelling value.
Collectively, the Smart Connected Digital Life (Smart Home, Office, Factories, Hospitalities, Transports, etc.) will contribute to a better quality of life, greater business efficiency, and new venues to generate revenue. This book will touch upon many of the services that can now be integrated in the Smart Connected Digital Life.
C-IoT with collection and processing of data can provide insights, which will lead to an improvement:
· For an individual living in a smart home, when he opens the door, an action will automatically disarm the alarm.
· For a transport industry, when driving a smart car, a collision is detected by a Bluetooth dongle reading vehicle data and automatically calls the emergency services.
· For a smart city, with smart parking meters, the sensors embedded in road surface can help find an empty spot and enable you to park quickly without frustration.
The combination of cyber-physical and social data can help us to understand events and changes in our surrounding environments better, monitor and control buildings, homes and city infrastructures, provide better healthcare and elderly care services among many other applications. To make efficient use of the physical-cyber-social data, integration and processing of data from various heterogeneous sources is necessary. Providing interoperable information representation and extracting actionable knowledge from deluge of human and machine sensory data are the key issues. We refer to the new computing capabilities needed to exploit all these types of data to enable advanced applications as physical-cyber-social computing.
1.2.6 Summary
The Internet has broken many physical barriers connecting people, companies, and communities of interests worldwide representing different markets.
Sensors generate data, data produces knowledge, knowledge drives action. Thus, making sense of the data that those devices generate creates the real value for users.
The introduction of smartphones has generated a wide acceptance and adoption by business, consumer and general population. Today, we see high growth in mobile traffic than landline. Increase longer life battery, introduction of tablets and growth of ecosystem for mobile applications will cause a gradual decline in the growth of PCs and rapid end of life of desktop equipment.
Miniaturization, progress with energy issues and cost reductions have resulted in rapid growth in deployment of networked devices and sensing, tightly connecting the physical world with the cyber-world as well as interconnected humans bringing along them virtual social interactions.
The scalability of Internet, advancement of wireless technology, accelerated growth of mobility, introduction of wearable devices, lower cost of sensing technology, lower cost of embedded computing, advancement of storage technology and cloud computing and services and the emergence of the area of analytics provide a perfect storm to the IoT across many markets. With C-IoT, more data are captured, tracked, analyzed in relation to relevant data from other applications that will be reviewed for taking a better and informed decision.
The number of devices connected to the Internet already exceeds the number of people on earth and is estimated ranges from 50 to 200 billion devices by 2020. The resulting system called IoT incorporates a number of technologies including WSN, pervasive computing, ambient intelligence, distributed systems, and context-aware computing. With growing adoption of smartphones and social media, citizens or human-in-the-loop sensing and resulting user-generated data and data generated by user-carried devices have also become key sources of data and information about the physical world and corresponding events. Data from all these sources will result in tremendous volume, large variety, and rapid changes (velocity).
The big data is not as in the past consists of numerical data and taking into account the internal of an organization but rather consists of a host of data from diverse sources and of all types – audio, video clips, social media and other forms spanning the internal, the environment and social culture and of course the supply chain.
Such information was not feasible before but thanks to technological advancement and IoT to sense more data that were passive objects. As a matter of fact, Big Data is becoming a potential gold mine and a great business to the point that contrasting to Big Data, a new category called small massive data is emerging providing a focused prospective to make decision and drive innovation and strive for a better quality of life. Thus, the CIO may be traditionally applied to Enterprise, but in the context of this book, with the introduction of IoT model, IoT platform to drive IoT innovative services, CIO is applied to all vertical markets small or large and furthermore, applied to IoT Services addressing the total supply chain for vertical market and crossing multiple vertical market in offering new class of IoT services that were not envisaged before.
With C-IoT, billions of devices and sensors, all communicating through the cloud and all feeding into a massive analytics solution to provide a complete picture of the individual or business, processes, and customers will be coming together.
Extracting value from your data requires integration of disparate tools. The challenge is to dramatically simplify big data processing and free users to focus on turning data into value with a hosted platform and an initial set of applications built around common workflows.
The C-IoT has the capability to collect and analyze feedback, report it to decision makers, enable them to take the appropriate action, and provide an analysis as to how well the actions taken worked.
The C-IoT can enable marketers to measure actual behavior in real-time rather than process-biased answers to unwanted or inadequate survey questions.
The C-IoT calls for delivering a Dashboard that allows CIO and user to visualize and get insights of big data in a graphical GIS-based form and relevantly located based on GPS. Interaction can be via mobile portable or wearable device phasing away from other traditional type of two-way communications.
This book describes IoT business consisting of three layers: sensing, gateways, and services. The definition is expanding from Internet of people, to IoT and now IoE. We are tapping into millions of objects that matter and bring them to Internet for tracking and extracting value that can bring a new dimension of information that was not possible before.
This book will assist the readers by providing supplementary material including case studies and code examples empowering a new level of collaborative innovation and creativity.
1.3 C-IoT Terms of References
This book introduces simplified and innovative concepts. This section provides definition and description of these concepts.
1.3.1 Introduction
1.3.1.1 IoT Landscape
The concept of IoT is not new. There are many early-IoT examples in the field of industrial control, process control, and telecommunication.
Fawzi Behmann, the coauthor of this book, was exposed to the concept of IoT in the late 1980s and early 1990s when he led a team of architects and developers into the design and implementation of a first computerized telecom alert system for a global carrier telecom facilities conforming to ITU TMN– Telecommunications Management Network Standards M.3000. The system that consists of network of computers provides three functions: Real time monitoring of equipment and systems, control based on fault analysis, provisioning, and performance, and supervisory of assessing impact on traffic and quality of services. Facilities alarms were monitored in real time via data acquisition systems with hundreds of digital and analog points identifying change of status or crossing defined limits. Such a change could have minor or major impact on traffic and services, which could have resulted in activating control options such as traffic rerouting. The system had built-in security including user access, functional access, and device and location information. Figure 1.1 illustrates an example of early-IoT deployment in the late 1980s and early 1990s with the emerging IoT in the 2010s.
Figure contrasts the early adoption of IoT with today’s emerging IoT. For example, applications implemented in the 1980s used private lines and private networks where as today, Virtual Private Networks and wireless technologies are used. Back then, computer networks were more expensive with a limited performance, memory and storage. User interface was typically a CRT (cathode ray tube). Today, however, systems are more powerful, less expensive, and come with higher capacity memory, higher storage capacity and wireless connectivity supporting diverse user interface devices and digital monitors [1].
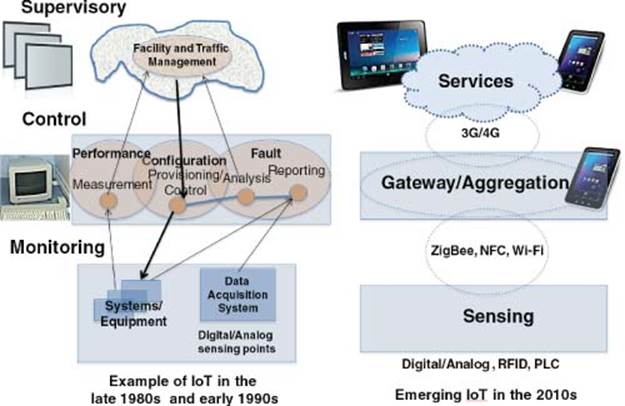
Figure 1.1 Contrast between early and current IoT Functional Model
With the advent of Internet and advancement of enabling technologies for sensing, microcontroller, connectivity, and storage of big data, Solutions and services are taking on new meaning depending on where we are in the current IoT deployment and extracting value from the data collected. Although, sensing devices and control may provide an immediate and local value that can benefit individuals, small businesses and contribute to operational efficiency of enterprise, but sharing the data at a larger scale can benefit multiple vertical markets and can then generate a much bigger value to many large entities. Take, for example, wearable devices for fitness and health monitoring, they are of immediate benefits to individuals, but if a person pay visit to a physician that may end up in medication and being in the hospital, this would involve physicians, hospitals, insurance coverage, prescription, and a host of other agencies. If they are interconnected and patient data is respected for privacy, a consolidation and consistency of data will now emerge. The person has ultimate access to all the data being collected, trends can be generated (connecting the dots), a faster service can be offered since authorized agencies have access and share the data. Insurance agency can respond if the prescribed medication is covered, and less headache on the part of the patient to deal with each of these agencies as before and a better resolution.
We start witnessing an emergence of a new level of services, some being offered by a utility company, some by a transport car services, others by a carrier (MVNO).
It becomes a question that has control or influence on critical technology, infrastructure, and ability to collaborate with other entities to develop a new class of services.
1.3.1.2 IoT and Internet of Everything (IoE)
We are currently experiencing the IoT, where millions of new devices are regularly being connected to the Internet. As these “things” add capabilities such as context awareness, increased processing power, and energy independence, and as more people and new types of information are connected, we will quickly enter the IoE, where things that were silent will have a voice.
When smart things everywhere are connected together, we will be able to do more and be more. This is the IoE, a paradigm shift that marks a new era of opportunity for everyone, from consumers and businesses to cities and governments.
IoE is changing our world, but its effect on daily life will be most profound. We will move through our days and nights surrounded by connectivity that intelligently responds to what we need and want – what we call the Digital Sixth Sense. Dynamic and intuitive, this experience will feel like a natural extension of our own abilities. We will be able to discover, accomplish, and enjoy more.
Powerful smart phones are a natural tool to deliver IoE experiences. And wireless networks, a fundamental layer of IoE connectivity, are integrated around the globe. Those elements are ready for everyone to leverage, and Qualcomm is making that easier than ever. Qualcomm visionary solutions are to deliver the connectivity and communication needed to support the IoE opportunity industry-wide.
Cisco defines IoE as bringing together people, process, data, and things to make networked connections more relevant and valuable than ever before – turning information into actions that create new capabilities, richer experiences, and unprecedented economic opportunity for businesses, individuals, and countries.
For simplicity, this book assumes that IoT will include both things and people.
1.3.2 Need for IoT Framework
Today, the market is flooded with information about IoT: Articles, papers, books, forums, and even ecosystem organization facilitating joint collaboration. This book will take a different approach by focusing on IoT connectivity that matters. In this context, the book will serve as good reference and guide to executives and leadership in business, colleges, and homes focusing on discernment on what matters in IoT. This book also intends to empower the reader with potential possibilities for a new innovative product, solutions and services and thus advancing IoT to a new level.
In order to achieve this, the book will focus on IoT for connectivity that matter and that result in better benefits such as improvement of efficiency of business and improving the quality of our lives. For example, IoT connectivity of things such as pens, erasers, staplers, hammers, and nails will not bring such value as that of IoT connectivity to control things such as doors, lights, and dishwashers. In this context, programming and managing a cluster of sensors for air condition for the home or enterprise could result in a lower operational cost. Smart parting where an individual is equipped with a smart parking map identify where is the available parking slot and can reach the available parking spot by visually looking at the green light on top of a parking spot seen from a distance. This can easily save time and avoid frustration.
This book will provide a definition and detailed description of the C-IoT model highlighting enabling technologies and standards; providing cases and examples in for several business applications highlighting requirements and implementation spanning from Infrastructure to Industry to Individual. C-IoT platform and other consideration will be highlighted. This book will also examine the C-IoT impact on our digital lives and businesses and some of the future challenges such as privacy and security.
In subsequent chapters, this book will cover:
· Technology and standards driving IoT
· Requirements for IoT in key areas
· Solutions examples in the areas of five key vertical market areas
· Impact on business and our lives.
1.3.3 C-IoT Domains and Business Applications Model
The core concept of the book is defined by two terms: C-IoT domains/business applications and C-IoT business model.
This book is taking the reader to a new level of IoT called C-IoT and thus providing differentiation and highlighting greater opportunities for creativity and innovation in the areas of personal quality of lives and advancement in business processes. This is accomplished by C-IoT domains/business applications providing a simple view of the market by identifying three principle domains represented by the three-part circles (Individual, Industry, and Infrastructure) and a sample of business applications represented by triangles that traverse these domains. The second concept is a simple business model C-IoT represented by the three-part triangle (Sensing, Gateway, and Services).
1.3.3.1 C-IoT Domains/Business Applications
The C-IoT defines three main domains
· Individual for smart living.
· Industry for business efficiency.
· Infrastructure for smart communities and cities.
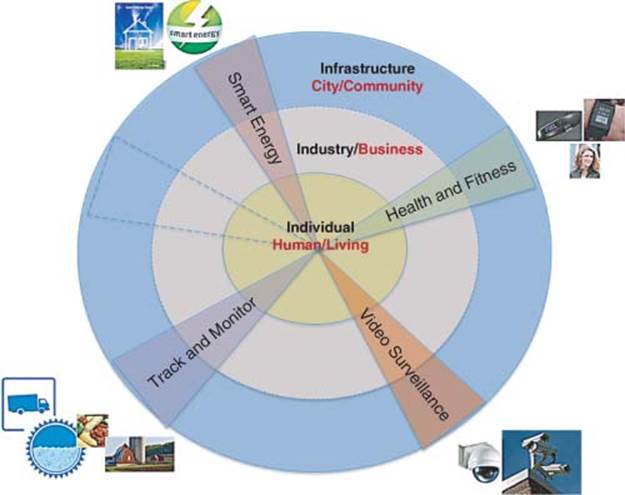
Figure 1.2 C-IoT domains and business applications
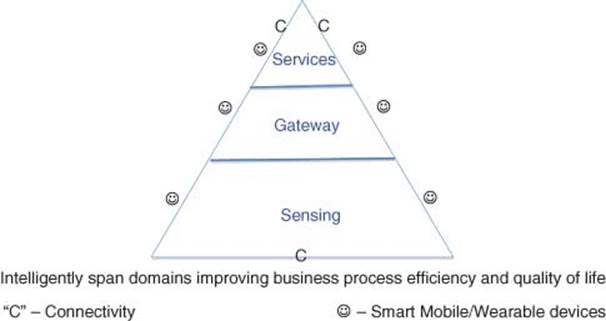
Figure 1.3 C-IoT model
Any business application may span one or more markets.
For example, in the same figure, the following business applications span the three domains:
· Health & Fitness
· Video Surveillance
· Track & Monitor
· Smart Energy.
Three circles as in Figure 1.2 represent domains and sample applications are represented by the triangles spanning the three domains.
Here is a general list of business applications:
1. Individual for smart living
a. Consumer Electronics and wearable devices (Quality of Living)
i. Fitness/health monitoring and tracking (Smart Living)
ii. Elderly, kids, pets, and so on (Safe Living)
iii. Time, leisure (Quality Living)
b. Home
i. Security/Surveillance – Alarms (smoke, motion, access, and video)
ii. Energy – meter, thermostat, appliances, and lighting
iii. Sprinkler system
iv. Entertainment
v. In-home healthcare devices – Embedded video
c. Smart connected car, transport
i. Engine diagnostics
ii. Traffic info/mapping
iii. GPS/GIS Location-based services
iv. Autonomous driving
2. Industry for business efficiency
a. Several markets are associated with Industry.
i. Factories. Automation, machine vision, robot, and machine learning
ii. Smart Manufacturing
iii. Agriculture (Produce, Livestock, etc.)
iv. Health. Clinical labs, health monitor and diagnostics, treatment, and health insurance
v. Construction: Smart building, heating, ventilation, and air-conditioning (HVAC), lighting control, and energy
vi. Smart Retails (Shops and Hospitality), Smart ePoS, vending machine, signage, ATM/Kiosks/Vending machines, and so on
vii. Smart Energy Grid, water, waste, pipeline, refinery, and air
viii. Smart Environment – Surveillance, Air and water quality
ix. Communications
3. Infrastructure for smart communities and cities
a. Public Transportation. Automotive, smart vehicles (V2X), trains, planes, buses, trucking, and cargo, Aerospace/Mil
b. Public Highways. Tolls, lighting, smart parking, meters, and so on
c. Public Safety. Police, fire, ambulance, surveillance, and drones
d. Disaster Management
e. Smart education, Security, and Defense
f. Smart City. Sustainable living and smart environment.
1.3.3.2 C-IoT Business Model
C-IoT Business Model is represented by the triangle in Figure 1.3 and consists of three layers: sensing, gateway, and services.
The model shows connectivity at each of the functional areas represented by the letter (C). User interface can also be at any of the three layers using mobile/wearable device and is represented by the smiling face symbol.
Today, many of the IoT business applications and solutions are point solutions.
By contrast, pre-IoT model represents a disjointed piece of the triangle and connectivity and interaction would require efforts and tools.
Example 1 If, for example, an IoT device such as iWatch, which has many sensors, can process data for local view and connect to the cloud for trends and analysis. This would be represented as a point solution with many sensors to provide, for example, reading on health and fitness reading. Another example would be to operate to open/close a garage door. This is represented by a second IoT point solution as shown in Figure 1.4.
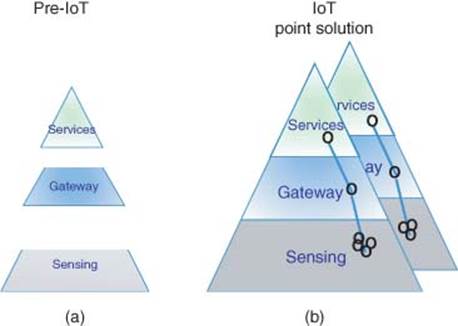
Figure 1.4 (a) Pre-IoT and (b) current IoT point solutions model
Figure 1.4 illustrates both pre-IoT and current IoT Point solution.
Example 2 If, for example, iWatch is to not only manage health and fitness but also control remotely video surveillance at home or open/close garage door (two other point solutions) then iWatch needs to intelligently interact, connect, and collaborate with these two other point solutions. This is represented by the horizontal connection between point solutions and is referred to as C-IoT. This is depicted by connecting two point solutions in the triangle both at the gateway level and at the service level. Of course, the example can be more complex than that.
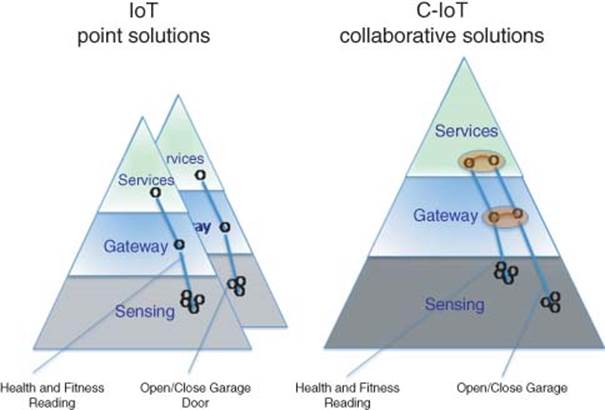
Figure 1.5 (a) IoT point solution and (b) C-IoT collaborative solution model
This C-IoT integrates intelligently and connecting two point solutions within the triangle as shown in Figure 1.5.
In the near future, there will be transformation toward C-IoT between two or more point solutions/systems providing greater insights that would result into better decision.
But such solution/services can impact any, some or the entire three domains: Individual, Industry, and Infrastructure. For simplicity, we highlighted three market cases that address our needs and wants: Health & Fitness, Video Surveillance, Track & Monitor and Smart Energy. More examples are provided in the book.
Example 3 Video Surveillance across Three Domains (Individual, Industry, Infrastructure) The following example shows a more progressive example of video surveillance business application crossing three domains: Individual (Apartment), Industry (Commercial), and Infrastructure (City Street).
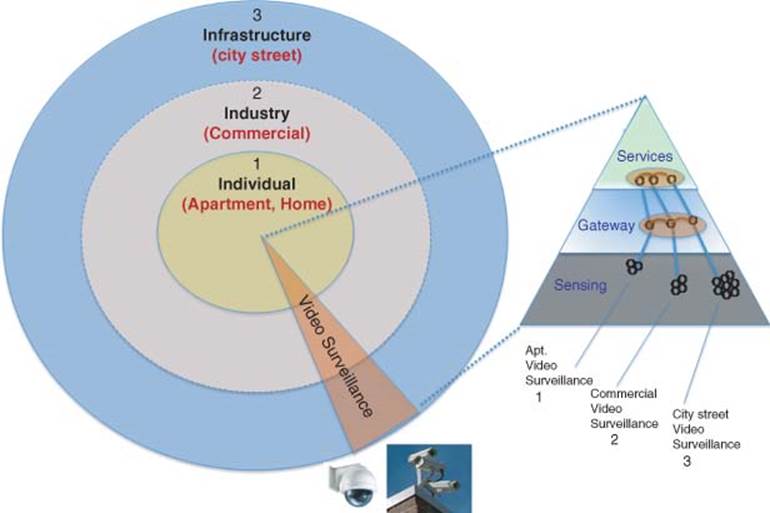
Figure 1.6 C-IoT domains and model for video surveillance application
A major fire has occurred in a multi-tenant building, which contains both apartments and commercial stores and restaurants. A fire alarm was sent from an apartment that has fire and was supported by video surveillance images detected by central alarm services. Shortly afterward, a fire alarm was issued from a restaurant caught on fire in the building and it was supported by a video surveillance images sent to the central alarm services. The central alarm services have sent an alert to the Fire department. However, because the building is in central downtown, the street video surveillance camera has also detected the fire prior from receiving the alert message from the central alarm monitoring services. Thus, in real-time all the first responder, commercial building and apartment issued alarm alert for action. Immediately, the emergency dispatching center was able to retrieve more information about the building and exact location of fire displayed on a GIS template and right fire truck and resources were dispatched immediately to the site to put off the fire in both locations.
Thus, with a C-IoT, and the support of the video surveillance at multiple locations representing individual (Apartment), Industry (Commercial Building), and Infrastructure (City Street), detailed information was correlated in real time, and proper action was taken to minimize damage and save lives.
The illustration of this C-IoT example is shown in Figure 1.6.
Example 4 Figure 1.6 shows a more general example of C-IoT for multiple business applications:
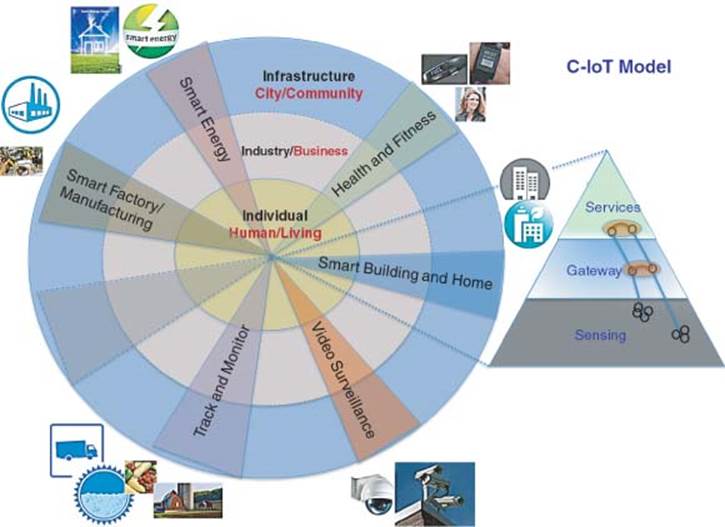
Figure 1.7 C-IoT general domains and sample applications
· Health & Fitness
· Smart Building & Home
· Video Surveillance
· Track & Monitor
· Smart Factory/Manufacturing
· Smart Energy
· Others.
These applications all cross the three domains: Infrastructure, Industry, and Individual. Figure 1.7 illustrates C-IoT domains and sample applications.
1.3.3.3 C-IoT and Internet of Service (IoS)
The C-IoT Business Model can also represent an integrated point solution represented by the connected lines spanning sensing, gateway, and services within the triangle. Multiple sensors feeding into Microcontroller in the sensing layer, which can be viewed and/or passed to the cloud layer via gateway, represent sensing. Data, trends, analysis can be carried out at the cloud layer and be viewed by a smart mobile device.
Motivation for C-IoT is the delivery of IoS (Internet of Service). Embedded things are connected to the cloud via smart IoT gateway software platform for delivery of IoS business. This will be covered in more details in Chapter 3. Thus, the IoS is a vision of the Internet of the Future (C-IoT) where everything that is needed to use software applications is available as a service on the Internet, such as the software itself, the tools to develop the software, the platform (servers, storage, and communication) to run the software.
1.3.3.4 Cyber-Collaborative IoT (C2-IoT)
While IT experts have long predicted security risks associated with the rapidly proliferating IoT, this is the first time the industry has reported actual proof of such a cyber attack involving common appliances – but it likely will not be the last example of an IoT attack. IoT includes every device that is connected to the Internet – from home automation products including smart thermostats, security cameras, refrigerators, microwaves, home entertainment devices such as TVs, gaming consoles to smart retail shelves that know when they need replenishing and industrial machinery – and the number of IoT devices is growing enormously.
The “IoT” holds great promise for enabling control of all of the gadgets that we use on a daily basis. It also holds great promise for cybercriminals who can use our homes’ routers, televisions, refrigerators, and other Internet-connected devices to launch large and distributed attacks. Internet-enabled devices represent an enormous threat because they are easy to penetrate, consumers have little incentive to make them more secure, the rapidly growing number of devices can send malicious content almost undetected, few vendors are taking steps to protect against this threat, and the existing security model simply will not work to solve the problem.
IoT devices are typically not protected by the anti-spam and anti-virus infrastructures available to organizations and individual consumers, nor are they routinely monitored by dedicated IT teams or alerting software to receive patches to address new security issues as they arise. The result is that Enterprises cannot expect IoT-based attacks to be resolved at the source; instead, preparations must be made for the inevitable increase in highly distributed attacks, phish in employee inboxes, and clicks on malicious links.
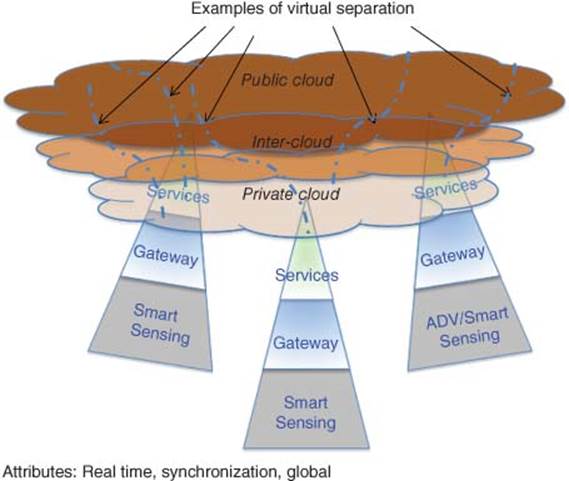
Figure 1.8 Cyber-collaborative IoT model
The view of the authors is that a long-term strategy would be required for the C-IoT. As the number of devices grows, so does the wireless chatter and noise. The chatter is building over all wireless communication channels: Wi-Fi, cellular, Bluetooth, NFCs, and others. There is no end in sight to the expected growth of wireless connected devices. Networks will need to be fortified and new methods of managing wireless traffic are being considered. Enriching wireless network traffic with rich context and history allows for dynamic network traffic prioritization based on the profiles of your customers. Always make sure that your most important customers always get the best Quality of Service, and know immediately when quality degrades.
The strategy to address Cyber-C-IoT is shown in Figure 1.8. Security measure would be required both in the gateway and cloud areas.
1.3.4 Roadmap of IoT
1.3.4.1 Evolution Roadmap of C-IoT
Figure 1.9 represents the vision of C-IoT roadmap transitioning from IoT point solution in 2010s to C-IoT in the 2020s to Cyber-C-IoT in the 2030s and beyond.
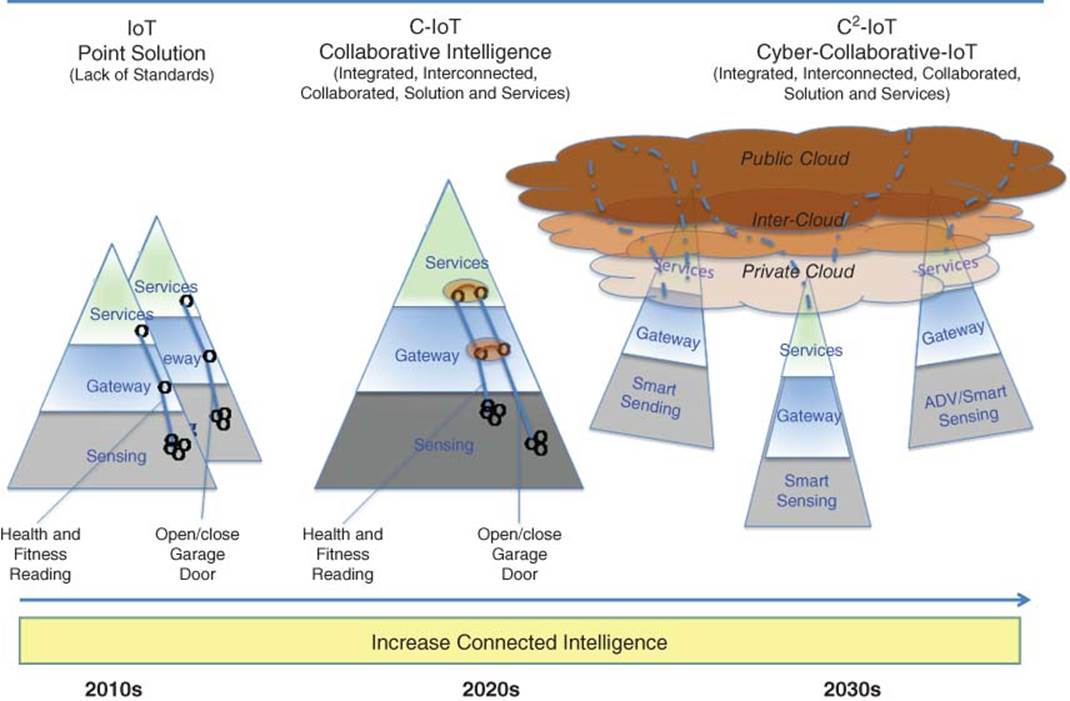
Figure 1.9 IoT evolution roadmap
1.3.5 C-IoT Platform/Developer Community
According to Wired magazine, 17% of the world’s software developers are already working on IoT projects, with 23% planning to start one in the next 6 months. The competition is sure to heat up.
In the IoT industry, there is a growing notion that “developers” will be its most critical group of stakeholders in the future. This belief stems from the fact that developers of digital applications have been the biggest driving force behind the growth of mobile industry in the past years. The grassroots-style, distinctly speculative innovation has fundamentally been what has brought the needed content into mobile devices, and the hope is that a similar growth-from-the-long-tail phenomenon would take place in the emergent IoT space as well.
ABI Research estimates that the number of developers involved in IoT activities will reach 1.7 million globally by the end of 2014. The size of the ecosystem is forecasted to surpass 3 million developers in 2019. For comparison, this would by then account for approximately 10% of all software developers [2].
The core enablers for productization comprise purpose-built cloud platforms and development kits, which are making the IoT accessible to developers who may differ greatly in terms of their resources and commitment.
Furthermore, there are also several other, more indirect enablers that will be critical for the IoT’s evolution. These include sensors and sensor engines, affordable 3D printers, as well as crowd funding platforms. Collectively, all these building blocks could eventually translate into a perfect storm of hardware innovation.
If we assume that data collected off connected things in a given vertical market and across many markets generate a huge set of data. Then, it will take creative processing and applications to extract value of the data. This was expressed in the previous section as IoT point solution moving toward C-IoT solutions/systems. This calls for a vast number of applications. Thus, 3–5 million IoT application developers are yet to be created, then this will create a huge market, service and revenue opportunities. These opportunities can touch individual in terms of quality, healthy, and safe living, to the shelter in terms of smart home and smart car to smart and comfortable working conditions and shopping cultural, travel, and leisure. As an individual is the core of a family which is a core of a community, city, state, and country, then advancement in quality living will lead to a smart society, culture, and city and overall to a smarter planet.
According to 2014 study on mobile health app developer conducted by Research2guidance, it is estimated that 100 000+ mobile healthcare apps will be published on the two leading platforms, iOS and Android, has more than doubled in only 2.5 years. Five hundred million smart phone users worldwide will be using a health care application by 2015, and by 2018, 50% of the more than 3.4 billion smart phone and tablet users will have downloaded mobile health applications. According to survey, developers’ device preference in the next 5 years is: 75% Smartphones, 45% Tablets, and 24% Smart watches. The highest business potential in the next 5 years is: 77% – Wearable sensors and 61% – Built-in sensors [3, 4].
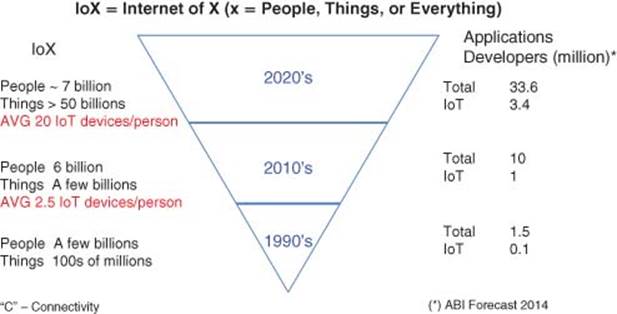
Figure 1.10 IoT contrasting IoE with IoT developers and apps
Figure 1.10 shows a composite picture of IoE (People and Things) contrasting with IoT developers at different time periods 1990s, 2010s, and 2020s.
1.3.6 C-IoT Opportunities for Applications, Solutions, and Systems
The Internet of People runs to billions of devices already. The IoT will involve ubiquitous smart objects that sense and communicate directly over the Internet creating more and better data. C-IoT is ubiquitous IoT or Collaborative IoE engaging things and people. C-IoT solutions/systems consists of smart sensing network with IP address assigned for smart objects with estimated tens of billions of smart objects, microcontrollers, potentially billions a year with sensor interfaces and wireless interfaces and connectivity to cloud for data analysis, storage, trends, and services.
According to Gartner, by 2020, component costs will have come down to the point that connectivity will become a standard feature, even for processors costing less than $1. This opens up the possibility of connecting just about anything, from the very simple to the very complex, to offer remote control, monitoring, and sensing, The fact is, that today, many categories of connected things in 2020 do not yet exist [5].
Business opportunities, which drive through the scale and usage of IoT technology span across Infrastructure, Industry, and Individual domains and include smart factories/manufacturing, smart grid, smart buildings, smart health, and fitness.
Emerging areas will witness rapid growth of connected things. This will lead to improved safety, security, and loss prevention in the insurance industry. IoT will also facilitate new business models, such as usage-based insurance calculated based on real-time driving data. The banking and securities industry will continue to innovate around mobile and micropayment technology using convenient point-of-sale (POS) terminals and will invest in improved physical security systems. IoT will also support a large range of health and fitness devices and services, combined with medical advances, leading to significant benefit to the healthcare sector.
Emerging connected sensor technology will lead to value creation in utilities, transportation, and agriculture. Most industries will also benefit from the generic technologies, in that their facilities will operate more efficiently through the use of smart building technology.
Following is a list of business opportunities spanning the three domains: Individual, Industry, and Infrastructure.
Individual – Smart quality of living
· Consumer electronics and wearable devices (Quality of Living)
· Home
· Smart connected car, transport.
Industry – Smart Business Efficiency
· Manufacturing
· Agriculture
· Health
· Building
· Retails.
Infrastructure – Smart communities/cities for sustainable environment and living
· Public transportation
· Public highways
· Public safety
· Disaster management
· Smart education
· Smart communities/cities.
To inspire innovators, entrepreneurs and business, following are set of examples.
1.3.6.1 Generic Examples of the IoT Benefits of Emerging Applications and Services
Future emerging applications and services will contribute toward time saving, operation costs, and streamline service provisioning.
· Connecting IoE to a network can quickly see the potential savings in time, cost, and labor.
· Transmitting information wirelessly at its source – from sensors, things such as vehicle, instrument, house, or business – and receiving valuable feedback not only automates manual processes, it helps to streamline service provisioning and billing.
· Multiply the number of connected devices, people and things you have, and you can see the powerful possibilities.
1.3.6.2 Examples of Business Applications and Solutions
Business Applications and Solutions are promised of improving communications among vertical markets. Benefits from device–device communications and remote monitoring/diagnostics will contribute toward cost saving and safety benefits.
· Applications and services connecting millions of diverse devices to a network, enabling two-way communication offered to key vertical markets such as heart monitors, vending machines, trucks, and turbine.
· Oil and Gas Industry – Delivering Cost Savings and Safety Benefits. Managing marginal well operations is labor intensive. Pumpers drive to each tank daily to check water and oil levels and equipment, including drilling motors. If levels are too high, pumps must be manually shut down to avoid spills and incurring fines and clean-up costs. Motor problems require a well to be shut down until repairs are made; both situations create a production loss. Pumpers can monitor tanks, motors, and other equipment anywhere from a PC or smart phone, 24/7.
· Electronic Vehicle Charging Stations. PEP stations needed a remote monitoring and reporting solution for its electric vehicle charging stations, which served building tenants. Cloud-based application provides a reliable wireless link to support real-time fault diagnostics. Benefits include: reduce call outs to fix faults, and receive reports on the utilization of all its equipment, which facilitated planning for new stations.
· People Awareness and Recruitment. Applications that provide a visibility for firms that are adopting device-to-device communication. Benefits include: improving prospects for direct sales, sales channel development, investment community awareness, and personnel recruitment.
1.3.6.3 Examples of Applications and Services for Supply Chain
Applications and Services for supply chain can provide critical information at different stages of supply chain providing cost saving and better services.
· Integrated Remote Health Monitoring Services. Traditional heart monitoring systems relied upon phone lines and even physical visits to deliver monitors and data; physicians waited for paper-based reports and technical analysis. An integrated remote monitoring system with a suitable wireless network provider deliver an effective solution that enables data to be automatically transmitted from heart monitoring devices to 24-h Monitoring Center, where credentialed technicians can interpret patient data, notify physicians of serious events, and upload reports to a web portal for physicians rapid access.
· Improve Efficiency and Improve Service Time. A system and application to remotely monitor medical systems. Benefits include minimize costly field repair visits and avoid downtime for vital patient treatment. Services enable timely problem identification and resolution. Benefits can be quantified in terms of recorded cost savings where recorded for both the medical systems and patients.
1.4 The Future
1.4.1 General Trends
We have witnessed a massive and ongoing revolution with computers and smartphones connected to the Internet. Smart mobile devices such as smartphones and tablet help individual to have access to information from one device. Through a set of apps, with such a device, an individual use it as a compass, navigate, take picture/videos, find gas stations, restaurants nearby, view emails, respond to telephone calls, play music, using it as a boarding pass, exchange contact information, pay a bill, and many other things all from one device.
At the end of this section in the summary section, we can see a potential use of future smart mobile/wearable device in the context of C-IoT.
While 2013 saw some remarkable advances in Micro-controller unit (MCU) and wireless technologies that further enable the IoT, 2014 has shown a forward move with the emergence of a more practical Internet of Useful Things. For some, this Internet of Useful Things promises a world where nearly every device continuously analyzes and transmits data about operational minutiae while filtering winnowing non-useful details.
The size of IoT opportunity by 2020 varies from one research firm to the other with an estimate over $10 trillion and over 50 billion connected devices.
The growth of connected things is accelerated by the massive growth of companion products to mobile devices, designed for consumers’ increasingly on-the-go lifestyle.
The trend toward a more useful world of connected devices hinges on a new class of smart sensors. Sensor integration and sensor fusion will continue to be the watch words for these new sensor networks. In turn, more sophisticated sensor systems will rely on a new class of processors – blending low power and high performance data lower price point needed to enable widespread use. Expect more everyday devices to become intelligent and networked, billions of devices – thermometers, cars, light switches, appliances, homes, are being connected to the Internet – each with its own IP address.
In 2014, portable and wearable computing promises to introduce major shifts in how humans interact with computing devices and information, dramatically reduce the gap between immediate information and the person for whom that information is the most useful. Health and fitness buffs already wear monitors that record their heart rate and the distance they run, coupling that to a PC to analyze the results. Wearable wireless medical devices include accelerometers to warn of falls, and insulin pumps and glucose monitors for diabetics. Each of these devices can connect to a smartphone via Bluetooth, and can issue an alert to their physician by triggering a call over the cellular network.
While enhanced hardware solutions continue to emerge for smart sensors, systems designers are looking to surround users with a more natural environment that provides an immersive experience via interacting with IoT devices and the cloud. Ultimately, all these key technologies – the Internet of Useful Things, and wearable computing – serve the purpose of bending technology to meet real needs as efficiently as possible. With the continued evolution of these key areas, the industry is moving rapidly toward that objective. Companies are encouraged to enabling a standards-based IoT where billions of devices of all types and capabilities are connected through interoperable Internet Protocols and Web Services.
Let us look into the future and see where IoT is heading and how C-IoT will impact Individual, Industry, and Infrastructure (3I’s) connecting to each other. The focus is to inspire the reader to invest now to profit from the future, explore some of potential opportunities that enable intelligent connectivity across the 3I’s.
1.4.2 Point Solutions
There is increasing number of devices connected to the Internet in many areas of our lives. Here are some examples of point solution impacting Individual, Industry, and Infrastructure:
1.4.2.1 Individual
· Smart watches (e.g., iWatch) and wearable devices send, receive, and retrieve health monitoring information that is carried on the wrist or other parts of the body. Imagine if such device is connected to other smart devices such as smartphone, smart tablet, smart t-shirt, smart eye-glass, and drive more value!
· Crack-pot with sensor to raise or lower temperature to adjust to the timing as to when dinner need to be ready when the individual wants.
· Wearable glasses (e.g., Google Glass) with the ability to send and receive lots of different information in real time in the direction of where the wearer is looking. Imagine if the law-enforcement or military agent wearing this has added image recognition capability with cloud-based real-time criminal facial recognition, and has cloud-based voice recognition, natural multi-language language translation!
· Biometric to protect password – Fingerprint sensor enabled into your smartphone. Swiping your finger will act as a password.
· Context-aware Smart TV provides TV content and two-way communications capabilities via the Internet. Smart screens and Smart TV also have a camera that can detect the context (who is watching the TV). The concept of two-way interactivity is extended to mirrors, windows, and other screens in homes, classrooms, and businesses. They are already on the computers and mobile devices in the form of touch screen and tablet computers.
· Smart garage door opener and add smartphone to it to operate remotely. Imagine if the smart garage door recognizes the home-owners car arriving, auto-discovery and auto-authenticate for entry then auto-notify the smart-thermostat to set the AC to the desired temperature for the specific home owner!
1.4.2.2 Industry
· Smart Parking Space that Waits for You. Imagine the time spent and frustration in finding a free parking spot – all can be solved with smart parking!
· Smart Ink. Several manufacturers have developed forms of ink that enable electronic circuits to be printed on just about anything. This will enable consumers of print ads to interact with those ads – giving Marketing Information System feedback, transporting consumers to Web sites, and enabling them to request more information or even order products.
· Smart Sports. Smart Basketball, golf ball, tennis ball, smart rackets, smart bats, smart sneakers, and so on as a connected object that can be recognized once it is in a specific space. Imagine if the smart sport devices have capabilities to provide real-time data analytic and real-time feedback to suggest to the sport player how to improve!
· Smart Clothing. Sensors built into the fabric, or printed on, clothing will give health and performance feedback to medical personnel and athletes. Marketers will use such clothing to monitor physiologic responses to marketing content, product and brand variations, and pricing changes. Imagine if smart clothing is context-aware whereby you can even change color and transparency of the clothes based on own heartbeat and temperature as well as heartbeat and temperature of the other person near-by!
1.4.2.3 Infrastructure
· New context-aware LED bulb that is fully dimmable, and adjustable color (by context who, when, etc.) with simple API, which can be controlled remotely. LED headlamps are evolving beyond just a standard replacement for headlights in new vehicles. Increasingly, premium features such as side illumination and cornering headlights are appearing, thanks to greater reliability, smaller size, and lower cost of brighter LEDs. A similar example can be drawn for LED for buildings or for streetlights.
· Smart Digital Signature. Taking traditional forms of promotion into the future, these will be ads that communicate to potential buyers, enabling them to interact with the ads, request more information, and buy products directly from the ad. This can be applied for any industry as well can be considered as digital banners mounted on street poles for promotion, generate awareness or as an amber alert helping law and enforcement in the search of someone.
1.4.3 Collaborative Internet of Things
1.4.3.1 Individual IoT
Individual for smart living covers consumer electronics and wearable devices, smart homes, and smart connected cars that are connected to Internet and communicated with each other.
Health and Wellness
Wireless sensor technology is allowing us to easily monitor the critical life-signs of patients. Previously, the lack of suitable sensors, combined with an unworkable tangle of wires, has severely limited medical applications. Now patients can be monitored effectively for serious conditions such as sleep apnea, while in bed sleeping. For monitoring critical parameters such as heart rate, while a patient is undergoing strenuous physical exercise, the connection of wires is impractical. This has evolved where people can now experience IoT through wearable devices such as wrist watches that not only monitor time and manage texts and emails but also monitor the blood sugar in a person’s system without the pain and suffering of a needle prick. The IoT has in fact conquered a lot of ground, even that of medicine and fitness.
BAN – Body Area Network
BAN is a network of devices applied on the person’s body that monitors different parameters and provides feedback information to the person. In addition, the information can be relayed to other, or stored for trends and analysis.
At the bigger picture, tracking will be required for the cardiovascular system, respiration system, mental activities, and others to provide a wholesome view of an individual and help guard against common cold, to difficulty in having quality sleep.
But the trend is to help people to stay healthy by monitoring and tracking their health practice. Most of the band devices have capability not only to show the real-time results on a mobile device, but also send it to the cloud for storage. As we understand many of the symptoms of diseases and disorders can be traced in the body in advance before they occur. Such stored data can be used to obtain clues about such diseases or disorders before they occur. Also, in the future, the collection of such data about different individuals (with permission of the person) can be used to provide valuable insights to the scientists as to how the body reacts when faced with certain disorders or incurable diseases.
The US FCC has approved a 40 MHz spectrum allocation for low-power medical BANs.
Today, the wearable devices are in its infancy, but according to IHS research, the market for Wearable devices could be worth $6 billion by 2016.
Using Google Glass, a physician can now works in hand-free way, have immediate access to patient medical record from any place in the hospital. The device can be used in the operating room to help a surgeon monitor and control in real-time medicalequipment without taking their eyes off the patient. It can also be used outside hospital at a site of an accident, where the paramedic can have access of medical information such as allergy about a person before they administer drug.
Robots can also play a role in the operating room in the future in assisting the surgeon on some of the difficult tasks and also can help in performing microsurgery when the surgeon is not in the room.
Home
Today, there are kits or gadget such as Raspberry Pi that enable you to connect your TV to the Internet for less than $25. Future TV will be Smart TV (Internet enabled and ready). For example, as you drive your car close to home, a signal can be sent out to open the garage door and adjust the thermostat setting in the home. As come close to the door, with video recognition will the door and various lights are turned on.
One example of smart device in the home is a “learning thermostat” by Nest. The device is using a series of sensors that monitors our daily schedule and adapt the climate as we come and go. The learning thermostat is promised to lower the cost of energy bill by 20%.
Another example by the same company called “Protect” is smart smoke detector that not only alerts the occupier via smartphone and has capability to call the emergency services. Advance model will have capability to communicate with home heating system and shut it down in the case of a fire or even a gas leak.
A more advance C-IoT is adding intelligence in communicating among various smart devices in the home. For example, when a person wakeup, a wearable device such as a wrest band can automatically send a signal to the smart thermostat to adjust the temperature, send a signal to the drapes to be opened, start the coffee machine, and so on.
Future homes will have modules of connected devices into a central system that can enable the consumer with smartphone or tablet to control all the functions in operating a home. With a touch of a button, user can exercise control over any system in the home such as security, climate control, or home entertainment. Turn on home projector, creating automatically the perfect ambience, sound system, and others can all be operated from a single app.
Smart Car
Having hundred’s of sensors in a car make it more smarter, providing alerts when service is required, provide a higher degree of safety and gadgets that provide the driver with an ultimate enjoyable driving experience. Smart inter-car connectivity and communications help in avoiding collision. Connecting with the environment and infrastructure, a drive can be alerted of traffic blocks of potential bad weather conditions.
Smart Electric Car
Most electric cars have today had a management app enable us to communicate with the car, with a third party such as emergency services if there is a trouble or accident.
CAR – Heads-Up Display
Researchers are busy trying to solve problems, such as glare and windshield curvature, that affect daylight readability. Automotive displays need to deliver very bright images in small affordable packages, have a long lifetime and not generate heat. The aerospace has a continuous influence into the design – aerodynamics of cars and now in terms of instrumentation and guidance system. The latest is head-up display (HUD) technology, which was originally developed for fighter jets. The head-up projection system creates a very high brightness monochromatic image that appears only when the driver looks in a particular location. Such a display would allow the driver to view transparent images for daytime navigation information as well as night vision imagery by projecting the images off the windshield. Projecting information directly into the driver’s line of sight allows people to process it up to 50% faster – due to shorter eye movement – and keep their attention focused on the road ahead. HUD technology is currently available on several high-end vehicles and is starting to show up in other segments. In fact, more than 35 vehicle models currently available in the United States have standard or optional HUDs. According to IHS Automotive, 9% of all new automobiles in 2020 will be equipped with HUD technology versus 2% in 2012. Sales this year alone is projected to climb 7% to 1.3 million units.
In the future, HUDs may alter the interior design of vehicles by eliminating the need for a center console equipped with a screen and a digital instrument cluster. A handful of Tier 1 supplier, such as Bosch, Continental, Delphi, Denso, Johnson Controls, Nippon Seiki, and Visteon, are currently exploring this issue. Engineers are scrambling to develop new HUD technology that can be cost-effectively mass-produced, while addressing issues such as noise, vibration, and harshness.
1.4.3.2 Industry
Industry for business efficiency covers several markets associated with industry such as factory automation, smart buildings, and smart retails.
With introduction of intelligence into equipment, IoT will revolutionize industries and making the business more efficient and provide customers with new services.
According to GE, today Industrial Internet (IoT for Industry) account for $32 trillion dollars. By 2025, it could reach to $82 trillion dollars of output or approximately one-half of the world economy. At GE Durathon battery factory in Schenectady, NY, the IoT helps the company collect data about processes going on 24 to 7. Through the 10 000 sensors on the assembly line and the sensors in every single battery, managers can instantly find out the status of production. They are able to share that information and data with coworkers in other departments.
According to O’Reilly’s David Stephenson, technology at GE and at similar manufacturers has resulted in innovations never before realized. “The Internet of Things promises to eliminate massive information gaps about real-time conditions on the factory floor that have made it impossible to fully optimize production and eliminate waste in the past,” he says [6].
Collaborative IoT and Manufacturing
Global competitive pressures are challenging industrial and manufacturing companies to drive inefficiencies out of their systems, manage workforce skills gaps, and uncover new business opportunities.
Factories and plants that are connected to the Internet are more efficient, productive and smarter than their non-connected counterparts. In a marketplace where companies increasingly need to do whatever they can to survive, those that do not take advantage of connectivity are lagging behind.
According to Rockwell Automation, only 10% of industrial operations are currently using the connected enterprise, which connects businesses to cyberspace to improve manufacturing functions. The machines were linked to FactoryTalk, software that lets the company’s employees have remote access to both historical and real-time data and features production dashboards that provide a comprehensive picture of the whole system so they can monitor performance. All of this software and hardware resulted in faster time-to-market, improved asset utilization and optimization, lower total cost of ownership, workforce efficiency, enterprise risk management, and smarter expenditures. The new system reduced maintenance costs and downtime, as well as the capability to collect more data. In turn, this afforded them the ability to aggregate data and present dashboards accessible on the Web that allow managers to monitor operations and KPIs (key performance indicators) across the enterprise. Extending the information from the process remotely has become a viable way to extend the manufacturing footprint, consolidate expertise if it cannot be sourced locally and to manage asset performance more efficiently.
Smart Grid
Many energy companies are spending billions of dollars in developing smart grid to improve the efficiency, reliability, and sustainability of our electricity supply. Analysts project that the smart grid market will surpass $400 billion by 2020. The smartness in such a system is to allow the energy companies to collect data view demands at every level from large areas to individual homes. The goal is to use the data to control the flow of electricity when we really needed. This approach of supply per demand and price per demand can result in an overall saving on resources and reducing cost both on the part of the provider and the consumer.
UT (University of Texas), for example, is developing smart grid for the consumer, which will help the consumers to monitor their own electricity but also have the ability to return excess back to the Grid.
Video Surveillance
Video surveillance cameras and other sensors are key solution system to protect commercial building. The system software has capability to recognize faces, images, and count people and vehicles. This will contribute on increasing worker safety and lowering cost.
IoT and Mines
Sine Wave, a company that focuses on technological solutions for businesses, has created a customized IoT program that resulted in increased safety and communication in mines. According to their website, they designed a browser-based application that allows users to communicate with the workers, operators, and machines in the mine, as well as “see a real-time view of all activities underground [including] custom mapping of each mining operation.” By knowing what is going on in the underground mines in real time, users can avoid safety hazards and respond to emergencies quickly.
NFC – Near Field Communications Technology
An NFC is a short-range secure technology that can be used by consumer to make a payment. For example, an NFC device can send data at a rate of 106, 212, or 424 kbits/s. NFC-enabled devices can be used in taxis, where payment can be done with swapping credit card but simply activating the app on your mobile device to start the payment process. This can expand to other adjacent markets such as restaurants and fast food, gas stations, food markets, and retail stores. Market introduction can be by introducing NFC as another method of payment adjacent to credit card payment devices. The overall benefit is to make the ecosystem cheaper and process of payment more convenient.
1.4.3.3 Infrastructure
Infrastructure for smart communities and cities is for sustainable environment and living, which include public transportation and highways, public safety, disaster management, smart education, and smart health care.
Effectively, a city is looking how to improve things by collecting information from sensors and analyze the data and improve its plan in appropriate areas.
Smart Cities
The effort by researchers to create human-to-human interface through technology in the late 1980s resulted in the creation of the ubiquitous computing discipline, whose objective is to embed technology into the background of everyday life. Currently, we are in the post-PC era where smartphones and other handheld devices are changing our environment by making it more interactive as well as informative.
A smart environment is the physical world that is richly and invisibly interwoven with sensors, actuators, displays, and computational elements, embedded seamlessly in the everyday objects of our lives, and connected through a continuous network.
The creation of the Internet has enabled individual devices to communicate with any other device in the world. The inter-networking reveals the potential of a seemingly endless amount of distributed computing resources and storage owned by various owners.
The advancements and convergence of MEMS technology, wireless communications, and digital electronics has resulted in the development of miniature devices having the ability to sense, compute, and communicate wirelessly in short distances. These miniature devices called nodes interconnect to form a WSN and find wide application in environmental monitoring, infrastructure monitoring, traffic monitoring, retail, and so on.
Waste Management
Waste management systems use IoT devices to monitor those who exceed waste limits. In some US cities, residential waste volume has declined because recycling measures were implemented. In the world, smart water systems and meters have reduced leaks and spillages with the help of sensors.
Large Event – Car Race
In a car race such as Formula-1, a race car can produce thousand’s of data points every time it goes around the track. Designers and engineers to look for improvement as to how to get an extra mile or kilometer per hour can then analyze the data collected.
Cattle Wellness
Cattle: Researcher is working on recognizing and preempts illness or infection in cattle before affecting the rest of the herd.
This can be accomplished by placing wireless devices on cattle to monitor their behavior pattern including movement and sleep in real time. Such a system is expected to reduce the high cost of medication and help increase milk yield.
Crops (Vine Field) – Optimal Results
Where a variety of sensors can be placed in vineyard to measure real-time changes in environmental conditions such as air temperature, relative humidity, soil moisture, solar radiation, and leaf wetness, the system feeds the data into a cloud-based software platform that can be viewed by employees to respond in real-time event. The outcome of analyzing the data will help in harvesting at the optimal time and help in the management of resources such as water and fertilizer.
Smart Delivery System (Drone)
To improve on service delivery in particular when lightweight item is ordered, the desire to have immediate delivery as soon as the order is ready. This is where drone comes into play. The drone can pick up the item being ordered and via GPS can travel toward the destination, descent, send an alert to the customer before descending, drop the item at the front door of the customer, and return to the base. Services can be applied to food order, books, and others. The US FAA has started granting licenses for certain commercial applications. Debate is still on for safety and privacy. Amazon is about to launch such services. Amazon estimates 80% of its deliveries are light enough (<5 lbs) for a drone to carry. Today, customers and hobbyist can order and operate drones under certain guidelines such as flying height is 40 ft.
Property/casualty companies also are investigating the employment of sensors in conjunction with geolocation systems to build risk profiles across various properties.
Security and Privacy
Security has become and remains to be a key challenge to secure access of content at anytime and anywhere. Security risks is now associated with the rapidly proliferating IoT. For the first time, the Industry has reported actual proof of a cyber attack involving common appliances.
The “IoT” holds great promise for enabling control of all of the gadgets that we use on a daily basis. It also holds great promise for cybercriminals who can use our homes’ routers, televisions, refrigerators, and other Internet-connected devices to launch large and distributed attacks. Internet-enabled devices represent an enormous threat because they are easy to penetrate, consumers have little incentive to make them more secure, the rapidly growing number of devices can send malicious content almost undetected, few vendors are taking steps to protect against this threat, and the existing security model simply will not work to solve the problem. Security strategy is required from the early stages of defining and developing an IoT solution looking at all aspects sensing, hardware, software, networking, cloud, storage, code, mobile devices, social media, processes, and others. Risks associated with access, data integrity, privacy, and network need to be identified, prioritized, and mitigated. Policy needs to be established as to handling the security risks. Technical requirement will include user identification and authentication, device identification and authentication, security function isolation, denial-of-service protection, and software and information integrity.
Privacy
All these intelligent devices and systems are generating a lot of data about individuals, homes, cars, industry, and cities. What happens to all the data collected? How is it protected? Data protection is becoming of increasing importance for both individuals and businesses. Various initiatives have started in this area but more innovative and collaborative work is needed!
Networking Infrastructure Solution
Networking Infrastructure Solution calls for providing reliable, secure operation in the most harsh environments and extreme temperatures to meet the most demanding applications, such as public safety, transportation, defense, oil and gas exploration, energy, and mining. Such solution exists in a scattered and silo fashion. More collaboration, integration is required to provide such secure network for operations.
1.4.3.4 Across Multiple Domains
IoT and Technologies
The IoT has many definitions, but revolves around connecting sensors, smart equipment, programmable logic controllers (PLCs), M2M, and RFID data with the Internet so that other systems or analytics software can respond to or make sense of the data. The great promise of the IoT is that information technology (IT) systems will have a real-time understanding of conditions, events, and material movements in the physical world.
M2M Opportunities
In the year 2020, the world will be more connected, wireless networks will connect more machines than people and M2M technology will help us to be more energy and cost-efficient, safer, and more secure. This is the era of connected intelligence.
The number of mobile connections is forecast by the GSM association to grow to 50 billion by the end of the decade. There will be several trillion wirelessly connected things, according to the Wireless World Research Forum. This increased use of mobile and M2M technology will deliver as much as $100 billion of annual savings thanks to material and energy efficiency savings (smart2020.org). The social and economic benefits are clear.
It is tempting to assume that cellular will hold the answer to M2M connectivity, but stop and ask yourself this question: are cellular networks designed for M2M or are they more about broadband connectivity for people?
It is worth noting that M2M devices communicate differently than humans and that there will be many more billions of them than us. These devices will communicate on a regular, optimized schedule and when they do speak, they do not say very much. So if machines and humans communicate so differently, why should machines and humans share the same networks? Perhaps one day that will be possible. Perhaps 5G cellular will deliver a common network approach. For the foreseeable future, M2M gateways will prevail in many scenarios.
M2M gateways offer the following key benefits:
Scaled to multiple settings (e.g., home, industrial, office, campus, city, and retail)
· A local intelligent node turns raw data into useful information
· A hub for cross-sector service and application convergence or “joined-up thinking”
· A secure node bridging broadband WAN and local area sensor networks, wireless and/or wired, which can even connect legacy-installed sensor/actuator nodes
· An aggregation node for a multitude of low-energy, low-cost sensor/actuator nodes.
1.4.4 C-IoT and RFID
1.4.4.1 Asset Management
Organizations are already using RFID tags combined with a mobile asset management solution to record and monitor the location of their assets, their current status, and whether they have been maintained.
1.4.4.2 Inventory Systems
An advanced automatic identification technology based on RFID technology has significant value for inventory systems. The system can provide accurate knowledge of the current inventory. The RFID can also help the company to ensure the security of the inventory. With the just in time tracking of inventory through RFID, the computer data can show whether the inventory stored in the warehouse is correct with quantity currently. Other benefits of using RFID include the reduction of labor costs, the simplification of business processes, and the reduction of inventory inaccuracies.
1.4.4.3 Product Tracking
RFID use in product tracking applications begins with plant-based production processes, and then extends into post-sales configuration management policies for large buyers.
1.4.4.4 Supply-Chair Merchandize Tracking
RFID can also be used for supply chain management in the fashion industry. The RFID label is attached to the garment at production can be read/traced throughout the entire supply chain and is removed at the POS.
1.4.4.5 Access Control (TX TAG, Conferences)
RFID tags are widely used in identification badges, replacing earlier magnetic stripe cards. These badges need only be held within a certain distance of the reader to authenticate the holder. Tags can also be placed on vehicles, which can be read at a distance, to allow entrance to controlled areas without having to stop the vehicle and present a card or enter an access code.
1.4.4.6 Transportation and Logistics
Logistics and transportation are major areas of implementation for RFID technology. Yard management, shipping and freight, and distribution centers use RFID tracking technology. In the railroad industry, RFID tags mounted on locomotives and rolling stock identify the owner, identification number, and type of equipment and its characteristics. This can be used with a database to identify the lading, origin, destination, and so on of the commodities being carried.
In commercial aviation, RFID technology is being incorporated to support maintenance on commercial aircraft. RFID tags are used to identify baggage and cargo at several airports and airlines. Some countries are using RFID technology for vehicle registration and enforcement. RFID can help detect and retrieve stolen cars.
1.4.4.7 Animal Identification
RFID tags for animals represent one of the oldest uses of RFID technology. Originally meant for large ranches and rough terrain, since the outbreak of mad-cow disease, RFID has become crucial in animal identification management. An implantable RFID tag or transponder can also be used for animal identification.
1.4.4.8 Sports
RFID for timing races began in the early 1990s with pigeon racing. RFID can provide race start and end timings for individuals in large races where it is impossible to get accurate stopwatch readings for every entrant.
1.4.4.9 Telemetry
Active RFID tags also have the potential to function as low-cost remote sensors that broadcast telemetry back to a base station. Applications of tagometry data could include sensing of road conditions by implanted beacons, weather reports, and noise level monitoring.
1.4.4.10 RFID – Big Data Filtering
Not every successful reading of a tag (observation) represents data useful for the purposes of the business. A large amount of data may be generated that is not useful for managing inventory or other applications. For example, a customer moving a product from one shelf to another, or a pallet load of articles that passes several readers while being moved in a warehouse, are events that do not produce data that is meaningful to an inventory control system.
Event filtering is required to reduce this data inflow to a meaningful depiction of moving goods passing a threshold. Various concepts have been designed, mainly offered as middleware performing the filtering from noisy and redundant raw data to significant processed data.
1.4.5 C-IoT and Nanotechnology
Nanotechnology will have impact on all aspects of IoT at the sensing level, gateway, and service levels. Here are some examples.
1.4.5.1 Food Safety
According to United Nations, 1.3 billion tons or one-third of global food production is wasted each year. In the future we expect nanotechnology will be embedded in our grocery and send alert as to when the food will go bad and thus ensure that the food on the shelf is always safe. Furthermore, typically the foods we eat are made of molecules of protein, fat, and carb. Research scientist is beginning to focus on nanotechnology to bring about super food that is good for our health.
1.4.5.2 Surgery
Nanotechnology can be used in some cases to replace surgery. For example, the small microsurgery material can be introduced through the vascular system and preprogrammed or guided by physician to perform various functions such as eliminated cancer cells before they can spread, changing new chromosome for old ones inside individual living human cells.
At the University of California, Nanotechnology can be used in developing particles that mimic the human cell called “nanosponges” that have a diameter of 85 nm or about 3000 times smaller than regular human blood cell. These nanosponges can be injected into the body by the millions, which can be used in various functions such as treating bacterial infections or eliminating foreign toxin by intercepting and attacking before damage to actual blood cell can be done.
1.4.5.3 Treatment
Nanotechnology can be used to have more effect than chemotherapy in attacking directly drug resistance cancer cells. Research has shown that nanotechnology treatment is 30 times more effective than traditional chemotherapy treatment and require 1/10 of chemical doze.
1.4.6 Cyber-Collaborative IoT (C2-IoT)
This book provides a visionary approach transitioning from IoT (point solution) to the Future/Collaborative IoT (C-IoT solutions/systems). Moving forward toward Cyber-Collaborative IoT (C2-IoT system of systems), we see major technology players such as nanotechnology, 5G to 10G, and others as disruptive technology that calls for cyber collaborative intelligence making sensing more intelligent, moving services from edge of the network to be distributed between End sensing node and cloud intelligence, inter-collaborative-cloud will remove global barriers and finally solutions and services will also be hosted by a distributed providers (as a result of consolidation among service providers, carriers, etc.). Inter-countries policies will be required to protect soft asset (information and intelligence). Privacy, safety will require a global level orchestration. Thus, the world (perhaps headed by the United Nations-IEEE and others?) can play a key role in fostering a new level of collaboration for advancing technology for humanity in terms of living conditions, peace, and economic/industrial growth.
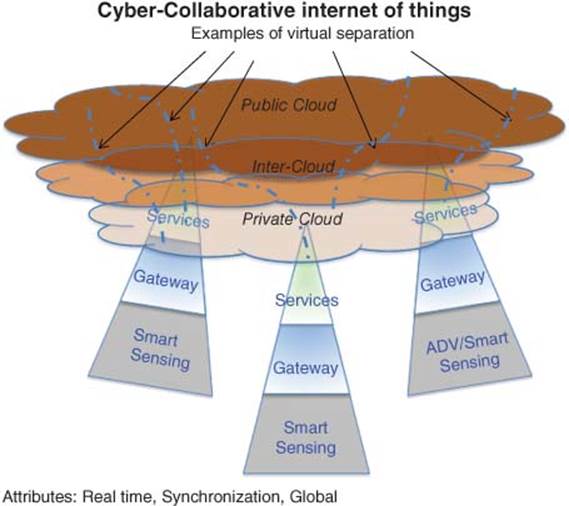
Figure 1.11 Future approach to scaling C-IoT
Figure 1.11 exemplifies the future approach to scale IoT globally and across all domains with security safeguard against hackers, and ensuring privacy.
1.4.7 C2-IoT and Ebola Case
Today, Ebola outbreak in West Africa has sickened over 8000 and killed over 4000. Because there is no off-the-shelf medicine to treat it, there is a high risk that Ebola will spread with people infected with the virus from Africa to other countries.
Ebola, being a very serious and contiguous virus, requires a global containment plan by the UN– World Health Organization. Such undertaking will require collaboration with many nations who possess advancement of medial technology and expertise in treatment and administration.
How will C2-IoT help in saving lives in countries impacted by the virus and contain the spread of the virus to other regions and countries?
Outlined below is an example of a C2-IoT-based plan and steps to be taken regarding the Ebola case. See Figure 1.12.
· Immediate creations of an Ebola Emergency Virtual Control Center to be staffed with experts from other nations to supervise treatment of those infected, and contain the virus from being spread locally, regionally, and globally.
· Establishing an emergency fund leveraging social media to get the message out for a worldwide donation of money that will help to pay for clinics, medicine, protective gear, instruments, devices, and others.
· Call for physicians and experts to collaborate, discuss cases and effect of the treatments on patients and possible approaches based on results from similar cases.
· Need of IoT wearable devices for infected patients to be remotely monitored minimizing chance on others not to be infected.
· For Treatment, Mobile Clinics will be installed to serve those that require treatment equipped with sensors and devices that are continually sending critical information to the cloud. Tracked information may include:
· Critical information collected in real-time of each individual inside the clinic,
· Treatment and effect on each patient,
· Types of drugs entering the clinics,
· Types of disposal of items leaving the clinics,
· Individuals coming in or going out of the clinics.
· Deployment of Law and Enforcement officers who received special training to handle such situations to monitor clinics, labs, and individuals. Officers are to be equipped with advance monitoring devices with audio and video communications capabilities.
· Because of shortage in medicine, a more proactive smart manufacturing facility is to be established with focus on switching mode of operations from “time-to-market” to “time-to-service.”
· Airports of infected regions of this virus are to screen all travelers leaving the countries, are to be accountable by responding to Ebola questionnaire.
· Key airports receiving travelers from infected regions are to be equipped with advanced screening equipment and protocol.
· Briefing: A Spokesperson of the Ebola Emergency Virtual Control Center is to provide regular briefings identifying issues and where help is needed.
· Umbrellas of interconnected websites dedicated to Ebola are to be created. Websites will be dedicated for each country being impacted, populated with information and Q&A that will be constantly updated. A mechanism is to be established to connect with families of those infected by the virus.
· Leverage social media to facilitate communications and generate awareness.
· Need for a group to prepare educational material and disseminate information and tips to media, schools, and public at large.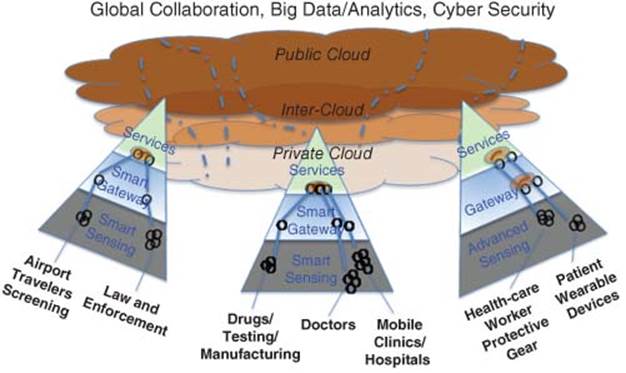
Figure 1.12 C2-IoT model and Ebola case
· Global Collaboration. UN, leading nations, experts, medicine, fund, and so on.
· Big Data. Ebola drug R&D and usage, patient record, physician/workers records, mobile clinics/hospitals, and so on.
· Analytics. Demand for drug/physicians/clinics, effectiveness of medicine, education, and so on.
· Cyber Security. Law and Enforcement, protecting virtual with physical at local sites, other regions, cloud, and so on.
The above shows that C2-IoT can be used without any physical boundaries connecting the physical (sensors, physicians, patients, clinics, drugs, etc.) with the virtual (information, knowledge, track history, trends, R&D results, insights, etc.). Such a system will have the major functions of sensing, connectivity to the clouds. The cloud will become a repository of all information pertaining to Ebola virus, patients, medicine, treatment, results, premises, and those who come in contact with patients. A great deal of computation and analysis of data collected will be required. Results and insights are to be shared among interested parties for the purpose of saving lives, treat those who are infected and protect the rest of the public from being impacted.
C2-IoT will enable connecting people-to-people-to-systems-to-knowledge-to-insights protecting all for privacy, hackers, and breakdowns. Mobile smart devices such as smartphones and tablets with cognitive computational capabilities and natural voice language processing would be required. Devices such as Watson (won Jeopardy competition in 2011) could become such device that process information at a very high speed and assist experts with filtered information which may include specific data, trends, modeling, comparisons, and other critical information that are needed by those engaged in the networks as well as those in the Ebola Emergency Virtual Control Center.
1.4.8 Summary
In this section, we have witness examples of potential future application for C-IoT where vast amount of sensors enable connecting things to the Internet on a daily basis.
Future smart mobile/wearable device connected to the clouds (local, public, and inter-cloud) enabled by C-IoT can deliver a vast set of functionalities that can be personalized based on where you are and what function you are engaged in. Security will be embedded and privacy will be authenticated based on unique identification such as biometric signature.
As we witness today with Watson winning Jeopardy in 2011 exhibiting a capability of understanding natural language, navigate through a wealth of stored information and knowledge, and using sophisticated algorithms to filter through big data and retrieve most suitable response. Such approach is being prepared for many of the markets such as health, traffic, finance, agriculture, businesses and as such impacting Individual, Industry, and Infrastructure.
The future focuses not only in making available insightful information to individuals localized to where they are, and their needs at anytime.
A person may have multiple jobs, but try to balance his life focusing to what is important that will bring great experience and rewarding results.
With a mobile/wearable device, an individual controls the environment in the home (lighting, security, climate, wellness, etc.), reviews the day’s schedule and missions to accomplish, receives assistance in the car to reach various destinations (car safety, traffic conditions, navigation, etc.), receives help and on-demand information for each of the missions (e.g., closest and cheapest gas station or electric power charge for the car and critical information and profile of the upcoming meeting), alerts and connects with business colleagues for lunch, prepares for an afternoon business meeting and gets profile of new individuals to meet, accesses to business records and stat related to the meeting, and is being alerted on the timing of the social function, and the device uses the smart parking function to direct for available parking slot. While the person is in a particular mission, he is constantly connected to the environment for any major alerts such as intruder approaching his home or entering his car – with a video surveillance he can in turn send the picture to the police with real-time information. Overall, this helps enrich experience, making time more efficient and generate rewarding results.
As mentioned such example can change scenario from time to time and relevant information and insights are readily available for viewing for action. Thus features and functions have been transported to a series of experiences of value being created. Thus, C-IoT business model is about creating experiences of value.
When the world around us becomes plugged in and aware, it will drive efficiencies like never before.
1.4.8.1 Collaborative IoT and Climate Change
While it may seem out of reach today (and possibly laughable to some), IoE will eventually allow us to become better stewards of our finite resources by improving how we sense, understand, and even manage our environment. As billions and even trillions of sensors are placed around the globe and in our atmosphere, we will gain the ability to literally hear our world’s “heartbeat.” Indeed, we will know when our planet is healthy or sick. With this intimate understanding, we can begin to eradicate some of our most pressing challenges, including hunger and ensuring the availability of drinkable water.
1.4.8.2 Secure, Reliable Connectivity in Extreme Environments
The rise of the IoT is bringing networking to new device types and locations. Networks must reliably and securely connect people and things in environments with weather and temperature extremes. These networks must also provide seamless mobile connectivity on devices with size, weight, and power limitations in any location, under any circumstance.
Wearable Devices, Health Monitoring, and Your TV
You are wearing a fitness/health device and watching television in your bedroom. The device is linked to your TV through shared logins or a simple linkage through your phone; so now, your TV knows about your body’s activity levels including your sleep/wake patterns.
Advertisers will make smarter TV buys and stop sending commercials to sleeping consumers. Taking this one step further, since your fitness device knows your activity levels, it could inform which commercials you see – for example, more active consumers might get the stepper and workout equipment commercials which are wasted on me.
Wearable, Mobile, and TV
To build on the example above, looping your smart phone into this relationship will give advertisers an additional dataset. Your GPS and cell tower data tell us where you have been locally and if you have been out of town/on vacation. We know if you go to the gym, play tennis, or like to dine out.
Based on this specific data, we are now able to send you digital (smart phone) and analog (TV) ads that are highly relevant to your behavior (and travels).
Location-Based Understanding
How do advertisers know where you go? Our mobile devices are constantly collecting information about our location and movements.
Just check your iPhone under Settings (Privacy – Location Information – System Services – Frequent Locations). The iPhone by default records all your movements and patterns. Advertisers could leverage this data to better understand individual consumer behavior and determine their value more accurately.
For example, I go to a coffee shop once a week; my wife goes almost every weekday. In a real-time bidding environment, her value to a coffee advertiser should be five times greater than mine based on her location history.
Or we can use historic behavior to send the right ad at the right time to the right person. If we know that someone goes to the movies every Friday, we should start sending targeted movie ads to him on Thursday instead of Saturday.
Linking this back to the rise in beacons and GPS-enabled phones, it is conceivable that we will be able to measure the impact a billboard had on us based on visits to or engagements with brand assets while in proximity to the brand’s billboard.
Web Analytics and Spatial Relations
I believe in 2015, we will be able to collect new forms of data, through the device browser, about how a mobile device is being used in its environment; this will allow us to segment web analytics or media consumption behavior in a much more granular way.
This next-generation information collection goes beyond device model and manufacturer to many more physical-world metrics such as device orientation in 3D space, ambient light levels, elevation of ground or change in user position (moving vs static).
We could then start to segment and target people based on a new set of options like whether someone is at home/work or on the move, or lying down as opposed to standing up.
Connected Homes
With connected refrigerators, lights, thermostats, and other sensors in the home, we can glean insights into the user’s current environment. Is it dark? Is it warm or cold? Is the TV on or off? What are they watching? Who is home? This and more can be gained by connecting addressable advertising with connected homes.
Taking this one step further, sooner or later our fridge will know what we are low on, and send us ads or recommendations based on previous contents and consumption patterns. Our connected TVs will know what we watch and who is watching; this will allow marketers and networks to bring truly relevant content to the viewer’s screen.
Fueled by the prevalence of devices enabled by open wireless technology such as Bluetooth, RFID, Wi-Fi, and telephonic data services as well as embedded sensor and actuator nodes, IoT has stepped out of its infancy and is on the verge of transforming the current static Internet into a fully integrated Future Internet [7]. Internet revolution led to the interconnection between people at an unprecedented scale and pace. The next revolution will be the interconnection between objects to create a smart environment.
References
1. [1] Behmann, F. (2014) How the Internet of Things Promotes Collaborative Innovation. Austin Business Journal (Oct. 20, 2014) http://www.bizjournals.com/austin/blog/techflash/2014/10/how-the-internet-of-things-promotes-innovation.html (accessed 10 December 2014).
2. [2] ABI https://www.abiresearch.com/press/iot-developers-to-total-3-million-in-2019-paving-t (accessed 18 November 2014).
3. [3] FDA – US Food and Drug Administration http://www.fda.gov (accessed 18 November 2014).
4. [4] Research2guidance http://www.research2guidance.com (accessed 18 November 2014).
5. [5] Gartner Research http://www.gartner.com/newsroom/id/2636073 (accessed 18 November 2014).
6. [6] Forbes http://www.forbes.com/sites/ptc/2014/07/01/how-the-internet-of-things-is-transforming-manufacturing/ (accessed 18 November 2014).
7. [7] Gubbi, J., Buyya, R., Marusic, S., and Palaniswam, M. (2012) Internet of Things (IoT): A Vision, Architectural Elements, and Future Directions.