Exam Ref 70-413 Designing and Implementing a Server Infrastructure, Second Edition (2014)
Chapter 5. Design and implement an Active Directory infrastructure (physical)
The previous chapter covered Active Directory’s logical structure, which is built using objects such as forests, domains, and organizational units (OUs). Whereas the logical makeup of Active Directory is primarily used to create a management structure for applying Group Policy and delegation of permissions, the physical structure is used to shape and manage replication and authentication traffic.
To authenticate to Active Directory, users must be able to contact a domain controller. SRV records in Domain Name System (DNS) are used to direct network clients to domain controllers for authentication, which is important when there are no domain controllers for the required domain in the user’s current site. There are also some complexities introduced when a user from one domain is a member of groups in another domain (this issue of interdomain authentication is discussed later in this chapter). Ideally, every location in your organization would contain at least two domain controllers to provide high availability to a local domain controller, but this scenario is often impossible (for many different reasons).
The other type of Active Directory network traffic is replication. Active Directory replication works in different ways, depending on the scope of the replication. For example, domain controllers within the same site perform replication as objects are modified, and intersite replication occurs in 15-minute intervals to optimize efficiency through com-pression. Although these intervals can be configured as replication windows, which disables intersite replication during certain time frames, many organizations require intersite replication to occur throughout the day. A large part of designing the site structure in Active Directory involves optimizing intersite replication, ensuring that the replication schedule fits the requirements of the organization and that the paths used by replication traffic are efficient and cost effective.
The physical design of your Active Directory implementation is based on balancing the network traffic required for replication with authentication. This balance is necessary, while still meeting the constraints of cost, physical security, administration capabilities, and corporate policy.
Objectives in this chapter:
![]() Objective 5.1: Design an Active Directory sites topology
Objective 5.1: Design an Active Directory sites topology
![]() Objective 5.2: Design a domain controller strategy
Objective 5.2: Design a domain controller strategy
![]() Objective 5.3: Design and implement a branch office infrastructure
Objective 5.3: Design and implement a branch office infrastructure
Objective 5.1: Design an Active Directory sites topology
The site topology in an Active Directory forest defines the physical locations within your organization and enables you to specify which locations contain domain controllers. Replication and authentication traffic use this structure to determine the most efficient path between domain controllers. By defining the site structure of your organization, Active Directory member computers can automatically connect to the domain controller within the site where they are currently connected. Sites can also be used to enhance printer discovery, telling clients where to find a local printer. (Chapter 4 discusses how sites can be used to link Group Policy Objects to streamline client configuration for location-specific requirements.)
In addition to using sites to define locations in an organization, Active Directory uses site links to define which sites are allowed to pass replication and authentication traffic and the path that this network traffic must take. Site links are a major part of your replication strategy because they are the primary tool for shaping and optimizing intersite traffic throughout your forest.
Both replication and authentication traffic should be considered when you design your physical Active Directory topology. It might be completely acceptable within your organization for intersite replication traffic to occur hours apart, but an intersite authentication requirement can significantly alter the design of your site and site link structure. Conversely, your organization might use intersite authentication only on rare occasions, but if frequent replication is required due to application requirements or centralized administration, you have to take this requirement into account during the design phase of your topology.
This objective covers how to:
![]() Plan for domain controller proximity
Plan for domain controller proximity
![]() Optimize replication
Optimize replication
![]() Design site links
Design site links
![]() Identify and resolve Active Directory replication conflicts
Identify and resolve Active Directory replication conflicts
Planning for domain controller proximity
In an ideal situation, every site in an Active Directory would have a domain controller with the necessary information to authenticate any user within the forest. Unfortunately, many companies cannot place a domain controller in each corporate location, either due to a lack of physical security, the cost of deploying domain controllers to every location, or mobile workers who do not have a physical office space. Fortunately, Active Directory was built to take on these challenges.
Besides being dispersed throughout an enterprise to optimize authentication performance, domain controllers in large or critical locations should be redundant. Having multiple domain controllers in a single location prevents authentication failures due to a single domain controller being offline. Instead of having multiple domain controllers within each site, ensure that authentication traffic can be routed efficiently to the next best offsite domain controller.
Figure 5-1 illustrates these concepts: Each of the four primary sites has two domain controllers, ensuring availability for authentication, even if one domain controller is unavailable. The two branch sites linked to the primary sites have no domain controllers, so their authentication traffic must be routed to the closest primary site.
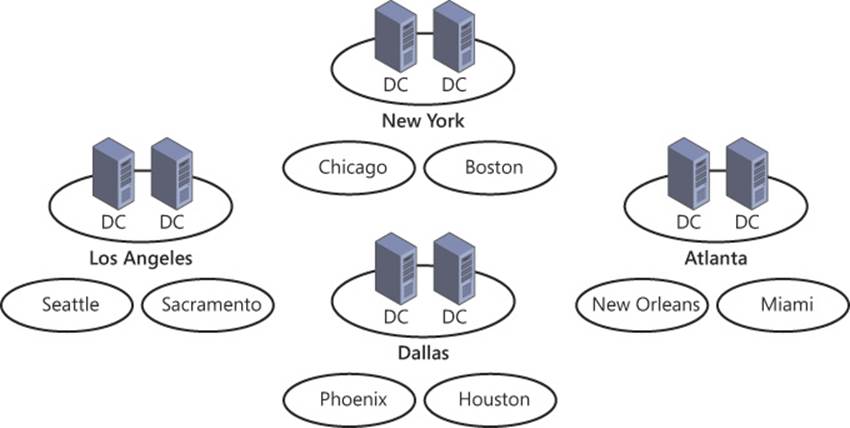
FIGURE 5-1 When a site does not contain a domain controller, authentication traffic must be routed to the closest site with a domain controller that can authenticate the client
In addition to client-domain controller proximity, there are some specific domain controllers in every Active Directory forest that need to be identified and incorporated into your plan for domain controller placement. Specifically, domain controllers that perform operations master roles or act as a global catalog server should be strategically located throughout your enterprise. Operations masters are critical for management aspects of Active Directory: They facilitate changes to the Active Directory schema, change passwords, and issue pools of ID numbers required for object creation. Although some operations master roles are performed by a single domain controller for the entire forest, others are handled by one domain controller in each domain (see Figure 5-2). Global catalog servers can help the balance between replication and authentication traffic by reducing the need for interdomain communication. (Operations master roles are discussed in more detail in Objective 5.2; global catalog servers are discussed in Objective 5.3.)
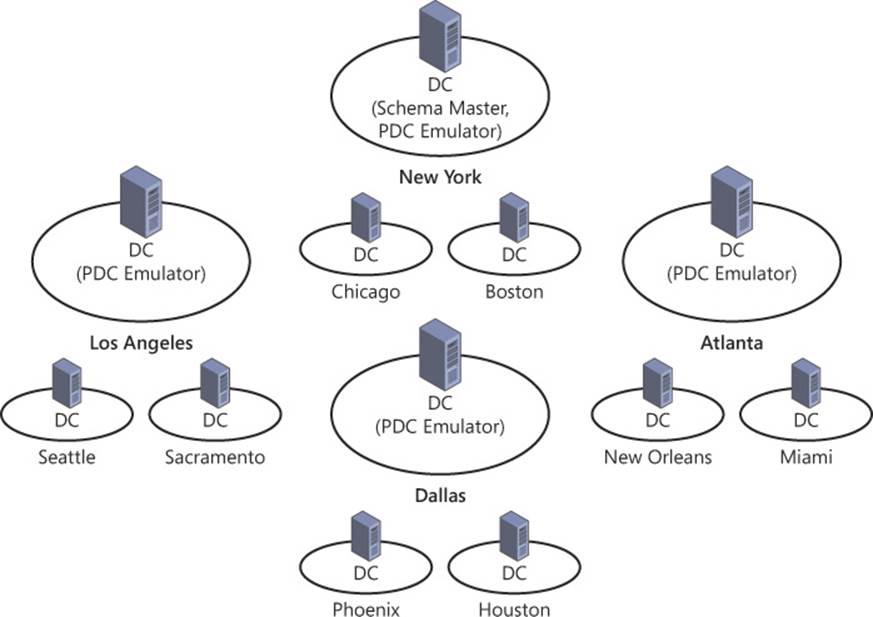
FIGURE 5-2 Even when each site contains a domain controller, some actions must be referred to the domain controller performing an operations master role
Forest root domain controllers enable users to authenticate between different domains in the same forest. Although domain controllers in a forest root domain usually reside in one or more centralized datacenters to optimize cross-domain authentication, sometimes it is necessary to place a forest root domain within specific sites to facilitate authentication between domains. Distributing domain controllers in the forest root throughout the site topology can facilitate authentication between domains or to applications operating in the forest root (see Figure 5-3).
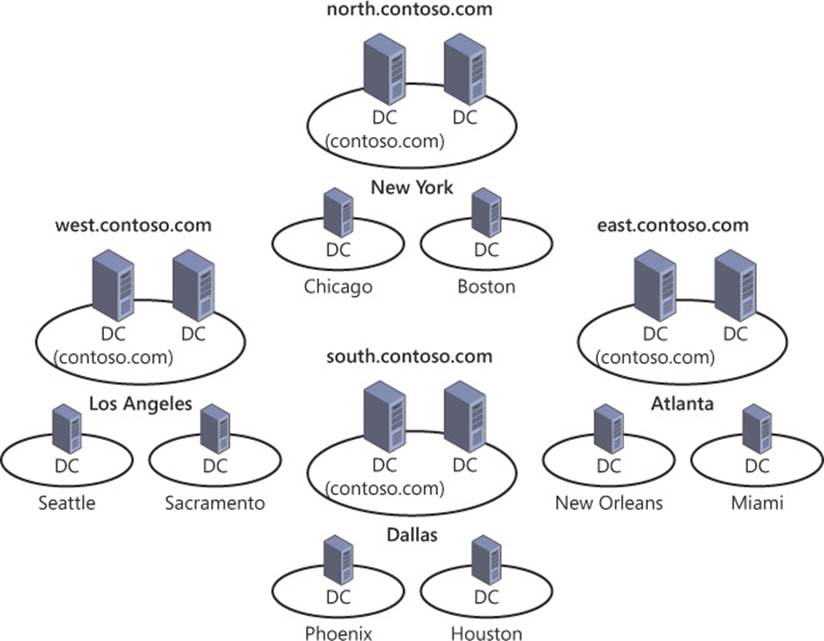
FIGURE 5-3 Communication with domain controllers in the forest root domain is sometimes required to facilitate cross-domain authentication
Remember that shortcut trusts can also be used to improve authentication to specific domains within the forest. Domain controllers in the forest root can also be heavily relied on by applications that integrate with Active Directory. Keep these factors in mind when you plan the placement of your domain controllers.
Be sure to consider application partitions when you plan domain controller proximity. If you use application partitions to manage replication of DNS or other data in Active Directory, you might want to add a domain controller from each to the application partition so the information stored in the partition is readily available to users.
Many applications integrate with Active Directory for identity and authentication purposes or for various other reasons. Placing a domain controller in close proximity to these application servers can help facilitate communication from the application to the domain controller, potentially improving application performance.
Optimizing Active Directory replication
The goal of Active Directory replication is to limit convergence, which is the amount of time between when an object is changed and when that change has been communicated to all applicable domain controllers. Latency can be the cause of several common problems within an Active Directory forest:
![]() Authentication failures due to delays in password changes
Authentication failures due to delays in password changes
![]() Authorization errors due to group membership changes
Authorization errors due to group membership changes
![]() Inconsistent application of Group Policy
Inconsistent application of Group Policy
![]() Name-resolution failures for Active Directory–integrated DNS zones
Name-resolution failures for Active Directory–integrated DNS zones
Within a single site, replication latency is typically very low because the network connectivity between domain controllers is both fast and stable. Replication within a site occurs whenever an object is updated to prevent user authentication or authorization from being erroneously denied. Logon failures can occur if a user’s password is updated on one domain controller and the user tries to authenticate by using another domain controller prior to the change being replicated. Because Active Directory sites typically represent a segment of the corporate network with fast and stable connectivity, replication traffic between domain controllers within a site is transmitted without compression. Although the lack of compression does lead to a negligible increase in bandwidth utilization, it reduces the overhead introduced with the compression and decompression process.
Each site contains an NTDS Site Settings node that contains a replication schedule within the site (see Figure 5-4). Because replication occurs automatically whenever an object is modified within the domain, this schedule is used only if no changes are made within the configured time frame. You should not modify this schedule.
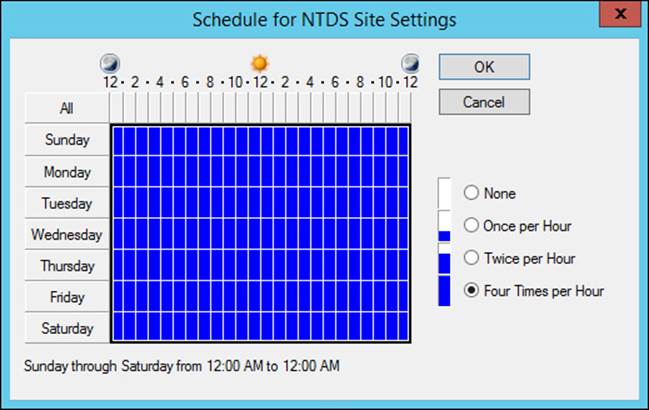
FIGURE 5-4 Replication within a site occurs whenever an object is updated; if no changes are made to objects, the replication occurs based on the site’s replication schedule
The replication topology within a site, which is created automatically by the Active Directory Knowledge Consistency Checker (KCC), is ring-shaped. Object changes are replicated around the ring in both directions, limiting the latency (see Figure 5-5).
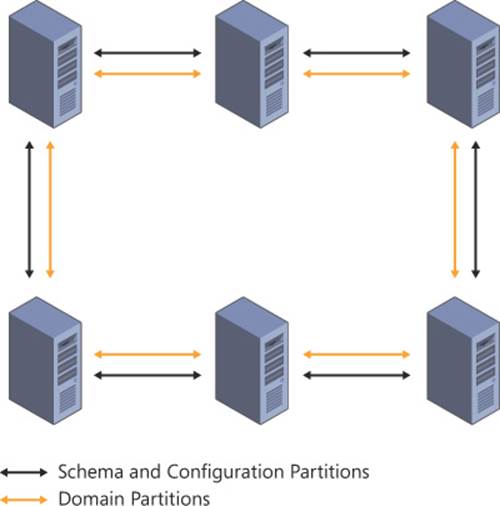
FIGURE 5-5 Within a single site with seven or fewer domain controllers and a single domain, partition replication occurs bidirectionally in a ring until all domain controllers are updated
In sites with more than seven domain controllers in the same domain, the ring can be optimized with a shortcut that splits the ring and reduces the time needed for a replication cycle to complete (see Figure 5-6).
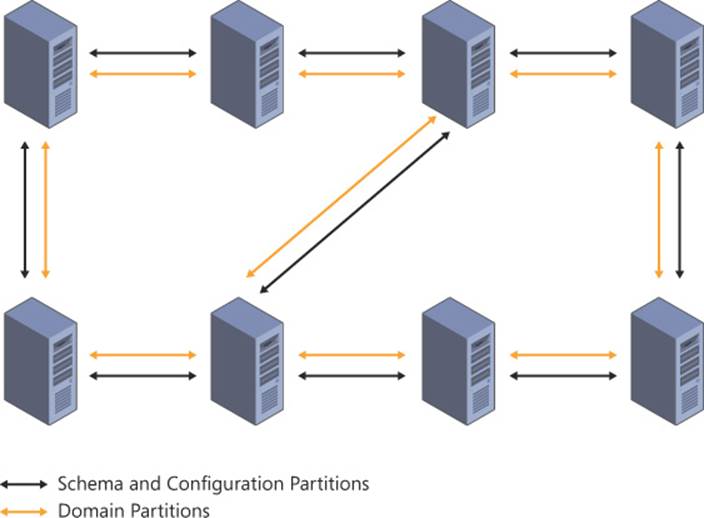
FIGURE 5-6 When a single site contains more than seven domain controllers hosting a single domain, replication is optimized with a shortcut that splits the ring and reduces replication latency
When domain controllers from multiple domains are contained within the same site, the replication topology becomes more complex. Although the common partitions (schema and configuration) are replicated in a ring topology spanning the entire site, separate ring topologies are created for each domain within the site. This configuration, which is automated by the KCC, is shown in Figure 5-7.
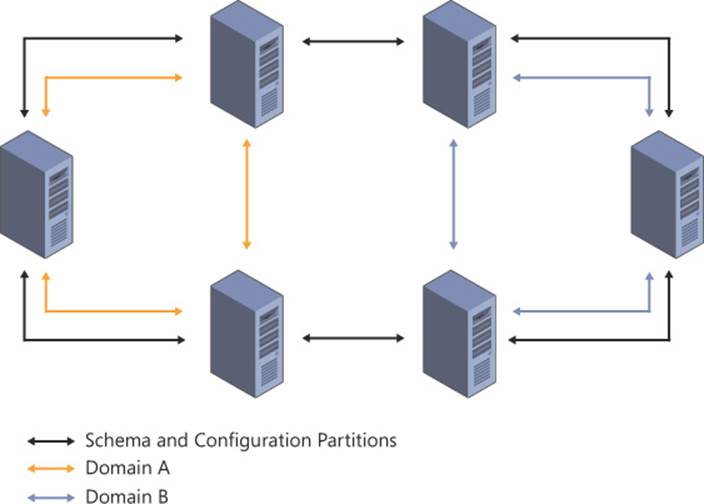
FIGURE 5-7 When multiple domains are contained within a single site, a replication ring topology is created for each partition being replicated
Intersite replication is more complex due to the limitations introduced by network connectivity over long ranges. Active Directory can automatically manage intersite replication, which is recommended for simple site topologies. In more complex site topologies, replication traffic can be managed with site links and site link bridges.
Replication across sites is optimized by the KCC, which analyzes site links and site link bridges to perform replication through the path with the lowest cost. Intersite replication occurs in intervals instead of being triggered when objects are updated. The default interval of 180 minutes can be reduced to 15-minute windows.
Changes to objects in Active Directory are collected by bridgehead servers, which manage intersite replication. Multiple bridgehead servers can be located within a site, depending on the domains and other partitions hosted within that site. Active Directory enables you to define preferred bridgehead servers, indicating which domain controllers you want to use to perform replication. If a preferred bridgehead server is not available (or not available to replicate a particular partition), replication for the directory partitions not hosted by an available preferred bridgehead server cannot complete. It is recommended to enable Active Directory to perform a bridgehead server manually to allow for automatic failover if a bridgehead server becomes unreachable.
Figure 5-8 shows a scenario in which a preferred bridgehead server cannot be used to complete replication for a domain partition. Site 1 contains two preferred bridgehead servers, but the domain partition containing the north.contoso.com domain cannot be replicated using either of these servers. In this scenario, the north.contoso.com domain cannot be replicated between the two sites.
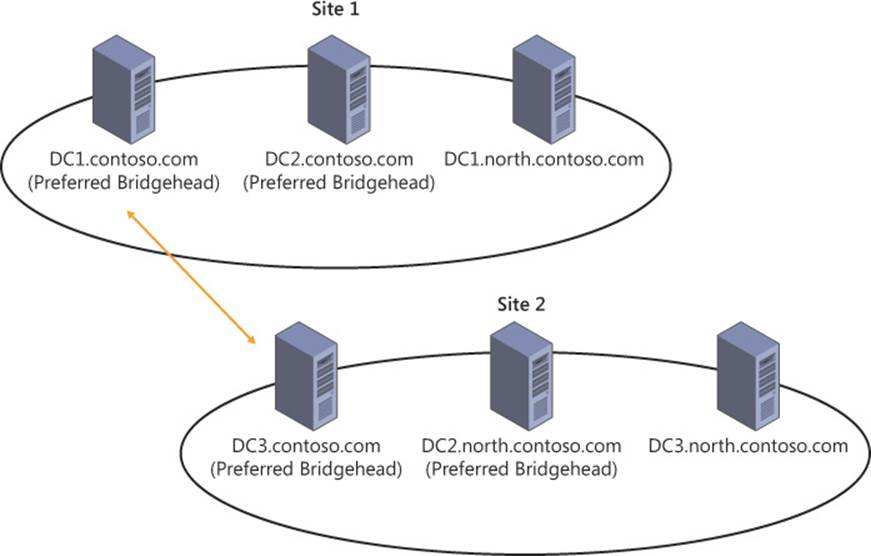
FIGURE 5-8 Preferred bridgehead servers perform replication unless a partition within the site cannot be replicated by using one of these servers
When a replication interval is reached, the replication traffic is compressed and transmitted to a bridgehead server in another site. Because a larger amount of data is being transmitted during each replication cycle for intersite replication, and the network links are typically slower than those within the site, compressing the replication traffic improves efficiency between sites.
Three aspects of intersite replication should always be considered to minimize latency and ensure the most efficient replication strategy. The first aspect is the replication path, which is defined by site links and site link bridges. By default, all site links are bridged, which enables Active Directory to manage these paths for you; but automatic site link bridging can be disabled in the IP transport method properties, which enables you to manage site link bridging manually. The primary goal of using the replication path is to lessen the number of steps required for replication to be completed, thereby limiting replication latency.
Figure 5-9 shows four site links: NY-ATL, NY-LA, DAL-LA, and DAL-ATL. Without bridging, two replication cycles are required before changes from the New York site reach Dallas.
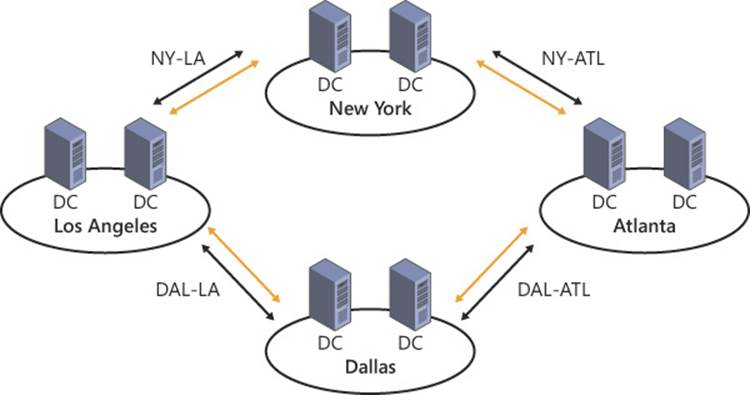
FIGURE 5-9 Site links connect sites for replication and authentication purposes
The second aspect of intersite replication includes the schedule and interval. An Active Directory replication schedule refers to the periods throughout the day when intersite replication is permitted. The replication schedule enables you to control whether you want replication to occur during normal business hours or only during off-peak hours. The replication interval configures how often the replication process occurs within the schedule. If your replication schedule is configured to allow replication throughout the day, and the interval is configured to initiate replication every 15 minutes, replication is triggered 96 times throughout the day.
The third aspect of intersite replication is Active Directory partitions. In an Active Directory forest, several partitions are used to store data (for example, the schema and configuration partitions have a forest-wide replication scope). Each domain in Active Directory is contained within its own partition and is replicated only to domain controllers within that domain. Application directory partitions are replicated to domain controllers that are specifically configured to maintain a copy of that partition.
When you consider all these factors of intersite replication, you see that replication between sites must be configured to limit latency for each Active Directory partition. The path and replication schedule should be managed so that replication requiring multiple steps occurs as quickly as possible. Ensure that domain partitions can be successfully replicated between sites, even if direct links must be created between sites that contain domain controllers from certain domains.
Real world: Administration in complex site topologies
Because intersite replication has a lower frequency than replication within a site, administration problems can occur in corporations that use a centralized management strategy, particularly those with a complex site structure. If a user requires an account unlock or password change, and an administrator resolves the problem in a site other than where the user is located, the changes might not be replicated to the user’s site for some time. Security problems can happen if administrators cannot disable a user’s account and have those changes take effect immediately. These problems can be mitigated by having administrators perform administrative actions on a writable domain controller within the user’s site. Any tools used to manage Active Directory objects (including Active Directory Administrative Center, Active Directory Users and Computers Wizard, and Active Directory cmdlets in PowerShell) can be configured to target a specific domain controller.
Designing site links
Site links are used to configure replication between two or more Active Directory sites. By configuring the cost associated with a site link, you can manage the way replication traffic travels through your site structure. Replication can be optimized and managed using site links, replication frequency, and the replication schedule. Each of these site links is viable only if at least two sites within a site link contain a domain controller hosting a copy of a partition to be replicated. If each of the branch offices shown in Figure 5-10 hosts its own domain, and no domain controllers from those domains exist outside of the site, the partitions hosting those domains are not replicated to the New York site or to the other branches.
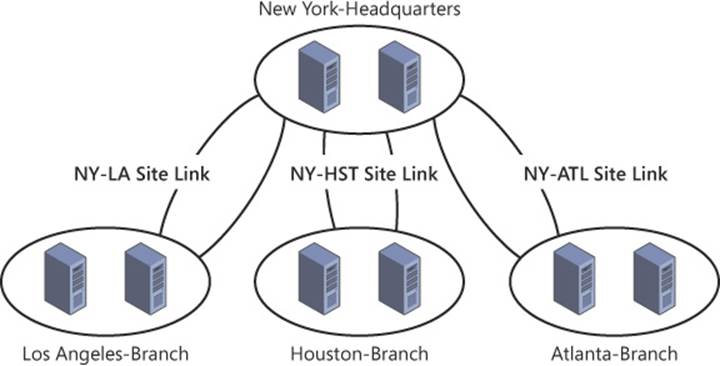
FIGURE 5-10 Site links enable you to shape replication traffic between sites
Site links perform several replication-related tasks. They define which sites can replicate to each other. Each site link contains a cost that is used by the KCC to determine the optimal replication path between sites. Site links also manage the replication schedule and interval, determining which times of day replication traffic is allowed and how frequently replication should be initiated during these windows.
By default, all site links are bridged; they are transitive, and any site can replicate to another site containing a domain controller that hosts a copy of the partition being replicated (assuming that replication schedules coincide). Clearing the Bridge All Site Links check box in the IP or SMTP Inter-Site transports (see Figure 5-11) and configuring site link bridges enables you to manage the sites that can replicate directly.
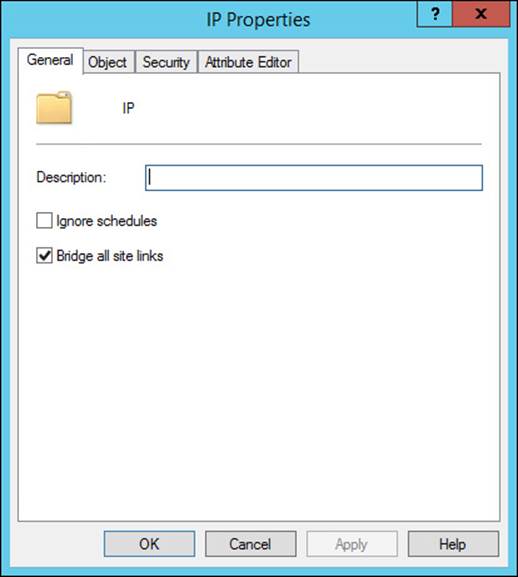
FIGURE 5-11 Properties of the IP Inter-Site transport, showing the Bridge All Site Links check box
Transitivity between site links through site link bridges or the Bridge All Site Links option can significantly reduce replication latency between sites. Although bridging all site links does relinquish a level of manual control over replication traffic, the shape of replication is managed automatically by the KCC. Manual configuration of site link bridges is recommended only for large deployments with a complex site structure.
Two time factors affect intersite replication. The replication schedule within a site link determines when the link can be used for replication and when replication traffic should be held until the next window. The interval determines how often the replication process should be performed during the replication window.
It is important to understand how site link schedules affect transitivity. When two sites containing a domain controller that hosts a copy of the same partition are connected through bridging, they can communicate with each other through a common site when replication on both links is triggered simultaneously. By using site link bridges, you can reduce the number of hops required for replication traffic, thereby reducing latency. Because bridged replication traffic occurs only when replication is triggered simultaneously for two bridged site links, the maximum replication interval for the two bridged site links is the resulting interval for replication traffic travelling across the bridge.
Figure 5-12 illustrates this concept. The NY-ATL and DAL-ATL site links are bridged and have replication frequencies of 30 minutes and 15 minutes, respectively. Every other time the Dallas and Atlanta sites perform replication, the New York and Atlanta sites perform replication simultaneously. The site link bridge enables replication to travel between New York and Dallas in a single replication session.
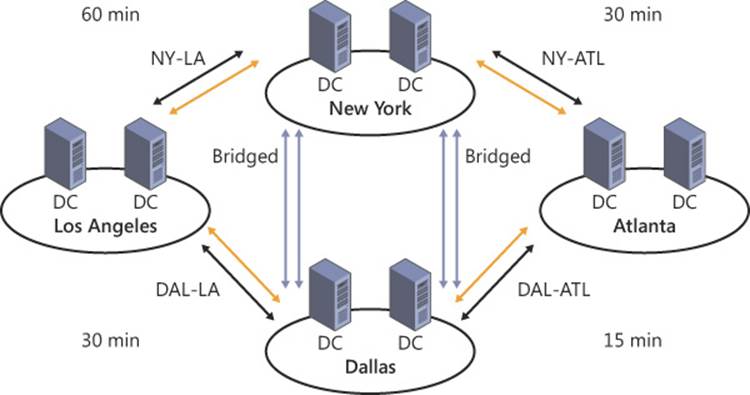
FIGURE 5-12 The frequency of bridged replication traffic is the highest value of the bridged site links
If the shared partner site is unavailable during the replication window, or if no domain controller hosting the partition is available, the two sites can communicate directly. Remember to consider time zone differences when you create replication schedules.
To illustrate these concepts, consider the following scenarios. An organization has three sites: corporate headquarters in New York and branch offices in Los Angeles and Seattle. Site links are created between each branch office and the New York headquarters site.
When the site links are not bridged, changes made in the Los Angeles site require two steps to complete replication to Seattle, regardless of the synchronization schedules (see Figure 5-13). This multistep process also occurs when the two site links are bridged but replication schedules do not coincide.
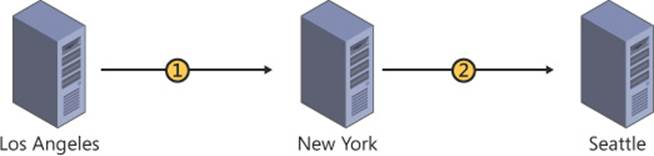
FIGURE 5-13 Site links without a site link bridge can result in multiple steps
If the site links are bridged, and replication for the two links occurs simultaneously (see Figure 5-14), replication traffic is passed through the common site in a single replication pass. Even if the common replication partner is unavailable or does not contain a domain controller hosting a copy of the partition being replicated, the two branch sites can replicate directly through the site link bridge.
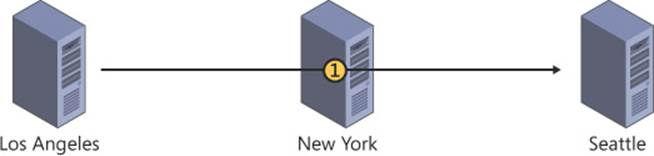
FIGURE 5-14 Replication across a site link bridge can be accomplished in a single replication cycle
When site links are bridged, the sum of the site link costs in the replication path is used to calculate the aggregate cost that determines the replication path. Site links must contain a common partner site to be bridged.
Several strategies can be used to perform replication between sites in large and complex topologies. A couple of factors should be considered to determine which of these strategies best fits your organization. The first factor is how your domain structure matches up with your site structure. Some Active Directory partitions, such as the schema and configuration partitions, must be replicated throughout the entire forest. Domain partitions have to be replicated only to sites with domain controllers within that domain. Your site link strategy should be designed specifically to optimize replication for partitions.
Figure 5-15 shows an example of replication scopes for partitions in a forest. The schema and configuration partitions must be replicated throughout the forest, but each domain in the forest has to be replicated only among the three sites represented by that domain. The partitions replicated across the forest are modified with less frequency than domain partitions, which is another factor that you should think about.
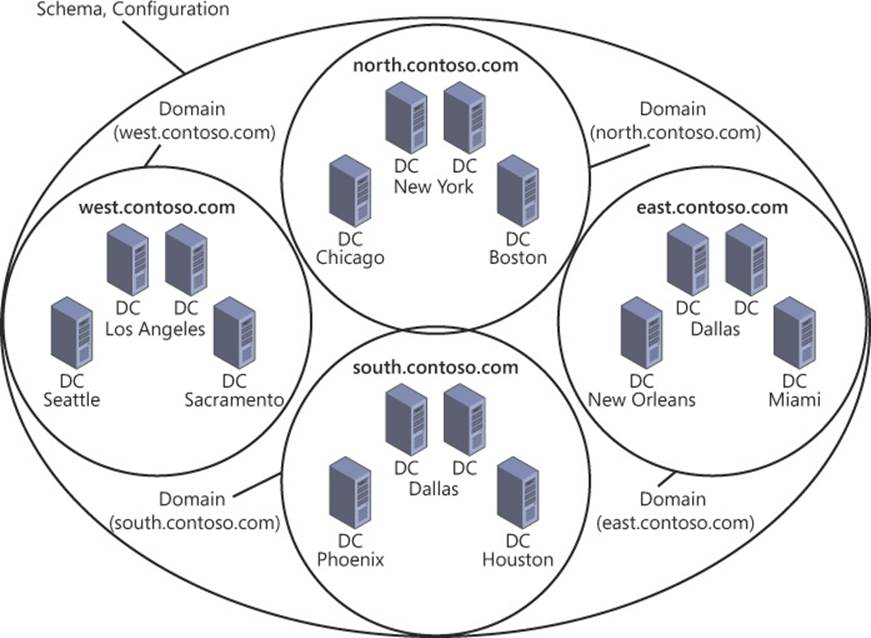
FIGURE 5-15 The replication scope of partitions in Active Directory should be considered when planning a replication strategy
Another factor is where changes to Active Directory objects occur (see Figure 5-16). For example, if Active Directory objects are centrally managed, you might need to ensure that replication from the central site occurs quickly to branch sites and be less concerned about replication coming from the branch sites going out to the rest of the forest. As mentioned throughout this chapter, the primary goal is to reduce latency when replicating object changes between sites.
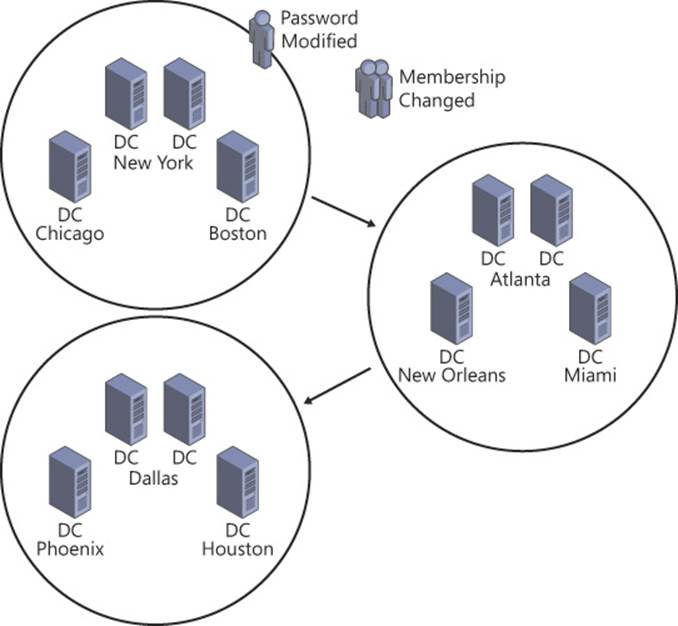
FIGURE 5-16 Administrative actions performed in one site, such as changes to user passwords or group membership, must be replicated before they are reflected in another site
 Exam Tip
Exam Tip
Site links and site link bridges form the basis of managing intersite replication traffic in Active Directory. Knowing the process to create and configure these objects and their design is important for the exam.
Identifying and resolving Active Directory replication conflicts
In large networks, particularly those spanning wide area network (WAN) links, fluctuations in network connectivity can be expected. Active Directory handles most network problems transparently by resuming replication after connectivity returns, but occasionally troubleshooting is necessary. It is also important to proactively monitor Active Directory replication to optimize the replication process or to identify errors before they become significant problems.
The repadmin command enables you to monitor and test replication. Table 5-1 lists the repadmin commands that can be used to monitor and troubleshoot Active Directory replication.
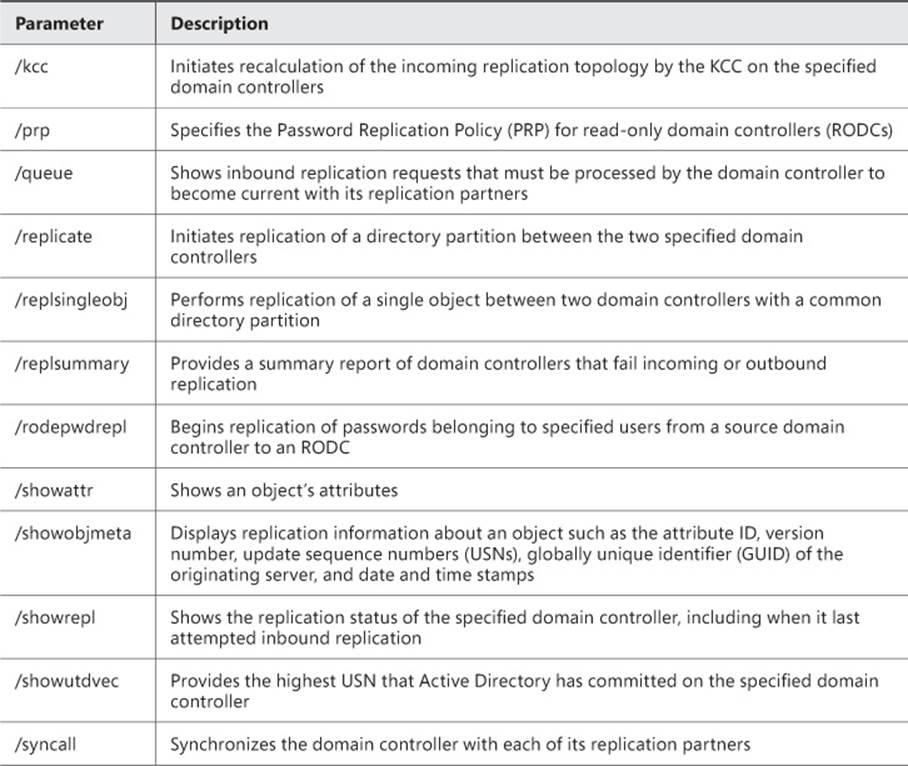
TABLE 5-1 Repadmin commands
Because of the tight relationship between Active Directory and DNS, many replication errors are actually related to problems in DNS. The dcdiag command-line tool enables you to perform a number of tests related to DNS name resolution and replication. To specifically test replication between DNS servers, you can use the dcdiag /test:replications command. The dcdiag /test:VerifyReplicas command can be used to verify that application directory partitions are properly replicated.
Active Directory replication errors are logged in the Directory Service log of the Event Viewer. Best practice dictates periodically monitoring the Directory Service log for replication errors. The Directory Service log is one of the first places you should look if you experience replication problems.
 Exam Tip
Exam Tip
You should be familiar with both the repadmin and dcdiag commands for the exam.
![]() Thought experiment: Planning an Active Directory replication strategy
Thought experiment: Planning an Active Directory replication strategy
In this thought experiment, apply what you’ve learned about this objective. You can find answers to these questions in the “Answers” section at the end of this chapter.
Your consulting firm has been asked to review the physical Active Directory topology of a client and make adjustments to its replication strategy to meet some new requirements. The client company has offices throughout the country, with multiple offices in most states.
1. Your client wants to limit replication traffic to an hour before and an hour after business hours. Due to time zone differences, the client has not been able to implement this requirement without a high amount of management workload. How could the client implement these changes with minimal effort?
2. Any changes to the Active Directory domain structure or schema are managed by an administrative team at corporate headquarters. The client wants to ensure that these types of changes occur as efficiently as possible. How could you ensure that the administrative team at corporate headquarters can make changes to the Active Directory domain and schema structure with the greatest efficiency?
Objective summary
![]() Read-only domain controllers (RODCs) can be used when a domain controller cannot be physically secured.
Read-only domain controllers (RODCs) can be used when a domain controller cannot be physically secured.
![]() The physical placement of domain controllers that perform operations master roles should be carefully planned to improve efficiency in tasks such as password changes and schema modifications.
The physical placement of domain controllers that perform operations master roles should be carefully planned to improve efficiency in tasks such as password changes and schema modifications.
![]() Site links and site link bridges enable you to change the shape and schedule of intersite Active Directory replication.
Site links and site link bridges enable you to change the shape and schedule of intersite Active Directory replication.
![]() Replication problems can be diagnosed by using the repadmin and dcdiag command-line tools.
Replication problems can be diagnosed by using the repadmin and dcdiag command-line tools.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. Which scenario is the best fit for a shortcut trust?
A. Users are in a site that does not contain a domain controller, which results in a subpar authentication performance.
B. Cross-domain authentication needs to be improved from one domain to another specific domain.
C. Authentication requests to the forest root domain need to be optimized.
D. Replication traffic needs to be prioritized between two specific sites.
2. After configuring site links between three sites (with only one site being contained in both site links), you notice that objects are not being replicated between the two sites that aren’t directly connected, even after multiple replication intervals. How could this happen?
A. The site links are not bridged.
B. The site links do not have overlapping schedules.
C. The Bridge All Site Links option is disabled.
D. The central site does not share the directory partition containing the objects to be replicated.
3. Which option best describes replication within a single site?
A. Domain controllers from each domain contained within the site form individual ring topologies.
B. Multiple overlapping bidirectional ring topologies are created, replicating each directory partition contained within the site between the domain controllers hosting a copy of that partition.
C. All domain controllers in the site perform replication in a bidirectional ring topology.
D. The replication shape is managed by the KCC, based on the configured site link topology.
4. Users complain that they cannot use their accounts after password resets by the corporate help desk. They state that their accounts become usable after a period of approximately one hour. What might cause this?
A. Replication latency has resulted in the users’ passwords not being written to the domain controller that they are using to authenticate.
B. The users are attempting to authenticate in a site without a domain controller.
C. The users are connecting at a site without a domain controller for the domain containing their user object.
D. The domain controller performing the PDC emulator master role cannot be reached.
5. How can latency in intersite replication be reduced? (Choose all that apply.)
A. Lessen the number of hops required to complete replication.
B. Lower the replication interval for site links.
C. Place a domain controller from each domain in every site.
D. Place a domain controller from the forest root domain in every site.
6. After selecting two domain controllers as preferred bridgehead servers, you notice that some objects within the site are not being updated properly when changes are made in another site. What might be causing this behavior?
A. The preferred bridgehead servers are not performing the operations master roles.
B. A domain controller containing the objects being modified is not available in the local site.
C. The Active Directory objects have not been modified within the local site.
D. The preferred bridgehead servers do not host a copy of all directory partitions contained within the site.
7. What conditions must be met for replication to occur across a site link bridge? (Choose all that apply.)
A. Preferred bridgehead servers must be selected.
B. A common site between the bridged site links must be available for replication.
C. A shared directory partition is necessary.
D. Simultaneous replication intervals must occur.
8. After you configure site links and site link bridges, what other step must you complete to constrain replication traffic to these defined site links and site link bridges?
A. Clear the Bridge Of All Site Links option in the Inter-Site Transport node.
B. Reboot the domain controller performing the infrastructure master role.
C. Delete the DEFAULTIPSITELINK site link.
D. Ensure that the changes were not made on a read-only domain controller.
9. What command is used to show inbound replication requests?
A. repadmin /showrepl
B. repadmin /queue
C. dcdiag /test:Replications
D. dcdiag /test:VerifyReplicas
10. Which command can be used to force replication of an object between two domain controllers?
A. repadmin /kcc
B. repadmin /replsingleobj
C. repadmin /replicate
D. repadmin /queue
Objective 5.2: Design a domain controller strategy
A major aspect of designing the physical structure of Active Directory is to ensure that clients and applications can always perform Active Directory tasks such as authentication in the most efficient way. Many of these functions can be performed by any domain controller, but some occur only when the client can communicate with a specific set of domain controllers. These domain controller roles, which are critical to the day-to-day operation of an Active Directory forest, require planning for placement within your enterprise. You should also be able to recognize the symptoms of one of these roles being unavailable to Active Directory.
Each of the tools available to increase performance of a particular action between client and domain controller has side effects or makes other changes to the behavior typically expected from a domain controller. Implementing these solutions in the wrong way can increase replication traffic between sites without offering any benefit for authentication. Understanding the impact of implementing changes to domain controllers helps you properly plan and design a domain controller strategy.
Domain controllers contain the information necessary to access resources throughout your corporate network. Security for domain controllers should start with the physical hardware and continue to the permissions used to control access to Active Directory resources. Some flexibility exists for configuring domain controllers, so you can delegate permissions to subordinate administrators or even deploy domain controllers in locations with limited physical security. You should understand the potential risks of having a domain controller compromised and what steps can be taken to mitigate those risks before and after a compromise occurs.
This objective covers how to:
![]() Use the global catalog
Use the global catalog
![]() Optimize operations master roles
Optimize operations master roles
![]() Plan for read-only domain controller (RODC) placement
Plan for read-only domain controller (RODC) placement
![]() Understand the partial attribute set
Understand the partial attribute set
![]() Use cloned domain controllers
Use cloned domain controllers
![]() Choose domain controller placement
Choose domain controller placement
Using the global catalog
The global catalog contains partial information for all objects within the entire forest. Domain controllers that function as global catalog servers contain full versions of objects within their domain and partial read-only copies of objects from other domains. Global catalog servers provide improved performance when performing searches for Active Directory objects. In these cases, the request to find the Active Directory object can be answered by a global catalog server in the local domain rather than being forwarded outside the domain.
Some circumstances in which the global catalog can be used to improve interaction with Active Directory include these:
![]() When a user attempts to log on using a User Principal Name (UPN) such as johnsmith@contoso.com, a global catalog server can be used to resolve the UPN.
When a user attempts to log on using a User Principal Name (UPN) such as johnsmith@contoso.com, a global catalog server can be used to resolve the UPN.
![]() When a user who is a member of a universal group from another domain logs on.
When a user who is a member of a universal group from another domain logs on.
![]() When a user performs a lookup using an Exchange global address list (GAL).
When a user performs a lookup using an Exchange global address list (GAL).
Without a global catalog server, each of these events has to traverse the domain hierarchy and the Active Directory site structure to locate a domain controller capable of performing the required lookup. Figure 5-17 shows the difference between having to traverse the Active Directory structure (User 1) and having a global catalog server available within the local site (User 2).
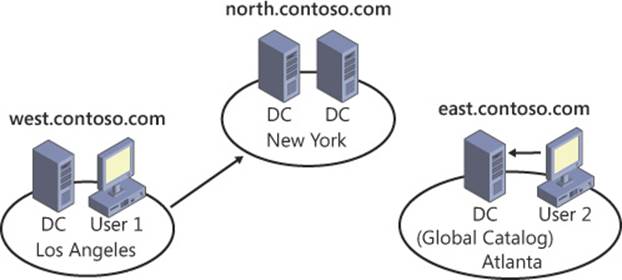
FIGURE 5-17 Deploying a global catalog server can greatly reduce the traffic required to authenticate a user or perform queries for Active Directory objects
A domain controller is configured as a global catalog server within the NTDS Settings properties for the domain controller in Active Directory Sites and Services (see Figure 5-18).
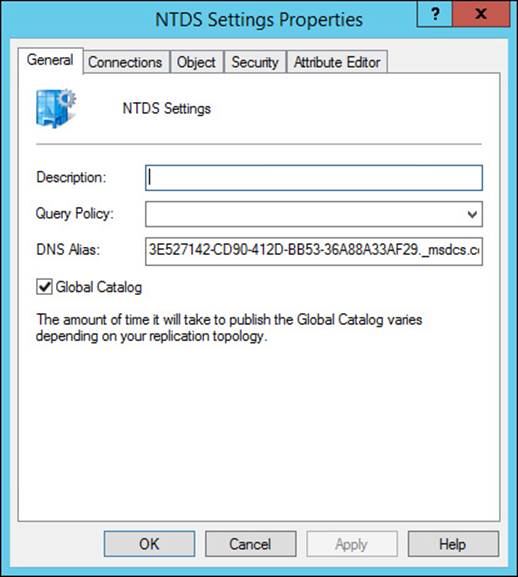
FIGURE 5-18 The global catalog can be enabled on a domain controller through the NTDS Settings properties for the domain controller
One issue with using global catalog servers is the increased amount of replication required, particularly in large forests with many domains. Replication traffic can be limited by implementing a select number of global catalog servers in each site. Finding a balance between replication and the traffic required to find Active Directory objects can be the most difficult aspect of managing the physical structure of Active Directory.
Global catalog servers are of no use in Active Directory forests that consist of a single domain. In a single-domain forest, each domain controller already contains a full writable copy of the entire forest, making the global catalog unnecessary. Large forests with a complex domain structure get the most benefit from deploying global catalog servers, but large forests also exaggerate the increased replication requirements of the partial attribute set.
Optimizing operations master roles
Domain controllers that perform operations master roles, also known as Flexible Single Master Operations (FSMO) roles, manage critical aspects of Active Directory. Three operations roles and two forest-wide operations master roles exist in each domain. Each role and its scope are described in Table 5-2.
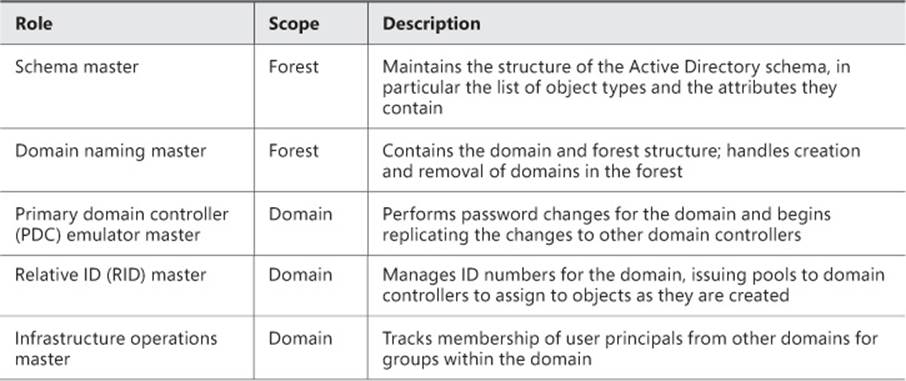
TABLE 5-2 Operations master roles in Active Directory
When an operations master becomes unavailable, different symptoms occur, depending on the role. When the schema master is unavailable, any attempted modifications to the schema fail. Additio n and removal of domains from the forest fail if the domain-naming master is offline. Problems with the RID master result in domain controllers being unable to create new objects after their RID pool is exhausted. Problems with users updating their passwords can be attributed to problems with the PDC emulator master. If the infrastructure master becomes unavailable, problems related to interdomain group membership can occur. Remember that problems related to a missing or unavailable operations master might not be noticed for an extended period of time.
Most actions on Active Directory objects can be accomplished using almost any domain controller. Because certain actions require access to a domain controller performing an operations master role, those servers should be carefully placed to optimize the performance of those actions (they should have network connectivity that is both fast and stable). Depending on the workload involved with handling an operations master role, the domain controllers performing these roles might require additional resources to support the additional workload.
 Exam Tip
Exam Tip
You will probably get at least one question on operations master roles in the 70-413 exam. You should know which roles are handled at the forest and domain levels and what each role does for Active Directory.
Planning for read-only domain controller (RODC) placement
Although the primary purpose for RODCs is security (protecting Active Directory from compromised passwords or changes submitted by a rogue domain controller), their use can also have other benefits. Much of the RODC configuration process, such as using the Password Replication Property (PRP) and administrative delegation, is accomplished through the RODC computer object in Active Directory (see Figure 5-19).
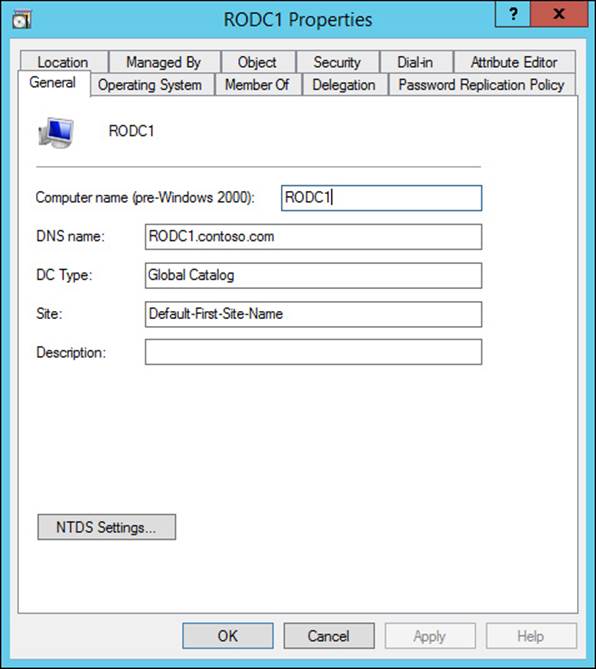
FIGURE 5-19 The properties window for an RODC in Active Directory
The first security benefit of implementing an RODC is that it contains a read-only copy of the Active Directory partitions it hosts, including the domain partition. RODCs are designed to be deployed in environments where the domain controller cannot be properly physically secured. Because the RODC does not perform outgoing replication, there is no potential for a physically compromised domain controller to have objects inserted or modified and then replicated to the rest of the domain. Because all partitions are read-only, RODCs do not perform outgoing replication, so any changes to Active Directory objects are immediately forwarded to a writable domain controller, not replicated from the stored partition. A side benefit of this configuration is that replication traffic is more limited when an RODC is used.
Another concern with domain controllers in an insecure location is the potential for passwords or other sensitive information contained within the Active Directory partitions stored on the domain controller to be compromised. RODCs use PRP, which prevents passwords from being cached by default, limiting the capability of malicious users from performing password attacks on a compromised RODC. The Filtered Attribute Set (FAS) can also be configured to manage Active Directory attributes that are replicated to RODCs.
If an RODC is stolen or otherwise compromised, Active Directory immediately remediates the possibility of cached passwords being compromised or the RODC being reintegrated into Active Directory. Deleting the computer object for the RODC triggers a window (shown in Figure 5-20) that asks if you want to reset passwords for user or computer accounts that were cached on the RODC. You can also export a list of the accounts that were cached on the RODC, enabling you to proactively communicate with users who might be affected.
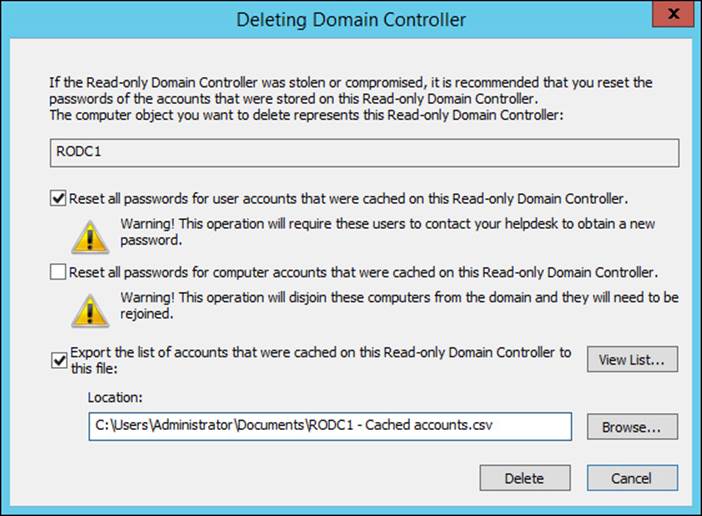
FIGURE 5-20 When deleting the computer object for an RODC, you can reset passwords for accounts cached on the RODC
Domain controller management is typically a job for high-level administrators such as Domain or Enterprise admins. When a domain controller is deployed, any local users and groups are removed, and access to the console is limited to the Domain Admins group. With RODCs, you can delegate control to local administrators to install drivers and updates. Local users can log on to the console of an RODC without having membership in a group that would provide administrative access to objects within Active Directory. Logging on to an RODC with a member of the Domain Admins group is not recommended.
Although loss of connectivity to a writable domain controller does not preclude an RODC from authenticating users, some actions (such as password changes and domain joins) require access to a writable domain controller.
Understanding the partial attribute set
The global catalog contains copies of every object in the domain, but only a subset of the attributes associated with those objects (primarily required attributes or those typically used for searches). You can customize this set of attributes, known as the partial attribute set, to meet the needs of your organization.
Many applications that modify the Active Directory schema also make use of the partial attribute set. For example, Microsoft Exchange Server uses the partial attribute set to contain fields used to perform searches of the GAL.
To configure the partial attribute set, the Active Directory Schema Microsoft Management Console (MMC) snap-in, must be enabled. It relies on the schmmgmt.dll file, which must be registered by running the regsvr32 schmmgmt.dll command from an elevated command prompt. Once enabled, launch an MMC window and add the Active Directory Schema snap-in. Because this management console enables you to make changes directly to the Active Directory schema, be careful when you make any changes. Changes should also be made on the domain controller performing the schema operations master role.
To modify the partial attribute set, navigate to the Attributes folder, locate the desired attribute, and select the Replicate This Attribute To The Global Catalog check box in the attribute properties (see Figure 5-21). After a change is applied to the partial attribute set, both the schema partition and the partial attribute set have to be replicated before the changes are available throughout the enterprise.
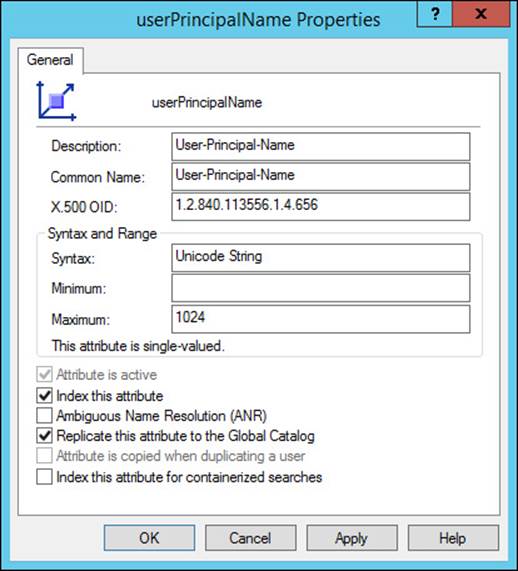
FIGURE 5-21 Attributes can be added to the partial attribute set with the Active Directory Schema snap-in
You can use the Get-ADObject PowerShell cmdlet to retrieve a list of attributes in the partial attribute set by querying the isMemberOfPartialAttributeSet flag, as shown in this example:
Get-ADObject -SearchBase "cn=Schema,cn=Configuration,dc=contoso,dc=com" -LDAPFilter "(is
MemberOfPartialAttributeSet=TRUE)"
Using cloned domain controllers
Windows Server 2012 introduced improved support for virtual domain controllers. Although they have been supported for some time, there was potential for damaging Active Directory if an old version of a virtual domain controller was introduced to the domain with a snapshot or backup. Windows Server 2012 Hyper-V hosts support a new identifier known as the VM-GenerationID, which is compared to the value in msDS-GenerationID before any changes are made to Active Directory.
The other major change for virtual domain controllers in Windows Server 2012 is the capability to quickly clone virtual machines (VMs) to rapidly deploy multiple domain controllers.
To clone a virtual domain controller, follow these steps:
1. Ensure that the domain controller is a member of the Cloneable Domain Controllers group.
2. Identify and remove any applications or services that do not support cloning, such as the following:
![]() Active Directory Certificate Services (AD CS)
Active Directory Certificate Services (AD CS)
![]() DHCP
DHCP
![]() Active Directory Lightweight Directory Services (AD LDS)
Active Directory Lightweight Directory Services (AD LDS)
3. Create a configuration file for the clone operation using the New-ADDCCloneConfigFile cmdlet.
4. After the config file is created, the virtual domain controller is cloned by exporting and then importing the VM.
Applications and services that do not support cloning can be identified with the Get-ADDCCloningExcludedApplicationList cmdlet, which should be run on the virtual domain controller being used as the source. The New-ADDCCloneConfigFile cmdlet enables you to configure options such as computer name, IP address, and DNS information (see Figure 5-22).
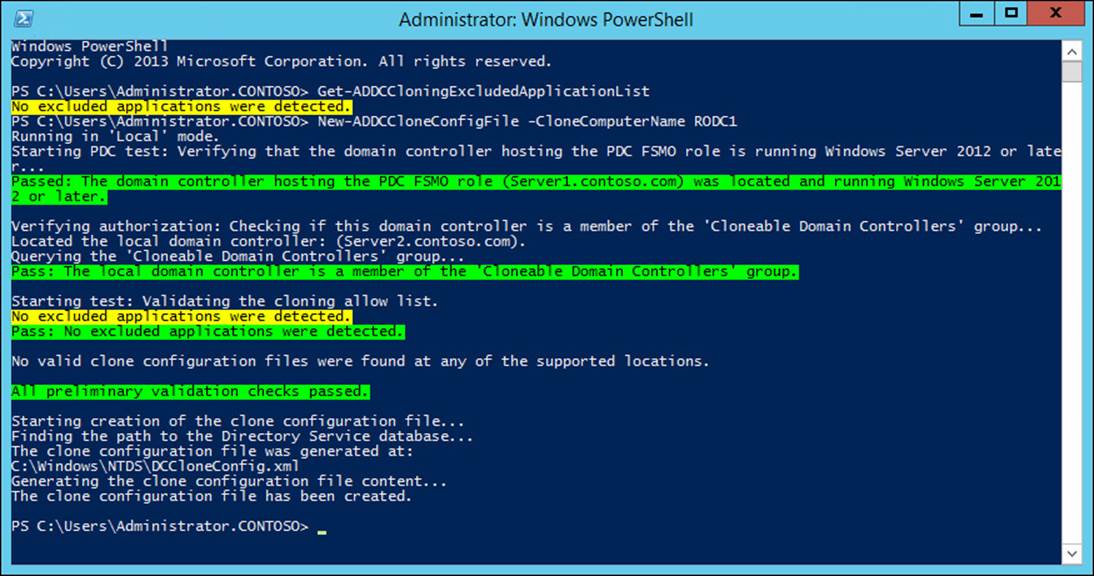
FIGURE 5-22 Creating the configuration file for a cloned domain controller
After the configuration file is created, the VM can be exported. Upon importing the VM as a copy, which generates a new unique ID, the cloning process takes place on the first startup (as shown in Figure 5-23).
FIGURE 5-23 The domain controller cloning process happens when the cloned VM is first started
Note: Cloning the Computer Account of the Domain Controller
Because the computer account of the domain controller is being cloned, the password for the new virtual domain controller must be set. The domain controller operating as the PDC emulator master for the domain must be available for the clone operation to complete.
 Exam Tip
Exam Tip
Virtual domain controllers and domain controller cloning are new and improved in Windows Server 2012 and Windows Server 2012 R2, making them good candidates for the exam. You should know the steps to take to clone a domain controller as well as the new features that make virtual domain controllers a more realistic proposition in Windows Server 2012.
Choosing domain controller placement
Regional domain controllers should be placed strategically to provide optimal authentication performance for domain clients within the physical region. Although domains are not always tied to regions, consider how the two structures compare when you plan domain controller placement. In some site topologies, it might be beneficial to deploy domain controllers from each domain to regional hubs, which streamlines replication to branch offices and provides optimal authentication performance.
Security should be a primary concern for domain controller placement. Ensure that domain controllers are not placed in an area where their physical security can be compromised. RODCs should be considered for locations that lack necessary physical security. When RODCs are used, their replication limitations should be taken into account.
In multidomain forests, global catalog servers can be used to improve authentication performance for users from other domains in the forest not available within the local site. Placement of global catalog servers must balance the need for optimized authentication with the extra cost associated with increased replication traffic. Sites or regions with large numbers of users are typically good candidates for global catalog servers as authentication performance becomes a higher priority.
The administration and management of domain controllers should be a consideration for placement. Although domain controllers can be managed remotely, you might want to ensure that a local management group can perform the necessary management tasks of maintaining local domain controllers.
![]() Thought experiment: Designing a domain controller deployment strategy
Thought experiment: Designing a domain controller deployment strategy
In this thought experiment, apply what you’ve learned about this objective. You can find answers to these questions in the “Answers” section at the end of this chapter.
Your company has been experiencing seemingly unrelated problems with the corporate network and has asked you to help identify and correct the root problems. The chief security officer (CSO) of your company also has some concerns over the configuration of Active Directory and wants you to look at some areas that might be vulnerable.
1. Your company is in the middle of implementing an application that integrates closely with Active Directory, even creating custom fields on some object types. During this integration process, the installation was cancelled due to performance issues. What might be causing these performance issues? How can you resolve the problem?
2. Some domains outside of corporate headquarters are experiencing performance degradation when gaining access to resources using membership in groups from other domains. What is the likely cause of these performance problems? Is there any way to improve performance in these scenarios?
3. The CSO is concerned that some of the custom fields being added to Active Directory objects by the new application might contain sensitive information and should not be replicated throughout the forest. You are worried that these fields might be replicating to global catalog servers you intend to implement. How can you prevent specific fields from being replicated to global catalog servers?
4. The CSO is also worried about domain controllers located in areas that do not meet the security requirements of the company. What capabilities do you have at your disposal to reduce the risk associated with a compromised domain controller? What additional benefits would this solution provide?
Objective summary
![]() Global catalog servers contain partial copies of every object in the Active Directory forest, enabling improved performance in cross-domain authentication and authorization.
Global catalog servers contain partial copies of every object in the Active Directory forest, enabling improved performance in cross-domain authentication and authorization.
![]() The object attributes included in the global catalog, which are known as the partial attribute set, can be configured using the Active Directory Schema snap-in.
The object attributes included in the global catalog, which are known as the partial attribute set, can be configured using the Active Directory Schema snap-in.
![]() Domain controllers that perform operations master roles handle specific tasks that require management by a single domain controller.
Domain controllers that perform operations master roles handle specific tasks that require management by a single domain controller.
![]() The PDC emulator master, RID master, and infrastructure master roles are performed within each domain.
The PDC emulator master, RID master, and infrastructure master roles are performed within each domain.
![]() Schema master and domain-naming master roles are handled at the forest level.
Schema master and domain-naming master roles are handled at the forest level.
![]() RODCs, which are helpful in environments with decreased physical security, enable delegation of some administrative tasks.
RODCs, which are helpful in environments with decreased physical security, enable delegation of some administrative tasks.
![]() Windows Server 2012 improves support for virtual domain controllers, including the safe use of snapshots and the capability to quickly clone virtual domain controllers.
Windows Server 2012 improves support for virtual domain controllers, including the safe use of snapshots and the capability to quickly clone virtual domain controllers.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. What domain controller capability can improve cross-domain authentication?
A. RODC
B. Domain naming master
C. Global catalog server
D. Infrastructure master
2. Which operations master roles are performed at the forest level? (Choose all that apply.)
A. PDC emulator master
B. Domain naming master
C. Infrastructure master
D. Schema master
3. Which operations master role is responsible for managing password changes at the domain level?
A. Schema master
B. Infrastructure master
C. PDC emulator master
D. RID master
4. What type of domain controller is best used for scenarios in which the domain controller cannot be physically secured?
A. Global catalog
B. Schema master
C. Infrastructure master
D. RODC
5. Which features are benefits of an RODC? (Choose all that apply.)
A. Read-only copy of Active Directory
B. Improved cross-domain authentication
C. Capability to limit password caching
D. Support for local administrator access
6. Which Active Directory feature makes use of the partial attribute set?
A. RODC
B. Domain controller cloning
C. Global catalog
D. Intersite replication
7. In what ways can the partial attribute set be modified? (Choose two.)
A. Adding a new domain to the forest
B. Deploying an application that integrates with Active Directory
C. Deploying a global catalog server
D. Manually modifying the schema using the Active Directory Schema snap-in
8. What are the steps to clone a virtual domain controller? (Choose all that apply.)
A. Add the source domain controller to the Cloneable Domain Controllers group.
B. Upgrade the domain to the Windows Server 2012 functional level.
C. Ensure that the source domain controller is not performing an operations master role.
D. Create a config file using the New-ADDCCloneConfigFile cmdlet.
9. Which of the following services do not support cloning? (Choose all that apply.)
A. AD CS
B. DHCP
C. Active Directory Domain Services (AD DS)
D. DNS
10. Which operations master role is critical for cloning a virtual domain controller?
A. Domain naming master
B. RID master
C. PDC emulator master
D. Infrastructure master
Objective 5.3: Design and implement a branch office infrastructure
The most complex aspect of implementing the physical structure of Active Directory can often be incorporating branch offices. In many enterprises, branch offices are small or insecure (or have a limited number of users). The cost associated with supporting a domain controller in numerous sites without large user bases can be prohibitive. Not only do you have to consider the cost of deploying a domain controller but also the costs of the infrastructure to support Active Directory. Branch offices typically require a reliable Internet connection, DNS, and DHCP support, and maintaining these items must be considered in planning. With the additional probability that an organization might have hundreds or thousands of branch offices, implementing and maintaining this infrastructure can become a complex endeavor.
Because of size and location, branch offices are often vulnerable, and deploying domain controllers in an environment in which the security is subpar can be dangerous. For these scenarios, RODCs are recommended because they provide several security mechanisms to protect an Active Directory forest in case of compromise.
Branch offices are often at the farthest point of a site topology, making them particularly susceptible to replication latency and an area of concern for authentication. Due to the limitations associated with placing a domain controller in a branch office, placing more than one domain controller to support multiple domains is usually not possible. Active Directory includes several features that alleviate some of the problems involved with having expansive site structures (some of them are discussed in this section).
Users in branch offices often require access to corporate resources that are located in another site. Any optimization you can provide to branch office users to minimize wait times or maximize availability increases productivity and saves your company money. Through the use of BranchCache, you can optimize WAN connectivity by using client- or server-based storage to retain a locally cached copy of corporate resources in other sites. This section discusses the steps required to implement BranchCache deployments in branch offices and enable content servers to support BranchCache clients.
This objective covers how to:
![]() Deploy RODCs
Deploy RODCs
![]() Implement Universal Group Membership Caching (UGMC)
Implement Universal Group Membership Caching (UGMC)
![]() Use the global catalog
Use the global catalog
![]() Support DNS and DHCP in the branch office
Support DNS and DHCP in the branch office
![]() Deploy BranchCache
Deploy BranchCache
![]() Implement confidential attributes
Implement confidential attributes
![]() Delegate administration
Delegate administration
![]() Modify the filtered attributes set
Modify the filtered attributes set
![]() Configure Password Replication Policy
Configure Password Replication Policy
![]() Configure hash publication
Configure hash publication
Improving branch office authentication
In many scenarios, replication and authentication performance with branch offices can be costly due to connectivity requirements, hardware cost, and maintenance. Deploying domain controllers and the infrastructure to support them can also be expensive, particularly when multiple branch offices must be supported. The security of domain controllers in branch offices can be questionable because small offices might not have the physical security capabilities often found in large corporate datacenters.
The features available to meet the needs of branch offices help improve security and authentication performance, but can have a cost in the form of increased network traffic for replication.
Deploying RODCs
The capabilities and benefits offered by RODCs have been discussed in some length. Although the security benefits provided by an RODC are the primary reason for their use, the capability to delegate local administrative rights and reduce replication traffic is another good reason to deploy RODCs in branch offices.
Several requirements exist for RODCs in your enterprise. First, the forest functional level must be Windows Server 2003 or higher. At least one writable domain controller running Windows Server 2008 or higher also must be deployed to the domain before an RODC can be deployed, and this domain controller must also be a DNS server for the domain.
RODCs can be deployed by using either PowerShell or wizard-based deployments. Much of the process is identical to deploying a writable domain controller. Several steps in an RODC deployment deal with the security features that set it apart, such as delegation of management and the PRP.
The first step of deploying an RODC is to prepare the forest using the adprep /rodcprep command, after which the Active Directory Domain Services (AD DS) role can be installed by using either the Add Roles and Features Wizard or the Install-WindowsFeature PowerShell cmdlet. After the role is installed, the RODC can be deployed through the Active Directory Domain Services Configuration Wizard.
To deploy an RODC instead of a writable domain controller, the Read Only Domain Controller (RODC) option must be selected on the Domain Controller Options page (see Figure 5-24).
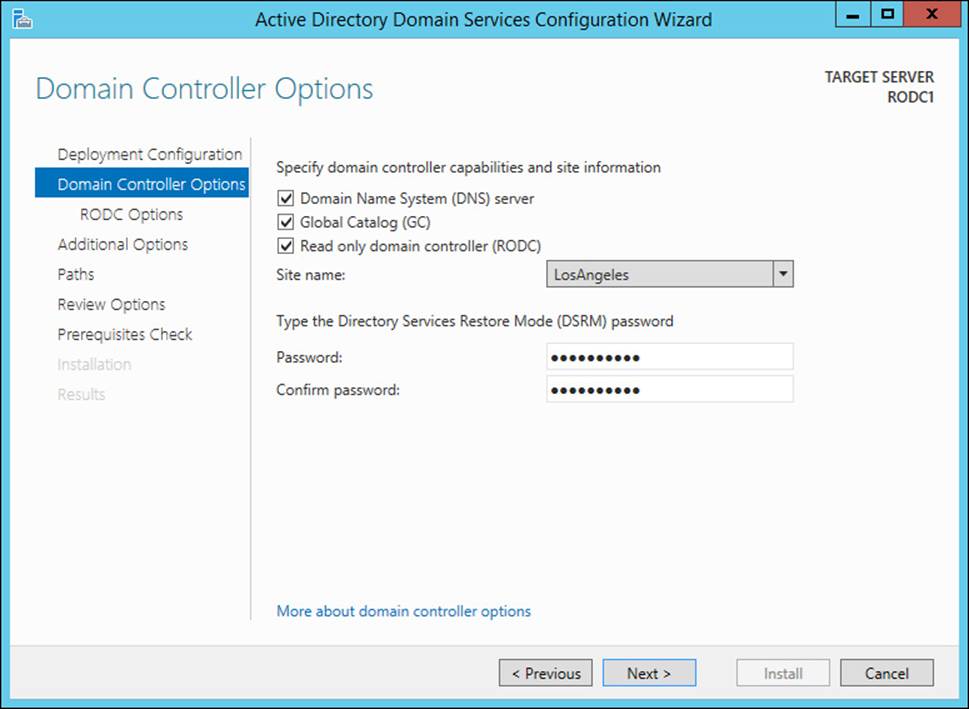
FIGURE 5-24 RODC deployment happens through the Active Directory Domain Services Configuration Wizard by choosing the Read Only Domain Controller (RODC) option
The RODC Options page (see Figure 5-25) enables you to choose a user or group to assign as the local administrator and configure the PRP for the RODC.
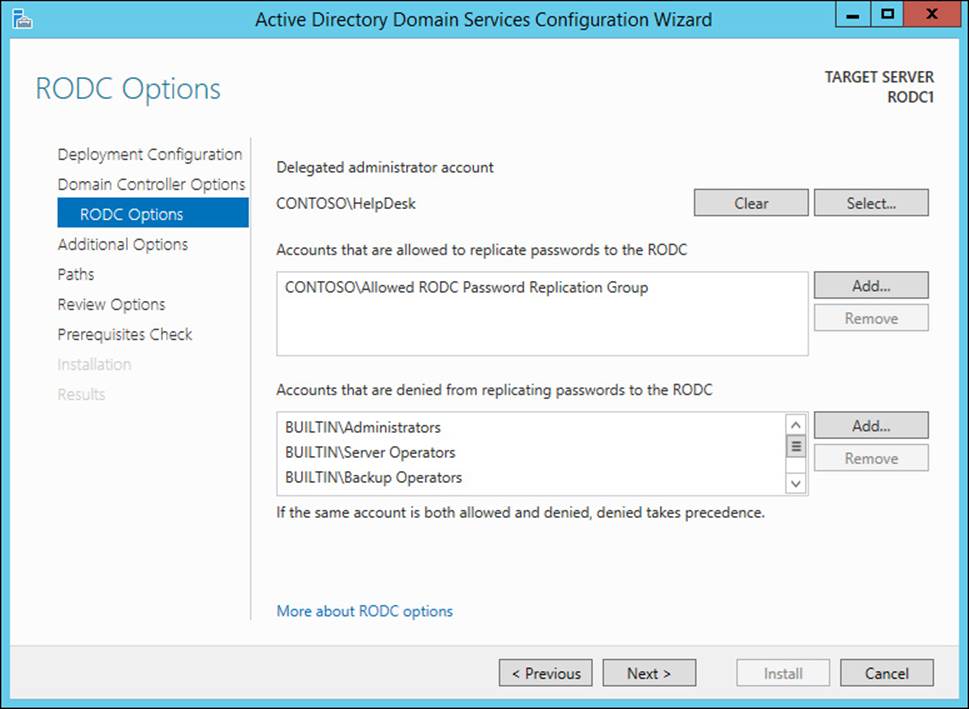
FIGURE 5-25 Deploying an RODC requires configuration of the delegated administrator account and PRP
Another way to deploy an RODC in your forest is to precreate the computer account for the RODC using the Active Directory Users and Computers Wizard, or PowerShell. A precreated RODC account includes the settings for delegated administration and the PRP, which reduces the configuration required later in the process. During the RODC account-creation process, you have the option to use Advanced mode, which enables you to manually configure the RODC options (PRP configuration is shown in Figure 5-26); otherwise, they are configured automatically.
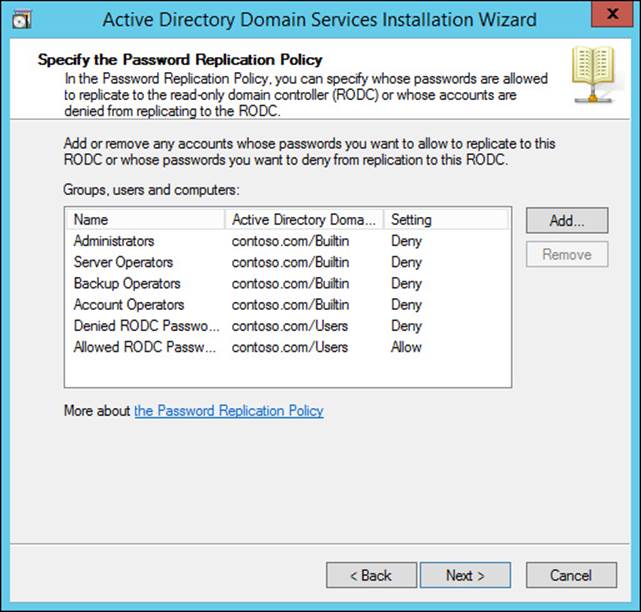
FIGURE 5-26 Precreation of an RODC account enables you to configure the PRP and delegated administration prior to RODC deployment
Upon deployment of an RODC with a precreated account, the Active Directory Domain Services Configuration Wizard indicates that a precreated account exists, giving you the option to use the existing account or to reinstall the domain controller. This behavior is shown in Figure 5-27.
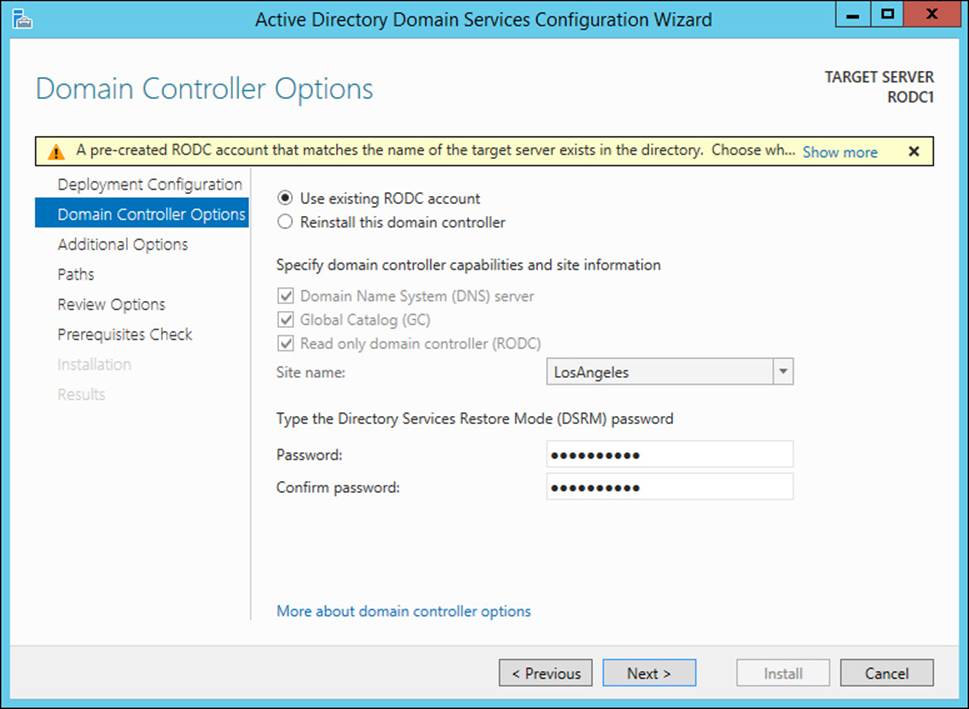
FIGURE 5-27 An RODC with a precreated account enables you to choose between using the existing account and reinstalling the domain controller upon deployment
Each of the steps of deploying an RODC can be completed using PowerShell. The Add-ADDSReadOnlyDomainControllerAccount can be used to precreate the RODC account and accepts the parameters listed in Table 5-3. These parameters can also be passed to the Install-ADDSDomainController cmdlet when the -ReadOnlyReplica parameter is used.
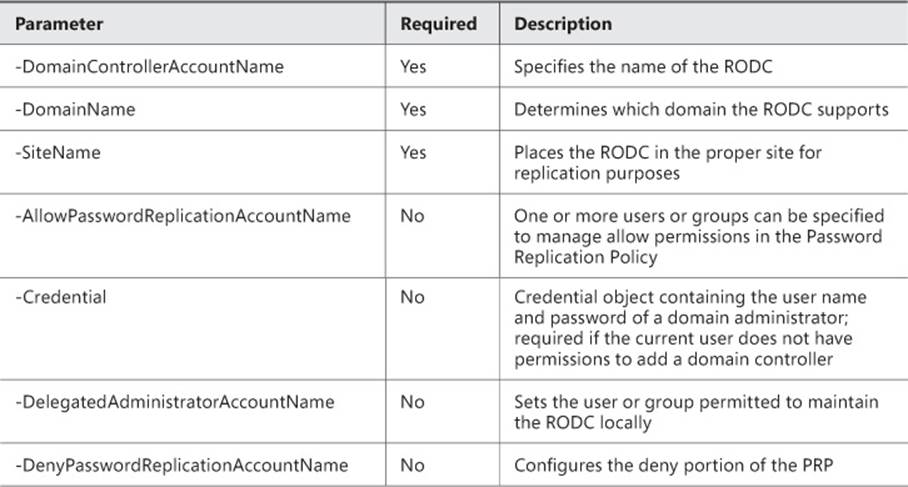
TABLE 5-3 Parameters used for RODC deployment with PowerShell
Implementing Universal Group Membership Caching (UGMC)
When a user is a member of a universal group located in another domain, additional steps in the authentication process (the authenticating domain controller must contact a global catalog server) are required. This process can become a source of performance problems when a site does not contain a global catalog server because performing this authentication over a WAN link might cause authentication delays and even deny the user’s logon attempt.
UGMC enables domain controllers within a site to store a user’s universal group membership locally upon initial logon. Subsequent logon attempts can then be authenticated without having to contact a global catalog server. UGMC is enabled with Active Directory Sites and Services. Within the NTDS Site Settings properties for a site, you can select the Enable Universal Group Membership Caching check box, as shown in Figure 5-28.
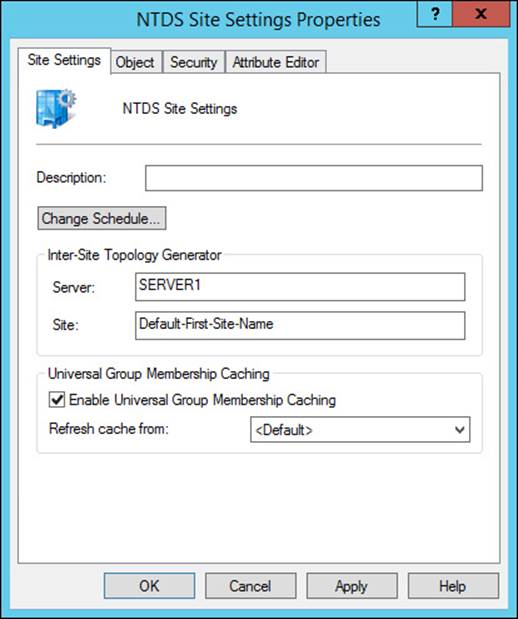
FIGURE 5-28 Enabling UGMC for the site
Using the global catalog
Global catalog servers should usually be deployed when authentication requirements outweigh replication drawbacks (in offices with a large number of users or forests with few domains, for example). Consider using UGMC to optimize authentication in sites large enough for a domain controller but not big enough to support the replication required for a global catalog server.
 Exam Tip
Exam Tip
Both UGMC and the global catalog are important for optimizing authentication in Active Directory. At a minimum, you should know how each feature can be helpful and what additional complexity comes from being enabled.
Implementing branch office infrastructure requirements
Regardless of the size of a corporate location or branch office, certain network infrastructure elements must be in place for standard networking and Active Directory authentication. DNS and DHCP are essential, although smaller locations can potentially receive support from DHCP and DNS servers in other sites.
Supporting DNS in the branch office
DNS should be deployed beside each domain controller in the forest—optimally on each domain controller so that Active Directory–integrated zones can be used. Even RODCs can be used as DNS servers, although they maintain only a read-only copy of the DNS zones. The DNS in a branch office should be configured in caching mode with forwarders configured to reference domain controllers that host the corporate root domain. This configuration provides optimal performance while enabling any DNS queries necessary for Active Directory to be resolved properly.
Supporting DHCP in the branch office
Because DHCP is such a necessary part of any network, some sort of DHCP in your branch offices is critical. Branch offices should ideally have redundant DHCP support through DHCP failover or split scopes, even if the secondary server is located off-site. DHCP can be a powerful tool for configuring network clients with the appropriate DNS server, thereby directing Active Directory member computers to domain controllers.
Deploying BranchCache
BranchCache is a technology that provides network optimization for remote locations by caching network resources on computers in the local network, thus reducing the amount of traffic required over slow and expensive WAN links. Windows Server 2012 and Windows 8 support two modes for BranchCache: hosted cache mode and distributed cache mode. Hosted cache mode uses Windows Server–based storage to contain the cache, whereas distributed cache mode stores the cache on Windows clients on the network.
Figure 5-29 illustrates the use of distributed cache mode to optimize WAN traffic to a content server in a remote site.
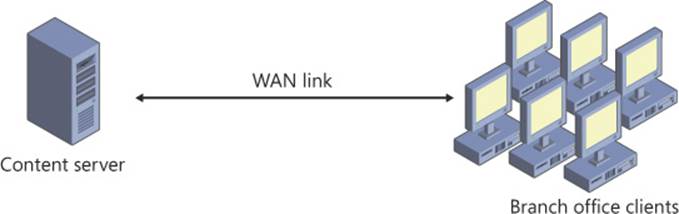
FIGURE 5-29 BranchCache in distributed cache mode is normally used when there is no available server-based storage within the local site
Not all WAN traffic is cached using BranchCache-only traffic originating from BranchCache-enabled content servers such as a Windows Server 2012 file server, an Internet Information Services (IIS)–based web server, and Windows Server Update Services (WSUS).
 Exam Tip
Exam Tip
Although BranchCache will probably not be tested heavily in the exam, you should expect one or two questions. You should know the difference between the two modes and what pieces must be in place for BranchCache to be implemented and used effectively.
Securing branch office deployments
Numerous challenges often prevent branch offices from meeting the security standards of your corporate datacenter. Physical security, maintenance schedules, and even the way users protect their passwords can be challenges without the plans and processes often associated with corporate IT environments.
Windows Server 2012 offers solutions to many aspects of securing information contained in Active Directory and prevents sensitive information about Active Directory objects from being read or modified by users without the proper permissions.
Implementing confidential attributes
Some attributes on Active Directory can be sensitive in your organization. Active Directory enables you to control what attributes are visible to users by defining this sensitive information as confidential attributes.
Confidential attributes are configured by defining the searchFlags value for an attribute by using Active Directory Service Interfaces (ADSI) Edit. Changing the searchFlags value from 0x0 (the default of 0) to 0x80 (128) marks the attribute as confidential (see Figure 5-30).
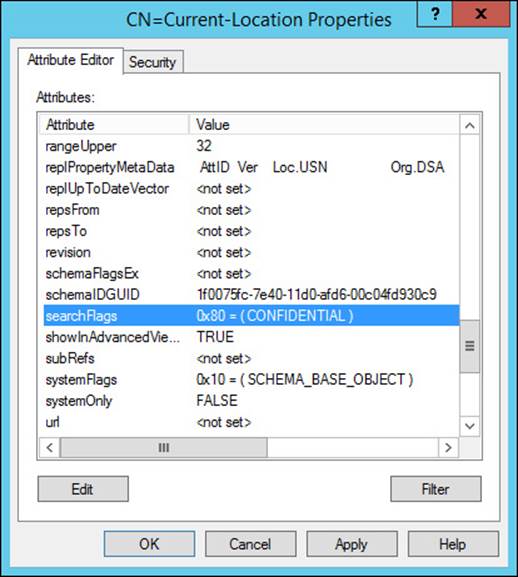
FIGURE 5-30 Setting the searchFlags value enables you to mark attributes as confidential
Delegating administration
Unlike writable domain controllers, RODCs enable you to delegate administrative access to the server without also granting access to the Active Directory domain. This enables you to permit local users within a branch to perform basic administration tasks such as performing software updates and installing drivers without compromising Active Directory.
You can delegate permission to an RODC on the Managed By tab of the RODC computer object in Active Directory, as shown in Figure 5-31. A user or group can be selected to provide local administrator rights to the RODC.
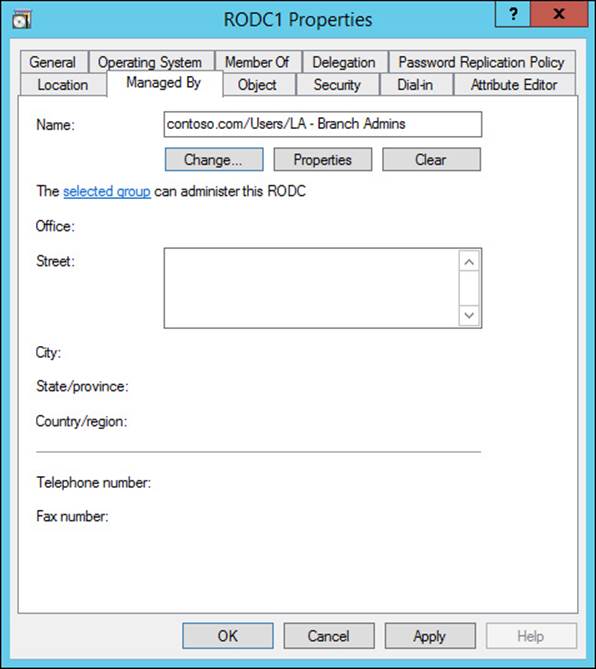
FIGURE 5-31 The Managed By tab of an RODC enables you to delegate administrative privileges to the domain controller
Note: Delegating RODC Administration
Because RODCs enable you to define only a single security principal for delegated administration, you should create a group specifically for that purpose. Other groups or users can be given membership to this group as needed to support your RODC.
Modifying the filtered attributes set
The filtered attribute set contains a list of object attributes that should not be replicated to an RODC. Because the primary reason for an RODC deployment is to lessen the risk involved with placing a domain controller in an insecure environment, the filtered attribute set should be used to prevent sensitive information from being replicated to RODCs.
As with confidential attributes, the filtered attribute set uses the searchFlags field in ADSI Edit to mark which attributes should not be replicated to RODCs. Setting the searchFlags value to 0x200 (512) adds the attribute to the filtered attribute set and prevents replication to RODCs.
Configuring Password Replication Policy
You can configure PRPs for RODCs. By adding users or groups to the Password Replication Policy tab of the RODC computer object in Active Directory, you determine and manage the users allowed to have their passwords cached by a particular RODC (see Figure 5-32). In the Advanced Password Replication Policy window, you can view the resultant policy of a PRP, enabling you to determine the results of a policy that might affect users’ membership in multiple groups.
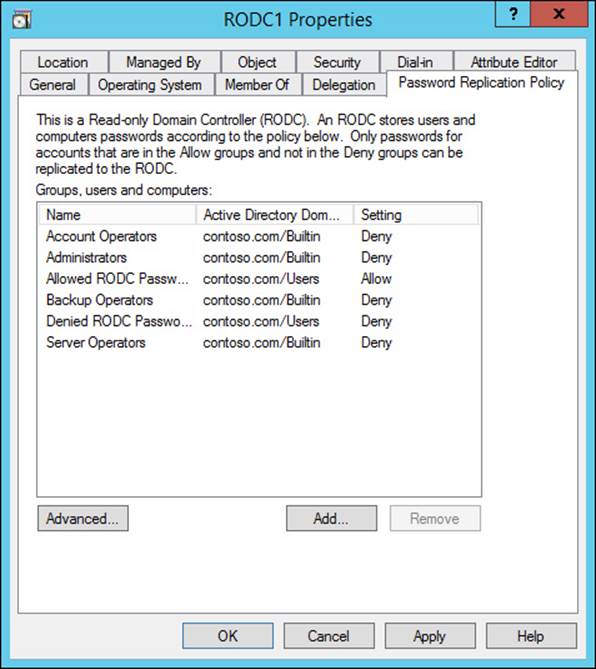
FIGURE 5-32 An RODC PRP is configured through the RODC computer object in Active Directory
The PRP for an RODC can also be managed using the PowerShell cmdlets listed in Table 5-4.
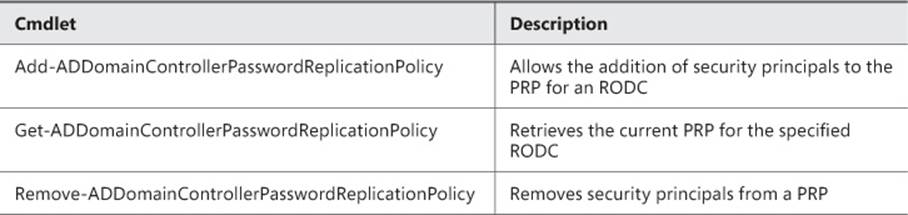
TABLE 5-4 Parameters used for deploying an RODC with PowerShell
Each of these cmdlets accepts the -Identity parameter, which is used to specify the RODC containing the PRP being managed. The allow and deny policies can be managed using the -AllowedList and -DeniedList parameters.
Configuring hash publication
To enable BranchCache support in your file servers, you must configure hash publication using Group Policy or local security policy.
BranchCache hash publication is configured in Group Policy under Computer Configuration, Policies, Administrative Templates, Network, Lanman Server, Hash Publication For BranchCache. When enabled, the setting enables you to configure automatic hash publication for all BranchCache-enabled shares, disallow hash publication on all shared folders, or allow hash publication for all shared folders (see Figure 5-33).
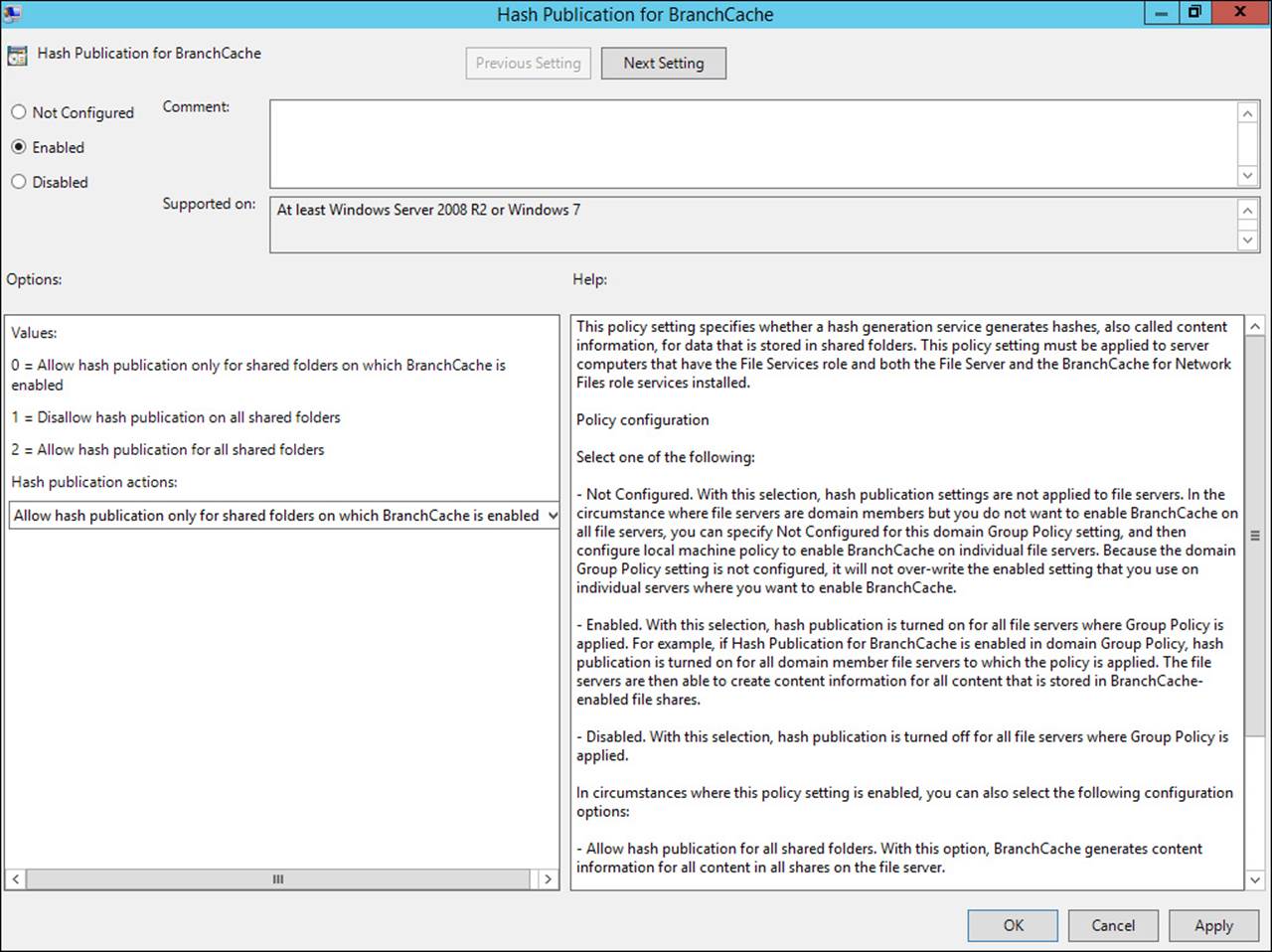
FIGURE 5-33 Hash publication can be enabled through Group Policy for all shared folders or only those that are BranchCache-enabled
![]() Thought experiment: Implementing a branch office deployment
Thought experiment: Implementing a branch office deployment
In this thought experiment, apply what you’ve learned about this objective. You can find answers to these questions in the “Answers” section at the end of this chapter.
You have been brought in by a large corporation to assist in implementing branch office deployments across the country. Answer the following questions regarding how you would meet corporate requirements for branch office deployments:
1. The corporate IT department is worried about deploying domain controllers in each branch, specifically because of lack of physical security and the risk of a compromised domain controller (which might result in the entire corporate network being compromised). What can you use to minimize the risk of deploying a domain controller in a branch office?
2. The IT department likes the idea of using RODCs in each branch office, but still has concerns about some specific user categories that should not have passwords saved to RODCs. What tool is available to prevent passwords from specific sets of users from being replicated to an RODC?
3. Corporate IT does not have the manpower to manage system updates, software installs, and driver updates on servers deployed in branch offices. This situation is problematic for domain controllers because only members of the Domain Admins group can log on to the console. Is there a way to enable local users to install software and updates on a branch office domain controller?
4. To keep costs down, network connectivity at each branch office is a relatively slow link. The IT department is worried about authentication performance, particularly for users with membership in universal groups from other domains. Configuring each branch office domain controller as a global catalog server would cause a significant uptick in replication traffic that might cause additional problems due to the slow network connectivity. What can you suggest to improve logon performance for branch office users?
5. In the past, the slow WAN link at each branch office used to access corporate file shares and SharePoint sites has resulted in reduced productivity. What capabilities are available to improve performance for corporate resources such as these in the branch offices?
Objective summary
![]() Both UGMC and the global catalog can be used to reduce authentication time for users with membership in universal groups in other domains.
Both UGMC and the global catalog can be used to reduce authentication time for users with membership in universal groups in other domains.
![]() BranchCache allows for WAN optimization through the use of a local cache. Both hosted cache and distributed cache are supported by using server-based or client-based storage, respectively.
BranchCache allows for WAN optimization through the use of a local cache. Both hosted cache and distributed cache are supported by using server-based or client-based storage, respectively.
![]() Confidential attributes can be configured to prevent certain Active Directory object attributes from being visible to all users.
Confidential attributes can be configured to prevent certain Active Directory object attributes from being visible to all users.
![]() Both the filtered attributes set and PRP enable you to manage the information that can be replicated to RODCs.
Both the filtered attributes set and PRP enable you to manage the information that can be replicated to RODCs.
![]() BranchCache requires support from content servers to cache network resources. File servers must be BranchCache-enabled, and hash publication must be configured for file shares.
BranchCache requires support from content servers to cache network resources. File servers must be BranchCache-enabled, and hash publication must be configured for file shares.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. What tool increases authentication performance in a multidomain forest without requiring replication of the partial attribute set?
A. BranchCache
B. UGMC
C. Confidential attributes
D. Global catalog
2. Which configuration options pertain specifically to RODC replication? (Choose all that apply.)
A. UGMC
B. Confidential attributes
C. Filtered attribute set
D. PRP
3. What method enables you to define the PRP and delegated administration for an RODC prior to deployment?
A. Group Policy
B. Precreating the RODC account
C. Install-ADDSDomainController PowerShell cmdlet
D. Local security policy
4. What command enables you to deploy an RODC using a precreated account?
A. Add-ADDSReadOnlyDomainControllerAccount -DomainControllerAccountName
B. Install-ADDSDomainController -UseExistingAccount
C. Install-ADDSReadOnlyDomainControllerAccount -DomainControllerAccountName
D. Add-ADDSDomainController -UseExistingAccount
5. What cmdlet enables you to add an entry to the PRP of an RODC?
A. Add-ADDomainControllerPasswordReplicationPolicy
B. Set-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicy
D. Remove-ADDomainControllerPasswordReplicationPolicy
6. What value must be set in the searchFlags field to configure confidential attributes?
A. 0x0
B. 0x80
C. 0x128
D. 0x200
7. Which BranchCache option uses client-based storage to cache network resources?
A. Hosted cache mode
B. Global catalog
C. Hash publication for BranchCache
D. Distributed cache mode
8. For which of the following resources does a branch office benefit from a BranchCache deployment? (Choose all that apply.)
A. SharePoint at corporate headquarters
B. File server at the branch office
C. File server at corporate headquarters
D. Public cloud–based web applications
9. What step must be taken to enable BranchCache support for a content server?
A. Enable BranchCache in hosted cache mode.
B. Install the BranchCache server feature.
C. Install Windows Server 2012 R2.
D. Configure hash publication.
10. How can a user be given administrative access to an RODC but not to Active Directory?
A. Select the user in the Managed By tab of the RODC computer object.
B. Add the user to the PRP for the RODC.
C. Add the user to the Domain Admins group.
D. Add the user to the RODC local Administrators group.
Answers
This section contains the solutions to the thought experiments and answers to the lesson review questions in this chapter.
Objective 5.1: Thought experiment
1. Configuring site links that include the sites for a specific time zone and then configuring the replication schedule for these site links enable you to configure replication based on office hours.
2. Changes to the schema should be made in the same location as the domain controller performing the schema operations master role.
Objective 5.1: Review
1. Correct answer: B
A. Incorrect: Shortcut trusts, which are used between two domains within a forest, have no impact on sites, particularly those without a domain controller.
B. Correct: Shortcut trusts are used to facilitate authentication requests from one domain to another. Rather than having to traverse the forest hierarchy, authentication requests can be referred directly to the appropriate domain controllers.
C. Incorrect: No improvements occur when attempting to create a shortcut trust to the forest root domain.
D. Incorrect: Shortcut trusts have no impact on replication. Site links would be used in this scenario.
2. Correct answer: D
A. Incorrect: Even if the two site links are not bridged, replication should still reach the site after two replication intervals.
B. Incorrect: Overlapping replication schedules are beneficial only if multiple site links are contained in a site link bridge.
C. Incorrect: Even with manual management of site link bridges, replication can reach across multiple site links.
D. Correct: If replication to one site is dependent on another, each directory partition should be represented in the site acting as the intermediary.
3. Correct answer: B
A. Incorrect: Domain controllers for each domain form ring topologies to replicate the domain partition, but they must also replicate the other directory partitions such as the schema and configuration partitions.
B. Correct: Replication within a single site uses a ring topology for each directory partition whether it is a domain, application directory, schema, or configuration partition.
C. Incorrect: All domain controllers are included in a ring only for partitions shared between every partition in the site.
D. Incorrect: Site links have no bearing on the replication topology within a site.
4. Correct answer: A
A. Correct: When an object is modified on a domain controller in one site, the changes must be replicated to be reflected on other domain controllers. With intersite replication, this process can take some time. This replication latency can occasionally cause authentication or authorization issues.
B. Incorrect: Even in a site without a domain controller authentication, traffic should be routed to the next closest domain controller for authentication.
C. Incorrect: If a site does not contain a domain controller for the user’s domain, the authentication request should be routed to a domain controller capable of authenticating the user.
D. Incorrect: The PDC emulator master is responsible for handling the initial password change. The replication process then takes over and must communicate the new password throughout the forest.
5. Correct answers: A, B
A. Correct: Reducing the number of steps in the replication process, either through new site links or site link bridges, should help reduce replication latency.
B. Correct: Although more frequent replication helps reduce latency, it can increase the workload on bridgehead servers’ network utilization over WAN links.
C. Incorrect: Placing domain controllers from every domain at each site increases replication traffic and provides no improvement in replication latency.
D. Incorrect: Deploying a domain controller from the forest root domain within each site increases replication traffic and does not reduce replication latency.
6. Correct answer: D
A. Incorrect: Operations master roles have no impact on which domain controllers perform as bridgehead servers and are not required to be performed by bridgehead servers.
B. Incorrect: If a domain controller for the domain is not available, authentication or authorization requests are passed on to another site.
C. Incorrect: When objects are modified in another site, the changes should be replicated to other sites.
D. Correct: If the preferred bridgehead servers do not host a copy of all directory partitions within the site, the domain controllers containing other domain partitions cannot receive updates from other sites.
7. Correct answers: C, D
A. Correct: Replication through a site link bridge can occur without preferred bridgehead servers being selected.
B. Incorrect: Even if a site common to two bridged site links is unavailable, the two remaining sites can perform replication.
C. Incorrect: Sites that perform replication through a site link bridge must share a directory partition.
D. Incorrect: Replication across a site link bridge can occur only if both site links have a simultaneous replication period.
8. Correct answer: A
A. Correct: Selecting the Bridge All Site Links check box results in replication being unconstrained between all sites in the forest.
B. Incorrect: Rebooting the infrastructure master has no effect on replication.
C. Incorrect: Deleting the DEFAULTIPSITELINK site link does not limit replication traffic to only the defined site links.
D. Incorrect: Changes made on an RODC are simply forwarded to a writable domain controller.
9. Correct answer: B
A. Incorrect: The /showrepl switch for repadmin shows the replication status for a domain controller, but does not show inbound requests.
B. Correct: The /queue switch for repadmin shows inbound replication requests for a domain controller.
C. Incorrect: The dcdiag /test:replications command runs the replications test for DNS servers.
D. Incorrect: The dcdiag /test:VerifyReplicas command checks the replication status of directory partitions.
10. Correct answer: B
A. Incorrect: The /kcc parameter forces the KCC to recalculate replication paths.
B. Correct: The /replsingleobj option enables you to specify an object and two domain controllers, replicating the object between the source and target domain controllers.
C. Incorrect: Full replication between two domain controllers can be triggered with the /replicate option.
D. Incorrect: The incoming replication queue for a domain controller can be viewed by using the /queue parameter.
Objective 5.2: Thought experiment
1. Applications that integrate closely with Active Directory sometimes make changes to the Active Directory schema. Changes to the schema are handled by the domain controller performing the schema master role. Placing these applications in the location that hosts the schema master is usually recommended.
2. When a user with a membership in universal groups from other domains authenticates, the other domain must be contacted unless a global catalog server exists within the user’s domain.
3. The partial attribute set replicates to global catalog servers throughout the forest. Managing the attributes contained in the partial attribute set enables you to prevent replication of these attributes to global catalog servers.
4. RODCs are the first step of providing protection in areas with concerns over physical security. Both the read-only nature of RODCs and the PRP help ensure limited risk from a compromised RODC.
Objective 5.2: Review
1. Correct answer: C
A. Incorrect: RODCs furnish no inherent benefits for cross-domain authentication.
B. Incorrect: Although the domain controller performing the domain naming master role does not improve cross-domain authentication performance, it is used when changes are made to the domain structure (such as adding or removing domains).
C. Correct: Global catalog servers use the partial attribute set to improve authentication performance.
D. Incorrect: The infrastructure master role tracks the membership of users outside the domain in groups within the domain. Authentication performance for users within the domain does not improve based on proximity to the infrastructure master.
2. Correct answers: B, D
A. Incorrect: The PDC emulator master role is performed at the domain level and handles password changes for the domain.
B. Correct: The domain naming master role is performed by a domain controller at the forest level to maintain a writable copy of the structure of domains within the forest.
C. Incorrect: Infrastructure masters are located within each domain to maintain a record of security principals from other domains with membership in universal groups in the local domain.
D. Correct: Schema changes are written to the schema master, which is a role performed at the forest level.
3. Correct answer: C
A. Incorrect: The schema master handles changes to the Active Directory schema.
B. Incorrect: Infrastructure master servers track security principals from other domains that are members of groups in the local domain.
C. Correct: The PDC emulator master handles password changes within its domain.
D. Incorrect: RID masters maintain RID pools for each domain, ensuring that each object in an Active Directory forest has a unique ID.
4. Correct answer: D
A. Incorrect: Global catalog servers contain the partial attribute set for the forest and do not provide any security benefits.
B. Incorrect: The schema master handles changes to the Active Directory schema.
C. Incorrect: No security benefits are gained by assigning the infrastructure master role to a server.
D. Correct: RODCs have several security benefits for locations with physical security limitations.
5. Correct answers: A, C, D
A. Correct: A compromised RODC does not allow changes to Active Directory objects to be written back to Active Directory.
B. Incorrect: RODCs do not improve authentication performance.
C. Correct: The PRP for an RODC enables you to limit password caching to the RODC.
D. Correct: An RODC can be managed by a local administrator without also providing full access to Active Directory objects.
6. Correct answer: C
A. Incorrect: RODCs make use of the filtered attributes set, not the partial attribute set. Both are configured with the searchFlags attribute in ADSI Edit.
B. Incorrect: Domain controller cloning is not associated with the partial attribute set.
C. Correct: Global catalog servers contain copies of attributes from every object in the domain; these attributes are determined by the partial attribute set.
D. Incorrect: Attributes are replicated between sites regardless of the partial attribute set.
7. Correct answers: B, D
A. Incorrect: Adding a new domain to a forest does not alter the schema or the partial attribute set.
B. Correct: Some applications that integrate with Active Directory, such as Microsoft Exchange Server, use the partial attribute set to make certain attributes readily available throughout the forest.
C. Incorrect: Deploying a global catalog server does not modify the partial attribute set.
D. Correct: You can modify the partial attribute set manually by using the Active Directory Schema snap-in.
8. Correct answers: A, D
A. Correct: The source domain controller must be added to the Cloneable Domain Controllers group.
B. Incorrect: The forest does not have to be at the Windows Server 2012 functional level to support cloned domain controllers.
C. Incorrect: Although it makes sense not to clone a domain controller performing an operations master role, it is not a requirement.
D. Correct: Creating the config file is one of the last steps of cloning a domain controller.
9. Correct answers: A, B
A. Correct: AD CS does not support cloning. Attempting to clone a virtual domain controller that is also performing the AD CS role results in failure.
B. Correct: The DHCP server role cannot be cloned.
C. Incorrect: The AD DS role supports cloning and is required to clone a virtual domain controller.
D. Incorrect: The DNS role supports cloning.
10. Correct answer: C
A. Correct: The domain naming master is not necessary for cloning a virtual domain controller.
B. Incorrect: A RID master is not used when cloning a virtual domain controller.
C. Correct: The PDC emulator master is responsible for password changes, and the virtual domain controller cloning process requires the PDC emulator master to be available.
D. Incorrect: The virtual domain controller cloning process does not require the infrastructure master server.
Objective 5.3: Thought experiment
1. RODCs help protect Active Directory from the risks involved with a compromised domain controller.
2. Configuring the PRP for an RODC helps protect users with elevated privileges or sensitive accounts from having their passwords stored on the domain controller.
3. RODCs support the assignment of local administrative privileges for this scenario.
4. UGMC, which can be configured for the site, improves authentication performance for users with membership in universal groups from other domains.
5. BranchCache can help optimize access to resources on corporate servers by creating a cache in the local site, either on a central server (hosted cache mode) or spread across clients (distributed cache mode).
Objective 5.3: Review
1. Correct answer: B
A. Incorrect: BranchCache is used to optimize access to corporate resources across slow WAN connections.
B. Correct: UGMC enables rapid authentication for users with membership in universal groups from other domains without the replication overhead associated with global catalog servers.
C. Incorrect: Confidential attributes prevent users from viewing sensitive attributes on Active Directory objects without the necessary permissions.
D. Incorrect: Although global catalog servers optimize authentication performance, there are significant replication costs.
2. Correct answers: C, D
A. Incorrect: UGMC is not specific to RODCs; it is an option for any site with a domain controller.
B. Incorrect: Confidential attributes affect any domain controller, not just RODCs.
C. Correct: The filtered attribute set determines what attributes can be replicated to RODCs.
D. Correct: An RODC PRP determines which users can have their passwords replicated to the RODC.
3. Correct answer: B
A. Incorrect: Group Policy does not allow you to configure the PRP and delegated administration for an RODC. These aspects of RODC configuration are usually specific to the site in which the RODC is deployed. Group Policy is best used for configuring multiple machines across one or more domains.
B. Correct: When you precreate the computer account for an RODC, you can use Advanced mode, which enables you to configure the PRP and the user or group delegated for administration.
C. Incorrect: Although the Install-ADDSDomainController cmdlet enables you to configure both the PRP and delegated administration, it occurs during deployment of the RODC, not before.
D. Incorrect: The local security policy of an RODC is not the proper place to configure the PRP and delegated administration, especially prior to deployment.
4. Correct answer: B
A. Incorrect: Although the Add-ADDSReadOnlyDomainControllerAccount with the -DomainControllerAccountName parameter enables you to precreate an RODC account, it does not actually deploy the RODC.
B. Correct: The Install-ADDSDomainController with the -UseExistingAccount parameter enables you to use a precreated RODC account to deploy an RODC.
C. Incorrect: Install-ADDSReadOnlyDomainControllerAccount is not a valid PowerShell cmdlet.
D. Incorrect: Add-ADDSDomainController is not a valid PowerShell cmdlet.
5. Correct answer: A
A. Correct: Add-ADDomainControllerPasswordReplicationPolicy enables you to add security principals to the PRP for an RODC from either an allow or deny standpoint.
B. Incorrect: Set-ADDomainControllerPasswordReplicationPolicy is not a valid PowerShell cmdlet.
C. Incorrect: Get-ADDomainControllerPasswordReplicationPolicy enables you to retrieve the existing PRP from an RODC.
D. Incorrect: Remove-ADDomainControllerPasswordReplicationPolicy removes security principals from an RODC PRP.
6. Correct answer: B
A. Incorrect: The default searchFlags value is 0x0.
B. Correct: A confidential attribute can be configured by setting the searchFlags field to 0x80.
C. Incorrect: The 0x80 value equates to 128, but 0x128 is incorrect.
D. Incorrect: A searchFlags value of 0x200 is used for filtered attributes, not confidential attributes.
7. Correct answer: D
A. Incorrect: Hosted cache mode uses server-based storage to host the cache.
B. Incorrect: Global catalog servers are not used for BranchCache.
C. Incorrect: Hash publication is part of the process to configure file servers to support BranchCache.
D. Correct: Distributed cache mode enables you to use client storage to contain BranchCache.
8. Correct answers: A, C
A. Correct: SharePoint sites hosted using IIS do support BranchCache optimization. Optimizing traffic across the WAN connection is the goal of BranchCache.
B. Incorrect: Although Windows Server–based file servers offer BranchCache support, no benefit is gained by caching what is already a local resource.
C. Correct: Windows Server–based file servers support BranchCache and are a common use-case for BranchCache optimization when located in another site.
D. Incorrect: Public web applications cannot be cached using BranchCache.
9. Correct answer: D
A. Incorrect: The BranchCache deployment mode does not determine whether a content server supports BranchCache.
B. Incorrect: BranchCache is not installed as a server feature on a content server.
C. Incorrect: BranchCache support is not a new feature in Windows Server 2012 R2.
D. Correct: Hash publication must be enabled for clients to use BranchCache when accessing resources from a content server.
10. Correct answer: A
A. Correct: Adding users and/or groups to the Managed By tab of the RODC gives them local administrator permissions to the domain controller.
B. Incorrect: The RODC PRP has no effect on which users have administrative privileges on the server.
C. Incorrect: Although the Domain Admins group would give users administrator permissions to the RODC, it would also give them access to the objects within Active Directory.
D. Incorrect: When a server is promoted to a domain controller, its local users and groups are removed.