Exam Ref 70-417 Upgrading Your Skills to Windows Server 2012 R2 (2014)
Chapter 2. Configure server roles and features
Exam 70-417 distills the three Windows Server 2012 MCSA certification track exams (70-410, 70-411, and 70-412) down to a single exam. The raw material from these three original MCSA exams includes a total of 18 major content areas or “domains” within Windows Server 2012. These 18 content areas are then further broken down into 62 specific objectives corresponding to job tasks.
That’s a lot of source material, but just a fraction—about one-third—of this original content is specified for 70-417. Specifically, just 22 objectives within 14 content areas made it into the official “Skills Measured” list for 70-417. These 14 official content areas are represented as the chapter names in this book.
As a result, most of the content areas in 70-417 appear only in a partial form compared to the original exams from which they were taken. This chapter is an example of that. The Configure Server Roles and Features domain is taken from the 70-410 exam, but only one of the three original objectives remains.
The questions you see from the Configure Server Roles and Features domain on the 70-417 exam will fall almost completely within Objective 2.1, within the topic of remote management. However, it’s a good idea to review the Microsoft website for the original objectives associated with this content area on the 70-410 exam. Don’t be surprised if on 70-417 you see a question relating to any of the original topics.
Objectives in this chapter:
![]() Objective 2.1: Configure servers for remote management
Objective 2.1: Configure servers for remote management
Objective 2.1: Configure servers for remote management
Windows Server 2012 and Windows Server 2012 R2 are much better suited to administering remote servers on the network than any of their predecessors. It’s not just that these operating systems offer new capabilities in remote management, which they do. It’s also that behind the scenes, existing technologies have been revised to simplify remote management.
As you study this section for the exam, above all, do not rely on what you learned for Windows Server 2008 and Windows Server 2008 R2. Some features might look the same, but they have in fact changed—such as the inbound rules you might use to enable various types of remote management, or the function of a particular command, or the name of the relevant Group Policy settings.
This section covers the following topics:
![]() Managing multiple servers with Server Manager
Managing multiple servers with Server Manager
![]() Configuring various server types for remote management
Configuring various server types for remote management
![]() Configuring Group Policy to enforce remote management settings
Configuring Group Policy to enforce remote management settings
Managing multiple servers with Server Manager
The new Server Manager in Windows Server 2012 and Windows Server 2012 R2 reveals big changes—both cosmetic and functional—and some of these changes are relevant for the 70-417 exam. The most significant of these new features is that you can now use Server Manager to manage multiple servers, as shown in Figure 2-1. One way you can use Server Manager to manage multiple servers is through the All Servers option in the navigation pane. You can also use the Create Server Group option on the Manage menu to create server groups, which are custom pages in Server Manager that allow you to manage subsets of your servers such as all your DNS servers. Finally, you can also multi-select servers on Server Manager pages, allowing you to perform some management tasks simultaneously on all the servers you selected.
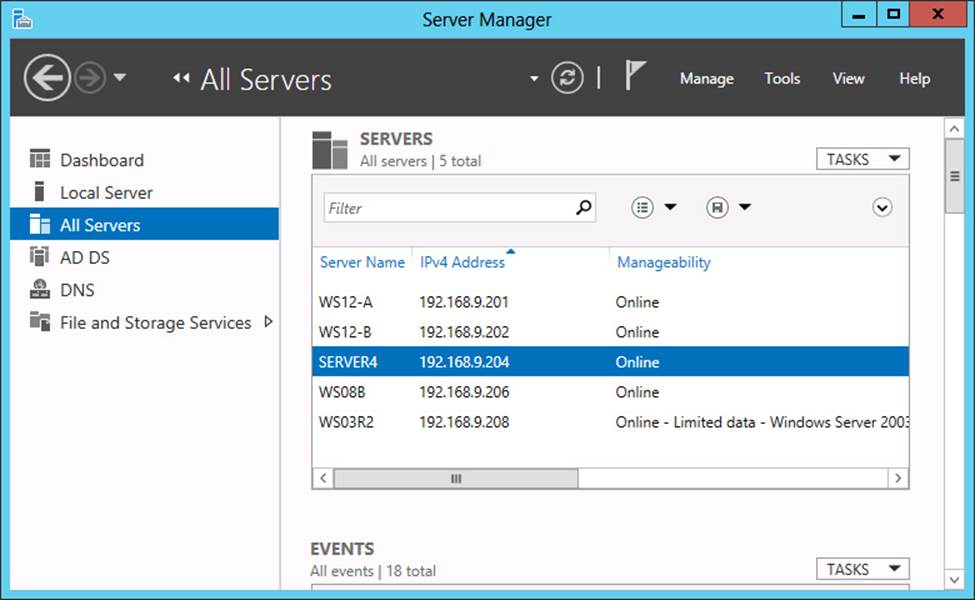
FIGURE 2-1 Server Manager is a multiserver management tool in Windows Server 2012 and Windows Server 2012 R2
More Info
See Chapter 1, “Install and Configure Servers,” for information about how to add servers to the All Servers page in Server Manager.
Adding non-domain-joined servers to Server Manager
It’s easy to add and manage servers through Server Manager when all of the servers are in the same Active Directory domain. These steps were shown in in Chapter 1, “Install and Configure Servers,” in the section “Objective 1.2: Configure Servers.” Adding servers in the same domain to Server Manager is so simple, in fact, that it’s almost certainly too simple to serve as the basis for an exam question.
Managing non-domain joined servers through Server Manager is, however, more complicated and requires a level of expertise that is more suitable for the exam. Typically, workgroup environments are not covered in MCSE exams, but “manage non-domain joined servers” has officially been added as a new task in the updated objectives for Windows Server 2012 R2. For these reasons, you will likely see a question on the 70-417 exam that tests your knowledge of this topic.
Simply adding workgroup servers to Server Manager is not difficult. You can easily add a workgroup server to Server Manager by using the Add Servers option on the Manage menu and then specifying it by IP address or DNS name as long as the target server is accessible on the network. However, the remote non-domain-joined server will appear in Server Manager only with an error message at first; no management operations will be possible immediately. These complications with managing remote workgroup servers in Server Manager have to do with the following four issues:
Note
Successful name resolution is an assumed prerequisite for remote management. The managing server and target server must be able to resolve each other’s computer names through DNS.
1. Remote computers aren’t automatically trusted for remote management on a managing server (as they are in a shared domain environment).
This is the only issue that is always present when the managing server running Server Manager and the server being targeted in Server Manager are not members of the same Active Directory domain.
To fix this problem, you need to configure the server running Server Manager to add the target server to its TrustedHosts list for remote management. To add the first server to the list, type the following at an elevated Windows PowerShell prompt:
Set-Item wsman:\localhost\Client\TrustedHosts TargetServer
where TargetServer is the name of the target server you want to manage through Server Manager.
To add additional servers to the list, add the –Concatenate and –Force options. For example, to add the server named Server2 to a TrustedHosts list that already includes one or more entries, type the following at an elevated Windows PowerShell prompt:
Set-Item wsman:\localhost\Client\TrustedHosts Server2 -Concatenate -Force
If you neglect to use the –Concatenate and –Force options when the TrustedHosts list contains pre-existing entries, the pre-existing entries will be deleted. To see the existing TrustedHosts lists for remote management, type the following at an elevated command prompt:
winrm get winrm/config/client
In the output, read the values next to TrustedHosts. If no computer name entries are present, you don’t need to use the –Concatenate and –Force options.
2. The correct administrator credentials aren’t automatically available for the remote server because there is no one administrator account common to both the managing server and the target server.
This issue is present whenever the user name and password of the currently logged-in administrator on the server running Server Manager do not exactly match the credentials (user name and password) of an administrator on the target server.
To fix this problem, right-click the server in Server Manager and select Manage As. Then specify the credentials of an administrator on the remote server.
3. User Account Control by default allows only the local built-in Administrator account on a target workgroup computer to run elevated processes remotely through Server Manager. By default, no other administrator accounts can perform management actions through Server Manager.
This issue is present on remote workgroup servers only. It is not present on remote servers joined to any domain.
To fix this problem, on the remote workgroup server, create a REG_DWORD registry entry named LocalAccountTokenFilterPolicy in HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System and then set its value to 1. You can do this by typing the following command at an elevated Windows PowerShell prompt:
New-ItemProperty -Name LocalAccountTokenFilterPolicy -path HKLM:\SOFTWARE\
Microsoft\Windows\CurrentVersion\Policies\System -propertyType DWord -value 1
4. The firewall rule allowing remote management for the Public network profile allows remote management only from computers located on a computer’s local subnet by default.
This issue is present on remote servers only when both of the following are true: The active network profile is Public (not Private or Domain) and when the server running Server Manager is on a different subnet.
To fix this problem, in Windows Firewall with Advanced Security, open the firewall rule named Windows Remote Management (HTTP-In) for the Public profile. On the Scope tab, in the Remote IP Address list, type the IP address of the server running Server Manager.
 Exam Tip
Exam Tip
Remember all four of these issues and their fixes for the exam.
Managing remote management tasks through All Servers
After you add remote servers to Server Manager, you can manage those particular servers from your local Server Manager console as long as they are enabled for remote management. Figure 2-2 shows a menu of management tasks you can perform on remote servers listed in the All Servers – Servers section in Server Manager. (These servers could naturally be added to a custom server group you create as well.) These tasks include adding roles and features, opening Computer Management (to review event logs, for example), opening a Windows PowerShell prompt on the remote server, and configuring NIC teaming.
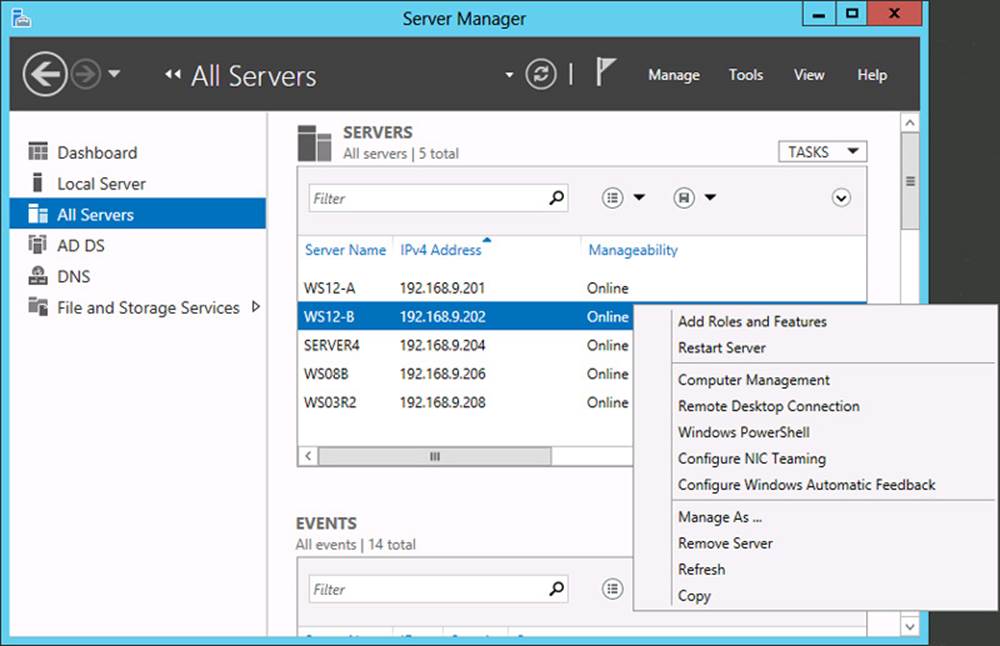
FIGURE 2-2 Remote management tasks in Server Manager
If you right-click a server that is a domain controller, you can access a much larger set of administrative options, including running many diagnostic tools, as shown in Figure 2-3.
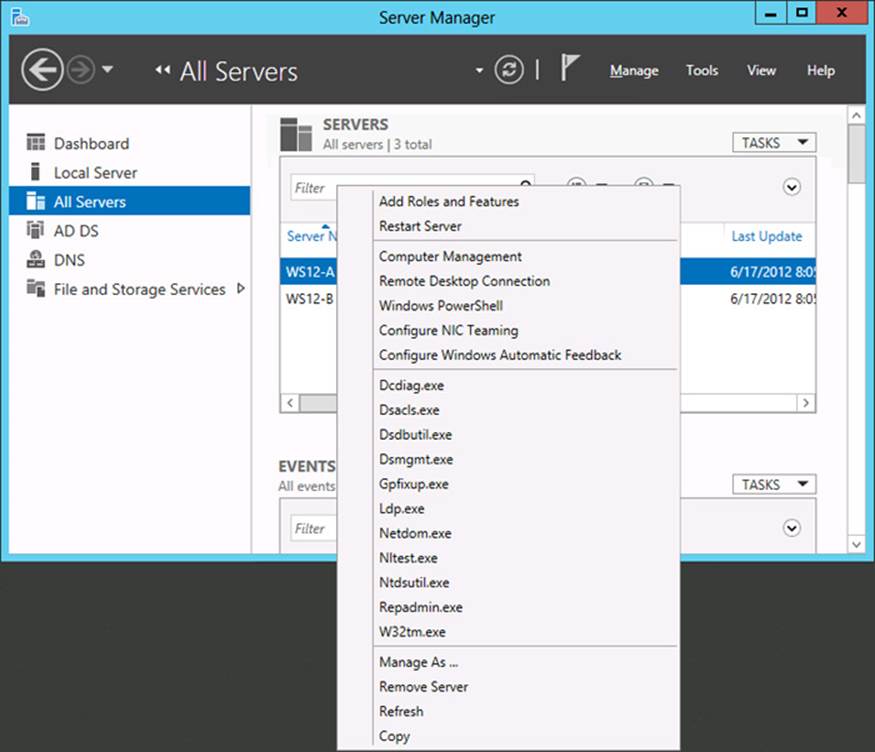
FIGURE 2-3 Remote management options on a domain controller
 Exam Tip
Exam Tip
None of the utilities shown in the shortcut menu in Figure 2-3 is new to Windows Server 2012 or Windows Server 2012 R2, but you are still likely to see one or more of them on the 70-417 exam. Make sure you review them.
On the All Servers page in Server Manager, you can use the following sections to perform everyday maintenance on the status of your servers:
![]() Events Use this section to check for errors and warnings on your servers without having to open a console on the remote machine.
Events Use this section to check for errors and warnings on your servers without having to open a console on the remote machine.
![]() Services Use this section to check for stopped services.
Services Use this section to check for stopped services.
![]() Best Practices Analyzer Use this section to compare the server configuration to a Best Practices standard.
Best Practices Analyzer Use this section to compare the server configuration to a Best Practices standard.
![]() Performance This section provides CPU and memory usage data of a server over time. To start CPU and memory performance monitoring, you need to right-click a server and select Start Performance Counters, as shown in Figure 2-4.
Performance This section provides CPU and memory usage data of a server over time. To start CPU and memory performance monitoring, you need to right-click a server and select Start Performance Counters, as shown in Figure 2-4.
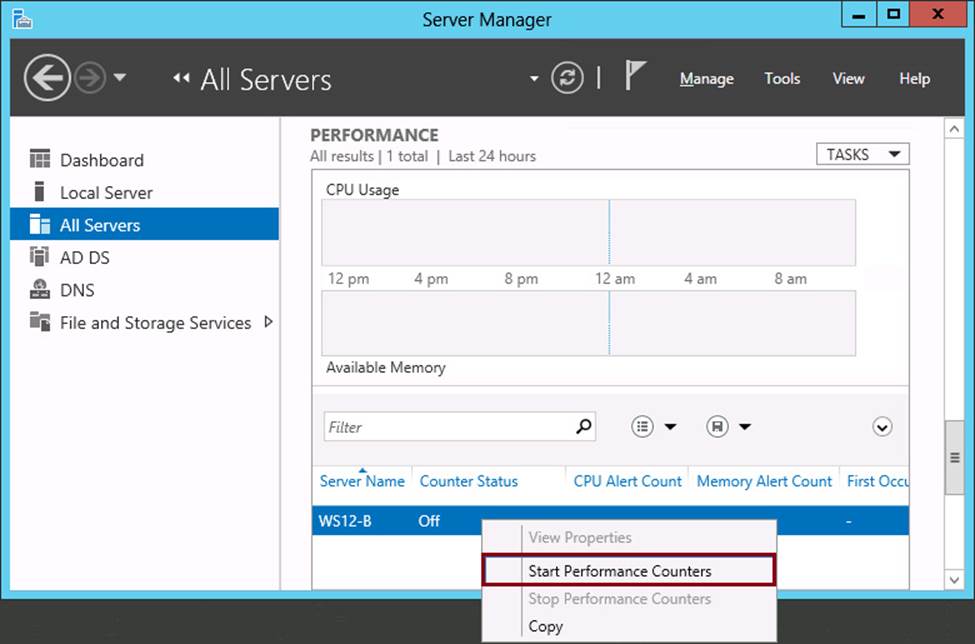
FIGURE 2-4 Monitoring CPU and memory performance
![]() Roles And Features Use this section to verify the installed roles and features on your servers. You can also use this section to remove roles and features.
Roles And Features Use this section to verify the installed roles and features on your servers. You can also use this section to remove roles and features.
Remote management in Windows Server 2012 and Windows Server 2012 R2 is enabled and configured by default. You can start remotely managing servers out of the box, as long as they are running Windows Server 2012 or Windows Server 2012 R2, they are in the same domain, and you have the proper administrative privileges. This ease of remote management is a welcome change from both Windows Server 2008 and Windows Server 2008 R2, in which you needed to configure a server to manage it remotely with admin tools.
Unfortunately, the fact that remote management is easy in Windows Server 2012 and Windows Server 2012 R2 doesn’t mean that questions about this topic on the exam will be just as easy. It’s the exam writers’ jobs to develop questions which require a reasonable amount of expertise to solve. For remote management, these questions could likely include scenarios in which you need to re-enable Windows Server 2012 R2 for remote management at the command line, enforce remote management settings through Group Policy, or create proper firewall settings on down-level servers, such as those running Windows Server 2008.
Understanding remote management types: DCOM and WinRM
A brief review of remote management technologies in Windows networks is helpful for exam preparation. Generally speaking, it’s important to remember that remote management in Windows networks is an umbrella term. Different remote management tools use different underlying technologies and require different preconfiguration steps.
For both local and remote management, Windows Management Instrumentation (WMI) provides an administrative interface to scripts, programs, and built-in Windows tools. For the purposes of remote management, WMI-based queries and configuration commands are typically passed through either of two protocols: Distributed Component Object Model (DCOM) or Windows Remote Management (WinRM). DCOM is an older, proprietary technology for software component communication across networks; WinRM is the Microsoft implementation of an independent standard called WS-Management Protocol.
WMI over DCOM
Traditional console-based tools such as Microsoft Management Console (MMC) snap-ins and Computer Management rely on WMI over DCOM when used for remote management. When used remotely, DCOM tools require only that you open certain ports on the firewall of the server you want to manage. If you don’t open those ports, you get a message like the one shown in Figure 2-5. This particular error message is helpful in that it informs you exactly which predefined inbound rules you need to enable by using either the Windows Firewall With Advanced Security tool or the Enable-NetFirewallRule cmdlet on the remote server:
![]() COM+ Network Access (DCOM-In)
COM+ Network Access (DCOM-In)
![]() All rules in the Remote Event Log Management group
All rules in the Remote Event Log Management group
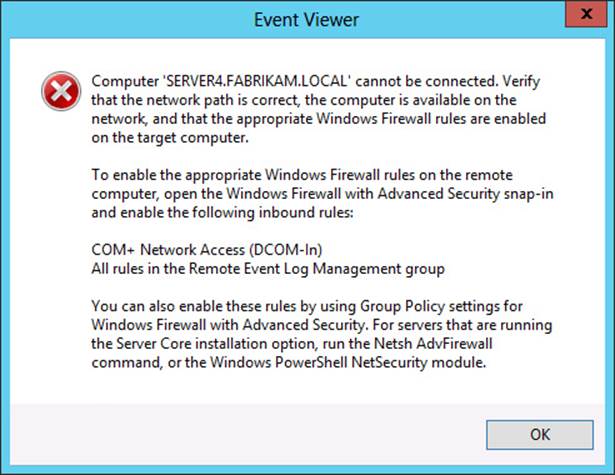
FIGURE 2-5 If you get this message, you’ve likely tried to use an MMC console for remote management without opening the proper ports
These two sets of rules allow you to connect to most MMC consoles in Windows Server 2012 and Windows Server 2012 R2. Other inbound rules you might need to create are Remote Volume Management (to use Disk Management remotely) and Windows Firewall Remote Management (to use Windows Firewall With Advanced Security remotely).
If you see a question about these DCOM-based remote management tools on the 70-417 exam, it’s unlikely to mention DCOM by name. Instead, the question will probably mention Computer Management or the name of another MMC console or snap-in.
 Exam Tip
Exam Tip
Remember that if you need to remotely manage a computer running Windows Server 2012 or Windows Server 2012 R2 by using Computer Management, you should enable certain firewall rules either by using Windows Firewall With Advanced Security or the Enable-NetFirewallRule cmdlet. (Enabling the remote management property is not sufficient.) This statement is true for both Server Core installations and Server With A GUI installations.
WMI over WinRM
The second type of protocol for accessing WMI is WinRM. WinRM isn’t new, but within Windows Server there’s been a movement toward WinRM-based tools and away from DCOM since Windows Server 2008. As you might remember, WinRM is a Windows service. The most notable tools that use WinRM for remote management are Windows PowerShell, WinRS (Windows Remote Shell), and Server Manager in Windows Server 2012 and Windows Server 2012 R2.
 Exam Tip
Exam Tip
Even though the WinRS command is not new, you should remember it for the exam. Use WinRS with the /r switch to specify the target computer on which you want to run another command. For example, type winrs /r:myserver ipconfig to run Ipconfig on a server named Myserver.
From an exam standpoint, the implications of WinRM being a service is that when a WinRM tool fails, the underlying cause could be that the WinRM service has stopped. (Note that WinRM by default starts automatically in Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2.)
There are also a couple of other important points to remember about WinRM. WinRM tools are firewall-friendly in that they communicate over a single port: either 5985 over HTTP or 5986 over HTTPS. (Yes, you read that correctly: The usual ports 80 and 443 are avoided for security reasons.) Besides requiring a single port to be open for communication, WinRM also requires a WinRM listener to be enabled on the server you want to manage remotely. As you might remember, both the listener and the port can be configured at once by executing the simple commandwinrm quickconfig at an elevated command prompt on the server you want to manage. (On servers running Windows Server 2012 or Windows Server 2012 R2, however, this step is normally not required because WinRM is enabled by default.)
Re-enabling Windows Server 2012 and Windows Server 2012 R2 for remote management through Server Manager
Remote management is governed in the GUI by the Remote Management property in Server Manager. However, this property enables only WinRM-based remote management, not DCOM-based administration. As a result, by default you can open a Windows PowerShell prompt on a remote server running Windows Server 2012 or Windows Server 2012 R2, or restart a remote server running Windows Server 2012 or Windows Server 2012 R2, because both of these options rely on WinRM. However, you receive an error if you attempt to open Computer Management without opening the needed ports on the remote server, even though this option appears on the shortcut menu of a server that has been added to Server Manager (as shown in Figure 2-2 and Figure 2-3.).
If you discover that you aren’t able to use Server Manager to remotely manage a server in the same domain running Windows Server 2012 or Windows Server 2012 R2, it’s possible that remote management has been disabled manually. If the server is running either a Server With A GUI installation or Minimal Server Interface, you can re-enable this functionality in the Server Manager interface on that remote server. To do so, perform the following steps:
1. In Server Manager, in the Properties area of the Local Server page, click the hyperlink for the Remote Management property, as shown in Figure 2-6.
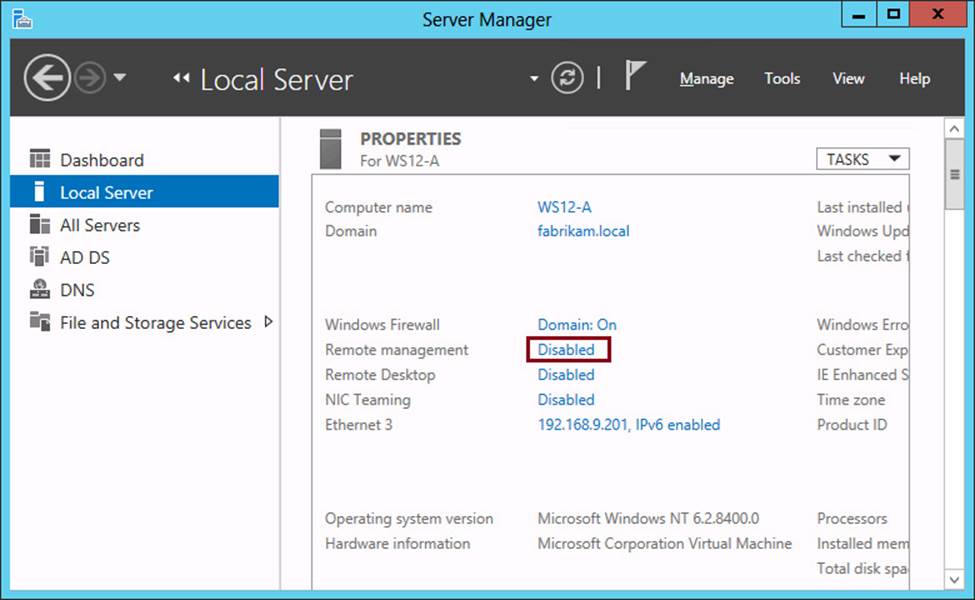
FIGURE 2-6 Re-enabling remote management for Server Manager
2. In the dialog box that opens, select Enable Remote Management Of This Server From Other Computers and then click OK.
Although you need to know how to perform this quick procedure, it might be a bit too straightforward to appear in an exam question. It’s easier to imagine a question in which you need to know how to re-enable remote management at the command prompt:
Configure-SMRemoting.exe -Enable
If you want to disable remote Server Manager management, type the following:
Configure-SMRemoting.exe –Disable
Note
You can also use Configure-SMRemoting -Get to view the current remote management setting on the server.
Note also that before Windows Server 2012, remote Server Manager management required many open ports, and Configure-SMRemoting was a Windows PowerShell script that opened all of those ports. In Windows Server 2012 and Windows Server 2012 R2, remote Server Manager management now relies only on WinRM for most features (such as deploying roles, restarting, and Windows PowerShell) and DCOM for some additional features (such as Computer Management). Consistent with this more efficient remote management method, Configure-SMRemoting configures only WinRM in Windows Server 2012 and Windows Server 2012 R2, and it’s now the equivalent of the command Winrm Quickconfig. As with enabling remote management in the interface or with Winrm Quickconfig, if you enable remote management with Configure-SMRemoting, you still need to enable the DCOM ports manually at a later point if you want more complete remote management functionality by using MMC consoles.
Enabling Remote management on Server Core with Sconfig
Sconfig is a text-based configuration tool that is available in the Server Core version of Windows Server. Sconfig first appeared in Windows Server 2008 R2, so if you received your MCSA in the first release of Windows 2008, you might have missed this handy utility.
Using Sconfig is easy. Just type Sconfig at the command prompt in Server Core and you get a menu of self-explanatory configuration options, one of which (choice #4) is to Configure Remote Management, as shown in Figure 2-7.
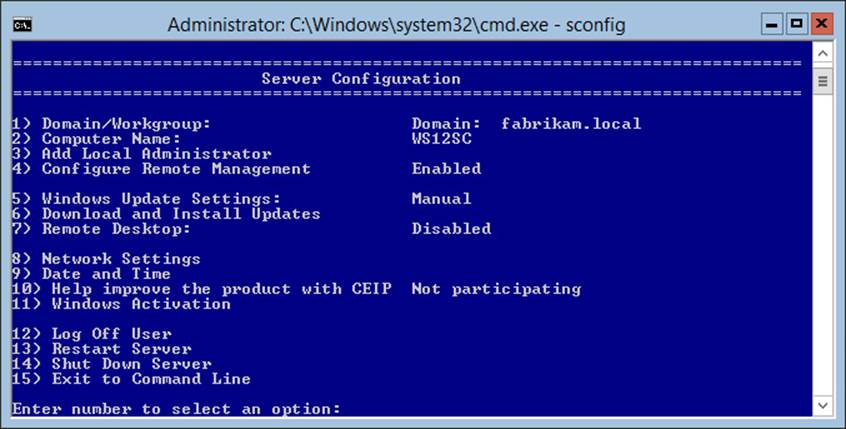
FIGURE 2-7 The Sconfig tool makes it easy to enable remote management in Server Core
Again, as with Winrm Quickconfig and Configure-SMRemoting, enabling remote management in Sconfig configures only WinRM-based remote management.
Configuring remote management of earlier versions of Windows Server
Server Manager can be used to remotely administer computers running older versions of Windows Server. For Windows Server 2008 and Windows Server 2008 R2, Server Manager can be used to perform many of the tasks available in Server Manager, but it can’t be used to add or remove roles. To manage remote servers that are running Windows Server 2008 or Windows Server 2008 R2, or to manage a remote server running Windows Server 2012 from a server running Windows Server 2012 R2, you must first install the following updates, in the order shown.
1. .NET Framework 4 (if the management computer is running the first release of Windows Server 2012) or .NET Framework 4.5 (if the management computer is running Windows Server 2012 R2).
2. Windows Management Framework 3.0 (if the management computer is running the first release of Windows Server 2012) or Windows Management Framework 4.0 (if the management computer is running Windows Server 2012 R2).
The Windows Management Framework download package updates WMI providers on the target servers. The updated WMI providers let Server Manager collect information about roles and features that are installed on the managed servers.
3. The performance update associated with Knowledge Base (KB) article 2682011 (or a superseding update), which allows Server Manager to collect performance data from Windows Server 2008 and Windows Server 2008 R2. (You don’t need to install this update on servers running Windows Server 2012 R2.)
Installing these updates makes these operating systems compatible with Server Manager in 2012. To configure the servers for remote management, run the Winrm Quickconfig command and (optionally) create the inbound firewall rules needed to support MMC traffic. As an alternative to running the Winrm Quickconfig command, you also can perform the following steps:
1. Open an elevated Windows PowerShell prompt.
2. Type Set-ExecutionPolicy RemoteSigned.
3. Type Configure-SMRemoting.ps1 -force -enable.
Note
You cannot use Server Manager to manage a server running Windows Server 2012 R2 from a server running the first release of Windows Server 2012. Also note that for servers running Windows Server 2003 SP2, Server Manager can indicate only whether a server is online or offline.
Using Group Policy to enable remote management
The most efficient way to configure remote management on multiple servers is to use Group Policy. Through Group Policy you can achieve two things: Create WinRM listeners on IP address ranges of your choice and create inbound firewall rules allowing WinRM and DCOM traffic. These steps are described in the following procedure:
1. In a Group Policy Object (GPO) Editor, navigate to Computer Configuration\Administrative Templates\Windows Components\Windows Remote Management and then select WinRM Service. This location within a GPO is shown in Figure 2-8.
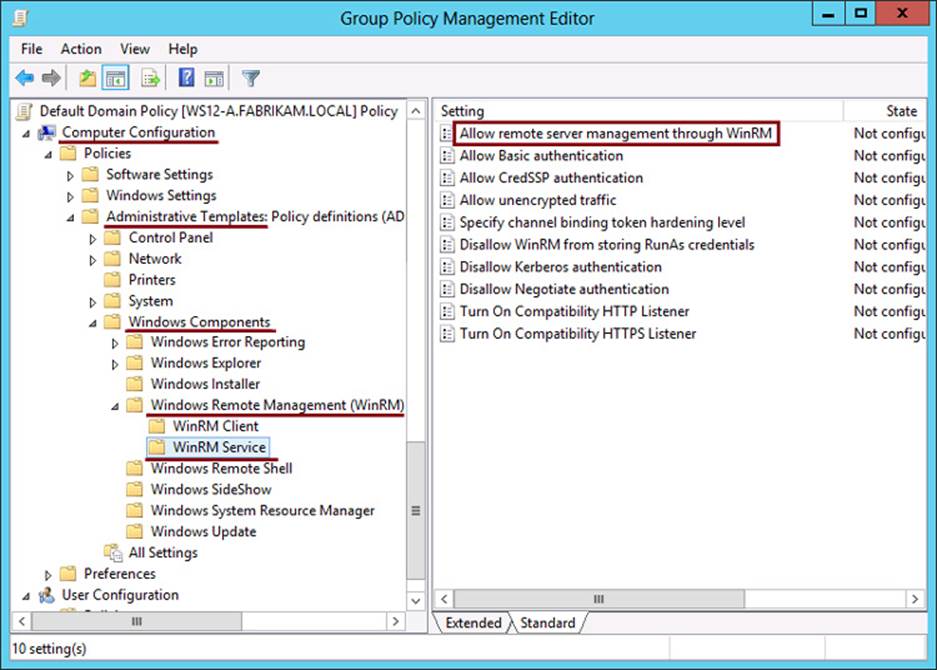
FIGURE 2-8 Configuring WinRM listeners through Group Policy
2. In the details pane, double-click Allow Remote Server Management Through WinRM.
3. In the dialog box that opens, select Enabled (shown in Figure 2-9).
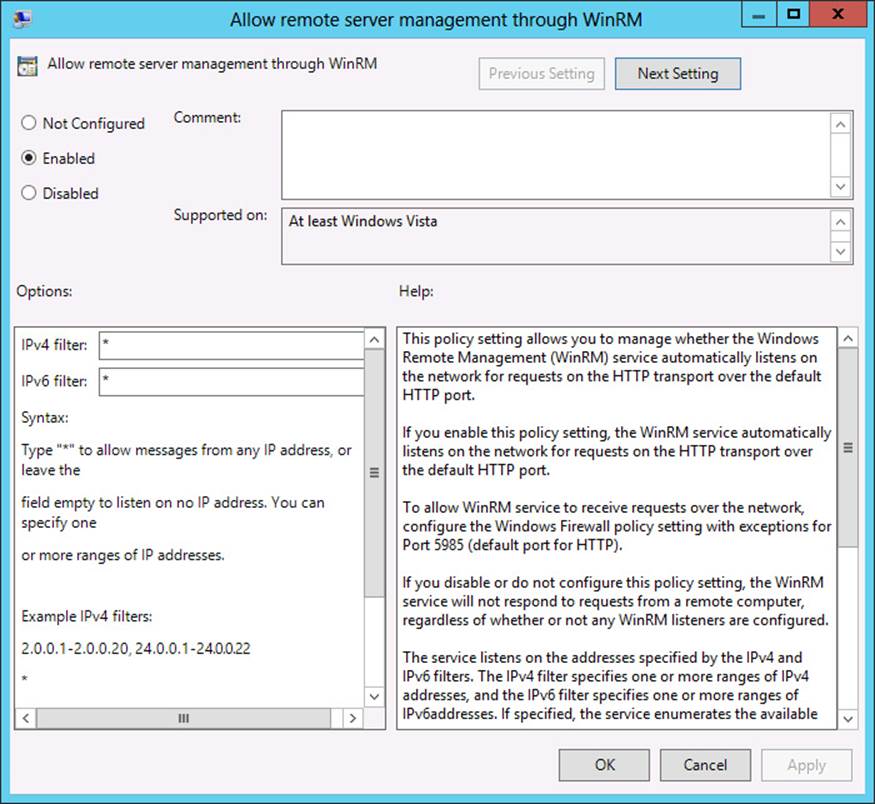
FIGURE 2-9 Configuring WinRM in Group Policy
4. In the IPv4 Filter text box and the IPv6 Filter text box, type the IP address on which you want to allow remote management through WinRM. If you want to enable remote management on all IP addresses, type *.
5. Click OK.
6. In the GPO console tree, navigate to Computer Configuration\Windows Settings\Security Settings\Windows Firewall With Advanced Security\Windows Firewall With Advanced Security.
7. Right-click Inbound Rules and then click New Rule.
8. In the New Inbound Rule Wizard, on the Rule Type page, select Predefined.
9. On the Predefined drop-down menu, select Remote Event Log Management. Click Next.
10. On the Predefined Rules page, click Next to accept the new rules.
11. On the Action page, leave Allow The Connection as the default selection and then click Finish.
12. Repeat steps 7 through 11 to create new inbound rules for the following additional predefined rule types:
![]() Windows Remote Management
Windows Remote Management
![]() COM+ Network Access
COM+ Network Access
![]() Remote Volume Management
Remote Volume Management
![]() Windows Firewall Remote Management
Windows Firewall Remote Management
A GPO configured with these inbound firewall rules is shown in Figure 2-10.
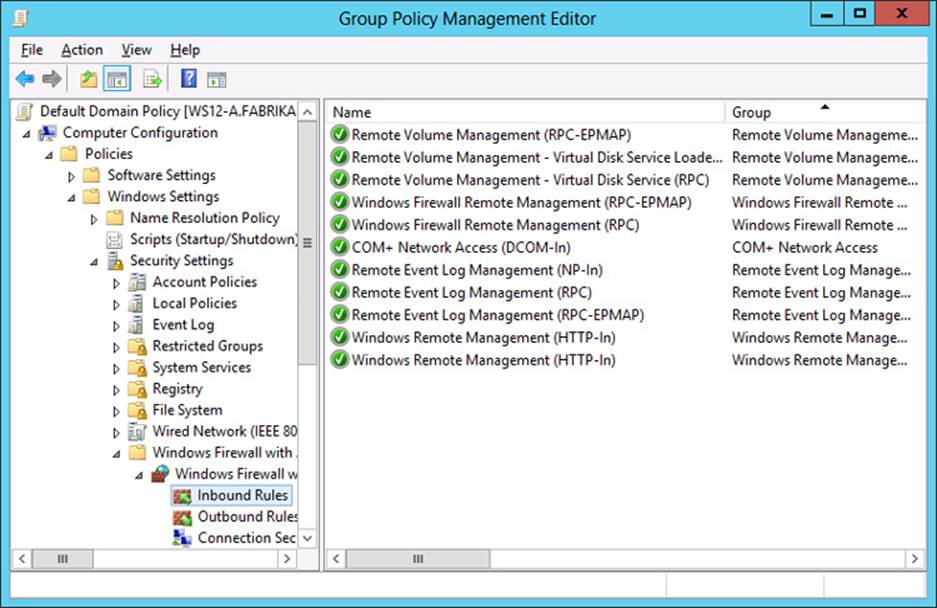
FIGURE 2-10 Firewall rules for remote management
Using Remote Server Administration Tools for Windows 8 and Windows 8.1
To support remote server management from client computers, you can download and install Remote Server Administration Tools for Windows 8 or Remote Server Administration Tools for Windows 8.1. Remote Server Administration Tools includes Server Manager, MMC snap-ins, consoles, Windows PowerShell modules, and some command-line tools for managing roles and features that run on Windows Server 2012 and Windows Server 2012 R2.
 Exam Tip
Exam Tip
In its original form on the 70-410 exam, the Configure Server Roles and Features domain includes objectives named “Configure File and Share Access” and “Configure Print and Document Services.” Even though these objectives aren’t officially indicated for the 70-417 exam, you might see a question about these topics that relates to older features which have not changed in Windows Server 2012 or Windows Server 2012 R2. If your knowledge about these topics is rusty, you should review them. For example, you should be able to answer the following questions: How do you configure access-based enumeration (ABE)? What is the Easy Print driver used for? When might you need to configure two printers for the same print device? What is the Volume Shadow Copy Service (VSS) used for?
Objective summary
![]() Remote management based on the WinRM service is enabled and configured by default in Windows Server 2012 and Windows Server 2012 R2. This is a change from earlier versions of Windows Server.
Remote management based on the WinRM service is enabled and configured by default in Windows Server 2012 and Windows Server 2012 R2. This is a change from earlier versions of Windows Server.
![]() Server Manager in Windows Server 2012 and Windows Server 2012 R2 allows you to manage multiple servers, including deploying roles to remove servers and opening a remote Windows PowerShell session. You can use Server Manager to manage remote servers without any additional configuration if the server running Server Manager and the target server are members of the same Active Directory domain. If the servers are not members of the same domain, you will need to add the remote server to the list of trusted hosts for WinRM on the server running Server Manager. Potentially, you will also have to perform other configuration steps, such as creating a registry key to override UAC restrictions. These other steps depend on factors discussed in this chapter.
Server Manager in Windows Server 2012 and Windows Server 2012 R2 allows you to manage multiple servers, including deploying roles to remove servers and opening a remote Windows PowerShell session. You can use Server Manager to manage remote servers without any additional configuration if the server running Server Manager and the target server are members of the same Active Directory domain. If the servers are not members of the same domain, you will need to add the remote server to the list of trusted hosts for WinRM on the server running Server Manager. Potentially, you will also have to perform other configuration steps, such as creating a registry key to override UAC restrictions. These other steps depend on factors discussed in this chapter.
![]() MMC consoles rely on DCOM as opposed to WinRM, so you need to enable different inbound firewall rules to use them for remote management. The number of inbound rules you need to enable has been greatly reduced in Windows Server 2012 and Windows Server 2012 R2, compared to previous versions.
MMC consoles rely on DCOM as opposed to WinRM, so you need to enable different inbound firewall rules to use them for remote management. The number of inbound rules you need to enable has been greatly reduced in Windows Server 2012 and Windows Server 2012 R2, compared to previous versions.
![]() Servers running pre-Windows Server 2012 versions of Windows Server can be managed remotely in Server Manager. To take full advantage of the administrative tasks and information available, you need to update these remote servers with .NET Framework 4 and Windows Management Framework 3.0 (if the management server is running Windows Server 2012) and with .NET Framework 4.5 and Windows Management Framework 4.0 (if the management server is running Windows Server 2012 R2).
Servers running pre-Windows Server 2012 versions of Windows Server can be managed remotely in Server Manager. To take full advantage of the administrative tasks and information available, you need to update these remote servers with .NET Framework 4 and Windows Management Framework 3.0 (if the management server is running Windows Server 2012) and with .NET Framework 4.5 and Windows Management Framework 4.0 (if the management server is running Windows Server 2012 R2).
![]() The best way to configure multiple servers for remote management is to use Group Policy. In Group Policy, you can configure WinRM and create all the inbound firewall rules you need to support your remote management.
The best way to configure multiple servers for remote management is to use Group Policy. In Group Policy, you can configure WinRM and create all the inbound firewall rules you need to support your remote management.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. A server named SC2012 is running a Server Core installation of Windows Server 2012 R2. You want to manage SC2012 remotely by using Server Manager.
Which of the following will not help you achieve your goal?
A. Configure-SMRemoting.exe
B. Sconfig.exe
C. Winrm Quickconfig
D. Repadmin.exe
2. Your company network includes 25 servers running either Windows Server 2012 or Windows Server 2008 R2 in a single domain. The servers running Windows Server 2008 R2 have been updated with Windows Management Framework 3.0. You now want to configure all of these servers for remote management through Windows PowerShell. What should you do? (Choose all that apply.)
A. Enable the Allow Remote Server Management Through WinRM setting in Group Policy.
B. Enable the Allow Remote Shell Access setting in Group Policy.
C. Configure an inbound firewall policy rule for COM+ Remote Administration.
D. Configure an inbound firewall policy rule for Windows Remote Management.
3. All of your servers are running Windows Server 2012 R2 and are enabled for remote management. You want to remotely manage three of these servers from a server named Admin01. However, when you attempt to manage remote servers through Computer Management on Admin01, you receive error messages.
You create a GPO named Remote Computer Management Firewall Rules and link it to the domain. You now want to use the GPO to create predefined firewall rules in Windows Firewall With Advanced Security. You want to create only the predefined firewall rules that open the ports necessary for remote management through Computer Management. Which of the following predefined inbound rules should you enable? (Choose all that apply.)
A. COM+ Network Access
B. Remote Event Log Management
C. Remote Volume Management
D. WMI
4. You work from a management server named Mgmt1 that is joined to the Corp.contoso.com domain. You want to use Server Manager on Mgmt1 to manage a standalone server named Web1.contoso.com while you are logged in with your normal domain account. Note the following information about Web1:
![]() Web1 is located on the same subnet as Mgmt1.
Web1 is located on the same subnet as Mgmt1.
![]() Web1 is not joined to any Active Directory domain.
Web1 is not joined to any Active Directory domain.
![]() The name of the local administrator account on Web1 is named Web1Admin.
The name of the local administrator account on Web1 is named Web1Admin.
![]() Web1 has a single Ethernet connection and its active network profile is Public.
Web1 has a single Ethernet connection and its active network profile is Public.
Which of the following steps are required to allow you to successfully manage Web1 through Server Manager? (Choose all that apply.)
A. On Web1, open the Windows Remote Management (HTTP-In) firewall rule for the Public profile and add the IP address of Mgmt1 to the list of remote IP addresses on the Scope tab.
B. Use the Manage As option in Server Manager to provide credentials of an administrator on Web1.
C. Set the value of the LocalAccountTokenFilterPolicy property to 1.
D. Add Web1 to the list of TrustedHosts for WinRM on Mgmt1.
 Thought experiment: Managing servers remotely at Fabrikam
Thought experiment: Managing servers remotely at Fabrikam
You are a network administrator at Fabrikam.com, whose network includes 20 servers and 250 clients, all of which belong to the Fabrikam.com domain. Ten servers are running Windows Server 2012 and ten servers are running Windows Server 2008 R2. All clients are running Windows 8.
The IT department is instituting a policy that removes IT personnel from the server room for most day-to-day administration. Administration of all servers from now on will normally be conducted remotely through Server Manager and various MMC consoles. Currently, administration is conducted locally in the server room or through a Remote Desktop connection. The remote management settings on all servers remain at their original defaults.
You can find the answers to these questions in the “Answers” section.
1. All of your servers are located in the server room. Which tool should you use to administer servers remotely from computers running Windows 8?
2. Which inbound rules do you need to create or enable on the servers running Windows Server 2012 to enable remote management through Server Manager?
3. You want to be able to remotely manage the servers running Windows Server 2012 using Computer Management, Disk Management, and Windows Firewall With Advanced Security. Which inbound rules should you enable in Group Policy?
4. You run the Winrm Quickconfig command on your servers running Windows Server 2008 R2. However, you find that you cannot manage these servers remotely by using Server Manager. In addition, some MMC administration tools don’t work as they do on the servers running Windows Server 2012. How should you fix this problem?
Answers
This section contains the answers to the Objective Review and the Thought Experiment.
Objective 2.1: Review
1. Correct answer: D
A. Incorrect: This command, when used with the –enable parameter, enables remote management on Windows Server 2012 and Windows Server 2012 R2.
B. Incorrect: This command opens a utility in Server Core that allows you to enable remote management of the local server.
C. Incorrect: This command enables remote management on Windows Server 2012 and Windows Server 2012 R2.
D. Correct: This tool helps administrators diagnose Active Directory replication problems between domain controllers. It doesn’t help you enable remote management.
2. Correct answers: A, D
A. Correct: Remote management through Windows PowerShell relies on the WinRM service. You can use this policy setting to configure WinRM listeners on your servers.
B. Incorrect: This policy setting does not affect Windows PowerShell.
C. Incorrect: This firewall rule does not open any of the ports needed by Windows PowerShell.
D. Correct: This firewall rule opens the port needed for WinRM-based communication and is required for Windows PowerShell remoting.
3. Correct answers: A, B, C
A. Correct: This predefined rule allows you to connect to a remote computer through Computer Management and use a few system tools, such as Shared Folders and Local Users And Groups.
B. Correct: This predefined rule group allows you to manage computers remotely in Computer Management through the Event Viewer system tool and the Task Scheduler system tool.
C. Correct: This predefined rule group allows you to use Disk Management remotely in Computer Management.
D. Incorrect: This predefined rule doesn’t enable you to use any tools in Computer Management.
4. Correct answers: B, C, D
A. Incorrect: This step is necessary only when the active network profile on the target server is Public and the server running Server Manager is found on a subnet that is different from the target server’s subnet. In this case, the Public profile is active on Web1, but Mgmt1 and Web1 are located on the same subnet.
B. Correct: The question states that you want to use your normal domain account on Mgmt1, so to manage Web1remotely, you will need to specify the credentials of an administrator on that machine.
C. Correct: To overcome restrictions related to User Account Control in workgroup environments, you need to create this REG_DWORD entry in HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion on the target server and set its value to 1.
D. Correct: Server Manager relies on WinRM. To use WinRM to manage a remote server outside of a domain environment, you need to add the target computer to the list of TrustedHosts on the managing computer. In this case, you need to add Web1 to the list of TrustedHosts on Mgmt1.
Thought experiment
1. You should use Remote Server Administration Tools for Windows 8.
2. You don’t need to create or enable any inbound rules. Servers running Windows Server 2012 have the required rules enabled by default.
3. You should enable COM+ Network Access (DCOM-In), Remote Event Log Management, Remote Volume Management, and Windows Firewall Remote Management.
4. You should install .NET Framework 4, Windows Management Framework 3.0, and the update associated with KB article 2682011.