CCNP Routing and Switching SWITCH 300-115 Official Cert Guide (2015)
Part VII. Securing Switched Networks
Chapter 22. Managing Switch Users
This chapter covers the following topics that you need to master for the CCNP SWITCH exam:
![]() Configuring Authentication: This section describes methods you can use to authenticate users when they need to connect to and manage a switch.
Configuring Authentication: This section describes methods you can use to authenticate users when they need to connect to and manage a switch.
![]() Configuring Authorization: This section covers methods that can authorize or grant privilege to administrative users on a switch.
Configuring Authorization: This section covers methods that can authorize or grant privilege to administrative users on a switch.
![]() Configuring Accounting: This section discusses methods that you can use to record events that occur while an administrative user is connected to a switch.
Configuring Accounting: This section discusses methods that you can use to record events that occur while an administrative user is connected to a switch.
Catalyst switches have a variety of methods that can secure or control user access. Users can be authenticated as they connect to or through a switch, and can be authorized to perform certain actions on a switch. User access can also be recorded as switch accounting information. This chapter discusses methods you can use to control who has access to a switch and what they can do once they are logged in.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt based on your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 22-1 outlines the major headings in this chapter and the “Do I Know This Already?” quiz questions that go with them. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes.”
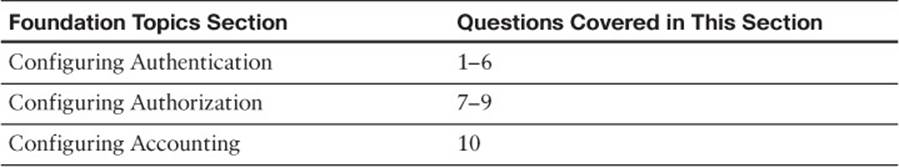
Table 22-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
1. The acronym AAA represents which three of the following functions?
a. Analysis
b. Authentication
c. Accounting
d. Administration
e. Authorization
f. Accounts
2. If the username command is used in a switch configuration, which one of the following authentication methods is implied?
a. Remote
b. Local
c. RADIUS
d. TACACS+
3. Which two external methods of authentication do Catalyst switches support?
a. Pre-shared key
b. Active Directory
c. RADIUS
d. KERBEROS
e. TACACS+
4. Which one of the following commands should be used to configure a vty line to use the myservers authentication method list?
a. line authentication myservers
b. authentication myservers
c. authentication method myservers
d. login authentication myservers
5. A RADIUS server is located at IP address 192.168.199.10. Which one of the following commands configures a Catalyst switch to find the server?
a. authentication radius 192.168.199.10
b. aaa radius 192.168.199.10
c. radius-server host 192.168.199.10
d. radius server 192.168.199.10
6. Suppose that the following configuration command has been entered on a Catalyst switch. Which one answer correctly identifies the authentication method that will be used first when a user tries to connect to the switch?
Switch(config)# aaa authentication login default radius tacacs+ local
a. RADIUS servers
b. Locally defined usernames
c. TACACS+ servers
d. Default line passwords
e. None of the these answers; all methods are tried simultaneously
7. If a user needs to be in privileged EXEC or enable mode, which part of AAA must succeed? (Choose one correct answer.)
a. Authentication
b. Authorization
c. Accounting
d. Administration
8. What happens if authorization is not configured on a switch? (Choose one correct answer.)
a. Authenticated users cannot use any switch commands.
b. Authenticated users must authenticate themselves to move to a higher privilege level.
c. Authenticated users can use any switch command.
d. Authorization cannot be disabled or omitted.
9. Which two of the following commands will begin a configuration that will authorize users to run any switch command and to make configuration changes?
a. aaa authorization commands ...
b. aaa authorization exec ...
c. aaa authorization config-commands ...
d. aaa authorization config all ...
e. aaa authorization any any
10. Suppose you would like to configure AAA accounting to keep a record of switch commands that are entered by users. Which one of the following commands should you enter to accomplish your goal?
a. aaa accounting exec default start-stop mymethods
b. aaa accounting commands 15 default start-stop mymethods
c. aaa accounting system commands start-stop mymethods
d. aaa accounting commands 15 default none mymethods
Foundation Topics
You can manage user activity to and through a switch with authentication, authorization, and accounting (AAA) features. AAA uses standardized methods to challenge users for their credentials before access is allowed or authorized. Accounting protocols also can record user activity on a switch.
In a nutshell, you can think of AAA in the following manner:
![]() Authentication: Who is the user?
Authentication: Who is the user?
![]() Authorization: What is the user allowed to do?
Authorization: What is the user allowed to do?
![]() Accounting: What did the user do?
Accounting: What did the user do?
As a network administrator, you have several methods to manage users who might try to log in to one of your switches to perform some operation. At the most basic level, you could avoid any authentication other than simple passwords configured on the switch console and vty lines. Authorization can be equally simple: When users successfully log in, they are authorized for EXEC level privileges. By entering the correct enable secret password, users can be authorized for a higher privilege level.
Under the simple scenario, if a user knows the correct password, he can connect to the switch. But who is that user? You might never know who actually logged in and changed the configuration or rebooted the switch! Instead, you could use the username command to configure individual usernames and passwords on the switch. That would solve the user anonymity problem, but your network might consist of many administrative users and many switches, requiring quite a bit of username configuration and maintenance.
A more scalable solution is to leverage AAA functions that are centralized, standardized, resilient, and flexible. For example, a centralized authentication server can contain a database of all possible users and their passwords, as well as policies to authorize user activities. As users come and go, their accounts can be easily updated in one place. All switches and routers query the AAA server to get up-to-date information about a user.

Cisco switches can use the following two protocols to communicate with AAA servers:
![]() TACACS+: A Cisco proprietary protocol that separates each of the AAA functions; communication is secure and encrypted over TCP port 49.
TACACS+: A Cisco proprietary protocol that separates each of the AAA functions; communication is secure and encrypted over TCP port 49.
![]() RADIUS: A standards-based protocol that combines authentication and authorization into a single resource; communication uses UDP ports 1812 and 1813 (accounting), but is not completely encrypted.
RADIUS: A standards-based protocol that combines authentication and authorization into a single resource; communication uses UDP ports 1812 and 1813 (accounting), but is not completely encrypted.
Both TACACS+ and RADIUS are arranged as a client/server model, where a switch acts as a client talking to a AAA server. Figure 22-1 shows a simplified view of the process. In the AAA client role, a switch is often called a network access device (NAD) or network access server (NAS). When a user tries to connect to a switch, the switch challenges the user for credentials, then passes the credentials along to the AAA server. In simple terms, if the user passes authentication, the AAA server returns an “accept” message to the switch. Otherwise, a “reject” message is returned.
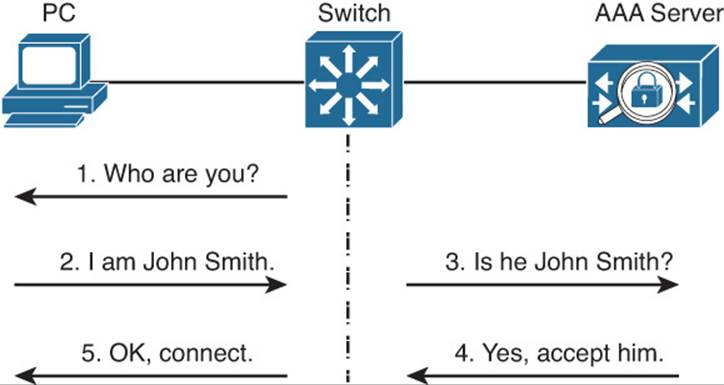
Figure 22-1 A Simplified View of AAA
Cisco implements AAA services in its Identity Services Engine (ISE) and Cisco Secure Access Control Server (ACS).
Configuring Authentication
Switch access can be granted only after a user’s identity has been validated. User authentication is commonly used on switches and routers to permit remote access to the network administration staff only. In this case, when someone uses Telnet or Secure Shell (SSH) to log in to a switch, that individual is challenged to provide a username and password. The individual’s credentials are then submitted to a device that can grant the user access.

User authentication can be handled by several methods:
![]() Usernames and passwords configured locally on the switch
Usernames and passwords configured locally on the switch
![]() One or more external Remote Authentication Dial-In User Service (RADIUS) servers
One or more external Remote Authentication Dial-In User Service (RADIUS) servers
![]() One or more external Terminal Access Controller Access Control System+ (TACACS+) servers
One or more external Terminal Access Controller Access Control System+ (TACACS+) servers
Any combination of these methods can be used. In fact, authentication must be defined by grouping the desired methods into a method list. The list contains the types or protocols that will be used, in the sequential order that they will be tried.
To use authentication on a Catalyst switch, you must configure several things in the following order:
Step 1. Enable AAA on the switch. By default, AAA is disabled. Therefore, all user authentication is handled locally by configuring usernames and passwords on the switch itself. To enable AAA, use the following global configuration command:
Switch(config)# aaa new-model
The new-model refers to the use of method lists, by which authentication methods and sources can be grouped or organized. The new model is much more scalable than the “old model,” in which the authentication source was explicitly configured.
Step 2. Define the source of authentication.
You can compare user credentials against locally configured usernames and passwords, or against a database managed by external RADIUS or TACACS+ servers.
Use locally configured usernames and passwords as a last resort, when no other authentication servers are reachable or in use on the network. To define a username, use the following global configuration command:
Switch(config)# username username password password
RADIUS or TACACS+ servers are defined in groups. First, define each server along with its secret shared password. This string is known only to the switch and the server, and provides a key for encrypting the authentication session. Use one of the following global configuration commands:
Switch(config)# radius-server host {hostname | ip-address} [key
string]
Switch(config)# tacacs-server host {hostname | ip-address} [key
string]
Then define a group name that will contain a list of servers, using the following global configuration command:
Switch(config)# aaa group server {radius | tacacs+} group-name
Define each server of the group type with the following server-group configuration command:
Switch(config-sg)# server ip-address
You can define multiple RADIUS or TACACS+ servers by repeating the commands in this step.
Step 3. Define a list of authentication methods to try.
You can list switch login authentication methods by giving the method a descriptive name or using the unnamed “default” method. List each method or protocol type in the order that it should be tried. If none of the servers for the first method responds, the switch will try the servers in the next method listed.
Use the following global configuration command to define a method list:
Switch(config)# aaa authentication login {default | list-name}
method1 [method2 ...]
Here the methods refer to the following keywords:
![]() tacacs+: Each of the TACACS+ servers configured on the switch is tried, in the order that it was configured.
tacacs+: Each of the TACACS+ servers configured on the switch is tried, in the order that it was configured.
![]() radius: Each of the RADIUS servers configured on the switch is tried, in the order that it was configured.
radius: Each of the RADIUS servers configured on the switch is tried, in the order that it was configured.
![]() local: The user’s credentials are compared against all the username commands configured on the local switch.
local: The user’s credentials are compared against all the username commands configured on the local switch.
![]() line: The line passwords authenticate any connected user. No usernames can be used.
line: The line passwords authenticate any connected user. No usernames can be used.
Tip
Be sure to add either the local or line methods at the end of the list, as a last resort. This way, if all the RADIUS or TACACS+ servers are unavailable or the switch is completely isolated from the rest of the network, a locally configured authentication method will eventually be used. Otherwise, you will never be able to access the switch until at least one of the servers comes back online.
Step 4. Apply a method list to a switch line.
First, select a line (console or vty for Telnet/SSH access) using the line line command. Then trigger the user authentication on that line to use an AAA method list. Use the following line-configuration command:
Switch(config-line)# login authentication {default | list-name}
You can use the default method list only if one list is sufficient for all circumstances on the switch. Otherwise, if you have configured named method lists, you can reference one of them here.
Step 5. After authentication is configured on a switch, it is a good idea to stay logged in on one session so that the authentication can be tested. If you exit the configuration session, you will not be able to log in again if the authentication is misconfigured. While you stay logged in on the original session, bring up a new Telnet session to the switch. If you can authenticate successfully, everything is configured properly.
Example 22-1 lists the commands necessary to configure a switch to use two TACACS+ servers to authenticate management users. The servers are 192.168.10.10 and 192.168.10.11, also known as the AAA group named myauthservers. AAA authentication group myauth is configured to try the TACACS+ server group; if none of the servers is available, local authentication will be used instead. Notice that a username lastresort is configured for that case. Finally, the myauth method is used to authenticate users on lines vty 0 through 15 for Telnet or SSH access.
Example 22-1 An Example AAA Authentication Configuration
Switch(config)# aaa new-model
Switch(config)# username lastresort password MySecretP@ssw0rd
Switch(config)# tacacs-server host 192.168.10.10 key t@c@csk3y
Switch(config)# tacacs-server host 192.168.10.11 key t@c@csk3y
Switch(config)# aaa group server tacacs+ myauthservers
Switch(config-sg)# server 192.168.10.10
Switch(config-sg)# server 192.168.10.11
Switch(config-sg)# exit
Switch(config)# aaa authentication login myauth group myauthservers local
Switch(config)# line vty 0 15
Switch(config-line)# login authentication myauth
Configuring Authorization
After a user is authenticated, the switch allows access to certain services or switch commands based on the user’s privilege level. Authenticated users are put at the EXEC level by default.
Certain commands, such as show interface, are available at the EXEC level. Other commands, such as configure terminal, are accessible only if the user is able to move into the privileged EXEC or enable mode.
Authorization provides a means of granting specific users the ability to perform certain tasks. As with authentication, authorization is performed by querying external RADIUS or TACACS+ servers. If the authorization server has an entry for a user and a service or command, the switch allows the user to perform that task.
Configure authorization by first defining any RADIUS or TACACS+ servers that will be used. These normally are defined as part of the authentication configuration and do not need to be redefined for authorization.
Next, define a method list of authorization methods that will be tried in sequence using the following global configuration command:
Switch(config)# aaa authorization {commands | config-commands
| configuration | exec | network | reverse-access} {default |
list-name} method1 [method2 ...]
Here you specify the function or service needing authorization with one of the following keywords:
![]() commands: The server must return permission to use any switch command at any privilege level.
commands: The server must return permission to use any switch command at any privilege level.
![]() config-commands: The server must return permission to use any switch configuration command.
config-commands: The server must return permission to use any switch configuration command.
![]() configuration: The server must return permission to enter the switch configuration mode.
configuration: The server must return permission to enter the switch configuration mode.
![]() exec: The server must return permission for the user to run a switch EXEC session. The server also can return the privilege level for the user so that the user immediately can be put into privileged EXEC (enable) mode without having to type in the enable command.
exec: The server must return permission for the user to run a switch EXEC session. The server also can return the privilege level for the user so that the user immediately can be put into privileged EXEC (enable) mode without having to type in the enable command.
![]() network: The server must return permission to use network-related services.
network: The server must return permission to use network-related services.
![]() reverse-access: The server must return permission for the user to access a reverse Telnet session on the switch.
reverse-access: The server must return permission for the user to access a reverse Telnet session on the switch.
You can identify the method with a descriptive name (list-name) if you are configuring more than one list. Otherwise, a single unnamed list is called the default list. Each authorization method then is listed in the order it will be tried. The methods can be any of the following values:
![]() group group-name: Requests are sent to the servers in a specific group.
group group-name: Requests are sent to the servers in a specific group.
![]() group {radius | tacacs+}: Requests are sent to all servers of this type.
group {radius | tacacs+}: Requests are sent to all servers of this type.
![]() if-authenticated: Requests are granted if the user already is authenticated.
if-authenticated: Requests are granted if the user already is authenticated.
![]() none: No external authorization is used; every user is authorized successfully.
none: No external authorization is used; every user is authorized successfully.
Tip
Only TACACS+ servers can authorize users with permission to use specific commands. RADIUS servers offer more of an all-or-nothing approach.
Next, you can apply an authorization method list to a specific line on the switch. Users accessing the switch through that line will be subject to authorization. Use the following line configuration command:
Switch(config-line)# authorization {commands level | exec | reverse-access}
{default | list-name}
If you do not use this command, the default group is used for all lines. To configure a switch to use AAA authorization for all lines, you enter the following:
Switch(config)# aaa authorization exec default group myauthservers none
The AAA servers contained in the group myauthservers (configured previously in Example 22-1) are used as a default method to allow authenticated users into the EXEC mode or any other privilege level granted.
Configuring Accounting
Catalyst switches also support the capability to use AAA for producing accounting information of user activity. This accounting information can be collected by RADIUS and TACACS+ servers. Again, the RADIUS and TACACS+ servers must already be configured and grouped as part of the authentication configuration.
As usual, you must define a method list giving a sequence of accounting methods by using the following global configuration command:
Switch(config)# aaa accounting {system | exec | commands level} {default
| list-name} {start-stop | stop-only | wait-start | none} method1 [method2
...]
The function triggering the accounting can be one of the following keywords:
![]() system: Major switch events such as a reload are recorded.
system: Major switch events such as a reload are recorded.
![]() exec: User authentication into an EXEC session is recorded, along with information about the user’s address and the time and duration of the session.
exec: User authentication into an EXEC session is recorded, along with information about the user’s address and the time and duration of the session.
![]() commands level: Information about any command running at a specific privilege level is recorded, along with the user who issued the command.
commands level: Information about any command running at a specific privilege level is recorded, along with the user who issued the command.
You can specify that certain types of accounting records be sent to the accounting server using the following keywords:
![]() start-stop: Events are recorded when they start and stop.
start-stop: Events are recorded when they start and stop.
![]() stop-only: Events are recorded only when they stop.
stop-only: Events are recorded only when they stop.
![]() none: No events are recorded.
none: No events are recorded.
Next, you can apply an accounting method list to a specific line (console or vty) on the switch. Users accessing the switch through that line will have their activity recorded. Use the following line-configuration command to accomplish this:
Switch(config-line)# accounting {commands level | connection | exec}
{default | list-name}
If you do not use this command, the default group will be used for all lines. In Example 22-2, AAA accounting is configured for all lines on the switch, using the AAA servers contained in the myauthservers group (configured in Example 22-1). User EXEC sessions will be recorded as they start and stop, along with user information. Any commands that are entered while a user is in privilege level 15 (enable mode) will be recorded, too.
Example 22-2 Configuring AAA Accounting
Switch(config)# aaa accounting exec default start-stop group myauthservers
Switch(config)# aaa accounting commands 15 default start-stop group myauthservers
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 22-2 lists a reference of these key topics and the page numbers on which each is found.


Table 22-2 Key Topics for Chapter 22
Complete Tables and Lists from Memory
There are no memory tables in this chapter.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
AAA
NAS
RADIUS
TACACS+
Use Command Reference to Check Your Memory
This section includes the most important configuration and EXEC commands covered in this chapter. It might not be necessary to memorize the complete syntax of every command, but you should remember the basic keywords that are needed.
To test your memory of the configuration commands presented in this chapter, cover the right side of Table 22-3 with a piece of paper, read the description on the left side, and then see how much of the command you can remember.
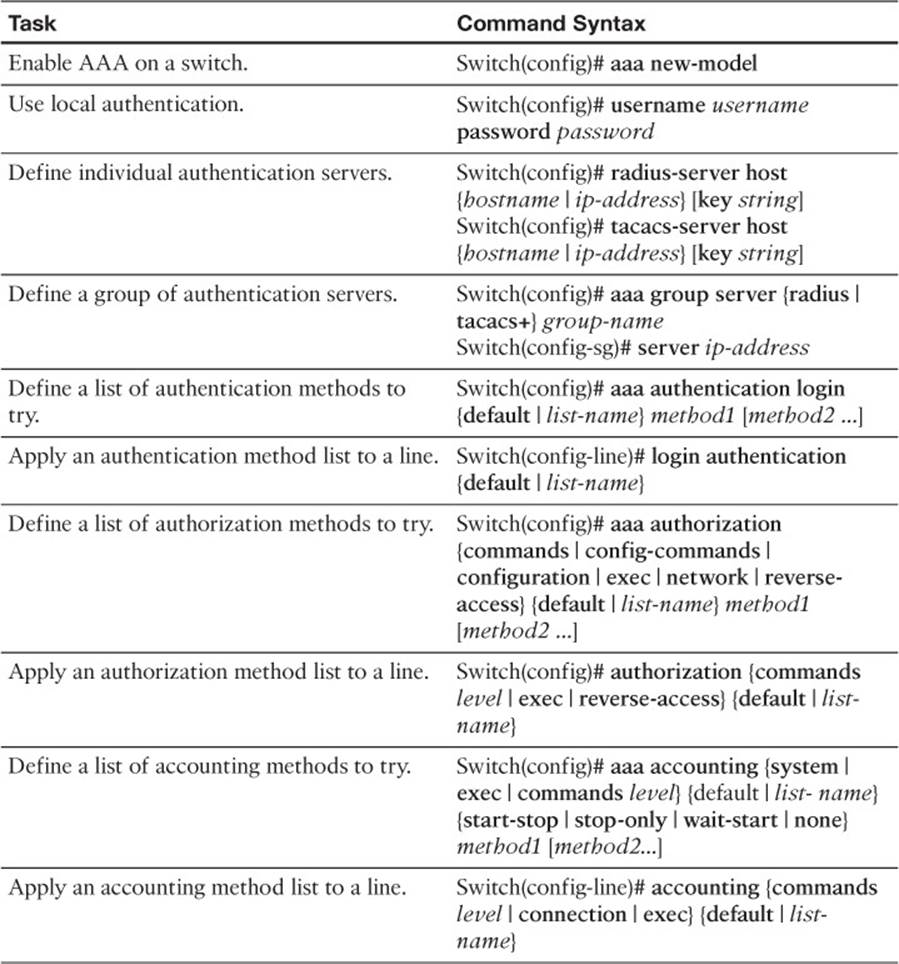
Table 22-3 AAA Configuration Commands