Learn PHP 7: Object-Oriented Modular Programming using HTML5, CSS3, JavaScript, XML, JSON, and MySQL (2016)
Chapter 2. Interfaces, Platforms, Containers, and Three-Tier Programming
Steve Prettyman1
(1)
Georgia, USA
Electronic supplementary material
The online version of this chapter (doi:10.1007/978-1-4842-1730-6_2) contains supplementary material, which is available to authorized users.
“As of January 2013, PHP was installed on more than 240 million web sites (39% of those sampled) and 2.1 million web servers.”
—Ide, Andy (2013-01-31). “PHP Just Grows & Grows ”
Chapter Objectives/Student Learning Outcomes
After completing this chapter, the student will be able to:
· Give examples of platforms or containers that can host PHP programs
· Create a simple dynamic web application using PHP
· Explain three-tier design and determine what is contained in each tier
· Design a three-tier application
· Explain each step of the program development lifecycle (PDLC)
· Define and explain MVC and Dependency Injection
PHP Platforms and Containers
PHP is a powerful language because it can be adapted for use on almost any hardware or software platform. The ease at which it interfaces with HTML and JavaScript provides the ability for PHP applications to run on any system that can host a browser. More and more applications are now being created using browsers as the main interface tool for the application. This allows the application to run on PCs, the Internet, and even in smart phones without the requirement of installing the actual application (or other software) on the device. It also allows users to experience the same “feel” for the application when they switch between devices.
In the following sections, we will take a brief look at some of the platforms and containers that can host PHP applications. We will use the words platform and container interchangeably. In this discussion we consider a platform or container a software tool that “hosts” the PHP program and any output returned by executing the program.
PHP PC Applications
PHP programs can be developed to run as PC applications hosted within an operating system. However, the skills needed to create these applications require an in-depth understanding of communication between operating systems and event-driven PHP programs. These advanced skills are beyond the concepts shown in this introductory book. However, some might also argue that the skills needed to accomplish this are unnecessary since a PHP program can run within any browser residing in any operating system.
PHP PC applications do have the ability to “create once” and “run anywhere,” as with other languages (such as Java). PHP PC applications can be created to require no (or little) code changes between PC operating systems and hardware platforms.
The GTK SDK (Software Development Kit) is one of several tools that can be used for PC application development. If you visit the web site ( http://gtk.php.net/ ), you can find information on the latest version and future development.
If you are curious about PHP PC application development, try the link below or search in your browser for “PHP GTK Tutorial”.
http://www.developertutorials.com/building-desktop-applications-in-php-8-02-01/
PHP Smart Phone Applications
PHP can also be used to create smart phone apps. Usually this occurs as an attempt to retrofit a current web application to the smart phone environment. Smart phone application development requires advanced skills in developing communication links between your program and the smart phone operating system.
Smart phone apps may be necessary to use some of the features built into the smart phone operating system (such as GPS). All smart phone operating systems provide API (Application Program Interface) calls that allow applications residing on the phone to use these features. Although web applications (discussed later in this chapter) can run in a browser on a smart phone, they cannot make API calls to the smart phone operating system (since they are not hosted within the phone itself). If the application requires the ability to interface with the smart phones operating system, it must reside on the smart phone.
Developing smart phone applications require advanced programming skills and an in-depth knowledge of the smart phone operating systems. Some of this hassle can be reduced by using one of the free smart phone SDKs (Software Development Kits) available today. Some SDKs now provide the ability to convert applications for use on multiple operating systems.
You should have good basic PHP skills before attempting to create smart phone applications.
PHP Facebook and Other Social Applications
PHP can be used to create applications (and games) that are hosted in the Facebook Canvas Platform and other social applications (such as Twitter). The techniques used in these applications are similar. We will take a brief look at the Facebook Canvas as an example.
Applications can uses tools in Facebook itself (such as the Facebook Login) using API (Application Program Interface) calls. For example, an application can use Facebook tools to monitor the use of the application. When a user signs in to an application (or game) using the Facebook sign-in, the user must acknowledge and accept the security levels necessary to run the program. By accepting these settings, the user is giving the application permission to make API calls to retrieve information (and may be change information) from the user’s Facebook environment.
You can create PHP applications that are merely hosted by Facebook that do not require the knowledge of API programming. Many advertisements that include click-through ability for more information are hosted in the Canvas but actually reside on a web server located somewhere else on the Internet. The Facebook Canvas does have the ability to interpret HTML and JavaScript code. This enables the developer to create an application that could both be displayed in the Canvas and externally in a browser.
Let’s take a brief look at how you could host an application in the Facebook Canvas.
You will keep the development in “developer’s” mode. This simply means that when you have completed the demo, everyone in Facebook will not be able to access the application. There are additional steps you must go through to make your application ‘live’ (seedevelopers.facebook.com for details).
Warning
Facebook constantly changes its security settings and API (Application Programmer Interface). Some of the following steps might slightly change over time. If you find these steps do not work, search the Internet for “A Simple PHP Facebook App” and check the creation date of the tutorial or videos to ensure that you have the most up-to-date information.
Do It
Complete the following:
1.
For this example, you need to use your browser to search for an existing secure web page (one that uses https instead of http). Facebook no longer allows non-secured web pages to be hosted in the Canvas. Since this is a PHP book, it would be preferable to find a web application that includes PHP code (one that has a file ending of php instead of html). However, you can use an HTML site for this example. Remember, this is just for demonstration and educational purposes. You should always request permission to host a web site in another site (such as Facebook Canvas). All web sites are assumed to be protected by copyright laws (even when there is no indication on the site that they are copyrighted).
Note: Some sites are secured to not allow their site to be hosted in another site. If you follow these directions and the site does not display, that may be the cause. If that happens, search for another secured web page.
You could elect to use your own web page (such as the hello world example). However, the web page will need a hosting environment (besides your PC). Facebook cannot interface with your localhost development environment. There are many low-price hosting sites now available; some for as little as $1 a month. Most hosting companies enable you to have secured sites (using https). However, there is usually an additional fee for this service.
When picking a host site, make sure to read the fine print to determine if it will host PHP applications. It is a good idea to have a hosting site for you to upload your test programs. Programs should be tested in multiple environments. Sometimes programs react differently in different environments.
If you have your own secure URL, or one that your school allows you to use, upload your Hello World program onto the host. Then test it to make sure it still works in the host and make sure that you know the actual URL address that will run the program.
2.
Sign in to Facebook ( www.facebook.com ). If you do not have a Facebook user ID/password, you can create one for free. This demo does not require you to completely build a Facebook page. If you have an existing account, you might consider creating an extra account (with a different e-mail address) just for your development needs.
3.
Once you are signed in to Facebook, go to the developer’s page (developers.facebook.com). Find the Menu on the page. Select Apps, and then select Add New App. A screen similar to the one shown in Figure 2-1 will appear. Locate and select the Facebook Canvas option.
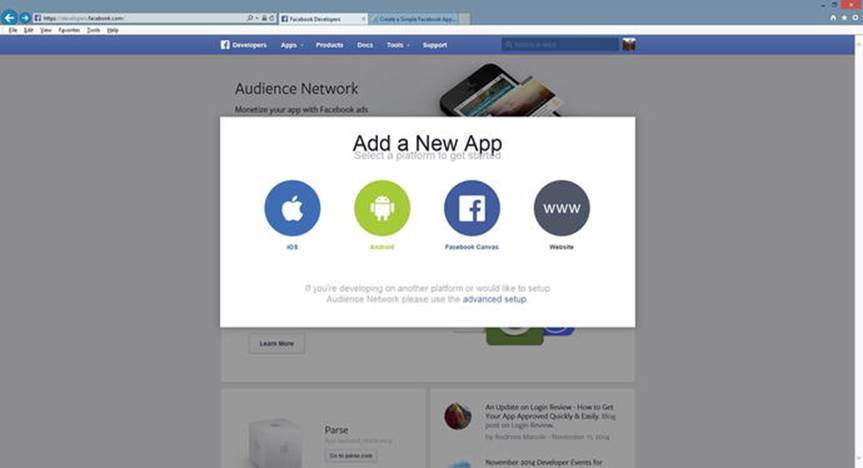
Figure 2-1.
Selecting Canvas from Facebook developer’s page (11/17/14)
(Remember that Facebook does change their screens. However, the sign-in process should be similar to this demo.)
The next screen requires you to enter a name for your application. Any unique name is fine since this application will not become live. You might also be prompted with some other questions related to whether this app is part of another app (no) and you may be requested to select a category (Apps for Pages would be fine). Once you have filled (and selected) the required information click the Create App ID button.
4.
You should now see a Quick Start page similar to Figure 2-2. Ignore the code at the top of the Quick Start page (it’s beyond what we want to accomplish). Scroll down the page to find the textbox that says, “Where Is Your App Hosted?”. You may see a textbox (not required) that requests you to enter a unique URL for your app. If you do not enter one, Facebook will generate one. For our demo, we will leave it blank.
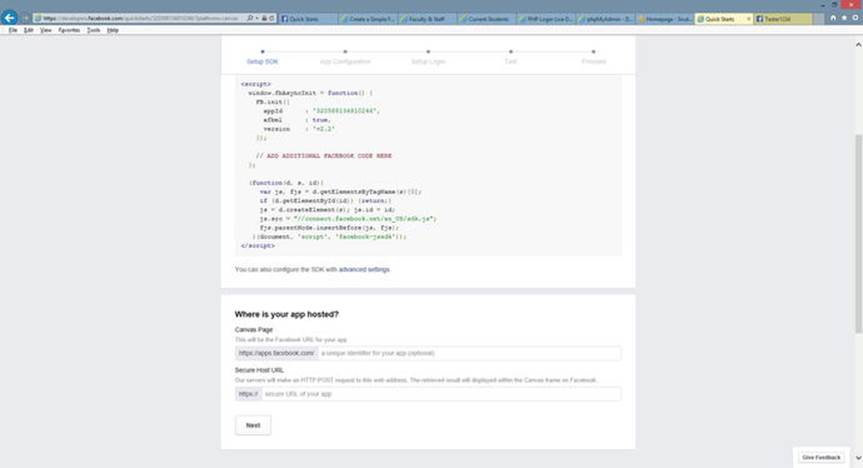
Figure 2-2.
The Facebook Quick Start page
Another textbox requires you to enter a secure URL to link your app into Facebook. This is the actual location of your application on the Internet. Enter the complete address of the secure web page you have discovered or enter the location of your “Hello World” program if it is hosted on a secure site (https).
Note: Facebook requires (at least) an ending slash for your link, something similar to:
www.mysita.com/projects/myfirstprogram.php/
Click the Next button.
5.
The next page displayed will show more example code. This code can be used to log in to your application using the Facebook login and has the ability to request Facebook permissions for your application. However, our demo does not need login ability or any Facebook permissions. Just click the Next button at the bottom of the page.
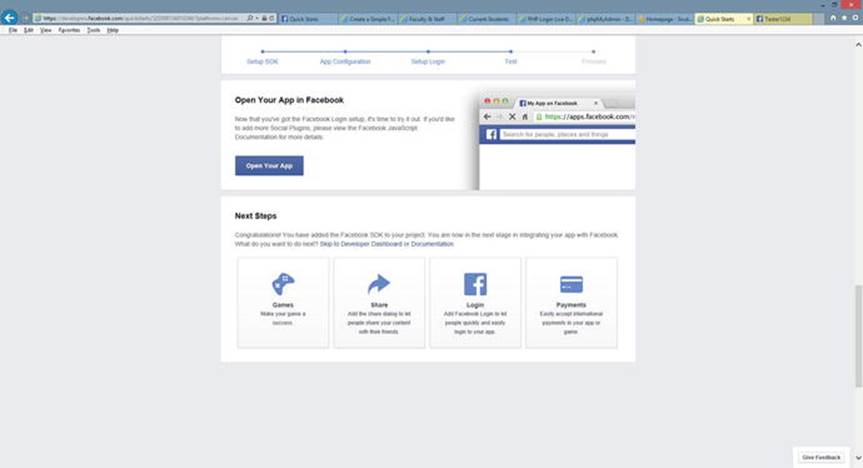
Figure 2-3.
The Facebook Open App page
6.
Click the Open Your App button. Once you click the button, Facebook will try to load your page in the Canvas.
However, if you have picked an existing secure web page and see a message similar to Figure 2-4, the page you selected might not allow hosting in another site. If this happens, go to Steps 7-10. If you were successful, skip to Step 11. However, copy and paste the URL (from the browser) that Facebook uses to display your page, so you can test it again, if needed.
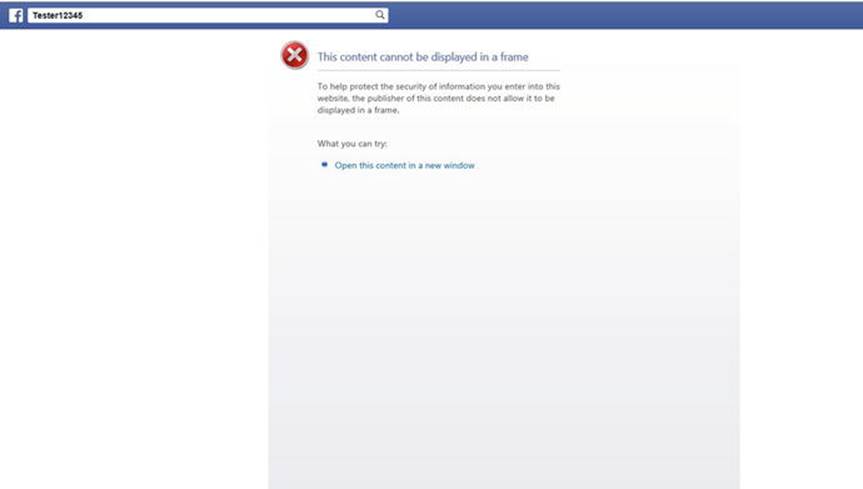
Figure 2-4.
Facebook open app failure
7.
If your page did not display, do the following. After you have copied the URL, close the test page. You now want to find the “Dashboard” for your app. If it is not visible on your Developers Facebook page, go to the menu at the top of the page and select Apps. A drop-down list should display showing the name of your app(s). Select your app.
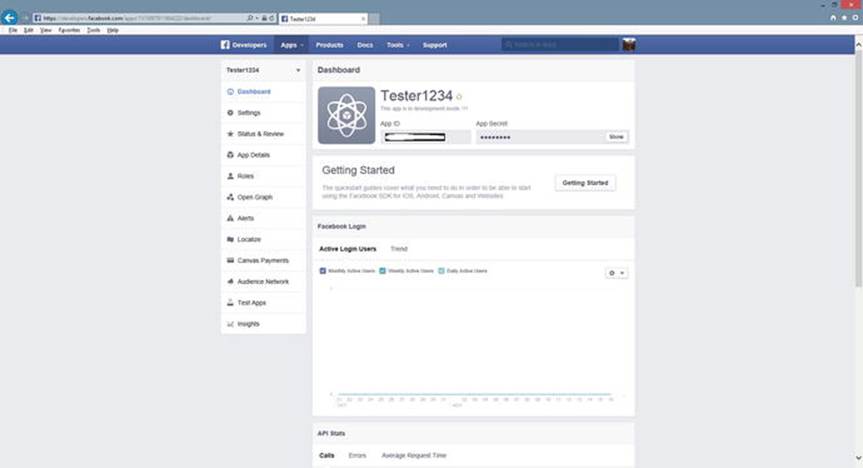
Figure 2-5.
The Facebook dashboard
8.
Once you have displayed your dashboard, select Settings on the left menu.
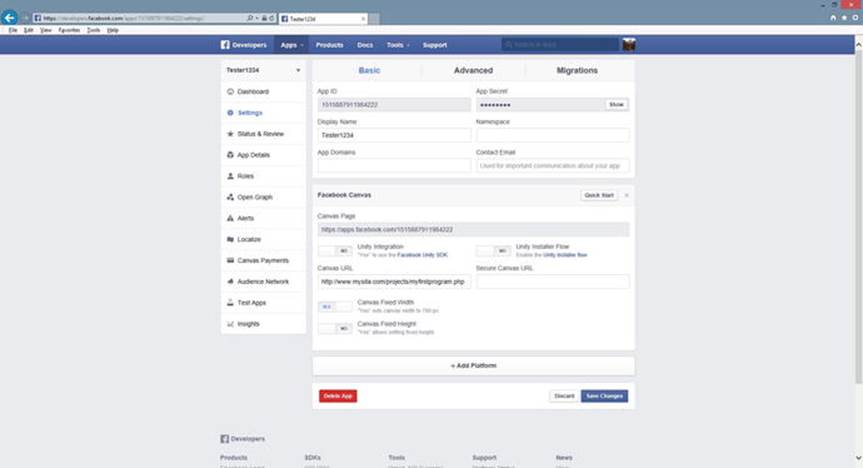
Figure 2-6.
The Facebook Settings page
9.
Scroll down to the bottom of the page. Locate Secured Canvas URL and erase the address that resides in this textbox. Type the location of another secured web page (https) in the box.
Remember, this must be a URL on the web, not your localhost. Click the Save Changes button.
10.
Now paste the URL of your app (if you lost the URL address, it is under Canvas Page on the Settings Page) in your browser.
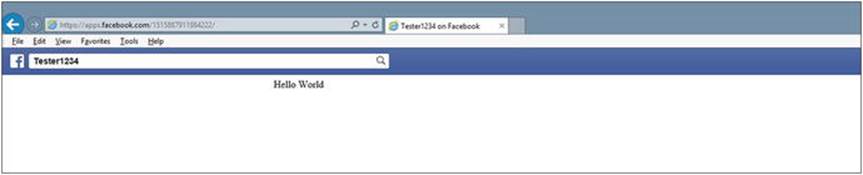
Figure 2-7.
Facebook working app
11.
You should now see your app display on the canvas within your Facebook page.
12.
Were you successful? What problems did you encounter following this example? How did you solve those problems?
Congratulations, you have created your first Facebook app (although it is not live). If you would like some of your friends to see your app, you can go back to the dashboard and select Rolls from the menu. You can then use your friends (yes, they have to be Facebook Friends) and give them a “role” in the development of your app (such as “Developers” or “Testers”). They then will have access to your app without it going live.
You are on your way to making lots of money as a Facebook game developer! Well, maybe not just yet. We left out a lot of coding to react with Facebook’s API. But hopefully you get the idea that Facebook can easily be used as a container for your PHP applications.
PHP, AJAX, and CSS—Web Applications
PHP and AJAX (Asynchronous JavaScript and XML) work well together. AJAX provides the ability to dynamically change portions of a web page without reloading the complete page. Most web pages have static areas (menus, headers, and footers) that do not change relative to user interaction. It is not necessary for these areas of the web page to change when the user interacts (clicks a button) with the page. AJAX can enable you to develop a container (in the following example, the container is located between the div tags) to display output from a program hosted on a web server; without disturbing the complete web page. Users can then view content on a web page (menu, header, and footer) when the results of the user’s interaction (clicking a button) is still being processed. If for some reason the program is slow, hung, or missing, the rest of the page still functions. You may have experienced this when you have displayed a page that hangs because a lot of information (a lot of ads) is trying to load at once and the page will not function because it must be completely loaded before it is usable.
AJAX also allows you to change the content of your PHP application on the web server without disturbing the web page. You can then update the code in your application without the user’s knowledge (as long as you keep the name of the application the same).
Let’s look at an example.
Note
Code example files are included on the book’s web site. You can copy and use these example without any changes. Every attempt has been made to ensure that code shown in this book is correct. Printing errors might affect the code shown (such as uppercase and lowercase being adjusted and parentheses being replaced with angled parentheses). All code available on the web site is functional.
Example 2-1. AJAX_Example_JavaScript.js
function getXMLHttp()
{
var xmlHttp;
try
{
xmlHttp = new XMLHttpRequest();
}
catch(e)
{
//Internet Explorer is different than the others
try
{
xmlHttp = new ActiveXObject("Msxml2.XMLHTTP");
}
catch(e)
{
try
{
xmlHttp = new ActiveXObject("Microsoft.XMLHTTP");
}
catch(e)
{
alert("Old browser? Upgrade today so you can use AJAX!")
return false;
}
}
}
return xmlHttp;
}
function AjaxRequest()
{
var xmlHttp = getXMLHttp();
xmlHttp.onreadystatechange = function()
{
if(xmlHttp.readyState == 4)
{
HandleResponse(xmlHttp.responseText);
}
}
xmlHttp.open("GET", "myfirstprogram.php", true);
xmlHttp.send(null);
}
function HandleResponse(response)
{
document.getElementById('AjaxResponse').innerHTML = response;
}
JavaScript—A scripting language that provides the ability for a web page to be interactive. With JavaScript, a web page can react to the user entering information into a textbox and/or clicking a button. If you need to brush up on JavaScript or need additional examples, review the free “The New Boston” (dthenewboston.com) videos at:
https://www.youtube.com/watch?v=yQaAGmHNn9s&list=PL46F0A159EC02DF82
For a more in-depth review of AJAX, review the free “The New Boston” ( thenewboston.com ) videos at:
https://www.youtube.com/playlist?list=PL6gx4Cwl9DGDiJSXfsJTASx9eMq_HlenQ .
If you don’t know JavaScript, don’t get too hung up on the details of this program. Let’s just look at a few key points. AJAX uses HTTP GET to request a program, similar to a browser requesting a page. In this example, an instance of the class XMLHttpRequest (which exists in the JavaScript libraries) is named XmlHttp. This object is then used to open the request for the myfirstprogram.php (like opening a pipe). Then the send method of the object sends the request (pushes the water down the pipe). If the file is returned back properly, the output of the file is placed on the HTML web page between div tags with an ID of AjaxResponse. If the browser can’t handle AJAX communication, an alert box will display suggesting the user upgrade the browser. Although it is unlikely that anyone is using a browser that cannot interpret AJAX code, you still should handle all possibilities.
Example 2-2. ajaxdemo.html
<head> <title>PHP Ajax Demo</title>
<meta charset="utf-8">
<link href="ajaxdemo.css" rel="stylesheet">
<script type='text/javascript' src='Ajax_Example_JavaScript.js'></script></head>
<body>
<div id="wrapper">
<div id="header"> <h1>PHP Ajax Demo</h1> </div>
<div id="content"> <h2>"Watch it!!"</h2>
<p>The words below will be replaced by "Hello World" which is pulled from the 'myfirstprogram.php' file via AJAX.</p>
<h2>AJAX DEMO</h2>
<input type='button' onclick='AjaxRequest();' value='Find Hello World!'/><br /><br />
<div id='AjaxResponse'>
Pay attention… Notice when you click the button that only this section changes.
</div> </div> <!-- end of content -->
<div id="footer">Copyright © 2015 Little Ocean Waves – Steve Prettyman
</div><!-- end of footer -->
</div> <!-- end of wrapper -->
</body></html>
For you to use this script, change the xmlHttp.open statement to select the file you wish to execute (instead of myfirstprogram.php). Change the document.getElementById line to include the ID of the div tag you want to use to host the output (instead of AjaxResponse) in your HTML file (see the HTML code in the next example).
HTML—Hypertext markup language is a markup language used to format the layout of a web page. HTML is interpreted by a browser, which then displays the results to the user.
For a more in-depth review of HTML, visit the free “The New Boston” (thenewboston.com) videos at:g https://www.youtube.com/playlist?list=PL081AC329706B2953 .
If you don’t know a lot about HTML, don’t worry. You only need to look at a few lines in this example. First, near the top of the code, a link tag pulls in the ajaxdemo.css file. This CSS file allows you to see a page with some graphic details. It allows you to demo that the page updates without the graphics from the CSS file repasting or blinking. Right below this line the script type tag loads in the JavaScript file from Example 2-1. If you named your file something else, this is the line you need to adjust with the new file name. If your files are not all in the same folder, you should include the folder name along with the file name.
In the middle of the HTML body section, the input type tag creates a button that will call the AjaxRequest function (contained in the JavaScript file) when clicked. This causes all the JavaScript code in Example 2-1 to execute. The last line we need to pay attention to is the <div id='AjaxResponse'> tag. The value in id (AjaxResponse) must match the object name used in the JavaScript getElementById code exactly. Assuming that they match correctly, once the button is clicked, the JavaScript code will request the myfirstprogram.php file and display the results between the div tags with the AjaxResponse ID.
Example 2-3. ajaxdemo.css
body { background-color: #000000;
font-family: Arial, Verdana, sans-serif; }
#wrapper { margin: 0 auto;
width: 85%;
min-width: 800px;
background-color: #cc0000;
color: #000066; }
#header { background-color: #ff0000;
color: #00005D; }
h1 { margin-bottom: 10px; }
#content { background-color: #ffffff;
color: #000000;
padding: 10px 20px;
overflow: auto; }
#footer { font-size: 80%;
text-align: center;
padding: 5px;
background-color: #0000FF;
color: #ffffff;
clear: both;}
h2 { color: #000000;
font-family: Arial, sans-serif; }
#floatright { float: right;
margin: 10px; }
Just to be complete, the CSS file is shown here. Don’t worry if you don’t know CSS. This file only makes the web site look nice for the demo. If you are going to use this file, make sure to save it in a file with the .css file extension. Also, if you are going to change the name of the file, make sure to also change the file name in the link tag (in the HTML file) to exactly match. Make sure to include any folder names, if necessary.
CSS— Cascading Style Sheets (CSS) work with HTML to display graphics on a web page. CSS describes the layout of the page, colors, text fonts, background images, and other characteristics of the web page. For a more in-depth review of CSS, visit the free “The New Boston” (thenewboston.com ) videos at:
https://www.thenewboston.com/videos.php?cat=40&video=18754g.
Double-check all three files (.js, .css, and .html) to make sure the names of the files match (exactly) the links that call them. If all the files are properly linked, the ajaxdemo.html file will first display, as shown in Figure 2-8.
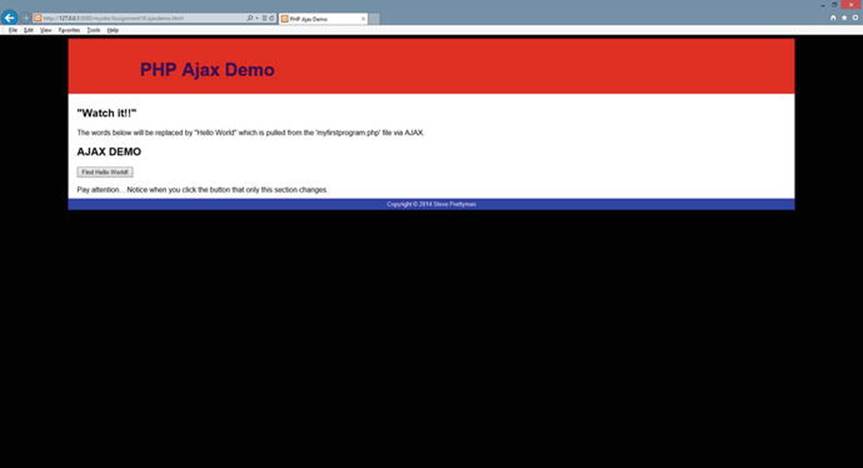
Figure 2-8.
ajaxdemo.html
If your code does not work, double-check the file names (make sure they do not have a .txt ending). If you see a blank page, there is something wrong. Look for typos in your code. Did you forget ;, {, (, or other coding? If you get an error message, paste it in your browser to discover possible solutions. If you do not see an error message, go to the logs (see Chapter 1) for Apache and PHP to determine other possible problems.
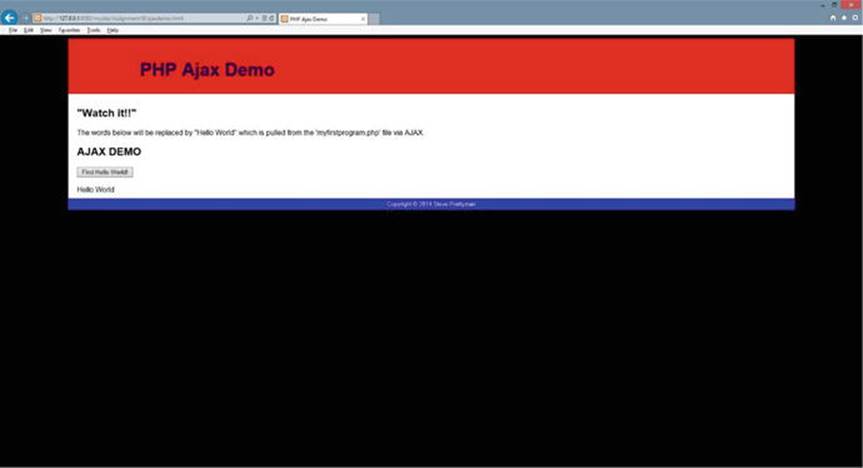
Figure 2-9.
The ajaxdemo.html file after the AJAX request
If there are no syntax errors (or incorrect file names or locations), when the user clicks the button, the page will request the myfirstprogram.php file using AJAX and will display the result of the execution of the program between the div tags. In this example, Hello World will be displayed.
Do It
1.
Copy the three files shown previously from the book’s web site into your projects folder (the location that you are running your projects in Apache). Run the HTML program. Was your test successful? If not, why not?
2.
Change the file name of your .js file and change the link tag in your HTML file to reflect the new file name. Test your HTML program. Was your test successful? If not, why not?
3.
Change the name of your PHP program. Make changes to the .js file to reflect the new name of your PHP program. Test your HTML program. Was your testing successful? If not, why not?
PHP, AJAX, and CSS—Smart Phone Web Applications
At this point, you should be beginning to discover the flexibility and power of creating PHP applications. You might be a little disappointed that we did not cover app development for smart phones in any detail. As mentioned, apps on smart phones usually do API calls to the operating system to request the use of applications residing on the phone (such as GPS). That level of coding is beyond entry-level. Thus, beyond what is covered in this book. However, there are times when we want to provide smart phones with the ability to access a web application from the browser on the phone. We can provide this ability with just a few changes to the previous demo. This provides you with an application that works with any size device that includes a browser.
You will make this change without adjusting the HTML (except for adding a link), JavaScript, or PHP code. You can adjust the ajaxdemo web page to format properly in smart phones or other mobile devices using CSS. In this example, you only need to change the HTML file to discover the size of the display (interface). Then CSS can be used to change the graphics to fit the proper screen size.
If the PHP file includes a lot of HTML (and/or other CSS code), we might need to also adjust the PHP file. However, we should always consider having CSS format the overall output (instead of the PHP file). This will allow you to use the same code in multiple containers (hosts) as you have seen demonstrated in this chapter.
You can add the following lines just below the link to the original CSS file in the ajaxdemo.html file.
<link href="ajaxdemomobile.css" rel="stylesheet" media="only screen and (max-device-width:480px)">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
Note
The new complete HTML file is located on the book’s web site.
These two lines will attempt to determine the size of the display screen and use the new CSS file for any screens that are 480px or less. The demo program, as is, will fit on most mobile devices. However, let’s adjust it to remove some of the spacing, padding, and margins.
Note
You can also use the CSS3 Flexbox Attribute for multiple device sizes. Since its use requires a little more understanding of CSS, we will stick with the “old style” method. You can find more information on CSS3 Flexbox at the following w3schools link.
http://www.w3schools.com/css/css3_flexbox.asp
Example 2-4. The ajaxdemomobile.css file
body { background-color: #000000;
font-family: Arial, Verdana, sans-serif;
margin: 0; }
#wrapper { margin: 0 auto;
width: 100%;
margin: 0;
min-width: 0px;
background-color: #cc0000;
color: #000066; }
#header { background-color: #ff0000;
color: #00005D;
font-size: 100%;
padding: 0.5px 0.5px 0.5px 0.5px; }
h1 { margin: 0px; }
#content { background-color: #ffffff;
color: #000000;
padding: 0.5px 0.5px;
overflow: auto; }
#footer { font-size: 80%;
text-align: left;
padding: 0px;
background-color: #0000FF;
color: #ffffff;
clear: both;}
h2 { color: #000000;
font-family: Arial, sans-serif;
margin: 0px; }
#floatright { float: none;
margin: 0px; }
Compare Example 2-4 to Example 2-3. The code in Example 2-4 is not perfect, but it does give you an idea of what can be adjusted in the original CSS file for display in mobile devices. This example reduces margins and padding to zero, or almost zero. This greatly reduces the wasted space on the display of a smaller mobile device.
Do It
1.
Locate the new HTML file and CSS file on the book’s web site. If you have a web host provider, upload these files (and the .js file) to the host. Try to access the HTML page from your smart phone. You can also try to display the page by using the URL location of the file on the book’s web site. Was your test successful? If not, why not? Did the page format properly on your phone? If not, what do you think needs to be adjusted?
Note
If you don’t have a host web site on the Internet, you can also test this CSS file by downloading one of the free mobile emulators available on the web (try www.download.com ). You can also change the link tag in the HTML file to point to the ajaxdemomobile.css file instead of theajaxdemo.css file. Then try reducing the size of your browser to simulate a smart phone screen.
PHP, HTML, JavaScript, CSS, and Dynamic Web Pages
As a last example of containers (hosts) for PHP programs, let’s consider the browser. As you have seen in this chapter, you can use an HTML file to call our PHP program (clicking the button in the previous demonstration). This, as detailed in Chapter 1, will cause the PHP program to execute and the results to be returned to the browser. You could also have your PHP program return HTML code.
Example 2-5. Dynamic HTML page created by a PHP program
<?php
print "<html>";
print "<head><title>My Program</title></head>";
print "<body>";
print "<h1>Hello World</h1>";
print "</body>";
print "</html>";
?>
You could return a complete HTML page (even with JavaScript and links) back to the device (browser) that requested the PHP program to execute. Example 2-5 would create a complete dynamic HTML page from within PHP code. The output created can even contain links to CSS files and embedded CSS tags for formatting. However, I urge caution on embedding CSS tags that depend on the container being a certain size. As the developer, you do not know what type of device will display the result (PC, smart phone, tablet, or pad). It would be better to provide multiple CSS files (as shown previously) to format the output for different devices.
In the previous examples, we have separated the initial interface (HTML and JavaScript) from the PHP program. You could actually place the HTML (to display the initial web page) and PHP code in the same file.
You can create a PHP file that will determine whether the user has ever requested the page before. If they have not, or the browser has timed them out, then the PHP program could display an initial HTML page for the user to interact (such as clicking a button). The same program could then call itself again to determine if the button has been clicked and return a response.
Let’s look at a different version of the Hello World program to do just that.
Example 2-6. The callmyself.php file
<?php
if (isset($_POST['submitbutton']))
{
print "<h1> Hello World </h1>";
}
else
{
print "<html><head><title>PHP Example</title></head>";
print "<form method='post' action='callmyself.php'>";
print "<input type='submit' id='submitbutton' name='submitbutton' value='Find Hello World!'/>";
print "</form>";
print "</body></html>";
}
?>
For a more in-depth demonstration of PHP If statements, visit the following free videos from “The New Boston” (thenewboston) at:
https://www.thenewboston.com/videos.php?cat=11&video=17004.
This program includes a simple if conditional statement to determine if the user has clicked the submit button.
The format of the if statement is as follows:
if (conditional statement)
{
// code to execute if the conditional statement is true
}
else
{
// code to execute if the conditional statement is false
}
A conditional statement usually compares two values to determine if they are the same or different or calls a method which returns a true or false value. We will look at functions returning values in a moment. Let’s look at a quick example of the first type.
Conditional statements use a comparison operator (==, <, >, <=, and >=) to determine if the statement is true or false.
If ( a > b)
{
print "it's A!";
}
else
{
print "it's B!";
}
In this example, the values in properties a and b are compared. If a is greater than b, then “it’s A!” is displayed. Otherwise, “it’s B!” is displayed. PHP does some type conversion when it determines that it might be necessary. For example, assume a = "5", and b = 6. PHP would convert the value in a from a string 5 to a number 5 so it can do the comparison. Many languages do not do this and will display an error if you try to compare strings and numbers. If you don’t want this conversion to occur, you can use some special comparison operators. For example, you can use three = signs to see if values are exactly the same (a === b) instead of two.
Security and performance—Whenever possible use === instead of ==. This will assure that you get exactly what you expect.
In Example 2-6, the if statement calls a method (isset). $_GET tries to retrieve the property ('submitbutton') and its value (“Find Hello World!”) from the HTML form, which used HTTP GET to pass the information (you could have used $_POST and HTTP POST). isset will return a falseor true back to the if statement, depending on whether or not $_GET could retrieve the property (and its contents). The true or false will cause the if statement to determine which block of code to execute.
As mentioned in Chapter 1, an object (such as a button) within an HTML form will produce a property and value combination based on the object’s name and whatever is contained in the value statement of that object. This is even true for submit buttons that have been given a name (id) and value (as in Example 2-6).
The first time the program is called from the browser, the button has not been clicked. So there is no submitbutton variable created. A false is returned by the isset method. The code jumps to the else section and executes the print statements that display the HTML form and submit button (as in Figure 2-10).
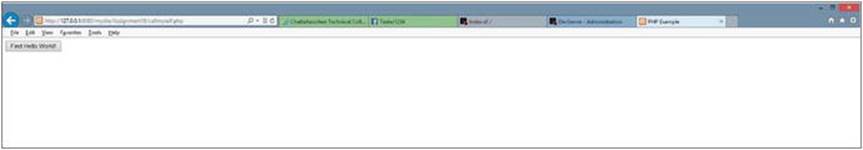
Figure 2-10.
callmyself.php before the button is clicked
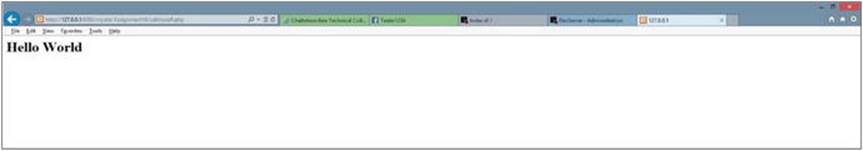
Figure 2-11.
callmyself.php after the button is clicked
When the user clicks the button, the program calls itself (look at the action parameter of the form tag). This time, since the user has clicked the button, there is a submitbutton property and a value ('Find Hello World!') for that variable. The program determines that the variable is “set” (has a value in it) and returns a true. The if statement then executes the one line of code between the if and else statements. Hello World is then displayed. The PHP program handled all the functionality of the application without using any existing static HTML page.
The advantage of this technique is that all code can be contained in one file. Thus, all changes occur in one place. The disadvantage of this technique is that all code is in one file. The more complicate the code, the “messier” it can become. One way to clean up the code would be to move the code into functions contained within other PHP libraries (we will look at this later). The additional disadvantage is that the file name cannot be changed without affecting the users. If you changed the file name to mynewprogram.php, you would need to inform all your users of the new name (and maybe location). The previous examples using AJAX allowed you to change the file name within the HTML code page, but did not require you to change the actual name of the HTML page that the user would request.
Do It
1.
Find the callmyself.php file on the book’s web site. Download the file to your Apache projects folder. Change and add print statements to display your complete name, the term, and your major. Test your program. Did your program run successfully? If not, why not?
PHP Three-Tier Architecture
Most of this chapter has been discovering the different platforms (or containers) that can “host” PHP applications. We have found that PHP can display its output in almost any container (PC, Facebook, smart phone/mobile device, or browser). The ease at which PHP can interact with JavaScript, HTML, and CSS has provided this flexibility. Today, almost any platform has the ability to interact with the Internet (and those that don’t will sometime in the future). Any platform that can interact with the Internet can also interact with a PHP application.
This independence (or flexibility) of the interface demonstrates a logical separation of the platform or host of the interface from other “tiers” (parts) of the application. This leads into a discussion of the three-tier architecture and the logical design of PHP applications. The larger the application, the more likely the application will need to be broken into modules. Also, it’s more likely that these modules could reside on different servers (or web servers). Larger applications likely will require multiple programmers writing code at the same time. These programmers may even use different languages to create the program modules.
Building a large application is not much different than assembling a car. The individual components of the car (body, wheels, electronics, and engine) are assembled individually first. Each completed component is then placed inside the chassis of the car. The components are then connected (hoses, wires, and belts) to other components. When completed, all components of the car work together. If a component breaks, it can be replaced without causing replacement or changes to any other component in the car.
The idea of modular (or component) programming is based on the methodology of blocks of code that can be created individually to be assembled with other modules to produce a working application. The modules can be modified or replaced without requiring changes to other modules. This methodology has been around for a while. Even today, many programs are not modular because smaller programs can work efficiently without being broken into modules. However, as these applications expand into larger applications they become more difficult to update or maintain. A change requires updating the complete application rather than just a module. At some point, an expanding application that has not be created with modules has to be redesigned from the ground up into modules for better maintenance and reliability.
As discussed in Chapter 1, a search engine can display a web page interface in a browser on the user’s PC. Once the user enters the search request, the information can be transmitted across the Internet to a remote server (we don’t know where), which executes a search application (we don’t know what program language was used to create it). The application then searches a database (we don’t know what DBMS or where it is located) for the requested information. The results are sent back to the application, which in turn, sends the information back to the browser (via the web server) on the user’s PC.

Figure 2-12.
Three-tier modular application design
The flow of information in this process causes the design of this type of web application to naturally fall into (at least) three tiers (modules); interface tier, business rules tier, and data tier. One advantage of breaking code into different tiers is the ability to reuse tiers with multiple applications. For example, our search engine could use the same business rules tier and data tier for multiple devices while using a different interface (PC app or smart phone app). Distinct tiers can also be updated without affecting other tiers. The smart phone app interface could be updated to use the latest features of the newest operating system without changes to the business rules or data tiers. Code within the business rules tier could be updated to fix logical bugs without requiring changes to the interface or data tiers. Let’s take a look at what typically occurs in each tier.
Modular Three-Tier Applications, Design, Programming—Three-tier design provides the ability to create programs that can be separated into an interface tier, business rules tier, and data tier. The interface tier contains all graphics and program code related to displaying information to the user. The business rules tier does not contain an interface. However, it processes any information submitted from the interface tier and can then submit information to the data tier to be stored. The data tier is the primary storage location for the application, which may include the use of a database. Each tier can be independently changed and built (compiled) without affecting the other tiers.
Do It
1.
What are the name of the three tiers of modular design?
2.
How is modular design similar to designing a building?
3.
How does modular programming make coding more efficient?
Interface Tier

Figure 2-13.
Interface tier
The interface tier (IT) displays information and provides the user the ability to interact with the application. Most interfaces provide a Graphical User Interface (GUI), which allows the user an attractive way to view information and interaction with the application. GUI interfaces provide common objects, including textboxes and buttons, which help the user to quickly adapt to new applications. In addition, pictures, images, icons, video, and sound can often be included to keep the user’s interest. Menus and other navigation objects are also commonly included to help the user move through the application successfully.
Objects—Objects are blocks of code that have already been compiled for use within an application. Objects can be placed into a program by making an instance of the object. Objects contain methods and properties. Methods (or functions) are blocks of code that accomplish a task (such as placing items in a list box). Properties (or variables) are characteristics of an object that can be changed (such as a background color). Objects are usually well tested and error free. By reusing existing objects, the programmer can quickly create more reliable programs.
This tier will display information using objects (such as labels and picture boxes) or scripting code (such as the ajaxdemo.html example in this chapter). The tier will also accept information from the user through interactive objects (such as textboxes and buttons). Static information can be provided from within the tier (via menus, logos, or footers). Dynamic information is usually provided to the tier from the business rules tier (such as the output from myfirstprogram.php shown in this chapter).
Some coding (shown in later chapters), which prepares information to be send to other tiers may be present in the interface tier. For example, JavaScript code that verifies that the user has entered all the required information or the proper information (numeric characters in an age textbox) is acceptable. Additional code may also prepare information received from the business rules tier to be displayed (such as converting numbers to text format) in the interface.
Verification/Verification Code—Verification code validates information. The code compares the information received to an expected standard format. For example, the code can verify that an e-mail address has both a @ and a . (period). If the information has both symbols, it could be considered “valid” (although we still are not sure that the e-mail address actually exists). If it does not have both symbols, the code is not valid. Information that is not valid usually will cause the program to display an error message to the user requesting valid information be reentered.
The interface must provide code with the ability to react to user interactions (clicking the Submit button), commonly called user events. Code may also be provided that prepares information provided by the user for use by other tiers (such as converting text entered by the user into number format for a calculation in the business rules tier).
Event—Event-driven languages (such as PHP) can execute blocks of code when an event occurs. Events can be something that the user has done (such as clicking a button). Events can also be fired by the operating system. Programs provide listener code that “hears” an event. When an event occurs, the code provides an event method, which then executes. A program chooses which events to listen for by the presence, or lack of, listener code.
The interface tier should not directly interact with a database management system or a database itself. By doing so, this would lock the tier into the database location and actual design of the database. The tier should not manipulate data (except for display purposes). Any accounting, mathematical calculations, or processing of data related to the application itself should be accomplished in the business rules tier.
Database Management System (DBMS)—A Database Management System is software that allows a user or an application to create and define a database. It also provides the ability to insert, update, or delete information in the database.
Do |
Don’t |
Format data for display |
Access data from database |
Verify correct information from user |
Calculate results |
Respond to user events |
Process information |
Handle the unexpected (exceptions) |
Verify user IDs and passwords |
Format data for business rules tier |
Do It
1.
Give three examples of items that would be included in the interface tier.
2.
Give three examples of items that would not be included in the interface tier.
3.
Can some program code exist in the interface tier? If so, what tasks does this code provide?
Business Rules Tier

Figure 2-14.
Business rules tier
The business rules tier processes all information and data received from the interface tier and the data tier. This tier will also return information requested by the interface tier (such as returning "Hello World") and submit information to the data tier for storage. Most of the actual programming code is contained in this tier.
The business rule tier code usually makes an application truly unique from another application. If an application is copyrighted, the uniquely creative algorithms are probably hidden in this tier. For example, many of the differences in web search engines and how the information will ultimately be displayed are embedded in the business rules tier.
Unlike the interface tier, which may contain code in the browser, all coding in the business tier is completed using a program(s) (such as PHP) on a server. Scripting and programming code residing on a server is secured by the server itself and cannot be accessed by the user. Business tier code can also reside on an application server (as a service) or on a web server (as a web service). Servers ensure that code in this tier is secure by not allowing direct access by the user.
Server/Application Server/Web Server—A server is connect to a network to provide services to any node (machine) on the network (or the Internet). A server can provide more than one service (communication, security, and/or storage) or can provide a specific service. Application servers house applications that are accessible to users on the network (or Internet). Web servers host web pages and web applications. They are usually exposed to access outside a corporation.
Service—Services are applications that reside in the memory of a computer or server that respond to requests from other applications. Services can be automatically loaded into memory when the computer or server is booted or they can manually be started and stopped when required. Services do not have GUI interfaces. The business rules tier can reside as a service(s) on a computer or server.
If information passed between the tiers of the application can be subject to possible manipulation by hackers, this tier may contain code, similar to the interface tier, to verify the validly and proper format of the data received.
Information passed from this tier to other tiers can be format for easy acceptance. For example, a dataset (similar to a table or spreadsheet) can be returned to the interface tier for display in a table or list box existing on a web page. A dataset could also be sent to the data tier to be inserted into a database.
Dataset—A dataset is a structure that can hold multiple data tables. A data table is similar to a table in a database (with rows, columns, and data) or a spreadsheet. Datasets are commonly used to pass information between tiers and between methods.
The business rules tier returns values to the tiers that request it. The tier does not provide any GUI interfaces or forms of any kind. Interfaces are not needed because the tier has no direct contact with the user at any time. All communication to the business rules tier is handled either through the interface tier or the data tier. Like the interface tier, the business rules tier does not directly update stored information in databases. All storage updates occur in the data tier.
Do |
Don’t |
Manipulate data |
Display information |
Format data |
Save data on secondary device |
Store data in memory |
Display error messages |
Raise exceptions |
|
Verify data |
Do It
1.
What tasks can business rule tier code accomplish that is similar to a task accomplished by code in the interface tier? Why is this code possibility duplicated in both tiers?
2.
How does the business rules tier pass and receive data (information)?
3.
Why must the business rules tier talk indirectly through the interface tier to provide information to the users?
Data Tier

Figure 2-15.
Data tier
The data tier’s main function is to store information on a secondary device or to return data to the business rules tier. Data can (and usually is) be stored in a database using a Database Management System (like MySQL). The tier interfaces with the business rules tier, since data may be manipulated before being displayed, as in the creation of a report. Data is returned from the tier in a format that the business rules tier (and program languages) can accept. Common formats include JSON, XML, SOAP, and datasets.
JSON—JavaScript Object Notation is a format, similar to XML, to store and exchange data. JSON can be viewed within an editor or browser. It is most commonly used to pass data between tiers.
XML—Extensible Markup Language is a markup language, similar to HTML, to store and describe data. XML can also be used to transmit data between tiers. We will provide an example of XML in Chapter 3 .
SOAP—Simple Object Access Protocol is used to exchange data with a web service. It works with HTTP (Hypertext Transfer Protocol) and SMTP (Simple Mail Transfer Protocol) to provide communication between an application and a web service.
Web Service—An application, without an interface, that can be called to process information. A web service can provide the functionality of the business tier and/or data tier remotely on a web server. The Web Services Description Language (WSDL) is used to describe calls to the web service and the format of information accept and returned by the web service. WSDL is similar to XML.
Validation with the data tier is done in the Database Management System and/or via program code. Validation in this tier is the last chance to make sure data is reliable and accurate before the database is updated. It is much easier to catch validation problems before they are stored than after invalid information has been recorded.
Data storage can be local and/or remote. Mobile devices can restrict storage to local databases (smart phones), but can also use WSDL (web services) to store and retrieve information remotely on a server or within a cloud (such as Microsoft Azure). Additionally, many applications save small amounts of information locally with cookies, or larger amounts of information in remote databases.
Microsoft Azure— Microsoft Azure is a cloud platform that provides data services, app services, and network services. Visual Studio Applications can be uploaded and secured in the Microsoft Azure cloud.
The data tier uses SQL statements (INSERT, DELETE, UPDATE, and SELECT) to retrieve and update information in a database. However, the actual request for the information to be changed comes from within the business rules tier. For example, a user requesting an address change in a web application would have to enter the requested change in the interface tier, format the update request in the business rules tier, and change the information in the database in the data tier.
Do |
Don’t |
Save data on secondary device |
Manipulate data |
Update data on secondary device |
Display error messages |
Raise exceptions |
Display information |
Verify data |
Do It
1.
Why must the data tier validate information again, before it is placed in a database?
2.
What type of code, if any, can exist in the data tier?
3.
What is SQL used for?
Putting It All Together
The Program Development Life Cycle (PDLC) leads us through the overall design and creation process for application development. The key to application development success is to properly plan the layout of your system before beginning the coding and development. By doing so, you reduce the amount of errors and problems that can occur. Many projects can run into a “corner” that the developer cannot get around because of poor planning up front. Different authors and instructors will vary on their estimates on the time to spend in the planning process because it is based on the individual. A more skilled, or more experienced individual may do less planning than someone who is not as confident. However, everyone plans out, at least, the required modules and the type of data flowing between the modules; even if it is done just on scratch paper. The key, also, is to revise your plan as you work through the coding and development process. As you start coding, you will discover “I did not think of that” scenarios. Go back, right then, and adjust your plan. The more you do so, the less likely that you will hit a “corner” that you cannot find a way to get around.
Always involve the user in your PDLC process, along with as strong a team of experts. Remember you are developing this project to make your customer happy. You may believe you have the ultimate design and solution. However, that does not matter if your user does not agree with you. Sometimes you do have to adjust your thinking to be more in line with the customer. Working in the industry I remember a major change-management system that was being created within my work group (I was so happy to not be involved in the project). The designers and coders created a very fancy and expensive, system that, once it was implemented in the data centers, was hardly used. Why? The data center personnel did not want a fancy system; they wanted a simple system that could quickly complete the tasks needed. Even though the original project took six months to complete, a data center employee spent a few weekends of his own time creating another system that accomplished what they wanted. That system was implemented and used for many years afterward.
Commonly the PDLC is defined with five steps; Planning and Information Gathering, Analysis, Design, Implementation, and Evaluation. In the planning and information gathering step, all requirements for the project and the project team are assembled. Initial documents are also created answering the questions “What are we trying to accomplish?”, “How are we going to accomplish it?”, and “What team are we going to use?” In the analysis step, a determination is made as to the feasibility of the project. Documents answer the questions “Can we accomplish the project with the team and resources available?”, “What additional resources need to be gathered?”, and “Can the project be accomplished in the timeframe and budget allocated?” If the project makes it past the analysis step (many projects don’t), then the actual design begins. In the design phase, a top-down approach begins by first looking at the overall required modules, and the data flow between the modules. More details are gradually added as the methods required are determined, a platform is decided on, communication tools come together, and information storage is designed.
After a detailed design has been created, and approved, the project goes into development and testing. Both unit testing (individual modules) and complete application testing will occur. After successful testing, the project is ready for the Implementation Step. During implementation decisions have to be made on how to install the project and when to install it. After implementation, the application is “live”. But still continuous evaluation should occur to determine efficiently needs, security problems, logical problems, and possible overall enhancements to the project. Eventually, most projects will then revert back to the first step of the process for the development of a new version.
This section assumes that the planning and information gathering and analysis steps have been completed successfully, which would move you into the design step. We will look, in general, at the process of determining what type of activities should occur in which tiers of an application. We will also look at the type of data or information that may flow between the tiers. In later chapters we will refine this analysis by determining the types of methods that would be required and the information and data that must flow into and out of these methods. We will also look at the actual activities and code that would be created for these methods.
The best way to learn is by doing, so let’s look at a case problem and go from there.
Case Study
Company: Atomic Fish Hatchery, Inc.
Project: Field Sales Ordering and Commission Application
Scope: This application will be accessible from multiple devices (mobile and PC) to allow field sales agents, managers, and payroll personnel easy access to necessary information. The system will accept information from the sales agent that will be used to determine purchase costs to the customer, sales volume for the sales manager, and commissions for the payroll department. Phase one of the project is the development of the application to accept information from the sales agents, display purchase cost, determination of commissions, and storage of the information into a MySQL database. After successful testing the platform, it will be moved and secured in the company’s cloud platform.
Inputs (from Sales Agent): Sales Agent Number, Customer Number, Order Number, Item Number, Quantity, and Special Needs
Outputs: (Additional information may be determined for future phases)
To database: In addition to the input from the sales agent: commission, sales total
The goal is to determine the types of information and processes that will occur in each tier and the data flow between the tiers. Once determined, this information could be used to develop a general empty structure of tiers that would eventually hold the completed project.
Interface Tier
The company has requested access from multiple devices. Thus, we must keep in mind that mobile devices (tablets and smart phones) will be used to input and output information in addition to laptops and PCs. We may decide to create multiple interfaces for each type of device. With three-tier design, you could design a system that shares the business rules tier and data tier contents while allowing this flexibility.
As a designer and/or programmer, you must determine the type of information that will be entered; several fields (Sales Agent Number, Customer Number, Order Number, Item Number, and Quantity) all indicate that numbers will be entered. You need to determine the size of these fields and verify that only numeric information is entered. The Amount field is the only field that possibly could be used in a future calculation. Therefore, all other fields can remain in text format. The Amount field would need to be converted to integer format before passing the information to the business rules tier. The Special Needs field would be a larger field that can accept alphanumeric characters. The database does not currently exist, so you would determine field sizes from company policy and/or current paper forms used. Once reviewed, it has been determined that the customer and sales agent numbers are eight characters. The order number and item numbers are currently six characters.
After gathering this information, you can now design the top view of the interface tier, as shown in Figure 2-16.
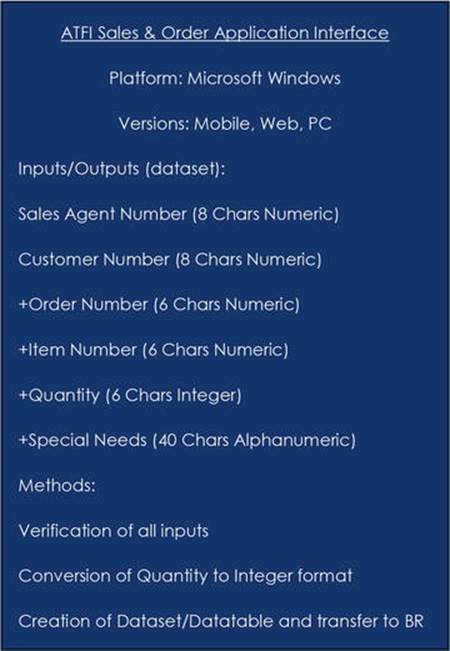
Figure 2-16.
Atomic Fish Hatchery Inc. sales and order application interface
Fields with + may be used more than once to enter in all information by the sales agent. When the actual datasets and data tables are created, multiple columns must be available for these entries.
An additional form (not pictured) would also exist to display the results of the order. This form would display a summary of the items purchased and the total cost. All information could be entered by the sales agent, submitted, and held in the interface tier (a cookie?), until the sales agent indicated that the order is complete. Then the information could be transferred to the business rules tier for processing. The business rules tier could then return the information to be displayed in the second form. The second form could include an “approved” (or cancel) button. Once “approved,” the information could then be passed to the data tier for storage.
Business Rules Tier
The business rules tier would include two processes. One process would accept the complete order (dataset/data table) and determine the total sales cost after the sales agent clicked a “competed order” button. It would then return a summary of this information to the second form. The other process would execute when the agent clicks an “approved” button. The process would then determine the commission and create a dataset (there are now additional fields) to be passed to the data tier. The information would then be passed for storage.
Additionally, to make sure order data is valid, methods would be needed to validate the fields received from the interface. The top view of the Business Rules Tier would the following shown in Figure 2-17.

Figure 2-17.
Atomic sales and order application business rules tier
Data Tier
In this case, the data tier is only used to store the information provided by the business rules tier. The tier would verify the information received and store it into the database, as shown in Figure 2-18.

Figure 2-18.
Atomic sales and order application data tier
There are many tools available to help in the design process. The important factor is that the designer include all the important information in the process. As an alternative to the example, you could remove the description of the datasets from the tiers and place them in the data flow between the tiers, as shown in Figure 2-19.
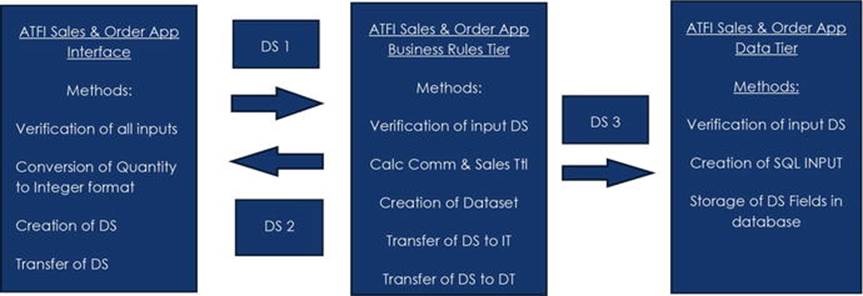
Figure 2-19.
Alternate three-tier model

Figure 2-20.
Atomic Sales and Order Application Three-Tier Model
Do It
1.
When must you convert numbers to numeric form (such as Integer) for storage within a database?
2.
Why use datasets to pass information between tiers?
3.
What items have been missed or ignored in the case example?
MVC and Dependency Injection
MVC (Model-View-Controller) is a design pattern used by software engineers (including PHP application designers) to communicate between the view and model using a controller. The controller is software that transfers any user input to the model. MVC design can be considered circular because the model, controller, and view have the ability to communicate with each other. The standard three-tier model is linear; for the Interface to receive or pass information to the data tier, it must pass the information through the business rules tier. There are many tools on the market (such as Ruby on Rails) that can assist software engineers in designing MVC applications.
Visit thenewboston.com for a generic example of an MVC application: https://www.thenewboston.com/videos.php?cat=88
MVC and Component Based Design can use Dependency Injection. Dependency Injection allows the program (client) that will use a block of code (such as a class) while not know the actual implementation of the block of code. This allows for independent development, updating, testing, and reusability of modules. This is similar to the ability of the ignition of a car communicating with the starter. The ignition has little knowledge of the starter component and how it operates. It does not even know the brand of starter. The ignition merely knows to send a signal (electricity) to the starter to tell it to operate. If the starter is replaced, the ignition is unaware and unaffected by the change, as long as the starter still operates when it receives the signal. While MVC and dependency injection are advanced topics, we will explore on example of dependency injection in Chapter 4.
Chapter Terms
Platform or Container |
GTK SDK |
Smart Phone API |
Facebook Canvas Platform |
Facebook API |
Facebook Developer’s Page |
AJAX |
HTTP GET |
XMLHttpRequest |
document.getElementById |
CSS |
Conditional Statement |
If Statement |
Three-Tier Architecture |
Interface Tier |
Business Rules Tier |
Data Tier |
Graphical User Interface (GUI) |
Objects |
Verification Code |
Events |
Database Management System |
Servers |
Application Servers |
Web Servers |
Service |
Dataset |
JSON |
XML |
SOAP |
WSDL |
SQL |
Microsoft Azure |
PDLC |
Planning and Information Gathering |
Analysis Step |
Design Step |
Implementation Step |
Evaluation Step |
MVC (Model-View-Controller) |
Dependency Injection |
Chapter Questions and Projects
Multiple Choice
1.
The interface tier
a.
Is the primary storage location for the application, which may include the use of a database
b.
Provides common objects, including textboxes and buttons, that help the user quickly adapt to new applications
c.
Should be used for any accounting, mathematical calculations, or processing of data related to the application
d.
Displays information and provides the user the ability to interact with the application
2.
A service is an application that
a.
Can be manually started and stopped when required
b.
Does not have an interface
c.
Resides in the memory of a computer
d.
All of the above
3.
SOAP stands for
a.
Security Object Access Protocol
b.
Simple Object Access Process
c.
Simple Object Access Protocol
d.
None of the above
4.
The five steps of PDLC are
a.
Planning and Information Storing, Analysis, Design, Implementation, and Evaluation
b.
Planning and Information Gathering, Analysis, Design, Implementation, and Evaluation
c.
Planning and Information Gathering, Analysis, Data, Implementation, and Evaluation
d.
Planning and Information Gathering, Analysis, Design, Observing, and Evaluation
5.
The Web Service Description Language is used to
a.
Describe calls to the web server and the format of information sent and returned by the web service
b.
Describe calls to the web service and the format of information accepted by the web service
c.
Describe the code being used in HTML documents
d.
Describe calls to the web service and discard the information received
6.
CSS stands for
a.
Cascading Static Styles
b.
Cascading Style Sheets
c.
Cascading Script Sheets
d.
Cache Style Scripts
7.
What type of code belongs between the <script>……</script> tags?
a.
Java
b.
HTML
c.
Servlets
d.
Javascript
8.
What is the three-tier architecture composed of?
a.
GUI/tags/validation
b.
interface/business/data access
c.
Objects/variables/SQL
d.
JSPs/servlets/sockets
9.
The best description for the Model View Controller (MVC) is
a.
An architectural pattern that divides a given software application into three interconnected parts.
b.
A programming language used to validate and secure information in any browser.
c.
A type of validator mainly used to check if the user entered the information on the correct format
d.
A type of method that is used to convert a harmful code so it cannot be executed by the compiler.
10.
What is performed in the Analysis step?
a.
Determination of the feasibility of the project
b.
Creation the code and error correction
c.
Determination of the logical data flow of the project
d.
Re-evaluation of the implemented application for possible improvements
11.
Why must you validate your code?
a.
To determine the capabilities of the browser you are using
b.
To make sure your information is correct and secure
c.
To make sure that you have only JavaScript and HTML5 code
d.
To check if your browser can run your code
12.
What is the correct HTML syntax for referring to an external cascading style sheet?
a.
<stylesheet>my_style_sheet.css</stylesheet>
b.
<link rel="stylesheet" type="text/css" href="my_style_sheet.css">
c.
<style src="my_style_sheet.css">
d.
None of these
13.
Which tier is used to store and retrieve data?
a.
Presentation tier
b.
Data tier
c.
Application tier
d.
None of these
14.
What does SQL stand for?
a.
Structured Question Language
b.
Structured Query Language
c.
Strong Question Language
15.
Which is true about smart phone APIs?
a.
The smart phone APIs allow procedural (method) calls to be made to the phones operating system.
b.
The smart phone APIs will allow web applications to make procedural (method) calls to the phone’s operating system.
c.
The smart phone APIs re not needed for applications that use GPS.
d.
Not all smart phones come equipped with an API.
16.
A dataset is similar to
a.
A paragraph of data
b.
Sets of two words together
c.
A table or spreadsheet
d.
None of these
True/False
1.
Facebook Canvas Platform can accept apps written in any code, not just in PHP.
2.
WSDL stands for Web Service Definition Language.
3.
AJAX is used to create more interactive applications.
4.
AJAX provides the ability to dynamically change portions of a web page with reloading the complete page.
5.
When using the HTTP GET function, the URL must be in quotation marks.
6.
A service is a function provided by a web server.
7.
The design step comes after the analysis steps have been completed successfully.
8.
MVC (Model-View-Controller) is a design pattern used by software engineers (including PHP application designers) to communicate between the view and model using a controller.
9.
Planning and information gathering is part of the PDLC.
10.
Dependency Injection allows the program client to enter a block of code to know the implementation of the block of code it will be using.
11.
Objects are blocks of code that have already been compiled for use within an application.
12.
HTML stands for Hypertext Markup Language.
13.
Method signature includes the method name, and the number, types, and order of its parameter.
14.
Datasets are not one of the many formats used when sending data between tiers in a three-tier architecture.
Short Answer/Essay
1.
In your own words, briefly describe each of the steps in the PDLC.
2.
Why do you think development of PC applications using PHP has decreased?
3.
Why do you think some web sites do not allow themselves to be inserted inside other sites (such as the Facebook Canvas)?
4.
What are the advantages of creating web pages that use AJAX?
Projects
1.
Using the steps of the PDLC demonstrated in this chapter, design the logic for a smart phone and mobile device application that allows your water meter reader to enter the full address and meter readings. The application should validate the information and send valid information to a MySQL database. If the information is not valid, a message should be displayed back to the user indicating the problem.
2.
Adjust the AJAX example in this chapter (the code is available on the book’s web site) to display a mini version of your resume.
3.
Adjust the Hello World (Example 2-6, callmyself.php) program to display your college/university name, address, and main phone number.
Term Project
1.
Using the information you have determined from the Chapter 1 Term Project assignment and the design techniques shown in this chapter, develop a logical design of the ABC Computer Parts Inventory application. This design should include all possible programs, interfaces, and data storage. The application design must be three-tier (interface, business rules, and data). Your final design should look similar to the examples shown in this chapter.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2025 All site design rights belong to S.Y.A.