5 Steps to a 5: AP Computer Science Principles 2024 - Sway J.S. 2023
3 Take a Diagnostic Exam
STEP 2 Determine Your Test Readiness
IN THIS CHAPTER
Summary: Taking the diagnostic exam will help you identify the areas that you need to review as well as give you an idea of what the questions on the actual multiple-choice exam will be like. After you’ve completed the test, use the evaluation tool at the end of this chapter to identify specifically what chapters you most need to review and adjust your study plan accordingly. This diagnostic exam includes questions from all of the “big ideas” covered in the AP Computer Science Principles course.

Key Ideas
![]() Taking the Diagnostic Exam will allow you to familiarize yourself with the AP Computer Science Principles exam.
Taking the Diagnostic Exam will allow you to familiarize yourself with the AP Computer Science Principles exam.
![]() Evaluate your performance on this test to identify your own strengths and weaknesses and then modify your study plan to prioritize the types of skills or areas of content you most need to work on.
Evaluate your performance on this test to identify your own strengths and weaknesses and then modify your study plan to prioritize the types of skills or areas of content you most need to work on.
How to Take the Diagnostic Test
Take this diagnostic exam when you begin to review for the exam. It will help you determine what you already know and what you need to spend time reviewing. It will also give you an idea of the format of questions on the AP exam.
Take the diagnostic exam in a simulated testing environment. Be in a quiet location where you will not be disturbed. Use the answer sheet in this manual and a pencil to answer the multiple-choice questions. The AP Computer Science Principles exam is still a pencil-and-paper exam! However, in 2021, the exam was also given in a digital format. Schools were able to select either digital or paper formats. One drawback of the digital format is that you cannot go back to review or change your answer for prior questions. The make-up exam dates only used the digital option.
Set a timer for two hours and try to pace yourself so you finish the exam. If you are not finished when the time is up, note how far you got, and then complete the rest of the exam. Answering all the questions will provide a better evaluation of what areas you need to review.
As you take the test, mark all the questions you were not sure about so you check the answer explanations for them as well as those you miss. But do not check an answer until you have finished all the questions after the two-hour testing period.

Test yourself in an exam-like setting. Take this diagnostic test and the practice exams at the end of this book in a place where you won’t be interrupted for two hours. Time yourself. If you use your cell phone to time yourself, make sure it’s completely silenced in airplane mode so you won’t be interrupted.
In the next section of this book, you’ll find helpful strategies for attacking both the multiple-choice exam and the Create performance task. The strategies were developed to help you prepare in the most effective and efficient way. Then in Step 4, you’ll begin the review of the concepts and skills tested. After taking this diagnostic exam, you will know which of these chapters you need to review the most.
AP Computer Science Principles Diagnostic Test
Multiple-Choice Questions
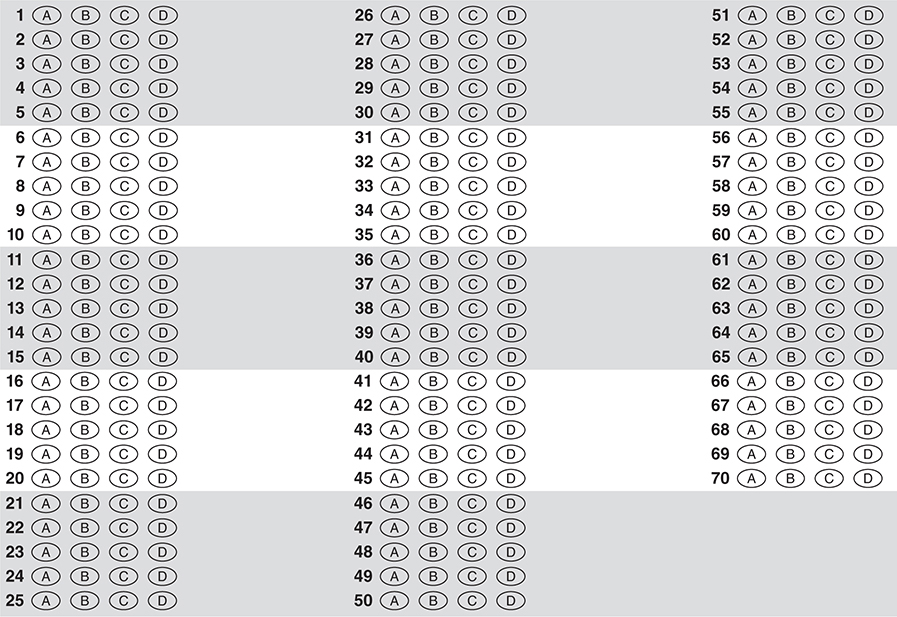
ANSWER SHEET
AP Computer Science Principles Diagnostic Test
Multiple-Choice Questions
Time: 2 hours
Number of questions: 70
The multiple-choice questions represent 70% of your total score.
Directions: Choose the one best answer for each question. The last eight questions have two correct answers; for these, you will be instructed to choose two answer choices.
Tear out the answer sheet on the previous page and grid in your answers using a pencil.
AP Computer Science Principles Exam Reference Sheet
On the AP Computer Science Principles exam, you will be given a reference sheet to use while you’re taking the multiple-choice test. A copy of this six-page reference sheet is included in the appendix of this book (reprinted by permission from the College Board).
To make taking this practice test like taking the actual exam, tear out the reference sheet so you can easily refer to it while taking the test. Save these reference pages since you’ll need to use them when you take AP Computer Science Principles Practice Exams 1 and 2 at the end of this book. If you misplace the Exam Reference Sheet, you can print another copy located at the end of the Student Handouts document: https://apcentral.collegeboard.org/pdf/ap-csp-student-task-directions.pdf?course=ap-computer-science-principles.
1. How are procedures abstract in computer science?
(A) They are blocks of code that do something specific.
(B) They represent the lowest level of code for the computer to run.
(C) They use actual values to represent concepts.
(D) They can be used without understanding or seeing the code used.
2. What do parameters used in a procedure provide?
(A) They allow software reuse for different values.
(B) They return calculated values from the procedure to the calling program.
(C) They provide a way to call a procedure from within another procedure.
(D) They provide the connection of an API to the procedure.
3. What happens when you “clean data”?
(A) Corrupt data records are corrected or removed.
(B) Incomplete data records are completed or removed.
(C) Duplicate records are removed.
(D) All of the above.
4. What causes an algorithm to be considered one that runs in an unreasonable amount of time?
(A) The solution is too inefficient for large datasets.
(B) There is not an algorithm that can solve it.
(C) It is solved most efficiently with large datasets.
(D) Multiple algorithms exist with different levels of efficiency.
5. What are statements, procedures, and libraries examples of?
(A) Low-level machine code that the computer uses to run the code
(B) Abstractions used in writing software because they can be used without knowing the details of how they work
(C) Algorithms that provide suggestions on how to approach writing the code to solve a problem
(D) Pseudocode that helps design a solution for coding challenges
6. What is an issue that organizations must handle when dealing with datasets?
(A) Ensuring that enough staff are on hand to process the data
(B) Ensuring that the bandwidth can handle the processing of the data
(C) Ensuring that people’s private data is not exposed
(D) Ensuring that the system can scale down after the data are sent to the cloud
7. How does the Internet work with the different equipment in use?
(A) The routers adjust for the different equipment manufacturers by sending data on the same equipment brands.
(B) Specific companies are approved to make equipment for the Internet.
(C) Vendors follow the protocols established to enable data to be sent and received across any equipment.
(D) The server farms handle the data once the data reach the Regional ISP (Internet Service Provider).
8. What is the binary equivalent of the decimal number 158?
(A) 10011111
(B) 10011110
(C) 10011101
(D) 10011000
9. How do selection statements determine which section of code to execute?
(A) Through the use of the Turing algorithm for analysis
(B) Through random number generators
(C) Through conditions that evaluate to true or false
(D) Through variables initialized to execute these statements
10. You are writing a program to help the school assign lockers each year. You have a list of student names and a separate list of locker numbers. The locker numbers match the index position for the list. Assume the lists are correctly initialized. What can replace to assign the student to the next available locker?

(A) lockerNum ← name
(B) lockerNum[index] ← name
(C) students ← lockerNum
(D) students[index] ← lockerNum
11. What do logical conditions always evaluate to?
(A) A Boolean value
(B) A value stored in a constant
(C) A “string” text field
(D) A real number
12. What is the process where algorithms are used with historical data to attempt to predict human needs or requests for information?
(A) Data excavation
(B) Trend prediction
(C) Social analysis
(D) Machine learning
13. What would be the starting and ending index positions for the substring function to extract everything up to but not including the “@” if you are given the following string: person@apcsp.org?
(A) 0, 5
(B) 0, 6
(C) 1, 6
(D) 1, 7
14. How is analog data converted to digital data?
(A) The analog curve is extrapolated and converted into x, y coordinate values.
(B) The analog data values are converted precisely to digital data.
(C) Samples of the analog data are taken and converted to bits.
(D) Samples of the analog data are approximated to mimic the smooth curve.
15. How do APIs simplify writing programs?
(A) By providing step-by-step instructions on how to use the programming language
(B) By importing the newly written software to the API for others to use
(C) By providing documentation on how to code the needed functionality
(D) By connecting prewritten and tested software to a new program
16. While algorithms can be analyzed mathematically, what information does the testing process provide?
(A) How often program statements execute
(B) The maximum size dataset the algorithm can handle
(C) The validity of the algorithm
(D) The clarity of the algorithm
17. Why is there a need to find different algorithms for problems that already have a solution?
(A) Different algorithms could use heuristics rather than precise values.
(B) Different algorithms could be more efficient.
(C) Different algorithms could use frequency analysis.
(D) Different algorithms could provide intractability.
18. Algorithms can be written with a combination of what three statements?
(A) Sequence / Selection / Iteration
(B) Series / Procedural / Functional
(C) Connection / Collection / Recursive
(D) Selection / Sorting / Searching
19. What is the most common way computer viruses are spread?
(A) By people clicking on an infected file
(B) From phishing attacks
(C) Through a rogue access point
(D) From random botnet attacks
20. Different levels of access to technological devices and the Internet due to economic or geographic reasons is referred to as:
(A) Binary split
(B) Demographic division
(C) Digital divide
(D) Technology rift
21. How does creating program components help with program development?
(A) Individual components can be added without additional testing.
(B) Adding tested components incrementally to working code helps create program functionality that is correct.
(C) Multiple people can write the components and still ensure compatibility.
(D) The components can be combined all at once to create the needed program functionality.
22. What is the name of the search method that provides higher or lower feedback with each iteration of the search?
(A) Bucket search
(B) Merge search
(C) Linear search
(D) Binary search
23. How does documentation help with maintaining programs?
(A) It journals the history of program changes, showing how the program first worked before changes.
(B) If code is modified, the documentation can guide the programmer in testing to ensure the functionality is still correct.
(C) It documents how to run the program in multiple languages for a global audience.
(D) It is useful for training new employees on how to learn the programming language.
24. Parallel computing consists of what two parts?
(A) A sequential section and a parallel section
(B) A parallel section and a distributed section
(C) A sequential section and a distributed section
(D) A sequential section and an iterative section
25. What could a binary number represent?
(A) A number in decimal
(B) A color
(C) Text
(D) All of the above
26. How can programmers avoid duplicating code?
(A) Through the use of selection statements
(B) Through the use of iteration
(C) Through sequential statements to process all data once
(D) Through the use of efficient algorithms
27. What is a problem that no algorithm exists to solve all instances called?
(A) Indeterminable problem
(B) Undecidable problem
(C) Infinite problem
(D) Exponential problem
28. Why should procedures be used?
(A) They ease the workload on the processors.
(B) They facilitate the storage of data.
(C) They make writing and maintaining programs easier through reuse of code.
(D) They control the flow of input and output data.
29. What can help with identifying and correcting program errors?
(A) Revisiting requirements
(B) Collaboration among team members
(C) Clustering requirements and tests
(D) Consolidating testing
30. How can financial transactions safely occur on the Internet?
(A) Through the use of symmetric keys
(B) Through certificates issued by Certificate Authorities (CAs) that validate the keys used
(C) Through the use of double authentication methods
(D) Through the use of frequency analysis
31. What is the definition of bandwidth?
(A) The frequency at which data can be transmitted across the Internet
(B) The speed at which data can be sent through the Internet
(C) The amount of data that can be transmitted in a fixed amount of time
(D) The delay between the request and the receipt of information on the Internet
32. Which type of loop is most effective to iterate over a list?
(A) Traversal loop
(B) REPEAT UNTIL
(C) FOR EACH
(D) REPEAT n TIMES
33. What is one way to help ensure the correctness of algorithms?
(A) By testing with small sets of expected data
(B) Through reuse of existing correct algorithms to build new algorithms
(C) Through documenting the functionality of the algorithm
(D) Through the use of heuristic algorithms
34. You are helping write the code to register students for classes. What can replace to make the program work? Assume all variables are initialized correctly.
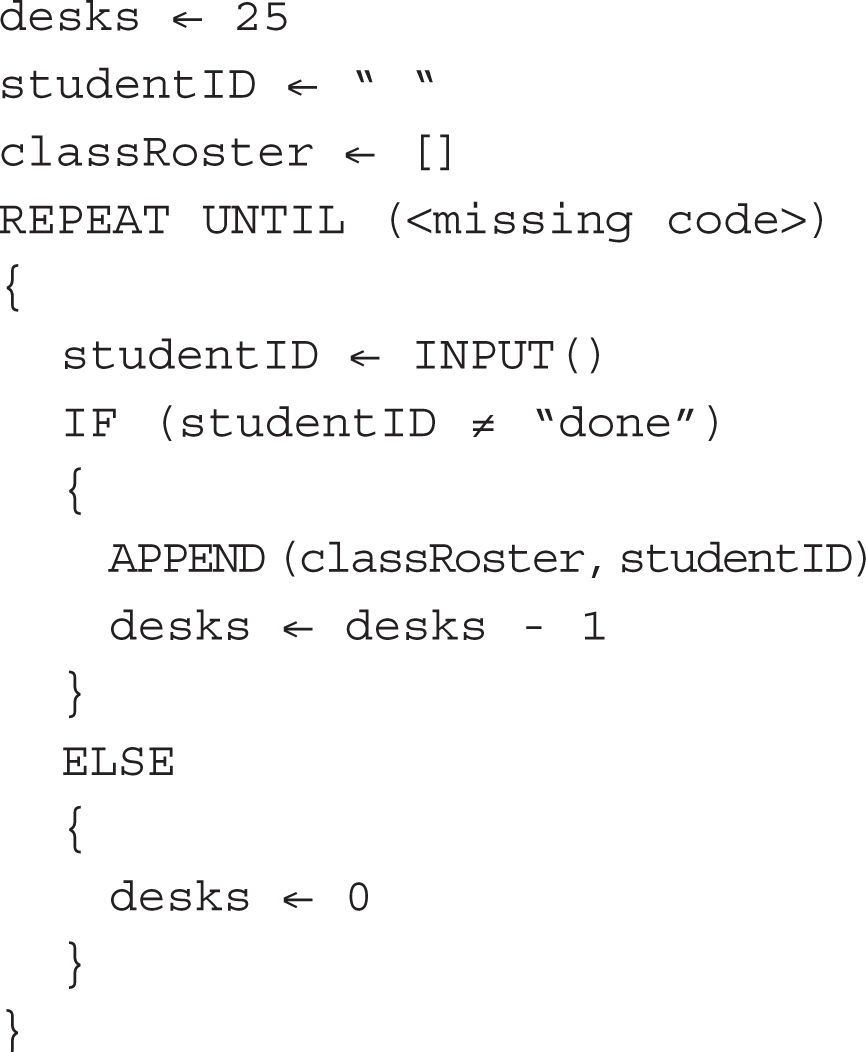
(A) desks = 25
(B) desks < 0
(C) desks = 0
(D) LENGTH (classRoster) = 0
35. An error that produces incorrect results is what type of error?
(A) Syntax error
(B) Runtime error
(C) Overflow error
(D) Logic error
36. Why is it important to write programs that are readable?
(A) They are easier to modify and debug.
(B) They run more efficiently.
(C) They effectively process all cases of input.
(D) They produce accurate results.
37. How is collaboration useful in defining requirements?
(A) The multiple viewpoints can provide several outcomes for the program.
(B) Applying differing experiences and skills provides better identification, analysis, and program development to meet requirements.
(C) The analysis can be divided among several people, speeding up the development process.
(D) Having multiple perspectives helps the group form alliances among the team members.
38. When would lossless data compression be preferred over a lossy one?
(A) When you need to restore the original file
(B) When the level of compression is more important than restoring to the original file
(C) When you need to display the file on mobile devices and websites
(D) When you have limited space available on your computer
39. How does the Internet process transactions securely?
(A) The public key encryption model is easy to use to encrypt data but intractable for decrypting.
(B) Frequency analysis is used to disguise the use of common letters in encrypted messages, which keeps passwords secure.
(C) Symmetric keys are used to encrypt and decrypt messages for speed in processing to avoid interception.
(D) Multiple alphabets are used to encrypt and decrypt messages to allow for use with different languages.
40. When does an overflow error occur?
(A) When a program exceeds the limit of lines of code for a programming language
(B) When the lines of output exceed the programming language limit
(C) When a “divide by zero” condition occurs
(D) When an integer needs more bits than are available to represent it
41. Why are simulations useful abstractions?
(A) They can test hypotheses without real-world constraints.
(B) They can change multiple options at the same time, leading to new insights.
(C) They can precisely test real-world events to identify the ultimate outcome.
(D) They can confirm the cause of events.
42. What is one way that data can be intercepted over a public network?
(A) A router
(B) A successful phishing attempt
(C) Keylogging software
(D) A rogue access point
43. What is an example of lower-level abstractions combining to make higher-level abstractions?
(A) Dividing functionality into separate modules that are all part of one program
(B) Writing pseudocode to identify what the program needs to do
(C) Creating help documentation so the user will know how to use the program
(D) Using a flowchart to identify program decisions
44. How is the Internet scalable?
(A) Through the ability for additional networks and routers to be added without impacting service
(B) Through the ability to add longer public keys to keep data secure
(C) Through the ability to add additional authentication for users
(D) Through the ability to add additional bandwidth to requests
45. Having your personally identifiable information (PII) stored online enhances your online experience with making online purchases, filling out forms, and other uses. A risk is that your PII data could be vulnerable to exposure through hacking or accidental disclosure. Which piece of information is classified as PII?
(A) Zip code
(B) Internet search history
(C) Language preference
(D) Time zone
Questions 46—50.
A GPS company is developing a new software app called “Find my car!” to work with self-driving vehicles. If you cannot remember where you parked your vehicle, or it’s raining when you are leaving a location, you can press a button on an app to summon your vehicle. The self-driving car will exit its parking spot and drive to your GPS location for you to enter the vehicle.
Here is a flowchart of the process.
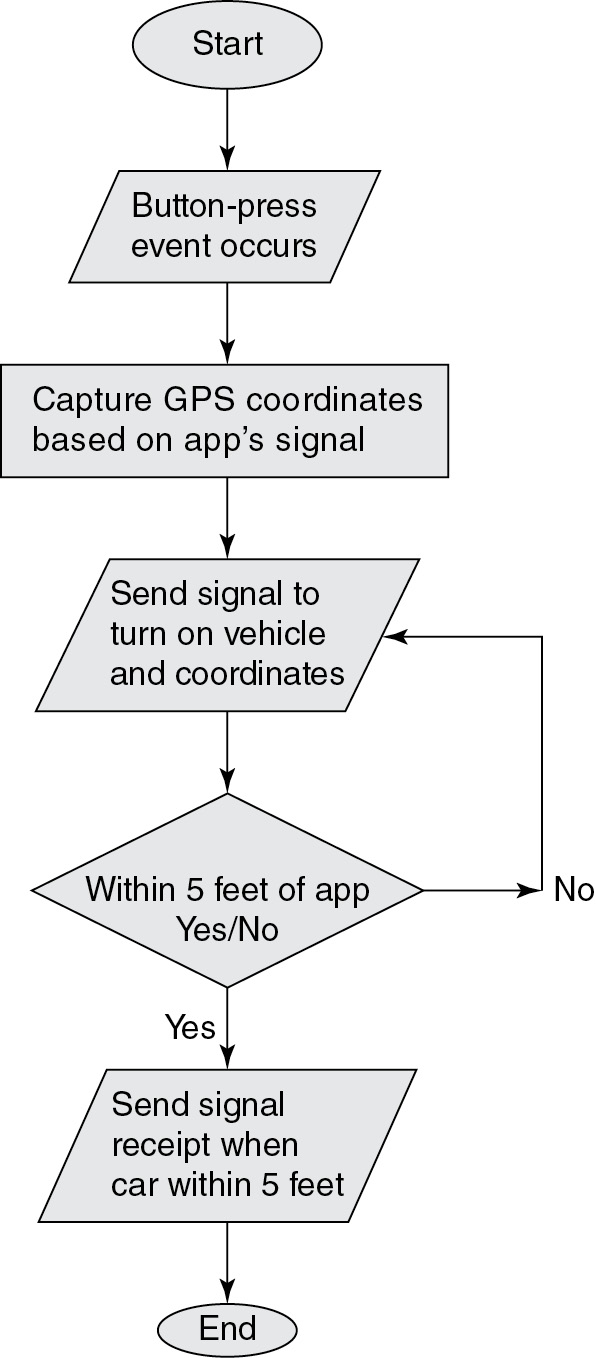
46. Is this a computing innovation? Why or why not?
(A) A computer program is not needed, so the app is not a computing innovation.
(B) The programming is completed by the GPS satellite, not this innovation, so the app is not a computing innovation.
(C) The programming is controlled by the self-driving car’s manufacturer, so the app is not a computing innovation.
(D) The app sends GPS coordinates to the vehicle, along with the signal to drive to the location, so the app is a computing innovation.
47. What output does the app produce?
(A) Instructions to start the vehicle and drive to the coordinates provided
(B) The button event to be pressed
(C) A signal to the GPS satellites to send current location coordinates
(D) Directions to get from the parking spot to the current location
48. What is the most likely privacy concern of the app?
(A) Two people using the app at the same location could cause the signal to be sent and recognized by both vehicles.
(B) Location data would be available and potentially used by the company to identify future needed updates to the app.
(C) Unauthorized individuals could use the app to summon someone else’s vehicle.
(D) People could enter the waiting vehicle before the driver gets to it.
49. Which of the following is the most likely potential harm of the app?
(A) Traffic congestion for drivers and pedestrians at restaurant and shopping entrances that were not designed for multiple waiting vehicles
(B) Increased air pollution if people leave their self-driving cars idling until they get to the vehicle
(C) Car accidents when people driving vehicles are maneuvering around the self-driving waiting vehicles
(D) Illegal parking as people leave their cars running to run into a store for a “quick” errand
50. What data is most likely to be needed for the app to work?
(A) Fingerprint reader for valid entry to the vehicle
(B) Accurate longitude and latitude coordinates
(C) Cameras for the vehicle to safely navigate to the signaled location
(D) Sensor to recognize the signal summoning the vehicle
51. Tracing what your code is doing is an example of which of the following terms?
(A) Discovery
(B) Debugging
(C) Traversing
(D) Scaffolding
52. What is an example of “metadata”?
(A) A line of code
(B) A header in a document
(C) Author of the document
(D) Test data
53. Why should we use an iterative development approach?
(A) Because each iteration improves or adds code to build a successful program
(B) To meet the legal requirements for code to handle sensitive data
(C) To be able to begin coding while remaining requirements are being defined
(D) To minimize the amount of time needed for testing
54. You need to write a program named calculate to compute the average temperatures for an area. What would be the best variable name for this and why?
(A) t—Variable names should be short so there is less opportunity for a typo.
(B) avgTemperature—Variable names should be descriptive to help others understand their purpose.
(C) calculateAvgTemp—Variable names should start with program name and then the variable name for ease of tracking.
(D) 1Temp—Variable names should begin with a number starting with 1, followed by 2, and so on to know how many there are.
55. How can you defend a phishing attack?
(A) Block incoming web traffic until the attack is over.
(B) Open the website in question directly rather than clicking on the link provided.
(C) Install antivirus software and keep it updated.
(D) Never open unexpected e-mail attachments.
56. On the AP exam, compound expressions can be created using which of the following operators?
(A) IS / IS NOT
(B) NOT / NOR
(C) IF / ONLY IF
(D) AND / OR
57. What does it mean when we say the Internet is redundant?
(A) Parts of it are unnecessary.
(B) If a path is down, packets can be routed a different way.
(C) It has a delay between the request and the response to the request.
(D) If there is an error, a backup system is brought online to be used.
58. What are packets in reference to the Internet?
(A) The delay in time from when a request is sent and received
(B) The individual sections of the IP address
(C) Information to be sent over the Internet broken into same-size groupings
(D) The intermediate locations that send information to their destination
59. What is the best use of spreadsheets and databases?
(A) Scale up to process more data
(B) Organize and filter data
(C) Create metadata
(D) Compress data
60. Which type of problem attempts to find the best solution from several possibilities?
(A) Algorithmic problem
(B) Decision problem
(C) Efficiency problem
(D) Optimization problem
61. What describes the process of keeping common or similar features and functionality while removing details that are different?
(A) Algorithm
(B) Decomposition
(C) Simulation
(D) Abstraction
62. A half-time program wants to randomly select a seat number for an attendee to come shoot baskets for the chance to win prize money. What code could randomly select a number from a list of seats checked in? Assume all variables are initialized correctly.
(A) selected ← (RANDOM(start, stop))
(B) ![]()
(C) REPEAT UNTIL (RANDOM(start, stop) = 0)
(D) 
63. What is a method to confirm a person’s credentials before providing access? Select two answers.
(A) Biometric identification
(B) Public key encryption
(C) A symmetric password
(D) A security token sent to a device such as a cell phone
64. Which of the following selection statements correctly tests if a number is less than 914? Select two answers.
![]()
(A) Selection 1 is correct.
(B) Selection 2 is correct.
(C) Selection 1 is incorrect.
(D) Selection 2 is incorrect.
65. How can you legally use an image on your website that you found on the Internet? Select two answers.
(A) You can use it copyright-free from the Internet.
(B) You can use it after paying a fee for use or obtaining written permission from the owner.
(C) You can use it if you provide attribution to the owner.
(D) You can use it if the author provided a Creative Commons license allowing such use.
66. What are key steps of any development process to ensure user requirements are met? Select two answers.
(A) Planning
(B) Feedback
(C) Creating
(D) Reflection
67. Which of the following are events that could trigger event-driven programming? Select two answers.
(A) Using a remote control for your TV
(B) A sensor sending data to a robot
(C) A program to calculate paycheck amounts
(D) A voice command
68. You have two procedures to select from to continuously loop through a series of digital billboard ads. Will both procedures successfully work? Assume the list of advertisements is correctly initialized and the programs will be restarted each time the ads change, usually weekly. There are 604,800 seconds in a week. Select two answers.
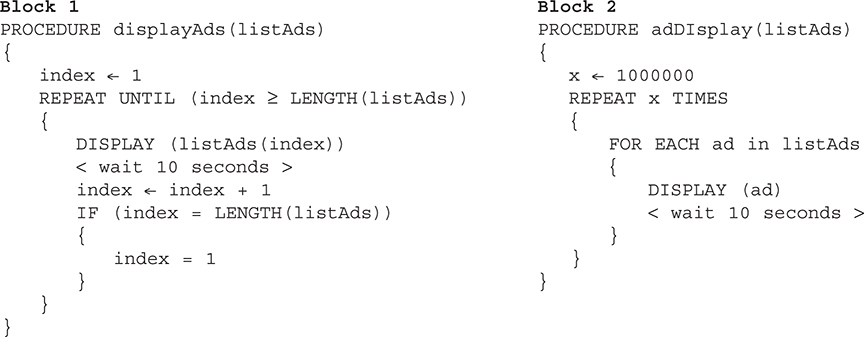
(A) Block 1 runs correctly.
(B) Block 1 does not run correctly.
(C) Block 2 runs correctly.
(D) Block 2 does not run correctly.
69. Your organization has determined that data used for assigning managers to high-volume sales stores is unintentionally biased. How can the bias in the data samples be corrected? Select two answers.
(A) Collect more data for a wider sample of data.
(B) Include a different type of data to add to the collection.
(C) Analyze the source of the data to identify existing bias to remove it.
(D) Review the attributes to include or ignore in your data collection and analysis.
70. You have the following procedure that is not working as expected to add numbers that are divisible by 2 or divisible by 3 to the end of a list. You collaborate with a classmate to help identify the problem. Assume the list of numbers passed as an argument holds valid numbers. What are the errors? Select two answers.
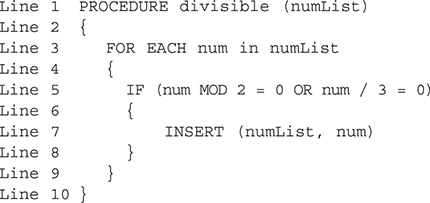
(A) Line 5 should use MOD in both places.
(B) Line 5 should use division “/” in both places.
(C) Line 7 should use APPEND rather than INSERT.
(D) Line 10 has an extra closing brace.
STOP. End of Exam.
![]() Answers and Explanations
Answers and Explanations
If further review is needed, the Big Idea where information can be found about the topic is included at the end of each question.
1. D—We do not need to know how a procedure works, only that it does. We need to know what input to provide and what output to expect. The details are hidden or abstracted away inside the procedure’s code. Big Idea 3: Algorithms and Programming
2. A—Parameters allow a procedure to be more flexible by permitting different values from the program to be sent to the procedure. Code does not have to be duplicated each time it needs to be used in the program. Big Idea 3: Algorithms and Programming
3. D—Cleaning data refers to taking raw data and checking it for errors. These errors could be corrupt, incomplete, or duplicate data. Cleaning could include either correcting or removing the identified data, depending on the specifications for a particular dataset. Big Idea 2: Data
4. A—Unreasonable problems may have an algorithm that can work for a small number of values, but as the dataset grows large, the time or memory requirements to run it are beyond current capabilities. Big Idea 3: Algorithms and Programming
5. B—These are some of the abstractions that can be used in writing software. Both procedures and libraries provide algorithms that can be used without knowing the details of how they work—which is the definition of procedural abstraction in computer science. Big Idea 3: Algorithms and Programming
6. C—Organizations handling datasets must protect the data to ensure that people’s private information is not accidentally revealed or able to be deduced or identified with basic data already publicly available. Big Idea 5: Impact of Computing
7. C—Protocols are a set of rules for a variety of services on the Internet. Data will move across any brand of equipment as long as the protocols are followed. Big Idea 4: Computing Systems and Networks
8. B—The decimal number converts to 10011110. Take the binary number and create a table of the powers of 2, starting with 20 in the right-most position.
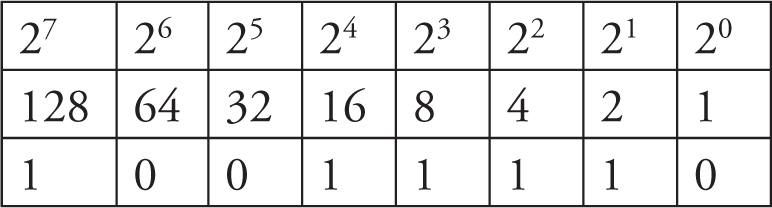
Subtract the largest value from the second row that is the same or less than the number, 158. In this case, subtract 158 — 128. Your remainder is 30. Place a 1 in the 128 column.
You can’t subtract 64 or 32 from 30 without ending up with a negative number, so place 0 in those two columns.
You can subtract 16 from 30 and have a positive result. Therefore, subtract 30 — 16 = 14, and place a 1 in the 16s column.
You can subtract 8 from 14, so place a 1 in the 8s column and subtract 14 — 8 = 6.
You can subtract 4 from 6, so place a 1 in the 4s column and subtract 6 — 4 = 2.
Since 2 — 2 = 0, place a 1 in the 2s column and a 0 in 1s column.
Big Idea 2: Data
9. C—The code associated with the selection statement is executed when the Boolean condition evaluates to be true. Additional code can be executed if the condition is false using the ELSE statement. Big Idea 3: Algorithms and Programming
10. B—The FOR EACH loop traverses the list of student names. Therefore, we have to keep track of our position in the lockerNum list with the index variable. We need to set the lockerNum list to the assigned student name and the locker number is the index position. Remember that lists start at index 1 for these exam questions. Big Idea 3: Algorithms and Programming
11. A—Logical conditions are in a Boolean format, using relational operators such as >, <, =. This means that each condition will always evaluate to either true or false. Big Idea 3: Algorithms and Programming
12. D—Machine-learning algorithms learn from and make predictions based on data to improve the experience for those using it. One example is search algorithms. These often infer additional details of your search criteria, such as showing the Mustang car versus the mustang horse if your other search criteria include automobiles. Big Idea 2: Data
13. C—The index starts at the first position, 1, and includes the “n” in person at index position 6. Remember that the index position starts at 1 for this exam.

Big Idea 3: Algorithms and Programming
14. C—Analog data is converted to digital data by taking samples at regular intervals. These samples are converted to bits to represent the analog data in a digital format. Big Idea 2: Data
15. D—APIs provide prewritten, pretested program modules to be used by other programs, greatly simplifying the process of writing a new program. This helps speed up writing and testing the code as well. Big Idea 3: Algorithms and Programming
16. A—Testing involves implementing the algorithm through code and executing it to determine how often statements execute. These are used to informally determine the algorithm’s efficiency. Big Idea 3: Algorithms and Programming
17. B—Different algorithms can be created to solve the same problem. These algorithms could provide new insights to the problem as well as be more efficient. Big Idea 3: Algorithms and Programming
18. A—All algorithms can be written with a combination of sequential, selection, and iterative statements.
• Sequential statements run one after the other.
• Selection statements are run only if the criteria are met.
• Iterative statements repeat while the criteria are met.
Big Idea 3: Algorithms and Programming
19. A—Viruses must be spread via an infected file. These are transmitted in ways to get people to click on them, and e-mail attachments are the most common way. Big Idea 5: Impact of Computing
20. C—The digital divide is the term used to denote the different levels of access to the Internet and/or access to computing devices based on geographic, demographic, or socioeconomic attributes. Big Idea 5: Impact of Computing
21. B—Developing program components and testing them before combining them with other working, tested code helps create larger, correct programs. Big Idea 3: Algorithms and Programming
22. D—A binary search uses the “divide and conquer” method to halve (divide by 2) the size of the dataset, and continues to search the half of the dataset the number could still be in. The "higher" or "lower" feedback is required to determine which half of the dataset to keep. This search is very efficient, and the dataset must be sorted for it to work. Big Idea 3: Algorithms and Programming
23. B—By documenting what the program does, if code is changed, the programmer changing it can test to ensure that the program still works as intended. Big Idea 1: Creative Development
24. A—Parallel computing systems have a sequential part and a parallel part. The parallel part spreads out the processing among multiple devices to reduce the time needed. The sequential part combines the results from the parallel processing. Big Idea 4: Computing Systems and Networks
25. D—The same binary number could represent a number, color, or text field. The program using the binary number knows how to interpret its meaning. Big Idea 2: Data
26. B—Iteration sets up conditions where code can be repeated either a specified number of times or until a condition is no longer met. Big Idea 3: Algorithms and Programming
27. B—Undecidable problems do not have an algorithm that can solve all cases. Big Idea 3: Algorithms and Programming
28. C—Procedures are blocks of code that can be reused through calling them as many times as needed in a program, rather than duplicating code. This makes the program more readable and easier to maintain. Big Idea 3: Algorithms and Programming
29. B—Collaboration is the process of working with one or more individuals on an activity or task. It is an effective way to test and correct code. Team members can test each other’s code and help each other correct any errors that are found. The collaborative efforts could occur in person or in a virtual format. Big Idea 1: Creative Development
30. B—Certificate Authorities (CAs) issue digital certificates that allow others using a site to confirm that the identity of that site is authentic. Big Idea 5: Impact of Computing
31. C—Bandwidth measures how much data can be transmitted from a location to another in a given amount of time. Big Idea 4: Computing Systems and Networks
32. C—A FOR EACH loop will check each element in a list from start to end without having to specify each one individually. Neither an “index out of bounds” error nor an infinite loop will occur. Big Idea 3: Algorithms and Programming
33. B—This is the concept behind libraries and APIs. Prewritten and tested algorithms and code can be used by other programs needing the same functionality in their program. It saves time as well as helps ensure that the new algorithms are correct. Big Idea 3: Algorithms and Programming
34. C—The classroom has 25 available desks, so the REPEAT UNTIL loop should continue until the number of available desks is 0. Big Idea 3: Algorithms and Programming
35. D—Logic errors occur when the program runs but there are unexpected results either in the steps the program executes or the output. An example would be using the wrong variable in a calculation that would give incorrect results. Big Idea 1: Creative Development
36. A—Readability makes code easier to understand and therefore easier to debug, maintain, and enhance. Big Idea 3: Algorithms and Programming
37. B—Having people with different perspectives and backgrounds helps identify new trends or ideas and potential solutions more easily than someone working alone or a in homogeneous group. Big Idea 1: Creative Development
38. A—Lossless data compression techniques enable the original, uncompressed file to be restored. Lossless techniques do not provide as much compression as a lossy technique, but always select this when you may need to restore the original file. Big Idea 2: Data
39. A—A good cryptographic model is easy to use in one direction, such as encrypting data, but very difficult to do in the other direction, the decryption of the data. This means that even if the information is intercepted, someone trying to exploit it will not be able to identify the correct decryption key needed. Big Idea 5: Impact of Computing
40. D—Many programming languages have a set limit for the integer size that can be represented. When that is exceeded, an overflow error occurs. Most languages do not display an error message. Instead, the sign bit is flipped and a positive number becomes negative and vice versa. Big Idea 2: Data
41. A—While models are usually on a smaller scale than the real-world feature they represent, they can be used to simulate actual events to see the result of changes to variables. These can be run without actual constraints, such as emulating an eclipse without having to wait for an actual eclipse to occur to test the hypotheses. Big Idea 3: Algorithms and Programming
42. D—A rogue access point on a network can capture data to save it, analyze it, or modify it. Big Idea 5: Impact of Computing
43. A—Each module handles functionality independently but can be combined with other modules to create new functionality. For example, if a module adds a text field to a list, it can be added to functionality to create and maintain a contact list on a smartphone. Big Idea 1: Creative Development
44. A—As the demand for Internet connections grows, new networks can be added along with additional routers as needed, without impacting existing services. Big Idea 4: Computing Systems and Networks
45. A—Your zip code, which is available in many public records, is considered part of your PII. Big Idea 5: Impact of Computing
46. D—A computing innovation has to have a computer program as part of its functionality. The proposed “Find my car!” app will have a program that will begin when the specified button is pushed to summon the vehicle. It will request current GPS coordinates through an API call and send them to the self-driving vehicle along with the command to turn on the car. Big Idea 5: Impact of Computing
47. A—The output of the app will be the longitude and latitude of the app’s location. An instruction to start the vehicle will also be output from it. Big Idea 1: Creative Development
48. B—Tracking and storing location data is likely to occur for the app to store coordinates for frequently visited locations. This is a privacy concern because the data will be available to the organization developing the app and potentially the self-driving vehicle’s manufacturer and any repair shop used. Anyone who uses the driver’s smartphone can pull up the app and view the history as well. Big Idea 5: Impact of Computing
49. A—Any traffic congestion at the entrance to businesses and organizations is a potential harm that is due to the app itself. There could be increased air pollution anytime people leave their car idling, but that is not due to the app. Car accidents and people parking illegally are harmful but are also not due to the app. Big Idea 5: Impact of Computing
50. B—The app will be activated by an event, the pressing of a button to start the program’s processing. For the app to work, it will need accurate longitude and latitude coordinates accessed through an API to a GPS (Global Positioning System). If the self-driving car cannot get within a few feet of the driver, the app will not be useful and people will not continue to use it. Big Idea 1: Creative Development
51. B—One method of debugging involves following or tracing each line of code to determine what the program is doing versus what it should be doing based on current variable values. Big Idea 1: Creative Development
52. C—Metadata means “data about data.” The only option that provides information about the data versus being data is information about the author. Big Idea 2: Data
53. A—The steps in an iterative development process are:
• Investigate and fully define the problem to be solved.
• Design a solution to solve the problem.
• Prototype to code the solution.
• Test to evaluate the solution.
These steps should be repeated as needed in additional iterations to further refine and improve the programs based on testing and feedback. Big Idea 1: Creative Development
54. B—Variable names should be descriptive and use “camel case” by capitalizing the first letter of the second and additional words, when two or more words are used for the variable name. Example: shoeSize. Big Idea 3: Algorithms and Programming
55. B—Typing in the link for the organization, such as your bank, directly in a new tab rather than clicking on the link provided will deflect a phishing attack. Big Idea 5: Impact of Computing
56. D—Using the AND and OR operators creates a compound expression. Both conditions for the AND must be true for the expression to be true, and at least one of the conditions needs to be true for an OR compound expression to be true. Big Idea 3: Algorithms and Programming
57. B—Internet redundancy means that if a path is down, then the packets can be sent via an alternate route to reach their destination. Big Idea 4: Computing Systems and Networks
58. C—Packets are same-size groupings of information to be sent over the Internet along different paths. Big Idea 4: Computing Systems and Networks
59. B—Technology tools such as spreadsheets and databases are designed to organize data and filter data through inquiries and reports to analyze it. Big Idea 2: Data
60. D—An optimization problem looks for the best solution to the problem. If someone wants to optimize their performance, they are looking to improve it. Anytime you are looking to enhance the outcome of something, you are looking for the best solution or to optimize it. Big Idea 3: Algorithms and Programming
61. D—Abstractions remove differing details to create a more general and more flexible concept. Big Idea 2: Data
62. A—Calling the RANDOM function with the correct start and stop numbers and storing it in a variable will correctly select an attendee to participate. Big Idea 3: Algorithms and Programming
63. A—A biometric indicator is something unique to the individual, such as a fingerprint or retina scan. It would be set up in advance for comparison purposes to anyone attempting to access the device.
D—A security token sent securely to a device such as a cell phone can ensure that the person is who they claim to be. The device to send the token to is set up in advance. Big Idea 5: Impact of Computing
64. A—Selection 1 is correct since it correctly tests if a number is less than 914.
B— Selection 2 is also correct because if a number is not greater than or equal to 914, then it can only be less than 914. Big Idea 3: Algorithms and Programming
65. B—Artifacts on the Internet are not necessarily free. They are someone else’s intellectual property. You may not use the image without paying the licensing fee or obtaining written permission from the owner to use it.
D —The Creative Commons licensing options allow creators to make their work available for viewing, and possibly for use by others, depending on the licensing option selected. Big Idea 5: Impact of Computing
66. B—Feedback from those who will use the system is key to refining the programming solution to meet the project’s requirements.
D—Reflection after each iteration of the development process also helps to ensure the program code will correctly meet the requirements. Big Idea 1: Creative Development
67. B—A sensor reading is an event. The robot’s code would test for certain conditions to cause different events based on the values of the sensor.
D—A voice command is an event. Event-driven programming is when code is executed only when something occurs that the program recognizes as a valid event, such as a voice command like “Hey Google,” “Siri,” or “Alexa.” Big Idea 1: Creative Development
68. A—Block 1 runs correctly. Each time the index reaches the last element in the list, it is reset to 1 to start displaying ads from the beginning of the list again.
C—Block 2 runs correctly. The loop is set to run one million times to keep cycling through the ads in the list, 24 hours a day, 7 days a week. The company expects the ads to change prior to reaching the one millionth time. The counter will be reset to one million each time the ads change. Big Idea 3: Algorithms and Programming
69. C—Analyzing the source of the data to identify existing bias in the data can correct the outcome of the algorithm. If historical data is used, and historically people with certain attributes were most often the managers of high-volume stores, then those people are more likely to be recommended for those high-volume stores.
D—Reviewing the data attributes, such as gender, age, income, or race, that you want the analysis to consider can help prevent or remove bias from the outcome. Big Idea 2: Data
70. A—To determine if a number is divisible by another number, the remainder must be 0. Therefore, both operations should be MOD.
C—To place the numbers at the end of the list, the APPEND command should be used rather than INSERT. Additionally, the number of parameters for the INSERT command on Line 7 are for the APPEND command rather than INSERT. Big Idea 3: Algorithms and Programming
Analyzing Your Performance on the Diagnostic Test
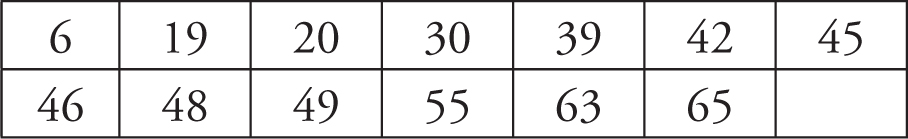
The exercise below will help you quickly and easily identify the chapters in Step 4 that you most need to review for the AP Computer Science Principles multiple-choice exam. Revise your study plan so that you prioritize the chapters with which you had the most difficulty.
Look at your answer sheet and mark all the questions you missed. Then shade in or mark an X in the boxes below that correspond to the question numbers that you missed. Then you will know what concepts you need to review the most.
Big Idea 1: Creative Development
![]()
Big Idea 2: Data
![]()
Big Idea 3: Algorithms and Programming

Big Idea 4: Computing Systems and Networks

Big Idea 5: Impact of Computing