5 Steps to a 5: AP Computer Science Principles 2024 - Sway J.S. 2023
6 The Explore Curricular Requirement
STEP 4 Review the Knowledge You Need to Score High
IN THIS CHAPTER
Summary: For the Explore curricular requirement is in its second year. You will do at least three activities during the school year to learn how to recognize a computing innovation and analyze it in specified ways. In conjunction, there will be a stimulus-type scenario. It will have a reading passage and potentially graphs and charts for you to review. There will be five multiple-choice questions requiring you to analyze the information in the passage to be able to select the best answer for the questions. To prepare, make sure you are working with the Explore Curricular Requirement document and NOT the Explore performance task, which is no longer required.

Key Ideas
![]() A computing innovation has a computer program that is essential to its operation.
A computing innovation has a computer program that is essential to its operation.
![]() Computing innovations have data as input, process the input, and create output in some form.
Computing innovations have data as input, process the input, and create output in some form.
![]() Computing innovations can be used in unintended ways.
Computing innovations can be used in unintended ways.
![]() Computing innovations may have privacy, security, or storage concerns.
Computing innovations may have privacy, security, or storage concerns.
![]() Computing innovations can have beneficial or harmful effects and an effect could be considered either, depending on your perspective.
Computing innovations can have beneficial or harmful effects and an effect could be considered either, depending on your perspective.
![]() There will be one Explore stimulus reading passage with five multiple-choice questions relating to the passage on the AP exam.
There will be one Explore stimulus reading passage with five multiple-choice questions relating to the passage on the AP exam.
Key Terms
Computing innovation
Beneficial effects
Harmful effects
Privacy concern
Security concern
Storage concern
Explore Curricular Requirement: The Basics
The Explore curricular requirement replaces the Explore performance task. Be sure you are using information from the College Board for the current AP exam. The focus of the Explore curricular requirement is identifying and analyzing computing innovations. There are three different activities that should be covered during your course with your teacher to help you prepare and practice this analysis. If you are preparing for the exam independently, don’t forget to include these activities.
In addition, the AP Computer Science Principles exam will have a stimulus-prompt-type scenario. It provides information, such as a paragraph to read and charts to review, about a made-up computing innovation. There will be five multiple-choice questions associated with the stimulus material on the exam. These questions will be grouped together with the passage.
The three activities done during the course are designed to prepare students for the stimulus questions. They build knowledge about the following:
• What makes an innovation a “computing” innovation
• Identifying and analyzing the data that feed into the computing innovation
• Potential risks to privacy, security, and storage of data collected and used by the computing innovation
• Intended and unintended effects of the computing innovation that could result in either beneficial or harmful impacts
Computing Innovations
A computing innovation is one that has a computer program that is essential to the innovation being able to operate. You should be able to describe the program and what it does for an innovation. If you can classify an innovation as any of the following, then it is a computing innovation.
• A physical innovation—such as a GPS
• Nonphysical computing software—such as an app
• Nonphysical computing concept—such as social networking

Input/Processing/Output
Another key topic you will see in the stimulus questions deals with the data used by the computing innovation. With the program you developed for your Create performance task, you had to demonstrate and write about input to your program and output from your program and how the program or a procedure within the program used the data to produce the output. This is the same idea, so you’ve had some experience with the concept!
A key concept is being able to distinguish the data from the device that collects the data. A lot of students have trouble with this, so be sure you’ve got it. For example, a sensor is a data collection device. It sends the data it collects to the program. The data would be values for distance, temperature, motion, among many others, and it is input to the computer program in the innovation.
The innovation’s program then processes the data and produces some type of output. With our example of sensor data, if the temperature is above a certain limit, an alert message may be sent or the air conditioner may be turned on. The message and “turn on” signal are examples of output.
Analyzing Data
You could also see questions about other important concepts related to analyzing a computing innovation’s data. These include the following:
• How the data collected could be traced to an individual (privacy)
• Who can access the data (security)
• Where the data is warehoused (storage)

Many students have difficulty with the difference between privacy and security. Be sure you can describe this.
Privacy is protecting our identity. If someone accesses partial data, could they piece together who we are through that data and other publicly available data? Similarly, if our data is supposed to be combined with a lot of other data in a way to mask our identities, is it possible to drill down and identify an individual? These are privacy issues.
Security deals with who can access our data. Organizations are supposed to limit who can see or update our data. Schools have to maintain a lot of data about students and teachers. Keeping your data secure includes ensuring another student will not be able to see your grades nor will you be able to see other students’ grades in an online gradebook. It also means that your science teacher may be able to view all of your grades but can only change your science grades, not your English or math grades.
Data storage concerns center around where the data is located. If your school data is stored on a local server, the data should be protected so only authorized people are able to access it. However, all organizations should keep backup copies of their data in case a disaster, like a burst water pipe, destroys their local server. If the backup data is stored in the cloud, is it encrypted while it is sent to the location in case it is intercepted? Who keeps it private and secure at the backup location?
Impact of Computing Innovations
The effects of any innovation, including computing innovations, are the results or outcomes from its intended use. These effects can be beneficial or harmful, and sometimes the same effect can be both to different people. When you are analyzing information in one of the stimulus questions, try to look at the effects from different viewpoints to help you see potential impacts and whether they would be considered a positive or a negative.
It is also important to recognize when computing innovations are used in ways they were not intended. Sometimes this can be great, such as when the World Wide Web branched out from its original intention of sharing scientific papers. The World Wide Web has had many beneficial impacts on society, giving us the ability to communicate with anyone in the world who has access in real time, on the economy through e-commerce and the ability to make purchases online, and on culture because we are able to view and learn about other cultures or see and set new trends.
There are also harmful effects related to the web. It’s not all unicorns and rainbows. People harass and cyberbully using the web. They commit fraud with online purchases, and they spew biased and inaccurate information about other cultures.
As you can see, it all depends. You need to be able to identify these aspects, and the three projects you did during your class would help you develop and practice these skills.
![]() Analyzing a Stimulus Question
Analyzing a Stimulus Question
Let’s try a practice question and analyze it as we go.
A food delivery company is developing an app to optimize the number of delivery personnel on duty for faster delivery. It is tracking historical data to use to predict future staffing needs. The historical data includes zip code, time of day, and order information.
To be able to streamline their weekly food order, the company started collecting orders per address. After collecting data, they noticed patterns with certain homes and concluded the homeowners are out of town during those weeks. They decide to offer a targeted ad to send to people who appear to be out of town in a regular pattern to order food for delivery when they return.
1. Predicting that homes could be empty on certain dates is an example of:
(A) A security concern since the regular drivers would know which homes did not order on a given week
(B) An economic impact to the company due to lost sales while regular customers are out of town
(C) A storage concern since that is extra data to be stored and tracked but is not likely to result in additional revenue
(D) A privacy concern since anyone with access to the data could identify the home
Let’s look at each option and see what it is asking. A security concern is one where people who should not be able to view or update our information have that capability. If our address is included in a list of those to receive a special ad, and anyone can see it, it is a security concern. However, the response goes on to state that the regular drivers would know which homes were potentially unoccupied. The drivers could know that without viewing the data. Also, the question is asking about predicting which homes could be unoccupied, which is not related to the security of the data. So option (A) is out.
Option (B) deals with lost revenue to the organization since regular customers did not order. While is it an economic impact, it is not due to predicting which homes will not be ordering in a particular week. It’s going to occur regardless, and could occur even if people are in town. So (B) is not the answer.
(C) is looking at the amount of data the company is collecting and storing for analysis. While that could be a concern, it is not due to the analysis that led to this prediction. Those are two separate events. (C) is also not the correct response.
Remember that a privacy concern is one where our identity could be exposed. The question references “predicting” that homes could be empty. If software is predicting that no one is home and our address is reasonably tied to that prediction, then it is a privacy concern for us. (D) is the correct answer.
2. Which potential harm is most likely to occur due to the new marketing program?
(A) Lost sales due to people traveling
(B) Lost sales due to public perception of the targeted ad
(C) Higher spoilage rate of food inventory that cannot be sold
(D) Fewer delivery drivers available for unexpected orders due to lower projected sales during certain weeks
There will be lost sales due to people traveling, but it’s only because they are out of town, not due to the new marketing program. Option (A) is not the correct answer.
In this option, (B), the lost sales are due to the public perception of those receiving the ad (and whomever they tell). Since it indicates their travel schedule is known, most people would not be happy about receiving an advertisement about that. When people feel exposed and the data is out of their control, they are more likely to stop using the service completely to feel like they are doing something to protect their data. (B) is the correct answer.
While food that goes bad is a cost and a harm to the restaurant, it is not related to the marketing program. (C) is not the answer.
Trying to schedule delivery drivers when sales are not known in advance is always difficult and an ongoing problem for any business doing deliveries. However, this potential issue is not related to the marketing program. (D) is not the correct answer.
3. The data in the chart shows the average distance a driver has to travel during a typical evening shift. What data is needed to schedule driver routes that is not provided in the chart?
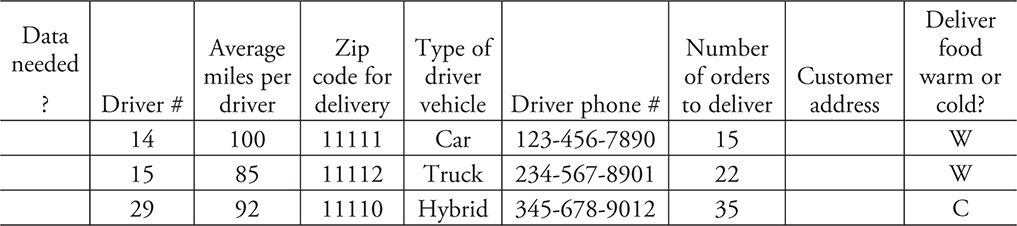
(A) Data with the next closest address
(B) Time of day
(C) If food needs to be kept warm or cold—to keep the food quality intact
(D) Toll roads on the route to the delivery location
To be able to schedule the routes for the drivers, we’ll need the number of orders, which is available in the chart, and zip code, which is also available. We would also need to know the next closest address to be able to schedule the route. A heuristic approach will be used to determine this using the next closest neighbor approach. Calculating the optimized route would run in an unreasonable amount of time. The correct answer is (A), as the next closest address is needed to plan the route. This can be accessed through a GPS program.
In option (B), the time of day is useful because traffic patterns do change, but it’s better to get the traffic patterns for the day of the week rather than the time of day.
Option (C) is important to delivering quality food, but with portable devices to keep food cool or hot, it is not a consideration in planning the driver route.
Option (D) can also impact the time it takes between locations, but with fast-pass cards that allow drivers to drive through toll booths and be counted electronically, it is not a significant factor. Without the next closest address, it would not be possible to know if a toll road is even on the route yet.
4. What is the most helpful expected output after processing the time of the order as input to the program?
(A) Ingredients needed to order to restock for next week’s order
(B) Approximate cooking time
(C) Driver name for the delivery
(D) Estimated delivery time
If the order time is added as input, there are several available outputs. The question asks for the most helpful expected output, so keep that in mind as you evaluate possible answers.
Option (A) is needed by the business, but it is not an expected output of this program, which is to plan the number of delivery drivers needed. (A) is not the correct answer.
Option (B) uses the approximate cooking time, which helps to know when the order will be ready, but that would be another useful input to have rather than an output. (B) is not the answer.
Option (C) would be an output to know who will take the order, but it is not the most helpful. (C) is not the answer.
Option (D) is the best option. With the input data available, the best output will be the estimated delivery time. That’s also what the customer wants to know!
5. What is a potential unintended use of this program?
(A) Employees placing fake orders to be scheduled to work
(B) As a route planning app in addition to an employee scheduling app
(C) Crime watch usage of neighborhoods where people are out of town
(D) Increased crime at empty homes based on the data stored by the company
While some employees may place fake orders, there is no guarantee that they will be called in to work. If caught, they would probably be fired, so it’s not worth the risk. (A) is not the correct answer.
While the company planned for the app to schedule delivery drivers, with the information available to it, it can also be used for route planning. Option (B) is the best answer.
Since the pattern emerged about people being out of town, the data may not be accurate in all cases, and this would not be helpful to the company’s main line of business. Option (C) is not correct.
If increased crime occurred due to the company’s data being available to others who commit the crimes, the company would probably end up out of business. (D) is not correct.
![]() Stimulus Practice Questions
Stimulus Practice Questions
A city has placed ramp metering lights, which are traffic lights on entrance ramps, to help improve the flow of traffic. A camera records data at the location and transmits it to the city’s data center.
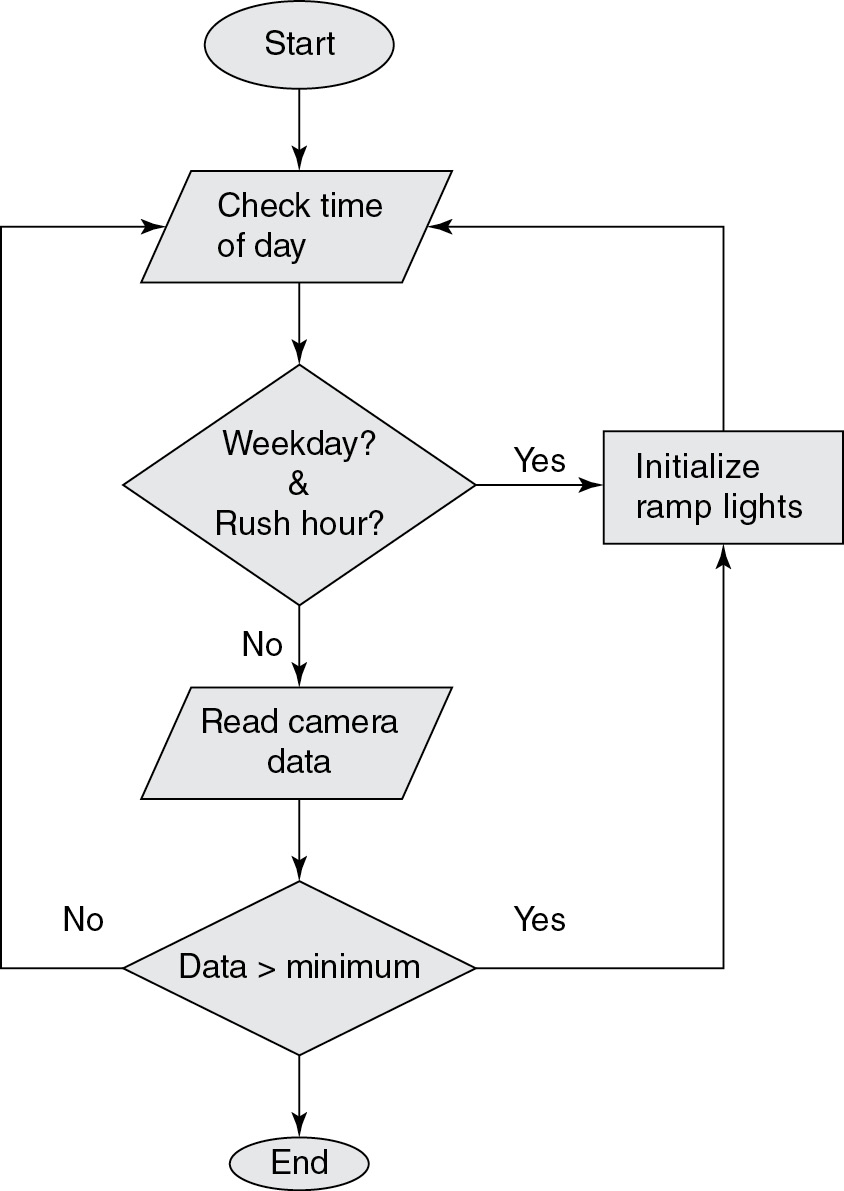
1. Which of the following data cannot be captured at the ramp entrance?
(A) Number of cars on the highway
(B) Date
(C) Location of the ramp meter
(D) Number of cars that pass through the entrance ramp each hour
2. What type of concern is most realistic?
(A) Privacy concern through capture of vehicle information
(B) Security concern if Department of Motor Vehicle employees can view the data
(C) Storage concern for the high amount of data collected due to high volume of vehicles that use the entrance ramp
(D) Personal protection concern due to potential sharing of data with other government agencies
3. If you are responsible for writing the code to activate values for the ramp light on and off cycles, what data could you use?
(A) Camera data
(B) Typical traffic patterns for weekdays
(C) Number of red/green cycles in an hour
(D) Pressure sensor data as cars enter the ramp
4. What is the least likely potential benefit to society from this innovation?
(A) People will change their routes to access the highway at less congested entrance ramps, improving the overall traffic flow.
(B) The air quality could improve with fewer traffic jams.
(C) There will be fewer accidents due to safer merging onto the highway.
(D) The better flow of traffic leads to decreased fuel consumption.
5. Now you’ve been asked to add code to your program to allow the activation signal to automatically turn off if traffic on the entrance ramp backs up and blocks side roads. What data is needed to do this?
(A) Sensors
(B) Cameras
(C) Average number of vehicles that fit on the ramp
(D) When side streets are blocked by the entrance ramp traffic
![]() Answers and Explanations
Answers and Explanations
1. A—The number of cars on the highway cannot be determined by the data that is available at the entrance ramp. The date and location of the entrance ramp and the number of cars that have used the entrance ramp hourly are available data.
2. A—With the camera taking photos of cars on the entrance ramp along with date, time, and location, the privacy of your information is a concern. The combination of the data can be used to identify the owner of the car, if not who was actually driving it. Your whereabouts can be tracked and you can be identified through it if the data is not adequately protected.
3. B—The typical traffic patterns will provide you with reasonable values to initialize the timing for the ramp lights. The camera and sensor are devices, not data. They provide data, but the specific data is not listed. The number of red/green cycles will vary per hour based on the amount of traffic. Knowing how many cycles could occur an hour is not useful data as it may change based on the input.
4. B—All of the options list a possible benefit. However, decreased air pollution is the least likely to occur since cars are still on the highway. It would also be difficult to prove that the improved air quality was exclusively a result of the ramp lights.
5. D—The data from sensors located on side streets would be needed as input to allow the shut-off feature to be programmed. Sensors and cameras alone are devices, not data. The average number of vehicles that fit on the ramp could help, but comparing the average to actual vehicles may not indicate that side streets are blocked. The current data from side street sensors is needed. Of course, the program would also need to turn the ramp lights back on once the side street traffic cleared.