CEH Certified Ethical Hacker Practice Exams Second Edition (2014)
Web-Based Hacking: Servers and Applications
This chapter includes questions from the following topics:
• Identify features of common web server architecture
• Identify web application function and architecture points
• Describe web server and web application attacks
• Identify web server and application vulnerabilities
• Identify web application hacking tools
• Describe SQL injection techniques, attacks, and tools
• Describe buffer overflow attacks
![]()
One of the easiest ways to get nerds all up in a bother, outside of comparing Jean-Luc Picard versus James T. Kirk as Captain of the Enterprise, is to mention Linux is “more secure” than Windows. Linux zealots (a touchy group that band together in the defense of their beloved open source OS) point to the general lack of cases involving Linux servers versus their Microsoft counterparts. Windows supporters fire back that there are simply more Microsoft boxes on the Internet and, therefore, it’s only logical that there would be more attacks and more vulnerabilities discovered because of the extra scrutiny. So, what’s the real truth?
If you’re bored someday, a little Google searching on the subject is enlightening. A study done by the SANS Institute seems to suggest that the Linux guys might be on the right side of the argument—at least from a web server perspective—although maybe not for the reason you might initially think. Their research showed that while attackers may not specifically target Microsoft web servers, they actually try to avoid attacking a Linux one—or at least one they think may be on a Linux system. To pull this off, they set up a fake bank with Apache (on a Linux box) and IIS servers supplying access. They found that when the OS was obscured, attackers spent relatively the same amount of effort on both sides; however, when the OS was easily discernable, the IIS attacks outnumbered Apache by almost 2 to 1.
Does this mean IIS is inherently less secure than an Apache install on Linux, or is it a treatise on the availability of more attack information on Microsoft machines than Linux “how-tos”? There’s plenty of evidence that Microsoft’s discovered security flaws and its respective critical patches for those flaws far outweigh those of its Apache peers. And there’s also plenty of evidence that the numbers argument no longer applies, since Microsoft IIS could be on its way down to third in the web server dominance race (Netcraft’s April numbers show Apache with 51 percent and IIS with 20 percent, with nginx at 19 percent). If there are, in fact, so many more Apache servers than IIS, by almost two to one, then logic would seem to dictate attackers would focus more on that offering. However, the facts just don’t show that.
I think the real answer to all this is, it depends on your perspective. No matter what OS/web server combination you use, there are steps to take in securing them that will frustrate an attacker’s ability to do you harm. With IIS, it may simply be that the ease of use leads to a lot more default vulnerabilities and attackers are counting on that. Or it may be that there are so many potential security flaws discovered with IIS, the return on investment in time of the attack means Windows is a better target. In any case, hackers have shown an aversion to attacking Apache and a preference for Windows. I’ll leave the “mine is more secure” argument to the nerd legions out there, although we may all soon be arguing nginx anyway.
These questions surround the web server and web application attacks you’ll need to be aware of. Businesses and corporations have many defenses arrayed against an attacker but oftentimes overlook the web server and applications they have sitting there, facing the public. Many attackers would argue that the customized, internal web applications are your best attack point to begin with, and it’s not a hard argument to make. After all, if the target organization is going to trust the public-facing stuff, why not have a look?
![]()
 STUDY TIPS Thankfully, most questions you’ll see about these topics are of the straightforward, definition-based variety. Be careful with the wording in these questions, though, because they’ll sometimes try to trick you up with petty minutiae instead of actually testing your knowledge. SQL injection and buffer overflow topics will more than likely make up the majority of your questions. Oh, you’ll see plenty of XSS and directory traversal stuff, and you’ll need to at least have an idea what Unicode and HTML entities are, but most of it is pretty easy. Lastly, you won’t be bothered with too many actual architecture questions (in regard to the web server type itself), but don’t give away an easy one.
STUDY TIPS Thankfully, most questions you’ll see about these topics are of the straightforward, definition-based variety. Be careful with the wording in these questions, though, because they’ll sometimes try to trick you up with petty minutiae instead of actually testing your knowledge. SQL injection and buffer overflow topics will more than likely make up the majority of your questions. Oh, you’ll see plenty of XSS and directory traversal stuff, and you’ll need to at least have an idea what Unicode and HTML entities are, but most of it is pretty easy. Lastly, you won’t be bothered with too many actual architecture questions (in regard to the web server type itself), but don’t give away an easy one.
1. Which of the following is used to disable file extensions in Apache servers?
A. disable_FS
B. mod_negotiation
C. stop_files
D. httpd.conf
2. You are examining connection logs from a client machine and come across this entry:
http://www.business123.com/../../../../../Windows/system.ini
Which attack does this most likely indicate?
A. Parameter manipulation
B. XSS
C. SQL injection
D. Directory traversal
3. A hacker is looking at a publicly facing web front end. One of the pages provides an entry box with the heading “Forgot password? Enter your e-mail address.” In the entry, he types anything’ OR ‘1’=’1.
A message appears stating “Your login information has been sent to a_user-name@emailaddress.target.com.”
Which of the following is true?
A. The cross-site scripting attempt has succeeded.
B. The SQL injection attempt has succeeded.
C. The parameter tampering has succeeded.
D. The buffer overflow attempt has succeeded.
4. Which of the following uses HTML entities properly to represent <script>?
A. <script>
B. (script)
C. &script&
D. "script"
5. A pen tester is examining a web front end on a target network. The page displays a Search text box form entry, allowing the user to search for items on the site. Instead of entering a search text string, the tester enters the following:
<script> function myFunction() { alert(“It worked!”); } </script>
After the tester clicks the Search button beside the entry box, a pop-up appears stating “It Worked.” Which of the following is true regarding this attempt?
A. The site is vulnerable to XSS.
B. Coding on the site is poor, and a buffer overflow attack may result in a DoS.
C. The attacker’s next entry in the Search box should be ‘ OR ‘1’=’1.
D. This is expected behavior on properly configured sites.
6. Which of the following is used by SOAP services to format information?
A. Unicode
B. HTML entities
C. NTFS
D. XML
7. A security administrator is called for advice. The sales staff has noticed a large number of orders being filled at prices far below those posted on the site. After some research, it does not appear that the web server or the underlying SQL database has been directly compromised. Next, the security administrator reviews the IDS logs and finds nothing unusual. Additionally, the local logs on the server itself do not show anything indicating a problem. Which of the following is the most likely explanation for the false orders?
A. The website uses hidden fields for price values, which have been altered by the attacker.
B. SQL injection has been used to update pricing in the database. After the order was placed, pricing was reset to normal, to cover tracks.
C. Server-side scripting was used to alter the price.
D. A tool such as Metasploit was used to carry out the attack.
8. Which of the following is a common SOA vulnerability?
A. SQL injection
B. XSS
C. XML denial of service
D. CGI manipulation
9. The source code of software used by your client seems to have a large number of gets() alongside sparsely used fgets(). What kind of attack is this software potentially susceptible to?
A. SQL injection
B. Buffer overflow
C. Parameter tampering
D. Cookie manipulation
10. Which code entry will stop input at 100 characters?
A. if (I > 100) then exit (1)
B. if (I >= 100) then exit (1)
C. if (I <= 100) then exit (1)
D. if (I < 100) then exit (1)
11. You are examining log files and come across this URL:
http://www.example.com/script.ext?template%2e%2e%2e%2e%2e%2f%2e%2f%65%74%63%2f%70%61%73%73%77%64
Which of the following best describes this potential attack?
A. This is not an attack but a return of SSL handshakes.
B. An attacker appears to be using Unicode.
C. This appears to be a buffer overflow attempt.
D. This appears to be an XSS attempt.
12. Which of the following tools can be used to clone a copy of a website to your machine, to be scrutinized later?
A. BurpSuite
B. NetCraft
C. HttpRecon
D. BlackWidow
13. Which character is your best option in testing for SQL injection vulnerability?
A. The @ symbol
B. A double dash
C. The + sign
D. A single quote
14. An angry former employee of the organization discovers a web form vulnerable to SQL injection. Using the injection string SELECT * FROM Orders_Pend WHERE Location_City = ‘Orlando’, he is able to see all pending orders from Orlando. If he wanted to delete the Orders_Pend table altogether, which SQL injection string should be used?
A. SELECT * FROM Orders_Pend WHERE Location_City = Orlando’;DROP TABLE Orders_Pend --
B. SELECT * FROM Orders_Pend WHERE ‘Orlando’;DROP_TABLE --
C. DROP TABLE Orders_Pend WHERE ‘Orlando = 1’ --
D. WHERE Location_City = Orlando’1 = 1’: DROP_TABLE --
15. Efforts to gain information from a target website have produced the following error message:
![]()
Which of the following best describes the error message?
A. The site may be vulnerable to XSS.
B. The site may be vulnerable to buffer overflow.
C. The site may be vulnerable to SQL injection.
D. The site may be vulnerable to a malware injection.
16. Which buffer overflow attack is designed to make use of memory that remains in use while a program is running?
A. Stack
B. Heap
C. Active
D. Permanent
17. Which of the following is a standard method for web servers to pass a user’s request to an application and receive data back to forward to the user?
A. SSI
B. SSL
C. CGI
D. CSI
18. An attacker performs a SQL injection attack but receives nothing in return. She then proceeds to send multiple SQL queries, soliciting TRUE or FALSE responses. Which attack is being carried out?
A. Blind SQL injection
B. SQL denial of service
C. SQL code manipulation
D. SQL replay
19. Which of the following can be used for remote password cracking of web servers? (Choose all that apply.)
A. Brutus
B. Nikto
C. THC-Hydra
D. Nessus
20. An attacker is attempting to elevate privileges on a machine by using Java or other functions, through nonvalidated input, to cause the server to execute a malicious piece of code and provide command-line access. Which of the following best describes this action?
A. Shell injection
B. File injection
C. SQL injection
D. URL injection
21. An attacker is successful in replaying a secure cookie, stolen during an XSS attack, even during an invalid session on the server. How is this possible?
A. A cookie can be replayed at any time, no matter the circumstances.
B. Encryption was accomplished at the application layer, using a single key.
C. Authentication was accomplished using XML.
D. Encryption was accomplished at the network layer.
22. HTML forms include several methods for transferring data back and forth. Inside a form, which of the following encodes the input into the Uniform Resource Identifier (URI)?
A. HEAD
B. PUT
C. GET
D. POST
23. An attacker is looking at a target website and is viewing an account from the store on URL http://www.anybiz.com/store.php?id=2. He next enters the following URL:
http://www.anybiz.com/store.php?id=2 and 1=1
The web page loads normally. He then enters the following URL:
http://www.anybiz.com/store.php?id=2 and 1=2
A generic page noting “An error has occurred” appears.
Which of the following is a correct statement concerning these actions?
A. The site is vulnerable to cross-site scripting.
B. The site is vulnerable to blind SQL injection.
C. The site is vulnerable to buffer overflows.
D. The site is not vulnerable to SQL injection.
24. Which of the following is the hexadecimal value of a NOP instruction?
A. 0x60
B. 0x70
C. 0x80
D. 0x90
25. An attacker is viewing a blog entry showing a news story and asking for comments. In the comment field, the attacker enters the following:
![]()
What is the attacker attempting to perform?
A. A SQL injection attack against the blog’s underlying database
B. A cross-site scripting attack
C. A buffer overflow DoS attack
D. A file injection DoS attack
26. An attacker attempts to manipulate an application by advancing the instruction pointer with a long run of instructions containing no action. What is this attack called?
A. File injection
B. Stack flipping
C. NOP-sled
D. Heap based
27. You are examining website files and find the following text file:
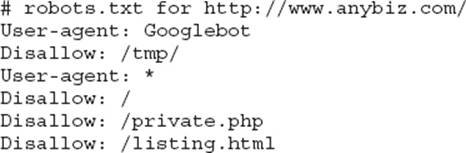
Which of the following is a true statement concerning this file?
A. All web crawlers are prevented from indexing the listing.html page.
B. All web crawlers are prevented from indexing all pages on the site.
C. The Googlebot crawler is allowed to index pages starting with /tmp/.
D. The Googlebot crawler can access and index everything on the site except for pages starting with /tmp/.
![]()
1. B
2. D
3. B
4. A
5. A
6. D
7. A
8. C
9. B
10. B
11. B
12. D
13. D
14. A
15. C
16. B
17. C
18. A
19. A, C
20. A
21. B
22. C
23. B
24. D
25. B
26. C
27. D
1. Which of the following is used to disable file extensions in Apache servers?
A. disable_FS
B. mod_negotiation
C. stop_files
D. httpd.conf
![]() B. mod_negotiation allows you to set items such as disabling file extensions. See, in HTTP, Accept headers are used to specify certain media types that are acceptable for the response. Accept headers can be used to indicate that the request is limited to a specific type of response, such as in a request for an in-line image. mod_negotiation is an Apache module that selects the document, from many available, that best matches the client’s capabilities. If the Accept header on the client side happens to be invalid, the server will respond with a 406 Not Acceptable error containing a pseudodirectory listing. If you’re a bad guy, this can be useful in learning more about the target system (for instance, an attacker might generate a list of base names or a list of interesting extensions or might look for backup files).
B. mod_negotiation allows you to set items such as disabling file extensions. See, in HTTP, Accept headers are used to specify certain media types that are acceptable for the response. Accept headers can be used to indicate that the request is limited to a specific type of response, such as in a request for an in-line image. mod_negotiation is an Apache module that selects the document, from many available, that best matches the client’s capabilities. If the Accept header on the client side happens to be invalid, the server will respond with a 406 Not Acceptable error containing a pseudodirectory listing. If you’re a bad guy, this can be useful in learning more about the target system (for instance, an attacker might generate a list of base names or a list of interesting extensions or might look for backup files).
![]() A and C are incorrect because so far as I know they do not exist.
A and C are incorrect because so far as I know they do not exist.
![]() D is incorrect because httpd.conf is a configuration file used in Apache to control what modules do and do not get loaded.
D is incorrect because httpd.conf is a configuration file used in Apache to control what modules do and do not get loaded.
2. You are examining connection logs from a client machine and come across this entry:
http://www.business123.com/../../../../../Windows/system.ini.
Which attack does this most likely indicate?
A. Parameter manipulation
B. XSS
C. SQL injection
D. Directory traversal
![]() D. Sure, directory traversal is an older attack (working mainly on now-outdated servers), but it’s still worth a shot and, more importantly to you, Dear Reader, it’s going to be on your test. In this attack, the hacker attempts to access restricted directories and execute commands outside intended web server directories. Also known as the dot-dot-slash attack, directory climbing, and backtracking, this attack basically sends HTTP requests asking the server to drop back to the root directory and give access to other folders. Assuming you know the folder directory structure, the location where you want to run commands, and so on, this one is easy enough to pull off.
D. Sure, directory traversal is an older attack (working mainly on now-outdated servers), but it’s still worth a shot and, more importantly to you, Dear Reader, it’s going to be on your test. In this attack, the hacker attempts to access restricted directories and execute commands outside intended web server directories. Also known as the dot-dot-slash attack, directory climbing, and backtracking, this attack basically sends HTTP requests asking the server to drop back to the root directory and give access to other folders. Assuming you know the folder directory structure, the location where you want to run commands, and so on, this one is easy enough to pull off.
![]() A is incorrect because parameter manipulation (also known as parameter tampering) deals with changing portions of the URL string in hopes of modifying data or eliciting a response. An example might be changing the orderID portion of a URL string to see whether you can peruse other users’ information.
A is incorrect because parameter manipulation (also known as parameter tampering) deals with changing portions of the URL string in hopes of modifying data or eliciting a response. An example might be changing the orderID portion of a URL string to see whether you can peruse other users’ information.
![]() B is incorrect because cross-site scripting (XSS) isn’t being discussed in this question. XSS is all about website design and dynamic content, passing client-side scripts into a web page viewed by a different person. In addition to simply bringing a machine down in a good old DoS attack, XSS can also be used to steal users’ cookies, upload malicious code to users connected to the server, and send pop-up messages to users.
B is incorrect because cross-site scripting (XSS) isn’t being discussed in this question. XSS is all about website design and dynamic content, passing client-side scripts into a web page viewed by a different person. In addition to simply bringing a machine down in a good old DoS attack, XSS can also be used to steal users’ cookies, upload malicious code to users connected to the server, and send pop-up messages to users.
![]() C is incorrect because SQL injection is not being performed here. SQL injection involves passing SQL queries through a web front end to manipulate, display, replace, or destroy records in the underlying database.
C is incorrect because SQL injection is not being performed here. SQL injection involves passing SQL queries through a web front end to manipulate, display, replace, or destroy records in the underlying database.
3. A hacker is looking at a publicly facing web front end. One of the pages provides an entry box with the heading “Forgot password? Enter your email address.” In the entry, he types anything’ OR ‘1’=’1.
A message appears stating “Your login information has been sent to a_username@emailaddress.target.com.”
Which of the following is true?
A. The cross-site scripting attempt has succeeded.
B. The SQL injection attempt has succeeded.
C. The parameter tampering has succeeded.
D. The buffer overflow attempt has succeeded.
![]() B. Any time you see ’ or 1=1, I can promise you it’s a SQL injection question. Because the hacker got a response, this site is susceptible to SQL injection. As an aside, it’s just as likely an attempt like this may fail to return an actual record, but if it does, you may wind up getting valuable information anyway in the form of an error message from the underlying SQL database. Remember, with SQL you’re simply trying to pass SQL queries through an entry point never made to take them (at least, not designed or thought of to do so anyway). What’s going on here, as much as we can tell from the question, is a result has been returned from the site from input designed as a SQL query and not the designed user input (username or e-mail address).
B. Any time you see ’ or 1=1, I can promise you it’s a SQL injection question. Because the hacker got a response, this site is susceptible to SQL injection. As an aside, it’s just as likely an attempt like this may fail to return an actual record, but if it does, you may wind up getting valuable information anyway in the form of an error message from the underlying SQL database. Remember, with SQL you’re simply trying to pass SQL queries through an entry point never made to take them (at least, not designed or thought of to do so anyway). What’s going on here, as much as we can tell from the question, is a result has been returned from the site from input designed as a SQL query and not the designed user input (username or e-mail address).
![]() A is incorrect because this is not an XSS attempt. Cross-site scripting would involve something like JavaScript inserting data into the page—usually to manipulate web content.
A is incorrect because this is not an XSS attempt. Cross-site scripting would involve something like JavaScript inserting data into the page—usually to manipulate web content.
![]() C is incorrect because parameter tampering is not in use here. Parameter tampering is inside the URL itself, manipulating parameters to change the response to something you’re looking for (changing order=13752+user=500 to order =13752+user=1 inside the URL, or something like that).
C is incorrect because parameter tampering is not in use here. Parameter tampering is inside the URL itself, manipulating parameters to change the response to something you’re looking for (changing order=13752+user=500 to order =13752+user=1 inside the URL, or something like that).
![]() D is incorrect because buffer overflow is not in play here. Buffer overflow is an attempt to write more data into an application’s prebuilt buffer area in order to overwrite adjacent memory, execute code, or crash a system (application).
D is incorrect because buffer overflow is not in play here. Buffer overflow is an attempt to write more data into an application’s prebuilt buffer area in order to overwrite adjacent memory, execute code, or crash a system (application).
4. Which of the following uses HTML entities properly to represent <script>?
A. <script>
B. (script)
C. &script&
D. "script"
![]() A. Cross-site scripting generally relies on web pages not properly validating user input, and HTML entities can be used to take the place of certain characters. In this case, the less-than sign (<) and the greater-than sign (>) surround the word script. The appropriate HTML entity for each is < and > (the lt and gt should give that one away).
A. Cross-site scripting generally relies on web pages not properly validating user input, and HTML entities can be used to take the place of certain characters. In this case, the less-than sign (<) and the greater-than sign (>) surround the word script. The appropriate HTML entity for each is < and > (the lt and gt should give that one away).
![]() B is incorrect because ( and ) stand for the open and close parentheses, respectively. For example, (hello) would read (hello) using HTML entities.
B is incorrect because ( and ) stand for the open and close parentheses, respectively. For example, (hello) would read (hello) using HTML entities.
![]() C is incorrect because & stands for the ampersand character (&).
C is incorrect because & stands for the ampersand character (&).
![]() D is incorrect because " stands for the quote character (“).
D is incorrect because " stands for the quote character (“).
5. A pen tester is examining a web front end on a target network. The page displays a Search text box form entry, allowing the user to search for items on the site. Instead of entering a search text string, the tester enters the following:
<script> function myFunction() { alert(“It worked!”); } </script>
After the tester clicks the Search button beside the entry box, a pop-up appears stating “It Worked.” Which of the following is true regarding this attempt?
A. The site is vulnerable to XSS.
B. Coding on the site is poor, and a buffer overflow attack may result in a DoS.
C. The attacker’s next entry in the Search box should be ‘ OR ‘1’=’1.
D. This is expected behavior on properly configured sites.
![]() A. This is a somewhat simplistic but undeniably classic example of cross-site scripting. A common cross-site scripting attempt is to insert malicious script into an input field on a site. If the site is not configured properly, it’ll become confused and execute the script instead of erroring out and telling you you’re naughty. By manipulating input fields, you can accomplish all sorts of things, such as redirecting users to an alternate site, stealing cookies or other data from users, and performing a plain-old DoS against the site/server.
A. This is a somewhat simplistic but undeniably classic example of cross-site scripting. A common cross-site scripting attempt is to insert malicious script into an input field on a site. If the site is not configured properly, it’ll become confused and execute the script instead of erroring out and telling you you’re naughty. By manipulating input fields, you can accomplish all sorts of things, such as redirecting users to an alternate site, stealing cookies or other data from users, and performing a plain-old DoS against the site/server.
![]() B is incorrect because although the site is undeniably configured poorly, there is no indication here a buffer overflow will work at all. It might, later, but we just can’t tell from this.
B is incorrect because although the site is undeniably configured poorly, there is no indication here a buffer overflow will work at all. It might, later, but we just can’t tell from this.
![]() C is incorrect because there is no indication here of a SQL injection vulnerability. As before, it may very well be vulnerable, but this question doesn’t provide that information.
C is incorrect because there is no indication here of a SQL injection vulnerability. As before, it may very well be vulnerable, but this question doesn’t provide that information.
![]() D is incorrect because the site is configured poorly to even allow XSS in the first place.
D is incorrect because the site is configured poorly to even allow XSS in the first place.
6. Which of the following is used by SOAP services to format information?
A. Unicode
B. HTML entities
C. NTFS
D. XML
![]() D. Simple Object Access Protocol (SOAP) is a protocol designing for exchanging structured information within web services across multiple variant systems. In other words, it’s a way for a program running in one kind of operating system (let’s say Windows Server 2008) to communicate with a program on another (such as Linux). It uses HTTP and XML to exchange information and specifies how to encode HTTP headers and XML files so that applications can talk to each other. One great advantage to this is also a great detriment, security-wise: Since HTTP is generally allowed through most firewalls, applications using SOAP can generally communicate at will throughout networks. Hmmmm.
D. Simple Object Access Protocol (SOAP) is a protocol designing for exchanging structured information within web services across multiple variant systems. In other words, it’s a way for a program running in one kind of operating system (let’s say Windows Server 2008) to communicate with a program on another (such as Linux). It uses HTTP and XML to exchange information and specifies how to encode HTTP headers and XML files so that applications can talk to each other. One great advantage to this is also a great detriment, security-wise: Since HTTP is generally allowed through most firewalls, applications using SOAP can generally communicate at will throughout networks. Hmmmm.
![]() A is incorrect because Unicode is not used by SOAP in this manner. It’s a standard for representing text in computing.
A is incorrect because Unicode is not used by SOAP in this manner. It’s a standard for representing text in computing.
![]() B is incorrect because HTML entities are not used by SOAP in this manner. They’re used to represent characters in HTML code.
B is incorrect because HTML entities are not used by SOAP in this manner. They’re used to represent characters in HTML code.
![]() C is incorrect because NTFS is a file system and has nothing to do with SOAP.
C is incorrect because NTFS is a file system and has nothing to do with SOAP.
7. A security administrator is called for advice. The sales staff has noticed a large number of orders being filled at prices far below those posted on the site. After some research, it does not appear that the web server or the underlying SQL
database has been directly compromised. Next, the security administrator reviews the IDS logs and finds nothing unusual. Additionally, the local logs on the server itself do not show anything indicating a problem. Which of the following is the most likely explanation for the false orders?
A. The website uses hidden fields for price values, which have been altered by the attacker.
B. SQL injection has been used to update pricing in the database. After the order was placed, pricing was reset to normal, to cover tracks.
C. Server-side scripting was used to alter the price.
D. A tool such as Metasploit was used to carry out the attack.
![]() A. This is actually more common than you might think. No, I’m not advising you to go do your Christmas shopping early—that could get you in serious trouble—I’m just stating an outright fact that many websites simply don’t have their collective stuff together. If you view the source code for a site offering products for sale, many times you can find the pricing secreted away in a “hidden” field (just do a search for “hidden” on the form). If you copy that source to your computer, alter the value in the hidden field, save, and launch the page in the browser, you can order at whatever price you set. The real point is, if anything is moving back and forth between client and server, it can be manipulated.
A. This is actually more common than you might think. No, I’m not advising you to go do your Christmas shopping early—that could get you in serious trouble—I’m just stating an outright fact that many websites simply don’t have their collective stuff together. If you view the source code for a site offering products for sale, many times you can find the pricing secreted away in a “hidden” field (just do a search for “hidden” on the form). If you copy that source to your computer, alter the value in the hidden field, save, and launch the page in the browser, you can order at whatever price you set. The real point is, if anything is moving back and forth between client and server, it can be manipulated.
![]() B and C are both incorrect for the same reason. This level of interaction would most certainly be easy to spot between the IDS and server logs. SQL injection involves passing SQL queries and commands through the interface and would be evident in the logs. Server-side includes (SSIs) are directives placed in HTML pages and evaluated on the server while the pages are being served.
B and C are both incorrect for the same reason. This level of interaction would most certainly be easy to spot between the IDS and server logs. SQL injection involves passing SQL queries and commands through the interface and would be evident in the logs. Server-side includes (SSIs) are directives placed in HTML pages and evaluated on the server while the pages are being served.
![]() D is incorrect because there is simply no evidence any tool has been used here. Of course, this might have been a super-talented, ace hacker who jumped in and out of the site leaving absolutely no crumbs to track him down with, but it’s very unlikely.
D is incorrect because there is simply no evidence any tool has been used here. Of course, this might have been a super-talented, ace hacker who jumped in and out of the site leaving absolutely no crumbs to track him down with, but it’s very unlikely.
8. Which of the following is a common SOA vulnerability?
A. SQL injection
B. XSS
C. XML denial of service
D. CGI manipulation
![]() C. Service-oriented architecture (SOA) is a software design idea that is based on specific pieces of software providing functionality as services between applications. The idea is to define how two applications can interact so that one can perform a piece of work for the other (better said, on behalf of the other). Each interaction is independent of any other and is self-contained. SOA programmers make extensive use of XML to carry all this out, and that leaves it vulnerable to crafty XML tampering. If an attacker can somehow pass an XML message with a large payload, or any of a number of other bad content, they can DoS an SOA application. This isn’t to imply it’s the only DoS available or that SOA is uniquely vulnerable (for instance, the only thing a specifically crafted XML attack can affect): It’s just a question, so don’t read too much into it.
C. Service-oriented architecture (SOA) is a software design idea that is based on specific pieces of software providing functionality as services between applications. The idea is to define how two applications can interact so that one can perform a piece of work for the other (better said, on behalf of the other). Each interaction is independent of any other and is self-contained. SOA programmers make extensive use of XML to carry all this out, and that leaves it vulnerable to crafty XML tampering. If an attacker can somehow pass an XML message with a large payload, or any of a number of other bad content, they can DoS an SOA application. This isn’t to imply it’s the only DoS available or that SOA is uniquely vulnerable (for instance, the only thing a specifically crafted XML attack can affect): It’s just a question, so don’t read too much into it.
![]() A, B, and D are incorrect because these attacks don’t necessarily apply here with SOA in this context.
A, B, and D are incorrect because these attacks don’t necessarily apply here with SOA in this context.
9. The source code of software used by your client seems to have a large number of gets() alongside sparsely used fgets(). What kind of attack is this software potentially susceptible to?
A. SQL injection
B. Buffer overflow
C. Parameter tampering
D. Cookie manipulation
![]() B. A buffer overflow is an attempt to write more data into an application’s prebuilt buffer area in order to overwrite adjacent memory, execute code, or crash a system (application). By inputting more data than the buffer is allocated to hold, you may be able to crash the application or machine or alter the application’s data pointers. gets() is a common source of buffer overflow vulnerabilities because it reads a line from standard input into a buffer until a terminating EOF is found. It performs no check for buffer overrun and is largely replaced by fgets().
B. A buffer overflow is an attempt to write more data into an application’s prebuilt buffer area in order to overwrite adjacent memory, execute code, or crash a system (application). By inputting more data than the buffer is allocated to hold, you may be able to crash the application or machine or alter the application’s data pointers. gets() is a common source of buffer overflow vulnerabilities because it reads a line from standard input into a buffer until a terminating EOF is found. It performs no check for buffer overrun and is largely replaced by fgets().
![]() A is incorrect because SQL injection has nothing to do with this scenario. No evidence is presented that this software even interacts with a database.
A is incorrect because SQL injection has nothing to do with this scenario. No evidence is presented that this software even interacts with a database.
![]() C is incorrect because parameter tampering deals with manipulating a URL.
C is incorrect because parameter tampering deals with manipulating a URL.
![]() D is incorrect because cookie manipulation has nothing to do with this software. As covered earlier, a cookie is a small file used to provide a more consistent web experience for a web visitor. Because it holds all sorts of information, though, it can be manipulated for nefarious purposes (using the Firefox add-on Cookie Editor, for instance).
D is incorrect because cookie manipulation has nothing to do with this software. As covered earlier, a cookie is a small file used to provide a more consistent web experience for a web visitor. Because it holds all sorts of information, though, it can be manipulated for nefarious purposes (using the Firefox add-on Cookie Editor, for instance).
10. Which code entry will stop input at 100 characters?
A. if (I > 100) then exit (1)
B. if (I >= 100) then exit (1)
C. if (I <= 100) then exit (1)
D. if (I < 100) then exit (1)
![]() B. There won’t be very many pure coding type questions on the exam, and when they do appear, they’re pretty clear cut. Because 0 (zero) is used in counting in computer programming code (many indeed start at 1, like FORTRAN, COBOL, and LUA, but the examples in your exam don’t), any value from 0 to 99 would suffice. Thus, an entry of 100 would represent the 101st character. Therefore, you can accept anything less than 100 as a character count: “I” must be less than 100 to be accepted, and if it’s 100 or above, exit and quit. So, if the character value count is equal to 100, or greater, exit the program (I >= 100).
B. There won’t be very many pure coding type questions on the exam, and when they do appear, they’re pretty clear cut. Because 0 (zero) is used in counting in computer programming code (many indeed start at 1, like FORTRAN, COBOL, and LUA, but the examples in your exam don’t), any value from 0 to 99 would suffice. Thus, an entry of 100 would represent the 101st character. Therefore, you can accept anything less than 100 as a character count: “I” must be less than 100 to be accepted, and if it’s 100 or above, exit and quit. So, if the character value count is equal to 100, or greater, exit the program (I >= 100).
![]() A, C, and D are all incorrect expressions. (I > 100) indicates any entry greater than 100, which does work; however, it leaves the extra 101st entry (that is, 100) as acceptable. (I < 100) would exit on any character entry less than 100 (meaning the only acceptable entries would be 101 characters or more—the exact opposite of what we’re trying to accomplish). Finally, (I <= 100) is just as bad, for obvious reasons.
A, C, and D are all incorrect expressions. (I > 100) indicates any entry greater than 100, which does work; however, it leaves the extra 101st entry (that is, 100) as acceptable. (I < 100) would exit on any character entry less than 100 (meaning the only acceptable entries would be 101 characters or more—the exact opposite of what we’re trying to accomplish). Finally, (I <= 100) is just as bad, for obvious reasons.
11. You are examining log files and come across this URL:
http://www.example.com/script.ext?template%2e%2e%2e%2e%2e%2f%2e%2f%65%74%63%2f%70%61%73%73%77%64
Which of the following best describes this potential attack?
A. This is not an attack but a return of SSL handshakes.
B. An attacker appears to be using Unicode.
C. This appears to be a buffer overflow attempt.
D. This appears to be an XSS attempt.
![]() B. Unicode is just another way to represent text, so why not use it to try to get past an IDS? Of course, in the real world every IDS would probably be looking for weird Unicode requests anyway (it isn’t ciphered or encrypted and really does nothing more than provide a cursory obfuscation), but let’s just stick with EC-Council and the CEH exam here for now. This request appears to be attempting a grab of some passwords:
B. Unicode is just another way to represent text, so why not use it to try to get past an IDS? Of course, in the real world every IDS would probably be looking for weird Unicode requests anyway (it isn’t ciphered or encrypted and really does nothing more than provide a cursory obfuscation), but let’s just stick with EC-Council and the CEH exam here for now. This request appears to be attempting a grab of some passwords:
%2e%2e%2f%2e%2e%2f%2e%2f% = ../../../
%65%74%63 = etc
%2f = /
%70%61%73%73%77%64 = passwd
![]() A, C, and D are all incorrect because this URL does not necessarily indicate any of these attacks and is quite clearly a Unicode attempt.
A, C, and D are all incorrect because this URL does not necessarily indicate any of these attacks and is quite clearly a Unicode attempt.
12. Which of the following tools can be used to clone a copy of a website to your machine, to be scrutinized later?
A. BurpSuite
B. NetCraft
C. HttpRecon
D. BlackWidow
![]() D. BlackWidow is an easy-to-use application that can perform all sorts of things—mainly, to this question, downloading a clone of a website for scanning and vulnerability discovery at your leisure. The following is from the developer’s website (sbl.net): “Black Widow is a state-of-the-art website scanner for both experts and beginners. It can download an entire website, or download portions of a site, and can build a site structure first, then download later; you select what to download. The integrated scripting engine is an easy to learn and use programing language to facilitate scanning ‘hard to scan’ sites. It allows you to control the scan by trapping the scanner event so you can process the request yourself.” Of course, there are plenty of other ways to do this—wget comes to mind as one—but, as I mentioned before, EC-Council will test specific tools on your exam, and this is an example.
D. BlackWidow is an easy-to-use application that can perform all sorts of things—mainly, to this question, downloading a clone of a website for scanning and vulnerability discovery at your leisure. The following is from the developer’s website (sbl.net): “Black Widow is a state-of-the-art website scanner for both experts and beginners. It can download an entire website, or download portions of a site, and can build a site structure first, then download later; you select what to download. The integrated scripting engine is an easy to learn and use programing language to facilitate scanning ‘hard to scan’ sites. It allows you to control the scan by trapping the scanner event so you can process the request yourself.” Of course, there are plenty of other ways to do this—wget comes to mind as one—but, as I mentioned before, EC-Council will test specific tools on your exam, and this is an example.
![]() A is incorrect because BurpSuite isn’t designed to pull an entire copy of a website externally and run through tests. The following is from the website (www.portswigger.net/burp/): “BurpSuite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.”
A is incorrect because BurpSuite isn’t designed to pull an entire copy of a website externally and run through tests. The following is from the website (www.portswigger.net/burp/): “BurpSuite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.”
![]() B is incorrect because NetCraft isn’t a tool to be used for this purpose. NetCraft is actually a security corporation in England that provides all sorts of security tools aimed at the web sector. It’s currently well known for its anti-phishing toolbar, which was hailed by Microsoft as being “among the most effective tools to combat phishing on the Internet.” This probably explains why Microsoft purchased licensing for NetCraft and added that functionality in Internet Explorer 7 as Microsoft Phishing Filter (also known as SmartScreen Filter in IE8).
B is incorrect because NetCraft isn’t a tool to be used for this purpose. NetCraft is actually a security corporation in England that provides all sorts of security tools aimed at the web sector. It’s currently well known for its anti-phishing toolbar, which was hailed by Microsoft as being “among the most effective tools to combat phishing on the Internet.” This probably explains why Microsoft purchased licensing for NetCraft and added that functionality in Internet Explorer 7 as Microsoft Phishing Filter (also known as SmartScreen Filter in IE8).
![]() C is incorrect because HttpRecon isn’t used in this manner. HttpRecon is known as a web server fingerprinting tool, providing “highly accurate identification of given httpd implementations” (www.computec.ch/projekte/httprecon/). HttpRecon uses traditional approaches, such as banner-grabbing, status code enumeration, and header ordering analysis, but also adds other analytical techniques to increase accuracy.
C is incorrect because HttpRecon isn’t used in this manner. HttpRecon is known as a web server fingerprinting tool, providing “highly accurate identification of given httpd implementations” (www.computec.ch/projekte/httprecon/). HttpRecon uses traditional approaches, such as banner-grabbing, status code enumeration, and header ordering analysis, but also adds other analytical techniques to increase accuracy.
13. Which character is your best option in testing for SQL injection vulnerability?
A. The @ symbol
B. A double dash
C. The + sign
D. A single quote
![]() D. SQL injection is all about entering queries and commands into a form field (or URL) to elicit a response, gain information, or manipulate data. On a web page, many times entries into a form field are inserted into a SQL command: When you enter your username and information into the fields and click the button, the SQL command in the background might read something like this:
D. SQL injection is all about entering queries and commands into a form field (or URL) to elicit a response, gain information, or manipulate data. On a web page, many times entries into a form field are inserted into a SQL command: When you enter your username and information into the fields and click the button, the SQL command in the background might read something like this:
![]()
In SQL, a single quote is used to indicate an upcoming character string. Once SQL sees that open quote, it starts parsing everything behind it as string input. If there’s no close quote, an error occurs because SQL doesn’t know what to do with it. If the web page is configured poorly, that error will return to you and let you know it’s time to start injecting SQL commands.
![]() A, B, and C are incorrect characters to use as part of a SQL injection test. The @ symbol is used to designate a variable in SQL (you’ll need to define the variable, of course). The + sign is used to combine strings (as in Matt+Walker). A double dash indicates an upcoming comment in the line.
A, B, and C are incorrect characters to use as part of a SQL injection test. The @ symbol is used to designate a variable in SQL (you’ll need to define the variable, of course). The + sign is used to combine strings (as in Matt+Walker). A double dash indicates an upcoming comment in the line.
14. An angry former employee of the organization discovers a web form vulnerable to SQL injection. Using the injection string SELECT * FROM Orders_Pend WHERE Location_City = ‘Orlando’, he is able to see all pending orders from Orlando. If he wanted to delete the Orders_Pend table altogether, which SQL injection string should be used?
A. SELECT * FROM Orders_Pend WHERE Location_City = ‘Orlando’;DROP TABLE Orders_Pend --
B. SELECT * FROM Orders_Pend WHERE ‘Orlando’;DROP_TABLE --
C. DROP TABLE Orders_Pend WHERE ‘Orlando = 1’ --
D. WHERE Location_City = Orlando’1 = 1’: DROP_TABLE --
![]() A. SQL queries usually read pretty straightforward, although they can get complicated pretty quickly. In this case you’re telling the database, “Can you check the table Orders_Pend and see whether there’s a city called Orlando? Oh, by the way, since you’re executing any command I send anyway, just go ahead and drop the table called Orders_Pend while you’re at it.” The only thing missing from SQL queries is a thank-you at the end.
A. SQL queries usually read pretty straightforward, although they can get complicated pretty quickly. In this case you’re telling the database, “Can you check the table Orders_Pend and see whether there’s a city called Orlando? Oh, by the way, since you’re executing any command I send anyway, just go ahead and drop the table called Orders_Pend while you’re at it.” The only thing missing from SQL queries is a thank-you at the end.
![]() B, C, and D are incorrect because these are not proper syntax.
B, C, and D are incorrect because these are not proper syntax.
15. Efforts to gain information from a target website have produced the following error message:
![]()
Which of the following best describes the error message?
A. The site may be vulnerable to XSS.
B. The site may be vulnerable to buffer overflow.
C. The site may be vulnerable to SQL injection.
D. The site may be vulnerable to a malware injection.
![]() C. Once again, you will get a few “gimme” questions on the exam. The error message clearly displays a SQL error, telling us there’s an underlying SQL database to contend with and it’s most likely not configured correctly (or we wouldn’t be getting an error message like this—through a web interface and telling us exactly what’s there—in the first place).
C. Once again, you will get a few “gimme” questions on the exam. The error message clearly displays a SQL error, telling us there’s an underlying SQL database to contend with and it’s most likely not configured correctly (or we wouldn’t be getting an error message like this—through a web interface and telling us exactly what’s there—in the first place).
![]() A, B, and D are all incorrect for the same reason: The error message simply doesn’t provide enough information to make those leaps. There is nothing here indicating cross-site scripting or buffer overflow on either side of the ledger. Although it’s true the error may indicate which kinds of malware may increase your odds of success, there’s nothing there to indicate, by itself, that the site is vulnerable.
A, B, and D are all incorrect for the same reason: The error message simply doesn’t provide enough information to make those leaps. There is nothing here indicating cross-site scripting or buffer overflow on either side of the ledger. Although it’s true the error may indicate which kinds of malware may increase your odds of success, there’s nothing there to indicate, by itself, that the site is vulnerable.
16. Which buffer overflow attack is designed to make use of memory that remains in use while a program is running?
A. Stack
B. Heap
C. Active
D. Permanent
![]() B. Granted, this is a little bit of a picky question, but you’ll definitely see something like this on your exam. Buffer overflows are all about the same thing: inputting more information into a buffer area that was designed for one action in order to write code to a different area of memory so it can be executed. At best, the code will execute, and you can do all sorts of good things. At worse, the program will reject the code and crash. A heap buffer attack takes advantage of the memory space set aside for the program itself. Heap is the memory area immediately “on top” of the program and is not temporary (it’s supposed to remain in use as long as the application is running). Pages in the heap can be read from and written to, which is what the attacker will be trying to exploit.
B. Granted, this is a little bit of a picky question, but you’ll definitely see something like this on your exam. Buffer overflows are all about the same thing: inputting more information into a buffer area that was designed for one action in order to write code to a different area of memory so it can be executed. At best, the code will execute, and you can do all sorts of good things. At worse, the program will reject the code and crash. A heap buffer attack takes advantage of the memory space set aside for the program itself. Heap is the memory area immediately “on top” of the program and is not temporary (it’s supposed to remain in use as long as the application is running). Pages in the heap can be read from and written to, which is what the attacker will be trying to exploit.
![]() A is incorrect only because of the actual buffer area being exploited. Whereas heap is memory set aside in the application and is not “temporary,” the stack is designed that way: Each task is added on top of the previous tasks and is executed in order. Overflow the buffer, and you can affect which area executes.
A is incorrect only because of the actual buffer area being exploited. Whereas heap is memory set aside in the application and is not “temporary,” the stack is designed that way: Each task is added on top of the previous tasks and is executed in order. Overflow the buffer, and you can affect which area executes.
![]() C and D are incorrect because neither is a buffer overflow attack type. These are added as distractors.
C and D are incorrect because neither is a buffer overflow attack type. These are added as distractors.
17. Which of the following is a standard method for web servers to pass a user’s request to an application and receive data back to forward to the user?
A. SSI
B. SSL
C. CGI
D. CSI
![]() C. Common Gateway Interface (CGI) is a standardized method for transferring information between a web server and an executable (a CGI script is designed to perform some task with the data). CGI is considered a server-side solution because processing is done on the web server and not the client. Because CGI scripts can run essentially arbitrary commands on your system with the permissions of the web server user and because they are almost always wrapped so that a script will execute as the owner of the script, they can be extremely dangerous if not carefully checked. Additionally, all CGI scripts on the server will run as the same user, so they have the potential to conflict (accidentally or deliberately) with other scripts (an attacker could, for example, write a CGI script to destroy all other CGI databases).
C. Common Gateway Interface (CGI) is a standardized method for transferring information between a web server and an executable (a CGI script is designed to perform some task with the data). CGI is considered a server-side solution because processing is done on the web server and not the client. Because CGI scripts can run essentially arbitrary commands on your system with the permissions of the web server user and because they are almost always wrapped so that a script will execute as the owner of the script, they can be extremely dangerous if not carefully checked. Additionally, all CGI scripts on the server will run as the same user, so they have the potential to conflict (accidentally or deliberately) with other scripts (an attacker could, for example, write a CGI script to destroy all other CGI databases).
![]() A is incorrect because server-side includes (SSIs) are directives placed in HTML pages and evaluated on the server while the pages are being served. They let you add dynamically generated content to an existing HTML page, without having to serve the entire page via a CGI program or other dynamic technology.
A is incorrect because server-side includes (SSIs) are directives placed in HTML pages and evaluated on the server while the pages are being served. They let you add dynamically generated content to an existing HTML page, without having to serve the entire page via a CGI program or other dynamic technology.
![]() B and D are incorrect because both are included as distractors. By now you’re certainly familiar with Secure Sockets Layer (SSL) and its value as an encryption method. CSI? Well, that’s just good television. Or it used to be, anyway.
B and D are incorrect because both are included as distractors. By now you’re certainly familiar with Secure Sockets Layer (SSL) and its value as an encryption method. CSI? Well, that’s just good television. Or it used to be, anyway.
18. An attacker performs a SQL injection attack but receives nothing in return. She then proceeds to send multiple SQL queries, soliciting TRUE or FALSE responses. Which attack is being carried out?
A. Blind SQL injection
B. SQL denial of service
C. SQL code manipulation
D. SQL replay
![]() A. Blind SQL injection is really kinda neat, even if you’re not a nerd. Sometimes a security admin does just enough to frustrate efforts, and you don’t receive the error messages or returned information you originally counted on. So, to pull out the info you want, you start asking it (the SQL database) a lot of true and false questions. For example, you could ask the database, “True or false—you have a table called USERS?” If you get a TRUE, then you know the table name and can start asking questions about it. For example, “Hey, database, got an entry in your USERS table named admin?” (SELECT * from USERS where name=’admin’ and 1=1;#’;). Blind SQL is a long, laborious effort, but it can be done.
A. Blind SQL injection is really kinda neat, even if you’re not a nerd. Sometimes a security admin does just enough to frustrate efforts, and you don’t receive the error messages or returned information you originally counted on. So, to pull out the info you want, you start asking it (the SQL database) a lot of true and false questions. For example, you could ask the database, “True or false—you have a table called USERS?” If you get a TRUE, then you know the table name and can start asking questions about it. For example, “Hey, database, got an entry in your USERS table named admin?” (SELECT * from USERS where name=’admin’ and 1=1;#’;). Blind SQL is a long, laborious effort, but it can be done.
![]() B, C, and D are all incorrect because, so far as I know, none of them is a recognized attack by EC-Council. I’m sure you can find ways to perform a DoS on a SQL database, and we’re manipulating SQL all over the place in these injection attacks, but these terms just aren’t recognized on your exam and are here solely as distractors.
B, C, and D are all incorrect because, so far as I know, none of them is a recognized attack by EC-Council. I’m sure you can find ways to perform a DoS on a SQL database, and we’re manipulating SQL all over the place in these injection attacks, but these terms just aren’t recognized on your exam and are here solely as distractors.
19. Which of the following can be used for remote password cracking of web servers? (Choose all that apply.)
A. Brutus
B. Nikto
C. THC-Hydra
D. Nessus
![]() A and C. Brutus is a fast, flexible remote password cracker. According to the tool’s website (www.hoobie.net/brutus/), it was originally invented to help its creator check routers and network devices for default and common passwords. It has since grown and evolved to much more and is among the more popular security tools available for remote password cracking. THC-Hydra (www.thc.org/thc-hydra/) is another remote password cracker. It’s a “parallelized login cracker” that provides the ability to attack over multiple protocols.
A and C. Brutus is a fast, flexible remote password cracker. According to the tool’s website (www.hoobie.net/brutus/), it was originally invented to help its creator check routers and network devices for default and common passwords. It has since grown and evolved to much more and is among the more popular security tools available for remote password cracking. THC-Hydra (www.thc.org/thc-hydra/) is another remote password cracker. It’s a “parallelized login cracker” that provides the ability to attack over multiple protocols.
![]() B is incorrect because Nikto is not a remote password cracker. It’s an open source web-server-centric vulnerability scanner that performs comprehensive tests against web servers for multiple items.
B is incorrect because Nikto is not a remote password cracker. It’s an open source web-server-centric vulnerability scanner that performs comprehensive tests against web servers for multiple items.
![]() D is incorrect because Nessus is not a remote password cracker; it’s a vulnerability assessment tool.
D is incorrect because Nessus is not a remote password cracker; it’s a vulnerability assessment tool.
20. An attacker is attempting to elevate privileges on a machine by using Java or other functions, through nonvalidated input, to cause the server to execute a malicious piece of code and provide command-line access. Which of the following best describes this action?
A. Shell injection
B. File injection
C. SQL injection
D. URL injection
![]() A. When it comes to web application attacks, there are many vectors and avenues to take. One of the more common is injecting something into an input string to exploit poor code. EC-Council defines these attacks in many ways. Also known as command injection, shell injection is defined as an attempt to gain shell access using Java or other functions. In short, the attacker will pass commands through a form input (or other avenue) in order to elevate privileges and open a shell for further naughtiness. It occurs when commands are entered into form fields instead of the expected entry.
A. When it comes to web application attacks, there are many vectors and avenues to take. One of the more common is injecting something into an input string to exploit poor code. EC-Council defines these attacks in many ways. Also known as command injection, shell injection is defined as an attempt to gain shell access using Java or other functions. In short, the attacker will pass commands through a form input (or other avenue) in order to elevate privileges and open a shell for further naughtiness. It occurs when commands are entered into form fields instead of the expected entry.
![]() B is incorrect because the EC-Council defines a file injection attack as one where the attacker injects a pointer in the web form input to an exploit hosted on a remote site. Sure, this may accomplish the same thing, but it’s not the best choice in this case.
B is incorrect because the EC-Council defines a file injection attack as one where the attacker injects a pointer in the web form input to an exploit hosted on a remote site. Sure, this may accomplish the same thing, but it’s not the best choice in this case.
![]() C is incorrect because SQL injection attacks involve using SQL queries and commands to elicit a response or action.
C is incorrect because SQL injection attacks involve using SQL queries and commands to elicit a response or action.
![]() D is incorrect because URL injection is not an attack type and is included here as a distractor.
D is incorrect because URL injection is not an attack type and is included here as a distractor.
21. An attacker is successful in replaying a secure cookie, stolen during an XSS attack, during an invalid session on the server by forcing a web application to act on the cookie’s contents. How is this possible?
A. A cookie can be replayed at any time, no matter the circumstances.
B. Encryption was accomplished using a single key.
C. Authentication was accomplished using XML.
D. Encryption was accomplished at the network layer.
![]() B. Cookies can be used for all sorts of things, and in this scenario it’s being replayed by an attacker to gain access to goodies. If a single key is used in encryption, a replay attack is possible, and cookie authentication is carried out at the application layer.
B. Cookies can be used for all sorts of things, and in this scenario it’s being replayed by an attacker to gain access to goodies. If a single key is used in encryption, a replay attack is possible, and cookie authentication is carried out at the application layer.
![]() A is incorrect because a replay attack of anything—cookie, stolen authentication stream, and so on—can’t necessarily be carried out at any time. Replay attacks require planning and proper setup.
A is incorrect because a replay attack of anything—cookie, stolen authentication stream, and so on—can’t necessarily be carried out at any time. Replay attacks require planning and proper setup.
![]() C is incorrect because XML has nothing to do with this.
C is incorrect because XML has nothing to do with this.
![]() D is incorrect because encryption is not carried out at the network layer here.
D is incorrect because encryption is not carried out at the network layer here.
22. HTML forms include several methods for transferring data back and forth. Inside a form, which of the following encodes the input into the Uniform Resource Identifier (URI)?
A. HEAD
B. PUT
C. GET
D. POST
![]() C. An HTTP GET is a method for returning data from a form that “encodes” the form data to the end of the URI (a character string that identifies a resource on the Web, such as a page of text, a video clip, an image, or an application). For example, if you were to enter a credit card number in a form using GET, the resulting URL might look something like https://somesite.com/creditcard.asp?c#=4013229567852219, where the long number is obviously a credit card number just sitting there waiting for anyone to use.
C. An HTTP GET is a method for returning data from a form that “encodes” the form data to the end of the URI (a character string that identifies a resource on the Web, such as a page of text, a video clip, an image, or an application). For example, if you were to enter a credit card number in a form using GET, the resulting URL might look something like https://somesite.com/creditcard.asp?c#=4013229567852219, where the long number is obviously a credit card number just sitting there waiting for anyone to use.
Generally speaking, a POST is “more secure” than a GET, although they both have their uses. If you’re wondering when a GET should be used as opposed to a POST, the answer has to do with a vocabulary lesson: defining the term idempotent. Thrown about with HTTP GET, idempotent is a mathematical concept about an operation property: If the operation can be performed without changing results, even if it is run multiple times, it’s considered idempotent. So, if the input return is assured of having no lasting effect on the state of the form in total, then using a GET is perfectly reasonable. Also, a GET can usually transfer only up to 8KB, whereas a POST can usually handle up to 2GB. However, keep in mind it may wind up including sensitive information in that URI. Suppose your form returns a credit card number and a bad guy is logging URIs: If HTTP GET is in place, the attacker may be able to derive the information. In short, users can manipulate both GET and POST, but GET is simply more visible because of its reliance on something that browsers render to the screen in an editable field. A POST is meant for pushing data directly, and a GET is used when the server is expected to pull something from the data submitted in the URL.
![]() A is incorrect because although HEAD and GET are similar, HEAD is not used in forms. It’s usually used to pull header information from a web server (remember your banner grabbing from earlier?) and to test links.
A is incorrect because although HEAD and GET are similar, HEAD is not used in forms. It’s usually used to pull header information from a web server (remember your banner grabbing from earlier?) and to test links.
![]() B is incorrect because HTTP PUT is not used in forms. It’s used to transfer files to a web server.
B is incorrect because HTTP PUT is not used in forms. It’s used to transfer files to a web server.
![]() D is incorrect because POST does not include the form data in the URI request. According to the World Wide Web Consortium (www.w3.org/), HTML specifications define the difference between GET and POST so that GET means that form data will be encoded by a browser into a URL, whereas POST means the form data is to appear within the message body. In short, a GET can be used for basic, simple retrieval of data, and a POST should be used for most everything else (such as sending an e-mail, updating data on a database, and ordering an item).
D is incorrect because POST does not include the form data in the URI request. According to the World Wide Web Consortium (www.w3.org/), HTML specifications define the difference between GET and POST so that GET means that form data will be encoded by a browser into a URL, whereas POST means the form data is to appear within the message body. In short, a GET can be used for basic, simple retrieval of data, and a POST should be used for most everything else (such as sending an e-mail, updating data on a database, and ordering an item).
23. An attacker is looking at a target website and is viewing an account from the store on URL http://www.anybiz.com/store.php?id=2. He next enters the following URL:
http://www.anybiz.com/store.php?id=2 and 1=1
The web page loads normally. He then enters the following URL:
http://www.anybiz.com/store.php?id=2 and 1=2
A generic page noting “An error has occurred” appears.
Which of the following is a correct statement concerning these actions?
A. The site is vulnerable to cross-site scripting.
B. The site is vulnerable to blind SQL injection.
C. The site is vulnerable to buffer overflows.
D. The site is not vulnerable to SQL injection.
![]() B. The URLs shown here are attempting to pass a SQL query through to see what may be going on in the background. Notice the first URL entered added and 1=1. Because this was a true statement, the page loaded without problem. However, changing that to a false statement—and 1=2—caused the database to return an error. This would now be considered “blind” SQL injection because the actual error was not returned to the attacker (instead, he got a generic page most likely configured by the database administrator). As an aside, sometimes the attacker won’t receive the error message or error page at all, but the site will be displayed differently—images out of place, text messed up, and so on—which also indicates blind SQL may be in order.
B. The URLs shown here are attempting to pass a SQL query through to see what may be going on in the background. Notice the first URL entered added and 1=1. Because this was a true statement, the page loaded without problem. However, changing that to a false statement—and 1=2—caused the database to return an error. This would now be considered “blind” SQL injection because the actual error was not returned to the attacker (instead, he got a generic page most likely configured by the database administrator). As an aside, sometimes the attacker won’t receive the error message or error page at all, but the site will be displayed differently—images out of place, text messed up, and so on—which also indicates blind SQL may be in order.
![]() A and C are incorrect because neither this attack nor the results have anything to do with cross-site scripting or buffer overflows.
A and C are incorrect because neither this attack nor the results have anything to do with cross-site scripting or buffer overflows.
![]() D is incorrect because the results indicate SQL injection is possible. Granted, it will take longer, because we can’t see error messaging, and will require lots of guesswork and trial and error, but it is susceptible.
D is incorrect because the results indicate SQL injection is possible. Granted, it will take longer, because we can’t see error messaging, and will require lots of guesswork and trial and error, but it is susceptible.
24. Which of the following is the hexadecimal value of a NOP instruction?
A. 0×60
B. 0×70
C. 0×80
D. 0×90
![]() D. EC-Council just adores the NOP instruction. The no-operation instruction effectively does nothing at all: It’s used to take up a few cycles doing absolutely nothing for the purpose of timing and lining up clock cycles. Bad guys can use it in scripting, though, to create a so-called NOP-sled, which slides the CPU instruction to a specific memory point (or just the end of the script). If you were to see something with a ton of 0x90 instructions in it, it may very well be a NOP-sled attempt.
D. EC-Council just adores the NOP instruction. The no-operation instruction effectively does nothing at all: It’s used to take up a few cycles doing absolutely nothing for the purpose of timing and lining up clock cycles. Bad guys can use it in scripting, though, to create a so-called NOP-sled, which slides the CPU instruction to a specific memory point (or just the end of the script). If you were to see something with a ton of 0x90 instructions in it, it may very well be a NOP-sled attempt.
![]() A, B, and C are incorrect because they do not represent the hex value of a NOP instruction.
A, B, and C are incorrect because they do not represent the hex value of a NOP instruction.
25. An attacker is viewing a blog entry showing a news story and asking for comments. In the comment field, the attacker enters the following:
![]()
What is the attacker attempting to perform?
A. A SQL injection attack against the blog’s underlying database
B. A cross-site scripting attack
C. A buffer overflow DoS attack
D. A file injection DoS attack
![]() B. This is a classic (an overly simplified but classic nonetheless) example of cross-site scripting. In a blog, the post entry field is intended to take text entry from a visitor and copy it to a database in the background. What’s being attempted here is to have more than just the text copied—the <script> indicator is adding a nice little pointer to a naughty website. If it works, the next visitor to the site who clicks that news story will be redirected to the bad site location.
B. This is a classic (an overly simplified but classic nonetheless) example of cross-site scripting. In a blog, the post entry field is intended to take text entry from a visitor and copy it to a database in the background. What’s being attempted here is to have more than just the text copied—the <script> indicator is adding a nice little pointer to a naughty website. If it works, the next visitor to the site who clicks that news story will be redirected to the bad site location.
![]() A, C, and D are all incorrect because this example contains nothing to indicate a SQL injection or a buffer overflow. Additionally, the idea here is not to perform a denial of service. Actually, it’s quite the opposite: The attacker wants the site up and operational so more and more users can be sent to badsite.com.
A, C, and D are all incorrect because this example contains nothing to indicate a SQL injection or a buffer overflow. Additionally, the idea here is not to perform a denial of service. Actually, it’s quite the opposite: The attacker wants the site up and operational so more and more users can be sent to badsite.com.
26. An attacker attempts to manipulate an application by advancing the instruction pointer with a long run of instructions containing no action. What is this attack called?
A. File injection
B. Stack flipping
C. NOP-sled
D. Heap based
![]() C. Computer languages usually contain a command most CPUs will recognize as “do nothing.” This no-operation (NOP) instruction serves to advance an instruction pointer to a known memory area. The idea behind it is to provide time for unknown activities to occur until it’s time to execute the main code (avoiding an exception code and a halt to the system or application). For a ridiculously over-simplified example, if you were “coding” a human’s morning routine and wanted them to brush their teeth, you might provide a whole bunch of “do nothings” in front and behind the “pick up toothbrush, put toothpaste on brush, and so on” steps—to provide space for things you may not be aware of.
C. Computer languages usually contain a command most CPUs will recognize as “do nothing.” This no-operation (NOP) instruction serves to advance an instruction pointer to a known memory area. The idea behind it is to provide time for unknown activities to occur until it’s time to execute the main code (avoiding an exception code and a halt to the system or application). For a ridiculously over-simplified example, if you were “coding” a human’s morning routine and wanted them to brush their teeth, you might provide a whole bunch of “do nothings” in front and behind the “pick up toothbrush, put toothpaste on brush, and so on” steps—to provide space for things you may not be aware of.
When it comes to attacks, hackers will send tons of NOP instructions in an effort to move the pointer to an area they control—and to execute the naughty payload there. This NOP-sled is relatively easy to see in action, and all IDSs will pick it up.
![]() A is incorrect because file injection occurs when the attacker injects a pointer in a web form input to an exploit hosted on a remote site. There is no file injection occurring in this example.
A is incorrect because file injection occurs when the attacker injects a pointer in a web form input to an exploit hosted on a remote site. There is no file injection occurring in this example.
![]() B is incorrect because the term stack flipping is not a recognized term on the CEH exam and is included here as a distractor.
B is incorrect because the term stack flipping is not a recognized term on the CEH exam and is included here as a distractor.
![]() D is incorrect because a heap-based buffer overflow deals with a buffer overflow specifically aimed at the lower part of the heap, to overwrite dynamic content there.
D is incorrect because a heap-based buffer overflow deals with a buffer overflow specifically aimed at the lower part of the heap, to overwrite dynamic content there.
27. You are examining website files and find the following text file:
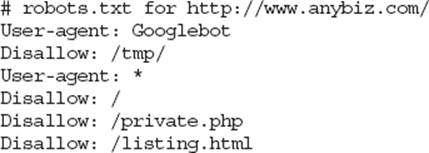
Which of the following is a true statement concerning this file?
A. All web crawlers are prevented from indexing the listing.html page.
B. All web crawlers are prevented from indexing all pages on the site.
C. The Googlebot crawler is allowed to index pages starting with /tmp/.
D. The Googlebot crawler can access and index everything on the site except for pages starting with /tmp/.
![]() D. The robots.txt file was created to allow web designers to control index access to their sites. There are a couple of things you need to know about this file—for your exam and the real world. The first is, no matter what the robots.txt file says, attackers using a crawler to index your site are going to ignore it anyway: It’s valid only for “good-guy” crawlers. After that, the rest is easy: robots.txt is stored on the root, is available to anyone (by design), and is read in order from top to bottom, much like an ACL on a router. The format is simple: Define the crawler (User-agent :name_of_crawler) and then define what it does not have access to. Most robot.txt files will make use of the * variable to signify all crawlers, but you can certainly get specific with who is allowed in and what they can see.
D. The robots.txt file was created to allow web designers to control index access to their sites. There are a couple of things you need to know about this file—for your exam and the real world. The first is, no matter what the robots.txt file says, attackers using a crawler to index your site are going to ignore it anyway: It’s valid only for “good-guy” crawlers. After that, the rest is easy: robots.txt is stored on the root, is available to anyone (by design), and is read in order from top to bottom, much like an ACL on a router. The format is simple: Define the crawler (User-agent :name_of_crawler) and then define what it does not have access to. Most robot.txt files will make use of the * variable to signify all crawlers, but you can certainly get specific with who is allowed in and what they can see.
In this example, from top to bottom, the Googlebot crawler is defined and restricted from seeing /tmp/ pages—no other restrictions are listed. After that, all other crawlers (User-agent: *) are restricted from seeing any page (Disallow: /). The last two lines are truly irrelevant because the condition to ignore all pages has been read.
For additional information here, if you think about what a robots.txt file does, you could consider it a pointer to pages you, as an attacker, really want to see. After all, if the security person on the site didn’t want Google indexing it, useful information probably resides there. On the flip side, a security-minded person may get a little snippy with it and have a little fun, sending you to some truly terrible Internet locations should you try to access one of the pages listed there.
![]() A and B are incorrect because the Googlebot crawler is allowed to crawl the site.
A and B are incorrect because the Googlebot crawler is allowed to crawl the site.
![]() C is incorrect because Googlebot is instructed to ignore all /tmp/ pages.
C is incorrect because Googlebot is instructed to ignore all /tmp/ pages.