CEH Certified Ethical Hacker Practice Exams Second Edition (2014)
Cryptography 101
This domain includes questions from the following topics:
• Identify fundamentals of cryptography and encryption techniques
• Learn about cryptographic algorithms
• Learn about how public and private keys are generated
• Get an overview of MD5, SHA, RC4, RC5, and Blowfish algorithms
• Learn about the digital signature and its components
• Learn about the method and application of digital signature technology
• Get an overview of digital certificates
• Learn about cryptanalysis and code-breaking methodologies
• Understand the types of cryptography attacks
• Describe a PKI system
![]()
I’ve lived in four different states and two foreign countries, and each stop along the way in my life offered something irreplaceable, unique, and downright cool. And almost without fail, I didn’t appreciate that irreplaceable, unique, and cool thing until I left for a new locale. Maybe it’s just human nature to look backward and romanticize the things no longer yours, but I think it’s valuable to pause where you’re at right now and take stock of the things you do have available to you and to sometimes marvel at how it’s all put together.
Technology is no different, and we’re all guilty of taking it for granted. When you examine how nearly anything in technology works, though, it’s almost a miracle to behold and something definitely not to be taken lightly or just accepted as a given, like gravity or rain. Cryptography is a prime example.
Consider the document I am typing right now. It’s made up of a bunch of 1s and 0s arranged in such a way as to present the text in a readable format on the screen—not to mention all the font formats, bolding, spacing, and other goodies I type in here to make it more pleasing to the eye. Just pause for a moment and consider the simple act of typing this sentence and how many bits it takes, properly formatted to display it onscreen or to save and transport it. Then figure out a way to encrypt it, also using a bunch of 1s and 0s.
The entire concept is mind-boggling if you really think about it and something we should all be grateful for. I mean, replacing a letter with a different one based on a number wheel as you write is one thing, and maybe replacing characters with symbols as you jot down on a sheet of paper doesn’t seem so exciting to you. But consider how this document’s 1s and 0s can be altered in such a way that they make no sense to an outsider but are perfectly readable for anyone I provide the key to. It’s downright magical, I tell you. Cryptography and cryptanalysis are big parts of the security world and have been ever since the earliest known communication between people. If you’re going to be an ethical hacker, you’re going to have to at least know the basics. The good news is, you are not required to break down the mathematics of the algorithms. The bad news, though, is that you need to know pretty much everything else about them.
![]()
 STUDY TIPS You’ll be asked a variety of questions about cryptography on the exam, ranging from simple identification to mind-altering questions you won’t even believe are part of this certification. The biggest thing you can do to prepare for the CEH cryptography questions is plain old organization: Commit to memory the categories (block and stream, symmetric and asymmetric, and so on) and get all your key words together.
STUDY TIPS You’ll be asked a variety of questions about cryptography on the exam, ranging from simple identification to mind-altering questions you won’t even believe are part of this certification. The biggest thing you can do to prepare for the CEH cryptography questions is plain old organization: Commit to memory the categories (block and stream, symmetric and asymmetric, and so on) and get all your key words together.
Also, make use of an old test-taking trick: Eliminating those answers you absolutely know to be wrong is faster and easier than trying to figure out which one is right. As an example, if you simply remember which algorithms are symmetric and which are asymmetric, you can oftentimes eliminate half the answers based on that qualifier in the question. Focus on the characteristics of algorithms—symmetric versus asymmetric, block versus stream—and you’re well on your way. And don’t forget your key lengths—you’ll be asked about them a lot.
Lastly, when it comes to encrypted messaging, PKI is always going to be high on the testing list. Simply remembering that you encrypt with a public key and decrypt with a private key will nab you a couple questions without fail, but you’ll definitely need to have a solid understanding of the entire system and what makes it: Questions on certificate authorities, trust systems, and cross-certification will undoubtedly show up. And, for goodness sake, be sure to know the difference between a digital certificate and a digital signature.
1. Which of the following describes the major difference between SSL and S-HTTP?
A. SSL operates at the network layer, and S-HTTP operates at the application layer.
B. SSL operates at the application layer, and S-HTTP operates at the network layer.
C. SSL operates at the transport layer, and S-HTTP operates at the application layer.
D. SSL operates at the application layer, and S-HTTP operates at the transport layer.
2. Which of the following would be the best choice to guarantee the integrity of messages in transit or storage?
A. Block cipher
B. Symmetric algorithm
C. Asymmetric algorithm
D. Hash algorithm
3. Which of the following are true regarding a PKI system? (Choose two.)
A. The CA encrypts all messages.
B. The CA is the trusted root that issues certificates.
C. The CA is the recovery agent for lost certificates.
D. The RA verifies an applicant to the system.
E. The RA issues all certificates.
F. The RA encrypts all messages.
4. A person approaches a network administrator and wants advice on how to send encrypted e-mail from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following offers a method for sending encrypted e-mail without having to pay for license fees or to manage a server?
A. IP Security (IPSec)
B. Multipurpose Internet Mail Extensions (MIME)
C. Pretty Good Privacy (PGP)
D. Hyper Text Transfer Protocol with Secure Socket Layer (HTTPS)
5. Which of the following encryption algorithms is your best choice if your primary need is bulk encryption and you need fast, strong encryption?
A. AES
B. ECC
C. RSA
D. MD5
6. You’re describing a basic PKI system to a new member of the team. He asks how the public key can be distributed within the system in an orderly, controlled fashion so that the users can be sure of the sender’s identity. Which of the following would be your answer?
A. Digital signature
B. Hash value
C. Private key
D. Digital certificate
E. Nonrepudiation
7. You are discussing hash values with a CEH instructor. Immediately after telling you the hash is a one-way algorithm and cannot be reversed, he explains that you can still discover the value entered into the hash, given enough time and resources. Which of the following hash anomalies might allow this?
A. L0phtCrack
B. Hash value compromise
C. Chosen plain text
D. Collision
8. What is the standard format for digital certificates?
A. X.500
B. X.25
C. XOR
D. X.509
9. An organization is concerned about corporate espionage and has evidence suggesting an internal employee has been communicating trade secrets to a competitor. After some investigation, the employee trading secrets was identified. Monitoring of the employee’s previous communications outside the company revealed nothing out of the ordinary, save for some large unencrypted e-mails containing image files of humorous pictures to external addresses. Which of the following is the most logical conclusion based on these facts?
A. E-mail encryption allowed the user to hide files.
B. The user hid information in the image files using steganography.
C. Logical watermarking of images and e-mails fed the sensitive files piece by piece to the competitor.
D. SMTP transport fuzzing was used.
10. A hacker has gained access to several files. Many are encrypted, but one is not, and it happens to be an unencrypted version of an encrypted file. Which of the following is the best choice for possibly providing a successful break into the encrypted files?
A. Cipher text only
B. Known plain text
C. Chosen cipher text
D. Replay
11. You are discussing a steganography tool that takes advantage of the nature of “white space” to conceal information. Which tool are you referring to?
A. Snow
B. GifShuffle
C. White Wipe
D. Tripwire
12. At the basic core of encryption approaches, two main methods are in play: substitution and transposition. Which of the following best describes transposition?
A. Bits are replaced with a different value.
B. Bits are removed.
C. The order of bits is changed.
D. The parity bits are changed.
13. Jack and Jill work in an organization that has a PKI system in place for securing messaging. Jack encrypts a message for Jill and sends it on. Jill receives the message and decrypts it. Within a PKI system, which of the following statements is true?
A. Jack encrypts with his private key. Jill decrypts with her private key.
B. Jack encrypts with his public key. Jill decrypts with her public key.
C. Jack encrypts with Jill’s private key. Jill decrypts with her public key.
D. Jack encrypts with Jill’s public key. Jill decrypts with her private key.
14. Which of the following would you find in an X.509 digital certificate? (Choose all that apply.)
A. Version
B. Algorithm ID
C. Private key
D. Public key
E. Key usage
F. PTR record
15. Which of the following is a secure substitute for Telnet?
A. SHA-1
B. RSA
C. SSL
D. SSH
16. An SSL session requires a client and a server to handshake information between each other and agree on a secured channel. Which of the following best describes the session key creation during the setup of an SSL session?
A. The server creates the key after verifying the client’s identity.
B. The server creates the key immediately on the client connection.
C. The client creates the key using the server’s public key.
D. The client creates the key after verifying the server’s identity.
17. Which encryption algorithm uses variable block sizes (from 32 to 128 bits)?
A. SHA-1
B. RC5
C. 3DES
D. AES
18. Which hash algorithm was developed by the NSA and produces output values up to 512 bits?
A. MD5
B. SHA-1
C. SHA-2
D. SSL
19. A hacker is attempting to uncover the key used in a cryptographic encryption scheme. Which attack vector is the most resource intensive and usually takes the longest amount of time?
A. Social engineering
B. Known plain text
C. Frequency analysis
D. Brute force
20. Which of the following best describes session key creation in SSL?
A. It is created by the server after verifying the user’s identity.
B. It is created by the server as soon as the client connects.
C. It is created by the client using the server’s public key.
D. It is created by the client after verifying the server’s identity.
21. In a discussion on symmetric encryption, a friend mentions that one of the drawbacks with this system is scalability. He goes on to say that for every person you add to the mix, the number of keys increases dramatically. If seven people are in a symmetric encryption pool, how many keys are necessary?
A. 7
B. 14
C. 21
D. 28
22. Which of the following is a true statement?
A. Symmetric encryption scales easily and provides for nonrepudiation.
B. Symmetric encryption does not scale easily and does not provide for nonrepudiation.
C. Symmetric encryption is not suited for bulk encryption.
D. Symmetric encryption is slower than asymmetric encryption.
23. The PKI system you are auditing has a certificate authority (CA) at the top that creates and issues certificates. Users trust each other based on the CA. Which trust model is in use here?
A. Stand-alone CA
B. Web of trust
C. Single authority
D. Hierarchical trust
24. A portion of a digital certificate is shown here:

Which of the following statements is true?
A. The hash created for the digital signature holds 160 bits.
B. The hash created for the digital signature holds 2,048 bits.
C. RSA is the hash algorithm used for the digital signature.
D. This certificate contains a private key.
25. Two bit strings are run through an XOR operation. Which of the following is a true statement for each bit pair regarding this function?
A. If the first value is 0 and the second value is 1, then the output is 0.
B. If the first value is 1 and the second value is 0, then the output is 0.
C. If the first value is 0 and the second value is 0, then the output is 1.
D. If the first value is 1 and the second value is 1, then the output is 0.
26. Which of the following attacks attempts to re-send a portion of a cryptographic exchange in hopes of setting up a communications channel?
A. Known plain text
B. Chosen plain text
C. Man in the middle
D. Replay
27. Within a PKI system, which of the following is an accurate statement?
A. Bill can be sure a message came from Sue by using his public key to decrypt it.
B. Bill can be sure a message came from Sue by using his private key to decrypt it.
C. Bill can be sure a message came from Sue by using her private key to decrypt the digital signature.
D. Bill can be sure a message came from Sue by using her public key to decrypt the digital signature.
28. Which of the following could be considered a drawback to using AES with a 256-bit key to share sensitive data?
A. The key size requires a long time to encrypt and decrypt messages.
B. It’s a complex algorithm that requires intense system configuration.
C. AES is a weak cypher.
D. Each recipient must receive the key through a different channel than the message.
29. One use of hash algorithms is for the secure storage of passwords: The password is run through a one-way hash, and the value is stored instead of the plain-text version. If a hacker gains access to these hash values and knows the hash algorithm used to create them, which of the following could be used to speed up his effort in cracking them?
A. Salt
B. Rainbow tables
C. Steganography
D. Collision
![]()
1. C
2. D
3. B, D
4. C
5. A
6. D
7. D
8. D
9. B
10. B
11. A
12. C
13. D
14. A, B, D, E
15. D
16. D
17. B
18. C
19. D
20. D
21. C
22. B
23. C
24. A
25. D
26. D
27. D
28. D
29. B
1. Which of the following describes a major difference between SSL and S-HTTP?
A. SSL operates at the network layer, and S-HTTP operates at the application layer.
B. SSL operates at the application layer, and S-HTTP operates at the network layer.
C. SSL operates at the transport layer, and S-HTTP operates at the application layer.
D. SSL operates at the application layer, and S-HTTP operates at the transport layer.
![]() C. OK, I’ll grant you the wording in this question is a little...weird, but I promise it’s apropos for your exam. Apparently EC-Council thinks writing S-HTTP will confuse you about HTTPS, which uses SSL for encryption. The differences? Well, S-HTTP and HTTPS (SSL) have a couple big ones. The first is the layer at which they operate: SSL works at the transport layer, and S-HTTP operates at the application layer. SSL tends to be application-independent, while S-HTTP is limited to the specific application using it. Lastly, SSL encrypts the entire communications channel, and S-HTTP encrypts each message independently. As an aside, S-HTTP is rarely (if ever) implemented in the real world.
C. OK, I’ll grant you the wording in this question is a little...weird, but I promise it’s apropos for your exam. Apparently EC-Council thinks writing S-HTTP will confuse you about HTTPS, which uses SSL for encryption. The differences? Well, S-HTTP and HTTPS (SSL) have a couple big ones. The first is the layer at which they operate: SSL works at the transport layer, and S-HTTP operates at the application layer. SSL tends to be application-independent, while S-HTTP is limited to the specific application using it. Lastly, SSL encrypts the entire communications channel, and S-HTTP encrypts each message independently. As an aside, S-HTTP is rarely (if ever) implemented in the real world.
![]() A, B, and D are incorrect because SSL does not work at the network or application layer.
A, B, and D are incorrect because SSL does not work at the network or application layer.
2. Which of the following would be the best choice to guarantee the integrity of messages in transit or storage?
A. Block cipher
B. Symmetric algorithm
C. Asymmetric algorithm
D. Hash algorithm
![]() D. Although it’s nice to know the terms block, stream, asymmetric, and asymmetric, they’re all irrelevant to this question. The key is the word integrity, and as you should already know from your study for this exam, that equates to a hash every time. Hash algorithms don’t encrypt anything at all. They’re one-way mathematical functions that take an input and typically produce a fixed-length string (usually a hex number), known as a hash, based on the arrangement of the data bits in the input. The sole purpose of a hash is to provide a means to verify the integrity of a piece of data—change a single bit in the arrangement of the original data, and you’ll get a different response.
D. Although it’s nice to know the terms block, stream, asymmetric, and asymmetric, they’re all irrelevant to this question. The key is the word integrity, and as you should already know from your study for this exam, that equates to a hash every time. Hash algorithms don’t encrypt anything at all. They’re one-way mathematical functions that take an input and typically produce a fixed-length string (usually a hex number), known as a hash, based on the arrangement of the data bits in the input. The sole purpose of a hash is to provide a means to verify the integrity of a piece of data—change a single bit in the arrangement of the original data, and you’ll get a different response.
![]() A is incorrect because block ciphers are not designed for integrity checks. They use methods such as substitution and transposition in their algorithms and are considered simpler, and slower, than stream ciphers. Data bits are split up into blocks and fed into the cipher, with each block of data (usually 64 bits at a time) then encrypted with the key and algorithm.
A is incorrect because block ciphers are not designed for integrity checks. They use methods such as substitution and transposition in their algorithms and are considered simpler, and slower, than stream ciphers. Data bits are split up into blocks and fed into the cipher, with each block of data (usually 64 bits at a time) then encrypted with the key and algorithm.
![]() B is incorrect because a symmetric algorithm is not designed to provide integrity checks. Also known as single key and shared key, symmetric encryption simply means one key is used both to encrypt and to decrypt the data. Therefore, as long as both the sender and the receiver know and have the secret key, communication can be encrypted between the two.
B is incorrect because a symmetric algorithm is not designed to provide integrity checks. Also known as single key and shared key, symmetric encryption simply means one key is used both to encrypt and to decrypt the data. Therefore, as long as both the sender and the receiver know and have the secret key, communication can be encrypted between the two.
![]() C is incorrect because asymmetric algorithms are not designed for integrity checks. Asymmetric encryption uses two keys—what the one key encrypts, the other key decrypts. The “public” key is the one used for encryption, whereas the “private” key is used for decryption.
C is incorrect because asymmetric algorithms are not designed for integrity checks. Asymmetric encryption uses two keys—what the one key encrypts, the other key decrypts. The “public” key is the one used for encryption, whereas the “private” key is used for decryption.
3. Which of the following is true regarding a PKI system? (Choose two.)
A. The CA encrypts all messages.
B. The CA is the trusted root that issues certificates.
C. The CA is the recovery agent for lost certificates.
D. The RA verifies an applicant to the system.
E. The RA issues all certificates.
F. The RA encrypt all messages.
![]() B and D. A PKI system consists of a bunch of parts, but the certificate authority is right at the top. The CA issues all the certificates for the system and is the one place everything in the system can go to for protected data. The registration authority does all sorts of stuff to take the load off the CA, and verifying the identity of an applicant wanting to use the system is one of the major tasks.
B and D. A PKI system consists of a bunch of parts, but the certificate authority is right at the top. The CA issues all the certificates for the system and is the one place everything in the system can go to for protected data. The registration authority does all sorts of stuff to take the load off the CA, and verifying the identity of an applicant wanting to use the system is one of the major tasks.
![]() A, C, E, and F are all incorrect because they do not correctly describe a PKI environment. The CA does not encrypt messages and is not a recovery agent for lost ones. The RA does not issue certificates or encrypt messages.
A, C, E, and F are all incorrect because they do not correctly describe a PKI environment. The CA does not encrypt messages and is not a recovery agent for lost ones. The RA does not issue certificates or encrypt messages.
4. A person approaches a network administrator and wants advice on how to send encrypted e-mail from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following offers a method for sending encrypted e-mail without having to pay for license fees or to manage a server?
A. IP Security (IPSec)
B. Multipurpose Internet Mail Extensions (MIME)
C. Pretty Good Privacy (PGP)
D. Hyper Text Transfer Protocol with Secure Socket Layer (HTTPS)
![]() C. I’m pretty sure you understand this comment already, but I’ll say it again here to reinforce it: Sometimes things on your CEH exam simply don’t match up with reality. This question is a prime example. EC-Council, and its documentation up through version 8, defines Pretty Good Privacy (PGP) as a free, open source e-mail encryption method available for all to use. In truth, PGP is now synonymous with a single company’s offering, based on the original PGP. The true open source, free side of it now is known more by OpenPGP (www.openpgp.org). OpenPGP uses a decentralized system of trusted introducers, which act in the same way as a certificate authority. Basically, in this web of trust relationship, if User A signs User B’s certificate, then anyone who trusts User A will also trust User B. You can find downloads for software still using the free, open PGP at www.pgpi.org/.
C. I’m pretty sure you understand this comment already, but I’ll say it again here to reinforce it: Sometimes things on your CEH exam simply don’t match up with reality. This question is a prime example. EC-Council, and its documentation up through version 8, defines Pretty Good Privacy (PGP) as a free, open source e-mail encryption method available for all to use. In truth, PGP is now synonymous with a single company’s offering, based on the original PGP. The true open source, free side of it now is known more by OpenPGP (www.openpgp.org). OpenPGP uses a decentralized system of trusted introducers, which act in the same way as a certificate authority. Basically, in this web of trust relationship, if User A signs User B’s certificate, then anyone who trusts User A will also trust User B. You can find downloads for software still using the free, open PGP at www.pgpi.org/.
![]() A is incorrect because IPSec is not intended as an e-mail encryption standard; it creates tunnels for the secure exchange of data from one system to another.
A is incorrect because IPSec is not intended as an e-mail encryption standard; it creates tunnels for the secure exchange of data from one system to another.
![]() B is incorrect because MIME is an Internet standard that allows the text-only protocol SMTP to transport nontext entities, such as pictures and non-ASCII character sets.
B is incorrect because MIME is an Internet standard that allows the text-only protocol SMTP to transport nontext entities, such as pictures and non-ASCII character sets.
![]() D is incorrect because HTTPS is not intended as an e-mail encryption standard. It sets up a secured means of transporting data within a session and is usually associated with web traffic.
D is incorrect because HTTPS is not intended as an e-mail encryption standard. It sets up a secured means of transporting data within a session and is usually associated with web traffic.
5. Which of the following encryption algorithms is your best choice if your primary need is bulk encryption and you need fast, strong encryption?
A. AES
B. ECC
C. RSA
D. MD5
![]() A. Questions like this on the exam are to be celebrated because they are easy—assuming you paid attention to my study tips at the beginning of this chapter. The question references bulk encryption—something fast and strong. This screams symmetric all the way, and the only symmetric algorithm listed here is AES.
A. Questions like this on the exam are to be celebrated because they are easy—assuming you paid attention to my study tips at the beginning of this chapter. The question references bulk encryption—something fast and strong. This screams symmetric all the way, and the only symmetric algorithm listed here is AES.
![]() B is incorrect because Elliptic Curve Cryptosystem (ECC) is not symmetric in nature. It’s primarily used for mobile devices and uses points on an elliptical curve, in conjunction with logarithmic problems, for encryption and signatures.
B is incorrect because Elliptic Curve Cryptosystem (ECC) is not symmetric in nature. It’s primarily used for mobile devices and uses points on an elliptical curve, in conjunction with logarithmic problems, for encryption and signatures.
![]() C is incorrect because RSA is an asymmetric choice, not a symmetric one. RSA achieves strong encryption through the use of two large prime numbers. Factoring these numbers creates key sizes up to 4,096 bits. RSA can be used for encryption and digital signatures, and it’s the modern de facto standard for those purposes.
C is incorrect because RSA is an asymmetric choice, not a symmetric one. RSA achieves strong encryption through the use of two large prime numbers. Factoring these numbers creates key sizes up to 4,096 bits. RSA can be used for encryption and digital signatures, and it’s the modern de facto standard for those purposes.
![]() D is incorrect because MD5 is a hash algorithm, and as we all know, hash algorithms don’t encrypt anything. Sure, they’re great at integrity checks, and, yes, you can pass a hash of something in place of the original (sending a hash of a stored password, for instance, instead of the password itself). However, this is not true encryption.
D is incorrect because MD5 is a hash algorithm, and as we all know, hash algorithms don’t encrypt anything. Sure, they’re great at integrity checks, and, yes, you can pass a hash of something in place of the original (sending a hash of a stored password, for instance, instead of the password itself). However, this is not true encryption.
6. You’re describing a basic PKI system to a new member of the team. He asks how the public key can be distributed within the system in an orderly, controlled fashion so that the users can be sure of the sender’s identity. Which of the following would be your answer?
A. Digital signature
B. Hash value
C. Private key
D. Digital certificate
E. Nonrepudiation
![]() D. This one is actually easy yet is confusing to a lot of folks. You have to remember the goal of this little portion of a PKI system—how does one know this public key really belongs to User Joe and not User Mike, and how can it be delivered safely to everyone? A digital certificate is the answer because it contains the sender’s public key and can be used to identify the sender. Because the CA provides the certificate and key (public), the user can be certain the public key actually belongs to the intended recipient. This simplifies distribution of keys as well, because users can go to a central authority—a key store, if you will—instead of directly to each user in the organization. Without central control and digital certificates, it would be a madhouse, with everyone chucking public keys at one another with wild abandon. And PKI is no place for Mardi Gras, my friend.
D. This one is actually easy yet is confusing to a lot of folks. You have to remember the goal of this little portion of a PKI system—how does one know this public key really belongs to User Joe and not User Mike, and how can it be delivered safely to everyone? A digital certificate is the answer because it contains the sender’s public key and can be used to identify the sender. Because the CA provides the certificate and key (public), the user can be certain the public key actually belongs to the intended recipient. This simplifies distribution of keys as well, because users can go to a central authority—a key store, if you will—instead of directly to each user in the organization. Without central control and digital certificates, it would be a madhouse, with everyone chucking public keys at one another with wild abandon. And PKI is no place for Mardi Gras, my friend.
![]() A is incorrect because although a digital signature does provide a means for verifying an identity (encryption with your private key, which can be decrypted only with your corresponding public key, proves you are indeed you), it doesn’t provide any means of sending keys anywhere. A digital signature is nothing more than an algorithmic output that is designed to ensure the authenticity (and integrity) of the sender. You need it to prove your certificate’s authenticity, but you need the certificate in order to send keys around.
A is incorrect because although a digital signature does provide a means for verifying an identity (encryption with your private key, which can be decrypted only with your corresponding public key, proves you are indeed you), it doesn’t provide any means of sending keys anywhere. A digital signature is nothing more than an algorithmic output that is designed to ensure the authenticity (and integrity) of the sender. You need it to prove your certificate’s authenticity, but you need the certificate in order to send keys around.
![]() B is incorrect because a hash value has nothing to do with sending public keys around anywhere. Yes, hash values are “signed” to verify authenticity, but that’s it. There is no transport capability in a hash. It’s just a number and, in this case, a distractor answer.
B is incorrect because a hash value has nothing to do with sending public keys around anywhere. Yes, hash values are “signed” to verify authenticity, but that’s it. There is no transport capability in a hash. It’s just a number and, in this case, a distractor answer.
![]() C is incorrect for a number of reasons, but one should be screaming at you from the page right now: You never, never, send a private key anywhere. If you did send your private key off, it wouldn’t be private anymore, now would it? The private key is simply the part of the pair used for encryption. It is never shared with anyone.
C is incorrect for a number of reasons, but one should be screaming at you from the page right now: You never, never, send a private key anywhere. If you did send your private key off, it wouldn’t be private anymore, now would it? The private key is simply the part of the pair used for encryption. It is never shared with anyone.
![]() E is incorrect because nonrepudiation is a definition term and has nothing to do with the transport of keys. Nonrepudiation is the means by which a recipient can ensure the identity of the sender and neither party can deny having sent or received the message.
E is incorrect because nonrepudiation is a definition term and has nothing to do with the transport of keys. Nonrepudiation is the means by which a recipient can ensure the identity of the sender and neither party can deny having sent or received the message.
7. You are discussing hash values with a CEH instructor. Immediately after telling you the hash is a one-way algorithm and cannot be reversed, he explains that you can still discover the value entered into the hash, given enough time and resources. Which of the following hash anomalies might allow this?
A. L0phtCrack
B. Hash value compromise
C. Chosen plain text
D. Collision
![]() D. A collision, in the world of hashes, occurs when plain text is fed into a hash until, eventually, two or more entries are found that create the same fixed-value hash result. In short, a collision occurs when two or more files create the same output. When a hacker can create a second file that produces the same hash value output as the original, he may be able to pass off the fake file as the original. This can obviously cause all sorts of problems, and when you think about what hashes are sometimes used for (such as storing hashes of passwords in a file instead of the passwords themselves), you can certainly understand where collisions are concerning. As an aside, it is just as likely you would find a new collision than the original collision, and without the knowledge of the original text, your results would be nothing more than an educated guess. For the purposes of the exam, though, just remember what a collision is and means.
D. A collision, in the world of hashes, occurs when plain text is fed into a hash until, eventually, two or more entries are found that create the same fixed-value hash result. In short, a collision occurs when two or more files create the same output. When a hacker can create a second file that produces the same hash value output as the original, he may be able to pass off the fake file as the original. This can obviously cause all sorts of problems, and when you think about what hashes are sometimes used for (such as storing hashes of passwords in a file instead of the passwords themselves), you can certainly understand where collisions are concerning. As an aside, it is just as likely you would find a new collision than the original collision, and without the knowledge of the original text, your results would be nothing more than an educated guess. For the purposes of the exam, though, just remember what a collision is and means.
![]() A is incorrect because L0phtCrack really has nothing to do with this question. It is a good-old password cracker in the Windows world, but it’s not a collision of hash values in any sense. It’s a “password auditing and recovery application” used to test password strength and “recover” lost passwords on Windows machines. It uses dictionary, brute-force, and hybrid attacks, as well as rainbow tables.
A is incorrect because L0phtCrack really has nothing to do with this question. It is a good-old password cracker in the Windows world, but it’s not a collision of hash values in any sense. It’s a “password auditing and recovery application” used to test password strength and “recover” lost passwords on Windows machines. It uses dictionary, brute-force, and hybrid attacks, as well as rainbow tables.
![]() B is incorrect for a couple of reasons. First, the term hash value compromise sounds really cool but has no meaning in the CEH world. This term could be construed to mean lots of things, but if you run a quick Google check (go ahead, I’ll wait), you’ll see that it’s not a definition term you’ll need to know. It’s a pretty good distractor, yes, but not a viable answer.
B is incorrect for a couple of reasons. First, the term hash value compromise sounds really cool but has no meaning in the CEH world. This term could be construed to mean lots of things, but if you run a quick Google check (go ahead, I’ll wait), you’ll see that it’s not a definition term you’ll need to know. It’s a pretty good distractor, yes, but not a viable answer.
![]() C is incorrect because chosen plain text is an attack used to determine the key used for encryption. It’s a variant of known plain text, where the hacker has both plain-text and corresponding cipher-text messages and scans them for repeatable sequences. These are compared to the cipher-text versions and—voilà—key found.
C is incorrect because chosen plain text is an attack used to determine the key used for encryption. It’s a variant of known plain text, where the hacker has both plain-text and corresponding cipher-text messages and scans them for repeatable sequences. These are compared to the cipher-text versions and—voilà—key found.
8. What is the standard format for digital certificates?
A. X.500
B. X.25
C. XOR
D. X.509
![]() D. This is a quick, simple question you’ll see on pretty much every study guide and practice test for CEH. It’s just something you’re going to need in your memory bank—one of those things you just know without thinking about it. The X.509 standard is a part of a much bigger series of standards, and it defines what should and should not be in a digital certificate. Because of the standard, any system complying with X.509 can exchange and use digital certificates to establish authenticity.
D. This is a quick, simple question you’ll see on pretty much every study guide and practice test for CEH. It’s just something you’re going to need in your memory bank—one of those things you just know without thinking about it. The X.509 standard is a part of a much bigger series of standards, and it defines what should and should not be in a digital certificate. Because of the standard, any system complying with X.509 can exchange and use digital certificates to establish authenticity.
![]() A is incorrect because X.500 has nothing to do with digital certificates. It’s actually a series of standards covering directory services, and it’s more applicable to things such as Active Directory in Windows-based networks. On a related but completely worthless note, it was developed by ITU-T way back in 1988.
A is incorrect because X.500 has nothing to do with digital certificates. It’s actually a series of standards covering directory services, and it’s more applicable to things such as Active Directory in Windows-based networks. On a related but completely worthless note, it was developed by ITU-T way back in 1988.
![]() B is incorrect because X.25 has nothing to do with digital certificates. X.25 is a protocol suite from ITU-T defining wide area network (WAN) communication.
B is incorrect because X.25 has nothing to do with digital certificates. X.25 is a protocol suite from ITU-T defining wide area network (WAN) communication.
![]() C is incorrect because XOR refers to a mathematical function. An XOR operation requires two inputs, which are compared by the operation. If the bits match, the output is 0; if they don’t, it’s 1.
C is incorrect because XOR refers to a mathematical function. An XOR operation requires two inputs, which are compared by the operation. If the bits match, the output is 0; if they don’t, it’s 1.
9. An organization is concerned about corporate espionage and has evidence suggesting an internal employee has been communicating trade secrets to a competitor. After some investigation, the employee trading secrets was identified. Monitoring of the employee’s previous communications outside the company revealed nothing out of the ordinary, save for some large unencrypted e-mails containing image files of humorous pictures to external addresses. Which of the following is the most logical conclusion based on these facts?
A. E-mail encryption allowed the user to hide files.
B. The user hid information in the image files using steganography.
C. Logical watermarking of images and e-mails fed the sensitive files piece by piece to the competitor.
D. SMTP transport fuzzing was used.
![]() B. In this circumstance, we know the employee has been sending sensitive documents out of the network. IDS obviously hasn’t picked up on anything, and there was nothing overtly done to give away the intent. The only thing out of the ordinary turned out to be large e-mail files holding nothing but images. Steganography is the most logical choice here, and the user simply folded the sensitive data into the latest joke image he found and sent it on its merry way.
B. In this circumstance, we know the employee has been sending sensitive documents out of the network. IDS obviously hasn’t picked up on anything, and there was nothing overtly done to give away the intent. The only thing out of the ordinary turned out to be large e-mail files holding nothing but images. Steganography is the most logical choice here, and the user simply folded the sensitive data into the latest joke image he found and sent it on its merry way.
![]() A is incorrect because e-mail encryption isn’t in place—it’s specifically called out in the question and wouldn’t necessarily allow external encryption or hide the information from later forensics examinations.
A is incorrect because e-mail encryption isn’t in place—it’s specifically called out in the question and wouldn’t necessarily allow external encryption or hide the information from later forensics examinations.
![]() C and D are incorrect because logical watermarking and SMTP transport fuzzing, so far as I know, don’t even exist. They sound cool and may appear legitimate, but they’re definitely not the answers we’re looking for.
C and D are incorrect because logical watermarking and SMTP transport fuzzing, so far as I know, don’t even exist. They sound cool and may appear legitimate, but they’re definitely not the answers we’re looking for.
10. A hacker has gained access to several files. Many are encrypted, but one is not, and it happens to be an unencrypted version of an encrypted file. Which of the following is the best choice for possibly providing a successful break into the encrypted files?
A. Cipher text only
B. Known plain text
C. Chosen cipher text
D. Replay
![]() B. There is definitely some room for argument on this question: Who’s to say all the files were encrypted in the same way? However, of the options presented, known plain text is the one that makes the most sense. In this attack, the hacker has both plain-text and cipher-text messages. Plain-text copies are scanned for repeatable sequences, which are then compared to the cipher-text versions. Over time, and with effort, this can be used to decipher the key.
B. There is definitely some room for argument on this question: Who’s to say all the files were encrypted in the same way? However, of the options presented, known plain text is the one that makes the most sense. In this attack, the hacker has both plain-text and cipher-text messages. Plain-text copies are scanned for repeatable sequences, which are then compared to the cipher-text versions. Over time, and with effort, this can be used to decipher the key.
![]() A is incorrect, but just barely so. I’m certain some of you are arguing that a cipher-text-only attack could also be used here because in that attack several messages encrypted in the same way are run through statistical analysis to eventually reveal repeating code, which may be used to decode messages later. Sure, an attacker might just ignore the plain-text copy in there, but the inference in the question is that he’d use both. You’ll often see questions like this where you’ll need to take into account the inference without over-thinking the question.
A is incorrect, but just barely so. I’m certain some of you are arguing that a cipher-text-only attack could also be used here because in that attack several messages encrypted in the same way are run through statistical analysis to eventually reveal repeating code, which may be used to decode messages later. Sure, an attacker might just ignore the plain-text copy in there, but the inference in the question is that he’d use both. You’ll often see questions like this where you’ll need to take into account the inference without over-thinking the question.
![]() C is incorrect because chosen cipher text works almost exactly like a cipher-text-only attack. Statistical analysis without a plain-text version for comparison can be performed, but it’s only for portions of gained cipher text. That’s the key word to look for.
C is incorrect because chosen cipher text works almost exactly like a cipher-text-only attack. Statistical analysis without a plain-text version for comparison can be performed, but it’s only for portions of gained cipher text. That’s the key word to look for.
![]() D is incorrect because it’s irrelevant to this scenario. Replay attacks catch streams of data and replay them to the intended recipient from another sender.
D is incorrect because it’s irrelevant to this scenario. Replay attacks catch streams of data and replay them to the intended recipient from another sender.
11. You are discussing a steganography tool that takes advantage of the nature of “white space” to conceal information. Which tool are you discussing?
A. Snow
B. GifShuffle
C. White Wipe
D. Tripwire
![]() A. Snow is one of the steganography tools the CEH exam covers. The following is from the Snow website: “The program snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.”
A. Snow is one of the steganography tools the CEH exam covers. The following is from the Snow website: “The program snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.”
![]() B is incorrect because GifShuffle is used to conceal messages in GIF images by shuffling bits in the color map. Because these changes are minutely small, GifShuffle leaves the image visibly unchanged. It’s also an open source tool.
B is incorrect because GifShuffle is used to conceal messages in GIF images by shuffling bits in the color map. Because these changes are minutely small, GifShuffle leaves the image visibly unchanged. It’s also an open source tool.
![]() C is incorrect because White Wipe is not a steganography tool. In fact, as far as I know, it’s not a tool at all. This is simply a distractor answer.
C is incorrect because White Wipe is not a steganography tool. In fact, as far as I know, it’s not a tool at all. This is simply a distractor answer.
![]() D is incorrect because Tripwire is not a steganography tool either. Rather, it’s a conglomeration of tool actions that perform the overall IT security efforts for an enterprise. It provides for integrity checks, regulatory compliance, configuration management, and all other sorts of goodies.
D is incorrect because Tripwire is not a steganography tool either. Rather, it’s a conglomeration of tool actions that perform the overall IT security efforts for an enterprise. It provides for integrity checks, regulatory compliance, configuration management, and all other sorts of goodies.
12. At the basic core of encryption approaches, two main methods are in play: substitution and transposition. Which of the following best describes transposition?
A. Bits are replaced with a different value.
B. Bits are removed.
C. The order of bits is changed.
D. The parity bits are changed.
![]() C. This is just a different way of asking you to define substitution and transposition. Substitution is exactly what it sounds like. Transposition doesn’t substitute at all; it changes the bit order altogether.
C. This is just a different way of asking you to define substitution and transposition. Substitution is exactly what it sounds like. Transposition doesn’t substitute at all; it changes the bit order altogether.
![]() A is incorrect because this is the definition for substitution. Substitution is exactly what it sounds like—bits are simply replaced by other bits.
A is incorrect because this is the definition for substitution. Substitution is exactly what it sounds like—bits are simply replaced by other bits.
![]() B is incorrect because bits aren’t technically removed with either function. They may be replaced, or reordered, but they are not removed.
B is incorrect because bits aren’t technically removed with either function. They may be replaced, or reordered, but they are not removed.
![]() D is incorrect because this answer has nothing, really, to do with encryption. Parity bits sounds sexy and exciting, but it’s meaningless in this context. Parity bits are used for basic error correction, not encryption.
D is incorrect because this answer has nothing, really, to do with encryption. Parity bits sounds sexy and exciting, but it’s meaningless in this context. Parity bits are used for basic error correction, not encryption.
13. Jack and Jill work in an organization that has a PKI system in place for securing messaging. Jack encrypts a message for Jill and sends it on. Jill receives the message and decrypts it. Within a PKI system, which of the following statements is true?
A. Jack encrypts with his private key. Jill decrypts with her private key.
B. Jack encrypts with his public key. Jill decrypts with her public key.
C. Jack encrypts with Jill’s private key. Jill decrypts with her public key.
D. Jack encrypts with Jill’s public key. Jill decrypts with her private key.
![]() D. When it comes to PKI encryption questions, remember the golden rule: Encrypt with public, decrypt with private. In this instance, Jack wants to send a message to Jill. He will use Jill’s public key—which everyone can get—to encrypt the message, knowing that only Jill, with her corresponding private key, can decrypt it.
D. When it comes to PKI encryption questions, remember the golden rule: Encrypt with public, decrypt with private. In this instance, Jack wants to send a message to Jill. He will use Jill’s public key—which everyone can get—to encrypt the message, knowing that only Jill, with her corresponding private key, can decrypt it.
![]() A is incorrect because you do not encrypt with a private key in a PKI system. Yes, you can encrypt with it, but what would be the point? Anyone with your public key—which everyone has—could decrypt it! Remember, private = decrypt, public = encrypt.
A is incorrect because you do not encrypt with a private key in a PKI system. Yes, you can encrypt with it, but what would be the point? Anyone with your public key—which everyone has—could decrypt it! Remember, private = decrypt, public = encrypt.
![]() B is incorrect because, in this case, Jack has gotten his end of the bargain correct, but Jill doesn’t seem to know what she’s doing. PKI encryption is done in key pairs—what one key encrypts, the other decrypts. So, her use of her own public key to decrypt something encrypted with Jack’s key—a key from a completely different pair—is baffling.
B is incorrect because, in this case, Jack has gotten his end of the bargain correct, but Jill doesn’t seem to know what she’s doing. PKI encryption is done in key pairs—what one key encrypts, the other decrypts. So, her use of her own public key to decrypt something encrypted with Jack’s key—a key from a completely different pair—is baffling.
![]() C is incorrect because there is no way Jack should have anyone’s private key, other than his own. That’s kind of the point of a private key—you keep it to yourself and don’t share it with anyone. As a note here, the stated steps would actually work—that is, one key encrypts, so the other decrypts—but it’s completely backward for how the system is supposed to work. It’s an abomination to security, if you will.
C is incorrect because there is no way Jack should have anyone’s private key, other than his own. That’s kind of the point of a private key—you keep it to yourself and don’t share it with anyone. As a note here, the stated steps would actually work—that is, one key encrypts, so the other decrypts—but it’s completely backward for how the system is supposed to work. It’s an abomination to security, if you will.
14. Which of the following would you find in an X.509 digital certificate? (Choose all that apply.)
A. Version
B. Algorithm ID
C. Private key
D. Public key
E. Key usage
F. PTR record
![]() A, B, D, and E. You are definitely going to need to know the digital certificate and what it contains. A digital certificate is an electronic file that is used to verify a user’s identity, providing nonrepudiation throughout the system. The certificate contains standard fields used for specific purposes. Those fields are Version, Serial Number, Subject, Algorithm ID (or Signature Algorithm), Issuer, Valid From and Valid To, Key Usage, Subject’s Public Key, and Optional.
A, B, D, and E. You are definitely going to need to know the digital certificate and what it contains. A digital certificate is an electronic file that is used to verify a user’s identity, providing nonrepudiation throughout the system. The certificate contains standard fields used for specific purposes. Those fields are Version, Serial Number, Subject, Algorithm ID (or Signature Algorithm), Issuer, Valid From and Valid To, Key Usage, Subject’s Public Key, and Optional.
![]() C is incorrect because a private key is never shared. The certificate usually is “signed” with an encrypted hash by the private key, but the key itself is never shared.
C is incorrect because a private key is never shared. The certificate usually is “signed” with an encrypted hash by the private key, but the key itself is never shared.
![]() F is incorrect because a PTR record is a part of the Domain Name System (DNS), not a digital certificate. A PTR record provides a reverse DNS lookup as a pointer to a canonical name.
F is incorrect because a PTR record is a part of the Domain Name System (DNS), not a digital certificate. A PTR record provides a reverse DNS lookup as a pointer to a canonical name.
15. Which of the following is a secure substitute for Telnet?
A. SHA-1
B. RSA
C. SSL
D. SSH
![]() D. Secure Shell (SSH) was created to fill a security need. Telnet provides easy administrative access, but it’s in the clear and ripe for theft. SSH performs the same functions—providing a channel for command execution and remote logging—but does so in a secured method, over a secured channel with strong authentication. As an aside, Telnet can do lots of things SSH cannot (providing some marginal interaction with generic TCP services, serving as a poor hacker’s web browser, and so on). Therefore, SSH is to be thought of as a secure alternative to Telnet, not a replacement.
D. Secure Shell (SSH) was created to fill a security need. Telnet provides easy administrative access, but it’s in the clear and ripe for theft. SSH performs the same functions—providing a channel for command execution and remote logging—but does so in a secured method, over a secured channel with strong authentication. As an aside, Telnet can do lots of things SSH cannot (providing some marginal interaction with generic TCP services, serving as a poor hacker’s web browser, and so on). Therefore, SSH is to be thought of as a secure alternative to Telnet, not a replacement.
![]() A is incorrect because SHA-1 is a hashing algorithm, not a means for encrypting a channel for communication exchange. It was published by the National Institute of Standards and Technology (NIST) as a better, stronger hash alternative and is now in its third cycle of development (SHA-2 and SHA-3 have been released).
A is incorrect because SHA-1 is a hashing algorithm, not a means for encrypting a channel for communication exchange. It was published by the National Institute of Standards and Technology (NIST) as a better, stronger hash alternative and is now in its third cycle of development (SHA-2 and SHA-3 have been released).
![]() B is incorrect because RSA is an encryption algorithm, achieving strong encryption through the use of two large prime numbers. Factoring these numbers creates key sizes up to 4,096 bits. RSA can be used for encryption and digital signatures and is the modern de facto standard.
B is incorrect because RSA is an encryption algorithm, achieving strong encryption through the use of two large prime numbers. Factoring these numbers creates key sizes up to 4,096 bits. RSA can be used for encryption and digital signatures and is the modern de facto standard.
![]() C is incorrect because SSL is an application layer protocol for managing security on Internet message transit. It uses RSA asymmetric encryption to encrypt data transferred over its connection.
C is incorrect because SSL is an application layer protocol for managing security on Internet message transit. It uses RSA asymmetric encryption to encrypt data transferred over its connection.
16. An SSL session requires a client and a server to handshake information between each other and agree on a secured channel. Which of the following best describes the session key creation during the setup of an SSL session?
A. The server creates the key after verifying the client’s identity.
B. The server creates the key immediately on the client connection.
C. The client creates the key using the server’s public key.
D. The client creates the key after verifying the server’s identity.
![]() D. In the CEH world, SSL has six major steps (others claim seven or more, but we’re studying for the CEH certification here, so we’ll stick with theirs). The six steps are (1) Client hello, (2) Server hello and certificate, (3) Server hello done message, (4) Client verifies server identity and sends Client Key Exchange message, (5) Client sends Change Cipher Spec and Finish message, and (6) Server responds with Change Cipher Spec and Finish message. The session key is created by the client after it verifies the server identity (using the certificate provided in step 2).
D. In the CEH world, SSL has six major steps (others claim seven or more, but we’re studying for the CEH certification here, so we’ll stick with theirs). The six steps are (1) Client hello, (2) Server hello and certificate, (3) Server hello done message, (4) Client verifies server identity and sends Client Key Exchange message, (5) Client sends Change Cipher Spec and Finish message, and (6) Server responds with Change Cipher Spec and Finish message. The session key is created by the client after it verifies the server identity (using the certificate provided in step 2).
![]() A is incorrect because the server does not create the session key.
A is incorrect because the server does not create the session key.
![]() B is incorrect for the same reason—the client creates the key, not the server.
B is incorrect for the same reason—the client creates the key, not the server.
![]() C is incorrect because the client does not use a “public key” for an SSL session. It’s a great distractor, trying to confuse you with PKI terms in an SSL question.
C is incorrect because the client does not use a “public key” for an SSL session. It’s a great distractor, trying to confuse you with PKI terms in an SSL question.
17. Which encryption algorithm uses variable block sizes (from 32 to 128 bits)?
A. SHA-1
B. RC5
C. 3DES
D. AES
![]() B. Questions on identifying encryption algorithms really come down to memorization of some key terms. Rivest Cipher (RC) encompasses several versions, from RC2 through RC6. It is an asymmetric block cipher that uses a variable key length up to 2,040 bits. RC6, the latest version, uses 128-bit blocks, whereas RC5 uses variable block sizes (32, 64, or 128).
B. Questions on identifying encryption algorithms really come down to memorization of some key terms. Rivest Cipher (RC) encompasses several versions, from RC2 through RC6. It is an asymmetric block cipher that uses a variable key length up to 2,040 bits. RC6, the latest version, uses 128-bit blocks, whereas RC5 uses variable block sizes (32, 64, or 128).
![]() A is incorrect because SHA-1 is a hash algorithm, not an encryption algorithm. If this question were about verifying integrity, this would be a good choice. However, in this case, it is a distractor.
A is incorrect because SHA-1 is a hash algorithm, not an encryption algorithm. If this question were about verifying integrity, this would be a good choice. However, in this case, it is a distractor.
![]() C is incorrect because although 3DES is a symmetric block cipher, it does not use variable block sizes. 3DES (called triple DES) uses a 168-bit key and can use up to three keys in a multiple-encryption method. It’s much more effective than DES but is much slower.
C is incorrect because although 3DES is a symmetric block cipher, it does not use variable block sizes. 3DES (called triple DES) uses a 168-bit key and can use up to three keys in a multiple-encryption method. It’s much more effective than DES but is much slower.
![]() D is incorrect because AES, another symmetric block cipher, uses key lengths of 128, 192, or 256 bits. It effectively replaces DES and is much faster than either DES or its triplicate cousin (3DES).
D is incorrect because AES, another symmetric block cipher, uses key lengths of 128, 192, or 256 bits. It effectively replaces DES and is much faster than either DES or its triplicate cousin (3DES).
18. Which hash algorithm was developed by the NSA and produces output values up to 512 bits?
A. MD5
B. SHA-1
C. SHA-2
D. SSL
![]() C. Both SHA-1 and SHA-2 were developed by the NSA; however, SHA-1 produced only a 160-bit output value. SHA-2 was developed to rectify the shortcomings of its predecessor and is capable of producing outputs of 224, 256, 384, and 512 bits. Although it was designed as a replacement for SHA-1 (which was supposed to have been phased out in 2010), SHA-2 is still not as widely used.
C. Both SHA-1 and SHA-2 were developed by the NSA; however, SHA-1 produced only a 160-bit output value. SHA-2 was developed to rectify the shortcomings of its predecessor and is capable of producing outputs of 224, 256, 384, and 512 bits. Although it was designed as a replacement for SHA-1 (which was supposed to have been phased out in 2010), SHA-2 is still not as widely used.
![]() A is incorrect because MD5 produces 128-bit output. It was created by Ronald Rivest for ensuring file integrity; however, serious flaws in the algorithm, and the advancement of other hashes, have resulted in this hash being rendered obsolete (U.S. CERT, August 2010). Despite this, you’ll find MD5 is still used for file verification on downloads and, in many cases, to store passwords.
A is incorrect because MD5 produces 128-bit output. It was created by Ronald Rivest for ensuring file integrity; however, serious flaws in the algorithm, and the advancement of other hashes, have resulted in this hash being rendered obsolete (U.S. CERT, August 2010). Despite this, you’ll find MD5 is still used for file verification on downloads and, in many cases, to store passwords.
![]() B is incorrect because SHA-1 produces a 160-bit value output. It was created by NSA and used to be required by law for use in U.S. government applications. However, serious flaws became apparent in late 2005, and the U.S. government began recommending the replacement of SHA-1 with SHA-2 after 2010 (see FIPS PUB 180-1).
B is incorrect because SHA-1 produces a 160-bit value output. It was created by NSA and used to be required by law for use in U.S. government applications. However, serious flaws became apparent in late 2005, and the U.S. government began recommending the replacement of SHA-1 with SHA-2 after 2010 (see FIPS PUB 180-1).
![]() D is incorrect because SSL isn’t even a hash algorithm. If you picked this one, you have some serious studying to do.
D is incorrect because SSL isn’t even a hash algorithm. If you picked this one, you have some serious studying to do.
19. A hacker is attempting to uncover the key used in a cryptographic encryption scheme. Which attack vector is the most resource intensive and usually takes the longest amount of time?
A. Social engineering
B. Known plaintext
C. Frequency analysis
D. Brute force
![]() D. I know you probably weren’t expecting a brute-force definition to show up so early, but sometimes this exam will throw terms in and out of objectives to see whether you’re paying attention. Brute-force attacks—whether attempting to crack a password or, in this case, to determine a key used in cryptography—are the longest and most resource intensive. If you think about what the attack is doing, this makes perfect sense. Although, eventually, every brute-force attack will be successful, the length of the key can make the length of time necessary to go through all possible iterations unacceptable. For example, if it takes your supercomputer 12 years to crack an algorithm key, it’s probably a safe bet that the target has changed it within that time span.
D. I know you probably weren’t expecting a brute-force definition to show up so early, but sometimes this exam will throw terms in and out of objectives to see whether you’re paying attention. Brute-force attacks—whether attempting to crack a password or, in this case, to determine a key used in cryptography—are the longest and most resource intensive. If you think about what the attack is doing, this makes perfect sense. Although, eventually, every brute-force attack will be successful, the length of the key can make the length of time necessary to go through all possible iterations unacceptable. For example, if it takes your supercomputer 12 years to crack an algorithm key, it’s probably a safe bet that the target has changed it within that time span.
![]() A is incorrect because social engineering requires little to no resources at all, and given the right individual on the phone (or sitting behind a desk), it could be pretty quick. Granted, this is a ridiculous answer here—who is actually going to hand over a cryptographic key to someone?—but stranger things have happened.
A is incorrect because social engineering requires little to no resources at all, and given the right individual on the phone (or sitting behind a desk), it could be pretty quick. Granted, this is a ridiculous answer here—who is actually going to hand over a cryptographic key to someone?—but stranger things have happened.
![]() B is incorrect because known plain text takes at least some of the time-crunching out for you. Remember in this attack that the hacker has both plain-text and cipher-text messages. Plain-text copies are scanned for repeatable sequences, which are then compared to the cipher-text versions. Over time, and with effort, this can be used to decipher the key; however, it is not as resource intensive as brute force.
B is incorrect because known plain text takes at least some of the time-crunching out for you. Remember in this attack that the hacker has both plain-text and cipher-text messages. Plain-text copies are scanned for repeatable sequences, which are then compared to the cipher-text versions. Over time, and with effort, this can be used to decipher the key; however, it is not as resource intensive as brute force.
![]() C is incorrect because, although this answer sounds really cool, it doesn’t fit with the question criteria (time and resource intensive). Frequency analysis relies on the fact that, in any given sample of English writing, there will be certain letters (and combinations of letters) that occur with more frequency than others. This kind of attack appeals to the math geeks in our field—and to those who tech-edit hacking books.
C is incorrect because, although this answer sounds really cool, it doesn’t fit with the question criteria (time and resource intensive). Frequency analysis relies on the fact that, in any given sample of English writing, there will be certain letters (and combinations of letters) that occur with more frequency than others. This kind of attack appeals to the math geeks in our field—and to those who tech-edit hacking books.
20. Which of the following best describes session key creation in SSL?
A. It is created by the server after verifying the user’s identity.
B. It is created by the server as soon as the client connects.
C. It is created by the client using the server’s public key.
D. It is created by the client after verifying the server’s identity.
![]() D. Depending on the book you’re reading, an SSL session can have anywhere from five to ten steps. For our purposes, there are six defined steps that start with an exchange of hello packets that allows the server to authenticate itself to the client (using public-key techniques and providing SSL version, session ID, and certificate). After these three handshake messages are exchanged, the client verifies the certificate and generates a secret key, which it then encrypts using the server’s public key. Finally, a finish message from the client is sent, and the server compares hashes, sending its own finish message to start the session.
D. Depending on the book you’re reading, an SSL session can have anywhere from five to ten steps. For our purposes, there are six defined steps that start with an exchange of hello packets that allows the server to authenticate itself to the client (using public-key techniques and providing SSL version, session ID, and certificate). After these three handshake messages are exchanged, the client verifies the certificate and generates a secret key, which it then encrypts using the server’s public key. Finally, a finish message from the client is sent, and the server compares hashes, sending its own finish message to start the session.
![]() A and B are incorrect because the server does not create the secret key.
A and B are incorrect because the server does not create the secret key.
![]() C is incorrect because the public key is used to encrypt the key, not to create it.
C is incorrect because the public key is used to encrypt the key, not to create it.
21. In a discussion on symmetric encryption, a friend mentions that one of the drawbacks with this system is scalability. He goes on to say that for every person you add to the mix, the number of keys increases dramatically. If seven people are in a symmetric encryption pool, how many keys are necessary?
A. 7
B. 14
C. 21
D. 28
![]() C. Symmetric encryption is really fast and works great with bulk encryption; however, scalability and key exchange are huge drawbacks. To determine the number of keys you need, use the formula N (N – 1) / 2. Plugging 7 into this, we have 7 (7 – 1) / 2 = 21.
C. Symmetric encryption is really fast and works great with bulk encryption; however, scalability and key exchange are huge drawbacks. To determine the number of keys you need, use the formula N (N – 1) / 2. Plugging 7 into this, we have 7 (7 – 1) / 2 = 21.
![]() A is incorrect because although symmetric key does use the same key for encryption and decryption, each new node requires a different key. Seven keys simply isn’t enough.
A is incorrect because although symmetric key does use the same key for encryption and decryption, each new node requires a different key. Seven keys simply isn’t enough.
![]() B is incorrect because 14 keys isn’t enough.
B is incorrect because 14 keys isn’t enough.
![]() D is incorrect because 28 keys is too many. Stick with the formula N (N – 1) / 2.
D is incorrect because 28 keys is too many. Stick with the formula N (N – 1) / 2.
22. Which of the following is a true statement?
A. Symmetric encryption scales easily and provides for nonrepudiation.
B. Symmetric encryption does not scale easily and does not provide for nonrepudiation.
C. Symmetric encryption is not suited for bulk encryption.
D. Symmetric encryption is slower than asymmetric encryption.
![]() B. Symmetric encryption has always been known for strength and speed; however, scalability and key exchange are big drawbacks. Additionally, there is no way to provide for nonrepudiation (within the confines of the encryption system). Symmetric encryption is good for a great many things when you don’t want all the overhead of key management.
B. Symmetric encryption has always been known for strength and speed; however, scalability and key exchange are big drawbacks. Additionally, there is no way to provide for nonrepudiation (within the confines of the encryption system). Symmetric encryption is good for a great many things when you don’t want all the overhead of key management.
![]() A is incorrect because symmetric encryption does not scale easily and does not provide for nonrepudiation. The single key used for each channel makes scalability an issue. Remember, the formula for number of keys is N (N – 1) / 2.
A is incorrect because symmetric encryption does not scale easily and does not provide for nonrepudiation. The single key used for each channel makes scalability an issue. Remember, the formula for number of keys is N (N – 1) / 2.
![]() C is incorrect because symmetric encryption is perfectly designed for bulk encryption. Assuming you can find a way to ensure the key exchange is protected, speed makes this the best choice.
C is incorrect because symmetric encryption is perfectly designed for bulk encryption. Assuming you can find a way to ensure the key exchange is protected, speed makes this the best choice.
![]() D is incorrect because one of the benefits of symmetric encryption is its speed. It is much faster than asymmetric encryption but doesn’t provide some of the benefits asymmetric provides us (scalability, nonrepudiation, and so on).
D is incorrect because one of the benefits of symmetric encryption is its speed. It is much faster than asymmetric encryption but doesn’t provide some of the benefits asymmetric provides us (scalability, nonrepudiation, and so on).
23. The PKI system you are auditing has a certificate authority (CA) at the top that creates and issues certificates. Users trust each other based on the CA. Which trust model is in use here?
A. Stand-alone CA
B. Web of trust
C. Single authority
D. Hierarchical trust
![]() C. Trust models within PKI systems provide a standardized method for certificate and key exchanges. The valid trust models include web of trust, single authority, and hierarchical. The single authority system has a CA at the top that creates and issues certs. Users then trust each other based on the CA at the top vouching for them. Assuming a single authority model is used, it’s of vital importance to protect it. After all, if it is compromised, your whole system is kaput.
C. Trust models within PKI systems provide a standardized method for certificate and key exchanges. The valid trust models include web of trust, single authority, and hierarchical. The single authority system has a CA at the top that creates and issues certs. Users then trust each other based on the CA at the top vouching for them. Assuming a single authority model is used, it’s of vital importance to protect it. After all, if it is compromised, your whole system is kaput.
![]() A is incorrect because “stand-alone CA” doesn’t refer to a trust model. It instead defines a single CA that is usually set up as a trusted offline root in a hierarchy or when extranets and the Internet are involved.
A is incorrect because “stand-alone CA” doesn’t refer to a trust model. It instead defines a single CA that is usually set up as a trusted offline root in a hierarchy or when extranets and the Internet are involved.
![]() B is incorrect because web of trust refers to a model where users create and manage their own certificates and key exchange and multiple entities sign certificates for one another. In other words, users within this system trust each other based on certificates they receive from other users on the same system.
B is incorrect because web of trust refers to a model where users create and manage their own certificates and key exchange and multiple entities sign certificates for one another. In other words, users within this system trust each other based on certificates they receive from other users on the same system.
![]() D is incorrect because although a hierarchical trust system also has a CA at the top (which is known as the root CA), it makes use of one or more intermediate CAs underneath it—known as RAs—to issue and manage certificates. This system is the most secure because users can track the certificate back to the root to ensure authenticity without a single point of failure.
D is incorrect because although a hierarchical trust system also has a CA at the top (which is known as the root CA), it makes use of one or more intermediate CAs underneath it—known as RAs—to issue and manage certificates. This system is the most secure because users can track the certificate back to the root to ensure authenticity without a single point of failure.
24. A portion of a digital certificate is shown here:
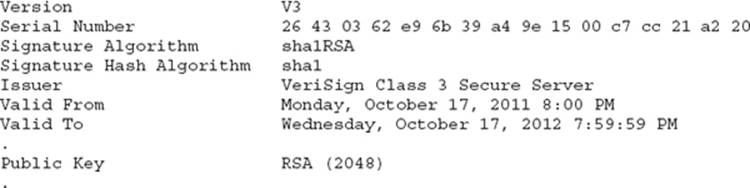
Which of the following statements is true?
A. The hash created for the digital signature holds 160 bits.
B. The hash created for the digital signature holds 2,048 bits.
C. RSA is the hash algorithm used for the digital signature.
D. This certificate contains a private key.
![]() A. Questions on the digital certificate are usually easy enough, and this is no exception. The algorithm used to create the hash is clearly defined as Signature Hash Algorithm (SHA-1), and, as we already know, SHA-1 creates a 160-bit hash output. This will then be encrypted by the sender’s private key and decrypted on the recipient’s end with the public key, thus verifying identity.
A. Questions on the digital certificate are usually easy enough, and this is no exception. The algorithm used to create the hash is clearly defined as Signature Hash Algorithm (SHA-1), and, as we already know, SHA-1 creates a 160-bit hash output. This will then be encrypted by the sender’s private key and decrypted on the recipient’s end with the public key, thus verifying identity.
![]() B is incorrect as a distractor because the RSA key size of 2,048 is listed in the public key section of the certificate.
B is incorrect as a distractor because the RSA key size of 2,048 is listed in the public key section of the certificate.
![]() C incorrect because RSA is not a hash algorithm. It is, without doubt, used as an encryption algorithm with this certificate (and uses a 2,048-bit key to do so) but does not hash anything.
C incorrect because RSA is not a hash algorithm. It is, without doubt, used as an encryption algorithm with this certificate (and uses a 2,048-bit key to do so) but does not hash anything.
![]() D is incorrect because (as I’m certain you are already aware) a private key is never shared. The public key is contained for recipients to use if they want to encrypt something to send back to the originator, but the private key is never shared.
D is incorrect because (as I’m certain you are already aware) a private key is never shared. The public key is contained for recipients to use if they want to encrypt something to send back to the originator, but the private key is never shared.
25. Two bit strings are run through an XOR operation. Which of the following is a true statement for each bit pair regarding this function?
A. If the first value is 0 and the second value is 1, then the output is 0.
B. If the first value is 1 and the second value is 0, then the output is 0.
C. If the first value is 0 and the second value is 0, then the output is 1.
D. If the first value is 1 and the second value is 1, then the output is 0.
![]() D. An XOR operation requires two inputs, and in the case of encryption algorithms, this would be the data bits and the key bits. Each bit is fed into the operation—one from the data, the next from the key—and then XOR makes a determination: If the bits match, the output is 0; if they don’t, it’s 1.
D. An XOR operation requires two inputs, and in the case of encryption algorithms, this would be the data bits and the key bits. Each bit is fed into the operation—one from the data, the next from the key—and then XOR makes a determination: If the bits match, the output is 0; if they don’t, it’s 1.
![]() A is incorrect because the two values being compared are different; therefore, the output would be 1.
A is incorrect because the two values being compared are different; therefore, the output would be 1.
![]() B is incorrect because the two values being compared are different; therefore, the output would be 1.
B is incorrect because the two values being compared are different; therefore, the output would be 1.
![]() C is incorrect because the two values being compared are the same; therefore, the output should be 0.
C is incorrect because the two values being compared are the same; therefore, the output should be 0.
26. Which of the following attacks attempts to re-send a portion of a cryptographic exchange in hopes of setting up a communications channel?
A. Known plain text
B. Chosen plain text
C. Man in the middle
D. Replay
![]() D. Replay attacks are most often performed within the context of a man-in-the-middle attack and not necessarily just for communications channel setup. They’re also used for DoS attacks against a system, to feed bad data in hopes of corrupting a system, to try to overflow a buffer (send more encrypted data than expected), and so on. The hacker repeats a portion of a cryptographic exchange in hopes of fooling the system into setting up a communications channel. The attacker doesn’t really have to know the actual data (such as the password) being exchanged; he just has to get the timing right in copying and then replaying the bit stream. Session tokens can be used in the communications process to combat this attack.
D. Replay attacks are most often performed within the context of a man-in-the-middle attack and not necessarily just for communications channel setup. They’re also used for DoS attacks against a system, to feed bad data in hopes of corrupting a system, to try to overflow a buffer (send more encrypted data than expected), and so on. The hacker repeats a portion of a cryptographic exchange in hopes of fooling the system into setting up a communications channel. The attacker doesn’t really have to know the actual data (such as the password) being exchanged; he just has to get the timing right in copying and then replaying the bit stream. Session tokens can be used in the communications process to combat this attack.
![]() A is incorrect because known plain text doesn’t really have anything to do with this scenario. Known plain text refers to having both plain-text and corresponding cipher-text messages, which are scanned for repeatable sequences and then compared to the cipher-text versions.
A is incorrect because known plain text doesn’t really have anything to do with this scenario. Known plain text refers to having both plain-text and corresponding cipher-text messages, which are scanned for repeatable sequences and then compared to the cipher-text versions.
![]() B is incorrect because it simply doesn’t apply to this scenario. In a chosen plain-text attack, a hacker puts several encrypted messages through statistical analysis to determine repeating code.
B is incorrect because it simply doesn’t apply to this scenario. In a chosen plain-text attack, a hacker puts several encrypted messages through statistical analysis to determine repeating code.
![]() C is incorrect because, in this instance, replay refers to the attack being described in the question, not man in the middle. I know you think this is confusing, and I do understand. However, this is an example of CEH wordplay you’ll need to be familiar with. Man in the middle is usually listed as an attack by every security guide; however, within the context of the exam, it may also refer solely to where the attacker has positioned himself. From this location, he can launch a variety of attacks—replay being one of them.
C is incorrect because, in this instance, replay refers to the attack being described in the question, not man in the middle. I know you think this is confusing, and I do understand. However, this is an example of CEH wordplay you’ll need to be familiar with. Man in the middle is usually listed as an attack by every security guide; however, within the context of the exam, it may also refer solely to where the attacker has positioned himself. From this location, he can launch a variety of attacks—replay being one of them.
27. Within a PKI system, which of the following is an accurate statement?
A. Bill can be sure a message came from Sue by using his public key to decrypt it.
B. Bill can be sure a message came from Sue by using his private key to decrypt it.
C. Bill can be sure a message came from Sue by using her private key to decrypt the digital signature.
D. Bill can be sure a message came from Sue by using her public key to decrypt the digital signature.
![]() D. Remember, a digital signature is a hash value that is encrypted with the user’s private key. Because the corresponding public key can decrypt it, this provides the nonrepudiation feature we’re looking for. This is the only instance on the exam where the private key is used for encryption. In general, public encrypts, and private decrypts.
D. Remember, a digital signature is a hash value that is encrypted with the user’s private key. Because the corresponding public key can decrypt it, this provides the nonrepudiation feature we’re looking for. This is the only instance on the exam where the private key is used for encryption. In general, public encrypts, and private decrypts.
![]() A is incorrect because not only does this have nothing to do with proving identity, but it also cannot work. Bill can’t use his own public key to decrypt a message sent to him. The keys work in pairs—if the message is encrypted with his public key, only his private key can decrypt it.
A is incorrect because not only does this have nothing to do with proving identity, but it also cannot work. Bill can’t use his own public key to decrypt a message sent to him. The keys work in pairs—if the message is encrypted with his public key, only his private key can decrypt it.
![]() B is incorrect because this has nothing to do with proving Sue’s identity. Sure, Bill will be using his own private key to decrypt messages sent to him by other users; however, it doesn’t provide any help in proving identity.
B is incorrect because this has nothing to do with proving Sue’s identity. Sure, Bill will be using his own private key to decrypt messages sent to him by other users; however, it doesn’t provide any help in proving identity.
![]() C is incorrect because there is no way Bill should have Sue’s private key. Remember, private keys are not shared with anyone, for any reason. This is why encrypting a hash with it works so well for the digital signing process.
C is incorrect because there is no way Bill should have Sue’s private key. Remember, private keys are not shared with anyone, for any reason. This is why encrypting a hash with it works so well for the digital signing process.
28. Which of the following could be considered a drawback to using AES with a 256-bit key to share sensitive data?
A. The key size requires a long time to encrypt and decrypt messages.
B. It’s a complex algorithm that requires intense system configuration.
C. AES is a weak cypher.
D. Each recipient must receive the key through a different channel than the message.
![]() D. AES is a strong and fast encryption algorithm established by NIST and adopted by the U.S. government to replace DES. The only real drawback is it is symmetric in nature, meaning the key used to encrypt and decrypt is the same. To use AES, you’d have to find some other way to exchange the key securely, separate from the message itself. This is why most secured communications make use of both symmetric and asymmetric cyphers to get a job done.
D. AES is a strong and fast encryption algorithm established by NIST and adopted by the U.S. government to replace DES. The only real drawback is it is symmetric in nature, meaning the key used to encrypt and decrypt is the same. To use AES, you’d have to find some other way to exchange the key securely, separate from the message itself. This is why most secured communications make use of both symmetric and asymmetric cyphers to get a job done.
![]() A is incorrect because symmetric algorithms are fast, and the key size of 256 does not slow it down at all.
A is incorrect because symmetric algorithms are fast, and the key size of 256 does not slow it down at all.
![]() B is incorrect because there is no more configuration efforts required for AES than there is for any other.
B is incorrect because there is no more configuration efforts required for AES than there is for any other.
![]() C is incorrect because AES is not a weak cypher. It’s adopted by the U.S. government and recognized as a strong encryption method—so long as the key is transmitted appropriately.
C is incorrect because AES is not a weak cypher. It’s adopted by the U.S. government and recognized as a strong encryption method—so long as the key is transmitted appropriately.
29. One use of hash algorithms is for the secure storage of passwords: The password is run through a one-way hash, and the value is stored instead of the plain-text version. If a hacker gains access to these hash values and knows the hash algorithm used to create them, which of the following could be used to speed up his effort in cracking them?
A. Salt
B. Rainbow tables
C. Steganography
D. Collision
![]() B. Rainbow tables are the result of a lot of effort in putting all known combinations of plain-text entries into a hash, one at a time, and capturing the hash value that’s created. Then, instead of having to brute force your way in and spending countless computational cycles, you can simply compare the hash value you stole from the password file to the rainbow table—once you find a match, voilà! Rainbow tables may be largely replaced in the real world, with the advent of massive computational offerings like FPGAs and GPUs, but they’re still relevant for your exam.
B. Rainbow tables are the result of a lot of effort in putting all known combinations of plain-text entries into a hash, one at a time, and capturing the hash value that’s created. Then, instead of having to brute force your way in and spending countless computational cycles, you can simply compare the hash value you stole from the password file to the rainbow table—once you find a match, voilà! Rainbow tables may be largely replaced in the real world, with the advent of massive computational offerings like FPGAs and GPUs, but they’re still relevant for your exam.
![]() A is incorrect because a salt is used to increase security on a password hash, not to crack it. A salt is a collection of random bits used as a key in addition to the hashing algorithm. Because the bits, and length, are random, a good salt makes a collision attack difficult to pull off.
A is incorrect because a salt is used to increase security on a password hash, not to crack it. A salt is a collection of random bits used as a key in addition to the hashing algorithm. Because the bits, and length, are random, a good salt makes a collision attack difficult to pull off.
![]() C is incorrect because steganography simply makes no sense here. Steganography involves hiding messages inside another medium—for example, hiding a message inside a .jpg file.
C is incorrect because steganography simply makes no sense here. Steganography involves hiding messages inside another medium—for example, hiding a message inside a .jpg file.
![]() D is incorrect because although the entire effort is in finding the correct collision to unlock the plain-text version, the collision itself isn’t an effort to speed things up.
D is incorrect because although the entire effort is in finding the correct collision to unlock the plain-text version, the collision itself isn’t an effort to speed things up.