CISSP Practice Exams, Third Edition (2015)
CHAPTER 10
Security Operations
This domain includes questions from the following topics:
• Administrative management responsibilities
• Operations department responsibilities
• Configuration management
• Trusted recovery states
• Redundancy and fault-tolerant systems
• E-mail security
• Threats to operations security
Operations security consists of the routine tasks involved with maintaining a network and its systems after they are developed and implemented. It includes ensuring that entities have the proper access privileges, that oversight is implemented, that network and systems run correctly and securely, and that applications are running in a secure and protected manner. It is also a very important topic, because as networks and computing environments continually evolve, individuals responsible for security operations must respond accordingly.
Q QUESTIONS
1. Which of the following is not a common component of configuration management change control steps?
A. Tested and presented
B. Service-level agreement approval
C. Report change to management
D. Approval of the change
2. A change management process should include a number of procedures. Which of the following incorrectly describes a characteristic or component of a change control policy?
A. Changes that are unanimously approved by the change control committee must be tested to uncover any unforeseen results.
B. Changes approved by the change control committee should be entered into a change log.
C. A schedule that outlines the projected phases of the change should be developed.
D. An individual or group should be responsible for approving proposed changes.
3. The requirement of erasure is the end of the media life cycle if it contains sensitive information. Which of the following best describes purging?
A. Changing the polarization of the atoms on the media.
B. It is uacceptable when media are to be reused in the same physical environment for the same purposes.
C. Data formerly on the media is made unrecoverable by overwriting it with a pattern.
D. Information is made unrecoverable, even with extraordinary effort.
4. Device backup and other availability solutions are chosen to balance the value of having information available against the cost of keeping that information available. Which of the following best describes fault-tolerant technologies?
A. They are among the most expensive solutions and are usually only for the most mission-critical information.
B. They help service providers identify appropriate availability services for the specific customer.
C. They are required to maintain integrity, regardless of the other technologies in place.
D. They allow a failed component to be replaced while the system continues to run.
5. Which of the following refers to the amount of time it will be expected to take to get a device fixed and back into production?
A. SLA
B. MTTR
C. Hot-swap
D. MTBF
6. Which of the following correctly describes Direct Access and Sequential Access storage devices?
A. Any point on a Direct Access Storage Device may be promptly reached, whereas every point in between the current position and the desired position of a Sequential Access Storage Device must be traversed in order to reach the desired position.
B. RAIT is an example of a Direct Access Storage Device, while RAID is an example of a Sequential Access Storage Device.
C. MAID is a Direct Access Storage Device, while RAID is an example of a Sequential Access Storage Device.
D. As an example of Sequential Access Storage, tape drives are faster than Direct Access Storage Devices.
7. A company has decided that it no longer wants to maintain its own servers and network environment because of increasing costs and liabilities. The company wants to move to a cloud-based solution, but needs to determine which type of solution best fits its needs. Which of the following provides a correct definition and mapping of a typical cloud-based solution?
A. Infrastructure as a Service is provided when a cloud provider delivers a computing platform that includes operating system, database, and web servers.
B. Software as a Service is provided when a cloud provider delivers an infrastructure environment similar to a traditional data center.
C. Platform as a Service is provided when a cloud provider delivers a computing platform that can include operating system, database and web servers.
D. Software as a Service is provided when a cloud provider delivers a software environment in the form of a computing platform.
8. Various levels of RAID dictate the type of activity that will take place within the RAID system. Which level is associated with byte-level parity?
A. RAID Level 0
B. RAID Level 3
C. RAID Level 5
D. RAID Level 10
9. Which of the following incorrectly describes IP spoofing and session hijacking?
A. Address spoofing helps an attacker to hijack sessions between two users without being noticed.
B. IP spoofing makes it harder to track down an attacker.
C. Session hijacking can be prevented with mutual authentication.
D. IP spoofing is used to hijack SSL and IPSec secure communications.
10. RAID systems use a number of techniques to provide redundancy and performance. Which of the following activities divides and writes data over several drives?
A. Parity
B. Mirroring
C. Striping
D. Hot-swapping
11. What is the difference between hierarchical storage management and storage area network technologies?
A. HSM uses optical or tape jukeboxes, and SAN is a standard of how to develop and implement this technology.
B. HSM and SAN are one and the same. The difference is in the implementation.
C. HSM uses optical or tape jukeboxes, and SAN is a network of connected storage.
D. SAN uses optical or tape jukeboxes, and HSM is a network of connected storage systems.
12. John and his team are conducting a penetration test of a client’s network. The team will conduct its testing armed only with knowledge it acquired from the Web. The network staff is aware that the testing will take place, but the penetration testing team will only work with publicly available data and some information from the client. What is the degree of the team’s knowledge and what type of test is the team carrying out?
A. Full knowledge; blind test
B. Partial knowledge; blind test
C. Partial knowledge; double-blind test
D. Zero knowledge; targeted test
13. What type of exploited vulnerability allows more input than the program has allocated space to store it?
A. Symbolic links
B. File descriptors
C. Kernel flaws
D. Buffer overflows
14. There are often scenarios where the IT staff must react to emergencies and quickly apply fixes or change configurations. When dealing with such emergencies, which of the following is the best approach to making changes?
A. Review the changes within 48 hours of making them.
B. Review and document the emergency changes after the incident is over.
C. Activity should not take place in this manner.
D. Formally submit the change to a change control committee and follow the complete change control process.
15. A small medical institution’s IT security team has become overwhelmed with having to operate and maintain IDS, firewalls, enterprise-wide antivirus solutions, data leakage prevention technologies, and centralized log management. Which of the following best describes what type of solution this organization should implement to allow for standardized and streamlined security operations?
A. Unified threat management
B. Continuous monitoring technology
C. Centralized access control systems
D. Cloud-based security solution
16. Fred is a new security officer who wants to implement a control for detecting and preventing users who attempt to exceed their authority by misusing the access rights that have been assigned to them. Which of the following best fits this need?
A. Management review
B. Two-factor identification and authentication
C. Capturing this data in audit logs
D. Implementation of a strong security policy
17. Which of the following is the best way to reduce brute-force attacks that allow intruders to uncover users’ passwords?
A. Increase the clipping level.
B. Lock out an account for a certain amount of time after the clipping level is reached.
C. After a threshold of failed login attempts is met, the administrator must physically lock out the account.
D. Choose a weaker algorithm that encrypts the password file.
18. Brandy could not figure out how Sam gained unauthorized access to her system, since he has little computer experience. Which of the following is most likely the attack Sam used?
A. Dictionary attack
B. Shoulder surfing attack
C. Covert channel attack
D. Timing attack
19. The relay agent on a mail server plays a role in spam prevention. Which of the following incorrectly describes mail relays?
A. Antispam features on mail servers are actually antirelaying features.
B. Relays should be configured “wide open” to receive any e-mail message.
C. Relay agents are used to send messages from one mail server to another.
D. If a relay is configured “wide open,” the mail server can be used to send spam.
20. John is responsible for providing a weekly report to his manager outlining the week’s security incidents and mitigation steps. What steps should he take if a report has no information?
A. Send his manager an e-mail telling her so.
B. Deliver last week’s report and make sure it’s clearly dated.
C. Deliver a report that states “No output.”
D. Don’t do anything.
21. Brian, a security administrator, is responding to a virus infection. The antivirus application reports that a file has been infected with a dangerous virus and disinfecting it could damage the file. What course of action should Brian take?
A. Replace the file with the file saved from the day before.
B. Disinfect the file and contact the vendor.
C. Restore an uninfected version of the patched file from backup media.
D. Back up the data and disinfect the file.
22. Guidelines should be followed to allow secure remote administration. Which of the following is not one of those guidelines?
A. A small number of administrators should be allowed to carry out remote functionality.
B. Critical systems should be administered locally instead of remotely.
C. Strong authentication should be in place.
D. Telnet should be used to send commands and data.
23. In a redundant array of inexpensive disks (RAID) systems, data and parity information are striped over several different disks. What is parity information used for?
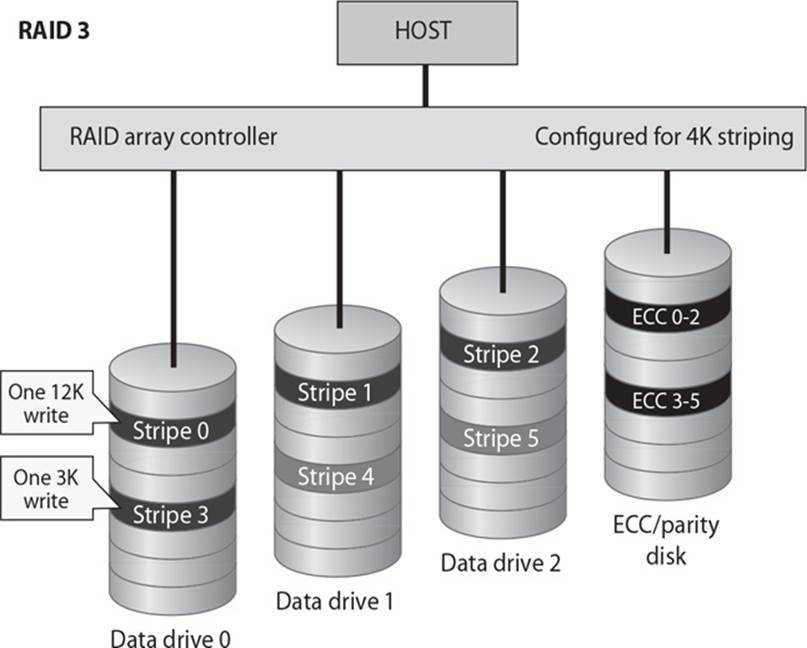
A. Information used to create new data
B. Information used to erase data
C. Information used to rebuild data
D. Information used to build data
24. Mirroring of drives is when data is written to two drives at once for redundancy purposes. What similar type of technology is shown in the graphic that follows?
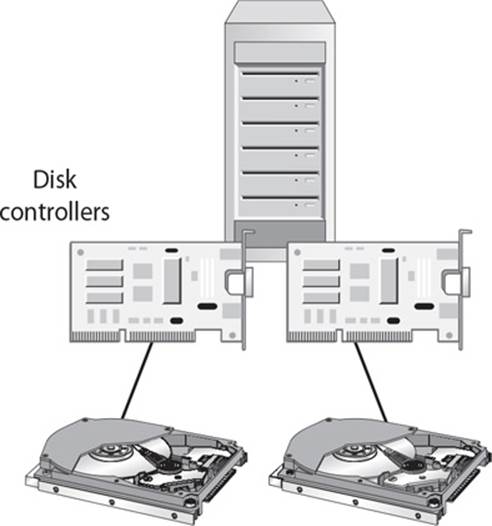
A. Direct access storage
B. Disk duplexing
C. Striping
D. Massive array of inactive disks
25. There are several different types of important architectures within backup technologies. Which architecture does the graphic that follows represent?
A. Clustering
B. Grid computing
C. Backup tier security
D. Hierarchical Storage Management
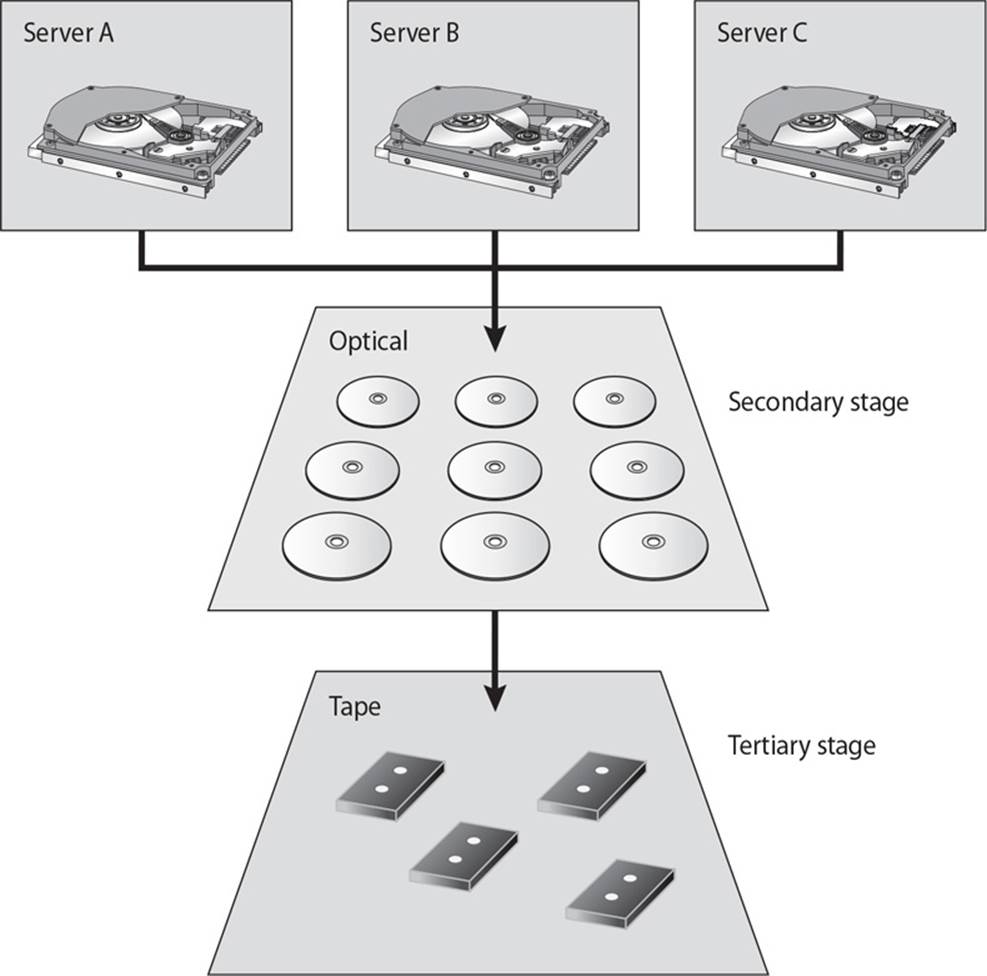
26. Which of the following is not considered a countermeasure to port scanning and operating system fingerprinting?
A. Allow access at the perimeter network to all internal ports
B. Remove as many banners as possible within operating systems and applications
C. Use TCP wrappers on vulnerable services that have to be available
D. Disable unnecessary ports and services
27. ___________ provides for availability and scalability. It groups physically different systems and combines them logically, which helps to provide immunity to faults and improves performance.
A. Disc duping
B. Clustering
C. RAID
D. Virtualization
28. Bob is a new security administrator at a financial institution. The organization has experienced some suspicious activity on one of the critical servers that contain customer data. When reviewing how the systems are administered, he uncovers some concerning issues pertaining to remote administration. Which of the following should not be put into place to reduce these concerns?
i. Commands and data should not be sent in cleartext.
ii. SSH should be used, not Telnet.
iii. Truly critical systems should be administered locally instead of remotely.
iv. Only a small number of administrators should be able to carry out remote functionality.
v. Strong authentication should be in place for any administration activities.
A. i, ii
B. None of them
C. ii, iv
D. All of them
The following scenario will be used for questions 29 and 30.
John is a network administrator and has been told by one of his network staff members that two servers on the network have recently had suspicious traffic traveling to them and then from them in a sporadic manner. The traffic has been mainly ICMP, but the patterns were unusual compared to other servers over the last 30 days. John lists the directories and subdirectories on the systems and finds nothing unusual. He inspects the running processes and again finds nothing suspicious. He sees that the systems’ NICs are not in promiscuous mode, so he is assured that sniffers have not been planted.
29. Which of the following describes the most likely situation as described in this scenario?
A. Servers are not infected, but the traffic illustrates attack attempts.
B. Servers have been infected with rootkits.
C. Servers are vulnerable and need to be patched.
D. Servers have been infected by spyware.
30. Which of the following best explains why John does not see anything suspicious on the reported systems?
A. The systems have not yet been infected.
B. He is not running the correct tools. He needs to carry out a penetration test on the two systems.
C. Trojaned files have been loaded and executed.
D. A back door has been installed and the attacker enters the system sporadically.
QUICK ANSWER KEY
1. B
2. A
3. D
4. A
5. B
6. A
7. C
8. B
9. D
10. C
11. C
12. B
13. D
14. B
15. A
16. A
17. B
18. B
19. B
20. C
21. C
22. D
23. C
24. B
25. D
26. A
27. B
28. B
29. B
30. C
A ANSWERS
1. Which of the following is not a common component of configuration management change control steps?
A. Tested and presented
B. Service-level agreement approval
C. Report change to management
D. Approval of the change
![]() B. A well-structured change management process should be established to aid staff members through many different types of changes to the environment. This process should be laid out in the change control policy. Although the types of changes vary, a standard list of procedures can help keep the process under control and ensure it is carried out in a predictable manner. A change control policy should include procedures for requesting a change to take place, approving the change, documentation of the change, testing and presentation, implementation, and reporting the change to management. Configuration management change control processes do not commonly have an effect on service-level agreement approvals.
B. A well-structured change management process should be established to aid staff members through many different types of changes to the environment. This process should be laid out in the change control policy. Although the types of changes vary, a standard list of procedures can help keep the process under control and ensure it is carried out in a predictable manner. A change control policy should include procedures for requesting a change to take place, approving the change, documentation of the change, testing and presentation, implementation, and reporting the change to management. Configuration management change control processes do not commonly have an effect on service-level agreement approvals.
![]() A is incorrect because testing and presentation should be included in a standard change control policy. All changes must be fully tested to uncover any unforeseen results. Depending on the severity of the change and the company’s organization, the change and implementation may need to be presented to a change control committee. This helps show different sides to the purpose and outcome of the change and the possible ramifications.
A is incorrect because testing and presentation should be included in a standard change control policy. All changes must be fully tested to uncover any unforeseen results. Depending on the severity of the change and the company’s organization, the change and implementation may need to be presented to a change control committee. This helps show different sides to the purpose and outcome of the change and the possible ramifications.
![]() C is incorrect because a procedure for reporting a change to management should be included in a standard change control policy. After a change is implemented, a full report summarizing the change should be submitted to management. This report can be submitted on a periodic basis to keep management up to date and ensure continual support.
C is incorrect because a procedure for reporting a change to management should be included in a standard change control policy. After a change is implemented, a full report summarizing the change should be submitted to management. This report can be submitted on a periodic basis to keep management up to date and ensure continual support.
![]() D is incorrect because a procedure for obtaining approval for the change should be included in a standard change control policy. The individual requesting the change must justify the reasons and clearly show the benefits and possible pitfalls of the change. Sometimes the requester is asked to conduct more research and provide more information before the change is approved.
D is incorrect because a procedure for obtaining approval for the change should be included in a standard change control policy. The individual requesting the change must justify the reasons and clearly show the benefits and possible pitfalls of the change. Sometimes the requester is asked to conduct more research and provide more information before the change is approved.
2. A change management process should include a number of procedures. Which of the following incorrectly describes a characteristic or component of a change control policy?
A. Changes that are unanimously approved by the change control committee must be tested to uncover any unforeseen results.
B. Changes approved by the change control committee should be entered into a change log.
C. A schedule that outlines the projected phases of the change should be developed.
D. An individual or group should be responsible for approving proposed changes.
![]() A. A well-structured change management process should be put into place to aid staff members through many different types of changes to the environment. This process should be laid out in the change control policy. Although the types of changes vary, a standard list of procedures can help keep the process under control and ensure it is carried out in a predictable manner. All changes approved by the change control committee must be fully tested to uncover any unforeseen results. Depending on the severity of the change and the company’s organization, the change and implementation may need to be presented to a change control committee. This helps show different sides to the purpose and outcome of the change and the possible ramifications.
A. A well-structured change management process should be put into place to aid staff members through many different types of changes to the environment. This process should be laid out in the change control policy. Although the types of changes vary, a standard list of procedures can help keep the process under control and ensure it is carried out in a predictable manner. All changes approved by the change control committee must be fully tested to uncover any unforeseen results. Depending on the severity of the change and the company’s organization, the change and implementation may need to be presented to a change control committee. This helps show different sides to the purpose and outcome of the change and the possible ramifications.
![]() B is incorrect because it is true that changes approved by the change control committee should be entered into a change log. The log should be updated as the process continues toward completion. It is important to track and document all changes that are approved and implemented.
B is incorrect because it is true that changes approved by the change control committee should be entered into a change log. The log should be updated as the process continues toward completion. It is important to track and document all changes that are approved and implemented.
![]() C is incorrect because once a change is fully tested and approved, a schedule should be developed that outlines the projected phases of the change being implemented and the necessary milestones. These steps should be fully documented, and progress should be monitored.
C is incorrect because once a change is fully tested and approved, a schedule should be developed that outlines the projected phases of the change being implemented and the necessary milestones. These steps should be fully documented, and progress should be monitored.
![]() D is incorrect because requests should be presented to an individual or group that is responsible for approving changes and overseeing the activities of changes that take place within an environment.
D is incorrect because requests should be presented to an individual or group that is responsible for approving changes and overseeing the activities of changes that take place within an environment.
3. The requirement of erasure is the end of the media life cycle if it contains sensitive information. Which of the following best describes purging?
A. Changing the polarization of the atoms on the media.
B. It is uacceptable when media are to be reused in the same physical environment for the same purposes.
C. Data formerly on the media is made unrecoverable by overwriting it with a pattern.
D. Information is made unrecoverable, even with extraordinary effort.
![]() D. Purging is the removal of sensitive data from a system, storage device, or peripheral device with storage capacity at the end of a processing period. This action is performed in such a way that there is assurance proportional to the sensitivity of the data that the data cannot be reconstructed. Deleting files on a medium does not actually make the data disappear; it only deletes the pointers to where the data in those files still live on the medium. This is how companies that specialize in restoration can recover the deleted files intact after they have been apparently/accidentally destroyed. Even simply overwriting media with new information may not eliminate the possibility of recovering the previously written information. This is why zeroization and secure overwriting algorithms are required. And, if any part of a medium containing highly sensitive information cannot be cleared or purged, then physical destruction must take place.
D. Purging is the removal of sensitive data from a system, storage device, or peripheral device with storage capacity at the end of a processing period. This action is performed in such a way that there is assurance proportional to the sensitivity of the data that the data cannot be reconstructed. Deleting files on a medium does not actually make the data disappear; it only deletes the pointers to where the data in those files still live on the medium. This is how companies that specialize in restoration can recover the deleted files intact after they have been apparently/accidentally destroyed. Even simply overwriting media with new information may not eliminate the possibility of recovering the previously written information. This is why zeroization and secure overwriting algorithms are required. And, if any part of a medium containing highly sensitive information cannot be cleared or purged, then physical destruction must take place.
![]() A is incorrect because it describes degaussing, which is an example of purging. A device that performs degaussing generates a coercive magnetic force that reduces the magnetic flux density of the storage media to zero. This magnetic force is what properly erases data from media. Data is stored on magnetic media by the representation of the polarization of the atoms. Degaussing changes this polarization by using a type of large magnet to bring it back to its original flux (magnetic alignment).
A is incorrect because it describes degaussing, which is an example of purging. A device that performs degaussing generates a coercive magnetic force that reduces the magnetic flux density of the storage media to zero. This magnetic force is what properly erases data from media. Data is stored on magnetic media by the representation of the polarization of the atoms. Degaussing changes this polarization by using a type of large magnet to bring it back to its original flux (magnetic alignment).
![]() B is incorrect because purging is required when media will be repurposed to a different compartment. When media are erased (cleared of their contents), they are said to be sanitized. This means erasing information so that it is not readily retrieved using routine operating system commands or commercially available forensic/data recovery software.
B is incorrect because purging is required when media will be repurposed to a different compartment. When media are erased (cleared of their contents), they are said to be sanitized. This means erasing information so that it is not readily retrieved using routine operating system commands or commercially available forensic/data recovery software.
![]() C is incorrect because it describes zeroization, which is an example of purging but does not describe purging itself. Media holding sensitive data must be properly purged, which can be accomplished through zeroization, degaussing, or media destruction.
C is incorrect because it describes zeroization, which is an example of purging but does not describe purging itself. Media holding sensitive data must be properly purged, which can be accomplished through zeroization, degaussing, or media destruction.
4. Device backup and other availability solutions are chosen to balance the value of having information available against the cost of keeping that information available. Which of the following best describes fault-tolerant technologies?
A. They are among the most expensive solutions and are usually only for the most mission-critical information.
B. They help service providers identify appropriate availability services for the specific customer.
C. They are required to maintain integrity, regardless of the other technologies in place.
D. They allow a failed component to be replaced while the system continues to run.
![]() A. Fault-tolerant technologies keep information available not only against individual storage device faults but even against whole system failures. Fault tolerance is among the most expensive possible solutions for availability and is commonly justified only for the most mission-critical information. All technology will eventually experience a failure of some form. A company that would suffer irreparable harm from any unplanned downtime can justify paying the high cost for fault-tolerant systems.
A. Fault-tolerant technologies keep information available not only against individual storage device faults but even against whole system failures. Fault tolerance is among the most expensive possible solutions for availability and is commonly justified only for the most mission-critical information. All technology will eventually experience a failure of some form. A company that would suffer irreparable harm from any unplanned downtime can justify paying the high cost for fault-tolerant systems.
![]() B is incorrect because service-level agreements (SLAs) help service providers, whether they are an internal IT operation or an outsourcer, decide what type of availability technology and service is appropriate. From this determination, the price of a service or the budget of the IT operation can be set. The process of developing an SLA with a business is also beneficial to the business. While some businesses have performed this type of introspection on their own, many have not, and being forced to go through the exercise as part of budgeting for their internal IT operations or external sourcing helps the business understand the real value of its information.
B is incorrect because service-level agreements (SLAs) help service providers, whether they are an internal IT operation or an outsourcer, decide what type of availability technology and service is appropriate. From this determination, the price of a service or the budget of the IT operation can be set. The process of developing an SLA with a business is also beneficial to the business. While some businesses have performed this type of introspection on their own, many have not, and being forced to go through the exercise as part of budgeting for their internal IT operations or external sourcing helps the business understand the real value of its information.
![]() C is incorrect because fault-tolerant technologies do not necessarily have anything to do with data or system integrity.
C is incorrect because fault-tolerant technologies do not necessarily have anything to do with data or system integrity.
![]() D is incorrect because “hot-swappable” hardware does not require shutting down the system and may or may not be considered a fault-tolerant technology. Hot-swapping allows the administrator to replace the failed component while the system continues to run and information remains available; usually degraded performance results, but unplanned downtime is avoided.
D is incorrect because “hot-swappable” hardware does not require shutting down the system and may or may not be considered a fault-tolerant technology. Hot-swapping allows the administrator to replace the failed component while the system continues to run and information remains available; usually degraded performance results, but unplanned downtime is avoided.
5. Which of the following refers to the amount of time it will be expected to take to get a device fixed and back into production?
A. SLA
B. MTTR
C. Hot swap
D. MTBF
![]() B. Mean time to repair (MTTR) is the amount of time it will be expected to take to get a device fixed and back into production. For a hard drive in a redundant array, the MTTR is the amount of time between the actual failure and the time when, after noticing the failure, someone has replaced the failed drive and the redundant array has completed rewriting the information on the new drive. This is likely to be measured in hours. For a nonredundant hard drive in a desktop PC, the MTTR is the amount of time between when the drive goes down and the time when the replaced hard drive has been reloaded with the operating system, software, and any backed-up data belonging to the user. This is likely to be measured in days. For an unplanned reboot, the MTTR is the amount of time between the failure of the system and the point in time when it has rebooted its operating system, checked the state of its disks, restarted its applications, allowed its applications to check the consistency of their data, and once again begun processing transactions.
B. Mean time to repair (MTTR) is the amount of time it will be expected to take to get a device fixed and back into production. For a hard drive in a redundant array, the MTTR is the amount of time between the actual failure and the time when, after noticing the failure, someone has replaced the failed drive and the redundant array has completed rewriting the information on the new drive. This is likely to be measured in hours. For a nonredundant hard drive in a desktop PC, the MTTR is the amount of time between when the drive goes down and the time when the replaced hard drive has been reloaded with the operating system, software, and any backed-up data belonging to the user. This is likely to be measured in days. For an unplanned reboot, the MTTR is the amount of time between the failure of the system and the point in time when it has rebooted its operating system, checked the state of its disks, restarted its applications, allowed its applications to check the consistency of their data, and once again begun processing transactions.
![]() A is incorrect because a service-level agreement (SLA) addresses the degree of availability that will be provided to a customer, whether that customer be an internal department within the same organization or an external customer. The MTTR is the amount of time it will be expected to get a device fixed and back into production. The MTTR may pertain to fixing a component or the device or replacing the device.
A is incorrect because a service-level agreement (SLA) addresses the degree of availability that will be provided to a customer, whether that customer be an internal department within the same organization or an external customer. The MTTR is the amount of time it will be expected to get a device fixed and back into production. The MTTR may pertain to fixing a component or the device or replacing the device.
![]() C is incorrect because hot-swapping refers to the replacement of a failed component while the system continues to run and information remains available. Usually degraded performance results, but unplanned downtime is avoided. Hot-swapping does not refer to the amount of time needed to get a system back up and running.
C is incorrect because hot-swapping refers to the replacement of a failed component while the system continues to run and information remains available. Usually degraded performance results, but unplanned downtime is avoided. Hot-swapping does not refer to the amount of time needed to get a system back up and running.
![]() D is incorrect because MTBF refers to mean time between failure, which is the estimated lifespan of a piece of equipment. It is calculated by the vendor of the equipment or a third party. The reason for using this value is to know approximately when a particular device will need to be replaced. It is used as a benchmark for reliability by predicting the average time that will pass in the operation of a component or a system until it needs to be replaced.
D is incorrect because MTBF refers to mean time between failure, which is the estimated lifespan of a piece of equipment. It is calculated by the vendor of the equipment or a third party. The reason for using this value is to know approximately when a particular device will need to be replaced. It is used as a benchmark for reliability by predicting the average time that will pass in the operation of a component or a system until it needs to be replaced.
6. Which of the following correctly describes Direct Access and Sequential Access storage devices?
A. Any point on a Direct Access Storage Device may be promptly reached, whereas every point in between the current position and the desired position of a Sequential Access Storage Device must be traversed in order to reach the desired position.
B. RAIT is an example of a Direct Access Storage Device, while RAID is an example of a Sequential Access Storage Device.
C. MAID is a Direct Access Storage Device, while RAID is an example of a Sequential Access Storage Device.
D. As an example of Sequential Access Storage, tape drives are faster than Direct Access Storage Devices.
![]() A. Direct Access Storage Device (DASD) is a general term for magnetic disk storage devices, which historically have been used in mainframe and minicomputer (mid-range computer) environments. A redundant array of independent disks (RAID) is a type of DASD. The key distinction between Direct Access and Sequential Access storage devices is that any point on a Direct Access Storage Device may be promptly reached, whereas every point in between the current position and the desired position of a Sequential Access Storage Device must be traversed in order to reach the desired position. Tape drives are Sequential Access Storage Devices. Tape storage is the lowest-cost option for very large amounts of data but is very slow compared to disk storage.
A. Direct Access Storage Device (DASD) is a general term for magnetic disk storage devices, which historically have been used in mainframe and minicomputer (mid-range computer) environments. A redundant array of independent disks (RAID) is a type of DASD. The key distinction between Direct Access and Sequential Access storage devices is that any point on a Direct Access Storage Device may be promptly reached, whereas every point in between the current position and the desired position of a Sequential Access Storage Device must be traversed in order to reach the desired position. Tape drives are Sequential Access Storage Devices. Tape storage is the lowest-cost option for very large amounts of data but is very slow compared to disk storage.
![]() B is incorrect because RAIT stands for redundant array of independent tapes. RAIT uses tape drives, which are Sequential Access Storage Devices. In RAIT, data are striped in parallel to multiple tape drives, with or without a redundant parity drive. This provides the high capacity at low cost typical of tape storage, with higher than usual tape data transfer rates, and optional data integrity. RAID, or redundant array of independent disks, is a type of Direct Access Storage Device. RAID combines several physical disks and aggregates them into logical arrays. When data is saved, the information is written across all drives. A RAID appears as a single drive to applications and other devices.
B is incorrect because RAIT stands for redundant array of independent tapes. RAIT uses tape drives, which are Sequential Access Storage Devices. In RAIT, data are striped in parallel to multiple tape drives, with or without a redundant parity drive. This provides the high capacity at low cost typical of tape storage, with higher than usual tape data transfer rates, and optional data integrity. RAID, or redundant array of independent disks, is a type of Direct Access Storage Device. RAID combines several physical disks and aggregates them into logical arrays. When data is saved, the information is written across all drives. A RAID appears as a single drive to applications and other devices.
![]() C is incorrect because both MAID, a massive array of inactive disks, and RAID, a redundant array of independent disks, are examples of Direct Access Storage Devices. Any point on these magnetic disk storage devices can be reached without traversing every point between the current and desired positions. This makes Direct Access Storage Devices faster than Sequential Access Storage Devices.
C is incorrect because both MAID, a massive array of inactive disks, and RAID, a redundant array of independent disks, are examples of Direct Access Storage Devices. Any point on these magnetic disk storage devices can be reached without traversing every point between the current and desired positions. This makes Direct Access Storage Devices faster than Sequential Access Storage Devices.
![]() D is incorrect because Sequential Access Storage Devices are slower than Direct Access Storage Devices. Tape drives are an example of Sequential Access Storage Device technology.
D is incorrect because Sequential Access Storage Devices are slower than Direct Access Storage Devices. Tape drives are an example of Sequential Access Storage Device technology.
7. A company has decided that it no longer wants to maintain its own servers and network environment because of increasing costs and liabilities. The company wants to move to a cloud-based solution, but needs to determine which type of solution best fits its needs. Which of the following provides a correct definition and mapping of a typical cloud-based solution?
A. Infrastructure as a Service is provided when a cloud provider delivers a computing platform that includes operating system, database, and web servers.
B. Software as a Service is provided when a cloud provider delivers an infrastructure environment similar to a traditional data center.
C. Platform as a Service is provided when a cloud provider delivers a computing platform that can include operating system, database, and web servers.
D. Software as a Service is provided when a cloud provider delivers a software environment in the form of a computing platform.
![]() C. Cloud computing is a general term that describes how network and server technology can be aggregated and virtualized and then partitioned to provide individual customers specific computing environments. This centralized aggregation and centralized control provides end users with on-demand self-service, broad access across multiple devices, resource pooling, rapid elasticity, and service metering capability. There are different types of cloud computing offerings. Platform as a Service (PaaS) is in place when a cloud provider delivers a computing platform, such as an operating system, database, and web server, as a holistic execution environment. Where Infrastructure as a Service (IaaS) is the “raw IT network,” PaaS is the software environment that runs on top of the IT network.
C. Cloud computing is a general term that describes how network and server technology can be aggregated and virtualized and then partitioned to provide individual customers specific computing environments. This centralized aggregation and centralized control provides end users with on-demand self-service, broad access across multiple devices, resource pooling, rapid elasticity, and service metering capability. There are different types of cloud computing offerings. Platform as a Service (PaaS) is in place when a cloud provider delivers a computing platform, such as an operating system, database, and web server, as a holistic execution environment. Where Infrastructure as a Service (IaaS) is the “raw IT network,” PaaS is the software environment that runs on top of the IT network.
![]() A is incorrect because Infrastructure as a Service (IaaS) is in place when a cloud provider offers the infrastructure environment of a traditional data center in an on-demand delivery method. Companies deploy their own operating systems, applications, and software onto this provided infrastructure and are responsible for maintaining them. IaaS cloud solutions often include additional resources, such as storage, firewalls, VLANs, load balancing, and other traditional network functionality.
A is incorrect because Infrastructure as a Service (IaaS) is in place when a cloud provider offers the infrastructure environment of a traditional data center in an on-demand delivery method. Companies deploy their own operating systems, applications, and software onto this provided infrastructure and are responsible for maintaining them. IaaS cloud solutions often include additional resources, such as storage, firewalls, VLANs, load balancing, and other traditional network functionality.
![]() B is incorrect because Software as a Service (SaaS) is in place when a cloud provider gives users access to specific application software (CRM, e-mail, games). The provider gives the customers network-based access to a specified number of copies of an application created specifically for SaaS distribution and use. In this type of offering, the cloud provider manages the infrastructure and platforms that the applications run within. Access to applications is commonly sold in an on-demand and subscription fee model. Cloud providers install and maintain the application, and end users access the software remotely from cloud clients. Cloud end users do not manage the cloud infrastructure and platform where the application runs.
B is incorrect because Software as a Service (SaaS) is in place when a cloud provider gives users access to specific application software (CRM, e-mail, games). The provider gives the customers network-based access to a specified number of copies of an application created specifically for SaaS distribution and use. In this type of offering, the cloud provider manages the infrastructure and platforms that the applications run within. Access to applications is commonly sold in an on-demand and subscription fee model. Cloud providers install and maintain the application, and end users access the software remotely from cloud clients. Cloud end users do not manage the cloud infrastructure and platform where the application runs.
![]() D is incorrect because Software as a Service (SaaS) is in place when a cloud provider gives users access to specific application software (CRM, e-mail, games) as described earlier. Software applications that are offered through a cloud provider are commonly virtualized to allow them to be scalable to meet high demands and run times. If the company in the question has business requirements for commonly used applications, then SaaS might be the best solution. In this type of situation, each employee would be provided credentials to interact with an instance of the needed application, and the cloud provider would carry out all of the “behind the scenes” maintenance and operation responsibilities.
D is incorrect because Software as a Service (SaaS) is in place when a cloud provider gives users access to specific application software (CRM, e-mail, games) as described earlier. Software applications that are offered through a cloud provider are commonly virtualized to allow them to be scalable to meet high demands and run times. If the company in the question has business requirements for commonly used applications, then SaaS might be the best solution. In this type of situation, each employee would be provided credentials to interact with an instance of the needed application, and the cloud provider would carry out all of the “behind the scenes” maintenance and operation responsibilities.
8. Various levels of RAID dictate the type of activity that will take place within the RAID system. Which level is associated with byte-level parity?
A. RAID Level 0
B. RAID Level 3
C. RAID Level 5
D. RAID Level 10
![]() B. Redundant array of inexpensive disks (RAID) provides fault tolerance for hard drives and can improve system performance. Redundancy and speed are provided by breaking up the data and writing it across several disks so that different disk heads can work simultaneously to retrieve the requested information. Recovery data is also created—this is called parity—so that if one disk fails, the parity data can be used to reconstruct the corrupted or lost information. Different activities that provide fault tolerance or performance improvements occur at different levels of a RAID system. RAID Level 3 is a scheme employing byte-level striping and a dedicated parity disk. Data is striped over all but the last drive with parity data held on only the last drive. If a drive fails, it can be reconstructed from the parity drive. The most common RAID levels used today are Levels 1, 3, and 5.
B. Redundant array of inexpensive disks (RAID) provides fault tolerance for hard drives and can improve system performance. Redundancy and speed are provided by breaking up the data and writing it across several disks so that different disk heads can work simultaneously to retrieve the requested information. Recovery data is also created—this is called parity—so that if one disk fails, the parity data can be used to reconstruct the corrupted or lost information. Different activities that provide fault tolerance or performance improvements occur at different levels of a RAID system. RAID Level 3 is a scheme employing byte-level striping and a dedicated parity disk. Data is striped over all but the last drive with parity data held on only the last drive. If a drive fails, it can be reconstructed from the parity drive. The most common RAID levels used today are Levels 1, 3, and 5.
![]() A is incorrect because only striping occurs at Level 0. Data are striped over several drives. No redundancy or parity is involved. If one volume fails, the entire volume can be unusable. Level 0 is used for performance only.
A is incorrect because only striping occurs at Level 0. Data are striped over several drives. No redundancy or parity is involved. If one volume fails, the entire volume can be unusable. Level 0 is used for performance only.
![]() C is incorrect because RAID 5 employs block-level striping and interleaving parity across all disks. Data are written in disk block units to all drives. Parity is written to all drives also, which ensures there is no single point of failure. RAID Level 5 is the most commonly used mode.
C is incorrect because RAID 5 employs block-level striping and interleaving parity across all disks. Data are written in disk block units to all drives. Parity is written to all drives also, which ensures there is no single point of failure. RAID Level 5 is the most commonly used mode.
![]() D is incorrect because Level 10 is associated with striping and mirroring. It is a combination of Levels 1 and 0. Data are simultaneously mirrored and striped across several drives and can support multiple drive failures.
D is incorrect because Level 10 is associated with striping and mirroring. It is a combination of Levels 1 and 0. Data are simultaneously mirrored and striped across several drives and can support multiple drive failures.
9. Which of the following incorrectly describes IP spoofing and session hijacking?
A. Address spoofing helps an attacker to hijack sessions between two users without being noticed.
B. IP spoofing makes it harder to track down an attacker.
C. Session hijacking can be prevented with mutual authentication.
D. IP spoofing is used to hijack SSL and IPSec secure communications.
![]() D. Secure Sockets Layer (SSL) and IPSec can protect the integrity, authenticity, and confidentiality of network traffic. Even if an attacker spoofed an IP address, he would not be able to successfully manipulate or read SSL- or IPSec-encrypted traffic, as he would not have access to the keys and other cryptographic material required.
D. Secure Sockets Layer (SSL) and IPSec can protect the integrity, authenticity, and confidentiality of network traffic. Even if an attacker spoofed an IP address, he would not be able to successfully manipulate or read SSL- or IPSec-encrypted traffic, as he would not have access to the keys and other cryptographic material required.
![]() A is incorrect because the statement is true. Address spoofing helps an attacker to hijack sessions between two users without being noticed. If an attacker wanted to take over a session between two computers, she would need to put herself in the middle of their conversation without being detected. Tools like Juggernaut and the HUNT Project enable the attacker to spy on the TCP connection and then hijack it.
A is incorrect because the statement is true. Address spoofing helps an attacker to hijack sessions between two users without being noticed. If an attacker wanted to take over a session between two computers, she would need to put herself in the middle of their conversation without being detected. Tools like Juggernaut and the HUNT Project enable the attacker to spy on the TCP connection and then hijack it.
![]() B is incorrect because the statement is true. Spoofing is the presentation of false information, usually within packets, to trick other systems and hide the origin of the message. This is usually done by hackers so that their identity cannot be successfully uncovered.
B is incorrect because the statement is true. Spoofing is the presentation of false information, usually within packets, to trick other systems and hide the origin of the message. This is usually done by hackers so that their identity cannot be successfully uncovered.
![]() C is incorrect because the statement is true. If session hijacking is a concern on a network, the administrator can implement a protocol, such as IPSec or Kerberos, that requires mutual authentication between users or systems.
C is incorrect because the statement is true. If session hijacking is a concern on a network, the administrator can implement a protocol, such as IPSec or Kerberos, that requires mutual authentication between users or systems.
10. RAID systems use a number of techniques to provide redundancy and performance. Which of the following activities divides and writes data over several drives?
A. Parity
B. Mirroring
C. Striping
D. Hot-swapping
![]() C. Redundant array of inexpensive disks (RAID) is a technology used for redundancy and/or performance improvement. It combines several physical disks and aggregates them into logical arrays. When data is saved, the information is written across all drives. A RAID appears as a single drive to applications and other devices. When striping is used, data is written across all drives. This activity divides and writes the data over several drives. Both write and read performance are increased dramatically because more than one head is reading or writing data at the same time.
C. Redundant array of inexpensive disks (RAID) is a technology used for redundancy and/or performance improvement. It combines several physical disks and aggregates them into logical arrays. When data is saved, the information is written across all drives. A RAID appears as a single drive to applications and other devices. When striping is used, data is written across all drives. This activity divides and writes the data over several drives. Both write and read performance are increased dramatically because more than one head is reading or writing data at the same time.
![]() A is incorrect because parity is used to rebuild lost or corrupted data. Various levels of RAID dictate the type of activity that will take place within the RAID system. Some levels deal only with performance issues, while other levels deal with performance and fault tolerance. If fault tolerance is one of the services a RAID level provides, parity is involved. If a drive fails, the parity is basically instructions that tell the RAID system how to rebuild the lost data on the new hard drive. Parity is used to rebuild a new drive so that all the information is restored.
A is incorrect because parity is used to rebuild lost or corrupted data. Various levels of RAID dictate the type of activity that will take place within the RAID system. Some levels deal only with performance issues, while other levels deal with performance and fault tolerance. If fault tolerance is one of the services a RAID level provides, parity is involved. If a drive fails, the parity is basically instructions that tell the RAID system how to rebuild the lost data on the new hard drive. Parity is used to rebuild a new drive so that all the information is restored.
![]() B is incorrect because mirroring occurs when data is written to two drives at once. If one drive fails, the other drive has the exact same data available. Mirroring provides redundancy. Mirroring occurs at Level 1 of RAID systems, and with striping in Level 10.
B is incorrect because mirroring occurs when data is written to two drives at once. If one drive fails, the other drive has the exact same data available. Mirroring provides redundancy. Mirroring occurs at Level 1 of RAID systems, and with striping in Level 10.
![]() D is incorrect because hot-swappable refers to a type of disk that is in most RAID systems. RAID systems with hot-swapping disks are able to replace drives while the system is running. When a drive is swapped out, or added, the parity data is used to rebuild the data on the new disk that was just added.
D is incorrect because hot-swappable refers to a type of disk that is in most RAID systems. RAID systems with hot-swapping disks are able to replace drives while the system is running. When a drive is swapped out, or added, the parity data is used to rebuild the data on the new disk that was just added.
11. What is the difference between hierarchical storage management and storage area network technologies?
A. HSM uses optical or tape jukeboxes, and SAN is a standard of how to develop and implement this technology.
B. HSM and SAN are one and the same. The difference is in the implementation.
C. HSM uses optical or tape jukeboxes, and SAN is a network of connected storage.
D. SAN uses optical or tape jukeboxes, and HSM is a network of connected storage systems.
![]() C. Hierarchical storage management (HSM) provides continuous online backup functionality. It combines hard disk technology with the cheaper and slower optical or tape jukeboxes. The HSM system dynamically manages the storage and recovery of files, which are copied to storage media devices that vary in speed and cost. The faster media hold the data that is accessed more often, and the seldom-used files are stored on the slower devices, or near-line devices. The storage media could include optical disks, magnetic disks, and tapes. This functionality happens in the background without the knowledge of the user or any need for user intervention. A storage area network, on the other hand, consists of large amounts of storage devices linked together by a high-speed private network and storage-specific switches. When a user makes a request for a file, he does not need to know which server or tape drive to go to—the SAN software finds it and provides it to the user.
C. Hierarchical storage management (HSM) provides continuous online backup functionality. It combines hard disk technology with the cheaper and slower optical or tape jukeboxes. The HSM system dynamically manages the storage and recovery of files, which are copied to storage media devices that vary in speed and cost. The faster media hold the data that is accessed more often, and the seldom-used files are stored on the slower devices, or near-line devices. The storage media could include optical disks, magnetic disks, and tapes. This functionality happens in the background without the knowledge of the user or any need for user intervention. A storage area network, on the other hand, consists of large amounts of storage devices linked together by a high-speed private network and storage-specific switches. When a user makes a request for a file, he does not need to know which server or tape drive to go to—the SAN software finds it and provides it to the user.
![]() A is incorrect because SAN is not a standard for how to develop and implement HSM. A SAN is a network of connected storage devices. SANs provide redundancy, fault tolerance, reliability, and backups, and they allow the users and administrators to interact with the SAN as one virtual entity. Because the network that carries the data in the SAN is separate from a company’s regular data network, all of this performance, reliability, and flexibility come, without impact to the data networking capabilities of the systems on the network.
A is incorrect because SAN is not a standard for how to develop and implement HSM. A SAN is a network of connected storage devices. SANs provide redundancy, fault tolerance, reliability, and backups, and they allow the users and administrators to interact with the SAN as one virtual entity. Because the network that carries the data in the SAN is separate from a company’s regular data network, all of this performance, reliability, and flexibility come, without impact to the data networking capabilities of the systems on the network.
![]() B is incorrect because HSM and SAN are not the same. Hierarchical storage management (HSM) uses conventional hard disk backup processes combined with optical/tape jukeboxes. A storage area network (SAN) uses a networked system of storage devices integrated into an established network.
B is incorrect because HSM and SAN are not the same. Hierarchical storage management (HSM) uses conventional hard disk backup processes combined with optical/tape jukeboxes. A storage area network (SAN) uses a networked system of storage devices integrated into an established network.
![]() D is incorrect because the statement is backward. HSM uses optical or tape jukeboxes, and SAN is a network of connected storage systems. HSM was created to save money and time. It provides an economical and efficient way of storing data by combining higher-speed, higher-cost storage media for frequently accessed data with lower-speed, lower-cost media for infrequently accessed data. SANs, on the other hand, are for companies that have to keep track of terabytes of data and have the funds for this type of technology. They are not commonly used in large or mid-sized companies.
D is incorrect because the statement is backward. HSM uses optical or tape jukeboxes, and SAN is a network of connected storage systems. HSM was created to save money and time. It provides an economical and efficient way of storing data by combining higher-speed, higher-cost storage media for frequently accessed data with lower-speed, lower-cost media for infrequently accessed data. SANs, on the other hand, are for companies that have to keep track of terabytes of data and have the funds for this type of technology. They are not commonly used in large or mid-sized companies.
12. John and his team are conducting a penetration test of a client’s network. The team will conduct its testing armed only with knowledge it acquired from the Web. The network staff is aware that the testing will take place, but the penetration testing team will only work with publicly available data and some information from the client. What is the degree of the team’s knowledge and what type of test is the team carrying out?
A. Full knowledge; blind test
B. Partial knowledge; blind test
C. Partial knowledge; double-blind test
D. Zero knowledge; targeted test
![]() B. The penetration testing team can have varying degrees of knowledge about the penetration target before the tests are actually carried out. These degrees of knowledge are zero knowledge, partial knowledge, and full knowledge. John and his team have partial knowledge; the team has some information about the target. Tests may also be blind, double-blind, or targeted. John’s team is carrying out a blind test, meaning that the network staff knows that the test will take place.
B. The penetration testing team can have varying degrees of knowledge about the penetration target before the tests are actually carried out. These degrees of knowledge are zero knowledge, partial knowledge, and full knowledge. John and his team have partial knowledge; the team has some information about the target. Tests may also be blind, double-blind, or targeted. John’s team is carrying out a blind test, meaning that the network staff knows that the test will take place.
![]() A is incorrect because John and his team do not have full knowledge of the target. Full knowledge means that the team has intimate knowledge of the target and fully understands the network, its software, and configurations. John’s team has information it gathered from the Web and partial information from the client. This is partial knowledge. The rest of the answer is correct; the team is conducting a blind test.
A is incorrect because John and his team do not have full knowledge of the target. Full knowledge means that the team has intimate knowledge of the target and fully understands the network, its software, and configurations. John’s team has information it gathered from the Web and partial information from the client. This is partial knowledge. The rest of the answer is correct; the team is conducting a blind test.
![]() C is incorrect because John and his team are not conducting a double-blind test. A double-blind test, also called a stealth assessment, is when the assessor carries out a blind test without the security staff’s knowledge. This enables the test to evaluate the network’s security level and the staff’s responses, log monitoring, and escalation processes, and is a more realistic demonstration of the likely success or failure of an attack.
C is incorrect because John and his team are not conducting a double-blind test. A double-blind test, also called a stealth assessment, is when the assessor carries out a blind test without the security staff’s knowledge. This enables the test to evaluate the network’s security level and the staff’s responses, log monitoring, and escalation processes, and is a more realistic demonstration of the likely success or failure of an attack.
![]() D is incorrect because John and his team do not have zero knowledge, nor are they conducting a targeted test. Zero knowledge means that the team does not have any knowledge of the target and must start from ground zero. John’s team is starting the project with knowledge it acquired about the target online and with information provided by the client. Targeted tests commonly involve external consultants and internal staff carrying out focused tests on specific areas of interest. For example, before a new application is rolled out, the team might test it for vulnerabilities before installing it into production. John’s team is not focusing its testing efforts on any one specific area.
D is incorrect because John and his team do not have zero knowledge, nor are they conducting a targeted test. Zero knowledge means that the team does not have any knowledge of the target and must start from ground zero. John’s team is starting the project with knowledge it acquired about the target online and with information provided by the client. Targeted tests commonly involve external consultants and internal staff carrying out focused tests on specific areas of interest. For example, before a new application is rolled out, the team might test it for vulnerabilities before installing it into production. John’s team is not focusing its testing efforts on any one specific area.
13. What type of exploited vulnerability allows more input than the program has allocated space to store it?
A. Symbolic links
B. File descriptors
C. Kernel flaws
D. Buffer overflows
![]() D. Poor programming practices allow more input than the software has allocated space to store it. This overwrites data or program memory after the end of the allocated buffer, and sometimes it allows the attacker to inject program code and then cause the processor to execute it in what is called a buffer overflow. This gives the attacker the same level of access as that held by the software that was successfully attacked. If the program was run as an administrative user or by the system itself, this can mean complete access to the system. Good programming practice, automated source code scanners, enhanced programming libraries, and strongly typed languages that disallow buffer overflows are all ways of reducing this type of vulnerability.
D. Poor programming practices allow more input than the software has allocated space to store it. This overwrites data or program memory after the end of the allocated buffer, and sometimes it allows the attacker to inject program code and then cause the processor to execute it in what is called a buffer overflow. This gives the attacker the same level of access as that held by the software that was successfully attacked. If the program was run as an administrative user or by the system itself, this can mean complete access to the system. Good programming practice, automated source code scanners, enhanced programming libraries, and strongly typed languages that disallow buffer overflows are all ways of reducing this type of vulnerability.
![]() A is incorrect because a symbolic link is a stub file that redirects access to system files or data to another place. If an attacker can compromise the symbolic link, then the attacker may be able to gain unauthorized access. (Symbolic links are used in Unix and Linux type systems.) This may allow the attacker to damage important data and/or gain privileged access to the system. A historical example of this was to use a symbolic link to cause a program to delete a password database, or replace a line in the password database with characters that, in essence, created an unpassworded root-equivalent account. Programs, and especially scripts, must be written to assure that the full path to the file cannot be circumvented.
A is incorrect because a symbolic link is a stub file that redirects access to system files or data to another place. If an attacker can compromise the symbolic link, then the attacker may be able to gain unauthorized access. (Symbolic links are used in Unix and Linux type systems.) This may allow the attacker to damage important data and/or gain privileged access to the system. A historical example of this was to use a symbolic link to cause a program to delete a password database, or replace a line in the password database with characters that, in essence, created an unpassworded root-equivalent account. Programs, and especially scripts, must be written to assure that the full path to the file cannot be circumvented.
![]() B is incorrect because file descriptors are exploited if a program makes unsafe use of a file descriptor and an attacker is able to cause unexpected input to be provided to the program, or cause output to go to an unexpected place with the privileges of the executing program. File descriptors are numbers many operating systems use to represent open files in a process. Certain file descriptor numbers are universal, meaning the same thing to all programs. Good programming practices, automated source code scanners, and application security testing are all ways of reducing file descriptor attacks.
B is incorrect because file descriptors are exploited if a program makes unsafe use of a file descriptor and an attacker is able to cause unexpected input to be provided to the program, or cause output to go to an unexpected place with the privileges of the executing program. File descriptors are numbers many operating systems use to represent open files in a process. Certain file descriptor numbers are universal, meaning the same thing to all programs. Good programming practices, automated source code scanners, and application security testing are all ways of reducing file descriptor attacks.
![]() C is incorrect because kernel flaws are problems that occur below the level of the user interface, deep inside the operating system. Flaws in the kernel that can be reached by an attacker, if exploitable, give the attacker the most powerful level of control over the system. It is important to ensure that security patches to operating systems—after sufficient testing—are promptly deployed in the environment to keep the window of vulnerability as small as possible.
C is incorrect because kernel flaws are problems that occur below the level of the user interface, deep inside the operating system. Flaws in the kernel that can be reached by an attacker, if exploitable, give the attacker the most powerful level of control over the system. It is important to ensure that security patches to operating systems—after sufficient testing—are promptly deployed in the environment to keep the window of vulnerability as small as possible.
14. There are often scenarios where the IT staff must react to emergencies and quickly apply fixes or change configurations. When dealing with such emergencies, which of the following is the best approach to making changes?
A. Review the changes within 48 hours of making them.
B. Review and document the emergency changes after the incident is over.
C. Activity should not take place in this manner.
D. Formally submit the change to a change control committee and follow the complete change control process.
![]() B. After the incident or emergency is over, the staff should review the changes to ensure that they are correct and do not open security holes or affect interoperability. The changes need to be properly documented and the system owner needs to be informed of changes.
B. After the incident or emergency is over, the staff should review the changes to ensure that they are correct and do not open security holes or affect interoperability. The changes need to be properly documented and the system owner needs to be informed of changes.
![]() A is incorrect because it is not the best answer. The changes should be reviewed after the incident is over, but not necessarily within 48 hours. Many times the changes should be reviewed hours after they are implemented—not days.
A is incorrect because it is not the best answer. The changes should be reviewed after the incident is over, but not necessarily within 48 hours. Many times the changes should be reviewed hours after they are implemented—not days.
![]() C is incorrect because, while it would be nice if emergencies didn’t happen, they are unavoidable. At one point or another, for example, an IT administrator will have to roll out a patch or change configurations to protect systems against a high-profile vulnerability.
C is incorrect because, while it would be nice if emergencies didn’t happen, they are unavoidable. At one point or another, for example, an IT administrator will have to roll out a patch or change configurations to protect systems against a high-profile vulnerability.
![]() D is incorrect because if an emergency is taking place, then there is no time to go through the process of submitting a change to the change control committee and following the complete change control process. These steps usually apply to large changes that take place to a network or environment. These types of changes are typically expensive and can have lasting effects on a company.
D is incorrect because if an emergency is taking place, then there is no time to go through the process of submitting a change to the change control committee and following the complete change control process. These steps usually apply to large changes that take place to a network or environment. These types of changes are typically expensive and can have lasting effects on a company.
15. A small medical institution’s IT security team has become overwhelmed with having to operate and maintain IDS, firewalls, enterprise-wide antivirus solutions, data leakage prevention technologies, and centralized log management. Which of the following best describes what type of solution this organization should implement to allow for standardized and streamlined security operations?
A. Unified threat management
B. Continuous monitoring technology
C. Centralized access control systems
D. Cloud-based security solution
![]() A. It has become very challenging to manage the long laundry list of security solutions almost every network needs to have in place. The list includes, but is not limited to, firewalls, antimalware, antispam, IDS/IPS, content filtering, data leak prevention, VPN capabilities, and continuous monitoring and reporting. Unified Threat Management (UTM) appliance products have been developed that provide all (or many) of these functionalities in a single network appliance. The goals of UTM are simplicity, streamlined installation and maintenance, centralized control, and the ability to understand a network’s security from a holistic point of view. Each security product vendor has its own UTM solution, but each has similar goals of allowing administrators to monitor and manage a variety of security-related applications and products through a single management console.
A. It has become very challenging to manage the long laundry list of security solutions almost every network needs to have in place. The list includes, but is not limited to, firewalls, antimalware, antispam, IDS/IPS, content filtering, data leak prevention, VPN capabilities, and continuous monitoring and reporting. Unified Threat Management (UTM) appliance products have been developed that provide all (or many) of these functionalities in a single network appliance. The goals of UTM are simplicity, streamlined installation and maintenance, centralized control, and the ability to understand a network’s security from a holistic point of view. Each security product vendor has its own UTM solution, but each has similar goals of allowing administrators to monitor and manage a variety of security-related applications and products through a single management console.
![]() B is incorrect because continuous monitoring in the security industry most commonly refers to information security continuous monitoring (ISCM), which allows companies to obtain situational awareness, ongoing awareness of information security, vulnerabilities, and threats to support business risk management decisions. Monitoring focuses on gathering data as it pertains to the health and security posture of an environment and does not combine all of the technologies mentioned in the question. Each network device and security solution (i.e., vulnerability scanners, firewalls, IDS, IPS, etc.) generates its own logs, and it is difficult to monitor these individually in order to understand what is actually taking place within an enterprise networked environment. Monitoring can take place through manual or automated processes, but when we are specifically addressing continuous monitoring, this is usually accomplished through automation. Automated continuous monitoring technologies attempt to aggregate and correlate these diverse log types to provide a single interface and holistic understanding of the environment. Continuous monitoring technologies also carry out automated scans of critical systems instead of the time-consuming and error-prone approach of manual scans and certification and accreditation processes. The Security Content Automation Protocol (SCAP) was one of the first specifications launched that allows different security product vendors to implement continuous monitoring capabilities in a standardized manner.
B is incorrect because continuous monitoring in the security industry most commonly refers to information security continuous monitoring (ISCM), which allows companies to obtain situational awareness, ongoing awareness of information security, vulnerabilities, and threats to support business risk management decisions. Monitoring focuses on gathering data as it pertains to the health and security posture of an environment and does not combine all of the technologies mentioned in the question. Each network device and security solution (i.e., vulnerability scanners, firewalls, IDS, IPS, etc.) generates its own logs, and it is difficult to monitor these individually in order to understand what is actually taking place within an enterprise networked environment. Monitoring can take place through manual or automated processes, but when we are specifically addressing continuous monitoring, this is usually accomplished through automation. Automated continuous monitoring technologies attempt to aggregate and correlate these diverse log types to provide a single interface and holistic understanding of the environment. Continuous monitoring technologies also carry out automated scans of critical systems instead of the time-consuming and error-prone approach of manual scans and certification and accreditation processes. The Security Content Automation Protocol (SCAP) was one of the first specifications launched that allows different security product vendors to implement continuous monitoring capabilities in a standardized manner.
![]() C is incorrect because centralized access control systems do not attempt to combine all of the security products and functions mentioned in the question. Centralized access control systems are used so that access control can be practiced in a standardized manner across various systems within a networked environment. Access control commonly encompasses identification, authentication, authorization, and accountability of the users who need to access a network’s resources. The network’s resources are usually provided through different system types (i.e., Windows, Unix, Linux, mainframes), and it is challenging to be able to practice access control across all of these diverse systems in a standardized and predictable manner. Centralized access control allows administrators to define and maintain access control policies across a heterogeneous environment that supports various users’ access needs.
C is incorrect because centralized access control systems do not attempt to combine all of the security products and functions mentioned in the question. Centralized access control systems are used so that access control can be practiced in a standardized manner across various systems within a networked environment. Access control commonly encompasses identification, authentication, authorization, and accountability of the users who need to access a network’s resources. The network’s resources are usually provided through different system types (i.e., Windows, Unix, Linux, mainframes), and it is challenging to be able to practice access control across all of these diverse systems in a standardized and predictable manner. Centralized access control allows administrators to define and maintain access control policies across a heterogeneous environment that supports various users’ access needs.
![]() D is incorrect because cloud-based security solution is a distractor answer. While there are security managed services that allow an outsourced company to manage and maintain a company’s security devices and solutions, this is not considered a cloud-based solution. Cloud-based solutions provide an infrastructure environment, platform, or application to a customer so that the customer does not need to spend time and money maintaining these items themselves. Some cloud providers might provide some of these security services within their Infrastructure as a Service (IaaS) offerings, but this is not the main focus of a cloud-based solution.
D is incorrect because cloud-based security solution is a distractor answer. While there are security managed services that allow an outsourced company to manage and maintain a company’s security devices and solutions, this is not considered a cloud-based solution. Cloud-based solutions provide an infrastructure environment, platform, or application to a customer so that the customer does not need to spend time and money maintaining these items themselves. Some cloud providers might provide some of these security services within their Infrastructure as a Service (IaaS) offerings, but this is not the main focus of a cloud-based solution.
16. Fred is a new security officer who wants to implement a control for detecting and preventing users who attempt to exceed their authority by misusing the access rights that have been assigned to them. Which of the following best fits this need?
A. Management review
B. Two-factor identification and authentication
C. Capturing this data in audit logs
D. Implementation of a strong security policy
![]() A. The goal of this question is for you to realize that management and supervisor involvement is critical to ensure that these types of things do not take place or are properly detected and acted upon if they do take place. If the users know that management will take action if they misbehave, this can be considered preventive in nature. The activities will only be known of after they take place, which means that the security office has to carry out some type of detective activity so that he can then inform management.
A. The goal of this question is for you to realize that management and supervisor involvement is critical to ensure that these types of things do not take place or are properly detected and acted upon if they do take place. If the users know that management will take action if they misbehave, this can be considered preventive in nature. The activities will only be known of after they take place, which means that the security office has to carry out some type of detective activity so that he can then inform management.
![]() B is incorrect because identification and authentication is preventive, not detective.
B is incorrect because identification and authentication is preventive, not detective.
![]() C is incorrect because audit logs are detective but not preventive. However, in order to be detective, the audit logs must be reviewed by a security administrator. While some of the strongest security protections come from preventive controls, detective controls such as reviewing audit logs are also required.
C is incorrect because audit logs are detective but not preventive. However, in order to be detective, the audit logs must be reviewed by a security administrator. While some of the strongest security protections come from preventive controls, detective controls such as reviewing audit logs are also required.
![]() D is incorrect because a security policy is preventive, not detective. A security policy is developed and implemented to inform users of what is expected of them and the potential ramifications if they do not follow the constructs of the policy.
D is incorrect because a security policy is preventive, not detective. A security policy is developed and implemented to inform users of what is expected of them and the potential ramifications if they do not follow the constructs of the policy.
17. Which of the following is the best way to reduce brute-force attacks that allow intruders to uncover users’ passwords?
A. Increase the clipping level.
B. Lock out an account for a certain amount of time after the clipping level is reached.
C. After a threshold of failed login attempts is met, the administrator must physically lock out the account.
D. Choose a weaker algorithm that encrypts the password file.
![]() B. A brute-force attack is an attack that continually tries different inputs to achieve a predefined goal, which can then be used to obtain credentials for unauthorized access. A brute-force attack to uncover passwords means that the intruder is attempting all possible sequences of characters to uncover the correct password. If the account would be disabled (or locked out) after this type of attack attempt took place, this would prove to be a good countermeasure.
B. A brute-force attack is an attack that continually tries different inputs to achieve a predefined goal, which can then be used to obtain credentials for unauthorized access. A brute-force attack to uncover passwords means that the intruder is attempting all possible sequences of characters to uncover the correct password. If the account would be disabled (or locked out) after this type of attack attempt took place, this would prove to be a good countermeasure.
![]() A is incorrect because clipping levels should be implemented to establish a baseline of user activity and acceptable errors. An entity attempting to log in to an account should be locked out once the clipping level is met. A higher clipping level gives an attacker more attempts between alerts or lockout. Decreasing the clipping level would be a good countermeasure.
A is incorrect because clipping levels should be implemented to establish a baseline of user activity and acceptable errors. An entity attempting to log in to an account should be locked out once the clipping level is met. A higher clipping level gives an attacker more attempts between alerts or lockout. Decreasing the clipping level would be a good countermeasure.
![]() C is incorrect because it is not practical to have an administrator physically lock out accounts. This type of activity can easily be taken care of through automated software mechanisms. Accounts should be automatically locked out for a certain amount of time after a threshold of failed login attempts has been met.
C is incorrect because it is not practical to have an administrator physically lock out accounts. This type of activity can easily be taken care of through automated software mechanisms. Accounts should be automatically locked out for a certain amount of time after a threshold of failed login attempts has been met.
![]() D is incorrect because using a weaker algorithm that encrypts passwords and/or password files would increase the likelihood of success of a brute-force attack.
D is incorrect because using a weaker algorithm that encrypts passwords and/or password files would increase the likelihood of success of a brute-force attack.
18. Brandy could not figure out how Sam gained unauthorized access to her system, since he has little computer experience. Which of the following is most likely the attack Sam used?
A. Dictionary attack
B. Shoulder surfing attack
C. Covert channel attack
D. Timing attack
![]() B. Shoulder surfing is a type of browsing attack in which an attacker looks over another’s shoulder to see items on that person’s monitor or what is being typed in at the keyboard. Sam probably viewed Brandy’s password as she typed it. Of the attacks listed, this is the easiest to execute in that it does not require any real knowledge of computer systems.
B. Shoulder surfing is a type of browsing attack in which an attacker looks over another’s shoulder to see items on that person’s monitor or what is being typed in at the keyboard. Sam probably viewed Brandy’s password as she typed it. Of the attacks listed, this is the easiest to execute in that it does not require any real knowledge of computer systems.
![]() A is incorrect because a dictionary attack is an automated attack involving the use of tools like Crack or L0phtcrack. Sam would need to be aware of these tools and know how to find and use them. A dictionary attack requires more knowledge of how computer systems work compared to shoulder surfing.
A is incorrect because a dictionary attack is an automated attack involving the use of tools like Crack or L0phtcrack. Sam would need to be aware of these tools and know how to find and use them. A dictionary attack requires more knowledge of how computer systems work compared to shoulder surfing.
![]() C is incorrect because a covert channel attack requires computer expertise. A covert channel is a communications path that enables a process to transmit information in a way that violates the system’s security policy. Identifying and using a covert channel requires a lot more computer expertise compared to a shoulder surfing attack.
C is incorrect because a covert channel attack requires computer expertise. A covert channel is a communications path that enables a process to transmit information in a way that violates the system’s security policy. Identifying and using a covert channel requires a lot more computer expertise compared to a shoulder surfing attack.
![]() D is incorrect because a timing attack requires intimate knowledge of how software executes its instruction sets so that they can be manipulated. Commonly a person who could successfully carry out this attack requires programming experience.
D is incorrect because a timing attack requires intimate knowledge of how software executes its instruction sets so that they can be manipulated. Commonly a person who could successfully carry out this attack requires programming experience.
19. The relay agent on a mail server plays a role in spam prevention. Which of the following incorrectly describes mail relays?
A. Antispam features on mail servers are actually antirelaying features.
B. Relays should be configured “wide open” to receive any e-mail message.
C. Relay agents are used to send messages from one mail server to another.
D. If a relay is configured “wide open,” the mail server can be used to send spam.
![]() B. Most companies have their public mail servers in their DMZ and may have one or more servers within their LAN. The mail servers in the DMZ are in this protected space because they are directly connected to the Internet. These servers should be tightly locked down and their relaying mechanisms should be correctly configured. If relays are configured “wide open” on a mail server, the mail server can be used to receive any mail message and send it on to the intended recipients, thereby contributing to the distribution of spam. Therefore, mail relays should not be configured “wide open.”
B. Most companies have their public mail servers in their DMZ and may have one or more servers within their LAN. The mail servers in the DMZ are in this protected space because they are directly connected to the Internet. These servers should be tightly locked down and their relaying mechanisms should be correctly configured. If relays are configured “wide open” on a mail server, the mail server can be used to receive any mail message and send it on to the intended recipients, thereby contributing to the distribution of spam. Therefore, mail relays should not be configured “wide open.”
![]() A is incorrect because it is true that antispam features are actually antirelaying features. It is important that mail servers have the proper antispam features enabled. Many companies also employ antivirus and content-filtering applications on their mail servers to try to stop the spread of malicious code, and not allow unacceptable messages through the e-mail gateway. It is important to filter both incoming and outgoing messages. This helps ensure that inside employees are not spreading viruses or sending out messages that are against company policy.
A is incorrect because it is true that antispam features are actually antirelaying features. It is important that mail servers have the proper antispam features enabled. Many companies also employ antivirus and content-filtering applications on their mail servers to try to stop the spread of malicious code, and not allow unacceptable messages through the e-mail gateway. It is important to filter both incoming and outgoing messages. This helps ensure that inside employees are not spreading viruses or sending out messages that are against company policy.
![]() C is incorrect because it is true that mail servers use a relay agent to send a message from one mail server to another. This relay agent needs to be properly configured so that a company’s mail server is not used by another for spamming activity. Spamming usually is illegal, so the people doing the spamming do not want the traffic to seem as though it originated from their equipment. They will find mail servers on the Internet or within company DMZs that have loosely configured relaying mechanisms and use these computers to send their spam.
C is incorrect because it is true that mail servers use a relay agent to send a message from one mail server to another. This relay agent needs to be properly configured so that a company’s mail server is not used by another for spamming activity. Spamming usually is illegal, so the people doing the spamming do not want the traffic to seem as though it originated from their equipment. They will find mail servers on the Internet or within company DMZs that have loosely configured relaying mechanisms and use these computers to send their spam.
![]() D is incorrect because it is true that if a relay is configured “wide open” the mail server can be used to send spam—and any other mail message it receives. This means that the server can be used to distribute advertisements for other companies, spam messages, and pornographic material.
D is incorrect because it is true that if a relay is configured “wide open” the mail server can be used to send spam—and any other mail message it receives. This means that the server can be used to distribute advertisements for other companies, spam messages, and pornographic material.
20. John is responsible for providing a weekly report to his manager outlining the week’s security incidents and mitigation steps. What steps should he take if a report has no information?
A. Send his manager an e-mail telling her so.
B. Deliver last week’s report and make sure it’s clearly dated.
C. Deliver a report that states “No output.”
D. Don’t do anything.
![]() C. If a report has no information (nothing to report), it should state, “No output.” This ensures that the manager is aware that there is no information to report and that John isn’t just slacking in his responsibilities.
C. If a report has no information (nothing to report), it should state, “No output.” This ensures that the manager is aware that there is no information to report and that John isn’t just slacking in his responsibilities.
![]() A is incorrect because John should still deliver his manager a report. It should say “No output.” Even though an e-mail achieves the objective of communicating that there’s nothing to report, a report should still be delivered for consistency.
A is incorrect because John should still deliver his manager a report. It should say “No output.” Even though an e-mail achieves the objective of communicating that there’s nothing to report, a report should still be delivered for consistency.
![]() B is incorrect because delivering last week’s report does not provide documentation or communicate to John’s manager that there is nothing to report this week. He should give his manager a report that reads, “No output.”
B is incorrect because delivering last week’s report does not provide documentation or communicate to John’s manager that there is nothing to report this week. He should give his manager a report that reads, “No output.”
![]() D is incorrect because if John doesn’t do anything when there is nothing to report, his manager must track John down and ask him for the report. For all she knows, John is slacking on his job duties. By providing a report that reads, “No output,” John is communicating this information to his manager in an efficient manner that she has come to expect.
D is incorrect because if John doesn’t do anything when there is nothing to report, his manager must track John down and ask him for the report. For all she knows, John is slacking on his job duties. By providing a report that reads, “No output,” John is communicating this information to his manager in an efficient manner that she has come to expect.
21. Brian, a security administrator, is responding to a virus infection. The antivirus application reports that a file has been infected with a dangerous virus and disinfecting it could damage the file. What course of action should Brian take?
A. Replace the file with the file saved from the day before.
B. Disinfect the file and contact the vendor.
C. Restore an uninfected version of the patched file from backup media.
D. Back up the data and disinfect the file.
![]() C. The best course of action is to install an uninfected version of a patched file from backup media. Attempts to disinfect the file could corrupt it, and it is important to restore a file that is known to be “clean.”
C. The best course of action is to install an uninfected version of a patched file from backup media. Attempts to disinfect the file could corrupt it, and it is important to restore a file that is known to be “clean.”
![]() A is incorrect because the previous day’s file could also be infected. It is best to replace the file entirely with a freshly installed and patched version.
A is incorrect because the previous day’s file could also be infected. It is best to replace the file entirely with a freshly installed and patched version.
![]() B is incorrect because disinfecting the file could cause damage, as stated in the question. In addition, the vendor of the application will not necessarily be useful in this situation. It is easier to restore a clean version of the file and move on with production.
B is incorrect because disinfecting the file could cause damage, as stated in the question. In addition, the vendor of the application will not necessarily be useful in this situation. It is easier to restore a clean version of the file and move on with production.
![]() D is incorrect because backing up the file will also back up the virus, and as the question stated, disinfecting the file will cause damage and potential data loss.
D is incorrect because backing up the file will also back up the virus, and as the question stated, disinfecting the file will cause damage and potential data loss.
22. Guidelines should be followed to allow secure remote administration. Which of the following is not one of those guidelines?
A. A small number of administrators should be allowed to carry out remote functionality.
B. Critical systems should be administered locally instead of remotely.
C. Strong authentication should be in place.
D. Telnet should be used to send commands and data.
![]() D. Telnet should not be allowed for remote administration because it sends all data, including administrator credentials, in cleartext. This type of communication should go over more secure protocols, as in SSH.
D. Telnet should not be allowed for remote administration because it sends all data, including administrator credentials, in cleartext. This type of communication should go over more secure protocols, as in SSH.
![]() A is incorrect because it is true that only a small number of administrators should be able to carry out remote functionality. This helps minimize the risk posed to the network.
A is incorrect because it is true that only a small number of administrators should be able to carry out remote functionality. This helps minimize the risk posed to the network.
![]() B is incorrect because it is true that critical systems should be administered locally instead of remotely. It is safer to send administrative commands over the internal, private network than it is to do so over a public network.
B is incorrect because it is true that critical systems should be administered locally instead of remotely. It is safer to send administrative commands over the internal, private network than it is to do so over a public network.
![]() C is incorrect because it is true that strong authentication should be in place for any administration activities. Anything less than strong authentication, such as a password, would be easy for an attacker to crack and thereby gain administrative access.
C is incorrect because it is true that strong authentication should be in place for any administration activities. Anything less than strong authentication, such as a password, would be easy for an attacker to crack and thereby gain administrative access.
23. In redundant array of inexpensive disks (RAID) systems, data and parity information are striped over several different disks. What is parity information used for?
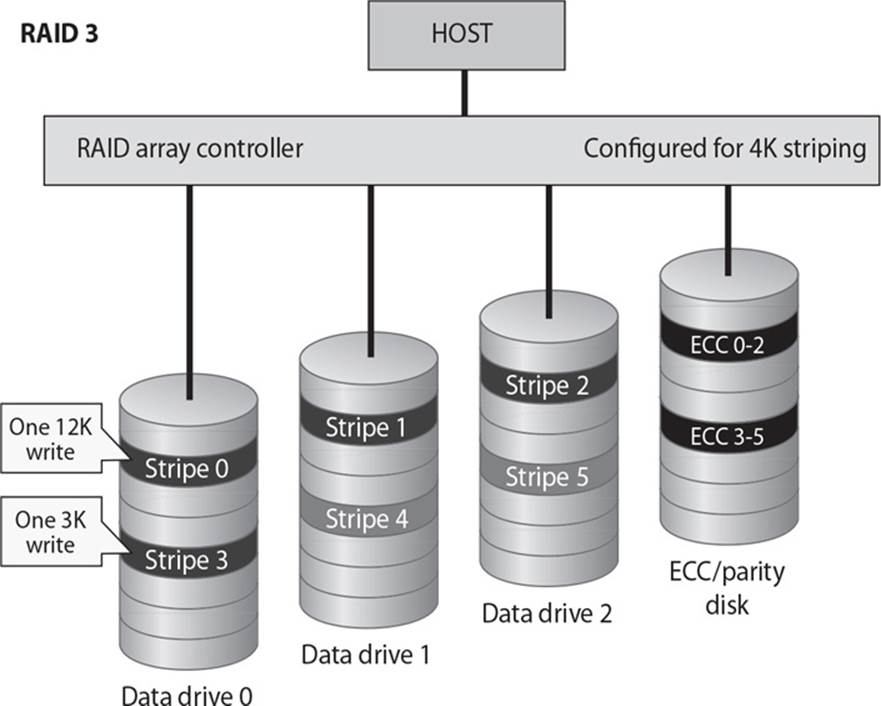
A. Information used to create new data
B. Information used to erase data
C. Information used to rebuild data
D. Information used to build data
![]() C. Redundant array of inexpensive disks (RAID) provides fault tolerance for hard drives and the data they hold and can improve system performance. Redundancy and speed are provided by breaking up the data and writing it across several disks so that different disk heads can work simultaneously to retrieve the requested information. Control data is also spread across each disk—this is called parity—so that if one disk fails, the other disks can work together and restore its data. If fault tolerance is one of the services a RAID level provides, parity is involved.
C. Redundant array of inexpensive disks (RAID) provides fault tolerance for hard drives and the data they hold and can improve system performance. Redundancy and speed are provided by breaking up the data and writing it across several disks so that different disk heads can work simultaneously to retrieve the requested information. Control data is also spread across each disk—this is called parity—so that if one disk fails, the other disks can work together and restore its data. If fault tolerance is one of the services a RAID level provides, parity is involved.
![]() A is incorrect because parity information is not used to create new data but is used as instructions on how to re-create data that has been lost or corrupted. If a drive fails, the parity is basically instructions that tell the RAID system how to rebuild the lost data on the new hard drive. Parity is used to rebuild a new drive so that all the information is restored.
A is incorrect because parity information is not used to create new data but is used as instructions on how to re-create data that has been lost or corrupted. If a drive fails, the parity is basically instructions that tell the RAID system how to rebuild the lost data on the new hard drive. Parity is used to rebuild a new drive so that all the information is restored.
![]() B is incorrect because parity information is not used to erase data but is used as instructions on how to re-create data that has been lost or corrupted.
B is incorrect because parity information is not used to erase data but is used as instructions on how to re-create data that has been lost or corrupted.
![]() D is incorrect because parity information is not used to build data but is used as instructions on how to re-create data that has been lost or corrupted.
D is incorrect because parity information is not used to build data but is used as instructions on how to re-create data that has been lost or corrupted.
24. Mirroring of drives is when data is written to two drives at once for redundancy purposes. What similar type of technology is shown in the graphic that follows?
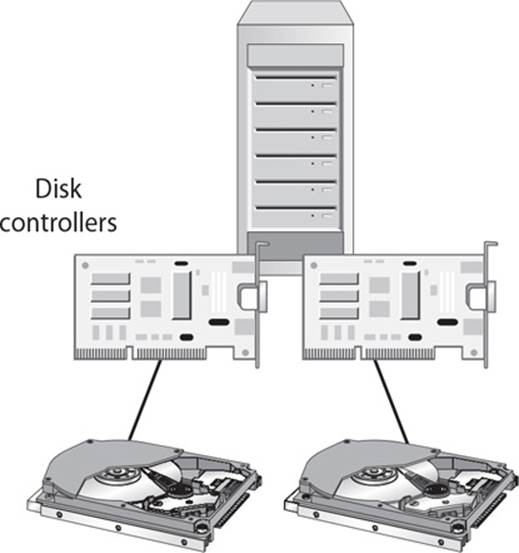
A. Direct access storage
B. Disk duplexing
C. Striping
D. Massive array of inactive disks
![]() B. Information that is required to always be available should be mirrored or duplexed. In both mirroring (also known as RAID 1) and duplexing, every data write operation occurs simultaneously or nearly simultaneously in more than one physical place. The distinction between mirroring and duplexing is that with mirroring the two (or more) physical places where the data is written may be attached to the same controller, leaving the storage still subject to the single point of failure of the controller itself; in duplexing, two or more controllers are used.
B. Information that is required to always be available should be mirrored or duplexed. In both mirroring (also known as RAID 1) and duplexing, every data write operation occurs simultaneously or nearly simultaneously in more than one physical place. The distinction between mirroring and duplexing is that with mirroring the two (or more) physical places where the data is written may be attached to the same controller, leaving the storage still subject to the single point of failure of the controller itself; in duplexing, two or more controllers are used.
![]() A is incorrect because direct access storage is a general term for magnetic disk storage devices, which historically have been used in mainframe and minicomputer (mid-range computer) environments. A redundant array of independent disks (RAID) is a type of Direct Access Storage Device (DASD).
A is incorrect because direct access storage is a general term for magnetic disk storage devices, which historically have been used in mainframe and minicomputer (mid-range computer) environments. A redundant array of independent disks (RAID) is a type of Direct Access Storage Device (DASD).
![]() C is incorrect because when data is written across all drives, the technique of striping is used. This activity divides and writes the data over several drives. The write performance is not affected, but the read performance is increased dramatically because more than one head is retrieving data at the same time. Parity information is used to rebuild lost or corrupted data. Striping just means data and potentially parity information is written across multiple disks.
C is incorrect because when data is written across all drives, the technique of striping is used. This activity divides and writes the data over several drives. The write performance is not affected, but the read performance is increased dramatically because more than one head is retrieving data at the same time. Parity information is used to rebuild lost or corrupted data. Striping just means data and potentially parity information is written across multiple disks.
![]() D is incorrect because in a massive array of inactive disks (MAID), rack-mounted disk arrays have all inactive disks powered down, with only the disk controller alive. When an application asks for data, the controller powers up the appropriate disk drive(s), transfers the data, and then powers the drive(s) down again. By powering down infrequently accessed drives, energy consumption is significantly reduced, and the service life of the disk drives may be increased.
D is incorrect because in a massive array of inactive disks (MAID), rack-mounted disk arrays have all inactive disks powered down, with only the disk controller alive. When an application asks for data, the controller powers up the appropriate disk drive(s), transfers the data, and then powers the drive(s) down again. By powering down infrequently accessed drives, energy consumption is significantly reduced, and the service life of the disk drives may be increased.
25. There are several different types of important architectures within backup technologies. Which architecture does the graphic that follows represent?
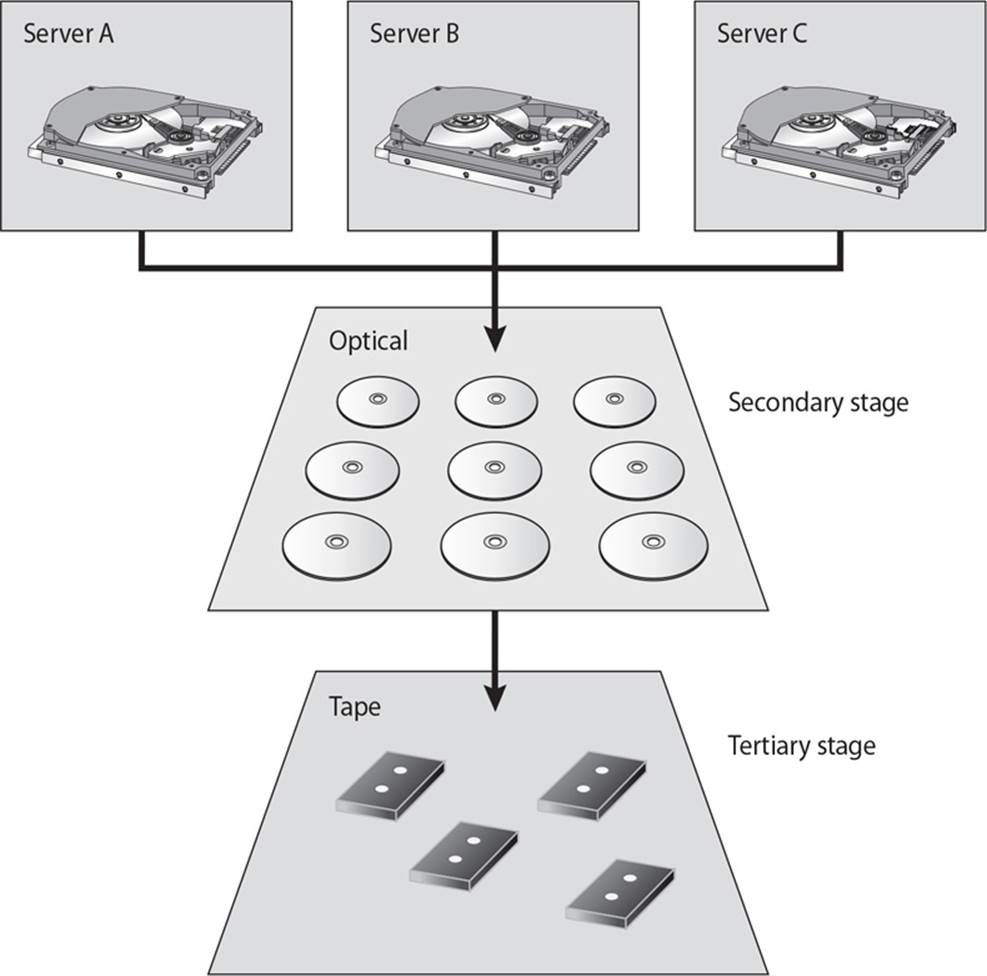
A. Clustering
B. Grid computing
C. Backup tier security
D. Hierarchical Storage Management
![]() D. Hierarchical Storage Management provides continuous online backup functionality. It combines hard disk technology with the cheaper and slower optical or tape jukeboxes. The HSM system dynamically manages the storage and recovery of files, which are copied to storage media devices that vary in speed and cost. The faster media hold the data that are accessed more often, and the seldom-used files are stored on the slower devices, or near-line devices.
D. Hierarchical Storage Management provides continuous online backup functionality. It combines hard disk technology with the cheaper and slower optical or tape jukeboxes. The HSM system dynamically manages the storage and recovery of files, which are copied to storage media devices that vary in speed and cost. The faster media hold the data that are accessed more often, and the seldom-used files are stored on the slower devices, or near-line devices.
![]() A is incorrect because clustering is a fault-tolerant server technology that is similar to redundant servers, except each server takes part in processing services that are requested. A server cluster is a group of servers that are viewed logically as one server to users and can be managed as a single logical system. Clustering provides for availability and scalability. It groups physically different systems and combines them logically, which provides immunity to faults and improves performance.
A is incorrect because clustering is a fault-tolerant server technology that is similar to redundant servers, except each server takes part in processing services that are requested. A server cluster is a group of servers that are viewed logically as one server to users and can be managed as a single logical system. Clustering provides for availability and scalability. It groups physically different systems and combines them logically, which provides immunity to faults and improves performance.
![]() B is incorrect because grid computing is load-balanced parallel means of massive computation, similar to clusters, but implemented with loosely coupled systems that may join and leave the grid randomly. Most computers have extra CPU processing power that is not being used many times throughout the day. Just like the power grid provides electricity to entities on an as-needed basis, computers can volunteer to allow their extra processing power to be available to different groups for different projects. The first project to use grid computing was SETI (Search for Extra-Terrestrial Intelligence), where people allowed their systems to participate in scanning the universe looking for aliens who are trying to talk to us.
B is incorrect because grid computing is load-balanced parallel means of massive computation, similar to clusters, but implemented with loosely coupled systems that may join and leave the grid randomly. Most computers have extra CPU processing power that is not being used many times throughout the day. Just like the power grid provides electricity to entities on an as-needed basis, computers can volunteer to allow their extra processing power to be available to different groups for different projects. The first project to use grid computing was SETI (Search for Extra-Terrestrial Intelligence), where people allowed their systems to participate in scanning the universe looking for aliens who are trying to talk to us.
![]() C is incorrect because backup tier security is not a formal technology and is a distracter answer.
C is incorrect because backup tier security is not a formal technology and is a distracter answer.
26. Which of the following is not considered a countermeasure to port scanning and operating system fingerprinting?
A. Allow access at the perimeter network to all internal ports
B. Remove as many banners as possible within operating systems and applications
C. Use TCP wrappers on vulnerable services that have to be available
D. Disable unnecessary ports and services
![]() A. Access to internal ports is not a countermeasure. Several countermeasures should be put in place to reduce this threat:
A. Access to internal ports is not a countermeasure. Several countermeasures should be put in place to reduce this threat:
• Disable unnecessary ports and services.
• Block access at the perimeter network using firewalls, routers, and proxy servers.
• Use an IDS to identify this type of activity.
• Use TCP wrappers on vulnerable services that have to be available.
• Remove as many banners as possible within operating systems and applications.
• Upgrade or update to more secure operating systems, applications, and protocols.
![]() B is incorrect because removing banners from operating systems and applications are countermeasures that should be put into place to make it harder for an attacker to fingerprint (identify) the software that is running on a system.
B is incorrect because removing banners from operating systems and applications are countermeasures that should be put into place to make it harder for an attacker to fingerprint (identify) the software that is running on a system.
![]() C is incorrect because TCP wrappers (software components) monitor incoming network traffic to the host computer and control what can and cannot access the services mapped to specific ports. When a request comes to a computer at a specific port, the target operating system will check to see if this port is enabled. If it is enabled and the operating system sees that the corresponding service is wrapped, it knows to look at an access control list, which spells out who can access this service.
C is incorrect because TCP wrappers (software components) monitor incoming network traffic to the host computer and control what can and cannot access the services mapped to specific ports. When a request comes to a computer at a specific port, the target operating system will check to see if this port is enabled. If it is enabled and the operating system sees that the corresponding service is wrapped, it knows to look at an access control list, which spells out who can access this service.
![]() D is incorrect because disabling ports and services is a critical countermeasure to reduce potential fingerprinting efforts. Enabled ports and services are clues used by the attacker to learn more about an environment. This knowledge enables the attacker to figure out the most successful ways of attacking.
D is incorrect because disabling ports and services is a critical countermeasure to reduce potential fingerprinting efforts. Enabled ports and services are clues used by the attacker to learn more about an environment. This knowledge enables the attacker to figure out the most successful ways of attacking.
27. ___________ provides for availability and scalability. It groups physically different systems and combines them logically, which helps to provide immunity to faults and improves performance.
A. Disc duping
B. Clustering
C. RAID
D. Virtualization
![]() B. Clustering is a fault-tolerant server technology that is similar to redundant servers, except each server takes part in processing services that are requested. A server cluster is a group of servers that are viewed logically as one server to users and can be managed as a single logical system. Clustering provides for availability and scalability. It groups physically different systems and combines them logically, which helps to provide immunity to faults and improves performance. Clusters work as an intelligent unit to balance traffic, and users who access the cluster do not know they may be accessing different systems at different times. To the users, all servers within the cluster are seen as one unit.
B. Clustering is a fault-tolerant server technology that is similar to redundant servers, except each server takes part in processing services that are requested. A server cluster is a group of servers that are viewed logically as one server to users and can be managed as a single logical system. Clustering provides for availability and scalability. It groups physically different systems and combines them logically, which helps to provide immunity to faults and improves performance. Clusters work as an intelligent unit to balance traffic, and users who access the cluster do not know they may be accessing different systems at different times. To the users, all servers within the cluster are seen as one unit.
![]() A is incorrect because this is a distracter answer. There is not an official technology with this name.
A is incorrect because this is a distracter answer. There is not an official technology with this name.
![]() C is incorrect because redundant array of inexpensive disks (RAID) provides fault tolerance for hard drives and can improve system performance. Redundancy and speed are provided by breaking up the data and writing them across several disks so different disk heads can work simultaneously to retrieve the requested information. RAID does not address scalability and performance.
C is incorrect because redundant array of inexpensive disks (RAID) provides fault tolerance for hard drives and can improve system performance. Redundancy and speed are provided by breaking up the data and writing them across several disks so different disk heads can work simultaneously to retrieve the requested information. RAID does not address scalability and performance.
![]() D is incorrect because virtualization is the creation of a virtual version of something, such as a hardware platform, operating system, storage device, or network resource. Hardware virtualization or platform virtualization refers to the creation of a virtual machine that acts like a real system with an operating system. Software executed on these virtual machines is separated from the underlying hardware resources by an abstraction layer.
D is incorrect because virtualization is the creation of a virtual version of something, such as a hardware platform, operating system, storage device, or network resource. Hardware virtualization or platform virtualization refers to the creation of a virtual machine that acts like a real system with an operating system. Software executed on these virtual machines is separated from the underlying hardware resources by an abstraction layer.
28. Bob is a new security administrator at a financial institution. The organization has experienced some suspicious activity on one of the critical servers that contain customer data. When reviewing how the systems are administered, he uncovers some concerning issues pertaining to remote administration. Which of the following should not be put into place to reduce these concerns?
i. Commands and data should not be sent in cleartext.
ii. Secure Shell (SSH) should be used, not Telnet.
iii. Truly critical systems should be administered locally instead of remotely.
iv. Only a small number of administrators should be able to carry out remote functionality.
v. Strong authentication should be in place for any administration activities.
A. i, ii
B. None of them
C. ii, iv
D. All of them
![]() B. All of these countermeasures should be put into place for proper remote administration activities.
B. All of these countermeasures should be put into place for proper remote administration activities.
![]() A is incorrect because sensitive commands and data should not be sent in cleartext (that is, they should be encrypted) to critical systems. For example, SSH should be used, not Telnet. SSH is a network protocol for secure data communication. It allows for remote shell services and command execution and other secure network services between two networked systems. It was designed as a replacement for Telnet and other insecure remote shell protocols such as the Berkeley rsh and rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure.
A is incorrect because sensitive commands and data should not be sent in cleartext (that is, they should be encrypted) to critical systems. For example, SSH should be used, not Telnet. SSH is a network protocol for secure data communication. It allows for remote shell services and command execution and other secure network services between two networked systems. It was designed as a replacement for Telnet and other insecure remote shell protocols such as the Berkeley rsh and rexec protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure.
![]() C is incorrect because sensitive commands and data should not be sent in cleartext (that is, they should be encrypted). For example, SSH should be used, not Telnet. Truly critical systems should be administered locally instead of remotely. Only a small number of administrators should be able to carry out this remote functionality.
C is incorrect because sensitive commands and data should not be sent in cleartext (that is, they should be encrypted). For example, SSH should be used, not Telnet. Truly critical systems should be administered locally instead of remotely. Only a small number of administrators should be able to carry out this remote functionality.
![]() D is incorrect because all of these countermeasures should be put into place for proper remote administration activities.
D is incorrect because all of these countermeasures should be put into place for proper remote administration activities.
The following scenario will be used for questions 29 and 30.
John is a network administrator and has been told by one of his network staff members that two servers on the network have recently had suspicious traffic traveling to them and then from them in a sporadic manner. The traffic has been mainly ICMP, but the patterns were unusual compared to other servers over the last 30 days. John lists the directories and subdirectories on the systems and finds nothing unusual. He inspects the running processes and again finds nothing suspicious. He sees that the systems’ NICs are not in promiscuous mode, so he is assured that sniffers have not been planted.
29. Which of the following describes the most likely situation as described in this scenario?
A. Servers are not infected, but the traffic illustrates attack attempts.
B. Servers have been infected with rootkits.
C. Servers are vulnerable and need to be patched.
D. Servers have been infected by spyware.
![]() B. Once the level of access is achieved, the attacker can upload a bundle of tools, collectively called a rootkit. A rootkit is software that implements stealth capabilities that are designed to hide the existence of certain processes or programs. Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it.
B. Once the level of access is achieved, the attacker can upload a bundle of tools, collectively called a rootkit. A rootkit is software that implements stealth capabilities that are designed to hide the existence of certain processes or programs. Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it.
![]() A is incorrect because in the situation laid out in the scenario, the system most likely is infected. The ICMP traffic is probably the commands and status data sent between the attacker and the compromised systems.
A is incorrect because in the situation laid out in the scenario, the system most likely is infected. The ICMP traffic is probably the commands and status data sent between the attacker and the compromised systems.
![]() C is incorrect because it is not the best answer. The servers may be vulnerable and may need to be patched, but that is not what is being asked in the question. Plus applying a patch will not eradicate an infected system of a rootkit.
C is incorrect because it is not the best answer. The servers may be vulnerable and may need to be patched, but that is not what is being asked in the question. Plus applying a patch will not eradicate an infected system of a rootkit.
![]() D is incorrect because it is not the best answer. The scenario best describes a situation where rootkits have been installed. Spyware may be a component of the rootkit, but Trojaned files are most likely installed, which can only happen with rootkits, not spyware.
D is incorrect because it is not the best answer. The scenario best describes a situation where rootkits have been installed. Spyware may be a component of the rootkit, but Trojaned files are most likely installed, which can only happen with rootkits, not spyware.
30. Which of the following best explains why John does not see anything suspicious on the reported systems?
A. The systems have not yet been infected.
B. He is not running the correct tools. He needs to carry out a penetration test on the two systems.
C. Trojaned files have been loaded and executed.
D. A back door has been installed and the attacker enters the system sporadically.
![]() C. The other tools in the rootkit may vary, but they usually comprise utilities that are used to cover the attacker’s tracks. For example, every operating system has basic utilities that a root or administrator user can use to detect the presence of the rootkit, an installed sniffer, and the back door. The hacker replaces these default utilities with new utilities, which share the same name. They are referred to as “Trojaned programs” because they carry out the intended functionality but do some devious activity in the background.
C. The other tools in the rootkit may vary, but they usually comprise utilities that are used to cover the attacker’s tracks. For example, every operating system has basic utilities that a root or administrator user can use to detect the presence of the rootkit, an installed sniffer, and the back door. The hacker replaces these default utilities with new utilities, which share the same name. They are referred to as “Trojaned programs” because they carry out the intended functionality but do some devious activity in the background.
![]() A is incorrect because it is not the best answer. It is possible that the systems are not infected, but this question asks what is the most likely situation.
A is incorrect because it is not the best answer. It is possible that the systems are not infected, but this question asks what is the most likely situation.
![]() B is incorrect because most rootkits have Trojaned programs that replace these utilities, because the root user could run ps or top and see there is a back-door service running, and thus detect the presence of an attack. Most rootkits also contain sniffers, so the data can be captured and reviewed by the attacker. For a sniffer to work, the system’s NIC must be put into promiscuous mode, which just means it can “hear” all the traffic on the network link. The default ipconfig utility allows the root user to employ a specific parameter to see whether or not the NIC is running in promiscuous mode. So, the rootkit also contains a Trojaned ipconfig program, which hides the fact that the NIC is in promiscuous mode.
B is incorrect because most rootkits have Trojaned programs that replace these utilities, because the root user could run ps or top and see there is a back-door service running, and thus detect the presence of an attack. Most rootkits also contain sniffers, so the data can be captured and reviewed by the attacker. For a sniffer to work, the system’s NIC must be put into promiscuous mode, which just means it can “hear” all the traffic on the network link. The default ipconfig utility allows the root user to employ a specific parameter to see whether or not the NIC is running in promiscuous mode. So, the rootkit also contains a Trojaned ipconfig program, which hides the fact that the NIC is in promiscuous mode.
![]() D is incorrect because there is most likely more than just installed back doors on these servers. Rootkits include back-door programs to allow attackers to remotely control compromised systems, but rootkits contain many other tools also.
D is incorrect because there is most likely more than just installed back doors on these servers. Rootkits include back-door programs to allow attackers to remotely control compromised systems, but rootkits contain many other tools also.