Building an Information Security Awareness Program: Defending Against Social Engineering and Technical Threats, First Edition (2014)
CHAPTER 1. What Is a Security Awareness Program?
Bill Gardner Marshall University, Huntington, WV, USA
Abstract
Not all attacks are technical. Now that we have built technical defenses around our networks, social engineering is used in the majority of recent breaches. The only defense against social engineering is an engaging security awareness program. A security awareness program helps with the development and enforcement of policies while at the same time helping to set the limits of what is acceptable and what is not acceptable behavior by the users of an organization's computer and telecommunication services. A security awareness program helps to limit risks of breaches to an organization's sensitive and confidential data. A security awareness program is defined as a formal program with the goal of training users of potential threats to an organization's information and how to avoid situations that might put the organization's data at risk.
Keywords
Security
Awareness
Policy
Policy development
Policy enforcement
Cost savings
Production increases
Formal program
Introduction
A security awareness program is a formal program with the goal of training users of the potential threats to an organization's information and how to avoid situations that might put the organization's data at risk.
The goals of the security awareness program are to lower the organization's attack surface, to empower users to take personal responsibility for protecting the organization's information, and to enforce the policies and procedures the organization has in place to protect its data. Policies and procedures might include but are not limited to computer use policies, Internet use policies, remote access policies, and other policies that aim to govern and protect the organization's data.
In information security, people are the weakest link. People want to be helpful. People want to do a good job. People want to give good customer service to their coworkers, clients, and vendors. People are curious. Social engineers seek to exploit these characteristics in humans. “Social Engineering is defined as the process of deceiving people into giving away access or confidential information” [1]. The only known defense for social engineering attacks is an effective security awareness program. Unless users understand the tactics and techniques of social engineers, they will fall prey and put the organization's data at risk.
A survey of recent breaches will reveal that a large majority of them took advantage of exploiting humans. One example is the RSA breach [2] where sophisticated attackers used targeted spear phishing to steal RSA SecurID authentication tokens that lead to a further breach at US defense contractor Lockheed Martin [3]. Another example is the “Aurora” attack against Google and other large software companies that used an attack that sent users to a website that infected users with a cutting-edge 0day exploit. The result was that a large amount of intellectual property including source code was stolen from companies including Google and Adobe [4].
Nowadays, online bad guys don't try to break in through the firewall. Bad guys go around the firewall. Organizations have spent billions of dollars developing layered defenses against online attackers. There are solutions such as antivirus, intrusion detection systems, intrusion prevention systems, and other technical solutions to protect information. With these sophisticated solutions in place, attackers are now turning to more targeted attacks focused on tricking users into clicking links or opening attachments.
Dave Kennedy's Social-Engineer Toolkit does an excellent job of modeling social engineer attacks such as website, attachment, human interface device (HID), and QR attacks for defenders to use to test their own environments [5]. This might sound simplistic, but what would most users do if they received an attachment that appears to come from the HR department that appears to be a spreadsheet of raises for everyone in the organization (Figure 1.1)? Curiosity might not just kill the cat; it might also put your data at risk.
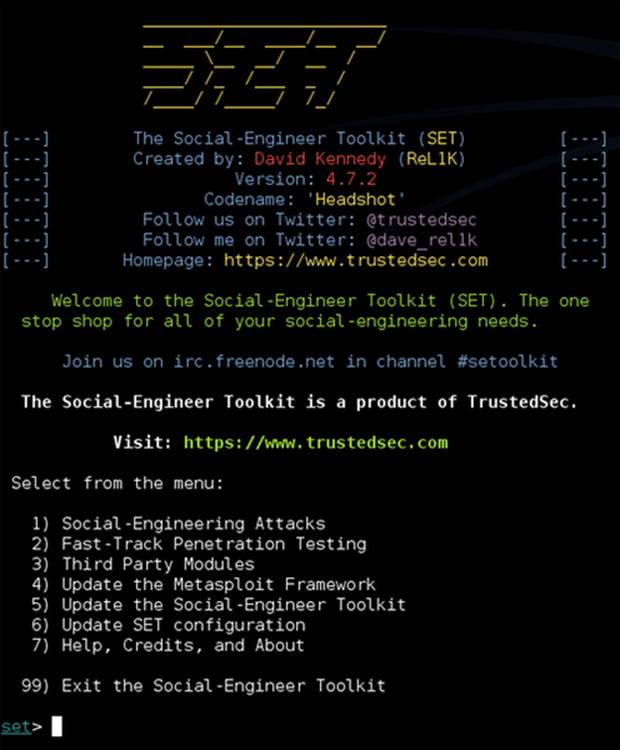
FIGURE 1.1 Social-Engineer Toolkit (SET).
While SET is a technical tool, its goal is to use nontechnical means to exploit humans who in turn exploit computers, which leads to data compromise [6]. SET can easily clone a website to an attacker's machine where exploits are then inserted into the website. At that point, the attacker will attempt to direct users to the cloned site. This might be accomplished by spear phishing, sending the user linked disguised by a link-shortening service or buying a domain to host the cloned site that looks legitimate. Once the user is on the cloned site, the attacker can use a number of different attack vectors to steal information or install backdoors to allow the attack to access the system as if the attacker was a legitimate user. SET also has the ability to encode these attacks, so they are not detected by antivirus and other software used to detect malware and intrusions. The credential harvester attack is accomplished through SET by cloning a site like Twitter, Facebook, or even a bank or credit card site with a username and password file. When the user attempts to log into the site, SET steals the username and password and logs the user into the legitimate website. We will discuss SET in more detail later in the book.
A security awareness program also is a building block of a mature security program. Policies and procedures are the first building blocks. The next layer is a security awareness program, also called user awareness training. Only when these two elements are in place do we then move to the next steps of patch management, log management, antivirus/HIDS, security appliances, and finally metrics. For years, organizations have thrown money at security, when that money would have been better spent training their users (Figure 1.2). The focus of this book is building a security awareness program step by step with the ultimate goal of building a mature security program.
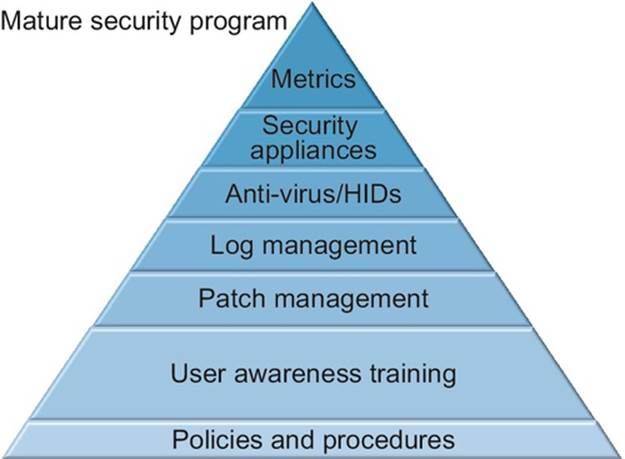
FIGURE 1.2 Elements of a mature security program.
Policy Development
Policy development sets the goals, limitations, and expectations of the organization's users. Depending on the size of the organization, these policies can be a number of documents addressing specific divisions of the organization's IT and HR structure, or it might in the case of smaller organizations be one single document that outlines the limitations and duties of those who use the organization's telephone, computer, e-mail, and other digital assets.
The most common policy is the computer use policy. Other separate policies that can be addressed in a separate document are e-mail usage, Internet usage, telephone usage, and fax usage. Computer use, also sometimes called acceptable use policy, defines the user's level of access to computer and telecommunication resources and their rights and limitation as to the use of those resources. The biggest goal of the acceptable use is to define where use ends and abuse begins. For example, it would be deemed an abuse in most organizations if user spends work time accessing porn and gambling sites. It would also be considered abuse if employees use phone and e-mail services for excessive personal communication during the workday. Most organizations understand that some personal use is necessary and the acceptable use policy to define what constitutes what is acceptable and what is not acceptable use of the organization's equipment and services.
Some organizations' usage policies are based on the template found on the Internet [7]. While these sorts of templates are useful, it is important to remember that they need to be customized to define the needs and missions of your organization.
The organization's human resources department also needs to be involved. In many cases, specific portions of the policies will have penalties that will be enforced by HR. In most cases, policies and procedure will have to be developed with regulations in mind. Those organizations that handle health data are likely to be covered by HIPAA/HITECH. Organizations that handle credit card transactions are likely to be covered by PCI DSS. Specifically, the HIPAA/HITECH physical standards of the security rule address issues including workstation use, 164.310(b); workstation security, 164.310(c); and device and media controls, 164.310(d)(1). HIPAA/HITECH also calls for punishing those who don't follow policies under the administrative standards of the security rule, specifically authorizations and/or supervision, workforce clearance procedure, and termination procedures, 164.308(a)(3).
Policy Enforcement
Policy without enforcement is a waste of time and a detriment to the organization. One of the goals of an effective security awareness program is to enforce policies by educating users on what the policies and the organization's expectations are.
There is nothing more useless than an unenforced policy. Many organizations spend a lot of time developing policies. Many times, these policies end up in a binder on a shelf in someone's office.
Giving copies of the acceptable use and other policies to the users is a good first step, but most of the time, the users will not spend the time to read the information. A security awareness program should be used to review these policies, especially the policies that apply to the use, abuse, and penalties for the abuse of the organization's communication and information technology infrastructure.
The goal of this book is to illustrate how to build an effective security awareness program from getting management buy-in to measuring the program using effective metrics. It is also written for anyone from a managerial level to the IT manager on the digital frontlines with an interest in starting a security awareness program. While we will be covering a lot of ground in this book, the end goal is for you to be able to develop an engaging security awareness program that will help your organization manage its risk when it comes to online threats.
Cost Savings
Data breaches cost money. If you are an organization covered by regulations such as HIPAA/HITECH or PCI DSS, the penalties for data breaches could be millions of dollars depending on the size of the breach. Additionally, many states now have breach notification laws that require organizations that lose data to inform those affected as to what was lost and in some cases provide credit protection to those affected. Ponemon Institute and Symantec released a report in June of 2013 that found that breaches in 2012 cost an average of $136 per record globally [8].
In May 2012, the US Department of Health and Human Services Office of Civil Rights fined the Idaho State University $400 K for health data breaches [9]. In June 2012, the Alaska Department of Health and Human Services (DHHS) agreed to pay $1.7 million to settle potential violations of HIPAA/HITECH [10].
The payment card industry has established fines of up to $500,000 per incident for data breaches [11]. In 2010, Genesco, a Nashville, TN-based sportswear company, was fined more than $13 million dollars for noncompliance with PCI DSS regulations after the firm discovered they had been hacked and regulators discovered noncompliance [12].
Production Increases
Less malware and computer problems can lead to less downtime and increased production in organizations. IT and security teams can actually spend time being proactive and moving the organization's mission forward instead of reactively responding to viruses and other malware infections and investigating possible actual data breaches [13].
Some infections and breaches can lead to days or possibly weeks of downtime. These sorts of disruptions lead to decreased profits for the organization and in some cases expose the organization to civil legal action, possible regulatory action, and possible loss of clients and business partners.
Some data breaches are not the result of an outside actor but are rather the mistake of an employee such as turning off a firewall [14] or not properly configuring a website to not display confidential data to the public [15]. Without the knowledge to properly do their jobs, employees continue to make mistakes.
The ultimate goal of a security awareness program is to manage an organization's risk. Most organizations have safety programs to keep employees safe at work. The goal of a security awareness program should be to keep an organization's data safe.
Management Buy-In
The first and most important step to building a security awareness program is getting the approval and support of the management structure of the organizations. Without managerial support, policies will go unwritten, policies will go unenforced, and management and employees will rebel against any structure, rules, or limitations being put on them in regard to securing the organization's information. Even in the face of regulations such as HIPAA/HITECH and PCI DSS, without support from the management of the organizations, security awareness indicatives will fail.
Management buy-in begins by demonstrating risk to management and then illustrating how a security awareness program will help them manage that risk. The second step is to show management how such a program can support the business goals of the organization including policy development, policy enforcement, cost savings, and production increases.
Illustrating risk includes case studies that are specific to the organization's industry. For example, if your organization is a law firm, use case studies and examples of lawyers and law firms that have been breached because of mistakes made by users. It is also important to illustrate the cunningness of attackers. Most people think of everyday nontargeted virus infections when they think of security, when the most dangerous attackers are technically advanced hackers looking to steal intellectual property, financial information, and trade secrets.
Management is not always receptive to change, especially when they think that such changes will get in the way of the business goals of the organization. Properly communicating with management in nontechnical terms is key to getting management buy-in. When managers from the top down understand the purposes and goals of a security awareness program and that such a program is in line with the business goals of the organization, mainly making money, they will be more receptive to implementing a security awareness program.
For the remainder of this book, we will continue to look at the specific step to a security awareness program from scratch with little or no money. Common sense approaches are the best way to combat a large number of modern threats to information. While some organizations offer paid, often canned security awareness programs, the focus of this book is to empower the reason to build their own program within their own organizations whether those organizations are small, medium, or large businesses or corporations or if they are nonprofit groups or even schools. Most of this information will also be useable by home users to better manage their risk when facing online threats, but home users are beyond the scope of this book.
Notes
[1] Social Engineering Framework. http://www.social-engineer.org/framework/Social_Engineering_Defined [accessed on 02.06.13].
[2] Digital Dao: Evolving Hostilities in the Global Cyber Commons. http://jeffreycarr.blogspot.com/2011/06/18-days-from-0day-to-8k-rsa-attack.html [accessed on 03.06.13].
[3] InformationWeek Security: RSA Breach: Eight Months Later. http://www.informationweek.com/security/attacks/rsa-breach-eight-months-later/231903048 [accessed on 03.06.13].
[4] Wired: Google Hack Attack Was Ultra Sophisticated, New Details Show. http://www.wired.com/threatlevel/2010/01/operation-aurora/ [accessed on 03.06.13].
[5] TrustedSec: Social Engineer Toolkit. https://www.trustedsec.com/downloads/social-engineer-toolkit/ [accessed on 04.06.13].
[6] Social Engineering Framework: Computer Based Social Engineering Tools: Social Engineer Toolkit (SET). http://www.social-engineer.org/framework/Computer_Based_Social_Engineering_Tools:_Social_Engineer_Toolkit_(SET) [accessed on 04.06.13]
[7] SANS: Information Security Policy Templates. http://www.sans.org/security-resources/policies/ [accessed on 04.06.13].
[8] Ponemon and Symantec Find Most Data Breaches Caused by Human and System Errors. http://www.symantec.com/about/news/release/article.jsp?prid=20130605_01&om_ext_cid=biz_socmed_twitter_facebook_marketwire_linkedin_2013Jun_worldwide_CostofaDataBreach [accessed on 05.06.13].
[9] HHS fines Idaho State University $400 K for health data breach. http://healthitsecurity.com/2013/05/22/hhs-fines-idaho-state-university-400k-for-data-breach/ [accessed on 06.06.13].
[10] Alaska DHSS settles HIPAA security case for $1,700,000. http://www.hhs.gov/ocr/privacy/hipaa/enforcement/examples/alaska-agreement.html [accessed on 06.06.13].
[11] PCI-DSS: Security—Penalties. https://financial.ucsc.edu/Pages/Security_Penalties.aspx [accessed on 06.06.13].
[12] Retailer fights PCI fines for noncompliance after breach, sues Visa. http://www.scmagazine.com/retailer-fights-pci-fines-for-noncompliance-after-breach-sues-visa/article/284088/ [accessed on 06.06.13].
[13] Downtime Rated Top Risk Of Data Breaches. http://www.informationweek.com/security/management/downtime-rated-top-risk-of-data-breaches/228201056 [accessed on 07.06.13].
[14] HHS fines Idaho State University $400 K for health data breach. http://healthitsecurity.com/2013/05/22/hhs-fines-idaho-state-university-400k-for-data-breach/ [accessed on 07.06.13].
[15] Brookhaven data breach 'was clerical error', officials say. http://www.newsday.com/long-island/towns/brookhaven-data-breach-was-clerical-error-officials-say-1.5426405 [accessed on 07.06.13].