Information Security Management Handbook, Sixth Edition (2012)
DOMAIN 4: APPLICATION DEVELOPMENT SECURITY
Malicious Code
Chapter 18. Twenty-Five (or Forty) Years of Malware History*
Robert M. Slade
As 1986 dawned, computer users around the world were unaware that life, as they knew it, would never be the same. Within weeks, the Brain computer virus would be unleashed upon an unsuspecting planet, and the computing world would never be the same again!
Well, not quite.
Brain [or BRAIN or (c)BRAIN] was probably written and released some time before 1986. It did become widespread, and well-known, and was likely the first virus written for the MS-DOS platform, but it was not the first virus ever written. (We will get back to it.)
It is hard to say where to start with viruses. Viruses work best when they work silently, so the most important ones did not cause a lot of fuss or fanfare. There are also a lot of people who claim “the first virus” was a particular game or prank or utility, even when these programs had nothing to do with reproduction, which is a central aspect of viruses (Figure 18.1).
I suppose we might begin with Howard Aiken. Not that computer viruses were his fault—far from it! Aiken designed computers in the 1940s and 1950s, which were operated at Harvard University, mostly in terms of work done for the U.S. Navy. (Grace Hopper was one of the crew that maintained and programmed these computers.) Aiken’s central design structure made a very strict separation between the programs that these computers used and the data that was operated upon. This arrangement, which became known as the Harvard Architecture, would have made it almost impossible for the viruses that we know today to operate. Unfortunately, the industry preferred the von Neumann architecture, which makes no distinction between programs and data, and the malware situation that we see today was set to emerge.
Of course, it did not emerge right away. There were a few related items that came up over the years, though. Like the game of Core Wars that programmers played, where some of the more successful programs created copies of themselves. Or the prank played one time (ironically to get attention for a security problem) where two programs would check for each other in a machine and, if the other had been killed, start up a new copy.
Figure 18.1 Some viruses do present some kind of symptom or message. These illustrations show the effect of the Cascade virus, which caused, over time, characters to fall from their normal position on the screen toward the bottom, eventually forming “piles” of letters at the base.
Core Wars
With programmers being who they are, the development of rogue programs became a sport. This is now enshrined in the game of “Core Wars.” A program that “simulates” a computer environment is run. A standard set of instructions, known as “Redstone code,” are used to build programs that battle each other within the simulated environment. The objective is survival. The use of such tactics as attack, avoidance, and replication is of interest to virus research, as is the trade-off between complexity of design and chance of destruction.
“Password trojans” were extremely popular in the university and college environments and have lately been followed by more malicious identity and monetary theft systems known as phishing. The original programs were simple: a facsimile of the normal login screen will generally get the user to enter his or her name and password. It is quite simple to have a program write this information to a file or even mail it to a specific account.
A famous, if relatively harmless, prank in earlier computers was the “cookie” program, which ran on PDP series computers. This program would halt the operation that the victim was working on and present a message requesting a cookie. If the user typed “cookie,” then processing would continue. There was a later viral program that followed this pattern, a “Spanish Cookie” virus. This copying of ideas—viruses using ideas that came from jokes and gags using symptoms of viruses—is relatively common (Figure 18.2).
The earliest reproductive program was the one called Creeper, which was created, as an experiment in “mobile” computing, at one of the earliest companies involved in research into computer networking, in 1971. Creeper copied itself from one machine to another over a network. It is, therefore, closer to our definition of a worm than a virus.
Viruses and Worms Begin
John Shoch and Jon Hupp, two researchers at Xerox PARC (Palo Alto Research Center) were interested in the concept of distributed processing—the ability of computers to work cooperatively on single or related tasks. The specific experimental program they were testing was the one that would examine other computers on the net, and, if a computer was idle after normal working hours, e.g., submit a copy of itself to the idle machine. In this way, the original program would spawn multiple copies of itself to idle machines to make use of the CPU time that would otherwise go to waste. By breaking a problem down into small chunks, each capable of solution on one of the machines on the network, you would have a large program consisting of small program segments working on individual machines. Because biological worms are defined by the fact that they have segmented bodies, they called this new type of program a “worm.”
Apple 1, 2, 3
The earliest case of a virus that succeeded “in the wild” goes back to late 1981. The idea was sparked by a speculation regarding “evolution” and “natural selection” in pirated copies of games at Texas A&M: the “reproduction” of preferred games and the “extinction” of poor ones. This led to considerations of programs that reproduced on their own. Apple II computer diskettes of that time, when formatted in the normal way, always contained the Disk Operating System (DOS). The programmer attempted to find the minimum change that would make a version of DOS that was viral, and then tried to find an “optimal” viral DOS. A group came up with an initial version of such a virus in early 1982, but quarantined it because of adverse effects.
Figure 18.2 This is a screenshot of the prank program known as Anthem. (The program also plays the French national anthem over a sound card.) This reversal of the screen is also a feature of an older virus, known as Flip.
A second version was allowed to “spread” through the disks of group members. A bug was identified after this viral DOS spread outside the group members, and a third version was written that avoided the memory problems: parts of the coding involve bytes that are both data and opcode. Version 3 was subsequently found to have spread into disk populations previously felt to be uninfected, but no adverse reactions were ever reported.
(For those who have Apple DOS 3.3 disks, location B6E8 in memory, toward the end of track 0, sector 0 on disk, should be followed by 18 zero bytes. If, instead, the text “(GEN xxxxxxx TAMU)” appears, the digits represented by the “x”s should be a generation counter for virus version 3.)
The story has an interesting postscript. In 1984, a malicious virus was found to be spreading through the schools where all this took place. Some disks appeared to have immunity. All of these immune disks turned out to be infected with version 3.
The Work of Dr. Cohen
No historical overview of viral programs can be complete without mention of the work of Fred Cohen. He first presented his ideas in a data-security seminar in 1983, and his seminar advisor, Len Adelman (the “A” in “RSA”), suggested the term “virus” to apply to Cohen’s concept. Cohen’s master’s thesis on the topic was published in 1984, and his doctoral dissertation, in 1986, expanded his earlier research.
His practical work proved the technical feasibility of a viral attack in any computer-system environment. Equally important, his theoretical study proved that the “universal” detection of a virus is undecidable, and therefore a “perfect” antiviral program is impossible. Cohen also outlined the three major classes of antiviral protection and that is the basis for all antiviral systems created to date.
Viruses Start to Spread
It is reasonably certain that the first major virus started to reproduce in 1986. Autumn 1987 really seemed to get the ball rolling with regard to virus research. In fact, most virus history seems to have happened between 1986 and 1990, with everything that followed being a repeat, in one form or another, of what had gone before.
(c)Brain
The “Brain” virus is probably the earliest MS-DOS virus. At one time, it was the most widespread of PC viral programs. Like the Apple viruses in the early 1980s, it was disk-based, rather than being related to program files. Until the advent of macro viruses, disk-based viruses (usually technically known as boot sector infectors or BSIs) were “superior” in terms of the numbers of infections created. The Brain family is prolific, although less so than Jerusalem.
(Seemingly, any successful virus spawns a plague of copies as virus writer-wannabes use it as a template.) Like the later Jerusalem virus, it seems that one of the lesser variants might be the “original.” The “ashar” version appears to be somewhat less sophisticated than the most common Brain, and Brain contains text that makes no sense unless Brain is “derived” from ashar. Brain contains other “timing” information: a “copyright” date of 1986 and an apparent “version” number of 9.0 (Figure 18.3).
Brain is at once sly and brazen about its work. It is, in fact, the first stealth virus, in that a request to view the boot sector of an infected disk on an infected system will result in a display of the original boot sector. However, the Brain virus is designed not to hide its light under a bushel: the volume label of infected diskettes becomes “(c)Brain” (or “(c)ashar” or “Y.C.1.E.R.P” for different variants). Hence, the name of the virus (Figure 18.4).
Figure 18.3 (c)BRAIN disk map.

Figure 18.4 BRAIN version with address text removed.
Lehigh
In November 1987, it appeared that certain failed disks reported at Lehigh University were due to something other than user carelessness. The Lehigh virus infected copies of COMMAND.COM, and, when run (usually upon booting from an infected disk), the virus stayed resident in memory. When any access was made to another disk, via the TYPE, COPY, DIR, or other normal DOS commands, any (and only) uninfected COMMAND.COM files would be infected. A counter was kept of infections: after four infections, the virus would overwrite the boot and FAT areas of disks. The extreme destructiveness of Lehigh probably limited its spread: aside from copies in research “zoos,” the Lehigh virus never spread off the campus.
CHRISTMA exec
In December 1987, IBM mainframe computers in Europe, connected via the EARN network, experienced a “mailstorm.” Such events were fairly common on the early “internetworks,” caused by various mailer problems. This particular mailstorm, however, was of unprecedented severity.
The CHRISTMA exec was a message that contained a script program. “Christmas card” messages with the REXX system can be more than just the usual “typewriter picture.” These messages could include forms of animation such as asterisk snowflakes falling on a winter scene, or a crackling fire from a Yule log. Typing either “christmas” or “christma” would generate the “card.” It really was not anything special—a very simplistic conifer shape made out of asterisks.
However, at the same time that it was displaying the tree on the screen, it was also searching for the lists of other users that either sent mail to, or received mail from, this account. The CHRISTMA exec would then mail copies of itself to all of these accounts (Figure 18.5).
CHRISTMA exec was thus the first e-mail virus, and the first script virus, over a decade before the much later Loveletter or LoveBug virus.
In March 1990, an MS-DOS virus, XA1 Christmas Tree, was discovered. Although it has no technical or programming aspects related to any of the network worms, it seems to have been written “in memor” of them. It contains (in German) the message “And still it is alive: the Christmas Tree!”
Jerusalem
Initially known as the “Israel” virus, the version reported by Y. Radai in early 1988 (also sometimes referred to as “1813” or Jerusalem-B) tends to be seen as the central virus in the family. Although it was the first to be very widely disseminated and was the first to be “discovered” and publicized, internal examination suggests that it was, itself, the outcome of previous viral experiments.
Although one of the oldest viral programs, the Jerusalem family still defies description, primarily because the number of variants makes it very difficult to say anything about the virus for sure. The “Jerusalem” that you have may not be the same as the “Jerusalem” of your neighbor. Like Brain before it, Jerusalem was used as a template by young virus writers who wanted to get into the act, but lacked the necessary programming skills.
Figure 18.5 Part (mostly the display section) of the script code for the CHRISTMA exec virus.
MacMag
The MacMag virus was relatively benign. It attempted to reproduce until 2 March 1988, using the disk-based INIT resource on the Mac system. When an infected computer was booted on that date, the virus would activate a message that “RICHARD BRANDOW, publisher of MacMag, and its entire staff would like to take this opportunity to convey their UNIVERSAL MESSAGE OF PEACE to all Macintosh users around the world.” Fortunately, on 3 March, the message appeared once and then the virus erased itself.
Richard Brandow was the publisher and editor of the MacMag computer magazine. Brandow at one point said that he had been thinking about the “message” for 2 years prior to releasing it. (Interestingly, in view of the fact that the date selected as a trigger, 2 March 1988, was the first anniversary of the introduction of the Macintosh II line. It is also interesting that a “bug” in the virus that caused system crashes affected only the Mac II.) Indeed, he was proud to claim “authorship,” in spite of the fact that he did not, himself, write the virus. (Brandow had apparently commissioned the programming of the virus, and the internal structure contains the name “Drew Davidson.”)
MacMag holds a number of “firsts” in the computer world. It seems to have been released via a dropper program that was embedded within a HyperStack data file, thus predating the later macro viruses. It also infected a commercial application and was widely spread in that manner.
Scores
The Scores Mac virus is interesting for a number of reasons, but it gets inclusion here simply because it was the first virus that had a definite company and application as a target.
Stoned, Michelangelo, and Other Variants
The Stoned virus was originally written by a high school student in New Zealand. All evidence suggests that he wrote it only for study and that he took precautions against its spread. Insufficient precautions, as it turned out: it is reported that his brother stole a copy and decided that it would be fun to infect the machines of his friends.
Stoned spawned a large number of mutations ranging from minor variations in the spelling of the payload message to the somewhat functionally different Empire, Monkey, and No-Int variations. Interestingly, only Michelangelo appears to have been as successful in reproducing.
Like the Apple viruses and Brain, Stoned was disk-based. Until the Word macro viruses came along in 1994, disk-based viruses were the dominant form.
If They Joke About It, Is It Mainstream?
The Modem virus was first “reported” on 6 October 1988. Although this may not constitute the very first virus hoax, many subsequent hoaxes have used many of the same features. The original report was supposed to have come from a telecommunications firm in Seattle (therefore laying claim to have come from some kind of authority), and claimed that the virus was transmitted via the “subcarrier” on 2400 bps modems, so you should use only 300 or 1200 bps. (There is no “subcarrier” on any modem.)
The initial source of the hoax seems to have been a posting on Fidonet, apparently by someone who gave his name as Mike RoChenle. This pseudonym was probably meant as a joke on “microchannel,” the then-new bus for IBM’s PS/2 machines.
The Internet Worm
The Internet Worm is possibly the preeminent case of a viral program in our time. In many ways, this fame (or infamy) is deserved: the Internet Worm is the story of data security in miniature. The Worm used trusted links, password cracking, security holes in standard programs, the almost ubiquitous buffer overflow, standard and default operations, and, of course, the power of viral replication.
Server computers on the networks are generally designed to run constantly—to be ready for “action” at all times. They are specifically set up to run various types of programs and procedures in the absence of operator intervention. Many of these utility programs deal with the communications between systems.
When the Worm was well established on a machine, it would try to infect another. Two of the major loopholes it used were a buffer overflow in the fingerd program and the debug mode of the sendmail utility, which was frequently left enabled.
Robert Tappan Morris (RTM) was a student of data security at Cornell University, when he wrote the Worm. The Worm is often referred to as a part of his research, although it was neither an assigned project, nor had it been discussed with his advisor.
RTM was convicted of violating the computer Fraud and Abuse Act on 16 May 1990. In March 1991, an appeal was denied. He was sentenced to 3 years of probation, a $10,000 fine, and 400 hours of community service.
More of the Same
At this point in time, most of the major viral and malware technologies had been invented. Most future nasties simply refined or rang changes on what had gone before.
More Shapes for Polymorphism
Christopher Pile, who was known to the blackhat community as the Black Baron, produced SMEG, the Simulated Metamorphic Encryption Engine. Polymorphism was a virus technology that had been known since the relatively unsuccessful V2P1 or 1260 virus in the early days, and even polymorphic engines were common. In May 1995, Pile was charged with 11 offences under the United Kingdom’s Computer Misuse Act 1990.
Good Times for All—Not!
The Good Times virus warning hoax is probably the most famous of all false alerts and was certainly the earliest that was widely distributed. The hoax probably started in early December 1994. Virus hoaxes and false alerts have an interesting double relationship with viruses: the hoax usually warns about a fictitious virus and also suggests that the reader send the alert to all friends and contacts, thus getting the user to do the reproductive part.
At the time of the original Good Times message, e-mail was almost universally text-based. The hoax warned of a viral message that would infect your computer if you even read it, and the possibility of a straightforward text message carrying a virus in an infective form is remote. It provided no information on how to detect, avoid, or get rid of the “virus,” except for its warning not to read messages with “Good Times” in the subject line. (The irony of the fact that many of the warnings contained these words seems to have escaped most people.)
Predictably, a member of the vx community produced a “Good Times” virus. Like the virus named after the older Proto-T hoax, the programmed “Good Times” was an uninteresting specimen, having nothing in common with the original alert.
Proof of Concept
Concept was not the first macro virus, a virus that embeds executable program script within a data file, ever created. HyperCard viruses were commonplace in the Macintosh environment, and a number of antivirus researchers had explored WordBasic and other malware-friendly macro environments before the virus appeared in August 1995.
However, Concept was the first macro virus to be publicly described as such and certainly the most successful in terms of spreading. For a while, it was easily the most widely encountered virus in the world, knocking disk-based viruses out of top spot for the first time. From the fall of 1995 until the “fast-burner” e-mail viruses of 2000, macro viruses were pretty consistently in the top spot.
Unlike earlier boot sector and program file viruses, macro viruses carried their own source code. This made it even easier for those with almost no programming skills to produce variants based on a copy they encountered.
The Power of E-Mail
By 1999, and the turn of the millennium, everyone had become convinced of the benefits of e-mail. So had virus writers.
W97M/Melissa (MAILISSA)
She came from alt.sex. Now, as the old joke goes, that I have your attention … At this instance, though, the lure of sex was certainly employed to launch the virus into the wild. The source of the infestation of the Melissa Word macro virus (more formally identified as some variation on W97M/Melissa) was a posting on the Usenet newsgroup alt.sex, probably originally on 26 March 1999. The message had an attachment, a Word document. The posting suggested that the document contained account names and passwords for Web sites carrying salacious material.
The document carried a macro that used the functions of Microsoft Word and the Microsoft Outlook mailer program to reproduce and spread itself. Melissa is not the fastest burning e-mail-aware malware to date, but it certainly held the record for a while. In 1994, an e-mail virus was impossible. Padgett Peterson, author of MacroList, one of the best available macro virus protection tools, stated, “For years we have been saying you could not get a virus just by opening E-Mail. That bug is being fixed.”
As a macro virus, Melissa also carried its own source code. As an e-mail virus, it spread widely. Therefore, it was widely used as a template for other variants, some of which appeared within days.
Happy99 (SKA)
Happy99 used e-mail to spread, but sent itself out as an executable attachment. To do this, it actually took over the computer’s connection to the Internet. Later viruses, using the same method, would actually prevent users from contacting antivirus Web sites for help with detection and disinfection (Figure 18.6).
PrettyPark
PrettyPark is versatile: not only is it a worm, but it also steals passwords and has backdoor functionality. Thus, it is one of first examples of the convergence that we have seen recently: malware containing functions from a variety of classes of nasty programs (Figure 18.7).
VBS/Loveletter
The Love Bug, as it will probably always be known, first hit the Net on 3 May 2000. It spread rapidly, arguably faster than Melissa had done the previous year.
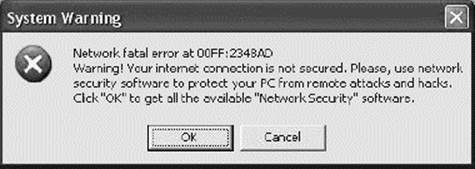
Figure 18.6 Viruses have many ways to disable protection, or to get you to disable it for them. The Fakespy would actually pop up this message, to direct the user to a site to download … well, anything the blackhats wanted, really.
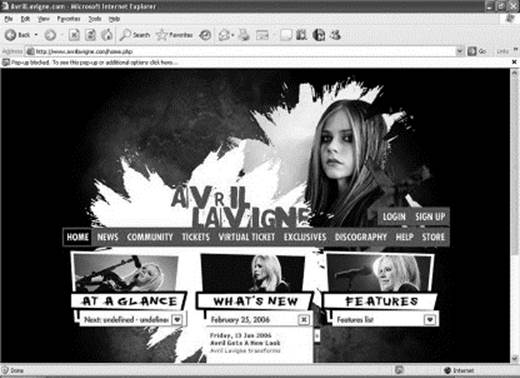
Figure 18.7 Some viruses take over many parts of your computer. The Avril-A virus would open this (legitimate) Web page in your Internet Explorer browser.
The message consisted of a short note urging you to read the attached love letter. The attachment filename, LOVE-LETTER-FOR-YOU.TXT.vbs, was a fairly obvious piece of social engineering. The .TXT bit was supposed to make people think that the attachment was a text file and thus safe to read. At that point, many people had no idea what the .VBS extension signified, and might in any case have been unaware that if a filename has a double extension, only the last filename extension has any special significance to Windows. Putting vbs in lowercase was likely meant to play down the extension’s significance.
VBS stood for Visual Basic Script, and, if you had updated your computer to Windows 98 or 2000, or even if you had updated to the latest version of Internet Explorer, it was now associated with Windows Script Host, a new batch language provided by Microsoft. Almost everybody had. Almost nobody knew the significance of VBS. As well as hugely rapid spread, Loveletter had a somewhat destructive payload that cost a lot of people their graphics and MP3 files.
VBS/Stages
VBS/Stages spread via Internet chat clients, e-mail, and mapped network drives. If it arrived by e-mail, the attachment is called LIFE_STAGES.TXT.SHS. The .SHS extension denotes a Windows scrap object, a file that can, in principle, be any kind of file and can be executed. Windows Explorer does not show the .SHS file extension, irrespective of whether file extensions are set to be displayed, thus providing another interesting way for viruses to hide what they are (Figures 18.8 through 18.10).
Linux Worms
By the spring of 2001, a number of examples of Linux malware were extent. Interestingly, the new Linux worms are similar to the Internet/Morris/UNIX worm in that they primarily relied on bugs in automatic networking software.
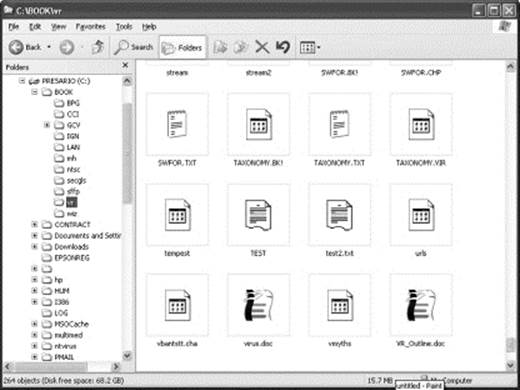
Figure 18.8 Note that the two “test” file icons look very similar to either text or undefined file icons.
Poly/Noped
This 2001 VBScript worm displays a message about stopping child pornography. It scans for JPEG files on the hard disk, looking for specific strings in the filename that the virus author obviously thought might relate to pornography. The worm will collect these files and e-mail them to addresses thought to belong to law enforcement agencies. Despite the attempt to prove that viruses can provide a socially useful service, this does not help anyone.
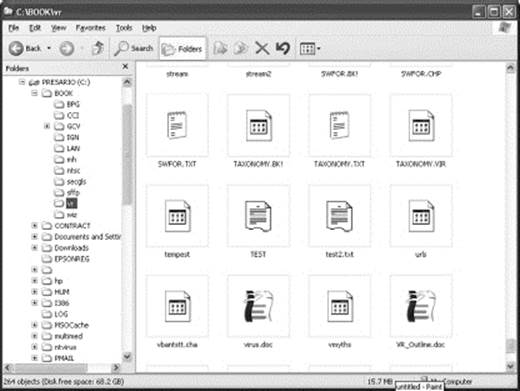
Figure 18.9 However, in detail view, although the SHS extension is still not shown, the fact that the files are scrap objects is noted.
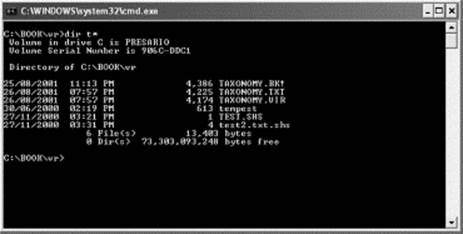
Figure 18.10 A directory listing in a DOS box does shows the SHS extension.
LINDOSE/WINUX
Summer of 2001 saw a virus that could infect both Linux ELF files and Windows PE-EXE files. Big deal. Jerusalem and sURIV3 could infect both .COM and .EXE files back in 1987.
Code Red
In 2001, Microsoft’s IIS contained a buffer overrun vulnerability in the index server, and Code Red used it to spread startlingly quickly as a worm. A later version, Nimda, took the multipartite concept (spreading via multiple objects or vectors) to new heights and would spread using the same worm activity, as well as e-mail attachment, file infection, and spreading over local area networks using drive shares (Figure 18.11).
Sircam
In 2001, Sircam searched for documents on your computer and incorporated the document into the virus itself, thus changing the size and name of the attachment. However, because it also mailed the document out to the addresses on your computer, it could breach your privacy. A later virus, Klez, did something similar. In one case, a confidential document from a security concern got sent to a mailing list.
Sobig.F
As I was struggling to get a book manuscript off to the publisher in August 2003, I was having a hard time keeping my e-mail open because of a massive deluge of Sobig.F infected messages. Sobig was one of the original spambotnet viruses, carrying with it software for its own SMTP server, a backdoor capability, and other utilities. It was at this point that virus writers seemed to start to think in commercial terms. Later, the authors of Bagle, Netsky, and MyDoom would actually engage in a type of war, trying to target and take down each other’s infected nets, while building their own to “rent” massive numbers of infected machines to spammers. Interestingly, the virus writers are also using the spambotnets as distribution systems to “seed out” new viruses as they are written.
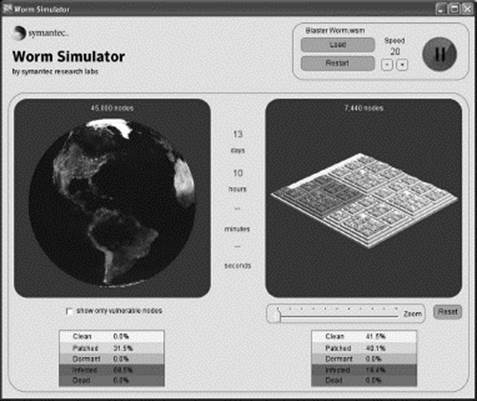
Figure 18.11 Worms can spread quickly, although some have a tendency to confine to a given location or range of Internet addresses. You can explore the patterns of spread with a worm simulator that can be downloaded from the Symantec Web site.
Spyware and Adware
There is a lot of controversy over a number of technologies generally described as adware or spyware. Most people would agree that the marketing functions are not specifically malicious, but what one person sees as “aggressive selling,” another will see as an intrusion or invasion of privacy. Therefore, it is not only difficult to say for sure whether a specific piece of software is adware or spyware, but also exactly when this type of malware started to appear, as malware.
Because it is so hard to draw the line between legitimate and malicious programs in this area, you will probably have to get spyware detection separately from antivirus scanning. After all, the antivirus companies have a good test: if you can make it reproduce, it is a virus. Certain companies involved in detecting spyware are trying to find similar functional definitions of spyware and adware, but the initial proposals have not been greeted with universal enthusiasm (Figure 18.12).
Even the spyware companies themselves admit that it is not always possible to determine which spyware is actually unwanted. A number of the spyware or adware programs are related to certain games or utilities. If you want the program that you downloaded from the Net, you have to let the spyware or adware run (Figure 18.13).
All questions of the difficulty of defining spyware aside, there is no question that there is an enormous amount of it out there. In fact, although a computer that seems to be running more slowly than usual has traditionally been suggested as the sign of a virus, now we are much more likely to find that the culprit is adware or spyware. (On one visit to a Web-based greeting card site, I found that it installed 150 pieces of spyware on my computer. Obviously, we do not read those greeting cards anymore.) Be careful out there: you no longer have to ask to download and install games or screensavers to get spyware these days. A lot of sites will do “browse by” installs when you simply visit or look at the site.
Figure 18.12 Spybot Search and Destroy, one of the spyware detecting programs you can find.
Can I Get a Virus on My Cell?
Or, Blackberry, PDA, smartphone, or other form of mobile computing device? The mobile issue is fairly simple. Mobile malware is already out there, although none of it has made much of an impact. So far. Eventually, it will. The only indicator that we have ever found about prevalence of malware on a given platform is the number of users. In other words, as soon as a lot of people are using a given mobile/smart cell phone operating system, there will be malware.
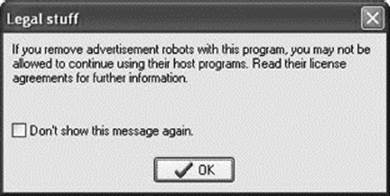
Figure 18.13 When you run Spybot, it warns you that deleting certain instances of spyware or adware may cause the program that you actually wanted to cease operating.
Even More of the Same
All of the foregoing will seem like old hat and ancient history. Unfortunately, the big malware names that have recently hit the news do not really bring anything new to the table. If anyone had been paying attention to malware, these “major new threats” would have failed to find any traction at all.
Conficker
The Conficker system began setting up botnets in late 2008. Of course, botnets had been around for more than 5 years at that point. Conficker used vulnerabilities that had been patched if the operating system was kept up to date. Unfortunately, we have seen that too many people do not learn the lessons of computer history and do not keep themselves up to date. The virus also used a variety of methods to spread, but all had been used before.
Conficker also tried to prevent those who had been infected from getting help. On an infected machine, the user would be prevented from contacting certain security sites. As versions of the virus came out, new sites were added to the list. Of course, this type of thing had been done before, and the only new twist this time was that one of the malware researchers got a clever idea for a simple Web page, which would tell if you were infected with Conficker, and which version of Conficker you had, simply by trying to load logos from sites that were banned by the different versions.
Stuxnet
The virus that has created the latest furor is Stuxnet, so I have to mention it. Once again, though, it used the same technologies that have been used in the past, although in slightly different ways. First off, it is fairly clear (although some people still disagree) that Stuxnet was targeted at a specific institution. Well, that happened back in 1987. (As a side issue, Stuxnet has also created concern because it related to SCADA [supervisory control and data acquisition] and PLC [programmable logic control] systems. In fact, it was directed at a program on the ordinary, which created the codes for such systems, so there was nothing new here, either.)
Secondly, there was the fear that there was something new about the fact that Stuxnet (one version of it, anyway) hitched a ride on USB sticks. I will admit that the specific weakness Stuxnet used (now closed, if you have kept your Windows Updates up to date) was clever. But this is basically the same type of technology that boot sector infectors used, and BRAIN, in 1986, was a BSI.
Summary
Well, it has been 25 (or 40) years, more or less, and what a long, strange trip it has been. From my perspective, it has been full of interesting technologies, and some even more fascinating people. (Others might have experienced a bit less curiosity and a lot more frustration.)
There are some developments that you might want to watch out for. I have always said that the only reason we have not been in worse shape than we already are, with respect to malware, is that the “enemy” was a collection of iconoclastic amateurs. Well, now some of them have turned professional, and there are even effective groups forming, instead of the bands of bickering individuals that we saw in years gone by. Malware has been regarded as not really part of security: merely a nuisance. Well, the danger is getting pretty real, now.
Viruses breach confidentiality and even try to break down your firewalls. Viruses have always infected desktop systems, but now those same systems are starting to run the servers for your enterprise.
New malware is often multipartite, and the virus writers are always finding new objects to infect and new places to hide. And we are also seeing increasing convergence, so that spambotnets will seed out a virus that will carry a remote access trojan to allow someone to set up a phishing Web site on your desktop machine.
The risk has been growing, slowly and steadily, for 20 years. The danger now is not something that you are unlikely to ever encounter personally, but one that seeks you out hundreds of times per day.
Additional Parts: Timeline
1971
A program called “Creeper” is created as an experiment to move from one machine to another over a network.
1977
“The Adolescence of P-1,” a novel by Thomas J. Ryan, describes a program that copies itself to various computers.
1980
John Shoch and Jon Hupp at Xerox PARC experiment with programs consisting of copying “segments” to different computers, calling the system as a whole a “worm.”
1981
First experiments with “viral” Apple DOS.
1983
Fred Cohen proposes the idea of reproductive programs in a security seminar.
1984
Cohen’s master’s thesis outlines the major forms of antiviral protection.
1986
Fred Cohen’s doctoral dissertation published.
The (c)Brain virus code contains a copyright date of 1986.
1987
A destructive virus is found on the campus of Lehigh University. The Lehigh virus never did spread off the campus.
The CHRISTMA exec message creates problems for IBM mainframe mail systems.
1988
First reported in February 1988, it was felt that Jerusalem had been circulating prior to November 1987.
The Stoned virus is released and becomes immensely successful, spawning many imitators and variants.
A 6 October Fidonet posting by “Mike RoChenle” announces the Modem virus, likely the first virus hoax.
In October 1988, a program called MOIN exec was reported to be loose on the nets. Although undoubtedly inspired by CHRISTMA, the description of MOIN appears to be more consistent with a trojan horse program. It purported to be a type of CHAT program and to provide the user who ran it with an e-mail “answering machine” capability (answering mail while the user was away), but also allowed an outside “caller” to submit commands to be run on the user’s account.
On 3 November 1988, Robert Morris Jr. releases or loses control of his Worm, ultimately infecting 4,000 to 6,000 UNIX-based machines, clogging mail queues and consuming enormous amounts of bandwidth.
In December 1988, VMS systems on DECNet networks were hit by a worm based on a file called HI.COM. On VMS systems, COM files are similar to the REXX exec files and MS-DOS batch files, using VMS DCL source code. HI.COM used the fact that DECNet nodes had, by default, a standard “anonymous” account that could be used by the network and other machines to gain limited access to a machine. This account was able to start processes running. The process that HI.COM started replicated, submitted itself to other machines, informed a specific account at a specific site, and waited until midnight on 24 December 1988, when it began mailing Christmas greetings to all users.
Thus, it seemed to have similarities to both CHRISTMA exec and the Morris Worm.
1989
1989 saw an explosion of new antivirus programs and companies, leading to a series of comparative reviews of the products by one Robert Slade. This year also saw a lot of really bad books published on the subject.
In the fall of 1989, the “AIDS Information” software package was sent to medical establishments and a number of other companies.
The WANK/W.COM worm of October 1989 and its successor owed most of its inspiration (if you can call plagiarism inspiration) to the Morris Worm and HI.COM.
In the fall of 1989, there was a large amount of media attention given to Datacrime and “Columbus Day” (actually different names for roughly the same virus). The promotion appeared to be instigated by a particular antiviral service vendor. It turned out that these viruses had far less distribution than was being claimed. Columbus Day thus can lay claim to being the first “media” virus, which obtains attention out of all proportion to its actual significance.
1990
The XA1 Christmas Tree PC virus, released in March 1990, although it contains the message “And still it is alive: the Christmas Tree!” owes no technical or programming detail to any of the network worms.
Elsevier publishes the “Computer Virus Handbook,” edited by Harold Joseph Highland, one of the first accurate and detailed references.
1991
The United States launches “Desert Storm,” an attack against Iraq.
Microsoft releases MS-DOS version 6, including an antiviral program universally acknowledged to be terrifically mediocre.
The April edition of InfoWorld carries an April Fools joke (story) about a virus, referred to as AF/91, that was supposed to have helped in reducing Iraqi air defenses during the war. The story was actually poking fun at the recent release of Windows 3.0.
Springer-Verlag publishes Alan Solomon’s “PC Viruses,” a detailed guide to the known malware.
1992
U.S. News and World Report publishes “Triumph without Victory,” a book about the Persian Gulf War. The book reports the InfoWorld AF/91.
April Fools story as fact. In 1998, another book reports the story as real, and even today many U.S. military people believe the story is true.
Although it was known to exist in February 1991, 2 March 1992, was the date that first made the majority of computer users aware of a virus. Michelangelo, a destructive variant of the earlier Stoned virus, triggered on 6 March. (The name, Michelangelo, was given due to the fact that Michelangelo Buonarroti, the Italian Renaissance artist, was born in Caprese on 6 March 1475. A friend of the earliest discoverer of the virus shared the same birth date.)
(As a piece of trivia, 6 March is also Ed McMahon’s birthday, leading to jokes about viral messages stating “Congratulations! Your computer may already be infected!”)
Springer-Verlag publishes David Ferbrache’s “Pathology of Computer Viruses,” one of the best academic texts on the topic.
1993
The Year of the Buyouts. Symantec and Central Point buy up dozens of smaller antiviral companies for market share. The purchased products and technologies are generally not included in the subsequent programs by the large vendors. Eventually, Symantec buys Central Point.
1994
Good Times, the first of a major wave of virus hoaxes, probably starts in December 1994.
Springer-Verlag publishes “Robert Slade’s Guide to Computer Viruses.”
The title was NOT my idea.
1995
Concept, first of the Word macro viruses, is released.
1996
The second edition of “Robert Slade’s Guide to Computer Viruses” is released, and, as one might expect, things were pretty quiet on the virus front.
1997
Researchers take a first look at beta versions of Windows 98 and note potential vulnerabilities. These are later used in the Melissa virus.
1998
Chernobyl/CIH, a particularly nasty beast. Happy99 and PrettyPark are also prevalent.
1999
Melissa, first of the “fast-burner” e-mail viruses.
2000
The LoveBug goes worldwide in hours.
2001
Linux worms start to be seen.
Code Red infects 350,000 IIS servers within 9 hours.
2002
It is quiet. Too quiet.
2003
Sobig is one of the most successful of the new breed of viruses that will eventually make up spambotnets.
2004
Jose Nazario writes “Defense and Detection Strategies Against Internet Worms,” the first academic review of worms as a specific class of malware.
2005
Addison-Wesley publishes Peter Szor’s “The Art of Computer Virus Research and Defense,” a demanding but accurate text for virus research.
2008
Conficker uses a number of previously used technologies, and, as a side effect of trying to keep people from getting help, allows a simple Web page to identify if a computer is infected and by which version.
2010
Stuxnet creates a huge furor among people who have not been paying attention to malware over the past 25 years.
tenworst.txt
The “how to protect yourself” piece is HELP!
A recent computer crime survey by the FBI found that almost all companies have some form of antivirus protection. In spite of that, viruses and malware are the largest category of computer crime encountered. In fact, not only is malware more than twice as large as the next category of computer crime, but, according to the statistics compiled for the survey, malware accounted for a third of the total dollar loss of all computer crime, totaling tens of billions of dollars per year in the United States. That means the loss is in the multiple millions of dollars per hour. Obviously, companies and computer users need help here.
One of the important things that Fred Cohen discovered was that a “perfect” antiviral program is inherently impossible: either it is going to miss a lot, or it is going to warn you about a lot of things that aren’t viruses.
What this means is that the price of effective and safe computing is constant vigilance. You cannot “set and forget” malware protection, and there is on step-by-step procedure to follow for every malware incident. Sorry.
However, we can give you some general advice that can help reduce your risk. A lot.
Prevention and Maintenance
Educate yourself. Learn about your enemy. Study malware.
Unfortunately, in this field, you cannot rely on someone else. You have no way of knowing whether an “expert” is giving you valid information about viruses, unless you are educated about viruses yourself.
A little education and basic policies can really help. You can reduce your risk further by training your systems’ users. (As a matter of fact, in the virus arena, a company can help reduce its own risk by providing security training for the general public. Fewer infected machines out there means less copies of viruses hitting your systems.)
Have some good, basic policies, like:
![]() Do not double-click on attachments. Do not open attachments until you have checked them out. You can check them by using an up-to-date scanner or by contacting the person who sent you the attachment, to be sure of what it is.
Do not double-click on attachments. Do not open attachments until you have checked them out. You can check them by using an up-to-date scanner or by contacting the person who sent you the attachment, to be sure of what it is.
![]() When sending attachments, be really specific. Do not just reply with the same subject line, or a vague “Here’s the stuff you wanted.” Use a subject line that says, “Here is a WordPerfect document file containing the Anderson contract.” In the body of the message, tell your correspondent, “Frank, this is Mary. This file is the third version of the contract with Anderson Corporation, as you requested on Thursday. The file is called ‘Anderson Contract 3.wpd’ and is 34,958 bytes long.” This gives the person on the other end some assurance that the message, and the file, really is from you, and is not just some ambiguous, “Hi, I’m fun! Open me!” virus or Trojan come-on.
When sending attachments, be really specific. Do not just reply with the same subject line, or a vague “Here’s the stuff you wanted.” Use a subject line that says, “Here is a WordPerfect document file containing the Anderson contract.” In the body of the message, tell your correspondent, “Frank, this is Mary. This file is the third version of the contract with Anderson Corporation, as you requested on Thursday. The file is called ‘Anderson Contract 3.wpd’ and is 34,958 bytes long.” This gives the person on the other end some assurance that the message, and the file, really is from you, and is not just some ambiguous, “Hi, I’m fun! Open me!” virus or Trojan come-on.
![]() Do not blindly use popular products as a company standard. We know this point will be controversial, but consider it carefully. You can read MS Word documents with OpenOffice or other office suite packages, or even with WordViewer, which is available from Microsoft. Internet Explorer is more dangerous than Firefox. MS Outlook is more dangerous than Pegasus. MS Windows … well, you get the picture. You do have options.
Do not blindly use popular products as a company standard. We know this point will be controversial, but consider it carefully. You can read MS Word documents with OpenOffice or other office suite packages, or even with WordViewer, which is available from Microsoft. Internet Explorer is more dangerous than Firefox. MS Outlook is more dangerous than Pegasus. MS Windows … well, you get the picture. You do have options.
![]() Disable Windows Script Host. Disable ActiveX. Disable VBScript.
Disable Windows Script Host. Disable ActiveX. Disable VBScript.
![]() Disable JavaScript. Disable cookies, although that is more for privacy than for viruses. Run with those dangerous technologies disabled by default. When you come across a Web site that requires them, ask yourself whether you really need what that site has to offer. Do not send HTML-formatted e-mail. Be wary of receiving HTML-formatted e-mail and use a mailer that informs you when you do receive such e-mail.
Disable JavaScript. Disable cookies, although that is more for privacy than for viruses. Run with those dangerous technologies disabled by default. When you come across a Web site that requires them, ask yourself whether you really need what that site has to offer. Do not send HTML-formatted e-mail. Be wary of receiving HTML-formatted e-mail and use a mailer that informs you when you do receive such e-mail.
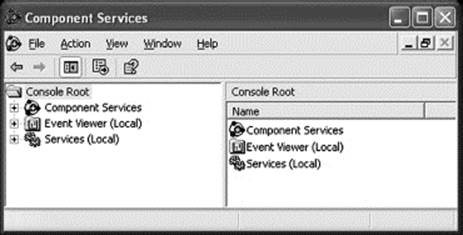
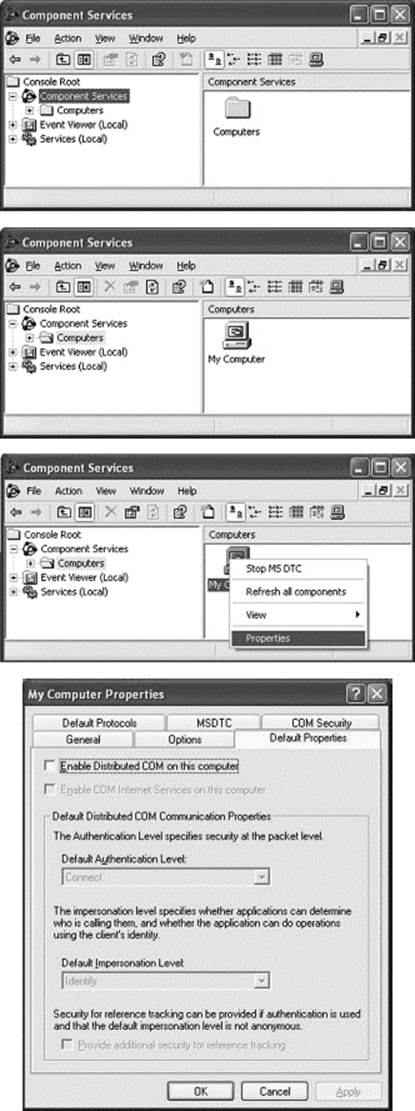
![]() Disable unnecessary services. Of course, few computer users know what services are necessary these days, so corporate IT offices should take the lead in this regard. For those who do not have an IT office that can provide a list, Thomas Greene’s book “Computer Security: for the Home and Small Office” has an excellent discussion of services and how to check for them. Disable DCOM, unless your company has an internal application that requires it. (Run “dcomcnfg/disable.”) In most Windows systems that is sufficient, or close to it. With Windows XP, double-click “Component Services,” then “Computers,” then right-click “My Computer” and select “Properties.” Under the “Default Properties” tab (note: NOT “COM Security”) make sure the “Enable Distributed COM on this computer” box is unchecked, as in the illustration.
Disable unnecessary services. Of course, few computer users know what services are necessary these days, so corporate IT offices should take the lead in this regard. For those who do not have an IT office that can provide a list, Thomas Greene’s book “Computer Security: for the Home and Small Office” has an excellent discussion of services and how to check for them. Disable DCOM, unless your company has an internal application that requires it. (Run “dcomcnfg/disable.”) In most Windows systems that is sufficient, or close to it. With Windows XP, double-click “Component Services,” then “Computers,” then right-click “My Computer” and select “Properties.” Under the “Default Properties” tab (note: NOT “COM Security”) make sure the “Enable Distributed COM on this computer” box is unchecked, as in the illustration.
DCOM is enabled on all Windows versions by default, and disabling it is unnecessarily complicated. These screen shots walk you through the process on Windows XP.
![]() Use more than one scanner. Have defense-in-depth. A content scanner on a firewall is convenient, but probably will take shortcuts. An on-access scanner is handy but must operate within the confines of the operating system. Do a manual scan with a different product once in a while, just to make sure.
Use more than one scanner. Have defense-in-depth. A content scanner on a firewall is convenient, but probably will take shortcuts. An on-access scanner is handy but must operate within the confines of the operating system. Do a manual scan with a different product once in a while, just to make sure.
You have a choice of a number of excellent antiviral scanners. Pick any two.
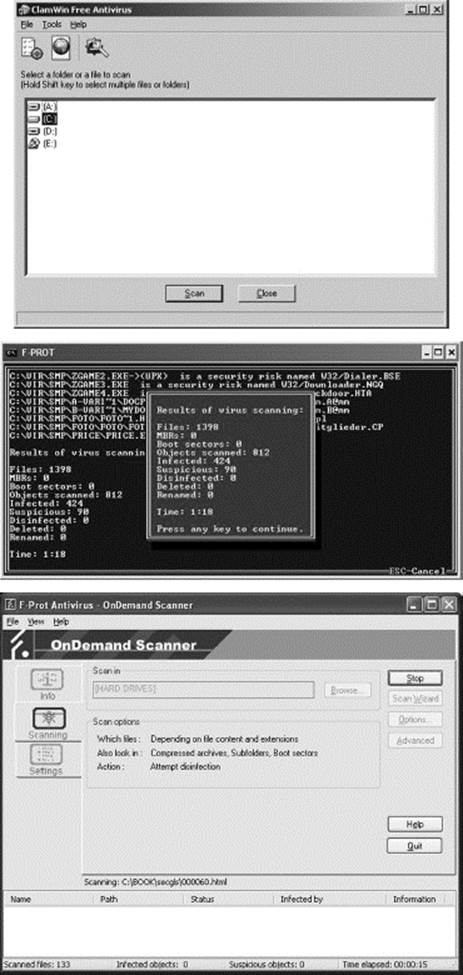
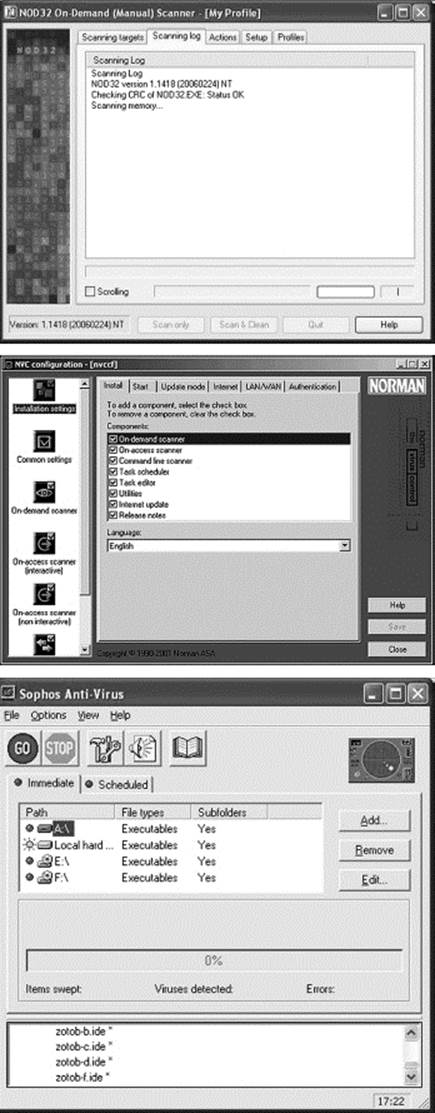
All scanners will miss some viruses and falsely report others. That is why we always recommend getting more than one. Note that even the old DOS version of F-Prot manages to find one sample that the other scanners miss.
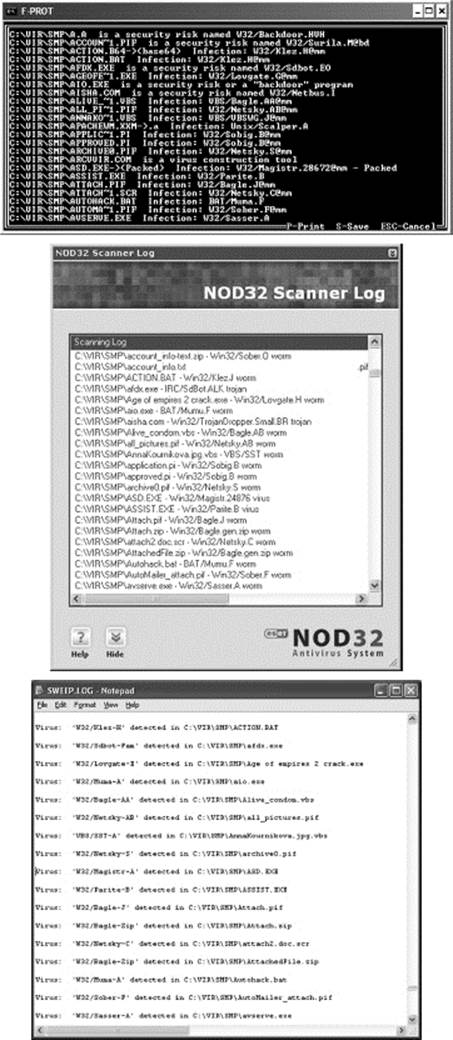
Of course, defense-in-depth is more than using multiple scanners—it is having protection at each layer of your network: at desktops, file servers, e-mail servers, gateways, and each point of entry into your network. It is also reasonable to have more than one vendor’s product in this mix-such as one vendor on the desktop and a different vendor on the e-mail servers.
![]() Do not think you are safe: everybody is at risk. Even virus experts get caught. You can too.
Do not think you are safe: everybody is at risk. Even virus experts get caught. You can too.
How to Tell if You Are Being Attacked
Well, partly this is where the education comes in. There is no one indicator of a malware attack, and the old traditional symptoms (remember spyware?) are not valid anymore.
However, there is one thing that most people could do and do not check what is outbound from your network. We have a fortress mentality when it comes to security: the bad guys are out there, and we have to watch anything inbound, but we never check the wagons on the way out. Simple traffic anomalies can tell you interesting things about your security. Is a lot of mail heading out? Maybe someone is infected with a spambotnet virus. Are certain machines trying to make a lot of connections over the Net? Maybe some machine is infected with a worm. Egress scanning is an important, and neglected, detection method in the modern environment.
Containing and Removing the Infection
Step one: Pull the network plug. If your machine has a wired connection, this is simple. If your network has a wireless LAN, you may need to take down the access point until you can figure how to turn off the wireless connection on the infected machine. Modern malware is net-aware, and if it has a connection, it will use it. Usually, a lot.
Step two is generally deciding whether you are going to do any forensic study to try and find out where the beast came from. Most people do not, because forensic investigation is time-consuming and requires specialized training. However, if you do want to look into the details, remember that a lot of the activity is counterintuitive.
A lot of people will immediately make a backup. Wrong move. Normal backup software destroys a lot of information that the forensics guys need. Best just to pull the plug and wait for them.
If you are not doing forensics, you probably just want to disinfect it.
Unfortunately, this is getting harder. Much recent malware ties itself so deeply into the system that normal disinfection may still leave the computer unusable. In this case, yes, make that backup, aiming primarily at your data. You may have to blow off the computer and reinstall all the software, so have your data image as up to date as possible. Reinstalling and reconfiguring the operating system and applications are time-consuming. Reinstalling data you have not got is impossible.
Determining Damages and Restoring Services
Once you have disinfected a machine, check it again to make sure.
Check it with another scanner: you might want to use more than two at this stage.
Do thorough checks on all machines on the same network as the infected machine. Check for unusual levels of traffic on your network.
Check the registry for entries with the name of the infected file, and also for entries in the same directory. Viruses frequently leave inactive copies around, ready to be started the next time you reboot your computer.
Check the hosts file in the \Windows\system32\drivers\etc directory.
Many viruses make changes to the file to block or redirect attempts to contact vendors for help.
Postmortem
In the midst of the fuss, take notes. That way you will be able to sit down calmly after the frenzy is over and learn something from the attack. Do you need different protection? Do you need new policies or training for your users? What caused the greatest problem, and what can be done about it?
* © Copyright Robert M. Slade. Used by permission.