Hacking Bootcamp: Learn the Basics of Computer Hacking (2016)
Chapter 3. Passwords
These days, passwords serve as the exclusive form of protection for networks and websites. If you have this piece of information, you will gain complete access to the owner’s account. This is the reason why hackers use different tools and techniques just to get passwords.
Password Cracking– Traditional Approaches
The following list shows you the traditional techniques used in cracking passwords:
· Guessing – This approach is only effective for weak passwords. For example, if the user created his password based on personal information (e.g. phone number, date of birth, favorite animal, etc.), you can easily determine the password by trying out different possibilities. This technique becomes more effective if the hacker knows a few things about the user.
· Shoulder Surfing – Here, you will look over the target’s shoulder as he or she types the password. This approach can give you excellent results if the target is a slow typist.
· Social Engineering – In this technique, you’ll exploit the target’s trust in order to get the needed information. For instance, you may call the target and pretend that you belong to the company’s IT department. You can tell the target that you need his password so you can access his account and make some important updates.
Password Cracking– Modern Techniques
In this section, you’ll learn about the latest techniques used in cracking passwords.
Important Note: This section uses some computer programs that you need to install.
The Dictionary Attack
In this approach, you have to use a text file that contains common passwords. You will try each password to see which one works. This approach offers ease and simplicity. However, you can only use it for weak passwords. To help you understand this technique, let’s analyze the following example:
A hacker uses Brutus (i.e. a popular password-cracking program) to access an FTP (i.e. file transfer protocol) server.
Before discussing the example, let’s talk about FTP servers first. An FTP server allows you to send or receive files through the internet. If a hacker gains access to a site’s FTP server, he may manipulate or remove the files within that server.
Now, you’re ready for the example. Here we go:
1. The hacker visits the FTP server’s login page.
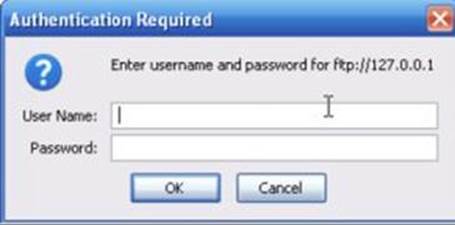
2. Then, he launches Brutus to crack the server’s password.
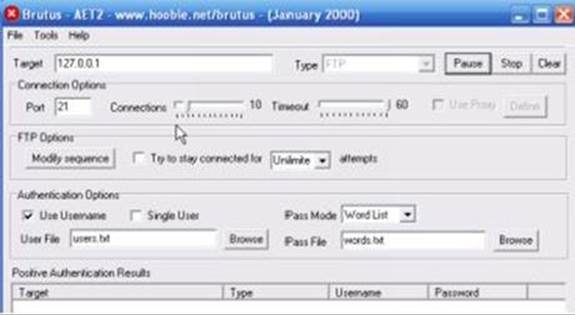
3. He indicates the server’s type (i.e. FTP) and IP address.
4. He enters a valid username.
5. He chooses the text file that contains the password list.
6. He clicks on the Start button. The Brutus program will connect to the FTP server and try to log in using the passwords inside the text file. If the process is successful, Brutus will show the correct password in its “Positive Authentication Results” section. Here’s a screenshot:
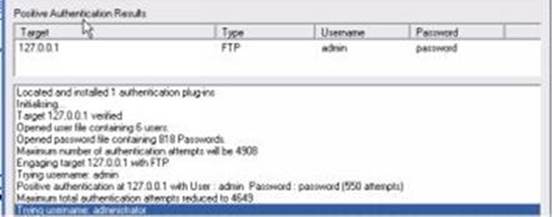
Important Note: Elite hackers use a proxy whenever they use this kind of computer program. Basically, a proxy hides your IP address by transmitting connection requests from a different computer. This is important since multiple login attempts create a lot of electronic“footprints.”
The Brute-Force Approach
IT experts claim that this approach can crack any type of password. Here, the hacker tries all possible combinations of numbers, letters and special symbols until he gets into the targeted account. The main drawback of this approach is that it is time-consuming. This is understandable– you have to try thousands of possible passwords just to access the target’s account.
The speed of this approach depends on two factors:
· The password’s complexity
· The computer’s processing power
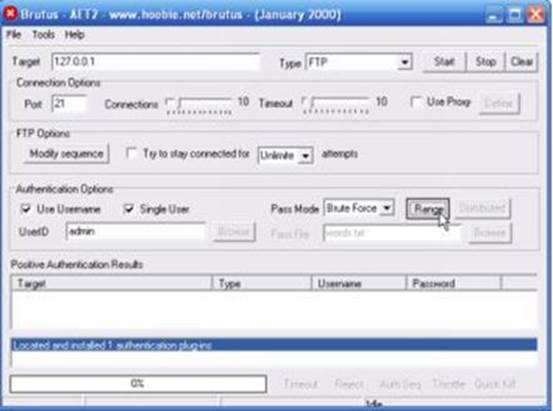
Brutus, the hacking tool used in the previous example, can also launch brute-force attacks against a server. Here’s how it works:
1. Specify the target’s IP address and server type. In the “Pass Mode” section, select “Brute Force” and hit “Range.” The image below will serve as your guide:
2. The screen will show you a dialog box (see below). Use this dialog box to configure the brute-force approach. Obviously, your job will be way much simpler if you have some idea about the target’s password. For instance, if you know that the website requires passwords with 5-10 characters, you’ll be able to narrow down the possibilities and shorten the whole process.
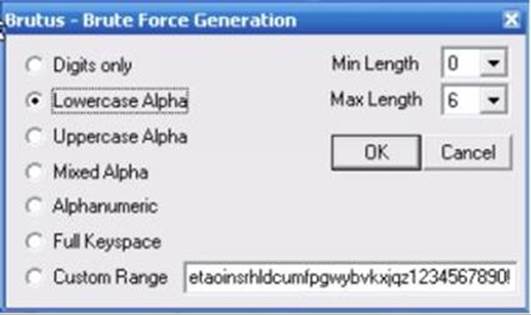
3. Hit the OK button. Brutus will log in to the targeted server by trying all possible passwords. You’ll see the results on the program’s GUI (i.e. graphical user interface).
Phishing
In this technique, you’ll steal confidential information (e.g. passwords) by fooling the victim. For example, a hacker pretended to be a bank representative and sent an email to the target user. The email required the user to change her password by clicking on a link. When the user clicked on the link, she saw a website similar to that of the actual bank. The website, however, is just a replica. Any information entered there will go to the hacker’s database or email account.
Important Note: Elite hackers use HTML to create phishing sites that look like official ones.
Here are the things you need to do when creating a phishing website:
1. Choose your target – Most hackers mimic the websites of email service providers. There are two reasons for this:
1. Users log in to their email account regularly. That means the hacker has a lot of opportunities to fool his target.
2. Email accounts are extremely useful. Most of the time, an email account is linked to other accounts (e.g. bank accounts). Thus, you can get loads of information about the user just by hacking his email account.
For this book, let’s assume that you want to create a phishing site for Gmail.
2. Copy the official webpage – Launch Mozilla Firefox (hackers recommend this browser because it is secure and customizable) and access the login page of the actual website. Press CTRL+S on your keyboard to create a local copy of the webpage.
3. Rename the file – After saving the webpage, change its name to “index.htm.” The index page is the first webpage that shows up whenever someone reaches a website; thus, you want the target user to believe that he reached the index webpage of the real site.
4. Create a script – You should create a computer script that will record the user’s login information. Most hackers use the PHP scripting language to accomplish this task. The image below shows you a basic PHP script that records login credentials.
Launch Notepad and enter the script. Save the file as “phish.php”.

5. Create an empty .txt file and save it as “list.txt”.
6. Add the script to the webpage – Use the file named index.htm using Notepad. Press CTRL+F, type “action”, and click on “Find Next”. Here’s a screenshot:
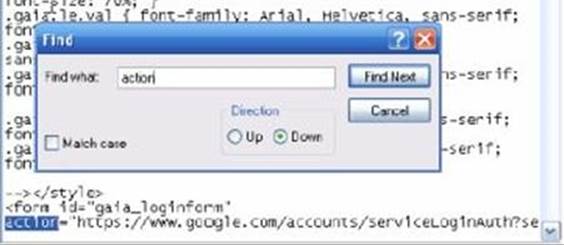
Look for “action” in the script’s “form id” section. You’ll see a URL there – delete it and type “phish.php”. By doing so, you’re instructing the form to send the user’s information to your PHP script rather than to Google.
Search for the part that says method=“post”. Replace “post” with “get” so that the code snippet is method=“get”.
7. Save the file and close it.
8. Upload the HTML file to a website host – The hosting service provider will give you a URL for the rigged webpage. You may use that URL for hacking purposes.
9. If you’ll visit the webpage, you’ll see that it looks exactly like the official Gmail login page. That webpage will record the usernames and passwords that will be entered into it. It will save the information side the empty .txt file.
Rainbow Tables
Basically, rainbow tables are huge lists of hash values for each possible character combination. To get a hash value, you have to transform a password (or a character combination) by running it through an algorithm. This is a one-way type of encryption: you cannot use the hash value to determine the original data. Most website databases use MD5, a mathematical algorithm used for hashing, to protect passwords.
Let’s assume that you registered for a site. You entered your desired login credentials (i.e. username and password). Once you hit the“Submit” button, the algorithm will process the password and store the hash value into the site’s database.
Since it’s impossible to determine passwords using hash values, you may be wondering how networks know whether your password is right or wrong. Well, when you enter your login credentials, the system runs those pieces of information through the algorithm. Then, it will compare the resulting hash with those saved in the site’s database. If the hash values match, you will be logged in.
Mathematical algorithms such as MD5 produce complex strings out of simple passwords. For instance, if you’ll encrypt“cheese” using MD5, you’ll get: fea0f1f6fede90bd0a925b4194deac11.
According to expert hackers, this method is more effective than the brute-force approach. Once you have created rainbow tables (i.e. lists of hash values), you can crack passwords quickly.
How to Prevent these Password-Cracking Techniques?
Social Engineering
To stop“social engineers,” you must be careful and attentive. If someone calls you, and you think that he’s using social engineering tactics on you, ask him questions that can prove his identity.
Important Note: Some elite hackers research about their targets. That means they may“prove their identity” by answering your questions. Because of this, if you still doubt what the person says, you should talk to the head of whichever department he says he’s from to get more information.
Shoulder Surfing
While entering your login credentials, make sure that no one sees what you are typing. If you see someone suspicious, approach him and practice your wrestling skills. Well, not really. You just have to be careful in entering your information.
Guessing
To prevent this attack, don’t use a password that is related to your personal information. Regardless of the love you have for your pet or spouse, you should never use their name as your password.
Dictionary Attack
You can protect yourself from this attack easily– don’t use passwords that are found in the dictionary. No, replacing letters with numbers (e.g. banana– b4n4n4) isn’t safe. It would be best if you’ll combine letters, numbers and special characters when creating a password.
Brute-Force Approach
To prevent this technique, you should use a long password that involves lots of numbers and special symbols. Long and complicated passwords pose difficult problems for“brute-forcers.” If the hacker cannot crack your password after several days of trying, he will probably look for another target.
Phishing
To protect yourself against this technique, you just have to check your browser’s address bar. For instance, if you should be in www.facebook.com but the address bar shows a different URL (e.g. www.pacebook.com, www.faccbook.com, www.focebook.com, etc.), you'll know that a hacker is trying to fool you.
Rainbow Tables
You can prevent this technique by creating a long password. According to elite hackers, generating hash tables for long passwords involves lots of resources.
“Password Crackers”
Here are the programs used by hackers in cracking passwords:
· SolarWinds
· Can and Abel
· RainbowCrack
· THC Hydra
· John the Ripper