Hacking Bootcamp: Learn the Basics of Computer Hacking (2016)
Chapter 4. How to Hack a Network
In this chapter, you will learn how to hack websites and computer networks. Study this material carefully because it will teach you important ideas and techniques related to hacking.
Footprinting
The term“footprinting” refers to the process of collecting data about a computer network and the company or organization it is linked to. This process serves as the initial step of most hacking attacks. Footprinting is necessary since a hacker must know everything about his target before conducting any attack.
Here are the steps that you need to take when footprinting a website:
1. You should research about the names and email addresses used in the website. This data can be extremely useful if you’re planning to execute social engineering tactics against the target.
2. Get the website’s IP address. To get this information, visit this site and enter the target’s URL. Then, hit the “Get IP” button. The screen will show you the IP address of your target website after a few seconds.
3. Ping the target’s server to check if it is currently active. Obviously, you don’t want to waste your time attacking a “dead” target. Elite hackers use www.just-ping.com to accomplish this task. Basically, www.just-ping.com pings any website from various parts of the globe.
To use this tool, just enter the target’s URL or IP address into the textbox and hit “ping!” Here’s a screenshot:
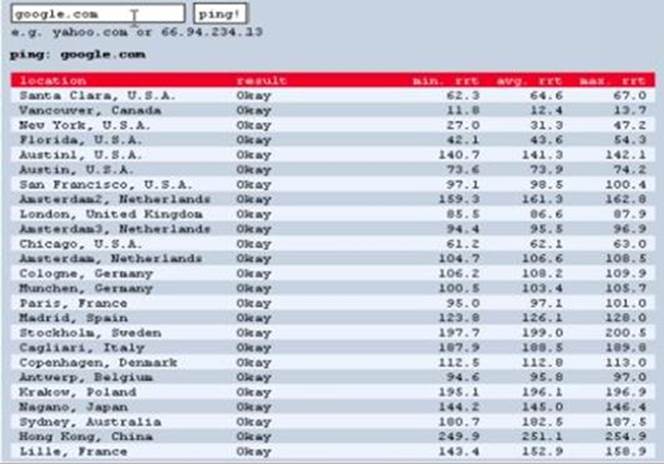
The webpage will show you whether the target is active or not.
4. Perform a WHOIS search on the website. Visit http://whois.domaintools.com and enter the target’s URL. The screen will show you lots of data about the person/company/organization that owns the target website.
Important Note: A WHOIS search provides hackers with different types of information such as names, addresses and phone numbers. This search also gives website-specific details (e.g. the website’s DNS, the domain’s expiration date, etc.).
Port Scanning
This is the second phase of the hacking process. After collecting information about the target, you should perform a“port scan.” Basically, a“port scan” is a process that detects the open ports and listening devices present in a network. That means you can use this step to identify the target’s weaknesses and defense systems.
The following exercise will illustrate how port scanning works:
1. Download Nmap from this site: http://nmap.org/download.html. Then, install the program into your computer.
Note: This software works for Windows and Macintosh computers.
2. Launch Nmap and enter the target’s URL. For this exercise, let’s assume that you want to hack a site called www.target-site.com.
3. Look for the “Profile” section and click on its dropdown button. The screen will show you several scanning options. Most of the time, elite hackers perform quick (and light) scans on their targets. Full version scans may trigger the target’s defense systems, so it would be best if you’ll stay away from those options. Here’s a screenshot of the dropdown menu:
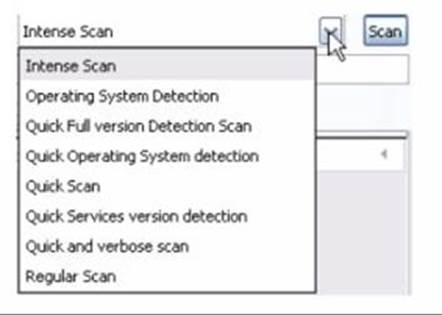
4. Hit the “Scan” button and wait for the results. Here’s a sample:
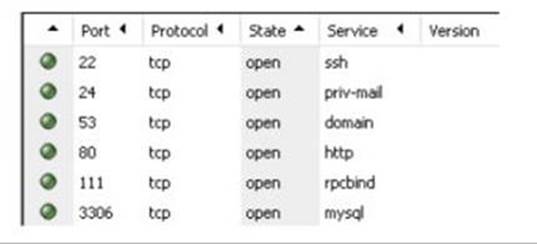
As you can see, Nmap can detect the ports and services present in the target.
Banner Grabbing
In this phase, you’ll get more information about the target’s ports and services. Hackers use telnet to get accomplish this task. The following exercise will help you to understand this phase:
1. Access your computer’s terminal (if you’re a Mac user) or command prompt (if you’re a Windows user).
Important Note: If your operating system is Windows Vista, you have to install telnet manually. Here’s what you need to do:
1. Go to the Control Panel and click on “Programs and Features”.
2. Hit “Turn Windows features on or off” and choose “Telnet Client”.
3. Hit the OK button.
4. The screen will show you a confirmation message.
2. Choose an open port. For this exercise, let’s assume that you selected port 21 (i.e. the FTP port). To determine the FTP software used by the target, use this syntax: telnet <the target’s URL> <the port number you selected>
For the present example, the command that you should run is:
telnet www.target-site.com 21
3. Your computer will determine the type and version of the selected port. Then, it will show the information on your screen. Here’s a sample:
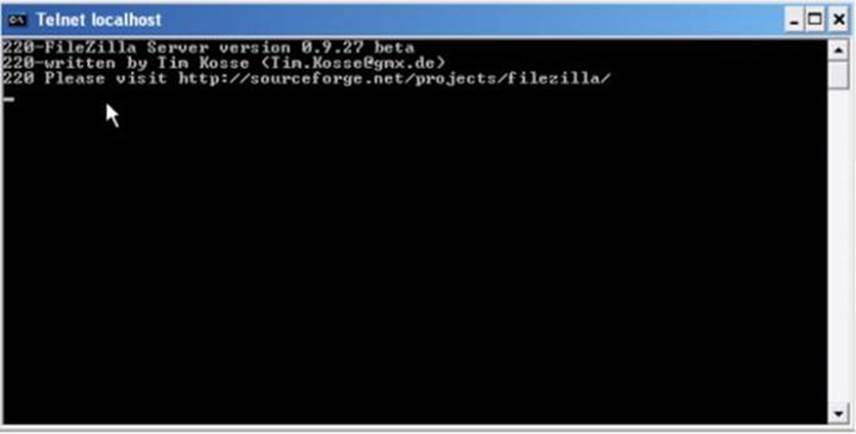
Looking for Weaknesses
Now that you have some information about the port’s software, you may start looking for an available“exploit” (i.e. a tool used for hacking computers/networks). If an exploit is available, you may use it on the targeted service and assume total control. If no exploit is available, on the other hand, you have to work on a different port.
Here are the exploit databases commonly used by hackers:
· osvdb
· exploit-db
· SecurityFocus
Many hackers look for another port when they don’t have an exploit for the current one. However, you can’t assume that all hackers will. Some hackers, particularly the experienced ones, will analyze the targeted port, look for weaknesses and create an exploit. Computer hackers refer to newly discovered weaknesses as“0-day.” These weaknesses offer the following benefits:
· Nobody knows how to fix the weakness. That means you may hack countless websites before the weakness is discovered and fixed.
· The discoverer may sell the weakness for a lot of money. People are willing to spend hundreds (or even thousands) of dollars just to get their hands on fresh vulnerabilities.
· Discovering network weaknesses and generating an exploit for them shows that you are skilled and knowledgeable. Other hackers will consider you as an expert.
The Most Common Hacking Attacks
Prior to discussing actual network penetrations, let’s talk about two of the most popular hacking attacks.
DoS– This is the abbreviation for“Denial-of-Service.” With this attack, the hacker wants to take down the server. That means legitimate users won’t be able to access the network or use the affected service/s. Most of the time, hackers accomplish this by sending an endless stream of data to the target network. This tactic forces the network to spend all available resources. Once the resources have been consumed, nobody will be able to use the network.
Buffer Overflow– Hackers also refer to this attack as“BoF.” Buffer overflow attacks occur when a computer program tries to save loads of data into a storage area (also known as“buffer”). Since buffers have limited storage capacity, the excess data goes to other areas. When this happens, the hacker may flood the network with malicious codes.
Two Types of Exploits
Hackers divide exploits into two categories, namely:
Local Exploits– These exploits require the hacker to access the target computer physically. In general, attackers use this exploit to escalate their access privileges on the machine or network. Simply put, you may use a local exploit to have admin privileges over your target.
Remote Exploits– These exploits are similar to their local counterparts. The only difference is that hackers may run a remote exploit without accessing the target physically; thus, remote exploits are safer in comparison to local ones.
Important Note: Most of the time, hackers use both types of exploits in their attacks. For instance, you may use a remote exploit to gain ordinary privileges. Then, you can use a local exploit to have admin access to the target. This approach allows you to control a machine or network completely.
Penetrating
This section will teach you how hackers penetrate their targets.
Programming Languages
While practicing your hacking skills, you’ll discover that hackers use different programming languages in creating exploits. The following list shows the most popular programming languages today:
· PHP – You’ll find lots of PHP exploits these days. When writing an exploit using this language, you have to start the code with “<?php” and end it with “?>”. Let’s assume that you want to inflict some temporary damages to an FTP server. If you’ll use the Exploit-DB database, you will find this exploit:
https://www.exploit-db.com/exploits/39082/
Here are the steps you need to take to when hacking a target:
1. Install the PHP language into your computer. You may visit this site to get PHP for free.
2. Copy the PHP code from Exploit-DB and paste it onto a word processor. Save the file as “exploit.php”.
3. Go to the 13th line of the exploit and enter your target’s IP address. Save the modified file into your computer’s PHP directory (i.e. the directory that contains the PHP .exe file).
4. Access your computer’s command prompt. Then, run the CD (i.e. change directory) command and specify the location of the PHP directory.
5. Type “php exploit.php” and press the Enter key.
6. Your computer will launch a DoS attack against your target. The attack will only stop once you close the command prompt.
7. Test the effects of your attack. To do this, visit the target website and click on the tabs/buttons. If the attack is successful, the website will lag and experience unusually long load times. After some time, the site may go offline completely.
· Perl – This language is as easy and simple as PHP. To use this programming language, you should:
1. Visit this site: http://www.activestate.com/activeperl. Then, download and install the right version of Perl.
2. Look for an exploit that you can use. For this book, let’s assume that you want to attack a WinFTP server using this exploit:
https://www.exploit-db.com/exploits/36861/
3. Modify the code by entering the required information (e.g. the URL of your target, the port you want to attack, etc.). Then, copy it onto a text file and save the document as “exploit.pl”.
4. Access the command prompt. Specify the location of the Perl file using the Change Directory command.
5. Type “perl exploit.pl” to run the exploit. The program will launch a DoS attack against your target. Just like in the previous example, this exploit will only stop once you close the command prompt window.