Ubuntu Unleashed 2017 Edition (2017)
Part IV: Ubuntu as a Server
Chapter 32. Lightweight Directory Access Protocol (LDAP)
In This Chapter
![]() Configuring the Server
Configuring the Server
![]() Configuring Clients
Configuring Clients
![]() Administration
Administration
![]() References
References
The Lightweight Directory Access Protocol (LDAP, pronounced ell-dap) is one of those technologies that, although hidden, forms part of the core infrastructure in enterprise computing. Its job is simple: It stores information about users. However, its power comes from the fact that it can be linked into dozens of other services. LDAP can power login authentication, public key distribution, email routing, and address verification; more recently, it has formed the core of the push toward single sign-on technology.
Tip
Most people find the concept of LDAP easier to grasp when they think of it as a highly specialized form of database server. Behind the scenes, Ubuntu uses a database for storing all its LDAP information; however, LDAP does not offer anything as straightforward as SQL for data manipulation.
OpenLDAP uses Sleepycat Software’s Berkeley DB (BDB), and sticking with that default is highly recommended. However, alternatives exist if you have specific needs.
This chapter looks at a relatively basic installation of an LDAP server, including how to host a companywide directory service that contains the names and email addresses of employees. LDAP is a client/server system, meaning that an LDAP server hosts the data and an LDAP client queries it. Ubuntu comes with OpenLDAP as its LDAP server, along with several LDAP-enabled email clients, including Evolution and Mozilla Thunderbird. This chapter covers all three of these applications.
Because LDAP data is usually available over the Internet—or at least your local network—it is imperative that you make every effort to secure your server. This chapter gives specific instruction on password configuration for OpenLDAP, and we recommend you follow the instructions closely.
Configuring the Server
If you have been using LDAP for years, you will be aware of its immense power and flexibility. But if you are just trying LDAP for the first time, it will seem like the most broken component you could imagine. LDAP has specific configuration requirements, is vastly lacking in graphical tools, and has a large number of acronyms to remember. On the bright side, all the hard work you put in is worth it because when it works LDAP improves your networking experience immensely. You should read the entire chapter and understand it before you start. Then, read the README file in /etc/ldap/schema before you do anything.
The first step in configuring your LDAP server is to install the client and server applications. Install the slapd and ldap-utils packages from the Ubuntu repositories. Doing so also installs three other packages: odbcinst, odbcinstdebian2, and unixodbc.
By default, Ubuntu configures slapd with the minimum options necessary to run the daemon. We are going to configure everything from that bare-bones installation up to where it will be useful.
Now you need to know the fully qualified domain name (FQDN) of your server. In a moment, you will begin to write/modify some configuration files, and this will be a vital part of that process. The example uses matthewhelmke.com. Whenever you see this, change it to your FQDN.
From the FQDN you acquire your domain component, which is the name of your domain as stored in DNS. This is abbreviated as dc. LDAP considers each part of a domain name (separated by a dot) to be domain components. In the example, there are two dc items: matthewhelmke and com.
OpenLDAP now uses a separate directory containing the cn=config Directory Information Tree (DIT) to configure the slapd daemon dynamically. This enables you to modify schema definitions, indexes, and so on without stopping and restarting the service, as was required in earlier versions. You need two files for this configuration: a back end that has only a minimal configuration and a front end that uses a traditional format that is compatible with and accessed by external programs using established standards.
Creating Your Schema
Start by loading some premade schema files. This makes configuration faster and easier by preloading some settings. If you are building an enterprise server, read the official OpenLDAP documentation and start from scratch so that you know precisely what everything on your server is doing and why. For the example, load these three files into the directory using these commands:
Click here to view code image
matthew@seymour:~$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/ldap/schema/cosine.ldif
matthew@seymour:~$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/ldap/schema/nis.ldif
matthew@seymour:~$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/ldap/schema/inetorgperson.ldif
Next, create a file called backend.matthewhelmke.com.ldif with these contents:
Click here to view code image
# Load dynamic backend modules
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulepath: /usr/lib/ldap
olcModuleload: back_hdb
# Database settings
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {1}hdb
olcSuffix: dc=matthewhelmke,dc=com
olcDbDirectory: /var/lib/ldap
olcRootDN: cn=admin,dc=matthewhelmke,dc=com
olcRootPW: changeMEtoSOMETHINGbetter
olcDbConfig: set_cachesize 0 2097152 0
olcDbConfig: set_lk_max_objects 1500
olcDbConfig: set_lk_max_locks 1500
olcDbConfig: set_lk_max_lockers 1500
olcDbIndex: objectClass eq
olcLastMod: TRUE
olcDbCheckpoint: 512 30
olcAccess: to attrs=userPassword by dn="cn=admin,dc=matthewhelmke,dc=com" write by
anonymous auth by self write by * none
olcAccess: to attrs=shadowLastChange by self write by * read
olcAccess: to dn.base="" by * read
olcAccess: to * by dn="cn=admin,dc=matthewhelmke,dc=com" write by * read
Make sure you change all instances of matthewhelmke and com to fit your FQDN and change the entry for olcRootPW to a more secure password of your choosing. Then, add the new file to the directory (I am assuming you are entering this command from the directory where the file was created):
Click here to view code image
matthew@seymour:~$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f backend.example.
com.ldif
Populating Your Directory
The back end is ready. Now you need to populate the front-end directory to make this useful. Create another file called frontend.matthewhelmke.com.ldif with the following contents:
Click here to view code image
# Create top-level object in domain
dn: dc=matthewhelmke,dc=com
objectClass: top
objectClass: dcObject
objectclass: organization
o: Example Organization
dc: Example
description: LDAP Example
# Admin user.
dn: cn=admin,dc=matthewhelmke,dc=com
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
userPassword: changeMEtoSOMETHINGbetter
dn: ou=people,dc=example,dc=com
objectClass: organizationalUnit
ou: people
dn: ou=groups,dc=matthewhelmke,dc=com
objectClass: organizationalUnit
ou: groups
dn: uid=john,ou=people,dc=matthewhelmke,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: matthew
sn: Helmke
givenName: Matthew
cn: Matthew Helmke
displayName: Matthew Helmke
uidNumber: 1000
gidNumber: 10000
userPassword: changeMEtoSOMETHINGbetter
gecos: Matthew Helmke
loginShell: /bin/bash
homeDirectory: /home/matthew
shadowExpire: -1
shadowFlag: 0
shadowWarning: 7
shadowMin: 8
shadowMax: 999999
shadowLastChange: 10877
mail: matthew@matthewhelmke.com
postalCode: 85711
l: Tucson
o: Example
mobile: +1 (520) xxx-xxxx
homePhone: +1 (520) xxx-xxxx
title: System Administrator
postalAddress: I'm not putting it in the book.
initials: MH
dn: cn=example,ou=groups,dc=example,dc=com
objectClass: posixGroup
cn: example
gidNumber: 10000
Remember to change the details to fit your information. Then add this to the LDAP directory:
Click here to view code image
matthew@seymour:~$ sudo ldapadd -x -D cn=admin,dc=example,dc=com -W -f
frontend.example.com.ldif
To check that your content has been added to the LDAP directory correctly, you can use ldapsearch, as follows:
Click here to view code image
matthew@seymour:~$ ldapsearch -xLLL -b "dc=example,dc=com" uid=john sn givenName cn
dn: uid=matthew,ou=people,dc=matthewhelmke,dc=com
cn: Matthew Helmke
sn: Helmke
givenName: Matthew
In this example, dn stands for distinguished name, uid refers to user identification, ou tells the organizational unit, dc represents domain component, cn is common name, sn is the family or surname, and many cultures know givenName as your first name.
When you use LDAP, you can organize your data in many ways. You can use a number of currently existing schemas, such as in the previous example using the LDIF files you loaded at the start, or you can write your own. The /etc/ldap/schemas directory has many fine examples in the files with a .schema suffix and a few that have been converted to LDAP Data Interchange Format (LDIF). To be used, the file must be in the LDIF (or when used as a file suffix, .ldif). You can convert one of the example schemas or create your own schema.
Configuring Clients
Although Ubuntu comes with a selection of email clients, there is not enough room here to cover them all. So, we discuss the two most frequently used clients: Evolution, the default; and Thunderbird. Both are powerful messaging solutions and so both work well with LDAP. Of the two, Thunderbird seems to be the easier to configure. We have had various problems with Evolution in the past in situations where Thunderbird has worked the first time.
Evolution
To configure Evolution for LDAP, click the arrow next to the New button and select Address Book. A new screen appears; its first option prompts you for the type of address book to create. Select On LDAP Servers.
For Name, just enter Address book, and for Server, enter the IP address of your LDAP server (or 127.0.0.1 if you are working on the server), as shown in Figure 32.1. Leave the port as 389, which is the default for slapd. Switch to the Details tab and set Search Base to be the entire DN for your address book (for example, ou=People,dc=matthewhelmke,dc=com). Set Search Scope to be Sub so that Evolution performs a comprehensive search. To finish, click Add Address Book.
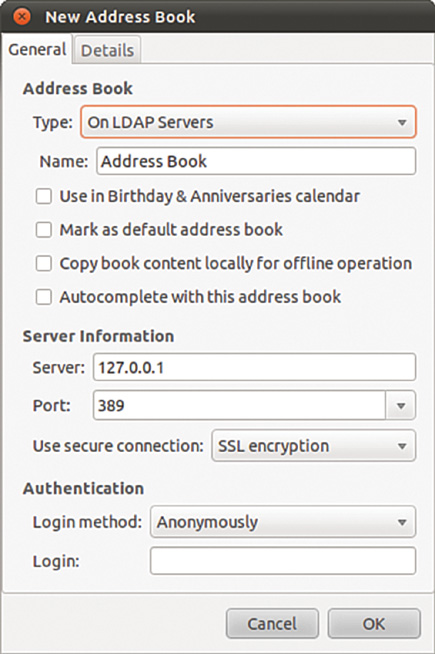
FIGURE 32.1 Configuring Evolution to use LDAP for addresses is easy for anonymous connections.
Thunderbird
Thunderbird is a little easier to configure than Evolution and tends to work better, particularly with entries that have multiple CNs. To enable it, go to the Edit menu, click Preferences, and then select Composition from the tabs along the top.
From the Addressing subtab, check the Directory Server box and click the Edit Directories button to its right. From the dialog box that appears, click Add to add a new directory. You can give it any name you want because this is merely for display purposes. As shown in Figure 32.2, set the Hostname field to be the IP address of your LDAP server (or 127.0.0.1 if you are working on the server). Set the Base DN to be the DN for your address book (for instance, ou=People,dc=matthewhelmke,dc=com) and leave the port number as 389. Click OK three times to get back to the main interface.
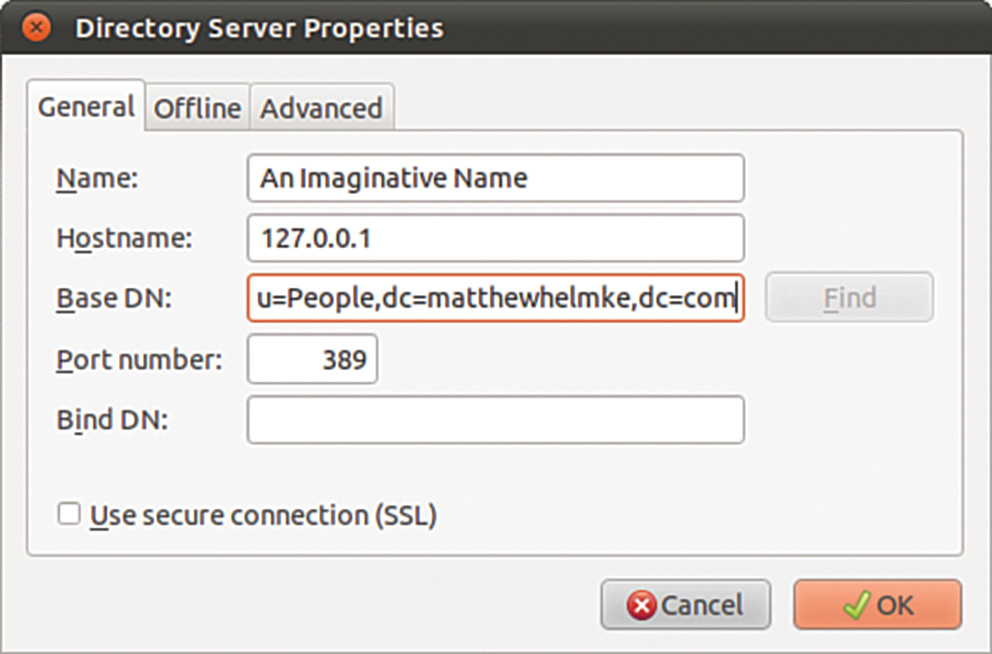
FIGURE 32.2 Thunderbird’s options are buried deeper than Evolution’s, but it does allow you to download the LDAP directory for offline use.
Administration
After you have your LDAP server and clients set up, they require little maintenance until something changes externally. Specifically, if someone in your directory changes jobs, changes her phone number, gets married (changing her last name [surname]), quits, or so forth, you need to be able to update your directory to reflect the change.
You installed some useful utilities with the ldap-utils package earlier. Here are what they do. Each one requires administration privileges, so use sudo.
![]() ldapsearch—Opens a connection to an LDAP server and searches its directory for requested information
ldapsearch—Opens a connection to an LDAP server and searches its directory for requested information
![]() ldapmodify—Opens a connection to an LDAP server and allows you to add or modify entries
ldapmodify—Opens a connection to an LDAP server and allows you to add or modify entries
![]() ldapadd—Opens a connection to an LDAP server and allows you to add an entry
ldapadd—Opens a connection to an LDAP server and allows you to add an entry
![]() ldapdelete—Opens a connection to an LDAP server and allows you to delete one or more entries
ldapdelete—Opens a connection to an LDAP server and allows you to delete one or more entries
None of these are simple to use, but all come with moderate amounts of documentation in their man pages.
A much smarter option is to use phpLDAPadmin, which is an LDAP administration tool that enables you to add and modify entries entirely through your web browser. The program is available in the Ubuntu software repositories as phpldapadmin.
Starting, stopping, or restarting the slapd daemon is done in the usual way for system daemons (that do not yet have Upstart methods written for them):
Click here to view code image
sudo /etc/init.d/slapd start/stop/restart
References
![]() www.openldap.org—The home page of the OpenLDAP project where you can download the latest version of the software and meet other users.
www.openldap.org—The home page of the OpenLDAP project where you can download the latest version of the software and meet other users.
![]() http://ldap.perl.org/—The home of the Perl library for interacting with LDAP provides comprehensive documentation to get you started.
http://ldap.perl.org/—The home of the Perl library for interacting with LDAP provides comprehensive documentation to get you started.
![]() https://help.ubuntu.com/lts/serverguide/openldap-server.html—Official Ubuntu Server documentation for OpenLDAP.
https://help.ubuntu.com/lts/serverguide/openldap-server.html—Official Ubuntu Server documentation for OpenLDAP.
![]() http://phpldapadmin.sourceforge.net/—The official documentation for phpLDAPadmin.
http://phpldapadmin.sourceforge.net/—The official documentation for phpLDAPadmin.
![]() The definitive book on LDAP is LDAP System Administration (O’Reilly) by Gerald Carter, ISBN: 1-56592-491-6. It is an absolute must for the bookshelf of any Linux LDAP administrator. For more general reading, try LDAP Directories Explained (Addison-Wesley) by Brian Arkills, ISBN: 0-201-78792-X. It has a much stronger focus on the Microsoft Active Directory LDAP implementation, however.
The definitive book on LDAP is LDAP System Administration (O’Reilly) by Gerald Carter, ISBN: 1-56592-491-6. It is an absolute must for the bookshelf of any Linux LDAP administrator. For more general reading, try LDAP Directories Explained (Addison-Wesley) by Brian Arkills, ISBN: 0-201-78792-X. It has a much stronger focus on the Microsoft Active Directory LDAP implementation, however.