Exam Ref 70-696 Managing Enterprise Devices and Apps (2014)
Chapter 1. Deploy and manage virtual applications
Virtualized applications provide administrators with more options than traditional applications. Rather than always requiring deployment through local installation, you can stream virtualized applications to clients. Virtualized applications don’t make modifications to a client’s registry or file system, so they can be removed as cleanly as they are installed. In this chapter, you learn about how to virtualize traditional applications, how to manage a virtualized application environment, and how to use RemoteApp to provide users with local access to applications running on remote servers.
Objectives in this chapter:
![]() Objective 1.1: Prepare virtual applications.
Objective 1.1: Prepare virtual applications.
![]() Objective 1.2: Manage application virtualization environments.
Objective 1.2: Manage application virtualization environments.
![]() Objective 1.3: Deploy and manage RemoteApp.
Objective 1.3: Deploy and manage RemoteApp.
Objective 1.1: Prepare virtual applications
Microsoft Application Virtualization (App-V) is a technology that enables you to virtualize applications so that they run in an environment that shields them from directly interacting with the operating system. Then you can run applications concurrently that are incompatible with each other. You use a special tool known as a sequencer to virtualize applications.
This section covers the following topics:
![]() Application virtualization concepts
Application virtualization concepts
![]() Sequencing an application
Sequencing an application
![]() Preparing the Sequencer environment
Preparing the Sequencer environment
![]() App-V Connection Groups
App-V Connection Groups
Application virtualization concepts
Users can use application virtualization to run applications locally even though those applications are not installed directly on the client computers. This works because App-V client software is installed directly on the client computers and simulates a specially prepared operating system environment. Virtualized applications run within that specially prepared simulated environment.
Virtualized applications do not interact directly with the client operating system but instead interact with the App-V client. The App-V client functions as a proxy through which the application uses operating system resources.
App-V provides the following benefits over traditionally deployed, locally installed applications. With App-V, you can:
![]() Run multiple versions of applications without conflict You can use App-V to run different versions of applications concurrently on the same client computer. For example, it is possible to run Microsoft Word 2007, Word 2010, and Word 2013 concurrently if they are all set up as App-V applications; otherwise, you cannot run these applications side by side on the same client computer. It also is possible to use App-V in conjunction with Remote Desktop Services (RDS). This enables users to run applications side by side on Remote Desktop Session Host servers.
Run multiple versions of applications without conflict You can use App-V to run different versions of applications concurrently on the same client computer. For example, it is possible to run Microsoft Word 2007, Word 2010, and Word 2013 concurrently if they are all set up as App-V applications; otherwise, you cannot run these applications side by side on the same client computer. It also is possible to use App-V in conjunction with Remote Desktop Services (RDS). This enables users to run applications side by side on Remote Desktop Session Host servers.
![]() Minimize application conflict Sometimes two or more applications cause conflicts with each other because of dynamic-link library (DLL) or application programming interface (API) conflicts. However, when you install these applications as App-V applications, there is no conflict because each App-V application runs in its own isolated environment.
Minimize application conflict Sometimes two or more applications cause conflicts with each other because of dynamic-link library (DLL) or application programming interface (API) conflicts. However, when you install these applications as App-V applications, there is no conflict because each App-V application runs in its own isolated environment.
![]() Simplify application removal App-V applications are not installed locally, so they can be removed completely. Clean removal is not always possible with applications that are installed directly on Windows-based clients, even if an application has been designed to remove all files and settings when it is uninstalled. Virtualized applications are easily removed after the user signs out from the computer and can be purged automatically from the App-V client cache.
Simplify application removal App-V applications are not installed locally, so they can be removed completely. Clean removal is not always possible with applications that are installed directly on Windows-based clients, even if an application has been designed to remove all files and settings when it is uninstalled. Virtualized applications are easily removed after the user signs out from the computer and can be purged automatically from the App-V client cache.
![]() Simplify application upgrades Instead of upgrading a locally installed application on all computers in your organization with a hotfix, service pack, or new versions, the modular nature of virtualized applications enables you to replace one version of an application with an updated version with less effort.
Simplify application upgrades Instead of upgrading a locally installed application on all computers in your organization with a hotfix, service pack, or new versions, the modular nature of virtualized applications enables you to replace one version of an application with an updated version with less effort.
![]() Minimize license compliance risks App-V has license group functionality, so you can ensure that only a specific number of users can run an application at any point in time.
Minimize license compliance risks App-V has license group functionality, so you can ensure that only a specific number of users can run an application at any point in time.
![]() Scale infrastructure Depending on the infrastructure model you use, you can add publishing servers to an App-V deployment as necessary to ensure that service levels are maintained as demand grows.
Scale infrastructure Depending on the infrastructure model you use, you can add publishing servers to an App-V deployment as necessary to ensure that service levels are maintained as demand grows.
![]() Take advantage of client hardware resources Even though App-V applications are not installed locally, they can use the local computer’s processor and RAM resources. In environments where client computers have inadequate hardware resources, this can lead to a better experience for the user than running applications on a Remote Desktop Session Host server would.
Take advantage of client hardware resources Even though App-V applications are not installed locally, they can use the local computer’s processor and RAM resources. In environments where client computers have inadequate hardware resources, this can lead to a better experience for the user than running applications on a Remote Desktop Session Host server would.
![]() Enable users to use roaming applications If applications are streamed rather than locally installed, users can sign in to any computer that has an App-V client installed and quickly access their application. You can also configure App-V to work with Microsoft User Experience Virtualization to allow users to have application settings for App-V applications roam across client computers.
Enable users to use roaming applications If applications are streamed rather than locally installed, users can sign in to any computer that has an App-V client installed and quickly access their application. You can also configure App-V to work with Microsoft User Experience Virtualization to allow users to have application settings for App-V applications roam across client computers.
![]() Give users quick access to their applications Because the application is streamed, access is faster than if the application is fully deployed from the server after the user is signed in. Depending on how you configure App-V, only some parts of the application prepared with App-V might be downloaded to the client computer. This means the user can start using an application without waiting for the entire application to be streamed from the server. App-V application components can be stored in a nonvola-tile cache, so an App-V application can run when a computer is offline and cannot access the server from which it originally streamed the application.
Give users quick access to their applications Because the application is streamed, access is faster than if the application is fully deployed from the server after the user is signed in. Depending on how you configure App-V, only some parts of the application prepared with App-V might be downloaded to the client computer. This means the user can start using an application without waiting for the entire application to be streamed from the server. App-V application components can be stored in a nonvola-tile cache, so an App-V application can run when a computer is offline and cannot access the server from which it originally streamed the application.
![]() Increase security for sensitive applications You can also configure the App-V client through Group Policy to ensure that applications can be run only when the computer is online. You can use Group Policy to provide sensitive applications to users in environments where employees are using their personal devices while ensuring that these sensitive applications are not available when the user leaves the organization premises.
Increase security for sensitive applications You can also configure the App-V client through Group Policy to ensure that applications can be run only when the computer is online. You can use Group Policy to provide sensitive applications to users in environments where employees are using their personal devices while ensuring that these sensitive applications are not available when the user leaves the organization premises.
More Info: App-V 5.0 Overview
You can learn more about App-V 5.0 at http://technet.microsoft.com/en-us/windows/jj835807.aspx.
Sequencing an application
Sequencing enables you to create a special version of a normal application that can run in the virtual environment the App-V client provides. In the sequencing process, the Application Virtualization Sequencer records all the modifications the application makes to files and settings during installation.
For example, when you install an application, sequencing writes program files to a particular directory, writes entries to the registry, and creates or modifies initialization (.ini) files and environment variables. The sequencing process records all the information necessary to run the program within the environment the App-V client provides.
The sequencing process involves the following general steps:
1. The Sequencer triggers the application’s standard installation process. It then records the following:
![]() Files that have been installed
Files that have been installed
![]() Registry settings that have been modified
Registry settings that have been modified
![]() Environment variables that have been configured
Environment variables that have been configured
![]() Dynamic-link libraries (DLLs) that have been registered
Dynamic-link libraries (DLLs) that have been registered
![]() Any other changes that have occurred to the system
Any other changes that have occurred to the system
2. The Sequencer creates a virtual environment and loads the application into this environment, including any data and modifications that occurred during the standard installation process.
3. The application starts so that any post-installation configuration tasks can be performed. If this step is not performed during sequencing, users will have to perform these post-installation tasks manually after deployment, storing any configuration settings locally on the client. During this process, the Sequencer determines which program components are required to start the application.
In more detail, to sequence an application you use the Application Virtualization Sequencing Wizard to install the application by performing the following general steps:
1. Open the Sequencer on the client.
2. Create a new virtual application package.
3. Verify that the operating system environment has no issues that might interrupt the sequencing process.
4. Choose the application type.
5. Choose the application installer location.
6. Provide a virtual application package name and a primary virtual application directory. The Sequencer will trigger the installation.
7. Answer questions that the installation routine presents.
These can include questions about license agreements, installation location, and other application installation options.
8. Run any additional files the installation might require.
9. Complete the installation.
10. Perform any post-installation configuration tasks.
11. Review the installation report.
12. Configure the streaming options.
13. Select the target operating system.
14. Create the package.
The Sequencer supports applications that need the computer to restart during the installation process. In these cases, the Sequencer will begin again after the client computer restarts and continues to sequence the application.
The App-V 5.0 Sequencer produces applications that you can use only with the App-V 5.0 client. The App-V 5.0 client cannot run applications sequenced for earlier versions of App-V. You must convert those applications to the App-V 5.0 format before they can run on computers running the App-V 5.0 client. You can run App-V 5.0–sequenced applications only on computers running Windows 8.1, Windows 8, Windows 7, Windows Server 2012, Windows Server 2012 R2, and Windows Server 2008 R2 with the Remote Desktop feature.
Custom installation
When you perform a custom application installation, you do not provide the Sequencer with the path to the application installer. Instead, you perform the application installation outside the Sequencer and have it record the changes that occur to files and settings. Custom installation is similar to a standard installation except that for a custom installation, you must manually trigger the installation rather than use the Sequencer to do this.
Sequencer options
Generally, the default Sequencer settings are appropriate for most application sequencing procedures. In some instances, though, you will want to change some or all of the settings. You can see the settings by clicking Options on the Tools menu of the Sequencer, which opens the Options dialog box. The advanced settings include the following:
![]() Scratch Directory Temporary files are saved in this location.
Scratch Directory Temporary files are saved in this location.
![]() Allow Microsoft Update To Run During Monitoring Microsoft Update runs during the monitoring process. This setting is disabled by default.
Allow Microsoft Update To Run During Monitoring Microsoft Update runs during the monitoring process. This setting is disabled by default.
![]() Append Package Version To Filename The version number is added to the file name. When an application is resequenced, the version is increased by 1.
Append Package Version To Filename The version number is added to the file name. When an application is resequenced, the version is increased by 1.
![]() Always Trust The Source Of Package Accelerators The Sequencer does not generate a prompt when a package accelerator is not signed by a trusted source.
Always Trust The Source Of Package Accelerators The Sequencer does not generate a prompt when a package accelerator is not signed by a trusted source.
![]() Parse Items The Sequencer monitors these areas of the file system and settings when sequencing an application.
Parse Items The Sequencer monitors these areas of the file system and settings when sequencing an application.
![]() Exclusion Items The Sequencer does not monitor these areas of the file system and settings when sequencing an application.
Exclusion Items The Sequencer does not monitor these areas of the file system and settings when sequencing an application.
The App-V Sequencer also supports the following:
![]() Package accelerators Package accelerators automate the sequencing process. They are useful when you need to sequence a particular application frequently.
Package accelerators Package accelerators automate the sequencing process. They are useful when you need to sequence a particular application frequently.
![]() Add-ons or plug-ins You can use the Sequencer to create an add-on or plug-in to extend the functionality of an application. For example, you could create an add-on for a sequenced web browser or a graphic design program. When you install an add-on or plug-in, you install the application first and then add the component.
Add-ons or plug-ins You can use the Sequencer to create an add-on or plug-in to extend the functionality of an application. For example, you could create an add-on for a sequenced web browser or a graphic design program. When you install an add-on or plug-in, you install the application first and then add the component.
![]() Middleware applications Use the middleware application type to sequence middle-ware or framework software that another sequenced application package requires. For example, a particular environment might be required to run a sequenced application. You can sequence this as middleware.
Middleware applications Use the middleware application type to sequence middle-ware or framework software that another sequenced application package requires. For example, a particular environment might be required to run a sequenced application. You can sequence this as middleware.
More Info: Sequencing an Application
You can learn more about sequencing an application at http://technet.microsoft.com/en-us/library/jj713438.aspx.
Preparing the Sequencer environment
The App-V Sequencer requires the following software:
![]() Windows 7 (x86 and x64), Windows 8 (x86 or x64), or Windows 8.1 (x86 or x64)
Windows 7 (x86 and x64), Windows 8 (x86 or x64), or Windows 8.1 (x86 or x64)
![]() Microsoft .NET Framework 3.51 and .NET Framework 4.5 (Full)
Microsoft .NET Framework 3.51 and .NET Framework 4.5 (Full)
![]() Windows PowerShell 3.0 (included with Windows 8.1 and Windows 8)
Windows PowerShell 3.0 (included with Windows 8.1 and Windows 8)
![]() Microsoft KB2533623 (an update for Windows 7)
Microsoft KB2533623 (an update for Windows 7)
![]() Microsoft Visual C++ 2008 Redistributable (x86 and x64; executable file install only)
Microsoft Visual C++ 2008 Redistributable (x86 and x64; executable file install only)
Installing the Sequencer involves running an executable file (.exe) or installing from a Windows installer package file (.msi). If you install from the .msi file, you do not need to install the Visual C++ 2008 Redistributable manually.
You should install the Sequencer on a client computer that runs the same operating system as the clients that will run the sequenced applications. When you are selecting the client on which to install the Sequencer, keep the following guidelines in mind:
![]() If your end users are using an x64 version of Windows 7, you should sequence applications on a computer running the x64 version of Windows 7 with the App-V Sequencer installed.
If your end users are using an x64 version of Windows 7, you should sequence applications on a computer running the x64 version of Windows 7 with the App-V Sequencer installed.
![]() If you have a mix of x86 and x64 clients, you can either sequence the x86 version of an application and deploy it to both architectures or sequence the x86 and x64 versions separately.
If you have a mix of x86 and x64 clients, you can either sequence the x86 version of an application and deploy it to both architectures or sequence the x86 and x64 versions separately.
![]() A computer running the Windows 8.1 or Windows 8 operating system will be able to run an application sequenced on a computer running the Windows 7 operating system.
A computer running the Windows 8.1 or Windows 8 operating system will be able to run an application sequenced on a computer running the Windows 7 operating system.
![]() Although an application sequenced on a computer running the Windows 8.1 or Windows 8 operating system will likely run when deployed through App-V to a computer running the Windows 7 operating system, Microsoft does not recommend this strategy. Instead, you should sequence applications that you intend to run on computers running the Windows 7 operating system on a computer running the Windows 7 operating system.
Although an application sequenced on a computer running the Windows 8.1 or Windows 8 operating system will likely run when deployed through App-V to a computer running the Windows 7 operating system, Microsoft does not recommend this strategy. Instead, you should sequence applications that you intend to run on computers running the Windows 7 operating system on a computer running the Windows 7 operating system.
The client that runs the Sequencer should have no applications installed beyond the base operating system and should be as close to the out-of-the-box experience (OOBE) as possible. As a best practice, do not use an existing computer that has had applications installed and then removed, because some applications might not uninstall fully and thus might affect the sequencing process. This is an important part of ensuring that sequencing works correctly. Sequencing involves capturing only those modifications made during application installation; additional applications and certain services can interrupt the sequencing process, causing it to fail.
In addition to these considerations, avoid using operating system images that include clients from antimalware applications and products such as System Center 2012 Configuration Manager or System Center 2012 Data Protection Manager.
Before performing a sequencing operation on a newly installed computer running the Windows 8.1 operating system, you should disable the following services:
![]() Windows Defender service
Windows Defender service
![]() Windows Search service
Windows Search service
Because you need to have the client in as close to an OOBE state as possible each time you sequence an application, it is much more efficient to install the Sequencer on a client that is running as a virtual machine. Then you can use a virtual machine snapshot to return the client to an unmodified configuration after you sequence each application. Ensure that you transfer the sequenced application to a network location before reverting the computer that performs the sequencing role.
More Info: Deploying the Sequencer
You can learn more about deploying the App-V Sequencer at http://technet.microsoft.com/en-us/library/jj713464.aspx.
App-V Connection Groups
Use App-V Connection Groups to group one or more App-V 5.0 packages. All the applications in an App-V Connection Group can interact with one another as if you had installed them on the same device while still isolating them from the rest of the system. System Center 2012 R2 Configuration Manager (or System Center 2012 Configuration Manager SP1) uses App-V virtual environments to take advantage of the functionality of App-V Connection Groups. An administrator defines the requirements for a virtual environment. When a client system meets those requirements, an App-V Connection Group is created on the client.
To create a virtual environment, perform the following general steps:
1. In the Software Library workspace of the Configuration Manager console, expand the Application Management node and click App-V Virtual Environments.
2. On the ribbon of the Configuration Manager console, click Create Virtual Environment.
3. In the Create Virtual Environment dialog box, provide a name for the virtual environment. Figure 1-1 shows this name set to the Adatum App-V virtual environment. Click Add to add an App-V deployment type.
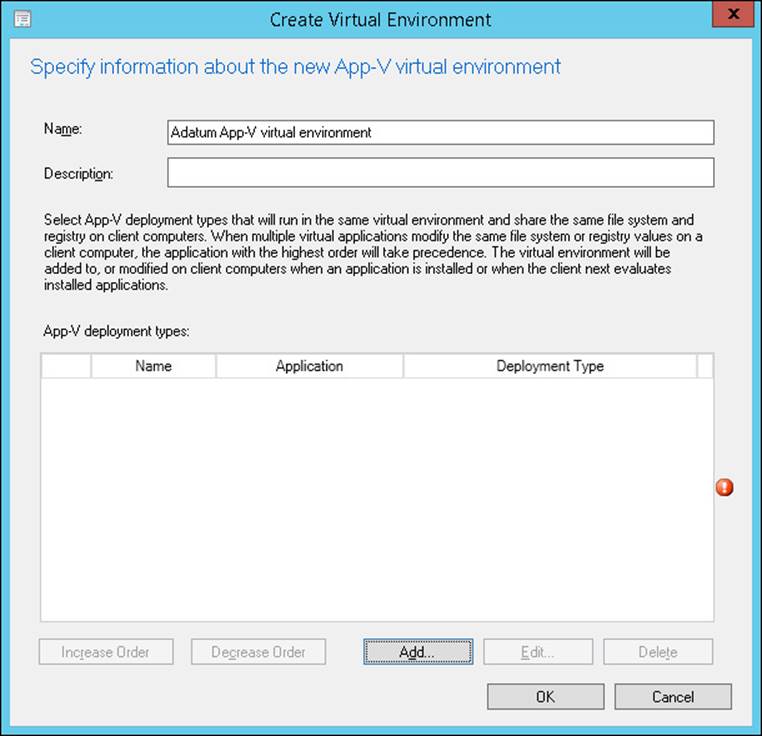
FIGURE 1-1 The Create Virtual Environment dialog box
4. In the Add Applications dialog box, provide a name for the group and click Add to add applications.
5. In the Specify Application dialog box, shown in Figure 1-2, select the application you want to add to the group. Click OK.
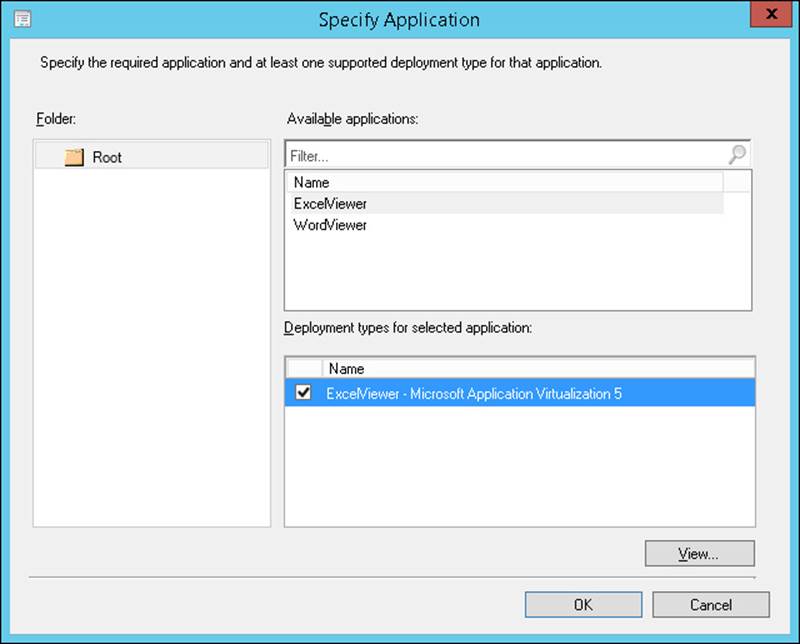
FIGURE 1-2 The Specify Application dialog box
6. In the Add Applications dialog box, add all the applications you want to use with the Connection Group. Figure 1-3 shows ExcelViewer and WordViewer added to the same virtual environment. Click OK.
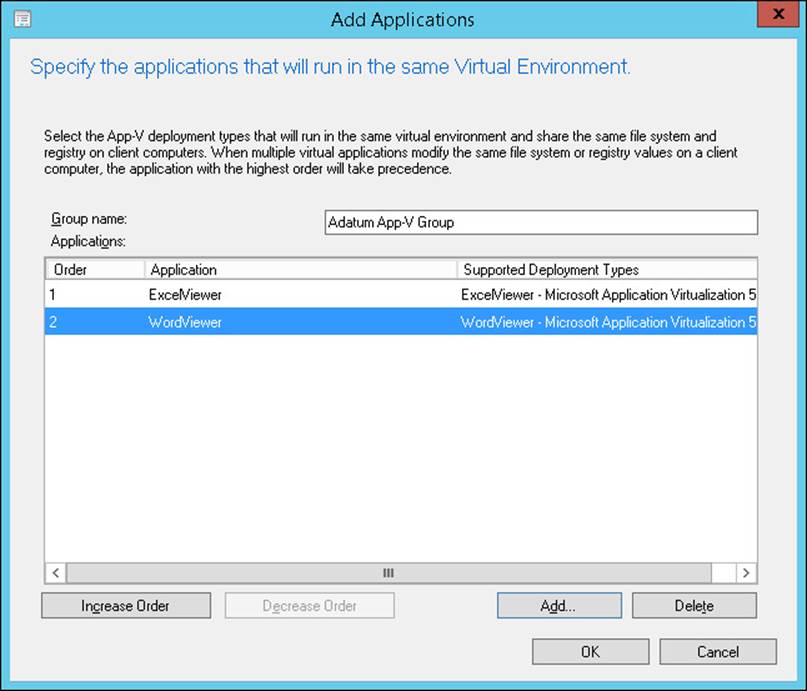
FIGURE 1-3 The Add Applications dialog box
7. In the Create Virtual Environment dialog box, review the applications that have been added to the virtual environment, as shown in Figure 1-4, and then click OK.
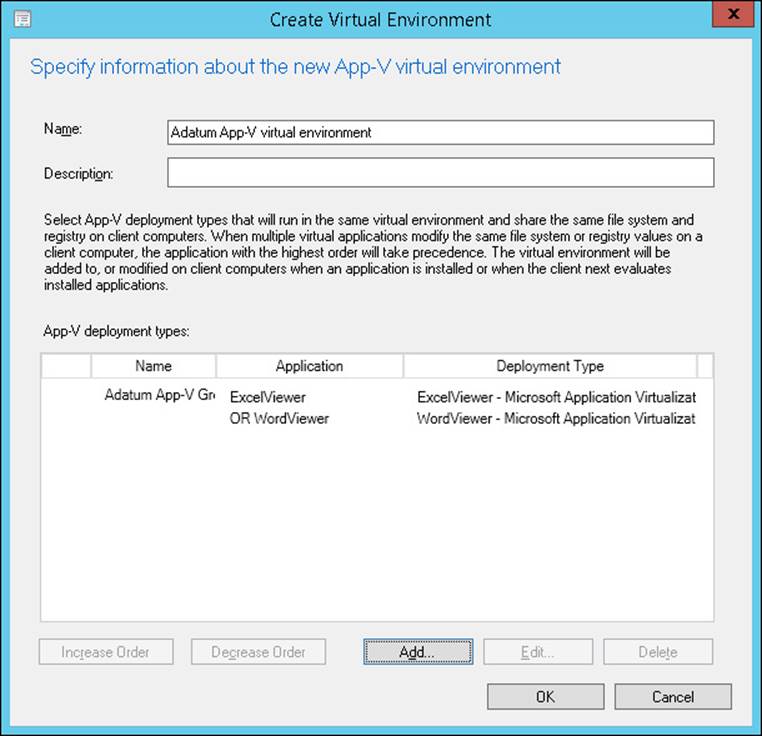
FIGURE 1-4 The Create Virtual Environment dialog box
When migrating existing connection groups from standalone App-V 5.0 virtual environments to virtual environments in which App-V 5.0 is integrated with System Center 2012 R2 Configuration Manager, you must create virtual environments that match the existing connection groups on client computers. You do this so that Configuration Manager manages the clients correctly, and the user’s environment within those connection groups remains the same.
The general process for migrating from App-V Connection Groups to a Configuration Manager virtual environment is as follows:
1. Create applications with Application Virtualization 5.0 deployment types for all existing App-V 5.0 packages for the virtual environments that you want to migrate.
2. Deploy the new applications with the purpose of Required.
3. After you deploy the applications, create virtual environments that match the connection groups they are replacing. The virtual environments must have the same App-V 5.0 deployments types in the same order. If the virtual environments do not match the App-V 5.0 Connection Groups, new connection groups will be created, and any user customizations in the shared isolation environment will be lost.
You can create new virtual environments in System Center 2012 R2 Configuration Manager. New virtual environments must contain at least one App-V deployment. When you deploy an App-V deployment type, the virtual environments associated with the deployment type also are deployed. This enables you to create App-V Connection Groups before all the applications for the new virtual environment are available. To create new App-V virtual environments in the Configuration Manager console, navigate to the Software Library workspace, the Application Management folder, and then the App-V Virtual Environments node. You add App-V deployment types to the virtual environments by using simple rules. An App-V deployment type can belong to more than one virtual environment.
More Info: App-V Connection Groups
You can learn more about App-V Connection Groups at http://technet.microsoft.com/en-us/library/jj713417.aspx.
 Exam Tip
Exam Tip
Remember what steps you need to take to allow virtualized applications to share data.
 Thought experiment: Application sequencing at Contoso
Thought experiment: Application sequencing at Contoso
You are preparing to sequence an important application at Contoso. This application has two versions, an x86 version and an x64 version. You intend to deploy the x86 version to computers running an x86 version of Windows 7. You intend to deploy the x64 version to computers running an x64 version of Windows 8.1. With this information in mind, answer the following questions:
1. How many times should you sequence the application?
2. Which services should you disable on the computer running Windows 8.1 x64 prior to sequencing the application?
Objective summary
![]() A virtualized application is isolated from the host operating system and interacts indirectly with it through the App-V client.
A virtualized application is isolated from the host operating system and interacts indirectly with it through the App-V client.
![]() You should sequence an application on the same platform as you intend to run it.
You should sequence an application on the same platform as you intend to run it.
![]() Applications sequenced on x64 platforms cannot run on x86 platforms, but applications sequenced on x86 platforms can run on x64 platforms.
Applications sequenced on x64 platforms cannot run on x86 platforms, but applications sequenced on x86 platforms can run on x64 platforms.
![]() App-V Connection Groups allow virtualized applications to share data.
App-V Connection Groups allow virtualized applications to share data.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. You use the App-V Sequencer to sequence an x64 application on a computer running Windows 8.1. Which of the following computers can run this application if the App-V client software has been installed? (Choose the best answer.)
A. The x64 version of Windows 8.1
B. The x86 version of Windows 8.1
C. The x64 version of Windows 7
D. The x86 version of Windows 7
2. You want to allow two virtualized applications, App-A and App-B, to share data when running on the same computer. Which of the following should you configure to allow this to occur? (Choose two. Each answer forms a complete solution.)
A. App-V Connection Group
B. App-V virtual environment
C. Plug-ins
D. Middleware application
3. You need to sequence an application that is updated on a regular basis. Which of the following should you use with the App-V Sequencer to automate this process?
A. Connection group
B. Middleware application
C. Add-on or plug-in
D. Package accelerator
Objective 1.2: Manage application virtualization environments
App-V can be run in several ways. You can run an App-V infrastructure with its own servers to stream apps and use a simpler structure by which to virtualize applications but deploy them in a traditional manner. You can also integrate App-V with Configuration Manager. Depending on how you’ve configured your organization’s infrastructure, you can manage App-V apps through Group Policy or through Configuration Manager.
This section covers the following topics:
![]() App-V infrastructure
App-V infrastructure
![]() App-V deployment models
App-V deployment models
![]() Deploying sequenced applications
Deploying sequenced applications
![]() App-V Group Policy
App-V Group Policy
App-V infrastructure
An App-V 5.0 deployment includes several elements, some of which must be present in all App-V 5.0 models and some of which are used only in specific App-V deployments.
These elements are as follows:
![]() Management Server The Management Server hosts a Microsoft Silverlight–enabled web application that App-V administrators use to manage the App-V infrastructure. The Management Server must have a good connection to the Management Server database. You can deploy the Management Server and Management Server database on the same server or on different servers.
Management Server The Management Server hosts a Microsoft Silverlight–enabled web application that App-V administrators use to manage the App-V infrastructure. The Management Server must have a good connection to the Management Server database. You can deploy the Management Server and Management Server database on the same server or on different servers.
![]() Publishing Server The Publishing Server is a web server that deploys applications to App-V clients. In previous versions of App-V, the Publishing Server was known as the streaming server. You deploy App-V applications to the Publishing Server in the App-V full infrastructure model by using the App-V Management Server console. App-V 5.0 applications are streamed from the Publishing Server by using HTTP.
Publishing Server The Publishing Server is a web server that deploys applications to App-V clients. In previous versions of App-V, the Publishing Server was known as the streaming server. You deploy App-V applications to the Publishing Server in the App-V full infrastructure model by using the App-V Management Server console. App-V 5.0 applications are streamed from the Publishing Server by using HTTP.
![]() Management Server database The Management Server database stores App-V configuration and settings data. The database is hosted on an SQL instance running SQL Server 2008 SP2, SQL Server 2008 R2, or SQL Server 2012. You can install the Management Server database separately from the Management Server, but if you do, you need to deploy the database first and then specify its location when you deploy the Management Server.
Management Server database The Management Server database stores App-V configuration and settings data. The database is hosted on an SQL instance running SQL Server 2008 SP2, SQL Server 2008 R2, or SQL Server 2012. You can install the Management Server database separately from the Management Server, but if you do, you need to deploy the database first and then specify its location when you deploy the Management Server.
![]() Reporting Server The Reporting Server records the following information: application use, client information, package information, schema changes, and system options. You configure the address of the Reporting Server by using App-V Group Policy settings. Clients forward data to this address, which the Reporting Server then forwards to the Reporting Server database.
Reporting Server The Reporting Server records the following information: application use, client information, package information, schema changes, and system options. You configure the address of the Reporting Server by using App-V Group Policy settings. Clients forward data to this address, which the Reporting Server then forwards to the Reporting Server database.
![]() Reporting Server database The Reporting Server database stores all the information forwarded to the Reporting Server. The instance that hosts the Reporting Server database must meet the same requirements as the instance that hosts the Management Server database. You can host both databases on the same server. You do not have to install SQL Server Reporting Services to deploy an App-V Reporting Server.
Reporting Server database The Reporting Server database stores all the information forwarded to the Reporting Server. The instance that hosts the Reporting Server database must meet the same requirements as the instance that hosts the Management Server database. You can host both databases on the same server. You do not have to install SQL Server Reporting Services to deploy an App-V Reporting Server.
App-V deployment models
App-V has three deployment models, each of which has separate infrastructure requirements. These are the full infrastructure model, the standalone model, and the Configuration Manager integrated model.
More Info: App-V Deployment Models
You can learn more about the full infrastructure model and the standalone model at http://technet.microsoft.com/en-us/library/dn595131.aspx.
Full infrastructure model
The App-V full infrastructure model, also known as the Enterprise model, uses all App-V server elements. It also requires the Sequencer to sequence applications and the App-V client deployed on client computers.
The App-V full infrastructure model provides an organization with all the functions of the Management Server, including authentication, instance limitation, and application metering. These functions have the following properties:
![]() Authentication You can use this to limit applications to specific authorized users. For example, members of the Research department can run a specific application but members of the Management department cannot run the application.
Authentication You can use this to limit applications to specific authorized users. For example, members of the Research department can run a specific application but members of the Management department cannot run the application.
![]() Instance limitation You can use a Management Server to limit the number of execution instances of a specific application to ensure that your organization meets its licensing obligations. Virtualized applications can be streamed to multiple computers, making it more challenging to ensure that instances of the application for which the organization is not licensed are not being run.
Instance limitation You can use a Management Server to limit the number of execution instances of a specific application to ensure that your organization meets its licensing obligations. Virtualized applications can be streamed to multiple computers, making it more challenging to ensure that instances of the application for which the organization is not licensed are not being run.
![]() Application metering You can generate historical data, recording how often an application is used and by which clients.
Application metering You can generate historical data, recording how often an application is used and by which clients.
When you use the App-V full infrastructure model, you should ensure that Publishing Servers have high-speed connections to the clients that use these applications. This ensures that users who use streaming applications get access to them quickly. Users who access applications from publishing servers located across wide area network (WAN) links have to wait much longer for their applications to open than users who access publishing servers on the local area network (LAN).
The App-V full infrastructure model is appropriate for organizations that:
![]() Need support for streamed applications.
Need support for streamed applications.
![]() Need authentication, instance limitation, and metering.
Need authentication, instance limitation, and metering.
![]() Have not already deployed Configuration Manager.
Have not already deployed Configuration Manager.
If an organization does not need to support streamed applications and does not require authentication, instance limitation, and metering functionality, it could use the standalone deployment method, which needs less infrastructure investment.
Standalone deployment model
The standalone deployment model is the least infrastructure-intensive version of application virtualization. It needs only a computer configured as an App-V Sequencer and clients with the App-V client installed. The standalone deployment model does not need a Management Server database, Publishing Server, or Management Server.
In the standalone deployment model, you use the App-V Sequencer to create sequenced App-V applications as packages in MSI format. You then deploy those sequenced applications in the same way you would deploy other applications in MSI format—for example, by using Group Policy, Microsoft Intune, System Center 2012 Configuration Manager SP1, or third-party application deployment technologies. The primary difference between deploying a traditional application in MSI format and deploying a sequenced, virtualized application in MSI format is that with the virtualized applications, you have to ensure that the App-V client is installed on the target device.
The standalone deployment model is appropriate for organizations that:
![]() Want the benefit of virtualized applications but do not need metering or application streaming.
Want the benefit of virtualized applications but do not need metering or application streaming.
![]() Want to deploy virtualized applications to clients on the Internet through Intune.
Want to deploy virtualized applications to clients on the Internet through Intune.
![]() Need to deploy only a small number of virtualized applications and so do not need to deploy the App-V full infrastructure model Configuration Manager.
Need to deploy only a small number of virtualized applications and so do not need to deploy the App-V full infrastructure model Configuration Manager.
Configuration Manager integrated model
The integrated model uses Configuration Manager to manage and measure the deployment of App-V virtualized applications. This deployment model uses the following components:
![]() App-V Sequencer You use this to create sequence App-V applications in App-V 5.0 format. You can also use the Sequencer to sequence applications in MSI format, which you can deploy using Configuration Manager.
App-V Sequencer You use this to create sequence App-V applications in App-V 5.0 format. You can also use the Sequencer to sequence applications in MSI format, which you can deploy using Configuration Manager.
![]() App-V client You need to deploy the App-V client to devices that want to access virtualized applications.
App-V client You need to deploy the App-V client to devices that want to access virtualized applications.
![]() Configuration Manager You manage and deploy virtualized applications to collections of computers by using Configuration Manager. Virtualized applications are streamed from Configuration Manager distribution points. To use all the features of App-V 5.0, you must have deployed System Center 2012 Configuration Manager SP1 or System Center 2012 R2 Configuration Manager.
Configuration Manager You manage and deploy virtualized applications to collections of computers by using Configuration Manager. Virtualized applications are streamed from Configuration Manager distribution points. To use all the features of App-V 5.0, you must have deployed System Center 2012 Configuration Manager SP1 or System Center 2012 R2 Configuration Manager.
In this integrated model, virtualized applications are deployed as Configuration Manager applications by using the special App-V 5.0 application type rather than from a Publishing Server.
When you use the App-V application type with Configuration Manager, virtualized applications can be streamed from distribution points in the same manner as when you use a Publishing Server in the App-V full infrastructure model. The advantage of the integrated model over the App-V full infrastructure model is that in the integrated model, virtualized applications can stream off any existing Configuration Manager distribution point. Configuration Manager distribution points can also take advantage of BranchCache and Background Intelligent Transfer Service (BITS) functionality.
Another advantage of the integrated model is that its deployment process can automatically determine whether the App-V client is present during application deployment and, if not, deploy the client before deploying the virtualized application. For example, if you deploy a virtualized application to a collection of 10 computers, and 5 of those computers do not have the App-V client installed, Configuration Manager can be set to deploy the App-V client automatically before deploying the virtualized application.
App-V applications can be listed as a deployment type in Configuration Manager. You can choose to deploy an application such as Microsoft Word to a computer and then build logic into the deployment so that, in some cases, the application is installed locally in a traditional manner, and in other cases, the application is installed as an App-V application. For example, Microsoft Word is installed locally if the computer is designated as the user’s primary device, but it is installed as an App-V application if the computer is not designated as the user’s primary device. The App-V deployment type enables administrators to perform temporary application deployment, which deploys the application to the client but does not make an ongoing configuration change in the client.
Although you can also use sequenced applications in MSI format with Configuration Manager, these applications will be deployed in their entirety to the target device and will not be streamed to the device through the Configuration Manager distribution point.
The integrated model still requires use of Group Policy if you want to configure App-V client cache settings. You can use this policy to control whether streamed applications will persist in the client cache.
More Info: Configuration Manager Integrated Model
You can learn more about the Configuration Manager integrated model at http://technet.microsoft.com/en-us/library/jj822982.aspx.
Deploying sequenced applications
The first decision you need to make when deploying sequenced applications is which type of delivery mechanism you will use. You can stream the applications, install the applications locally, or use a mixture of streaming and local installation. Independent of the method you use, you can run a sequenced application only if the App-V client is present on the client device. When you are deciding which mechanism to use, keep in mind the following information.
Streaming applications
When applications are streamed, the application is available to the user as soon as enough of the application has transferred from the server to the client that the application can start. You can configure streaming so that applications are available only when the client is online. You might want to use this option with sensitive applications to which you want to control access. You can also configure streaming so that applications are available when the client is offline. In this situation, the application is stored in the client’s cache. Streaming sequenced applications use the .appv file format.
Local installation of applications
A local installation has the benefits of a virtualized application (such as minimizing compatibility problems with other applications) while also keeping the application available when the client is offline without relying on the application remaining in the client’s App-V cache. Locally installed applications are delivered to the client by using local install, Group Policy, Intune, System Center 2012 Configuration Manager SP1 or System Center 2012 R2 Configuration Manager, or another application deployment solution.
When you deploy a sequenced application and locally install it, the entire sequenced application is downloaded to the client before the application is run. The application is always available for offline use—unlike with streamed applications, you cannot ensure that a user will not have access to a sequenced application when that user’s computer is not connected to the organizational network.
Locally installed sequenced applications use the .msi format rather than the .appv format. Using the .msi format enables you to treat a sequenced application in the same way that you would treat a traditional local installation. You can deploy a sequenced application by using Intune and Group Policy, an approach that was not possible with earlier versions of App-V. You cannot import sequenced applications to an App-V Publishing Server by using the .msi format.
When you deploy a sequenced application in .msi format, you need to ensure that the App-V client is present on the target client; if it is not, the application cannot run. You can use Programs And Features on a client to remove a sequenced application deployed in .msi format.
You can use the .msi format with sequenced applications when you create thick images for operating system deployment.
Streaming and local installation of applications combined
You might use a mixture of streaming and local installation. For example, when some applications don’t need to be on the client devices permanently but you want the users to have access to them quickly, stream these applications; when other applications need to be on the client devices permanently but need to be isolated from other applications, install these applications locally as App-V applications.
After you decide which delivery mechanism you want to use, you need to select a deployment technology. You can use the following products to deploy sequenced applications:
![]() System Center 2012 Configuration Manager SP1 and System Center 2012 R2 Configuration Manager Configuration Manager supports both streaming and local installation. You can configure a single application to be streamed or locally installed, depending on the conditions that exist on the client. You can configure Configuration Manager to detect whether the App-V client is present on the device. If App-V is not present, Configuration Manager will deploy it before deploying the sequenced application. You can use Configuration Manager reporting functionality to monitor application use.
System Center 2012 Configuration Manager SP1 and System Center 2012 R2 Configuration Manager Configuration Manager supports both streaming and local installation. You can configure a single application to be streamed or locally installed, depending on the conditions that exist on the client. You can configure Configuration Manager to detect whether the App-V client is present on the device. If App-V is not present, Configuration Manager will deploy it before deploying the sequenced application. You can use Configuration Manager reporting functionality to monitor application use.
![]() App-V Publishing Server You can stream applications from App-V Publishing Servers. Use Group Policy to provide clients with the location of publishing servers. Administrators can use App-V Reporting Server functionality to meter application use. If you want to allow application streaming and you are not using System Center 2012 Configuration Manager SP1, you must deploy an App-V Publishing Server.
App-V Publishing Server You can stream applications from App-V Publishing Servers. Use Group Policy to provide clients with the location of publishing servers. Administrators can use App-V Reporting Server functionality to meter application use. If you want to allow application streaming and you are not using System Center 2012 Configuration Manager SP1, you must deploy an App-V Publishing Server.
![]() Group Policy deployment Use Group Policy software deployment to deploy sequenced applications in .msi format locally. You cannot use Group Policy to meter application use.
Group Policy deployment Use Group Policy software deployment to deploy sequenced applications in .msi format locally. You cannot use Group Policy to meter application use.
![]() Manual deployment Use the .msi file to install the sequenced application manually on a computer. Use this method infrequently because it requires substantially more time than an automated deployment method.
Manual deployment Use the .msi file to install the sequenced application manually on a computer. Use this method infrequently because it requires substantially more time than an automated deployment method.
![]() Logon scripts Use the Msiexec.exe command to install an .msi file.
Logon scripts Use the Msiexec.exe command to install an .msi file.
![]() Microsoft Intune Use Intune to deploy the .msi file to remote clients that infrequently connect to the organizational network.
Microsoft Intune Use Intune to deploy the .msi file to remote clients that infrequently connect to the organizational network.
Streaming and the App-V application cache
Streamed applications are transferred from App-V Publishing Servers or Configuration Manager distribution points to App-V clients over the HTTPS protocol. Streamed applications start running on the client as soon as enough of the virtualized application has transferred to the client to begin running. For example, rather than downloading an entire 1 GB application before beginning to run, the application might start to run when only some of its files have been transferred. The rest of the application streams to the client as necessary.
The App-V client stores streamed applications in the local App-V cache. As long as a particular application is in the cache, it will be loaded from there the next time the user wants to run it—the device will not need to reacquire the application from the publishing server or distribution point. As long as an application is in the cache, that application can be used when the device is not connected to the Publishing Server or distribution point.
You can configure the Shared Content Store (SCS) Mode Group Policy item so that sequenced applications can run only when the device is connected to the Publishing Server or distribution point. When you enable this policy, the streamed application will not be stored in the App-V cache and must be reacquired each time the user wants to run it. This policy is only available if the App-V templates are present in Group Policy.
Not all virtualized application deployment methods ensure that the sequenced application can be streamed to the client. Applications can be streamed when you do the following:
![]() Deploy the application by using the App-V full infrastructure model.
Deploy the application by using the App-V full infrastructure model.
![]() Deploy the application by using the App-V deployment type in Configuration Manager.
Deploy the application by using the App-V deployment type in Configuration Manager.
If you are using the App-V full infrastructure model, you need to configure clients with the address of the Publishing Server by using Group Policy. You can configure Group Policy with the address of up to five publishing servers. You use the App-V Management Server web application to import applications in App-V format and publish them to publishing servers. You also use the App-V Management Server web application to configure permissions.
When using App-V sequenced applications with Configuration Manager, clients use Configuration Manager distribution points as the source for streamed applications. These clients use the Configuration Manager client to determine which applications they are eligible to consume.
Configuring dependencies
An advantage of using Configuration Manager as opposed to other deployment methods is that you can configure dependencies. When you configure a dependency, the client checks whether the specified prerequisite software environment is present. In the case of sequenced applications, you can configure Configuration Manager to check whether the App-V software is present on the client. If the App-V software is present, the deployment proceeds as usual. If the App-V software is not present, Configuration Manager will deploy it before deploying the sequenced application.
To configure the App-V client as a dependency for an application, perform the following steps:
1. In the Software Workspace of Configuration Manager, click Software Library.
2. In the Application Management folder, click Applications.
3. Right-click the virtualized application and then click Properties.
4. On the Deployment Types tab, click the deployment associated with App-V 5, as shown in Figure 1-5, and then click Edit.
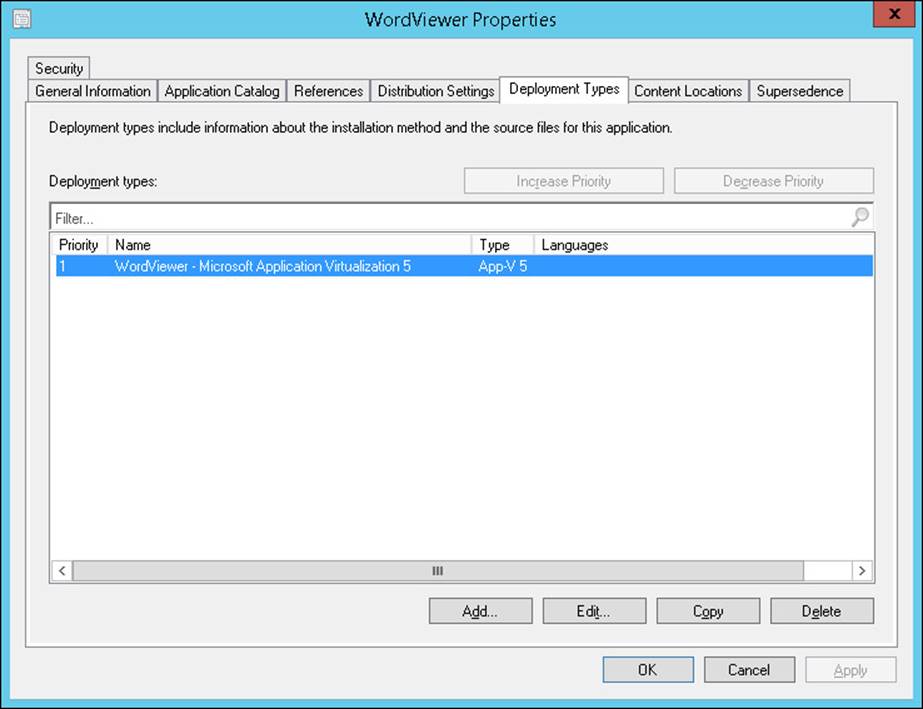
FIGURE 1-5 Deployment types
5. Click the Dependencies tab and then click Add.
6. In the Add Dependency dialog box, click Add.
7. In the Specify Required Application dialog box, click Microsoft Application Virtualization (App-V) Client 5.0. You must have already added Microsoft Application Virtualization (App-V) Client 5.0 to Configuration Manager before you can perform this step.
8. On the Deployment Types page for the selected application, click Microsoft Application Virtualization, as shown in Figure 1-6, and then click OK.
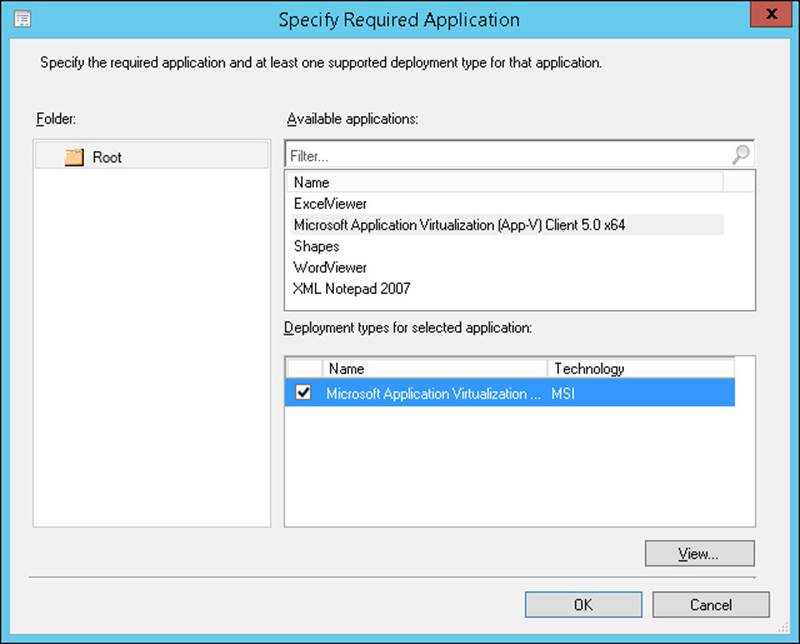
FIGURE 1-6 Specify Required Application dialog box
9. In the Add Dependency dialog box, type App-V Apps in the Dependency Group Name box and then click OK.
10. In the Application Properties dialog box, click OK.
App-V Group Policy
When you use the App-V full infrastructure model, you use Group Policy to configure important App-V settings, including the location of publishing servers and the behavior of the client cache. You do not need to use Group Policy to configure App-V if you are using the standalone deployment model.
To configure App-V Group Policy, add the App-V policy template to the Group Policy store on your domain controller. These policies can be downloaded from the Microsoft website.
After you place the templates in the Group Policy store, you can find App-V policies in the Computer Configuration\Policies\Administrative Templates\System\App-V node of a Group Policy Object (GPO). App-V policies are spread across the following six nodes:
![]() Client Coexistence Use the policy in this node to enable automatic migration to App-V 5.0 of packages that were created by using a previous version of App-V.
Client Coexistence Use the policy in this node to enable automatic migration to App-V 5.0 of packages that were created by using a previous version of App-V.
![]() Integration Use the policies in this node to specify the file paths in a user profile that do not roam with the user profile when used with App-V. Also, use the policies in this node to configure the location of symbolic links to the current version of the published package.
Integration Use the policies in this node to specify the file paths in a user profile that do not roam with the user profile when used with App-V. Also, use the policies in this node to configure the location of symbolic links to the current version of the published package.
![]() Publishing Use the policies in this node to specify the location of the Publishing Server.
Publishing Use the policies in this node to specify the location of the Publishing Server.
![]() Reporting Use the policy in this node to specify the location of the App-V Reporting Server to client devices.
Reporting Use the policy in this node to specify the location of the App-V Reporting Server to client devices.
![]() Scripting Use the policy in this node to configure whether scripts defined in the package manifest configuration files should run.
Scripting Use the policy in this node to configure whether scripts defined in the package manifest configuration files should run.
![]() Streaming Use the policies in this node to configure settings related to package streaming.
Streaming Use the policies in this node to configure settings related to package streaming.
Notable policies include the following:
![]() Publishing Server 1 Settings This policy is located in the Publishing node. Use it to specify the location of the first publishing server and the properties of that publishing server. There are five publishing server settings policies, so you can configure up to five publishing servers for each App-V client. In each of these policies, you can configure the following publishing server settings:
Publishing Server 1 Settings This policy is located in the Publishing node. Use it to specify the location of the first publishing server and the properties of that publishing server. There are five publishing server settings policies, so you can configure up to five publishing servers for each App-V client. In each of these policies, you can configure the following publishing server settings:
![]() Publishing Server Display Name This is the name of the publishing server shown in the App-V client interface.
Publishing Server Display Name This is the name of the publishing server shown in the App-V client interface.
![]() Publishing Server URL This is the URL of the publishing server.
Publishing Server URL This is the URL of the publishing server.
![]() Global Publishing Refresh Use this setting to enable global publishing refresh. This performs a global refresh to update the list of available published applications.
Global Publishing Refresh Use this setting to enable global publishing refresh. This performs a global refresh to update the list of available published applications.
![]() Global Publishing Refresh On Logon Use this setting to enable a global publishing refresh at logon.
Global Publishing Refresh On Logon Use this setting to enable a global publishing refresh at logon.
![]() Global Publishing Refresh Interval When you enable global publishing refresh, you need to specify a frequency. Use the interval setting to specify the refresh interval for global publishing refresh.
Global Publishing Refresh Interval When you enable global publishing refresh, you need to specify a frequency. Use the interval setting to specify the refresh interval for global publishing refresh.
![]() Global Publishing Refresh Interval Unit When you have set the number of units, you need to set the unit itself. You can select either Hour or Day.
Global Publishing Refresh Interval Unit When you have set the number of units, you need to set the unit itself. You can select either Hour or Day.
![]() User Publishing Refresh Use this setting to configure user publishing refresh. This refresh occurs on a user basis for the applications published to the user rather than globally.
User Publishing Refresh Use this setting to configure user publishing refresh. This refresh occurs on a user basis for the applications published to the user rather than globally.
![]() User Publishing Refresh On Logon Use this setting to configure user publishing refresh at logon.
User Publishing Refresh On Logon Use this setting to configure user publishing refresh at logon.
![]() User Publishing Refresh Interval Use this setting to specify the refresh interval for user publishing refresh.
User Publishing Refresh Interval Use this setting to specify the refresh interval for user publishing refresh.
![]() User Publishing Refresh Interval Unit Use this setting to specify the interval unit, in either hours or days, for the user publishing refresh cycle.
User Publishing Refresh Interval Unit Use this setting to specify the interval unit, in either hours or days, for the user publishing refresh cycle.
![]() Package Installation Root Use this policy to specify where all new App-V applications and updates will be installed on the client.
Package Installation Root Use this policy to specify where all new App-V applications and updates will be installed on the client.
![]() Shared Content Store (SCS) mode Use this policy to specify whether streamed package contents are saved to the local hard disk. This policy is useful when you want to grant access to streamed applications but do not want those applications to be available when the client is offline.
Shared Content Store (SCS) mode Use this policy to specify whether streamed package contents are saved to the local hard disk. This policy is useful when you want to grant access to streamed applications but do not want those applications to be available when the client is offline.
![]() Specify what to load in background (that is, Autoload) This policy enables you to specify which packages App-V acquires automatically on a client computer from a publishing server. The options are Previously Used, None, and All. When enabled, the Previously Used option is the default; previously used applications will be downloaded automatically from the App-V Publishing Server in the background, which increases the speed at which an application loads.
Specify what to load in background (that is, Autoload) This policy enables you to specify which packages App-V acquires automatically on a client computer from a publishing server. The options are Previously Used, None, and All. When enabled, the Previously Used option is the default; previously used applications will be downloaded automatically from the App-V Publishing Server in the background, which increases the speed at which an application loads.
Depending on security concerns, organizations that use the App-V full Infrastructure model and the integrated model might choose to prevent streamed package contents from being saved to the local hard disk by using the SCS Mode policy. For example, you would use this policy if an application needed to be used on a client in an unsecure location where the application should not be stored locally, or if the application should not be accessible when the device cannot connect to the publishing server.
 Exam Tip
Exam Tip
Remember the different App-V models.
 Thought experiment: App-V deployment planning at Contoso
Thought experiment: App-V deployment planning at Contoso
You are planning the deployment of App-V at Contoso. Your primary interest is the ability to meter application usage and limit the number of concurrent instances of application execution. Contoso does not have a Configuration Manager deployment. With this information in mind, answer the following questions:
1. Which deployment model is suitable for Contoso?
2. Which protocol will clients use to access streamed applications?
Objective summary
![]() You can deploy App-V by using the full infrastructure, standalone, or Configuration Manager integrated model.
You can deploy App-V by using the full infrastructure, standalone, or Configuration Manager integrated model.
![]() App-V applications can run only on computers on which a compatible App-V client is installed.
App-V applications can run only on computers on which a compatible App-V client is installed.
![]() App-V applications can stream from an App-V server or a Configuration Manager distribution point. This enables the applications to deploy more quickly.
App-V applications can stream from an App-V server or a Configuration Manager distribution point. This enables the applications to deploy more quickly.
![]() When sequenced, App-V applications are available in .msi format. You can deploy App-V applications locally in the same manner as you would deploy any other application in .msi format.
When sequenced, App-V applications are available in .msi format. You can deploy App-V applications locally in the same manner as you would deploy any other application in .msi format.
![]() When deploying App-V applications by using Configuration Manager, you can configure the App-V client as a dependency. This means that the App-V client will be deployed if it is not present on the target computer.
When deploying App-V applications by using Configuration Manager, you can configure the App-V client as a dependency. This means that the App-V client will be deployed if it is not present on the target computer.
![]() You can use Group Policy to manage App-V settings, but you must import the App-V–related Group Policy template.
You can use Group Policy to manage App-V settings, but you must import the App-V–related Group Policy template.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. You have deployed the Configuration Manager integrated model. You want to deploy App-V applications to some of the computers in your organization; however, the App-V client is not installed on every computer that is a Configuration Manager client. The App-V client should be deployed only to computers that need it to run applications. How can you ensure that computers that are subject to an App-V application deployment are able to run those applications?
A. Deploy the App-V client to all computers.
B. Configure the App-V client as a dependency for each App-V application.
C. Configure each App-V application as a dependency for the App-V client.
D. Configure each computer to subscribe to the RemoteApp feed.
2. You want to ensure that users with laptop computers have access to App-V applications only when they are on site. Which of the following strategies could you pursue to accomplish this goal? (Choose two. Each correct answer provides a complete solution.)
A. Use the App-V full infrastructure model.
B. Use the standalone deployment model.
C. Use the Configuration Manager integrated model.
D. Use RD Web Access.
3. Which of the following servers must you deploy to support the App-V full infrastructure model?
A. Management Server
B. Publishing Server
C. Configuration Manager site server
D. Remote Desktop Session Host server
Objective 1.3: Deploy and manage RemoteApp
Session virtualization is the process by which an application or desktop environment runs remotely, but the display of that application or desktop environment occurs locally. The advantage of this approach is that applications that might otherwise require resources the local device might not have, such as an appropriate processor or enough RAM, can be used locally with the processing, memory, and storage resources the back-end infrastructure provides.
This section covers the following topics:
![]() Application presentation strategies
Application presentation strategies
![]() Preparing RemoteApp applications
Preparing RemoteApp applications
![]() Group Policy settings
Group Policy settings
Application presentation strategies
Remote Desktop Session Host servers provide session virtualization and can exist in the form of either a full desktop session or a remote application. The following sections describe these two application presentation methods.
Remote desktops
Remote Desktop Session Host servers (formerly known as Terminal Servers) provide users with access to a full remote desktop experience. In this scenario, users securely connect to the remote session through their local Remote Desktop Connection (RDC) client. From the users’ perspective, their desktop environment appears the same, even though it actually is running on a remote server. Users have access to applications in the same way as if those applications were running locally, even though the applications are running on the Remote Desktop Session Host. Each user establishes his or her own private session that does not affect any other users that are connected to the same Remote Desktop Session Host.
To access a remote desktop, the user account (or domain global group) of the connecting user must be added to the Remote Desktop Users group on the computer to which he or she is connecting. By default, this group has no members.
Installing the Remote Desktop Session Host role on a server automatically enables Remote Desktop connections to the local computer. If you do not install the Remote Desktop Session Host role, you can still enable Remote Desktop access to any Windows-based operating system by modifying the system properties to allow remote connections. You can allow remote connections and select the users who can connect remotely by using System Properties in Control Panel.
Remote Desktop is well suited to single-task workers such as point-of-sale terminals or data entry workers. In such scenarios, it is important to provide a consistent desktop experience for all workers. Remote desktops also perform well over limited bandwidth, making this solution suitable for branch offices where IT support might be limited. Another common use for Remote Desktop is to enable users to access their corporate desktop. For example, users can work from home by connecting to their workstations, or users in bring your own device (BYOD) scenarios can connect to a standard operating system environment from their personal devices.
Remote applications
Users access Remote Application (RemoteApp) programs remotely through Remote Desktop Services, but the programs appear as if they are running on the end user’s local computer. These applications can appear on the Start menu like any locally installed application. Users can interact with RemoteApp applications in the same manner that they interact with locally installed applications. Running the application on the server avoids compatibility issues that might prevent you from installing the application locally. RemoteApp is suited to applications that you need to manage centrally or that require higher computing requirements than the users’ desktops might have—for example, an application that requires large amounts of RAM or one that requires intensive graphics processing. RemoteApp works with Windows clients that include the Remote Desktop software and Windows RT clients on which the Remote Desktop Connection app is installed.
Remote Desktop Web Access
Remote Desktop Web Access (RD Web Access) allows end users to access applications through a special website. RD Web Access provides a secure way to:
![]() Present remote applications.
Present remote applications.
![]() Provide access to remote virtual desktops.
Provide access to remote virtual desktops.
![]() Connect to a remote computer.
Connect to a remote computer.
Users can access a secure site, typically at https://ServerFQDN/RDWeb, and establish an SSL session between the client and the RD Web Access server. After authentication, users see a list of any applications or desktops that they have permission to use.
Users also see a link to connect to a remote desktop. This link presents a web-based version of the Remote Desktop Protocol (RDP) client where the users can configure devices, resources, and additional options. Users enter the name of the computer to which they want to connect and configure the options they require. Then they have to sign in to the computer to which they are connecting by using a valid user name and password.
For users who do not need a full desktop or users who are not on the corporate network, RD Web Access is an attractive solution because you need to provide users with only the URL of the RD Web Access server. Applications started from this interface are fully functional and save files back to the company network by default, although users can save files to the local computer if required. RD Web Access is suitable for:
![]() Users outside the corporate network who need to run corporate applications—for example, users who work from home or use laptops in the field.
Users outside the corporate network who need to run corporate applications—for example, users who work from home or use laptops in the field.
![]() Users in remote offices where no VPN is in place.
Users in remote offices where no VPN is in place.
![]() Users who need to access corporate applications from a computer in a public location such as a hotel or an airport.
Users who need to access corporate applications from a computer in a public location such as a hotel or an airport.
![]() Kiosk machines that are locked down so that they grant access to only a limited set of applications through the Internet—for example, public access machines that grant any user access to a certain corporate application.
Kiosk machines that are locked down so that they grant access to only a limited set of applications through the Internet—for example, public access machines that grant any user access to a certain corporate application.
Preparing RemoteApp applications
Before you can make an application available remotely, you must install it on each Remote Desktop Session Host server that will offer that application. Proper planning and installation of the application ensures that your users can access it in a multiuser environment. You can deploy applications that you want to make remotely available only after you have deployed the Remote Desktop Session Host role.
When you are planning a remote application deployment, consider the following factors:
![]() Suitability for multiuser environments This consideration is the most important. Historically, most end user applications have functioned well in a multiuser environment; however, this is not always the case. You must check with the application vendor to see whether a multiuser configuration is supported. Some vendors can provide fixes that enable you to deploy an application in a multiuser environment. If they cannot, you might have to deploy the application to traditional desktops or find another application that can support a multiuser environment.
Suitability for multiuser environments This consideration is the most important. Historically, most end user applications have functioned well in a multiuser environment; however, this is not always the case. You must check with the application vendor to see whether a multiuser configuration is supported. Some vendors can provide fixes that enable you to deploy an application in a multiuser environment. If they cannot, you might have to deploy the application to traditional desktops or find another application that can support a multiuser environment.
![]() Application compatibility You have to investigate whether there are compatibility issues with existing applications on the Remote Desktop Session Host server. Ensure that you thoroughly test the proposed application before putting it into the production environment. You might need multiple Remote Desktop Session Hosts so that incompatible applications can be run separately from each other, and you might need multiple session collections to create silos of applications.
Application compatibility You have to investigate whether there are compatibility issues with existing applications on the Remote Desktop Session Host server. Ensure that you thoroughly test the proposed application before putting it into the production environment. You might need multiple Remote Desktop Session Hosts so that incompatible applications can be run separately from each other, and you might need multiple session collections to create silos of applications.
![]() Application dependencies Install, on the same Remote Desktop Session Host server, related applications or applications that have dependencies on other local applications. For example, all the applications of an application suite should be installed on the same Remote Desktop Session Host unless otherwise prescribed by the vendor.
Application dependencies Install, on the same Remote Desktop Session Host server, related applications or applications that have dependencies on other local applications. For example, all the applications of an application suite should be installed on the same Remote Desktop Session Host unless otherwise prescribed by the vendor.
![]() Capacity requirements There are no firm numbers that indicate how many clients a single Remote Desktop Session Host server can support. Resource requirements for remotely delivered applications depend on several factors, including the application requirements, the number of concurrent sessions, and how many applications (and other services) the Remote Desktop Session Host is running. Several tools can provide sizing guidance. Server administrators should monitor their server performance closely in Remote Desktop Session Hosts and listen to the feedback end users provide, adding server resources as required. Microsoft offers white papers to assist in capacity planning.
Capacity requirements There are no firm numbers that indicate how many clients a single Remote Desktop Session Host server can support. Resource requirements for remotely delivered applications depend on several factors, including the application requirements, the number of concurrent sessions, and how many applications (and other services) the Remote Desktop Session Host is running. Several tools can provide sizing guidance. Server administrators should monitor their server performance closely in Remote Desktop Session Hosts and listen to the feedback end users provide, adding server resources as required. Microsoft offers white papers to assist in capacity planning.
Installing an application on a Remote Desktop Session Host is not like installing an application on a traditional desktop. Remote Desktop Session Hosts operate in two modes, install mode and execute mode. The server must be placed into install mode to install multiuser applications properly. In install mode, Windows ensures that the appropriate registry entries and initialization (.ini) file settings are configured for the application to function in multiuser environments. After the application is successfully installed, the server must be returned to execute mode. You can change the mode of the server in two ways:
![]() Use the command prompt To use the command prompt, from a command prompt, perform these steps:
Use the command prompt To use the command prompt, from a command prompt, perform these steps:
A. Use the change user /install command to place the server into install mode.
B. Install the application.
C. Use the change user /execute command to return the server to execute mode so that users can access the application.
![]() Use Control Panel The Programs section of Control Panel lists the Install Application On Remote Desktop applet. This applet starts a wizard that automatically puts the server into install mode and then prompts for the location of the application’s installation executable file. The administrator installs the application and completes the wizard. This returns the server to execute mode.
Use Control Panel The Programs section of Control Panel lists the Install Application On Remote Desktop applet. This applet starts a wizard that automatically puts the server into install mode and then prompts for the location of the application’s installation executable file. The administrator installs the application and completes the wizard. This returns the server to execute mode.
Publishing and configuring RemoteApps
The session collection interface in Remote Desktop Management Service (RDMS) provides a link for you to publish RemoteApp programs, or you can publish from the link on the Tasks drop-down menu. Clicking the Publish RemoteApps Programs link starts the Publish RemoteApp Programs Wizard. The wizard presents a list of all the default applications that are available for publishing. Other applications must be mapped by manually adding the path to the executable file that starts the program.
After the applications are published, you can configure them further by editing the application properties:
![]() Choose whether to show the remote application in RD Web Access. By default, the setting is Yes.
Choose whether to show the remote application in RD Web Access. By default, the setting is Yes.
![]() Create web folders by typing the name of the folder you want to create.
Create web folders by typing the name of the folder you want to create.
![]() Assign command-line parameters.
Assign command-line parameters.
![]() Restrict access to the remote application to specific users or groups. By default, all users who can access the collection have access to the application.
Restrict access to the remote application to specific users or groups. By default, all users who can access the collection have access to the application.
![]() Set file type associations for the remote application. File type associations apply only to users who are connected by the RemoteApp and Desktop Connections feed. Users who are connected by RD Web Access cannot use file type associations.
Set file type associations for the remote application. File type associations apply only to users who are connected by the RemoteApp and Desktop Connections feed. Users who are connected by RD Web Access cannot use file type associations.
You can also use the Remote Desktop Services PowerShell module to create, update, and delete RemoteApp applications. To publish a new remote application, use the New RDRemoteApp cmdlet. For example, to publish the Windows PowerPoint Viewer application and have it display in RD Web Access, use the following command:
New-RDRemoteApp -Alias PPTViewer -DisplayName PPTViewer -FilePath "C:\
Program Files(x86)\Microsoft Office\Office14\PPTVIEW.exe" -ShowInWebAccess True
-CollectionName RemoteApps -ConnectionBroker LON-SVR1.Adatum.com
Managing connections to RemoteApp applications
After a collection is created and RemoteApp applications are added to the collection, a user can connect to the collection and run RemoteApp applications by using the RDC, by signing in to the RDWeb page, or by subscribing to the RemoteApp feed. If users subscribe to the RemoteApp feed, the applications appear on the Start screen of their computer if it is running Windows 8.1 or Windows 8 or on the Start menu of their Windows 7–based computer.
Connecting with RDC
Users can connect to a remote desktop by using the standard RDP client, Remote Desktop Connection (RDC). The user needs to enter the name of the remote computer in the Computer box and then click Connect. If the computer to which the user is trying to connect allows remote access and if the user is in the Remote Desktop Users group for that computer, the user can sign in to that computer. The user will be presented with a desktop just as if he or she were signing in locally. A user connecting in this fashion has access to all the resources of the remote computer just as if he or she were sitting at the local console.
The RDC client has a number of tabs with options that can be configured to control the user experience. These tabs are as follows:
![]() General Provide the name of the computer to which you want to connect and the user name you are using to connect. You can also save this configuration in an RDP file or open an RDP file that might have been provided to you.
General Provide the name of the computer to which you want to connect and the user name you are using to connect. You can also save this configuration in an RDP file or open an RDP file that might have been provided to you.
![]() Display Configure the resolution and color depth of the remote session.
Display Configure the resolution and color depth of the remote session.
![]() Local Resources Specify which local resources will be available to the client computer, such as printers, the Clipboard, local drives, and audio settings.
Local Resources Specify which local resources will be available to the client computer, such as printers, the Clipboard, local drives, and audio settings.
![]() Programs Configure a specific program to start upon connection.
Programs Configure a specific program to start upon connection.
![]() Experience Choose the level of visual quality to transmit to the client computer from the remote computer based on the available bandwidth of the connection.
Experience Choose the level of visual quality to transmit to the client computer from the remote computer based on the available bandwidth of the connection.
![]() Advanced Specify how authentication to the server will occur and configure the Remote Desktop Gateway (RD Gateway) settings.
Advanced Specify how authentication to the server will occur and configure the Remote Desktop Gateway (RD Gateway) settings.
Connecting with the RemoteApp and Desktop Connections feed
Computers running Windows 8, Windows 8.1, Windows RT, and Windows RT 8.1 can subscribe to the Remote Desktop web feed. With the subscription, applications published to the feed are automatically added to the Start screen on the subscribed device.
After the subscription is established, the Remote Desktop web feed is available from the Start screen or Start menu. Users can manually enter the URL to connect to the feed by using the RemoteApp And Desktop Connections applet in Control Panel, as shown in Figure 1-7, or an administrator can configure the default connection URL with Group Policy.
FIGURE 1-7 Access RemoteApp And Desktops dialog box
You can access the feed by using the following URL: https://<fqdn of rdweb server>/Rdweb/webfeed.aspx, or users can use their email addresses to subscribe to the feed. If you intend to allow use of an email address to subscribe to the feed, create a TXT record on the DNS server. The record name must be named _msadc, and the text field must contain the URL for the Remote Desktop web feed.
Group Policy settings
In a large organization, it is not practical to configure each remote desktop connection separately. Many Group Policy settings are available to manage the remote desktop or remote application experience for users. After the application presentation method has been determined and the applications have been published, you can use Group Policy to control how the session hosts that house those applications will be accessed. Group Policy enables you to configure settings that can be applied to both users and computers. Many of the same settings appear in both user and computer configurations—for example, session time limits. Typically, if the same settings are configured for both users and computers, the computer setting will override the user setting.
Computer settings
Computer settings affect all users connecting to the remote computer. Computer settings, shown in Figure 1-8, include the following categories:
![]() RD Licensing Control which Remote Desktop Session Host servers are issued Remote Desktop Services client access licenses
RD Licensing Control which Remote Desktop Session Host servers are issued Remote Desktop Services client access licenses
![]() Remote Desktop Connection Client Control security aspects of the connection, such as allowing .rdp files or determining whether passwords can be saved
Remote Desktop Connection Client Control security aspects of the connection, such as allowing .rdp files or determining whether passwords can be saved
![]() Remote Desktop Session Host Control many aspects of the Remote Desktop Session Host, such as device redirection, limiting the number of connections, user profiles, security, detection of network quality, and session limits
Remote Desktop Session Host Control many aspects of the Remote Desktop Session Host, such as device redirection, limiting the number of connections, user profiles, security, detection of network quality, and session limits
FIGURE 1-8 Remote Desktop Services policies showing computer settings
User settings
User settings are settings for particular groups of users connecting to remote computers. User settings, shown in Figure 1-9, include the following categories:
FIGURE 1-9 Remote Desktop Services policies showing user settings
![]() RD Gateway Set the gateway server address and authentication method.
RD Gateway Set the gateway server address and authentication method.
![]() Remote Desktop Connection Client Control .rdp files and the saving of passwords.
Remote Desktop Connection Client Control .rdp files and the saving of passwords.
![]() Remote Desktop Session Host Control many aspects of the user session, such as device redirection, user profiles, security, and session limits.
Remote Desktop Session Host Control many aspects of the user session, such as device redirection, user profiles, security, and session limits.
![]() RemoteApp And Desktop Connections Specify the default connection URL. This setting is new for Windows Server 2012, and it’s particularly useful for distributing the Remote Desktop web feed URL. This Group Policy setting is shown in Figure 1-10.
RemoteApp And Desktop Connections Specify the default connection URL. This setting is new for Windows Server 2012, and it’s particularly useful for distributing the Remote Desktop web feed URL. This Group Policy setting is shown in Figure 1-10.
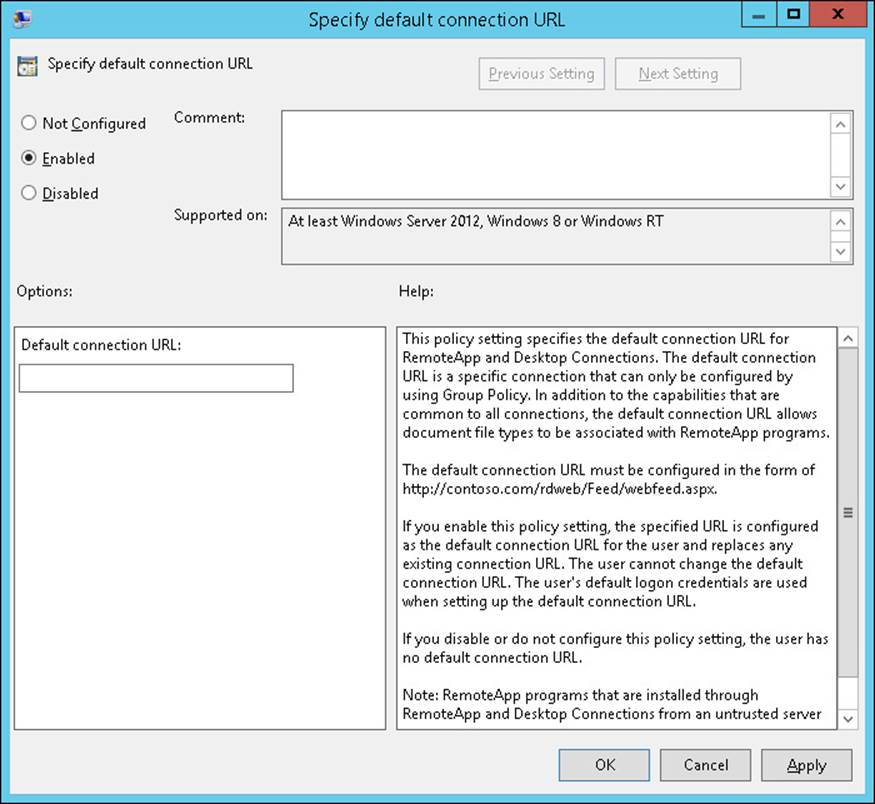
FIGURE 1-10 Specify default connection URL
 Exam Tip
Exam Tip
Remember how to configure a computer running Windows 8.1 or Windows 8 to subscribe to the RemoteApp feed.
 Thought experiment: BYOD at Tailspin Toys
Thought experiment: BYOD at Tailspin Toys
Interns at Tailspin Toys have been given Microsoft Surface 2 devices, which run the Windows RT 8.1 operating system. The Remote Desktop app has been installed on these devices. Interns are to use these devices to run x86 and x64 applications running on a server running Windows Server 2012 R2 with Remote Desktop Services installed.
1. What method could you use to enable an intern to access x86 and x64 RemoteApp applications quickly?
2. What steps would you take to ensure that RemoteApp applications automatically appeared on the Start screens of the Surface 2 devices the interns use?
Objective summary
![]() Remote Desktop enables a user to access a desktop environment remotely that was hosted on another computer where that desktop is displayed on the local device.
Remote Desktop enables a user to access a desktop environment remotely that was hosted on another computer where that desktop is displayed on the local device.
![]() RemoteApp uses the same technology as remote desktop but involves displaying an application that is running on a remote computer on a local device.
RemoteApp uses the same technology as remote desktop but involves displaying an application that is running on a remote computer on a local device.
![]() RD Web Access allows users to launch remote desktop sessions and RemoteApp sessions from a specially configured web page.
RD Web Access allows users to launch remote desktop sessions and RemoteApp sessions from a specially configured web page.
![]() Group Policy settings enable you to configure how a remote desktop and RemoteApp are configured.
Group Policy settings enable you to configure how a remote desktop and RemoteApp are configured.
![]() Computers running Windows 8.1 and Windows 8 can subscribe to a RemoteApp feed through Group Policy or through an item in Control Panel.
Computers running Windows 8.1 and Windows 8 can subscribe to a RemoteApp feed through Group Policy or through an item in Control Panel.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. What steps can you take to make RemoteApp applications automatically available to users who have computers running Windows 8.1 that are joined to the domain while expending the least amount of administrative effort?
A. Configure a subscription to the Remote Desktop web feed by using Group Policy.
B. Configure a subscription to the Remote Desktop web feed by using Control Panel.
C. Configure the address of the RD Web Access server as the home page in Windows Internet Explorer on each client.
D. Place shortcuts to each RemoteApp in a shared folder.
2. Which of the following Windows PowerShell cmdlets could you use to create a RemoteApp application?
A. Remove-RDRemoteApp
B. Get-RDRemoteApp
C. New-RDRemoteApp
D. Set-RDRemoteApp
3. You want to enable users to subscribe to the RemoteApp feed by using their organizational email address from the Control Panel setting on their computers running Windows 8.1. Which of the following steps must you take to prepare DNS to support this configuration?
A. Create a TXT record named _msadc with the URL for the Remote Desktop web feed in the text field.
B. Create an MX record with the FQDN for the RD Web Access server
C. Create an NS record with the FQDN for the RD Web Access server.
D. Create a CNAME record with the FQDN of the RD Web Access server.
Answers
Objective 1.1
Thought experiment
1. You should sequence the application twice, once for the computers running Windows 7 x86 and once for the computers running Windows 8.1 x64.
2. You should disable the Windows Defender and Windows Search services before sequencing the application on a computer running Windows 8.1 x64.
Objective review
1. Correct answer: A
A. Correct: You should sequence an application on the platform on which you run it. An x64 application can only be sequenced on an x64 version of an operating system.
B. Incorrect: You cannot use an x86 version of Windows to sequence an x64 application.
C. Incorrect: You should sequence an application on the platform on which you run it. Even though this might work, it is not the best answer because it is not the platform on which it will be run.
D. Incorrect: You cannot use an x86 version of Windows to sequence an x64 application.
2. Correct answers: A and B
A. Correct: App-V Connection Groups allow virtualized applications to share data when running on the same computer.
B. Correct: Virtual environments function in a similar manner to App-V Connection Groups, but they use Configuration Manager rather than an App-V server.
C. Incorrect: Plug-ins extend the functionality of the application. They don’t allow virtualized applications to interact.
D. Incorrect: A middleware application type enables you to sequence middleware or framework software that another sequenced application package requires.
3. Correct answer: D
A. Incorrect: You use a connection group when you need applications to share data with each other.
B. Incorrect: The middleware application type enables you to sequence middleware or framework software that another sequenced application package requires.
C. Incorrect: You can use the Sequencer to create an add-on or plug-in to extend the functionality of an application.
D. Correct: Package accelerators automate the sequencing process. They are useful when you need to sequence a particular application frequently.
Objective 1.2
Thought experiment
1. Because you want to use application metering and instance limitation, the full infrastructure model is appropriate.
2. The HTTPS protocol delivers streamed applications to clients.
Objective review
1. Correct answer: B
A. Incorrect: You should deploy the client only to computers that need it.
B. Correct: Configuring the App-V client as a dependency will trigger a check to verify that the App-V client is installed before attempting to deploy the application. If the client is not present, it will be installed.
C. Incorrect: This sequence is reversed. The client should be a dependency for the application.
D. Incorrect: RemoteApp is not related to the App-V client application.
2. Correct answers: A and C
A. Correct: You can configure the App-V full infrastructure model so that App-V applications are streamed and not stored in the cache. This means that the application can run only if connectivity can be established.
B. Incorrect: This model involves local installation and allows offline use.
C. Correct: You can configure Configuration Manager so that only streaming versions of the app are deployed and configure the cache so that applications are not available offline.
D. Incorrect: Although it is possible to deploy App-V on a Remote Desktop Session Host server to host virtualized applications, this is not an optimal solution to this situation.
3. Correct answers: A and B
A. Correct: You need to deploy an App-V Management Server for the App-V full infrastructure model.
B. Correct: You need to deploy an App-V Publishing Server for the App-V full infrastructure model.
C. Incorrect: You don’t need to deploy a Configuration Manager site server for the App-V full infrastructure model.
D. Incorrect: You don’t need to deploy a Remote Desktop Session Host server for the App-V full infrastructure model.
Objective 1.3
Thought experiment
1. You could configure RD Web Access. Interns could access the RD Web Access website and use it to launch RemoteApp applications.
2. You would subscribe the Surface 2 devices to the Remote Desktop web feed. RemoteApp applications would automatically be published to the Surface 2 Start screens.
Objective review
1. Correct answer: A
A. Correct: Configuring a subscription to the Remote Desktop web feed by using Group Policy accomplishes the objective with minimum administrative effort.
B. Incorrect: Configuring a subscription to the Remote Desktop web feed by using Control Panel involves substantial administrative effort.
C. Incorrect: Configuring the address of the RD Web Access server as the home page in Windows Internet Explorer on each client involves substantial administrative effort.
D. Incorrect: Placing shortcuts to each RemoteApp in a shared folder involves substantial administrative effort.
2. Correct answer: C
A. Incorrect: The Remove-RDRemoteApp Windows PowerShell cmdlet enables you to remove an existing RemoteApp application.
B. Incorrect: The Get-RDRemoteApp Windows PowerShell cmdlet enables you to view the properties of a RemoteApp application.
C. Correct: The New-RDRemoteApp Windows PowerShell cmdlet enables you to create a RemoteApp application.
D. Incorrect: The Set-RDRemoteApp Windows PowerShell cmdlet enables you to modify an existing RemoteApp application.
3. Correct answer: A
A. Correct: You need to create a TXT record named _msadc with the URL for the Remote Desktop web feed in the text field.
B. Incorrect: You need to create a TXT record named _msadc with the URL for the Remote Desktop web feed in the text field.
C. Incorrect: You need to create a TXT record named _msadc with the URL for the Remote Desktop web feed in the text field.
D. Incorrect: You need to create a TXT record named _msadc with the URL for the Remote Desktop web feed in the text field.