Exam Ref 70-696 Managing Enterprise Devices and Apps (2014)
Chapter 4. Manage compliance and endpoint protection settings
For many industries, the configuration of computers and devices is subject to compliance legislation. You can use the System Center 2012 R2 Configuration Manager compliance functionality to ensure that your organization’s managed devices meet the necessary configuration standards. Configuration Manager also includes antimalware functionality so you can monitor and remediate malware incidents on clients in your organization’s environment.
Objectives in this chapter:
![]() Objective 4.1: Build a configuration item.
Objective 4.1: Build a configuration item.
![]() Objective 4.2: Create and monitor a baseline.
Objective 4.2: Create and monitor a baseline.
![]() Objective 4.3: Configure Endpoint Protection.
Objective 4.3: Configure Endpoint Protection.
Objective 4.1: Build a configuration item
This objective deals with building configuration items for Configuration Manager. Such items enable you to evaluate the configuration of a Configuration Manager client. You can configure these items for Windows, Mac OS X, and mobile device clients.
This section covers the following topics:
![]() Overview of compliance settings
Overview of compliance settings
![]() Configuration items
Configuration items
![]() Creating configuration items
Creating configuration items
![]() Configuration item settings
Configuration item settings
![]() Remediation
Remediation
Overview of compliance settings
The Compliance Settings feature in Configuration Manager enables you to assess and manage configuration settings for Windows-based computers, Mac operating system (Mac OS X) computers, and devices running the Windows RT, Windows Phone, Windows Mobile, iOS, and Android mobile operating systems.
You can use compliance settings to:
![]() Monitor the version of a device’s installed operating system.
Monitor the version of a device’s installed operating system.
![]() Verify whether applications are installed and configured correctly.
Verify whether applications are installed and configured correctly.
![]() Check for prohibited applications or security settings.
Check for prohibited applications or security settings.
![]() Check that specific software updates are installed.
Check that specific software updates are installed.
![]() Configure features and security settings on mobile devices.
Configure features and security settings on mobile devices.
![]() Remediate noncompliant settings automatically (when supported).
Remediate noncompliant settings automatically (when supported).
![]() Configure user data and profiles settings such as folder redirection, offline files, and roaming user profiles (applicable for Windows 8.x and newer only).
Configure user data and profiles settings such as folder redirection, offline files, and roaming user profiles (applicable for Windows 8.x and newer only).
![]() Configure company resource access by using remote connection, virtual private network (VPN), Wi-Fi, and certificate profiles. (This is applicable only for devices running Windows 8.x and newer, iOS, and Android operating systems.)Compliance settings consist of one or more configuration items. Configuration items contain the specific settings and rules that define the requirements necessary to meet compliance. You can group configuration items into configuration baselines. You deploy configuration baselines to client systems to evaluate compliance and, potentially, perform remediation.
Configure company resource access by using remote connection, virtual private network (VPN), Wi-Fi, and certificate profiles. (This is applicable only for devices running Windows 8.x and newer, iOS, and Android operating systems.)Compliance settings consist of one or more configuration items. Configuration items contain the specific settings and rules that define the requirements necessary to meet compliance. You can group configuration items into configuration baselines. You deploy configuration baselines to client systems to evaluate compliance and, potentially, perform remediation.
More Info: Compliance Settings Overview
You can learn more about compliance settings at http://technet.microsoft.com/en-us/library/gg682139.aspx.
Configuration items
Configuration items contain one or more unique settings and values that you want to compare for compliance evaluation. For example, does a particular registry key have a particular setting, is a specific software update installed, or is the most recent version of an installed application deployed on the client?
Within a configuration item, you specify the compliance settings you are evaluating and the rules that should take effect based on those settings. You can use a single configuration item to evaluate multiple settings. When configuring a compliance rule as part of a configuration item, you can define the noncompliance severity that the client reports if the evaluation reveals noncompliance. If the configuration item supports remediation, you can specify the setting in the configuration item that you want to remediate—for example, changing a registry key value from 0 to 1.
You can specify configuration items for the following device types:
![]() Windows
Windows
![]() Mobile device
Mobile device
![]() Mac OS X
Mac OS X
Windows configuration items
You can specify Windows-based configuration items based on values related to the following settings:
![]() Active Directory Query
Active Directory Query
![]() Assembly
Assembly
![]() File System
File System
![]() IIS Metabase
IIS Metabase
![]() Registry Key
Registry Key
![]() Registry Value
Registry Value
![]() Script
Script
![]() SQL Query
SQL Query
![]() WQL Query
WQL Query
![]() XPath Query
XPath Query
Depending on the specific setting, you can configure rules for reporting purposes or for performing remediation tasks.
Mobile device configuration items
Mobile device configuration items enable you to configure settings that you can apply to managed Windows, iOS, and Android devices. Some common settings include the following:
![]() Password
Password
![]() Device
Device
![]() Email management
Email management
![]() Store
Store
![]() Browser
Browser
![]() Security
Security
![]() Windows Server work folders
Windows Server work folders
You apply these configuration settings to devices that you manage through the Microsoft Intune connector.
Mac OS X configuration items
Mac OS X configuration items are rules that you want to evaluate for managed Mac OS X computers. Configuration items include:
![]() Mac OS X Preferences.
Mac OS X Preferences.
![]() Scripts.
Scripts.
Creating configuration items
You can create a configuration item by using any of the following methods:
![]() Create a configuration item manually.
Create a configuration item manually.
![]() Create a child configuration item from an existing Windows-based configuration item.
Create a child configuration item from an existing Windows-based configuration item.
![]() Import configuration data.
Import configuration data.
![]() Copy an existing configuration item.
Copy an existing configuration item.
Create a configuration item manually
The most direct way to create a configuration item is to select the Configuration Items node, which is located under Compliance Settings in the Assets And Compliance workspace. Click Create Configuration Item on the ribbon. This starts the Create Configuration Item Wizard.
On the General page of the Create Configuration Item Wizard, shown in Figure 4-1, configure the following basic settings about the configuration item:
![]() Name Provide a name for the configuration item.
Name Provide a name for the configuration item.
![]() Description Provide a description for the configuration item.
Description Provide a description for the configuration item.
![]() Type Specify whether this configuration item is for Windows clients, mobile devices, or Mac OS X clients. When specifying the type as Windows clients, you can specify whether the configuration item is an application. This reveals additional options that you can use for detecting the application.
Type Specify whether this configuration item is for Windows clients, mobile devices, or Mac OS X clients. When specifying the type as Windows clients, you can specify whether the configuration item is an application. This reveals additional options that you can use for detecting the application.
![]() Categories Provide an administrative category that you can use to tag your configuration items.
Categories Provide an administrative category that you can use to tag your configuration items.
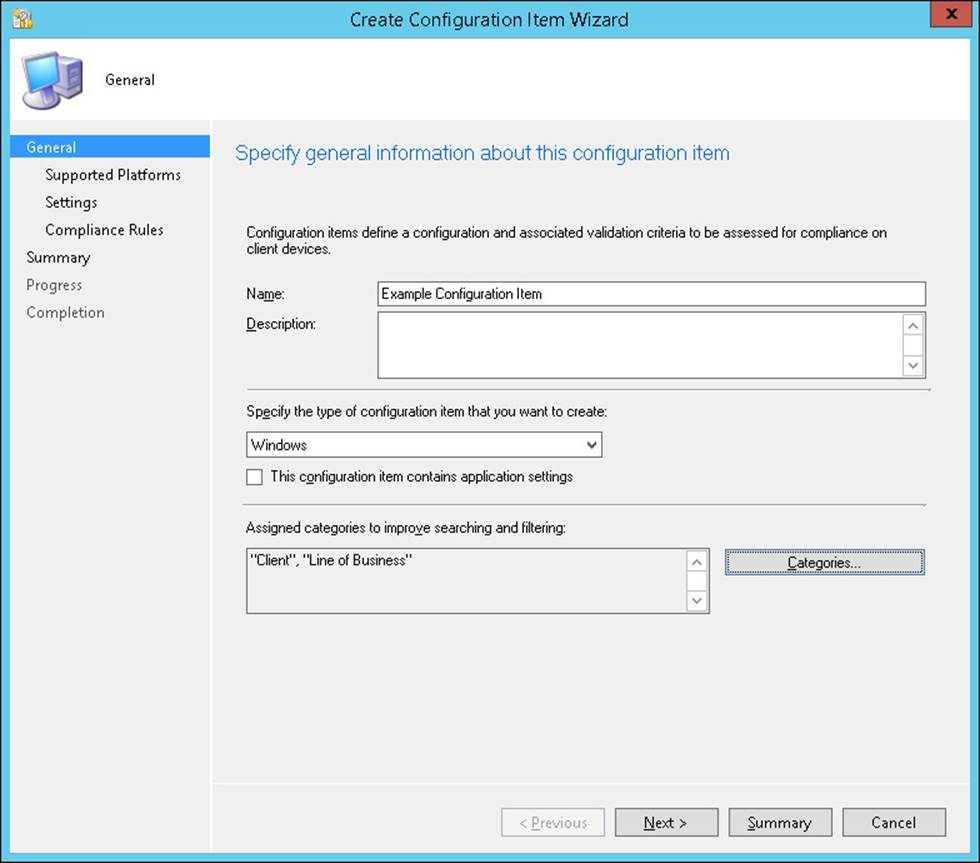
FIGURE 4-1 Create Configuration Item Wizard
After completing the General page, the wizard takes different paths, depending on which type of configuration item you are creating. Table 4-1 describes the pages that appear for each of the types.
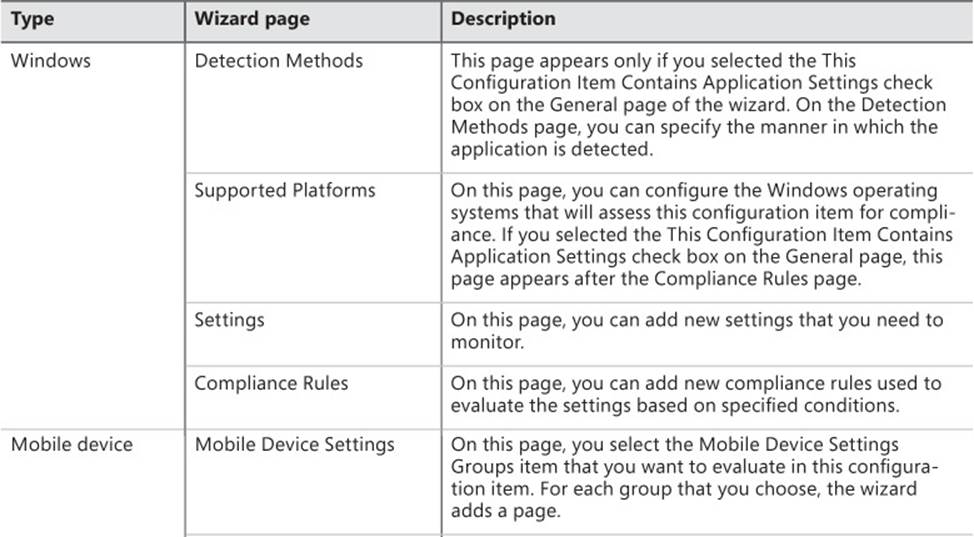
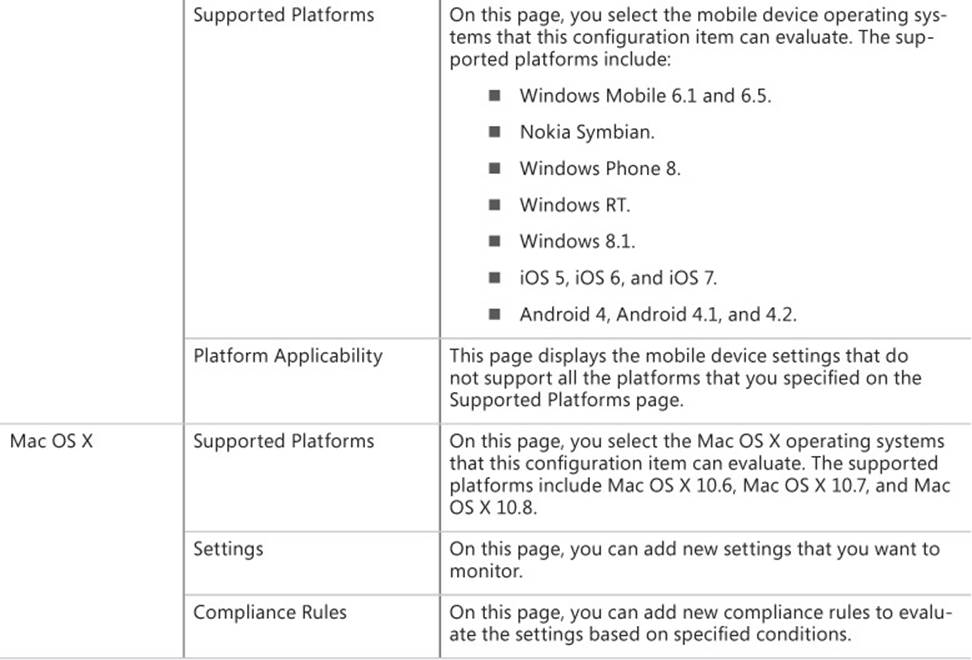
TABLE 4-1 Create Configuration Item Wizard options
Create a child configuration item
Use the create a child configuration item method to create a configuration item that inherits the properties of an existing configuration item. You then can refine the properties with a more detailed configuration. To create a child configuration item, select the configuration item that you want to use as a parent and then, on the ribbon, click Create Child Configuration Item. This starts the Create Child Configuration Item Wizard.
The Create Child Configuration Item Wizard has the same options as the Create Configuration Item Wizard except that you cannot remove or modify settings inherited from the parent configuration item. You can add settings or compliance rules to refine a configuration item further for a specific baseline. You can create child configuration items only for Windows-based configuration items.
Import configuration data
You can import configuration items that you have:
![]() Exported from other sites.
Exported from other sites.
![]() Downloaded as part of configuration packs from the Microsoft website or from other vendors.
Downloaded as part of configuration packs from the Microsoft website or from other vendors.
To import configuration data, select the Configuration Items node and then, on the ribbon, click the Import Configuration Data button. This starts the Import Configuration Data Wizard. In this wizard, you import one or more cabinet (.cab) files with configuration data, which you can use in Configuration Manager.
Copy existing configuration items
You use the copy existing configuration items method to create a configuration item with the properties of an existing configuration item but for which you want to modify some settings. When you copy a configuration item, you do not maintain a relationship between the new configuration item and the configuration item that you copied. To copy a configuration item, select the configuration item you want to copy and then, on the ribbon, click Copy. This opens the Configuration Item Name dialog box. Provide a name for the copy in the dialog box to create a copy. Then you can edit it as you would edit a configuration item that you created manually.
Configuration item revision history
Configuration Manager maintains a revision history of each configuration item. When you modify a configuration item, you do not lose the previous settings, and you can still use the previous settings in a configuration baseline. When you select the Configuration Items node, you can view in the Revision column the number of times a configuration item has been revised.
To manage revisions, select the configuration item that you want to work with and then, on the ribbon, click the Revision History button. In the Configuration Item Revision History window, the following options are available for you:
![]() Show All Revisions or Show Revisions In Use You can use this drop-down list to switch between all the revisions of the current configuration item and only the revisions that are being used in a configuration baseline.
Show All Revisions or Show Revisions In Use You can use this drop-down list to switch between all the revisions of the current configuration item and only the revisions that are being used in a configuration baseline.
![]() Compare With Current Revision When you select an older version of the configuration item, you can use this button to view the difference between that revision and the latest revision.
Compare With Current Revision When you select an older version of the configuration item, you can use this button to view the difference between that revision and the latest revision.
![]() Delete Use this button to delete a particular revision.
Delete Use this button to delete a particular revision.
![]() Export Use this button to export a particular revision to a .cab file so that you can import the revision into another instance of Configuration Manager.
Export Use this button to export a particular revision to a .cab file so that you can import the revision into another instance of Configuration Manager.
![]() Copy Use this button to copy a particular revision to create a new configuration item.
Copy Use this button to copy a particular revision to create a new configuration item.
![]() Restore Use this button to restore a particular revision. Restoring a revision creates a new revision that is based on the settings of the restored revision.
Restore Use this button to restore a particular revision. Restoring a revision creates a new revision that is based on the settings of the restored revision.
![]() Properties Use this button to view the properties of a particular revision.
Properties Use this button to view the properties of a particular revision.
More Info: Creating Configuration Items
You can learn more about creating configuration items at http://technet.microsoft.com/en-us/library/gg712331.aspx.
Configuration item settings
You have several choices for the types of settings to monitor when you create a configuration item for Windows operating systems, mobile device support, or Mac OS X. Each type of configuration setting is evaluated against its own compliance rules and has its own values to monitor.
When configuring compliance rules, the options you have range from simply checking whether a setting exists to comparing it to a specific value. You then specify the severity level if the condition is not met.
Windows settings
When you create a Windows configuration item, you can monitor several aspects of Windows-based computers. The following list describes the setting types that you can monitor for computers running Windows operating systems:
![]() Active Directory Query Use this setting type to construct a query to find values in Active Directory Domain Services (AD DS).
Active Directory Query Use this setting type to construct a query to find values in Active Directory Domain Services (AD DS).
![]() Assembly Use this setting type to specify an assembly from the global assembly cache to assess for compliance on computers.
Assembly Use this setting type to specify an assembly from the global assembly cache to assess for compliance on computers.
![]() File System Use this setting type to specify a file or folder to assess for compliance on computers.
File System Use this setting type to specify a file or folder to assess for compliance on computers.
![]() IIS Metabase Use this setting type to specify the Internet Information Services (IIS) metabase setting to assess for compliance on computers.
IIS Metabase Use this setting type to specify the Internet Information Services (IIS) metabase setting to assess for compliance on computers.
![]() Registry Key Use this setting type to specify a registry key to assess for compliance on computers.
Registry Key Use this setting type to specify a registry key to assess for compliance on computers.
![]() Registry Value Use this setting type to specify a registry value to assess for compliance on computers.
Registry Value Use this setting type to specify a registry value to assess for compliance on computers.
![]() Script Use this setting type to specify two scripts:
Script Use this setting type to specify two scripts:
![]() A discovery script to identify and return a value
A discovery script to identify and return a value
![]() A remediation script to remediate the noncompliant setting
A remediation script to remediate the noncompliant setting
![]() SQL Query Use this setting type to specify a SQL query to assess for compliance on computers.
SQL Query Use this setting type to specify a SQL query to assess for compliance on computers.
![]() WQL Query Use this setting type to specify a Windows Management Instrumentation (WMI) Query Language (WQL) query to assess for compliance on computers.
WQL Query Use this setting type to specify a Windows Management Instrumentation (WMI) Query Language (WQL) query to assess for compliance on computers.
![]() XPath Query Use this setting type to specify the XML file path and XML Path Language (XPath) query to assess for compliance on computers.
XPath Query Use this setting type to specify the XML file path and XML Path Language (XPath) query to assess for compliance on computers.
In addition, when using the Windows configuration item type, you can specify that the configuration item must include application settings. Depending on the application settings, the wizard displays detection methods for applications. You have the following options for detecting applications:
![]() Always Assume Application Is Installed
Always Assume Application Is Installed
![]() Use Windows Installer Detection
Use Windows Installer Detection
![]() Detect A Specific Application And Deployment Type
Detect A Specific Application And Deployment Type
![]() Use A Custom Script To Detect This Application
Use A Custom Script To Detect This Application
Mobile device settings
When you create a mobile device configuration item, you can monitor several setting groups for compliance. These setting groups are as follows:
![]() Password This group includes typical password settings such as the password length and password expiration.
Password This group includes typical password settings such as the password length and password expiration.
![]() Device This group contains device restriction settings.
Device This group contains device restriction settings.
![]() Email Management This group includes typical settings for email such as allowed protocols, attachments, and archives.
Email Management This group includes typical settings for email such as allowed protocols, attachments, and archives.
![]() Store This group contains application store settings.
Store This group contains application store settings.
![]() Browser This group contains default web browser settings.
Browser This group contains default web browser settings.
![]() Internet Explorer This group contains Internet Explorer settings for Windows-based clients.
Internet Explorer This group contains Internet Explorer settings for Windows-based clients.
![]() Content Rating This group contains content rating for audio, video, and app content.
Content Rating This group contains content rating for audio, video, and app content.
![]() Cloud This group enables you to specify cloud restrictions that apply to mobile devices.
Cloud This group enables you to specify cloud restrictions that apply to mobile devices.
![]() Security This group includes typical security settings such as file signing, apps, Bluetooth, and cameras.
Security This group includes typical security settings such as file signing, apps, Bluetooth, and cameras.
![]() Peak Synchronization This group includes settings that control the hours and frequency of mobile device synchronization.
Peak Synchronization This group includes settings that control the hours and frequency of mobile device synchronization.
![]() Roaming This group includes settings that configure download options for mobile devices when they are roaming.
Roaming This group includes settings that configure download options for mobile devices when they are roaming.
![]() Encryption This group includes encryption settings for devices, email, and storage cards.
Encryption This group includes encryption settings for devices, email, and storage cards.
![]() Wireless Communications This group includes settings to configure wireless network connections for mobile devices.
Wireless Communications This group includes settings to configure wireless network connections for mobile devices.
![]() Certificates This group specifies the certificates to install on mobile devices.
Certificates This group specifies the certificates to install on mobile devices.
![]() System Security This group includes settings for system security, including firewall, automatic updates, and antimalware protection.
System Security This group includes settings for system security, including firewall, automatic updates, and antimalware protection.
![]() Windows Server Work Folders This group enables you to configure Windows Server work folder settings.
Windows Server Work Folders This group enables you to configure Windows Server work folder settings.
Mac OS X settings
You can monitor the following setting types on Configuration Manager clients running the Mac OS X operating system:
![]() Mac OS X Preferences This setting type includes preferences within Mac OS X that use the following data types on application IDs and keys: string, date and time, integer, floating point, and Boolean.
Mac OS X Preferences This setting type includes preferences within Mac OS X that use the following data types on application IDs and keys: string, date and time, integer, floating point, and Boolean.
![]() Script This setting type allows a script to run that returns the value to be assessed for client compliance.
Script This setting type allows a script to run that returns the value to be assessed for client compliance.
Compliance rules
The simplest compliance rule to configure is an Existential rule. Existential rules test whether a setting exists. You can choose whether the compliance state exists or does not exist. In addition to testing for existence, the File system setting also supports the following compliance rule: File Exists The Following Number Of Times. This rule uses any of the available operators to compare values from 0 through 9999.
Another type of rule is the Value rule. You use value rules to compare the current value in the configuration item to a specified value by using one of the available operators. Some of the setting types support more than just a simple comparison. For example:
![]() The value rule for the Registry Key setting enables you to evaluate permissions on a registry key for compliance.
The value rule for the Registry Key setting enables you to evaluate permissions on a registry key for compliance.
![]() The value rule for the File System setting enables you to evaluate the following properties:
The value rule for the File System setting enables you to evaluate the following properties:
![]() Date Modified
Date Modified
![]() Date CreatedSize (Bytes)
Date CreatedSize (Bytes)
![]() Product Name
Product Name
![]() File Version
File Version
![]() Company
Company
![]() Secure Hash Algorithm 1 (SHA-1)
Secure Hash Algorithm 1 (SHA-1)
![]() Attributes
Attributes
![]() Permissions
Permissions
![]() The value rule for the Assembly setting enables you to evaluate the following properties: Version, Culture, and Public Key Token.
The value rule for the Assembly setting enables you to evaluate the following properties: Version, Culture, and Public Key Token.
Depending on the compliance rule you create, you can choose from several relational operators to compare a current value to a desired value. You can use the following operators for this purpose:
![]() Equals
Equals
![]() Not Equal To
Not Equal To
![]() Greater Than
Greater Than
![]() Greater Than Or Equal To
Greater Than Or Equal To
![]() Less Than
Less Than
![]() Less Than Or Equal To
Less Than Or Equal To
![]() Between
Between
![]() One Of
One Of
![]() None Of
None Of
Severity levels
Computers that do not comply with one or more of the objects or settings in the configuration item send a state message and a status message with one of the following noncompliant severity levels:
![]() None
None
![]() Information
Information
![]() Warning
Warning
![]() Critical
Critical
![]() Critical With Event
Critical With Event
Computers that do not comply with one or more of the objects or settings in the configuration item log a Windows application event message (Event ID: 11857) of the type Error. State messages and status messages the client sends have the noncompliant severity level of Critical With Event.
Remediation
Configuration Manager supports remediation only for the following configuration items:
![]() Registry values
Registry values
![]() Scripts
Scripts
![]() WQL query configuration items
WQL query configuration items
![]() All mobile phone settings
All mobile phone settings
![]() Mac OS X Preferences
Mac OS X Preferences
Remediation is available only when the type operator is set to Equals in all cases except for mobile phone settings. During remediation, Configuration Manager performs one of the following actions based on the setting type:
![]() Create the value if it does not exist (when the rule type is Value and the operator is Equals).
Create the value if it does not exist (when the rule type is Value and the operator is Equals).
![]() Set the value if it exists but is not compliant.
Set the value if it exists but is not compliant.
![]() Run a remediation script when using a script-based configuration item.
Run a remediation script when using a script-based configuration item.
![]() Set the value for the mobile device settings if supported by the mobile device operating system. (Not all mobile devices support the same settings.)
Set the value for the mobile device settings if supported by the mobile device operating system. (Not all mobile devices support the same settings.)
The method in which you configure remediation depends on the type of setting:
![]() For a registry value or WQL query configuration item, in the compliance rule, select the Remediate Noncompliance Rules When Supported check box. If you select this check box, the remediation action will be one of the following:
For a registry value or WQL query configuration item, in the compliance rule, select the Remediate Noncompliance Rules When Supported check box. If you select this check box, the remediation action will be one of the following:
![]() Create The Value If It Does Not Exist.
Create The Value If It Does Not Exist.
![]() Set The Value If It Exists But Is Not Compliant.
Set The Value If It Exists But Is Not Compliant.
![]() For a script configuration setting, you need to provide an appropriate remediation script.
For a script configuration setting, you need to provide an appropriate remediation script.
![]() For mobile device configuration settings, on each setting group that you add to the configuration item, you must select the Remediate The Noncompliant Settings check box.
For mobile device configuration settings, on each setting group that you add to the configuration item, you must select the Remediate The Noncompliant Settings check box.
Configuration item remediation occurs only when the item is included in a baseline deployment that you also have configured for remediation. (For remediation to be successful, you must configure remediation both on the compliance rule and in the deployment properties of the configuration baseline in which the configuration item is listed.) Due to the requirement for both the item and deployment to support remediation, you can use the same configuration item in both remediating and nonremediating deployments.
 Exam Tip
Exam Tip
Remember which configuration item types allow remediation.
 Thought experiment: Configuration Items at Contoso
Thought experiment: Configuration Items at Contoso
You are testing the compliance functionality of Configuration Manager. Specifically, you are interested in monitoring the configuration of mobile devices and determining whether a prohibited file-sharing application is installed on Configuration Manager clients running the Windows 8.1 operating system. With this information in mind, answer the following questions:
1. What must you configure in addition to Configuration Manager to manage mobile device configuration item settings?
2. Which configuration item type could you use to determine whether a prohibited application is installed on Configuration Manager clients running the Windows 8.1 operating system?
Objective summary
![]() The Compliance Settings feature enables you to assess and manage configuration settings for Configuration Manager clients.
The Compliance Settings feature enables you to assess and manage configuration settings for Configuration Manager clients.
![]() Configuration items contain one or more unique settings and values that you want to compare for compliance evaluation.
Configuration items contain one or more unique settings and values that you want to compare for compliance evaluation.
![]() Use the create a child configuration item method to create a configuration item that inherits the properties of an existing configuration item.
Use the create a child configuration item method to create a configuration item that inherits the properties of an existing configuration item.
![]() Use the copy existing configuration items method to create a configuration item with the properties of an existing configuration item but for which you want to modify some settings.
Use the copy existing configuration items method to create a configuration item with the properties of an existing configuration item but for which you want to modify some settings.
![]() Configuration Manager maintains a revision history of each configuration item. When you modify a configuration item, you do not lose the previous settings, and you can still use the previous settings in a configuration baseline.
Configuration Manager maintains a revision history of each configuration item. When you modify a configuration item, you do not lose the previous settings, and you can still use the previous settings in a configuration baseline.
![]() Configuration Manager supports the following noncompliant severity levels: None, Information, Warning, Critical, and Critical With Event.
Configuration Manager supports the following noncompliant severity levels: None, Information, Warning, Critical, and Critical With Event.
![]() Configuration Manager supports remediation only for the following configuration items: registry values, scripts, WQL query configuration items, all mobile phone settings, and Mac OS X Preferences (where the value type operator is set to Equals).
Configuration Manager supports remediation only for the following configuration items: registry values, scripts, WQL query configuration items, all mobile phone settings, and Mac OS X Preferences (where the value type operator is set to Equals).
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. Which of the following configuration item types supports remediation? (Choose two. Each correct answer provides a complete solution.)
A. Registry values
B. Registry keys
C. WQL query
D. XPath query
2. Which the following setting types would you use in a configuration item to determine whether a particular file was present on a Configuration Manager client?
A. Active Directory query
B. Assembly
C. File system
D. Registry value
3. Which of the following setting types would you use in a configuration item to determine whether a specific registry key was present on a Configuration Manager client?
A. Registry value
B. WQL query
C. Script
D. Registry key
4. Which of the following setting types would you use in a configuration item to run a script to remediate a noncompliant setting?
A. WQL query
B. Script
C. File system
D. Assembly
5. You have a WMI query language query that determines the amount of free disk space on a computer’s operating system volume. Which of the following setting types would you use in a configuration item to determine whether a Configuration Manager client had more than 15 GB of free space on the operating system volume? (Choose the best answer.)
A. WQL query
B. Script
C. File system
D. Registry value
Objective 4.2: Create and monitor a baseline
Configuration baselines enable you to collect configuration items, software updates, and even other configuration baselines as a way of determining compliance. You can create your own baselines or import preexisting baselines through configuration packs. You can use the results of a compliance check to create a new collection.
This section covers the following topics:
![]() Configuration baselines
Configuration baselines
![]() Creating configuration baselines
Creating configuration baselines
![]() Deploying configuration baselines
Deploying configuration baselines
![]() Configuration packs
Configuration packs
![]() Viewing compliance information
Viewing compliance information
Configuration baselines
A configuration baseline is a group of configuration items, software updates, and other configuration baselines. If a system is noncompliant with one item in a configuration baseline, it is noncompliant with the configuration baseline.
If you include configuration items for multiple products and system settings in a single baseline, you increase the baseline’s complexity. This makes managing the baseline more difficult. A simpler approach is to create several single product or system settings baselines and then deploy the baselines to the Configuration Manager collections to which you want to apply them. When you evaluate the baselines, the compliance results are easier for you to analyze. You can use the same configuration item in multiple configuration baselines.
After you create a configuration baseline, you can deploy it to a collection. This enables that collection’s devices or primary devices of the collection’s users to download the configuration baseline and assess compliance with each of the baseline’s configuration items.
Client settings contain the default schedule for running evaluations as shown in Figure 4-2. When you deploy a configuration baseline to a collection, you can specify remediation settings, alert settings, and a schedule for that configuration baseline to use for evaluating the client systems.
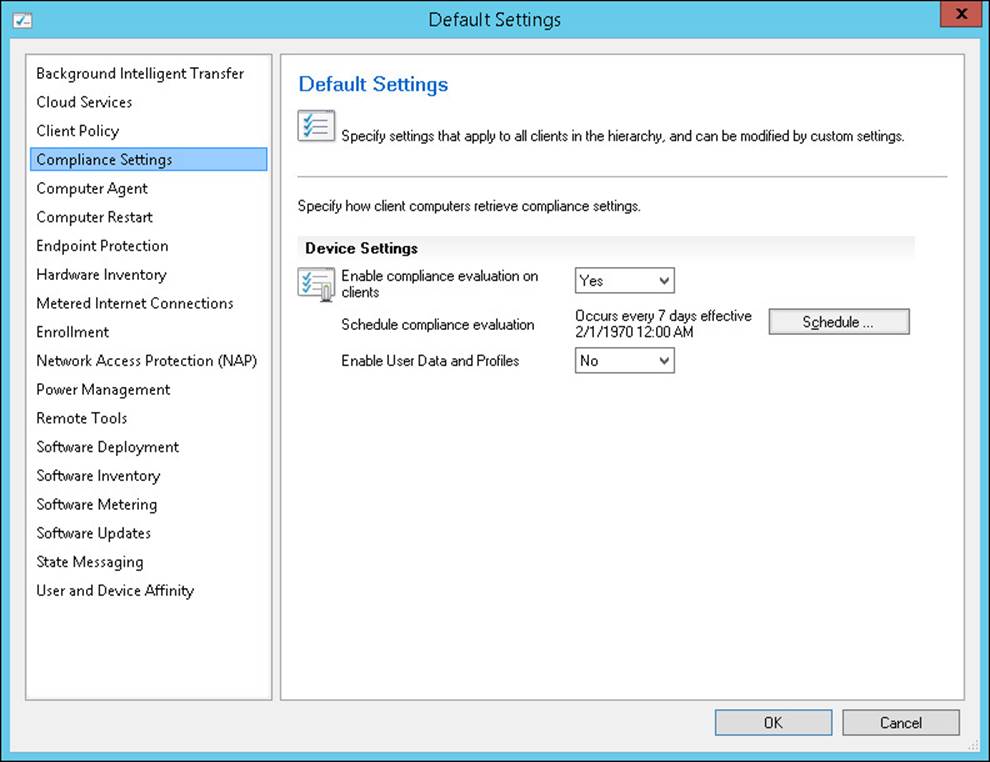
FIGURE 4-2 Compliance Settings
You can use the evaluation results of the configuration baseline to create a collection. If the configuration baseline contains configuration items that do not support automatic remediation, you can use this collection as a target so that an additional task can remediate the issue. For example, you might use the configuration items in a configuration baseline to detect a forbidden application. You then can create a collection based on the configuration baseline and deploy an application or package to uninstall the forbidden application.
You can create collections based on the following compliance states: Compliant, Error, Non-Compliant, and Unknown. You can access the wizard for creating the collection by selecting the configuration baseline and then selecting the Deployment tab. When you select a deployment on the Deployment tab, a Create New Collection menu appears on both the ribbon and the Actions menu. You can use this option to create a query-based collection according to the state you have chosen.
More Info: Configuration Baselines
You can learn more about configuration baselines at http://technet.microsoft.com/en-au/library/gg712268.aspx.
Creating configuration baselines
You can create a configuration baseline in one of the following ways:
![]() Create a configuration baseline manually, using the Create Configuration Baseline dialog box.
Create a configuration baseline manually, using the Create Configuration Baseline dialog box.
![]() Import configuration data.
Import configuration data.
![]() Copy an existing configuration baseline.
Copy an existing configuration baseline.
If a configuration item has multiple revisions, you can specify which version of the configuration item is used in the baseline.
Create a configuration baseline manually
The most direct way to create a configuration baseline is to select the Configuration Baselines node, which is located under Compliance Settings in the Assets And Compliance workspace, and then click the Create Configuration Baseline button on the ribbon. This launches the Create Configuration Baseline dialog box, shown in Figure 4-3.
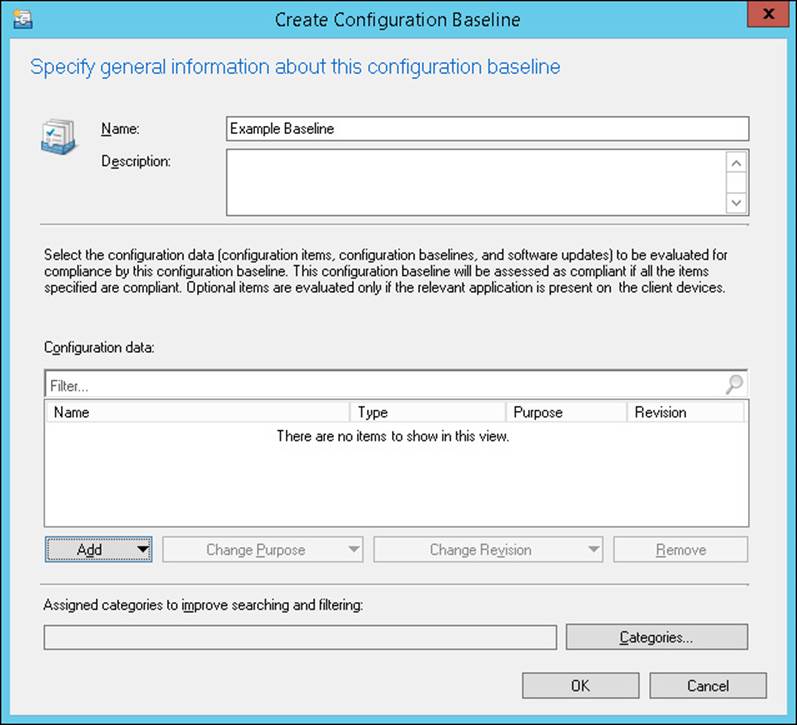
FIGURE 4-3 Create Configuration Baseline
Import configuration data
The process to import the configuration baselines is the same as the process to import configuration items. You use the Import Configuration Data Wizard to import one or more .cab files containing configuration baselines, configuration items, or both. Then you can use them in Configuration Manager.
Copy an existing configuration baseline
You use this method to create a configuration baseline when you want a configuration baseline with the properties of an existing configuration baseline. After you make the copy, you can modify the properties to create the configuration baseline you require. When you copy a configuration baseline, you do not maintain a relationship between the new configuration baseline and the configuration baseline that you copied. To copy a configuration baseline, select the configuration baseline that you want to copy and then, on the ribbon, click Copy. This opens the Configuration Baseline Name dialog box.
Deploying configuration baselines
Deploying a configuration baseline to a collection of client devices enables you to perform an evaluation of those devices against the baseline. To deploy a configuration baseline, select an existing configuration baseline and then, on the ribbon, click Deploy. This opens the Deploy Configuration Baselines dialog box shown in Figure 4-4.
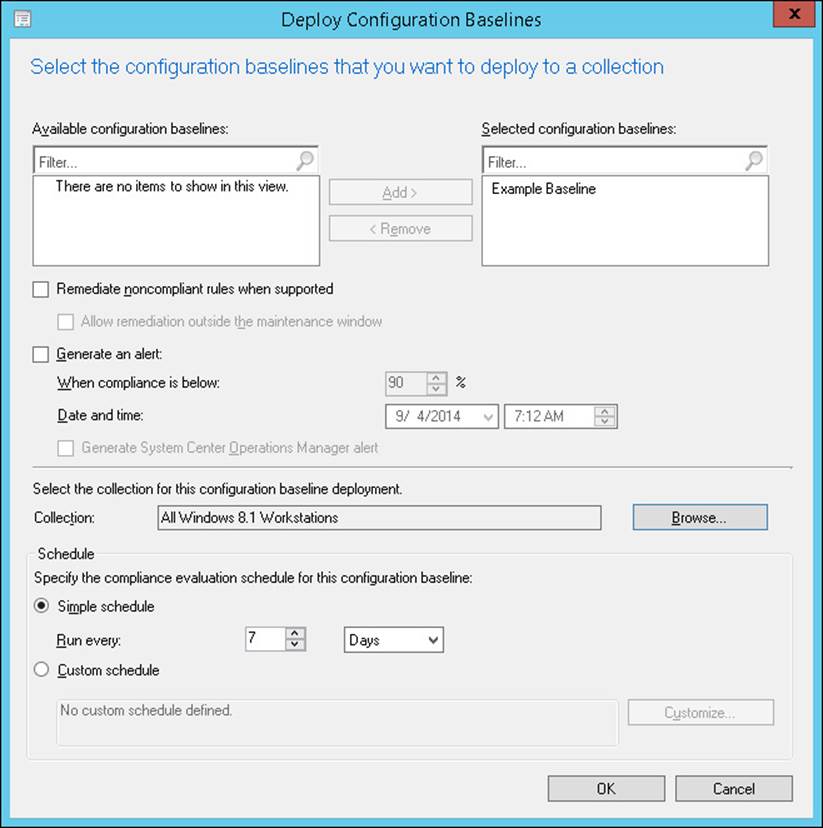
FIGURE 4-4 Deploy Configuration Baselines
The following settings are available in the Deploy Configuration Baselines dialog box:
![]() Available Configuration Baselines Use this list box to select any additional baselines you want to deploy as part of this deployment.
Available Configuration Baselines Use this list box to select any additional baselines you want to deploy as part of this deployment.
![]() Selected Configuration Baselines This list box displays the baselines that are selected for this deployment.
Selected Configuration Baselines This list box displays the baselines that are selected for this deployment.
![]() Remediate Noncompliant Rules When Supported You can configure certain configuration items for automatic remediation. If you enable remediation, you also can allow the remediation process to ignore maintenance windows by selecting the Allow Remediation Outside The Maintenance Window check box.
Remediate Noncompliant Rules When Supported You can configure certain configuration items for automatic remediation. If you enable remediation, you also can allow the remediation process to ignore maintenance windows by selecting the Allow Remediation Outside The Maintenance Window check box.
![]() Generate An Alert When Compliance Is Below The Specified Percentage After The Specified Date And Time When you enable this setting, the compliance percentage check box and the Date And Time check box are also selected. If the specified percentage of systems is not compliant by the specified date and time, Configuration Manager generates an alert. If you are using System Center 2012 R2 Operations Manager, you can configure Configuration Manager to send the alert to Operations Manager as well, by enabling Generate System Center Operations Manager Alert in this dialog box.
Generate An Alert When Compliance Is Below The Specified Percentage After The Specified Date And Time When you enable this setting, the compliance percentage check box and the Date And Time check box are also selected. If the specified percentage of systems is not compliant by the specified date and time, Configuration Manager generates an alert. If you are using System Center 2012 R2 Operations Manager, you can configure Configuration Manager to send the alert to Operations Manager as well, by enabling Generate System Center Operations Manager Alert in this dialog box.
![]() Select The Collection For This Configuration Baseline Deployment Use the Browse button in this option to select the user or device collection to which this baseline will deploy.
Select The Collection For This Configuration Baseline Deployment Use the Browse button in this option to select the user or device collection to which this baseline will deploy.
![]() Specify The Compliance Evaluation Schedule For This Configuration Baseline Use the default schedule configured on the default client settings or customize the evaluation schedule for the deployment.
Specify The Compliance Evaluation Schedule For This Configuration Baseline Use the default schedule configured on the default client settings or customize the evaluation schedule for the deployment.
More Info: Deploying Baselines
You can learn more about deploying baselines at http://technet.microsoft.com/en-us/library/hh219289.aspx.
Configuration packs
Configuration packs are predefined configuration items or configuration baselines that Microsoft and other developers provide to organizations. These configuration packs often represent best-practice configurations for common operating systems, server roles, services, and programs. For example, some auditing firms use configuration packs to assess whether an organization complies with specific regulations regarding computer configuration.
You can download Microsoft and some non-Microsoft configuration packs from the Microsoft System Center Marketplace. In addition, you can find configuration packs created by users on several Configuration Manager community support websites. You also can add existing Configuration Manager 2007 configuration packs to System Center 2012 R2 Configuration Manager by using the import functionality.
After you download and import a configuration pack, you can use the configuration items and configuration baselines as they are. Alternatively, you can use them as a starting point for your own configuration settings and then modify the imported configuration packs to meet your requirements.
Viewing compliance information
You can use the Configuration Manager Control Panel item to evaluate the baselines for compliance settings manually or to view the evaluation results for the compliance settings baselines. You require local administrator rights to view a report in the Configuration Manager Control Panel item.
To view compliance on a Configuration Manager client, you can access the Configuration Manager Properties dialog box within Control Panel. The Configurations tab of the Configuration Manager Properties dialog box displays the following basic information:
![]() A list of all the configuration baselines, including the last version of the baseline that was downloaded
A list of all the configuration baselines, including the last version of the baseline that was downloaded
![]() The last time the evaluation was performed and the results of the evaluation
The last time the evaluation was performed and the results of the evaluation
![]() The configuration baseline evaluations (if any) that are currently running on this computer
The configuration baseline evaluations (if any) that are currently running on this computer
You can use the Configurations tab to perform the following actions:
![]() Evaluate You can select a deployed configuration baseline and then use the Evaluate button to run the evaluation outside the current schedule.
Evaluate You can select a deployed configuration baseline and then use the Evaluate button to run the evaluation outside the current schedule.
![]() View Report When you click the View Report button, an Internet Explorer window appears, displaying a report on the selected configuration baseline. The report displays the compliance status of the baseline and all the configuration items that are in the configuration baseline.
View Report When you click the View Report button, an Internet Explorer window appears, displaying a report on the selected configuration baseline. The report displays the compliance status of the baseline and all the configuration items that are in the configuration baseline.
![]() Refresh The Refresh button updates the display with current information.
Refresh The Refresh button updates the display with current information.
The Configuration Manager site receives the compliance information the client systems generate in the form of state messages. You can use this information to:
![]() View the compliance of the deployment.
View the compliance of the deployment.
![]() Create collections based on the state of configuration items.
Create collections based on the state of configuration items.
![]() Generate and view compliance reports.
Generate and view compliance reports.
Compliance monitoring
Like all deployments, you can monitor the compliance baseline deployments in the Monitoring workspace in the Deployments node. When you select a compliance deployment, the preview pane displays the following:
![]() General information This section includes the name of the deployment and the target collection.
General information This section includes the name of the deployment and the target collection.
![]() Compliance statistics This section includes a pie chart displaying the relative number of Compliant, Error, Non-Compliant, and Unknown client systems. The total asset count and the time of the summarization appear with a link to a detailed status view.
Compliance statistics This section includes a pie chart displaying the relative number of Compliant, Error, Non-Compliant, and Unknown client systems. The total asset count and the time of the summarization appear with a link to a detailed status view.
![]() Related objects This section includes links to the target collection and the deployed baseline.
Related objects This section includes links to the target collection and the deployed baseline.
When you click the View Status link in the preview pane, Configuration Manager displays a more detailed view of the compliance information. The Deployment Status window shows general information similar to the information in the preview pane, including the name of the baseline and target collection and the time the last summarization ran. The Compliant, Error, Non-Compliant, and Unknown tabs display detailed information such as the configuration items, the number of assets, and a list of clients. You can use the More Details link to view the details of a specific asset.
Compliance management reports
The following reports, some of which are listed in Figure 4-5, are available for viewing compliance evaluation results:
![]() List Of Unknown Assets For A Configuration Baseline
List Of Unknown Assets For A Configuration Baseline
![]() List Of Rules Conflicting With A Specified Rule For An Asset
List Of Rules Conflicting With A Specified Rule For An Asset
![]() List Of Assets By Compliance State For A Configuration Item In A Configuration Baseline
List Of Assets By Compliance State For A Configuration Item In A Configuration Baseline
![]() Rules And Errors Summary Of Configuration Items In A Configuration Baseline For An Asset
Rules And Errors Summary Of Configuration Items In A Configuration Baseline For An Asset
![]() Summary Compliance Of A Configuration Baseline For A Collection
Summary Compliance Of A Configuration Baseline For A Collection
![]() Summary Compliance By Configuration Items For A Configuration Baseline
Summary Compliance By Configuration Items For A Configuration Baseline
![]() Summary Compliance By Configuration Baseline
Summary Compliance By Configuration Baseline
![]() List Of Assets By Compliance State For A Configuration Baseline
List Of Assets By Compliance State For A Configuration Baseline
![]() Details Of Compliant Rules Of Configuration Items In A Configuration Baseline For An Asset
Details Of Compliant Rules Of Configuration Items In A Configuration Baseline For An Asset
![]() Compliance History Of A Configuration Item
Compliance History Of A Configuration Item
![]() Compliance History Of A Configuration Baseline
Compliance History Of A Configuration Baseline
![]() Details Of Conflicting Rules Of Configuration Items In A Configuration Baseline For An Asset
Details Of Conflicting Rules Of Configuration Items In A Configuration Baseline For An Asset
![]() Details Of Remediated Rules Of Configuration Items In A Configuration Baseline For An Asset
Details Of Remediated Rules Of Configuration Items In A Configuration Baseline For An Asset
![]() Details Of Noncompliant Rules Of Configuration Items In A Configuration Baseline For An Asset
Details Of Noncompliant Rules Of Configuration Items In A Configuration Baseline For An Asset
![]() Details Of Errors Of Configuration Items In A Configuration Baseline For An Asset
Details Of Errors Of Configuration Items In A Configuration Baseline For An Asset
![]() List Of Unknown Assets For A Configuration Item
List Of Unknown Assets For A Configuration Item
![]() Details Of Conflicting Rules Of Configuration Items In A Configuration Baseline For An Asset
Details Of Conflicting Rules Of Configuration Items In A Configuration Baseline For An Asset
![]() Details Of Compliant Rules Of Configuration Items In A Configuration Baseline For An Asset
Details Of Compliant Rules Of Configuration Items In A Configuration Baseline For An Asset
![]() Summary Compliance By Configuration Policies
Summary Compliance By Configuration Policies
![]() List Of Assets With Certificate Nearing Expiry
List Of Assets With Certificate Nearing Expiry
![]() List Of Assets By Certificate Insurance Status
List Of Assets By Certificate Insurance Status
![]() Certificate Issuance History
Certificate Issuance History
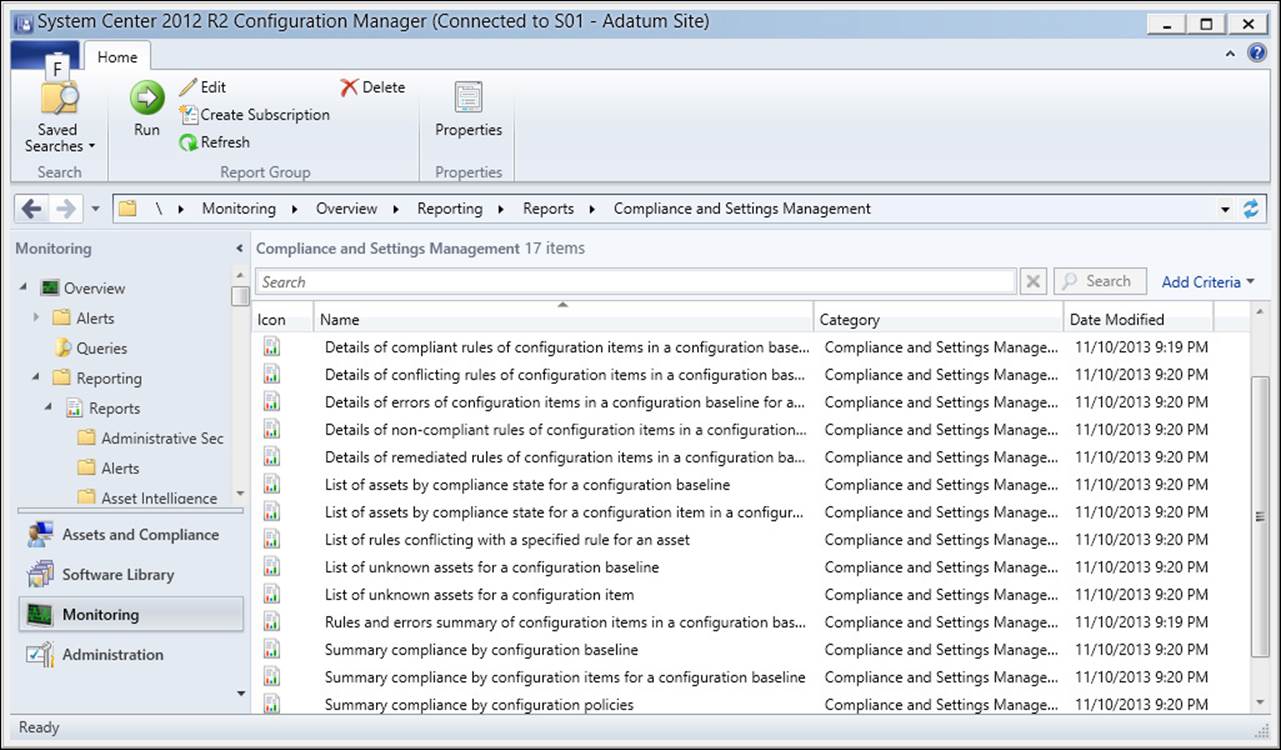
FIGURE 4-5 Compliance reports
More Info: Monitor Compliance Settings
You can learn more about monitoring compliance settings at http://technet.microsoft.com/en-us/library/gg712303.aspx/.
 Exam Tip
Exam Tip
Remember that you can use the compliance results as the basis for creating new collections.
 Thought experiment: Compliance Monitoring at Fabrikam
Thought experiment: Compliance Monitoring at Fabrikam
You are using Configuration Manager’s compliance functionality to monitor compliance across multiple device collections at your organization. A specific baseline, which includes a large number of configuration items, reports a large percentage of noncompliant clients. You’re interested in determining whether a large number of configuration items or just one or two items are causing the noncompliant result. With this information in mind, answer the following questions:
1. Which report would you use to determine the specific configuration items in a baseline that are triggering noncompliance when applied to a collection?
2. Which report would you view to determine the compliance trend for a configuration baseline?
Objective summary
![]() A configuration baseline is a group of configuration items, software updates, and other configuration baselines.
A configuration baseline is a group of configuration items, software updates, and other configuration baselines.
![]() You can group configuration items into configuration baselines.
You can group configuration items into configuration baselines.
![]() You deploy configuration baselines to client systems to evaluate compliance and (potentially) perform remediation.
You deploy configuration baselines to client systems to evaluate compliance and (potentially) perform remediation.
![]() You can use the evaluation results of the configuration baseline to create a collection.
You can use the evaluation results of the configuration baseline to create a collection.
![]() Configuration packs are predefined configuration items or configuration baselines that Microsoft and other developers provide to organizations.
Configuration packs are predefined configuration items or configuration baselines that Microsoft and other developers provide to organizations.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. Which of the following can you include in a configuration baseline? (Choose two. Each correct answer provides a complete solution.)
A. Configuration item
B. Antimalware policy
C. Windows Firewall policy
D. Software updates
2. Which of the following options must you select when deploying a configuration baseline so that configuration items are automatically remediated when it is possible to do so? (Choose two. Each correct answer provides a complete solution.)
A. Select The Collection For This Configuration Baseline Deployment
B. Select The Compliance Evaluation Schedule For This Configuration Baseline
C. Generate An Alert When Compliance Is Below The Specified Percentage After The Specified Date And Time
D. Remediate Noncompliant Rules When Supported
3. You want an alert to be generated if the percentage of computers in a specific collection that isn’t compliant after two weeks rises above 25 percent. Which of the following settings must you configure when configuring the deployment of a configuration baseline? (Choose two. Each correct answer provides part of a complete solution.)
A. Remediate Noncompliant Rules When Supported
B. Generate An Alert When Compliance Is Below The Specified Percentage After The Specified Date And Time
C. Select The Compliance Evaluation Schedule For This Configuration Baseline
D. Select The Collection For This Configuration Baseline Deployment
4. A configuration baseline includes a configuration item that tests for the presence of a particular file on the operating system volume. You want to create a collection of all computers in the Sydney Windows 8.1 Computers collection on which this file is not present on the operating system volume. Which of the following compliance states should you use as the basis for creating a new collection?
A. Compliant
B. Non-Compliant
C. Error
D. Unknown
Objective 4.3: Configure Endpoint Protection
System Center Endpoint Protection is an antimalware client that you can deploy, manage, and monitor as part of your organization’s Configuration Manager deployment. You can also use System Center Endpoint Protection to manage the firewall settings of Configuration Manager clients.
This section covers the following topics:
![]() System Center Endpoint Protection
System Center Endpoint Protection
![]() Implement Endpoint Protection
Implement Endpoint Protection
![]() Antimalware policies
Antimalware policies
![]() Windows Firewall policies
Windows Firewall policies
![]() Policy management
Policy management
![]() Monitoring Endpoint Protection status
Monitoring Endpoint Protection status
![]() Configuring alerts
Configuring alerts
System Center Endpoint Protection
System Center Endpoint Protection is an antimalware client. Prior to the release of System Center 2012, this client was part of the ForeFront suite of products. When you deploy the Configuration Manager Endpoint Protection feature, an Endpoint Protection client installs on Configuration Manager client computers. You can use the Endpoint Protection client to:
![]() Detect and remediate malware, rootkit, network, and spyware vulnerabilities The Endpoint Protection client provides protection by performing scheduled scans on a computer or by enabling real-time protection. Both these methods monitor file and program activity on a computer. The client can use Network Inspection System to inspect network traffic for the most commonly used protocols, such as HTTP, Server Message Block (SMB), and Simple Mail Transfer Protocol (SMTP).
Detect and remediate malware, rootkit, network, and spyware vulnerabilities The Endpoint Protection client provides protection by performing scheduled scans on a computer or by enabling real-time protection. Both these methods monitor file and program activity on a computer. The client can use Network Inspection System to inspect network traffic for the most commonly used protocols, such as HTTP, Server Message Block (SMB), and Simple Mail Transfer Protocol (SMTP).
![]() Automatically download antimalware definitions and engine updates You can deploy policies that define how often antimalware definitions are updated and how a client obtains the updates.
Automatically download antimalware definitions and engine updates You can deploy policies that define how often antimalware definitions are updated and how a client obtains the updates.
![]() Manage Windows Firewall settings Endpoint Protection provides basic management of Windows Firewall for the domain, private, and public profiles. Settings include enabling or disabling the firewall; notifying the user when Windows Firewall blocks a new program; and blocking all incoming connections, including those in the list of allowed programs.
Manage Windows Firewall settings Endpoint Protection provides basic management of Windows Firewall for the domain, private, and public profiles. Settings include enabling or disabling the firewall; notifying the user when Windows Firewall blocks a new program; and blocking all incoming connections, including those in the list of allowed programs.
Integrating Endpoint Protection with Configuration Manager provides the following benefits:
![]() Flexible source locations for client updates You can use a variety of source locations for definition updates. You can configure Endpoint Protection to:
Flexible source locations for client updates You can use a variety of source locations for definition updates. You can configure Endpoint Protection to:
![]() Obtain updates that Configuration Manager or Windows Server Update Services (WSUS) distributes.
Obtain updates that Configuration Manager or Windows Server Update Services (WSUS) distributes.
![]() Allow direct connection to Microsoft Update and the Microsoft Malware Protection Center.
Allow direct connection to Microsoft Update and the Microsoft Malware Protection Center.
![]() Obtain updates from a Universal Naming Convention (UNC) file share.
Obtain updates from a Universal Naming Convention (UNC) file share.
![]() The ability to take advantage of the management infrastructure Endpoint Protection uses the existing Configuration Manager infrastructure to communicate policy settings to clients and retrieve status information from clients.
The ability to take advantage of the management infrastructure Endpoint Protection uses the existing Configuration Manager infrastructure to communicate policy settings to clients and retrieve status information from clients.
![]() Enhanced monitoring and reporting Configuration Manager provides extensive monitoring capabilities such as email notifications, in-console monitoring, and reports that inform administrators of malware presence and the security status of client computers.
Enhanced monitoring and reporting Configuration Manager provides extensive monitoring capabilities such as email notifications, in-console monitoring, and reports that inform administrators of malware presence and the security status of client computers.
More Info: Introduction to Endpoint Protection
You can learn more about Endpoint Protection at http://technet.microsoft.com/en-us/library/hh508781.aspx.
Implement Endpoint Protection
Implement Endpoint Protection by performing the following general steps:
1. In the central administration site or a standalone site, install the Endpoint Protection Point Site System role.
2. Create collections as necessary and then configure Endpoint Protection alerts for each collection. Subscribe to alerts as necessary.
3. Determine the source for obtaining updates to malware definitions and the antimalware engine. You must configure additional roles, such as the Software Update Point role, if you plan to use Configuration Manager software updates as the update source.
4. Configure antimalware policies as needed. The Default Antimalware Policy will apply to all Endpoint Protection clients in the hierarchy. You can create and deploy custom antimalware policies that will override the settings in the default policy.
5. Configure client settings for Endpoint Protection. You can use client settings to install and enable Endpoint Protection clients on client computers. As you enable clients, any antimalware policies that you have configured through client settings will come into effect. You can create and deploy custom client settings to target specific collections as needed.
6. Optionally, create and deploy Windows Firewall policies. You can configure Windows Firewall profile settings and then deploy the policy to specific collections.
7. Monitor and manage Endpoint Protection by using the console and alerts.
Prerequisites
To implement Endpoint Protection within your Configuration Manager primary site or hierarchy, you must meet the following prerequisites:
![]() Endpoint Protection point Before you can install the Endpoint Protection client on workstations, you must install and configure an Endpoint Protection Point Site System role at the top site in the hierarchy, whether that is a central administration site or a standalone primary site.
Endpoint Protection point Before you can install the Endpoint Protection client on workstations, you must install and configure an Endpoint Protection Point Site System role at the top site in the hierarchy, whether that is a central administration site or a standalone primary site.
![]() Client settings To install the Endpoint Protection client on workstations, you must configure the appropriate default client settings or create and deploy a custom client setting that targets specific collections.
Client settings To install the Endpoint Protection client on workstations, you must configure the appropriate default client settings or create and deploy a custom client setting that targets specific collections.
![]() Software update point If you want to use software updates to deliver antimalware definition and engine updates, you must implement the Software Updates feature of Configuration Manager.
Software update point If you want to use software updates to deliver antimalware definition and engine updates, you must implement the Software Updates feature of Configuration Manager.
![]() Reporting services point Before you can run reports related to Endpoint Protection, you must configure a reporting services point site system.
Reporting services point Before you can run reports related to Endpoint Protection, you must configure a reporting services point site system.
![]() Security permissions The Endpoint Protection Manager security role provides the ability to create and modify antimalware and Windows Firewall policies. This security role also enables you to deploy Endpoint Protection policies to collections, to monitor status, and to create and modify console alerts and reports. You must configure the security role before you implement Endpoint Protection.
Security permissions The Endpoint Protection Manager security role provides the ability to create and modify antimalware and Windows Firewall policies. This security role also enables you to deploy Endpoint Protection policies to collections, to monitor status, and to create and modify console alerts and reports. You must configure the security role before you implement Endpoint Protection.
You can download specific Endpoint Protection clients to protect Mac computers and Linux clients from the Microsoft Volume Licensing Service Center. You cannot manage these clients from the Configuration Manager console. However, you can use a System Center 2012 Operations Manager management pack to manage Linux clients from Operations Manager.
More Info: Prerequisites
You can learn more about Endpoint Protection prerequisites at http://technet.microsoft.com/en-us/library/hh508780.aspx.
The Site System role
You must deploy the Endpoint Protection Point Site System role before you can install Endpoint Protection on client computers. Consider the following factors when you deploy this Endpoint Protection role:
![]() Deployment within a Configuration Manager hierarchy You can install the Endpoint Protection point only on a single site system server. You must locate this server within the central administration site for a hierarchy configuration or in the primary site in a standalone primary site configuration. You also must accept the specific Endpoint Protection license agreement when prompted.
Deployment within a Configuration Manager hierarchy You can install the Endpoint Protection point only on a single site system server. You must locate this server within the central administration site for a hierarchy configuration or in the primary site in a standalone primary site configuration. You also must accept the specific Endpoint Protection license agreement when prompted.
![]() Microsoft Active Protection Service membership When you install an Endpoint Protection point, you may specify the default Microsoft Active Protection Service membership setting. If you choose to join the service, Configuration Manager automatically collects information about detected software and sends it to Microsoft. Based on this information, Microsoft creates new antimalware definitions. You can choose from two levels of membership:
Microsoft Active Protection Service membership When you install an Endpoint Protection point, you may specify the default Microsoft Active Protection Service membership setting. If you choose to join the service, Configuration Manager automatically collects information about detected software and sends it to Microsoft. Based on this information, Microsoft creates new antimalware definitions. You can choose from two levels of membership:
![]() Basic membership If you choose this membership, basic information is sent to Microsoft, which includes information about where the software originated and the actions the user or application performed. This level of membership will not alert the user if the service detects a change by a software program that has not been subject to risk assessment.
Basic membership If you choose this membership, basic information is sent to Microsoft, which includes information about where the software originated and the actions the user or application performed. This level of membership will not alert the user if the service detects a change by a software program that has not been subject to risk assessment.
![]() Advanced membership This level of membership will alert the user when the service detects a change by software that has not been subject to risk assessment by Microsoft. In addition to basic information, this membership level will send information such as software location, file names, how the software operates, and the effect that the software has had on the computer.
Advanced membership This level of membership will alert the user when the service detects a change by software that has not been subject to risk assessment by Microsoft. In addition to basic information, this membership level will send information such as software location, file names, how the software operates, and the effect that the software has had on the computer.
![]() Verification of installation status You can verify the successful installation of an Endpoint Protection point by monitoring the SMS_ENDPOINT_PROTECTION _MANAGER component for a message with the ID of 500. An ID of 500 indicates that the component has started. The EPSetup.log file also provides details about the installation status.
Verification of installation status You can verify the successful installation of an Endpoint Protection point by monitoring the SMS_ENDPOINT_PROTECTION _MANAGER component for a message with the ID of 500. An ID of 500 indicates that the component has started. The EPSetup.log file also provides details about the installation status.
Client settings
You can use Default Client Settings to apply Endpoint Protection installation settings to all clients within the hierarchy. You would create and configure a Custom Client Device Settings item if you needed to apply unique settings to members of a specific collection. For example, you might want to deploy Endpoint Protection to a small group of computers first to test it before you deploy it to the entire hierarchy. Over time, you can add clients to the target collection to provide a phased deployment.
Figure 4-6 shows the Endpoint Protection settings of Default Client Settings.

FIGURE 4-6 Endpoint Protection settings
The Endpoint Protection section provides several settings that relate to the installation of the Endpoint Protection client. Table 4-2 describes these settings.
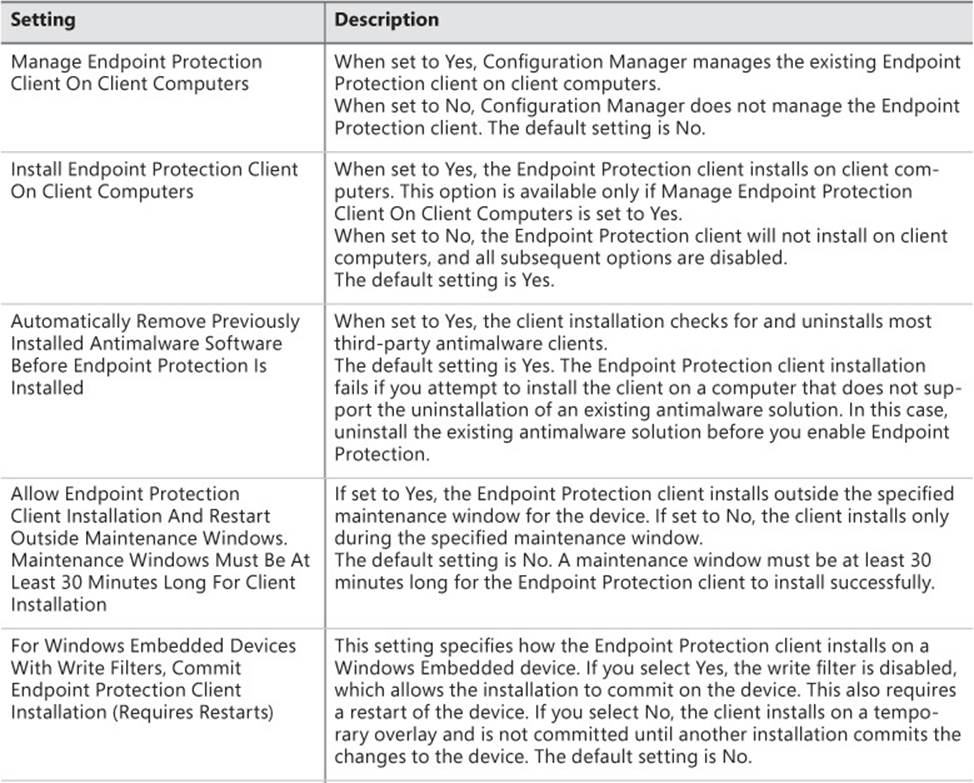
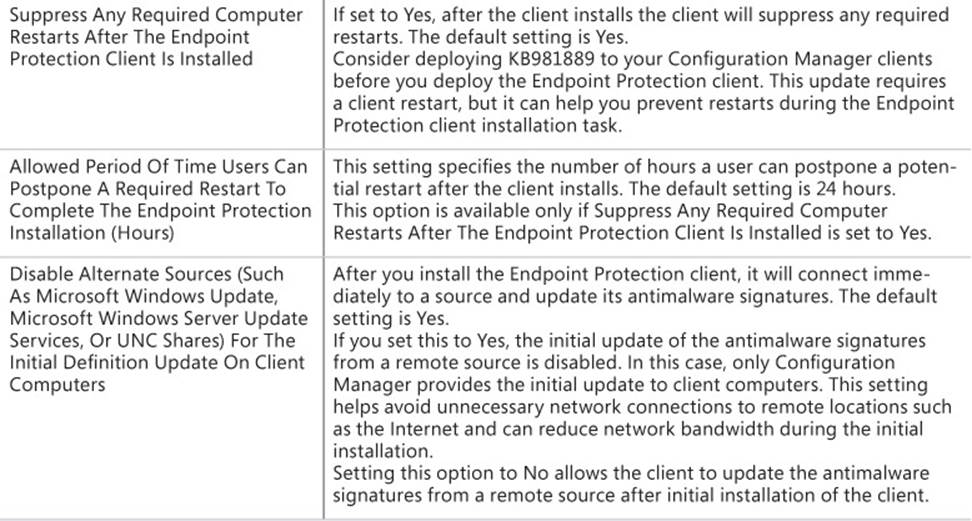
TABLE 4-2 Endpoint Protection settings
Antimalware policies
You use an antimalware policy to control configuration settings for the Endpoint Protection client on client computers. When you configure client settings to install Endpoint Protection on client computers, a default client antimalware policy is applied to provide initial protection after the installation.
Figure 4-7 shows the default client antimalware policy.
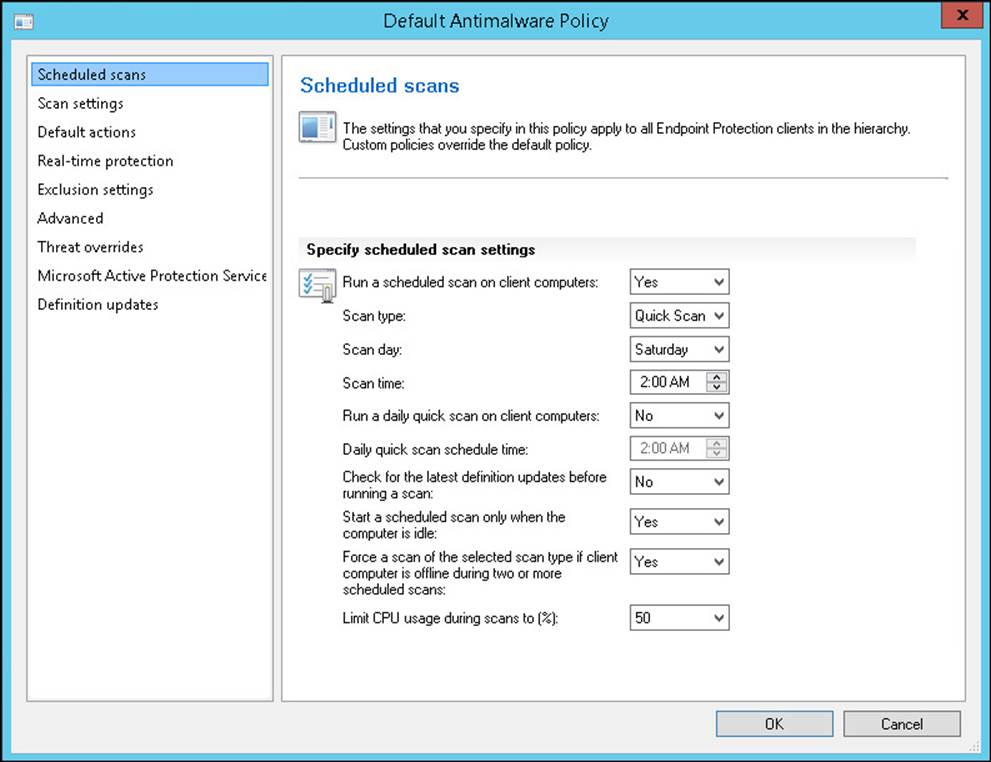
FIGURE 4-7 Scheduled Scans
You can import preconfigured policy templates, or you can create your own custom antimalware policy and deploy the policy to collections. This enables you to provide different Endpoint Protection client settings based on the requirements of the computers contained within a collection. For example, you might have a group of computers in a collection that require specific files or file locations excluded from the malware scan processes. A custom antimalware policy enables you to address this requirement.
If you deploy a custom antimalware policy to a collection, the custom policy settings merge with the default client antimalware policy. A single computer might be a member of multiple collections that have an assigned policy. The client uses priority evaluation to determine which policy to apply. The policy with the highest priority, which is the lowest number displayed in the Priority column, will take precedence. That policy then applies appropriate settings to the Endpoint Protection client software.
To modify the default antimalware policy, perform the following procedure:
1. In the Configuration Manager console, click the Assets And Compliance workspace.
2. Expand the Endpoint Protection node and then click Antimalware Policies.
3. In the results pane, click Default Client Malware Policy.
4. On the ribbon, click Properties.
The Default Antimalware Policy dialog box appears.
Settings that you configure in the Default Antimalware Policy dialog box apply to all computers in the hierarchy on which the Endpoint Protection client is installed unless overridden by a custom malware policy that is assigned to the client.
To create and deploy a custom antimalware policy, perform the following procedure:
1. In the Configuration Manager console, click the Assets And Compliance workspace.
2. Expand the Endpoint Protection node and then click Antimalware Policies.
3. On the ribbon, click Create Antimalware Policy.
The Create Antimalware Policy dialog box appears. In this dialog box, you can provide a name and specify configuration settings.
4. To assign a custom antimalware policy to a collection, choose the policy to deploy and then, on the ribbon, click Deploy.
The Select Collection dialog box appears.
5. In the Select Collection dialog box, select the collection to which you want to deploy this policy and then click OK.
You also can import an existing Endpoint Protection template by selecting the Antimalware Policies node and then clicking Import on the ribbon. Configuration Manager provides several preconfigured antimalware policy settings for high security, standard desktop, server role-based, or performance-optimized scenarios.
Table 4-3 lists the available antimalware policy settings.
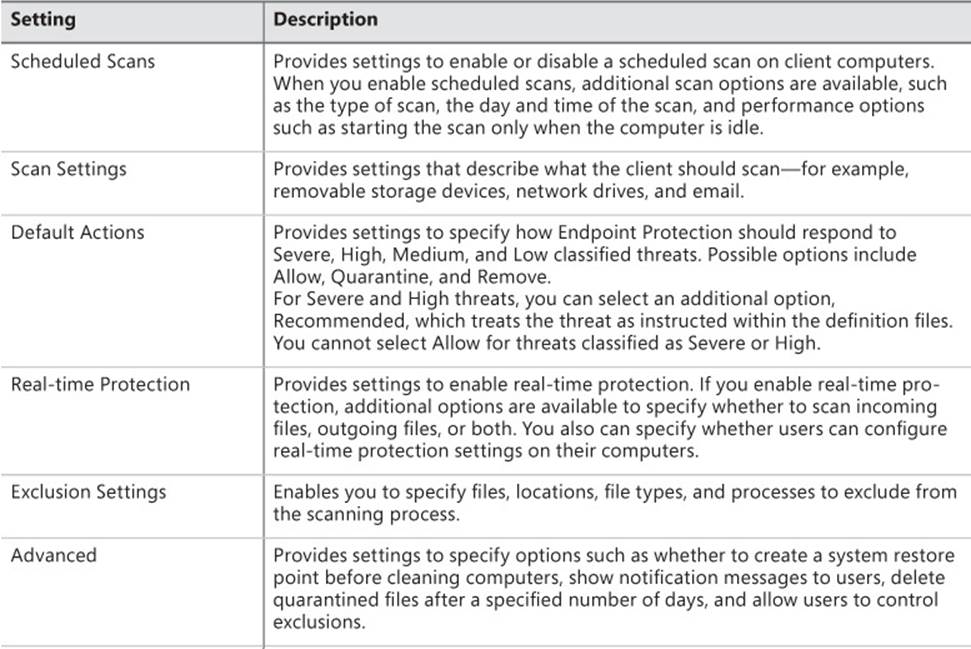
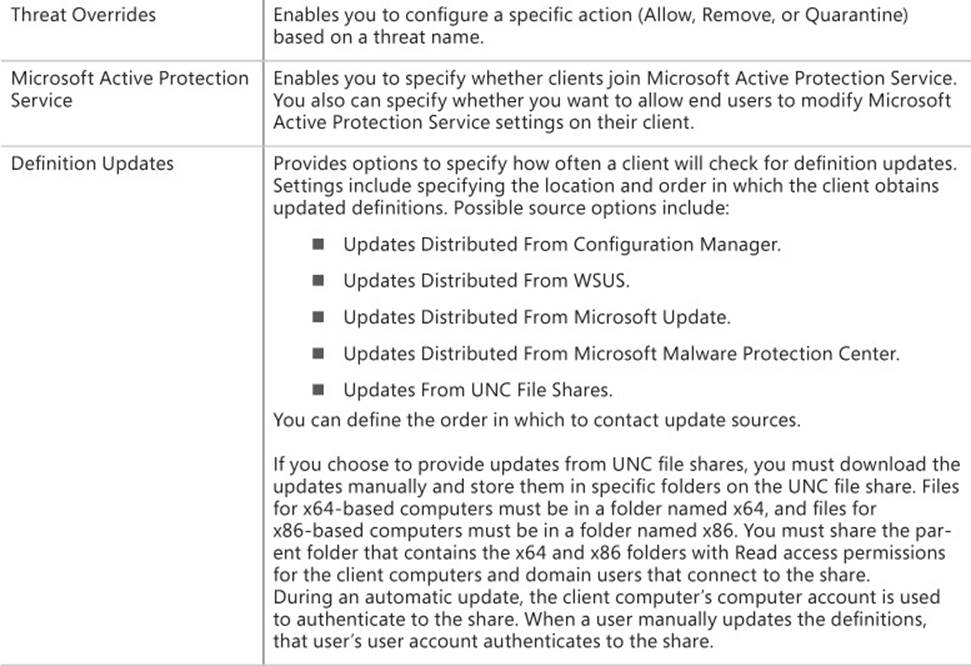
TABLE 4-3 Antimalware policy settings
More Info: Antimalware Policies
You can learn more about antimalware policies at http://technet.microsoft.com/en-us/library/hh508785.aspx.
Windows Firewall policies
Endpoint Protection provides you with the ability to control basic settings for Windows Firewall. You can configure a firewall policy to establish the following settings for each type of network profile, including domain, private, and public:
![]() Enable Windows Firewall This setting controls whether Windows Firewall is turned on or off. Options include Yes, No, and Not Configured.
Enable Windows Firewall This setting controls whether Windows Firewall is turned on or off. Options include Yes, No, and Not Configured.
![]() Block All Incoming Connections, Including Those In The List Of Allowed Programs This setting is available only if Enable Windows Firewall is set to Yes for the corresponding network profile. This setting controls whether incoming connections are allowed to the client computers. Options include Yes, No, and Not Configured.
Block All Incoming Connections, Including Those In The List Of Allowed Programs This setting is available only if Enable Windows Firewall is set to Yes for the corresponding network profile. This setting controls whether incoming connections are allowed to the client computers. Options include Yes, No, and Not Configured.
![]() Notify The User When Windows Firewall Blocks A New Program This setting is available only if Enable Windows Firewall is set to Yes for the corresponding network profile. This setting controls whether users are notified when Windows Firewall blocks a program. Options include Yes, No, and Not Configured.
Notify The User When Windows Firewall Blocks A New Program This setting is available only if Enable Windows Firewall is set to Yes for the corresponding network profile. This setting controls whether users are notified when Windows Firewall blocks a program. Options include Yes, No, and Not Configured.
In a manner similar to how you create a custom antimalware policy, you can create a firewall policy and then deploy the policy to a collection. There is no default Windows Firewall policy. During the policy deployment, you also can configure a schedule to evaluate compliance to the policy. This enables you to view deployment status for the policy to determine which clients are compliant or noncompliant with the Windows Firewall policy.
To create and deploy a firewall policy, perform the following procedure:
1. In the Configuration Manager console, click the Assets And Compliance workspace.
2. Expand the Endpoint Protection node and then click Windows Firewall Policies.
3. On the ribbon, click Create Windows Firewall Policy. The Create Windows Firewall Policy dialog box appears. Provide a name and description and then click Next.
4. On the Profile Settings page, configure settings for each of the network profiles, if required, and then complete the wizard.
To assign a firewall policy to a collection, perform the following procedure:
1. Select the policy you want to deploy and then, on the ribbon, click Deploy.
The Deploy Windows Firewall Policy dialog box appears.
2. Click the Browse button and, in the Select Collection dialog box, select the appropriate device collection. Click OK.
3. Under Specify The Compliance Evaluation Schedule For This Configuration Baseline, specify the schedule to evaluate client compliance with the policy. The default value is to evaluate compliance every seven days. Click OK to close the Deploy Windows Firewall Policy dialog box.
When you deploy a Windows Firewall policy to a device collection, the policy applies to clients in a random order over a two-hour period. This helps decrease the impact on the network.
Policy management
After you deploy antimalware and Windows Firewall policies, you can perform a number of policy management tasks. Table 4-4 provides a summary of them.
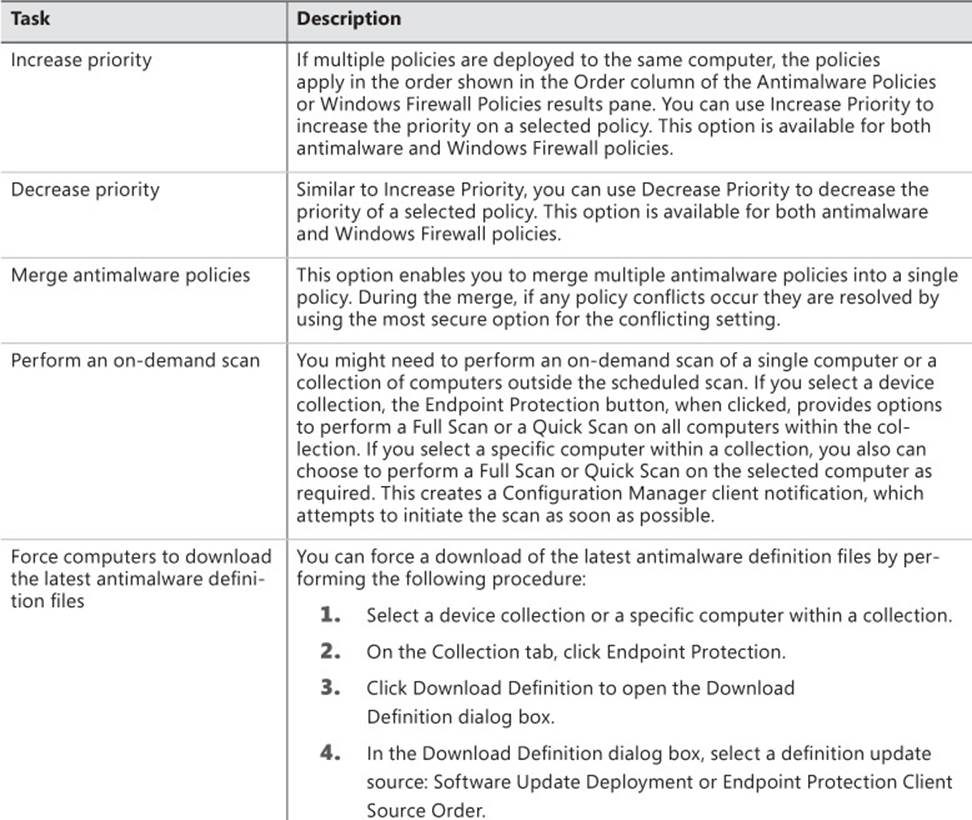
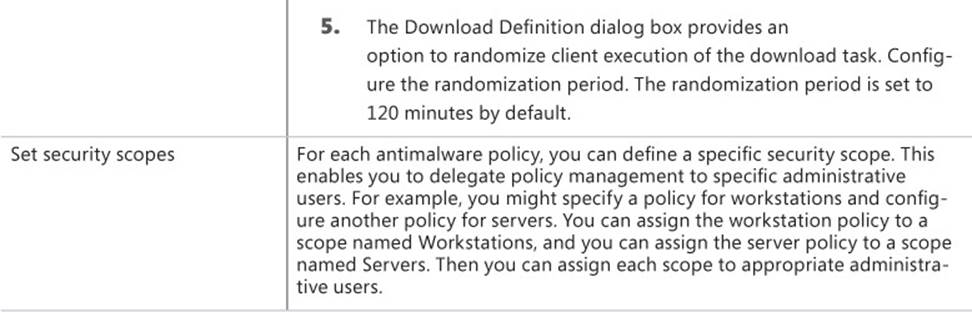
TABLE 4-4 Policy management tasks
More Info: Managing Policies
You can learn more about managing policies at http://technet.microsoft.com/en-us/library/hh524342.aspx.
Monitoring Endpoint Protection status
Configuration Manager provides extensive functionality, enabling you to monitor the status of the Endpoint Protection client. You can use Configuration Manager to perform the following monitoring tasks:
![]() Ensure that computers have successfully installed the Endpoint Protection client.
Ensure that computers have successfully installed the Endpoint Protection client.
![]() Determine the status of the antimalware definition files on computers.
Determine the status of the antimalware definition files on computers.
![]() Determine which types of malware have been detected, how many computers have been affected, and the remediation status.
Determine which types of malware have been detected, how many computers have been affected, and the remediation status.
Table 4-5 describes the methods to monitor Endpoint Protection status and compliance.
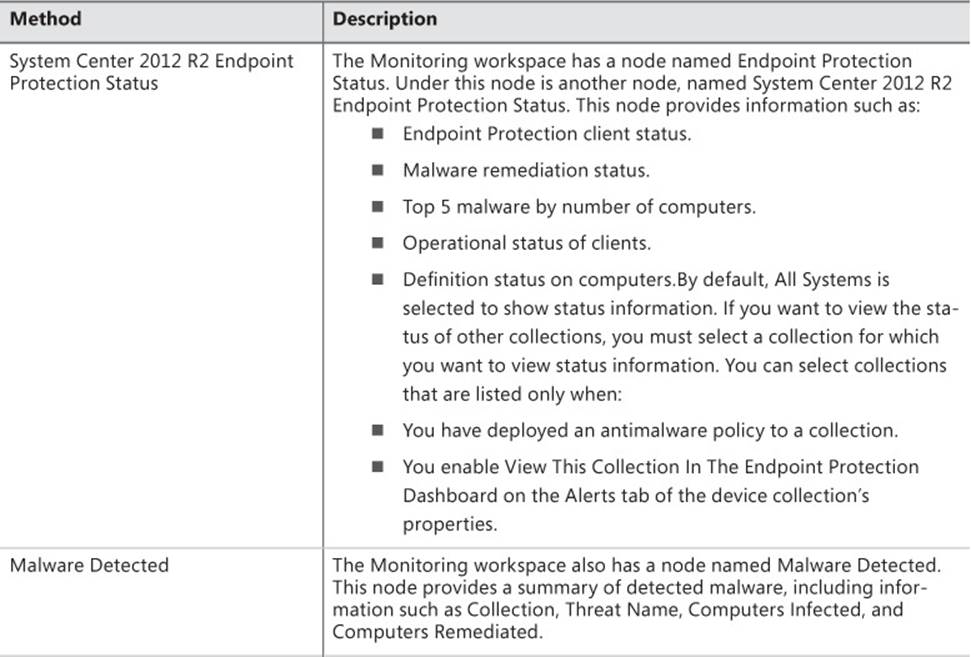
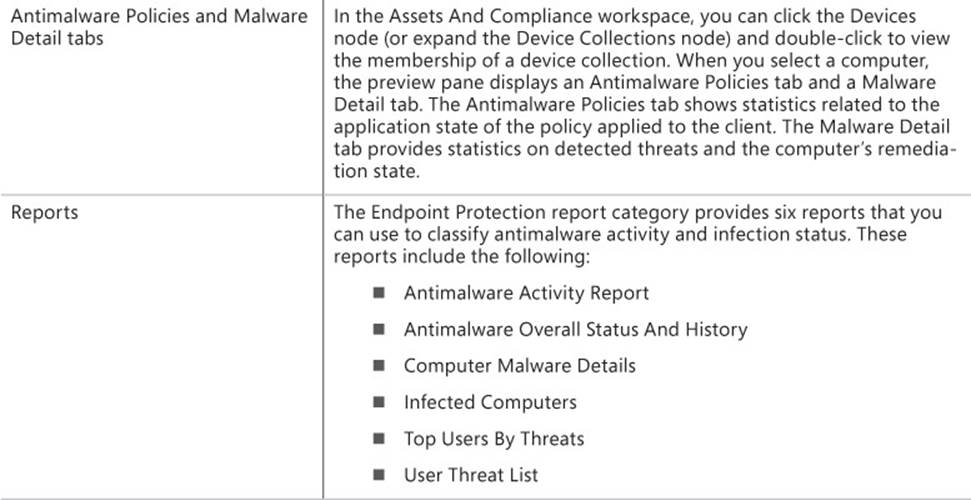
TABLE 4-5 Endpoint Protection monitoring methods
More Info: Monitoring Endpoint Protection
You can learn more about monitoring Endpoint Protection at http://technet.microsoft.com/en-us/library/hh508769.aspx.
Configuring alerts
You can use Configuration Manager alerts to notify administrative users when specific events have occurred within the hierarchy. You can configure alerts for each collection by opening the Properties dialog box of that collection and then selecting the Alerts tab and clicking Add. This displays the Add New Collection Alerts dialog box, shown in Figure 4-8. Table 4-6 describes the Endpoint Protection events that you can enable to generate alerts.
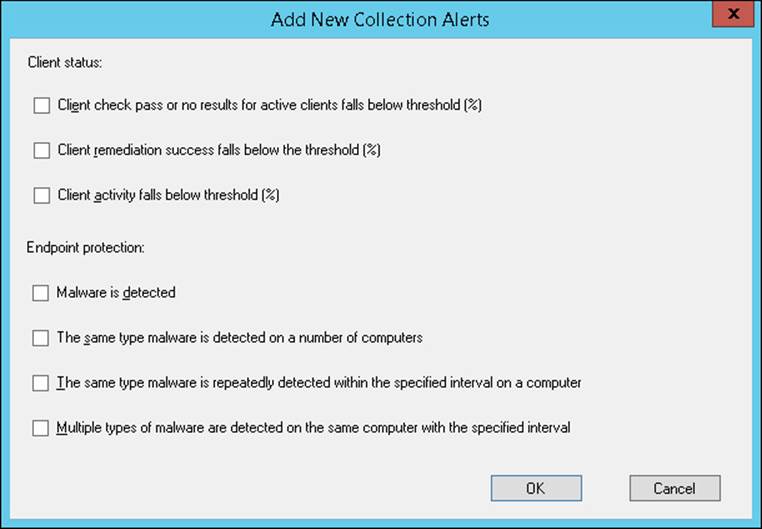
FIGURE 4-8 Add New Collection Alerts
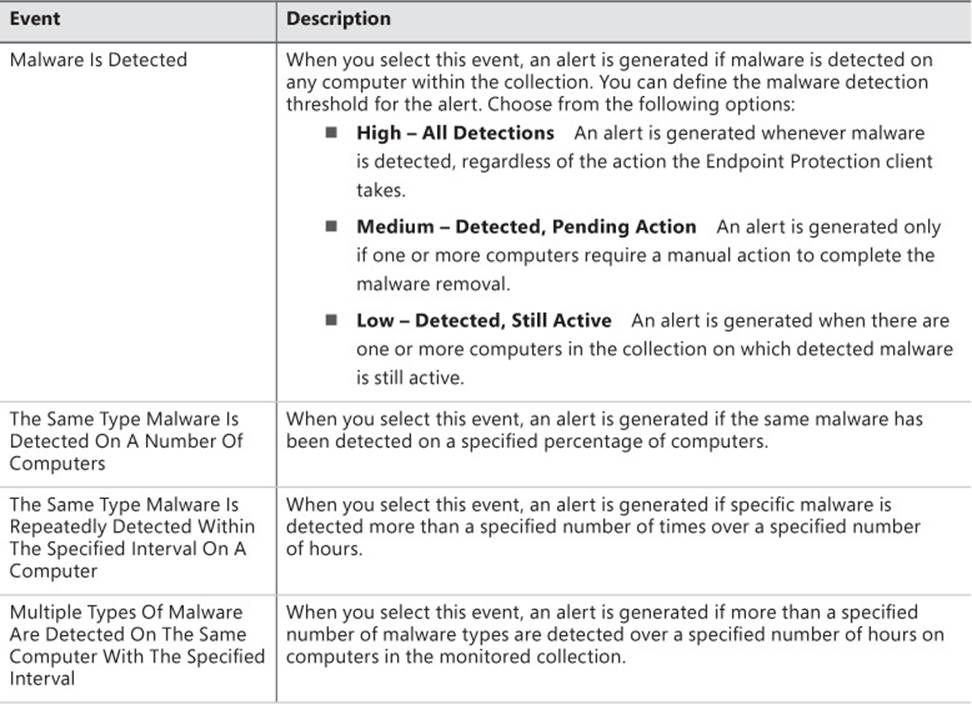
TABLE 4-6 Endpoint Protection alert settings
For each event, you also can specify the severity of the alert itself. Choose Critical, Warning, or Information.
More Info: Configuring Alerts
You can learn more about configuring alerts for Endpoint Protection in Configuration Manager at http://technet.microsoft.com/en-us/library/hh508782.aspx.
 Exam Tip
Exam Tip
Remember how antimalware policy priority works.
 Thought experiment: Endpoint Protection at Tailspin Toys
Thought experiment: Endpoint Protection at Tailspin Toys
You have noticed that computers at your organization’s Brisbane branch office seem more susceptible to malware infection than computers at other locations. Some computers are being infected repeatedly by the same type of malware. Sometimes the same malware infects multiple collections. You are configuring the collection alert settings for the Brisbane computers collection. With this information in mind, answer the following questions:
1. Which alert option should you configure to detect repeat infections on the same computer?
2. Which alert option should you configure to detect the same malware on multiple computers?
Objective summary
![]() System Center Endpoint Protection is an antimalware client that can detect and remediate malware, rootkit, network, and spyware vulnerabilities; automatically download antimalware definitions and engine updates; and manage Windows Firewall settings.
System Center Endpoint Protection is an antimalware client that can detect and remediate malware, rootkit, network, and spyware vulnerabilities; automatically download antimalware definitions and engine updates; and manage Windows Firewall settings.
![]() Endpoint Protection requires a Configuration Manager Endpoint Protection point, which you configure with client settings and, depending on how you want definition updates delivered, a software update point.
Endpoint Protection requires a Configuration Manager Endpoint Protection point, which you configure with client settings and, depending on how you want definition updates delivered, a software update point.
![]() You use an antimalware policy to control configuration settings for the Endpoint Protection client on client computers.
You use an antimalware policy to control configuration settings for the Endpoint Protection client on client computers.
![]() You can configure a firewall policy to establish settings for each type of network profile, including domain, private, and public.
You can configure a firewall policy to establish settings for each type of network profile, including domain, private, and public.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. Which of the following locations can host antimalware definition update files for an Endpoint Protection client? (Choose three. Each correct answer provides a complete solution.)
A. FTP site
B. Microsoft Update/Microsoft Malware Protection Center
C. UNC file share
D. WSUS server
2. Your organization has a central administration site; the Sydney primary site; the Melbourne primary site; and secondary sites at Canberra, Geelong, and Newcastle. The Geelong site is a secondary site of the Melbourne site. Clients in the Geelong site will be using System Center Endpoint Protection. In which site should you deploy the Endpoint Protection Point Site System role?
A. Central administration site
B. Melbourne
C. Sydney
D. Geelong
3. Which of the following would you configure in an antimalware policy to ensure that files on volume E were not scanned for malware by the Endpoint Protection client?
A. Advanced settings
B. Real-time protection
C. Exclusion settings
D. Threat overrides
4. Which of the following antimalware policy settings would you configure to have a system restore point automatically created by the Endpoint Protection client before cleaning malware from computers?
A. Real-time protection
B. Exclusion settings
C. Advanced settings
D. Threat overrides
Answers
Objective 4.1
Thought experiment
1. You must configure the Intune connector to manage mobile device configuration item settings.
2. You could look for application-specific registry settings by using Registry Key settings or look for files related to the application by using File System configuration item settings.
Objective review
1. Correct answers: A and C
A. Correct: Registry values support remediation.
B. Incorrect: Registry keys do not support remediation. Registry values do.
C. Correct: WQL queries support remediation.
D. Incorrect: XPath queries do not support remediation.
2. Correct answer: C
A. Incorrect: You use an Active Directory query setting type to perform an Active Directory query to locate values in Active Directory.
B. Incorrect: You use the Assembly setting type to determine whether an assembly from the global assembly cache is present.
C. Correct: You can use a File System setting type in a configuration item to determine whether a particular file is present on a Configuration Manager client.
D. Incorrect: You use a Registry Value setting type to check for a registry value.
3. Correct answer: D
A. Incorrect: You use a Registry Value setting type to check for a registry value. You use Registry Key to check for a registry key.
B. Incorrect: You use the WQL query setting to determine whether a WQL query run on a Configuration Manager client matches a specific value.
C. Incorrect: You can use the Script setting type to run a script that checks for a specific result or runs as a remediation script to remedy a noncompliant setting.
D. Correct: You use a Registry Key setting type to check for a registry key.
4. Correct answer: B
A. Incorrect: You use this setting to determine whether a WQL query run on a Configuration Manager client matches a specific value.
B. Correct: You can use the Script setting type to run a script that checks for a specific result or runs as a remediation script to remedy a noncompliant setting.
C. Incorrect: You can use a File System setting type in a configuration item to determine whether a particular file is present on a Configuration Manager client.
D. Incorrect: You use the Assembly setting type to determine whether an assembly from the global assembly cache is present.
5. Correct answer: A
A. Correct: You use this setting to determine whether a WQL query run on a Configuration Manager client matches, is greater than, or is less than a specific value.
B. Incorrect: Although you could call a script that runs the query, the best answer is to use the WQL query type directly rather than calling a WQL query in a script.
C. Incorrect: You can use a File System setting type in a configuration item to determine whether a particular file is present on a Configuration Manager client.
D. Incorrect: You use a Registry Value setting type to check for a registry value.
Objective 4.2
Thought experiment
1. You can use the Summary Compliance By Configuration items for a configuration baseline when looking at a collection. You use the detailed report for a specific asset.
2. You would use the compliance history of a configuration baseline report to view configuration baseline compliance trend data.
Objective review
1. Correct answers: A and D
A. Correct: A configuration baseline is a group of configuration items, software updates, and other configuration baselines.
B. Incorrect: A configuration baseline is a group of configuration items, software updates, and other configuration baselines.
C. Incorrect: A configuration baseline is a group of configuration items, software updates, and other configuration baselines.
D. Correct: A configuration baseline is a group of configuration items, software updates, and other configuration baselines.
2. Correct answers: A and D
A. Correct: You need to select the collection to which the configuration baseline will be deployed when deploying a baseline.
B. Incorrect: Although you can specify a schedule, you can use the default schedule, so Select The Compliance Evaluation Schedule For This Configuration Baseline is not mandatory.
C. Incorrect: You don’t need to generate alerts to accomplish this goal.
D. Correct: You select Remediate Noncompliant Rules When Supported to remediate noncompliant rules when possible.
3. Correct answers: B and D
A. Incorrect: You select Remediate Noncompliant Rules When Supported to remediate noncompliant rules when possible.
B. Correct: You need to configure Generate An Alert When Compliance Is Below The Specified Percentage After The Specified Date And Time to accomplish your goal.
C. Incorrect: Although you can specify a schedule, you can use the default schedule, so Select The Compliance Evaluation Schedule For This Configuration Baseline is not mandatory.
D. Correct: You need to select the collection to which the configuration baseline will be deployed when deploying a baseline.
4. Correct answer: B
A. Incorrect: The file will be present on computers that are compliant.
B. Correct: Computers that are noncompliant do not have the file and will form the basis of the new collection.
C. Incorrect: The Error state doesn’t allow you to determine whether the file is present and should not be used as the basis for the new collection.
D. Incorrect: The Unknown state doesn’t allow you to determine whether the file is present and should not be used as the basis for the new collection.
Objective 4.3
Thought experiment
1. You should configure The Same Type Malware Is Repeatedly Detected Within The Specified Interval On A Computer.
2. You should configure The Same Type Malware Is Detected On A Number Of Computers.
Objective review
1. Correct answers: B, C, and D
A. Incorrect: You can’t configure the Endpoint Protection client to retrieve antimalware definition updates from an FTP site.
B. Correct: Antimalware definition update files for the Endpoint Protection client can be retrieved from Microsoft Update/Microsoft Malware Protection Center.
C. Correct: Antimalware definition update files for the Endpoint Protection client can be hosted on a UNC file share.
D. Correct: Antimalware definition update files for the Endpoint Protection client can be hosted through WSUS.
2. Correct answer: A
A. Correct: You deploy the Endpoint Protection Point Site System role at the top of the Configuration Manager hierarchy.
B. Incorrect: You deploy the Endpoint Protection Point Site System role at the top of the Configuration Manager hierarchy.
C. Incorrect: You deploy the Endpoint Protection Point Site System role at the top of the Configuration Manager hierarchy.
D. Incorrect: You deploy the Endpoint Protection Point Site System role at the top of the Configuration Manager hierarchy.
3. Correct answer: C
A. Incorrect: Advanced settings enable you to configure options such as whether to create a system restore point before cleaning computers, show notification messages to users, delete quarantined files after a specified number of days, and allow users to control exclusions.
B. Incorrect: Use real-time protection settings to enable real-time protection. If you enable real-time protection, additional options are available to specify whether to scan incoming files, outgoing files, or both. You also can specify whether users can configure real-time protection settings on their computers.
C. Correct: Exclusion settings enable you to specify files, locations, file types, and processes to exclude from the scanning process.
D. Incorrect: Threat overrides settings enable you to configure a specific action (Allow, Remove, or Quarantine) based on a threat name.
4. Correct answer: C
A. Incorrect: Use real-time protection settings to enable real-time protection. If you enable real-time protection, additional options are available to specify whether to scan incoming files, outgoing files, or both. You also can specify whether users can configure real-time protection settings on their computers.
B. Incorrect: Exclusion settings enable you to specify files, locations, file types, and processes to exclude from the scanning process.
C. Correct: Advanced settings enable you to configure options such as whether to create a system restore point before cleaning computers, show notification messages to users, delete quarantined files after a specified number of days, and allow users to control exclusions.
D. Incorrect: Threat overrides settings enable you to configure a specific action (Allow, Remove, or Quarantine) based on a threat name.