Exam Ref 70-696 Managing Enterprise Devices and Apps (2014)
Chapter 5. Manage Configuration Manager clients
The Configuration Manager client is software that you deploy to devices that you intend to manage using System Center 2012 R2 Configuration Manager. The client performs tasks locally, based on the instructions received from Configuration Manager. Collections enable you to group devices or users for performing tasks by using Configuration Manager.
Objectives in this chapter:
![]() Objective 5.1: Deploy and manage the client agent.
Objective 5.1: Deploy and manage the client agent.
![]() Objective 5.2: Manage collections.
Objective 5.2: Manage collections.
![]() Objective 5.3: Configure and monitor client status.
Objective 5.3: Configure and monitor client status.
Objective 5.1: Deploy and manage the client agent
This objective deals with how to deploy the Configuration Manager client. It covers the properties of the client itself, the site systems that need to be present within the Configuration Manager hierarchy to support client deployment, the process of installing the client, and the management of client settings.
This section covers the following topics:
![]() The Configuration Manager client
The Configuration Manager client
![]() Site systems used in client deployment
Site systems used in client deployment
![]() Client installation
Client installation
![]() Client assignment
Client assignment
![]() Client settings
Client settings
The Configuration Manager client
You deploy the Configuration Manager client to devices to perform tasks on behalf of the Configuration Manager server. The Configuration Manager client consists of multiple elements that run in the background. These elements perform tasks based on the site configuration and policy.
On computers running Windows operating systems, the user interface (UI) for the Configuration Manager client consists of two parts: the Configuration Manager control panel and Software Center. If you managed previous versions of Configuration Manager, you are likely familiar with the Configuration Manager control panel. You access it through Control Panel on supported computers running Windows operating systems. You configure and manage the Configuration Manager client software for computers running Mac OS X, Linux, and UNIX operating systems through the command-line interface.
Unlike the Configuration Manager control panel, which is generally used by users with Administrative privileges, Software Center is designed for use by end users. Software Center, shown in Figure 5-1, provides end users with the ability to interact with the app distribution process.
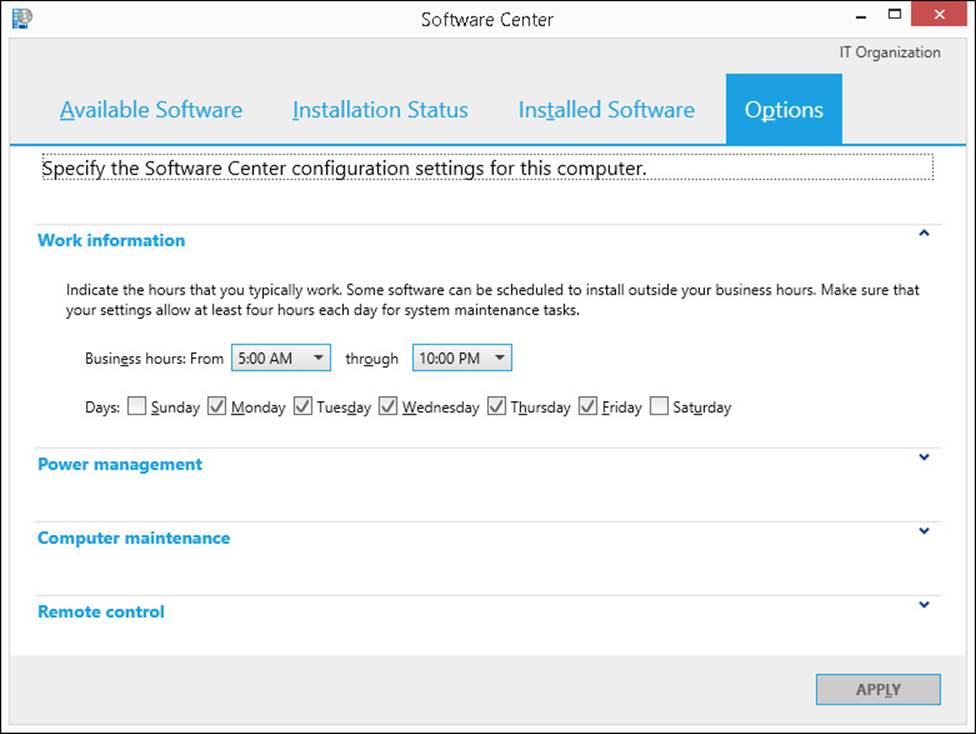
FIGURE 5-1 Software Center Options dialog box
The tabs of the Configuration Manager Properties dialog box are as follows:
![]() General This tab, shown in Figure 5-2, enables you to view identifying information about the client. This includes the build number, the assigned site, the type of certificate, and the management point the client is using.
General This tab, shown in Figure 5-2, enables you to view identifying information about the client. This includes the build number, the assigned site, the type of certificate, and the management point the client is using.
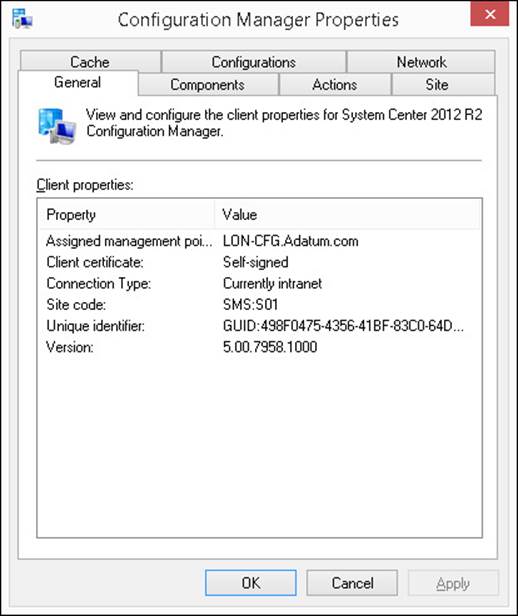
FIGURE 5-2 Configuration Manager Properties General tab
![]() Components This tab enables you to view information about the installed components and agents. When you install the client, this installs all client components and agents, even if you disable them at the site. On this tab, you can view versions of the individual components and whether they are enabled or disabled. This tab is shown in Figure 5-3.
Components This tab enables you to view information about the installed components and agents. When you install the client, this installs all client components and agents, even if you disable them at the site. On this tab, you can view versions of the individual components and whether they are enabled or disabled. This tab is shown in Figure 5-3.
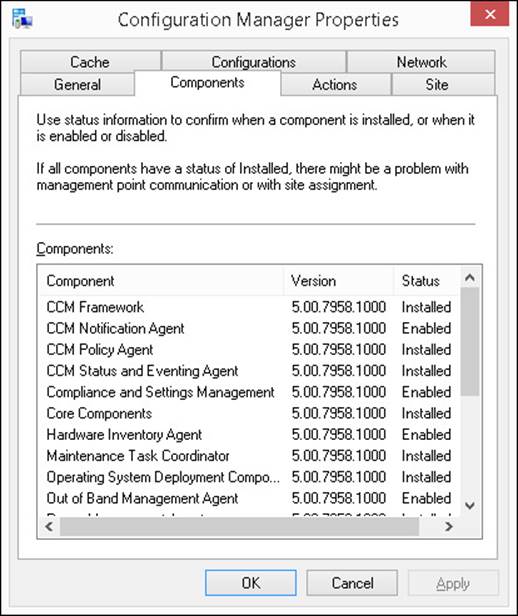
FIGURE 5-3 Configuration Manager Properties Components tab
![]() Actions This tab enables you to initiate client actions when you do not want to wait until the scheduled time. Client actions include starting a hardware or software inventory cycle, retrieving user or machine policy updates, and similar actions. Figure 5-4 shows this tab.
Actions This tab enables you to initiate client actions when you do not want to wait until the scheduled time. Client actions include starting a hardware or software inventory cycle, retrieving user or machine policy updates, and similar actions. Figure 5-4 shows this tab.
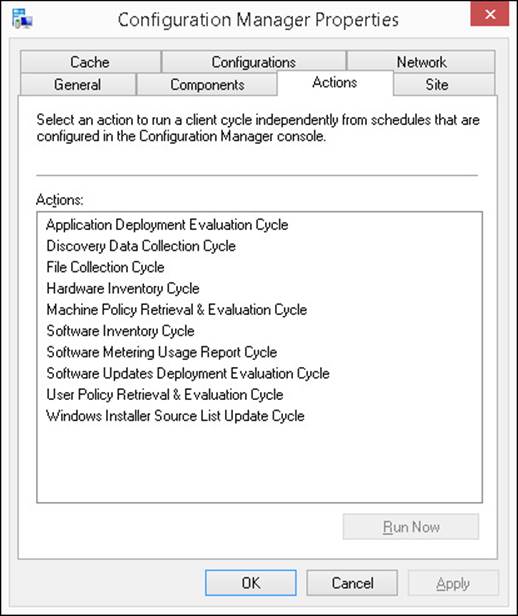
FIGURE 5-4 Configuration Manager Properties Actions tab
![]() Site This tab enables you to assign a client to a site either automatically or manually. Changes to this tab require local administrator rights.
Site This tab enables you to assign a client to a site either automatically or manually. Changes to this tab require local administrator rights.
![]() Cache Use this tab to configure the client cache settings. On this tab, you can change the cache location from the default location of %systemroot%\Ccmcache to a different location, or you can delete files from the cache. You also can change the cache’s size. Changes to this tab require local administrator rights.
Cache Use this tab to configure the client cache settings. On this tab, you can change the cache location from the default location of %systemroot%\Ccmcache to a different location, or you can delete files from the cache. You also can change the cache’s size. Changes to this tab require local administrator rights.
![]() Configurations This tab enables you to view the configuration baselines assigned to this client. You also can run an evaluation and view a local report of the client’s compliance. Access to local compliance reports from this tab requires local administrator rights.
Configurations This tab enables you to view the configuration baselines assigned to this client. You also can run an evaluation and view a local report of the client’s compliance. Access to local compliance reports from this tab requires local administrator rights.
![]() Network This tab enables you to configure settings for Internet-based management. Changes to this tab require local administrator rights.
Network This tab enables you to configure settings for Internet-based management. Changes to this tab require local administrator rights.
Users can set the following preferences for software delivery or remote control by using Software Center:
![]() Specify their work information, which includes business hours and days. Users must set aside at least four hours a day for Configuration Manager maintenance tasks.
Specify their work information, which includes business hours and days. Users must set aside at least four hours a day for Configuration Manager maintenance tasks.
![]() Exclude their system from the Configuration Manager Power Management feature if the Configuration Manager policy permits this.
Exclude their system from the Configuration Manager Power Management feature if the Configuration Manager policy permits this.
![]() Specify how software maintenance occurs. Users can specify that their systems install software after business hours or the suspension of Software Center activities while in presentation mode.
Specify how software maintenance occurs. Users can specify that their systems install software after business hours or the suspension of Software Center activities while in presentation mode.
![]() Override remote control settings for their computers if Configuration Manager policy permits it. Users can specify settings such as the level of remote access and whether permission is required to start a remote control session.
Override remote control settings for their computers if Configuration Manager policy permits it. Users can specify settings such as the level of remote access and whether permission is required to start a remote control session.
More Info: Client Settings
You can learn more about client settings at http://technet.microsoft.com/en-us/library/gg682067.aspx.
Workgroup-based clients
You can use Configuration Manager to manage computers that are not part of a domain. These computers, referred to as workgroup-based computers, must meet the following prerequisites:
![]() You must install the Configuration Manager client software manually on each workgroup-based computer by using an account with local administrator privileges.
You must install the Configuration Manager client software manually on each workgroup-based computer by using an account with local administrator privileges.
![]() You must configure a network access account to allow access to resources in the site server domain for clients that are not domain members.
You must configure a network access account to allow access to resources in the site server domain for clients that are not domain members.
There also are features that Configuration Manager does not support for workgroup-based computers, including:
![]() Using client push installation.
Using client push installation.
![]() Targeting users for application deployment.
Targeting users for application deployment.
![]() Performing global roaming.
Performing global roaming.
![]() Using Active Directory Domain Services (AD DS) to locate site system servers.
Using Active Directory Domain Services (AD DS) to locate site system servers.
![]() Using Active Directory discovery.
Using Active Directory discovery.
An alternative to managing nondomain client computers by using Configuration Manager is to manage them by using Microsoft Intune. In this scenario, ensure that you deploy the nondomain-joined client on a network with connectivity to the Internet.
Internet-based clients
You can use Configuration Manager to manage clients on internal networks and clients on external networks with Internet connectivity. Clients on external networks that have Internet connectivity are referred to as Internet-based clients. Configuration Manager uses HTTPS to communicate securely with these clients. To configure a client for Internet-based client management, you must obtain a computer certificate from a trusted certification authority (CA). You must also configure the client with the Internet fully qualified domain name (FQDN) of the management point. After you configure the client, you can manage it as long as the client retains connectivity to the Internet-facing site systems for its assigned Configuration Manager site.
To support HTTPS, you need to deploy a certificate from a trusted CA on the Configuration Manager site systems with which clients communicate. This can be from an internal CA that the client is configured to trust or from an external trusted CA. When using an internal enterprise CA, you can use only version 2 templates because Configuration Manager does not support certificates issued from version 3 and version 4 templates.
Internet-based clients do not support all Configuration Manager features. Specifically, Configuration Manager does not support the following client features on the Internet:
![]() Client deployment over the Internet, such as client push and software update–based client deployment. Use manual client installation instead.
Client deployment over the Internet, such as client push and software update–based client deployment. Use manual client installation instead.
![]() Auto-site assignment.
Auto-site assignment.
![]() Network Access Protection (NAP).
Network Access Protection (NAP).
![]() Wake On LAN (WOL).
Wake On LAN (WOL).
![]() Operating system deployment. However, you can deploy task sequences that do not deploy an operating system, such as task sequences that run scripts and maintenance tasks on clients.
Operating system deployment. However, you can deploy task sequences that do not deploy an operating system, such as task sequences that run scripts and maintenance tasks on clients.
![]() Remote control.
Remote control.
![]() Out-of-band management, which enables you to manage the computer before the operating system is active.
Out-of-band management, which enables you to manage the computer before the operating system is active.
![]() Software deployment to users unless the Internet-based management point can authenticate the user in AD DS by using Windows authentication (Kerberos authentication or Windows NT LAN Manager). This is possible when the Internet-based management point trusts the forest in which the user account resides.
Software deployment to users unless the Internet-based management point can authenticate the user in AD DS by using Windows authentication (Kerberos authentication or Windows NT LAN Manager). This is possible when the Internet-based management point trusts the forest in which the user account resides.
An alternative to Internet-based client management is to use DirectAccess, a feature supported for clients running the Enterprise editions of Windows 7, Windows 8, and Windows 8.1 operating systems. DirectAccess enables clients on the Internet to access internal network resources through an always-on, computer-authenticated virtual private network (VPN). DirectAccess has prerequisites, including a requirement that the computers be domain joined and that you deploy a DirectAccess server. A further alternative is to manage Internet-based clients by using Intune.
More Info: Internet-Based Client Management
You can learn more about Internet-based client management at http://blogs.technet.com/b/configurationmgr/archive/2013/12/11/a-closer-look-at-internet-based-client-management-in-configmgr-2012.aspx.
Mac OS X computers
System Center 2012 Configuration Manager Service Pack 1 (SP1) introduced support for Mac OS X computers. Configuration Manager supports the following versions of the Mac operating systems:
![]() Mac OS X 10.6 (Snow Leopard)
Mac OS X 10.6 (Snow Leopard)
![]() Mac OS X 10.7 (Lion)
Mac OS X 10.7 (Lion)
![]() Mac OS X 10.8 (Mountain Lion)
Mac OS X 10.8 (Mountain Lion)
![]() Mac OS X 10.9 (System Center R2 Configuration Manager only)
Mac OS X 10.9 (System Center R2 Configuration Manager only)
Mac OS X computers are limited to the following Configuration Manager features:
![]() Hardware inventory You can use the hardware inventory data collected from Mac OS X computers in the same way as data collected from Windows-based computers; that is, you can use it to create collections, reports, and queries. You also can use the Configuration Manager console feature Resource Explorer to view hardware inventory data for Mac OS X computers.
Hardware inventory You can use the hardware inventory data collected from Mac OS X computers in the same way as data collected from Windows-based computers; that is, you can use it to create collections, reports, and queries. You also can use the Configuration Manager console feature Resource Explorer to view hardware inventory data for Mac OS X computers.
![]() Software deployment You can use Configuration Manager to deploy software that is packaged in the following formats to Mac OS X computers:
Software deployment You can use Configuration Manager to deploy software that is packaged in the following formats to Mac OS X computers:
![]() Mac OS Installer Package (.pkg)
Mac OS Installer Package (.pkg)
![]() Mac OS X Application (.app)
Mac OS X Application (.app)
![]() Apple Disk Image (.dmg)
Apple Disk Image (.dmg)
![]() Meta Package File (.mpkg)
Meta Package File (.mpkg)
![]() Compliance settings Configuration Manager supports the use of Mac OS X Preference settings (.plist files) to enforce the configuration of different elements on Mac OS X computers, or shell scripts to monitor and remediate settings.
Compliance settings Configuration Manager supports the use of Mac OS X Preference settings (.plist files) to enforce the configuration of different elements on Mac OS X computers, or shell scripts to monitor and remediate settings.
Configuration Manager client software installation and management for Mac OS X computers requires the use of public key infrastructure (PKI) certificates. The Configuration Manager client software for Mac OS X computers always performs certificate revocation checking, and you cannot disable this functionality. If a Mac OS X computer is unable to perform the check, it will not connect to the Configuration Manager site systems.
Mac OS X computers communicate with Configuration Manager site systems as if they were Internet-based clients. This means that all communication happens by using HTTPS. You must configure management points and distribution points to support Mac OS X computers.
To configure a management point and a distribution point to support Mac OS X computers, perform the following procedure:
1. In the Configuration Manager console, click Administration.
2. In the Administration workspace, expand Site Configuration and then click Servers And Site System Roles.
3. Select the computer that has the management point role assigned. In the details pane, right-click Management Point and then click Properties.
4. In the Management Point Properties dialog box, under Client connections, click HTTPS.
5. Select the Allow Mobile Devices And Mac Computers To Use This Management Point check box and then click OK.
6. Select the computer that has the distribution point role assigned. In the details pane, right-click Distribution Point and then click Properties.
7. In the Distribution Point Properties dialog box, under Specify How Client Computers Communicate With This Distribution Point, select HTTPS.
8. Under Create A Self-Signed Certificate Or Import A PKI Client Certificate, select Import Certificate and then click Browse.
9. Browse to the web server certificate that was created previously for the distribution point and then click OK.
More Info: Managing Mac OS X
You can learn more about managing Mac OS X with Configuration Manager at http://blogs.technet.com/b/pauljones/archive/2013/06/02/managing-mac-os-x-with-system-center-2012-configuration-manager.aspx.
Linux and UNIX computers
System Center 2012 Configuration Manager SP1 introduced support for computers running the Linux or UNIX computer system. The following versions of Linux and UNIX are supported:
![]() Oracle Linux 5 and 6
Oracle Linux 5 and 6
![]() Red Hat Enterprise Linux 4, 5, and 6
Red Hat Enterprise Linux 4, 5, and 6
![]() Solaris 9, 10, and 11
Solaris 9, 10, and 11
![]() SUSE Linux Enterprise Server 9, 10, and 11
SUSE Linux Enterprise Server 9, 10, and 11
![]() Debian 5 and 6
Debian 5 and 6
![]() CentOS-5.0 and CentOS 6
CentOS-5.0 and CentOS 6
![]() Ubuntu 12.4 LTS and 10.4 LTS
Ubuntu 12.4 LTS and 10.4 LTS
![]() IBM AIX 5.3, 6.1, and 7.1
IBM AIX 5.3, 6.1, and 7.1
![]() HP-UX 11i v2 and 11i v3
HP-UX 11i v2 and 11i v3
Configuration Manager supports the following features on Linux-based and UNIX-based computers:
![]() Hardware inventory You can use hardware inventory data collected from Linux and UNIX computers in the same way as data collected from Windows-based computers; that is, you can use it to create collections, reports, and queries. You also can use Resource Explorer to view hardware inventory data for Linux-based and UNIX-based computers.
Hardware inventory You can use hardware inventory data collected from Linux and UNIX computers in the same way as data collected from Windows-based computers; that is, you can use it to create collections, reports, and queries. You also can use Resource Explorer to view hardware inventory data for Linux-based and UNIX-based computers.
![]() Software deployment You can use Configuration Manager to deploy software to Linux-based and UNIX-based computers by using packages and programs. Using Configuration Manager for deploying software on Linux-based and UNIX-based computers does not support any kind of user interaction.
Software deployment You can use Configuration Manager to deploy software to Linux-based and UNIX-based computers by using packages and programs. Using Configuration Manager for deploying software on Linux-based and UNIX-based computers does not support any kind of user interaction.
Linux-based and UNIX-based computers are also workgroup-based clients and, therefore, have the same prerequisites and limitations of workgroup-based computers. Furthermore, the Configuration Manager client software for Linux and UNIX does not support Server Message Block (SMB) communication, forcing all communication with distribution points to happen over HTTP or HTTPS.
To configure a distribution point to support Linux-based and UNIX-based computers, perform the following steps:
1. In the Configuration Manager console, click Administration.
2. In the Administration workspace, expand Site Configuration and then click Servers And Site System Roles.
3. Select the computer that has the distribution point role assigned. In the details pane, right-click Distribution Point and then click Properties.
4. In the Distribution Point Properties dialog box, under Specify How Client Computers Communicate With This Distribution Point, select either HTTP or HTTPS.
5. If you selected HTTPS in step 4, under Create A Self-Signed Certificate Or Import A PKI Client Certificate, select Import Certificate, click Browse, find a web server certificate that you created previously for the distribution point, and then click OK.
More Info: UNIX and Linux Support
You can learn more about UNIX and Linux support at http://blogs.msdn.com/b/steverac/archive/2013/06/27/unix-and-linux-support-in-configmgr-2012-sp1.aspx.
Client installation
To deploy the components of the Configuration Manager client software efficiently to potential resources, you need to decide which deployment method to use. Consider the benefits of each installation method and decide which method suits your environment best. The client deployment methods are as follows:
![]() Client push installation This method pushes the software for the Configuration Manager client software to client computers. You can automate this deployment method so that client installation occurs on systems assigned to the site, or you can manually initiate a client push installation to any discovered system supported for client installation.
Client push installation This method pushes the software for the Configuration Manager client software to client computers. You can automate this deployment method so that client installation occurs on systems assigned to the site, or you can manually initiate a client push installation to any discovered system supported for client installation.
![]() Group Policy installation This method uses Group Policy to publish or assign the Configuration Manager client software to computers when the Group Policy Object (GPO) updates on the computer.
Group Policy installation This method uses Group Policy to publish or assign the Configuration Manager client software to computers when the Group Policy Object (GPO) updates on the computer.
![]() Software update point installation Use this method to install the Configuration Manager client software installation program (CCMSetup.exe) as a software update to a software update point. This is useful if Windows Server Update Services (WSUS) is in use in the environment, particularly if you have Windows Firewall enabled and not configured to support other installation methods.
Software update point installation Use this method to install the Configuration Manager client software installation program (CCMSetup.exe) as a software update to a software update point. This is useful if Windows Server Update Services (WSUS) is in use in the environment, particularly if you have Windows Firewall enabled and not configured to support other installation methods.
![]() Manual installation In this method, you manually initiate the Configuration Manager client software installation on computers by using CCMSetup.exe. If AD DS contains published information from Configuration Manager, and if you run CCMSetup.exe without any command-line parameters, the client installation process will retrieve the published client installation parameters from AD DS.
Manual installation In this method, you manually initiate the Configuration Manager client software installation on computers by using CCMSetup.exe. If AD DS contains published information from Configuration Manager, and if you run CCMSetup.exe without any command-line parameters, the client installation process will retrieve the published client installation parameters from AD DS.
![]() Logon script installation This method uses CCMSetup.exe in a logon script to trigger the client installation. This method ensures that the Configuration Manager client software is installed on all computers to which the user has local administrator permissions and that are members of the domain in which the policy that applies the logon script is configured.
Logon script installation This method uses CCMSetup.exe in a logon script to trigger the client installation. This method ensures that the Configuration Manager client software is installed on all computers to which the user has local administrator permissions and that are members of the domain in which the policy that applies the logon script is configured.
![]() Upgrade installation (software deployment) Use this method to upgrade existing client software on computers to newer Configuration Manager versions.
Upgrade installation (software deployment) Use this method to upgrade existing client software on computers to newer Configuration Manager versions.
![]() Operating system deployment When using operating system deployment to deploy a new operating system or to upgrade an existing one, you can include the Configuration Manager client software as part of the operating system deployment process.
Operating system deployment When using operating system deployment to deploy a new operating system or to upgrade an existing one, you can include the Configuration Manager client software as part of the operating system deployment process.
![]() Computer imaging Use this method to preinstall the Configuration Manager client software on a master image computer that will be used to build your enterprise’s computers.
Computer imaging Use this method to preinstall the Configuration Manager client software on a master image computer that will be used to build your enterprise’s computers.
Depending on the client installation method you use, the complexity of configuration can vary significantly. However, all the installation methods use the same files and complete the installation in essentially the same way. The installation process for the Configuration Manager client software for Windows-based clients uses the following files:
![]() CCMSetup.exe
CCMSetup.exe
![]() Client.msi
Client.msi
![]() CCMSetup.msi
CCMSetup.msi
CCMSetup.exe
CCMSetup.exe generally begins the client installation process and runs in all client installation methods. CCMSetup performs the following actions:
![]() Determines the location from which to download client prerequisites and installation files. If you start CCMSetup without command-line options, and if you have extended the AD DS schema for Configuration Manager, the setup process reads the client installation properties from AD DS to find an appropriate management point. If you have not extended the Active Directory schema, CCMSetup searches Domain Name System (DNS) or Windows Internet Naming Service (WINS) for a management point to contact. Alternatively, you can specify a management point by providing the /mp:<ComputerName> switch or a specific Universal Naming Convention (UNC) location by using the /source:<path> switch.
Determines the location from which to download client prerequisites and installation files. If you start CCMSetup without command-line options, and if you have extended the AD DS schema for Configuration Manager, the setup process reads the client installation properties from AD DS to find an appropriate management point. If you have not extended the Active Directory schema, CCMSetup searches Domain Name System (DNS) or Windows Internet Naming Service (WINS) for a management point to contact. Alternatively, you can specify a management point by providing the /mp:<ComputerName> switch or a specific Universal Naming Convention (UNC) location by using the /source:<path> switch.
![]() Downloads and installs client prerequisite files. Files include the client.msi file and all prerequisite software necessary for install.
Downloads and installs client prerequisite files. Files include the client.msi file and all prerequisite software necessary for install.
CCMSetup copies all the files it needs to the %systemroot%\CCMSetup\Logs folder and creates the Ccmsetup.log file in the same location. Numerous switches are available for modifying the behavior of CCMSetup.exe.
Client.msi
After CCMSetup.exe installs the required prerequisites on the intended client, CCMSetup invokes Client.msi by using MSIExec, a Windows Installer file. MSIExec then installs the client on the system. Client.msi creates the client.msi.log file in the %systemroot%\CCMSetup folder.
You can modify the Client.msi installation behavior by providing specific properties on the CCMSetup.exe command line. Alternatively, you can specify the properties on the Installation Properties tab of the Client Push Installation Properties dialog box. These settings publish to AD DS, and several installation methods use them.
CCMSetup.msi
You also can use GPOs to deploy the Configuration Manager client software. GPOs use the CCMSetup.msi file to initiate the installation process. This file is located in the <installation directory>\bin\i386 folder on the Configuration Manager site server.
More Info: Client Installation Options
You can learn more about Configuration Manager client installation options at http://technet.microsoft.com/en-us/library/gg699356.aspx.
Deploying to Mac OS X computers
Because Configuration Manager treats computers running the Mac OS X operating system as Internet-based computers, all communication with the management point and distribution point must happen by using HTTPS. Before deploying the client, you must configure the Configuration Manager environment to support the Mac OS X computers. To ensure that your environment supports Mac OS X computers, perform the following procedure:
1. Deploy certificates and configure the client certificate template for Mac OS X computers:
A. Deploy a web server certificate to the computers that will run the following site system roles:
![]() Management Point
Management Point
![]() Distribution Point
Distribution Point
![]() Enrollment Point
Enrollment Point
![]() Enrollment Proxy Point
Enrollment Proxy Point
B. Deploy a client authentication certificate to the computers running the following site system roles:
![]() Management Point
Management Point
![]() Distribution Point
Distribution Point
C. Configure the client certificate template in the CA to allow Read And Enroll permission to the account that will be used to enroll the certificate on the Mac OS X computers.
2. Configure the following Configuration Manager site system roles that Mac OS X computers use:
A. Management Point. Configure the following settings:
![]() HTTPS Communication
HTTPS Communication
![]() Allow Client Connections From The Internet
Allow Client Connections From The Internet
![]() Allow Mobile Devices And Mac Computers To Use The Management Point
Allow Mobile Devices And Mac Computers To Use The Management Point
B. Distribution Point. Configure the following settings:
![]() HTTPS Communication
HTTPS Communication
![]() Allow Client Connections From The Internet
Allow Client Connections From The Internet
C. Install an enrollment point and an enrollment proxy point.
3. Configure Default Client Settings to support Mac OS X computers:
A. Set Allow Users To Enroll Mobile Devices And Mac Computers to Yes.
B. Create a new profile to assign clients to a Configuration Manager site by using a CA and the certification template that you changed in step 1.
After you configure the environment correctly to support Mac OS X computers, you can download and install the Configuration Manager client software on existing Mac OS X computers. To install the client on Mac OS X computers, perform the following procedure:
1. Download and extract the client source files for Mac OS X clients. You do this by downloading the ConfigmgrMacClient.msi file from the Microsoft Download Center to a Windows-based computer and then running the ConfigmgrMacClient.msi file to extract the Mac client package, named Macclient.dmg. Copy the Macclient.dmg file to the Mac OS X computer on which you want to install the client and run the file to extract its contents to a local disk.
2. Install the client on the Mac OS X computer and enroll it as a client. You do this by running the following commands:
sudo ./ccmsetup
sudo ./CMEnroll –s <enrollment_proxy_server_name> -ignorecertchainvalidation -u
<'username'>
3. Restart the Mac OS X computer.
In organizations that use System Center 2012 R2 Configuration Manager only, the Enrollment Wizard starts after you install the client on the computer running Mac OS X. It enables you to enroll the computer by specifying domain credentials and the name of the enrollment proxy point server.
More Info: Install Mac OS X Client
You can learn more about installing the Mac OS X client at http://technet.microsoft.com/en-us/library/jj591553.aspx.
Deploying to Linux-based and UNIX-based computers
Cumulative update 1 for System Center 2012 Configuration Manager SP1 and later provides a universal installer that you can use to deploy the Configuration Manager client to any supported version of Linux or UNIX. Prior to the cumulative update 1 for System Center 2012 Configuration Manager SP1, each Linux or UNIX version had its own install package that had to be downloaded and installed on the client computer to make it a Configuration Manager client.
To install the client by using the universal installer, perform the following procedure:
1. Copy the install script and the client installation (.tar) file to the Linux-based or UNIX-based computer. The name of the .tar file will be Ccm-universal-x86.<build>.tar or ccm-universal-x64.<build>.tar, where x86 is for use on 32-bit clients, x64 is for use on 64-bits, and build represents the build number for the installer.
2. On the Linux-based or UNIX-based computer, run the following command:
./install –mp <FQDN of management point> -sitecode <site_code> ccm-universal-<x86
or x64>.<build>.tar
3. Review the contents of Scxcm.log in the /V/Opt/Microsoft folder to confirm that the installation occurred.
More Info: Installing the Client on Linux and UNIX Computers
You can learn more about installing the client on Linux and UNIX computers at http://technet.microsoft.com/en-us/library/jj573939.aspx.
Extending the schema
Although it is not mandatory, extending the AD DS schema and publishing Configuration Manager information in AD DS helps simplify the client deployment process and site management. When you extend the AD DS schema and publish Configuration Manager information in AD DS, this simplifies the client installation process by storing Configuration Manager– related information in Active Directory, which enables clients to retrieve the data during installation. You can use AD DS publishing with any installation method on domain-joined Windows clients to enable automatic site assignment. AD DS publishing also enables you to provide the client with the name of the management point with which to communicate, in addition to other information.
Configuration Manager publishes the following client installation properties to AD DS:
![]() The default management point used to download content for the client installation.
The default management point used to download content for the client installation.
![]() The Configuration Manager site code.
The Configuration Manager site code.
![]() The HTTP port used for client communication.
The HTTP port used for client communication.
![]() The HTTPS port used for client communication.
The HTTPS port used for client communication.
![]() A setting indicating that the client must communicate using HTTPS.
A setting indicating that the client must communicate using HTTPS.
![]() The fallback status point. If the site has multiple fallback status points, the first to be installed is the only one published to AD DS.
The fallback status point. If the site has multiple fallback status points, the first to be installed is the only one published to AD DS.
![]() The selection criteria for certificate selection. This might be required when the client has more than one valid certificate.Installation properties specified on the Installation Properties tab of the Client Push Installation Properties dialog box.
The selection criteria for certificate selection. This might be required when the client has more than one valid certificate.Installation properties specified on the Installation Properties tab of the Client Push Installation Properties dialog box.
![]() Automatic updates when alterations are made to default ports for site systems.
Automatic updates when alterations are made to default ports for site systems.
Only a member of the Schema Admins group, or an enterprise administrator who has sufficient permissions to modify the schema, can extend it. If you extend the schema prior to installation, Configuration Manager configures the site automatically to publish site information during installation. At the end of the installation, the Configuration Manager site server publishes site information to AD DS. However, you can extend the schema after installing Configuration Manager and configure the site manually to publish to AD DS.
You can extend the Active Directory schema by using either of the following methods:
![]() The LDIFDE command-line tool (Ldifde.exe) and the ConfigMgr_ad_schema.ldf file. You must modify the ConfigMgr_ad_schema.ldf file to include the name of the Active Directory forest prior to modifying the schema.
The LDIFDE command-line tool (Ldifde.exe) and the ConfigMgr_ad_schema.ldf file. You must modify the ConfigMgr_ad_schema.ldf file to include the name of the Active Directory forest prior to modifying the schema.
![]() The ExtADSch.exe tool. ExtADsch.exe creates a log file in the root of the system drive called Extadsch.log.
The ExtADSch.exe tool. ExtADsch.exe creates a log file in the root of the system drive called Extadsch.log.
You can find both the executable files in either the \SMSSETUP\BIN\i386 folder or the \SMSSETUP\BIN\x64 folder on the installation media. ExtADSch.exe is a standalone executable file; however, the ConfigMgr_ad_schema.ldf file requires you to run the following command to use it.
ldifde –i –f ConfigMgr_ad_schema.ldf –v –j <location to store log file>
More Info: Extend Schema
You can learn more about extending the schema at http://technet.microsoft.com/en-us/library/gg712272.aspx.
Site systems used in client deployment
The process of installing the Configuration Manager client software uses several site systems. In addition to the site systems that play a direct role in client deployment, several site systems might participate in client deployment.
The following site system roles are involved directly with installing client devices:
![]() Management point
Management point
![]() Fallback status point
Fallback status point
![]() Software update point
Software update point
![]() Enrollment point and enrollment proxy point
Enrollment point and enrollment proxy point
![]() Distribution point
Distribution point
![]() Reporting services point
Reporting services point
Management point
A management point is usually required to complete the client installation process because the client might need to contact a distribution point to download necessary prerequisite software. The installation process is complete when the client has registered with a primary site, receives its initial policy assignment, and then retrieves the policy. This initial policy sets the components to their desired state. In most installation methods, the client downloads CCMSetup.exe and Client.msi files from a management point and any other prerequisites from a distribution point. After the installation program is complete, the client contacts the management point to register itself and obtains its site assignment. It then reports the state of the installation. If the client cannot contact the management point, all the client components will show as Installed instead of Enabled or Disabled.
The client software follows several methods to locate the management point and uses the methods in the following order:
1. Setup parameters As part of the installation command, you can specify a management point.
2. AD DS The client software will query AD DS for an appropriate management point.
3. Domain Name System (DNS) The client will search for a service (SRV) resource record type for a management point. To find the right SRV record in DNS, you must configure clients with their site code.
4. Windows Internet Naming Service (WINS) A management point will update its WINS record with appropriate information automatically. If a client is a WINS client, WINS is the last resource the client software uses to locate a management point.
Automatic client assignment is determined using boundaries that are members of a boundary group, where that boundary group has automatic assignment enabled. In previous versions of Configuration Manager, automatic site assignment would fail, and Configuration Manager would not manage clients if they fell outside all boundaries. With System Center 2012 Configuration Manager, you can configure a fallback site for client assignment at the hierarchy level. If you install a client that is outside any of the configured boundary groups, the automatic site assignment process will use this site, and the installation process will complete successfully.
Fallback status point
The fallback status point is an optional site system that you can use during the client installation process. A fallback status point monitors client deployment and identifies unmanaged clients because unmanaged clients cannot communicate with a management point. The fall-back status point relies on unauthenticated connections from clients over HTTP. You should use a dedicated system for the fallback status point so that if a site system is not available, the client can contact the fallback status point to report the error. You cannot configure the fallback status point as a highly available role.
The reports that the Configuration Manager client software produces use data sent by clients through the fallback status point. Mobile devices that are enrolled by Configuration Manager and mobile devices that are managed by using the Exchange Server connector do not use a fallback status point.
Software update point
You can install the Configuration Manager client software by using software update point push installations. If you choose to use this method, configure the software update point on a WSUS server to install the client when computers scan for applicable software updates.
Enrollment point and enrollment proxy point
Mobile devices use the enrollment point for enrollment with Configuration Manager, and the enrollment proxy point manages the enrollment requests from the mobile devices. These site system roles are not required if you plan to manage mobile devices by using only the Exchange connector.
Distribution point
Most client installation methods copy the necessary installation files from a management point. In certain circumstances, the installation process uses a distribution point instead. When you deploy an operating system by using the Configuration Manager Operating System Deployment feature, the task sequence action that installs the client software downloads the operating system from a distribution point. If you use Pre-Boot Execution Environment (PXE) boot in conjunction with operating system deployment, Configuration Manager installs the Windows Deployment Services PXE server on the distribution point.
Reporting services point
In addition to the required and optional roles that client installation uses directly, you might find it useful to install a reporting services point. This will enable you to view any reports about the client installation process or the status of the clients.
More Info: Site System Roles Used For Client Deployment
You can learn more about site system roles used for client deployment at http://technet.microsoft.com/en-au/library/gg681976.aspx.
Client assignment
You cannot manage a client until it is assigned to a site. After client installation is complete, the client is assigned automatically to a site so that the client can be managed. You can assign client devices to any primary site; however, you cannot assign client devices either to a secondary site or to a central administration site.
Most clients will reside within site-assignment boundary groups and will be assigned automatically to a site based on the boundary definition. You can configure a fallback site for clients that might be outside the configured boundaries of any site. You also can assign a client to a site through a client.msi property either directly or through the Installation Properties tab of the Client Push Installation Properties dialog box.
If you have not extended AD DS, you have two options for site assignment. You can specify a site code by using the Client.msi property SMSSITECODE=site code, or you can assign a group of clients to a site manually by using Group Policy. You also can choose to install a client offline instead of installing it immediately to a site.
If the client automatic assignment fails, the client software remains installed, but Configuration Manager will not manage it until you assign the client to a site. If the client is unassigned, it will attempt to perform automatic assignment each time the CCMExec process starts.
After the client is assigned to a site, it remains assigned to that site even if the client changes its IP address and roams to another site. A client can move to another site only when an administrator reassigns it manually.
More Info: Client Site Assignment
You can learn more about client site assignment at http://technet.microsoft.com/en-us/library/gg682060.aspx.
Client settings
You can configure client software in the Administration workspace in the Client Settings node of the Configuration Manager console. You configure the Default Client Settings object with settings that will apply to all clients. The Default Client Settings object always has a priority of 10,000, and you cannot change this setting. Therefore, the Default Client Settings object is applied first, and custom settings will override the default settings when you assign them to collections. You can configure custom settings for any of the categories or a combination of categories found in the Default Client Settings object.
Client settings are hierarchy-wide settings that, by default, affect all clients in the hierarchy. Because Configuration Manager considers these settings as global data, modifications that you make to Default Client Settings at one site replicate to all other primary sites in the hierarchy and to the central administration site.
Custom settings
In the Administration workspace, in the Client Settings node of the Configuration Manager console, you can create custom client settings. The Default Client Settings object applies to all clients, and if you want to configure a setting for all devices or users, you can modify the Default Client Settings option. However, if you need to change some settings for a specific collection of users or devices, you will need to create a custom setting.
Reasons for creating custom client settings include:
![]() Creating a custom client setting for a group of systems on which software metering should be disabled.
Creating a custom client setting for a group of systems on which software metering should be disabled.
![]() Creating a custom client setting for a group of systems to increase or decrease the frequency of status messages.
Creating a custom client setting for a group of systems to increase or decrease the frequency of status messages.
![]() Creating a custom client setting for a group of servers to prevent them from configuring an affinity with a user automatically.
Creating a custom client setting for a group of servers to prevent them from configuring an affinity with a user automatically.
After creating a custom client setting object, deploy it to one or more collections to apply it. To deploy a custom client setting to a collection, right-click the custom client setting and then click Deploy. You can then choose the collections to which you want to deploy the custom client setting.
Note that you cannot configure certain settings through a custom client device policy. Table 5-1 lists the settings that you can configure only in the Default Client Settings object.
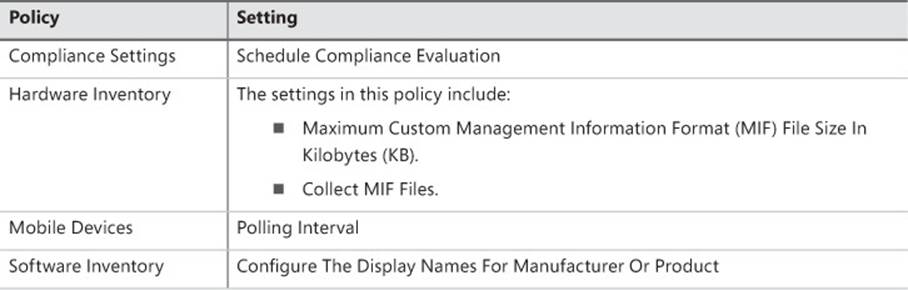
TABLE 5-1 Default client settings policy settings
Multiple client device settings
Assigning multiple client device settings to a collection enables you to create different client device-settings objects for separate Configuration Manager feature sets. For example, you might have a client device-settings object for software deployment and another client device-settings object for hardware inventory.
All client setting objects are assigned a priority level. Configuration Manager processes each setting object in order, with lower numerical values overriding higher numerical values. When you create a new custom client setting, it receives the next available priority. When you delete a custom client settings object, the priority on all client settings that have a higher priority reduces by one. For example, consider when you have four custom client settings: ClientSetting1, ClientSetting2, ClientSetting3, and ClientSetting4. ClientSetting1 was created first and has a priority of one. ClientSetting2 was created second and has a priority of two. ClientSetting3 has a priority of three, and ClientSetting4 has a priority of four. If you delete ClientSetting2, ClientSetting1 will retain its priority of one, the priority of ClientSetting3 will be adjusted to two, and the priority of ClientSetting4 will be adjusted to three.
You can use the Configuration Manager console’s Resultant Client Settings functionality to determine the resultant client settings when multiple client settings are applied. In the Assets And Compliance workspace, right-click the device, user, or user collection for which you want to see resultant client settings, click Client Settings, and then click Resultant Client Settings.
More Info: Client Settings
You can learn more about client settings at http://technet.microsoft.com/en-au/library/gg682109.aspx.
 Exam Tip
Exam Tip
Remember how settings are resolved when multiple client settings apply through collection membership.
 Thought experiment: Configuration Manager client deployment
Thought experiment: Configuration Manager client deployment
You are planning the deployment of the Configuration Manager client at Contoso. As part of the planning process, you need to determine how to handle computers that are not joined to the domain and computers that are running the Mac OS X operating system. With this information in mind, answer the following questions:
1. What steps do you need to take to install the Configuration Manager client on nondomain-joined Windows-based computers?
2. Which site system roles require web server certificates when you use Configuration Manager to manage computers running Mac OS X?
3. Which site system roles require client authentication certificates when you use Configuration Manager to manage computers running Mac OS X?
Objective summary
![]() On computers running Windows operating systems, the UI for the Configuration Manager client consists of two parts: the Configuration Manager control panel and Software Center.
On computers running Windows operating systems, the UI for the Configuration Manager client consists of two parts: the Configuration Manager control panel and Software Center.
![]() Users can set the preferences for software delivery or remote control by using Software Center.
Users can set the preferences for software delivery or remote control by using Software Center.
![]() You must manually install the Configuration Manager client software on workgroup-based computers and configure a network access account to allow access to resources in the site server domain for clients that are not domain members.
You must manually install the Configuration Manager client software on workgroup-based computers and configure a network access account to allow access to resources in the site server domain for clients that are not domain members.
![]() To configure a client for Internet-based client management, obtain a computer certificate from a trusted certification authority (CA). You must configure the client with the Internet fully qualified domain name (FQDN) of the management point.
To configure a client for Internet-based client management, obtain a computer certificate from a trusted certification authority (CA). You must configure the client with the Internet fully qualified domain name (FQDN) of the management point.
![]() Extending the schema simplifies the client installation process by storing Configuration Manager–related information in Active Directory.
Extending the schema simplifies the client installation process by storing Configuration Manager–related information in Active Directory.
![]() You can assign client devices to any primary site but cannot assign client devices either to a secondary site or to a central administration site.
You can assign client devices to any primary site but cannot assign client devices either to a secondary site or to a central administration site.
![]() The Default Client Settings object is applied first, and custom settings will override the default settings when you assign them to collections.
The Default Client Settings object is applied first, and custom settings will override the default settings when you assign them to collections.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. Of which domain security group must a user account be a member if it will be used to extend the schema with information about Configuration Manager?
A. Domain Admins
B. Schema Admins
C. Enterprise Admins
D. Protected Users
2. You are working with a Configuration Manager deployment in which the Active Directory schema has not been extended. Which of the following methods can you use to assign a site code to clients? (Choose two. Each correct answer provides a complete solution.)
A. Use the Client.msi property SMSSITECODE=site code.
B. Configure an answers.txt file.
C. Configure Group Policy.
D. Configure an unattend.xml file.
3. What is the priority of the Default Client Settings object?
A. 1
B. 100
C. 1,000
D. 10,000
4. Which of the following settings cannot be configured through a custom client device policy? (Choose three. Each correct answer provides a complete solution.)
A. Software Inventory: Configure The Display Names For Manufacturer Or Product
B. Compliance Settings: Schedule Compliance Evaluation
C. Mobile Devices: Polling Interval
D. Cloud Services: Allow Access To Cloud Distribution Point
Objective 5.2: Manage collections
You can use collections to manage and organize groups of computers, mobile devices, users, and security groups throughout your Configuration Manager environment. You also can use collections to help accomplish many Configuration Manager management tasks. In this section, you learn about the various types of collections, the methods to create collections, and the process of monitoring collections.
This section covers the following topics:
![]() Collections
Collections
![]() Collection rules
Collection rules
![]() Maintenance windows
Maintenance windows
![]() Power management
Power management
![]() Monitoring collections
Monitoring collections
Collections
Collections represent resource groups that consist of devices such as computers and mobile devices or users and user groups from all of the hierarchy’s sites. You can use collections to accomplish several management and configuration tasks, including:
![]() Organizing resources into manageable units to create an organized and logical structure of resources.
Organizing resources into manageable units to create an organized and logical structure of resources.
![]() Organizing collections of target resources to perform Configuration Manager operations on multiple resources simultaneously. Configuration Manager operations can include operations such as application deployments and installation of software updates.
Organizing collections of target resources to perform Configuration Manager operations on multiple resources simultaneously. Configuration Manager operations can include operations such as application deployments and installation of software updates.
![]() Targeting groups of computers with specific configurations, such as:
Targeting groups of computers with specific configurations, such as:
![]() Client settings.
Client settings.
![]() Power-management settings.
Power-management settings.
![]() Maintenance-window settings.
Maintenance-window settings.
![]() Organizing computers based on their compliance status, with a specific baseline.
Organizing computers based on their compliance status, with a specific baseline.
![]() Integrating with role-based administration to specify collections that a specific administrative user can access.
Integrating with role-based administration to specify collections that a specific administrative user can access.
You can view or modify collections by using the User Collections and Device Collections nodes found in the Assets And Compliance workspace. User collections can contain Users and User Groups. Device collections can contain devices managed by Configuration Manager.
Configuration Manager includes seven predefined user and device collections as described in Table 5-2.
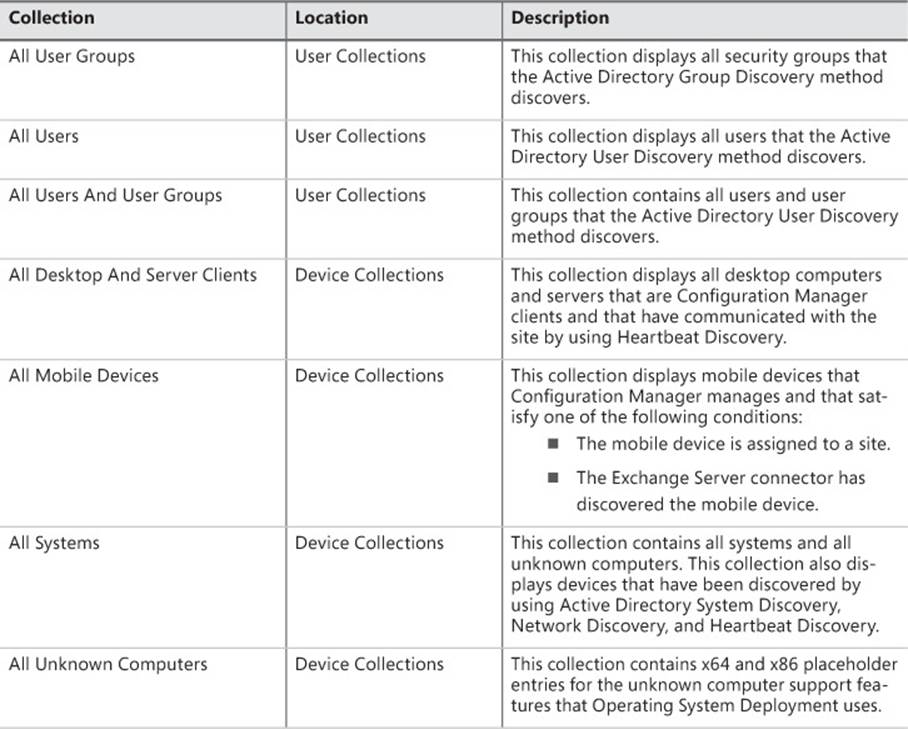
TABLE 5-2 Predefined collections
More Info: Configuration Manager Collections
You can learn more about Configuration Manager collections at http://technet.microsoft.com/en-us/library/gg682177.aspx.
Collection rules
You can use rules to manage the membership of Configuration Manager collections. Table 5-3 describes the different rule types you can use to manage the membership of Configuration Manager collections.

TABLE 5-3 Collection rule types
When you create a new collection, you specify a base collection called a limiting collection. The limiting collection becomes a foundation for resources that can be added to the new collection. You can use limiting collections along with role-based access control to ensure that delegated administrators can see only objects that are relevant for their administrative tasks.
Configuration Manager reevaluates all of a collection’s rules on a specified schedule. You can also trigger on-demand reevaluation of collection membership. The default schedule to evaluate the membership of custom collections is once every seven days.
Configuration Manager supports incremental evaluation of members of a collection. This feature runs separately from the full update cycle, and it scans periodically for new resources or resources that have changed since the previous collection evaluation. If you enable incremental evaluation, incremental collection member evaluation runs every five minutes. Figure 5-5 shows enabling incremental updates during collection creation.
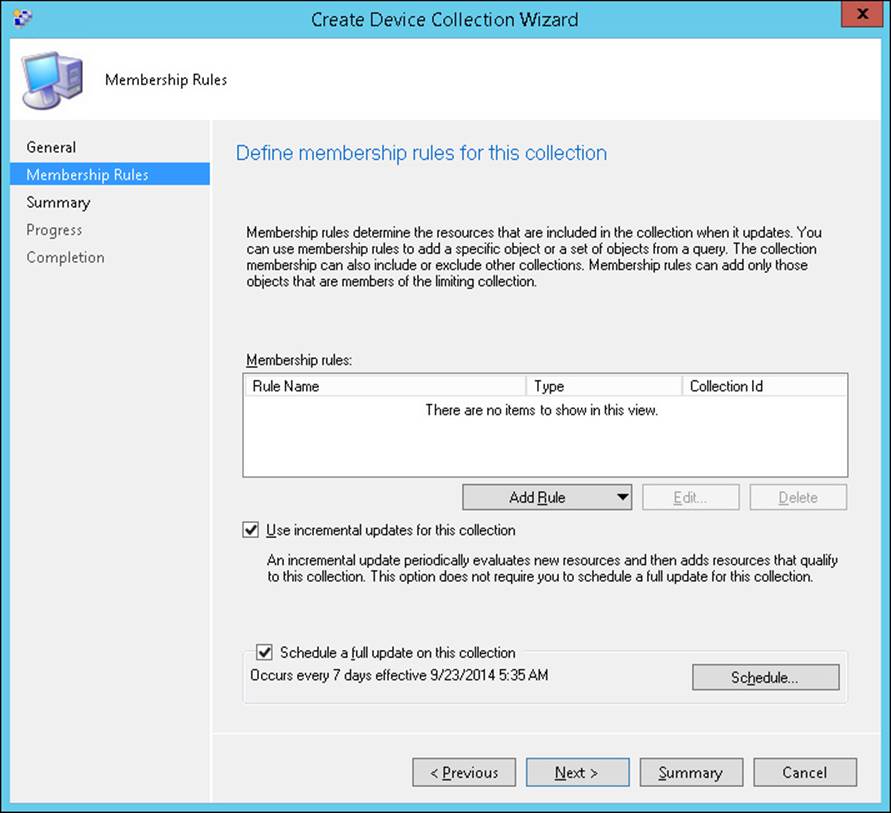
FIGURE 5-5 Membership Rules page of the Create Device Collection Wizard, showing options for incremental updates and scheduling full updates
Maintenance windows
Maintenance windows enable you to configure a specific period during which required deployments, software-update installations, configuration-item remediation, and task sequences can run on a client. Assigning a specific start time for a program deployment does not ensure that the program runs at that time. However, you can configure maintenance windows to ensure that the assigned program installations and the restarts that Configuration Manager triggers do not occur at inconvenient or undesirable times.
For example, you might configure a required application deployment that installs a large application and then restarts the computer. To avoid running this during normal business hours, you might configure the deployment to run at 2:00 A.M. on a specific day. However, an executive might have taken a portable computer on a business trip before you deployed the program. When the executive returns to the office after the scheduled start time, the portable computer would start to install the application a few minutes after the computer connects to the office network. This could affect the system performance of the computer and, after installation, force a restart at the very time the executive wants to check an important email message or make a presentation. To avoid this scenario, configure an overnight maintenance window for a collection of which the executive’s computer is a member. This ensures that the installation and restarts do not occur during normal business hours.
You can configure maintenance windows by opening the Properties dialog box of a specific collection and then selecting the Maintenance Windows tab as shown in Figure 5-6.
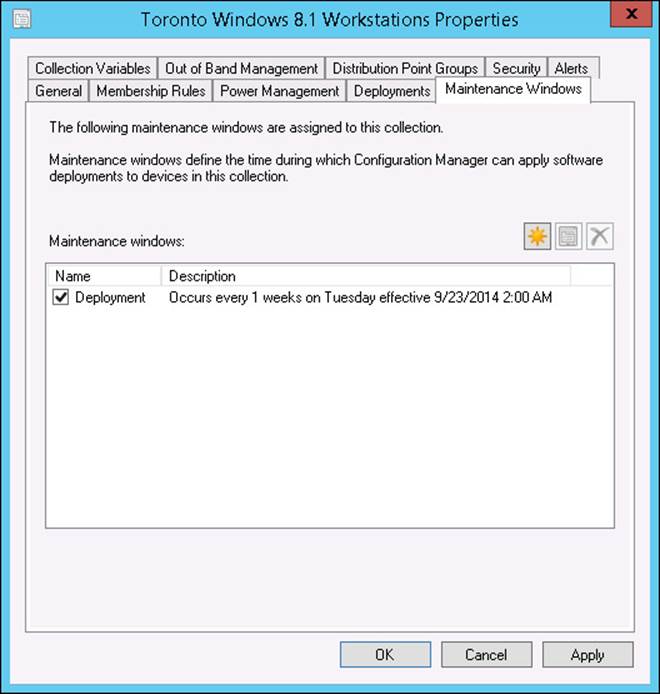
FIGURE 5-6 Maintenance Windows tab
Maintenance windows do not affect the following configuration management processes:
![]() Policy download and evaluation
Policy download and evaluation
![]() Data collection and reporting of inventory and metering data
Data collection and reporting of inventory and metering data
![]() Remediation for Network Access Protection (NAP)
Remediation for Network Access Protection (NAP)
![]() Transmission of Wake On LAN wake-up packets
Transmission of Wake On LAN wake-up packets
![]() Out-of-band management
Out-of-band management
![]() Application deployment content downloads
Application deployment content downloads
![]() Deployments, software-update deployments, configuration-item remediation, or task sequences that are optional or specifically configured to ignore maintenance windows
Deployments, software-update deployments, configuration-item remediation, or task sequences that are optional or specifically configured to ignore maintenance windows
![]() User-initiated deployments
User-initiated deployments
Changes to maintenance windows that occur during a maintenance window do not take effect while the current maintenance window is in effect.
A required deployment does not run during a maintenance window that is shorter or has less time remaining than the deployed software’s configured maximum run time. For example, a deployment that has a run time of 45 minutes does not run if only 30 minutes remain in the maintenance window. In addition, if you configure the maximum run time of deployed software as unknown, the software might run past the end of a maintenance window.
A client computer can be a member of more than one collection with maintenance windows. When a client computer is a member of two or more collections with maintenance windows, that computer’s maintenance windows will be a combination of the defined collections’ maintenance windows.
For example, PC1 is a member of Collection A, Collection B, and Collection C. The maintenance windows for each of the collections are as follows:
![]() Collection A’s maintenance window is from 5 P.M. to 8 P.M.
Collection A’s maintenance window is from 5 P.M. to 8 P.M.
![]() Collection B’s maintenance window is from 4 A.M. to 7 A.M.
Collection B’s maintenance window is from 4 A.M. to 7 A.M.
![]() Collection C’s maintenance window is from 7 P.M. to 11 P.M.
Collection C’s maintenance window is from 7 P.M. to 11 P.M.
Therefore, PC1’s maintenance windows will be from 4 A.M. to 7 A.M. and from 5 P.M. to 11 P.M. When using maintenance windows, consider the following best practices:
![]() When you use maintenance windows to restrict system changes, you should create collections specifically for this purpose instead of using the default collections or other custom collections.
When you use maintenance windows to restrict system changes, you should create collections specifically for this purpose instead of using the default collections or other custom collections.
![]() When you configure maintenance windows, include a description of the maintenance window in the collection’s name for easy identification.
When you configure maintenance windows, include a description of the maintenance window in the collection’s name for easy identification.
More Info: Maintenance Windows
You can learn more about maintenance windows at http://technet.microsoft.com/en-us/library/hh508762.aspx.
Power management
Use Configuration Manager to configure and monitor standard Windows power options throughout the managed environment. Configuration Manager power management enables you to apply a power plan to managed computers and monitor power consumption to minimize costs and provide environmental benefits for your organization.
Table 5-4 describes the external dependency for implementing power management by using Configuration Manager.
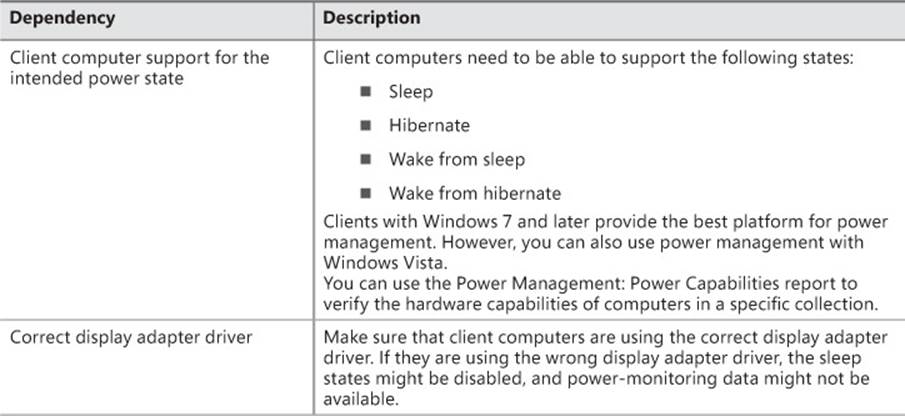
TABLE 5-4 Power management dependencies
Table 5-5 lists the prerequisites for implementing power management by using Configuration Manager.
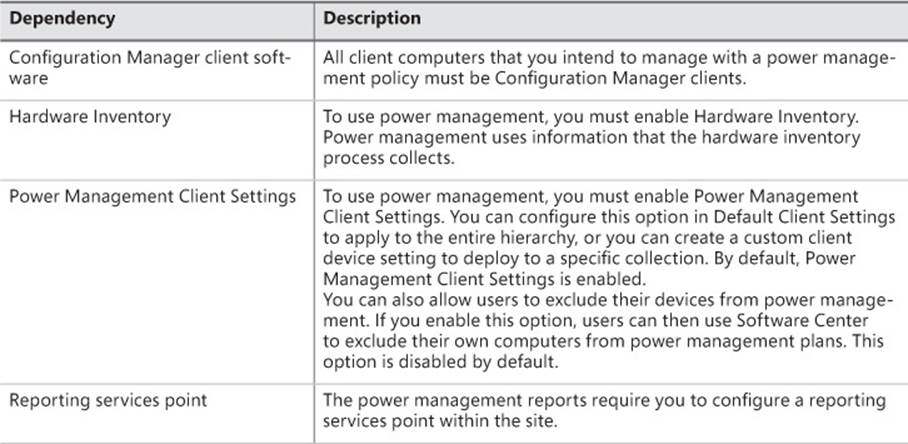
TABLE 5-5 Power management prerequisites
To implement an enterprise-wide power management solution, you must:
1. Monitor the current power state and usage.
Your first step to effective power management is to collect data and analyze reports that outline current power settings and consumption. Power management uses hardware inventory to collect data. You can view the hardware inventory by using reports and graphs to determine optimal power management settings for your environment. During your monitoring stage, you can use a number of reports that provide information related to current power settings on computers in a collection; power management capabilities of a computer; and current computer, monitor, and user activity over a period of time. You can also use the reports to provide information related to current power consumption for a specified collection over a period of time, current power consumption costs for a specified collection over a period of time, and computers not capable of power management.
2. Plan power management plans.
After monitoring and collecting baseline data, you can use the gathered information to decide on the types of power management settings you want to deploy. It is important to determine specific settings that you want to enable or disable to meet your organizational requirements.
3. Apply power management policies.
After carefully planning your power management settings, you can configure and apply the required plan settings to a specific collection. Depending on the settings required, you can specify default power plans, or you can create your own customized power plan.
4. Check compliance and reports.
As the power management settings take effect, you can track ongoing power consumption and settings on all managed computers and troubleshoot any problems. Various reports provide details about power usage, costs, and environmental impact.
Power management plan settings
When you are ready to apply power management settings, you can choose to implement a default power plan or customize your own plan for both peak and nonpeak time intervals. Default power plans include:
![]() Balanced.
Balanced.
![]() High Performance.
High Performance.
![]() Power Saver.
Power Saver.
Depending on the power plan that you use and the peak or nonpeak configuration, various power management settings might or might not be applied. You cannot modify default plans. However, if you choose to create a customized power plan, you can modify and apply your own settings to match specific requirements. Figure 5-7 shows the Balanced power plan.
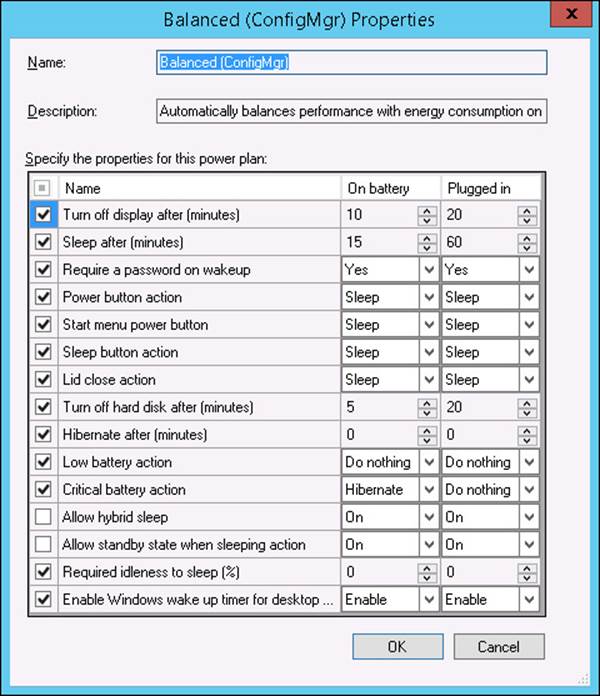
FIGURE 5-7 Power plan settings
Table 5-6 describes the available power management settings.
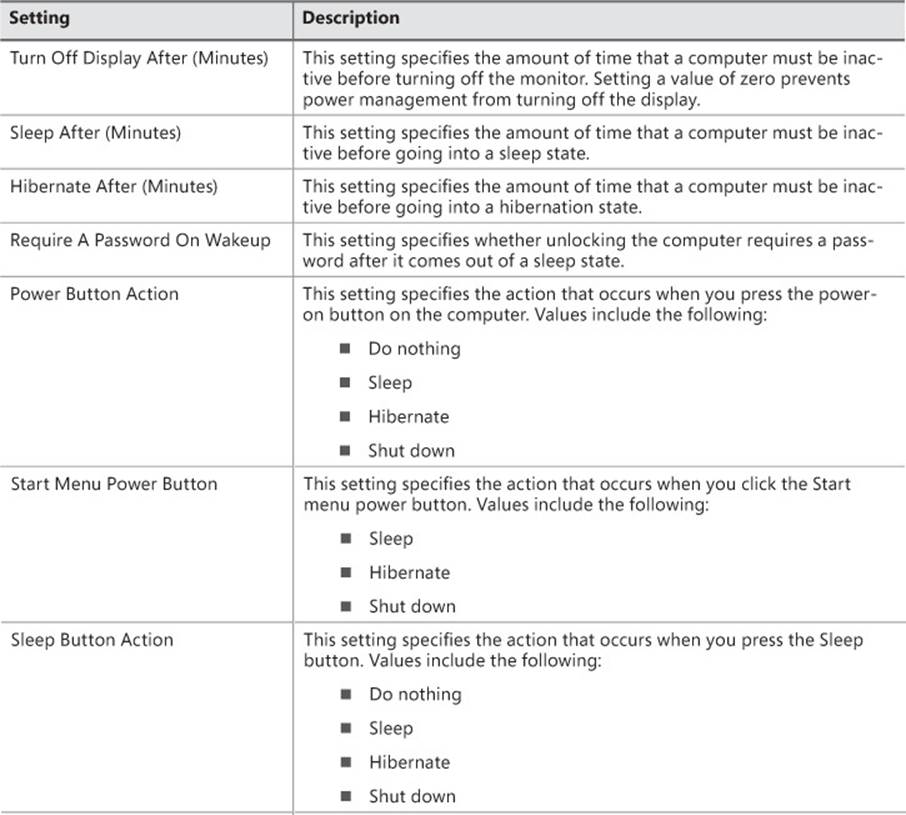
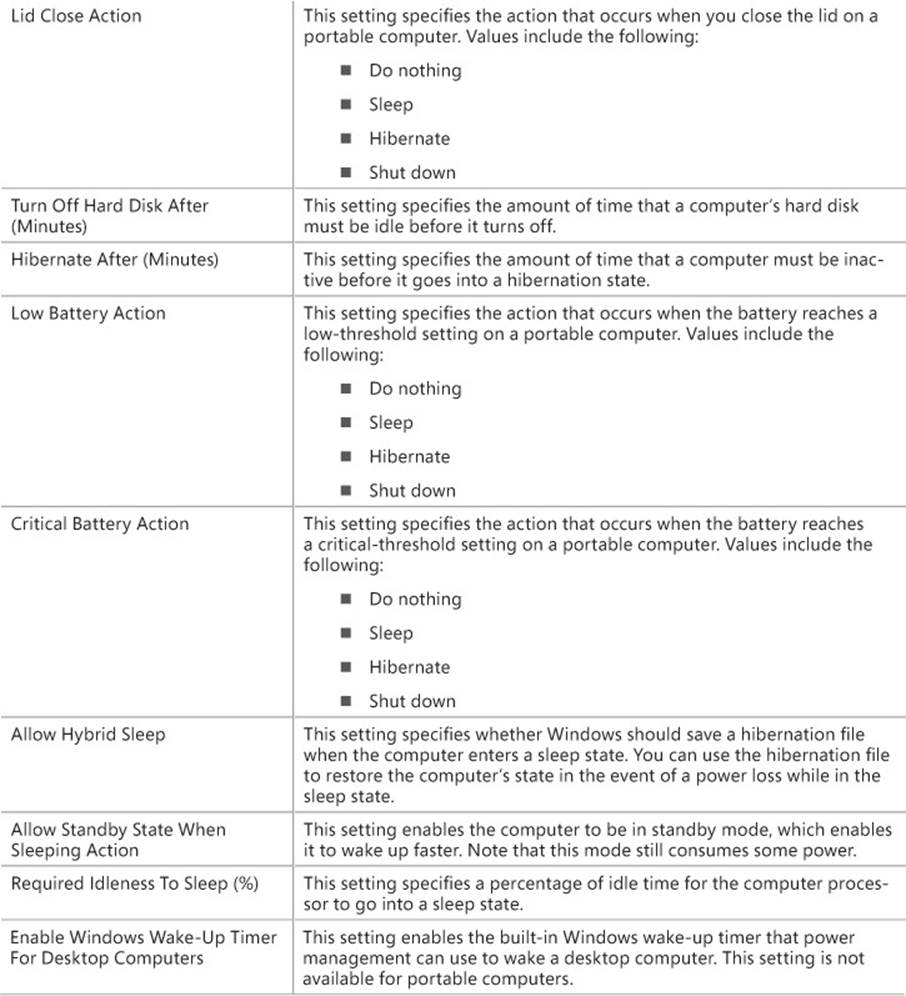
TABLE 5-6 Power management settings
You can configure each of the power management settings twice: once for on-battery systems and once for plugged-in systems. To apply a power plan to a collection of computers, perform the following procedure:
1. Right-click the collection that is to have the power management policy and then click Properties.
2. Click the Power Management tab and then select Specify Power Management Settings For This Collection.
Figure 5-8 shows this for the Toronto Windows 8.1 Workstations collection.
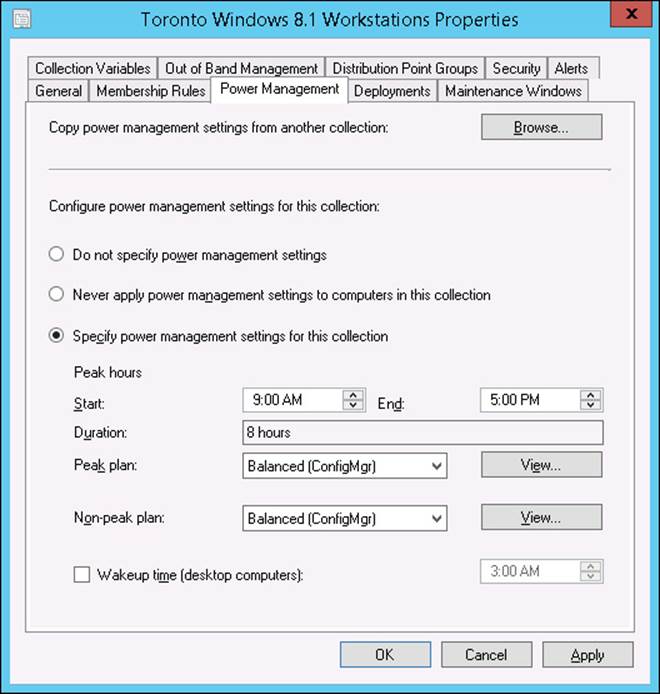
FIGURE 5-8 Power Management tab
3. Specify a power plan for both peak and nonpeak times.
If you are creating a customized power plan, the Edit button is available for editing specific power management settings.
Power management reports
You can view and analyze various reports related to power consumption, environmental impact, and power management settings in your Configuration Manager environment. The site database retains power management data used by daily reports for 31 days. The site database retains data used by monthly reports for 13 months. You might consider saving or exporting the results from critical reports if you want to be able to perform long-term analysis.
To view power management reports, perform the following procedure:
1. In the Monitoring workspace, expand the Reporting node and then expand the Reports node.
2. Click the Power Management folder.
3. In the results pane, shown in Figure 5-9, select the report to view and then, on the ribbon, click Run.
FIGURE 5-9 Power management reports
Depending on the report, you might need to provide additional criteria to view the data results.
More Info: Power Management
You can learn more about power management at http://technet.microsoft.com/en-us/library/gg699392.aspx.
Monitoring collections
Because several Configuration Manager features are based on collections, you should know how to monitor the collections. You might want to know when the collections are created, modified, or deleted. You also might want to view status messages that pertain to members of a specific collection. You can monitor collection-based tasks by using the following methods:
![]() Component Status The Component Status node, under the System Status node in the Monitoring workspace, contains the SMS_COLLECTION_EVALUATOR component. This component provides status information related to collections.
Component Status The Component Status node, under the System Status node in the Monitoring workspace, contains the SMS_COLLECTION_EVALUATOR component. This component provides status information related to collections.
![]() Log files The Colleval.log file is associated with the SMS_COLLECTION_EVALUATOR component and provides detailed status information related to collection evaluation and management. This log file is located in the c:\Program Files\Microsoft Configuration Manager\Logs folder.
Log files The Colleval.log file is associated with the SMS_COLLECTION_EVALUATOR component and provides detailed status information related to collection evaluation and management. This log file is located in the c:\Program Files\Microsoft Configuration Manager\Logs folder.
![]() Status Message Queries The Status Message Queries node, under the System node in the Monitoring workspace, provides the following status-message queries to assist in collection monitoring:
Status Message Queries The Status Message Queries node, under the System node in the Monitoring workspace, provides the following status-message queries to assist in collection monitoring:
![]() All Status Messages For A Specific Collection At A Specific Site
All Status Messages For A Specific Collection At A Specific Site
![]() Collection Member Resources Manually Deleted
Collection Member Resources Manually Deleted
![]() Collections Created, Modified, And Deleted
Collections Created, Modified, And Deleted
![]() Reports The Reports node includes several reports that pertain to collection-based tasks. The reports include:
Reports The Reports node includes several reports that pertain to collection-based tasks. The reports include:
![]() All Collections.
All Collections.
![]() All Resources In A Specific Collection.
All Resources In A Specific Collection.
![]() All Package And Program Deployments To A Specified Collection.
All Package And Program Deployments To A Specified Collection.
![]() Inventory Classes Assigned To A Specific Collection.
Inventory Classes Assigned To A Specific Collection.
![]() Issues by incidence detail for a specified collection.
Issues by incidence detail for a specified collection.
To view all reports that pertain to collections, you can perform a search on the Reports node for Collections. Figure 5-10 shows the results of this search.
FIGURE 5-10 Collection-related reports
 Exam Tip
Exam Tip
Remember the default evaluation schedule period for rule-based collections.
 Thought experiment: Power management at Tailspin Toys
Thought experiment: Power management at Tailspin Toys
You are the Configuration Manager administrator at Tailspin Toys. You are setting up Configuration Manager to manage the power settings for the fleet of laptop computers used at Tailspin Toys. With this information in mind, answer the following questions:
1. Which power management setting would you configure to ensure that the computer shuts down when the battery reaches the critical-threshold setting?
2. Which power management setting would you configure to ensure that a portable computer is shut down when the lid is closed?
Objective summary
![]() Collections represent resource groups that consist of devices such as computers and mobile devices or users and user groups from all of the hierarchy’s sites.
Collections represent resource groups that consist of devices such as computers and mobile devices or users and user groups from all of the hierarchy’s sites.
![]() You can use a direct rule to add a specific resource to a collection. If you add a resource to a collection by using a direct rule, the resource will remain in the collection until manually removed.
You can use a direct rule to add a specific resource to a collection. If you add a resource to a collection by using a direct rule, the resource will remain in the collection until manually removed.
![]() You can use a query rule to add members to a collection based on their attributes.
You can use a query rule to add members to a collection based on their attributes.
![]() The default schedule to evaluate the membership of custom collections is once every seven days; incremental collection member evaluation runs every five minutes.
The default schedule to evaluate the membership of custom collections is once every seven days; incremental collection member evaluation runs every five minutes.
![]() Maintenance windows enable you to configure a specific period during which required deployments, software-update installations, configuration-item remediation, and task sequences can run on a client.
Maintenance windows enable you to configure a specific period during which required deployments, software-update installations, configuration-item remediation, and task sequences can run on a client.
![]() Configuration Manager power management enables you to apply a power plan to managed computers.
Configuration Manager power management enables you to apply a power plan to managed computers.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. Which of the following can you add to a collection by using a direct membership rule? (Choose two. Each correct answer provides a complete solution.)
A. Router
B. Switch
C. Active Directory security group
D. User account
2. You have created a collection by using a query rule. You have not enabled incremental updates. How often will the membership of the collection be updated by default?
A. Once an hour
B. Once a day
C. Once every 7 days
D. Once every 10 days
3. Which of the following activities are not affected by maintenance windows? (Choose three. Each correct answer provides a complete solution.)
A. Configuration item remediation
B. User-initiated software deployment
C. Policy download and evaluation
D. Centralized software deployments
4. Which of the following client settings must be enabled if you want to use Configuration Manager to manage power settings for computers running Windows 8.1?
A. Hardware Inventory
B. Remote Tools
C. Software Inventory
D. Compliance Settings
Objective 5.3: Configure and monitor client status
System Center 2012 R2 Configuration Manager includes the Client Status feature that you can use to monitor client health and activity. The client health evaluator works outside the normal client processes to enable an administrator to discover issues with the clients, particularly issues that clients would be unable to report. This section describes how to use the Client Status feature and how to use the Configuration Manager console to monitor and evaluate client health.
This section covers the following topics:
![]() Verifying client installation
Verifying client installation
![]() Client status
Client status
![]() Client health evaluation and remediation
Client health evaluation and remediation
![]() Client health reports
Client health reports
![]() Client health alerts
Client health alerts
Verifying client installation
You can verify the Configuration Manager client software’s installation success in a number of ways, from both the server side and the client side. To verify that the Configuration Manager client software installed successfully, you can examine client log files, Control Panel in the client computer, and current information in collections and status reports.
Table 5-7 describes methods for verifying a successful client installation.
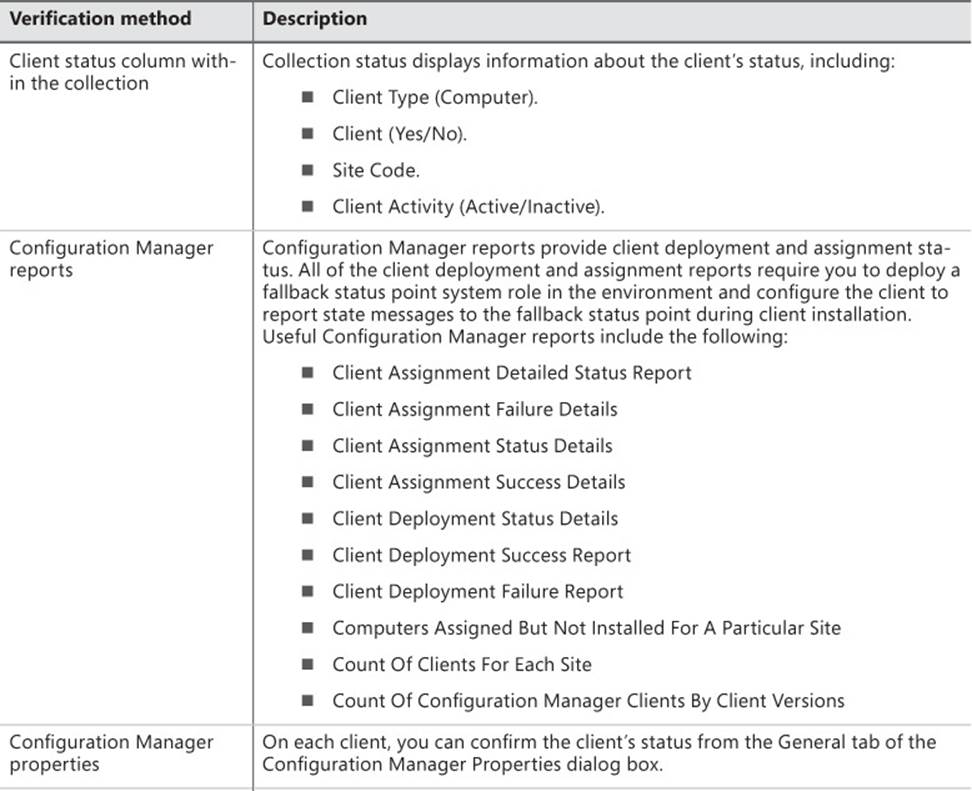
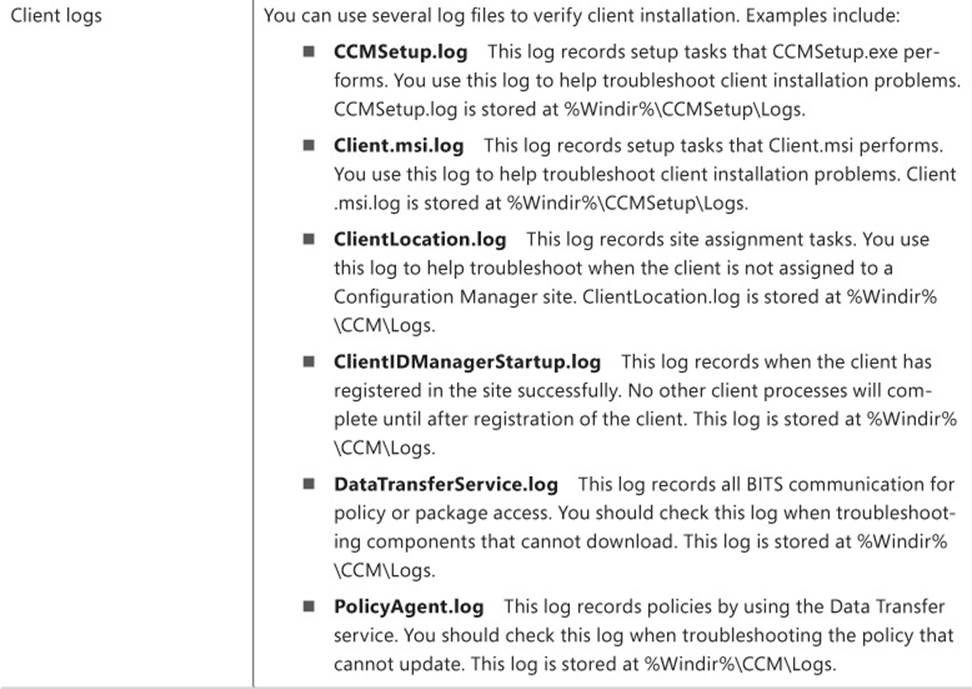
TABLE 5-7 Verifying client installation
Client status
The System Center 2012 R2 Configuration Manager client agent runs a scheduled task to evaluate its client health status. The health status of a client enables you to determine the answers to the following questions:
![]() How many clients are healthy in the hierarchy?
How many clients are healthy in the hierarchy?
![]() How many clients are inactive in the hierarchy because they have been powered off for a long time or because the Configuration Manager client agent is not installed?
How many clients are inactive in the hierarchy because they have been powered off for a long time or because the Configuration Manager client agent is not installed?
![]() What is the main cause of unhealthy clients in the hierarchy?
What is the main cause of unhealthy clients in the hierarchy?
The task runs daily between midnight and 1:00 A.M. by default. Then, the client sends the evaluation results to a management point as a status message. Similar to the initial installation process, if the client fails to send its status message to a management point, it will then send the status message to a fallback status point if one exists in your hierarchy. If you have not installed a fallback status point in your hierarchy, the site server might not receive some evaluation results. The site server summarizes the evaluation results and activities of the client’s health and then displays them in the Configuration Manager console in the Client Status folder located in the Monitoring workspace.
When you click the Client Status node, the results pane displays some statistics and the Recent Alerts section. The statistics have links showing the percentage of clients that are healthy, unhealthy, or unknown, and active or inactive. Recent Alerts shows the alerts the Client Health feature generates because of meeting defined thresholds for client health and activity.
If you click the different links, this creates a temporary node under the Devices node in the Assets And Compliance workspace, and the console changes automatically to the newly created temporary node. Temporary nodes remain in the Configuration Manager console until you remove them manually or close the console. For example, when you click the Active Clients That Failed Client Check link—which denotes the clients that failed the client health checks—a temporary node for these unhealthy clients is created and selected automatically.
More Info: Client Status
You can learn more about client status at http://technet.microsoft.com/en-us/library/hh338432.aspx.
Client health evaluation and remediation
Client Status in the Configuration Manager console receives its information from the Client Health evaluation engine running on each client. The Client Health evaluation engine is an executable file named CCMEval.exe. This engine can perform health checks by using rules and can automatically rectify some configuration problems through a process termed remediation.
CCMEval.exe is installed with the Configuration Manager client agent and runs on computers. However, it is not part of the mobile device client. When you install the Configuration Manager client agent, the install process creates a scheduled task named Configuration Manager Health Evaluation. This task runs Ccmeval.exe at a time between midnight and 1:00 A.M. The client reports the results as a state message to the client’s management point or a fallback status point if the management point is unavailable.
You can run the Configuration Manager Health Evaluation process on demand by running CCMEval.exe as required. Client health evaluation and remediation is only available to Windows-based computers. To view the client health rules that the Client Health evaluation engine is using, you can look in the <client location>\ccmeval.xml file. You can disable remediation of a client system by setting the following registry value to True: HKLM \Software\Microsoft\CCM\CCMEval\NotifyOnly.
If the computer is not running when the scheduled Configuration Manager Health Evaluation task is due to run, the task will run automatically as soon as it can, such as when you load the operating system or bring the computer out of sleep mode. Table 5-8 lists the health evaluation rules and remediation actions.
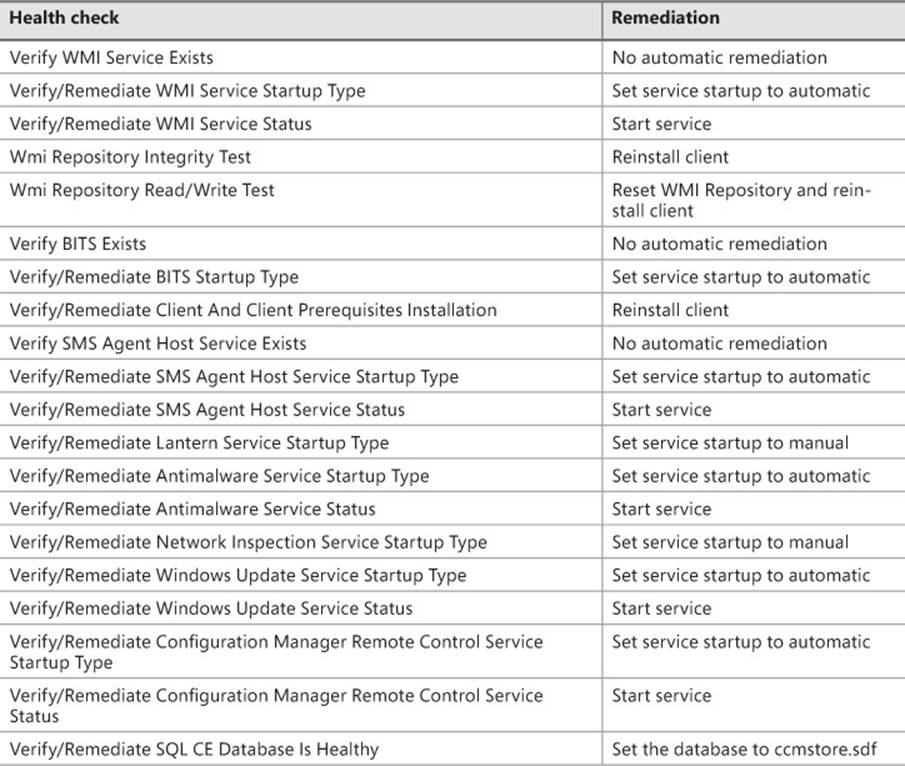
TABLE 5-8 Health evaluation rules
Client health reports
In addition to the Client Check and Client Activity information in the Configuration Manager console, you can use the Client Status reports. After you have installed and configured a reporting services point role, the Client Status reports are located in the Client Status folder in the Configuration Manager console or the ConfigMgr_<site code>\Client Status path in the reporting website.
Table 5-9 lists the available reports.
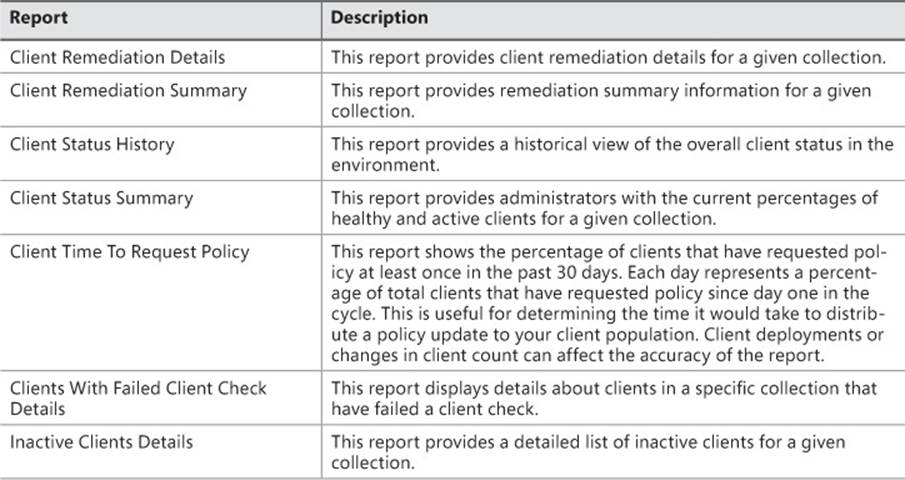
TABLE 5-9 Client health reports
Client health alerts
The Alerts feature can use data from the Client Status feature to generate alerts in the Configuration Manager console. To configure alerts for Client Status, open the Properties dialog box for any collection. On the Alerts tab, click Add. You can add the following alert conditions:
![]() Client Check Pass Or No Results For Active Clients Falls Below Threshold (%)
Client Check Pass Or No Results For Active Clients Falls Below Threshold (%)
![]() Client Remediation Success Falls Below The Threshold (%)
Client Remediation Success Falls Below The Threshold (%)
![]() Client Activity Falls Below Threshold (%)
Client Activity Falls Below Threshold (%)
After you have configured the alerts, the alerts that generate appear in the Alerts node of the Monitoring workspace and in the Client Status node. You also can subscribe to alerts to receive email notifications if you require email in addition to the in-console alert feature.
 Exam Tip
Exam Tip
Remember that not all health issues can be remediated.
 Thought experiment: Client monitoring at Contoso
Thought experiment: Client monitoring at Contoso
You are the Configuration Manager administrator at Contoso. You are concerned that a number of client computers that Configuration Manager manages at your organization are either inactive or regularly failing client health checks. With this information in mind, answer the following questions:
1. How can you determine which clients have failed client health checks?
2. How can you determine which clients in a collection are inactive?
Objective summary
![]() The System Center 2012 R2 Configuration Manager client agent runs a scheduled task to evaluate its client health status.
The System Center 2012 R2 Configuration Manager client agent runs a scheduled task to evaluate its client health status.
![]() If the client fails to send its status message to a management point, it will then send the status message to a fallback status point if one exists in your hierarchy.
If the client fails to send its status message to a management point, it will then send the status message to a fallback status point if one exists in your hierarchy.
![]() The Client Health evaluation engine is an executable file named CCMEval.exe. This engine can perform health checks by using rules and can automatically rectify some configuration problems through a process termed remediation.
The Client Health evaluation engine is an executable file named CCMEval.exe. This engine can perform health checks by using rules and can automatically rectify some configuration problems through a process termed remediation.
![]() You can run the Configuration Manager Health Evaluation process on demand by running CCMEval.exe as required. Client health evaluation and remediation is only available to Windows-based computers.
You can run the Configuration Manager Health Evaluation process on demand by running CCMEval.exe as required. Client health evaluation and remediation is only available to Windows-based computers.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. You want to run Configuration Manager Health Evaluation immediately rather than waiting for it to occur at the scheduled time. Which of the following files would you run to accomplish this task?
A. CCMEval.exe
B. CCMSetup.exe
C. CMTrace.exe
D. CCMSetup.msi
2. Which of the following health evaluation rules supports remediation?
A. Verify BITS Exists
B. Verify/Remediate Windows Update Service Status
C. Verify SMS Agent Host Service Exists
D. Verify File Exists
3. Which of the following reports would you run to view remediation details for a given collection?
A. Client Status History
B. Client Remediation Details
C. Client Status Summary
D. Inactive Clients Details
Answers
Objective 5.1
Thought experiment
1. You must install the client manually, using an account with local administrator privileges. You also must configure a network access account to allow access to resources in the site server domain for clients that are not domain members.
2. The computers running the Management Point, Distribution Point, Enrollment Point, and Enrollment Proxy Point roles require web server certificates when you want to use Configuration Manager to manage computers running Mac OS X.
3. The computers running the Management Point and Distribution Point roles require client authentication certificates when you want to use Configuration Manager to manage computers running Mac OS X.
Objective review
1. Correct answer: B
A. Incorrect: The user account used to extend the schema must be a member of the Schema Admins domain security group.
B. Correct: The user account used to extend the schema must be a member of the Schema Admins domain security group.
C. Incorrect: The user account used to extend the schema must be a member of the Schema Admins domain security group.
D. Incorrect: The user account used to extend the schema must be a member of the Schema Admins domain security group.
2. Correct answers: A and C
A. Correct: You can assign a site code to a Configuration Manager client by using the Client.msi property SMSSITECODE=site code.
B. Incorrect: You cannot assign a site code to a Configuration Manager client by using an answers.txt file.
C. Correct: You can assign a site code to a Configuration Manager client by using Group Policy.
D. Incorrect: You cannot assign a site code to a Configuration Manager client by using an unattend.xml file.
3. Correct answer: D
A. Incorrect: The Default Client Settings object has a default priority of 10,000.
B. Incorrect: The Default Client Settings object has a default priority of 10,000.
C. Incorrect: The Default Client Settings object has a default priority of 10,000.
D. Correct: The Default Client Settings object has a default priority of 10,000.
4. Correct answers: A, B, and C
A. Correct: You can cannot configure the Software Inventory: Configure The Display Names For Manufacturer Or Product setting through a custom client policy.
B. Correct: You cannot configure the Compliance Settings: Schedule Compliance Evaluation setting through a custom client policy.
C. Correct: You cannot configure the Mobile Devices: Polling Interval setting through a custom client policy.
D. Incorrect: You can configure the Cloud Services: Allow Access To Cloud Distribution Point setting through a custom client policy.
Objective 5.2
Thought experiment
1. Configure the Critical Battery Action power management setting.
2. Configure the Lid Close Action power management setting.
Objective review
1. Correct answers: C and D
A. Incorrect: You cannot add a router to a collection because a router cannot be managed by Configuration Manager.
B. Incorrect: You cannot add a switch to a collection because a switch cannot be managed by Configuration Manager.
C. Correct: You can add an Active Directory security group to a collection by using a direct membership rule.
D. Correct: You can add a user account to a collection by using a direct membership rule.
2. Correct answer: C
A. Incorrect: By default, collection membership is reevaluated once every 7 days.
B. Incorrect: By default, collection membership is reevaluated once every 7 days.
C. Correct: By default, collection membership is reevaluated once every 7 days.
D. Incorrect: By default, collection membership is reevaluated once every 7 days.
3. Correct answers: A, B, and C
A. Correct: Configuration item remediation is not affected by maintenance windows.
B. Correct: User-initiated software deployment is not affected by maintenance windows.
C. Correct: Policy download and evaluation are not affected by maintenance windows.
D. Incorrect: Although it is possible to configure a centralized software deployment specifically to ignore maintenance windows, by default, centralized software deployment only occurs during the times specified in the maintenance window.
4. Correct answer: A
A. Correct: You must enable Hardware Inventory to be able to use Configuration Manager to manage power settings for computers running Windows 8.1.
B. Incorrect: You do not need to enable Remote Tools to be able to use Configuration Manager to manage power settings for computers running Windows 8.1.
C. Incorrect: You do not need to enable Software Inventory to be able to use Configuration Manager to manage power settings for computers running Windows 8.1.
D. Incorrect: You do not need to enable Compliance Settings to be able to use Configuration Manager to manage power settings for computers running Windows 8.1.
Objective 5.3
Thought experiment
1. Run the Clients With Failed Client Check Details report.
2. Run the Inactive Clients Details report to determine which clients are no longer active in a collection.
Objective review
1. Correct answer: A
A. Correct: You run CCMEval.exe to trigger the health evaluation process.
B. Incorrect: CCMSetup.exe is used in the client deployment process.
C. Incorrect: CMTrace.exe is used to view log files.
D. Incorrect: CCMSetup.msi is used in the Configuration Manager setup process.
2. Correct answer: B
A. Incorrect: The Verify BITS Exists health check does not support automatic remediation.
B. Correct: The Verify/Remediate Windows Update Service Status health check supports automatic remediation.
C. Incorrect: The Verify SMS Agent Host Service Exists health check does not support automatic remediation.
D. Incorrect: The Verify File Exists health check does not support automatic remediation.
3. Correct answer: B
A. Incorrect: The Client Status History report provides a historical view of the overall client status in the environment.
B. Correct: You would run the Client Remediation Details report to view remediation details for a given collection.
C. Incorrect: The Client Status Summary report provides the current percentages of healthy and active clients for a given collection.
D. Incorrect: The Inactive Clients Details report provides a detailed list of inactive clients for a given collection.