Exam Ref 70-414 Implementing an Advanced Server Infrastructure (2014)
Chapter 3. Plan and implement a server virtualization infrastructure
Virtualization has grown over the years to become the primary method for server deployment in many enterprise data centers. The increased use of virtualization makes this skillset highly valuable for an administrator. This chapter looks at the exam objectives surrounding planning and implementation of server virtualization.
Objectives in this chapter:
![]() Objective 3.1: Plan and implement virtualization hosts
Objective 3.1: Plan and implement virtualization hosts
![]() Objective 3.2: Plan and implement virtual machines
Objective 3.2: Plan and implement virtual machines
![]() Objective 3.3: Plan and implement virtualization networking
Objective 3.3: Plan and implement virtualization networking
![]() Objective 3.4: Plan and implement virtualization storage
Objective 3.4: Plan and implement virtualization storage
![]() Objective 3.5: Plan and implement virtual machine movement
Objective 3.5: Plan and implement virtual machine movement
![]() Objective 3.6: Manage and maintain a server virtualization infrastructure
Objective 3.6: Manage and maintain a server virtualization infrastructure
Objective 3.1: Plan and implement virtualization hosts
The first objective for the 70-414 exam relates to basic planning and implementation for virtualization hosts, or the computers on which virtual machines will be deployed. As virtual machines provide the infrastructure necessary for many enterprises, planning and implementation of the hosts is a key aspect for success of the deployment.
This objective covers how to:
![]() Plan for and implement delegation of virtual environment (hosts, services, and VMs), including self-service capabilities
Plan for and implement delegation of virtual environment (hosts, services, and VMs), including self-service capabilities
![]() Plan and implement multi-host libraries, including equivalent objects
Plan and implement multi-host libraries, including equivalent objects
![]() Plan for and implement host resource optimization
Plan for and implement host resource optimization
![]() Integrate third-party virtualization platforms
Integrate third-party virtualization platforms
![]() Deploy Hyper-V hosts to bare metal
Deploy Hyper-V hosts to bare metal
Planning for and implementing virtual environment delegation
System Center Virtual Machine Manager (VMM) enables role-based delegation of management. In addition, VMM also has self-service capabilities that enable users to deploy virtual machines and services to private clouds, as well as create templates and change other settings. This section examines both delegation and self-service.
Delegation with VMM
VMM contains several user roles that contain the various capabilities necessary to perform certain tasks. This section examines the roles available and how to assign users to those roles.
Defining User Roles in VMM
User roles delegate administration of certain tasks within VMM. For example, you might have several host groups defined, such as a host group for developers. You can delegate administration of that host group to a development team lead so that he or she can create virtual machines when needed. User roles can be assigned with a limited scope so that actions performed by an administrator apply only to the host group or cloud for which they have permissions.
VMM defines four built-in user roles profiles. User role profiles contain various capabilities that define what a given user role can do. Table 3-1 describes the user role profiles and their capabilities in VMM.
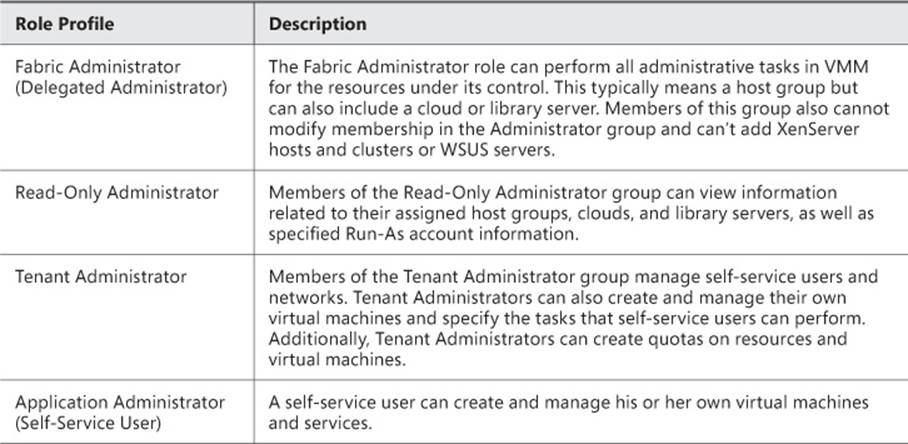
TABLE 3-1 User role profiles in VMM
Delegating Administration in VMM
Delegating administration in VMM involves either adding users to the built-in Administrator user role or creating user roles with the user role profiles covered in the previous section. As with most other user role management tasks in Windows, you can nest groups inside of the user roles in VMM. For example, you might add the Domain Admins group to the Administrator user role in VMM, thereby enabling anyone in the Domain Admins group to administer the VMM deployment.
Adding users to the Administrator user role is accomplished in the Settings workspace in VMM, by selecting the Properties of the Administrator user role. When you do so, clicking the Members tab shows the current members of the user role, from which you can add or remove as necessary. This is illustrated in Figure 3-1.
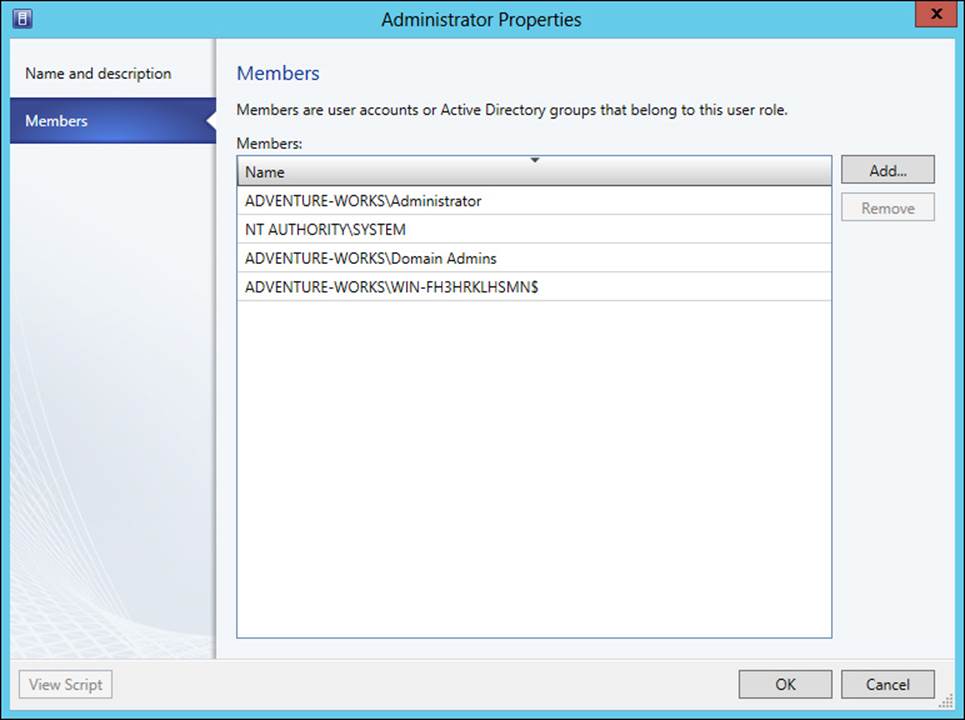
FIGURE 3-1 Viewing membership of the Administrator user role
Creating a user role is also accomplished from the Settings workspace in the VMM console. Selecting Create User Role invokes the Create User Role Wizard, which first gathers name and description information about the user role to be created, as shown in Figure 3-2.
FIGURE 3-2 Using the Create User Role Wizard to create a new user role
On the next page of the wizard, you select the user role profile to apply to the user role being created. You can choose from the profiles described in Table 3-1. This page is shown in Figure 3-3.
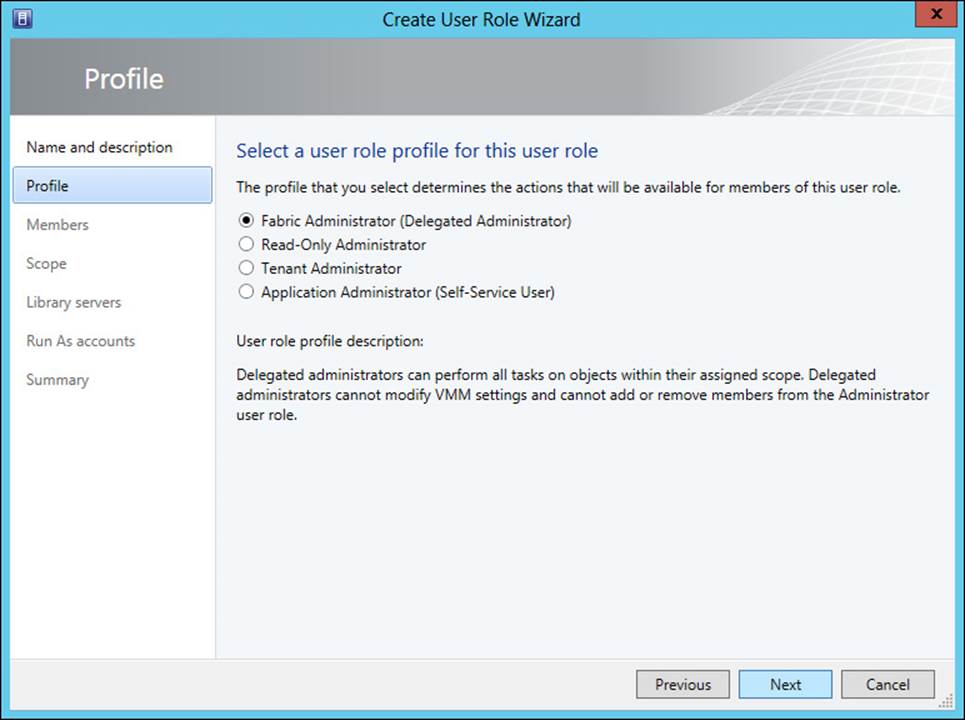
FIGURE 3-3 Selecting a user role profile
Next, membership for the user role is chosen, as shown in Figure 3-4.
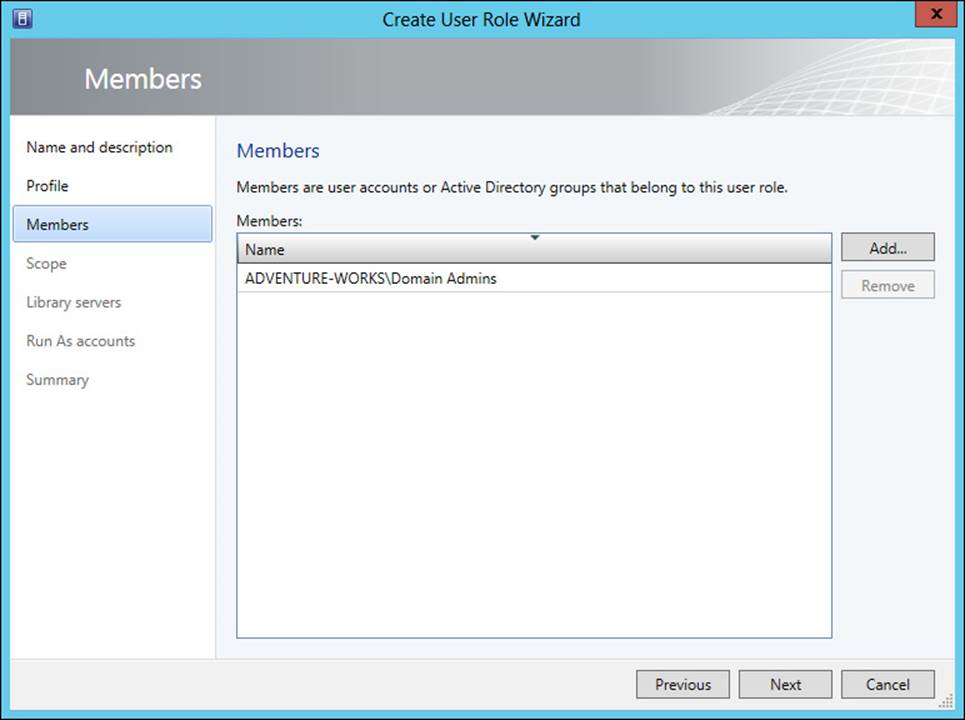
FIGURE 3-4 Configuring membership for the user role
The scope to which the user role will apply is configured in the next page of the wizard, shown in Figure 3-5.
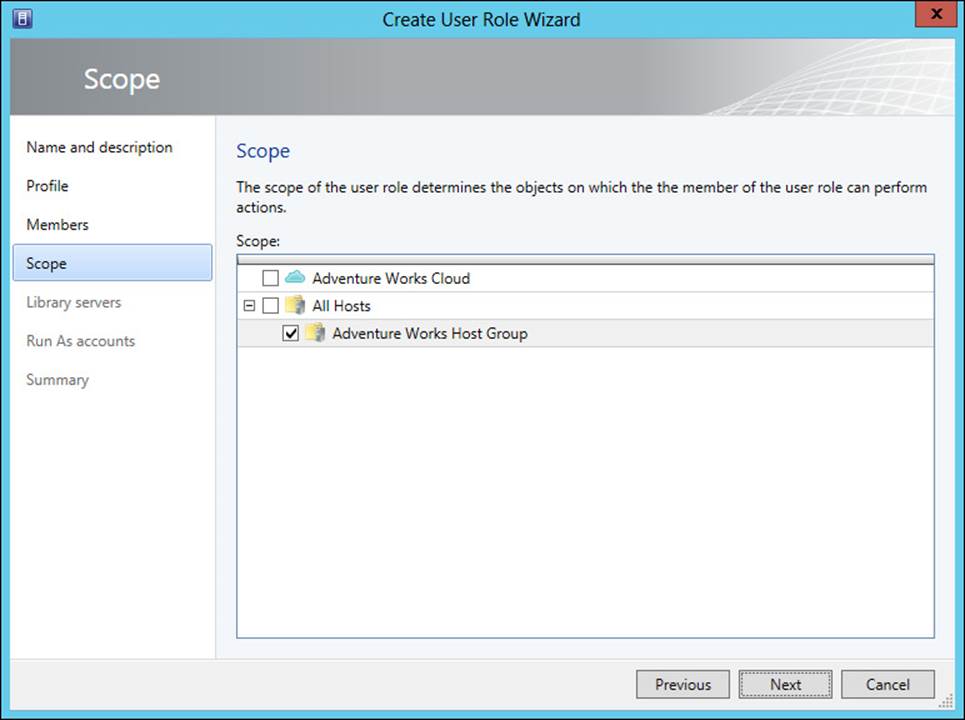
FIGURE 3-5 Configuring scope for the user role
The library servers and Run As accounts for the user role are configured next, as shown in Figure 3-6 and Figure 3-7.
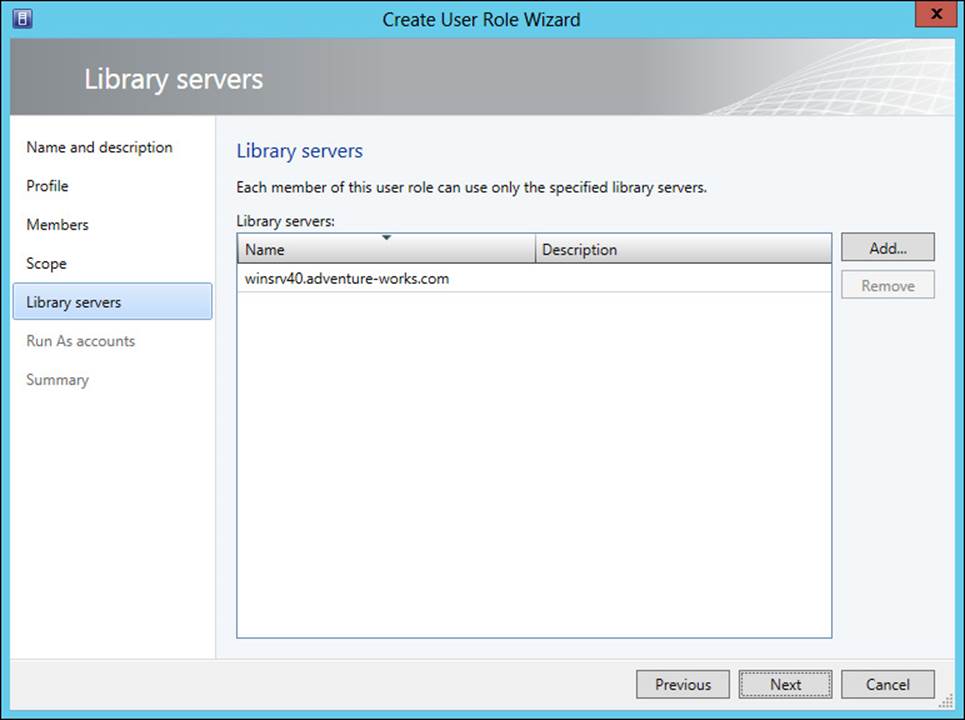
FIGURE 3-6 Configuring library servers
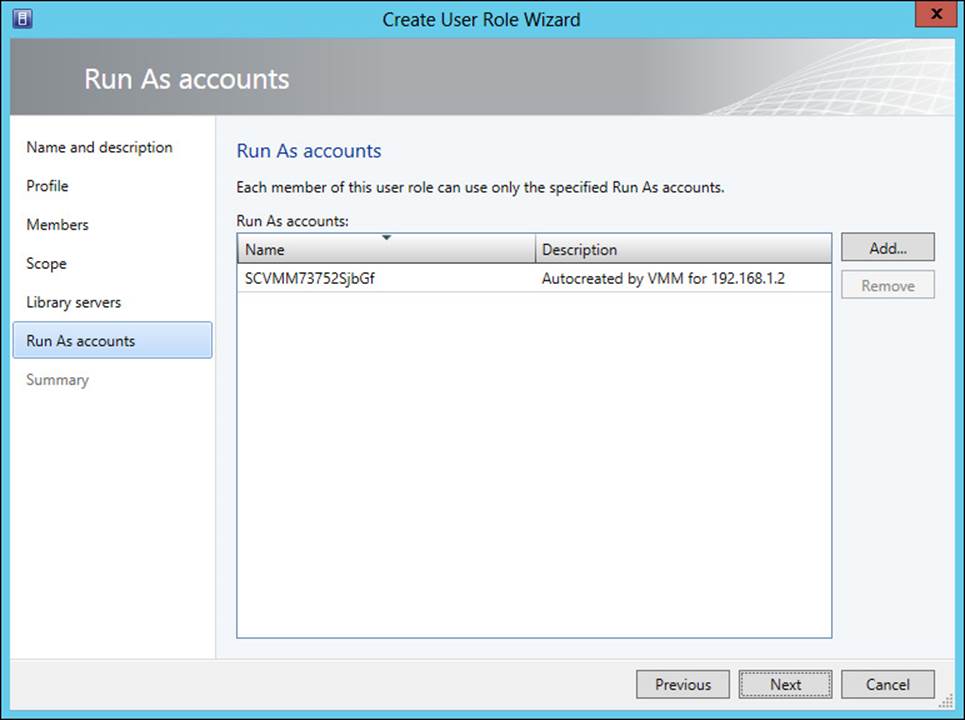
FIGURE 3-7 Configuring Run As accounts
Similar steps are used to create other user roles, with the exception of the Tenant Administrator role. The Tenant Administrator role has additional settings that can be configured, including quotas, networking, resources, and actions. Quotas can be set at the role level or at the member level, as shown in Figure 3-8.
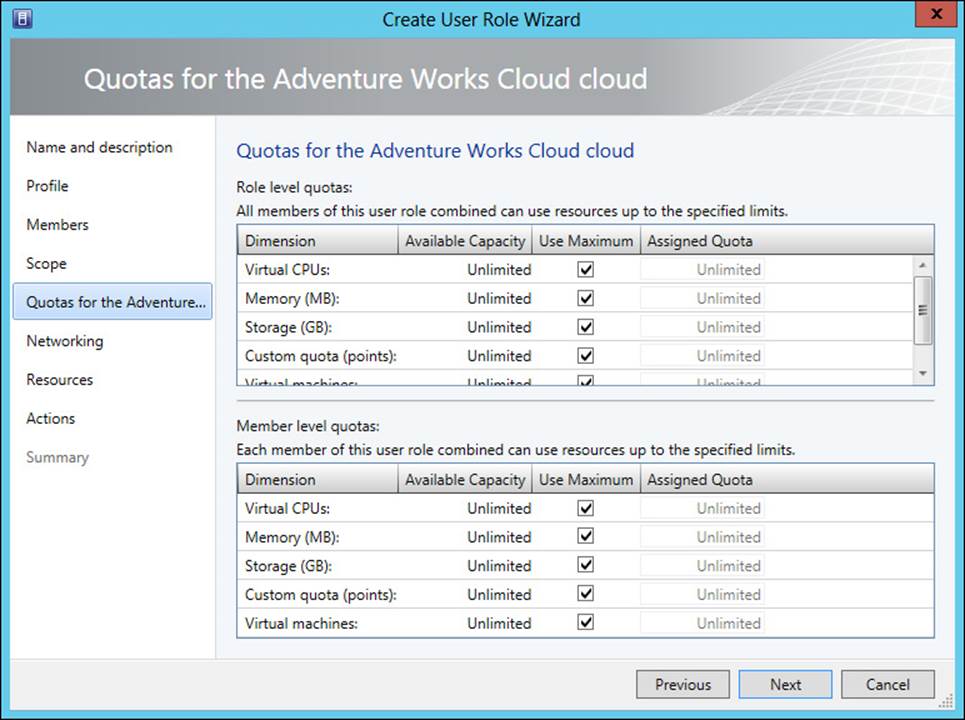
FIGURE 3-8 Setting Quotas for a Tenant Administrator user role
Permitted actions need to be specified for the Tenant Administrator and Application Administrator user roles. This is also accomplished in the Create User Role Wizard, as shown in Figure 3-9.
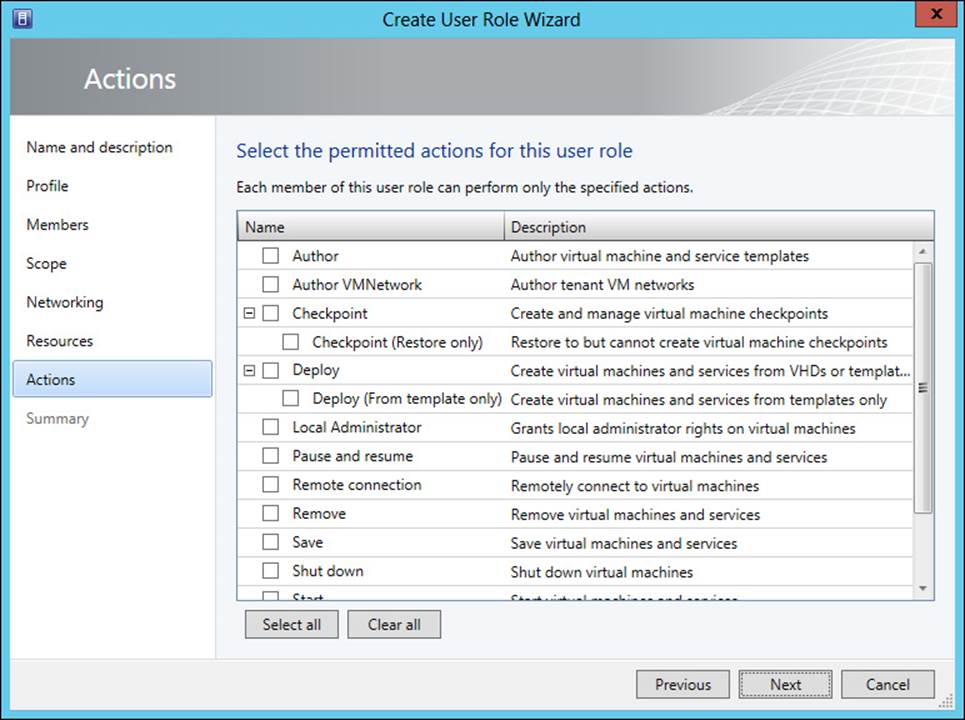
FIGURE 3-9 Configuring permitted actions for a user role
You can test the permissions and view of a given user role right within the VMM console by selecting Open New Connection from the down arrow in the top-left corner of the VMM console ribbon. The Connect To Server dialog box will display and, once connected, the Select User Role dialog box will display (see Figure 3-10), within which you can select a user role for the session.
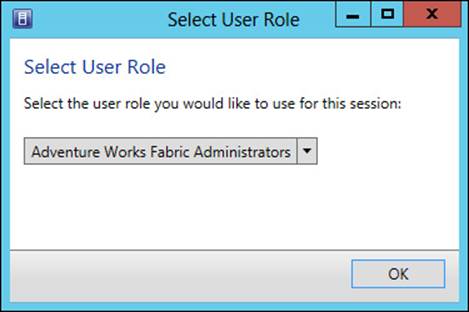
FIGURE 3-10 Selecting a user role for a new session
There are also Windows PowerShell cmdlets for working with user roles, several of which are described in Table 3-2. Virtual Machine Manager in System Center 2012 R2 adds new cmdlets. You can see a full list of cmdlets, including those for System Center 2012 R2, athttp://technet.microsoft.com/en-us/library/jj654428.
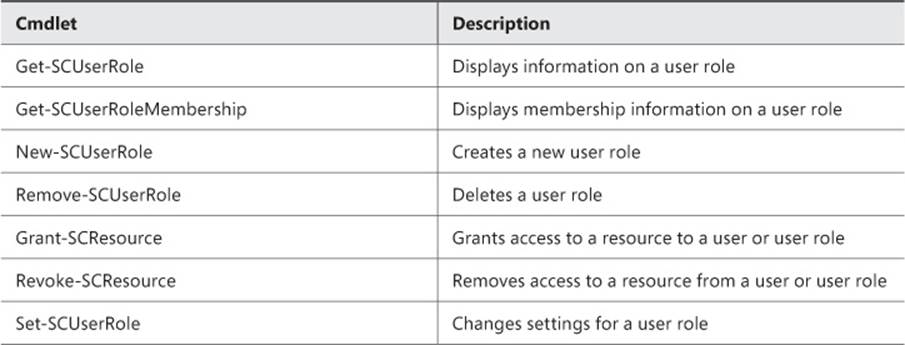
TABLE 3-2 Windows PowerShell cmdlets for working with user roles
More Info: User Roles in VMM
See http://technet.microsoft.com/en-us/library/gg696971.aspx for more information on user roles in VMM.
Self-service in VMM
Self-service in VMM enables users to deploy virtual machines and services as well as create templates and profiles. Enabling self-service means creating one or more roles with the Application Administrator (Self-Service User) role capabilities using the Create User Role Wizard already discussed. When configured, users in the role can log in using the VMM console.
More Info: VMM Self-Service
See http://technet.microsoft.com/en-us/library/gg610573.aspx and http://technet.microsoft.com/en-us/library/jj860419.aspx for more information on self-service in VMM.
Planning and implementing multi-host libraries
Multi-host libraries entail library objects that are shared or distributed across multiple library servers in VMM. When an object, such as a template, is shared among multiple library servers, you can mark the object as being the same by making it an equivalent object.
More Info: Libraries
If you need additional information on libraries themselves, see http://technet.microsoft.com/en-us/library/gg610598.aspx for an overview.
Planning libraries means choosing the location or locations where library servers will be placed. You might place a library server at a remote site to enable local virtual machines to take advantage of that library server’s objects.
Library servers need to be in the same domain or a two-way trusted domain with the VMM management server. Additionally, the firewall rules need to allow File and Print Sharing traffic from the VMM management server. Adding library servers requires the Administrator or Delegated Administrator user role.
Creating a multi-host library involves copying the same files or objects to each server taking part in the multi-host library. File-based library resources can be marked as equivalent objects, as discussed later in this section. The following steps are used to create a multi-host library:
1. Create a file share on each server and copy files there or copy the files to an already-created library share in VMM. Alternatively, you can also import a physical resource in VMM.
2. Mark files as equivalent objects as appropriate.
Creating equivalent objects
Equivalent objects enable a file-based object in a library share to be used by VMM without needing to retrieve it from a specific site. Equivalent objects are created by associating them through the VMM console in the Library workspace. Specifically, you click an object and then select its equivalent object while holding Ctrl and select Mark Equivalent from the ribbon or the shortcut menu. Doing so reveals the Equivalent Library Objects dialog box, shown in Figure 3-11.
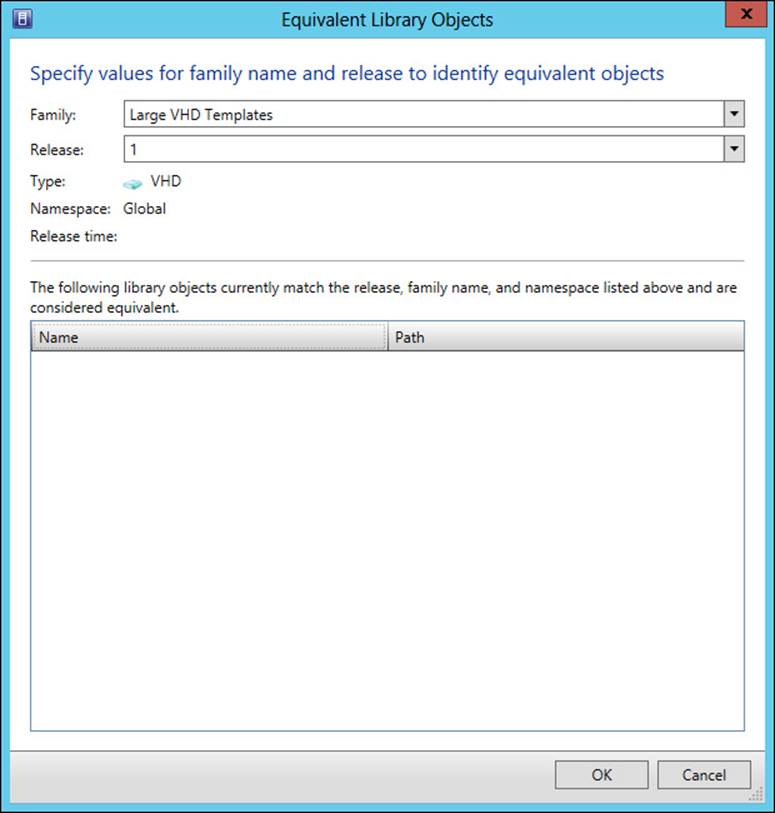
FIGURE 3-11 Creating an equivalent library object
The family and release should be entered for the library objects being marked as equivalent. For example, in Figure 3-11, the family being created is Large VHD Templates and its release is 1. These values should be changed to the necessary values based on your equivalent objects.
Equivalent objects are helpful when you have large files, such as an ISO in multiple VMM libraries, and you need to ensure that the local copy is used. For example, you might provision a virtual machine and want to ensure that the ISO in the local library is used. You could mark the ISOs as equivalent so that the local ISO is used.
More Info: Equivalent Objects
See http://technet.microsoft.com/en-us/library/gg610650.aspx for more information on creating or modifying equivalent objects.
Planning for and implementing host resource optimization
Optimizing host resources involves ensuring that the virtual machine host servers have enough resources to service their virtual machines and enough resources for normal operation of the server itself. VMM contains settings related to host reserves. Host reserves are used to keep a certain level of resources available to the host server. You can set the following parameters related to host reserves:
![]() CPU percentage
CPU percentage
![]() Memory
Memory
![]() Disk space
Disk space
![]() Maximum disk I/O per second
Maximum disk I/O per second
![]() Network capacity percentage
Network capacity percentage
When using host reserves, the parent host group for the server sets the default host reserves for the servers within its group. However, host reserves can be changed on a per-server basis by selecting the Override Host Reserve Settings From The Parent Host Group check box, as shown inFigure 3-12.
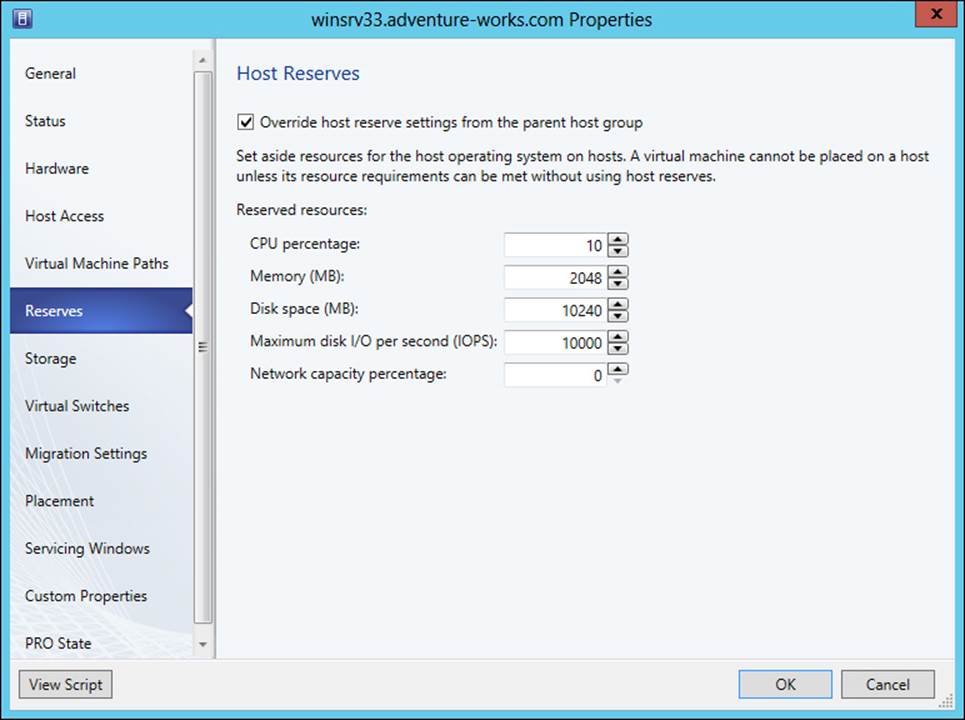
FIGURE 3-12 Configuring host reserves in VMM
Beyond manual configuration of host reserves, you can also configure reserves dynamically using dynamic optimization and power optimization. Dynamic optimization is discussed later in this chapter. Power optimization is used to conserve power by turning off hosts when additional resources are required. Power optimization requires that the host group be configured for migration using dynamic optimization.
More Info: Power Optimization
See http://technet.microsoft.com/en-us/library/gg675109.aspx for more information on power optimization.
Integrating third-party virtualization platforms
VMM integrates with third-party virtualization platforms, such as VMware vCenter Server and Citrix XenServer. VMM can then manage virtual machines on those platforms.
Adding a VMware vCenter Server is accomplished within the Fabric workspace by selecting VMware vCenter Server from the Add Resources menu. When adding a server, you enter the computer name, the port to use for communication, a Run As account, and whether to communicate in secure mode, as illustrated in Figure 3-13.
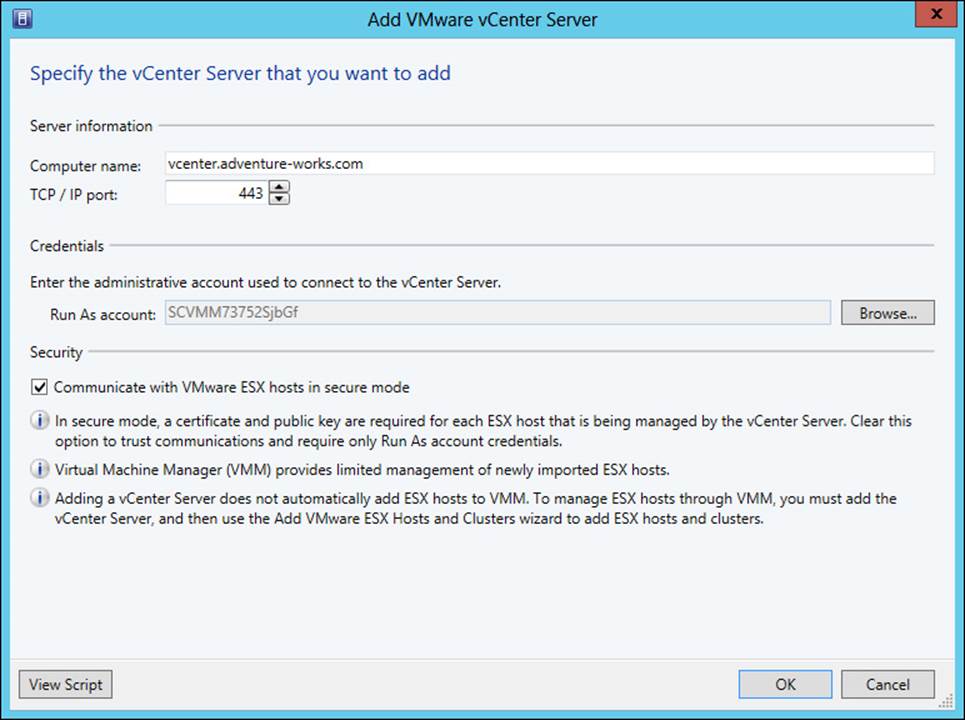
FIGURE 3-13 Adding a VMware vCenter Server to the Fabric workspace
More Info: VMware vCenter Server and ESX Hosts
Once the VMware vCenter Server has been added, you can then proceed to adding the ESX hosts. See http://technet.microsoft.com/en-us/library/gg610652.aspx for more information on adding ESX hosts to VMM and http://technet.microsoft.com/en-us/library/gg610683.aspxfor an overview of management tasks for ESX hosts.
Unlike the VMware vCenter Server integration, adding Citrix XenServer hosts and clusters doesn’t require adding the XenServer first. XenServer hosts and clusters can be added by simply selecting Citrix XenServer Hosts and Clusters from the Add Resources menu of the Fabric workspace.
More Info: Citrix XenServer
See http://technet.microsoft.com/en-us/library/gg610628.aspx for an overview of Citrix XenServer in VMM.
Deploying Hyper-V hosts to bare metal
As of System Center 2012 SP1, Virtual Machine Manager can find computers that are candidates for deployment as Hyper-V hosts from bare metal—in other words, with no operating system installed on them. To do so, the computer needs to meet certain criteria, such has having an out-of-band management method like Intelligent Platform Management Interface (IPMI) version 1.5 or version 2.0, Data Center Management Interface (DCMI) version 1.0, System Management Architecture for Server Hardware (SMASH) version 1.0 on WS-Management, or a custom protocol.
Additionally, the infrastructure needs to have a PXE server in the same subnet with the Windows Deployment Services role to install the operating system along with an appropriate operating system image.
More Info: Workflow for Hyper-V Hosts from Bare Metal
Microsoft has identified a workflow for deployment available at http://technet.microsoft.com/en-us/library/gg610634.aspx.
 Thought experiment: Delegating VMM
Thought experiment: Delegating VMM
In this thought experiment, apply what you’ve learned about this objective. You can find an answer in the “Answers” section at the end of this chapter.
You’re tasked with designing and implementing the delegation for the VMM implementation in your organization. The VMM implementation includes three Hyper-V servers. Your organization consists of an infrastructure team along with two development teams. The development teams have enough expertise to be able to create their own virtual machines.
Describe the user roles that you might use for the delegated administration.
Objective summary
![]() Several built-in user profiles in VMM can be used to build user roles.
Several built-in user profiles in VMM can be used to build user roles.
![]() You can use multi-host libraries as a means to keep equivalent objects, such as templates, located on servers close to the client.
You can use multi-host libraries as a means to keep equivalent objects, such as templates, located on servers close to the client.
![]() VMM enables you to provide reserved host resources to ensure that the host has enough memory, CPU, and other resources to continue normal operations.
VMM enables you to provide reserved host resources to ensure that the host has enough memory, CPU, and other resources to continue normal operations.
![]() VMM integrates with VMware vCenter Server and Citrix XenServer and can manage virtual machines hosted on those platforms.
VMM integrates with VMware vCenter Server and Citrix XenServer and can manage virtual machines hosted on those platforms.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. Which of the following is not a valid host reserve setting?
A. Memory
B. Disk Status
C. CPU Percentage
D. Disk Space
2. Which role or roles can add XenServer hosts and clusters to VMM?
A. Fabric Administrator
B. Administrator
C. Self-Service Role
D. Tenant Administrator
3. What is the default port used for communication between VMM and a VMware vCenter Server?
A. 443
B. 5150
C. 5297
D. 3389
Objective 3.2: Plan and implement virtual machines
Once the underlying infrastructure has been planned and implemented, you can begin planning the virtual machines (VMs) that will act as guests atop the Hyper-V hosts. This section looks at highly available virtual machines and other aspects related to the virtual machines themselves.
This objective covers how to:
![]() Plan for and implement highly available VMs
Plan for and implement highly available VMs
![]() Plan for and implement guest resource optimization, including shared VHDx
Plan for and implement guest resource optimization, including shared VHDx
![]() Configure placement rules
Configure placement rules
![]() Create Virtual Machine Manager templates
Create Virtual Machine Manager templates
Planning and implementing highly available VMs
Making a virtual machine highly available is easier than ever with System Center 2012. When planning highly available VMs, you should consider the hosts on which the virtual machines will reside. For example, making a highly available VM hosted on two servers located physically next to each other in the data center isn’t really helpful if there’s a power loss or other catastrophic event at that data center. An option for configuration in VMM is the possible nodes to which a VM can migrate. This option can be used to configure both the preferred owner of a VM and the hosts to which the VM can fail.
More Info: Preferred Hosts
See http://technet.microsoft.com/en-us/library/jj628161.aspx for more information on preferred and possible owner configuration in VMM.
You should consider each point of failure in the VM’s availability chain. The host servers should have different power sources, physical locations, network connectivity, and so on. Reducing or removing the single points of failure will help to make the VM highly available.
Another option for high availability for VMs is an availability set. An availability set is used to ensure that VMs providing the same service are located on separate nodes of a cluster. This helps to alleviate service downtime if a given VM host goes offline.
More Info: Availability Sets
See http://technet.microsoft.com/en-us/library/jj628165.aspx for more information on configuring availability sets in VMM.
When configuring high availability, you have four options for the priority of the VM:
![]() High
High
![]() Medium
Medium
![]() Low
Low
![]() Do not restart automatically
Do not restart automatically
When a node in a cluster fails, higher priority VMs are allocated resources before those with lower priority. If the node to which the VM is moved doesn’t have enough available resources, those VMs with lower priority may not be started. This is important for planning in that you should ensure that important VMs are given high priority over those that serve a less valuable role in the organization.
Implementing highly available VMs is accomplished when creating a virtual machine or after creation through the virtual machine’s Properties dialog box.
Adding the high availability option is accomplished by selecting Make This Virtual Machine Highly Available at the Configure Hardware phase of virtual machine creation, within the Availability section, as shown in Figure 3-14.
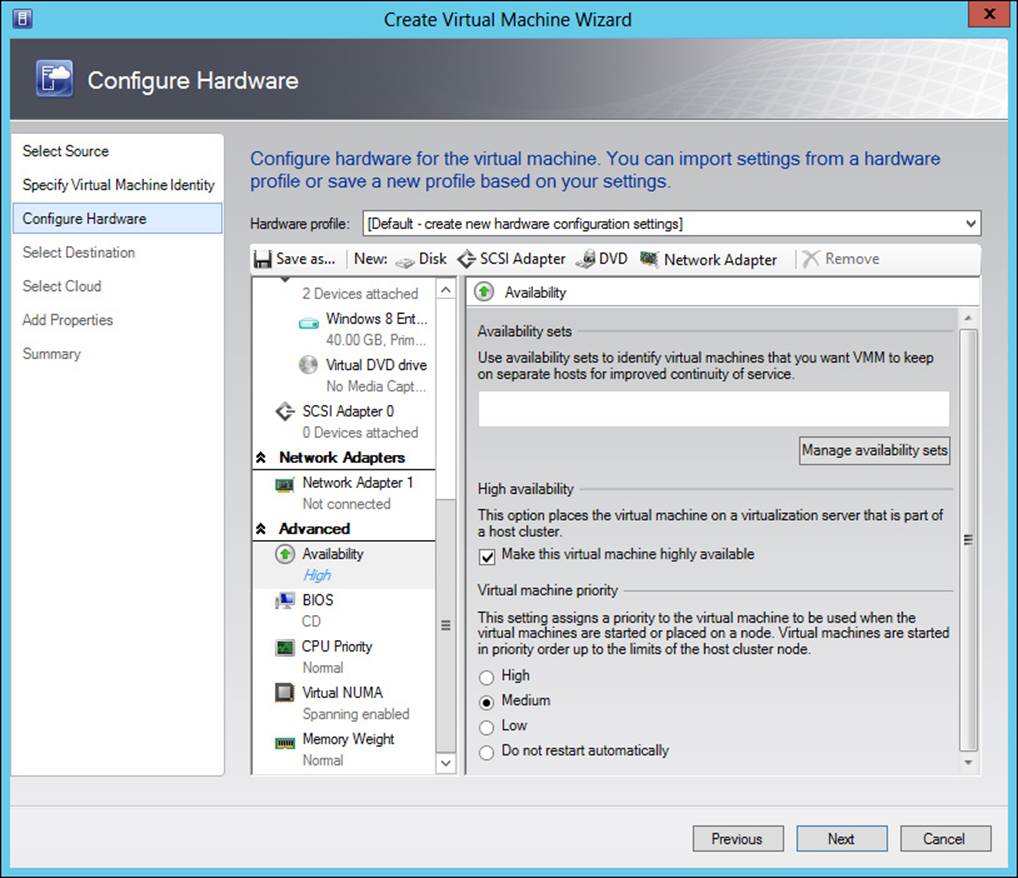
FIGURE 3-14 Adding high availability to a virtual machine
Planning for and implementing guest resource optimization
Several items can be configured to help optimize VM resource usage. Among these are dynamic memory, smart page file, and RemoteFX.
Dynamic memory enables the host to allocate a range of RAM (Random Access Memory) to a virtual machine and to recover that RAM when it’s not needed by the VM. Four dynamic memory settings are found within the Hardware Configuration section of a VM’s properties (shown inFigure 3-15) or at configuration time:
![]() Startup Memory
Startup Memory
![]() Minimum Memory
Minimum Memory
![]() Maximum Memory
Maximum Memory
![]() Memory Buffer Percentage
Memory Buffer Percentage
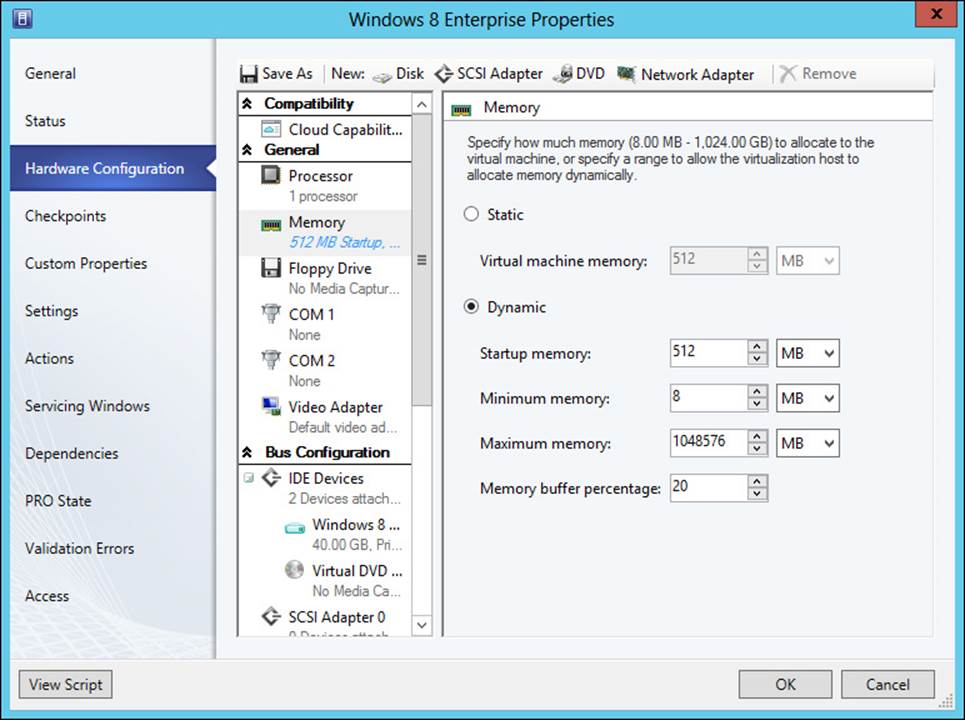
FIGURE 3-15 Dynamic memory settings
Startup Memory defines the amount of RAM that will be allocated to the VM on boot, while Minimum and Maximum Memory define the lowest and highest amounts of RAM that will be available to the virtual machine at any given time.
The Memory Buffer Percentage defines the amount of additional memory that will be allocated to the virtual machine to account for incremental changes to the amount of RAM needed at a given point in time. While Hyper-V can allocate memory very quickly, there are times when the virtual machine would benefit from having slightly more RAM available. The Memory Buffer Percentage is calculated as a percentage of the currently allocated RAM. For example, if the virtual machine has 1,000 megabytes (MB) of memory currently in use and a 10 percent buffer, then Hyper-V will actually allocate 1,100 MB.
Another setting not directly related to dynamic memory is Memory Weight. Memory Weight defines how the host allocates memory to a given virtual machine. There are four settings related to Memory Weight:
![]() High
High
![]() Normal
Normal
![]() Low
Low
![]() Custom
Custom
When a host is low on memory, the virtual machines with higher priority will have memory allocated before those with a lower priority. While these settings aren’t directly related to dynamic memory, they can affect performance of a virtual machine.
Smart Paging, which creates paging files for virtual machine startup, is used when the Hyper-V host doesn’t have enough startup memory available. Assume a virtual machine has 2,048 MB startup memory allocated to it, but the last time it was running, it was using 500 MB. Now when the virtual machine is restarted, it will need all 2,048 MB of startup memory. In this way, Smart Paging helps to alleviate virtual machine restart failures. Hyper-V uses the following rules, all of which need to be met, for determining when Smart Paging will be used:
![]() The virtual machine is being restarted (but not started from an Off state).
The virtual machine is being restarted (but not started from an Off state).
![]() The Hyper-V host has no physical memory available.
The Hyper-V host has no physical memory available.
![]() The Hyper-V host cannot recover memory from its other virtual machines.
The Hyper-V host cannot recover memory from its other virtual machines.
Smart Paging files exist only during virtual machine startup and are only used for this purpose.
RemoteFX requires the Remote Desktop Virtualization Host role service on the Hyper-V hosts that will provide RemoteFX to virtual machines. RemoteFX can be added to a virtual machine through the Display section of its Properties dialog box.
 Exam Tip
Exam Tip
RemoteFX is no longer within the objective domain for the 70-414 exam.
Shared VHDx
Storage for a virtual machine cluster can be made using a shared virtual hard disk (.vhdx file). Shared VHDx can be used with cluster-shared volumes (CSV) or on Scale-Out File Servers on an SMB-based share. In either case, both servers need to be capable of failover clustering, running Windows Server 2012 R2, and within the same Active Directory domain.
Note: Shared VHDx
Shared VHDx is not appropriate for the operating system itself.
A prerequisite for using a shared VHDx is to have clustered virtual machines already created through a Hyper-V cluster. Once the virtual machines are created, adding a shared VHDx is accomplished through the Failover Cluster Manager. Specifically, add a SCSI Controller and new virtual hard disk to one of the virtual machines and then select Enable Virtual Hard Disk Sharing within the SCSI Controller Advanced Features.
 Exam Tip
Exam Tip
The Add-VMHardDiskDrive Windows PowerShell cmdlet can be used with the -ShareVirtualDisk parameter to share the virtual hard disk.
Once the disk has been added and shared, the final step is to create a guest cluster on the virtual machines.
Configuring placement rules
When a virtual machine is created, VMM evaluates the possible hosts for the virtual machine using several performance criteria for the host and also the expected utilization of the VM. The result is a scale of 1 to 5 stars based on how well VMM believes a given host can service the virtual machine being created (see Figure 3-16).
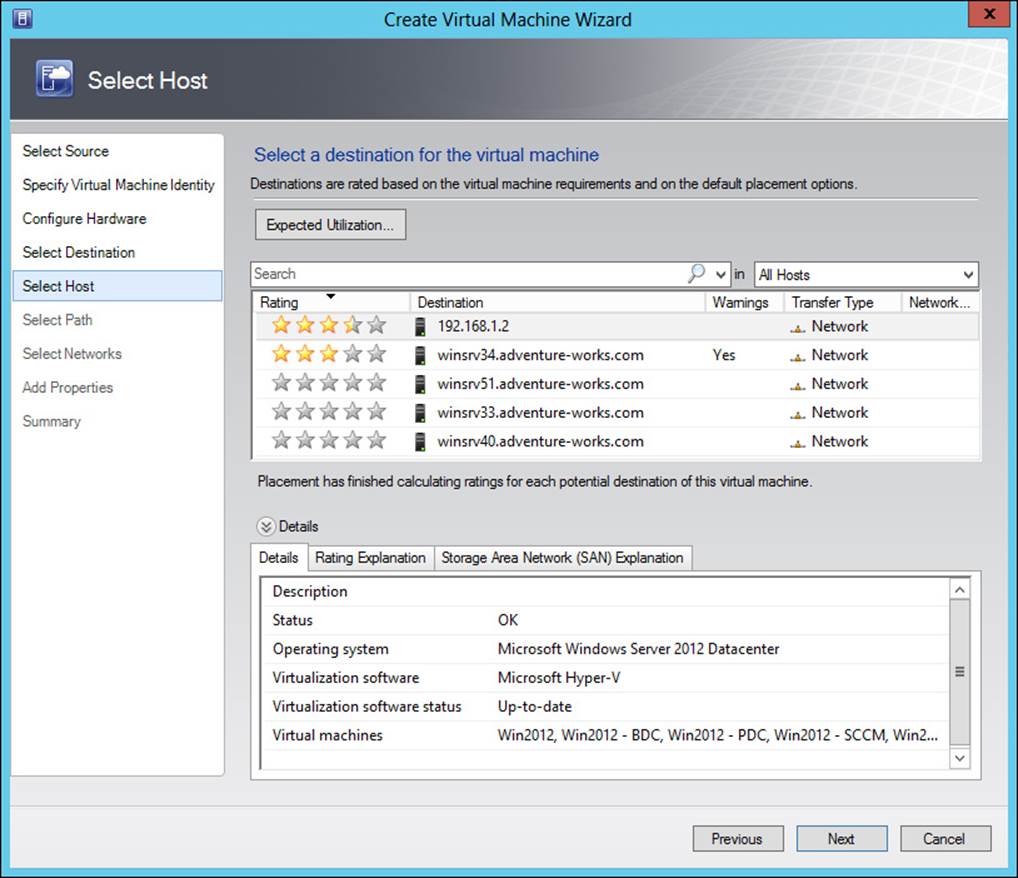
FIGURE 3-16 Virtual machine placement in VMM
Clicking Expected Utilization enables you to change how the hosts are rated according to the expected usage pattern for the virtual machine. You can change four criteria:
![]() Expected CPU Utilization (default 20%)
Expected CPU Utilization (default 20%)
![]() Required Physical Disk Space (GB) (default 0)
Required Physical Disk Space (GB) (default 0)
![]() Expected Disk I/O Per Second (default 0)
Expected Disk I/O Per Second (default 0)
![]() Expected Network Utilization In Megabits Per Second (default 0)
Expected Network Utilization In Megabits Per Second (default 0)
More Info: Placement and Host Ratings
See http://technet.microsoft.com/en-us/library/jj860428.aspx for more information on placement and host ratings.
Placement rules are created at the host group level, and by default host groups inherit placement rules from their parent host group. Placement rules are created by first creating custom properties. Several custom properties are already available, and you can create your own as well. For example, you might create a custom property that defines the application layer on which virtual machines operate (such as data layer, web layer, business rules layer, and so on). In such a scenario, you may have certain hosts designated for servicing virtual machines in the web layer. Creating a custom property and assigning that as a placement rule would then ensure that virtual machines would be placed on hosts that met the custom property.
Create a custom property in the Manage Custom Properties dialog box (shown in Figure 3-17), which is accessed through host group, virtual machine, and other Properties dialog boxes in VMM. The custom property can then be associated with various objects in VMM, such as hosts, host groups, virtual machines, and so on.
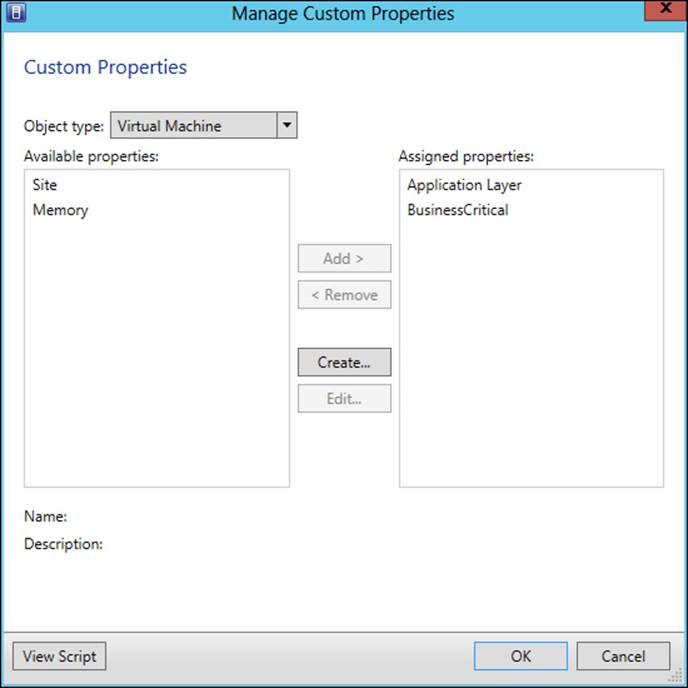
FIGURE 3-17 Managing a custom property and assigning it to a virtual machine object type
Once the custom property is created, you then assign values for it through each of the appropriate hosts, host groups, or virtual machines. Placement rules are then configured within the host group to which the custom property should apply. For example, Figure 3-18 shows placement rules for the All Hosts host group, with one placement rule defined for the Application Layer custom property previously defined.
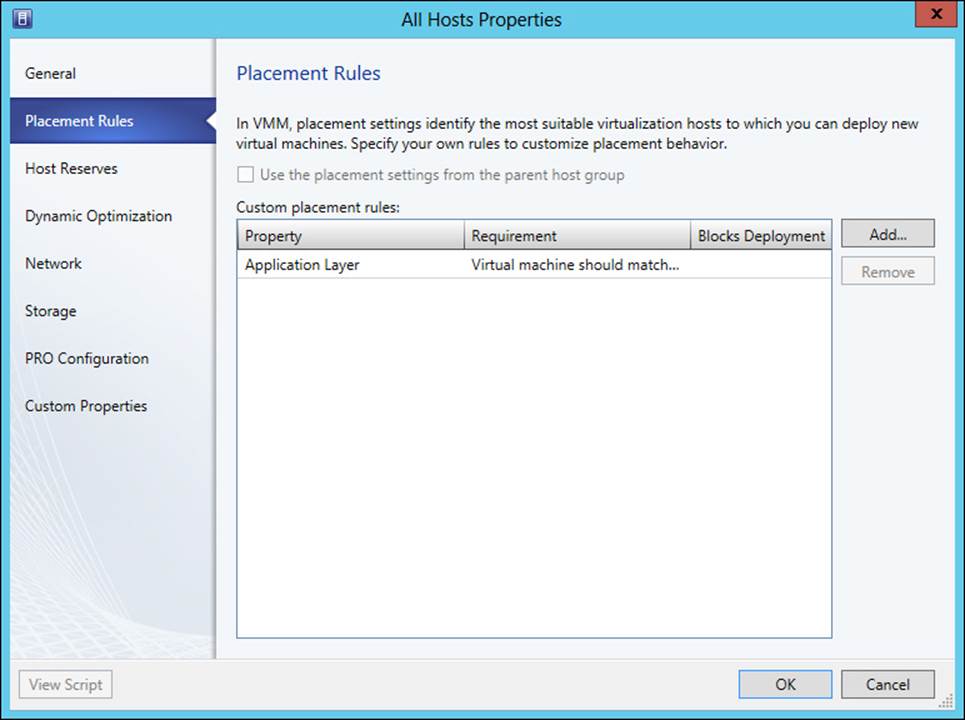
FIGURE 3-18 Viewing placement rules for the All Hosts group
Adding a placement rule is accomplished by clicking Add, which reveals the Create Custom Requirement dialog box shown in Figure 3-19.
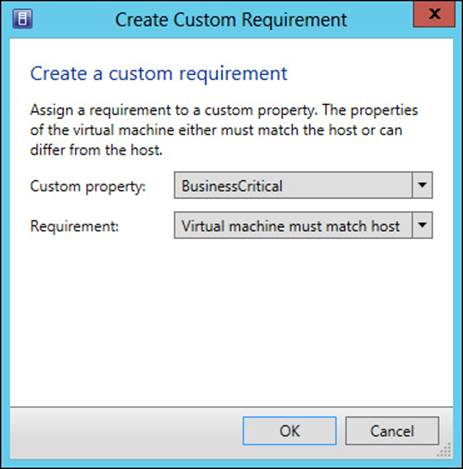
FIGURE 3-19 Creating a placement rule
There are four criteria for matching the rule, contained in the Requirement drop-down list:
![]() Virtual Machine Must Match Host
Virtual Machine Must Match Host
![]() Virtual Machine Should Match Host
Virtual Machine Should Match Host
![]() Virtual Machine Must Not Match Host
Virtual Machine Must Not Match Host
![]() Virtual Machine Should Not Match Host
Virtual Machine Should Not Match Host
These criteria enable you to configure how the placement rules will be evaluated. For example, when one of the “must” criteria is selected, the deployment of a virtual machine will be blocked if it doesn’t meet the placement rule.
There are also Windows PowerShell cmdlets related to placement rules, including:
![]() Add-SCCustomPlacementRule
Add-SCCustomPlacementRule
![]() Get-SCCustomPlacementRule
Get-SCCustomPlacementRule
![]() Remove-SCCustomPlacementRule
Remove-SCCustomPlacementRule
![]() Set-SCCustomPlacementRule
Set-SCCustomPlacementRule
Creating Virtual Machine Manager templates
Virtual Machine Manager templates are library resources that contain information about the configuration for a virtual machine. Being a library resource, Virtual Machine Manager templates are created in the Library workspace by selecting Create VM Template from the Home ribbon. Doing so invokes the Create VM Template Wizard, shown in Figure 3-20.
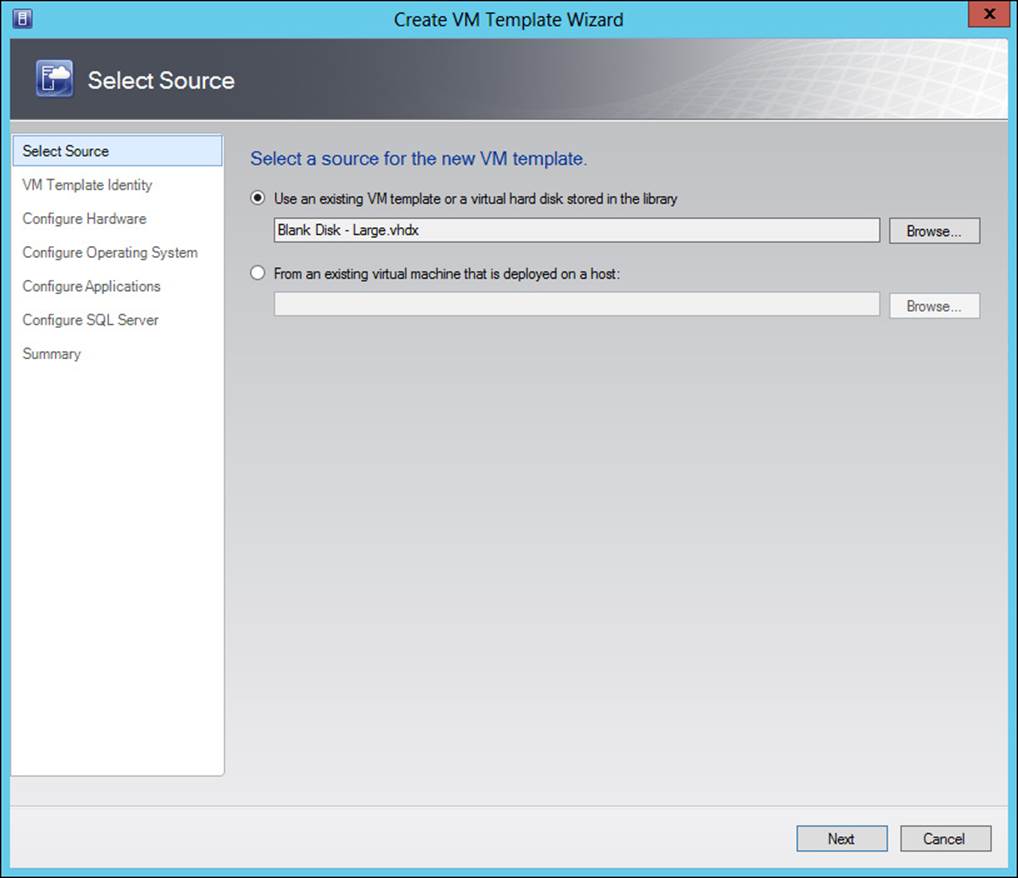
FIGURE 3-20 Beginning the Create VM Template Wizard
As displayed in Figure 3-20, you can create a VM template by using a virtual hard disk, by using another VM template, or by using an existing virtual machine. The VM Template Identity page enables you to set the name for the template and its description. The Configure Hardware page is used to configure hardware settings for the template and is shown in Figure 3-21.
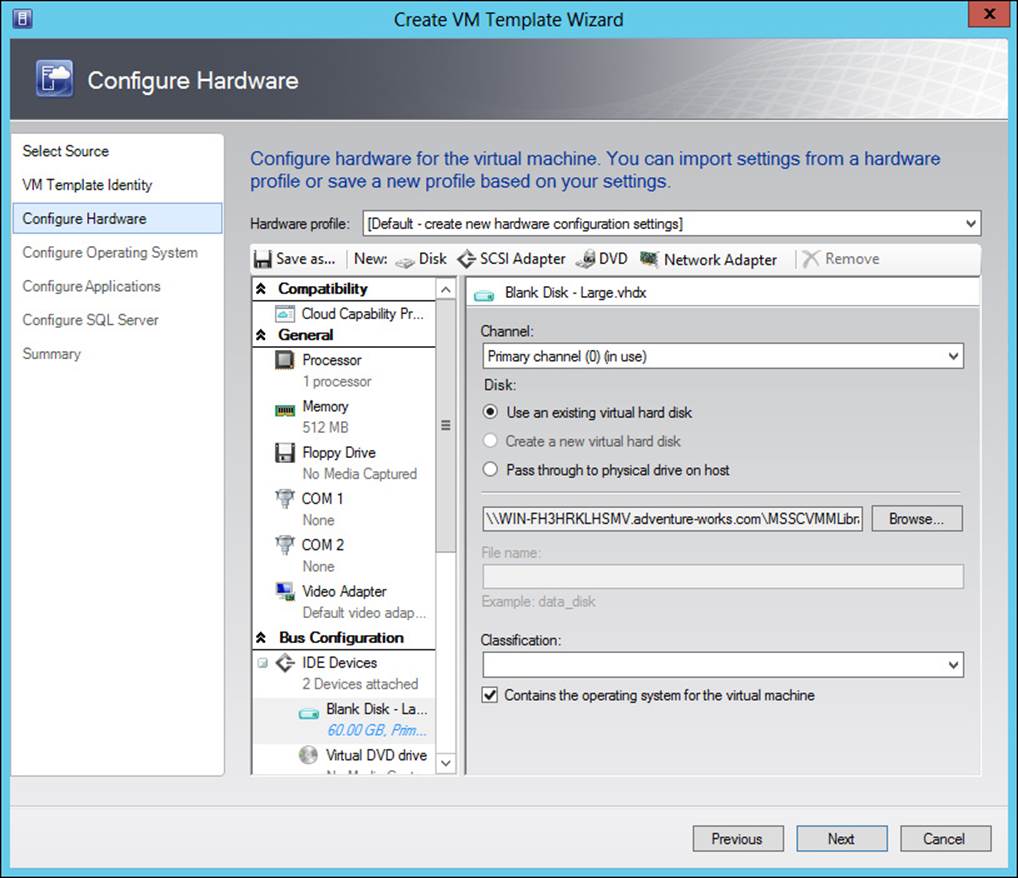
FIGURE 3-21 Configuring hardware settings for the template
The Configure Operating System page, shown in Figure 3-22, is used to configure operating system parameters for the template. It’s important to note that you can choose a Guest OS Profile from among these options:
![]() Default - Create New Windows Operating System Customization Settings (as depicted in Figure 3-22)
Default - Create New Windows Operating System Customization Settings (as depicted in Figure 3-22)
![]() None - Customization Is Not Required
None - Customization Is Not Required
![]() Create New Linux Operating System Customization Settings
Create New Linux Operating System Customization Settings
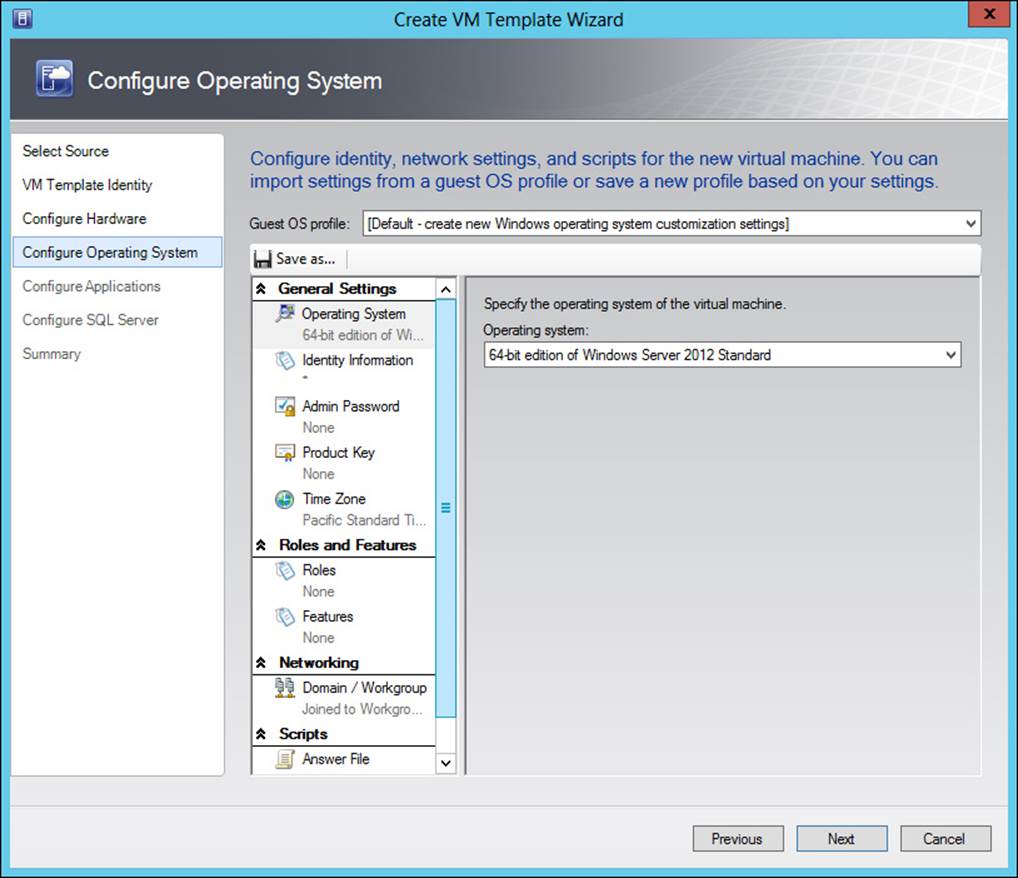
FIGURE 3-22 Configuring operating system settings for the template
The Guest OS Profile option chosen determines what settings are available for configuration. For example, when the Create New Linux Operating System Customization Settings option is chosen, only Operating System, Identify Information, Root Credentials, and Time Zone can be set and a RunOnce set of scripts defined.
If you choose the default option and are installing Windows Server 2003 or above, the next page shown is Configure Applications, depicted in Figure 3-23. Clicking Add enables you to add an application based on the profile chosen.
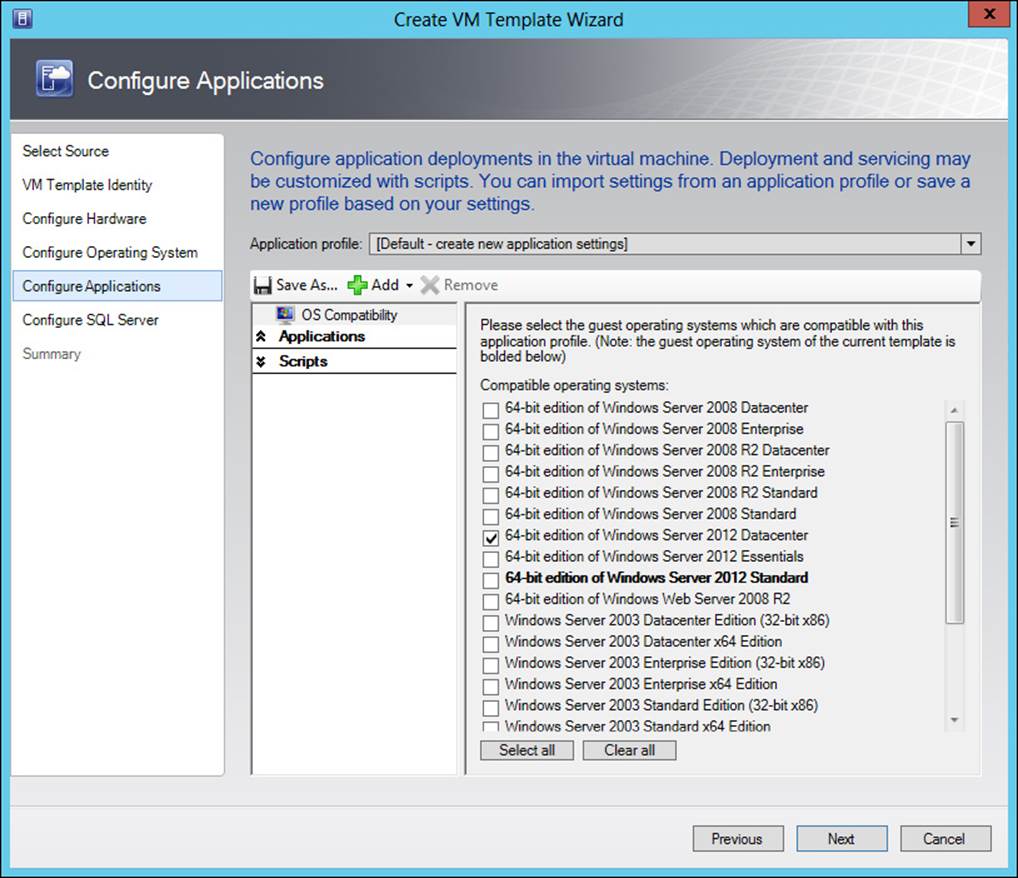
FIGURE 3-23 Configuring applications in the template
Finally, you can also deploy SQL Server, as shown in Figure 3-24.
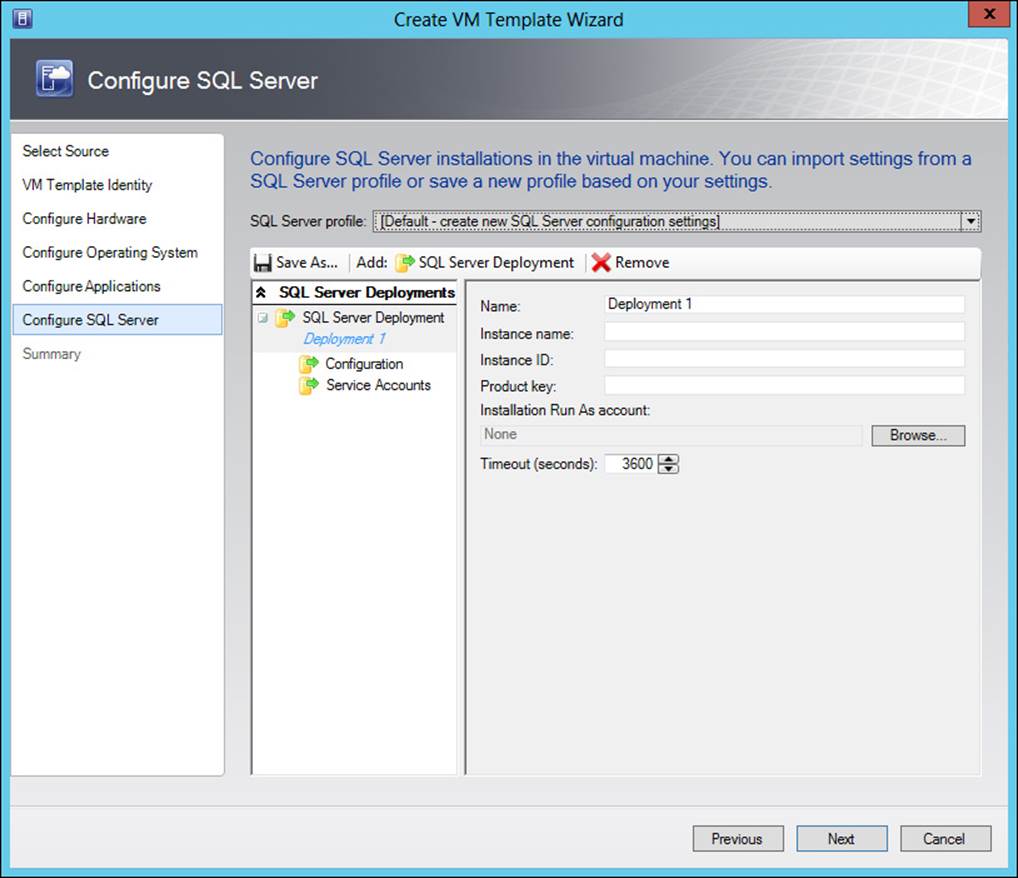
FIGURE 3-24 Configuring SQL Server as part of a VM template
More Info: Creating Templates
See http://technet.microsoft.com/en-us/library/bb963734.aspx for more information on creating virtual machine templates.
 Thought experiment: Understanding dynamic memory and virtual machines
Thought experiment: Understanding dynamic memory and virtual machines
In this thought experiment, apply what you’ve learned about this objective. You can find an answer in the “Answers” section at the end of this chapter.
Your organization has been using dynamic memory as a means to maintain memory requirements for its v irtual machine hosts. However, recently users have been reporting that some of the client computers are slow when starting new applications. Once the application is open, the users don’t report any issues and the application performs as expected. You suspect that it might be related to the dynamic memory settings.
Discuss the settings for dynamic memory and some options to solve the issue being reported.
Objective summary
![]() When planning highly available VMs, you can set priority for the VM, availability sets, and preferred hosts.
When planning highly available VMs, you can set priority for the VM, availability sets, and preferred hosts.
![]() Guest resources can be optimized by using dynamic memory and by using RemoteFX.
Guest resources can be optimized by using dynamic memory and by using RemoteFX.
![]() Hyper-V can use a Smart Paging file to help restart a virtual machine when there isn’t enough available memory.
Hyper-V can use a Smart Paging file to help restart a virtual machine when there isn’t enough available memory.
![]() Placement rules are used as part of the measurements to determine the host on which a virtual machine should reside.
Placement rules are used as part of the measurements to determine the host on which a virtual machine should reside.
![]() Virtual Machine Manager templates are used to rapidly configure virtual machines with the same configurations.
Virtual Machine Manager templates are used to rapidly configure virtual machines with the same configurations.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. When planning high availability, the priority of a virtual machine can be set. Which of the following is not an option for that priority?
A. High
B. Do Not Restart Automatically
C. Medium
D. Automatic
2. Which of the following criteria must be met for Smart Paging to be used?
A. The host is out of physical memory.
B. The virtual machine is off and is being started.
C. The virtual machine is running and needs a larger paging file.
D. The Dynamic Memory Smart Paging option is enabled.
3. Which of the following cannot be used as the basis for a virtual machine template?
A. A virtual machine that has already been deployed
B. An existing template in the library
C. A virtual hard disk in the library
D. A predefined operating system image
Objective 3.3: Plan and implement virtualization networking
Creating specialized networks for virtual machines can help with security and provide advanced configurations where virtual machines can communicate only with each other. This section looks at the objectives surrounding virtual networks. Several of the objectives, such as Virtual Local Area Networks (VLANs) and converged networks, relate closely to each other and are addressed throughout this section.
This objective covers how to:
![]() Plan for and configure Virtual Machine Manager logical networks
Plan for and configure Virtual Machine Manager logical networks
![]() Plan for and configure IP address and MAC address settings across multiple Hyper-V hosts, including IP virtualization
Plan for and configure IP address and MAC address settings across multiple Hyper-V hosts, including IP virtualization
![]() Plan for and implement Windows Server Gateway
Plan for and implement Windows Server Gateway
![]() Plan for and configure virtual network optimization
Plan for and configure virtual network optimization
![]() Plan and implement VLANs and pVLANS
Plan and implement VLANs and pVLANS
![]() Plan and implement VM networks
Plan and implement VM networks
![]() Plan and implement converged networks
Plan and implement converged networks
Planning for and configuring Virtual Machine Manager logical networks
Logical networks are collections of networking objects, such as IP addresses and subnets, VLANs, and related information used to help organize the structure of virtual machines. Logical networks are conceptual, which means they aren’t tied directly to (though they are still dependent on) the physical network infrastructure. This means you can set up a logical network to support virtual machines based on business need, even though those virtual machines may be physically connected to different switches in different geographical locations.
Planning logical networks
When planning for logical networks, you might use various strategies. For example, you might create a logical network based on an application layer (such as the database layer, web or frontend layer, and so on) or based on a purpose, such as quality assurance.
VMM requires that a logical network exist in order to deploy virtual machine services. However, VMM creates a logical network automatically when a Hyper-V host is added. The automatically created logical network matches the first DNS suffix label on each of the host’s network adapters. These logical networks essentially match the physical topology.
Three important concepts surround logical networks:
![]() Network sites
Network sites
![]() Static IP address pools
Static IP address pools
![]() Media Access Control (MAC) address pools
Media Access Control (MAC) address pools
More Info: Logical Networks
See http://technet.microsoft.com/en-us/library/jj721568.aspx for more information on logical networks and http://technet.microsoft.com/en-us/library/jj870823.aspx for common scenarios for logical networks. You can also view common scenarios for networking athttp://technet.microsoft.com/en-us/library/jj870823.aspx.
Network Sites
A network site provides the link between a subnet or subnets, VLANs, and subnet/VLAN pairs and a logical network. Network sites enable you to further refine a logical network. For example, assume that you have two physical data centers in different locations. For redundancy, you want to service web traffic from each of these data centers. You could create a logical network to represent the web traffic and then create a network site for each data center. Doing so would enable you to maintain host groups for each data center while still using the same logical network for ease of management.
Static IP Address Pools
Static IP address pools provides a means by which VMM can assign IP addresses to Windows-based virtual machines. Static IP address pools can optionally contain information such as DNS servers, default gateway, and Windows Internet Name Service (WINS) servers.
Static IP address pools aren’t necessary where Dynamic Host Configuration Protocol (DHCP) has already been deployed. However, if your configuration uses network virtualization, then an IP address pool must be created so that VMM can provide IP information to the virtual machines deployed on the virtual network.
 Exam Tip
Exam Tip
When you use static IP addresses assigned by VMM, you need to configure a static MAC address for the virtual machine as well.
Static IP address pools can also be created to support multicasting on the virtual machine network, with a few prerequisites:
![]() Network virtualization must be enabled on the logical network.
Network virtualization must be enabled on the logical network.
![]() Multicast must be selected for the IP address pool.
Multicast must be selected for the IP address pool.
![]() The IP version (IPv4 or IPv6) needs to be the same for both the VM network and the logical network.
The IP version (IPv4 or IPv6) needs to be the same for both the VM network and the logical network.
 Exam Tip
Exam Tip
Prior to the Windows Server 2012 R2 release, the GET-SCVMNetwork cmdlet was the only way to view the IP address version information.
IP address pools are covered in the section titled “Planning for and configuring IP address and MAC address settings across multiple Hyper-V hosts” later in this chapter.
MAC Address Pools
VMM can also be used to assign MAC addresses to network devices on Windows-based virtual machines. There are two default MAC address pools, one for Hyper-V and Citrix XenServer hosts and another for VMware ESX hosts. You can add MAC address pools as needed for your topology. Doing so is discussed in the section titled “Planning for and configuring IP address and MAC address settings across multiple Hyper-V hosts” later in this chapter.
Creating a logical network
Logical networks are created in the Fabric workspace by selecting Logical Network from the Create drop-down list. Doing so invokes the Create Logical Network Wizard, shown in Figure 3-25 and Figure 3-26.
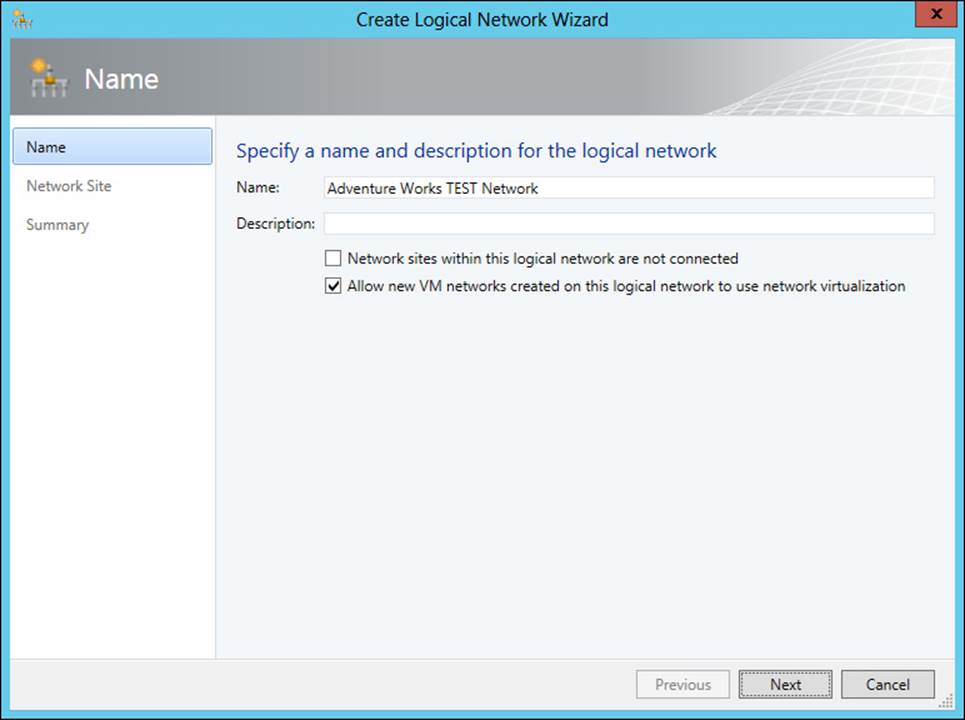
FIGURE 3-25 Creating a logical network
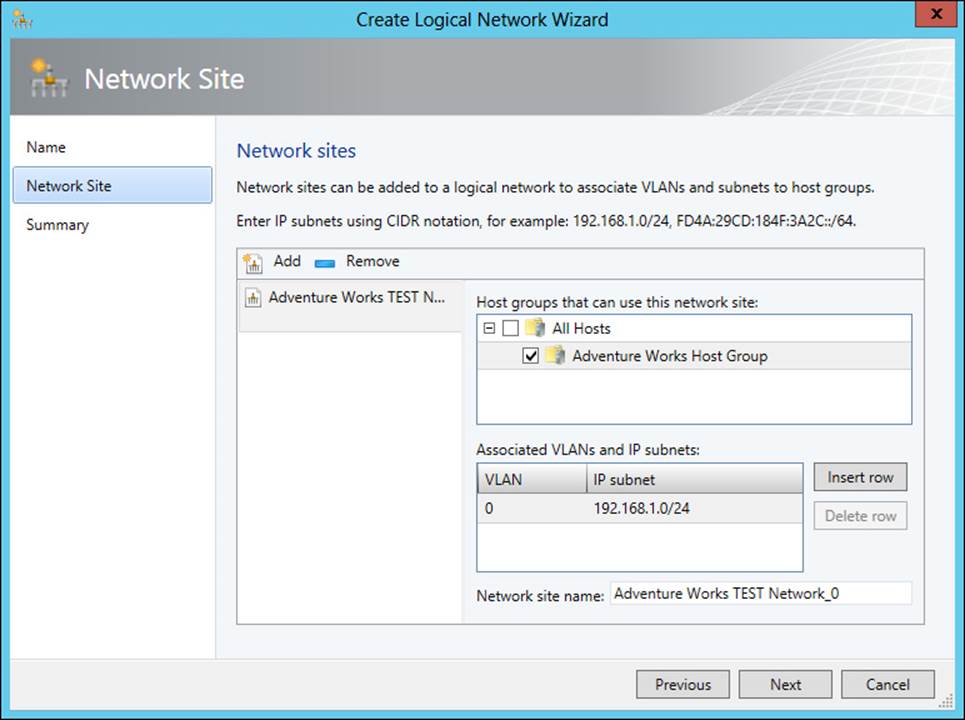
FIGURE 3-26 Adding a network site to a logical network
The two options shown on the Name page of the wizard are:
![]() Network Sites Within This Logical Network Are Not Connected
Network Sites Within This Logical Network Are Not Connected
![]() Allow New VM Networks Created On This Logical Network To Use Network Virtualization
Allow New VM Networks Created On This Logical Network To Use Network Virtualization
If you select the first option, indicating that the network sites aren’t connected, another option is revealed:
![]() Network Sites Within This Logical Network Contain Private VLANs (pVLANs)
Network Sites Within This Logical Network Contain Private VLANs (pVLANs)
This option, along with its parent option indicating that the networks are not connected, is used for topologies that contain VLANs. If the virtual machines will use Hyper-V hosts, then the Allow New VM Networks Created On This Logical Network To Use Network Virtualization option can be chosen.
Another possibility when creating networks is that virtual machines will be connected to an external network. In this case, you shouldn’t create a logical network using VMM; rather, you should add a virtual switch. See http://technet.microsoft.com/en-us/library/jj614619.aspx for more information on this scenario.
Once the network is configured, you can change settings related to the logical network in its Properties dialog box.
Virtual switch extensions are add-ons that enhance virtual switches to enable features that you might find on a traditional network switch, such as traffic shaping. Virtual switch extensions also enable third-party vendors to write add-ons that hook into the virtual switch. Virtual switch extensions can be managed through the Hyper-V console and also using Virtual Machine Manager. See http://technet.microsoft.com/en-us/library/dn249411.aspx for more information on virtual switch extension management with System Center 2012 R2.
Converged networks are networks that handle both normal network traffic and traffic for storage. Windows Server 2012 and Windows Server 2012 R2 both support converged networks.
Planning for and configuring IP address and MAC address settings across multiple Hyper-V hosts
You can use VMM to manage IP address and MAC address settings across Hyper-V hosts. This can be accomplished by managing each host through the Fabric workspace in VMM and by using logical network items and IP address and MAC address pools.
Hyper-V networking
Managing Hyper-V networking through VMM is accomplished by selecting the host and then opening the Virtual Switches page of the Properties dialog box. On the Virtual Switches page, shown in Figure 3-27, you can add, remove, and configure the networking for the Hyper-V host.
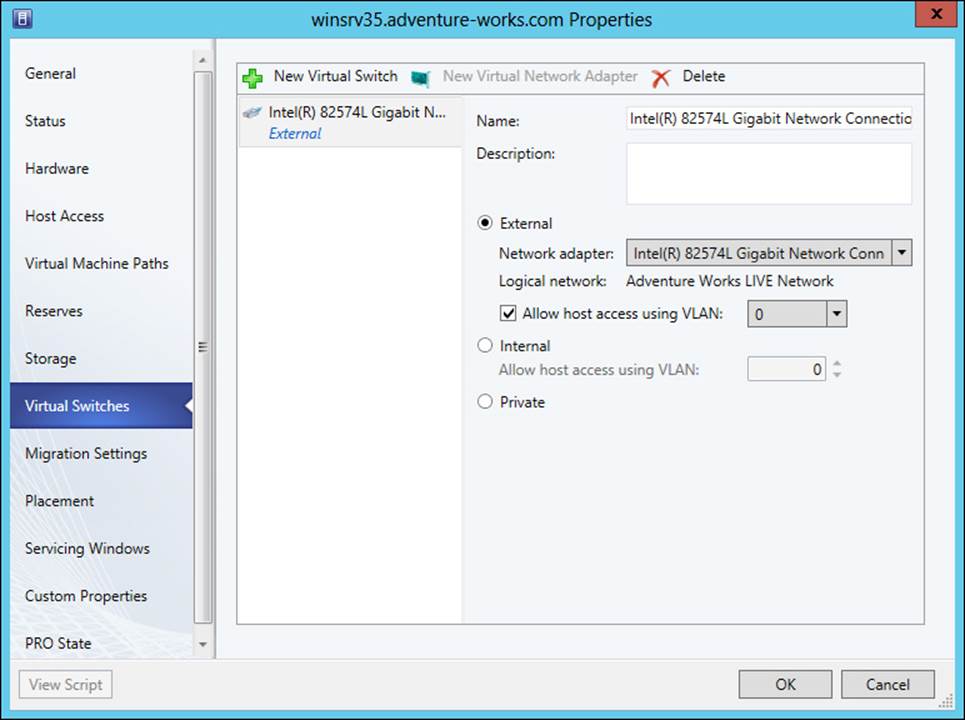
FIGURE 3-27 Configuring a virtual switch in a Hyper-V host
As Figure 3-27 shows, three types of network bindings can be created:
![]() External Use the External option when the virtual machines need to communicate with servers outside of the virtual machine fabric, such as external servers and the Hyper-V host operating system itself.
External Use the External option when the virtual machines need to communicate with servers outside of the virtual machine fabric, such as external servers and the Hyper-V host operating system itself.
![]() Internal An internal switch is used for communication to other virtual machines on the same host and to the Hyper-V host itself.
Internal An internal switch is used for communication to other virtual machines on the same host and to the Hyper-V host itself.
![]() Private A private switch is used to enable communication only with other virtual machines on the host and not on the Hyper-V host or any other external network.
Private A private switch is used to enable communication only with other virtual machines on the host and not on the Hyper-V host or any other external network.
More Info: Hyper-V Networking
See http://technet.microsoft.com/en-us/library/gg610603.aspx for additional network settings for Hyper-V. Logical switches enable you to apply virtual switch settings across multiple Hyper-V hosts. See http://technet.microsoft.com/en-us/library/jj628154.aspx for more information on logical switches.
IP address pools
IP address pools are configured within the Fabric workspace by selecting Create IP Pool from the Home ribbon. Doing so invokes the Create Static IP Address Pool Wizard, shown in Figure 3-28.
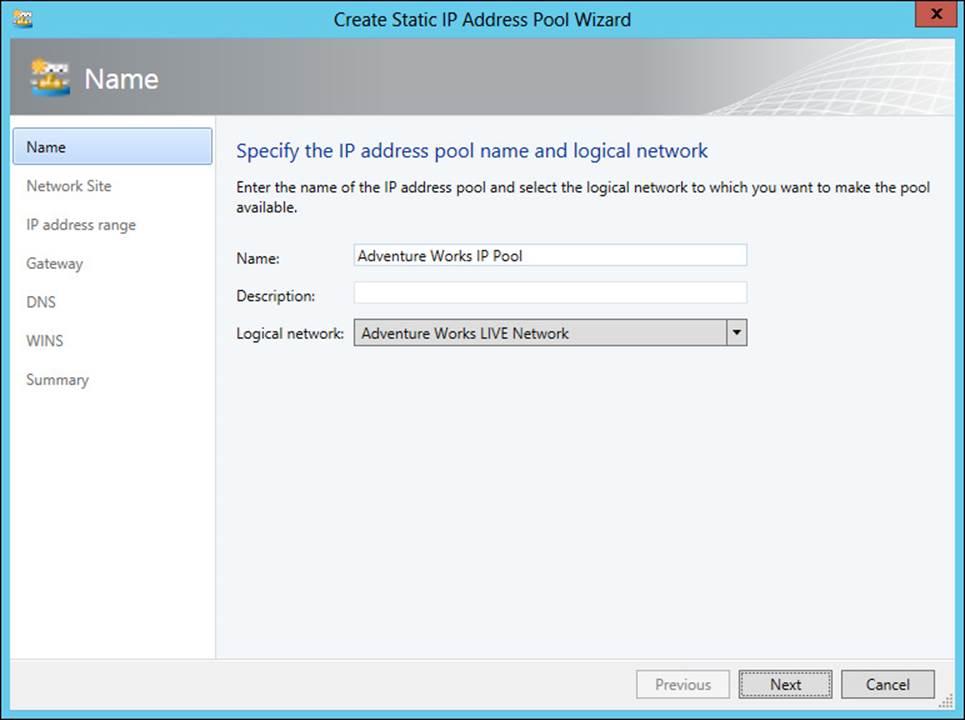
FIGURE 3-28 Creating an IP address pool
The network site is configured next. You can choose an existing network site or create a new one, as shown in Figure 3-29.
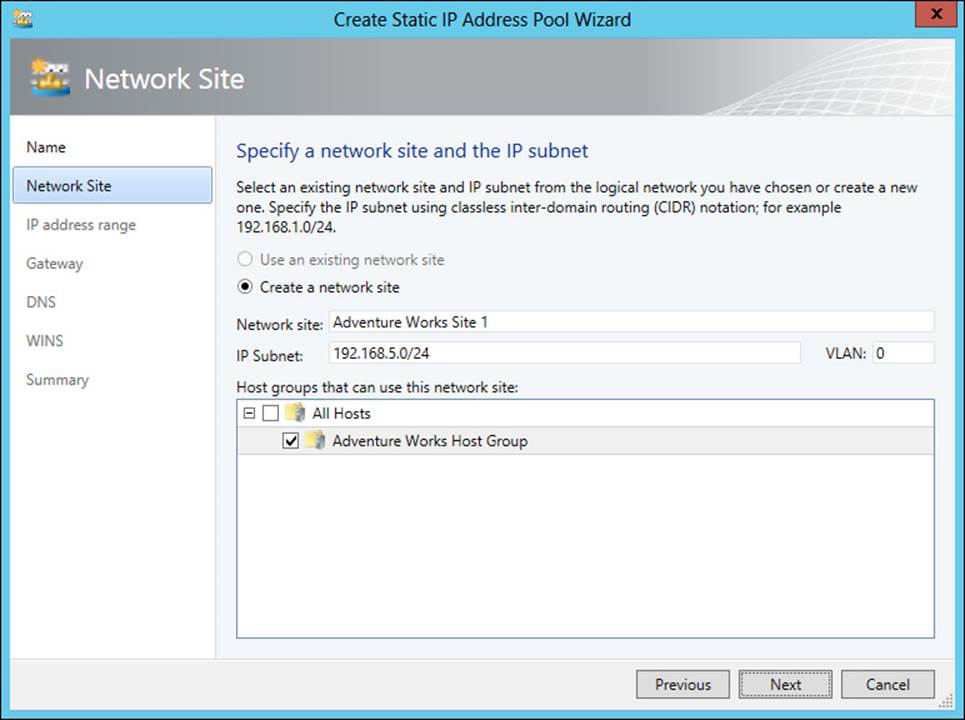
FIGURE 3-29 Creating a new network site
The IP address range is configured next, and you can also set aside reserved addresses within the subnet for virtual IPs (VIPs) or for other purposes. See Figure 3-30 for an example.
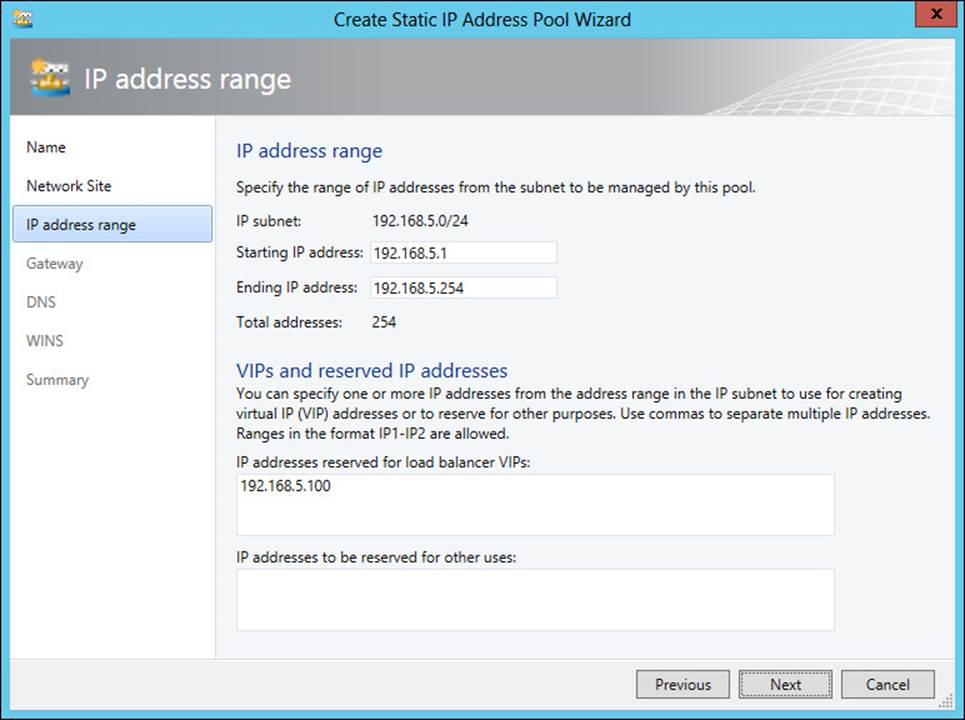
FIGURE 3-30 Configuring the IP address range
The next several screens in the Create Static IP Address Pool Wizard enable you to specify optional settings, such as the default gateway (or multiple default gateways), DNS servers, and WINS servers. Providing these settings is a good idea when VMM will manage the IP addresses for virtual machines, because the virtual machines will receive all of this basic networking information without any additional configuration necessary.
IP address pools are helpful for a delegation scenario, where normal IP address management would be accomplished by a separate team, such as a network team. In these instances, the network team can designate a range of IP addresses, which can then be added to Virtual Machine Manager for actual assignment to virtual machines.
More Info: IP Address Pools
See http://technet.microsoft.com/en-us/library/gg610590.aspx for more information on creating IP address pools.
MAC address pools
MAC address pools are created in the Fabric workspace by selecting Create MAC Pool from the Home ribbon. Doing so invokes the Create MAC Address Pool Wizard, shown in Figure 3-31.
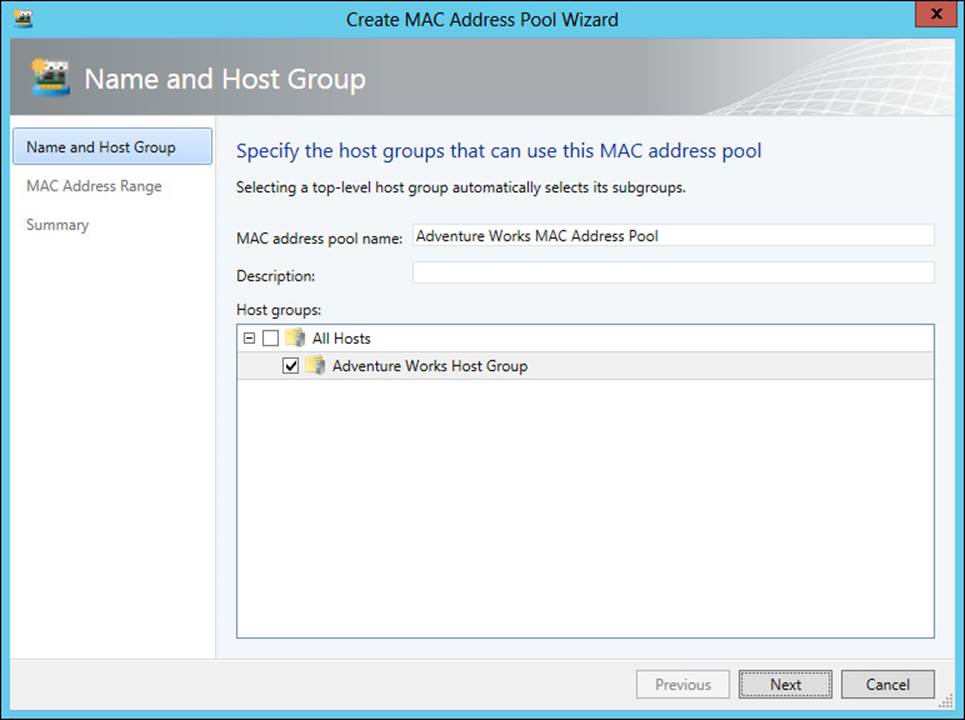
FIGURE 3-31 Creating a MAC address pool
As in IP address pool creation, you select the host group(s) to which the pool will apply. On the next page you enter the range of MAC addresses to use.
Creating a VM network
When network virtualization is enabled, you can create a virtual machine network. This is accomplished through the VMs and Services workspace by selecting Create VM Network from the Home tab. Doing so begins the Create VM Network Wizard, shown in Figure 3-32.
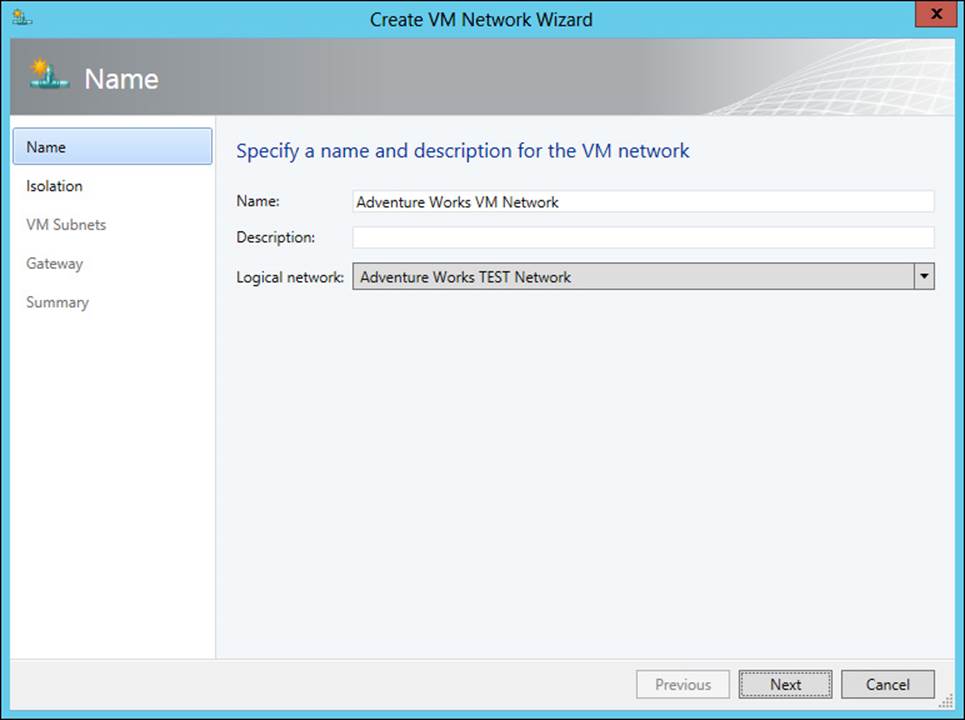
FIGURE 3-32 Beginning the Create VM Network Wizard
Once the name and logical network (and optionally a description) are chosen, you choose the isolation for the VM network, as shown in Figure 3-33.
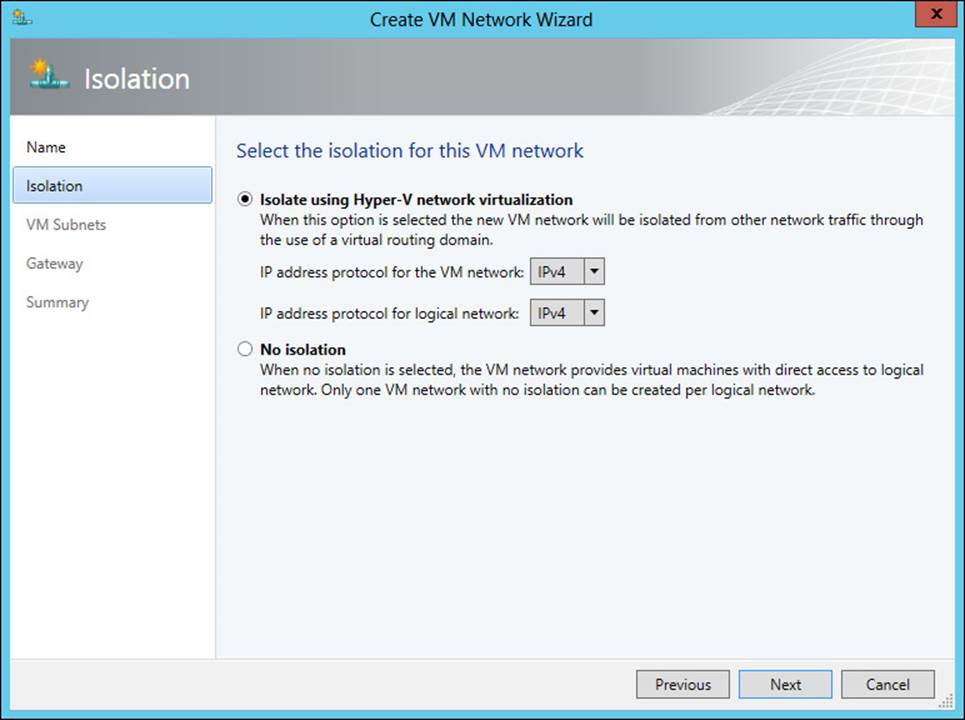
FIGURE 3-33 Choosing an isolation type for a VM network
It’s worth noting that if the only option available is No Isolation, that typically means the logical network doesn’t have network virtualization enabled.
The subnet(s) to use for the VM network are specified next, as shown in Figure 3-34.
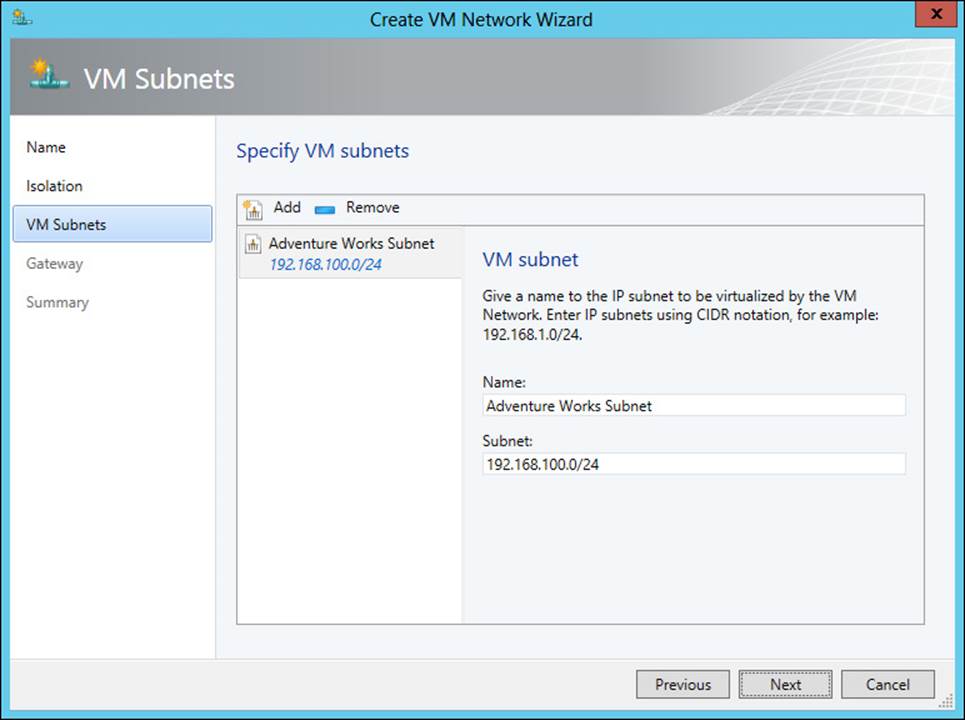
FIGURE 3-34 Adding a subnet for a VM network
Finally, a gateway is chosen, as depicted in Figure 3-35.
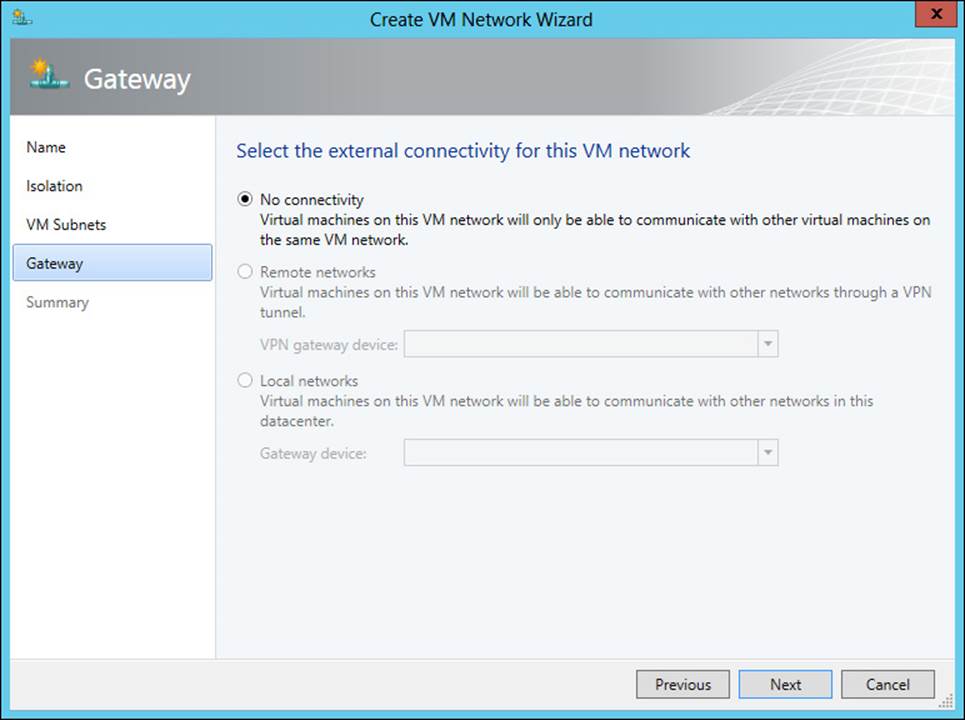
FIGURE 3-35 Choosing a gateway for the VM network
More Info: VM Networks
See http://technet.microsoft.com/en-us/library/jj628157.aspx and http://technet.microsoft.com/en-us/library/jj721575.aspx for additional information on VM networks.
Planning for and configuring network optimization
Network optimization refers to two capabilities included with Windows Server 2012 and available on certain network adapters. Specifically, TCP Chimney Offload and virtual machine queue are used for network optimization. VMM detects when these capabilities are available, and the virtual network or virtual switch will reflect their availability.
Virtual machine queue creates a separate network queue for each virtual machine and connects that queue directly to the virtual machine, thus bypassing other layers involved in the processing of network traffic. Adapters that support TCP Chimney Offload perform much of the network processing on the adapter itself, thereby reducing the number of host resources needed for this purpose.
Network optimization is configured at the virtual machine level by adding a network adapter to the virtual machine and selecting the Enable Virtual Network Optimizations check box.
Planning for and implementing Windows Server Gateway
Windows Server Gateway provides routing between virtual and physical networks to facilitate advanced scenarios, such as tenant isolation and virtual private network (VPN) connections between virtual machines in the cloud and those on site. See http://technet.microsoft.com/en-us/library/dn313101.aspx for more information on scenarios for Windows Server Gateway.
Implementing Windows Server Gateway has several requirements, depending on the configuration and need. You’ll need more hardware to run a clustered Windows Server Gateway configuration, for example. See http://technet.microsoft.com/en-us/library/dn423897.aspx for more information on the specific hardware requirements.
 Thought experiment: Configuring virtual switches
Thought experiment: Configuring virtual switches
In this thought experiment, apply what you’ve learned about this objective. You can find an answer in the “Answers” section at the end of this chapter.
You’re configuring network settings for your virtual network. Specifically, you’re configuring virtual switches. You need to configure a switch that enables WSUS virtual machines to connect to Microsoft to obtain updates. You also need to configure a network with a credit card application, and those virtual machines should only be able to communicate with each other.
Discuss the options available for the virtual switch that will facilitate this scenario.
Objective summary
![]() Logical networks are used to abstract the physical network from that used for virtual machines.
Logical networks are used to abstract the physical network from that used for virtual machines.
![]() VMM enables complex network configurations based on the need for the virtual machine network.
VMM enables complex network configurations based on the need for the virtual machine network.
![]() VMM can configure IP address and MAC address pools and create virtual IP addressing and virtual networks for isolated communication.
VMM can configure IP address and MAC address pools and create virtual IP addressing and virtual networks for isolated communication.
![]() Network optimization is a function of the network adapter hardware and, when available, can be configured through VMM.
Network optimization is a function of the network adapter hardware and, when available, can be configured through VMM.
![]() Windows Server Gateway is used to facilitate advanced networking, such as VPN and tenant isolation for virtual machines.
Windows Server Gateway is used to facilitate advanced networking, such as VPN and tenant isolation for virtual machines.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. When creating a logical network, which option needs to be chosen to enable network virtualization?
A. Allow New VM Networks Created In This Logical Network To Use Network Virtualization
B. This Logical Network Can Use Network Virtualization
C. Allow This Logical Network To Be Virtualized
D. This VM Network Can Use Network Virtualization
2. Which of the following are features of network optimization? (Choose all that apply.)
A. TCP Chimney Offload
B. Virtual Network Queue
C. Virtual machine queue
D. TCP Chimney Stack Offload
3. Which of the following is a prerequisite for configuring network virtualization?
A. At least one virtual machine
B. Hyper-V hosts
C. TCP Offload enabled
D. Network adapter support
Objective 3.4: Plan and implement virtualization storage
Virtualization storage is a key element to a successful virtual machine deployment. Understanding the options and choosing the correct solution will help you prepare for this task when you encounter it.
This objective covers how to:
![]() Plan for and configure Hyper-V host clustered storage, including standalone and clustered setup using SMB and CSV
Plan for and configure Hyper-V host clustered storage, including standalone and clustered setup using SMB and CSV
![]() Plan for and configure Hyper-V guest storage, including virtual Fibre Channel, iSCSI, and shared VHDx
Plan for and configure Hyper-V guest storage, including virtual Fibre Channel, iSCSI, and shared VHDx
![]() Plan for storage optimization
Plan for storage optimization
![]() Plan for and implement storage using SMB 3.0 file shares
Plan for and implement storage using SMB 3.0 file shares
Planning for and configuring Hyper-V host clustered storage
Hyper-V can use local storage, such as that directly connected to the server, or remote storage, such as a file share. At a different level, storage support in VMM consists of block storage, such as that provided through logical unit numbers (LUNs) by iSCSI, Fibre Channel, and SAS, and file storage, such as that provided through SMB or NAS. This section examines the basic configuration of Hyper-V storage as well as the objective surrounding SMB 3.0 file shares for Hyper-V storage.
The type of storage available in the organization will determine the planning involved in its configuration. VMM helps to abstract the storage layer for virtual machines and Hyper-V hosts. For example, VMM can create logical units rather than relying on the underlying storage configuration.
Storage can be assigned at the host group level. Therefore, when planning storage you should consider allocating storage according to the needs of the host group. For example, a host group for development servers likely doesn’t need the fastest (and probably most expensive) storage in the organization. Storage classifications, discussed later in this section, can help with the assignment of storage.
Microsoft has identified a workflow for configuration storage in VMM. The workflow consists of the following steps. These steps are prerequisites for adding storage to Hyper-V hosts and clusters.
1. Use the Add Storage Devices Wizard to configure the storage discovery. See the section titled “Configuring SMB and CSV storage” later in this chapter for more details.
2. Assign a classification to the discovered storage based on organizational criteria. See http://technet.microsoft.com/en-us/library/gg610685.aspx for more information.
3. Select a method for creating logical units for use with rapid provisioning. This step is especially important when using rapid provisioning with SAN-based cloning and snapshots. See http://technet.microsoft.com/en-us/library/gg610624.aspx for more information on this step.
4. Provision the logical units using VMM or using a native method for logical unit creation provided by the storage vendor. See http://technet.microsoft.com/en-us/library/gg696973.aspx for more information.
5. Allocate storage to a host group within VMM. See http://technet.microsoft.com/en-us/library/gg610686.aspx for additional details on this step.
One of the more important areas in which you can plan storage for virtual machines is around the classifications. You can create classifications based on your organization’s storage capacity, speed, and availability. For example, your organization may have a large storage area network (SAN) that’s highly available and mirrored across sites. However, space on the SAN is expensive and therefore limited to production servers. You might create a classification that indicates this storage is to be used for production-level purposes.
Note: Awindows PowerShell cmdlet for Adding Storage Providers
The Add-SCStorageProvider Windows PowerShell cmdlet can be used to add storage providers.
Configuring SMB and CSV storage
Selecting Storage Devices from the Add menu of the Fabric workspace reveals the Add Storage Devices Wizard, shown in Figure 3-36. From here, you can add a Windows-based file server or other storage devices to the VMM fabric.
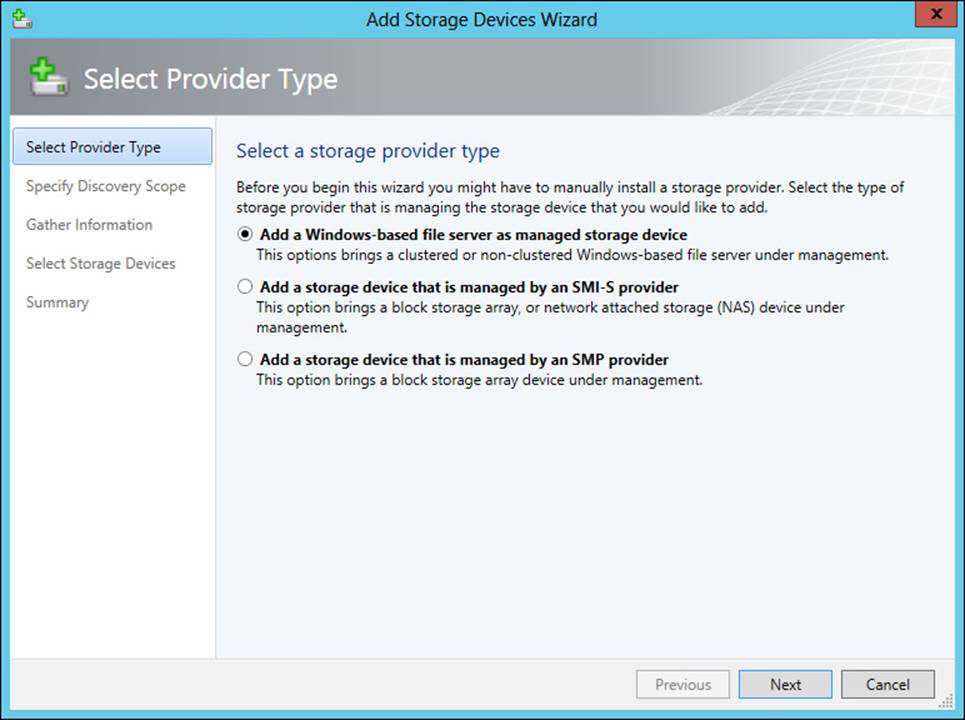
FIGURE 3-36 Configuring a storage device in VMM
The next step is to enter the details of the server on which the storage resides (not depicted here) and then select the SMB share, shown in Figure 3-37.
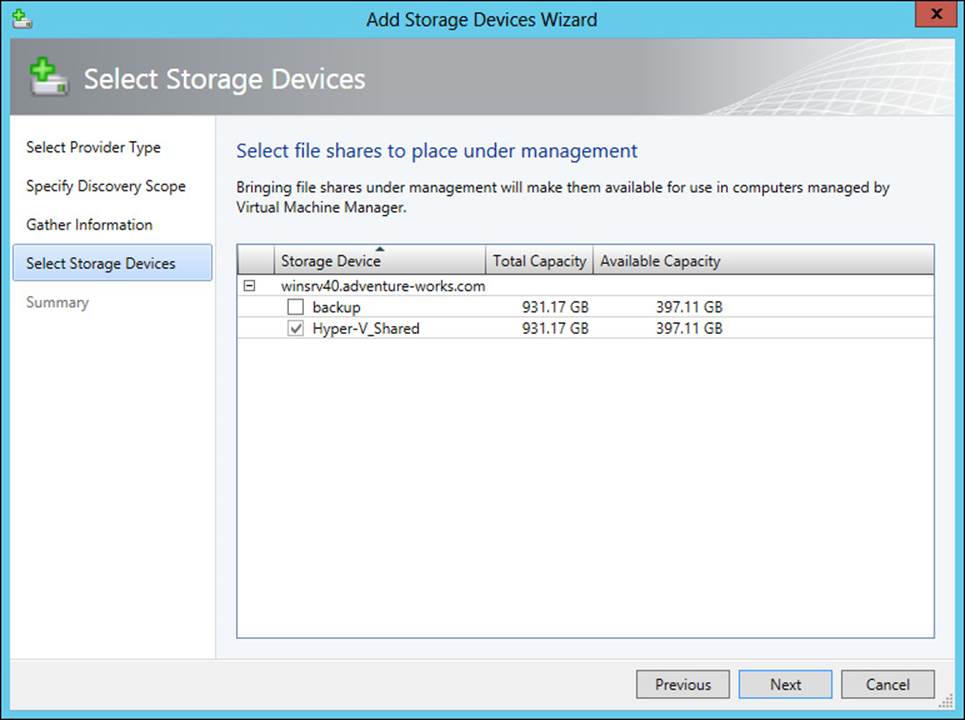
FIGURE 3-37 Choosing a file share
After the storage has been discovered, you create a file share. This step may be confusing for storage devices created from existing SMB shares because there’s already an SMB share exposed by the underlying Windows server. You essentially create another share on top of that storage device. Finally, storage is assigned to hosts or clusters through the host or cluster’s Properties dialog box.
Cluster-shared volumes (CSVs) are also available for use in VMM and enable cluster members to share the same disk. This helps to provide faster failover capabilities, among other advantages. When working with CSVs, there are several tasks similar to those needed when working with other types of storage, such as creation of logical units and so on. You can also convert storage to CSV in VMM by selecting Convert To CSV on the Available Storage tab of a host cluster Properties dialog box.
More Info: SMB and CSV
See http://technet.microsoft.com/en-us/library/gg610696.aspx for more information on configuring logical units for Hyper-V hosts, http://technet.microsoft.com/en-us/library/jj134187.aspx for more information on SMB, and http://technet.microsoft.com/en-us/library/gg610692.aspx for information on using CSV with VMM and Hyper-V.
Planning for and configuring Hyper-V guest storage
Guest storage refers to the storage used by virtual machines. There are several methods for providing this storage, three of which will be covered in this section:
![]() Virtual Fibre Channel
Virtual Fibre Channel
![]() iSCSI
iSCSI
![]() Pass-through disk
Pass-through disk
Like planning for storage in general, planning for guest storage is largely dependent on the available infrastructure. For instance, you need Fibre Channel capabilities to deploy virtual Fibre Channel, so if that’s not available then there’s no need to plan for its use. However, for the exam you should still understand how to add Fibre Channel devices.
Working with virtual Fibre Channel
Fibre Channel is added in the Storage area of the Fabric workspace. Selecting Storage Devices from the Add Resources menu reveals the Add Storage Devices Wizard (seen previously in Figure 3-36). On the Select Provider Type page, shown in Figure 3-36, selecting the Add A Storage Device That Is Managed By An SMI-S Provider option enables the Fibre Channel storage to be added.
More Info: Fibre Channel
The “How to Add and Classify Virtual Fibre Channel Devices in VMM” article on TechNet contains additional information on this process. See http://technet.microsoft.com/en-us/library/dn303340.aspx for the article.
Working with iSCSI
As of System Center 2012 SP1, VMM can manage the iSCSI Target Server functionality in Windows Server 2012. The iSCSI Target Server can be configured using the Add-SCStorageProvider Windows PowerShell cmdlet.
More Info: iSCSI and Windows PowerShell
See http://technet.microsoft.com/en-us/library/jj860422.aspx for limitations and Windows PowerShell cmdlets for iSCSI and VMM.
Working with pass-through disks
Pass-through disks enable Hyper-V to work directly with an underlying physical disk, such as a disk connected directly to the server or through a SAN LUN. Pass-through disks typically offer better performance than a traditional VHD stored on another disk. Pass-through disks are managed at the virtual machine level.
Planning for storage optimization
When considering optimization of storage in VMM, one way guest performance can be improved is by using fixed disks rather than dynamically expanding disks. The underlying disk architecture is vital for performance with SAN-based technologies, typically offering higher performance than file share–based disks for virtual machine storage.
Operations Manager offers Performance and Resource Optimization (PRO) tip integration with VMM, and this integration offers an opportunity for performance improvement as well. Integration with Operations Manager is discussed in the “Manage and maintain a server virtualization infrastructure” section of this chapter.
 Thought experiment: Configuring host and guest storage
Thought experiment: Configuring host and guest storage
In this thought experiment, apply what you’ve learned about this objective. You can find answers to these questions in the “Answers” section at the end of this chapter.
You’ll be configuring both the overall host storage solution and guest storage for your organization. The organization consists of a single data center with three sites, all with high-speed connections. Your organization utilizes a SAN for all disk storage, including physical servers.
1. Discuss the process of configuring host storage from a high level.
2. Discuss the options for guest storage and how those might be configured for optimal performance.
Objective summary
![]() VMM can manage storage for Hyper-V hosts, both standalone and clustered.
VMM can manage storage for Hyper-V hosts, both standalone and clustered.
![]() Storage devices are added (discovered), classified, and provisioned, all from within the Fabric workspace of VMM.
Storage devices are added (discovered), classified, and provisioned, all from within the Fabric workspace of VMM.
![]() VMM can use storage on SMB-based file shares and through SMI-S and SMP.
VMM can use storage on SMB-based file shares and through SMI-S and SMP.
![]() Guest storage for virtual machines is accomplished using virtual Fibre Channel, iSCSI, and pass-through disks.
Guest storage for virtual machines is accomplished using virtual Fibre Channel, iSCSI, and pass-through disks.
![]() Storage optimization is achieved through multiple methods, including use of pass-through disks where appropriate and by utilizing Performance and Resource Optimization (PRO) tips through integration with Operations Manager.
Storage optimization is achieved through multiple methods, including use of pass-through disks where appropriate and by utilizing Performance and Resource Optimization (PRO) tips through integration with Operations Manager.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. Which cmdlet is used to add a storage provider to VMM?
A. Add-SCStorageHost
B. Add-SCStorageProvider
C. Add-VMMStorageHost
D. Add-SCStorageUnit
2. During which phase of host storage provisioning do you apply ratings to discovered storage?
A. Classify
B. Discover
C. Provision
D. Allocate
3. Which of the following is a prerequisite for using virtual Fibre Channel for guest storage?
A. An environment with NAS storage
B. A supported Fibre Channel adapter
C. Appropriate IP addressing
D. iSCSI Target Server role
Objective 3.5: Plan and implement virtual machine movement
Being able to move virtual machines between hosts is a powerful and highly useful feature in an enterprise. The scenario is useful to provide load balancing and disaster recovery, and to migrate a virtual machine to a new host when needed for an upgrade or other feature. This section looks at virtual machine movement and its related exam objectives.
This objective covers how to:
![]() Plan for and configure live and storage migration between Hyper-V hosts
Plan for and configure live and storage migration between Hyper-V hosts
![]() Plan for and manage P2V and V2V
Plan for and manage P2V and V2V
![]() Plan for and implement virtual machine migration between clouds
Plan for and implement virtual machine migration between clouds
Planning for and configuring live and storage migration between Hyper-V hosts and clouds
There are several types of migrations for virtual machines, including live and storage migration, as identified in the exam objectives. There are also quick migrations and quick storage migrations. A quick migration, sometimes called a cluster transfer, is used to migrate virtual machines between cluster nodes using Windows Failover Cluster. Quick migrations involve some downtime because the virtual machine state is saved (hibernated) while the disk is brought online by the other cluster node. Quick storage migrations move the storage for a virtual machine from one storage provider to another. Quick storage migrations also involve downtime.
When planning migrations, the underlying storage and network infrastructure will dictate the available options. If SAN-based infrastructure is not in place, none of the SAN options are available. Obviously, live migrations are preferred for environments where downtime is not acceptable, but live migrations can also consume resources, so setting a concurrency limit (discussed in the section titled “Live migrations” in this chapter) is important.
Also consider the use of snapshots. Migrating a virtual machine that has snapshots can take longer over networks, and the migration may fail if the snapshots are removed but not yet deleted by Hyper-V. Use the Status column in Hyper-V Manager to ensure that the status is not Merge In Progress, or wait until the merge is complete.
More Info: Migrations
See http://technet.microsoft.com/en-us/library/jj628158.aspx for additional information on migrations, including limitations for live migrations.
Network-based storage migrations
When migrating a virtual machine, using network-based storage migrations are the slowest solution. Network migrations use Background Intelligent Transfer Service (BITS) to copy the virtual machine between locations.
You can also perform a manual migration using the Migrate VM Wizard, shown in Figure 3-38.
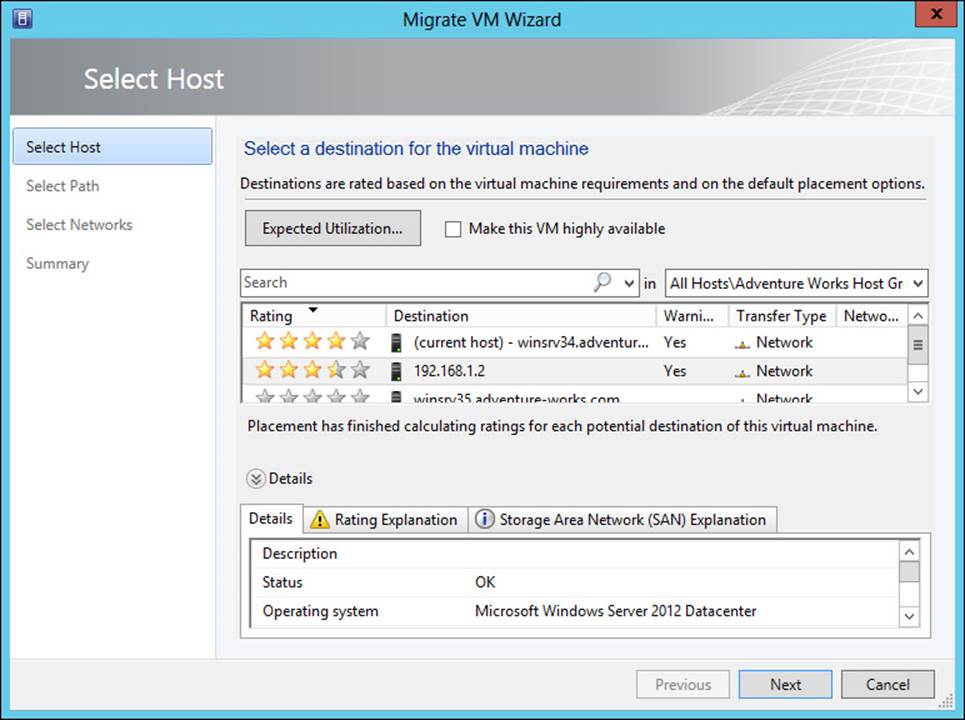
FIGURE 3-38 Performing a migration using the Migrate VM Wizard
More Info: Manual Migration
See http://technet.microsoft.com/en-us/library/jj860432.aspx for step-by-step instructions and options for manual migration.
SAN-based migrations
Though no longer mentioned directly on the newly revised objectives for the Windows Server 2012 R2 exam, SAN migrations are still a viable option for migration. When Hyper-V hosts have access to the LUN on a SAN, a SAN migration can be performed. SAN migrations can transfer virtual machines into and out of a cluster. However, a dedicated LUN (not using CSV) needs to be available when transferring out of a cluster. SAN migrations are supported with the following infrastructure:
![]() Fibre Channel
Fibre Channel
![]() iSCSI SAN
iSCSI SAN
![]() N_Port ID (NPID) Virtualization
N_Port ID (NPID) Virtualization
Using SANs with VMM involves certain configuration steps depending on the needs of the environment and the type of SAN deployed. For example, older SAN technology may require Virtual Disk Service (VDS) be installed. See http://technet.microsoft.com/en-us/library/gg610594.aspx for details on rapid provisioning, which contains insight into creating templates that can be used for SAN migrations.
SAN migrations are used by default when migrating virtual machines using the Migrate VM Wizard. This can be changed on the Select Path page of the Migrate VM Wizard by selecting Transfer Over The Network Even If A SAN Transfer Is Available.
Live migrations
As its name implies, a live migration takes place without downtime. As of System Center 2012 SP1, live migrations can be performed both within and outside of a failover cluster, including between standalone hosts and between nodes in different clusters, though the hosts must be domain joined. System Center 2012 SP1 also enables live storage migration and live virtual system migration, which migrates both the machine and underlying storage at the same time. Finally, live migrations can also take place simultaneously, and there’s a configurable limit on the number of migrations that can take place at once.
Migration settings are configured at the host level within the Migration Settings page of the host’s Properties dialog box, shown in Figure 3-39.
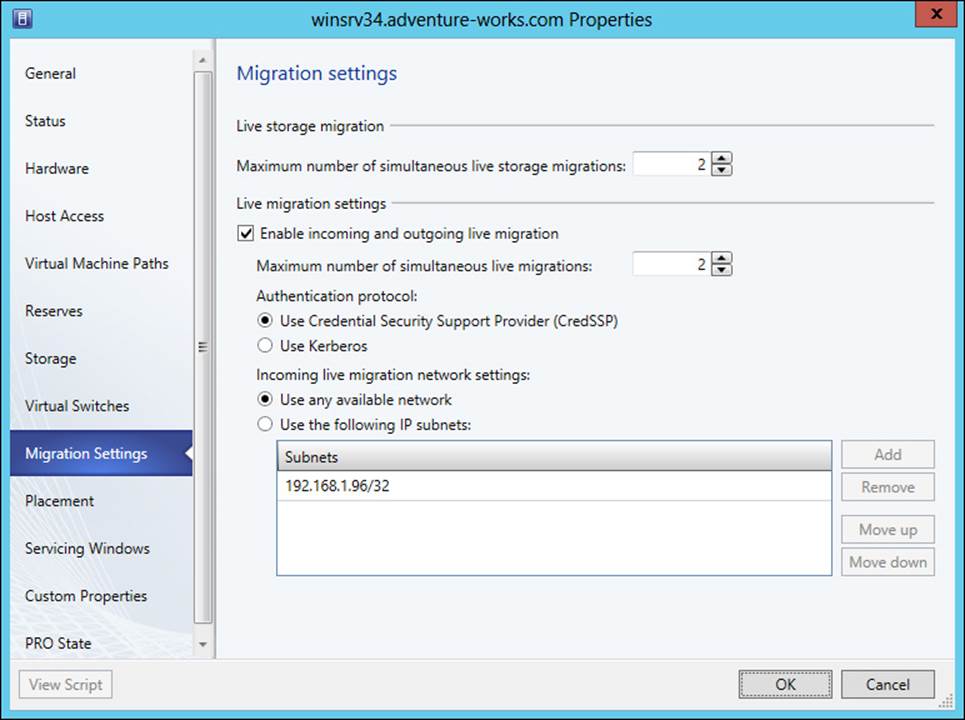
FIGURE 3-39 Live migration settings in VMM
When manually performing a migration, if the hosts can see the same SMB 3.0 file share, the Live transfer type is available for the migration. There are three settings related to live migrations available with System Center 2012 R2. These include compression and using SMB as a transport, both of which are configured within the Advanced Features section of Hyper-V Live Migration settings on the Hyper-V host.
More Info: Live Migrations
See http://technet.microsoft.com/en-us/library/jj860434.aspx for more information on live migrations.
Planning for and managing P2V and V2V
Physical to virtual (P2V) and virtual to virtual (V2V) migrations help facilitate management of virtual machines by VMM. P2V typically occurs when organizations move from physical to virtualized infrastructure. When planning P2V, there are certain limitations and other considerations. First among those limitations is that P2V has been removed from Virtual Machine Manager 2012 R2. Therefore, if you have a scenario that involves Virtual Machine Manager 2012 R2, you can automatically know that P2V is not an option. However, other scenarios may appear, in which case it’s helpful to also know other limitations and considerations for P2V. The physical computer being migrated needs to have at least 512 MB of RAM and an ACPI BIOS while also residing in a nonperimeter network. The physical computer also cannot have encrypted volumes or volumes larger than 2,048 GB, and cannot be on Itanium architecture.
P2V migrations can be performed in online or offline mode. In online mode (the default for most situations), the physical computer being migrated remains online while Volume Shadow Copy Service (VSS) is used to create a copy of NTFS volumes and data from VSS-aware applications. Offline mode, which is recommended for domain controller migrations and is required for FAT volumes, takes the physical computer offline, boots it into the Windows Preinstallation Environment (Windows PE), and then creates a clone of the physical volumes into a virtual hard disk (VHD).
P2V migrations to VMM are compatible with numerous Windows-based operating systems, as denoted in Table 3-3.
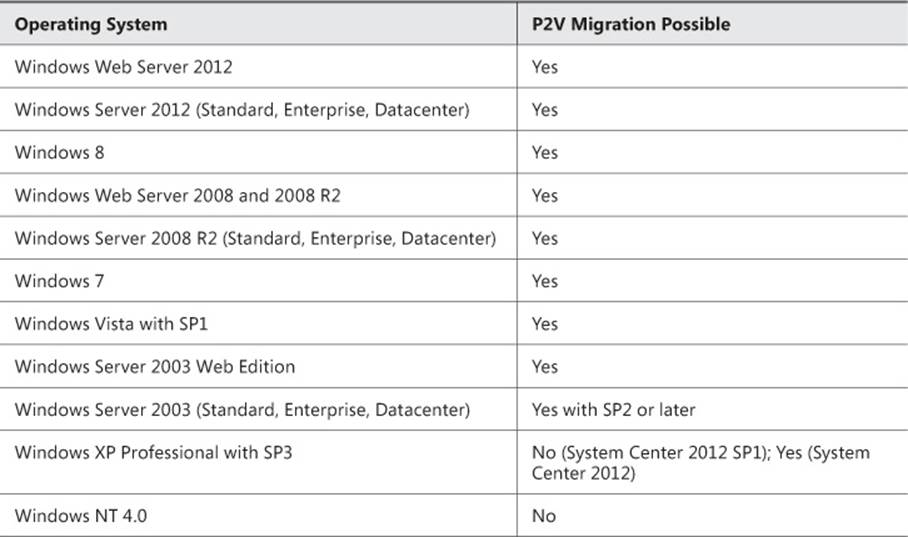
TABLE 3-3 P2V operating system support
Migrating a virtual machine for P2V is accomplished from within the VMs and Services workspace in VMM by selecting Convert Physical Machine from the Create Virtual Machine drop-down list. Doing so invokes the Convert Physical Server (P2V) Wizard, shown in Figure 3-40.
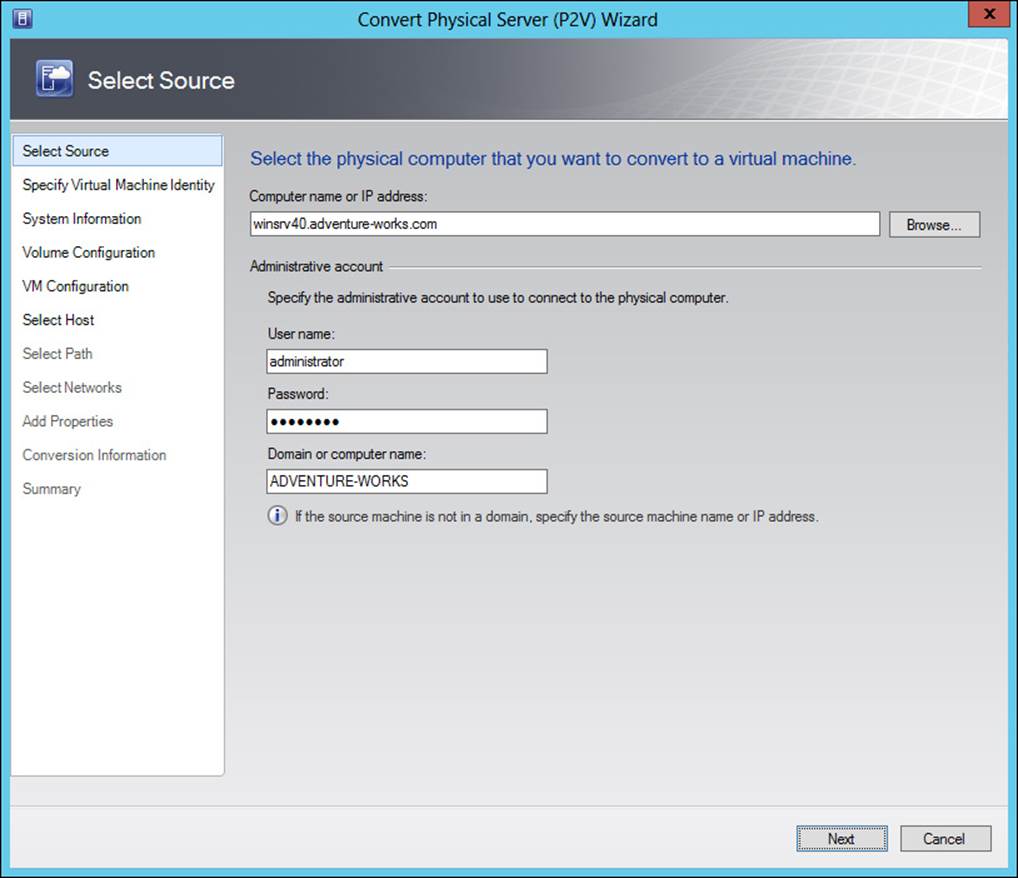
FIGURE 3-40 Beginning the conversion process
More Info: Performing a P2V Migration
See http://technet.microsoft.com/en-us/library/hh427286.aspx for a walkthrough of a P2V migration.
A virtual to virtual (V2V) migration is done for conversions of existing virtual machines hosted in Citrix XenServer and VMware vCenter. Like P2V migrations, there are certain limitations to V2V scenarios. Specifically, virtual machines hosted on XenServer can’t be migrated in a V2V manner, but rather need to be converted using P2V methods. Like P2V methods, XenServer migrations can only be performed on Windows-based virtual machines.
When using System Center 2012, V2V conversions from VMware can be accomplished if the VMware server is running ESX/ESXi 3.5 Update 5 or ESX/ESXi 4.0, 4.1, or 5.1. System Center 2012 SP1 only supports migrations from ESX/ESXi 4.1 and 5.1. Additionally, VMware tools must be uninstalled from the virtual machine before beginning the migration.
Like P2V conversions, beginning a V2V conversion is accomplished in the VMs and Services workspace by selecting Convert Virtual Machine from the Create Virtual Machine drop-down list.
More Info: VMware V2V
See http://technet.microsoft.com/en-us/library/gg610672.aspx for a step-by-step migration process for V2V from VMware.
 Thought experiment: Migrating computers to virtual machines
Thought experiment: Migrating computers to virtual machines
In this thought experiment, apply what you’ve learned about this objective. You can find an answer in the “Answers” section at the end of this chapter.
You’ll be migrating a set of physical computers for a legacy Windows NT 4.0 domain. The domain has two domain controllers running Windows NT 4.0 and three Windows XP Professional computers.
Describe the options for migrating these computers to virtual machines, along with limitations therein.
Objective summary
![]() Several types of migrations are available for virtual machines, including SAN-based, live, network, quick, and quick storage.
Several types of migrations are available for virtual machines, including SAN-based, live, network, quick, and quick storage.
![]() SAN migrations can be performed with the appropriate underlying architecture, including Fibre Channel, iSCSI SAN, and NPID.
SAN migrations can be performed with the appropriate underlying architecture, including Fibre Channel, iSCSI SAN, and NPID.
![]() P2V migrations help facilitate a virtualized infrastructure.
P2V migrations help facilitate a virtualized infrastructure.
![]() V2V migrations can be accomplished from VMware ESX hosts, but XenServer hosts follow a P2V path.
V2V migrations can be accomplished from VMware ESX hosts, but XenServer hosts follow a P2V path.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. Which mode of migration is recommended for domain controllers in a P2V scenario?
A. Online
B. Offline
C. SAN
D. Cluster
2. Which migration type results in minimal or no downtime?
A. Network
B. Quick
C. Offline
D. Live
3. Simultaneous live migrations are configured in which area of VMM?
A. Per host
B. Per virtual machine
C. Per SAN
D. For each virtual machine template
Objective 3.6: Manage and maintain a server virtualization infrastructure
This entire chapter is dedicated to planning and implementing the infrastructure necessary for virtualization. However, a few areas of the infrastructure can be further enhanced. These areas include integration with System Center Operations Manager, resource optimization, and the creation of service templates, among others. This section looks at some of those additional features that can help with an enterprise virtualization infrastructure.
This objective covers how to:
![]() Manage dynamic optimization and resource optimization
Manage dynamic optimization and resource optimization
![]() Integrate Operations Manager with System Center Virtual Machine Manager and System Center Service Manager
Integrate Operations Manager with System Center Virtual Machine Manager and System Center Service Manager
![]() Update virtual machines in libraries
Update virtual machines in libraries
![]() Plan for and implement backup and recovery of virtualization infrastructure by using System Center Data Protection Manager (DPM)
Plan for and implement backup and recovery of virtualization infrastructure by using System Center Data Protection Manager (DPM)
Managing dynamic optimization and resource optimization
Dynamic optimization performs live migrations of virtual machines within host clusters that are configured for such migrations. Additionally, there’s a power optimization setting that can turn off hosts when they’re not needed. This section focuses on optimization through VMM.
Note: Dynamic Optimization
As discussed later in this chapter, many of the same functions previously performed using Performance and Resource Optimization (PRO) are also performed with dynamic optimization.
Dynamic optimization and power optimization are configured on a host group basis. The Administrator or Delegated Administrator role is necessary to configure these optimizations, though delegated administrators are limited to configurations for their predefined host groups. From the Fabric workspace, selecting Dynamic Optimization from a host group’s Properties dialog box reveals the screen shown in Figure 3-41.
FIGURE 3-41 Configuring dynamic optimization for a host group
You can configure the aggressiveness with which VMM will attempt to optimize the virtual machine load within a group. The three basic settings for aggressiveness are High, Medium (the default setting), and Low. There are intermediary settings as well, between Medium and High and between Medium and Low.
A High aggressiveness setting means that optimization will occur more frequently when VMM deems that a small gain might be had by doing so. On the other hand, Low aggressiveness means that VMM will perform fewer migrations and only do so when there’s a large performance gain or a large resource utilization imbalance between hosts within the host group.
Note: Default Frequency
The default frequency is 10 minutes.
There are four configurable resource thresholds after which dynamic optimization may occur. These include:
![]() CPU
CPU
![]() Memory
Memory
![]() Disk I/O
Disk I/O
![]() Network I/O
Network I/O
These thresholds can be thought of as available resources, or the resources that the host must keep available at all times to keep dynamic optimization from occurring. Figure 3-41 shows a Medium aggressiveness and 30 percent CPU utilization. This means that if the available CPU on a host falls below 30 percent, it becomes a candidate for dynamic optimization of its virtual machines.
You can also configure VMM to perform dynamic optimization automatically, and you can set the interval in which the dynamic optimization will occur. If you don’t configure automatic dynamic optimization, you can manually trigger the optimization through the Fabric workspace.
Power optimization migrates virtual machines and turns off the host when not needed. It’s important to recognize that power optimization applies to hosts and not virtual machines. Power optimization requires a quorum be maintained for host clusters. If the host cluster was created outside of VMM, then at least four hosts will remain active at all times and not subject to power optimization.
Power optimization is scheduled to run at all times but can be configured through the Settings dialog box, shown in Figure 3-42, found within the Power Optimization area of the Dynamic Optimization page.
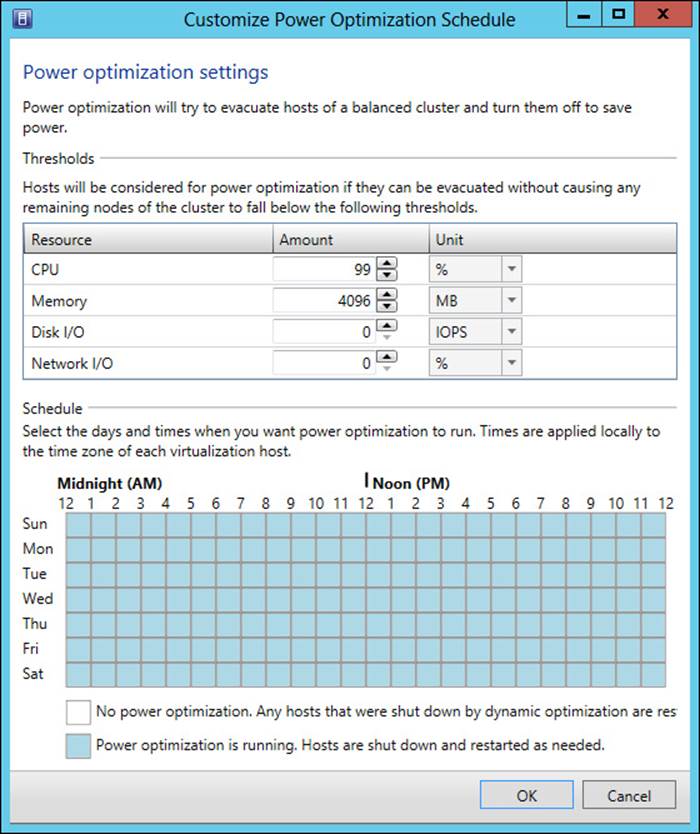
FIGURE 3-42 The Power Optimization Settings page in VMM
More Info: Dynamic Optimization and Power Optimization
See http://technet.microsoft.com/en-us/library/gg675109.aspx and http://technet.microsoft.com/en-us/library/gg675118.aspx for more information on dynamic and power optimization.
Integrating Operations Manager with VMM and Service Manager
Integrating Operations Manager with VMM involves installing the Operations Manager console on the VMM management server, installing Operations Manager agents on the VMM management server, virtual machines, and hosts (as appropriate), and importing management packs. Integration of Operations Manager and VMM was covered in Chapter 1. This objective focuses on taking advantage of that integration through the use of PRO tips.
Dynamic optimization replaces some of the PRO functionality previously achieved with integration with Operations Manager. Specifically, the PRO CPU Utilization and PRO Memory Utilization monitors for hosts that are no longer used. However, Operations Manager and PRO tips are still quite useful for VMM. This section looks at integration of Operations Manager and enabling PRO tips.
Working with PRO tips
Once integration is complete, you can manage the connection between Operations Manager and VMM from within the Settings workspace of VMM. In the Operations Manager Settings dialog box, you can enable the connection, as well as enable PRO, enable Maintenance Mode, and test PRO. See Figure 3-43 for the Operations Manager Settings dialog box.
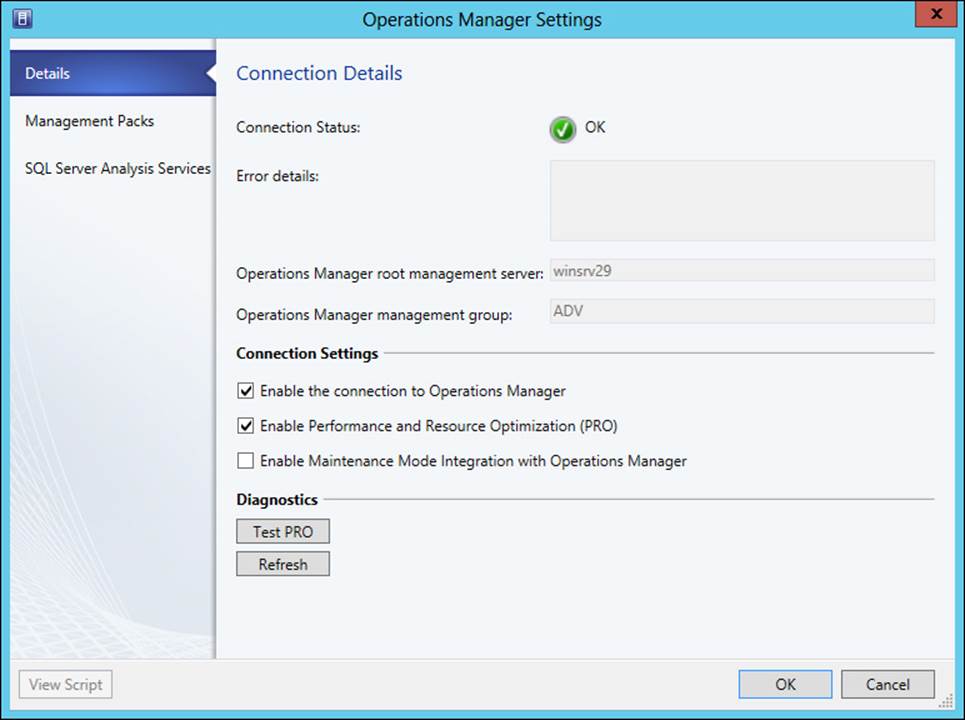
FIGURE 3-43 The Connection Details page in VMM
Clicking Test PRO reveals a PRO tip alert like the one shown in Figure 3-44.
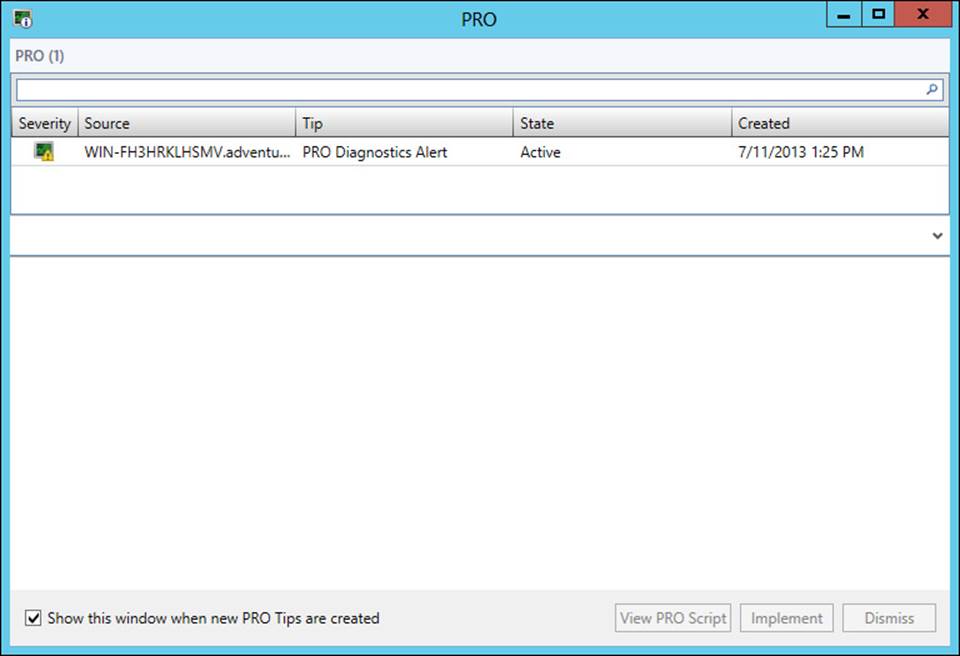
FIGURE 3-44 A test PRO alert in VMM
If the test PRO alert isn’t generated, you may find some useful debug information in the Jobs workspace in VMM. You can also use the Windows PowerShell cmdlet Test-SCPROTip to generate the test PRO tip.
PRO can be configured for host groups, host clusters, clouds, services, hosts, and virtual machines. With System Center 2012, you can change the configuration of PRO for each type of monitor being used. For instance, you may want to remediate certain PRO monitors but just view others.
Configuring PRO is accomplished in the Properties dialog box of a given host or host group. Figure 3-45 shows an example of two host monitors, one configured for Monitor and one for Remediate.
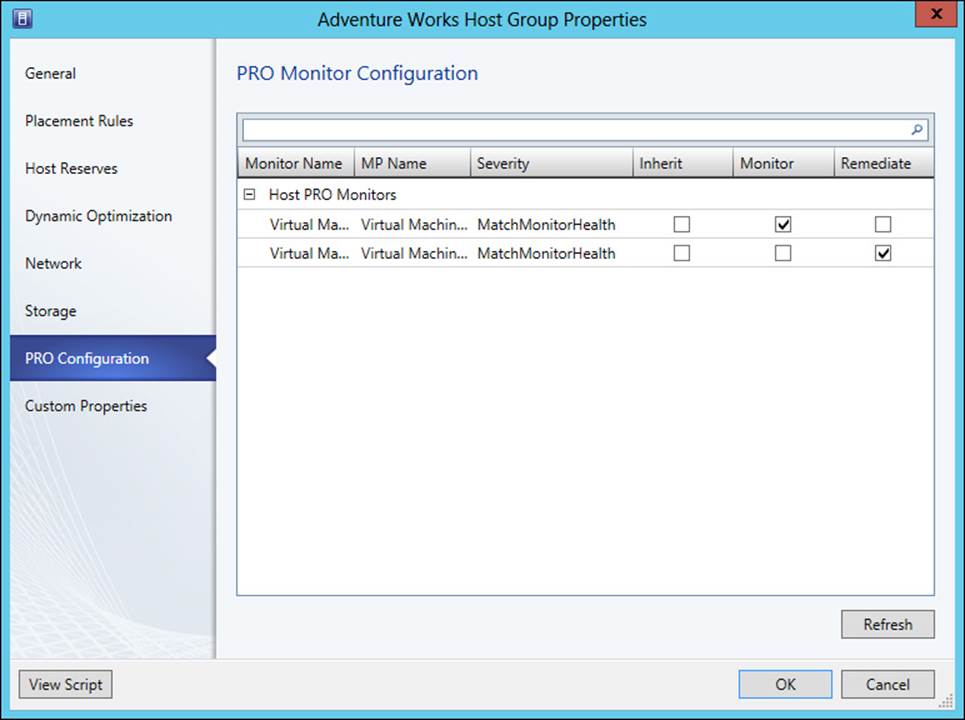
FIGURE 3-45 The PRO Monitor Configuration page for a host group
Integration of System Center Service Manager and Operations Manager is accomplished through the use of connectors. Connectors for Operations Manager can be used for alerts and configuration items. Connectors are created in Service Manager through the Connectors pane in the Administration workspace. When Create Connector is selected, the choice of whether to create an Operations Manager alert connector or an Operations Manager configuration item (CI) connector will be among the available connectors.
A wizard is used to create both types of connectors. When creating an alert connector, you’ll define the routing rule containing the criteria for the alert, shown in Figure 3-46.
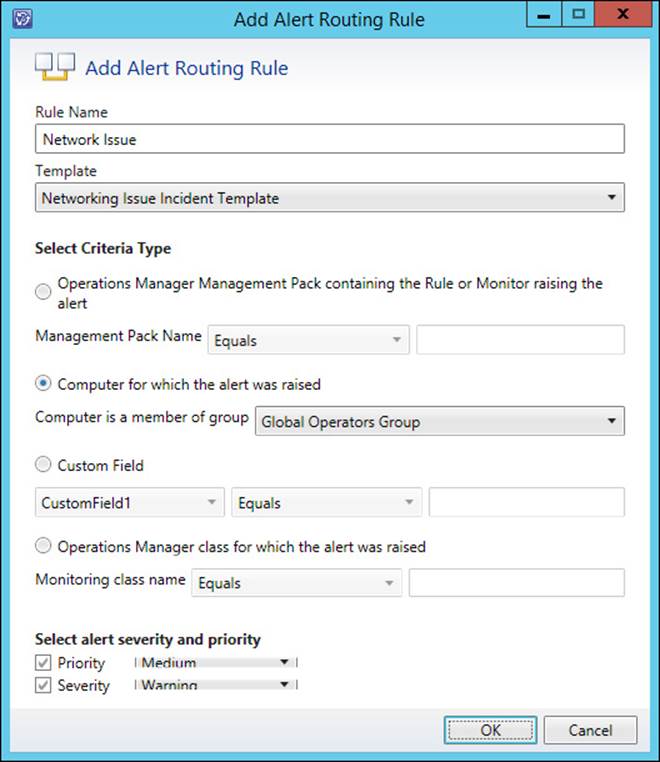
FIGURE 3-46 Creating an alert routing rule for Operations Manager
Alternatively, when creating a CI connector, the configuration items are chosen as part of the wizard, as shown in Figure 3-47.
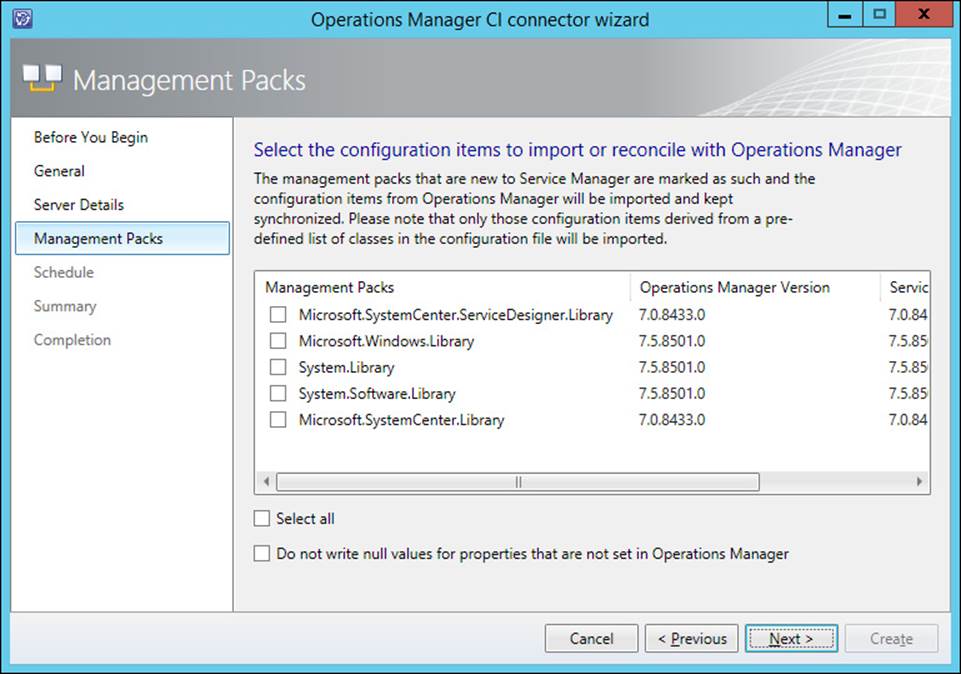
FIGURE 3-47 Selecting configuration items for a CI connector
More Info: Operations Manager Connectors
See http://technet.microsoft.com/en-us/library/hh524325.aspx for more details on creating connectors.
Update virtual machine images in libraries
As discussed in the first objective in this chapter, libraries are used to store common objects that can be used across a virtual environment, including images for virtual machines. Library objects can be versioned, which assists in managing updates.
Figure 3-48 shows a library resource called test.iso that’s currently in release 3.
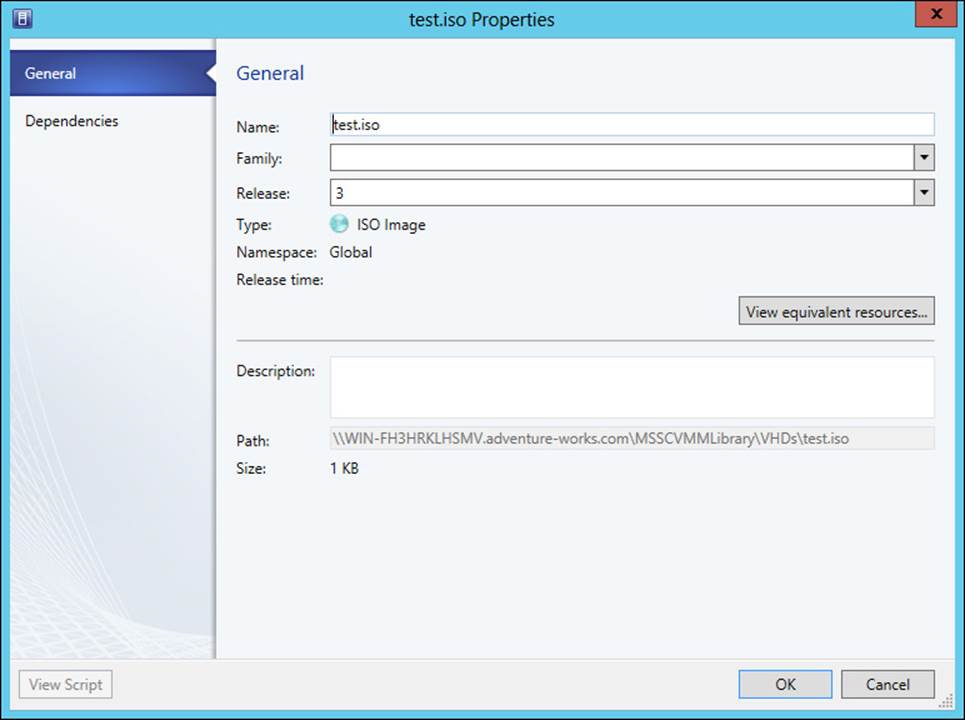
FIGURE 3-48 Viewing a library resource in VMM
You can view the dependencies of the resource on the Dependencies tab. Doing so enables you to see any other objects that are currently using the resource.
Updating the library resource is typically accomplished outside of VMM. For instance, updating a template or a new ISO image would be done independent of VMM. You can then use VMM to update the release and other details.
More Info: Configuring the VMM Library
See “Configuring the VMM Library” for details on the configuration options for the VMM library. It’s available at http://technet.microsoft.com/library/gg610598.aspx.
Planning for and implementing backup and recovery of virtualization infrastructure using DPM
Data Protection Manager (DPM), part of System Center 2012, can be used to protect virtual machines, whether the virtual machine is hosted on a standalone Hyper-V server or a cluster. To do so, DPM installs a protection agent on the host servers (and on the file server in the case of SMB 3.0 storage). DPM provides real-time, live backups of virtual machines and doesn’t require downtime. DPM can send backups to disk, Windows Azure backup, or tape. When backed up to tape, recovery will take much longer than a disk-based backup. Therefore, planning for DPM usage in this scenario involves determining the needs for rapid recovery. One option would be to use disk-based storage for recent backups and tape-based storage for long-term storage for archival purposes.
There are limitations to the live online backups, however. If any of these limitations apply, then offline backups are performed. If the virtual machine has any dynamic disks or disks that are not NTFS, then an offline backup is the only option. If the Backup Integration Service (Volume Snapshot) isn’t running or if the machine itself is offline, then the live backup won’t be able to run. When running DPM in a cluster environment, if the Cluster Resource Group is not available, then DPM will also need to perform a backup in offline mode. In many instances, DPM works in conjunction with VSS to perform its online backups. This means that the File Server VSS Agent role service should be installed on the file servers providing shared storage, such as SMB 3.0 file shares.
The storage requirements for DPM are an important part of planning the deployment. Each DPM server can provide backups for up to 800 virtual machines. You can arrive at a rough estimate of the storage requirement simply by calculating the total allocated storage for each virtual machine.
Regardless of the storage and other factors in use, the DPM protection agent needs to be installed. This can be installed using the DPM console or manually. The manual option needs to be used for nondomain computers or those where a firewall or other limitation prevents the DPM console method from working.
One additional concept for DPM concerns protection groups. You can create logical groupings in DPM to gather similar resources or group together resources that should be treated the same from a data-protection standpoint.
More Info: Configuring DPM
See http://technet.microsoft.com/en-us/library/hh757970.aspx for more information on configuring DPM for various storage scenarios and for live migrations.
 Thought experiment: Dynamic optimization
Thought experiment: Dynamic optimization
In this thought experiment, apply what you’ve learned about this objective. You can find an answer in the “Answers” section at the end of this chapter.
Your virtual infrastructure consists of 56 virtual machines running Windows Server 2012, running across eight Hyper-V hosts. You’ve configured dynamic optimization along with live migrations between Hyper-V hosts. You’ve found that there has been an unacceptable increase in network traffic, and you believe it’s being caused by dynamic optimization.
Discuss some things you can do to adjust dynamic optimization.
Objective summary
![]() Operations Manager can be integrated with VMM to provide PRO tips.
Operations Manager can be integrated with VMM to provide PRO tips.
![]() Service templates can be versioned, and new versions can be applied to running services, thereby applying the updates to the services.
Service templates can be versioned, and new versions can be applied to running services, thereby applying the updates to the services.
![]() The library stores objects that are used within a VMM environment. Library objects can be versioned and updated.
The library stores objects that are used within a VMM environment. Library objects can be versioned and updated.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
1. Which of the following are valid resource thresholds for dynamic optimization?
A. CPU
B. Memory
C. Disk I/O
D. Available Disk
2. Which command generates a test PRO tip when configuring VMM and Operations Manager integration?
A. Set-SCPROTip
B. Test-SCPROTip
C. Gen-SCPROTip
D. Set-OpsPROTip
3. To which of the following does power optimization apply?
A. Virtual machines
B. Hosts
C. Grids
D. Library objects
Answers
This section contains the solutions to the thought experiments and answers to the lesson review questions in this chapter.
Objective 3.1: Thought experiment
Solving this thought experiment can involve two user roles—the main Administrator role and the Application Administrator (Self-Service) user role. Because there’s only one infrastructure team, you shouldn’t need a Tenant or Fabric Administrator role.
Objective 3.1: Review
1. Correct answer: B
A. Incorrect: Memory is a valid host reserve setting.
B. Correct: Disk status is not a valid host reserve setting.
C. Incorrect: CPU percentage is a valid host reserve setting.
D. Incorrect: Disk space is a valid host reserve setting.
2. Correct answer: B
A. Incorrect: Fabric Administrator cannot perform this operation.
B. Correct: Administrator is the only role that can add XenServer hosts and clusters.
C. Incorrect: Self-Service users cannot perform this operation.
D. Incorrect: Tenant Administrators cannot perform this operation.
3. Correct answer: A
A. Correct: Port 443 is the default port for this communication.
B. Incorrect: 5150 is not the default port.
C. Incorrect: 5297 is not the default port.
D. Incorrect: 3389 is not the default port and is typically used for Remote Desktop.
Objective 3.2: Thought experiment
There are four settings related to dynamic memory: Startup Memory, Minimum Memory, Maximum Memory, and Memory Buffer Percentage. There’s also an ancillary setting, Memory Weight, that defines how the host allocates memory resources.
Because users are reporting slow application start times, it’s not likely that the Startup Memory is to blame, since that relates to the virtual machine itself. You might be tempted to increase the Minimum Memory, and if the host has enough memory, this is a reasonable step. However, another option would be to increase the Memory Buffer Percentage, because that will keep additional memory in reserve based on the amount of RAM currently in use on the VM.
Objective 3.2: Review
1. Correct answer: D
A. Incorrect: High is an option for priority.
B. Incorrect: Do not restart automatically is an option for priority.
C. Incorrect: Medium is an option for priority.
D. Correct: Automatic is not an option for priority.
2. Correct answer: A
A. Correct: The host is out of physical memory is one of the criteria for use of Smart Paging.
B. Incorrect: The virtual machine needs to be in a restart state, not coming from an Off state.
C. Incorrect: Smart Paging is not used for virtual machines that are running.
D. Incorrect: The Dynamic Memory Smart Paging option does not exist.
3. Correct answer: D
A. Incorrect: A virtual machine that has already been deployed can be used.
B. Incorrect: An existing template in the library can be used.
C. Incorrect: A virtual hard disk in the library can be used.
D. Correct: A predefined operating system image cannot be used for this purpose.
Objective 3.3: Thought experiment
There are three options for communicating with virtual switches: external, internal, and private. The WSUS server will need to use a virtual switch with external access. The virtual machines involved in the credit card application will need to use a private virtual switch. The internal virtual switch enables communication between the virtual machine and any other virtual machine on the host or the host itself.
Objective 3.3: Review
1. Correct answer: A
A. Correct: Allow New VM Networks Created In This Logical Network To Use Network Virtualization is the correct option for this question.
B. Incorrect: This Logical Network Can Use Network Virtualization is not an available option.
C. Incorrect: Allow This Logical Network To Be Virtualized is not an available option.
D. Incorrect: This VM Network Can Use Network Virtualization is not an available option.
2. Correct answers: A, C
A. Correct: TCP Chimney Offload is one of the ways in which VMM can optimize network traffic.
B. Incorrect: Virtual Network Queue is not an option.
C. Correct: Virtual machine queue is one of the ways in which VMM can optimize network traffic.
D. Incorrect: TCP Chimney Stack Offload is not an option.
3. Correct answer: B
A. Incorrect: Virtual machines are not a prerequisite for network virtualization configuration.
B. Correct: Hyper-V hosts are required to use network virtualization.
C. Incorrect: TCP Offload is not related to this question.
D. Incorrect: Network adapter support is not related to this question.
Objective 3.4: Thought experiment
1. The high-level process for configuring storage is identified by Microsoft as:
A. Discover storage.
B. Classify storage.
C. Select logical unit method.
D. Provision storage.
E. Allocate storage.
2. Guest storage can use virtual Fibre Channel or pass-through disks, depending on how the hosts are configured. Both options offer good performance, since they would both be using the underlying SAN.
Objective 3.4: Review
1. Correct answer: B
A. Incorrect: Add-SCStorageHost is not used to add a storage provider to VMM.
B. Correct: Add-SCStorageProvider
C. Incorrect: Add-VMMStorageHost is not used to add a storage provider to VMM.
D. Incorrect: Add-SCStorageUnit is not used to add a storage provider to VMM.
2. Correct answer: A
A. Correct: Classify is the phase of host storage provisioning where you apply ratings to discovered storage
B. Incorrect: Discover is not the phase of host storage provisioning where you apply ratings to discovered storage.
C. Incorrect: Provision is not the phase of host storage provisioning where you apply ratings to discovered storage.
D. Incorrect: Allocate is not the phase of host storage provisioning where you apply ratings to discovered storage.
3. Correct answer: B
A. Incorrect: An environment with NAS storage s not a prerequisite for using virtual Fibre Channel for guest storage.
B. Correct: A supported Fibre Channel adapter
C. Incorrect: Appropriate IP addressing s not a prerequisite for using virtual Fibre Channel for guest storage.
D. Incorrect: iSCSI Target Server role s not a prerequisite for using virtual Fibre Channel for guest storage.
Objective 3.5: Thought experiment
Because the domain controllers run Windows NT 4.0, you can’t perform a P2V migration. You must upgrade the servers to a later, supported operating system before performing the migration. Assuming that the Windows XP Professional computers are running at least SP3, they can be migrated.
Objective 3.5: Review
1. Correct answer: B
A. Incorrect: Online is not the recommended mode of migration for domain controllers in a P2V scenario.
B. Correct: Offline migration is the recommended mode of migration for domain controllers in a P2V scenario.
C. Incorrect: SAN is not the recommended mode of migration for domain controllers in a P2V scenario.
D. Incorrect: Cluster is not the recommended mode of migration for domain controllers in a P2V scenario.
2. Correct answer: D
A. Incorrect: Network migrations are the slowest solution.
B. Incorrect: Quick migrations involve some downtime.
C. Incorrect: In offline migration, the physical computer is taken offline, resulting in some downtime.
D. Correct: Live migration results in minimal or no downtime.
3. Correct answer: A
A. Correct: Simultaneous live migrations are configured at the host level.
B. Incorrect: Simultaneous live migrations are not configured per virtual machine.
C. Incorrect: Simultaneous live migrations are not configured per SAN.
D. Incorrect. Simultaneous live migrations are not configured for each virtual machine template.
Objective 3.6: Thought experiment
First, you can disable dynamic optimization automatic live migrations to see whether that has any effect on the network traffic. If the network traffic goes down with dynamic optimization automatic live migrations disabled, then it’s time to look for additional configuration settings to help.
Dynamic optimization has several settings that can be configured to define its behavior. Notably, you can configure how aggressive dynamic optimization is. The aggressiveness setting will determine the amount of benefit needed for VMM to undertake a dynamic optimization operation. Additionally, you can configure the interval on which dynamic optimization is run. Finally, you can configure the available resources on each host or as a group.
Objective 3.6: Review
1. Correct answers: A, B, C
A. Correct: CPU is a valid threshold.
B. Correct: Memory is a valid threshold.
C. Correct: Disk I/O is a valid threshold.
D. Incorrect: Available Disk is not a valid threshold.
2. Correct answer: B
A. Incorrect: Set-SCPROTip is not a valid command.
B. Correct: Test-SCPROTip generates a test PRO diagnostic.
C. Incorrect: Gen-SCPROTip is not a valid command.
D. Incorrect: Set-OpsPROTip is not a valid command.
3. Correct answer: B
A. Incorrect: Power optimization does not apply to virtual machines.
B. Correct: Power optimization applies to hosts.
C. Incorrect: Grids are not valid objects in VMM.
D. Incorrect: Power optimization does not apply to library objects.