Exam Ref 70-417 Upgrading Your Skills to Windows Server 2012 R2 (2014)
Chapter 7. Configure a network policy server infrastructure
Network Access Protection (NAP), as you know, is a Windows Server technology that enforces health requirements on client computers as they attempt to connect to a company network. These health requirements can relate to the status of software updates, of anti-virus protection, of host firewall status, or of spyware protection. NAP was first introduced in Windows Server 2008.
In a move that surprised many, Microsoft announced with the release of Windows Server 2012 R2 that NAP has been officially deprecated (set on a path to obsolescence). Some improved alternative to NAP might very well appear in a future version of Windows Server, but for now, you still have to deal with NAP on the 70-417 exam. Questions about NAP are not being phased out.
Although NAP doesn’t include any significant new features in Windows Server 2012 or Windows Server 2012 R2, one important new feature, System Health Validator (SHV) Multi-configuration, did appear in Windows Server 2008 R2. This new feature falls within “Configure Network Access Protection,” the one NAP objective listed for the 70-417 exam.
Objectives in this chapter:
![]() Objective 7.1: Configure Network Access Protection (NAP)
Objective 7.1: Configure Network Access Protection (NAP)
Objective 7.1: Configure Network Access Protection
NAP can be deployed in many different configurations, depending on whether it is enforced through DHCP, virtual private networks (VPNs), IPSec, Remote Desktop Services Gateway, or 802.1x. It’s important to review how NAP enforcement is configured.
Most of NAP has remained the same since Windows Server 2008, but there is one new feature in NAP that falls within the Configure Network Access Protection objective: SHV Multi-configuration.
This section covers the following topics:
![]() How NAP works
How NAP works
![]() Configuring NAP
Configuring NAP
![]() SHV Multi-configuration
SHV Multi-configuration
How NAP works
First, let’s review some basic NAP concepts. When a client computer first attempts to connect to a network, its first point of contact could be a DHCP server, a VPN server, or another type of device. In a NAP infrastructure, this first point of contact is configured as a NAP enforcement point, and the NAP client is configured to report its system status (called a statement of health or SoH) to this NAP enforcement point.
The NAP enforcement point uses the RADIUS protocol to forward the SoH and connection request to a Network Policy Server (NPS). The NPS server uses connection request policies to determine whether the client connection request will be processed by NAP. If evaluated by NAP, the client request is next processed by network policies, which provide potential instructions about whether to allow the connection, block the connection, or allow restricted access only to a remediation server or set of servers. Of all the instructions defined in various network policies, only one set is applied to a connection: that of the first network policy whose conditions match the connection request.
Figure 7-1 shows an example of a simple NAP infrastructure.
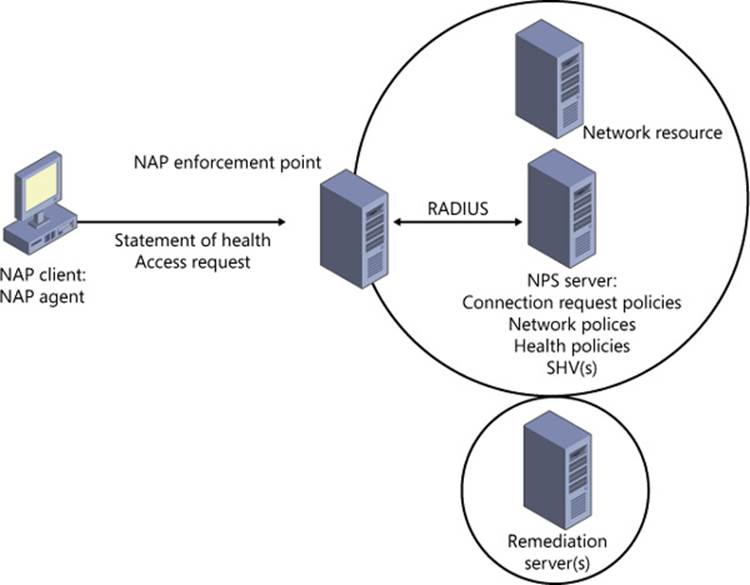
FIGURE 7-1 A NAP infrastructure
 Exam Tip
Exam Tip
NAP enforcement types can have particular requirements that affect a NAP infrastructure. For example, both VPN and 802.1x enforcement require the NAP server to have installed a computer certificate to support server authentication through Protected Extensible Authentication Protocol (PEAP). This certificate typically is provided by a local enterprise certificate authority (CA). Another example is that IPsec enforcement requires you to install at least one Health Registration Authority (HRA) server in addition to the other NPS components. These HRA servers also require a computer certificate and comprise what is called a trusted server group for NAP IPsec clients.
Network policies usually include health policies as matching conditions. Health policies, for their part, determine whether a NAP client matches an indicated state of failing or passing a health check according to an SHV. Windows Server includes one built-in SHV, Windows Security Health Validator.
Besides the network policies that assess the health compliance of NAP clients, an additional network policy is normally also included to match clients that are not NAP-capable. These network policies include a condition named “NAP-Capable” (meaning “NAP capability status”) whose value is configured as “Computer is non NAP-capable.” (NAP-capable computers are ones that send an SoH.) Network policies created to match non-NAP-capable clients may be configured either to allow or block the connection request.
 Exam Tip
Exam Tip
A network policy can include both a Health Policy condition and a NAP-Capable condition. If you configure the NAP-Capable condition with a value of “Computer is NAP-capable”, then the network policy checks for health requirements only on clients that send an SoH.
The following list further describes these components involved in NAP processing:
![]() Connection request policies Rules that determine whether a connection request will be processed by network policies.
Connection request policies Rules that determine whether a connection request will be processed by network policies.
![]() Network policies Rules that compare the health of connection requests to health policy statements and accordingly allow access, block access, or allow remediated access to those requests. Network policies include conditions and condition values configured to match different types of clients. The Health Policy condition uses a health policy check to match a client. The NAP-Capable condition matches clients based on whether they have sent an SoH. The MS-Service class condition is used to match particular DHCP scopes.
Network policies Rules that compare the health of connection requests to health policy statements and accordingly allow access, block access, or allow remediated access to those requests. Network policies include conditions and condition values configured to match different types of clients. The Health Policy condition uses a health policy check to match a client. The NAP-Capable condition matches clients based on whether they have sent an SoH. The MS-Service class condition is used to match particular DHCP scopes.
![]() Health policies A statement of health compliance or noncompliance according to a particular SHV.
Health policies A statement of health compliance or noncompliance according to a particular SHV.
![]() SHVs A software component that performs a particular set of tests about the safety of a client connection.
SHVs A software component that performs a particular set of tests about the safety of a client connection.
![]() Windows SHVs The default SHV and only SHV built into Windows Server.
Windows SHVs The default SHV and only SHV built into Windows Server.
 Exam Tip
Exam Tip
Make sure you understand network policies and conditions well for the 70-417 exam.
Figure 7-2 illustrates how these components could work together in a particular example of NAP processing.
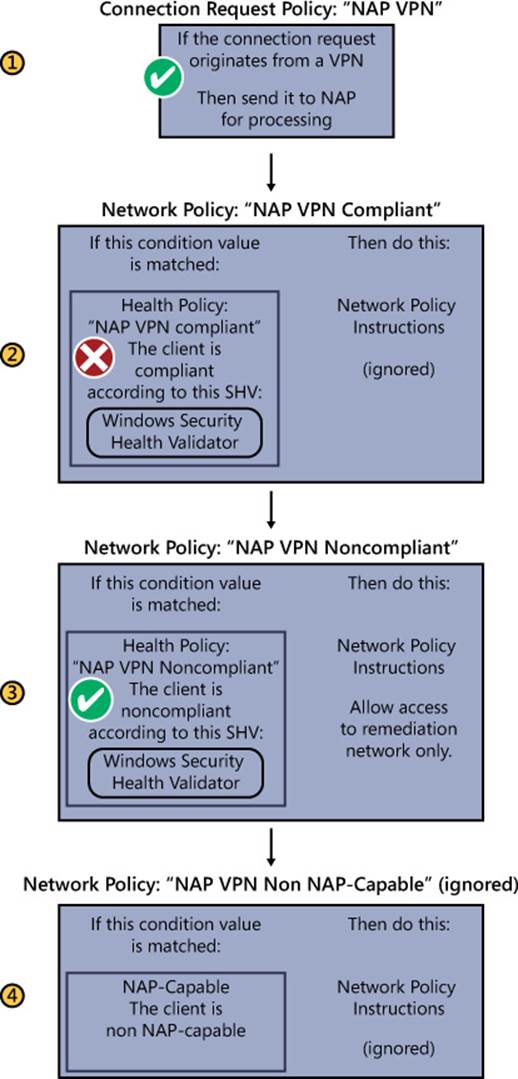
FIGURE 7-2 The first network policy that accurately describes a stated health policy condition about a NAP client provides the instructions about how to handle the NAP client request
Configuring NAP
The procedures for configuring the various NAP enforcement types all differ from each other, but they do share common steps. In general, you first configure the NAP server by using the Configure NAP Wizard. You start this wizard by clicking Configure NAP in the details pane when the NPS (Local) node is selected in the console, as shown in Figure 7-3.
FIGURE 7-3 Configuring the NAP server
You use the Configure NAP Wizard to specify the NAP enforcement type you want to implement and to create the required connection request policies, network policies, and health policies. After running the wizard, you create security groups for NAP and configure Group Policy. You can also modify the policies created by the wizard, for example, by adding an MS-Service class condition to match the profile name you have assigned a DHCP scope on your DHCP server. This condition would accompany the Health Policy condition automatically added by the Configure NAP Wizard, as shown in Figure 7-4.
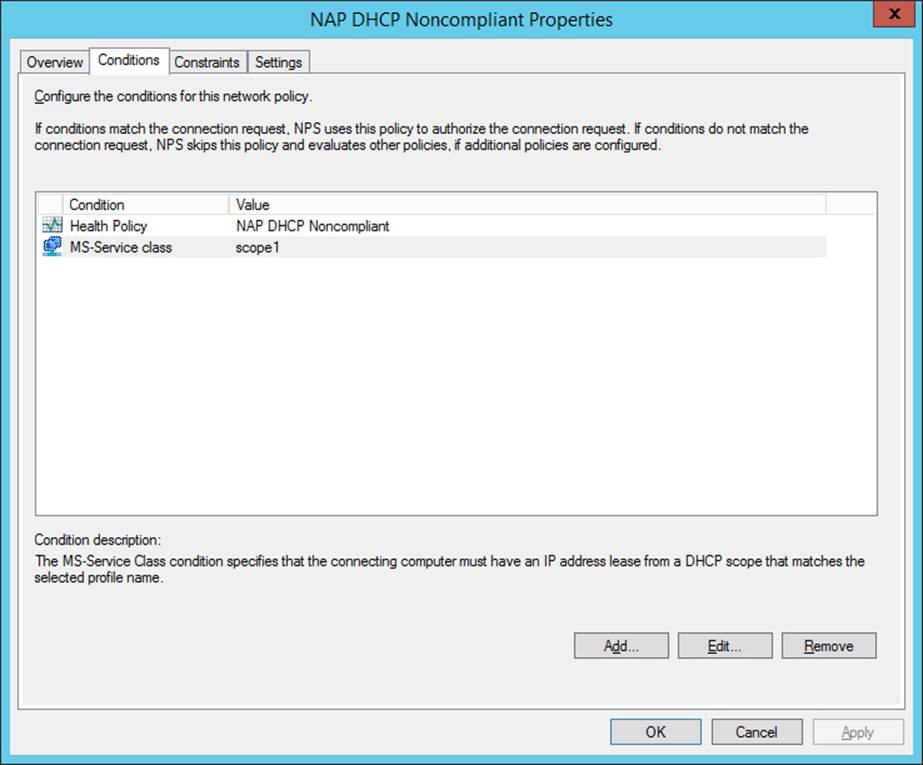
FIGURE 7-4 The matching conditions for a particular network policy named NAP DHCP Noncompliant
 Exam Tip
Exam Tip
Remember that the network policy conditions shown in Figure 7-4 are used to match a state of health compliance for a particular DHCP scope. To use the MS-Service class condition shown you have to assign the scope a profile name (here, “scope1”) in the scope properties on the DHCP server. The MS-Service class condition lets you apply different network policies (and therefore different levels of access protection) to different scopes.
More Info
For more information about configuring the various NAP enforcement types, visit http://technet.microsoft.com/en-us/library/dd314175(v=ws.10).aspx.
 Exam Tip
Exam Tip
In particular, configuring NAP with IPsec enforcement requires extra steps beyond those stated above. Although the configuration steps haven’t changed since Windows Server 2008, it’s recommended that you review IPsec-specific NAP topics such as HRAs and HRA automatic discovery as they are described at http://technet.microsoft.com/en-us/library/dd125312(v=ws.10).aspx.
SHV multi-configuration
Windows Server 2008 allowed you to configure just one set of health tests for each SHV. As a result, an NPS server couldn’t normally adjust its health checks to suit different NAP client types.
This limitation could sometimes present a problem. In some scenarios, you might prefer to apply different health checks to different enforcement methods, computers, or users. For example, you might want to require all VPN-connected computers to have their antivirus software both enabled and up-to-date but require local DHCP-based connections to have their antivirus software only enabled. To meet such a requirement in Windows Server 2008, you normally needed to use two NPS servers.
In Windows Server 2008 R2 and later, however, you can now create multiple configurations for each SHV. After you create additional configurations beyond the default configuration, you can specify which SHV configuration you want to use for a particular health policy. Figure 7-5shows an example of multiple configurations created for the built-in SHV, Windows Security Health Validator.
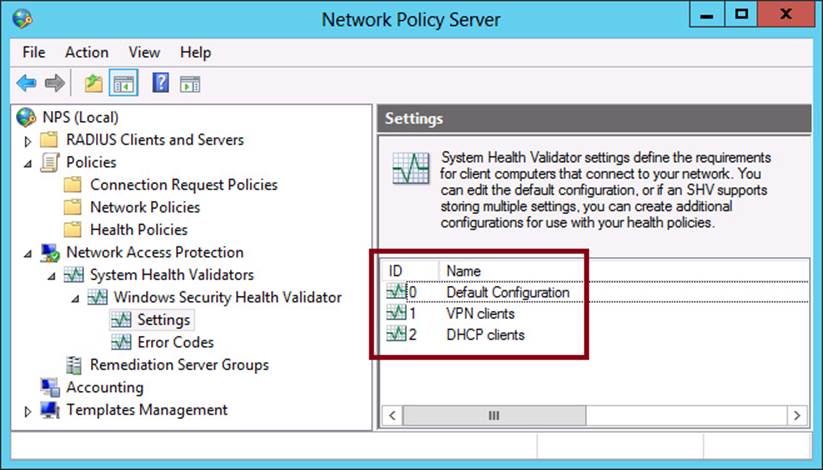
FIGURE 7-5 An SHV with three configured sets of health requirements
Default configuration
Since Windows Server 2008 R2, a Settings node now appears in the Network Policy Server console beneath the default Windows Security Health Validator (and beneath any additional SHVs you have installed that are also compatible with multiple configurations). When you select the Settings node, only the Default Configuration appears by default. This configuration can’t be deleted or renamed.
Creating additional SHV configurations
To create an additional configuration for an SHV, perform the following steps. (These steps demonstrate the procedure using the built-in Windows Security Health Validator as the SHV.)
1. In the Network Policy Server console tree, navigate to Network Access Protection\System Health Validators\Windows Security Health Validator\Settings.
2. Right-click Settings and then click New, as shown in Figure 7-6.
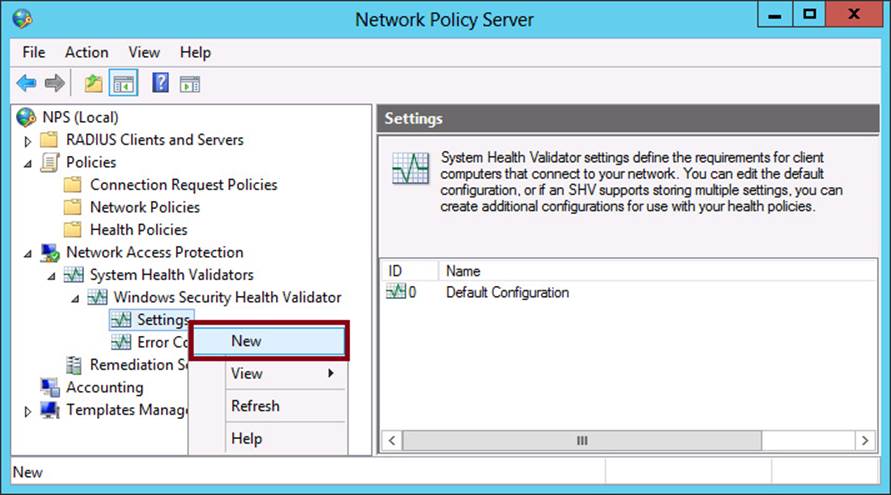
FIGURE 7-6 Creating an additional SHV configuration
3. In the Configuration Friendly Name dialog box, type a name for the new configuration and then click OK.
4. In the Windows Security Health Validator window, shown in Figure 7-7, specify the desired system health requirements for the configuration.
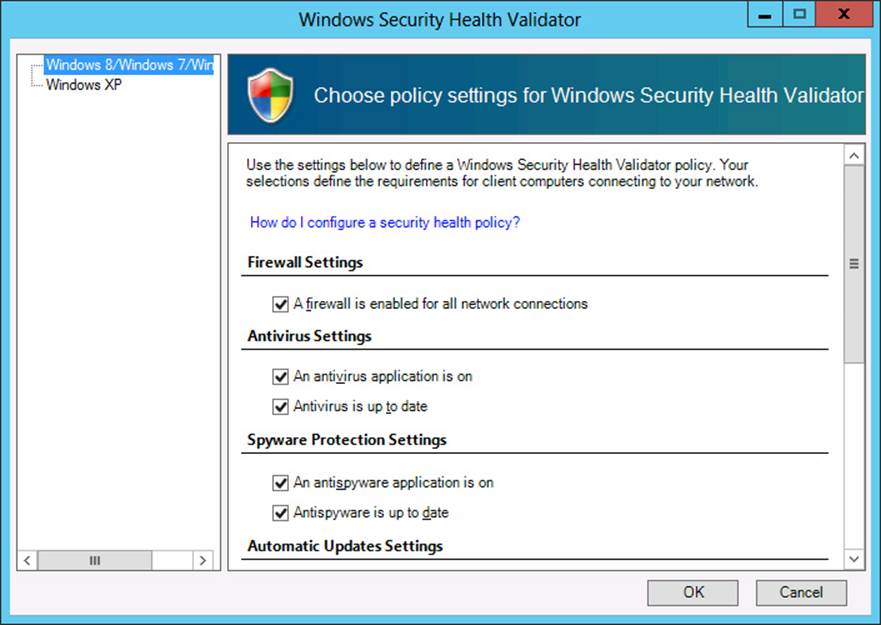
FIGURE 7-7 Specifying settings for a new SHV configuration
You can enable any of the following health checks:
![]() A Firewall Is Enabled For All Network Connections If this check box is selected, the client computer must have a firewall that is registered with Windows Security Center and that is enabled for all network connections.
A Firewall Is Enabled For All Network Connections If this check box is selected, the client computer must have a firewall that is registered with Windows Security Center and that is enabled for all network connections.
![]() An Antivirus Application Is On If this check box is selected, the client computer must have an antivirus application installed, registered with Windows Security Center, and turned on.
An Antivirus Application Is On If this check box is selected, the client computer must have an antivirus application installed, registered with Windows Security Center, and turned on.
![]() Antivirus Is Up To Date If this check box is selected, the client computer can also be checked to ensure that the antivirus signature file is up-to-date.
Antivirus Is Up To Date If this check box is selected, the client computer can also be checked to ensure that the antivirus signature file is up-to-date.
![]() An Antispyware Application Is On If this check box is selected, the client computer must have an antispyware application installed, registered with Windows Security Center, and turned on. (Not available for Windows XP.)
An Antispyware Application Is On If this check box is selected, the client computer must have an antispyware application installed, registered with Windows Security Center, and turned on. (Not available for Windows XP.)
![]() Antispyware Is Up To Date If this check box is selected, the client computer can also be checked to ensure that the antispyware signature file is up-to-date. (Not available for Windows XP.)
Antispyware Is Up To Date If this check box is selected, the client computer can also be checked to ensure that the antispyware signature file is up-to-date. (Not available for Windows XP.)
![]() Automatic Updating Is Enabled If this check box is selected, the client computer must be configured to check for updates from Windows Update. You can choose whether to download and install them.
Automatic Updating Is Enabled If this check box is selected, the client computer must be configured to check for updates from Windows Update. You can choose whether to download and install them.
![]() Security Update Settings Use this section to define health checks related to security updates. If you select the option to restrict access for clients that do not have all available security updates installed, clients will be designated as noncompliant if they do not meet this requirement according to the criteria you specify. You can specify the minimum severity level required for the updates and the minimum number of hours allowed since the client has checked for security updates. You can also choose require clients to use Windows Server Update Services (WSUS), Windows Update, or both sources.
Security Update Settings Use this section to define health checks related to security updates. If you select the option to restrict access for clients that do not have all available security updates installed, clients will be designated as noncompliant if they do not meet this requirement according to the criteria you specify. You can specify the minimum severity level required for the updates and the minimum number of hours allowed since the client has checked for security updates. You can also choose require clients to use Windows Server Update Services (WSUS), Windows Update, or both sources.
 Exam Tip
Exam Tip
Remember that the two anti-spyware checks are not available for Windows XP.
Assigning an SHV configuration to a health policy
To assign different health checks to different NAP client types, you can assign different SHV configurations to the health policies created for these different client types. For example, you might want to assign one SHV configuration to your VPN client health policies and another to your DHCP client health policies.
It’s best to use the Configure NAP Wizard to generate your health policies automatically. The health policies created by the Configure NAP Wizard will be assigned appropriate names and be set as conditions in new, correctly configured network policies. Normally there will be two health policies for each client type, one compliant and one noncompliant. For example, if you run the Configure NAP Wizard twice and specify first VPN and then DHCP as the network connection methods, the wizard will generate the four health policies shown in Figure 7-8. For each client type, the noncompliant health policy serves as a matching condition for clients that do not pass one of the health checks.
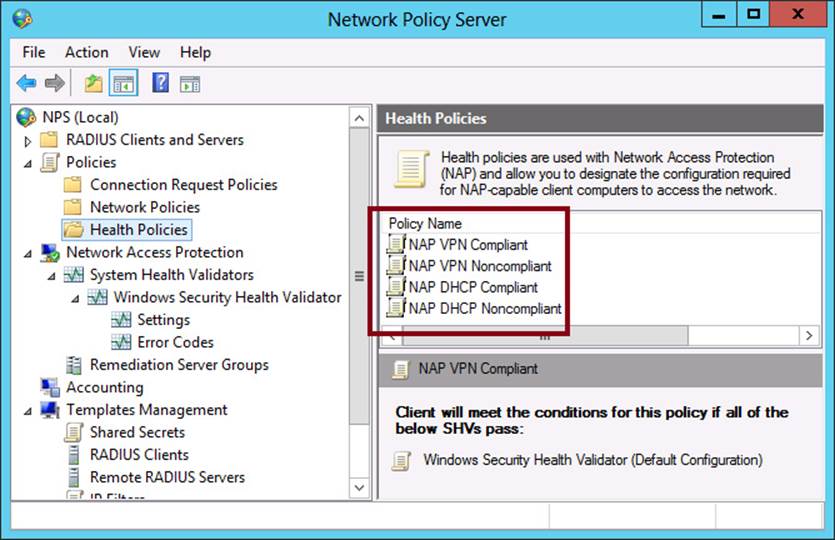
FIGURE 7-8 The Configure NAP Wizard creates a compliant and noncompliant health policy for each network connection method
If you want to assign a custom SHV configuration to a certain type of client, the only thing you have to do after running the Configure NAP Wizard is to modify the properties of the newly created health policies. You want to specify the same SHV configuration for both the compliant and noncompliant versions of the same NAP client type (for example, VPN or DHCP).
By default, when a new health policy is created, the Default Configuration of the SHV is used to define the health checks for that health policy. To assign a nondefault SHV configuration instead, perform the following steps:
1. In the Network Policy Server console, navigate to Policies\Health Policies and then double-click the name of the health policy that you want to modify.
2. On the Settings tab, in the SHVs Used In This Health Policy list, click the drop-down arrow in the Setting column for the Windows Security Health Validator SHV to see a list of available configurations. (Figure 7-9 shows an example.)
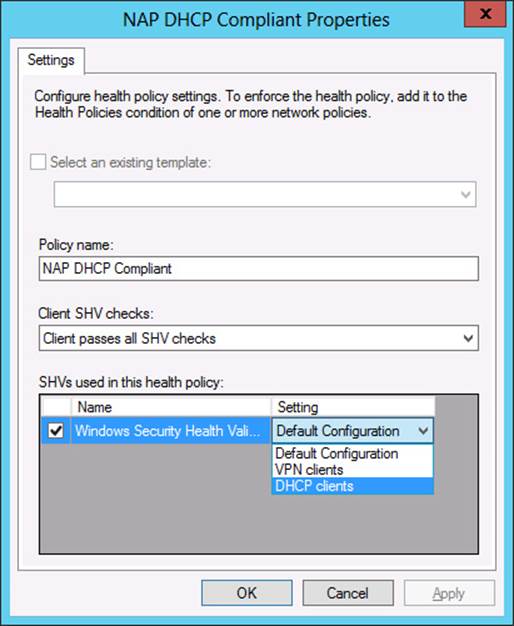
FIGURE 7-9 Assigning an SHV configuration to a health policy
3. Select the desired configuration in the Setting drop-down list and then click OK.
Objective summary
![]() NAP is a technology that enforces health requirements on client computers as they attempt to connect to a network.
NAP is a technology that enforces health requirements on client computers as they attempt to connect to a network.
![]() The NAP feature most likely to be tested is SHV Multi-configuration. This feature first appeared in Windows Server 2008 R2. With SHV Multi-configuration, you can define different sets of health checks for a single SHV. You might use this feature to assign a higher health standard for certain types of NAP clients, such as VPN clients.
The NAP feature most likely to be tested is SHV Multi-configuration. This feature first appeared in Windows Server 2008 R2. With SHV Multi-configuration, you can define different sets of health checks for a single SHV. You might use this feature to assign a higher health standard for certain types of NAP clients, such as VPN clients.
![]() After you create a new configuration for an SHV, you can assign that configuration to health policies. The configuration is applied to a particular NAP client type if you modify the health policies created for that client type.
After you create a new configuration for an SHV, you can assign that configuration to health policies. The configuration is applied to a particular NAP client type if you modify the health policies created for that client type.
![]() NAP has not changed much since Windows Server 2008, so you should be prepared to answer some of the same types of questions about this feature that you saw when you last earned your certification.
NAP has not changed much since Windows Server 2008, so you should be prepared to answer some of the same types of questions about this feature that you saw when you last earned your certification.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. You have deployed NAP in your network with VPN enforcement. You have deployed a single NPS on a computer running Windows Server 2012 R2 and are using Windows Security Health Validator as the only SHV.
Through your NAP policies, VPN clients that are evaluated as noncompliant are allowed access only to a set of remediation servers.
You now want to implement NAP with DHCP enforcement. However, you only want to log noncompliant DHCP clients. You don’t want to block noncompliant DHCP clients from accessing any part of the network.
What should you do?
A. Create a new configuration for the SHV for the DHCP clients.
B. Install an additional SHV and configure it for the DHCP clients.
C. Modify the default NAP DHCP connection request policy.
D. Modify the default NAP DHCP Noncompliant network policy.
2. You have deployed NAP in your network with VPN enforcement. You have deployed a single NPS on a computer running Windows Server 2012 R2 and are using Windows Security Health Validator as the only SHV. Your VPN clients are allowed only restricted access to the network if either security updates or virus definitions are not up-to-date.
You now want to implement NAP with DHCP enforcement. However, you want to use NAP to ensure only that automatic updates and antivirus software are enabled on the DHCP client.
What should you do?
A. Create a new configuration for the SHV for the DHCP clients.
B. Install an additional SHV and configure it for the DHCP clients.
C. Modify the default NAP DHCP connection request policy.
D. Modify the default NAP DHCP Noncompliant network policy.
3. You have been testing a new deployment of NAP in your network. NAP is currently configured so that VPN clients with antivirus software that is not up-to-date log their status with the NPS. These clients are currently not blocked from network access.
You now want to change your NAP configuration so that the access of the same VPN clients is now restricted to a set of remediation servers on the company network.
How can you achieve this goal?
A. Modify the NAP VPN Compliant network policy.
B. Modify the NAP VPN Noncompliant network policy.
C. Modify the NAP VPN Compliant health policy.
D. Modify the NAP VPN Noncompliant health policy.
 Thought experiment: Configuring NAP at Fabrikam
Thought experiment: Configuring NAP at Fabrikam
You work as a network administrator for Fabrikam.com. A month ago, you began testing NAP on VPN clients. You configured the Windows Security Health Validator to determine whether VPN clients had antivirus software enabled. In your current configuration, clients that are determined to be noncompliant simply report their status. They are not denied access to the network.
In the month since you implemented NAP, you have successfully remediated the client computers that have reported their antivirus application as disabled. You now are ready to move beyond the testing and want to modify your configuration to enforce a stricter NAP policy. You can find the answers to these questions in the “Answers” section.
1. Currently, your NAP policies determine only whether an antivirus application is enabled on the client. You now want to add a second health check, to ensure that a firewall is enabled on the client. You also want to ensure that the client firewall is automatically enabled if it is determined to be in a disabled state. How can you achieve this?
2. You want to completely block access to VPN clients that are determined to be infected. How can you achieve this without blocking other clients?
3. You want to assign additional security update health checks to users who are members of the Finance group who connect through a VPN. How can you achieve this?
Answers
This section contains the answers to the Objective Review and the Thought Experiment.
Objective 7.1: Review
1. Correct answer: D
A. Incorrect: An SHV configuration does not affect how a client request is handled. It is used only to perform health checks on a client.
B. Incorrect: A new SHV would not determine whether a client connection is allowed or blocked. That behavior is determined by network policies.
C. Incorrect: Connection request policies do not determine how noncompliant client requests are handled. They determine whether connection requests are evaluated by NAP.
D. Correct: The Configure NAP Wizard creates a NAP DHCP Noncompliant policy that determines how noncompliant DHCP client requests are handled. To allow noncompliant DHCP clients to access the network and simply log the noncompliance, you need to modify the properties of this policy.
2. Correct answer: A
A. Correct: You can create an additional configuration for the SHV that performs only the desired checks on DHCP clients. You then need to assign this configuration to the health policies created for DHCP clients.
B. Incorrect: You don’t need to install an additional SHV. The built-in SHV includes the health checks you need. You need only to create a second configuration of the built-in SHV.
C. Incorrect: A connection request policy doesn’t determine which particular health checks are performed. It determines whether a connection request is evaluated by NAP.
D. Incorrect: A network policy doesn’t allow you to specify particular health checks to be performed. It specifies a health policy that in turn specifies a SHV configuration. To modify which health checks are performed, you need to change the SHV configuration.
3. Correct answer: B
A. Incorrect: You don’t want to change how compliant VPN clients are handled. You want to change how noncompliant VPN clients are handled.
B. Correct: A network policy determines how compliant or noncompliant connection requests are handled. In this case, you want to change how noncompliant VPN clients are handled. To achieve your goal, modify the NAP Enforcement setting on the Settings tab of the NAP VPN Noncompliant network policy. Change the setting from Allow Full Network Access to Allow Limited Access.
C. Incorrect: A health policy doesn’t change how the connection requests from compliant or noncompliant clients are handled. It changes only how connection requests are evaluated.
D. Incorrect: A health policy doesn’t change how the connection requests from compliant or noncompliant clients are handled. It changes only how connection requests are evaluated.
Thought experiment
1. Modify the Windows Security Health Validator policy so that it verifies that a firewall is enabled for all network connections. Next, in the network policy that matches the VPN clients that are noncompliant, select the option on the Settings tab to enable auto-remediation of client computers.
2. Create a new health policy that specifies the client SHV check as Client Reported As Infected By One Or More SHVs. Create a new network policy that specifies the new health policy as a condition, and configure the new network policy to deny access. Move the new network policy to the top of the list of network policies.
3. First run the Configure NAP Wizard and specify VPN as the connection method and the Finance group as the user group to which the policy should apply. Next, create a second configuration for the Windows Security Health Validator that performs a check of security updates in the manner you wish. Finally, attach the new configuration of the Windows Security Health Validator to the new health policies just created by the Configure NAP Wizard.