Exam Ref 70-417 Upgrading Your Skills to Windows Server 2012 R2 (2014)
Chapter 8. Configure and manage Active Directory
This domain is inherited from Exam 70-411: Administering Windows Server 2012. Two of the four original objectives from that domain are officially listed for the 70-417 exam: Configure Domain Controllers and Maintain Active Directory. More important for our upgrade exam purposes, these objectives together include just two new features that have appeared since Windows Server 2008: domain controller cloning and the Active Directory Recycle Bin.
Objectives in this chapter:
![]() Objective 8.1: Configure domain controllers
Objective 8.1: Configure domain controllers
![]() Objective 8.2: Maintain Active Directory
Objective 8.2: Maintain Active Directory
Objective 8.1: Configure domain controllers
Our interest in “configuring domain controllers” is quite narrow here. Although you might see a few questions on the 70-417 exam that tests only what you needed to know in this area for your Windows Server 2008 certification (how to configure read-only domain controllers, for example), the most important topic within this objective will be domain controller cloning. Domain controller cloning is a genuinely new feature in Windows Server 2012 and Windows Server 2012 R2, and you will almost certainly see questions about this topic on the 70-417 exam. The first thing you need to know? The cloning capability applies only to virtualized domain controllers.
This section covers the following topic:
![]() Configure domain controller cloning
Configure domain controller cloning
Cloning domain controllers
In Windows Server 2012 and Windows Server 2012 R2, you can, you can now deploy additional domain controllers in a domain by safely copying an existing virtual domain controller. In earlier versions of Windows Server, the fastest way to deploy a new domain controller, physical or virtual, was to start a fresh sysprepped image, promote the new server based on that image to a domain controller, and then complete additional configuration requirements as necessary. Cloning is much faster.
Cloning a domain controller has certain environmental requirements. In addition, cloning a domain controller is a special, specific procedure that includes adding the source virtual machine (VM) to a built-in group account and running certain Windows PowerShell cmdlets prior to exporting and importing.
It’s also worth noting that cloning seems perfect for questions on the 70-417 exam. Not only is this feature new in Windows Server 2012 and Windows Server 2012 R2, but the cloning prerequisites and the cloning procedure also are made up of details that are just specific enough for the exam. For this reason, be sure to learn these details well, such as the specific names of cmdlets and xml files.
Prerequisites for cloning
To clone a domain controller, three different servers need to be running Windows Server 2012 or Windows Server 2012 R2:
![]() The host server with the Hyper-V server role installed, on which the source VM is running as a guest
The host server with the Hyper-V server role installed, on which the source VM is running as a guest
![]() A second server, physical or virtual, that is itself a domain controller in the same domain as the VM to be cloned, and that is hosting the PDC Emulator operations master role
A second server, physical or virtual, that is itself a domain controller in the same domain as the VM to be cloned, and that is hosting the PDC Emulator operations master role
![]() The source VM to be cloned that is a domain controller, and that cannot be hosting the PDC Emulator operations master role
The source VM to be cloned that is a domain controller, and that cannot be hosting the PDC Emulator operations master role
Note also that the domain controller clone that results from the cloning procedure will be located in the same site as the source domain controller.
Add the source domain controller to the Cloneable Domain Controllers group
If your environment meets the prerequisites, you are ready to begin the cloning procedure. The first step in this procedure is to add the source VM that is a domain controller to the Cloneable Domain Controllers global security group. This built-in group account is new to Windows Server 2012 and Windows Server 2012 R2 and is found in the Users container within a domain, as shown in Figure 8-1.
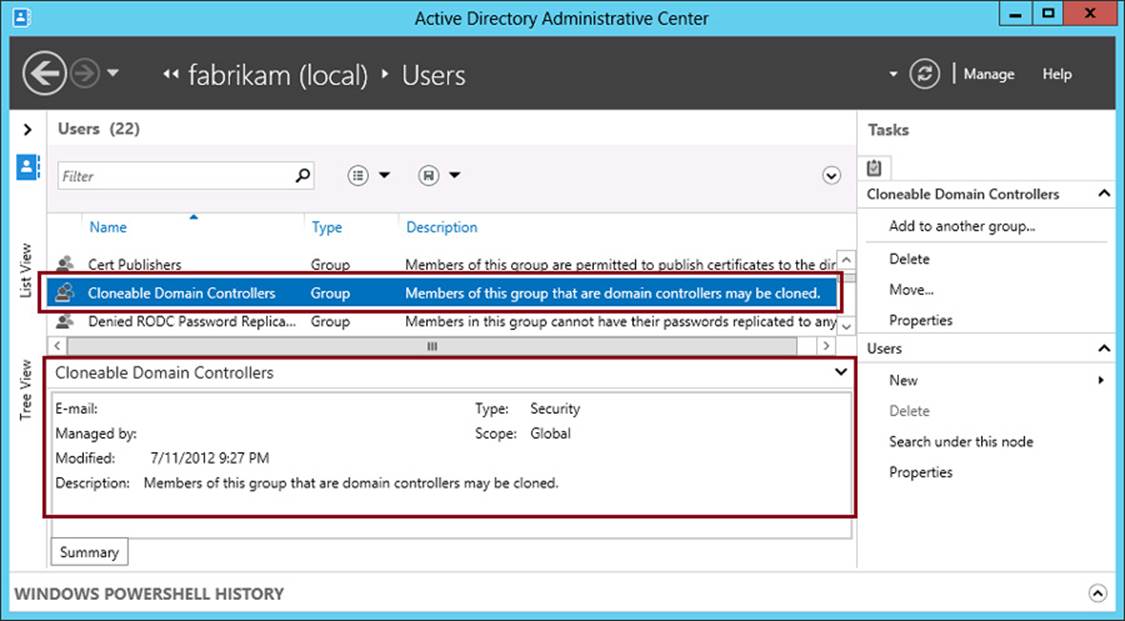
FIGURE 8-1 Windows Server 2012 and Windows Server 2012 R2 include a new Cloneable Domain Controllers global security group
PowerShell
To add a user or computer account to a new security group, you can use the Add-ADGroupMember cmdlet. For more information about this cmdlet, visit http://technet.microsoft.com/en-us/library/ee617210.aspx.
Review applications with the Get-ADDCCloningExcludedApplicationList cmdlet
The next step in cloning a virtual domain controller is to run the Get-ADDCCloningExcludedApplicationList cmdlet on the source VM. The purpose of this cmdlet is to present a list of applications or services that are not evaluated for cloning and that are installed on the source VM. If no such applications are found, the cmdlet provides the output shown in Figure 8-2. If an unevaluated application is found, an output similar to the one in Figure 8-3 is displayed.
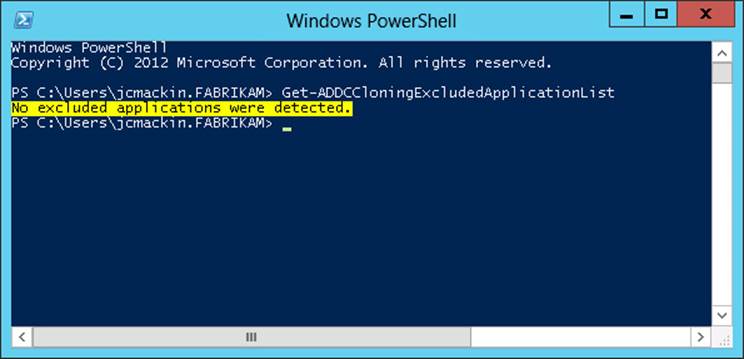
FIGURE 8-2 Output of Get-ADDCCloningExcludedApplicationList revealing no unsafe applications
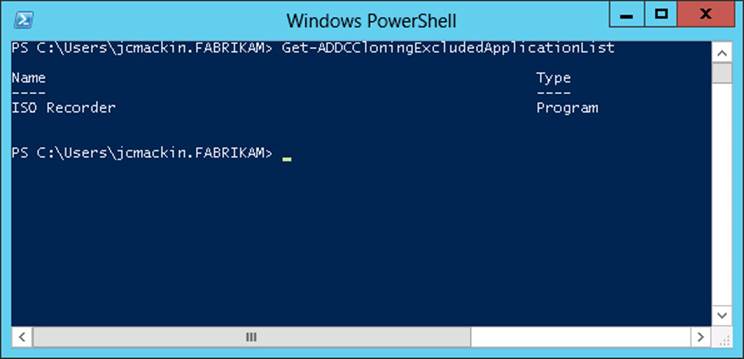
FIGURE 8-3 Output of Get-ADDCCloningExcludedApplicationList revealing a potentially unsafe application
If the cmdlet returns a list of services and installed programs, review the list. Consult the software vendor of each application to determine whether it can be safely cloned. If any applications or services in the list cannot be safely cloned, you must uninstall them from the source domain controller at this point.
Next, if you determine that the services or applications returned by the Get-ADDCCloningExcludedApplicationList cmdlet are safe for cloning, you can add them to an inclusion list stored in a file named CustomDCCloneAllowList.xml. To do so, use the -GenerateXml parameter with the same cmdlet. For example, the following command generates the excluded application list as a file named CustomDCCloneAllowList.xml at the specified folder path (C:\Windows\NTDS) and forces an overwrite if a file by that name is found to already exist at that path location:
Get-ADDCCloningExcludedApplicationList -GenerateXml -Path C:\Windows\NTDS -Force
The output of this command is shown in Figure 8-4, and the contents of the CustomDCCloneAllowList.xml file are shown in Figure 8-5.
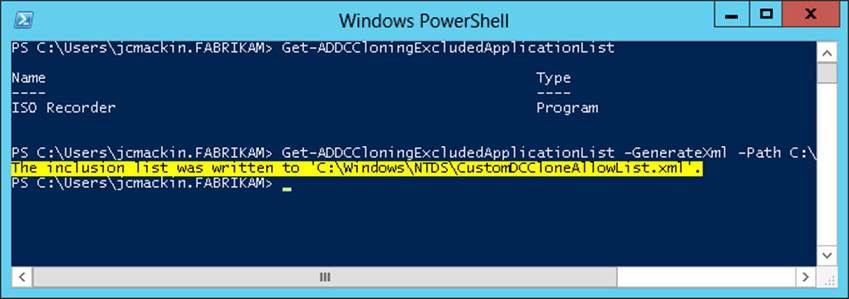
FIGURE 8-4 Adding detected applications to the inclusion list
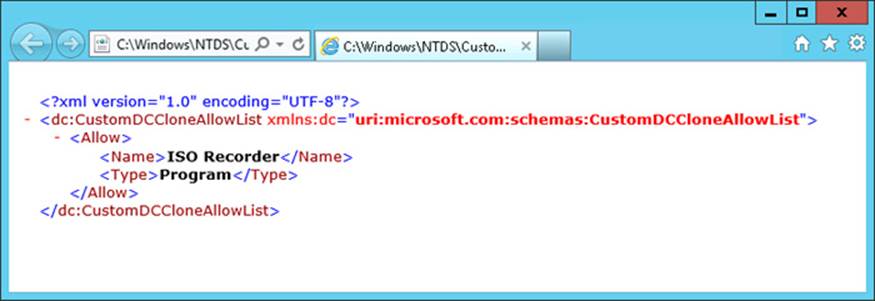
FIGURE 8-5 The CustomDCCloneAllowList.xml file
After you perform this step, the Get-ADDCCloningExcludedApplicationList cmdlet will provide the output shown in Figure 8-6.
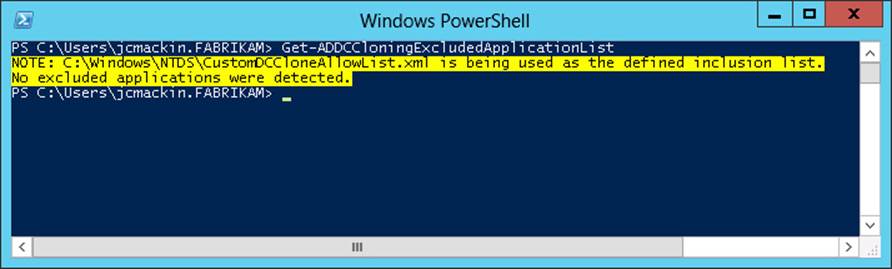
FIGURE 8-6 The output of Get-ADDCCloningExcludedApplicationList after adding a detected application to the inclusion list
Note that if any programs originally returned by the Get-ADDCCloningExcludedApplicationList cmdlet are not added to the inclusion list (CustomDCCloneAllowList.xml), the next step will fail.
More Info
For more information about the Get-ADDCCloningExcludedApplicationList cmdlet, visit http://technet.microsoft.com/en-us/library/hh852291.
Run the New-ADDCCloneConfigFile cmdlet on the source VM
The New-ADDCCloneConfigFile cmdlet runs a list of prerequisite checks on the source VM and generates a clone configuration file, DCCloneConfig.xml, if all the checks succeed. The clone configuration file includes settings that you have specified for the new clone VM, such as an IP address configuration and computer name, by using parameters with the cmdlet. If the command runs successfully, the DCCloneConfig.xml file is saved in a location (C:\Windows\NTDS) that will automatically configure the clone with these settings when you later start the clone for the first time, so you don’t need to look for the file or move it from its default location. (If you don’t specify a name for the clone, one will be chosen automatically. If you don’t specify a static IP configuration, it will be set dynamically.)
The checks succeed if the answers to the following three questions are all “yes”:
![]() Is the PDC Emulator operations master role hosted on a domain controller running Windows Server 2012 or later?
Is the PDC Emulator operations master role hosted on a domain controller running Windows Server 2012 or later?
![]() Is the source domain controller a member of the Cloneable Domain Controllers group?
Is the source domain controller a member of the Cloneable Domain Controllers group?
![]() Are all programs and services originally listed in the output of the Get-ADDCCloningExcludedApplicationList cmdlet now either removed or captured in CustomDCCloneAllowList.xml?
Are all programs and services originally listed in the output of the Get-ADDCCloningExcludedApplicationList cmdlet now either removed or captured in CustomDCCloneAllowList.xml?
A successful check of a source domain controller is shown in Figure 8-7.
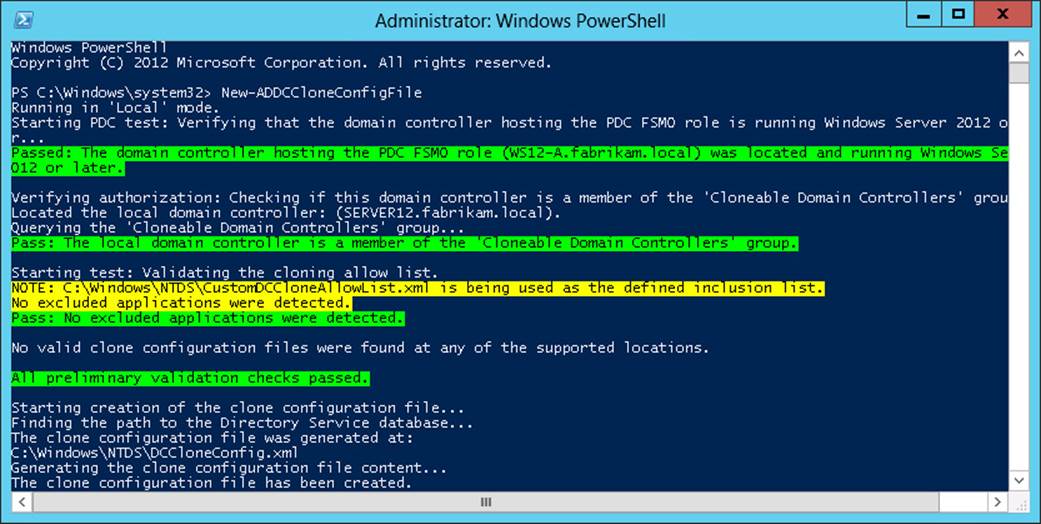
FIGURE 8-7 The output of the New-ADDCCloneConfigFile cmdlet
 Exam Tip
Exam Tip
You need to remember the function of both the CustomDCCloneAllowList.xml file and the DCCloneConfig.xml file, and that these files are saved in %Systemroot%\NTDS.
More Info
For more information about the New-ADDCCloneConfigFile cmdlet, visit http://technet.microsoft.com/en-us/library/jj158947.
Export and then import the VM of the source domain controller
To clone the VM, first shut it down. Then, you can use the Export command in Hyper-V Manager to copy the VM files to a location you choose. To export the VM using Windows PowerShell instead, use the Export-VM cmdlet as in the following example:
Export-VM –Name Test –Path D:\
At this point, you must delete all the snapshots in the Snapshots subdirectory of the exported VM. If desired, you can then copy the exported VM and its associated files to another computer running Windows Server 2012 or later that has the Hyper-V role installed.
Next, you can use the Import command in Hyper-V Manager to import the exported VM. Use the Copy The Virtual Machine (Create A New Unique ID) option when importing the VM, as shown in Figure 8-8. To perform this step in Windows PowerShell, use the Import-VM cmdlet as in the following example:
Import-VM -Path 'D:\Test2\Virtual Machines\8F148B6D-C674-413E-9FCC-4FBED185C52D.XML' –
Copy -GenerateNewId
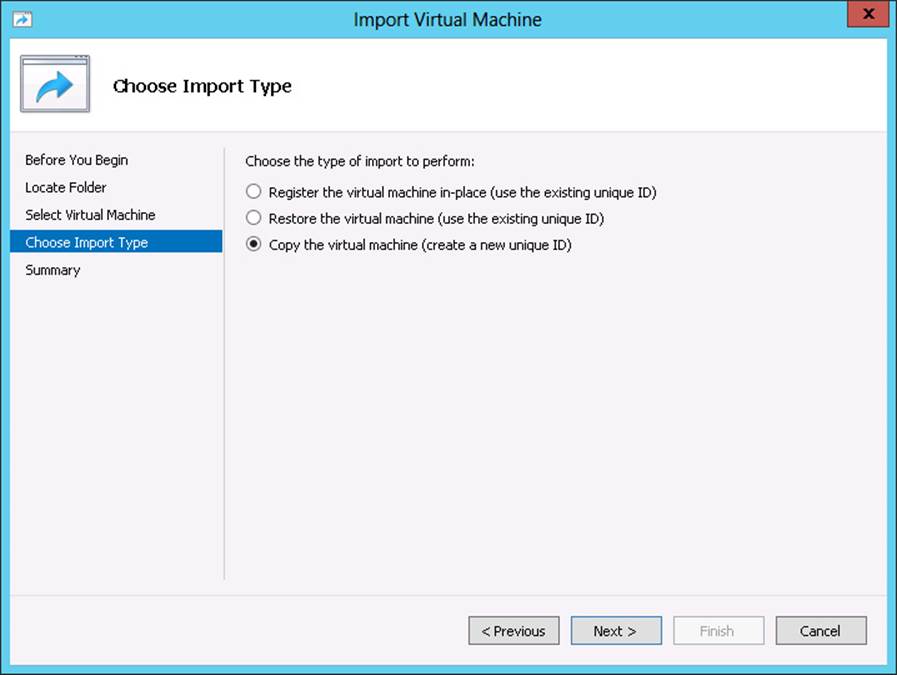
FIGURE 8-8 Creating a unique ID when importing an image allows you to use the source image again
Finally, after importing the copy of the source VM, you can restart the source VM and then start the new clone VM.
 Exam Tip
Exam Tip
Remember that you can use Dcpromo with the /CreateDCAccount option to create an RODC account in Active Directory. For more information about the options still used with Dcpromo in Windows Server 2012 and Windows Server 2012 R2, type Dcpromo /? at a command prompt.
Objective summary
![]() Windows Server 2012 and Windows Server 2012 R2 allow you to clone a virtualized domain controller for rapid deployment of a new domain controller.
Windows Server 2012 and Windows Server 2012 R2 allow you to clone a virtualized domain controller for rapid deployment of a new domain controller.
![]() The source VM must be a member of the Cloneable Domain Controllers global security group.
The source VM must be a member of the Cloneable Domain Controllers global security group.
![]() Three computers must be running Windows Server 2012 or later: the host server running Hyper-V, the guest VM that is the domain controller to be cloned, and a third domain controller that owns the PDC Emulator operations master role for the domain.
Three computers must be running Windows Server 2012 or later: the host server running Hyper-V, the guest VM that is the domain controller to be cloned, and a third domain controller that owns the PDC Emulator operations master role for the domain.
![]() You need to use the Get-ADDCCloningExcludedApplicationList cmdlet to determine whether any applications or services on the source domain controller have not yet been determined to be safe for cloning. You must either uninstall such applications or add them to the inclusion list by running the same cmdlet again with the -GenerateXml switch.
You need to use the Get-ADDCCloningExcludedApplicationList cmdlet to determine whether any applications or services on the source domain controller have not yet been determined to be safe for cloning. You must either uninstall such applications or add them to the inclusion list by running the same cmdlet again with the -GenerateXml switch.
![]() Next, run the New-ADDCCloneConfigFile cmdlet to run prerequisite checks to determine whether the domain controller is ready to be cloned.
Next, run the New-ADDCCloneConfigFile cmdlet to run prerequisite checks to determine whether the domain controller is ready to be cloned.
![]() When the domain controller passes the prerequisite checks, use Hyper-V Manager or the Export-VM and Import-VM cmdlets to copy the VM. Be sure to delete the snapshots of the exported VM before you import. When importing, choose the option to copy the VM and create a new unique ID.
When the domain controller passes the prerequisite checks, use Hyper-V Manager or the Export-VM and Import-VM cmdlets to copy the VM. Be sure to delete the snapshots of the exported VM before you import. When importing, choose the option to copy the VM and create a new unique ID.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. You are a network administrator for Fabrikam.com. The Fabrikam.com network includes a private cloud built on six physical servers with the Hyper-V role installed, three of which are running Windows Server 2012 R2, and three of which are running Windows Server 2008 R2. These physical servers host a total of 24 virtualized guest servers, including domain controllers, infrastructure servers, database servers, and application servers. All VMs are members of the Fabrikam.com domain.
One of the virtualized domain controllers is named DC1. DC1 is hosted on a physical server named HYPV1. You want to clone DC1 to add another domain controller to the Fabrikam.com domain.
Which of the following is not a requirement for cloning DC1?
A. DC1 must own the PDC emulator role.
B. HYPV1 must be running Windows Server 2012 or later.
C. DC1 must be running Windows Server 2012 or later.
D. All programs and services originally listed in the output of the Get-ADDCCloningExcludedApplicationList cmdlet when it is run on DC1 must be added to the Allow list in CustomDCCloneAllowList.xml.
2. You want to clone a domain controller named VDC1 that is running Windows Server 2012 R2 within a VM. VDC1 is hosted on a server named Host01, which is also running Windows Server 2012 R2.
VDC1 belongs to the Contoso.local domain and owns both the PDC Emulator and Infrastructure Master operations master roles for that domain. Contoso.local currently includes just one other domain controller, named VDC2. VDC2 is running Windows Server 2008 R2 and is the only global catalog server in Contoso.local.
You want to create a new domain controller named DC3 that is based on a clone of VDC1. Which steps do you need to take before you can achieve this? (Choose all that apply.)
A. Move the Infrastructure Master operations master role to VDC2.
B. Make VDC1 a global catalog server.
C. Upgrade VDC2 to Windows Server 2012 or Windows Server 2012 R2.
D. Make Host01 a member of the Cloneable Domain Controllers global security group.
E. Make VDC1 a member of the Cloneable Domain Controllers global security group.
3. You want to clone a domain controller named DCA.fabrikam.local that is running Windows Server 2012 in a VM. DCA is hosted on a server named HV01, which is also running Windows Server 2012.
When you run the cmdlet Get-ADDCCloningExcludedApplicationList on DCA, the output displays the name of a single application, App1. You want to ensure that App1 is made available on all future domain controllers that result from cloning DCA. You have verified that App1 is safe for cloning.
What should you do next?
A. Export the DCA VM.
B. Add App1 to the CustomDCCloneAllowList.xml file.
C. Run the New-ADDCCloneConfigFile cmdlet.
D. Run the New-VirtualDiskClone cmdlet.
Objective 8.2: Maintain Active Directory
Windows Server 2008 R2 introduced Active Directory Recycle Bin, a Windows PowerShell–based feature that allowed you to restore objects deleted from the Active Directory Domain Services database. Windows Server 2012 brings this functionality of Active Directory Recycle Bin to Active Directory Administrative Center, the graphical tool for managing Active Directory Domain Services that also first appeared in Windows Server 2008 R2.
This section covers the following topics:
![]() Restoring deleted objects in Active directory
Restoring deleted objects in Active directory
![]() Using Active Directory Recycle Bin to restore deleted objects
Using Active Directory Recycle Bin to restore deleted objects
![]() Setting the deleted object lifetime in a domain
Setting the deleted object lifetime in a domain
Restoring deleted objects in Active Directory
Before Windows Server 2008 R2, there were just two methods you could use to restore an object that had accidentally been deleted from Active Directory Domain Services: You could perform an authoritative restore with the Ntdsutil command-line utility, or you could use the LDP utility to perform a procedure called tombstone reanimation. Both of these methods, however, had significant drawbacks. With Ntdsutil, the drawbacks were that you first had to boot the domain controller into Directory Services Restore Mode (making the domain controller temporarily unavailable to clients on the network) and that you could only restore deleted objects that you had previously backed up. With tombstone reanimation, the drawbacks were that it was a complicated procedure and that it couldn’t be relied on to restore an object’s group memberships.
 Exam Tip
Exam Tip
Remember that you use Ntdsutil to perform an authoritative restore and LDP to perform tombstone reanimation.
More Info
For more information about performing an authoritative restore with Ntdsutil, visit http://technet.microsoft.com/en-us/library/cc755296(v=WS.10).aspx. For more information about reanimating tombstoned objects, visit http://technet.microsoft.com/en-us/magazine/2007.09.tombstones.aspx.
Active Directory Recycle Bin
Windows Server 2008 R2 first removed these drawbacks with Active Directory Recycle Bin. With Active Directory Recycle Bin, you don’t have to take the domain controller offline to restore a deleted object, and the original group memberships of the deleted objects are preserved when you restore them.
Windows Server 2008 R2 introduced Active Directory Recycle Bin in a Windows PowerShell-only mode. Windows Server 2012 and Windows Server 2012 R2 make this new feature more accessible by bringing its functionality to the graphical Active Directory Administrative Center tool. For the exam, you need to know how to enable and use Active Directory Recycle Bin in both Windows PowerShell and Active Directory Administrative Center.
Enabling Active Directory Recycle Bin
For the exam and the real world, remember that the Active Directory Recycle Bin is not enabled by default. You can use Active Directory Recycle Bin to restore only those objects that have been deleted after the feature is enabled. Objects you deleted before then can be restored only through authoritative restore or tombstone reanimation.
To enable Active Directory Recycle Bin in Windows PowerShell, first make sure that all domain controllers in the domain are running Windows Server 2008 R2 or later. In addition, the functional level of your forest must be set to Windows Server 2008 R2 or higher. You can use the Get-ADForest cmdlet to check the functional level of your forest:
Get-ADForest ForestName
If you need to raise the functional level of the forest, you can use the Set-ADForestMode cmdlet with the following syntax:
Set-ADForestMode -Identity ForestName -ForestMode Windows2008R2Forest
Once your environment meets the prerequisites of Active Directory Recycle Bin, you can enable the feature by using the following Windows PowerShell command:
Enable-ADOptionalFeature 'Recycle Bin Feature' -scope ForestOrConfigurationSet -target
DomainName -server DomainControllerName
To enable Active Directory Recycle Bin in the graphical user interface (GUI) in Windows Server 2012 and Windows Server 2012 R2, open Active Directory Administrative Center from the Tools menu in Server Manager. Then, in Active Directory Administrative Center, right-click the domain icon in the console tree and select Enable Recycle Bin from the shortcut menu, as shown in Figure 8-9.
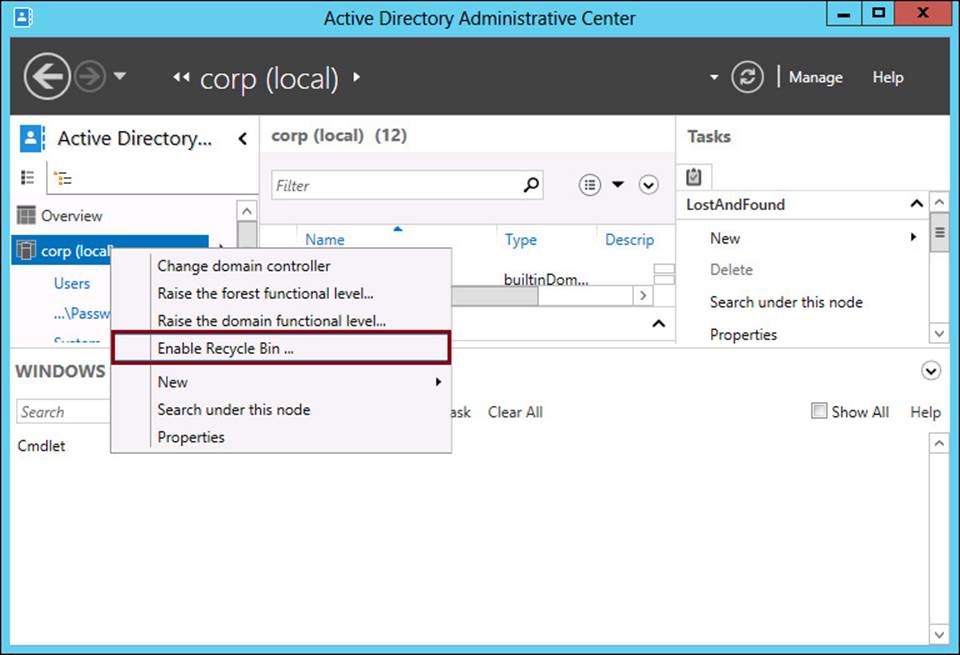
FIGURE 8-9 Enabling Active Directory Recycle Bin in Windows Server 2012 and Windows Server 2012 R2
 Exam Tip
Exam Tip
Remember that Active Directory Recycle Bin requires all domain controllers to be running Windows Server 2008 R2 or later, and similarly, that the forest functional level must be set to Windows Server 2008 R2 or higher.
Enabling Active Directory Recycle Bin is irreversible. In some environments, allowing administrators to see previously deleted objects might be undesirable. Consequently, you should make sure that Active Directory Recycle Bin is compatible with your organization’s security policy before enabling the feature.
Restoring Deleted Objects in Active Directory Administrative Center
A new Deleted Objects container appears in Active Directory Administrative Center at the root of the domain container after you enable Active Directory Recycle Bin, as shown in Figure 8-10. Objects that you delete appear in this container for a period of time called the deleted object lifetime, which is 180 days by default.
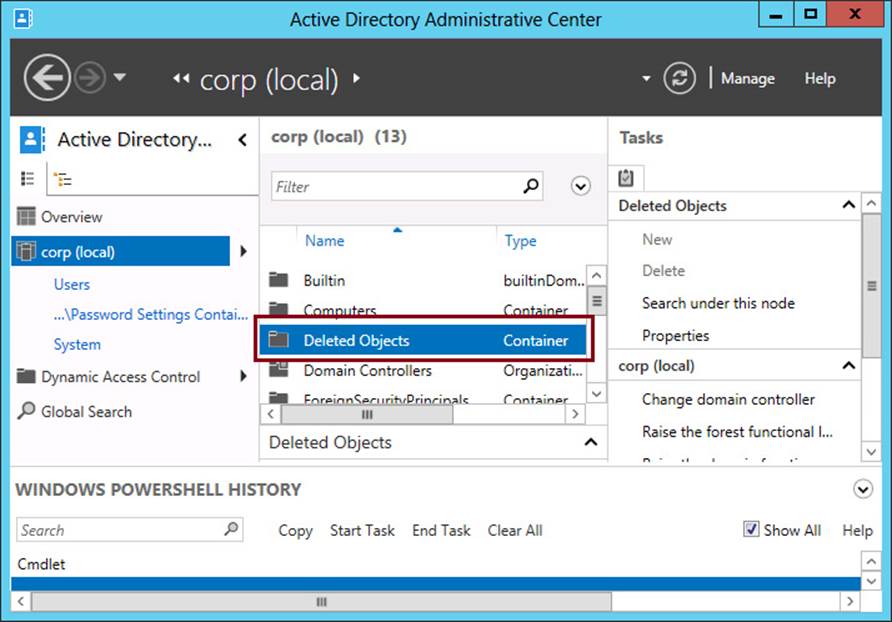
FIGURE 8-10 A Deleted Objects container appears after you enable Active Directory Recycle Bin
Restoring an object in the GUI is simple—so simple, in fact, that it might be challenging for the exam writers to devise difficult questions about restoring objects from the GUI. To restore the object to its last known parent container, just right-click the object and select Restore from the shortcut menu, as shown in Figure 8-11.
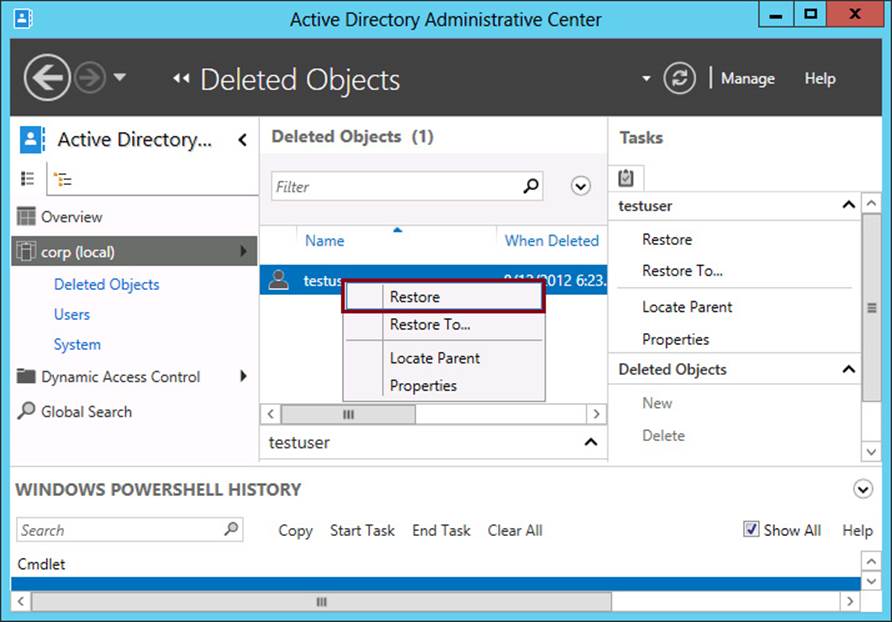
FIGURE 8-11 Restoring a deleted object in Active Directory
 Exam Tip
Exam Tip
In preparing for the Maintain Active Directory objective, make sure you review the functions and features of the Ntdsutil utility. Even though this utility has not changed since Windows Server 2008, it’s an essential Active Directory maintenance tool. A good way to review the capabilities of Ntdsutil is to type ntdsutil help at a command prompt on a domain controller. Alternatively, you can search for the utility online at the TechNet web site. Be sure to review all of the Ntdsutil contexts, such as Snapshot, which allows you to create and manage snapshots of the Active Directory database, and Files, which allows you to move the Active Directory database (Ntds.dit) to a new location.
To restore an object to a different container, select Restore To and select the new container in which you want the object to appear. The Locate Parent option opens the former parent container in the console.
One potential complication in restoring an object might occur if you have deleted both the container and the object. In this case, you need to restore the parent before the child object, or choose to restore the object to another container.
Restoring Deleted Objects in Windows PowerShell
To restore a deleted object in Windows PowerShell, first use the Get-ADObject cmdlet with the -Filter and -IncludeDeletedObjects parameters, and then pipe the result to the Restore-ADObject cmdlet. For example, to restore a deleted user with the display name “Mary,” type the following command at an elevated Windows PowerShell prompt:
Get-ADObject -Filter {DisplayName -eq "Mary"} -IncludeDeletedObjects | Restore-ADObject
Here’s another example: To restore a user whose canonical name (CN) is like “Jorge,” type the following:
Get-ADObject -Filter {CN -like "Jorge"} -IncludeDeletedObjects | Restore-ADObject
In the real world, it doesn’t make much sense to restore a deleted object by using Windows PowerShell if you don’t have to. However, don’t be surprised if the Windows PowerShell method of Active Directory Recycle Bin still appears on the exam.
 Exam Tip
Exam Tip
Don’t forget about the Dsamain tool, which was introduced in Windows Server 2008. Dsamain allows you to mount a shadow copy-enabled backup or Ntdsutil snapshot of the Active Directory database. After using Dsamain to mount an Active Directory backup or Ntdsutil snapshot, you can use Ldp.exe to view the historical contents of the database, including object attributes. When you use Dsamain, be sure to mount the backup or snapshot in a port other than port 389, which is the reserved LDAP port used by the currently running instance of the Active Directory database. For more information about Dsamain, search for “Active Directory Domain Services Database Mounting Tool (Snapshot Viewer or Snapshot Browser) Step-by-Step Guide” or visit http://technet.microsoft.com/en-us/library/cc753609(v=ws.10).aspx.
More Info
For more information about how to use Get-ADObject, visit http://technet.microsoft.com/en-us/library/ee617198.aspx.
Deleted object lifetime
By default, you have only 180 days to restore an object after it is deleted. This period is known as the deleted object lifetime and is governed by the msDS-DeletedObjectLifetime attribute assigned to the domain. To change the value of this attribute, use the Set-ADObject cmdlet in the following manner:
Set-ADObject -Identity "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,
DC=<mydomain>,DC=<com>" –Partition "CN=Configuration,DC=<mydomain>,DC=<com>" –Replace:@
{"msDS-DeletedObjectLifetime" = <value>}
 Exam Tip
Exam Tip
The Configure and Manage Active Directory domain is taken from the 70-411 exam. In its original form, the domain includes two additional objectives: the Configure Service Authentication objective and the Configure Account Policies objective. Thus, do not be surprised if you see a question related to one of these objectives on the 70-417 exam. You should review older topics that fall within the scope of these objectives, such as Managed Service Accounts and Password Settings Objects, especially if you haven’t dealt with these features since you earned your Windows Server 2008 certification.
Replace DC=<mydomain>,DC=<com> with the appropriate forest root domain name of your Active Directory environment and replace <value> with the new value of the deleted object lifetime.
For example, to set the deleted object lifetime to 365 days, run the following command:
Set-ADObject -Identity "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuratio
n,DC=contoso,DC=com" –Partition "CN=Configuration,DC=contoso,DC=com" –Replace:@{"msDS-
DeletedObjectLifetime" = 365}
 Exam Tip
Exam Tip
Remember that domains with a functional level of Windows Server 2008 or higher perform replication of the SYSVOL folder by using the Distributed File System Replication (DFSR) engine. Lower functional levels use the File Replication Service (FRS) instead.
Objective summary
![]() Windows Server 2008 R2 introduced Active Directory Recycle Bin, a Windows PowerShell–based tool that allowed you to restore a deleted object such as a user without taking the domain controller offline and without risk of losing the object’s group memberships.
Windows Server 2008 R2 introduced Active Directory Recycle Bin, a Windows PowerShell–based tool that allowed you to restore a deleted object such as a user without taking the domain controller offline and without risk of losing the object’s group memberships.
![]() Windows Server 2012 and Windows Server 2012 R2 bring the functionality of Active Directory Recycle Bin to the GUI, in the Active Directory Administrative Center.
Windows Server 2012 and Windows Server 2012 R2 bring the functionality of Active Directory Recycle Bin to the GUI, in the Active Directory Administrative Center.
![]() Active Directory Recycle Bin must first be enabled. Once enabled, it can’t be disabled.
Active Directory Recycle Bin must first be enabled. Once enabled, it can’t be disabled.
![]() Once Active Directory Recycle Bin is enabled, a Deleted Object container appears at the root of the domain in Active Directory Administrative Center. You can easily find and restore objects from this location.
Once Active Directory Recycle Bin is enabled, a Deleted Object container appears at the root of the domain in Active Directory Administrative Center. You can easily find and restore objects from this location.
![]() Deleted objects have a default lifetime of 180 days. This period is a configurable attribute of a domain, called the deleted object lifetime. To change the deleted object lifetime, use the Set-ADObject cmdlet.
Deleted objects have a default lifetime of 180 days. This period is a configurable attribute of a domain, called the deleted object lifetime. To change the deleted object lifetime, use the Set-ADObject cmdlet.
Objective review
Answer the following questions to test your knowledge of the information in this objective. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of the chapter.
1. You are a network administrator for Contoso.com. You have learned that a user account was accidentally deleted from the Contoso.com Active Directory domain. The domain controllers in your network are all running Windows Server 2012 R2. Active Directory Recycle Bin is not yet enabled.
You want to restore the deleted user account without taking any domain controller offline. What should you do?
A. Perform an authoritative restore of the deleted user account with the Ntdsutil utility.
B. Reanimate the tombstone of the deleted object.
C. Enable Active Directory Recycle Bin, and use Active Directory Administrative Center to restore the object.
D. Enable Active Directory Recycle Bin, and use Windows PowerShell to restore the object.
2. You are a network administrator for Contoso.com. You have learned that a user account for a user named Dan Park was accidentally deleted from the Contoso.com Active Directory domain. The domain controllers in your network are all running Windows Server 2012 R2. Active Directory Recycle Bin was enabled at the time the object was deleted.
You want to restore the deleted user account without taking any domain controller offline. What should you do?
A. Restore the object from the Deleted Objects container in Active Directory Administrative Center.
B. Perform an authoritative restore using the Ntdsutil utility.
C. Reanimate the tombstone of the deleted object.
D. Run the following command:
Get-ADObject -Filter {displayName -eq "Dan Park"} | Restore-ADObject
3. You are a network administrator for Adatum.com. You have learned that all 10 user accounts in the Finance department were accidentally deleted from the Adatum.com Active Directory domain. The domain controllers in your network are all running Windows Server 2012 R2. Active Directory Recycle Bin was enabled at the time the user accounts were deleted.
You attempt to restore the deleted user accounts in Active Directory Administrative Center, but you receive errors indicating that object’s parent is deleted.
You want to restore the deleted user accounts. What should you do?
A. Use the Set-ADObject cmdlet to extend the deleted object lifetime in the domain.
B. Re-create the parent organizational unit of the user accounts and then restore the user accounts.
C. Restore the parent organizational unit of the user accounts and then restore the user accounts.
D. Restart a domain controller in Directory Services Restore Mode and perform an authoritative restore of the deleted user accounts.
 Thought experiment: Configuring and managing Active Directory at Proseware
Thought experiment: Configuring and managing Active Directory at Proseware
You are a network administrator for Proseware.com. The Proseware.com network consists of a single Active Directory domain, including two domain controllers. One domain controller named DC1 is running Windows Server 2012 R2, and the other named DC2 is running Windows Server 2008 R2. Both domain controllers are running in GUI mode in VMs, on host servers running Windows Server 2012 R2.
One of your goals as a network administrator is to help improve both the resiliency and scalability of the network. Proseware.com has been experiencing rapid growth, and you want the network to handle increasingly heavy workloads in the coming months and years. You also want to be able to improve fault tolerance so that configuration errors such as accidental deletions can be quickly reversed.
With this information in mind, answer the following questions. You can find the answers to these questions in the “Answers” section.
1. Is DC1 is eligible for cloning? Why or why not?
2. You install a third domain controller named DC3. DC3 is running a fresh installation of Windows Server 2012, with no additional software or applications. Which step(s) must you take before DC3 can be cloned?
3. You export the DC3 VM. Which step(s) must you take before importing the exported VM?
4. How would you find out if Active Directory Recycle Bin is enabled on the Proseware.com domain?
5. If Active Directory Recycle Bin is not enabled, how would you determine whether this feature can be enabled in the domain?
Answers
This section contains the answers to the Objective Reviews and the Thought Experiment.
Objective 8.1: Review
1. Correct answer: A
A. Correct: DC1 must not own the PDC Emulator operations master role.
B. Incorrect: The host server must be running Windows Server 2012 or Windows Server 2012 R2.
C. Incorrect: The source virtualized domain controller must be running Windows Server 2012 or later.
D. Incorrect: Cloning cannot occur unless every program listed in the output of the Get-ADDCCloningExcludedApplicationList cmdlet also appears on the inclusion list, CustomDCCloneAllowList.xml.
2. Correct answers: C, E
A. Incorrect: The cloned domain controller can be the Infrastructure Master. It cannot be the PDC Emulator. Also, the Infrastructure Master role should not be placed on a global catalog server.
B. Incorrect: It is not necessary to make VDC1 a global catalog server to clone it.
C. Correct: The PDC Emulator in the domain needs to be running Windows Server 2012 or Windows Server 2012 R2.
D. Incorrect: The host computer doesn’t need to be in any global security group.
E. Correct: The domain controller you want to clone must be a member of the Cloneable Domain Controllers global security group.
3. Correct answer: B
A. Incorrect: You shouldn’t export the VM until you add App1 to the Allow list and run the New-ADDCCloneConfigFile cmdlet.
B. Correct: The next step is to add App1 to the Allow list, called CustomDCCloneAllowList.xml, by running the Get-ADDCCloningExcludedApplicationList with the -GenerateXml switch.
C. Incorrect: You should run the New-ADDCCloneConfigFile cmdlet only after you add App1 to the inclusion list. This cmdlet runs a list of prerequisite checks on the source VM.
D. Incorrect: You don’t use this cmdlet to clone a domain controller. You would use the cmdlet to clone a virtual disk.
Objective 8.2: Review
1. Correct answer: B
A. Incorrect: The solution requires that no domain controller should be taken offline. To perform an authoritative restore with the Ntdsutil utility, you first need to take a domain controller offline by booting it in Directory Services Restore Mode.
B. Correct: You cannot restore the object by using Active Directory Recycle Bin because this feature was not enabled when the object was deleted. To restore the object without taking a domain controller offline, you will have to reanimate the tombstone of the object.
C. Incorrect: You cannot restore the object by using Active Directory Recycle Bin because this feature was not enabled when the object was deleted.
D. Incorrect: You cannot restore the object by using Active Directory Recycle Bin because this feature was not enabled when the object was deleted.
2. Correct answer: A
A. Correct: Restoring the deleted object in the GUI is by far the simplest option. You can restore the object in Active Directory Administrative Center because Active Directory Recycle Bin was enabled when the object was deleted and at least one of your domain controllers is running Windows Server 2012 or Windows Server 2012 R2.
B. Incorrect: You should not perform an authoritative restore because this procedure requires you to take a domain controller offline.
C. Incorrect: Although you can perform this procedure, it is unnecessarily complicated. In addition, through this procedure the object you restore might be stripped of its group memberships, so it is not the best option.
D. Incorrect: This command will not work without the -IncludeDeletedObjects switch.
3. Correct answer: C
A. Incorrect: The errors indicate that the objects’ parent is deleted. Extending the deleted object lifetime will have no effect on the state of the parent container.
B. Incorrect: You need to restore the original parent container, not re-create one with the same name.
C. Correct: If the parent container is deleted, you are able to restore it from the Deleted Objects container. After it is restored, you are able to restore its child objects.
D. Incorrect: This step would not help. Restoring the deleted objects in Directory Services Restore Mode would not affect the underlying problem that the parent container is missing.
Thought experiment
1. No, it is not. Although DC1 and the host computer both meet the requirements of running Windows Server 2012 or later, the network environment does not meet the requirement of a second domain controller running Windows Server 2012 or later with the PDC Emulator role.
2. You need to ensure that DC1 holds the PDC Emulator role and transfer the role to that computer if necessary. In addition, you need to add DC3 to the Cloneable Domain Controllers global security group.
3. You need to delete the snapshots in the Snapshots subdirectory.
4. You can look in Active Directory Administrative Center and determine whether a Deleted Objects container exists at the root of the domain.
5. Use the Get-Forest cmdlet to determine the functional level of the forest. The forest needs to be running at the Windows Server 2008 R2 functional level or higher.