CCNA Wireless 200-355 Official Cert Guide (2016)
Chapter 14. Wireless Security Fundamentals
This chapter covers the following topics:
![]() Anatomy of a Secure Connection—This section provides an overview of the types of information that should be protected over a wireless connection and the functions that you can use to provide protection.
Anatomy of a Secure Connection—This section provides an overview of the types of information that should be protected over a wireless connection and the functions that you can use to provide protection.
![]() Wireless Client Authentication Methods—This section describes many of the common methods that you can use to authenticate clients on a wireless network.
Wireless Client Authentication Methods—This section describes many of the common methods that you can use to authenticate clients on a wireless network.
![]() Wireless Privacy and Integrity Methods—This section discusses two methods that you can leverage to keep data obscured from eavesdroppers and to discover when data has been tampered with over a wireless connection.
Wireless Privacy and Integrity Methods—This section discusses two methods that you can leverage to keep data obscured from eavesdroppers and to discover when data has been tampered with over a wireless connection.
![]() WPA and WPA2—This section explains two important industry standards that specify a suite of security methods for wireless security.
WPA and WPA2—This section explains two important industry standards that specify a suite of security methods for wireless security.
![]() Securing Management Frames with MFP—This section discusses a method that you can use to prevent attacks that use management frames to disrupt a wireless network.
Securing Management Frames with MFP—This section discusses a method that you can use to prevent attacks that use management frames to disrupt a wireless network.
![]() Configuring Wireless Security—This section covers the configuration steps needed to implement WPA and WPA2 security on a wireless LAN.
Configuring Wireless Security—This section covers the configuration steps needed to implement WPA and WPA2 security on a wireless LAN.
This chapter covers the following exam topics:
![]() 5.0—Configuration of Client Connectivity
5.0—Configuration of Client Connectivity
![]() 5.1—Identify authentication mechanisms
5.1—Identify authentication mechanisms
![]() 5.1a—LDAP, RADIUS, local authentication, WebAuth, 802.1X, PSK
5.1a—LDAP, RADIUS, local authentication, WebAuth, 802.1X, PSK
![]() 5.2—Configuring WLAN authentication mechanisms on the controller
5.2—Configuring WLAN authentication mechanisms on the controller
![]() 5.2a—WebAuth, 802.1X, PSK
5.2a—WebAuth, 802.1X, PSK
![]() 5.2b—TKIP deprecation
5.2b—TKIP deprecation
As you know by now, wireless networks are complex. Many technologies and protocols work behind the scenes to give end users a stable, yet mobile, connection to a wired network infrastructure. From the user’s perspective, a wireless connection should seem no different than a wired connection. A wired connection can give users a sense of security; data traveling over a wire is probably not going to be overheard by others. A wireless connection is inherently different; data traveling over the air can be overheard by anyone within range.
Therefore, securing a wireless network becomes just as important as any other aspect. A comprehensive approach to wireless security focuses on the following areas:
![]() Identifying the endpoints of a wireless connection
Identifying the endpoints of a wireless connection
![]() Identifying the end user
Identifying the end user
![]() Protecting the wireless data from eavesdroppers
Protecting the wireless data from eavesdroppers
![]() Protecting the wireless data from tampering
Protecting the wireless data from tampering
The identification process is performed through various authentication schemes. Protecting wireless data involves security functions like encryption and frame authentication.
This chapter covers many of the methods you can use to secure a wireless network. Be warned—wireless security can be a confusing topic because it is filled with many acronyms. Some of the acronyms rhyme like words from a children’s book. In fact, this chapter is a story about WEP, PSK, TKIP, MIC, AES, EAP, EAP-FAST, EAP-TLS, LEAP, PEAP, WPA, WPA2, CCMP, and on and on it goes. When you finish with this chapter, though, you will come away with a clear view of what these terms mean and how they all fit together.
As a CCNA Wireless engineer, you will need to have a basic understanding of the wireless security framework and the common methods you can use to build it. You will also need to know how to configure the most robust methods in a wireless network.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 14-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes.”
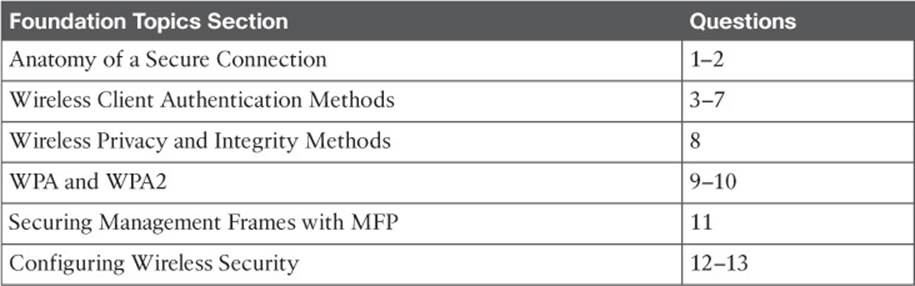
Table 14-1 “Do I Know This Already?” Section-to-Question Mapping
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following are necessary components of a secure wireless connection? (Choose all that apply.)
a. Encryption
b. MIC
c. Authentication
d. All of these answers are correct.
2. Which one of the following is used to protect the integrity of data in a wireless frame?
a. WIPS
b. WEP
c. MIC
d. EAP
3. Which one of the following is a wireless encryption method that has been found to be vulnerable and is not recommended for use?
a. AES
b. WPA
c. EAP
d. WEP
4. Which one of the following is used as the 802.11 authentication method when 802.1x is used on a WLAN?
a. Open authentication
b. WEP
c. EAP
d. WPA
5. A Cisco WLC is configured for 802.1x authentication, using an external RADIUS server. The controller takes on which one of the following roles?
a. Authentication server
b. Supplicant
c. Authenticator
d. Adjudicator
6. Which one of the following authentication methods uses a certificate to authenticate the AS but not the client?
a. LEAP
b. PEAP
c. EAP-FAST
d. EAP-TLS
7. Which one of the following authentication methods requires digital certificates on both the AS and the supplicants?
a. TKIP
b. PEAP
c. WEP
d. EAP-TLS
8. Which one of the following is currently the most secure data encryption and integrity method for wireless data?
a. WEP
b. TKIP
c. CCMP
d. WPA
9. WPA2 differs from WPA in which one of the following ways?
a. Allows TKIP
b. Mandates CCMP
c. Allows WEP
d. Allows TLS
10. A pre-shared key is used in which of the following wireless security configurations?
a. WPA personal mode
b. WPA enterprise mode
c. WPA2 personal mode
d. WPA2 enterprise mode
11. Which of the following is required to implement MFP on a WLAN to protect both the wireless infrastructure and the client? (Select all that apply.)
a. WPA
b. WPA2
c. CCXv4 or v5
d. CCXv5
e. WEP
12. Which one of the following options should you select to configure WPA2 personal on a WLAN?
a. 802.1x
b. PSK
c. TKIP
d. CCMP
13. Which of the following wireless security methods have been deprecated due to their weaknesses? (Choose all that apply.)
a. AES
b. TKIP
c. WEP
d. CCMP
e. EAP
Foundation Topics
Anatomy of a Secure Connection
In the previous chapters of this book, you have learned about wireless clients forming associations with wireless access points (APs) and passing data back and forth across the air. The main focus has been on the radio frequency (RF) conditions, the modulation schemes, and the management of airtime that are all necessary to send data from one place to another successfully.
As long as all clients and APs conform to the 802.11 standard, they can all coexist—even on the same channel. Not every 802.11 device is friendly and trustworthy, however. Sometimes it is easy to forget that transmitted frames do not just go directly from the sender to the receiver, as in a wired or switched connection. Instead, they travel according to the transmitter’s antenna pattern, potentially reaching any receiver that is within range.
Consider the scenario in Figure 14-1. The wireless client opens a session with some remote entity and shares a confidential password. Because two untrusted users are also located within range of the client’s signal, they may also learn the password by capturing frames that have been sent on the channel. The convenience of wireless communication also makes it easy for transmissions to be overheard and exploited by malicious users.
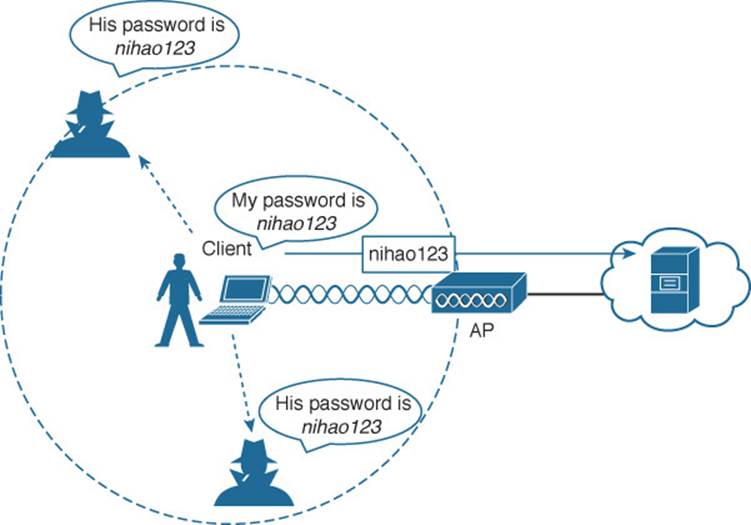
Figure 14-1 Wireless Transmissions Reaching Unintended Recipients
If data is sent through open space, how can it be secured so that it stays private and intact? The 802.11 standard offers a framework of wireless security mechanisms that can be used to add trust, privacy, and integrity to a wireless network. A Cisco unified wireless network can go even further by detecting and preventing malicious activity. The following sections give an overview of the wireless security framework. Each element is described in more detail later in the chapter.
Authentication
In Chapter 6, “Understanding 802.11 Frame Types,” you learned that wireless clients must discover a basic service set (BSS) and then request permission to associate with it. Clients should be authenticated by some means before they can become functioning members of the wireless LAN. Why?
Suppose that your wireless network connects to corporate resources where confidential information can be accessed. In that case, only devices known to be trusted and expected should be given access. Guest users, if they are permitted at all, should be allowed to join a different guest WLANwhere they can access nonconfidential or public resources. Rogue clients, which are not expected or welcomed, should not be permitted to associate at all. After all, they are not affiliated with the corporate network and are likely to be unknown devices that happen to be within range of your network.
To control access, wireless networks can authenticate the client devices before they are allowed to associate. Potential clients must identify themselves by presenting some form of credentials to the APs. Figure 14-2 shows the basic client authentication process.
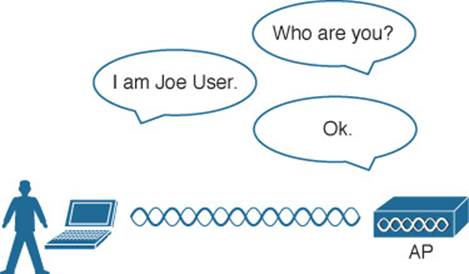
Figure 14-2 Authenticating a Wireless Client
Wireless authentication can take many forms. Some methods require only a static text string that is common across all trusted clients and APs. The text string is stored on the client device and presented directly to the AP when needed. What might happen if the device was stolen or lost? Most likely, any user who possessed the device could still authenticate to the network. Other more stringent authentication methods require interaction with a corporate user database. In those cases, the end user must enter a valid username and password—something that would not be known to a thief or an imposter.
If you have ever joined a wireless network, you might have focused on authenticating your device or yourself, while implicitly trusting the nearest AP. For example, if you turn on your wireless device and find a wireless network that is available at your workplace, you probably join it without hesitating. The same is true for wireless networks in an airport, a hotel, a hot spot, or in your home—you expect the AP that is advertising the SSID to be owned and operated by the entity where you are located. But how can you be sure?
Normally, the only piece of information you have is the SSID being broadcast or advertised by an AP. If the SSID looks familiar, you will likely choose to join it. Perhaps your computer is configured to automatically connect to a known SSID so that it associates without your intervention. Either way, you might unwittingly join the same SSID even if it was being advertised by an imposter.
Some common attacks focus on a malicious user pretending to be an AP. The fake AP can send beacons, answer probes, and associate clients just like the real AP it is impersonating. Once a client associates with the fake AP, the attacker can easily intercept all communication to and from the client from its central position. A fake AP could also send spoofed management frames to disassociate or deauthenticate legitimate and active clients, just to disrupt normal network operation.
To prevent this type of man-in-the-middle attack, the client should authenticate the AP before the client itself is authenticated. Figure 14-3 shows a simple scenario. Even further, any management frames received by a client should be authenticated too, as proof that they were sent by a legitimate and expected AP.
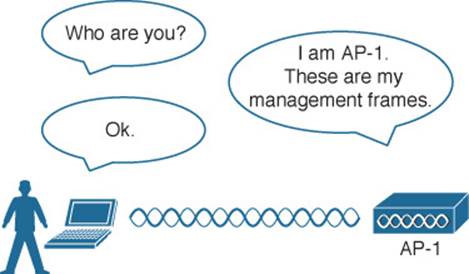
Figure 14-3 Authenticating a Wireless AP
Message Privacy
Suppose that the client in Figure 14-3 must authenticate before joining the wireless network. It might also authenticate the AP and its management frames after it associates but before it is itself authenticated. The client’s relationship with the AP might become much more trusted, but data passing to and from the client is still available to eavesdroppers on the same channel.
To protect data privacy on a wireless network, the data should be encrypted for its journey through free space. This is accomplished by encrypting the data payload in each wireless frame just prior to being transmitted, then decrypting it as it is received. The idea is to use an encryption method that the transmitter and receiver share, so the data can be encrypted and decrypted successfully.
In wireless networks, each WLAN may support only one authentication and encryption scheme, so all clients must use the same encryption method when they associate. You might think that having one encryption method in common would allow every client to eavesdrop on every other client. That is not necessarily the case because the AP should securely negotiate an encryption key to use for each associated client.
Ideally, the AP and a client are the only two devices that have the encryption keys in common so that they can understand each other’s data. No other device should know about or be able to use the same keys to eavesdrop and decrypt the data. In Figure 14-4, the client’s confidential password information has been encrypted before being transmitted. The AP can decrypt it successfully before forwarding it onto the wired network, but other wireless devices cannot.
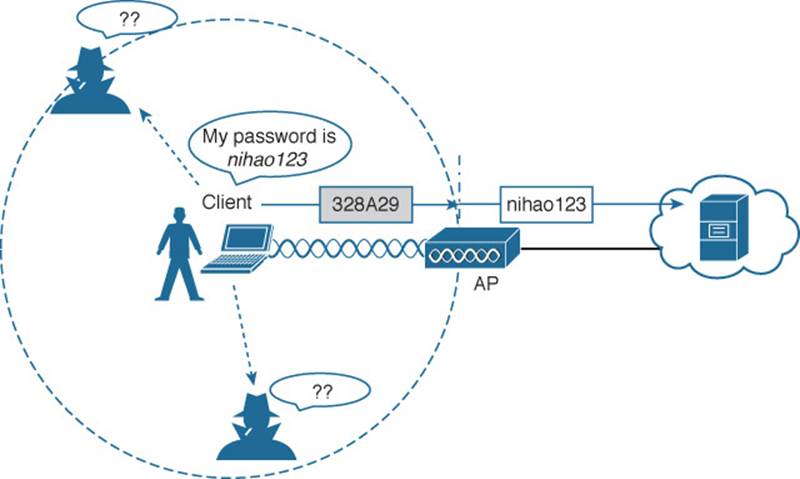
Figure 14-4 Encrypting Wireless Data to Protect Data Privacy
The AP also maintains a “group key” that it uses when it needs to send encrypted data to all clients in its cell at one time. Each of the associated clients uses the same group key to decrypt the data.
Message Integrity
Encrypting data obscures it from view while it is traveling over a public or untrusted network. The intended recipient should be able to decrypt the message and recover the original contents, but what if someone managed to alter the contents along the way? The recipient would have a very difficult time discovering that the original data had been modified.
A message integrity check (MIC) is a security tool that can protect against data tampering. You can think of a MIC as a way for the sender to add a secret stamp inside the encrypted data frame. The stamp is based on the contents of the data bits to be transmitted. Once the recipient decrypts the frame, it can compare the secret stamp to its own idea of what the stamp should be, based on the data bits that were received. If the two stamps are identical, the recipient can safely assume that the data has not been tampered with. Figure 14-5 shows the MIC process.
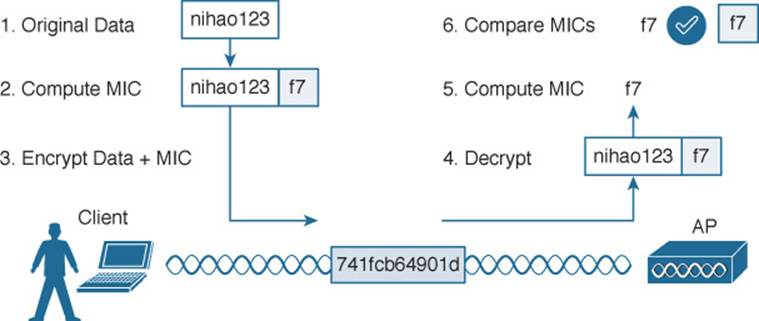
Figure 14-5 Checking Message Integrity over a Wireless Network
Intrusion Protection
Many of the tools in the wireless security framework operate as choreographed steps between a client and an AP. Because both the client and the AP are active participants in securing the connection between them, the data they are exchanging can be protected. In other words, much of the security framework focuses on keeping attackers from joining the wireless network and from tampering with existing associations.
Wireless attacks do not stop there; they can involve malicious activity from a variety of angles or vectors. A wireless intrusion detection system (IDS) can monitor wireless activity and compare that against a database of known signatures or patterns. Cisco APs can recognize some signatures and inform their controllers. Controllers have a set of 17 signatures that can match against data coming from many APs. Controller-based IDS can also detect rogue APs and contain them, if needed.
Cisco Prime Infrastructure (PI) is a wireless management system that can go even further by offering a wireless intrusion protection system (wIPS). The wIPS can recognize a rich set of hundreds of signatures, implementing customizable policies to blacklist clients or rogue devices and block SSIDs. It can also integrate with Cisco Mobility Services Engine (MSE) for granular analysis. Chapter 18, “Managing Cisco Wireless Networks,” discusses the PI platform in greater detail.
For the CCNA Wireless exam, you should understand the basics of wireless IPS. Know that wireless security threats can be grouped into the following categories:
![]() Rogue devices
Rogue devices
![]() Ad hoc networks
Ad hoc networks
![]() Client association issues
Client association issues
![]() Passive or active attacks
Passive or active attacks
Despite your best efforts to configure and secure every piece of your wireless network, someone could always bring in his own AP or wireless router and connect it to the wired network. A rogue AP is one that is not part of your wireless infrastructure but that is close enough to be overheard or to cause interference. Any clients that associate with a rogue AP are known as rogue clients. Cisco controllers can discover both.
Controllers can collect beacon information that is overheard by legitimate APs. Rogue AP detection algorithms running on the controllers and Prime Infrastructure can classify APs as rogue if they do not appear in the database of APs known to your network. As a wireless network administrator, you can override the classification and declare an AP as either friendly or rogue.
When coupled with an MSE, Prime Infrastructure can locate rogue APs so that you can go and find them. Controllers can even transmit special probe frames to determine if a rogue AP is connected to your wired network. This happens if the probe frames are received by the rogue AP over the air and then delivered back to the controller through the wired network.
Controllers can go one step further and attempt to contain the rogue AP so that it does not become a security risk to your own network. Over-the-air rogue containment works by listening for any wireless clients that associate with a rogue AP. The controller then sends spoofed deauthentication frames to those clients so that they think the rogue AP has dropped them.
Based on information gathered by the controllers, a wIPS can detect many types of wireless network attacks. Attacks can range from completely passive, such as an eavesdropper silently capturing wireless frames, to active ones that attempt to disrupt wireless service. For example, an attacker might send a flood of association requests to an AP to overwhelm it with fake potential clients—to the point where the AP can no longer service real clients. Another type of attack is similar to Cisco’s rogue containment, where the attacker sends spoofed deauthentication frames to legitimate clients to continually knock them off the network.
Tip
In a nutshell, controller-based IDS can detect and contain, while PI-based wIPS can detect, contain, and prevent. Although you should not need to know the specifics about wireless IDS and IPS and their respective attack signatures, you can investigate further on your own by navigating to Security > Wireless Protection Policies on a controller and Services > Mobility Services > wIPS Profiles in Prime Infrastructure.
Wireless Client Authentication Methods
You can use many different methods to authenticate wireless clients as they try to associate with the network. The methods have been introduced over time, and have evolved as security weaknesses have been exposed and wireless hardware has advanced. This section covers the most common authentication methods you might encounter.
Open Authentication
In Chapter 6, you learned about the frames that are used when a client asks to join a wireless network. The original 802.11 standard offered only two choices to authenticate a client: open authentication and WEP.
Open authentication is true to its name; it offers open access to a WLAN. The only requirement is that a client must use an 802.11 authentication request before it attempts to associate with an AP. No other credentials are needed.
When would you want to use open authentication? After all, it does not sound very secure, because it is not. With no challenge, any 802.11 client may authenticate to access the network. That is, in fact, the whole purpose of open authentication—to validate that a client is a valid 802.11 device by authenticating the wireless hardware and the protocol. Authenticating the user’s identity is handled as a true security process through other means.
You have probably seen a WLAN with open authentication when you have visited a public location. If any client screening is used at all, it comes in the form of web authentication (WebAuth). A client can associate right away, but must open a web browser to see and accept the terms for use and enter basic credentials. From that point, network access is opened up for the client. Most client operating systems flag such networks to warn you that your wireless data will not be secured in any way if you join. Figure 14-6 shows an open WLAN discovered on a Windows-based client. Notice the shield-shaped caution icon and the security type Unsecured.
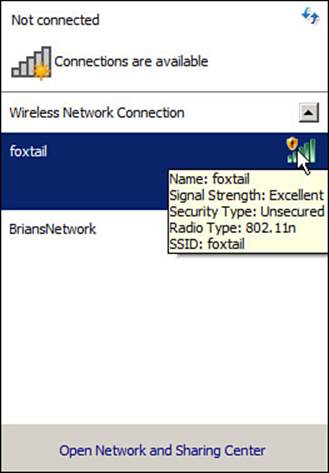
Figure 14-6 Discovering a WLAN with Open Authentication
WEP
As you might expect, open authentication offers nothing that can obscure or encrypt the data being sent between a client and an AP. As an alternative, the 802.11 standard has traditionally defined Wired Equivalent Privacy (WEP) as a method to make a wireless link more like or equivalent to a wired connection.
WEP uses the RC4 cipher algorithm to make every wireless data frame private and hidden from eavesdroppers. The same algorithm encrypts data at the sender and decrypts it at the receiver. The algorithm uses a string of bits as a key, commonly called a WEP key, to derive other encryption keys—one per wireless frame. As long as the sender and receiver have an identical key, one can decrypt what the other encrypts.
You can configure up to four WEP keys to be used on a WLAN, although only one of them can be active. The key number is included in the wireless frame so that the sender and receiver can know which one of the four to use.
WEP is known as a shared-key security method. The same key must be shared between the sender and receiver ahead of time, so that each can derive other mutually agreeable encryption keys. In fact, every potential client and AP must share the same key ahead of time so that any client can associate with the AP.
The WEP key can also be used as an optional authentication method as well as an encryption tool. Unless a client can use the correct WEP key, it cannot associate with an AP. The AP tests the client’s knowledge of the WEP key by sending it a random challenge phrase. The client encrypts the challenge phrase with WEP and returns the result to the AP. The AP can compare the client’s encryption with its own to see whether the two WEP keys yield identical results.
WEP keys can be either 40 or 104 bits long, represented by a string of 10 or 26 hex digits. As a rule of thumb, longer keys offer more unique bits for the algorithm, resulting in more robust encryption. Except in WEP’s case, that is. Because WEP was defined in the original 802.11 standard in 1999, every wireless adapter was built with encryption hardware specific to WEP. In 2001, a number of weaknesses were discovered and revealed, so work began to find better wireless security methods. By 2004, the 802.11i amendment was ratified and WEP was officially deprecated. Both WEP encryption and WEP shared-key authentication are widely considered to be weak methods to secure a wireless LAN.
You might think such a clear call to move away from a weak or flawed security method would be easy and quick to achieve. In practice, it has taken many years to move away from WEP. Why?
Because WEP was implemented in wireless adapter hardware, any better security schemes had to leverage variations of WEP without the benefit of new cryptographic hardware. Wireless hardware manufacturers are usually reluctant to commit to build products until the technology is firmly established in the IEEE 802.11 standard. Therefore, WEP was an underlying theme for a very long time. In fact, for backward compatibility, you will still find it supported by clients, APs, and controllers even today. As you work through the rest of this chapter, notice how wireless security schemes have evolved and improved, and notice how many of them leverage WEP to some extent.
802.1x/EAP
With only open authentication and WEP available in the original 802.11 standard, a more secure authentication method was needed. Client authentication generally involves some sort of challenge, a response, and then a decision to grant access. Behind the scenes, it can also involve an exchange of session or encryption keys, in addition to other parameters needed for client access. Each authentication method might have unique requirements as a unique way to pass information between the client and the AP.
Rather than build additional authentication methods into the 802.11 standard, a more flexible and scalable authentication framework, the Extensible Authentication Protocol (EAP), was chosen. As its name implies, EAP is extensible and does not consist of any one authentication method. Instead, EAP defines a set of common functions that actual authentication methods can use to authenticate users. As you read through this section, notice how many authentication methods have EAP in their names. Each method is unique and different, but each one follows the EAP framework.
EAP has another interesting quality: It can integrate with the IEEE 802.1x port-based access control standard. When 802.1x is enabled, it limits access to a network media until a client authenticates. This means that a wireless client might be able to associate with an AP, but will not be able to pass data to any other part of the network until it successfully authenticates.
With open and WEP authentication, wireless clients are authenticated locally at the AP without further intervention. The scenario changes with 802.1x; the client uses open authentication to associate with the AP, and then the actual client authentication process occurs at a dedicated authentication server. Figure 14-7 shows the three-party 802.1x arrangement that consists of the following entities:
![]()
![]() Supplicant—The client device that is requesting access
Supplicant—The client device that is requesting access
![]() Authenticator—The network device that provides access to the network (usually a wireless LAN controller [WLC])
Authenticator—The network device that provides access to the network (usually a wireless LAN controller [WLC])
![]() Authentication server (AS)—The device that takes user or client credentials and permits or denies network access based on a user database and policies (usually a RADIUS server)
Authentication server (AS)—The device that takes user or client credentials and permits or denies network access based on a user database and policies (usually a RADIUS server)
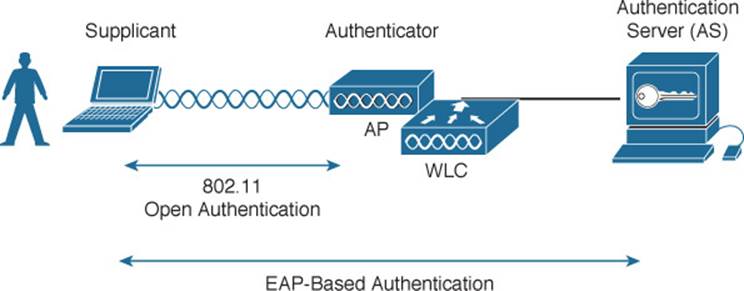
Figure 14-7 802.1x Client Authentication Roles
The controller becomes a middleman in the client authentication process, controlling user access with 802.1x and communicating with the authentication server using the EAP framework.
The following sections provide an overview of several common EAP-based authentication methods.
LEAP
As an early attempt to address the weaknesses in WEP, Cisco developed a proprietary wireless authentication method called Lightweight EAP (LEAP). To authenticate, the client must supply username and password credentials. Both the authentication server and the client exchange challenge messages that are then encrypted and returned. This provides mutual authentication; as long as the messages can be decrypted successfully, the client and the AS have essentially authenticated each other.
At the time, WEP-based hardware was still widely used. Therefore, LEAP attempted to overcome WEP weaknesses by using dynamic WEP keys that changed frequently. Nevertheless, the method used to encrypt the challenge messages was found to be vulnerable, so LEAP has since been deprecated. Even though wireless clients and controllers still offer LEAP, you should not use it.
EAP-FAST
Cisco developed a more secure method called EAP Flexible Authentication by Secure Tunneling (EAP-FAST). Authentication credentials are protected by passing a protected access credential (PAC) between the AS and the supplicant. The PAC is a form of shared secret that is generated by the AS and used for mutual authentication. EAP-FAST is a sequence of three phases:
![]() Phase 0—The PAC is generated or provisioned and installed on the client.
Phase 0—The PAC is generated or provisioned and installed on the client.
![]() Phase 1—After the supplicant and AS have authenticated each other, they negotiate a Transport Layer Security (TLS) tunnel.
Phase 1—After the supplicant and AS have authenticated each other, they negotiate a Transport Layer Security (TLS) tunnel.
![]() Phase 2—The end user can then be authenticated through the TLS tunnel for additional security.
Phase 2—The end user can then be authenticated through the TLS tunnel for additional security.
Notice that two separate authentication processes occur in EAP-FAST—one between the AS and the supplicant and another with the end user. These occur in a nested fashion, as an outer authentication (outside the TLS tunnel) and an inner authentication (inside the TLS tunnel).
The PAC is made up of three parts:
![]() PAC key—A 32-octet key used to establish the tunnel
PAC key—A 32-octet key used to establish the tunnel
![]() PAC-Opaque—A variable length field that contains the user credentials
PAC-Opaque—A variable length field that contains the user credentials
![]() PAC-Info—A variable length field used to pass information about the PAC issuer, PAC key lifetime, and so on
PAC-Info—A variable length field used to pass information about the PAC issuer, PAC key lifetime, and so on
Like other EAP-based methods, a RADIUS server is required. However, the RADIUS server must also operate as an EAP-FAST server to be able to generate PACs, one per user.
PEAP
Like EAP-FAST, the Protected EAP (PEAP) method uses an inner and outer authentication; however, the AS presents a digital certificate to authenticate itself with the supplicant in the outer authentication. If the supplicant is satisfied with the identity of the AS, the two will build a TLS tunnel to be used for the inner client authentication and encryption key exchange.
The digital certificate of the AS consists of data in a standard format that identifies the owner and is “signed” or validated by a third party. The third party is known as a certificate authority (CA) and is known and trusted by both the AS and the supplicants. The supplicant must also possess the CA certificate just so that it can validate the one it receives from the AS. The certificate is also used to pass a public key, in plain view, which can be used to help decrypt messages from the AS.
Notice that only the AS has a certificate for PEAP. That means the supplicant can readily authenticate the AS. The client does not have or use a certificate of its own, so it must be authenticated within the TLS tunnel using one of the following two methods:
![]() MSCHAPv2—Microsoft Challenge Authentication Protocol version 2
MSCHAPv2—Microsoft Challenge Authentication Protocol version 2
![]() GTC—Generic Token Card; a hardware device that generates one-time passwords for the user or a manually generated password
GTC—Generic Token Card; a hardware device that generates one-time passwords for the user or a manually generated password
EAP-TLS
PEAP leverages a digital certificate on the AS as a robust method to authenticate the RADIUS server. It is easy to obtain and install a certificate on a single server, but the clients are left to identify themselves through other means. EAP Transport Layer Security (EAP-TLS) goes one step further by requiring certificates on the AS and on every client device.
With EAP-TLS, the AS and the supplicant exchange certificates and can authenticate each other. A TLS tunnel is built afterward so that encryption key material can be securely exchanged.
EAP-TLS is considered to be the most secure wireless authentication method available; however, implementing it can sometimes be complex. Along with the AS, each wireless client must obtain and install a certificate. Manually installing certificates on hundreds or thousands of clients can be impractical. Instead, you would need to implement a Public Key Infrastructure (PKI) that could supply certificates securely and efficiently and revoke them when a client or user should no longer have access to the network. This usually involves setting up your own CA or building a trust relationship with a third-party CA that can supply certificates to your clients.
Tip
EAP-TLS is practical only if the wireless clients can accept and use digital certificates. Many wireless devices, such as communicators, medical devices, and RFID tags, have an underlying operating system that cannot interface with a CA or use certificates.
Wireless Privacy and Integrity Methods
The original 802.11 standard supported only one method to secure wireless data from eavesdroppers: WEP. As you have learned in this chapter, WEP has been compromised, deprecated, and can no longer be recommended. What other options are available to encrypt data and protect its integrity as it travels through free space?
TKIP
During the time when WEP was embedded in wireless client and AP hardware, yet was known to be vulnerable, the Temporal Key Integrity Protocol (TKIP) was developed. TKIP is the product of the 802.11i working group and the Wi-Fi Alliance.
TKIP adds the following security features using legacy hardware and the underlying WEP encryption:
![]() MIC—An efficient algorithm to add a hash value to each frame as a message integrity check to prevent tampering; commonly called “Michael” as an informal reference to MIC.
MIC—An efficient algorithm to add a hash value to each frame as a message integrity check to prevent tampering; commonly called “Michael” as an informal reference to MIC.
![]() Time stamp—A time stamp is added into the MIC to prevent replay attacks that attempt to reuse or replay frames that have already been sent
Time stamp—A time stamp is added into the MIC to prevent replay attacks that attempt to reuse or replay frames that have already been sent
![]() Sender’s MAC address—The MIC also includes the sender’s MAC address as evidence of the frame source.
Sender’s MAC address—The MIC also includes the sender’s MAC address as evidence of the frame source.
![]() TKIP sequence counter—Provides a record of frames sent by a unique MAC address, to prevent frames from being replayed as an attack.
TKIP sequence counter—Provides a record of frames sent by a unique MAC address, to prevent frames from being replayed as an attack.
![]() Key mixing algorithm—Computes a unique 128-bit WEP key for each frame.
Key mixing algorithm—Computes a unique 128-bit WEP key for each frame.
![]() Longer initialization vector (IV)—The IV size is doubled from 24 to 48 bits, making it virtually impossible to exhaust all WEP keys by brute-force calculation.
Longer initialization vector (IV)—The IV size is doubled from 24 to 48 bits, making it virtually impossible to exhaust all WEP keys by brute-force calculation.
TKIP became a reasonably secure stopgap security method, buying time until the 802.11i standard could be ratified. Some attacks have been created against TKIP, so it, too, should be avoided if a better method is available. In fact, TKIP was deprecated in the 802.11-2012 standard.
CCMP
The Counter/CBC-MAC Protocol (CCMP) is that better method. CCMP consists of two algorithms:
![]() AES counter mode encryption
AES counter mode encryption
![]() Cipher Block Chaining Message Authentication Code (CBC-MAC) used as a message integrity check
Cipher Block Chaining Message Authentication Code (CBC-MAC) used as a message integrity check
The Advanced Encryption Standard (AES) is the current encryption algorithm adopted by U.S. National Institutes of Standards and Technology (NIST) and the U.S. government, and widely used around the world. In other words, AES is open, publicly accessible, and represents the most secure encryption method available today.
Before CCMP can be used to secure a wireless network, the client devices and APs must support the AES counter mode and CBC-MAC in hardware. CCMP cannot be used on legacy devices that support only WEP or TKIP. How can you know if a device supports CCMP? Look for the WPA2 designation, which is described in the following section.
WPA and WPA2
This chapter covers a variety of authentication methods and encryption and message integrity algorithms. When it comes time to configure a WLAN with wireless security, should you try to select some combination of schemes based on which one is best or which one is not deprecated? Which authentication methods are compatible with which encryption algorithms?
The Wi-Fi Alliance has worked out a couple of ways to do that. The IEEE 802.11i standard defines best practice wireless security methods. While that standard was still being developed, the Wi-Fi Alliance introduced its Wi-Fi Protected Access (WPA) industry certification. WPA was based on parts of 802.11i and included 802.1x authentication, TKIP, and a method for dynamic encryption key management.
Once 802.11i was ratified and published, the Wi-Fi Alliance included it in full in its WPA Version 2 (WPA2) certification. WPA2 offers the capabilities of WPA, to be backward compatible, while adding the superior CCMP algorithms. Table 14-2 summarizes the simple differences between WPA and WPA2.
![]()

Table 14-2 Comparing WPA and WPA2
Notice that WPA and WPA2 specify 802.1x, which implies EAP-based authentication, but they do not require any specific EAP method. Instead, the Wi-Fi Alliance certifies interoperability with methods like EAP-TLS, PEAP, EAP-TTLS, and EAP-SIM.
Also notice that WPA can support either TKIP or AES for its data privacy and integrity, while WPA2 supports only AES. This is because TKIP has been deprecated. You should avoid using WPA and leverage WPA2 instead.
The WPA and WPA2 standards also support two authentication modes, based on the scale of the deployment:
![]() Personal mode—A pre-shared key is used to authenticate clients on a WLAN.
Personal mode—A pre-shared key is used to authenticate clients on a WLAN.
![]() Enterprise mode—An 802.1x EAP-based authentication method must be used to authenticate clients.
Enterprise mode—An 802.1x EAP-based authentication method must be used to authenticate clients.
Tip
Personal mode is usually easier to deploy in a small environment or with clients that are embedded in certain devices. Be aware that every device using the WLAN must be configured with an identical pre-shared key. If you ever need to update or change the key, you must touch every device.
Securing Management Frames with MFP
Normally, APs send 802.11 management frames on a BSS with no effort to secure the contents. When clients receive management frames, they assume that the frames were sent by legitimate APs that control their own BSSs. Malicious users can exploit this implicit trust by crafting their own spoofed management frames that appear to come from actual APs.
To mitigate attacks that leverage AP management frames, Cisco developed Management Frame Protection (MFP), which is available in the following two forms:
![]() Infrastructure MFP—To protect the integrity of management frames, APs add a MIC toward the end of each frame; other neighboring APs also participating in infrastructure MFP can determine whether overheard management frames have been tampered with and can alert their controllers.
Infrastructure MFP—To protect the integrity of management frames, APs add a MIC toward the end of each frame; other neighboring APs also participating in infrastructure MFP can determine whether overheard management frames have been tampered with and can alert their controllers.
![]() Client MFP—Protects the integrity of management frames through a MIC and encryption that only associated clients and neighboring APs can understand.
Client MFP—Protects the integrity of management frames through a MIC and encryption that only associated clients and neighboring APs can understand.
Notice that infrastructure MFP is based on a coordinated effort of APs only. Participating APs compute and tag management frames with a MIC value and then listen to detect any evidence of tampering. Wireless clients cannot participate.
Client MFP, in contrast, uses a MIC to protect management frame integrity and adds end-to-end encryption to protect the privacy of management frame contents. Clients must be capable of participating too, to decrypt the management frames and validate the MIC value. Clients using MFP can safely ignore any disassociation, deauthentication, and WMM quality of service (QoS) action frames that are broadcast and any unicast frames that are not signed.
To use client MFP, client devices must support Cisco Compatible Extensions Version 5 (CCXv5) and must use WPA2 with either TKIP or CCMP. This implies that the clients already have a secure relationship with the AP. This same secure link is used to send trusted management frames. The frames are encrypted in a way that only the MFP-capable client can understand. Infrastructure MFP does not require any special client feature.
The 802.11w amendment also addresses protection for management frames using a service called Protected Management Frames (PMF). Only management frames that are considered to be robust are protected: disassociation, deauthentication, and robust action. 802.11w uses security associations (SAs) to protect management frames to clients and an SA teardown protection mechanism to keep malicious devices from spoofing information to tear down existing sessions. 802.11w also protects robust management frames that are broadcast or multicast using the Broadcast/Multicast Integrity Protocol (BIP). 802.11w can be used only on WLANs that are configured for WPA2 personal mode (pre-shared key) or WPA2 enterprise mode (802.1X) security.
Configuring Wireless Security
Wireless security is fairly straightforward to configure. Each WLAN has its own security policies. You can configure the security settings when you create a new WLAN or you can edit the parameters of an existing one. Keep in mind that you should use WPA2 and CCMP as a best practice. You can select personal or enterprise mode based on your environment and its security policies.
According to the CCNA Wireless exam blueprint, you should know how to configure WPA2 with pre-shared keys and 802.1x. You should also know how to configure EAP and RADIUS support on Cisco wireless LAN controllers. These topics are covered in the following sections.
Tip
Wireless security methods are configured on a per-WLAN basis. The configuration steps you learn in this chapter will be applied in Chapter 15, “Configuring a WLAN.”
Configuring WPA2 Personal
You can configure WPA2 personal mode and the pre-shared key in one step. Navigate to WLANs and select Create New or select the WLAN ID of an existing WLAN to edit. Make sure that the parameters on the General tab are set appropriately.
Next, select the Security > Layer 2 tab. In the Layer 2 Security drop-down menu, select WPA+WPA2, as shown in Figure 14-8 for the WLAN named secure. In the WPA+WPA2 Parameters section of the Layer 2 page, you can enable WPA or WPA2 with the WPA Policy and WPA2 Policy-AES check boxes. In Figure 14-9, WPA2 has been selected.
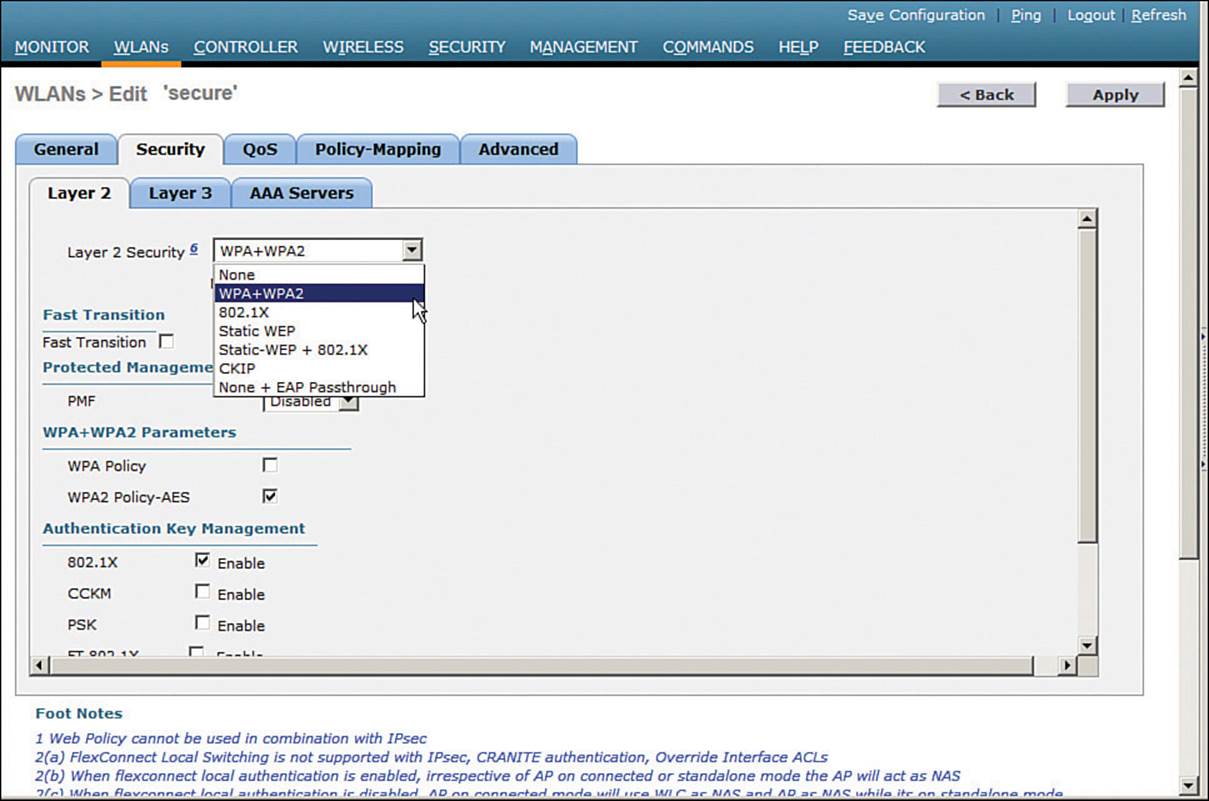
Figure 14-8 Selecting the WPA+WPA2 Security Suite for a WLAN
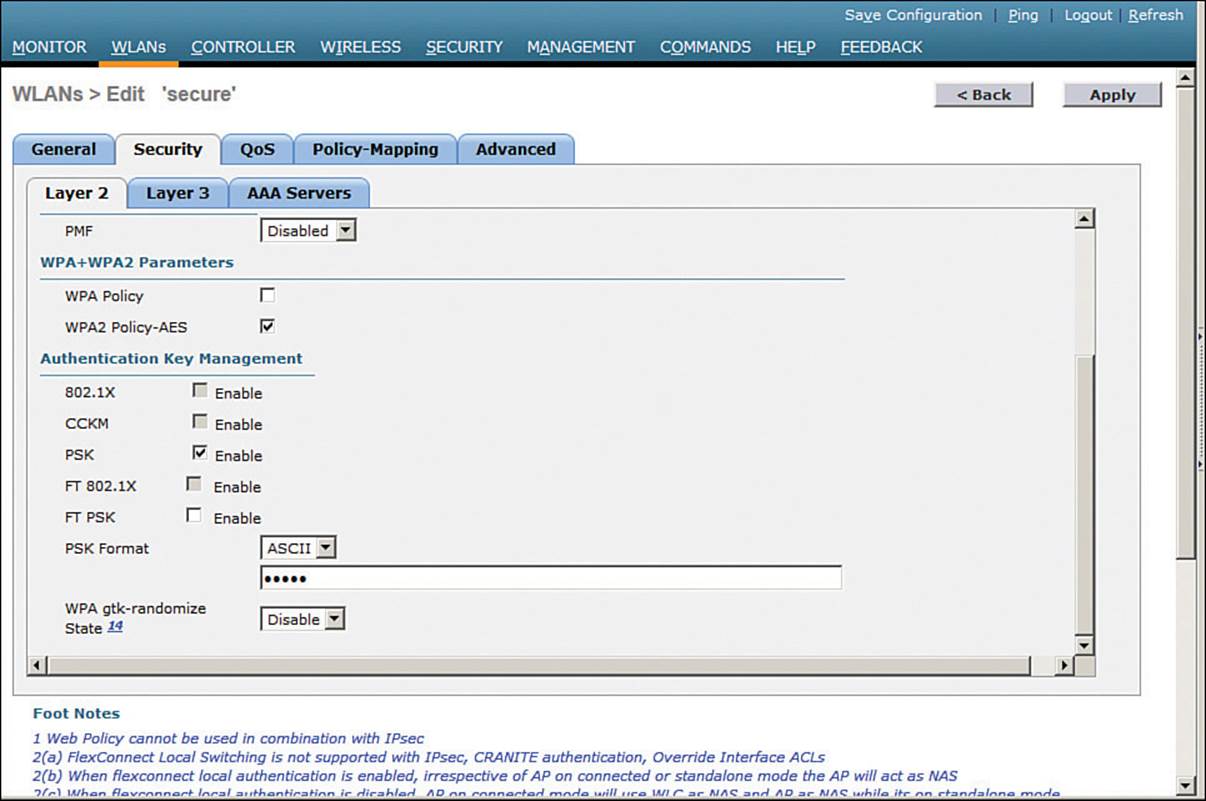
Figure 14-9 Selecting WPA or WPA2-AES and Authentication Key Management
Tip
The controller will allow you to enable both WPA and WPA2 check boxes. You should do that only if you have legacy clients that require WPA support and are mixed in with newer WPA2 clients. Be aware that the WLAN will only be as secure as the weakest security suite you configure on it. Ideally, you should use WPA2 with AES/CCMP and try to avoid any other hybrid mode. Hybrid modes such as WPA with AES and WPA2 with TKIP can cause compatibility issues; in addition, they have been deprecated.
For WPA2 personal mode, select to enable PSK under the Authentication Key Management settings section. This will use a pre-shared key to authenticate clients on the WLAN. Be sure to click the Apply button to apply the WLAN changes you have made.
Configuring WPA2 Enterprise Mode
You can use WPA2 enterprise mode to authenticate wireless clients with 802.1x and EAP through an external RADIUS server located somewhere on the wired network. You should begin by configuring one or more RADIUS servers on the controller. Navigate to Security > AAA > RADIUS > Authentication. Click the New button to define a new server or select the Server Index number to edit an existing server definition.
In Figure 14-10, a new RADIUS server is being defined. Enter the server’s IP address and the shared secret key that the controller will use to communicate with the server. Make sure that the RADIUS port number is correct; if not, you can enter a different port number. The server status should be Enabled, as selected from the drop-down menu. You can disable a server to take it out of service if needed. To authenticate wireless clients, check the Enable box next to Network User. Click the Apply button to apply the new settings.
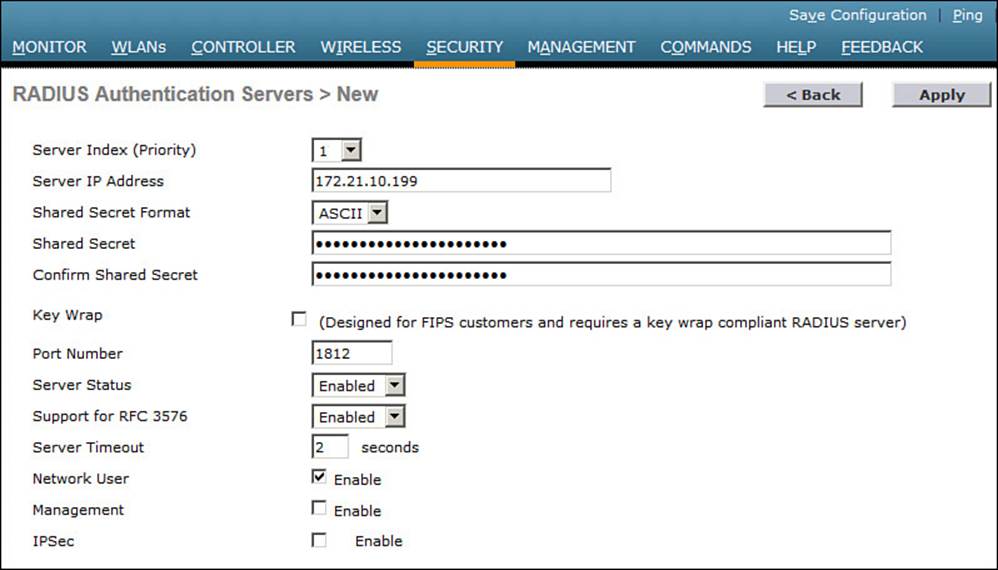
Figure 14-10 Defining a RADIUS Server for WPA2 Enterprise Authentication
Next, you will need to enable 802.1x authentication on the WLAN. Navigate to WLANs and select a new or existing WLAN to edit. Under the Security > Layer 2 tab, select WPA+WPA2 and make sure that the WPA2 Policy-AES box is checked. Select 802.1x under the Authentication Key Management section. Figure 14-11 illustrates the settings that are needed on the WLAN named MoreSecure.
Tip
The default settings for a new WLAN are WPA2 with AES and 802.1x.
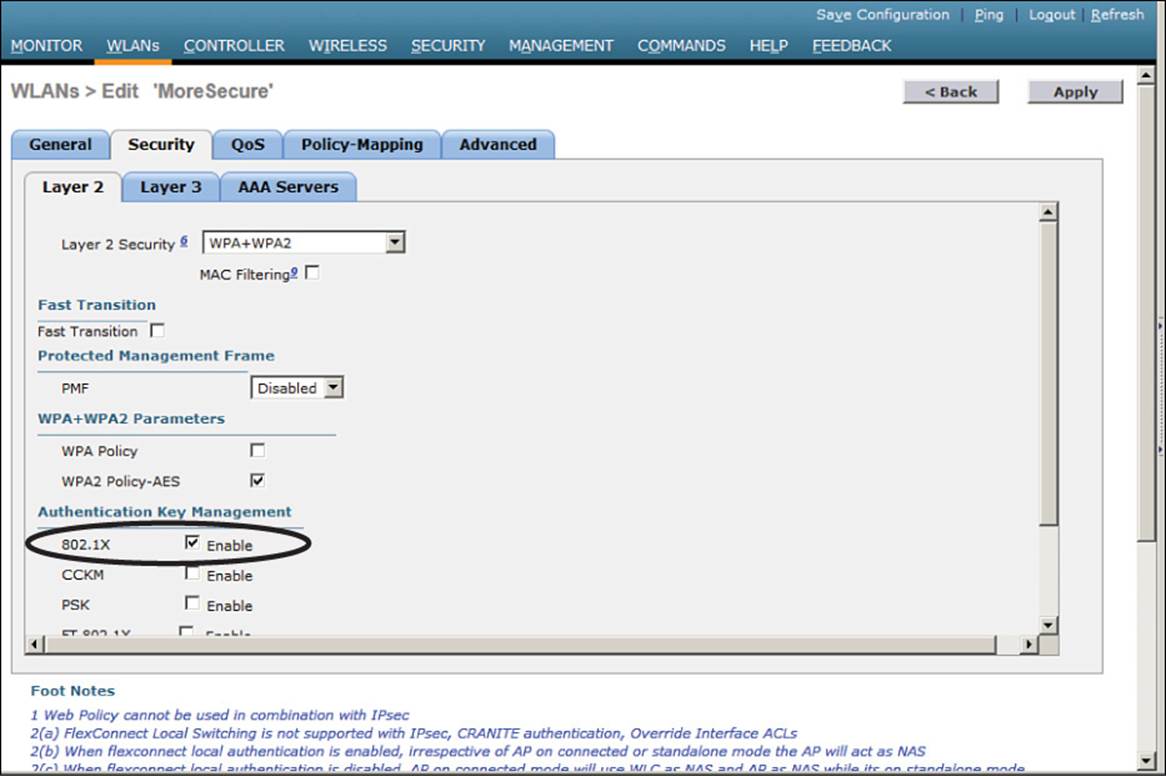
Figure 14-11 Enabling WPA2 Enterprise Mode with 802.1x Authentication
By default, a controller will use the global list of RADIUS servers in the order you have defined under Security > AAA > RADIUS > Authentication. You can override that list on the AAA Servers tab, where you can define which RADIUS servers will be used for 802.1x authentication. You can define up to three RADIUS servers that will be tried in sequential order, designated as Server 1, Server 2, and Server 3. Choose a predefined server by clicking the drop-down menu next to one of the server entries. In Figure 14-12, the RADIUS server at 172.21.10.176 will be used as Server 1. After you finish selecting servers, you can edit other WLAN parameters or click the Apply button to make your configuration changes operational.
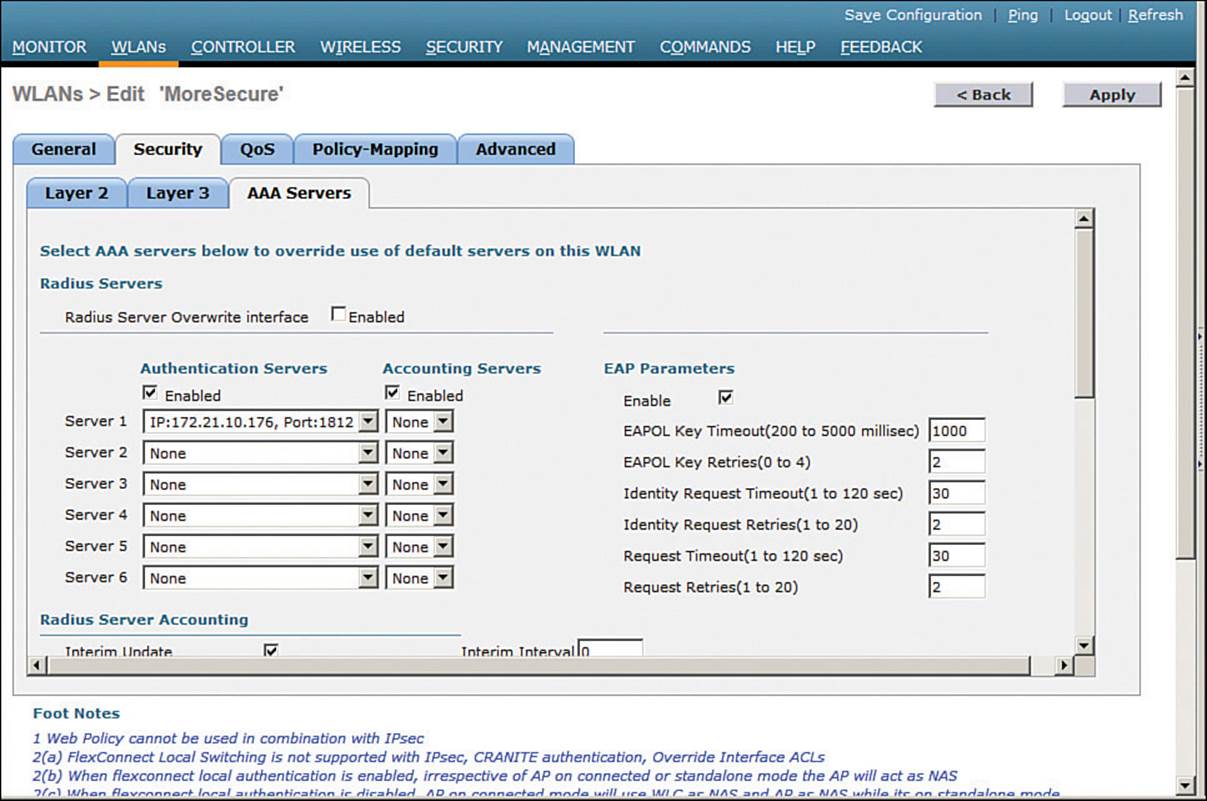
Figure 14-12 Selecting RADIUS Servers to Authenticate Clients in the WLAN
Tip
As you worked through the WPA2 enterprise configuration, did you notice that you never saw an option to use a specific authentication method like PEAP or EAP-TLS? The controller only has to know that 802.1x will be in use. The actual authentication methods are configured on the RADIUS server. The client’s supplicant must also be configured to match what the server is using.
Configuring WPA2 Enterprise with Local EAP
If your environment is relatively small or you do not have a RADIUS server in production, you can use an authentication server that is built in to the WLC. This is called Local EAP, which supports LEAP, EAP-FAST, PEAP, and EAP-TLS.
First, you will need to define and enable the local EAP service on the controller. Navigate to Security > Local EAP > Profiles and click the New button. Enter a name for the local EAP profile, which will be used to define the authentication server methods. In Figure 14-13, a new profile called MyLocalEAP has been defined. Click the Apply button to create the profile. Now you should see the new profile listed, along with the authentication methods it supports, as shown in Figure 14-14. From this list, you can check or uncheck the boxes to enable or disable each method.
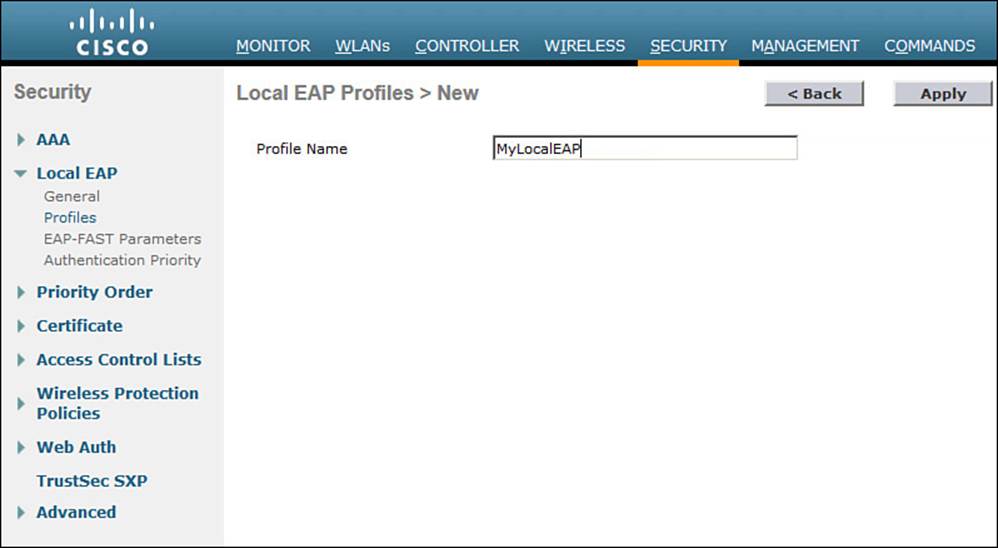
Figure 14-13 Defining a Local EAP Profile on a Controller
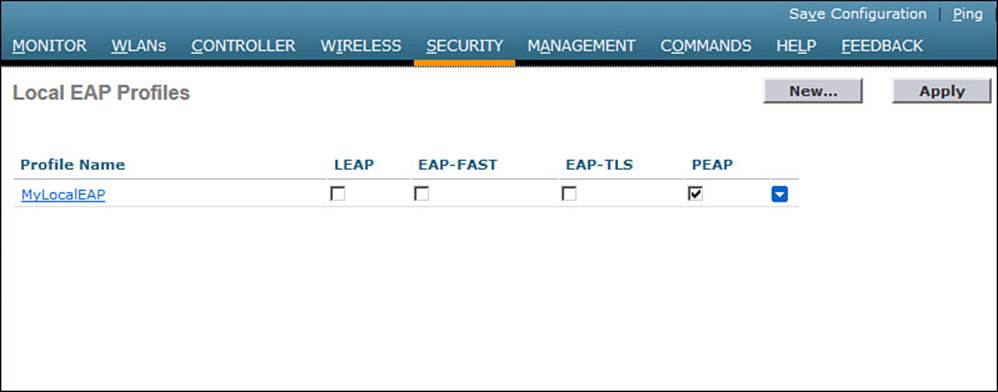
Figure 14-14 Displaying Configured Local EAP Profiles
Select the profile name to edit its parameters. In Figure 14-15, the profile named MyLocalEAP has been configured to use PEAP. Click the Apply button to activate your changes.
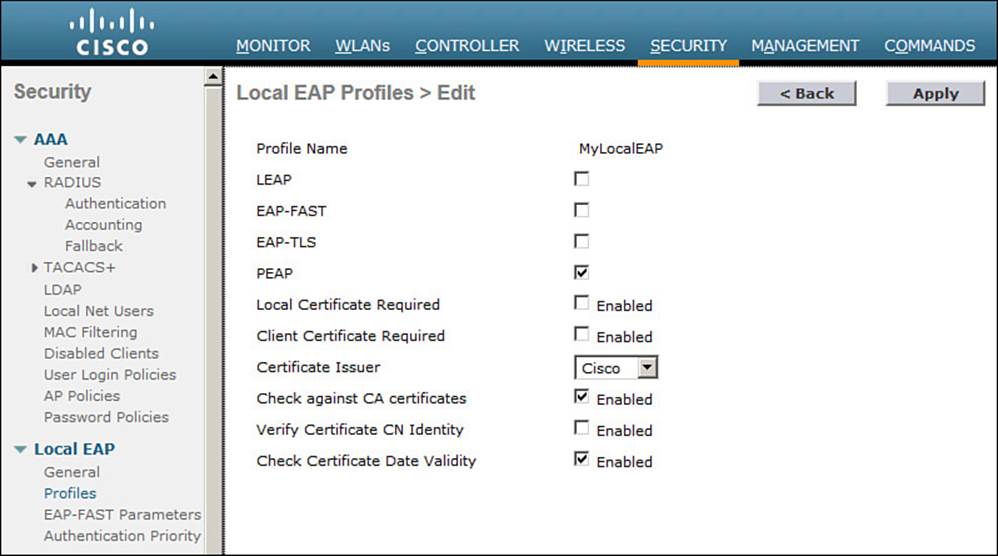
Figure 14-15 Configuring a Local EAP Profile to Use PEAP
Next, you need to configure the WLAN to use the Local EAP server rather than a regular external RADIUS server. Navigate to WLANs, select the WLAN ID, and then select the Security > Layer 2 tab and enable WPA2, AES, and 802.1x as before.
If you have defined any RADIUS servers in the global list under Security > AAA > RADIUS > Authentication or any specific RADIUS servers in the WLAN configuration, the controller will use those first. Local EAP will then be used as a backup method.
To make Local EAP the primary authentication method, you must make sure that no RADIUS servers are defined on the controller. Select the AAA Servers tab and make sure that all three RADIUS servers use None from the drop-down menu. In the Local EAP Authentication section, check the Enabled box to begin using the Local EAP server. Select the EAP profile name that you have previously configured. In Figure 14-16, the Local EAP authentication server is enabled and will use the MyLocalEAP profile, which was configured for PEAP.
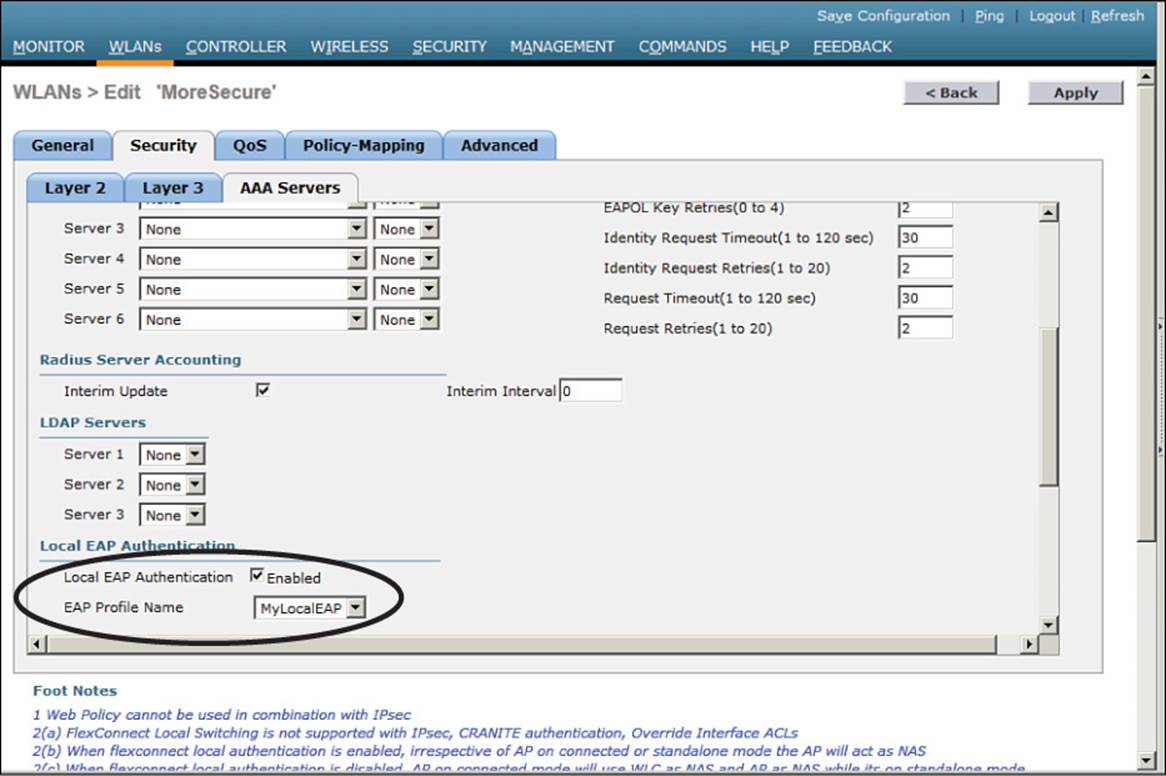
Figure 14-16 Enabling Local EAP Authentication for a WLAN
Because the Local EAP server is local to the controller, you will have to maintain a local database of users or define one or more LDAP servers on the controller. You can create users by navigating to Security > AAA > Local Net Users.
Exam Preparation Tasks
As mentioned in the section, “How to Use This Book,” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 21, “Final Review,” and the exam simulation questions on the DVD.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 14-3 lists a reference of these key topics and the page numbers on which each is found.
![]()

Table 14-3 Key Topics for Chapter 14
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
802.11w
802.1x
authentication server (AS)
authenticator
certificate authority (CA)
Counter/CBC-MAC Protocol (CCMP)
EAP Flexible Authentication by Secure Tunneling (EAP-FAST)
EAP Transport Layer Security (EAP-TLS)
enterprise mode
Extensible Authentication Protocol (EAP)
Lightweight EAP (LEAP)
Management Frame Protection (MFP)
message integrity check (MIC)
open authentication
personal mode
protected access credential (PAC)
Protected EAP (PEAP)
Protected Management Frame (PMF)
Public Key Infrastructure (PKI)
RADIUS server
supplicant
Temporal Key Integrity Protocol (TKIP)
Wired Equivalent Privacy (WEP)
wireless intrusion protection system (wIPS)
Wi-Fi Protected Access (WPA)
WPA Version 2 (WPA2)
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.