Learning Bitcoin (2015)
Chapter 4. Understanding the Blockchain
|
"With e-currency based on cryptographic proof, without the need to trust a third party middleman, money can be secure and transactions effortless." |
||
|
--Satoshi Nakamoto, Bitcoin developer |
||
Bitcoin's underlying transaction database is called the Blockchain. Its novel design, as a distributed ledger, allows it to function without any trusted central authority. Understanding how it works is essential for integrating information systems with Bitcoin. In this chapter, you will be given a simplified explanation of the blockchain's internal mechanisms. Building on the previous chapters, we'll cover the following subjects in more detail:
· Keys, transactions, and blocks
· Digital signatures
· Cryptographic hashes
· The Blockchain
· Nodes and miners
· Decentralized design
· Network attacks
· Alternative coins
The Genesis block
September 15th, 2008 marked a defining moment for the finance industry, as Lehman Brothers, at that time the fourth largest investment bank, filed for chapter 11 bankruptcy after massive losses in stock price and assets. The collapse marked the beginning of the Global Financial Crisis of 2008.
Shortly after, Bitcoin, a new type of virtual currency, was launched by an anonymous developer, or group of developers, under the name Satoshi Nakamoto. The software was built on a publicly-accessible transaction ledger, that is distributed and validated by a network of independent nodes. More importantly, its design was powerfully resilient to attacks.
The mysterious developer launched Bitcoin at the beginning of 2009. Encoded in the first block of transactions was a message highly relevant to the state of global financial affairs at that time:
"The Times 03/Jan/2009 Chancellor on brink of second bailout for banks."
The first block of transactions, called the "genesis block", set forth Bitcoin, a new peer-to-peer digital currency. As the quoted headline was published by The Times on January 3, 2009, the message acts as proof that the block was indeed created after that time. From the intention of the comment on the failure of fractional reserve lending, we get a glimpse into the mind of its developer, Satoshi Nakamoto.
Note
Simply put, fractional reserve banking allows a bank to lend more money than it has on reserve. The modern financial system largely accepts the practice of fractional reserve banking with policy controlled by a central bank. The central bank's primary method of control is through interest rates.
More importantly, Bitcoin and its technology The Blockchain was released and open sourced to the world. The Bitcoin Blockchain was a solution to the difficult problem of preventing double spending when creating a distributed virtual currency.
Double spending occurs when two transactions are accepted with an amount that exceeds the available balance. Up until that time, a decentralized solution to the double spending problem remained open. Satoshi's solution was the Blockchain.
Satoshi Nakamoto
Satoshi Nakamoto has remained anonymous since releasing Bitcoin. Records of his e-mails and forum posts exist from the end of 2008 through 2010. During that time, he worked with developers to release the source code and respond to the development topics. He also commented on relevant financial topics such as banking and fractional reserve lending.
Tip
Satoshi Nakamoto's e-mails and forum posts have been archived on the website of the Satoshi Nakamoto Institute (http://satoshi.nakamotoinstitute.org). It's a great resource for understanding the intentions behind the design of Bitcoin.
As quickly as he appeared, he vanished without much trace. To this day, we don't have much information on him. Many people have theorized about who Satoshi could be, yet nothing we have is conclusive.
However mysterious his character may be, his legacy remains the Bitcoin whitepaper.
The whitepaper
The Bitcoin whitepaper was released to the public on October 31st, 2008, a couple of months before Bitcoin's blockchain was launched. In the whitepaper, Satoshi explained how the blockchain could support a purely decentralized e-currency without the need for a central authority. Satoshi writes:
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without the burdens of going through a financial institution.
The whitepaper mentions the issues with relying on the financial institutions as trusted third parties to process transactions. He particularly mentioned the costs of mediating reversible transactions which put merchants at risk of fraud, thus increasing transaction costs. The principal design goal was to ensure that whoever owns the keys controls the money. The common scenario involves a buyer who orders an item from a merchant using a credit card. As fraud against the merchant, the buyer can dispute the payment or claim an unauthorized payment. In Bitcoin, reversing the transaction is not possible.
Satoshi proposed a solution that relies on cryptographic proof. Transactions are signed and distributed on a public network. The design allows irreversible transactions sent directly between peers without centralized authority.
He was able to deliver the solution, based on a new type of data structure called the blockchain.
Note
You can download a copy of the Bitcoin whitepaper from https://bitcoin.org/bitcoin.pdf.
The blockchain
The public ledger which records each Bitcoin transaction is built on a data structure called the blockchain. Transactions are grouped into blocks, and shared and validated by a network of nodes. Consensus on the network determines which blocks are accepted.
Previously, the double-spending problem was difficult to solve without a trusted third party. To be able to accept a transaction, the available balance had to be validated by a central authority, ensuring synchronization between all the transactions.
Implementing this in a decentralized way was difficult because of the complexities of sharing data between independent nodes. If two transactions were created at the same time, but with only enough funds available for the first transaction, the second must be rejected: the double spending problem.
As we examine the blockchain, we will see how it solves the double spending problem in a resilient and decentralized way.
Keys, transactions, and blocks
To help you understand how Bitcoin transactions work, we'll need to explain how some of its basic mechanisms work with various cryptographic algorithms. With the classic example of sending money between Alice and Bob, we will illustrate how the Bitcoin network confirms a transaction.
Creating a transaction
Let's start with an example where Alice wants to send 4.0BTC to Bob. Alice has a bitcoin wallet with two addresses along with the corresponding private keys that control the two amounts 1.2BTC and 2.8BTC. To receive the money, Bob will generate a private key with a Bitcoin address:
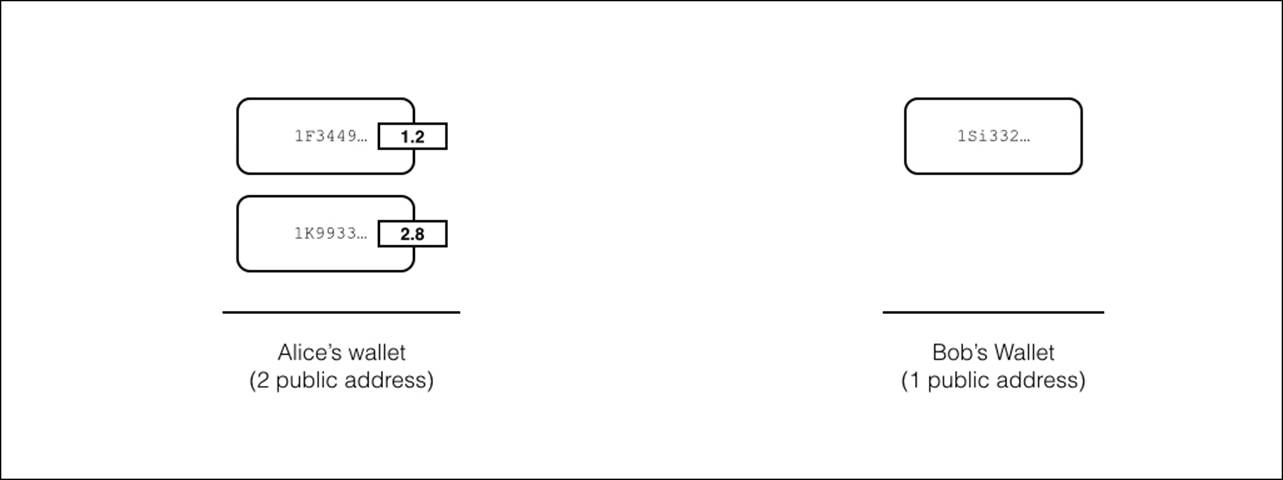
Figure 4.1 - Alice has a wallet with two addresses. Bob has a wallet with one address. Alice wants to send 4.0BTC to Bob.
To transfer the bitcoin, we need to create a valid transaction and broadcast it to the Bitcoin network for confirmation. If confirmed by the network, the transferred amount will be available for spending by the receiver.
The transaction can record a transfer between two or more parties, using many inputs for the sources of bitcoin and many outputs for the receivers of bitcoin. Inputs and outputs are used to move the money between the addresses.
Each input must reference exactly one output from a previous transaction. Thus, on the blockchain, bitcoin is sent through scripts which hand-off the money between the addresses. As each address is controlled by a private key, the money is transferred between the owners of the private keys. There is sometimes the misconception that there is a single bitcoin that gets moved, when in fact there is no bitcoin, or fraction of a bitcoin, that is individually assigned to an address. Transfers of bitcoins are actually controlled by matching the inputs and outputs of the previous transactions. Thus, the full history of transactions funding the transaction are needed to validate a transfer.
The following Figure 4.3, illustrates how the transactions are used to connect the inputs and outputs to send bitcoin. From the example, Alice will send 4.0BTC by combining her two addresses as inputs. Written in the transaction, the amounts 1.2BTC and 2.8BTC are listed as inputs from Alice and sent to Bob as an output with the amount of 4.0BTC.
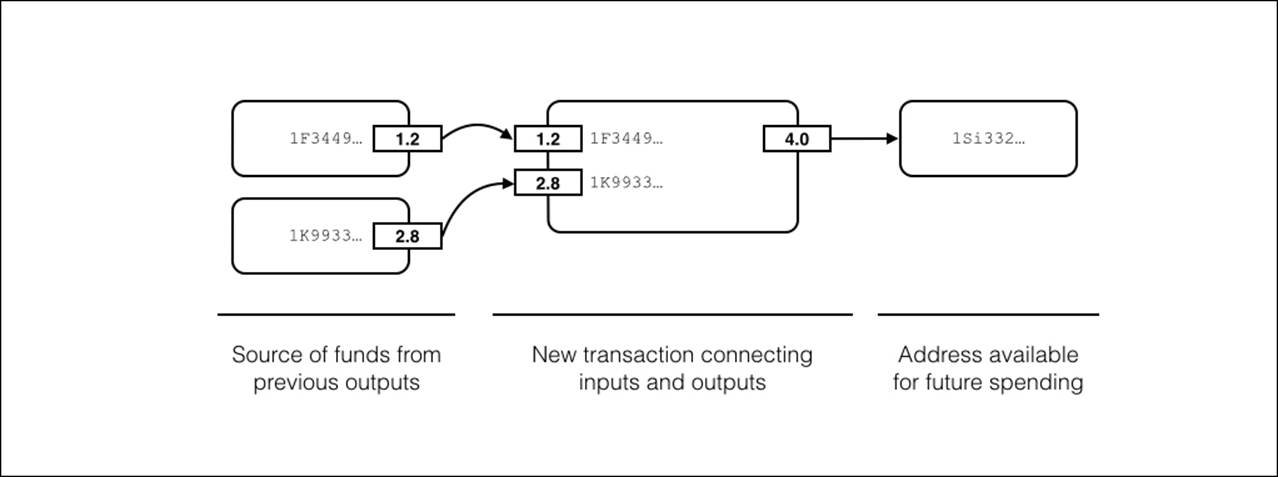
Figure 4.3 - Bitcoin transaction showing its two inputs and one output
Before broadcasting the transaction, we'll need to prove to the network that Alice was the original sender of the transaction. By proving to the network that we have the private keys, the nodes validating the transaction can agree that the transaction originated from the owner.
For each public address listed in Alice's wallet, there is a private key. With her private keys, she can sign the transaction using a digital signature. Verification of the signature is proof that she signed the transaction and that it hasn't been modified since.
After the transaction has been confirmed by the network, Bob will have 4.0BTC available to spend as an input to a new transaction. The linkage continues as transactions continue connecting the inputs and the outputs. Imagining the chain of transactions, one can see how quickly the money is fanned out between new addresses.
Digital signatures
One classic problem addressed by cryptography is how one party can send a document to another party with proof that it was not modified or forged. For example, let's say Alice has a message that she wants to send to Bob. Before trusting the document, Bob wants to be sure that the message has not been modified:
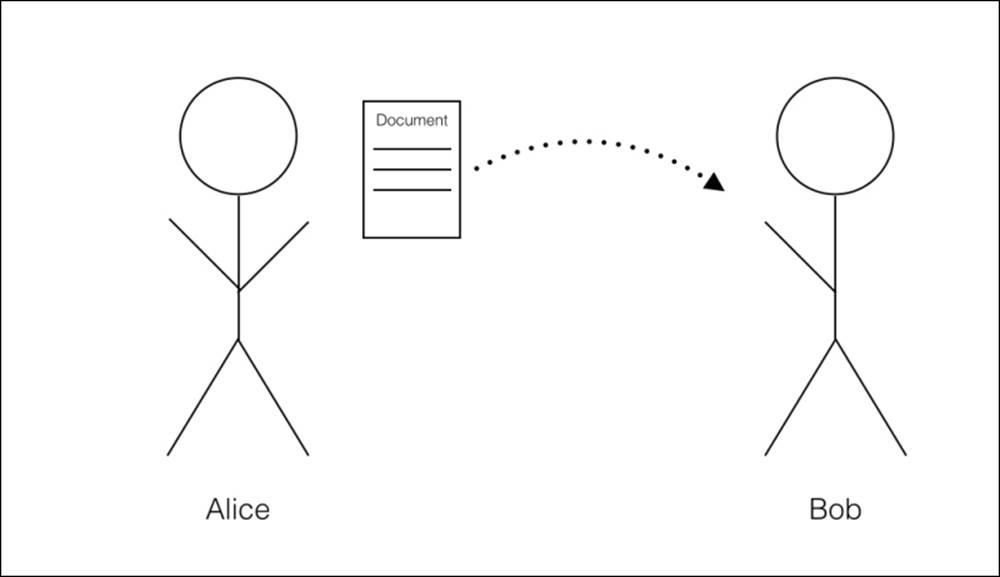
Figure 4.3 - Bob requests proof that the document originated from Alice
Alice needs a way to digitally sign the document with proof that it's an exact copy of the original document. Using a digital signature, Bob can verify the copy. If valid, he can be sure that the document has not been modified.
Digital signatures rely on a set of keys designated as public and private. Signing a document with a private key creates a signature that can be verified with its associated public key. Any signed document verified by the public key can be assumed to be original.
Public key encryption
Public key encryption is a cryptographic algorithm that uses two mathematically generated keys to encrypt and decrypt a message, or to digitally sign a document. The private key is used to encrypt or sign the document, and the public key is used to decrypt the message or verify the signature.
The two keys are generated at the same time by an asymmetric cryptographic algorithm. The keys are mathematically bound and cannot be interchanged. In other words, the public key only functions with its corresponding private key.
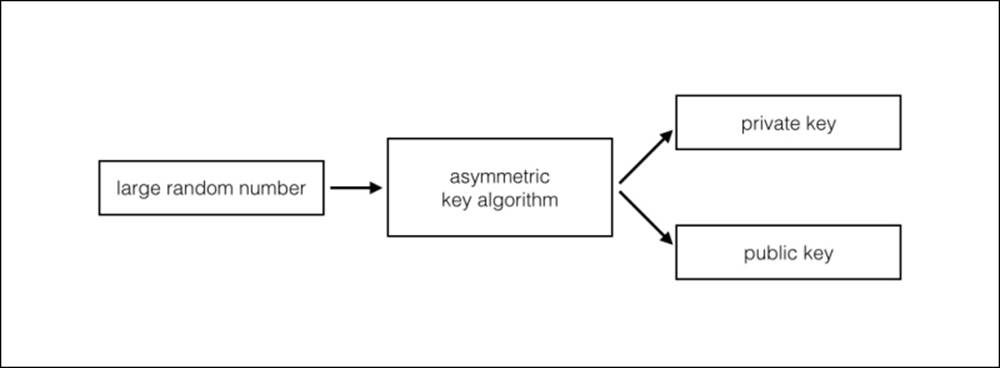
Figure 4.4 - Asymmetric key algorithms generate a public and private key from a large random number
Public and private keys are simply long numbers. An example private key looks as follows:
3082011302010104209ea335d666d9e097c5a5e92ef32228a18c3615aa38e13fb593712a11f039c148a081a53081a2020101302c06072a8648ce3d0101022100fffffffffffffffffffffffffffffffffffffffffffffffffffffffefffffc2f300604010004010704410479be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798483ada7726a3c4655da4fbfc0e1108a8fd17b448a68554199c47d08ffb10d4b8022100fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141020101a14403420004a6b634eb85a8d9d6fe34bc6666760b3343c40f7709392541bc2d3b7666eda4d7c7c8dd578af2790870a591c0f17e285ce99cb2dd950b37b00f1031675bb678d6
Its public key looks as shown next:
04a6b634eb85a8d9d6fe34bc6666760b3343c40f7709392541bc2d3b7666eda4d7c7c8dd578af2790870a591c0f17e285ce99cb2dd950b37b00f1031675bb678d6
These two keys are mathematically related and cannot be interchanged with any other key.
Signing a document
In the example with Alice and Bob, using encryption software, Alice creates a public and private key pair. She then sends a copy of the public key to Bob. As the public key can only be generated by the private key, Bob can assume that Alice is the holder of the private key.
Before sending the document to Bob, Alice signs the document with her private key and includes the signature in the document.
Later, when Bob receives the document, he can verify the signature with the copy of the document. If the signature is valid, Bob can safely assume that Alice was the signer:
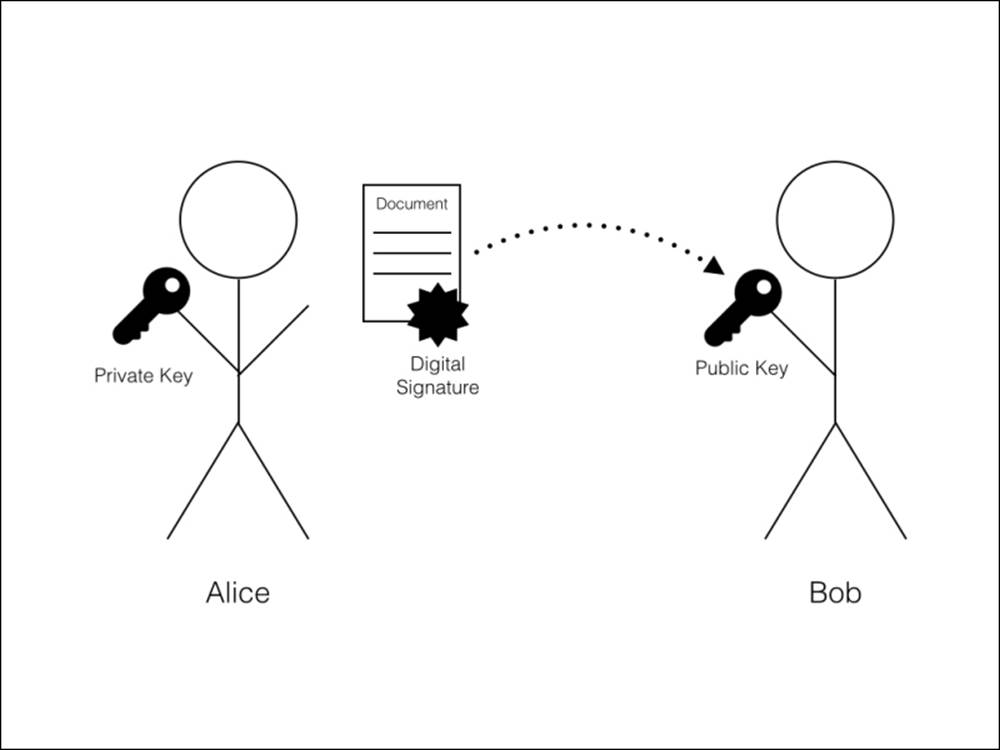
Figure 4.1 - Bob uses Alice's public key to verify that the document originated from her and has not been modified.
Elliptic Curve Cryptography
Bitcoin uses Elliptic Curve Digital Signature Algorithms (ECDSA), for generating public/private key pairs. The algorithm generates random keys based on the mathematics around elliptic curves.
Due to its features, ECDSA is suitable for signing Bitcoin transactions. For example, some algorithms can only generate both keys at the same time. With the ECDSA algorithm, a public key can be generated from a private key any time but not the other way around.
Bitcoin addresses
Bitcoin addresses are generated from the public key through a few steps that involve cryptographic hashes. To explain the process, we'll first introduce cryptographic hashing algorithms.
Cryptographic hashes
Cryptographic hashing algorithms, or just hashes, are functions that can produce a digest of a document. The digest is usually a small string of characters, depending on the hashing algorithm used. As one example, the popular hashing algorithm called SHA256 produces a digest 40 characters in length from a document of any size.
The smallest change to the document will produce a radically different digest. Thus, a digest can be used to verify the changes between the documents.
There is a mathematical relationship between the document and its digest, but it is impossible to generate a document from its digest. Digests do not contain enough information:
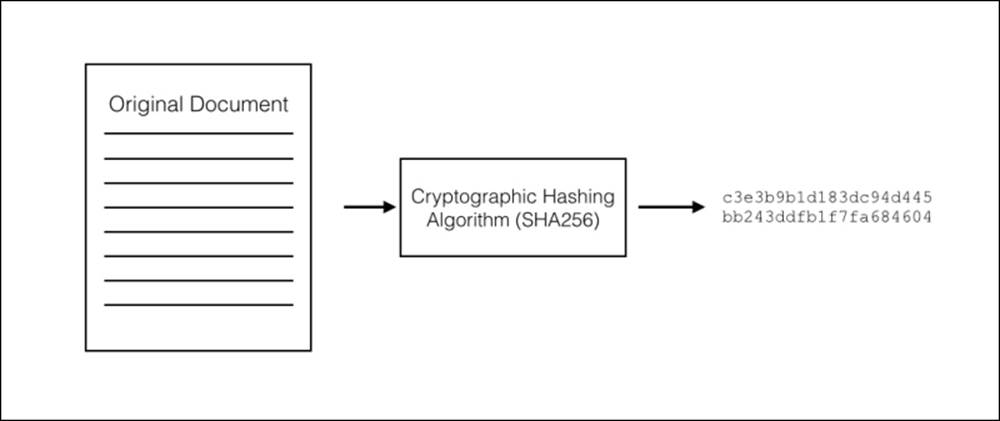
Figure 4.6 - Cryptographic hashes generate a digest of a document, representing the document in its original state.
The digest is useful for verifying if any changes have been made between a copy and its original. By comparing the copy's hash against the original hash, we can verify if the contents have been modified. Thus, cryptographic hashes can be used to seal a valid copy (see Figure 4.7).
In Bitcoin, digital signatures are applied to the transaction and are used to verify that it was created by the holder of the private keys. The Bitcoin address that is used to send the money is created by using different hashing algorithms. The signature and Bitcoin address are both included in the transaction. If valid, the transfer of money can be confirmed on the network.
Bitcoin relies on cryptographic hashes for many of its internal functions. Primarily, every transaction is hashed and the digest is signed to ensure that no changes have been made since it was created by the sender. Blocks of transactions are also hashed to make sure no changes have been made to its list of transactions.
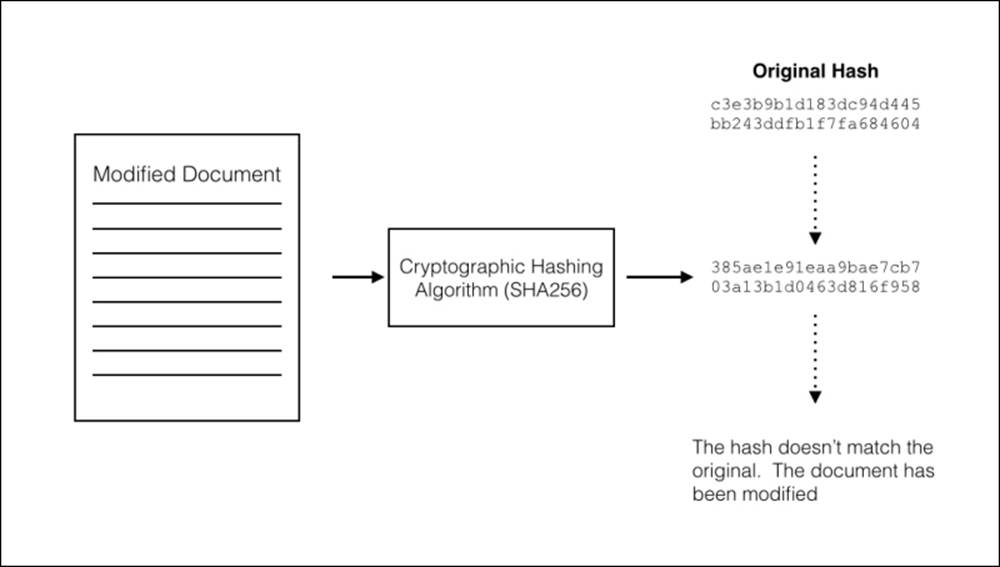
Figure 4.7 - By comparing the digests we can detect changes in the document.
Generating a Bitcoin address
Bitcoin addresses are generated from the public key hash of an ECDSA key pair. Let's walk through a simplified explanation of this process with the follow pair:
Private Key:
18E14A7B6A307F426A94F8114701E7C8E774E7F9A47E2C2035DB29A206321725
Public Key Hash:
600FFE422B4E00731A59557A5CCA46CC183944191006324A447BDB2D98D4B408
Note
The public/private keys listed in the chapter are given in "Hexadecimal" format. Typically, we count numbers with the digits 0 through 9. In hexadecimal, we count with the digits 0 through 9 plus A, B, C, D, E, and F. Thus, in hexadecimal format, there are 16 digits to represent a value. Counting to the decimal number 32 in hexadecimal would look as follows:
0,1,2,3,4,5,6,7,8,9,A,B,C,D,E,F,10,11,12,13,14,15,16,17,18,19,1A,1B,1C,1D,1E,1F
To generate the Bitcoin address, SHA256 and RIPEMD-160 hashing functions are first applied to the public key:
010966776006953D5567439E5E39F86A0D273BEE
To identify which network the address is intended for, a network identifier is added to the front of the address. In the preceding example, we simply add 00, which identifies the main network, to the beginning of the key:
00010966776006953D5567439E5E39F86A0D273BEE
Note
The main network is the official blockchain network used for public transactions. In addition to the main network, there is also a test network, named Testnet3, used by the developers to test bug fixes and new functionality.
Next, a checksum is calculated. Checksums are used to ensure that the address has a valid set of characters. That is, if one of the characters is mistyped, the checksum digit will be invalid. Thus, Bitcoin wallets can use the checksum to make sure you didn't enter a bogus Bitcoin address. In the previous example, the checksum is calculated as "D61967F6" and appended to the end of the string:
00010966776006953D5567439E5E39F86A0D273BEED61967F6
Finally, a BASE58 function is applied to the network identifier, hash, and checksum. BASE58 is a way to encode large numeric values into an alphanumeric string of characters. The BASE58 value can be easily read or written by humans, making it practical for creating Bitcoin public addresses.
16UwLL9Risc3QfPqBUvKofHmBQ7wMtjvM
The result is a public address we can use to receive bitcoin and the private key needed to spend them. Using our Bitcoin wallet or other tools, we can generate unlimited random private keys and their addresses. This process is usually automated.
In summary, we create a private key and its Bitcoin address by starting with a large random number. An Elliptic Curve algorithm is used to generate the private/public key pair from the random number. Finally, the Bitcoin address is generated by transforming the public key through several hashing functions, appending a checksum, and encoding it with BASE58.
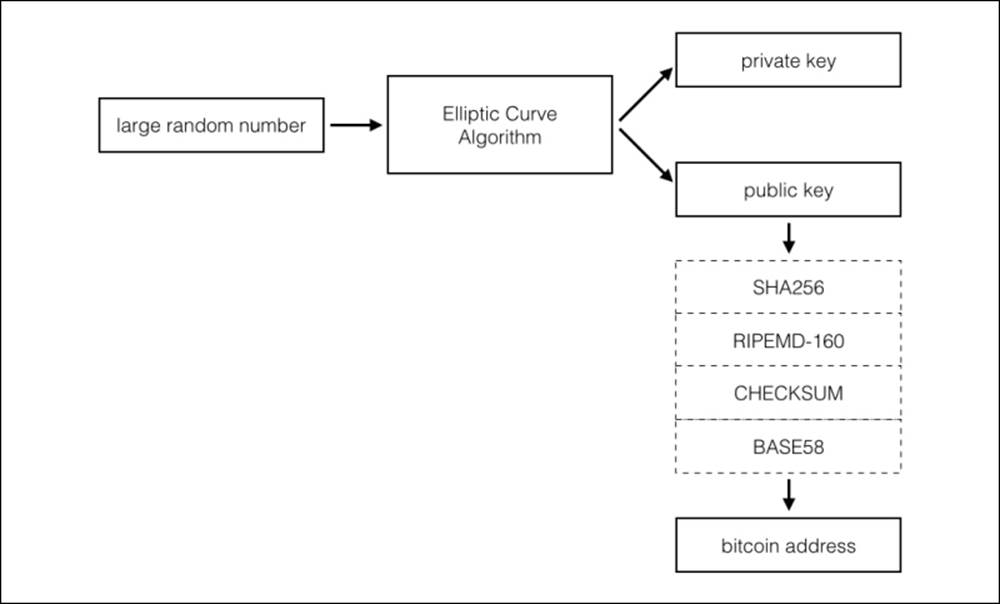
Figure 4.7 - The process of generating a Bitcoin address from a public key
Signing a transaction
The last step needed before broadcasting the transaction to the network is to include a digital signature.
Using the private keys from each input address listed, the sender can prove that they have ownership of the funds stored in the address. The network can then verify the signature with access to the public key. Transactions with invalid digital signatures are simply discarded.
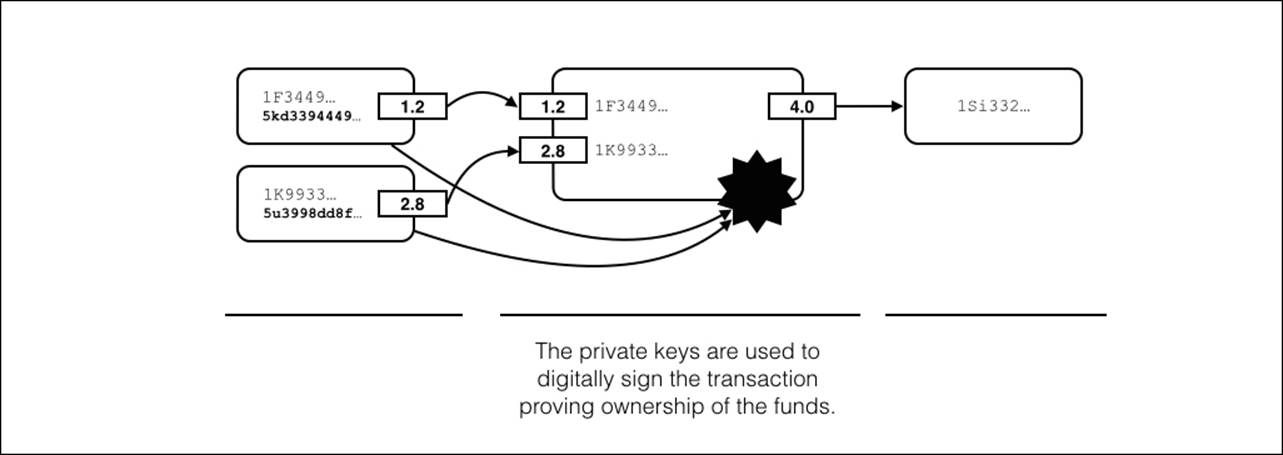
Figure 4.8 - A Bitcoin transaction with the attached digital signature.
At any point, the private key is never shared. Figure 4.8 illustrates the digital signature and how it's attached to the transaction.
Once signed, our valid transaction is now ready to broadcast to the Bitcoin network for confirmation.
Decentralized network
The Bitcoin network consists of many thousands of nodes, with some called miners, and each connected directly to one another. Unlike a centralized or distributed network, Bitcoin relies on a decentralized network.
A decentralized network is extremely resilient because there is no central point of failure. If one or more nodes are taken offline, the remaining nodes can reroute their connection to the network through other online nodes.
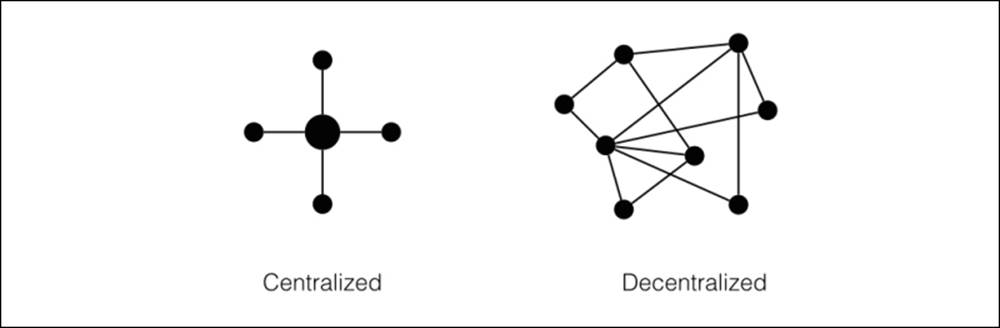
Figure 4.9 - Centralized networks have a single point of failure; this is not so with decentralized networks.
In fact, the early incarnation of the Internet, called ARPANET and built by the US Department of Defense, used a decentralized design to build an information network that would be able to function even if a large portion of the network was down.
Bitcoin is a money protocol that is built on a decentralized network. Each node is independent and can join or leave the network at any time. While on the network, each node can talk to the other nodes using the Bitcoin protocol. With this protocol, it's able to script and validate the transactions or other types of digital contracts.
Bitcoin is essentially programmable money designed to run on a decentralized network.
Broadcasting the transaction
To broadcast our signed transaction to the network, we first need to connect to one or more of the existing nodes. When connected, our node becomes part of the network and is able to send and receive transactions.
The nodes on the network listen for broadcasted transactions and share them with the other nodes. Each node can maintain a copy of every transaction created, and use them to validate new bitcoin transactions and ensure there's sufficient balance before relaying them to the other nodes.
New transactions broadcast to the network are initially labeled as unconfirmed, meaning that the network has not yet agreed that they are valid. A transaction must have sufficient balance and a valid digital signature before it can be validated.
Valid transactions are grouped and into a block by the miner. After a verification process, which involves a difficult mathematical problem, the confirmed blocks are accepted and exchanged between the nodes. The blocks of transactions are time-stamped and chained together to form a "blockchain". Each node maintains its own copy of the blockchain and repeats the process by listening for new transactions.
The blockchain
Bitcoin uses a unique and novel way of storing and distributing its transaction ledger. To create a database of transactions that is both resilient and transparent, it distributes all its transactions across a global network of nodes. This database is called the blockchain. To understand how the blockchain works, we'll explore how the blocks are used to group and distribute the transactions.
Blocks
The blockchain is a chain of blocks linked together, from the genesis block to the latest block, as shown in the following Figure 4.11. Every node connected to the network maintains a complete copy of the entire blockchain. This redundancy results in a very resilient system.
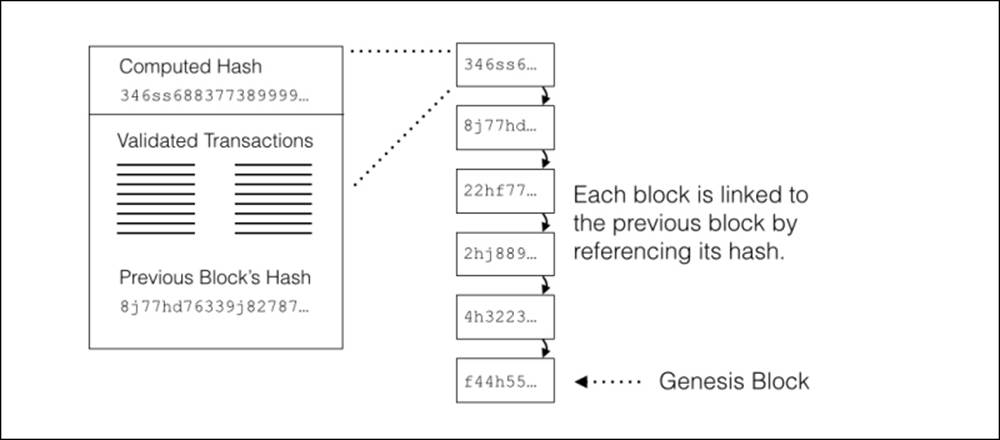
Figure 4.11 - The blockchain consists of many blocks chained together.
New blocks are mined by the nodes listening for transactions on the network. The nodes can share and relay the transactions amongst themselves. When a new transaction is received by a node, it is added to the new block. The new block is kept locally until a difficult computing problem is solved using the new block as the base of the solution.
New blocks with solutions to the difficult problem are eligible for a reward of newly mined bitcoin, plus the transaction fees included with each transaction.
Referring back to cryptographic hashes, a hash value is used to represent the confirmation of the block. A hash value is computed on the block and its transactions, along with the hash value of the previous block. Any changes to the block can be validated against its hash.
The chains of hashes are critical to the integrity of the chain. Each new block contains within it the hash of the previous block. If any of the transactions are modified, the hash, as well as the rest of the chain, becomes invalid. Therefore, as the chain grows and more copies of it are maintained by independent miners, the more difficult it becomes to modify the public ledger.
Today, the Bitcoin network's combined computing power is noted as the largest supercomputer on earth. The large amount of computer power is what protects the Bitcoin network from attacks. Any attacker would need to overtake more than half of the network's computer power to be able to double spend.
The result is a database of transactions that are distributed for redundancy and cryptographically protected from modifications. Anyone can download a copy of the blockchain and query it for transactions. With the full blockchain, the value of any address can be known for any point in time. The addresses with unspent balances can then be used as inputs to a new transaction.
Forks
Due to their independent nature, the network of nodes can consist of either honest or malicious nodes. Honest nodes only accept valid transactions and reject any that double spend or have invalid signatures. Malicious nodes may make an attempt to accept a corrupt transaction or selectively reject the other transactions.
To isolate and reject the bad nodes on the network, consensus between the nodes exists on what ruleset to accept. This consensus determines which blocks are accepted on the network. Since the genesis block, a large majority of the nodes have agreed to "play nicely" rather than to corrupt, due to the reward of earning new bitcoin. This consensus forms the longest and most trustworthy chain.
Due to changes in how the nodes can accept/reject blocks, it is possible for the blockchain to fork and create a side blockchain. Figure 4.12 illustrates a blockchain fork:
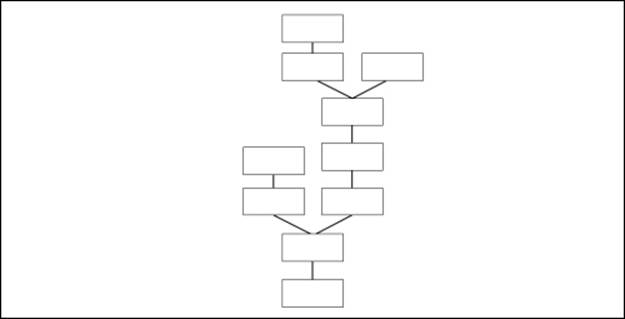
Figure 4.12 - Blockchains can fork
If a corrupted block is detected by the network, the result is a fork in the chain. Without validations from the network, the blocks become orphans and the fork invalid. Valid blocks are added to the valid portion of the chain. From the network's perspective, the longest chain of valid blocks is considered the official blockchain. From any block, there is one path back to the genesis block.
Note
The longest chain actually includes the total difficulty needed to produce the chain, not just the individual blocks. This is important for certain types of attacks. Difficulty and attacks will be covered later in the chapter.
Blocks from shorter chains are called orphans. Orphans are eventually abandoned and not used for anything. All the valid transactions included in the shorter chain are copied and added to a new block, and eventually integrated into the longer chain.
Bug fixes or major version updates can also cause a fork in the blockchain. As new nodes implement a version update, the result can be a fork and change. This is how the Bitcoin network accepts or rejects the changes to the protocol and software. Therefore, it's possible to have multiple versions of the software evolve through the blockchain.
Note
Back in March of 2013, a miner running version 0.8.0 of the software released a block that was incompatible with the other miners. To resolve this issue, the miners were asked to revert to 0.7.0 until a fix was issued. After the fix was released, a hard fork in the chain resulted. For the most part it was seamless. However, the miners operating on the 0.8.0 fork lost their mining rewards.
In summary, all the nodes connected to the Bitcoin network can relay transactions. The nodes are connected to each other through a decentralized network. To validate transactions, each node maintains a full copy of the blockchain. The blockchain is built from a chain of blocks. Each block contains a list of valid transactions and is linked to the previous block in the chain.
While all the nodes help to build the Bitcoin network, some nodes can choose to mine for new bitcoins. These nodes are called Miners. Mining is the process of using a new block of transactions as the base to a difficult puzzle to solve with computational power. If it is solved, the miner is rewarded new bitcoins, plus the transaction fees included with each transaction.
The Bitcoin supply
The total number of Bitcoins is fixed at 21 million and is distributed as a reward to the miners who solve a difficult computing problem. Rewards are given out approximately every 10 minutes, depending on the total number of miners competing for the reward. The difficulty of the problem is adjusted, to compensate for the changes in the number of miners competing, every two weeks.
Starting with the genesis block in the year 2009, 50 bitcoins were released as rewards. After every 210,000 blocks, the reward is halved to compensate for the anticipated increase in global computer power. It takes about four years to mine 210,000 blocks.
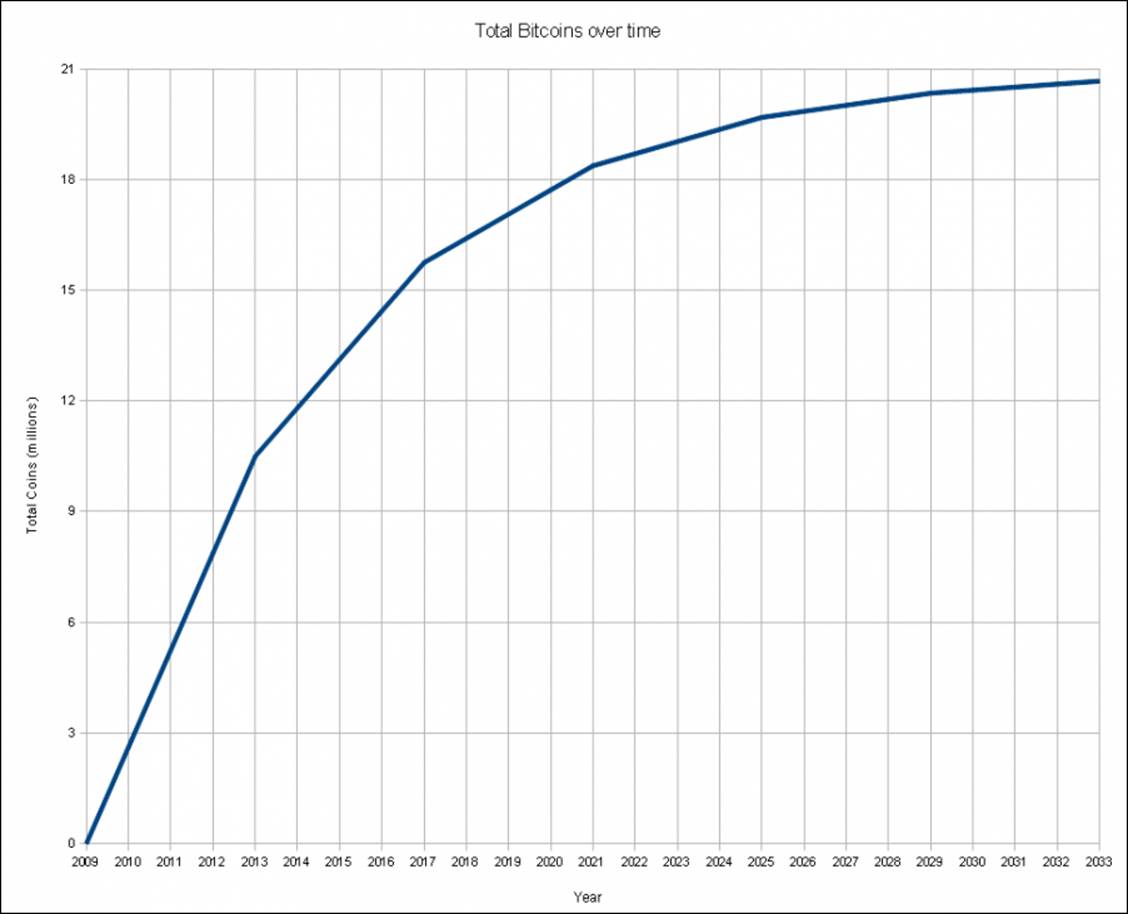
Figure 4.13 - Bitcoin distribution over time
In the preceding figure, 4.13, a distribution curve shows how the number of bitcoins given as rewards decreases over time. Given that Bitcoin is divisible by 8 decimal places, it is estimated that the last fraction of Bitcoin will be found around the year 2140.
Note
Moore's law is based on the observation that computing power will double every two years. The Bitcoin distribution curve was planned to compensate for Moore's law.
To earn the mining reward, a miner must broadcast proof, called proof of work, that they have solved a difficult computing problem.
Proof of work
Miners compete for the Bitcoin reward by submitting a "proof of work" to the network. Generating the proof of work involves the computation of a hash value on the block. The miner is looking for the smallest hash value possible.
The target value, called difficulty, is published by the network. If the hash value of the new block is less than the difficulty value published, then the miner has found a valid solution that is eligible as proof of work.
Blocks are accepted on the network as other miners confirm the proof of work.
Confirmation
If another miner accepts the proof of work, the miner is awarded the new bitcoins and that block becomes the next block in the longest blockchain. All transactions grouped in the block are given a confirmation. All miners then start the process of mining on top of that chain.
As more blocks are added to the chain, the confirmation count for each transaction is increased. The more confirmations the transaction has, the more difficult it is to modify the chain of blocks.
Note
Although you can accept a payment with just one or two confirmations, it's highly recommended to have at least six confirmations to have mathematical trust that the transaction cannot be reversed.
However, if the transaction risk is very low, like paying for a cup of coffee, one can accept a payment with zero confirmations. There have been some efforts to build a statistical model to calculate the risk of accepting payments with less than six confirmations. From the model, the service provider can guarantee and insure the transaction.
Difficulty level
As competition for the Bitcoin reward can vary, based on the number of miners on the network, the difficulty level can be adjusted to keep the reward rate at approximately once every 10 minutes.
The difficulty level is calculated from the rate at which the last blocks were accepted. If the rate of blocks found is less than 10 minutes, the difficulty will be increased; if it takes more than 10 minutes, it's decreased. The difficulty level is updated every 2,016 blocks.
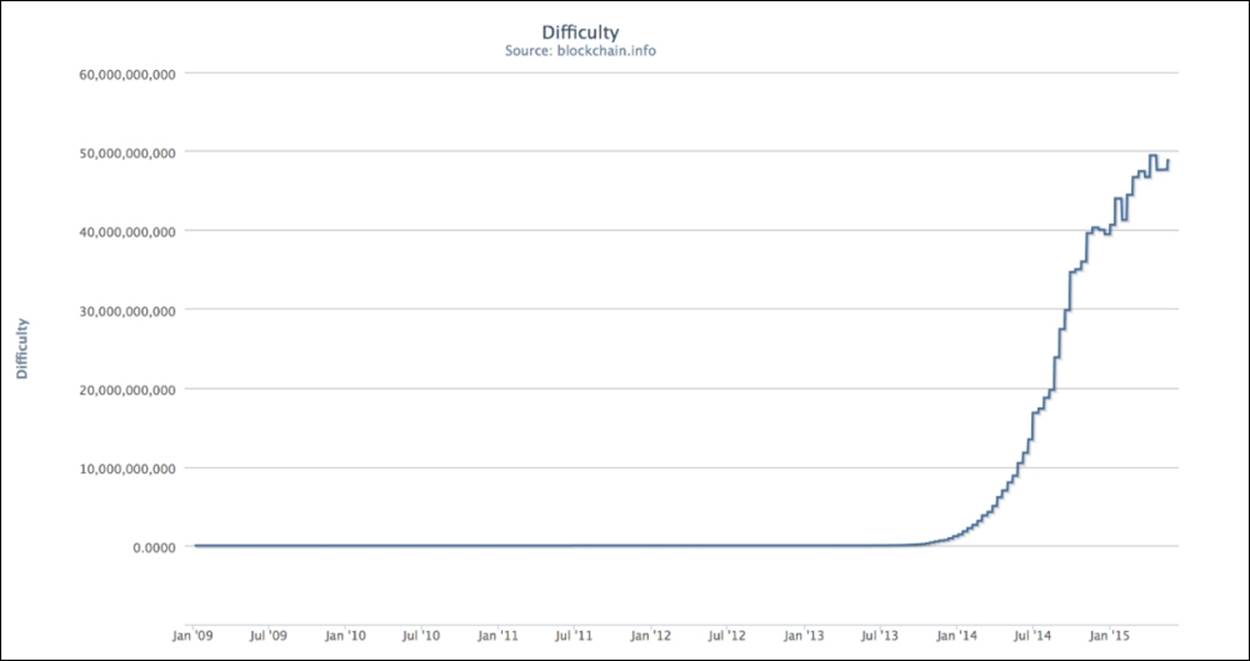
Figure 4.14 - Bitcoin difficulty levels since the genesis block (source: blockchain.info).
Shown in figure 4.14 is the network's calculated difficulty levels since the genesis block. Note how the difficulty level has dramatically increased in 2014 as the amount of competition has increased.
Mining
When a node is actively searching for a hash value below the difficulty level, it is considered a miner. The actual process of mining includes listening for transactions to create the new block which is used to compute the hash value. Collectively, all the nodes on the network follow a basic workflow for mining:
· New transactions are broadcasted to the network. The nodes relay new transactions to the other nodes. New transactions are initially marked as unconfirmed.
· Each node collects and validates the transactions into a new block. The nodes continuously listen for new transactions and update the block as needed.
· Each node looks for the solution to a difficult problem that involves computing a hash of the block. The solution to the problem includes finding a hash value that's less than the published target.
· If a solution is found, it's broadcasted to the network. The solution consists of the block of transactions and the hash value. The proof is easily verified by the other nodes on the network.
· If all the transactions in the block and its hash value are valid, the block becomes the longest chain. All miners begin mining on top of that chain and the process is repeated.
Solving a difficult problem
The goal of every miner is to produce a block of transactions with a hash value that's lower than the difficulty level published by the network. It would be extremely unlikely that computing the very first hash of a block of transaction will produce this hash value.
To allow another try, the Bitcoin protocol allows the miners to add a nonce to the end of the transaction, which is ignored by the network.
The nonce is a simple number that is incremented for each try. Each increment of the nonce results in another unique hash value. Since the hash values can be radically different from just a single character change, a large range of values is generated.
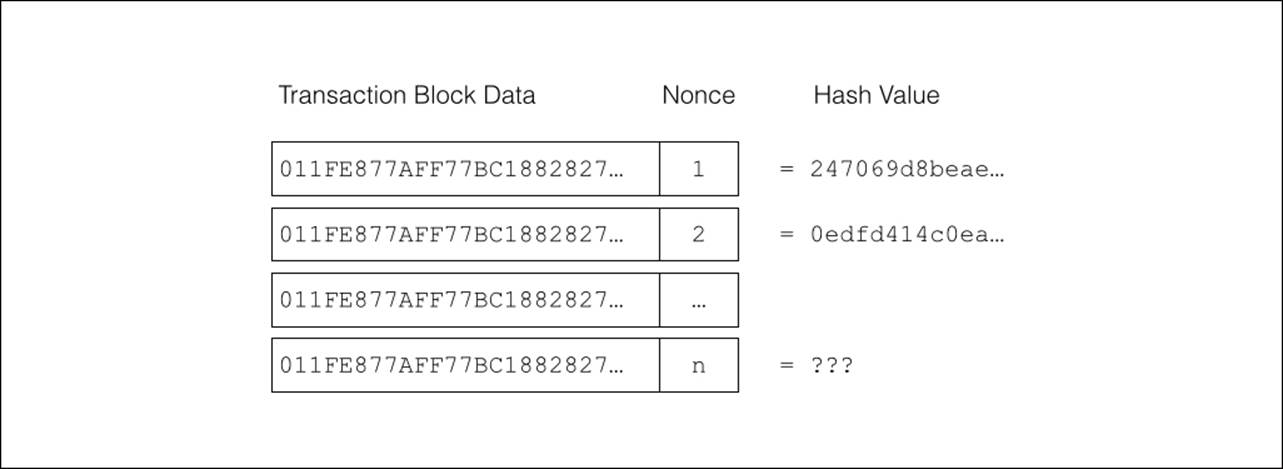
Figure 4.15 - Using a nonce to search for hash values
As shown in figure 4.15, the same transaction block data is used multiple times with an incremental nonce value. Each iteration of the nonce produces a unique and random hash value. The miners simply compute a hash for each sequential nonce until a hash is found which is less than the difficulty level.
Mining is highly competitive. In the beginning, it was common for a laptop computer to solve the puzzle. Today, however, it requires special hardware that can perform billions or even trillions of hashes per second.
Included in the new block is a Bitcoin address created by the miner. Once a valid hash value is found, the block is broadcasted to the network. If accepted, the new block becomes part of the chain and the new bitcoin reward is officially minted. Coins are generally accepted, after 100 blocks, as money that is available to spend.
Note
As mining is highly competitive, large groups of mining pools exist. A mining pool consists of hundreds or even thousands of nodes that join together to earn a mining reward. If any node in the pool wins a reward, it is split up to the whole pool divided by the amount of computing power each node provided.
Transaction fees
Transaction fees are small amounts paid to the miner for confirming your transaction. In some cases a fee is not required, but by paying a fee you are contributing to the incentive to mine.
The fee requirements are based on a ruleset accepted by the network. One rule is used to prevent payments intended to spam the network. If your transaction is less than 0.01BTC then a transaction fee of 0.0001BTC is required.
A transaction fee can be required, based on the miner, if the transaction size exceeds 10,000 bytes. As illustrated earlier in the chapter, a transaction can include many inputs and outputs which are simply stored as bytes in a record. The total number of bytes is the total transaction size. A simple way to estimate the size of a transaction is by using the following formula:
size_in_bytes = 148 * number_of_inputs + 34 * number_of_outputs + 10
Lastly, transaction fees are used to prioritize old and high-value coins. Based on the inputs listed in your transaction, a function is used to calculate the average age by the size of the transaction. If it is below a specific threshold, then a fee will be required. To simplify the priority calculations, one can assume that a single bitcoin can be spent one day after receiving it without paying a fee.
Note
To prioritize old and high-value coins, the wallet software calculates the value of all the inputs in bitcoin multiplied by its age. The sum of all the inputs is then divided by the total size of the transaction in bytes. If the result is less than 0.576, then a fee will be required.
Fees are deducted directly from the transaction, reducing the output total by the amount of the fee. There is no output allocated specifically for the transaction fee.
Rules for requiring a transaction fee are shared similarly between the miners. However, each miner has the option of choosing which rules to implement. It is possible for a miner to accept any valid transaction without a fee. However, the majority that require a fee can delay or ignore transactions that bypass the fee structure. Therefore, to improve the chance of having your transaction confirmed as quickly as possible, it's best to follow the documented transaction fee structure.
Network attacks
The Bitcoin network is protected by the consensus of the network. Valid transactions and changes to the software must be accepted by the majority of the miners on the network. Let's discuss the attacks that could occur:
51 percent attacks
It is theoretically possible for a large amount of computing power to overtake the network and accept double spending or prevent confirmations. This is called the 51 percent attack.
Although theoretically possible, the opposing argument to the attack notes the amount of computing power needed to perform the attack. Some argue that it is not financially feasible to execute the attack as the network could quickly reject the malicious blocks. It would be difficult for a large pool of nodes to produce a segment of the blockchain of more than six blocks in a row with a corrupt transaction.
Race attacks
A malicious spender could try to double spend by broadcasting two transactions to the network at the same time. Given that the merchant would accept a transaction without any confirmation, it's possible to double spend in this way.
The quick antidote to this attack is to simply wait for confirmation of both the transactions.
Finney attacks
The Finney attack is named after the Bitcoin developer Hal Finney. In this attack, a miner must pre-mine one transaction into a new block and spend the coins before releasing the block. If the payment is still unconfirmed, the new block will include a double spending transaction. The solution is to wait for at least six confirmations.
Note
Hal Finney is also known as the first person to have received a Bitcoin payment. He is credited with creating the first Proof of Work system. He worked through an illness that left him paralyzed until his death in August of 2014. http://en.wikipedia.org/wiki/Proof-of-work_system.
Alternative coins
The Bitcoin software is open source and available to the public. From the public repository, many "alternative coins" have been created by copying the source code and re-configuring specific parameters. Each alt-coin can implement a different ruleset independent of any other alt-coin.
Generally, alt-coins implement different quantities for the total money supply or different block rates. For example, Litecoin has a total supply of 84 million coins and a mining rate of approximately two minutes.
Other alt-coins may implement a built-in inflation. For example, Friecoin has a built-in demurrage that's 5 percent per year. Basically, if you hold 1 Friecoin, it will be worth 5 percent less if you spend it one year later. This was used as an incentive to promote spending.
As another interesting coin, Namecoin uses its blockchain to record information about the ownership of names. The most popular use for this mechanism is to record the ownership of domain names. Using the Namecoin blockchain, one can earn Namecoins by mining and using the coins to purchase one's own .bit domain name.
The world of alt-coins is changing rapidly, with many new ideas being tested. Yet, it is not uncommon to see the rise and fall of new alt-coins. One should investigate the size and history of any alt-coin before investing.
We will explore alt-coins in detail later in the book.
Summary
The blockchain is quickly proving to be a very impressive technology for recording the transfer of money. Due to its decentralized design, it is extremely resilient and completely transparent. It will continue to be a powerful force in the financial world as it develops over time.
In the next chapter, we'll set up and install our own Bitcoin node.
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2026 All site design rights belong to S.Y.A.