Bitcoin for the Befuddled (2015)
Chapter 3. STORING YOUR BITCOINS SAFELY, SECURELY, AND CONVENIENTLY
Unfortunately, nothing can be protected against loss with 100 percent certainty, but when done correctly, bitcoins can be stored extremely safely and securely, perhaps more so than any other financial asset. Stored incorrectly, however, bitcoins are vulnerable to loss due to technical failures (e.g., a computer or hard drive failure) or everyday disasters, and they can be an easy target for thieves as well. So before you purchase a significant amount of bitcoins, you need to learn how to—and how not to—store them.
In this chapter, we’ll explain various methods of storing bitcoins and comment on their appropriateness for different use cases. Some storage methods are more secure than others but are less convenient. Once you are comfortable with the methods and concepts discussed in this chapter, you’ll be prepared to handle bitcoins in any quantity.

Storing Your Private Key(s)
Where are your bitcoins stored? It’s a surprisingly tricky question. You must know that (1) the amount of bitcoins in your account is recorded on the blockchain, and (2) to access those bitcoins, you need to use a private key. The blockchain may be stored in a different location than your private key, and because both are necessary to use your bitcoins, it would seem at first that it is difficult to say exactly where your bitcoins are stored. But millions of identical copies of the blockchain are distributed all over the world, and because no disaster will ever erase every copy of the blockchain, you don’t need to worry about how and where it is stored. Instead, you should focus on your private key. You (and only you) know your private key, so wherever you store this key is where your bitcoins are. Consequently, storing your bitcoins really means storing your private key. If you use a Bitcoin wallet, which is a collection of addresses and private keys, your bitcoins are stored wherever you store that collection (usually on a computer, phone, or portable USB drive in a wallet file).
The remainder of this chapter explains the challenge of storing your private key (or collection of private keys) in a way that prevents accidental loss and theft. Bitcoin allows you to be your own bank. But being your own bank comes with great responsibility and requires you to take serious security precautions. Alternatively, you can trust a third-party service provider to be your Bitcoin bank, in which case you won’t need to worry about security directly; instead, you’ll need to trust your service provider to keep your bitcoins safe. Fortunately, storing bitcoins securely is easy, even for beginners (see “Paper Wallets” on page 39).
Hot Storage vs. Cold Storage
Bitcoin storage methods are often distinguished by whether they are hot or cold, depending on whether or not the private keys are stored on Internet-connected devices. Hot storage refers to private keys that are stored on an online device or computer. Cold storage refers to private keys that are not accessible via the Internet. For example, if you use an offline computer to generate a Bitcoin address and its corresponding private key, any bitcoins sent to that address are in cold storage. But how can others send you bitcoins if your address was generated on an offline computer? Well, you share it with them! You can safely copy your public Bitcoin address and post it on a website (or email it to all your friends). However, the private key exists only on the offline computer where it was generated and remains confidential.
Because sending bitcoins requires a private key and an Internet connection, hot wallets are more convenient to use, but cold storage methods are more secure and better suited for long-term bitcoin storage. Note that a hot wallet cannot become cold by going offline.1 Once a private key has been exposed to the Internet, it is unsafe to assume that it will provide the same protection as one that was never exposed.
Sometimes, companies may advertise that they store their clients’ Bitcoin funds in cold storage as a security feature but will simultaneously claim that those funds can be conveniently moved to a hot wallet automatically. This is a red flag. If any company states that it has an automated process for transferring funds from cold to hot wallets, most likely none of its funds are stored in cold storage. Cold storage requires a person to physically access an offline computer and manually authorize a Bitcoin transaction. You’ll learn how to do this in “Storing Large Amounts of Bitcoins” on page 38.
Personal vs. Hosted Wallets
Many companies offer Bitcoin wallet services and programs to help you store your bitcoins. To the uninitiated, it isn’t always clear whether these companies offer a personal wallet or a hosted wallet. With a personal wallet, you and only you know the private keys. The company that created the software does not control your bitcoins. Alternatively, with a hosted wallet, a third party knows your private keys and doesn’t reveal them to you, but the company will send, receive, and store bitcoins on your behalf (not unlike a traditional bank, which stores your cash in a vault and won’t give you the keys to open it). Some companies also offer software as a service. In this case, they host the wallet software on their servers but not the private keys. Users can log in, send and receive bitcoins, and monitor Bitcoin transactions using their own private keys (which the company never receives). We refer to such services as online personal wallets because the private keys are not hosted.
With both wallet types, the user interfaces may look and function in similar ways, but the ramifications of using one kind of wallet versus the other are quite different. In particular, the question of who is liable if bitcoins are stolen may be determined by who had access to the private keys. If you’re in doubt, ask whether you have access to the private keys.
NOTE
The liability distinction can become blurred if multiple private keys are used to control the same bitcoins. A few online services require two private keys to spend the same bitcoins, one held by the company and the other by the customer. Assigning liability can be trickier in these cases (although as you’ll see later in “Fragmented Private Keys and Multi-Signature Addresses” on page 41, using multiple private keys to store bitcoins is typically a good idea).
The benefits of using a hosted wallet are that it is user-friendly and you don’t have to worry directly about Bitcoin storage security. However, the hosting company must be both trustworthy and competent in that it will not maliciously run away with your bitcoins or let thieves steal them. Another detail to consider is that government or law enforcement officials can ask a hosting company to hand over your bitcoins. The company might oblige this demand, even if you would have disputed the request.
Although hosted wallets may be a popular choice for many future Bitcoin users due to their user-friendliness, we’ll focus on personal wallets. Even if you decide to use a hosted wallet and let someone else manage the safety and security details, this chapter will help you make an informed decision when you’re choosing hosted wallet service providers.
Safety, Security, and Convenience
Consider three major factors when you’re comparing storage methods:
1. Safety (preventing the accidental loss of bitcoins)
2. Security (preventing the theft of bitcoins)
3. Convenience (ability to easily and quickly spend your bitcoins)
These factors can sometimes conflict with each other. Methods that make it convenient for you to spend your bitcoins are probably inadvertently making it easier for a thief to spend them as well. Similarly, making many copies of your private key and giving them to friends and family for safekeeping is a good strategy to prevent accidental loss; however, this strategy also makes it more likely that your private key will fall into the wrong hands. Combining safety, security, and convenience into one storage method is an area of constant innovation, and some newer methods have demonstrated an excellent balance of all three (see “Special Mention: The Bitcoin Hardware Wallet” on page 42).
Most people use two storage methods: one for storing small amounts of bitcoins conveniently but less securely and another for storing large amounts less conveniently but very securely. As Crowley the Crocodile illustrates in the comic at the start of this chapter, this is similar to having a small amount of cash in your pocket but keeping most of your money in a traditional bank account.
In the following sections, we’ve grouped storage approaches into two categories:
• Methods for small amounts of bitcoins that are convenient, easy to use, and reasonably safe
• Methods for long-term storage of large amounts of bitcoins that are extremely safe and secure (but not as convenient)
Storing Small Amounts of Bitcoins
Many easy-to-use methods for storing bitcoins are handy, but they all share one fundamental weakness: A sufficiently sophisticated attacker could potentially breach the layers of security and access your bitcoins from a remote location. However, this situation is not that different from the same event happening with traditional online banking. A hacker in a remote location, whether just on the other side of town or in another country, could drain your bank account by stealing your identity and deciphering your login credentials. For example, if you access your online bank account using a laptop, a malicious program could monitor your keyboard presses (i.e., a keylogger) and steal your password. Banks remedy this weakness by implementing strict daily withdrawal limits or other measures that mitigate the impact of fraudulent access. With Bitcoin, the best mitigation strategy is to store the majority of your funds in cold storage, which cannot be accessed remotely, and to use the more convenient methods for daily spending only.
Three reliable and easy-to-use methods for sending and receiving small amounts of bitcoins are described in the following subsections:
• Online hosted wallet services
• Online personal wallet services
• Personal hot wallet
Online Hosted Wallet Services
As discussed briefly earlier in this chapter, online hosted wallet services are popular because they tend to be easy to use, and users don’t typically need to know about Bitcoin’s inner workings. No software installation is required; users just sign up and log in to their wallet via a website using a web browser. Online hosted wallets seem familiar because they work like most traditional financial services. For example, when you open a bank account, the service handles your money on your behalf and manages all transfers, deposits, bill payments, and security measures. The same holds true of a hosted Bitcoin wallet: Although the bitcoins are yours, they are not directly in your possession (because you do not have access to the private keys). If the wallet service provider goes bankrupt, for example, you may lose your bitcoins.
Many providers hold bitcoins on behalf of hundreds or thousands of people and have invested in significant security measures. But it’s difficult to know for sure whether the service provider is secure enough if it doesn’t reveal the details of its storage methods. Be cautious; if you are able to access your hosted wallet using just a username and simple password, that is a warning sign that your provider might be vulnerable to online attacks (if you can access your bitcoins easily, so can a thief). Quality wallet service providers, such as the U.S.-based company Coinbase (which also offers convenient ways to buy bitcoins; see Chapter 4) require the use of two-factor authentication for users to access their bitcoins. Two-factor authentication requires the use of a phone, or another secondary device, in addition to a username and password.
Unfortunately, because the Bitcoin world is so new, no hosted wallet provider can claim a long track record of incident-free bitcoin storage.2 For this reason, at this time we recommend that you do not trust any third parties with large amounts of bitcoins. Also, note that hosted wallets offer the least amount of privacy when you use bitcoins, because the provider knows who you are, the number of bitcoins you have, and all of your incoming and outgoing transactions.
Online Personal Wallet Services
Online personal wallets, like the My Wallet service provided by Blockchain .info,3 look and behave much like hosted wallets but with a key difference.4 These wallet services provide you with the tools to send and receive bitcoins, but they don’t know your private key. Instead, once the website loads locally on your device, (i.e., is no longer communicating with a distant web server), you generate your private keys from a password you type in. Whenever you send someone bitcoins, a signed transaction is sent to the web server, but your password (and hence your private keys) never leave your device. Fundamentally, this means these services cannot steal your funds. In addition, if the company goes bankrupt or otherwise disappears, you are only inconvenienced temporarily and none of your bitcoins are lost.
Although just as easy to use as hosted wallets, online personal wallets place a much greater responsibility on the user. Typically, you access these wallets online via a username and password, just as you would a hosted wallet, but if you forget your password, in this case you have no recourse. Because the service providers don’t know your passwords, they cannot help you recover them.5 If you use this method, be sure to write down your password in multiple secure places!
Online personal wallets often offer much greater privacy than hosted wallets, especially if they don’t require any personally identifying information to register an account. But the service provider may keep track of usage patterns and other data that could subsequently be requested by law enforcement.
Personal Hot Wallet
Like the Electrum wallet discussed in Chapter 2, a personal hot wallet is a software program that runs on a device you own. Because no third party is needed to operate a personal hot wallet, using one maintains the spirit of decentralization that underpins Bitcoin. These programs give you complete control over your bitcoins without sacrificing convenience. However, an even greater responsibility is placed on you than if you use an online wallet service. Your private keys are saved on the same device that connects to the Internet and communicates with the Bitcoin network (the defining feature of a hot wallet); therefore, you need to be vigilant about protecting your device from malware, viruses, and other hacking attempts that could lead to theft.
Is hacker theft likely to happen to you? To become a target of an attack, you would have to keep a large amount of bitcoins in your hot wallet and have advertised this information somehow. Both conditions are not recommended! Using a personal hot wallet is like carrying a traditional physical wallet; it’s unlikely that you’ll get mugged, but you shouldn’t keep too much cash in your wallet or wave it around just in case.
As with a physical wallet, you can lose your hot wallet. If you are storing your private keys on your computer, keep in mind that your computer might be lost, stolen, or destroyed—and the bitcoins in your hot wallet might be worth more than the computer! Fortunately, unlike a physical wallet, you can back up your Bitcoin wallet. However, be mindful of where you store your backups. You may want to avoid using cloud storage, for example.
Many personal hot wallets are available (a full discussion of the different choices is provided in Chapter 9). Electrum (http://electrum.org/) and Multibit (http://multibit.org/) are recommended. Both are open source, have been in use for many years, are available on most platforms, and are lightweight (don’t require significant computer resources). The original hot wallet, Bitcoin Core (formerly Bitcoin-Qt; http://bitcoin.org/), requires significant computer resources to run; therefore, casual users may opt not to use it.
Storing Large Amounts of Bitcoins
Cold storage methods, as described earlier, require physical access to information that is not accessible via the Internet. These five storage methods dramatically reduce the risk of theft:
• Paper wallets
• Encrypted paper wallets
• Offline transaction signing
• Fragmented private keys
• Multi-signature addresses
Instead of worrying about cyber-thieves, you only have to worry about local burglars (and only those who are Bitcoin-savvy). Most of these methods are suitable for safely storing large amounts of bitcoins for long periods of time. However, if you are storing a large Bitcoin fortune, consider having a security expert audit your storage method.
Note that you can safely experiment with any of these five methods using an online computer, as long as you use small amounts of bitcoins. Once you are comfortable with a particular method, you’ll need either a dedicated offline computer (preferred) or at least a computer you can take offline temporarily.
When you’re evaluating cold storage methods, it’s handy to have the open source Bitcoin wallet generator at http://bitaddress.org/.
NOTE
You can download the entire website at http://bitaddress.org/ and run it on your computer after you disconnect from the Internet.
When you first access the website, you’ll be asked to move your cursor over a box of letters and numbers (or type letters) randomly to provide a source of randomness that the site uses to generate a Bitcoin address. The reason you need to do this that it is very challenging for computers to generate random numbers by chance because they follow strict instructions, making the results more predictable. For unimportant applications, such as playing Solitaire on your computer, a mediocre random number generator used to shuffle the virtual deck is no big deal, but for storing money, high-quality randomness is very important.
Paper Wallets
Using a paper wallet is perhaps one of the simplest and most popular cold storage methods. This involves generating a Bitcoin address and private key on an offline computer and then writing both down on a piece of paper but not saving a copy of the information on the computer itself. You can then store the piece of paper in a file cabinet, a personal safe, or in a safety deposit box at a bank. With the piece of paper safely locked away, you can continue sending bitcoins to the associated Bitcoin address for safekeeping. When you eventually decide to spend your saved bitcoins, you can use the import private key or import paper wallet function that most Bitcoin wallet programs include. At this point, your bitcoins will no longer be in cold storage.
If you want to spend only some of your saved bitcoins and keep the rest in a paper wallet, after importing your private key into a hot wallet, you should immediately store the remainder of your bitcoins in a new paper wallet (paper wallets are one-time use only). But be sure to prepare the new paper wallet ahead of time before importing bitcoins from the old paper wallet.
NOTE
Alternatively, you can spend a fraction of your paper wallet bitcoins by using a technique known as offline transaction signing, which is described in “Offline Transaction Signing” on page 40.
Provided you keep the paper private key in a safe place, the paper wallet method is suitable for storing large amounts of bitcoins indefinitely. However, keep in mind such physical risks as flooding and fire. Also, do not scan, take photos of, or expose your paper private key to other methods of duplication, or you will compromise your paper wallet. Your bitcoins are only as safe as the least secure method by which you store your private keys. In particular, consider that some office photocopiers maintain records of every document they copy. The safest way to make a duplicate of your paper wallet, which is recommended, is to clearly handwrite a few extra copies and store those copies securely.
Encrypted Paper Wallets
The encrypted paper wallet method was invented to further improve the security of the paper wallet method. Essentially, instead of writing down the private key on a piece of paper, you write down an encrypted version of it. The only way to decrypt your private key is with a password you choose, preventing thieves from accessing your private key and your bitcoins.
Hundreds of encryption schemes can be used for this purpose, but the most common scheme is BIP38 encryption.
NOTE
The Bitcoin developer community maintains a wish list of features called Bitcoin Improvement Proposals (BIPs), and this encryption standard is #38 on the list (features that have been implemented, such as this one, are still often referred to by their BIP numbers).
To create a BIP38-encrypted paper wallet (go to http://bitaddress.org/ and shake your mouse back and forth until you’ve generated enough random data and the Paper Wallet tab appears), you choose a passphrase and then generate a Bitcoin address with its associated encrypted private key. Your private key should start with the number 6, as opposed to a normal private key, which starts with the number 5.
NOTE
In computer science, passwords typically serve one of two functions: Either they are used to authenticate a user by asking the user to provide a password at the appropriate time, or they are used to encrypt data. For authentication, one can often get away with a short, word-length password (even though it is typically still a bad idea to do this). However, passwords used for data encryption must always be long: If they are shorter than 40 characters, they are often easy to crack. Hence, when passwords are used for this purpose, as we discuss in this section, it is a common convention to call them passphrases instead.
But be forewarned: If you forget your passphrase, you’ll permanently lose access to your bitcoins. Therefore, it’s best to also write down your passphrase and store it in a different location than the paper wallet. As with ordinary paper wallets, make backup copies of the encrypted paper wallet to protect against flooding, fires, or theft. Always assume that your wallet is unsafe to ensure you are being vigilant about safety. If your encrypted paper wallet is stolen, use your duplicate copy to import your bitcoins into a hot wallet, and then store them in a new encrypted paper wallet. Even if a perpetrator eventually determines your passphrase, you will have moved your bitcoins by then.
Offline Transaction Signing
Offline transaction signing is the entry-level security method for Bitcoin businesses or serious users who regularly handle large amounts of bitcoins. This method requires two computers and is considerably more advanced than using paper wallets. One computer has a personal hot wallet that works just like Electrum, but the private keys are omitted. Therefore, when you click send bitcoins, you will be asked to perform an extra authorization step using a second computer, which contains the private keys and is not connected to the Internet. This second offline computer also has a Bitcoin wallet program installed and only functions to authorize, or digitally sign, the transaction. You use the offline computer to create a file that contains the digitally signed transaction, which you then copy to the online computer and broadcast to the Bitcoin network (see Figure 3-1).
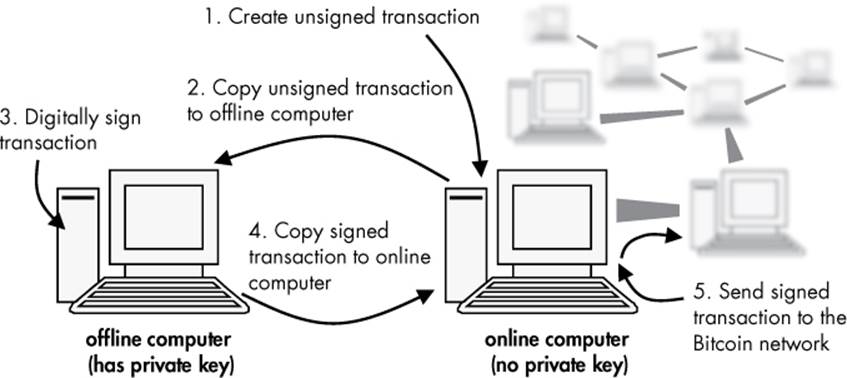
Figure 3-1: A schematic of how an offline and online computer work together to securely sign Bitcoin transactions without exposing a private key to the Internet
The online computer never ascertains the private keys. Offline transaction signing is similar to having a financial administrator with no signing authority write checks that then need to be signed by an authorized person before being mailed out. Although this method is very secure and can be used to store fairly large amounts of bitcoins, making many transactions per day can be a cumbersome process. One potential risk is losing the private keys stored on your offline computer; therefore, you should make backups of those private keys for reliable, long-term storage. Another risk is that your private keys may be compromised if your offline computer is stolen or seized.
An advantage of offline transaction signing instead of just importing keys from paper wallets is that a cold-to-hot storage transition never happens. Your bitcoins are always in cold storage, even when you spend from the address where they are stored.
You can use the Electrum offline transaction-signing feature, provided you have two computers. Another highly recommended wallet for offline transaction signing is the Armory Bitcoin Client (http://bitcoinarmory.com/), which is open source and designed with maximum security in mind. Armory offers many advanced security features, and if you are serious about highly secure Bitcoin storage and are an advanced Bitcoin user, you should certainly explore this option.
Fragmented Private Keys and Multi-Signature Addresses
Fragmented private keys and multi-signature addresses involve splitting into pieces the information required to spend bitcoins and storing them in disparate geographic locations. Both techniques achieve extremely high levels of Bitcoin storage security and safety. As enterprise-level Bitcoin security strategies, they are (or should be) implemented by large Bitcoin businesses (major currency exchanges, hedge funds with Bitcoin assets, etc.). Let’s look at each strategy in turn.
Fragmented Private Keys
Using a cryptographic trick known as secret sharing, a Bitcoin private key can be divided into many fragments, and only a certain number are required to reconstruct the key. This is sometimes referred to as an “m of n” private key, where m and n stand for the necessary and available number of fragments. For example, a private key might be split into five fragments, but any three can be used to reconstruct the key, making a “3 of 5” private key. None of the individual pieces on their own reveal any meaningful information about the private key. This strategy is very useful for highly secure Bitcoin storage because companies can store each fragment in a separate, safe place; if one fragment gets damaged or compromised, the bitcoins will still be safe. In addition, other fragments can be used to move the bitcoins to a new address. Several different cryptographic protocols are used for secret sharing, but the most popular is Shamir’s Secret Sharing method, for which organizations can easily find open source implementations on the Web.
Multi-Signature Addresses
Using multi-signature addresses, or multiple private keys, as opposed to using a single private key in multiple pieces, also provides a similar level of highly secure storage. Bitcoins are stored in an address that requires more than one private key to use them. Companies can specify how many keys exist and the number required to spend the stored bitcoins; for example, if three keys are specified, any two keys could be sufficient to complete a transaction. For safekeeping, businesses can also distribute these keys to different people if the organizations don’t want to entrust a single person with the authority to move bitcoins. For example, a Bitcoin bank can ensure that no single employee (even the CEO or president) is solely able to move customers’ funds. Each employee at the Bitcoin bank can have his own private key, with all of the keys corresponding to the same Bitcoin address, but no single private key is sufficient to move the bitcoins. To authorize the transfer of bitcoins from the bank’s Bitcoin address, multiple employees need to use their private keys to digitally sign the transaction. One main difference exists between multiple private keys and multiple fragments of a single private key: With multiple private keys, at no point does one person ever have complete control, whereas with multiple fragments of a single private key, the person who combines the pieces to construct the private key has complete control. Using multiple private keys is an extremely secure and responsible way to manage very large amounts of bitcoins.
Special Mention: The Bitcoin Hardware Wallet
The hardware wallet is a relatively new Bitcoin storage method. It is a small device that fits in your pocket and stores your private keys in such a way that no one can extract them from the device. The hardware wallet acts as the offline computer in the previously mentioned offline transaction-signing method, but it is more convenient because you can plug it into your online computer. Your bitcoins are never at risk, even if you have viruses on your online computer. When you click send bitcoins in your Bitcoin wallet software on the online computer, you then need to confirm the transaction on the hardware device—usually by pressing a button. The hardware wallet uses the internally stored private keys to sign a transaction, which is then sent to the online computer.
This method is almost as convenient as using the personal hot wallet, but it is more secure because it is impossible for your private keys to be exposed to the Internet. Your bitcoins on the device will always be in cold storage. One downside to this method is that you need to purchase a piece of hardware, as opposed to just downloading a free open source program. Another disadvantage of using your hardware wallet is that you can lose it, which might result in lost bitcoins (although some hardware wallets provide ways to back up your bitcoins). Although the hardware wallet is an excellent combination of convenience and security, you might not want to rely on one to store your bitcoins for decades, because no data is yet available on the lifetime or durability of such devices.
TREZOR
One brand of hardware wallet that has received a lot of attention is Trezor (http://www.bitcointrezor.com/). We find the Trezor hardware wallet to be an excellent, relatively easy-to-use use device, but because Trezor devices are new, there is still the possibility that a bug or security flaw is yet to be discovered (as is true, in principle, of Bitcoin itself).
Created by SatoshiLabs, the Trezor (see Figure 3-2) is a small device that “stores your bitcoins” (that is, it stores your private keys). When you want to spend your bitcoins, you use a USB cable to plug the Trezor into a laptop. It doesn’t have to be your own laptop; you can use a complete stranger’s laptop and still safely spend your bitcoins. This is, perhaps, the defining feature of the Trezor: It doesn’t require you to trust the laptop that you plug it into. This is helpful if you’re traveling and don’t have your own laptop with you: You can use any computer at your destination. Since most bitcoins are stolen by exploiting security holes in smartphones and laptops, using the Trezor dramatically cuts down on the risk of Bitcoin theft. So how does it work?

Figure 3-2: The Trezor device
Smartphones and laptops are also devices that can store private keys, but unlike the Trezor, they treat those keys like any other data, i.e., as information that can be viewed, copied, or modified. Viruses on a laptop can search for the private key data, copy them, and broadcast them to a remote server, leading to stolen bitcoins. The Trezor, on the other hand, never allows the private key data to be viewed or copied by you or a virus. Instead, when you want to spend bitcoins, it uses its internal private keys to sign a transaction that it then gives you. The Trezor is like a paranoid chef who will never reveal his secret recipe but will cook for you anytime you want.
Configuring the Trezor is slightly laborious (it may take 5–10 minutes for beginners), but this does not need to be done more than once.
1. Plug the Trezor into your laptop.
2. Visit https://mytrezor.com/. Install the necessary plugins so that your laptop knows how to communicate with the Trezor. You may need to restart your browser to continue once the plugins are installed.
3. Navigate to https://mytrezor.com/ again. The website will recognize that your Trezor has not been configured yet and will ask you to give your device a unique name. Enter a name and click Continue.
4. Enter a new PIN using your laptop.
5. Enter the PIN again to verify you did not make a mistake in the previous step.
6. The Trezor device will now display a recovery seed so that you can recover your bitcoins in case you lose your device. This is the only time that the Trezor will ever reveal (indirectly) its private keys (they are derived from the seed). Once the configuration process is done, the private keys can never again be viewed or accessed. Write down the recovery seed on a piece of paper (or two), and store it in a safe place.
7. Congratulations, you are ready to use your Trezor! If you have bitcoins stored elsewhere, you can send them to your Trezor by clicking Account ▸ Receive to find a receiving Bitcoin address.
Operating the Trezor is much simpler:
1. Plug the Trezor into a laptop.
2. Open a Bitcoin wallet program on the laptop that is configured to work with the Trezor (or visit https://mytrezor.com/, a website created by SatoshiLabs designed specifically for Trezor users).
3. On the laptop, choose how many bitcoins you want to spend and where you want to send them. Click Send.
4. The Trezor will ask you to enter your PIN. (This is to prevent someone from being able to steal your Trezor and spend your bitcoins.) Enter your PIN using the laptop.
5. The Trezor will display the transaction details. Press the corresponding button on the Trezor to confirm (or the other button to deny) the transaction. The Trezor will now create a signed Bitcoin transaction and send it to the laptop.
6. The laptop automatically broadcasts the transaction to the Bitcoin network. Your bitcoins have been sent!
These steps take only a minute to carry out and are quite convenient for tasks like online shopping (the Trezor was not designed, however, to be used at a point-of-sale terminal like the cash register at a coffee shop).
The Trezor also supports advanced features, such as the use of passwords (in addition to the PIN) and hierarchical deterministic wallets for multiple accounts. These features are more than we can cover in this little box, but you are encouraged to check out the Trezor website (http://www.bitcointrezor.com/) for more details. At the time of this writing, the Trezor is selling for about $120, but you can pay only with bitcoins.
Special Mention: The Bitcoin Brain Wallet
Using the brain wallet to store bitcoins is a unique and somewhat mind-blowing technique. In this method, you store bitcoins entirely in your brain by memorizing your private key. We should note in advance that this storage method is impractical in several respects and recommended only for Bitcoin/cryptography experts. Because nothing tangible exists to steal or seize, you can use this method to store your bitcoins when you don’t have control over your physical environment (e.g., living in a dorm room, crossing through security checkpoints, etc.). However, you must create a long, unforgettable passphrase that you can commit to memory, especially if you will be storing large amounts of bitcoins. Then you feed the passphrase into a computer program (running on an offline computer) that accepts any text as input and outputs a private key and Bitcoin address. In the following example, the passphrase is short and easy to guess, so your stored bitcoins would be at risk.
passphrase: "bitcoin for the befuddled" <--- way too short
private key: 5JS1PoX1e7b48VnBtaeYohJvoe8NTGBTdBa9KELJR9UjoeL9ukx
bitcoin adddress: 1EjtJ53dXFT7cmP5ETiQuyc9fPy96FEPBh
However, the following passphrase is sufficiently complex.
passphrase: "crowley likes beaches, lisp programming, ravioli and sasquatches
conradbarski chriswilmer nostarchpress"
private key: 5Ke7Unhs9Ghc4UmhVZXptjPZiVFn48fnN1xGeoctsKrHdpdJtAD
bitcoin address: 1FqwT4844gvjP6GCELW5NaR1gMCQKRcaSP
After generating your passphrase on an offline computer, you ignore the private key and copy only the Bitcoin address. You do not want to store the private key anywhere, even on an offline computer. You’ll need the private key when you want to move your bitcoins, and at that point you can re-create it from your memorized passphrase (and import it into a Bitcoin wallet, like Electrum, or use it for offline transaction signing). By not storing the private key anywhere, you prevent others from stealing it from you, either physically or digitally. You can write down your passphrase and keep it hidden in a safe place, of course, but then it wouldn’t strictly be a brain wallet (however, it can be a good idea).
Brain wallets are useful for reasonably long-term storage (a few years) of significant amounts of bitcoins, but they are not convenient for day-to-day transactions. Also, storing large amounts of bitcoins in a brain wallet for decades could be risky, because you might forget the password. Additionally, people are inherently deficient at choosing passphrases that computers cannot guess, and increasingly powerful computers might be capable of guessing every possible passphrase that a human could generate. For very long-term storage of large quantities of bitcoins, it is safest to use a randomly generated private key (with a high-quality source of randomness).
Choosing the Storage Method That’s Right for You
The best storage route to take is to start small and choose an easy storage method that you’re comfortable with (see Figure 3-2). Keep in mind that human error while using a complicated Bitcoin storage scheme is a real risk factor. Once you’re more comfortable with how Bitcoin works, you can gradually increase the amount of bitcoins you own and the level of security you use.
Although no system is 100 percent secure, you can store your bitcoins more securely than gold or traditional currencies. Storing bitcoins might seem less secure than having cash in a traditional bank account, but the reason might be simply that many people feel less comfortable with unfamiliar technology. Someday we might look back and think it should have been obvious that a decentralized currency that is impossible to counterfeit and is built on cryptographic principles is more secure than traditional currencies.
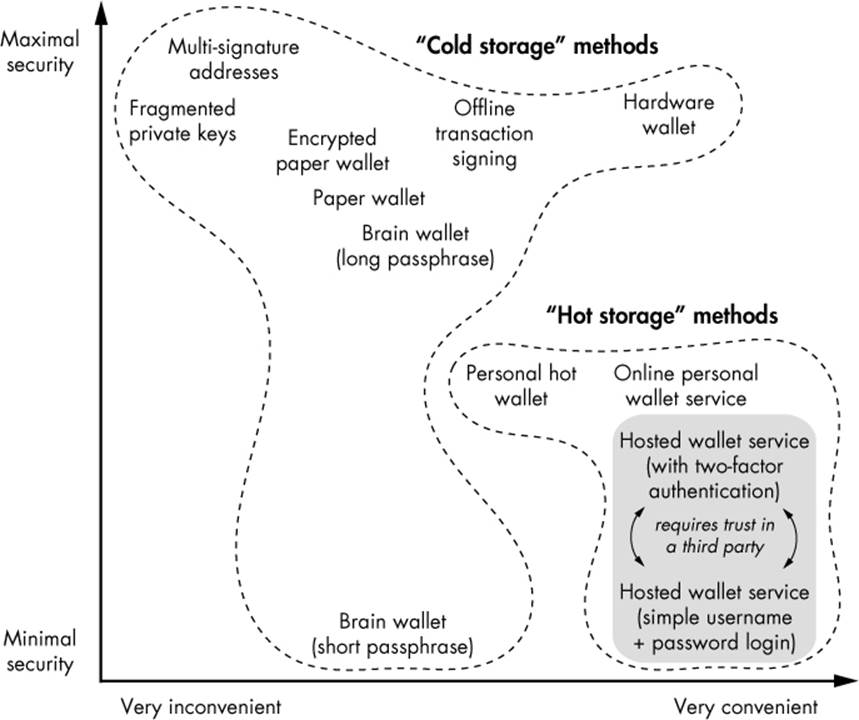
Figure 3-3: A summary of Bitcoin storage methods. These strategies span the spectrum from low security (but convenient) to high security (but inconvenient). This chart is not comprehensive because new methods are constantly being developed. For example, one of the best methods on this chart, the hardware wallet, was not possible until 2014, five years after the start of Bitcoin.