5 Steps to a 5: AP Computer Science Principles 2024 - Sway J.S. 2023
AP Computer Science Principles Practice Exam 2
STEP 5 Build Your Test-Taking Confidence
Multiple-Choice Questions
ANSWER SHEET

AP Computer Science Principles Practice Exam 2
Multiple-Choice Questions
Time: 2 hours
Number of questions: 70
The multiple-choice questions represent 70% of your total score.
Directions: Choose the one best answer for each question. The last eight questions of the test have two correct answers; for these, you will be instructed to choose two answer choices.
Tear out the answer sheet on the previous page and grid in your answers using a pencil. Consider how much time you have left before spending too much time on any one problem.
AP Computer Science Principles Exam Reference Sheet
On the AP Computer Science Principles exam, you will be given a reference sheet to use while you’re taking the multiple-choice test. A copy of this six-page reference sheet is included in the Appendix of this book (reprinted by permission from the College Board).
To make taking this practice test like taking the actual exam, you should tear out the reference sheet so you can easily refer to it while taking the test. Save these reference pages since you’ll need to use them when you take AP Computer Science Principles Practice Exam 2.
If you lose the pages, the reference sheet is also available near the end of the PDF publication “AP Computer Science Principles Student Handouts” on the College Board website. Here is the URL:
https://apcentral.collegeboard.org/pdf/ap-csp-student-task-directions.pdf?course=ap-computer-science-principles
1. When running a program that counts the number of records in a large dataset, you receive an error on your computer screen, in binary format: 11110001.
Convert the error message from binary to decimal to be able to look it up.
(A) 239—Invalid operation. Corrupt data caused the error.
(B) 240—Decimal numbers are stored imprecisely in computers. A rounding error occurred.
(C) 241—Overflow error. The object exceeded its maximum size. The dataset is too large to run on your computer.
(D) 404—Error message not found.
2. You read in the news about an employee who took advantage of decimal numbers used with currency exchanges to steal money. What is the most likely way the employee accomplished this?
(A) The employee redirected the overflow amount when it occurred and deposited it in his account.
(B) The employee took advantage of rounding and deposited the fractional amounts.
(C) The amount is represented in binary and when the right-most bit was a 1, he replaced it with a 0 and deposited the difference.
(D) The employee converted to euros and then back to U.S. dollars. The difference in the exchange rate was deposited into his account.
3. Saving your information from an online form to be able to autofill fields in future forms captures some of your Personally Identifiable Information (PII). This could be an example of
(A) an ethical matter.
(B) a legal problem.
(C) a privacy concern.
(D) a security issue.
4. What order should the following procedures be used in creating an app to reserve a study room in the library?
• checkAvail()—checks the availability of the time requested since multiple people can use the app at the same time
• recordResv()—records the room reservation
• requestTime()—asks for a reservation time for the study room
• timesAvail()—displays the times the room is available
• updateTimes()—updates the times available to be displayed
(A) requestTime(), recordResv(), timesAvail(), checkAvail(), updateTimes()
(B) requestTime(), timesAvail(), recordResv(), updateTimes()
(C) timesAvail(), requestTime(), checkAvail(), recordResv(), updateTimes()
(D) requestTime(), recordResv(), updateTimes()
Questions 5 and 6 are based on the code below. Assume the variables and list already have values.
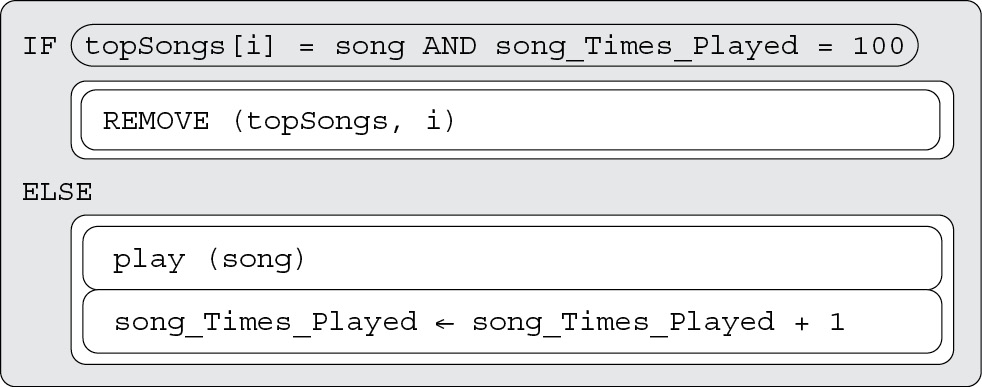
5. What is the code doing?
(A) Playing a song from the topSongs list
(B) If a song is in topSongs, playing it, then removing it
(C) Removing a song from topSongs if it has been played 100 times; otherwise playing the song and increasing the number of times played
(D) This code will not run as written.
6. In the above code, after a song has been deleted from the list once, it keeps being removed after the user adds it back to the list. What is the best way to fix this error?
(A) Change the program to allow songs to be played 1,000 times before being deleted.
(B) Send the user a message to confirm they want to delete the song, stating it can never be added back to the list.
(C) Write a new procedure to add a song back to the list if it had been on the list previously.
(D) Set song_Times_Played back to 0 after removing a song.
7. Which of the following will evaluate to false?

(A) i and ii
(B) ii and iii
(C) i and iii
(D) i, ii, and iii
8. Which of the following will evaluate to true?

(A) i
(B) ii
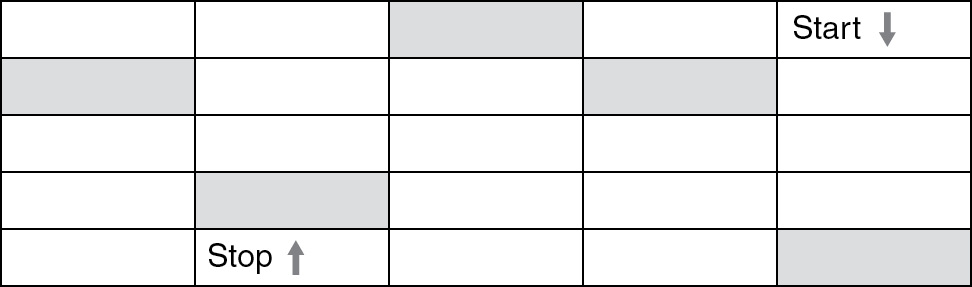
(C) i and iii
(D) ii and iii
9. A group that is watching sea turtle nests records data about their nests. Which of the following is metadata?
(A) Daily temperature of the nest
(B) Date the eggs were laid
(C) Nest tag
(D) Number of data fields tracked
10. The video the nest watchers took of the baby sea turtles making their way to the water is too large to send. How can the volunteers compress the video to get it to the scientists in full resolution?
(A) Lossless compression will allow the scientists to see the video in full resolution.
(B) Lossy compression will make the file small enough to send.
(C) They should be combined for the best compression.
(D) Any compression technique will be sufficient.
11. When analyzing a list of potential employees for promotion that an algorithm produced, the team noticed that there were no members of a particular group included. With further research, it was determined that part of the criteria that the algorithm used included prior employees in that position, which had few from that particular group. What is this is an example of?
(A) Bias
(B) Citizen science
(C) Single criteria elimination
(D) Targeted data
12. Which of the following techniques would be best to use to further analyze patterns that emerged during data mining?
i. Classifying data to categorize it into distinct groups
ii. Cleaning data to determine which data to include in the processing
iii. Clustering data to separate data with similarities into subclasses
iv. Filtering to set conditions so only records meeting the criteria are included
(A) i, ii, iii
(B) i, iii, iv
(C) i, ii, iv
(D) i, ii, iii, iv
13. The data you are analyzing shows a surprising correlation between parking tickets and pizza orders. What should you do with this information?
(A) Document the trend to share with management.
(B) Perform additional data collection from new sources to verify the correlation.
(C) Determine if the pizza order caused the parking ticket.
(D) Determine if the parking ticket caused the pizza order.
14. A good business practice is to send a copy of data off-site in the event of a catastrophic event such as a fire at the organization’s primary server location. How can organizations keep their data secure while transmitting and storing in an off-site location?
(A) They should encrypt their data using public key encryption.
(B) They should use a symmetric key encryption algorithm to protect their data.
(C) They should only send nonsensitive data off-site.
(D) They should make physical copies of their data and ship it to the off-site location weekly.
15. In putting together a team, the project manager wants to have members with different backgrounds, even if they are in nonrelated fields. What is the best reason for this idea?
(A) Different experiences will help develop leaders on the team.
(B) There will be support for the project from all areas that have team members involved.
(C) The team members will ensure the project excels in their area of expertise.
(D) Different perspectives will help develop a better product.
16. What should an organization with extra computers and large amounts of data that they are unable to process consider?
(A) Utilizing a distributed computing model
(B) Adding extra servers to their location to be available when needed
(C) Limiting the amount of data collected to balance the available processor speed
(D) Maintaining a sequential computing model
17. Which of the following will help organizations gain insights about their business?
(A) Collecting and analyzing large amounts of data to identify patterns and trends they can use to their advantage
(B) Separating large amounts of data into smaller datasets and analyzing those for faster results
(C) Developing decryption data techniques to be able to drill down and analyze data the government posts online
(D) Creating copies of company data to let each division do their own analysis without impacting others
18. How does data streaming on the Internet work?
(A) Data is sent along the shortest path to reduce buffering.
(B) Packets are created at the sender’s end and reassembled at the receiver’s end.
(C) It uses HTML to share documents among users when requested through their web browsers.
(D) It creates redundancy, so when part of the Internet is down, information can keep flowing.
19. How do Internet packets travel to their destination?
(A) Router to router based on the travelling salesman algorithm
(B) Along the same path to stay in order
(C) Timed to arrive at the destination in their correct order
(D) Along a variety of different paths
20. What action does the Internet Protocol (IP) perform?
(A) It ensures packets can be transmitted across different equipment used with the Internet.
(B) It enforces the Internet’s rules for website names.
(C) It classifies the data into clusters used for Internet traffic analysis.
(D) It measures the latency on the Internet to determine the fastest path to send the data.
21. You are writing code to count duplicates in an existing list. What code could replace for the algorithm to work correctly? Assume all variables have been correctly initialized.

(A) listNums[index] > listNums[index - 1]
(B) listNums[index] < number
(C) listNums[index] = number
(D) listNums[index] = listNums[index + 1]
22. What is bandwidth?
(A) The amount of data that can be transmitted in a specified amount of time
(B) The speed at which that data can be downloaded
(C) The size of the cable that connects homes and businesses to the Internet
(D) The amount of delay between requesting data and receiving it
23. How can consumers ensure that a website is not a phishing scam before making an Internet purchase?
(A) Go to the website directly rather than clicking a link from an e-mail.
(B) Call the company directly.
(C) Use antivirus software and keep it up-to-date.
(D) Use a firewall to block malware.
24. With regard to multifactor authentication methods, a security token texted to your cell phone is an example of which category?
(A) Knowledge
(B) Possession
(C) Inherence
(D) All of the above
25. Which of the following ensures you have a strong password?
(A) You can remember it without writing it down
(B) A string that includes special characters and uppercase and lowercase letters
(C) It is at least 8 characters long
(D) All of the above
26. Why is the Internet designed to be fault-tolerant?
(A) So the system doesn’t crash when people make typos in their web requests
(B) So the Internet can keep running even when it has malware
(C) So it can keep running when sections of it are not working
(D) So as companies expand to new locations, IP conflicts can be resolved
27. When analog data is converted to digital data,
(A) the data match exactly.
(B) the digital data is an approximation of the analog data.
(C) the analog data approximates the digital data.
(D) the digital data has more values than the analog data.
28. While crowdsourcing is often used to fund projects, what is another use in practice today?
(A) Diagnosing medical conditions by asking if others have similar symptoms
(B) Asking those who register with a company to evaluate new products
(C) Lowering costs by using the crowd’s computers during periods of activity
(D) Matching people needing work with job openings
29. If data analysis identifies new patterns, what should a company do with the information?
(A) Further analyze the data pattern identified to make strategic decisions.
(B) Change the prices on their products to match the findings for increased sales.
(C) Get their products to market faster to increase their profit.
(D) Use it to place targeted ads with people who are repeat customers.
30. What value will the following code display? Assume all values are correctly initialized.
num is a variable holding an integer value.
DISPLAY (num MOD 10)
(A) The value in the ones position
(B) The value in the tens position
(C) The current value in the variable num
(D) The quotient of num divided by 10
31. Which code segment will correctly add a name to a team roster?
Assume all variables and lists are appropriately initialized.

(A) Block 1
(B) Block 2
(C) Both Block 1 and Block 2
(D) Neither Block 1 or Block 2
32. Which algorithm will determine if a number is even?
(A) 
(B) Assume list is initialized with integers.
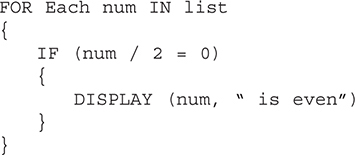
(C) 
(D) 
33. Why is a binary search the most effective way to search a sorted dataset?
(A) The item searched for bubbles to the beginning of the dataset after one pass.
(B) It uses machine learning with each pass of the data to learn where the data is located in the file.
(C) It eliminates half the dataset with each iteration of the search.
(D) It merges sections of data to only have to search one section with each iteration.
Questions 34—38 are related to this passage and chart.
To help people who are expecting a package to be delivered while they are away from home, a new “open it yourself” app is being developed. The purpose is to give certain people and/or organizations a special code to key in to open and close your door.
Here is a chart with basic information:
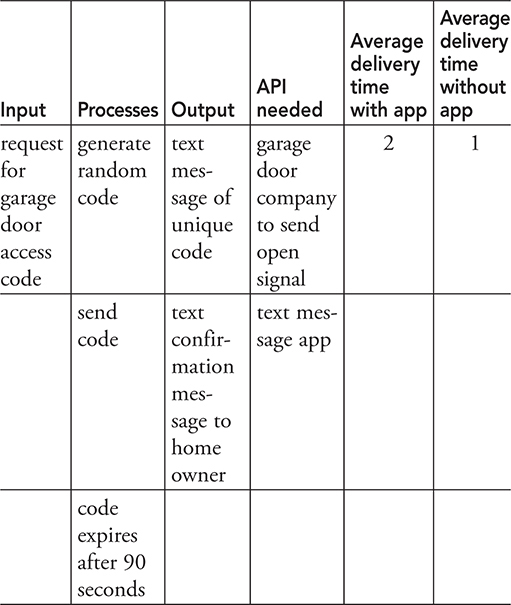
34. What input is needed for the application?
(A) An address
(B) Product description and dimensions
(C) Time of day
(D) A code requested by the delivery person
35. What is a security concern related to the data?
(A) Neighbors or people walking or driving past the house could see the delivery.
(B) Your data is accessible by companies in the cloud.
(C) The code is not encrypted.
(D) If there is a power outage, the garage door will stay up.
36. What output is provided?
(A) Signal to open door
(B) Alert text message to delivery company
(C) Unique code to delivery person
(D) All of the above
37. What is a most likely benefit?
(A) Packages are not left out so they are not vulnerable to “porch pirates.”
(B) Weather will not ruin packages.
(C) More online sales result for everyone because safe delivery is ensured.
(D) A regular delivery person for a route ensures the process is done correctly.
38. What is an impact to society?
(A) More delivery drivers will be employed because these deliveries take longer.
(B) The economy will get a boost with more purchases due to safer deliveries.
(C) Most businesses will use or offer this service.
(D) Less theft will occur as businesses will have proof that a delivery was made, lowering overall costs for everyone.
39. If a programmer tested the following code with the values indicated, would the program correctly calculate the average of the test scores?
Assume all variables and lists have been appropriately initialized.

(A) Yes, the code works as it should for both test cases.
(B) No, the code does not average the test scores correctly for either test.
(C) No, the code only works for the Test1 scores.
(D) No, the code only works for the Test2 scores.
40. When should a heuristic algorithm be used?
(A) When a problem is unable to process in reasonable time but a “close enough” solution is acceptable
(B) When the data is not sorted and cannot be placed in the order needed
(C) When a problem is undecidable because not enough information is known
(D) When searching is needed but efficiency is a requirement
41. How many times do FOR EACH loops run with lists?
(A) Once
(B) Until the index for the list is 0
(C) For the LENGTH of the list
(D) Until the user types STOP
42. Which code below can replace the missing code to select data that is less than the targetValue and even? Assume all variables have been properly initialized.

(A) (num MOD 2 = 0) OR (targetValue < num)
(B) (targetValue > num) AND (targetValue MOD 2 = 0)
(C) (num MOD 2 = 0) AND (targetValue > num)
(D) (targetValue > num) OR (NOT(num MOD 2 > 0))
43. Which type(s) of statement is needed to find all records in a list that are positive?
(A) Sequential and iterative
(B) Selection and sequential
(C) Selection
(D) Iterative and selection
44. Grace and Ada write algorithms and test them with increasingly large datasets. Algorithm 1 is still running while Algorithm 2 completed before midnight. What can you determine about the algorithms?
(A) 1 has an exponential efficiency and 2 has a polynomial efficiency.
(B) 1 has a polynomial efficiency and 2 has an exponential efficiency.
(C) 1 is unsolvable and 2 is decidable.
(D) 1 is decidable and 2 is unsolvable.
45. Each of the following can make an algorithm more readable except:
(A) Well-named variables and procedures
(B) Consistent formatting within the code
(C) Procedures that have one purpose
(D) Minimizing the use of loops so the program flow will be clearer
46. For a block of code under an ELSE statement to run, the selection criteria result must be which of the following?
(A) Repetitive
(B) Compound
(C) True
(D) False
47. Which set of pseudocode will correctly cause an alarm clock to chime at the correct time?
(A) Compare alarm time to current time
If the times are not equal, check a.m./p.m. indicator
If a.m./p.m. is equal, turn on alarm
(B) Compare alarm time to current time
If the times are equal, check a.m./p.m. indicator
If a.m./p.m. is equal, turn on alarm
(C) Compare alarm a.m./p.m. indicator to time a.m./p.m.
If not equal, compare alarm time to current time
If the times are equal, turn on alarm
(D) Compare alarm a.m./p.m. indicator to time a.m./p.m.
If not equal, compare alarm time to current time
If the times are not equal, turn on alarm
48. Which diagram matches the code below?

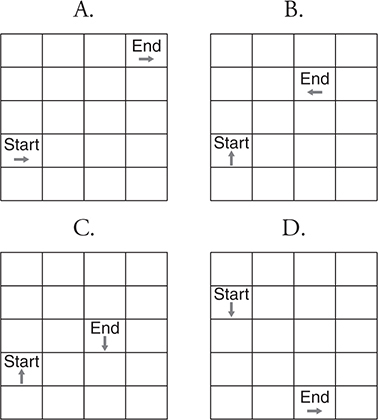
49. You need to swap the first and last values in a list. Which option produces the correct process?
(A) ![]()
(B) 
(C) 
(D) 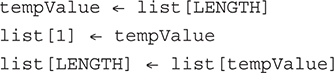
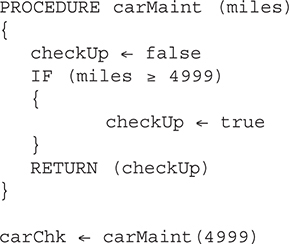
50. What is the value of carChk after the code below runs?
(A) False
(B) True
(C) 5000
(D) 4999
51. Which of the following places the numbers in ascending order?
i. 01011110
ii. 01011101
iii. 92
(A) i, ii, iii
(B) i, iii, ii
(C) ii, iii, i
(D) iii, ii, i
52. Will the code run as expected to dispense items purchased in a vending machine?
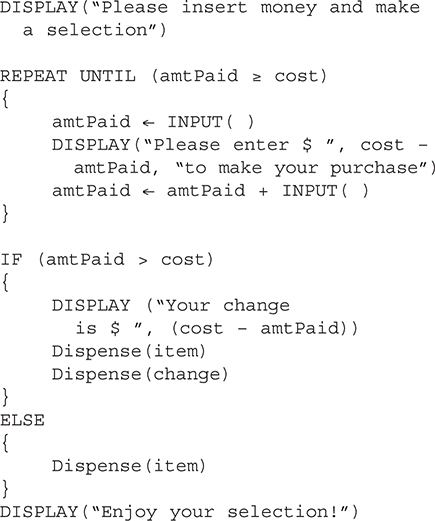
(A) Yes, the code works as expected.
(B) The REPEAT UNTIL loop is an infinite loop.
(C) The calculation of the amount of change to return is incorrect.
(D) The > sign should be < in the IF statement.
53. What is displayed after the following code runs?
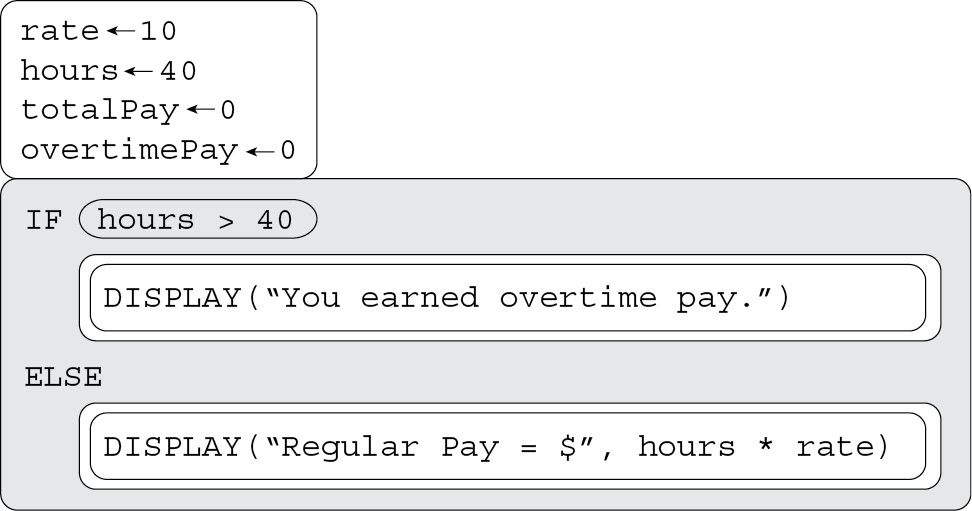
(A) You earned overtime pay.
(B) Regular Pay = $40 * 10
(C) 400
(D) Regular Pay = $400
54. How many times does the following loop run?

(A) The REPEAT loop will run 5 times.
(B) The REPEAT loop executes once and exits the loop after numSold’s value changes.
(C) The REPEAT loop never ends, creating an infinite loop because numSold’s value keeps changing.
(D) The program has an error and will not run.
Questions 55—57 refer to the following code.

55. What will the code display?
(A) dog, dogfood, cat, catfood, fish
(B) dog, dogfood, cat, catfood, fish, fishfood
(C) fish, fishfood
(D) fish
56. What is the length of the list “pets” after the code runs?
(A) 4
(B) 5
(C) 6
(D) 7
57. What is value of pets[3] after the following code is run?
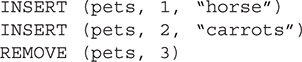
(A) It is an empty field.
(B) dog
(C) dogfood
(D) cat
58. What is this code doing? The list named numbers contains integers. Assume all variables are correctly initialized.

(A) Calculating how many numbers are in the list
(B) Calculating the sum of all the values in the list
(C) Calculating the average of the values in the list
(D) Calculating the minimum value in the list
59. What should project teams do to produce a better software product?
(A) Break down the problem into manageable units.
(B) Code while requirements are being finalized to have more time for testing.
(C) Spend testing time only on the complicated sections.
(D) Not allow any changes from the user.
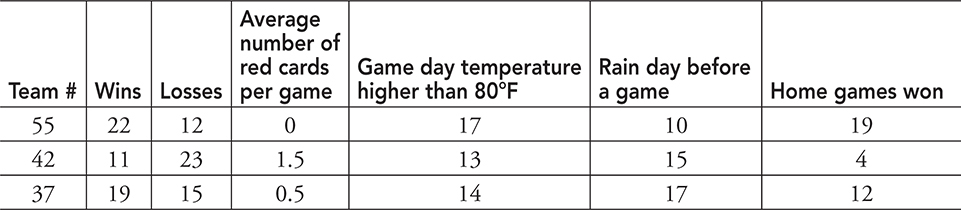
60. A soccer league tracks certain stats by team as seen in the table below. Which of the following CANNOT be determined by the data?
(A) If a team wins more often when the number of red cards is less than 1 per game
(B) If a team wins more when they were the home team
(C) If days where the temperature was 80°F were also rainy
(D) Team winning percentage
61. What is this block of code doing?
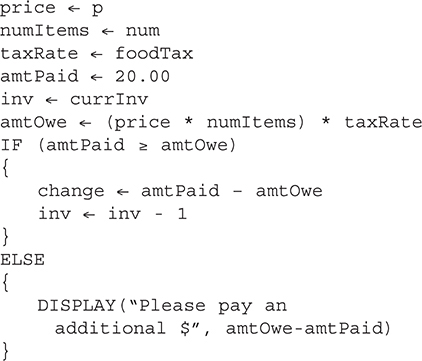
i. Calculates the tax rate for an item
ii. Calculates current inventory numbers
iii. Calculates the change owed the customer or if the customer needs to pay more for their purchase
(A) i and ii
(B) i and iii
(C) ii and iii
(D) i, ii, and iii
62. Which set of code will move the robot from start to stop? The robot may not use gray blocks.
(A)

(B)

(C)

(D)

63. Which of the algorithms below will produce the same result? Select two answers.
(A) Processing a list from the beginning to the end and counting the number of elements that begin with the letter “a”
(B) Processing a list from the end to the beginning and counting the number of elements that begin with the letter “a”
(C) Processing the list with a merge search to group the elements that begin with “a” and then counting them
(D) Processing the list with a procedure to see if the element begins with the letter “a” and keeping count with a local variable
64. An alarm company records the number of times each door is opened and closed. The alarm cannot be set if a door is still open. How can the alarm company code this option in its software? Select two answers.
(A) If the door count multiplied by 2 gives an odd number, then the door is open.
(B) If door count MOD 2 = 1, then the door is open.
(C) If the number of times a door is opened does not equal the number of times it is closed, then the door is open.
(D) If the quotient of dividing the door count by two is an even number, then the door is open.
65. A simulation for a new app to allow students to place a lunch order by 11:00 a.m. to speed up the lunch line is being tested. What information will the simulation provide? Select two answers.
(A) If a new line at the pick-up station will cause a slowdown
(B) If students will use the app often enough to make it worth the cost of developing
(C) If the app will decrease the amount of wasted food
(D) If the app can speed up the lunch line
66. If two people need to collaborate on a document but are in two different locations, what is the best solution? Select two answers.
(A) One person should travel to the other person’s location for better communication.
(B) Assign a different person to work on the document that is located in the same place as one of the others.
(C) Use a cloud-based service for the document so both can edit the current version of the document.
(D) Hold video conferences for them to speak face-to-face to discuss the document.
67. Why are “citizen scientists” being used on projects? Select two answers.
(A) They can record local data to be included in global databases.
(B) They are paid minimum wage.
(C) They can record data over a longer period of time.
(D) Retired scientists can maintain involvement in their area of expertise.
68. Which items can be represented by two binary digits? Select two answers.
(A) Pizza with 10 slices
(B) Number of eyes humans have
(C) Number of letters in the word “dog”
(D) Number of donuts in a dozen
69. Which expressions are equivalent to: number ≤ 42 AND (grade ≥ 9)? Select two answers.
(A) NOT (number > 42) AND (grade = 9 OR grade > 9)
(B) (number < 43) AND (grade > 8)
(C) (number < 42) AND (NOT (grade < 9)
(D) (number > 43) AND (grade > 10)
70. What data structures provide the ability to code once and repeat multiple times in a program? Select two answers.
(A) Selection statements
(B) Sequential statements
(C) Iterative statements
(D) Procedures
STOP. End of Exam.
![]() Answers and Explanations
Answers and Explanations
If further review is needed, the Big Idea where information can be found about the question is included at the end of each answer’s explanation.
1. C—11110001 converts to 241. The error is that the number was larger than the computer could handle, resulting in an overflow error. Big Idea 2: Data
2. B—The way floating point numbers are stored can cause rounding errors. The employee sent the fractional part of numbers to the separate account, and it accumulated over time. For example, if the number was $1.988889, then $0.008889 could be sent to the extra account. Big Idea 2: Data
3. C—Storing personal information about you can be a privacy issue if the data is not protected. Additionally, the data could be sold without your knowledge. Big Idea 5: Impact of Computing
4. C—The program should display available times so people can see if the time they want is available. They can then request a time. The app should check to ensure the time has not already been taken since multiple people can use the app at the same time. Then the reservation can be recorded and the list of available times updated. Big Idea 3: Algorithms and Programming
5. C—If the song has already been played 100 times, it will be removed from the list topSongs. Otherwise, it will be played and the number of times it is played will increase by 1. Big Idea 3: Algorithms and Programming
6. D—The number of times the song has been played is still set to 100, so even after the user adds it back to the list, the next time it is played, both conditions in the IF statement will be true, and it will be removed again. Resetting it back to 0 after it has been removed from the list is the best way to resolve the problem. Big Idea 3: Algorithms and Programming
7. C—The first and third conditions evaluate to be false. The only time an OR condition is false is when both are false, and the NOT operator takes the opposite of the value, so true would become false and false would become true. Big Idea 3: Algorithms and Programming
8. B—Only the second condition evaluates to be true. Both values must be true with an AND to be true, and one or both need to be true with an OR for it to be true. Big Idea 3: Algorithms and Programming
9. D—Metadata is data about data, and the number of data fields volunteers track is about the data. The other fields are data about the sea turtle nests. Big Idea 2: Data
10. A—Only the lossless compression technique will allow the original uncompressed video to be restored for the scientists to review. Big Idea 2: Data
11. A—This is an example of unintended bias in the algorithm. By using prior experience in a position as criteria for future hiring, the data would have naturally excluded this group, leading the algorithm to also exclude them from future promotions. Big Idea 5: Impact of Computing
12. D—All of the methods can be used with further analysis. Big Idea 2: Data
13. B—A correlation identified in the data analysis may not show that a cause and effect relationship actually exists. Further research and data from new sources is needed to confirm if the relationship exists. Big Idea 2: Data
14. A—Sending transaction data off-site can present a security concern if the data is not encrypted. Public key encryption has not been broken and is the standard today. Big Idea 5: Impact of Computing
15. D—A team with diverse skills and backgrounds can deliver a better product in a collaborative environment. Big Idea 1: Creative Development
16. A—A distributed computing model uses multiple devices to run a program. This can greatly speed up the processing time for the data. Big Idea 4: Computing Systems and Networks
17. A—Smaller datasets may not have enough data to identify patterns or true trends. Big Idea 2: Data
18. B—The Internet has an end-to-end architecture because packets are created by breaking the information into smaller segments at one end (the sender’s) and are reassembled at the other end (the receiver’s). Big Idea 4: Computing Systems and Networks
19. D—Packets travel along many different paths to reach their final destination. They arrive out of order and are then reassembled at the destination. Big Idea 4: Computing Systems and Networks
20. A—Protocols are rules that are followed to ensure data can communicate across all equipment. Big Idea 4: Computing Systems and Networks
21. C—When the element at the current index position in the inner REPEAT UNTIL loop equals the value in the outer FOR EACH loop, then a duplicate exists and the counter should be incremented. Big Idea 3: Algorithms and Programming
22. A—Bandwidth measures the amount of data that can be transmitted in a specific amount of time. Therefore, knowing how much data needs to be downloaded on a regular basis is a key measurement. Big Idea 4: Computing Systems and Networks
23. A—Phishing scams can make a website look very realistic. To be sure you are at an authentic website, search to find the link yourself or type it into your browser rather than clicking on a link. Big Idea 5: Impact of Computing
24. B—Multifactor authentication usually requires two of three categories: knowledge—such as a password, possession—something they have, such as a unique security token, or inherence—something they are, used with fingerprint login. The security token texted to a cell phone is an example of possession. Big Idea 5: Impact of Computing
25. D—A good password should be easy to remember, contain uppercase and lowercase letters, contain symbols, and be at least 8 characters long. Big Idea 5: Impact of Computing
26. C—Fault tolerance means the Internet will continue to function and reroute packets when parts of it are down. Big Idea 4: Computing Systems and Networks
27. B—The digital data approximates the analog data by taking samples of the analog data at a specified rate based on the need. A higher sampling rate will more closely approximate the analog data. Big Idea 2: Data
28. D—Crowdsourcing is used in many ways and more are coming into use. Helping people find available jobs is one use. Big Idea 5: Impact of Computing
29. A—Companies should take the findings from the data-mining results and make strategic decisions to determine when and how to take advantage of the new information. The other decisions can be made based on current sales and projections and do not need data-mining techniques. Big Idea 2: Data
30. A—MOD provides the remainder after dividing. The remainder of a number after dividing by 10 will be the value in the ones column. Big Idea 3: Algorithms and Programming
31. B—Block 1 is an infinite loop. Block 2 will add the new name correctly. Big Idea 3: Algorithms and Programming
32. A—The MOD operator returns the remainder when two numbers are divided. If a number is divided by 2 and the remainder is zero, then it is an even number. Big Idea 3: Algorithms and Programming
33. C—The binary search is most efficient as a divide-and-conquer algorithm because half the data can be removed with each iteration of the search. The item can be found or determined that it is not in the dataset in a minimal number of passes. Big Idea 3: Algorithms and Programming
34. D—For the application to be able to open the garage door, a code specific to that delivery needs to be provided to the delivery person and entered into the app. The address and time of day are needed to schedule the delivery, but are not needed by the app. The product dimensions are needed for loading the truck efficiently, but the app does not need the information.
35. B—Having your data controlled by the app company is a security risk. You have no idea who has access to it and how safely it is maintained. For option A, anyone traveling past your home at the right time would know you had received a delivery. This is not an issue related to the app’s use of data. Similarly, with D, if the garage door stayed open for any reason, it is not an issue with the app. Option C could be an issue if the code stayed active, but the table shows that it expires 90 seconds after it is entered.
36. C—The app sends output, first to the delivery person with the unique code. Then once the code is typed in, the app outputs an alert text message to the app owner. The app does not send a message to the delivery company, nor does it send the signal for the garage door to open.
37. A—The most likely benefit is that packages will remain safe. “Porch pirates” who take packages off people’s doorstep will be thwarted! Depending on a location’s overhang, the weather may not have ruined them previously, but this is not the most likely benefit. People may order online more often due to safe delivery, but this is not the most likely or measurable benefit. And let’s hope the regular delivery person ensures the delivery is correct, following the algorithm, but this is not the best benefit of using the app.
38. A—The chart shows the average delivery time without the app and the amount of time it takes to make a delivery if using this app. It takes about twice as long to make the delivery using the app once the driver arrives at the location. Therefore, more delivery drivers will be hired to ensure timely delivery is still possible. While some people may purchase more online since they can get safe deliveries, this is difficult to measure whether it is related to the app or not. Maybe they just got a raise and have more income for purchases. More delivery businesses may offer the service as a result, but that is not a huge impact to society. There may be a lower theft rate, but it is not indicated in the data we have.
39. D—The code only includes test scores that are greater than 0. Test1 scores have a 0 that will not be included in the average, but it should. The IF statement should be removed to correctly calculate test averages in all cases. Big Idea 3: Algorithms and Programming
40. A—A heuristic is finding the best approximate solution when the actual solution is intractable due to current memory and/or space limitations. Big Idea 3: Algorithms and Programming
41. C—FOR EACH loops will run for each element in a list. Big Idea 3: Algorithms and Programming
42. C—To test if a number is even, you can use MOD with 2, and a remainder of 0 means it is even. Use less than “<” to determine if a number is less than another. Use AND for both conditions to be true to select the number. Be sure to use the correct variable, “num”, to test the conditions. Big Idea 3: Algorithms and Programming
43. D—Iterative code will loop until every item in the list is checked, and a selection statement is needed to determine if a number is positive. Big Idea 3: Algorithms and Programming
44. A—Tractable algorithms run efficiently for large and small datasets and have a polynomial efficiency, while intractable algorithms cannot run efficiently for large datasets and have exponential efficiency. Big Idea 3: Algorithms and Programming
45. D—Readability is a feature of algorithms that are clear and easy to understand. Every feature except D helps others understand what its intended purpose is. Loops should be used to shorten the code, which makes it more readable. Big Idea 3: Algorithms and Programming
46. D—The selection criteria must be false for the code associated with an ELSE to run. Big Idea 3: Algorithms and Programming
47. B—Option B compares the time first, and if equal, it then checks the a.m./p.m. indicator. Big Idea 3: Algorithms and Programming
48. C—This diagram starts and ends in the correct block facing in the correct direction. Remember that rotating left three times is the same as a right turn, and rotating right three times is the same as a left turn. Big Idea 3: Algorithms and Programming
49. C—The temporary variable is assigned the value at the end of the list. Then the last element can be assigned the value in the first position. Finally, the first position in the list is assigned the value in the temporary variable. Big Idea 3: Algorithms and Programming
50. B—checkUp is set to true if miles ≥ 4999. Since miles is 4999, checkUp will be true. Big Idea 3: Algorithms and Programming
51. D—The binary number 01011101 = 9310, and the binary number 01011110 = 9410, so the numbers in ascending order go from iii, ii, i for 92, 93, 94. Big Idea 2: Data
52. C—The amount of change due calculates a negative number. The calculation should be amtPaid — cost rather than cost — amtPaid. Big Idea 3: Algorithms and Programming
53. D—The ELSE condition will run because hours is not greater than 40. Therefore, the program will display answer D. Big Idea 3: Algorithms and Programming
54. D—The criteria for the REPEAT loop is incorrect. It must be a constant or a variable holding an integer value, not a Boolean value. Big Idea 3: Algorithms and Programming
55. D—The only time the animal is displayed is when it is a fish. Big Idea 3: Algorithms and Programming
56. C—The length of the list, pets, is 6 as there are 6 elements in it. Big Idea 3: Algorithms and Programming
57. C—The INSERT command moves current values over a position each time.
The REMOVE command shifts list values to the left.
After these commands, pets[3] = dogfood. Big Idea 3: Algorithms and Programming
58. C—value1 is storing the sum of all the values in the list. value2 counts the number of items in the list. value3 is the sum divided by the number of values, which provides the average value of all the elements in the list. Big Idea 3: Algorithms and Programming
59. A—None of the other options will produce better, or even working, code. Big Idea 1: Creative Development
60. C—The only information that cannot be determined from the table is if it rained on days that were 80°F or warmer. Big Idea 2: Data
61. C—The block of code calculates the current inventory, change owed, if any, and the additional amount to pay, if any. It does not calculate the tax rate. That is provided and used to calculate the total amount due. Big Idea 3: Algorithms and Programming
62. B—The code starts and stops in the correct block facing the correct direction. Remember that rotate blocks do not move forward. They rotate the direction within the current block. Big Idea 3: Algorithms and Programming
63. A, B—Processing a list from the beginning to the end or the end to the beginning with the same code in each to find and count the elements that start with an “a” will produce the same results. A merge search does not exist (but a merge sort does). The local variable that counts the words would not be available outside of the procedure. Big Idea 3: Algorithms and Programming
64. B, C—If one variable represents the number of door openings and closings, then modulus math, which gives the remainder after division, can determine if a number is even or odd. An odd number would mean a door is open. Option C uses two variables for the same door, one to count the number of times a door opened and the other to record the number of times it closed. If these are not the same, then a door is open and the alarm cannot be set. Big Idea 3: Algorithms and Programming
65. A, D—The simulation can show if the lunch line will speed up and if a new bottleneck will be created at the pick-up line. The simulation will not show how often the app will be used or if food will be wasted. Big Idea 3: Algorithms and Programming
66. C, D—Cloud-based storage can be accessed from any location with an Internet connection and is a good solution for storage when people are in different locations. Video conferences will help the collaboration effort. Big Idea 1: Creative Development
67. A, C—With training, “citizen scientists” can provide a wealth of data over longer periods of time and they could be anywhere in the world, creating more data from a variety of locations. Big Idea 5: Impact of Computing
68. B, C—Two binary digits can hold up to the decimal equivalent 3, so only the numbers 0, 1, 2, and 3 can be stored using two binary digits. Big Idea 2: Data
69. A, B—Both of these are different ways of stating (number ≤ 42) AND (grade ≥ 9). NOT (number > 42) is the same as (number ≤ 42) as is (number < 43). (grade = 9 OR grade > 9) is a longer way of stating (grade ≥ 9). (grade > 8) also represents (grade ≥ 9). Big Idea 3: Algorithms and Programming
70. C, D—Procedures can be coded once and called as many times as the program needs. Iterative statements, also called loops, can repeat a block of code as many times as needed in a program. Big Idea 3: Algorithms and Programming
Analyzing Your Performance on Practice Exam 2
The exercise below will help you quickly and easily identify the chapters in Step 4 that you most need to review for the AP Computer Science Principles multiple-choice exam. Revise your study plan so that you prioritize the chapters with which you had the most difficulty.
Look at your answer sheet and mark all the questions you missed. Then shade in or mark an X in the boxes below that correspond to the question numbers that you missed. For what concepts did you miss the most questions? As you review, keep in mind the number of questions to expect from each section, spending more time on those that will appear the most. See Chapter 1 on “What You Need to Know About the AP Computer Science Principles Assessment” for those percentages.
Big Idea 1: Creative Development
Big Idea 2: Data
Big Idea 3: Algorithms and Programming
Big Idea 4: Computing Systems and Networks
![]()
Big Idea 5: Impact of Computing