5 Steps to a 5: AP Computer Science Principles 2024 - Sway J.S. 2023
AP Computer Science Principles Practice Exam 1
STEP 5 Build Your Test-Taking Confidence
Multiple-Choice Questions
ANSWER SHEET

AP Computer Science Principles Practice Exam 1
Multiple-Choice Questions
Time: 2 hours
Number of questions: 70
The multiple-choice questions represent 70% of your total score.
Directions: Choose the one best answer for each question. The last eight questions of the test have two correct answers; for these, you will be instructed to choose two answer choices.
Tear out the answer sheet on the previous page and grid in your answers using a pencil. Consider how much time you have left before spending too much time on any one problem.
AP Computer Science Principles Exam Reference Sheet
On the AP Computer Science Principles exam, you will be given a reference sheet to use while you’re taking the multiple-choice test. A copy of this six-page reference sheet is included in the Appendix of this book (reprinted by permission from the College Board).
To make taking this practice test like taking the actual exam, you should tear out the reference sheet so you can easily refer to it while taking the test. Save these reference pages since you’ll need to use them when you take AP Computer Science Principles Practice Exam 2.
If you lose the pages, the reference sheet is also available near the end of the PDF publication “AP Computer Science Principles Student Handouts” on the College Board website. Here is the URL:
https://apcentral.collegeboard.org/pdf/ap-csp-student-task-directions.pdf?course=ap-computer-science-principles
1. You won the lottery and elected to receive a lump sum! The largest number the bank’s computer can store is 231 - 1, or 2,147,483,647. After depositing your lottery winnings of $2,500,000,000, what will the result be?
(A) Your winnings were more than the largest number the bank’s computers could hold, so an overflow error will occur.
(B) Since decimal numbers are stored imprecisely in computers, a rounding error will occur.
(C) The amount will be represented in machine code format, so converting it to decimal will show the balance in a more readable format.
(D) The amount will cause a runtime error.
2. You stop by and purchase your favorite snack after school one day. You notice the cash register shows the change you are owed as $0.04999999 rather than $0.05. How is this possible?
(A) The cash register DISPLAY procedure has an error.
(B) A rounding error occurred.
(C) It’s displaying the change owed in a different currency.
(D) The amount is represented as a string field rather than a number.
3. You are assigned a parking space in a large parking lot by an automated machine. You recognize that the parking space number is displayed in binary, but the parking spots are labeled in decimal numbers. Convert the parking space number 10011011 to decimal to know where to park and avoid getting towed.
(A) 154
(B) 155
(C) 157
(D) 9F
4. When designing a web page, you see a color you want to use listed in binary as: 01010000, 11001000, 01111000. Which color is it, given the decimal equivalents (red, green, blue)?
(A) (32, 76, 414)
(B) (50, 118, 78)
(C) (80, 200, 120)
(D) (128, 310, 170)
5. Your bank asks for your phone number to associate it with your account. What is this an example of?
(A) A privacy concern
(B) Multifactor authentication
(C) A phishing attempt
(D) Asymmetric authentication
6. You have to change a program written a year ago by someone else. A sample section of code is below. How could the original program author have helped anyone making changes at a later date?

(A) Provided the original program requirements
(B) Added a video describing the program design and functionality
(C) Used procedure and variable names that described their purpose and content
(D) Provided written documentation of the application development process
Questions 7—8 are based on the code below. Assume all lists and variables have been properly initialized.
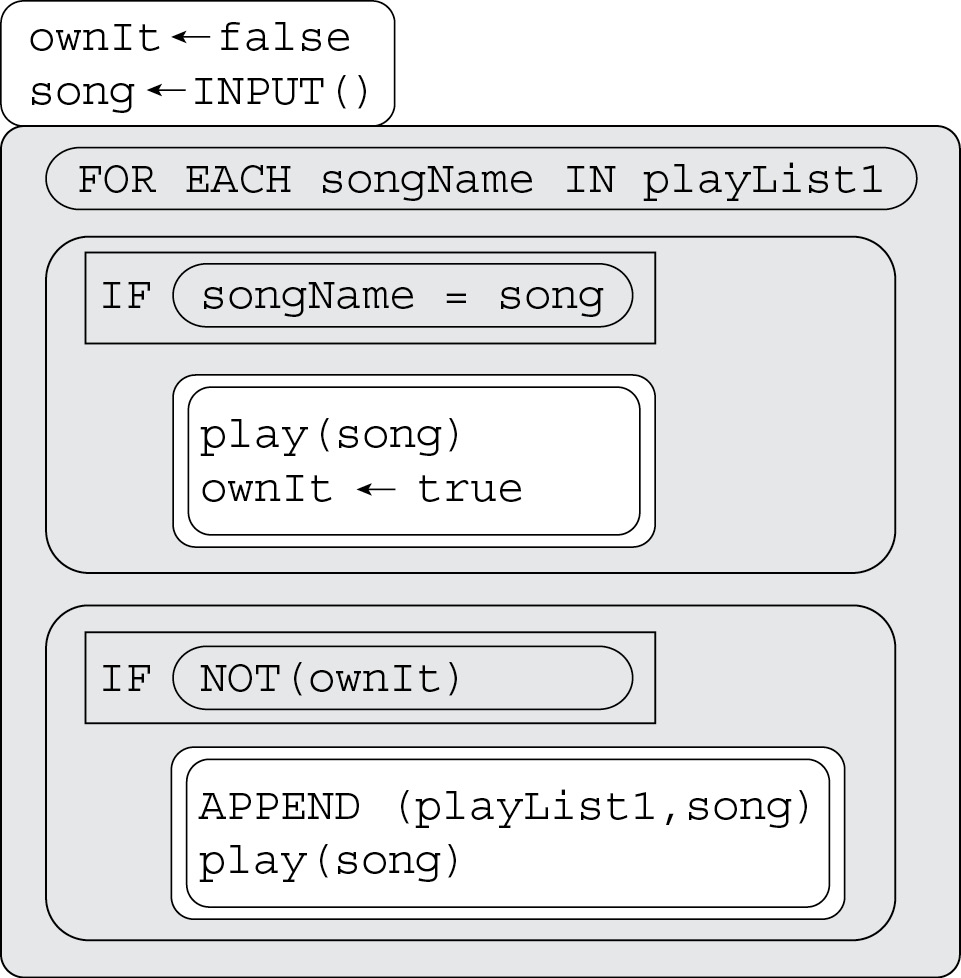
7. What does the code do?
(A) Plays a song from the playlist.
(B) If a song requested by the user is in the playlist, plays it; otherwise adds it to the end of the playlist and then plays it.
(C) Moves a song from its current position in the playlist to the end of it, then plays the next one in the list.
(D) Identifies songs the user wants to hear but does not own. Provides a way to purchase the song and appends it to their playlist.
8. In the code, if “play” is a procedure, what does “song” represent in the line: play(song)?
(A) It is the name of the procedure for documentation purposes.
(B) It is an input value where the user requests the song to be played.
(C) It is a value being passed to the procedure via an argument.
(D) It is an expression that must be evaluated to be used in the procedure.
9. Which statement is NOT true?
(A) Lower level languages are easier to debug because the language is closest to what the computer executes.
(B) Higher level languages are easier to debug because the language is closer to natural language.
(C) Lower level languages provide less abstraction.
(D) Higher level languages are easier for people to code in because they are more abstract.
10. If a simulation of the solar eclipse is set up to test the effectiveness of glasses to safely view the sun, which scenario is most likely if the first test shows the glasses are inadequate?
(A) The team can modify the degree of darkness and retest quickly to determine the threshold of effectiveness.
(B) The team should stop the test and notify the company that makes the glasses.
(C) The team should rerun the test multiple times to ensure the results are valid.
(D) The team should rewrite the code for the simulation, and then retest.
11. A simulation of conditions for a new sensor to be used with self-driving cars is being designed. The pseudocode for the test is below.

Which condition is not a useful simulation test for the sensor?
(A) Multiple obstacles at the same time.
(B) Zero incidents.
(C) Set up objects at 3 feet, less than 3 feet, and greater than 3 feet to determine the action taken.
(D) If the car causes an accident by swerving.
12. Which of the following will evaluate to “true”?
i. (true AND true) OR (true AND false)
ii. NOT(true OR false)
iii. NOT(false) AND NOT(true AND false)
(A) i and ii
(B) i and iii
(C) ii and iii
(D) i, ii, and iii
13. What outcome will the Boolean conditions in the diagram produce at steps 1, 2, and 3?
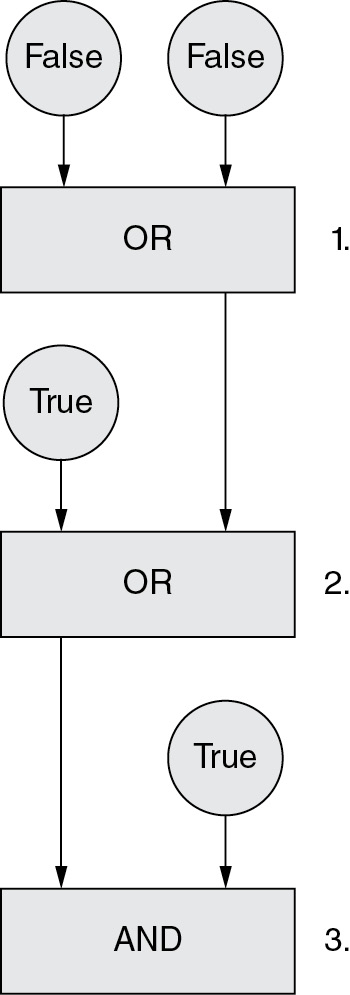
(A) 1—True, 2—True, 3—True
(B) 1—False, 2—False, 3—True
(C) 1—False, 2—True, 3—True
(D) 1—True, 2—False, 3—False
14. A camera watching an eagle’s nest starts recording when a motion detector starts. Which of the following is metadata?
(A) The latitude and longitude of the nest
(B) The date and time the motion is detected
(C) The number of eagles using the nest
(D) The number of frames per second the camera records
15. Susie’s mother wants a copy of a photo from a family vacation that Susie took. The picture is too large to e-mail. How should Susie compress the image if her mother wants to print a large copy of it suitable for framing?
(A) She should use a lossless compression technique, which will be needed to print a version with high enough quality to frame.
(B) She should use a lossy compression technique to obtain enough compression to send the image.
(C) They should be combined for the best compression technique.
(D) Any compression technique will be sufficient in this case.
16. Which one of the following would be a good project for citizen scientists and why?
(A) Counting pine trees in urban conditions to get accurate data about the spread of the pine beetle
(B) Identifying new stars using personal telescopes to keep costs lower for the tracking organization
(C) Reading different-genre books and evaluating them so book publishers know which types of book manuscripts to accept and market
(D) Counting fish in a lake to know if the fish are safe to consume
17. What describes the process of searching datasets for incomplete data records to process?
(A) Classifying
(B) Cleaning
(C) Clustering
(D) Filtering
18. A teacher wants to determine student opinions of computer science before and after taking a course. She gives students a survey on the first and last days of class. The survey includes questions about students’ impressions of computer science, if the teacher communicated effectively, if the teacher was positive about the course material, and if students gave their best effort in the course. What questions can be determined from the survey data?
i. If students who moved from a negative to positive impression of computer science after taking the course also thought the teacher communicated effectively
ii. Which students plan to major in computer science after taking the course
iii. If the students who did not change their existing view of computer science after taking the course gave their best effort in the course
(A) i
(B) i and iii
(C) ii and iii
(D) i, ii, and iii
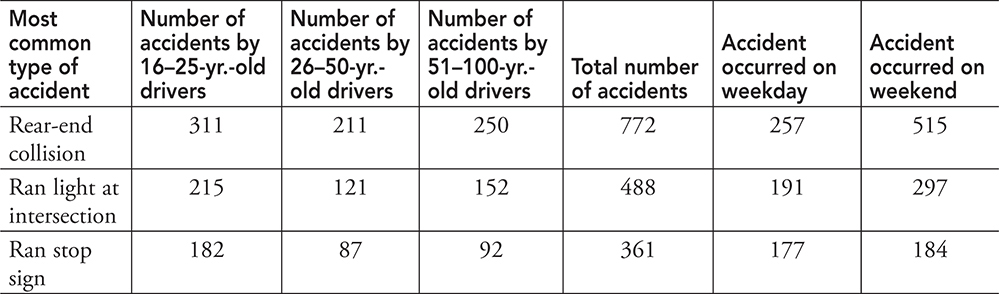
19. Given the table of data about car accidents below, which outcome is supported by the data?
(A) Drivers ages 16—25 have the fewest accidents.
(B) More accidents occur on the weekdays.
(C) Drivers age 26—50 have fewer accidents than the other two age groups.
(D) Adult drivers have more accidents on weekdays during rush hour.
20. Why do businesses and scientists attempt to analyze large datasets?
(A) To gain insights smaller subsets of data may not provide
(B) To confirm findings from smaller datasets
(C) To identify potential problems in the metadata
(D) To obtain economies of scale with hardware needed to store the data
21. How do the World Wide Web and the Internet work together?
(A) They perform the same functionality.
(B) The web uses HTTP to share web pages using the Internet.
(C) The Internet uses the web to connect devices to share data.
(D) The Internet is an application that runs using the web.
22. If a fire occurs at a major Internet hub, what is the result?
(A) Internet traffic will be routed to its destination a different way because of the redundancy built into the Internet.
(B) The part of the globe that is served by that Internet hub will be down because of the end-to-end architecture of the Internet.
(C) Different IP addresses will be assigned to devices that were impacted by the unavailability of the Internet hub.
(D) People can use dedicated phone lines as a backup with no change in service.
23. The time it took to complete a task sequentially was 25 seconds. The time it took to complete the same task using a parallel computing model was 10 seconds. What is the speedup?
(A) 2.5
(B) 0.4
(C) 15
(D) -15
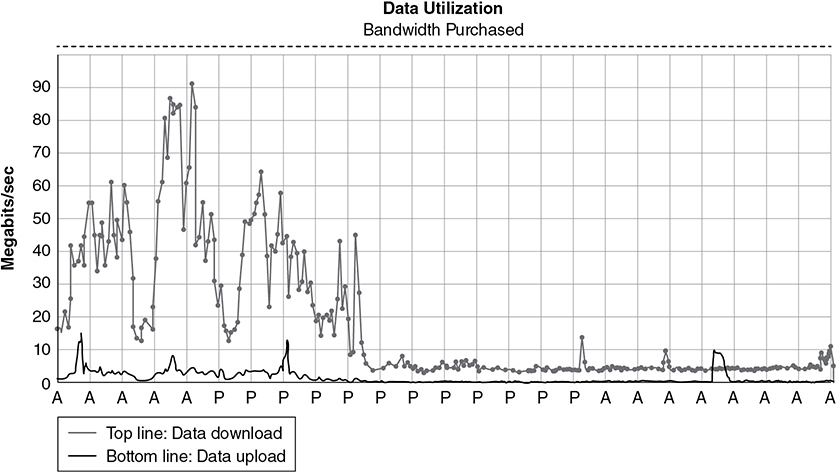
24. If a company is trying to determine whether to upgrade its bandwidth based on the following graph, what should they measure?
(A) Amount of data uploaded because it includes strategic company backup data
(B) Amount of data downloaded because it has the largest impact on the bandwidth
(C) Frequency of the peak times
(D) Number of devices used on the network
25. Why is the trust model of the Internet important?
(A) It ensures the private security key has not been compromised.
(B) It establishes a dedicated line between two destinations to ensure security.
(C) It enables the secure transfer of data, such as a credit card transaction, which allows online purchasing.
(D) It ensures the privacy of customers making online transactions.
26. You notice a file being uploaded every night to a site you are not familiar with. Opening the file, it looks like a file of your work from the day. This could be an example of a
(A) computer virus.
(B) keylogger file.
(C) network worm.
(D) phishing attack.
27. You are part of a team that created facial recognition software. However, you just learned an innocent person was taken into custody using only facial recognition software. What can the team do to remove any bias in the future?
(A) Create better training materials for interpreting the results
(B) Use photos of a more diverse population to train the algorithm for recognition
(C) Contact lawmakers to support regulation of the use of facial recognition software
(D) Add new members to the team to increase the diversity to better identify and avoid bias
28. You make a compressed version of an old classic song to send to a friend. You notice that the sound quality is not as sharp as the original. What is the likely cause?
(A) The file was compressed with a lossy algorithm.
(B) The file was compressed with a lossless algorithm.
(C) The file was corrupted during the copying process.
(D) The file was copied from a digital version rather than the original analog version.
29. Which of the following is true about packets?
(A) The receiving device acknowledges the first and last packets to indicate receipt of the data stream.
(B) Packets travel in order to their destination.
(C) Packets follow the shortest path to their destination.
(D) Packets are reassembled at their final destination.
30. How do TCP and IP interact?
(A) IP forwards the data to the ISP to identify which TCP to use.
(B) TCP hands off control to HTTP, which passes it to IP.
(C) TCP creates packets from the data to be sent and transfers control to IP for routing. TCP then reassembles the packets at the destination.
(D) IP uses UDP in conjunction with TCP to securely send data.
31. An e-mail goes out from your organization’s payroll department to all employees stating that everyone needs to confirm or update their banking information to ensure paychecks are deposited on time. It turns out that this was not an e-mail from the payroll department. It is most likely a
(A) computer virus.
(B) keylogger attack.
(C) phishing attack.
(D) malware insertion point.
32. You need to share a confidential file with another organization. You know the file needs to be encrypted to prevent unauthorized access to its contents. What is the best method of encryption to use?
(A) Certificate Authorities (CAs) to validate the security of the organization where you are sending the data
(B) Multifactor authentication to ensure multiple steps of security
(C) Public key encryption so you do not have to share the encryption key
(D) Symmetric key encryption so you each have the encryption and decryption keys
33. What is a benefit of the government posting databases for public use?
(A) It is a way to identify the need for new policies and regulations.
(B) Consumers can learn more about how their individual data is being collected, stored, and used.
(C) Companies can opt out to prevent competitors from learning about their business.
(D) All businesses can access the data at no cost, aiding organizations that would otherwise not have the resources to obtain the data on their own.
34. Which algorithm will display the smallest number in a list of positive numbers? Assume max is a variable holding the largest number in the list.
(A) 
(B) 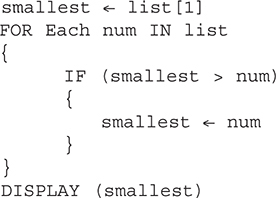
(C) 
(D) 
35. Which of these is a Boolean expression?
(A) X ← 57
(B) Y ← temp * 120 / 100
(C) (temp > 32)
(D) 72 + 12 — (12 * 6) → z
36. What can be determined from the following program flow?

(A) A game is played by calling different procedures.
(B) An error will occur due to invalid procedure names.
(C) Parameters are missing from the procedures, resulting in a runtime error.
(D) A compile time error occurs due to Score() and HighScore().
37. Which statement’s format is incorrect?
(A) 
(B) x ← x + y
(C) list[i] ← list[j]
(D) ![]()
38. Which algorithm should be used to find a phone number on a contact list?
I.
Sort the contact list by name
Search for the phone number using a binary search
Display the correct phone number
II.
Sort the contact list by area code
Search for the phone number using a linear search
Display the correct phone number
(A) I.
(B) II.
(C) I and II are equally effective.
(D) A combination of both I and II should be used.
39. Why does a computer playing chess use a heuristic algorithm?
(A) It ensures that the computer only wins a certain number of times, making it a more enjoyable experience for people.
(B) It ensures that humans only win a certain percentage based on statistics.
(C) It takes too long to analyze all possible moves, so the computer takes the next best move.
(D) It checks each possible combination of moves for the best move.
40. You are determining the attributes for an AI (Artificial Intelligence) algorithm for a bank to use for approving customers for loans. You select age, income, employment status, and active-loan status as attributes to consider. The bank finds that very few new loans are being offered to college-educated individuals due to existing college loans. This is an example of bias in
(A) analyzing the data.
(B) collecting the data.
(C) preparing the data.
(D) reporting the data.
41. If a list named snacks contains the values:
![]()
A variable place is assigned the value:
place ← LENGTH(snacks)
What will the value snacks[place] contain?
(A) 5, the number of items in the list.
(B) 6, the number of letters in the word “grapes.”
(C) grapes, which is the value in the 5th position of the list.
(D) Error, a list cannot be accessed in this way.
42. Will both of the following two blocks produce correct results? Assume all variables have been properly initialized.
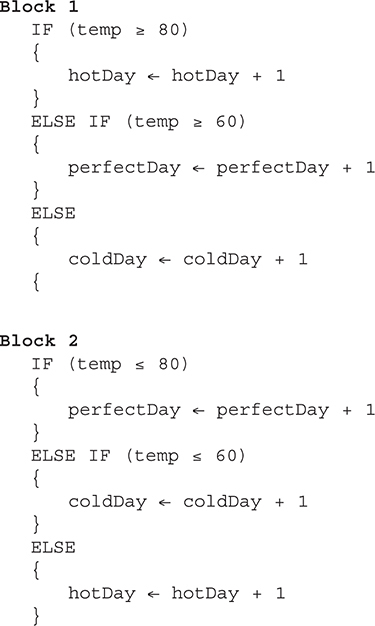
(A) Only Block 1 is correct.
(B) Only Block 2 is correct.
(C) Both blocks are correct.
(D) Neither block is correct.
43. Determining that an algorithm has a polynomial efficiency means it runs in
(A) an acceptable amount of time even for large datasets.
(B) less time for worst-case scenarios than average scenarios.
(C) an exponential amount of time possibly even for small datasets, making it unable to run for large datasets.
(D) a fractional amount of time for fractional values.
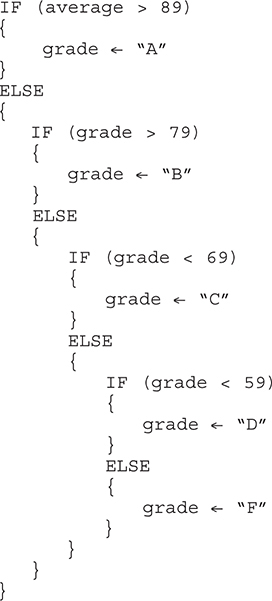
44. Which set of code will calculate the letter grade correctly for a 10-point scale? Assume average is a variable holding the student average.
(A)
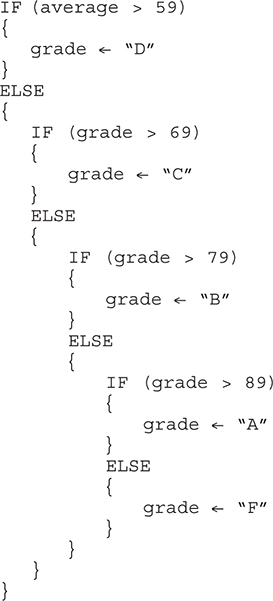
(B)

(C)

(D)
45. The code below is a robot algorithm. Which diagram matches the code?

(A) 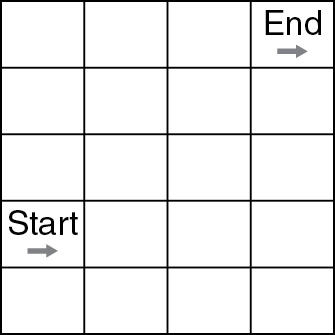
(B) 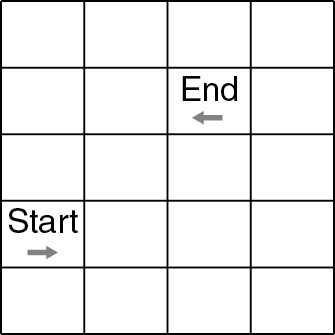
(C) 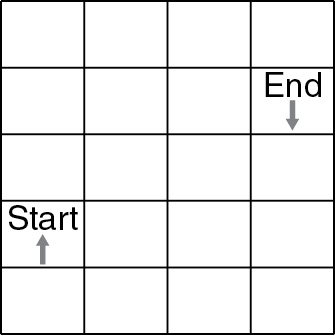
(D) 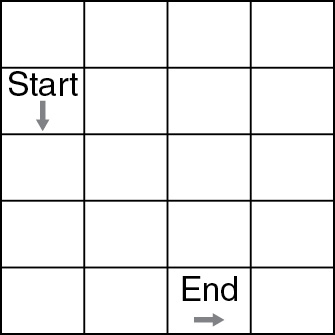
46. What benefit does an API provide?
(A) It allows programmers to share their code via the API for others to test.
(B) It connects software components providing prewritten and tested code available for use.
(C) It provides algorithms for difficult code to be reviewed.
(D) It provides documentation programmers can use for their programs rather than creating their own.
47. What is the value of x after the code below runs?

(A) -10
(B) 10
(C) 4
(D) -4
48. What is the value of y after the following statements?
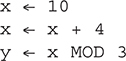
(A) 0
(B) 2
(C) 3
(D) 4
49. What is displayed after the following code runs?
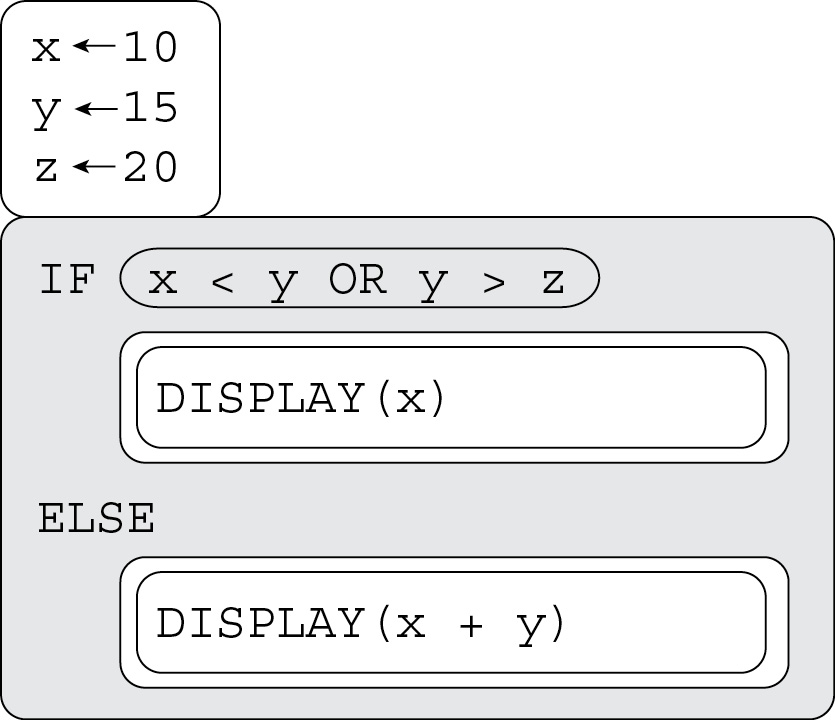
(A) 10
(B) 15
(C) 20
(D) 25
50. Which of the following two algorithms produces the sum of the elements in the list? Assume the list is initialized and is not empty.

(A) Block 1
(B) Block 2
(C) Blocks 1 and 2
(D) Neither Block 1 nor 2
51. What will the following code produce?

A. “Hello World!” will be printed multiple times.
B. The code inside the REPEAT UNTIL loop never executes.
C. The REPEAT UNTIL loop never ends, creating an infinite loop.
D. The program will have a runtime error.
52. What will the code display?

(A) popcorn, candy, grapes, apples, banana
(B) popcorn, candy, grapes, apples, banana, banana
(C) popcorn, candy, grapes, apples, banana, banana, banana
(D) popcorn, candy, grapes, apples, banana, banana, banana, banana
53. What is the value of snacks after the following code is run?

(A) 5, 6, 7, 8, candy, grapes, apples, banana
(B) popcorn, candy, grapes, apples, popcorn, candy, grapes, apples
(C) popcorn, popcorn, popcorn, popcorn, candy, grapes, apples, banana
(D) popcorn, popcorn, popcorn, popcorn, popcorn, popcorn, popcorn, popcorn
54. If a procedure accepts two strings as parameters and returns a combined string, what is the procedure doing?

(A) Appending
(B) Attaching
(C) Bonding
(D) Concatenating
55. What is an iterative software development process designed to do?
(A) Produce better software with a proven process
(B) Shorten the time of developing software by beginning to code while the requirements are being determined
(C) Eliminate the testing step by using only APIs
(D) Develop it right the first time through the iterative process
56. Suppose your program needs to process all values less than a specified value, but your actual test results do not match the expected test results. What is NOT a debugging technique you can use to identify the problem?
(A) Hand-tracing the code
(B) Adding DISPLAY statements to see values in variables at different points in your program
(C) Using a visualizer to view the code as it is executing
(D) Rerunning the code to verify the results
57. Which set of code will move the robot from start to stop and end facing the correct direction? The robot may not move into gray blocks.
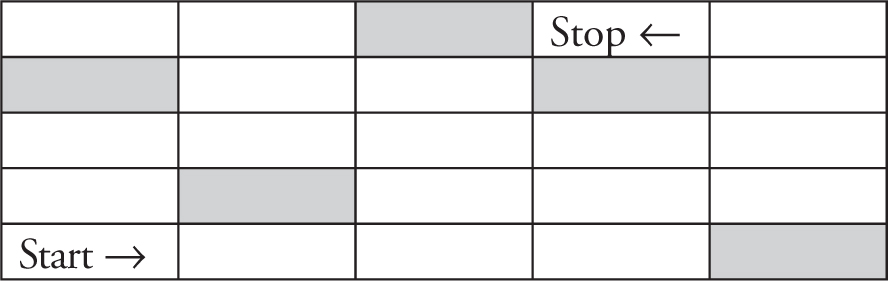
(A)

(B)
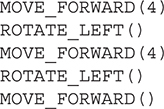
(C)

(D)

Questions 58—62 are related to this passage and chart.
There is an app to help farmers know when fruit is ready to harvest. You are planning to use this and modify it to create a new app to help grocery shoppers know how ripe fruit in the grocery store is. You also plan to let consumers enter any food allergies into the app.
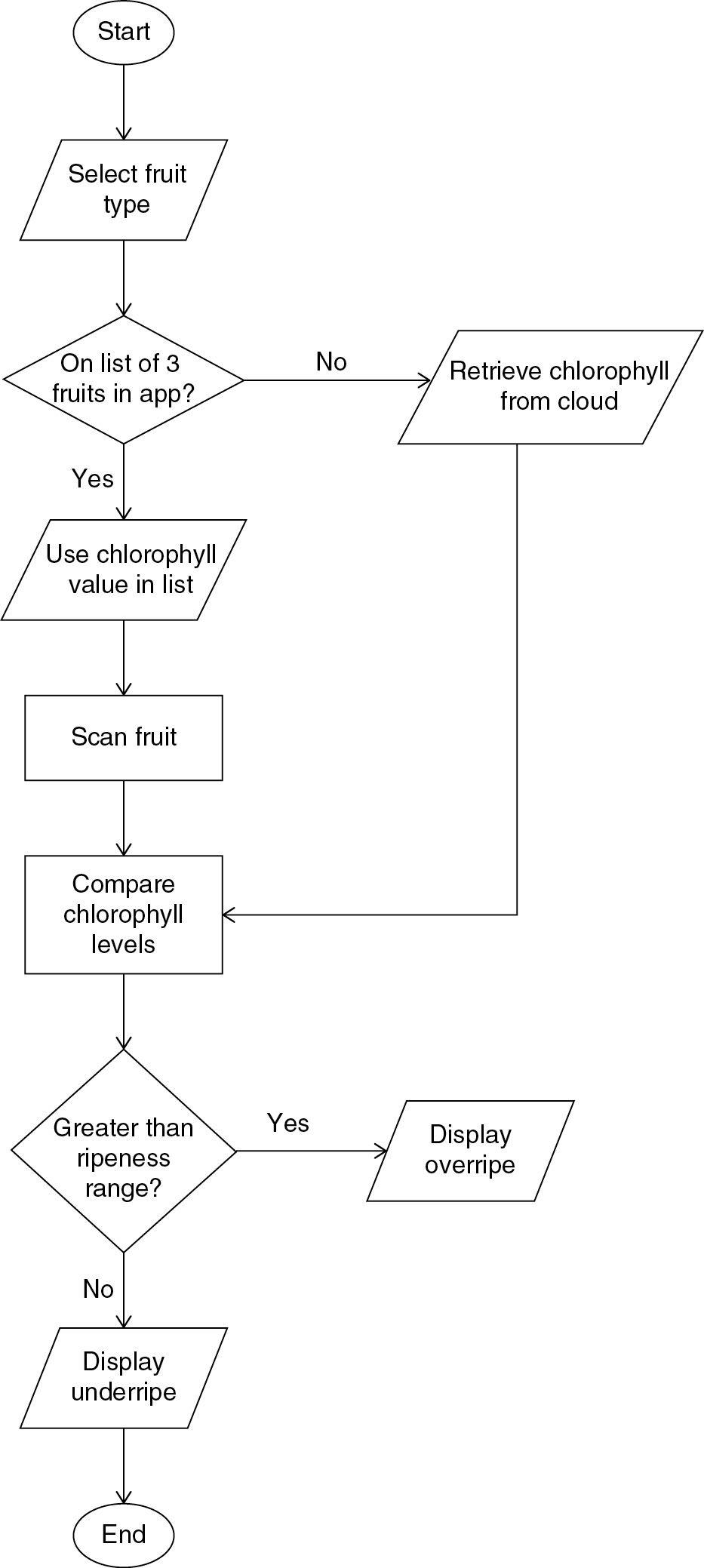
58. What input data is most likely to be needed for the app to work?
(A) Chlorophyll levels of fruit
(B) Image of fruit ripeness levels based on color
(C) Date of harvesting and average number of days to get to store shelf
(D) Scheduled delivery dates of fruit at local grocery stores
59. Which of the following is the most likely potential impact on the economy due to widespread use of the app?
(A) People are less likely to eat overripe fruit, losing the health benefits and incurring higher medical costs.
(B) More food will go to waste if people do not purchase it based on the app results.
(C) As information spreads about which grocery chain has the freshest fruit, other chains will suffer as people move their shopping to the stores with fresher fruit. People could lose their jobs as a result.
(D) Medical costs will go down as people are eating more fruit.
60. Which of the following is the most likely potential benefit of the app?
(A) Less likelihood of people squeezing fruit in the store to test its ripeness and potentially bruising it
(B) Fewer germs left on fruit in the stores from people handling it
(C) Fruit lasting longer in homes and more likely to be eaten, increasing people’s general healthiness
(D) Less money wasted with fruit that quickly goes bad
61. What is the most likely storage concern of the app?
(A) If fruit comparison data is stored in the cloud, you must have a strong enough signal to connect to the Internet for the app to work.
(B) There are so many different types of fruit, the app cannot store them all.
(C) Maintaining a record of the stores with the freshest fruits will take a lot of storage space, slowing down the app.
(D) Having to store data in the cloud and retrieving fruit ripeness values stored in the cloud will make the app too slow for most consumers.
62. What process does the app need to perform?
(A) Measure the size of the piece of fruit
(B) Record grocery store name and date
(C) Identify the fruit for correct comparisons
(D) Compare chlorophyll levels in the piece of fruit to a value representing chlorophyll levels in an average ripe piece of that fruit
63. Cloud-based data storage is best when what conditions are true of those working with the data? Select two answers.
(A) They are in a secured location.
(B) They are in separate locations.
(C) They are dealing with sensitive data.
(D) They have limited storage at their location.
64. Computers have enabled new innovations in a variety of industries. In the entertainment business, it has become much easier to purchase and share new music. What concern has been raised as a result? Select two answers.
(A) People are modifying other people’s content and claiming the Creative Commons licensing allows it.
(B) People are being discovered for their music because others are posting it to music-sharing sites.
(C) People are sharing content without the author/owner’s permission.
(D) Artists are adding their music to streaming services with Creative Commons licensing, bypassing record companies.
65. An organization collects massive amounts of data, more than they can currently process. What options should they consider using to be able to process their data to gain insights? Select two answers.
(A) Centralized computing system
(B) Distributed computing system
(C) Parallel computing system
(D) Sequential computing system
66. Which two protocols are responsible for breaking the data into packets and putting it back together at the destination? Select two answers.
(A) TCP
(B) HTTP
(C) FTP
(D) UDP
67. Why should public key encryption be used? Select two answers.
(A) It is shorter than other ciphers.
(B) It cannot be broken with brute force techniques.
(C) It uses an asymmetric key, making it harder to decrypt.
(D) It uses a symmetric key, making it harder to decrypt.
68. Which of the following can be stored in a bit? Select two answers.
(A) The result of a number MOD 2
(B) A Boolean variable
(C) A variable that could hold a range of positive values
(D) A computer that can be on, off, or in “sleep” mode
69. A company is trying to separate information it has into data and metadata. Which of the following would be considered metadata about documents? Select two answers.
(A) Author of document
(B) File size
(C) Internal page number
(D) Table of Contents
70. What is important to remember when converting a music file from analog data to digital data? Select two answers.
(A) Analog data is a set of continuous values.
(B) Copies of analog data files are more precise.
(C) A higher sampling rate will result in a more accurate digital version.
(D) The samples are compressed to create a smaller digital file.
STOP. End of Exam.
![]() Answers and Explanations
Answers and Explanations
If further review is needed, the Big Idea where information can be found about the question is included at the end of each answer’s explanation.
1. A—The huge lottery winnings added to your previous balance were more than the largest integer the bank account could accommodate, so an overflow error occurred. Big Idea 2: Data
2. B—Real numbers (e.g., numbers with fractions) are stored imprecisely in the computer’s memory and can cause rounding errors. This is why they should not be used for monetary transactions. The clerk owes you a nickel. Big Idea 2: Data
3. B—Take the binary number and create a table of the powers of 2, starting with 20 in the right-most position. For every column there is a 1 in the binary number, add the corresponding value of 2x. Big Idea 2: Data
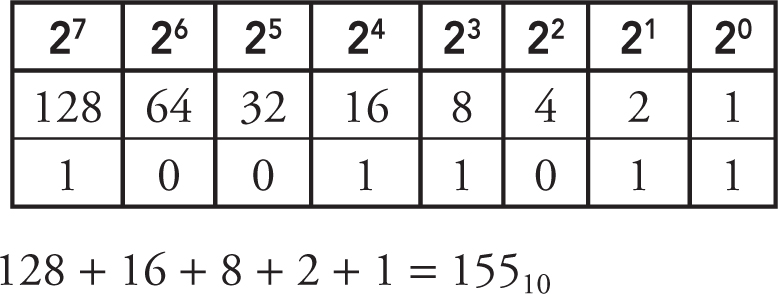
4. C—You need to convert the number for each color from binary to decimal:
01010000 for red, 11001000 for green, 01111000 for blue.
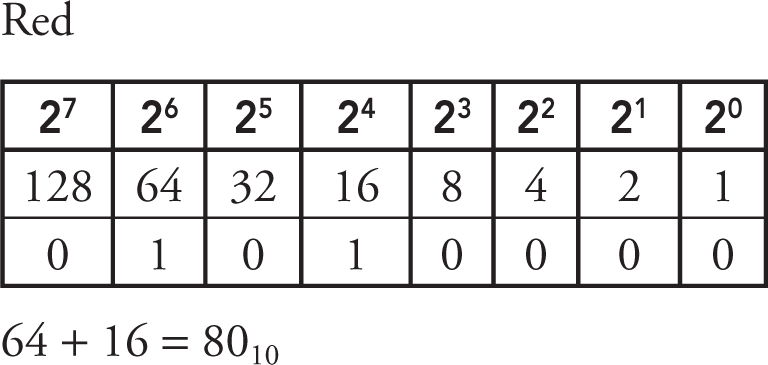
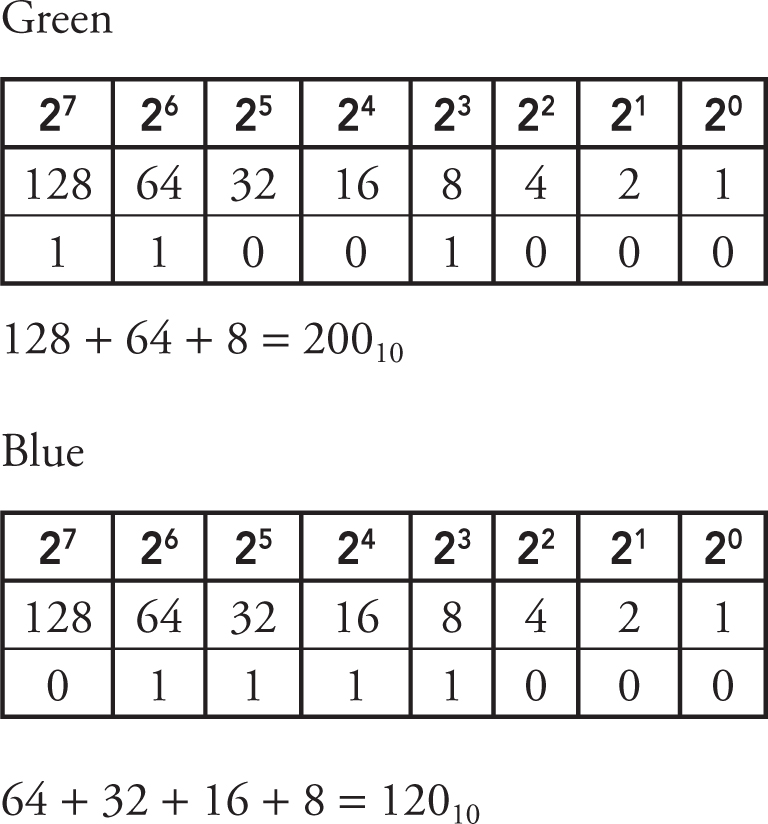
The result is (80, 200, 120), which is option C. Big Idea 2: Data
5. B—Multifactor authentication uses two methods to verify someone is who they say they are. Often a pass code or token is sent via text to the phone number or e-mail linked with the account. The code must be typed in by the customer to gain access to the account. Big Idea 5: Impact of Computing
6. C—Using well-named procedures and variable names makes code more readable and understandable. The original program requirements would not be useful, as it may not have been updated as the program was modified. Similarly, a video may help to explain the original programmer’s thought process, but it may be out-of-date and not very useful for understanding the code they wrote. Documenting the development process will not be useful to someone changing the code. Big Idea 3: Algorithms and Programming
7. B—If the song the user typed is in the playlist, it will be played and a Boolean variable marked as true for ownership of the song. Otherwise, after checking all songs in the playlist, if it is not already there, the song will be added to the playlist and then played. Big Idea 3: Algorithms and Programming
8. C—When calling the procedure, play, the value is passed to it using an argument. The value in the argument is then loaded into the parameter. It is a parameter when used internally in the procedure. Big Idea 3: Algorithms and Programming
9. A—Lower-level languages are written in code closer to machine language. These are more difficult to debug for most people because the code is less like our natural speaking language. Big Idea 3: Algorithms and Programming
10. A—A benefit of models and simulations is the ability to modify a variable and retest quickly. Running the test with the same values does not help the analysis. Running one test and then stopping is not an effective use of a simulation. Unless an error was identified, which it was not in this scenario, then rewriting the code will not determine if the glasses are effective to safely protect people’s eyes. Big Idea 3: Algorithms and Programming
11. D—If the car causes an accident in the simulation, that is not a test of the sensor itself. Ensuring the sensor can read multiple objects and that it does not give a false reading when there are no objects plus ensuring the boundary conditions around the 3 foot limit are all good conditions to test. Big Idea 3: Algorithms and Programming
12. B—The only time an AND condition is true is when both conditions are true. An OR condition is true when either or both conditions are true. Evaluating the conditions provided, only i and iii are true. Big Idea 3: Algorithms and Programming
13. C—The only time an AND condition is true is when A and B are both true. An OR condition is true when either or both conditions are true. Evaluating the conditions in the diagram will produce the results in answer C. Big Idea 3: Algorithms and Programming
14. D—Everything is data about the nest and the eagles using the nest except the number of frames the camera can record, which is data about the data, or metadata. Big Idea 2: Data
15. A—Only the lossless compression technique will allow the original uncompressed photo to be restored. Big Idea 2: Data
16. A—A project that is good for citizen scientists would be one where specialized equipment, such as a telescope or fish finder, would not be required and that can be based on facts versus personal opinion. Counting trees would be the best use in this example. Big Idea 5: Impact of Computing
17. B—Cleaning involves finding and either correcting or eliminating incomplete records. It also involves standardizing the data for the analysis to be performed. It could include filtering out some complete and correct data that is not needed for the planned analysis. Big Idea 2: Data
18. B—The survey results will show if students changed their mind in either direction or maintained their viewpoint about computer science if they felt the teacher communicated effectively and if they felt they gave their best effort. It will not show if students plan to major in computer science. Big Idea 2: Data
19. C—The data in the table shows that drivers in the 26—50 age bracket have the least number of accidents. The data cannot tell us when the drivers had an accident. Big Idea 2: Data
20. A—Smaller datasets may not have enough data to identify patterns or true trends. If a trend is noticed in a smaller dataset, processing larger datasets may not be necessary. The analysis of a large dataset will not identify metadata issues, nor determine when hardware purchases should be made. Big Idea 2: Data
21. B—The World Wide Web is an application that uses HTTP to share documents, videos, images, and other files among devices connected to the Internet. Big Idea 4: Computing Systems and Networks
22. A—The redundancy designed into the Internet means data can be sent via different paths to reach its destination. Big Idea 4: Computing Systems and Networks
23. A—The speedup for a parallel model is the sequential time/parallel time. In this case, it is 25 / 10 = 2.5. Big Idea 4: Computing Systems and Networks
24. B—Bandwidth measures the amount of data that can be transmitted in a specified amount of time. Therefore, knowing how much data needs to be downloaded on a regular basis is a key measurement, as people generally download far more than they upload. Big Idea 4: Computing Systems and Networks
25. C—Certificate authorities, or CAs, issue digital certificates to customers that confirm ownership of their encrypted keys with secure Internet communications. This enables us to have online shopping, among other secure online transactions. Big Idea 5: Impact of Computing
26. B—This is a keylogger file. Your typing keystrokes are recorded and then uploaded to a server where the keylogger is programmed to report. The data is then analyzed, searching for credit card numbers, passwords, or other personal and confidential information. Big Idea 5: Impact of Computing
27. B—The facial recognition software needs more examples from a wider population of faces as input to better “learn” to recognize and compare facial features. Big Idea 5: Impact of Computing
28. A—The file was compressed using a lossy algorithm. The lossy algorithm cannot restore the file to its original size. You get more compression resulting in a smaller file, but some of the data is lost and a full file restoration is not possible. Big Idea 2: Data
29. D—Packets are created at the sending end of the transmission and reassembled at the final destination. Big Idea 4: Computing Systems and Networks
30. C—TCP creates packets and passes control of them to IP, which routes them to their final destination. TCP then reassembles the packets to display. Big Idea 4: Computing Systems and Networks
31. C—Phishing attacks attempt to get users to type in personal information such as passwords or account information on websites that look just like the real organization’s website. Big Idea 5: Impact of Computing
32. C—Public key encryption models are the most secure. No key needs to be shared to encrypt or decrypt the file. The public key is used to encrypt, and the receiver’s private key is used to decrypt. Big Idea 5: Impact of Computing
33. D—One of many benefits is that all organizations can access the data, making it easier for new businesses to have and analyze data the established ones may have. Big Idea 5: Impact of Computing
34. B—This is the only option that will capture the smallest number in a list. Answers A and C are incorrect since the variable smallest is set to -1 and the list only has positive numbers. D has the variable smallest initially set to the largest number in the list and then tests to see if it is smaller than the numbers in the list, which will never be true. Big Idea 3: Algorithms and Programming
35. C—Booleans can only be true or false, and C is the only option that is a comparison that can evaluate to true or false. Answers A and B assign values to variables and option D would produce an error. Big Idea 3: Algorithms and Programming
36. A—The flow of procedures called indicates a game is being played due to the descriptive names they were assigned. The procedure names and parameters are all correct. Big Idea 3: Algorithms and Programming
37. D—You cannot have an ELSE statement without an IF statement. Big Idea 3: Algorithms and Programming
38. B—The first algorithm sorts by name but then uses a binary search using phone number. This may not return correct results. Therefore, option II using a linear search on a contact list sorted by area code will return the correct results and is more effective. Big Idea 3: Algorithms and Programming
39. C—A heuristic is finding a good approximate solution when the actual solution would take too long or too many resources. A computer checking all possible chess moves drastically slows the processing down, so a heuristic solution will improve the speed and the overall game experience for the player. Big Idea 3: Algorithms and Programming
40. C—This bias occurred in preparing the data by selecting active-loan status as an attribute to consider. Big Idea 5: Impact of Computing
41. C—Since place is 5, the length of the snacks list, snacks[place], refers to the element at the 5th position of the list, which is “grapes.” List elements can be accessed using a constant, such as list[2], or a variable as in this example, list[place]. Big Idea 3: Algorithms and Programming
42. A—Block 1 produces correct results based on the temperature. Block 2 counts all temperatures ≤ 80 to be a perfectDay, rather than separating them by temperature. The condition in the IF statement is set up in the wrong order. Big Idea 3: Algorithms and Programming
43. A—Algorithms with polynomial (cubed, squared, linear) efficiency will run small and large datasets in a reasonable amount of time. Big Idea 3: Algorithms and Programming
44. D—A causes any grade higher than 59 to be assigned the letter grade D. B uses greater than rather than less than in the condition to evaluate. C will be off by one. D is correct. Big Idea 3: Algorithms and Programming
45. D—Only option D ends up in the correct block facing in the correct direction. Remember that ROTATE commands do not move the robot forward a block. They only change the direction in the current block the robot is in. Big Idea 3: Algorithms and Programming
46. B—An API (Application Programming Interface) connects software modules, making working programs such as Google Maps available for use in other programs. Big Idea 3: Algorithms and Programming
47. B—The procedure calcTemp is called with 50 as the argument. 50 is then stored in the parameter temp. Follow the order of operations in the formula to determine the answer the code will return. Big Idea 3: Algorithms and Programming
48. B—MOD calculations provide the remainder when the two numbers are divided. x is assigned the value 10 in the first line of code. In the second line, 4 is added to the current value of x, which is 10, and the new value of 14 is stored back in x. Then the line x MOD 3 takes the current value of x, divides by 3, and returns ONLY the remainder. 14 divided by 3 is 4 with a remainder of 2. The answer to 14 MOD 3 is 2. Big Idea 3: Algorithms and Programming
49. A—An OR condition only needs one of the conditions to be true for the overall condition to be true. Since 10 is less than 15, the value of x will be displayed. Big Idea 3: Algorithms and Programming
50. B—Block 1 calculates the total of the list indices. Block 2 calculates the sum of the elements of the list. Watch for questions like these on the exam. Big Idea 3: Algorithms and Programming
51. B—Code inside the loop will never run because 10 > 5 before the loop runs the first time. Big Idea 3: Algorithms and Programming
52. D—Each time the value in the list is not “banana,” the word “banana” is appended to the end of the list. Big Idea 3: Algorithms and Programming
53. A—The value at snacks[j] is replaced by number [j + 4], which is 1 + 4 or 5, then 2 + 4 or 6, then 3 + 4 or 7, then 4 + 4 or 8 as j iterates through the values 1—4. Big Idea 3: Algorithms and Programming
54. D—The procedure concatenates or glues the strings together. Big Idea 3: Algorithms and Programming
55. A—None of the other options will produce better code or even code that works. The iterative development process improves the code in each iteration based on testing and feedback. This process helps ensure working code is produced that meets the requirements. Big Idea 1: Creative Development
56. D—Rerunning the code as it is does not aid in the debugging process. The other three options will provide information to help isolate where the error occurs. Watch for questions that include NOT. Big Idea 1: Creative Development
57. A—This option is correct. The arrow is in the correct square and facing in the correct direction. The ROTATE commands only change the direction in the current block. They do NOT move the robot forward. Big Idea 3: Algorithms and Programming
58. A—As shown in the flowchart, the app uses the chlorophyll levels from the plant to determine ripeness. This level is needed as input. The image of ripe fruit will not be useful for comparing chlorophyll levels. The date of harvesting and days to get to the store shelf would be difficult to track for each fruit shipment, and it’s unlikely the app could access such data. The delivery dates at local stores are nice to know from a personal level but does not provide data this app needs to function.
59. B—More food could go to waste if people using the app do not purchase available fruit because they might not eat it in time. It’s also possible that once people get it home, they may throw away fruit that is still good to eat. People are already not going to eat fruit that has gone bad, so option A is not significant. Based on deliveries, the grocery store with the freshest fruit is likely to change daily, so this is a minimal impact, if any. There are many medical conditions that eating fruit will not help, so it is not likely there will be a huge impact from option D.
60. C—People will hopefully stop handling the fruit and inadvertently bruising it and leaving germs, but that’s not likely since habits are hard to change. Less money may be wasted, but the most likely benefit is C. People can purchase fruit that is not quite ripe and eat it over several days as it ripens.
61. B—There are many types of fruit, and smart devices have a limited amount of space for storing data. You can see in the chart that the app only stores 3 fruit values that the user can chose. The remaining fruit comparison data is retrieved from the cloud as needed. Users will need Internet access if they want to compare a fruit other that the 3 stored locally on the device, but that is not a storage issue. The flowchart does not show the app recording stores with the freshest fruit, so that is not a concern for the app. Option D is possible, but B is the most likely storage issue.
62. D—The app will need to take the chlorophyll level measurement as input, and the processing will involve comparing the measured level to the average chlorophyll level for a ripe piece of fruit. A is the measurement of the size, not the amount of chlorophyll. The grocery store name and date is not relevant to the app’s processing. The user will select the fruit as an input value that is used in the process, but that is not the process.
63. B, D—Cloud-based storage can be accessed from any location with an Internet connection and is a good solution for storage when local storage options are limited. Sensitive data should not be stored in the cloud. Big Idea 2: Data
64. A, C—Some people ignore the Creative Commons licensing guidelines and either take other people’s intellectual property and modify it without permission or share it on other sites or with friends without the owner’s permission. Big Idea 5: Impact of Computing
65. B, C—Both parallel and distributed computing systems can speed up the processing of the data the company collects by spreading out the processing among multiple devices and then combining the results. Big Idea 4: Computing Systems and Networks
66. A, D—TCP and UDP make the packets and put them back together. UDP does not send an acknowledgment while TCP does. Big Idea 4: Computing Systems and Networks
67. B, C—Public key encryption creates such long keys that brute force techniques are ineffective. The keys are asymmetric, meaning different keys are used to encrypt and decrypt the data. Big Idea 5: Impact of Computing
68. A, B—A bit can only hold two possible values, 0 and 1. Therefore, any data it holds can only be represented by these two values. Any number MOD 2 will produce 0 or 1, and Boolean values are either true or false. Big Idea 2: Data
69. A, B—The author of a document and the file size for the document are both pieces of metadata. They are about the document, rather than part of the document itself. Page numbers and the Table of Contents are content within the document, not metadata. Big Idea 2: Data
70. A, C—Analog data is a series of values that are connected in a smooth data line. The sampling rate determines how closely the digital version matches the analog version. A higher sampling rate will create more instances of data from the analog version to include in the digital version, thereby creating a version that is a closer match to the original analog one. Big Idea 2: Data
Analyzing Your Performance on Practice Exam 1
The exercise below will help you quickly and easily identify the chapters in Step 4 that you most need to review for the AP Computer Science Principles multiple-choice exam. Revise your study plan so that you prioritize the chapters with which you had the most difficulty.
Look at your answer sheet and mark all the questions you missed. Then shade in or mark an X in the boxes below that correspond to the question numbers that you missed. Review the concepts where you missed the most questions. Keep in mind the number of questions to expect from each section, spending more time on those that will appear the most. See Chapter 1 on “What You Need to Know About the AP Computer Science Principles Assessment” for those percentages.
Big Idea 1: Creative Development

Big Idea 2: Data
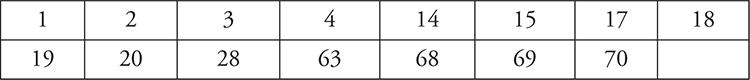
Big Idea 3: Algorithms and Programming
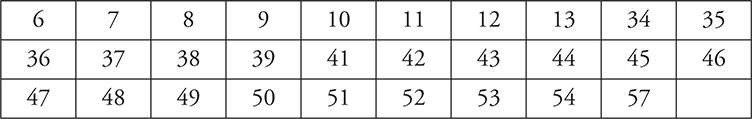
Big Idea 4: Computing Systems and Networks
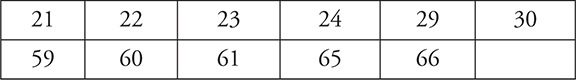
Big Idea 5: Impact of Computing