Total Information Risk Management (2014)
PART 2 Total Information Risk Management Process
CHAPTER 8 TIRM Process Stage C
Information Risk Treatment
Abstract
This chapter is a step-by-step guide for implementing the information risk treatment stage of the TIRM process. Information risk treatment first identifies and ranks the root causes of the information risks, for which potential information risk treatments are identified. To evaluate and select the right information risk treatment options, the costs, benefits, and expected implementation risks have to estimated. The benefits are, therefore, calculated with the help of the risk figures from stage B. Communicating effectively to the most important stakeholders increases their support during implementation. Information risk treatment plans are developed then implemented, and the effectiveness of the information risk treatments are verified at the end of stage C. Finally, lessons learned are summarized to improve the next cycle of the TIRM process.
Keywords
Identification of Information Risk Causes; Information Risk Treatment Identification; Determining Costs and Benefits of Information Risk Treatment; Communication to Stakeholders; Implementation of Information Risk Treatments; Verification of the Effectiveness of Information Risk Treatments
What you will learn in this chapter
![]() How to identify causes of information risks
How to identify causes of information risks
![]() How to find appropriate treatments for information risk
How to find appropriate treatments for information risk
![]() How to determine the costs, benefits, and risks of information risk treatments
How to determine the costs, benefits, and risks of information risk treatments
![]() How to evaluate, select, and communicate information risk treatments to stakeholders
How to evaluate, select, and communicate information risk treatments to stakeholders
![]() How to implement information risk treatments and verify their effectiveness
How to implement information risk treatments and verify their effectiveness
Introduction
Motivation and goals for stage C
Assessing information risks does not create much benefit if those assessments are not used later to mitigate the information risks. Information risk treatment is therefore the action phase; here, changes to working practices and procedures are made, enabling an organization to be better able to control information risks. These changes can be made in business processes, hardware, software, policies, and organizational structure. The changes can be either incremental or disruptive. ISO 31000 describes risk treatment as “selecting one or more options for modifying risks, and implementing those options” (ISO, 2009, p. 18).
Overview of stage C
Information risk treatment is carried out by following eight steps (Figure 8.1). First, the causes of information quality problems that lead to the major information risks are analyzed in step C1. Based on the actual causes of information risks, appropriate information risk treatments are identified in step C2, for which the costs, benefits, and implementation risks are estimated in step C3. The potential information risk treatments are evaluated and the best treatments are selected in step C4. The list of information risks and selected information risk treatment are then communicated to all key stakeholders in step C5 to obtain their feedback and buy-in for the implementation stage. In step C6, information risk treatment plans are developed, which are implemented in step C7. Finally, the effectiveness of the information risk treatments is verified in step C8. Information risk treatment is a cycle that only ends when an information risk becomes tolerable or reaches a level that is satisfying.
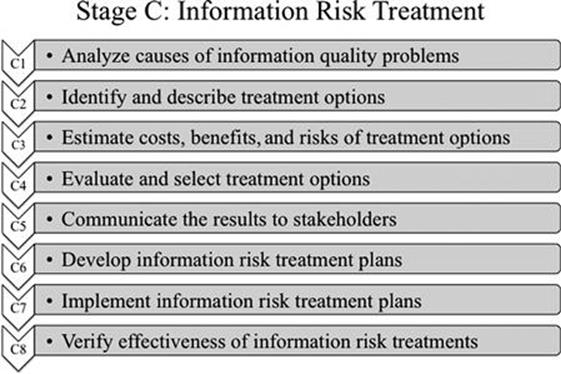
FIGURE 8.1 Eight steps to treating information risk.
Three types of workshops can be organized for stage C. The first workshop is information risk treatment identification, the purpose of which is to analyze the causes of information quality problems in step C1 and identify and analyze potential information risk treatments in step C2. This is usually a one-day workshop, but it could also take much longer if the scope of the TIRM process is particularly wide-ranging. It should involve the process manager, process facilitator, one or two business process representatives, and one or two IT representatives.
The second workshop is information risk treatment selection, the purpose of which is to identify the costs, benefits, and risks of each information treatment option in step C3; participants in this workshop should be the same people as in the previous workshop with the addition of the process sponsor. The second workshop also normally takes one day, but, again, it depends on the scope of the TIRM process. An evaluation, of which treatment options should be recommended to the decision makers in the organization, should be undertaken as part of this workshop; the decision makers will have the final say as to which information risk treatment options are to be implemented.
The third workshop is for step C6 and its purpose is information risk treatment plan development, which, as the name says, is to develop information risk treatment plans for the information risk treatments that were selected. The duration of the workshop and its participants should mirror those of the first workshop.
Output of this stage
The outputs of stage C are:
![]() An analysis of the causes of each information quality problem.
An analysis of the causes of each information quality problem.
![]() A preselection of appropriate information risk treatment options.
A preselection of appropriate information risk treatment options.
![]() A cost, benefit, and risk analysis of the treatment options.
A cost, benefit, and risk analysis of the treatment options.
![]() A ranked list and evaluation of information risk treatment options.
A ranked list and evaluation of information risk treatment options.
![]() An implementation plan for each selected information risk treatment option.
An implementation plan for each selected information risk treatment option.
![]() An implementation report for each selected information risk treatment option.
An implementation report for each selected information risk treatment option.
Step C1: Analyze causes of information quality problems
The information risk assessment stage has created a ranked list of information risks that require treatment. In this step (Figure 8.2), the causes of the information quality problems that lead to these risks are analyzed. In many information quality methodologies, this step is also called root cause analysis. David Loshin describes it as “an iterative process of analyzing a problem to determine the actual cause” (Loshin, 2001, p. 382).
FIGURE 8.2 Step C1 in context.
Information quality problems are caused by a variety of reasons. The causes can be technological, organizational, or human. An example of a technological cause is that software is poorly implemented or not available. An organizational cause can be that a business process to update customer data is not clearly defined. An example of a human cause could be that employees are not sufficiently motivated to collect data of high quality or they make errors during data entry. So, you can classify the causes and categorize them on the basis of whether they are technological, organizational, or human.
In this step, the causes of information quality problems are identified and then ranked on the basis of their importance (Figure 8.3).
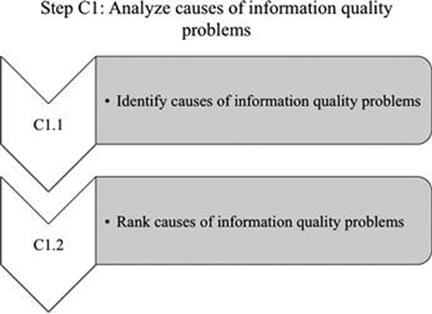
FIGURE 8.3 Activities in step C1.
C1.1 Identify causes of information quality problems
First, the causes of information quality problems need to be identified. This can be done in a number of different ways.
A simple method suggested by Danette McGilvray is to ask five “why” questions to get to the source of the problem (McGilvray, 2008). The questions do not have to actually start with the word “why,” but each question should lead closer to the actual cause of the information quality problem. For example:
![]() Why is the customer data incorrect? Because it is out of date.
Why is the customer data incorrect? Because it is out of date.
![]() So, why is the customer data out of date? Because nobody updates the customer data.
So, why is the customer data out of date? Because nobody updates the customer data.
![]() So, why does nobody update the customer data? Because there are no formalized processes and requirements to update the customer data.
So, why does nobody update the customer data? Because there are no formalized processes and requirements to update the customer data.
![]() So, why are there no formalized processes and requirements? Because there is no entity in the organization responsible for governing data.
So, why are there no formalized processes and requirements? Because there is no entity in the organization responsible for governing data.
Information quality problems are caused at some point during the information life cycle. The information life cycle can be divided into a number of different stages—for example, when information is created and collected, processed and stored, accessed and used, maintained and updated, and disposed of. It is reasonable to identify causes of information quality problems along the information life cycle. Using the information flow maps created in substep A5.2 as a basis does this.
Another method that is used in information quality (IQ) management and risk management to model the causes of problems is the Fishbone diagram (McGilvray, 2008; see also Chapter 11), which “is structured by separating causes into major categories (represented by the lines of the fish backbone) with branches and sub-branches that describe more specific causes in those categories” (ISO, 2009, p. 57). The position of the cause in the information life cycle and the technology, organization, and people (TOP) classification can be used as the categories in the fishbone diagram. An example is shown in Figure 8.4.
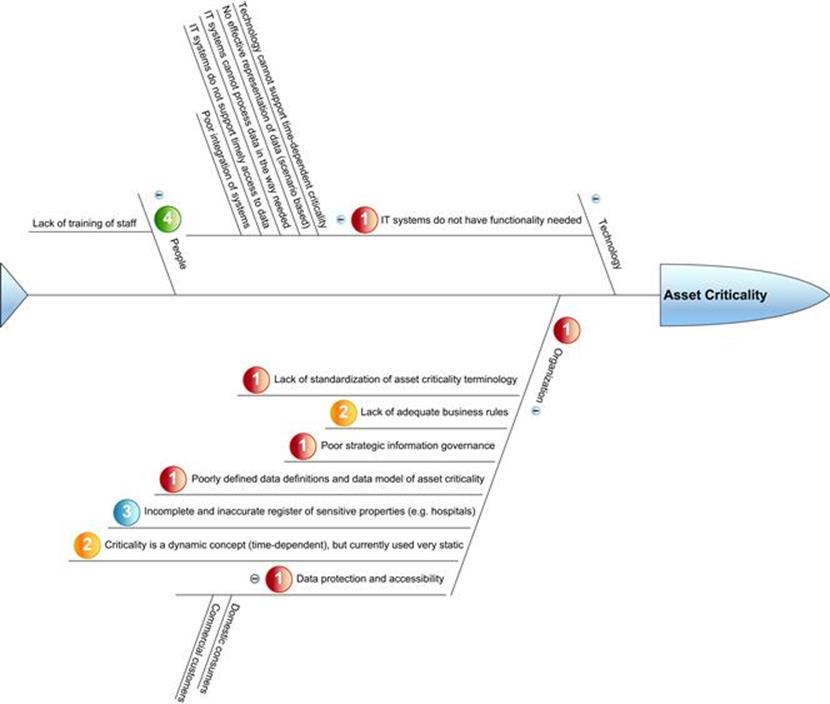
FIGURE 8.4 Illustration of a fishbone diagram for information quality root-cause analysis.
C1.2 Rank causes of information quality problems
The identified IQ causes should be prioritized based on the severity of the resulting information risks and the degree to which each cause can be modified. As several IQ problems can have the same causes, one information risk treatment might mitigate a number of different information risks. A ranked list should be created that will help prioritize information risk treatment options.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
In stage B of the TIRM process, four information quality problems were identified that cause information risks in the three business processes. These are in the scope of the TIRM process initiative at the call center. As a reminder, the ranked table of information risks is shown in Table 8.1.
Table 8.1
Ranked List of Information Risks at Call Center
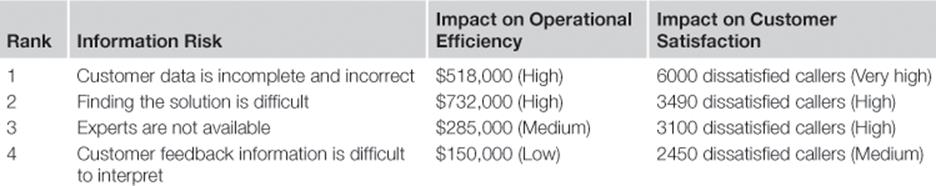
The TIRM process manager wants to now identify the causes of each of the information quality problems. Together with the TIRM process facilitator and the IT system and database representatives, he first investigates where, in the information processing chain, the causes of the information quality problem could be generated. Looking at the information flow map created in substep A.5.2 does this (Figure 8.5), and finds the spots along the information life cycle where the causes might lie. We will illustrate it for the information quality problem that customer data is incomplete and incorrect. One example for an issue at the beginning of the information life cycle is that call center agents input data fields with default or invalid values, make spelling errors, or leave fields empty during information creation. During the information maintenance life-cycle stage, data decays over time when it is not maintained properly by the call center agents and the client company.
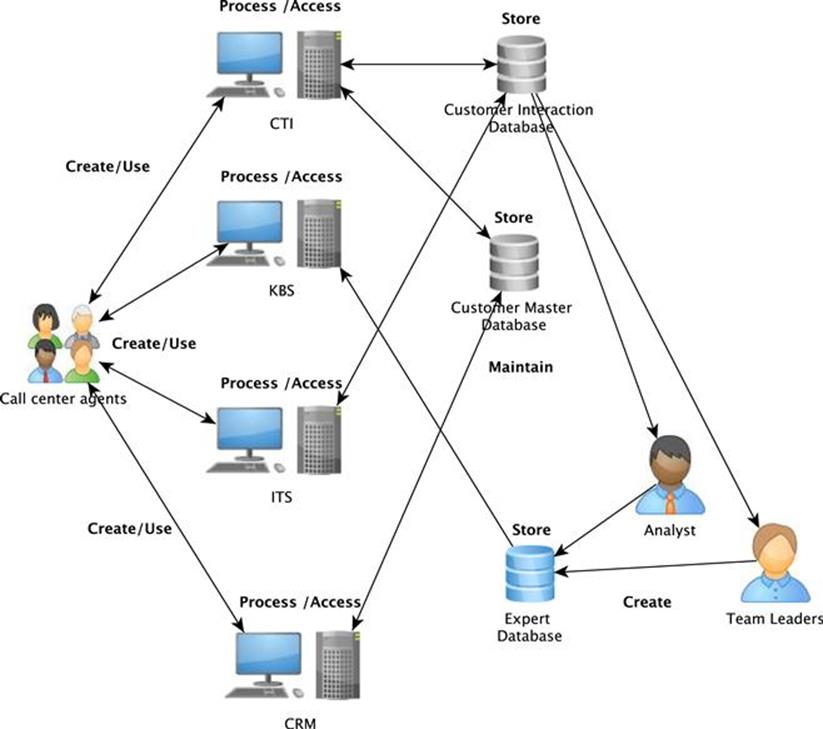
FIGURE 8.5 Example of an information flow diagram.
As a next step, for the information quality problem that customer data is incomplete and incorrect, the team identifies the root causes of the issues that appear during the information life cycle and classifies them into technological, organizational, or people factors using a Fishbone diagram, as shown in Figure 8.6.
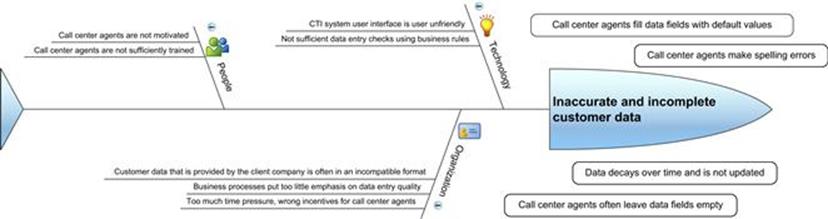
FIGURE 8.6 Illustration of a fishbone diagram used for IQ root-cause analysis at the call center.
Finally, the TIRM team ranks the root causes in a table based on how important the causes are for the mitigation of the information risks (Table 8.2).
Step C2: Identify and describe treatment options
After having the causes of the information quality problems identified, the next step (Figure 8.7) is to find possible actions that can be taken to mitigate the information risks. This can be done in two substeps, as shown in Figure 8.8.
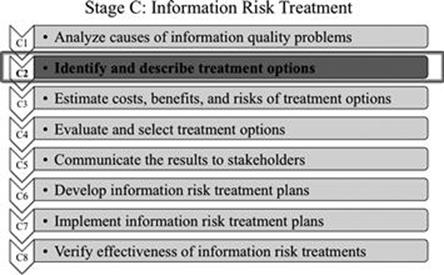
FIGURE 8.7 Step C2 in context.
FIGURE 8.8 Activities in step C2.
C2.1 Identify information risk treatment options
For each information risk selected in step B9, potential information risk treatments should be identified, with due consideration being given to the causes of the underlying information quality problem. Information risk treatments can often result in projects for information quality improvement. Projects that do not improve information quality only deal with the symptoms and not with the causes of the problems. However, treatment of symptoms should be considered if the treatment of the root causes is not feasible or too costly.
So, how can appropriate information risk treatments be identified? Examining how the causes and/or consequences of the information quality problems can be modified to decrease the information risk can do this. A straightforward way to brainstorm for information quality improvement is, therefore, to go through each cause of an information quality problem that leads to the risk, and look for options as to how the causes can be delimited. Depending on whether a cause of an information quality problem lies in technology, organization, or human behavior, the appropriate information risk treatment will often be found to be in the same category as the cause. Moreover, as explained in step C1, causes are located at distinct points along the information life cycle, and often, suitable information risk treatments can be found at a similar point of the information life cycle. But, you should also look for solutions that are outside the box, which means that they can be in a different information life cycle or in a different category. Redesigning the business processes could, for example, potentially solve a problem that arises through people behavior, therefore a human cause would be treated with an organizational change.
Table 8.3 offers a template that can be used to brainstorm for appropriate information risk treatments using the information life cycle and the TOP categorization. The example shown in the table is taken from a case study with a manufacturing company.
Table 8.2
Ranked List of Root Causes for the IQ Problem That Customer Data Is Incomplete and Incorrect
|
Rank |
Short Description |
Category |
|
1 |
Too much time pressure, wrong incentives for call center agents |
Organization |
|
2 |
Business processes put too little emphasis on data entry quality |
Organization |
|
3 |
CTI system user interface is user unfriendly |
Technology |
|
4 |
Insufficient data entry checks using business rules |
Technology |
|
5 |
Call center agents are not motivated |
People |
|
6 |
Call center agents are not sufficiently trained |
People |
|
7 |
Customer data that is provided by the client company is often in an incompatible format |
Organization/Technology |
|
8 |
Team leaders do not emphasize importance of data |
Organization |
Table 8.3
Example: Identification of Potential Information Risk Treatment Options
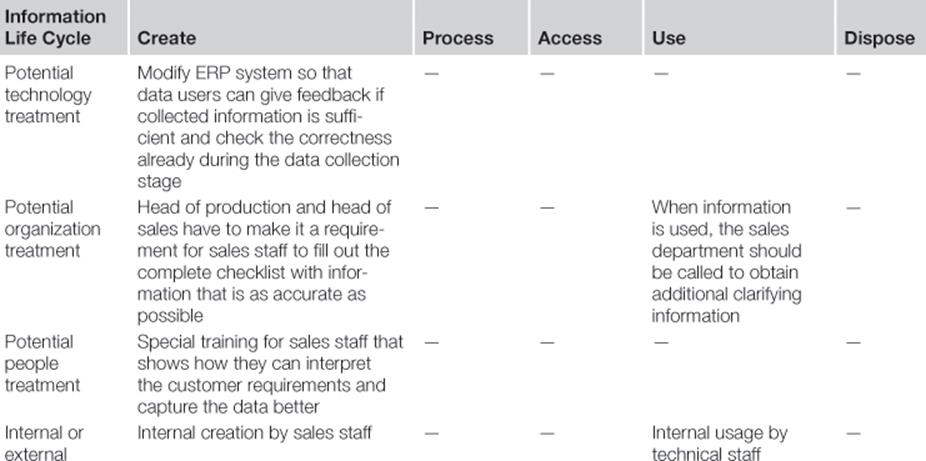
For each information quality problem, a list of information risk treatment options is iteratively generated. If there are several information risk treatment options for one information risk treatment, it should be examined if they can be implemented in parallel or if they are exclusive alternatives that cannot be implemented at the same time.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
For each root cause, potential information risk treatment options are identified at the call center by the TIRM team, which are shown in Table 8.4.
Table 8.4
Potential Information Risk Treatments
|
Root Cause |
Category |
Potential Information Risk Treatment |
|
Too much time pressure, wrong incentives for call center agents |
Organization |
Change incentive system for call center agents and team leaders so that performance measurement also incorporates the quality of the data entered and updated |
|
Business processes put too little emphasis on data entry quality |
Organization |
Formalize data entry and update requirements in business processes |
|
CTI system user interface is user unfriendly |
Technology |
Optimize user friendliness of CTI system for simplified data entry |
|
Not sufficient data entry checks using business rules |
Technology |
Create business rules that are checked during and after data entry and update |
|
Call center agents are not motivated |
People |
Change incentive system for call center agents and team leaders so that performance measurement also incorporates the quality of the data entered and updated |
|
Call center agents are not sufficiently trained |
People |
Organize data entry and update training for call center agents |
|
Customer data that is provided by the client company is often in an incompatible format |
Organization/technology |
Work with companies to improve the compatibility of the systems to handle data that has different formats |
|
Team leaders do not emphasize importance of data |
Organization |
Change incentive system for call center agents and team leaders so that performance measurement also incorporates the quality of the data entered and updated |
C2.2 Describe information risk treatment options
Each information risk treatment option identified in substep C2.1 should be described further:
![]() What is the title of the information risk treatment?
What is the title of the information risk treatment?
![]() What, exactly, needs to be done?
What, exactly, needs to be done?
![]() How are information risks expected to be modified by the information risk treatment?
How are information risks expected to be modified by the information risk treatment?
![]() With which other information risk treatments would this treatment be compatible or not compatible?
With which other information risk treatments would this treatment be compatible or not compatible?
![]() Which technological, organizational, and/or human-related changes would be required?
Which technological, organizational, and/or human-related changes would be required?
![]() What would be the timescale of the change?
What would be the timescale of the change?
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
The TIRM team further describes each of the identified information risk treatment options per the following example description.
Title of Information Risk Treatment: Change the Incentive System for Call Center Agents and Team Leaders
Change the incentive system for call center agents and team leaders so that performance measurement also incorporates the quality of the data entered and updated; this proposed change requires:
![]() Preapproval of the board of directors
Preapproval of the board of directors
![]() Redesign of the incentive system to include data entry and update quality as factors
Redesign of the incentive system to include data entry and update quality as factors
![]() Development of appropriate measurement metrics
Development of appropriate measurement metrics
![]() Drafting of required policy, business process, and technology changes
Drafting of required policy, business process, and technology changes
![]() Final approval by the board of directors
Final approval by the board of directors
![]() Implementation of the new incentive system
Implementation of the new incentive system
Two information quality problems will be mitigated by the information risk treatment, namely, the customer data is incomplete and incorrect and that finding the solution is difficult. This is because both information quality problems are directly related to the root causes that are modified by the information risk treatment:
1. Too much time pressure, inappropriate incentives for call center agents
2. Call center agents are not motivated
3. Team leaders do not emphasize the importance of data
The TIRM sponsor decides that the changes preferably should be implemented within one calendar year after the preapproval of the board of directors.
Step C3: Estimate costs, benefits, and risks of treatment options
The ISO 31000 standard for risk management states that “selecting the most appropriate risk treatment option involves balancing the costs and efforts of implementation against the benefits derived” (ISO, 2009, p. 19). In this step (Figure 8.9), expected costs and benefits of information risk treatments are identified (Figure 8.10). There are always things that may not proceed as expected during the implementation of an information risk treatment. These implementation risks should be considered during the evaluation of the information risk treatments.
FIGURE 8.9 Step C3 in context.
FIGURE 8.10 Activities in step C3.
C3.1 Estimate costs of information risk treatment options
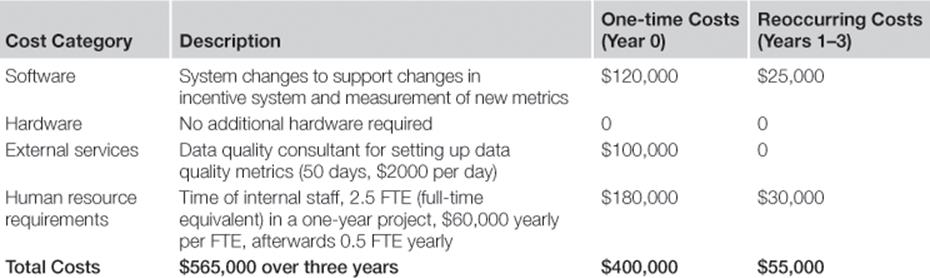
First, expected costs for the options need to be estimated, which could include, for example, personnel costs, training costs, hardware costs, software costs, and external service provider costs. The costs should be split up into one-time costs and recurring costs.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
The management team at the call center decides to look at a three-year time horizon when evaluating information risk treatment investments. The TIRM team determines the costs for each information risk treatment. An example of the information risk treatment to change the incentive system for call center agents and team leaders is shown in Table 8.5.
Table 8.5
Costs for Information Risk Treatment to Change the Incentive System for Call Center Agents and Team Leaders
C3.2 estimate benefits of information risk treatment options
Second, the benefits of each information risk treatment option are estimated. Before this calculation can be done, the workshop participants have to estimate the new expected likelihood of the occurrence of information quality problems, after the information risk treatment has been successfully implemented, for each task that is affected by the risk treatment. Then, to determine the expected benefits of a potential information risk treatment, the level of information risk is compared before and after the treatment option has been implemented.
However, the benefits of an information risk treatment might only become visible gradually, which should be explicitly considered in the modeling. For instance, in the first two years after treatment implementation, there are no benefits yet; in years two to five, only 50% of the benefits can be achieved; and from year five onward, 100% of the benefits are achieved. Moreover, to improve the reliability of the results, expected costs and benefits can be estimated in three scenarios—that is, a worst-case, average, and best-case scenario. An examination should also be undertaken of which other benefits that go beyond the scope of the process might accrue from the information risk treatment option.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
The TIRM team at the call center estimated the benefits for each information risk treatment. For instance, it is estimated that the information risk treatment to change the incentive system for call center agents and team leaders can reduce the likelihood of the occurrence of the information quality problems that customer data is incomplete and incorrect by 40% and that finding the solution is difficult by 35%. Half of the benefits, so it is expected, will start from the second year and will be fully realized in the third year. The benefits over three years are shown in Table 8.6.
Table 8.6
Benefits of Information Risk Treatment to Change the Incentive System for Call Center Agents and Team Leaders

C3.3 Identify implementation risks for each information risk treatment option
Third, there might be implementation risks associated with the risk treatment option—for example, the costs might be higher than expected, the benefits might not be fully realized, or other aspects of the organization might be negatively affected. Potential implementation risks should be identified and documented for each information risk treatment option.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
The TIRM team at the call center organizes a brainstorming session to identify potential implementation risks for each information risk treatment. Implementation risks of the information risk treatment to change the incentive system for call center agents and team leaders are presented in Table 8.7, and are evaluated overall as high for this information risk treatment.
Table 8.7
Implementation Risks of Information Risk Treatment to Change the Incentive System for Call Center Agents and Team Leaders
|
Implementation Risk |
Likelihood |
Consequence |
|
No final approval is given by board of directors |
Very low |
Investment is completely wasted |
|
Final approval by board of directors is delayed |
Medium |
Slightly increased costs and benefits will take longer to be realized |
|
Design of new incentive system takes longer |
High |
Increased costs and benefits will take longer to be realized |
|
Implementation of new incentive system takes longer |
Medium |
Increased costs and benefits will take longer to be realized |
|
Software changes do not work and need redesign |
Low |
Significantly increased costs and benefits will take longer to be realized; quality of service might be affected |
|
Problems in user adoption |
Medium |
Benefits will not be fully realized |
|
Measurement metric do not drive the right behavior |
Low |
Benefits will not be realized |
Step C4: Evaluate and select treatment options
In this step (Figure 8.11), information risk treatment options are evaluated, with due consideration being given to the costs, benefits, and risks of the option. Risk treatment options are selected, taking this evaluation and the overall organizational priorities and culture into account. Moreover, a five-step scale from very low, low, medium, high, to very high can be used to evaluate the priority of the risk treatment option.
FIGURE 8.11 Step C4 in context.
Note that sometimes when the risk is not tolerable, it can be decided to treat a risk although it is not justifiable on economic grounds as suggested by the ISO 31000 standard (ISO, 2009).
The selected information risk treatment options should be ranked in a list, taking their overall evaluation and priority evaluation into account. A recommendation should be forwarded to the senior decision makers who will have the final say as to which information risk treatment options are approved for implementation.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
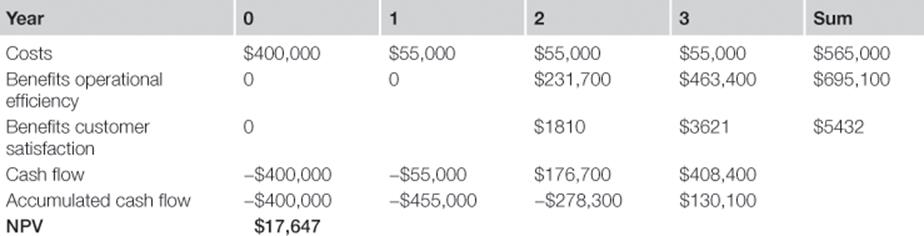
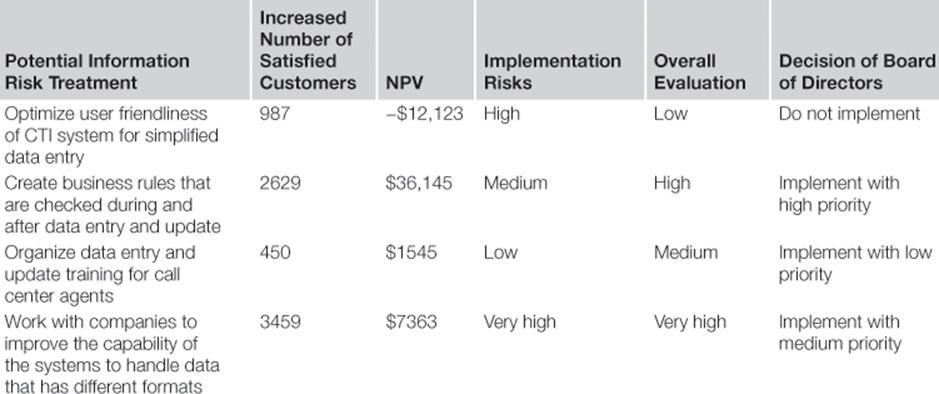
To prepare the evaluation for the board of directors, the TIRM process manager brings the benefits and costs for each information risk treatment into a single table and calculates the accumulated cash flow and net present value (NPV) over three years (Table 8.8). He discusses with the TIRM process sponsor which recommendations should be given to the board of directors. For those information risk treatments that should be proposed to the board, a business case is created that describes the information risk treatments and presents the hard numbers.
Table 8.8
Investment Analysis of the Information Risk Treatment to Change the Incentive System for Call Center Agents and Team Leaders
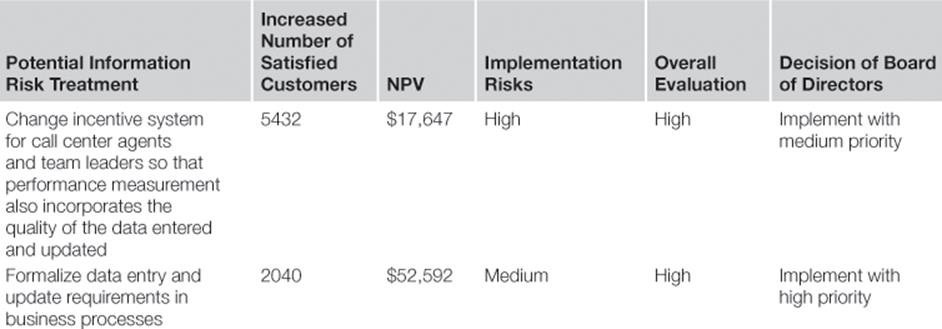
The TIRM process sponsor presents the business cases to the board of directors who make the final decision as to which information risk treatments should now be implemented (Table 8.9).
Table 8.9
Investment Evaluation of Potential Information Risk Treatments
Step C5: Communicate the results to stakeholders
The support of stakeholders is paramount to manage the successful implementation of selected information risk treatments (Figure 8.12). Communicating the results is therefore an important part of both risk management and information quality management practices. Therefore, the list of information risks and selected information risk treatments should be communicated in this step to all relevant stakeholders. This can be done in many different ways, such as in the form of a written report or in a meeting in which the results are presented. The stakeholders should be encouraged to give feedback, which should be carefully considered since in response to such feedback, it might mean that changes or modifications are required to previously made decisions.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
The TIRM team develops a communication plan, which is presented in Table 8.10. A number of events are organized separately for each of the stakeholder groups to communicate the messages. A discussion session that involves team leaders and members of the IT department is also organized to set the foundation for good cooperation and collaboration during the implementation of the information risk treatment.
Table 8.10
Communicating Plan
|
Stakeholder Group |
Why are They Important? |
Which Message Should be Sent Out? |
|
Board members |
Approval absolutely essential at many stages during implementation. |
Implementing the information risk treatment measures will improve customer satisfaction and decrease operational costs. |
|
Team leaders |
Their support is necessary to change the behaviors of call center agents. |
Fewer information quality problems mean fewer business problems and daily incidents that the team leaders need to deal with. |
|
Call center agents |
A number of causes of information quality problems are directly related to the call center agents’ behaviors. |
Higher-quality data will make it easier for call center agents to better serve customers. There will be less frustration in the daily job and less effort will be needed to deliver good job performance. |
|
IT department |
The IT department needs to be encouraged to work out solutions that will work in practice. They need to be motivated to cooperate effectively with other parts of the business. |
Only through close cooperation with the business side will the implementation of information risk treatments be successful. It will enable the IT department to perform the data management activities to higher standards. Improved data quality will open new opportunities for data analytics. |
|
Client companies |
There might be service disruptions when changes are executed. Informing clients about plans will help them to understand that the information risk treatments are in their interests. |
Information risk treatments are implemented to improve customer satisfaction levels even further. The disruptions during implementation will be reduced to a minimum. The benefits will accrue quickly. |
FIGURE 8.12 Step C5 in context.
Step C6: Develop information risk treatment plans
Once the most important stakeholders agree to the proposed treatments, the best way to implement the treatment has to be investigated. In this step (Figure 8.13), for each information risk treatment selected for implementation, an information risk treatment plan is developed. There are usually many different ways to implement an information risk treatment. The most effective way to implement the option is determined after considering the prevailing culture and the lessons learned in the organization, because this will give you a steer toward the most effective route.
FIGURE 8.13 Step C6 in context.
As part of the preparation of an information risk treatment plan, the following things should be documented, according to the ISO 31000 standard (ISO, 2009, p. 20):
![]() The reasons for selection of treatment options, including expected benefits to be gained
The reasons for selection of treatment options, including expected benefits to be gained
![]() Those who are accountable for approving the plan and those responsible for implementing the plan
Those who are accountable for approving the plan and those responsible for implementing the plan
![]() Proposed actions
Proposed actions
![]() Resource requirements including contingencies
Resource requirements including contingencies
![]() Performance measures and constraints
Performance measures and constraints
![]() Reporting and monitoring requirements
Reporting and monitoring requirements
![]() Timing and schedule
Timing and schedule
Moreover, a project team needs to be chosen and sometimes selection of software required has to be made (see Chapter 12). Advice from external consultants who have experience of the type of information risk treatment should also be considered if this level of expertise does not currently exist in the organization.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
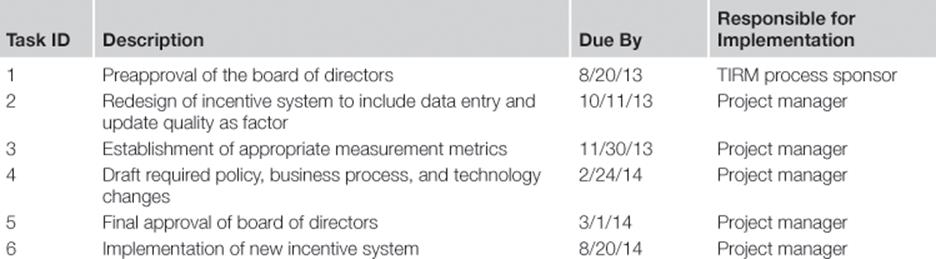
For each information risk treatment, the TIRM team, in coordination with the board of directors, chooses a project manager and an implementation plan is developed by the TIRM process manager. An example is given in Table 8.11 for the information risk treatment to change the incentive system for call center agents and team leaders.
Table 8.11
Implementation Plan for the Information Risk Treatment to Change the Incentive System for Call Center Agents and Team Leaders
Step C7: Implement information risk treatment plans
In this step (Figure 8.14), each selected information risk treatment is implemented according to the approved information risk treatment plan developed in step C6. The implementation should be fully documented. General best-practice principles in project management apply during implementation. You can use any project management methodology that is accepted in your organization; select the one you consider is most appropriate for the type and scale of the implementation project. If suitable, the implementation can initially be done on a small scale, as this will enable you to check if the addressed information risks can be treated successfully. You can then expand the treatment to the full scope.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
During the course of the year, implementation of each of the selected information risk treatments commences using the priorities set out in step C4. Each project manager documents the progress of the implementation using the template shown in Table 8.12. If additional actions are required, when, for example, problems arise during implementation, then the project manager of an information risk treatment can escalate the issues, if required, to the TIRM process manager.
Table 8.12
Project Status Report for Information Risk Treatment to Change the Incentive System for Call Center Agents and Team Leaders
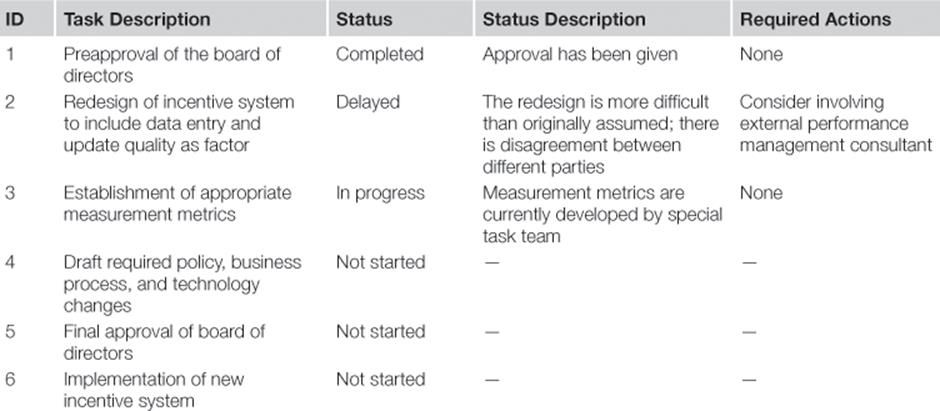
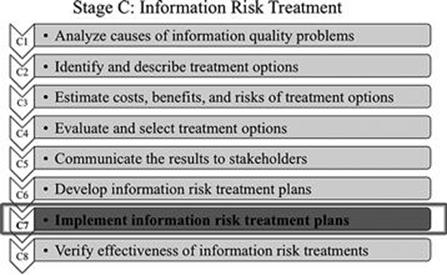
FIGURE 8.14 Step C7 in context.
Step C8: Verify effectiveness of information risk treatments
The effectiveness of the implemented information risk treatment is verified in this step (Figure 8.15). The costs and benefits are checked and compared with the planned expected costs and benefits. Lessons learned should be documented to improve information risk treatments in the future.
![]() EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
EXAMPLE: TIRM PROCESS APPLIED AT A CALL CENTER
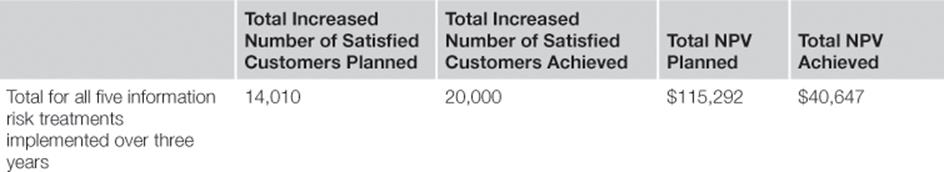
After all five information risk treatments have been fully implemented and three years have passed, it is time for the TIRM team at the call center to verify the benefits and summarize the learnings. The TIRM process manager realizes that it is difficult to measure the benefits that have accrued from each individual information risk treatment because the information risk treatments are interdependent. He, therefore, decides to look at the overall benefits of all five implemented information risk treatments. In fact, a clear increase in satisfied customers and decrease in operational costs could be measured, as shown in Table 8.13. Taken as a whole, the investment has been worthwhile, although the NPV is much lower than expected, as the actual implementation costs exceeded the planned costs and some of the benefits were not realized. The good news is that the NPV is still positive and that the increase in the number of satisfied customers has been higher than anticipated.
Table 8.13
Comparison of Planned versus Realized Benefits
To learn from the implementation of these information risk treatments, the TIRM process manager organizes sessions with each of the project managers to summarize the key learnings, which are presented in Table 8.14.
Table 8.14
Summary of Lessons Learned During Information Risk Implementation
|
Information Risk Treatment |
Lessons Learned |
|
Change incentive system for call center agents and team leaders. |
Redesign of incentive systems is a huge effort on its own. Measurement metrics need to be objective and fair and have to be sufficiently tested. This requires more effort than anticipated. |
|
Formalize data entry and update requirements in business processes. |
Formalization of requirements makes it clearer to employees what is required. Stronger focus should be placed on enforcement of the requirements. |
|
Create business rules that are checked during and after data entry and update. |
Business rules started only to be effective after they have been combined with incentives and formalization of requirements. |
|
Organize data entry and update training courses for call center agents. |
Training was more effective than originally expected. Call center agents are more motivated in data entry when they understand why it is important. |
|
Work with companies to improve the capability of the systems to handle data that has different formats. |
Establishing good relationships with the client companies is key to get a better understanding of the customer data that is handed over. Capability to handle different formats was vastly improved through this information risk treatment. |
While some aspects did not work out as well as anticipated, the TIRM process sponsor and the board of directors are, overall, very pleased with the outcomes. Consequently, they decide to run the TIRM process on an annual basis to further optimize data and information assets at the call center. The lessons learned are considered in the next cycle of the TIRM process.
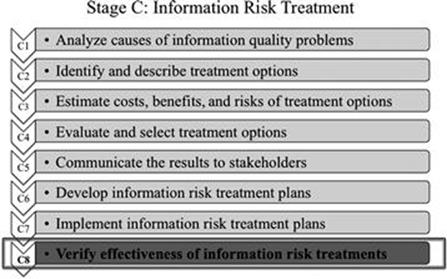
FIGURE 8.15 Step C8 in context.
Summary
This chapter presented stage C of the TIRM process, which is an eight-step approach to identify, evaluate, and implement suitable treatments for the information risks acknowledged in stage B. Information risk treatment first identifies and ranks the root causes of the information risks after which potential information risk treatments are identified. To evaluate and select the right information risk treatment options, the costs, benefits, and expected implementation risks have to estimated. The benefits are, therefore, calculated using the risk figures from stage B. Communicating effectively to the most important stakeholders increases their support during implementation. Information risk treatment plans are developed then implemented, and the effectiveness of the information risk treatments are verified at the end of stage C. Finally, lessons learned are summarized to improve the next cycle of the TIRM process, which starts back at stage A. The next cycle of the TIRM process does not require the same amount of effort, as a lot of information has already been collected and needs only to be updated. Additionally, your organization is already very familiar with the way in which the TIRM process is run.
In the next chapter, we discuss strategies to better integrate the TIRM process within the organization.
References
1. International Organization for Standardization (ISO). ISO 31000:2009 Risk Management—Principles and Guidelines on Implementation 2009; Available at http://www.iso.org/iso/catalogue_detail?csnumber=43170; 2009.
2. International Organization for Standardization (ISO). ISO/IEC 31010:2009 - Risk Management—Risk Assessment Techniques 2009; Available at http://www.iso.org/iso/catalogue_detail?csnumber=43170; 2009.
3. Loshin D. Enterprise Knowledge Management: The Data Quality Approach San Francisco: Morgan Kaufmann 2001.
4. McGilvray D. Executing Data Quality Projects: Ten Steps to Quality Data and Trusted Information™. Burlington, MA: Morgan Kaufmann; 2008.