Beginners guide to hacking and penetration testing (2017)
Maintaining access:
Part of maintaining access comes in a couple ways.
1) Once we have access to the system it is important to create an administrator account (or a couple). If we gained access with an existing administrator account this will be easy, otherwise if we gained access with a lower level account we will want to try and escalate that user's privileges. When creating an account try to keep it within the existing naming structure as to not draw unwanted attention.
2) When are you using those accounts? This is a difficult one to decide. Using the accounts on off hours can alert a particularly attentive system administrator. Using them during business hours (depending on how you are using your access) could just as well draw unwanted attention. You will need to think about these questions.
3) Location: Are you accessing the network locally or remotely? Are you even accessing it from the same city, state, or country? If you are working remotely, you may want to use a VPN to make it seem like you are closer than you are. Running through a VPN will also help protect your identity.
4) Slow and steady: Once you gain access you may be tempted to start running around like a kid in the toy store. You will need to temper your excitement and remember to take things slow. Downloading terabytes of data will likely get you caught before you get very far. Take things slow and steady, fly under the radar as it were and try not to stand out.
5) Clear out those log files! Depending on the server or computer(s) that you are on will depend on where and how those systems log what you have been doing. Do your research and either delete or alter the log files to help hide your activities. Metasploit has a module called timestomp. Timestomp is used to alter the timestamp of Windows logs.
Hardware hacking:
Using a computer program isn't the only way to get into a computer or network. In this section we will be looking at hardware hacking. We will also learn how to build our own USB backing device and setting up an Android phone for hacking!
USB Rubbery Ducky:
Another tool is called the USB Rubber Ducky by the team at Hak5.org. This tool looks like any other USB device, however it holds a small board capable of delivering various payloads of our choosing.

When plugged into a computer (Windows, Linux, OS X) the computer recognizes it as a USB keyboard. The significance of this is that since it's a "keyboard" an antivirus will not detect it as a virus, in fact the antivirus will assume it's the user inputting commands, well inputting commands at 1,000 words per minute!
The device uses a simple scripting language and a micro USB that is plugged into the device to execute and store your payloads. Two very easy deployment methods would be to do a USB drop, where you leave it somewhere that a person may find it, relying on a person's curiosity to see what's on it. Another method would be to find a unlocked computer and quickly plug it in.
SCRIPT SAMPLE:
REM PAYLOAD WILL PAUSE OPEN NOTEPAD THEN TYPE A HELLO WORLD TEXT WINDOWS r
DELAY 100
STRING notepad.exe DELAY 200
STRING HELLO WORLD! I'M ON YOUR NOTEPAD!
The encode can be loaded to various system or you can use the online tool: https://ducktoolkit.com/
Tool can be found at: https://hakshop.com/products/usb-rubber-ducky-deluxe
Making a USB hacking toolkit:
We can't always carry our computers or various hacking tools with us everywhere we go, so how cool would it be to have some of our password crackers, forensics tools, even our OS with us in our pocket? In this section we will be looking at building our own USB hacking toolkit. We will be able to carry around various OS' and run a whole slew of software on other people's computers without installing anything on them.
Note: It should be noted that any "hacking" tool will likely flag your anti-virus. You will need to make your own determination as to how confident you feel in using it.
Needed:
• A Windows computer to build software portion of the drive
• A USB Drive: Preferably a USB 3 drive. The larger the drive the better
1. Plugin USB Drive into your computer
2.  Download YUMI -Multiboot USB Creator https://www.pendrivelinux.com/yumi-multiboot-usb- creator/
Download YUMI -Multiboot USB Creator https://www.pendrivelinux.com/yumi-multiboot-usb- creator/
3.
4. Double click the Yumi application to launch and click I Agree
5.
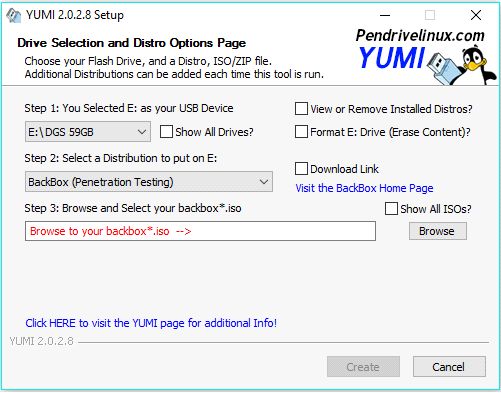
6. Click the drop down box on Step 1 and select your drive
7. Step 2 click the drop down box and select the software you want to install
8. Assuming that you don't already have the ISO file click the Visit the… blue text to the right, this will take you to that particular software page to download your ISO file. Clicking the Download Link box may or may not take you there directly
9. Once you have downloaded your ISO file click the Browse button and select your ISO file
10.  Then click Create on the bottom to get started
Then click Create on the bottom to get started
11.
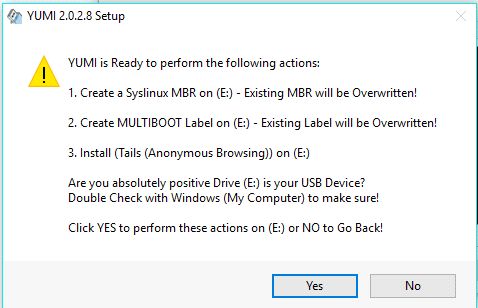
12. You will be asked to confirm, click Yes
13. When the file finishes installing you will be asked if you wish to add more distributions. Repeat the above steps for all software you wish to install.
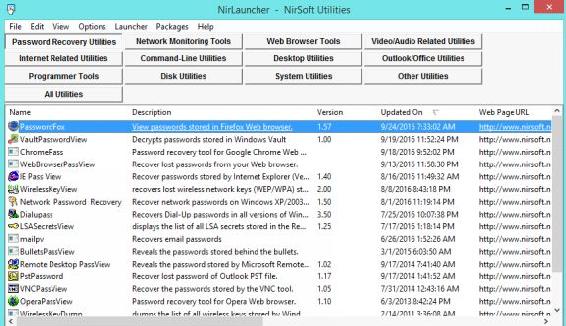
14. NirLauncher http://launcher.nirsoft.net/
15.
16. Nirlauncher has a large number of useful programs for hacking including password decrypt for browsers, wireless, VNC, and other programs. The great thing about this also is the program package does not require a install. You can simply unzip this to your USB drive and launch it.
Hacking with Android:
Love it or hate it, Android is a versatile platform that makes for an excellent portable hacking platform. While this is no real replacement for an actual computer, it is still useful for certain situations or in a pinch. Below we will look at using an Android phone (In this example I am using a used Samsung Galaxy S4).
Jailbreaking:
Chances are if you haven't jailbroken a phone before, you have at least heard the term before. Jailbreaking your phone essentially unlocks it to install unauthorized applications, remove certain restrictions, and overall give you more freedom when it comes to your overall phone operations. The act of jailbreaking your phone runs the small risk of bricking it or rendering it useless (you can more than likely do a factory reset to fix this). Jailbreaking your phone may or may not void your warranty or may not be allowed by your phone carrier so before doing this, take into consideration all of these factors.
Also jailbreaking or installing any of the applications mentioned here is this guide is as always done at your own risk. Overall the risk of damage is pretty rare and the process of jailbreaking your phone has become incredibly simple.
Enable Developer Mode:
The first thing you will want to do is enable developer mode on your phone. To do this go to: Settings - About Phone then tap Build number 7 times, this will open a new option (Developer options).
Under the Developer options you are free to tweak your phone as you like, but the main one we want to enable is USB debugging.
Security Setting:
Under the Security option make sure Unknown sources is checked. This will allow us to load apk files (Android installer files) outside of the store.
KingRoot:
So the rooting tool that we will be using is KingRoot, KingRoot is an easy, free program that will allow us to root our phone without having to go through any elaborate steps. As of this writing it supports: Samsung, Huawaei, LG, Google, and hTC.

From your phone open a browser and navigate to https://kingroot.net from there click the Download APK for Android to download the file to your phone and run. The instructions from there are pretty straight forward and the only recommendation that I would make is plug your phone in. The entire process should only take a couple minutes. If the root does not work the first time or two don't worry, just run it again. When the root is successful, you will see a rooted status. From there we are free to install 3rd party programs that we would not normally be able to run.
Some useful apps:
Below are some applications that are free that I found to be useful.
• zANTI: Billed as a Mobile Pentesting Toolkit zANTI has a number of useful tools at the palm of our hands. Some of the useful tools are: Nmap, Man in the Middle attacks, WiFi Scans, and vulnerability assessment. The program can be found at: https://www.zimperium.com/zanti- mobile-penetration-testing
• Fing: Can be used to do a number of network scans, maps, and audits. The program can be found in the Play store.
• AnDOSid: Is a network stress tool, ie. It's designed to DDoS a website.