CCNP Security SISAS 300-208 Official Cert Guide (2015)
Part V: Advanced Secure Network Access
Chapter 18. TrustSec and MACSec
This chapter covers the following exam topics:
![]() Describe SGA
Describe SGA
![]() Describe TrustSec architecture
Describe TrustSec architecture
![]() SGT classification—dynamic/static
SGT classification—dynamic/static
![]() SGT transport—inline tagging and SXP
SGT transport—inline tagging and SXP
![]() SGT enforcement—SGACL and SGFW
SGT enforcement—SGACL and SGFW
![]() MACSec
MACSec
Throughout this book, you have been exposed to many ways of controlling network access based on the context of a user and device. There is virtual local area network (VLAN) assignment, in which access is controlled at the Layer-3 edge or by isolating that VLAN into a segmented virtual network (VRFs). Additionally, there is access control list (ACL) assignment, which can be a local ACL, called into action by a RADIUS attribute, or a downloaded ACL (dACL). These ACLs are applied ingress at the switch port or at the virtual port in the case of the Wireless LAN Controller (WLC).
These are all very good access control methods, but controlling access only at the point of network ingress can leave room for a more desirable and scalable solution. In this chapter, you will learn about one such Cisco enhancement to make access control more scalable and powerful; it’s called TrustSec. This is a very confusing name to give to a solution because Cisco has redefined what TrustSec means numerous times. However, you will learn about it in the context expected for the exam, and that definition of TrustSec is a policy-defined segmentation solution that provides advanced enforcement. This was formerly referred to as security group access (SGA).
TrustSec is a natural progression on top of the IEEE 802.1AE industry standard, commonly referred to as MACSec. This standard defines a Layer-2 encryption for Ethernet environments very similar to Wi-Fi Protected Access (WPA).
This chapter focuses on the fundamentals of TrustSec and MACSec as well as showing the configuration of the many devices available for use in a TrustSec environment. Basic use cases are presented for security group ACL, and security group firewalls.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 18-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes.”
Table 18-1 “Do I Know This Already?” Section-to-Question Mapping
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. What is a security group tag?
a. A luggage tag applied by TSA workers at airports to flag bags as they enter security checkpoints
b. An internal assignment used in ISE to represent a local copy of an Active Directory group
c. A 16-bit value that represents the context of a user and/or a device
d. An RFID tag used to identify a wireless asset to ISE
2. Where are security groups defined in the ISE administrative GUI?
a. Administration > System > Security Group Access > Security Group
b. Policy > Policy Elements > Results > Security Group Access
c. Policy > Policy Elements > Dictionaries > System > Security Group Access
d. Policy > Firewall > Identity by TrustSec
3. What are three ways that an SGT can be assigned to network traffic?
a. Manual binding of the IP address to an SGT
b. Manually configured on the switch port
c. Dynamically assigned by the network access device
d. Dynamically assigned by the 802.1X authorization result
e. Manually configured in the NAC agent profile
f. Dynamically assigned by the AnyConnect network access manager
4. True or False? An SGT-capable device can automatically map traffic to an SGT based on the VLAN of that traffic.
a. True
b. False
5. Which peering protocol can be used to transmit a mapping of IP address to SGTs between SGT-capable devices when traffic is crossing non–SGT-capable network segments?
a. Enhanced Interior Gateway Routing Protocol (EIGRP)
b. Intermediate System—Intermediate System (IS-IS)
c. Border Gateway Protocol (BGP)
d. Security Group Exchange Protocol (SXP)
6. What are two modes of SXP peers?
a. Speaker
b. SGT-Reflector
c. Listener
d. SGT-Sender
7. How is the SGT transmitted when using native tagging?
a. The SGT is included in the Cisco Metadata (CMD) portion of the Layer-2 Frame.
b. The SGT is included in 802.1Q trunking.
c. The SGT is included in Inter-Switch-Link (ISL) trunking.
d. The SGT is carried in Cisco Discovery Protocol (CDP) messages.
8. When using native tagging of SGTs, how can an administrator ensure confidentiality and integrity of the tag?
a. By enabling MD5 authentication between SGT peers
b. By enabling IEEE 802.1AE (MACSec) between the switches
c. By enabling IEEE 802.1AE (MACSec) between the endpoint and the access switch
d. By configuring peer-to-peer GRE tunnels between the switches
9. What are two methods of enforcement with SGTs?
a. SG-ACLs on switches.
b. SG-ACLs on routers.
c. SG-Firewalls.
d. SG-Appliances.
e. SGTs are not enforced.
10. What is the difference between uplink MACSec and downlink MACSec?
a. Uplink MACSec defines the encrypted traffic entering the switch from the endpoint, whereas downlink MACSec is the encrypted traffic leaving the switch, destined to the endpoint itself.
b. There is no difference between uplink and downlink MACSec.
c. The difference is solely based on the encryption algorithm used.
d. Uplink MACSec defines the encrypted connection between network infrastructure components, whereas downlink MACSec defines the encrypted connection between the access layer device and the endpoint.
Foundation Topics
Ingress Access Control Challenges
VLAN assignment and downloadable ACLs (dACLs) are fantastic ways of controlling access to a network. However, when a network grows, so do the challenges of keeping up with the ingress access controls. Let’s take a look at each one of these standard use cases individually and discuss the challenges.
VLAN Assignment
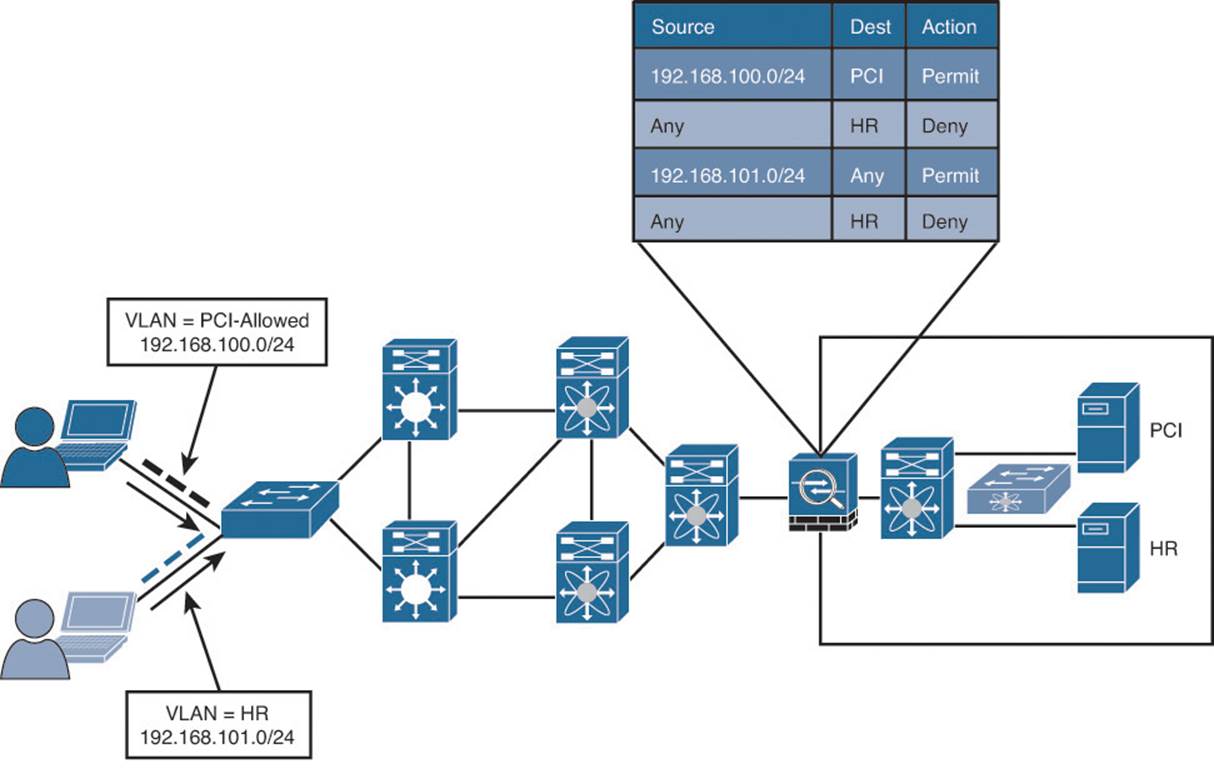
VLAN assignment based on the context of a user or device is a common way to control access to the network. Let’s use a hypothetical scenario of controlling access to servers that contain credit card data, which falls under the realm of Payment Card Industry (PCI) regulatory compliance:
1. A user is a member of the Retail-Managers group in Active Directory.
2. The posture of the system is compliant.
3. Therefore, ISE assigns the user into the PCI-Allowed VLAN on the switch or WLC. To use that VLAN assignment to control access to the servers that house that PCI data, an ACL must be applied somewhere. Let’s assume the ACL is applied at a firewall between the campus/branch networks and the data center.
4. The ACL on the data center firewall must be updated to include all the source IP addresses of PCI-Allowed VLANs throughout the entire network infrastructure.
Figure 18-1 illustrates the concept of VLAN-based access control on a single switch.
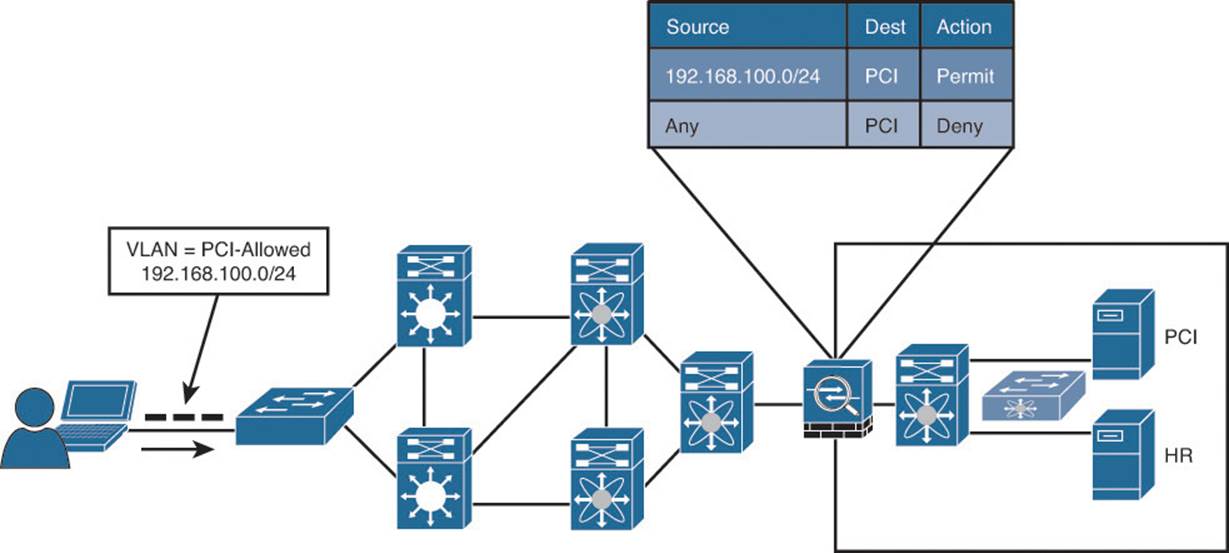
Figure 18-1 Controlling access with VLANs on a single switch.
Next, the company has decided to control access to the HR server, so that only members of the HR Department can talk to HR servers. Another set of rules must be built that assign the HR VLAN and another set of entries in the access list. Figure 18-2 illustrates the concept of controlling access with two VLANs on a single switch.