Implementing Cisco IOS Network Security (IINS) Foundation Learning Guide, Second Edition (2013)
Part III: Threat Control and Containment
Chapter 9. Firewall Fundamentals and Network Address Translation
This chapter teaches firewall concepts, technologies, and design principles. At the end of this chapter, you will be able to do the following:
• Explain the operations of the different types of firewall technologies
• Describe firewall technologies that historically have played, and still play, a role in network access control and security architectures
• Introduce and describe the function and building blocks of Network Address Translation
• List design considerations for firewall deployment
• Describe guidelines for firewall ruleset creation
Introducing Firewall Technologies
A firewall protects network devices from intentional, hostile intrusions that could threaten information assurance (availability, confidentiality, and integrity) or lead to a denial-of-service (DoS) attack. A firewall can protect a hardware device or a software program running on a secure host computer. This chapter introduces the firewall technologies that Cisco uses in routers and security appliances.
Firewall Fundamentals
The term firewall is a metaphor. By segmenting a network into different physical subnetworks, firewalls can limit the damage that can spread from one subnet to another, just as the fire doors and firewalls that are used in a building limit the spread of fire, heat, and structural collapse. In network security terms, a firewall is a software or hardware barrier between an internal (trusted) network and an external (untrusted) network. In this sense, a firewall is a set of related programs that enforces an access control policy between two or more networks.
In principle, as shown in Figure 9-1, a firewall is a pair of mechanisms that perform these two separate functions, which are set by policies:
• One mechanism blocks bad traffic.
• The second mechanism permits good traffic.
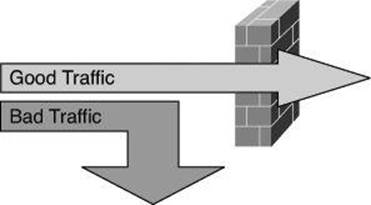
Figure 9-1. Firewall: Enforcing Access Control
A firewall can be defined as follows:
A system or group of systems that enforces an access control policy between two networks.
Because this definition is very generic, almost anything can be considered a firewall. Many network access technologies can be used to build a firewall:
• Packet-filtering routers
• LAN switches
• Complex systems integrating many hosts into a firewall system
Note
Depending on which definition you look at regarding firewall technologies, proxy servers and gateways may or may not be included. Proxy gateways, discussed later in this chapter, are also referred to as application layer firewalls. The Cisco IronPort Web Security Appliance is an example of a proxy server.
Firewalls mean different things to different organizations, and each organization has unique requirements. Nevertheless, all firewalls usually share some common properties:
• Must be resistant to attacks: Compromise of the firewall system should be very unlikely, because it would enable an attacker to disable the firewall or change its access rules.
• Must be the only transit point between networks: All traffic between networks must flow through the firewall. This requirement prevents a hacker from using a backdoor connection to bypass the firewall and violate the network access policy.
• Enforces the access control policy of an organization: The access control policy should define what the firewall permits or denies.
By performing network access control, you can use a firewall as a protective measure against the following:
• Exposure of sensitive hosts and applications to untrusted users: A firewall hides most of the functionality of a host and permits only the minimum required connectivity to a host. Complexity is thus reduced, and many possible vulnerabilities are not exposed.
• Exploitation of protocol flaws: You can program a firewall to inspect protocol messages and verify their compliance with the protocol, whether it is Layer 3, Layer 4, or a higher-layer protocol. The firewall limits what attackers can send to their target, preventing the delivery of malformed packets that are used in an attempt either to crash a system or to gain access to an application.
• Malicious data: A firewall can detect and block malicious data sent to clients or servers inside the application stream, thereby stopping it from infecting the server or the client. Because firewalls are located on critical interconnection points of the network, enforcing the network access policies is simple, scalable, and robust. Sometimes a small number of firewalls can handle most of the network access control needs of an organization.
Firewalls are often misunderstood, and false assumptions are often made about their capabilities. Although it is true that firewalls would not be necessary if host and application security could be made extremely robust, many organizations use firewalls as a replacement for host or application security. Such an attitude is extremely dangerous because it can completely ignore host and application security even in extreme cases, such as connecting a sensitive server inside an Internet firewall.
Today, firewalls are such a mainstream technology that they are often considered a panacea for many security issues. While you should be aware of the benefits of the firewall model, you should also be aware of the many limitations that firewalls have and how to mitigate some of these limitations:
• Because firewalls are used in critical points of the network, their misconfiguration can have disastrous consequences. Firewalls are often a single point of failure when it comes to security; a single mistake in a configuration rule or firewall code can compromise the network access policy.
• Many modern applications require that the firewall handle, in addition to the primary control connection, secondary connections that are created to carry, for example, data. A typical example is an application that opens dynamic sessions from the outside to the inside after an initial client request initiated from the inside to the outside. Multimedia applications such as those for audio streaming and videoconferencing are examples where the user opens one session from the inside to the outside to request a feed. To support the streaming, however, additional sessions are opened from the outside to the inside, and by default the firewall rejects those new incoming requests. Once firewall vendors have a chance to study the new protocol, they can create a rule that forces the firewall to peek inside the payload of the original outgoing packet to gain information about the additional sessions that will be created and to prepare for those new incoming sessions.
• End users, when faced with a restrictive firewall, might find their own methods of bypassing it. For example, inside users may use wireless broadband from the protected network to an Internet service provider (ISP) and create a backdoor connection to the protected network.
• Because firewalls are commonly placed at chokepoints, the design of the firewall model must ensure network performance is not affected by inspecting all the traffic.
• Tunneling unauthorized data over authorized connections (covert channels) is simple and generally impossible to detect. This activity usually requires the help of someone on the trusted side of the firewall.
Firewalls in a Layered Defense Strategy
In a layered defense scenario, firewalls provide perimeter security of the entire network and of internal network segments in the core. For example, system administrators can use a firewall to separate the human resources and financial networks of an organization from other networks or network segments within the organization.
A layered defense strategy combines different types of firewalls in layers to add depth to the information defense of an organization, as shown in Figure 9-2. For example, traffic that comes in from the untrusted network first encounters a packet filter on the outer router, located in the perimeter security. The traffic next goes to the screened host firewall or bastion host system, which applies more rules to the traffic and discards suspect packets. This bastion host system is also part of the perimeter security. The traffic then goes to an interior screening router, part of the core network security. The traffic moves to the internal destination host only after this routing. This type of demilitarized zone (DMZ) setup, located between the perimeter and the core, is called a screened subnet configuration. Endpoint traffic moves in the network after it has been properly authenticated by sophisticated Identity services.
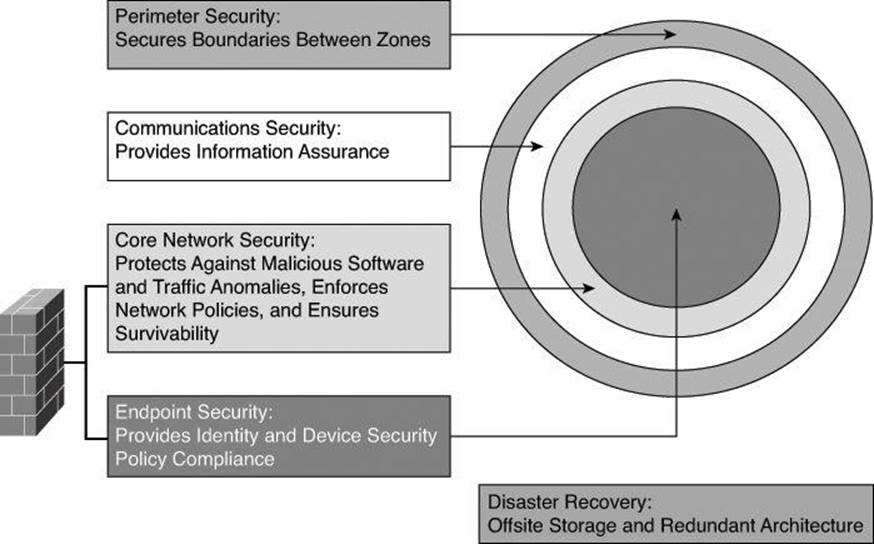
Figure 9-2. Layered Defense Strategy
Two recurring terms in this chapter are bastion host and packet filter, which are defined as the following:

• Bastion host: A computer that is expected to be attacked and therefore is hardened. An example of a bastion host is firewall software installed on a workstation that is already running a commonly available operating system. Before the firewall is put into production, the workstation needs to be hardened to protect against the potential vulnerability that the operating system has.
• Packet filter: Typically, a router configured with access lists used to filter out unwanted traffic.
A common misconception is that a layered firewall topology is all that you need in place to declare your internal network to be safe. This myth is probably encouraged by the booming firewall business; however, you need to consider the following factors when building a complete defense-in-depth environment:
• A significant number of intrusions come from hosts within the network. For example, firewalls often do little to protect against viruses downloaded through email.
• Firewalls do not protect against rogue modem or rogue wireless access point installations. In addition, and most important, a firewall is not a substitute for informed administrators and users.
• Firewalls do not replace backup and disaster recovery mechanisms resulting from attack or hardware failure. An in-depth defense also includes offsite storage and redundant hardware topologies.
Defense in depth and diversity of defense are related topics. Defense in depth calls for multiple levels of defense; diversity of defense calls for using different types of technologies in that defense.

An example of implementing both diversity of defense and defense in depth is using a perimeter router as a packet filter and using a stateful firewall to segment the unprotected segment from the protected segment.
Static Packet-Filtering Firewalls
Packet-filtering firewalls work primarily at the network layer of the Open Systems Interconnection (OSI) model, or the IP layer of TCP/IP, as shown in Figure 9-3. Packet-filtering firewalls are generally considered Layer 3 devices, but they typically have the capability to permit or deny traffic based on Layer 4 information, such as protocol, and source and destination port numbers, in addition to the Layer 3 source and destination IP address. Packet filtering uses rules and ACLs to determine whether to permit or deny traffic based on source and destination IP addresses, protocol, source and destination port numbers, and packet type. Packet-filtering firewalls are usually part of a router firewall.
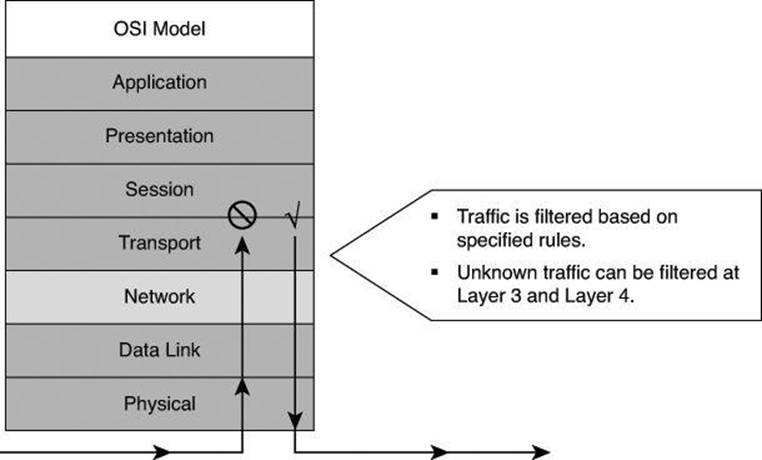
Figure 9-3. How Static Packet Filters Map to the OSI Model
Recall that services rely on specific ports to function; for example, Simple Mail Transfer Protocol (SMTP) servers listen to port 25 by default. Because packet-filtering firewalls filter traffic according to static packet header information, they are sometimes referred to as static filters. By restricting certain ports, you can restrict the services that rely on those ports. For example, blocking port 25 on a specific workstation prevents an infected workstation from broadcasting email viruses across the Internet.
Packet-filtering firewalls are similar to packet-filtering routers but with some differences in implementation. Packet filters are very scalable, application independent, and have high performance standards; however, they do not offer the complete range of security solutions required in modern networks. For example, a packet filter does not have the capability to understand dynamic protocols upon which a client request requires additional incoming connections to be initiated from the outside, toward the inside client.
Any device that uses ACLs can perform packet filtering. Cisco IOS router configurations commonly use ACLs, not only as packet-filtering firewalls but also to select specified types of traffic that is to be analyzed, forwarded, or influenced in some way. Later in this chapter, you will see examples of both ingress and egress filtering done with ACLs.
Figure 9-4 shows a simple packet-filtering example using a Cisco router.
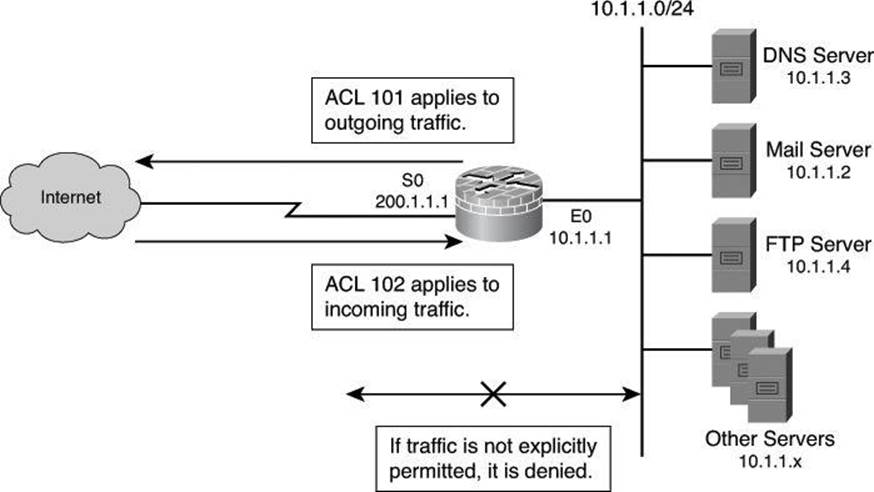
Figure 9-4. Static Packet Filter in Action
In most network topologies, you need to protect the Ethernet interface connecting to the internal (inside) network, while the serial interface that connects to the Internet (outside) is unprotected. In Figure 9-4, the internal addresses that the firewall must protect are in the 10.1.1.0/24 subnet (on the Ethernet interface). The IP address of the Ethernet 0 interface is 10.1.1.1/24.
The particular network security policy shown in Figure 9-4 (ACL 101) allows all users from the inside to access Internet services on the outside. Therefore, all outgoing connections are accepted. The router checks only packets coming from the Internet (security policy ACL 102). In this case, the ACL allows Domain Name System (DNS), SMTP, and FTP services, and the return of traffic initiated from the inside. ACL 102 denies access to all other services.
Packet-filter firewalls (or packet filters) use a simple policy table lookup that permits or denies traffic based on the following possible criteria:
• Source IP address
• Destination IP address
• Source port number
• Destination port numbers
• Synchronize/start (SYN) packet receipt
The firewalls are extremely fast because they do little computation. The rules are extremely easy to implement because they require little security expertise. Router manufacturers easily embed packet-filtering logic in silicon and, consequently, packet filtering is a feature of most routers. Packet-filtering firewalls are relatively inexpensive. Even if other firewalls are used, implementing packet filtering at the router level affords an initial degree of security at the network and transport layers.
Packet filters do not represent a complete firewall solution. However, they are a key element of a secure architecture.
The following are disadvantages of packet filters:
• Packet filtering is susceptible to IP spoofing. Hackers send arbitrary packets that fit ACL criteria and pass through the filter.
• Packet filters do not filter fragmented packets well. Because fragmented IP packets carry the Layer 4 header in the first fragment and packet filters may filter based on information found in the Layer 4 header, fragments after the first fragment are passed unconditionally. A decision to use packet filters assumes that the filter of the first fragment accurately enforces the policy.
• Complex ACLs are difficult to implement and maintain correctly.
• Packet filters cannot dynamically filter certain services. For example, sessions that use dynamic port negotiations are difficult to filter without opening access to a whole range of ports.
• Packet filters are stateless. They examine each packet individually rather than in the context of the state of a connection.
Application Layer Gateways
Application layer firewalls, also called proxy firewalls or application gateways, provide a higher level of security than packet-filtering firewalls because they allow the greatest level of control. Application gateways operate on Layers 3, 4, 5, and 7 of the OSI model, as shown in Figure 9-5.
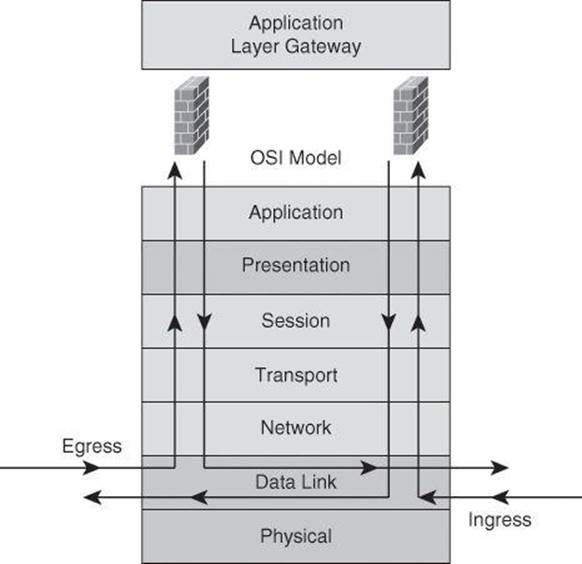
Figure 9-5. Application Layer Gateway in Action
Most application layer firewalls include specialized application software and proxy servers. A proxy is an application that does work on behalf of something else. Proxy services are special-purpose programs that manage traffic through a firewall for a specific service, such as HTTP or FTP. Proxy services are specific to the protocol that they are designed to forward, and they can provide increased access control, perform careful detailed checks for valid data, and generate audit records about the traffic that they transfer.
Proxy firewalls act as intermediaries between networks to determine whether to allow the communication to proceed. No direct connection exists between an outside user and internal network resources, because the original connection stops in the proxy and a new connection is set between the proxy and the outside destination. For this reason, the only IP address of the network that is visible from the Internet is the IP address of the outside interface of the proxy. The client connects to the proxy server and submits an application layer request. The application layer request includes the true destination and the data request itself. The proxy server analyzes the request and can filter or change the packet contents. The server makes a copy of each incoming packet, changes the source address, and sends the packet to the destination address. The destination server replies to the proxy server, and the proxy server passes the response back to the client.
Sometimes, application layer firewalls support only a limited number of applications, or even just one application. Some of the more common applications that an application layer firewall might support include email, web services, DNS, Telnet, FTP, Usenet news, Lightweight Directory Access Protocol (LDAP), and Finger.
Application layer firewalls provide several advantages:
• Application layer firewalls authenticate individuals, not devices: These firewalls typically allow you to authenticate connection requests before allowing traffic to an internal or external resource. This process enables you to authenticate the user requesting the connection instead of authenticating the device.
• Application layer firewalls make it is harder for hackers to spoof and implement DoS attacks: An application layer firewall enables you to prevent most spoofing attacks, and DoS attacks are limited to the application firewall itself. The application firewall can detect DoS attacks, and thus reduce the burden on your internal resources.
• Application layer firewalls can monitor and filter application data: You can monitor all data on a connection, so you can detect application attacks such as malformed URLs, buffer-overflow attempts, unauthorized access, and more. You can even control the commands or functions you allow an individual to perform based on the authentication and authorization information.
• Application layer firewalls can provide detailed logging: Using application layer firewalls, you can generate detailed logs and monitor the actual data that the individual is sending across a connection. This logging can prove extremely useful if a hacker finds a new type of attack, because you can monitor what the hacker does and how the machine does it, and then address the attack. Besides using logging for security purposes, you can use it for management purposes by keeping track of who is accessing what resources, how much bandwidth is used, and how often a user accesses the resources.
The topology in Figure 9-6 represents a typical proxy server deployment. A client inside the network is requesting access to a website. The client browser uses a proxy server for all HTTP requests. Perfect examples of proxy gateways performing application layer filtering are the Cisco IronPort Web Security Appliance (WSA) and the Cisco IronPort Email Security Appliance (ESA). Network security policies force all client connections to go through the proxy server. As shown in Figure 9-6, the browser connects to the proxy server to make requests. Client-side DNS queries and client-side routing to the Internet are not needed when using a proxy server. The client has to reach only the proxy server to make the request.
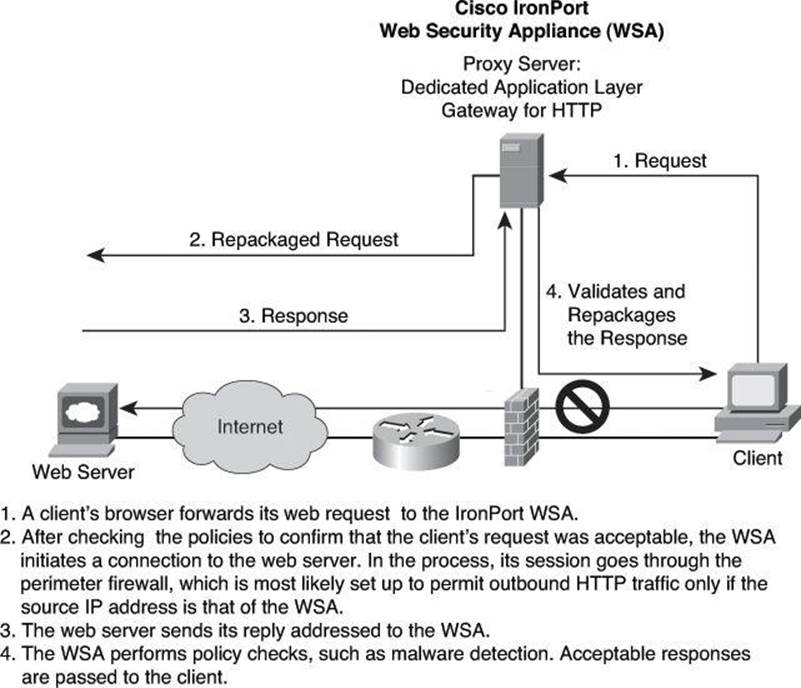
Figure 9-6. Proxy Server Communication Process
When the proxy server receives the request from a client, it performs user authentication according to the rules applied to it and uses its Internet connection to access the requested website. It forwards only packets that match the firewall rules. On the return route, the proxy server analyzes the packet, including the Layer 5 and Layer 7 header and payload, to ensure that the server allows the content of the reply back in (as an example, checking whether the payload carries hidden malware) before forwarding the packet to the client.
In spite of how an application layer firewall works, with its thorough inspection of the request and response, this firewall provides only a limited number of services, such as HTTP and FTP; however, this type of firewall provides the highest level of filtering for those specific protocols.
The main limitation of application layer firewalls is that they are process intensive because the server evaluates a significant amount of information embedded in many packets. This type of technology requires many CPU cycles and a lot of memory to process every packet that needs inspection, which sometimes creates throughput problems. In addition, the detailed logging can create disk space problems. To address these issues, you can use one of two solutions:
• Employ a context transfer protocol: Using a context transfer protocol, where identity-specific information tracks users, enables you to perform only authentication and authorization; you cannot monitor data on the connection, only whether the user is authorized to go on the Internet. This solution is not a real firewall per se, because packets are checked not for their content but for the validity of their source and destination addresses. This solution would be similar to a packet filter that has the capability to learn the source and destination information dynamically and match return traffic based on that information.
• Monitor only key applications: With this solution, you limit the application layer firewall to process only certain application types (such as email, Telnet, FTP, or web services) and then, perhaps, process only connections to specific internal resources. The problem with this approach is that you are not monitoring all applications and connections, and this creates a security weakness.
Application layer firewalls typically do not support all applications, such as multimedia or peer-to-peer file sharing applications (to name a few). Instead, they are generally limited to one or a few connection types, typically common applications such as email, Telnet, FTP, and web services. Therefore, an application layer firewall cannot monitor data on all applications: it monitors data only on applications it intrinsically understands.
Finally, application layer firewalls sometimes require you to install vendor-specific software on the client, which the firewall uses to handle the authentication process and any possible connection redirection. This limitation can create scalability and management problems if you must support thousands of clients.
Dynamic or Stateful Packet-Filtering Firewalls
Stateful packet filters, or stateful firewalls, are the most versatile and therefore the most common firewall technologies in use. Stateful filtering provides dynamic packet-filtering capabilities to firewalls. Stateful inspection is a firewall architecture that is classified at the network layer, although for some applications it can analyze traffic at Layer 4 and Layer 5, too, as shown in Figure 9-7. Some stateful firewalls can analyze traffic up to Layer 7 under special circumstances and additional configuration.
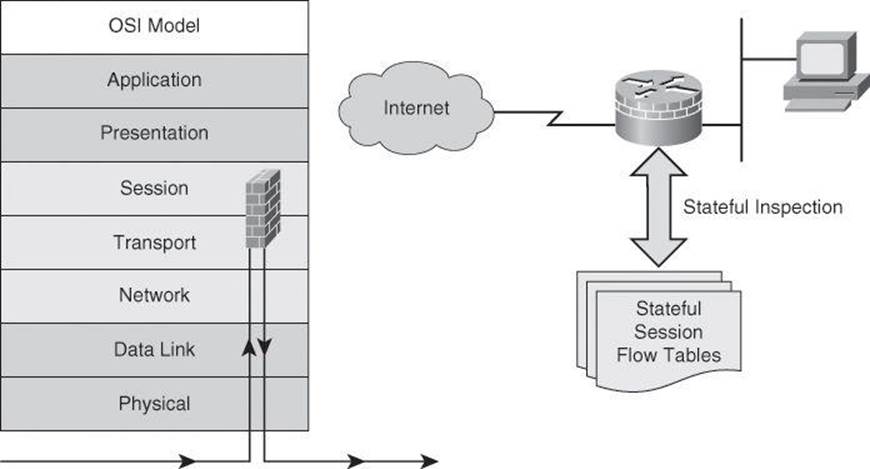
Figure 9-7. Stateful Packet-Filtering Firewall
Unlike static packet filtering, which examines a packet based on the information in its header, stateful inspection tracks each connection traversing all interfaces of the firewall and confirms that the session is valid. Stateful packet filtering maintains a state table and allows modification of the security rules on-the-fly. The state table is part of the internal structure of the firewall and tracks all sessions and inspects all packets passing through the firewall. If packets have the expected properties that are predicted by the state table, the firewall allows them to pass. The state table changes dynamically according to traffic flow.
Stateful firewalls use a state table to keep track of the actual communication process. From a transport layer perspective, the firewall examines information in the headers of Layer 3 packets and Layer 4 segments. For example, the firewall looks at the TCP header for SYN, reset (RST), acknowledgment (ACK), FIN, and other control codes to determine the state of the connection. In this scenario, the session layer is responsible for establishing and tearing down the connection.
When an outside service is accessed, the stateful packet filter firewall “remembers” certain details of the request by saving the state of the request in the state table. Each time a TCP or User Datagram Protocol (UDP) connection is established for inbound or outbound connections, the firewall logs the information in a stateful session flow table. When the outside system responds to the request, the firewall server compares the received packets with the saved state to allow or deny network access.
The stateful session flow table contains the source and destination addresses, port numbers, UDP connection information and TCP sequencing information, and additional flags for each TCP connection associated with a particular session. This information creates a connection object against which the firewall compares all inbound and outbound packets. The firewall permits data only if an appropriate connection exists to validate the passage of that data.
More advanced stateful firewalls include the capability to parse FTP port commands and update the state table to allow FTP to work transparently through the firewall. Advanced stateful firewalls can also provide TCP sequence number randomization, and DNS query and response matching to ensure that the firewall allows packets to return only in response to queries that originate from inside the network. These features reduce the threat of TCP RST flood attacks and DNS cache poisoning. Some stateful firewalls can also check the validity of protocol commands to ensure that intrusive and dangerous commands are not admitted on the network.
Packets inside the network must make their way to the outside network. This can possibly expose internal IP addresses to potential hackers. That is why most firewalls incorporate Network Address Translation (NAT) with stateful inspection and proxy servers for added security.
Stateful firewalls keep track of the state of a connection: they know whether the connection is in an initiation, data transfer, or termination state. This information is useful when you want to deny the initiation of connections from external devices (default behavior of a firewall) but allow your inside users to establish connections to these external devices and permit the responses to come back through the stateful firewall.
Figure 9-8 shows a successfully established HTTP TCP session that leads to a dynamic ACL rule entry on the outside interface that permits response packets from the web server to the client.
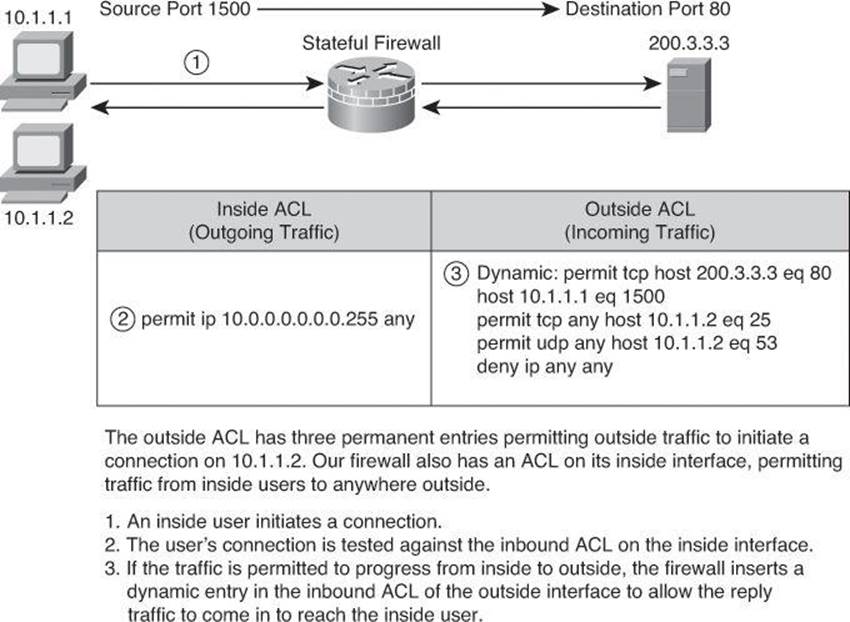
Figure 9-8. Stateful Packet Filtering
Stateful packet-filtering firewalls are good to use for the following applications:
• As a primary means of defense: In most situations, a stateful firewall is used as a primary means of defense by filtering unwanted, unnecessary, or undesirable traffic.
• As an intelligent first line of defense: Networks use routing devices that support a stateful function as a first line of defense or as an additional security boost on perimeter routers.
• As a means of strengthening packet filtering: Stateful filtering provides more stringent control over security than packet filtering does, without adding too much cost.
• To improve routing performance: Stateful packet-filtering devices perform better than packet filters or proxy servers. Stateful firewalls do not require a large range of port numbers to allow returning traffic back into the network, providing that the firewall is familiar with the protocol and its behavior. The state table determines whether a packet is returning traffic. If it is not returning traffic, the filtering table filters the traffic.
• As a defense against spoofing and DoS attacks: Stateful packet filtering works on packets and connections. In particular, stateful firewalls track the state of the connection in the state table listing every connection or connectionless transaction. By determining whether packets belong to an existing connection or are from an unauthorized source, stateful firewalls allow only traffic from connections that are listed in the table. As an example, during the three-way handshake of a TCP session, the firewall tracks the flag and therefore can predict what the following exchange between the client and the server will be. When the firewall removes a connection from the state table (for instance, because of the connection termination following the TCP four-way handshake as a goodbye), the firewall does not allow any more traffic from that device. In addition, the stateful firewall can log more information than a packet-filtering firewall can, including when a connection was set up, how long it was up, and when it was torn down. This logging makes connections harder to spoof.
Stateful firewalls have the following limitations:
• Stateful firewalls cannot prevent application layer attacks: For example, your network might allow traffic to port 80 on a web server. Your stateful firewall examines the destination address in the Layer 3 packet and the destination port number in the segment. If there is a match, the stateful firewall allows the incoming and outgoing traffic. One problem with this approach is that the stateful firewall does not examine the actual contents of the HTTP connection.
• Not all protocols have a state: UDP and Internet Control Message Protocol (ICMP) do not have a state, so a stateful firewall does not know whether the session is initiating, transmitting, or finishing, as it would with TCP. For example, UDP has no defined process for how to set up, maintain, and tear down a connection. The firewall can provide only limited support for these protocols compared to the thorough information the firewall has regarding, as an example, a TCP connection. Routers define UDP connections on an application-by-application basis.
• Some applications open multiple connections: On earlier (more basic) stateful firewalls, if the client was inside the network and the server was outside the network, both stateful and packet-filtering firewalls had problems dealing with the data connection that the FTP server established to the client. You needed to open a whole range of ports to allow this second connection. Cisco IOS Firewall does not have this problem. The firewall monitors FTP control traffic and discovers information exchanged between the client and the server, which it uses to prepare the data path established from the server in the direction of the client. In this scenario, the firewall is not filtering the traffic at the application layer; it is only reading some purposeful information to prepare for the data. Here we are not talking about application inspection, discussed earlier, where the firewall reads the payload of Layer 7 to assess the FTP commands or some strings found in the FTP payload.
• Stateful firewalls do not authenticate users by default: Stateful firewall technology itself does not mandate user authentication. Add-on functionality is used to provide a feature such as proxy authentication.
Other Types of Firewalls
Over the years, variations of standard stateful firewalls have emerged. Some examples of those variations, which provide additional or restrictive features, are deep packet inspection (DPI) firewalls and Layer 2 firewalls.
Application Inspection Firewalls, aka Deep Packet Inspection
Application inspection firewalls ensure the security of applications and services. Some applications require special handling by the firewall application inspection function. Applications that require special application inspection functions are those that embed IP addressing information in the user data packet or that open secondary channels on dynamically assigned ports.
The application inspection function works with NAT to help identify the location of the embedded addressing information. This arrangement allows NAT to translate embedded addresses and to update any checksum or other fields that are affected by the translation.
The application inspection function also monitors sessions to determine the port numbers for secondary channels. Many protocols open secondary TCP or UDP ports. The initial session on a well-known port negotiates dynamically assigned port numbers. The application inspection function monitors these sessions, identifies the dynamic port assignments, and permits data exchange on these ports for the duration of the specific session.
An application inspection firewall behaves in different ways according to each layer:
• Transport layer mechanism: From a transport layer perspective, the application inspection firewall acts like a stateful firewall by examining information in the headers of Layer 3 packets and Layer 4 segments. For example, the application inspection firewall looks at the TCP header for SYN, RST, ACK, FIN, and other control codes to determine the state of the connection.
• Application layer mechanism: The application inspection firewall checks the conformity of commands within a known protocol. For example, when the application inspection firewall checks the SMTP message type, it allows only acceptable message types on Layer 7 (such as, DATA, HELO, MAIL, NOOP, QUIT, RCPT, and RSET). In addition, the application inspection firewall checks whether the command attributes that are used (for example, length of a message type) conform to the internal rules. These rules often trust the RFC of a specific protocol. Sometimes, application layer firewalls provide protocol support for HTTP, and the application inspection firewall can determine whether the content is really an HTML website or a tunneled application, such as Instant Messaging or GoToMyPC. In the case of a tunneled application, the application inspection firewall would block the content or terminate the connection. Future development will provide application inspection support for more protocols on an application inspection firewall.
There are several advantages of an application inspection firewall:
• Application inspection firewalls are aware of the state of Layer 4 and Layer 5 connections.
• Application inspection firewalls check the conformity of application commands.
• Application inspection firewalls have the capability to check and affect Layer 7.
• Application inspection firewalls can prevent more kinds of attacks than stateful firewalls can. For example, application inspection firewalls can stop an attacker from trying to set up a virtual private network (VPN) tunnel (triggered from inside the network) through an application firewall by way of tunneled HTTP requests.
Transparent Firewalls (Layer 2 Firewalls)
Cisco IOS routers, Cisco ASA Adaptive Security Appliance Software, Cisco Firewall Services Module, and Cisco ASA Services Module offer the capability to deploy a security appliance in a secure bridging mode as a Layer 2 device to provide rich Layer 2 through 7 security services for the protected network, as illustrated in Figure 9-9. This capability enables businesses to deploy security appliances into existing network environments without the need to readdress the network. Although the security appliance can be invisible to devices on both sides of a protected network, as shown in Figure 9-9, administrators can use an exposed IP address to manage the appliance.
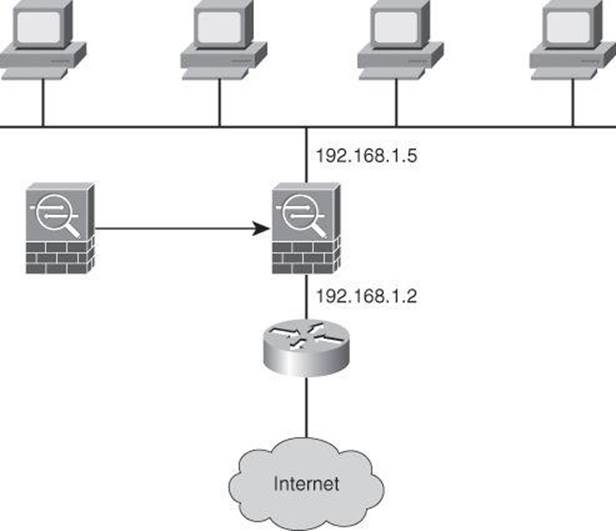
Figure 9-9. Transparent Firewalling: Firewall Interfaces All in the Same Subnet
Note
Layer 2 firewalls, also known as transparent firewalls, are sometimes referred to as bumps in the wire or as stealth firewalls.
Tip
Additional information on transparent firewalls is available in CCNP Security FIREWALL 642-618 Official Cert Guide (Cisco Press).
NAT Fundamentals
As you read earlier in this book, IPv6 will not require NAT. However, at the time of this writing, more than 99 percent of Internet traffic is still running on IPv4. NAT enables private IPv4 internetworks that use nonregistered IPv4 addresses to connect to the Internet. NAT, defined originally in RFC 1631 and enhanced in RFC 3022, operates in routers and other devices to provide address simplification and conservation. Usually, NAT connects two networks and translates the private (inside local) addresses in the internal network into public addresses (inside global) before packets are forwarded to another network, as shown in Figure 9-10. As part of this functionality, you can configure NAT to use only one address for the entire network to the outside world. Using only one address effectively hides the internal network, thus providing additional security.
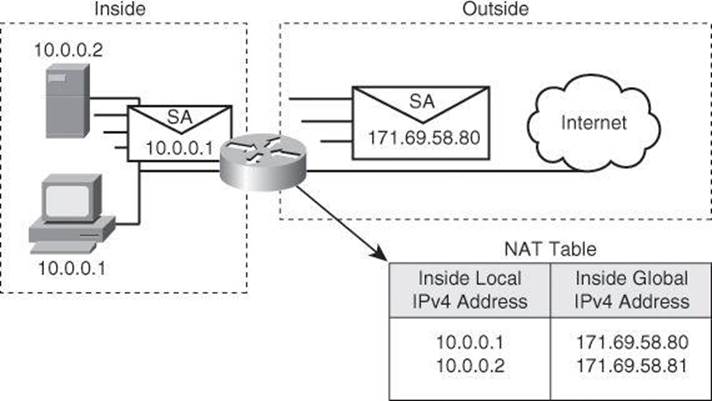
Figure 9-10. Example of Network Address Translation
Chapter 3 mentioned RFC 1918 and the private address space. These private addresses provide a very large pool of addresses to be used inside the corporate network. These addresses, which are not routable, need to be translated for outbound traffic. A common practice is for these inside addresses to be translated by a single public IP address, often the IP address of the outside-facing interface of the firewall. This technique of translating many inside users to one single outside IP address will be discussed later in this chapter.
Multiple device types can be configured to perform NAT services. Although firewalls are most common, routers and Layer 3 switches are also capable of deploying this service.
Cisco defines the following list of NAT terms:
• Inside local address: The IPv4 address that is assigned to a host on the inside network. The inside local address is likely not an IPv4 address assigned by a service provider, but rather one that falls within reserved private IPv4 address spaces.
• Inside global address: A legitimate IPv4 address that is assigned by the network interface card (NIC) or service provider that represents one or more inside local IPv4 addresses to the outside world.
• Outside local address: The IPv4 address of an outside host as it appears to the inside network. Not necessarily a public address, the outside local address is allocated from a routable address space. Outside NAT (NATting the address of an outside entity when it appears on the inside network) is beyond the scope of this book.
• Outside global address: The IPv4 address that is assigned to a host on the outside network by the host owner. The outside global address is allocated from a globally routable address or network space.
NAT offers the following benefits:
• Eliminates the need to readdress all hosts that require external access, saving time and money.
• Conserves addresses through application port-level multiplexing. With NAT overloading, internal hosts can share a single registered IPv4 address for all external communications. In this type of configuration, relatively few external addresses are required to support many internal hosts, thus conserving IPv4 addresses. NAT overload, a term used by Cisco, is often referred to as PAT, which will be covered next.
One of the main features of NAT is dynamic Port Address Translation (PAT), which is also referred to as “NAT overload” in Cisco IOS configuration. PAT allows you to translate multiple internal addresses into a few external addresses, or even a single external address, essentially allowing the internal addresses to share one external address, as shown in Figure 9-11. With NAT overload, as shown in Figure 9-11, as long as the local host uses a unique source port, the router translates only the IP address and not the port. However, in the third entry, host 10.6.1.6 uses source port number 2031, which is already in use by host 10.6.1.2. In this situation, the router translates both source address and source port to create a unique combination that will be used to allow the return traffic to be mapped and translated back to the proper inside host.
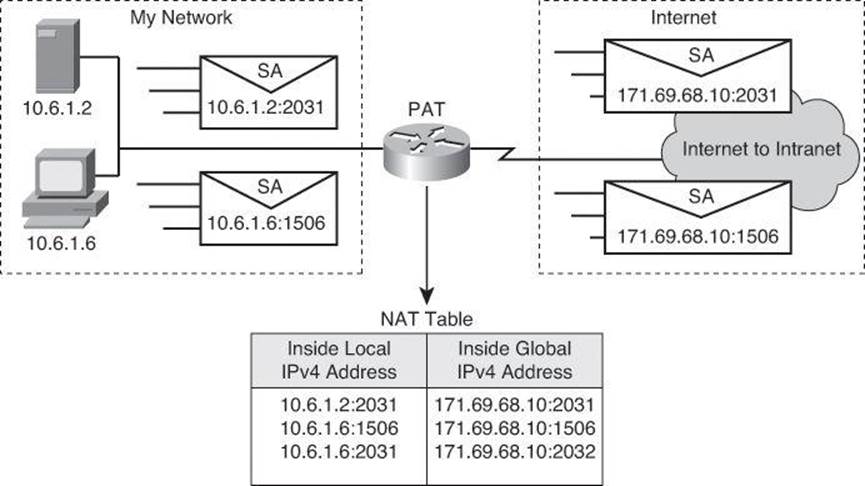
Figure 9-11. Example of Port Address Translation (aka NAT Overload) on Cisco IOS Router
PAT uses unique source port numbers on the inside global IPv4 address to distinguish between translations. Because the port number is encoded in 16 bits, the total number of internal addresses that NAT can translate into one external address is, theoretically, as many as 65,536 minus the 1023 reserved ports, so about 64,000 ports. Port numbers from 0 to 1023 are used for well-known ports and thus typically aren’t used for source ports.
PAT attempts to preserve the original source port. If the source port is already allocated, PAT attempts to find the first available port number. It starts from the beginning of the appropriate port group, 0 to 511, 512 to 1023, or 1024 to 65535. If PAT does not find an available port from the appropriate port group and if more than one external IPv4 address is configured, PAT moves to the next IPv4 address and tries to allocate the original source port again. PAT continues trying to allocate the original source port until it runs out of available ports and external IPv4 addresses.
Dynamic PAT is typically used when translating private addresses into routable Internet addresses, for outbound network traffic. You can configure static or dynamic inside source translation; however, dynamic PAT is typically used because there are not enough global addresses.
Example of Translating an Inside Source Address
Figure 9-12 illustrates a router that is translating a source address inside a network into a source address outside the network. The steps for translating an inside source address are as follows:
Step 1. The user at host 1.1.1.1 opens a connection to Host B.
Step 2. The first packet that the router receives from host 1.1.1.1 causes the router to check its NAT table.
• If a static translation entry has been configured, the router goes to Step 3.
• If no static translation entry exists, the router determines that the source address 1.1.1.1 (SA 1.1.1.1) must be translated dynamically. The router then selects a global address from the dynamic address pool and creates a translation entry (in the example, 2.2.2.2).
Step 3. The router replaces the inside local source address of host 1.1.1.1 with the translation entry global address and forwards the packet.
Step 4. Host B receives the packet and responds to host 1.1.1.1 by using the inside global IPv4 destination address 2.2.2.2 (DA 2.2.2.2).
Step 5. When the router receives the packet with the inside global IPv4 address, the router performs a NAT table lookup by using the inside global address as a key. If dynamic PAT is configured, the lookup includes the destination port as well, which acts as a tiebreaker. The router finds the original host IP address and translates back to the inside local address 1.1.1.1, forwarding the packet to host 1.1.1.1.
Step 6. Host 1.1.1.1 receives the packet and continues the conversation. The router performs Steps 2 through 5 for each packet.
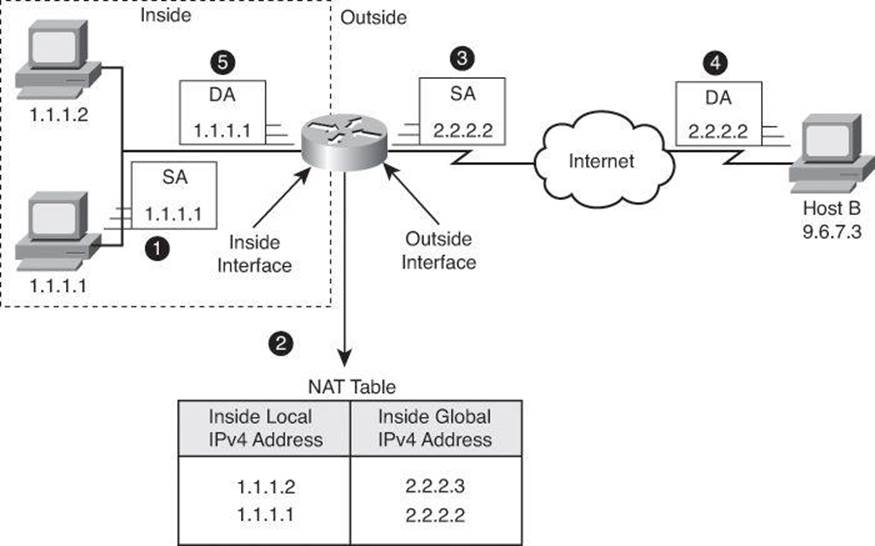
Figure 9-12. Translating Inside Source Address
Inbound access requires a different type of NAT. For servers such as host 1.1.1.1 in Figure 9-13, inbound access from the Internet requires a unique and persistent global IPv4 address. The service must have a known and unique identifier (IP address) for DNS servers to translate the service URL into the same global IPv4 address and make the service reachable.
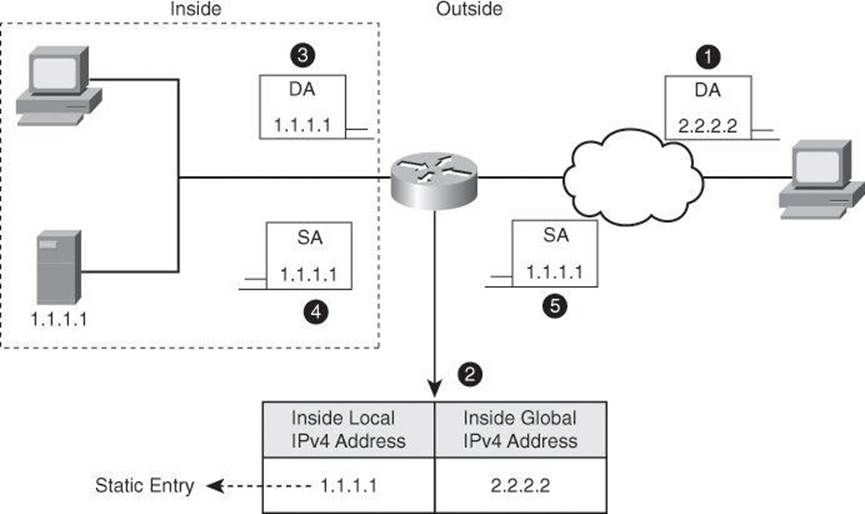
Figure 9-13. Static Translation
For this reason, static NAT is used to manually configure the translation between the known inside local address, in the example 1.1.1.1, and the known global address, in the example 2.2.2.2. This is a static NAT entry that makes all packets be translated:
• A client sends a request, shown in step 1 of Figure 9-13, to 2.2.2.2 which is the public address of the server located inside our network. Upon receiving the packet, shown in Step 2, the router translates the destination address of 2.2.2.2 to 1.1.1.1.
• The router forwards the packet, with the real destination IP address, to the server, as shown in Step 3.
• The server returns its reply with source IP address of 1.1.1.1, shown in Step 4.
• The router looks at its NAT table and finds a static entry for 1.1.1.1 and translates it to its global address of 2.2.2.2 before forwarding the packet to the client, as shown in Step 5.
• Outbound packets, originated by the server 1.1.1.1, find the matching static entry as well, and all packets are translated accordingly.
NAT Deployment Choices
The deployment modes in NAT operations are as follows:
• Static NAT: Maps an unregistered IPv4 address to a registered IPv4 address. One-to-one static NAT is particularly useful when a device must be accessible from outside the network.
• Dynamic NAT: Maps an unregistered IPv4 address to a registered IPv4 address from a group of registered IPv4 addresses. Dynamic NAT is “many-to-many” translation: in this scenario, many inside users are translated to many global addresses. These global addresses are grouped together in a NAT pool. Dynamic NAT is useful for outbound client access, when you have fewer outside global IP addresses than inside local hosts. Each inside user will have a public address that will be assigned and reserved to it for a period of time for NAT.
• Dynamic PAT (NAT overload): Maps multiple unregistered IPv4 addresses to a few or even a single registered IP address (many-to-one) by tracking port numbers and using different ports, if needed. NAT Overload is also known as PAT, and is a form of dynamic translation.
• Policy NAT: Uses ACLs to perform NAT differently based on ACL criteria (for instance source addresses, destination addresses, and ports). A group of hosts might translate to a global address pool when sending traffic to the Internet, while translating to a nonoverlapping private address when sending traffic to remote offices.
• Static PAT: Uses ACLs to perform translation by allowing a specific UDP or TCP port on a global address to be translated to a specific port on a local address. That is, both the address and the port numbers are translated. This is referred to as port forwarding on home routers, such as Linksys models.
Note
PAT is not implemented in exactly the same way in Cisco IOS and Cisco ASA. In Cisco IOS, PAT translates the source port only if needed. With Cisco ASA, the source port of an outbound connection is always translated to a randomly generated port number.
Firewall Designs
Ultimately, firewalls are referred to as firewall systems because they implement access control using multiple technologies. These technologies might even be implemented in different physical devices. When planning your firewall system, it is important to enable and use the firewall technologies that match your security requirements.
Typically, stateful packet filtering is the building-block technology. Stateful packet filters are good central access control components. Access rules are created for Layer 3 and Layer 4 criteria to define which traffic classes can traverse the firewall. These access rules define the first level of trust relationships that are enforced through the firewall.
As you design the access rules, other firewall technologies will be necessary. Application layer inspection expands matching criteria and access control actions to upper layers, providing an additional level of security. Proxy services, including user authentication, allow for user-based rules that result in more granular and context-aware access control.
Best practices documents are a composite effort of security practitioners. This partial list of best practices is generic and serves only as a starting point for your own firewall security policy:
• Position firewalls at key security boundaries, separating security domains with different levels of trust.
• Firewalls are the primary security device, but it is unwise to rely exclusively on a firewall for security.
• Deny all traffic by default and permit only services that are needed.
• Implement various firewall technologies, matching your application mix and security policy requirements.
• Ensure that physical access to the firewall is controlled.
• Regularly monitor firewall logs. Cisco Security Manager and other Cisco management tools are available for this purpose.
• Practice change management for firewall configuration changes.
Remember that firewalls primarily protect from technical attacks originating from the outside. Inside attacks tend to be nontechnical in nature.
Firewall Policies in a Layered Defense Strategy
Firewall access rules are the building blocks for access control. An enterprise firewall could have hundreds if not thousands of rules. Access rule creation, management, and auditing are critical to implementing a sound security posture effectively and efficiently. Too many redundant rules might result in performance degradation. Ineffective or obsolete rules might result in trust exploitation and security breaches.
When defining access rules, multiple criteria can be used as a starting point:
• Rules based on service control: Determine the types of Internet services that can be accessed, inbound or outbound. The firewall may filter traffic based on IP address and TCP port number. It may provide proxy software that receives and interprets each service request before passing it on. It may host the server software itself, such as a web or mail service. An example of a rule based on service control would be: allow HTTP, allow HTTPS, deny everything else.
• Rules based on direction control: Determine the direction in which particular service requests may be initiated and allowed to flow through the firewall. An example of a rule based on direction control would be: allow HTTP outbound, but not inbound.
• Rules based on user control: Control access to a service according to which user is attempting to access it. This feature is typically applied to users inside the firewall perimeter (local users). It may also be applied to incoming traffic from external users. The latter requires some form of secure authentication technology, such as is provided in IP Security (IPsec). An example of a rule based on user control would be: allow campus VLANs HTTP access, deny it for wireless VLANs.
• Rules based on behavior control: Control how particular services are used. For example, the firewall may filter email to eliminate spam, or it may enable external access to only a portion of the information on a local web server. An example of a rule based on behavior control would be open negotiated FTP ports after learning them during connection setup.
Typically, a combination of these criteria is used to define restrictive policies that permit only the required traffic, while blocking anything else.
Access rules are typically implemented using ACLs. That is the case with Cisco IOS and Cisco ASA firewalls. For that reason, access rules are effectively ordered lists of permit and deny statements, applied to specific interfaces, as represented in Figure 9-14.
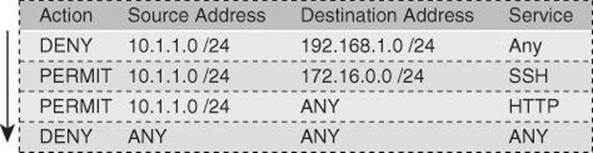
Figure 9-14. Firewall Access Rule Structure: Top-Down Process
The ruleset is evaluated sequentially from the top, and the rule that first matches the new connection is evaluated, permitting or denying the connection. When a rule matches a connection, all subsequent rules are ignored.
Because rules use ACLs, there is an implicit deny-all rule at the end of the list. If a connection does not match any of the rules, by default, it will be denied.
Firewall Rules Design Guidelines
When creating firewall rules, use the following guidelines:
• Use a restrictive approach, as opposed to a permissive approach, for all interfaces and all directions of traffic. This translates into simple rulesets that permit the required traffic flows and deny everything else.
• The previous guideline implies that you should take a somewhat paranoid stance and assume that malicious traffic could come from any security domain, even the most trusted ones. This stance results in outbound rules becoming as important as inbound rules, even though they apply to “trusted” internal traffic.
• A tradeoff should be made between access control, performance, and rule maintenance. Specific and granular rules provide more control over the allowed or denied traffic, but also result in longer rulesets and more change-management and maintenance challenges. Observe the use of any keywords matching sources, destinations, and ports, as they may allow unwanted traffic.
• For a given access requirement, more specific rules should be pushed to the top, while more generic rules should be pushed to the bottom. The top-down processing order demands this approach to prevent shadow rules when creating exceptions to a given access policy.
• Filtering impossible packets is a common practice. An example is antispoofing rules that are aimed at blocking private IPv4 address spaces in the source address of inbound Internet packets.
• Auditing and change management are crucial. Obsolete rules tend to clutter the ruleset and cause breaches to the access policy.
Lack of a formal methodology for rule creation and maintenance often results in issues that affect the security posture or the ability of the firewall to process traffic.
These issues are, among others, based on consistency, completeness, and compactness. Consistency issues result in potential security breaches.
The following is a list of potential consistency issues with firewall rules:
• Promiscuous rules: Allow more access than necessary to meet access requirements. An example is the use of any keywords in ACLs, allowing access from all IP addresses when access is only necessary from a single subnet. Another example is a rule that allows access to a system on multiple ports when only a subset of those ports is required.
• Redundant rules: Result when a given rule duplicates a portion of the access that is permitted or denied by another rule. An example is a rule that allows a single IP address to access a server on a particular TCP port when an existing rule already allows all IP addresses to access that port. Another example is a rule that allows access to a port on a host when other rules allow the same type of access due to the membership of the port in a service group.
• Shadowed rules: Result when the incorrect ordering of rules in the ruleset completely prevents the execution of one or more firewall rules. An example is configuring a rule that denies access to a particular website below a rule that allows access to all websites. Another example is placing a rule that allows access to a server on a single port from a single IP address below a rule that blocks all access to the server from all IP addresses. The existence of the first rule would shadow the second rule, rendering it useless.
• Orphaned rules: These are rules that exist in the firewall ruleset but never match traffic passing through the firewall. An example is a rule designed to allow access to a database server that incorrectly specifies a nonexistent destination IP address. Another example is a rule designed to allow HTTP access to a server that no longer hosts a website.
Tip
Here’s a trick used by David Chapman, a technical reviewer on this book: to discover orphan rules, reset access list counters on the first of each month. At the end of the month, check which ACL entries still have their counters at zero, and flag these entries for removal.
Completeness issues might also result in security breaches:
• Errors in rule specification: Include errors that are made in the translation between business requirements and technical or product-specific firewall rules. Sometimes, the rules simply do not meet business requirements due to a misunderstanding about business requirements. Other times, firewall administrators fail to specify a rule necessary to meet business requirements. Specifying the incorrect port for a service is an example, such as creating a rule for port 8080 when the business requirement called for standard port 80 for the HTTP service.
• Data entry errors: Include errors made when converting a technical rule definition into the firewall policy format and entering that rule into the firewall rule base. An example would be mistyping a port number, such as creating a rule for port 23 when the technical specification indicated port 53. Another example would be mistyping a source or destination address or failing to input a rule included in the technical specification.
Compactness issues typically result from obsolete rules, too much granularity, or an informal approach to defining the order of rules within the ruleset. These issues affect performance and, therefore, the ability to provide firewall services effectively. The firewall evaluates the rules inefficiently, often matching traffic flows after hundreds if not thousands of rules have been unnecessarily evaluated.
Summary
In this chapter, you have learned that a firewall is a set of rules designed to enforce an access control policy between two networks. You learned how to create firewall rules to implement your security policies. You also learned that firewall systems are a combination of packet filtering, stateful inspection, application layer inspection, and other technologies. You saw that NAT is a complementary technology to firewalling and that it allows for dynamic and static translations.
You saw that change management, ruleset auditing, and monitoring are critical firewall design considerations and that common issues found in firewall rule design include promiscuous rules, redundant rules, shadowed rules, and orphaned rules.
References
For additional information, refer to these resources:
Cisco Systems, Inc. “Configuring Network Address Translation: Getting Started,” http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080094e77.shtml.
Mason, Andrew. Cisco Firewall Technology (Cisco Press, 2007).
Review Questions
Use the questions here to review what you learned in this chapter. The correct answers are found in the Appendix, “Answers to Chapter Review Questions.”
1. Which of the following are firewalls? (Choose all that apply.)
a. Static packet filters
b. URL filters
c. Application layer gateways
d. Layer 2 switches
2. Stateful packet-filtering firewalls are good to use for all the following applications except:
a. As a primary means of defense
b. As an intelligent first line of defense
c. To sanitize web traffic of malware
d. As a means of strengthening packet filtering
e. To improve routing performance
3. Match the following names and characteristics:
Names
a. Packet-filtering firewalls
b. Application layer gateways
c. Stateful packet filters
d. Application inspection firewalls
Characteristics
1. Work primarily at the network level of the OSI model
2. Are the most common firewalls
3. Monitor sessions to determine the port numbers for secondary channels
4. Were the first application layer firewalls
4. Which threats can be mitigated using ACLs? (Choose all that apply.)
a. Malicious payloads
b. Spam
c. ICMP message filtering
d. IP address spoofing
5. Cisco IronPort Web Security Appliance is an example of which of the following?
a. Stateless packet filter
b. Application layer gateway
c. Stateful packet firewall
d. Intrusion detection system
6. Match the following translation definitions and characteristics:
Translation types
a. Static NAT
b. Dynamic NAT
c. Dynamic PAT
d. Policy NAT
Characteristics
1. Translation depends on both source and destination
2. Translation is many-to-many
3. Translation is one-to-one
4. Translation is many-to-one
7. Match the following bases of firewall access rules with the examples:
Basis of firewall access rules:
a. Service control
b. Direction control
c. User control
d. Behavior control
Firewall access rules examples
1. Allow HTTP outbound, but not inbound
2. Allow campus VLANs HTTP access, deny it for wireless VLANs
3. Open negotiated FTP ports after learning them during connection setup
4. Allow HTTP, allow HTTPS, deny everything else