Implementing Cisco IOS Network Security (IINS) Foundation Learning Guide, Second Edition (2013)
Part I: Networking Security Fundamentals
Chapter 2. Security Strategy and Cisco Borderless Network
In this chapter, you learn about the Cisco vision of a security strategy for Cisco Borderless Networks. You read about the architecture, components, and underlying technologies, and see Cisco products and solutions within the architecture.
In this chapter, you learn about the following Cisco Borderless Networks topics:
• Cisco Borderless Network Architecture
• Cisco security portfolio of products solving issues of Borderless Networks
• Cisco SecureX Architecture presenting its features and benefits
• Cisco threat control and containment products and technologies
• Cisco content security products and technologies
• Cisco VPN solutions and technologies
• Security management products and technologies
Borderless Networks
Borders are dissolving in multiple dimensions in current networks.
The device border is being dissolved by the phenomenon of mobility. Expect to see billions of new network mobile devices moving into enterprises worldwide over the next few years. If you consider constant reductions and streamlining in IT budgets, organizations face serious challenges to support a growing number of mobile devices at a time when resources are being reduced.
The application border is also dissolving. This is driven by market forces in cloud computing and cloud services. Organizations of all kinds are taking advantage of offerings such as Software as a Service (SaaS) and Infrastructure as a Service (IaaS) to reduce costs and simplify the deployment of new services and applications. These cloud services add challenges in visibility (how do you identify and mitigate threats that come to and from a trusted network?), control (who controls the physical assets, encryption keys, and so on?), and trust (do you trust cloud partners to ensure that critical application data is still protected when it is off the enterprise network?).
The location border is being blurred by constant changes to the workplace experience and millions of professionals that engage in work-related activities equally from home, the office, or while traveling. Borders are blurring in the organization as well, between consumers and workers and between the various functions within the organization. The borders between the company and its partners, customers, and suppliers are also fading. As a result, the network is having an increasing demand to connect anyone, anything, anywhere, at any time.
Taken together, these trends are driving consistent innovation of network-based business processes as the Internet morphed from a network to a platform for integrating supply chains, exchanging information for business intelligence, outsourcing entire business functions, and establishing new relationships. This trend will only accelerate as cloud computing matures.
The market changes also represent a challenge to security teams within the organization. They now need to manage uncontrolled consumer devices coming into the network, and provide seamless and context-aware services to users all over the world. The location of the data and services they access is almost irrelevant. Their location could be internal to the organization, or it could be in the cloud. This makes protecting data and services a challenging proposition.
The paradigm of access anytime, anywhere, using any device changes the network management approach that has traditionally been used to design and maintain networks. Scalability, availability, performance, and other metrics become much more complex as the IT organization moves beyond the infrastructure it can directly control. These metrics are no longer linear, but multidimensional. IT organizations need to manage the same metrics, but across the device, the application, and the location border.
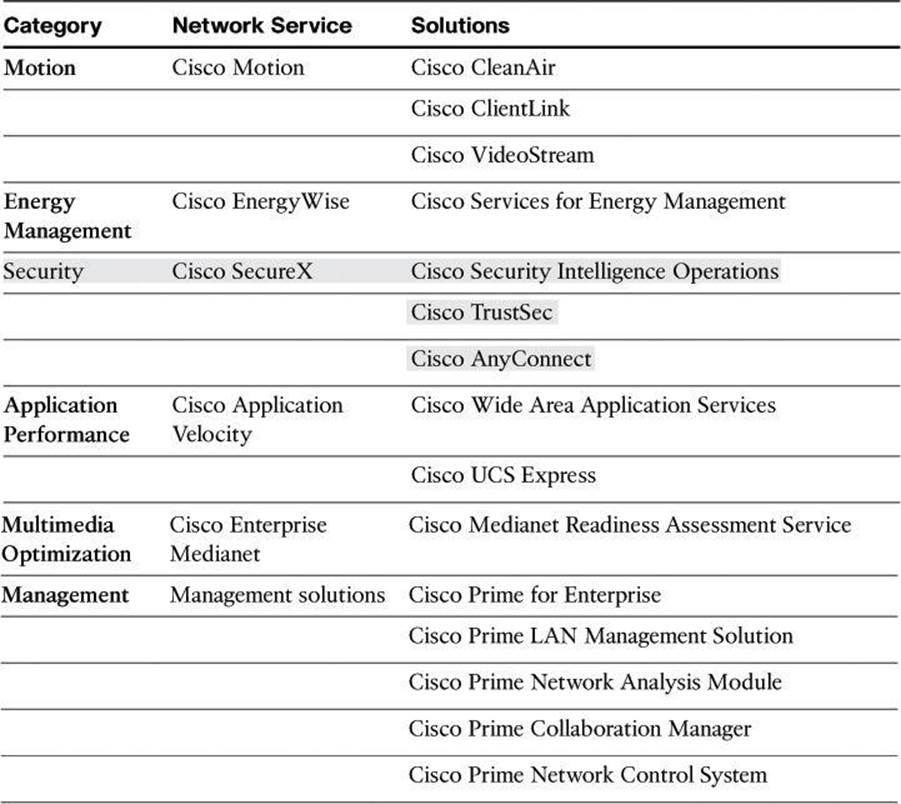
Cisco Borderless Network Security Architecture
The Cisco Borderless Network Architecture, shown in Figure 2-1, addresses these issues using a comprehensive set of integrated components:
• Borderless end zone: Implemented by security controls aimed at protecting end devices and preventing intrusion to and from those end devices. Malware, viruses, and other types of malicious code are commonplace. The borderless end zone is built to detect these threats and eradicate them, or at least mitigate them, even before users connect to the network. As users connect from multiple locations, the network reacts to suspicious behavior by controlling access based on the security posture of the connecting endpoint. This reaction mitigates the impact of endpoint-based threats and helps contain their effect in a cost-effective manner.
• Borderless Internet: Implemented by scanning and enforcement engines, which are deployed onsite and offsite and managed by the organization itself but also by cloud providers. These scanning and enforcement engines inspect network content from Layer 2 through Layer 7, assuming the role of firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS), network proxies, web gateways, and so on. These engines are located throughout the corporate network, but also rely on cloud-based services for security intelligence, real-time updates, and scanning support for mobile users, remote offices, and public network-resident devices such as network sensors or supervisory control and data acquisition (SCADA) systems.
• Borderless data center: Data centers deserve special attention in a cloud-driven business environment. The Cisco Borderless Network Architecture leverages existing infrastructure components such as Cisco Adaptive Security Appliances (ASA), IPS sensors, and switching components such as Cisco Catalyst and Cisco Nexus switches, layering virtualized components on top to provide security solutions that are built for “in the cloud” deployment, “by the cloud” deployment, and “for the cloud” deployment.
• Policy management layer: Security policy is managed in central locations and then enforced throughout the network based on context-specific variables. When an employee on an untrusted network in Moscow checks email via Outlook Web Access (OWA), that employee can view messages but is precluded from downloading attachments.
• Borderless Network Services: Professional and technical services are provided by Cisco and its partners. Cisco and its partners help an organization achieve the full benefits of the deployment of the Cisco solutions by providing consulting services in areas such as wireless, unified communication, data center, and, of course, network security, to name a few.
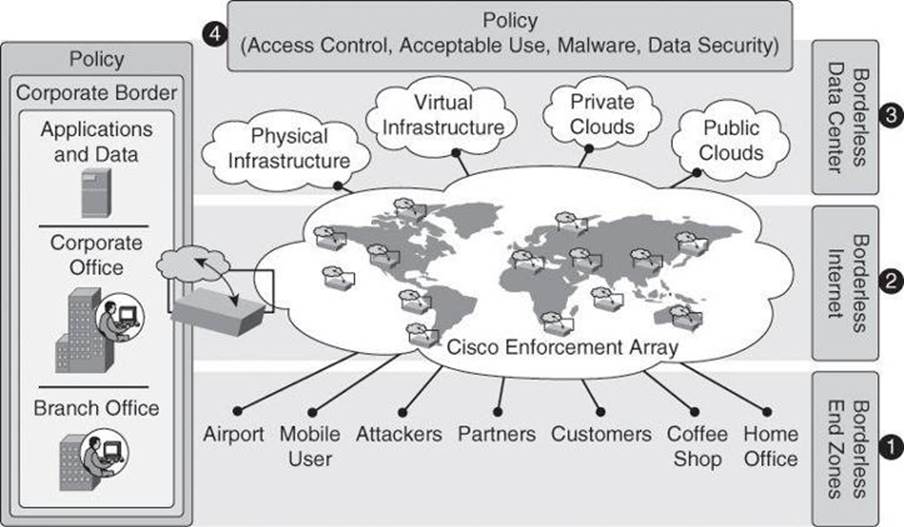
Figure 2-1. Cisco Borderless Network Security Architecture
The type of distributed, shared security intelligence, in the form of log files, vulnerability scanning data, system configuration, and event data, is available on a “publish and subscribe” basis in industry-standard formats. Additionally, onsite security information is supplemented by security telemetry in the cloud. All of this data will be available to analysts for event detection and forensics, but the network will also consume this data itself in order to react to anomalies, enforce policies, or block attacks in real time.
Borderless End Zone
Each major component of the architecture results in specific benefits. The borderless end zone offers deployment flexibility and strong security services in multiple dimensions as users connect to the network.
PCs and mobile devices are active participants in borderless network security in several ways. In borderless security, all endpoints authenticate themselves to the organization’s network and submit to a health and configuration check before gaining access. This is true for employees and third-party users. Once admitted to the network, endpoints and users are given access to specific applications and data based upon parameters such as user role, location, time of day, and so on. This does not require multiple authentications. Rather, the network understands whether a user is working from an office desk, from a home PC, or from an untrusted network around the world and enforces policies for access controls, data confidentiality, and encrypted transport accordingly. Finally, endpoints continue to have onboard security defenses, but this will evolve from current fat client software to a cloud-based model—especially for mobile devices with limited resources.
The Cisco AnyConnect client is one of the building blocks of this architectural component, providing multiple layers of defense even before users connect to the network, leveraged around Secure Sockets Layer (SSL) VPNs.
Figure 2-2 provides a summary of the advantages of the borderless end zone. Many of the concepts presented in this figure are beyond the scope of this book but are explored in greater details in other Cisco literature and courses.
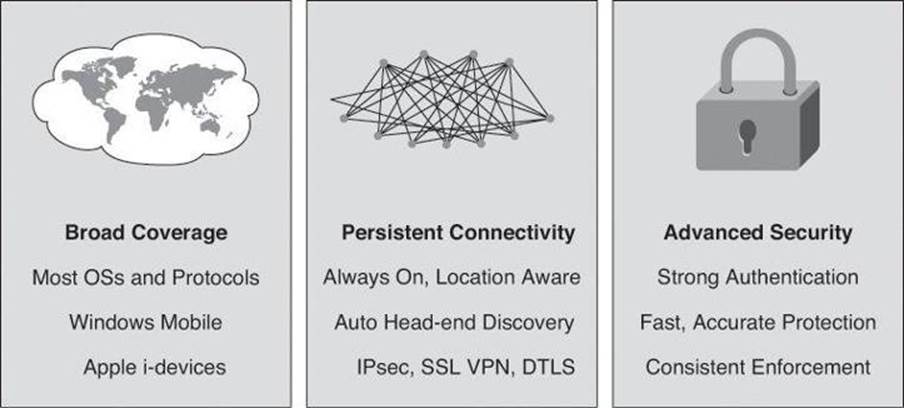
Figure 2-2. Borderless End Zone Advantages and Technologies
The other side of the equation is represented by enforcement engines that make up the security array. Cisco has a strong security product line that includes firewalls, IPSs, web security, and email security. These detection and enforcement engines are evolving in two ways:
• They are built to be highly scalable and interpret and control traffic at the application level. This capability allows the network to catch up with malicious attackers, who are increasingly utilizing application layer threats to perpetrate their plans.
• They are available in multiple forms: appliance, module in a switch, or router and hybrid hosted.
Borderless Internet
The combination of intelligent endpoints and an array of scanning and enforcement engines makes the network work as a system with integrated, collaborative, and adaptive security. This is a sharp contrast with a point product approach, where function-specific products create “islands of security” constrained by independent threat, systems, and policy management. These disparate point tools are antithetical to the dynamic and integrated security that is required for borderless networks to fulfill the “any user, any content, any location, any time” nature.
The Cisco Borderless Network Architecture demands teamwork and cooperation akin to that of a symphony orchestra, where all of the individual “instruments” come together to achieve a common goal, as shown in Figure 2-3.
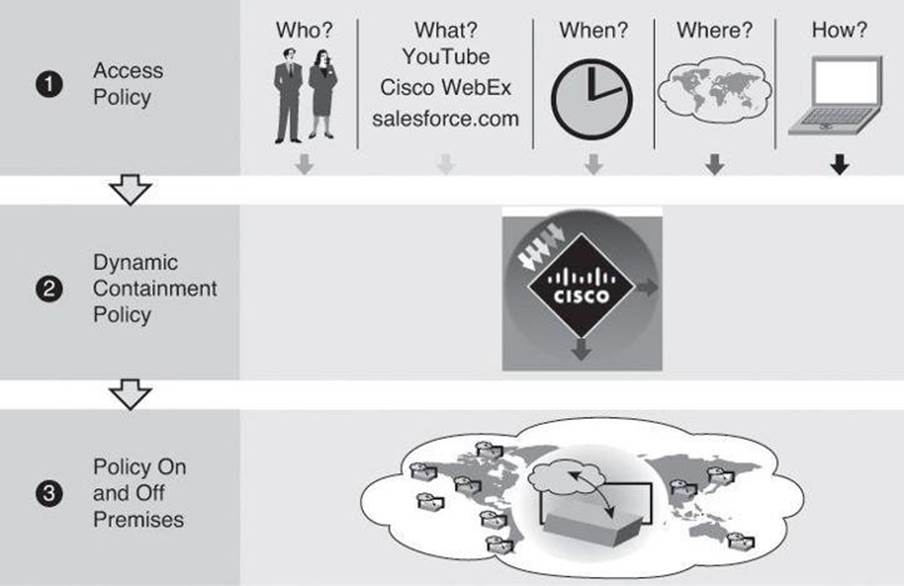
Figure 2-3. Intelligent Access Policies Provides Context Awareness for Adaptive Securing of Endpoints
Given the “borderless” aspect of Borderless Networks, security defenses must also extend beyond the enterprise network to mobile devices and cloud services. Using the Cisco Borderless Network Architecture, corporate LANs and WANs coordinate activities with service provider networks, distributed endpoints, and the Internet itself. No one vendor has all of the security products or resources to solve this challenge alone. Borderless network security requires industry ingenuity and collaboration. Cisco partners with leading security and networking vendors to extend the reach of the system beyond the confines of corporate networks.
Borderless Data Center
The borderless data center component of the architecture provides solutions that adjust to data center environments. Figure 2-4 illustrates the progression of service deployment in a heavily virtualized environment, such as that of data center.
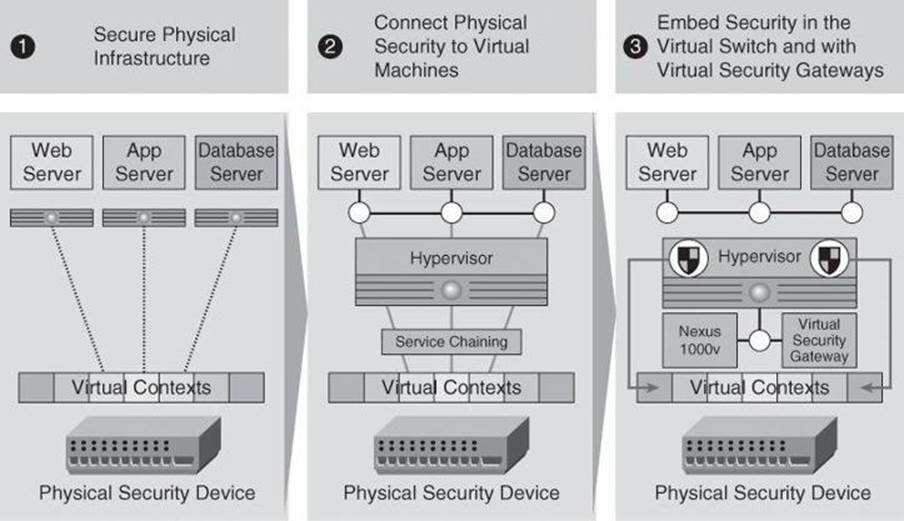
Figure 2-4. Evolution of Security in the Data Center
Virtual appliances provide trusted access to virtualized data centers in enterprise and cloud provider environments while meeting virtualization requirements of dynamic policy-driven operation, mobility-transparent enforcement, and scale-out deployment for dense multitenancy, where one service provider might be hosting for multiple different clients. But it does not stop there. Network connectivity is also virtualized and embedded into virtual machines. Virtual switches connect virtual machines within a single physical device, integrating network switch ports into the hypervisor.
An example of this architecture is the Cisco Virtual Security Gateway (VSG), a security virtual appliance that leverages the Cisco Nexus 1000V switch to provide zone-based trust services to virtual machines. Cloud providers can leverage the Cisco VSG to significantly enhance their multitenant scaling and also generate additional revenue by offering security and monitoring services to their customers. In effect, the Cisco VSG enables a broad set of multitenant workloads having varied security profiles to share a common compute infrastructure on premises (in the enterprise virtual data center and private cloud) or off premises (in the service provider cloud). By associating one or more virtual machines (VM) into distinct trust zones, the Cisco VSG ensures that access to trust zones is controlled and monitored through established security policies.
Policy Management Layer
The policy management layer is a higher-level function that can span multiple operational devices. Cisco’s vision is to make the interface between policy and enforcement systems open and built on industry standards. Therefore, if a customer chooses to use a Cisco application entitlement system and an enterprise data loss prevention (DLP) policy manager from RSA, both should work smoothly with existing network infrastructure. This significantly reduces operational complexity for Cisco customers because one set of policies can be enforced across a wide variety of infrastructure.
Borderless Network Services
Cisco Borderless Network Services covers many areas listed in Table 2-1. However, our focus for this book is restricted to the security solutions. Table 2-1 provides only a restricted list of SecureX core components. SecureX solutions and components will be presented in the next section of this chapter.
Table 2-1. Cisco Borderless Network Services
Borderless Security Products
The architectural approach to security found in the Cisco Borderless Network Architecture, shown in Figure 2-5, results in distinct categories of Cisco products, technologies, and solutions. These product categories are built into the design of borderless network security and apply to multiple components of the architecture. For instance, a Cisco ASA can be found as an on-premises scanning engine in the borderless Internet component, but also as a firewall in the borderless data center.
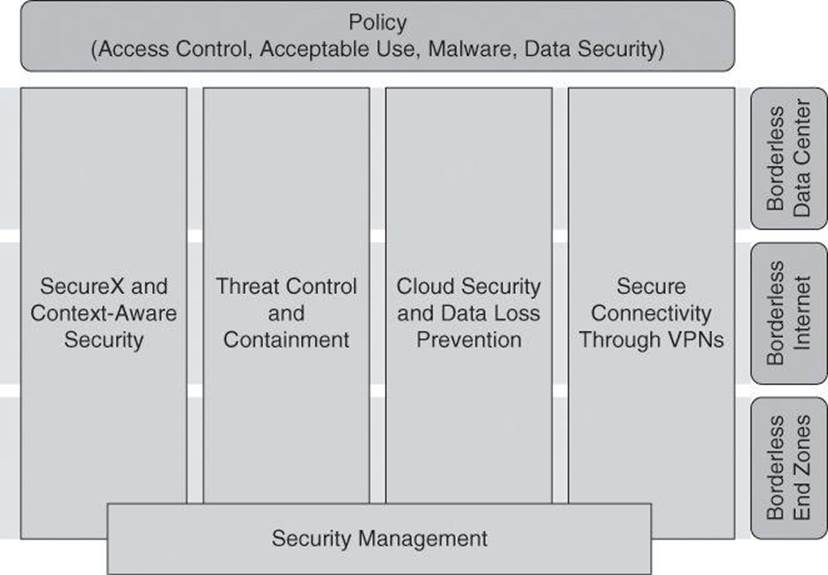
Figure 2-5. Policy Management Provided by Cisco Borderless Security Products
In the following sections, we look at the pillars of security found in the Cisco Borderless Network approach.
SecureX, a Context-Aware Security Approach
Cisco SecureX is an access control strategy that allows for more effective, higher-level policy creation and enforcement for mobile users, connecting from anywhere, at any time, using any device. Because Cisco SecureX uses a broad array of parameters for policy, it allows for much more effective security and enables situational awareness, as represented in Figure 2-6. Instead of many complex firewall rules, security policy can now be based on context. For example, a salesperson accesses a global sales forecast from her laptop while in California; when she attempts to access that same sales forecast from the business center of the hotel where she is staying in China, the computer used is not detected as a corporate asset, and the request would be disallowed.
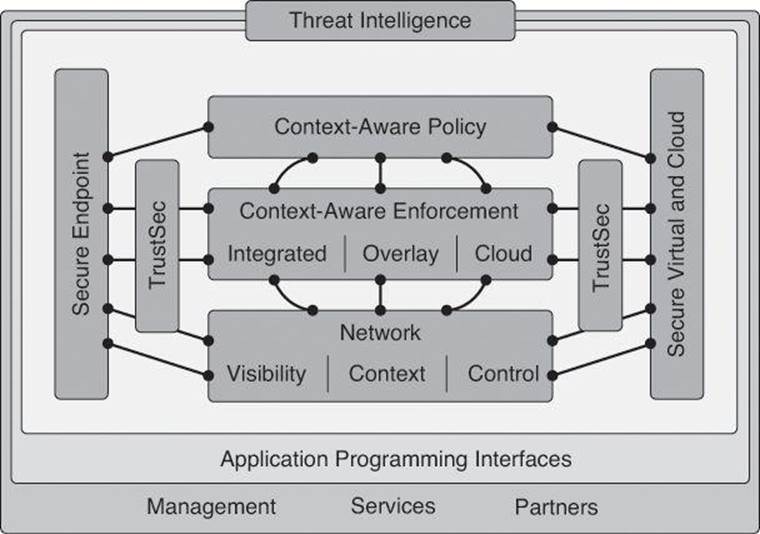
Figure 2-6. SecureX Context Awareness
This sort of intelligent policy enforcement uses next-generation scanning elements that are meshed into the new Cisco SecureX Architecture. Within this new architecture, the next-generation endpoint is able to automatically find the nearest scanning element somewhere in the virtual security fabric and to make a seamless connection. The behavior of a hacker halfway around the world is noted, that information is shared, and traffic from the servers of the hacker is blocked because your network now knows that it comes from someone that it cannot trust. Policy is centrally managed, but intelligence is gathered globally, with highly distributed enforcement.
Table 2-2 provides a list of Cisco security solutions that are part of the Cisco SecureX Architecture as presented in the Cisco SecureX product brochure.
Table 2-2. Cisco SecureX Security Products
SecureX Core Components
To enforces security policies across the entire distributed network, not just at a single point in the data stream, SecureX relies on the following core components.
Context-Aware Policies
At the core of the Cisco SecureX Architecture is context awareness, which allows enforcement elements (such as firewalls, web proxies, IPS sensors, and even network infrastructure elements such as routers and switches) to define the access policy by using information such as the identity of the user, the security posture of the connecting device, the point of access to the network, and many other components.
Cisco Security Intelligence Operations (SIO)
Many of the Cisco security products listed in Table 2-2 stay ahead of the latest threats by using real-time threat intelligence from Cisco Security Intelligence Operations (SIO). Cisco SIO is the world’s largest cloud-based security ecosystem, using almost a million live data feeds from deployed Cisco email, web, firewall, and IPS solutions. Cisco SIO will be discussed further later in this chapter.
TrustSec
Cisco TrustSec relies on context awareness to enforce policy and at the same time provide access flexibility and situational access control.
Traditional access control parameters, such as the user identity, are considered. The user identity is the base component that the network gathers to initiate the determination of context. IEEE 802.1X is typically used to define the identity of those entering the network. Nonauthenticated devices, such as IP phones and printers, are also considered.
Other conditions are gathered from the Cisco AnyConnect client and the array of enforcement devices. Allowing an employee with high security clearance into the network on a weekday, using an uninfected corporate laptop from a campus office wired network, is not the same as allowing the same person (same identity) on a weekend evening to use an unknown PC, possibly infected with a virus, from a hotspot Internet café. AnyConnect and the device at the point of entry to the network determine this information.
The result is a different access policy and conditions that are based on the situational context of connectivity of individuals and devices, as illustrated by Figure 2-7.
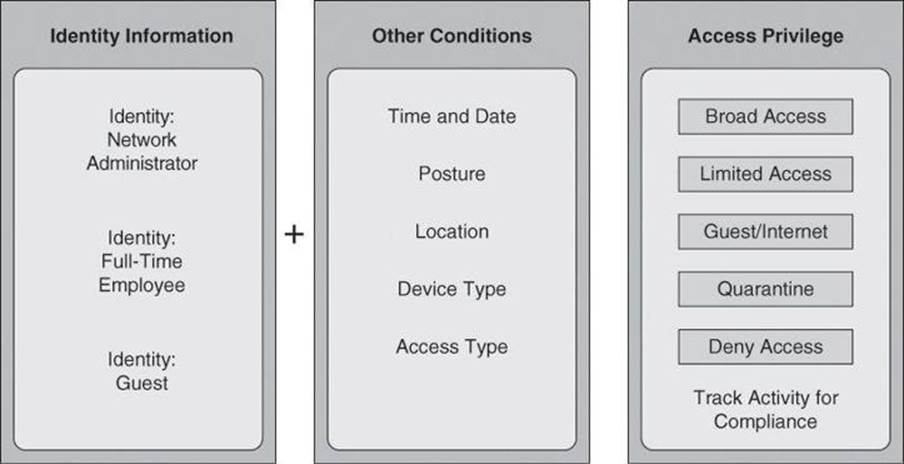
Figure 2-7. Context-Aware Policies Decide Access Privileges
The same individual might be allowed into corporate resources with broad access under certain conditions, while forced into a quarantine area to update the antivirus software or unlock a user password under other conditions. The network, as a system, adapts to each circumstance.
So, as explained above, Cisco TrustSec extends context awareness through policy-based access control for any user and any device seeking access to the distributed network. Figure 2-8 illustrates the components of this function.
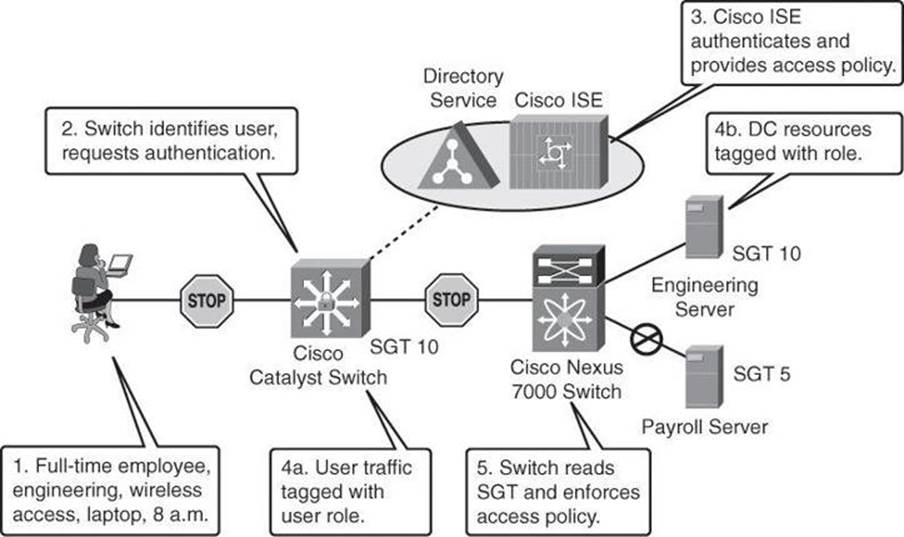
Figure 2-8. Secure Resources Using TrustSec
First, users are authenticated and authorized based on who, what, where, when, and how. Endpoint devices are also analyzed to determine if they meet corporate security policy before being granted access. Nonauthenticating devices, such as IP phones or video cameras, are also automatically identified and inventoried. Note that more and more endpoint devices, such as network printers, are 802.1x capable.
Next, traffic from any authenticated device is tagged with a unique, context-based access policy marker known a security group tag (SGT). Network devices along the data path read this tag and enforce its associated policy by restricting access to predetermined network destinations and resources. The devices do so by using security group access control lists (SGACL).
Finally, Cisco TrustSec provides data confidentiality. This is known as MAC Security (MACsec). For example, a policy may require that any employee from the finance department accessing the payroll server must have their data secured. Cisco TrustSec understands this policy and can direct the network to dynamically encrypt the data of the user.
In summary, TrustSec restricts user access using Security Group Access (SGA). Access policy is inserted as SGTs into devices. The SGA reads and enforces policy tags on TrustSec-enabled Cisco switches along data paths using SGACLs.
AnyConnect
The Cisco AnyConnect client provides a secure connectivity experience across a broad set of PC- and smartphone-based mobile devices. The enforcement devices provide posture assessment, access control services, and policy enforcement. They also start the encryption process to provide confidentiality via MACsec.
The Cisco AnyConnect Secure Mobility Solutions provide an innovative way to protect mobile employees on PC-based or smartphone platforms. These solutions use SSL or IP Security (IPsec) VPNs to deliver a more seamless, always-on, and always-protected experience to end users, while enabling IT administrators to enforce policies and block malware with cloud-based or hybrid web security. Cisco AnyConnect Secure Mobility is available to computers, tablets, and smartphones. For a complete list of Cisco AnyConnect Secure Mobility Client for Mobile Platforms, visit http://www.cisco.com/en/US/prod/collateral/vpndevc/ps5743/ps5699/ps10884/datasheet_c78-678242.html.
The Cisco AnyConnect Secure Mobility Client is a lightweight, highly modular security client that provides easily customizable capabilities. The client provides broad operating system support from traditional operating systems such as Windows and Linux, to mobile devices such as smartphones and tablets (Apple iOS, Windows Mobile, Android, and others), as illustrated in Figure 2-9.
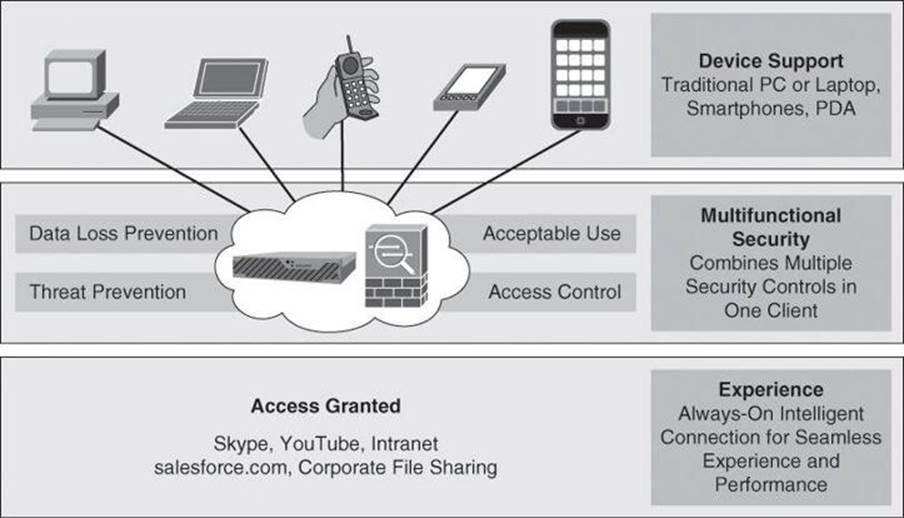
Figure 2-9. AnyConnect at Work
Cisco AnyConnect provides an always-on solution that finds the nearest enforcement element and enforces multiple types of policies. This includes the use of SSL and IPsec VPNs (IKEv2 only), 802.1 X authentications and authorization, Cisco Network Admission Control (NAC), and other posture and enforcement elements. Using this consolidated client, the network implements data loss prevention, threat prevention, acceptable use policies, and access control mechanisms, all with one lightweight client that eliminates the need for multiple software elements enforcing individual security controls.
Cisco Identity Services Engine
Cisco Identity Services Engine (ISE) is the centralized policy engine for business-relevant policy definition and enforcement. Cisco ISE complements global contextual information that is offered by Cisco SIO, with localized context awareness provided by Cisco AnyConnect and the scanning and enforcement elements for effective access policy enforcement.
Cisco ISE combines the functionality of other Cisco products, such as the Cisco Secure Access Control Server for authentication, authorization, and accounting (AAA) services and Cisco NAC, into this next-generation policy server.
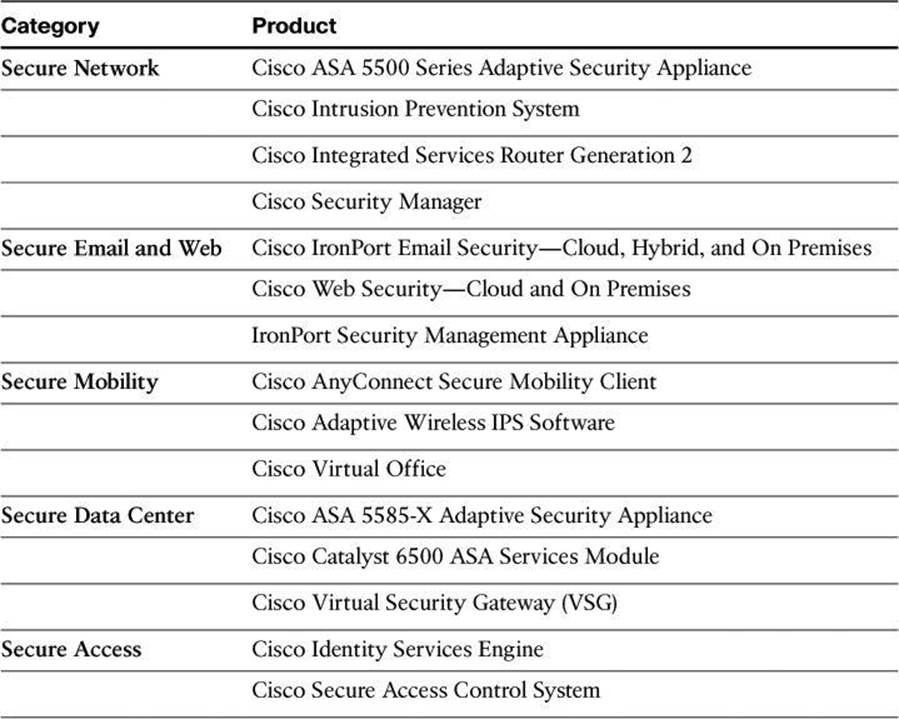
Threat Control and Containment
The Cisco threat control and containment solution offers comprehensive protection for your network through network-wide visibility, simplified policy control, and proactive system protection. The Cisco threat control and containment solution regulates network access, isolates infected systems, prevents intrusions, and protects critical business assets. This solution counteracts malicious traffic such as worms, viruses, and malware before it affects your business, by using centralized policy, configuration, and threat event management.
Threat prevention products have been a flagship of Cisco security for a long time. Integrated security controls found in Cisco Adaptive Security Appliance (ASA), Cisco Integrated Services Routers (ISR), and IPS sensors provide a multidimensional approach to detecting, mitigating, and responding to threats at various levels.
• Cisco ASA: Cisco ASAs provide proven firewall services and context- and application-aware capabilities for comprehensive, real-time threat defense. ASAs implement a truly unified threat management service, with the integration of VPN and intrusion prevention technologies in various forms.
• Cisco ISRs: Through software- and hardware-integrated security functions, ISRs can easily become part of the army of security controls in networks of all kinds. These functions include zone-based policy firewall, Cisco IOS IPS, and the integration of SSL and IPsec VPN technologies.
• Cisco IPS: Intrusion prevention is accomplished in a distributed fashion, from IPS 4200 appliances to integrated hardware modules such as the Advanced Inspection and Prevention Security Services Module (AIP-SSM) for ASA or the Intrusion Detection Services Module (IDSM) for Cisco Catalyst 6500. These IPS sensors support a variety of IPS technologies, including signature-based, anomaly-based, policy-based, and reputation-based techniques.
These threat prevention mechanisms are integrated into the fabric of the network. Flexible deployment options include standalone appliances, virtualized devices, and service modules that are embedded into routers and switches.
Note
Cisco TechWiseTV has produced excellent videos on different security products. Check them out:
“Fundamentals of Intrusion Prevention”: http://youtu.be/w-z2kS9dlcI
“Fundamentals of ISE”: http://youtu.be/sel1F7mKdtI
“Fundamentals of TrustSec”: http://youtu.be/78-GV7Pz18I
Many other informative videos from TechWiseTV can be found at http://www.youtube.com/user/techwisetv?ob=0.
Cisco Security Intelligence Operation
Cisco SIO is the back-end security ecosystem that detects threat activity, researches and analyzes the threats, and provides real-time updates and best practices to keep organizations informed and protected. Cisco SIO, considered the largest threat analysis system providing blended threat protection, consists of three pillars:
• Threat intelligence, which is called Cisco SensorBase
• The automatic and human development process, called the IronPort Threat Operations Center
• The automated and best practices content that is pushed to network elements in the form of dynamic updates
Cisco SIO is a security intelligence center that baselines the current state of threats on a worldwide basis, and provides the network as a system with valuable information to detect, prevent, and react to threats. SIO acts as an early warning system by correlating threat information from the SensorBase, analyzed by the Threat Operations Center. SIO then feeds this information to enforcement elements, for live threat prevention based on malware outbreaks, current vulnerabilities, and zero-day attacks.
Cisco SIO weighs and processes the data, automatically categorizing threats and creating rules using more than 200 parameters. Security researchers also collect and supply information about security events that have the potential for widespread impact on networks, applications, and devices.
Rules are dynamically delivered to deploy Cisco security devices every three to five minutes. The Cisco SIO team also publishes security best practice recommendations and tactical guidance for thwarting threats.
Cisco’s products participating and benefiting from Cisco SIO are IPS, ASA, IronPort Email Security Appliance (ESA), and IronPort Web Security Appliance (WSA). The AnyConnect telemetry module can even be used to send endpoint web malware traffic information back to the web filtering infrastructure of IronPort WSA.
Some interesting statistics on Cisco SIO at the time of printing:
• It is estimated that more than 700,000 sensors participate in Cisco SIO.
• Cisco SIO analyzes more than 5 billion web requests daily coming from Cisco equipment such as IronPort WSA.
• It is estimated that 35 percent of all email traffic worldwide is checked against Cisco SIO.
Cisco SIO is a powerful way of analyzing traffic based on reputation, blocking malware and spam, and providing a granular web categorization and application classification.
Cloud Security, Content Security, and Data Loss Prevention
Cloud computing represents one of the most significant shifts in IT that many of you are likely to see in your lifetime. Reaching the point where computing functions as a utility has great potential, promising innovations that cannot yet be imagined. However, this breakthrough business model also imposes new security risks.
Not in any order of importance or severity, following is a list of the top threats to cloud computing, according to the Cloud Security Alliance (https://cloudsecurityalliance.org/):
• Abuse and nefarious use of cloud computing
• Insecure interfaces and APIs
• Malicious insiders
• Shared technology issues
• Data loss or leakage
• Account or service hijacking
• Unknown risk profile
Vendors, providers, and customers alike are concerned about the consequences if cloud computing is not properly secured, and the loss of direct control over systems for which they are nonetheless accountable.
Cloud computing is a double-edged sword: it introduces more security concerns but it provides security opportunities. Regarding security concerns about cloud computing, consider, for example, an organization that has embraced Software as a Service (SaaS) and uses cloud-based services such as Google Apps for Business and SalesForce. In a traditional cloud service, if a user leaves the organization, the administrator would need to visit both the SalesForce website and the Google Apps for Business website and proceed to nullify that user’s accounts at each of those sites. However, if the organization has implemented the Cisco SaaS Access Control solution offered on Cisco IronPort WSA (discussed later), the administrator would only need to cancel the user’s account from the WSA.
Content Security
Before we jump in to cloud computing, let’s review some of Cisco’s offerings for content security.
Content security refers to the threat prevention capabilities that provide malware protection against spyware, viruses, spam, and inappropriate content. Examples of content security products from Cisco include the following:
• Cisco IronPort Web Security Appliance (WSA), which scans the content of a web page for malware prior to passing it to the inside user who initiated the request
• Cisco IronPort Email Security Appliance (ESA), which scans incoming email against spam
• Cisco ASA 5500 Series Content Security and Control Security Services Module (CSC-SSM) running Trend Micro’s antivirus and anti-spyware technologies.
Cisco IronPort WSA and ESA are discussed further later in this section.
Data Loss Prevention
Also known as data leak prevention systems or extrusion prevention systems, data loss prevention (DLP) systems monitor outbound traffic to ensure that confidential information doesn’t fall into the wrong hands.
Cisco IronPort WSA and ESA both offer solutions to scan outbound traffic against preconfigured and customizable rules, thus preventing corporate or personal information from leaving the organization’s premises.
Cloud-Based Security
Traditional threat prevention is now augmented to extend the system to email and web security, two key elements of the new mobile, cloud-based business environment.
Cisco offers both on-premises and cloud-based security for web and email traffic. For web security, Cisco offers the IronPort WSA as an on-premises device and IronPort ScanSafe as a cloud-based solution. For email security, Cisco offers the IronPort ESA either as an on-premises device or as a cloud-based service.
Web Security
Cisco offers both on-premises and cloud-based web security solutions, ScanSafe and the Cisco IronPort WSA, respectively. The WSA is what we commonly refer to as a web-proxy server.
Web malware is a common vehicle used to materialize threats in cloud services. Instead of creating their own malicious websites, hackers exploit the vulnerabilities of an open and dynamic web to distribute their malware. Web malware infection from reputable websites that have been compromised is not only a reality, but is now hackers’ preferred route to infect victims.
This change has made traditional methods of control, such as antivirus software, less effective, and it requires an alternative approach to security.
Web security architecture from Cisco presents a flexible approach and deployment options for implementing services such as URL filtering, web content filtering, real-time scanning, web traffic and application control, malware prevention, and others. ScanSafe is a cloud-based solution that enhances security while enabling cost savings by eliminating the need to purchase, deploy, and maintain hardware required for on-premises solutions. IronPort WSA is an on-premises solution that offers data loss prevention capabilities, URL filtering, and other web security controls.
ScanSafe Web Security analyzes every web request to determine if content is malicious, inappropriate, or acceptable based on the defined security policy. This offers effective protection against threats, including zero-day threats, that would otherwise be successful.
ScanSafe Web Security is powered by Outbreak Intelligence, which is composed of numerous correlated detection technologies, automated machine-learning heuristics, and multiple “scanlets.” Outbreak Intelligence builds a detailed view of each web request and the associated security risk to ensure that ScanSafe customers use the web safely.
Figure 2-10 illustrates the integration of ScanSafe with the Cisco AnyConnect client, to provide seamless deployment of context-aware policies, protected at the application layer against web malware.
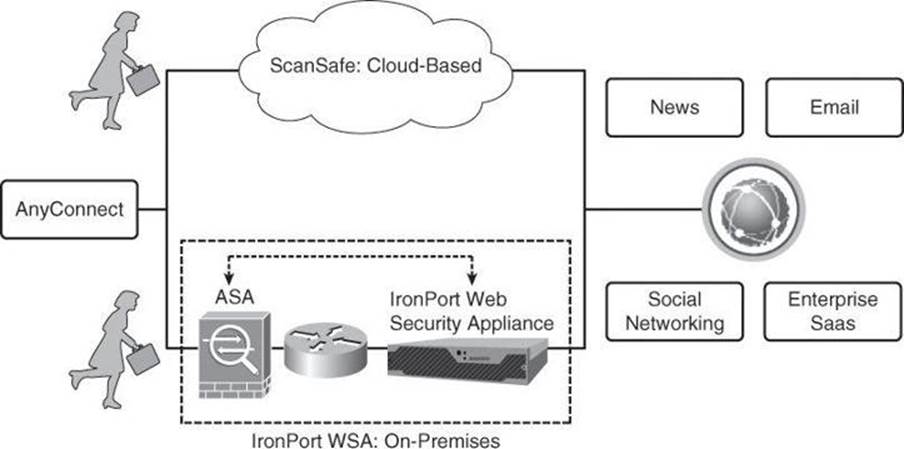
Figure 2-10. ScanSafe Integration with Cisco AnyConnect
This is the highlighted functionality:
• Integrated management and reporting that covers all aspects of the solution
• Consistent policy and security for all users, regardless of location, whether they connect from their cubicle or from the boardroom in an adjacent corporate building, as an example
• Numerous ways to integrate with existing network infrastructure and authentication services
• Bidirectional content-based policy enforcement
• Dynamic content classification
• Control over HTTP and HTTPS communications
• Accurate zero-day threat protection
• All security extended to remote and roaming users in addition to on-premises users
Figure 2-11 also illustrates the use of IronPort Web Security Appliances on premises. In combination with ASAs, this solution implements acceptable use policies, malware prevention, and single sign-on to SaaS providers.
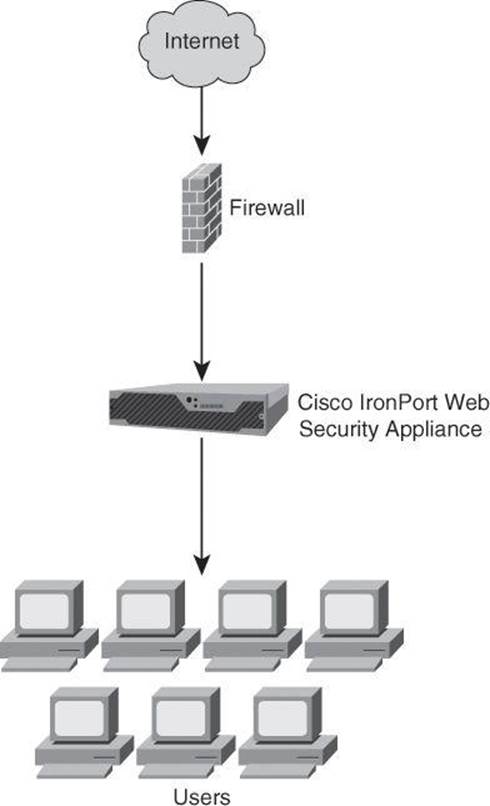
Figure 2-11. Cisco IronPort WSA on Premises
Cisco AnyConnect users use VPN technologies to connect to the corporate network via ASA, and their identity is then shared with WSAs for an integrated, context-aware web security solution.
Email Security
Cisco offers both on-premises and hosted email security solutions, using Cisco IronPort Email Security Appliance, as shown in Figure 2-12.
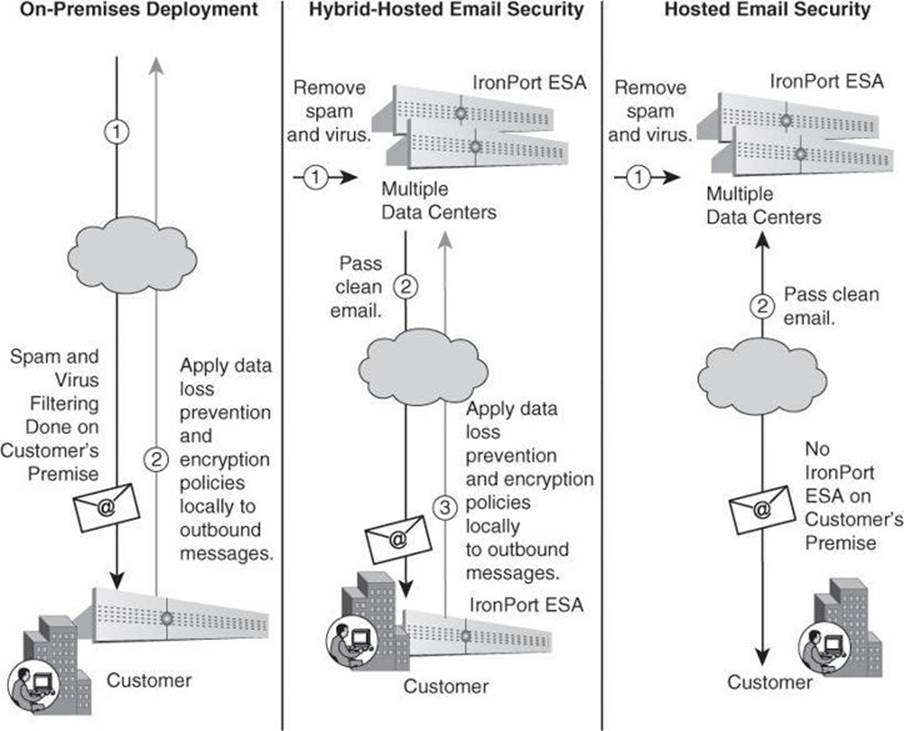
Figure 2-12. Cisco IronPort Email Security Solutions
Cisco IronPort Email Security solutions provide outstanding protection to organizations of all sizes. Sophisticated and scalable mechanisms help to do the following:
• Minimize the downtime that is associated with email-borne malware
• Simplify the administration of corporate mail systems
• Reduce the burden on technical staff, while offering insight into mail system operation
Best-in-class technologies work together to prevent and respond to multilevel threats. They include the following:
• Spam protection: The Cisco spam protection combines best-of-breed conventional techniques with IronPort’s breakthrough context-sensitive detection technology to eliminate the broadest range of known and emerging email threats.
• Data loss prevention: Cisco has partnered with RSA, a leader in data loss prevention technology, to provide an integrated data loss protection solution, RSA Email DLP, on Cisco IronPort ESAs. This solution ensures compliance with industry and government regulations worldwide and helps prevent confidential data from leaving customer networks.
• Virus defense: Cisco IronPort Virus Outbreak Filters detect new virus outbreaks in real time, then quarantine suspicious messages, offering protection before traditional antivirus solutions.
• Email encryption tracking and reporting tools: Cisco IronPort Preboot Execution Environment (PXE) encryption technology revolutionizes email encryption, meeting compliance requirements while delivering powerful, business-class email features.
IronPort solutions offer a choice of features and functionality available as appliance-based, cloud-based, hybrid, or managed solutions (where the solution is on premises but managed by Cisco’s expert staff).
Secure Connectivity Through VPNs
Ensuring the privacy and integrity of all information is vital to your business. You can achieve privacy and integrity by using IPsec and SSL VPNs, as shown in Figure 2-13. As your company uses the flexibility and cost effectiveness of the Internet to extend its network to branch offices, telecommuters, customers, and partners, security is paramount. You must create a manageable, cost-effective communications infrastructure that will do the following:
• Improve productivity
• Enable new business applications
• Help you comply with information privacy regulations
• Enhance business efficiency
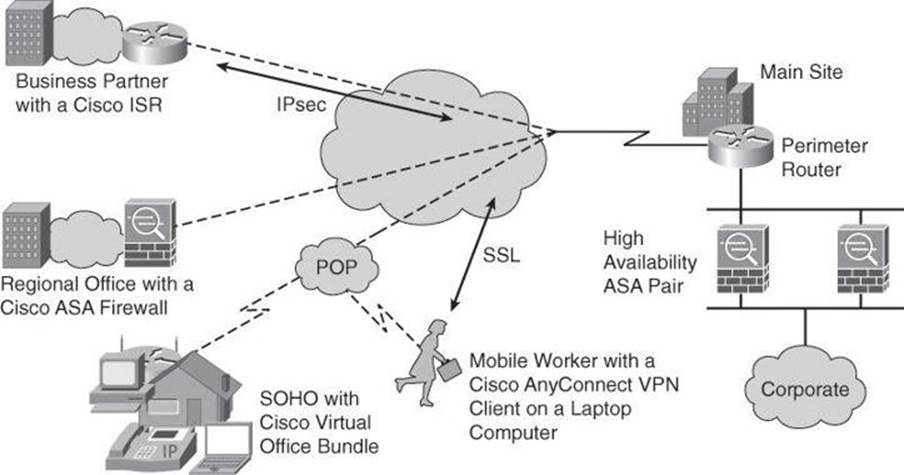
Figure 2-13. VPN Deployment Options
Cisco VPN solutions implement a set of products and security life-cycle services that are an essential element of the Borderless Network Architecture. By incorporating capabilities that secure the network, the endpoints, and the applications and messages, this systems-based approach delivers comprehensive security of your communications. The solution has two major elements:
• Secure communications for remote access: This element provides highly secure, customizable access to corporate networks and applications by establishing an encrypted tunnel across the Internet.
• Secure communications for site-to-site connections: This element provides an Internet-based WAN infrastructure for connecting branch offices, home offices, or the sites of business partners to all or portions of your network.
Security Management
Cisco network management systems help you automate, simplify, and integrate your network to reduce operational costs and improve productivity. The tools within the network management systems provide innovative ways to centrally and consistently manage your network to achieve critical functions such as availability, responsiveness, resilience, and security.
These network management systems also help reduce the troubleshooting and planning time that is associated with the introduction of new services such as voice, wireless, and security management. Solutions-focused tools simplify network management systems, including the management of devices, configurations, users, and services.
The tools available for security management are
• Device managers: Embedded into security devices in the form of HTML content. All you have to do is point your browser to an active IP address of the device, and the device manager immediately provides a comprehensive tool for one-to-one configuration and monitoring. ASDM, the Adaptive Security Device Manager, is an example of this approach for the ASA 5500 security appliances.
• Cisco Configuration Professional: A GUI-based device management tool for Cisco access routers. This tool simplifies routing, firewall, IPS, VPN, unified communications, WAN, and LAN configuration through GUI-based wizards. Cisco Configuration Professional is a valuable productivity enhancing tool for network administrators and channel partners for deploying routers with increased confidence and ease. This tool offers a one-click router lock-down and an innovative voice and security auditing capability to check and recommend changes to router configuration. This tool also monitors router status and troubleshoots WAN and VPN connectivity issues.
• Cisco Security Manager: Provides configuration and monitoring capabilities for firewalls, routers, switches, IPS sensors, and other security solutions. This tool uses multiple approaches to security management, including device-focused and policy-focused options.
Cisco Security Manager
Cisco Security Manager is a powerful but easy-to-use solution that enables you to centrally provision all aspects of device configurations and security policies for the Cisco family of security products. The solution is effective for managing even small networks consisting of fewer than ten devices, but also scales to efficiently manage large-scale networks that are composed of thousands of devices. Scalability is achieved through intelligent policy-based management techniques that can simplify administration and promote policy uniformity among devices. As a simple example, the administration might come up with a new login banner that is pushed to Cisco devices, such as routers, firewalls, and switches, using CSM. If in the future the legal department changes the wording of the login banner, CSM could deploy the new banner in a matter of minutes to all the devices.
Some of the features of Cisco Security Manager include the following:
• Supports provisioning for Cisco router platforms running a Cisco IOS Security Software image, Cisco ASA 5500 Series Adaptive Security Appliances, Cisco PIX 500 Series Security Appliances, Cisco IPS 4200 Series Sensors, and Cisco Catalyst 6500 Series Advanced Inspection and Prevention Security Services Module (AIP-SSM)
• Responds faster to threats by allowing you to define and assign new security policies to thousands of devices in a few simple steps
• Provides a rich GUI for superior ease of use
• Offers multiple views that provide flexible methods to manage devices and policies, including the ability to manage the security network visually on a topology map
• Contains extensive animated help for the new user, which reduces the learning time
• Allows you to centrally specify which policies are shared and automatically inherited by new devices to ensure that corporate policies are implemented consistently, while providing optional flexibility
• Integrates with Cisco Secure Access Control Server (ACS) to provide granular role-based access control to devices and management functions, though this functionality is removed once you upgrade to CS ACS 5.2
• Provides the ability to assign specific tasks to each administrator during the deployment of a policy, with formal change control and tracking, and allows the security and network operations staff to work together as a single team with effective coordination
Summary
In this chapter, you learned about the Cisco Borderless Network Architecture. This chapter examined the Cisco Security portfolio of products and, more specifically, reviewed the following:
• Cisco SecureX Architecture (at a high level), highlighting its features and benefits and providing examples of Cisco products that fall within this category
• Cisco threat control and containment products and technologies, such as the Cisco ASA and Cisco IPS, and illustrating their high-level features and benefits
• Cisco content security and data loss prevention technologies, such as Cisco IronPort WSA and ESA, and illustrating their high-level features and benefits
• Cisco VPN solutions and technologies, and illustrating their high-level features and benefits
• The different security management products and technologies, focusing at a high level on Cisco Security Manager
References
For additional information, refer to these Cisco.com resources:
“Borderless Networks,” http://www.cisco.com/en/US/netsol/ns1015/architecture.html
Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 3.0, Chapter 7, “Configuring AnyConnect Telemetry to the WSA,” http://www.cisco.com/en/US/docs/security/vpn_client/anyconnect/anyconnect30/administration/guide/ac07telemetry.pdf
“Cisco AnyConnect Secure Mobility Solution,” http://www.cisco.com/en/US/prod/collateral/vpndevc/ps5743/ps5699/ps10884/at_a_glance_c45-578609.pdf
“Cisco SecureX,” http://www.cisco.com/en/US/netsol/ns1167/index.html
“Cisco TrustSec,” http://www.cisco.com/en/US/netsol/ns1051/index.html
“Cisco Network Identity and Access Policy Solution,” http://www.cisco.com/en/US/prod/collateral/vpndevc/ps5712/ps2086/network_id_vds.html
Cisco’s TechWiseTV, http://www.youtube.com/ciscoCIN
Securing the Borderless Network, http://www.ciscopress.com/bookstore/product.asp?isbn=1587058863
Review Questions
Use the questions here to review what you learned in this chapter. The correct answers are found in the Appendix, “Answers to Chapter Review Questions.”
1. Match each Cisco SecureX component with its definition.
a. Context-aware enforcement
b. Cisco TrustSec
c. Cisco SIO
d. Cisco AnyConnect
_____ 1. Extends the access control functionality end to end, using security group tags.
_____ 2. Used for real-time insight into the global threat environment.
_____ 3. Provides a consistent user interface and consolidates traditional function-specific client software products into one.
_____ 4. Allows enforcement elements to use identity and location information to define access policy.
2. The ASA, ISR, and IPS are all part of which product category?
a. Threat control and containment
b. Cisco TrustSec
c. Cisco SecureX
d. Cisco SIO
e. Content security
3. Which two Cisco products provide data loss prevention in cloud services environments? (Choose two.)
a. Cisco TrustSec
b. Cisco ScanSafe
c. Cisco SecureX
d. Cisco IronPort ESA
e. Cisco ASA
4. Using Cisco TrustSec functionality, what needs to happen before security group tags are assigned?
a. MACsec confidentiality policy needs to be created
b. Access policies are built in Cisco ISE
c. Security group ACLs need to be defined
d. User authentication mode needs to be selected
5. The Cisco ISE policy engine combines the functionality of which two Cisco products? (Choose two.)
a. Cisco AnyConnect
b. Cisco Secure ACS
c. Cisco Security Manager
d. CiscoWorks
e. Cisco NAC
All materials on the site are licensed Creative Commons Attribution-Sharealike 3.0 Unported CC BY-SA 3.0 & GNU Free Documentation License (GFDL)
If you are the copyright holder of any material contained on our site and intend to remove it, please contact our site administrator for approval.
© 2016-2025 All site design rights belong to S.Y.A.