Implementing Cisco IOS Network Security (IINS) Foundation Learning Guide, Second Edition (2013)
Part III: Threat Control and Containment
Chapter 7. Planning a Threat Control Strategy
Current trends in security threat vectors require a carefully planned threat control strategy. Trends affecting security include persistent application layer exploits, using social engineering to exploit the trust architecture of the enterprise, the pervasiveness of mobility and consumerization, and the insidious motivations behind the behavior of the attackers. All of these trends result in the need for dynamic security intelligence gathering and distribution, early warning systems, and application layer inspection for mobile services where data and applications are hosted in the cloud. This chapter suggests design principles to plan a threat control and containment strategy using firewalls and intrusion prevention systems in Cisco IOS environments. (Note that in previous chapters you have started to see how to use switches and routers to provide protection; in upcoming chapters, we will further explore the protection provided by routers when used for filtering, firewalling, and encrypting traffic.) In this chapter, we will
• Evaluate the current state of enterprise security in the presence of evolving threats
• Describe design considerations for a threat protection strategy to mitigate threats as part of a risk management strategy
• Describe how Cisco strategizes threat control and containment
Threats Revisited
Previous chapters of this book discussed the evolution of threats in information security. Recent trends indicate that threats have become global in nature, increasingly sophisticated, and pervasive. New exploits are designed to have a global impact in minutes. Blended threats, which use multiple means of propagation, are more sophisticated than ever. The trends are becoming regional and global in nature. Attackers are also learning to be dynamic and reactive, changing their approach rapidly if needed. I remember a discussion I had with the director of network security for the federal reserve bank of his country; he remarked, “We have a small team of professionals working 8 hours per shift at protecting our network, but there are hundreds of hackers coming at us 24 hours per day, nonstop.” This network security team had to make sure that every crease of their network was secure. The hacker had to find only one open, minuscule gap to exploit.
Threats are also becoming persistent. After the initial attack starts, subsequent attacks may come in waves as infected systems join the network. Because infections are so complex and have so many end users (employees, vendors, and contractors), multiple types of endpoints (company desktop, home, and server), and multiple types of access (wired, wireless, VPN, and dial-up), infections are difficult to eradicate.
Trends in Network Security Threats
Evolution in technology and craftiness of hackers bring in new threat vectors. Threat vectors are the methods used to get to the desired target. More recent threat vectors are increasingly sophisticated, and the motivation of the attackers is reflected in their impact. Recent threat vectors include the following:
• Cognitive threats: social networks (likejacking)
• Smartphones, tablets, and consumer electronics exploits
• Widespread website compromises
• Disruption of critical infrastructure
• Virtualization exploits
• Memory scraping
• Hardware hacking
• IPv6-based attacks
The following is a list of the specific trends that can be gathered from the evolution of threats in information security:
• Insidious motivation, high impact: The primary motivation of the attacker is no longer just fame and notoriety. It is mostly political and financial, aimed at economic espionage and money-making activities. Malicious attackers use a businesslike, structured process not only to write code, but also to “conduct business.” It is common to see a lifecycle approach to software development and a businesslike environment where developers cooperate and make attack tools publicly available.
• Targeted, mutating, stealth threats: The modus operandi is increasingly stealth, using mutating malware that changes by the minute. In some instances, hundreds of variants of the same malware are created in a matter of hours.
Cybercriminals see value in fine-tuning their efforts so that their malware reaches a single high-profile target or performs a specific function. An example of a high- profile target attack effort would include attacking critical infrastructure, government operations, and organizations with massive amounts of customer identity information.
Attackers use strength in numbers. Botnets with specific targets are the norm, whereas large-scale worms with no individual objective are less common or effective. In the past, botnets would use centralized command and control. Botnets today use peer-to-peer control, so there is no central controller to take down.
• Threats consistently focusing on the application layer: Known application layer attacks such as cross-site scripting and SQL injection are still relevant, as well as other vulnerabilities such as iFrame injection, which result from programming errors in web services environments. Increasingly, attacks have demonstrated that criminals looking for financial gain can exploit vulnerabilities resulting from web programming errors as new ways of penetrating important organizations. Attacks exploiting web browser vulnerabilities are common.
• Social engineering front and center: Social engineering continues to attract victims who are willing to share information with people they believe are known to them. Nowhere is this trend more visible than in social networks, a prime target of attacks. One noticeable shift in social engineering is that criminals are spending more time figuring out how to assume someone’s identity, perhaps by generating emails from an individual’s computer or social networking account.
• Threats exploiting the borderless network: Smartphones are general-purpose computers, so worms, viruses, and other malware will increasingly target them. Open mobile platforms are a prime target, and as more workers use their consumer devices for business-critical activities, endpoint security becomes a critical security control.
Data is now stored everywhere, with the advent of cloud computing and cloud services. Cloud security is a major concern for organizations of all kinds. A technology is often the victim of its own success. As a technology becomes more popular, it appears more prominently on hackers’ radar screens, thus motivating them to attack this new technology. As an example, it is expected that as IPv6 becomes more pervasive, IPv6 vulnerabilities and threats will become more commonplace.
Threat Mitigation and Containment: Design Fundamentals
The result of the recent trends in information security threats is the need for an updated, carefully planned threat control and mitigation strategy, and a revision of old design paradigms.
• Policies and process definition: The nature and frequency of attacks, and the increasingly high stakes in terms of organizational and business risk, call for a more formal approach to defining threat control policies. What probably started as a reactive process, and then moved to a more socialized process, needs to become a formal process in the wake of botnets, industrial espionage, and identity theft.
• Mitigation technologies: The mutating and stealth nature of attacks requires more accuracy in detection and prevention technologies. It also requires a more automated process, where networks and applications react to attacks and mitigate them with little or no human intervention. This used to be a more manual process in the past; however, organizations can no longer risk the potential consequences of this manual approach.
• End-user awareness: Data is stored everywhere, and users access mission-critical resources from multiple locations at multiple times, using multiple types of devices. The new paradigm must get the end user more involved with security, where in the past this was a function that was fully performed by IT.
Threat Control Design Guidelines
These new paradigms result in specific design guidelines for the threat control and containment architecture:
• Stick to the basics: The fundamental design guidelines are still valid. Implement a layered security approach, where defense in depth defines redundant, overlapping security controls to mitigate risk and provide fault tolerance. The threat control design should consider both internal and external networks to be untrusted and apply policy for both inbound and outbound traffic.
• Risk management: This should be a central consideration. Logging and monitoring are still critical functions.
• Distributed security intelligence: Because data and access are everywhere, there should also be security “sensors” everywhere. Security needs to be embedded in network elements, operating systems, and applications. This network of sensors needs to be integrated. Actionable, relevant, highly dynamic security information should be available to security devices and controls.
• Security intelligence analysis: This army of sensors and security controls will produce vast amounts of information. Event management, incident management, and, in more general terms, security intelligence management require a central approach to analysis and correlation, including correlation with third parties and external sources. This analysis should result in relevant threat information that should be automatically distributed to security devices and controls in a timely manner.
• Application layer visibility: Application layer inspection is critical and should be implemented efficiently and effectively.
• Incident response: Incident response should be automated and dynamic, providing end users the means to respond and mitigate.
Application Layer Visibility
Application layer security controls provide visibility at higher layers, up to Layer 7 (as shown in Figure 7-1), necessary to match protocol and application anomalies that are purposefully crafted to exploit application and operating system vulnerabilities. This functionality is necessary in firewalls and intrusion prevention systems, and it should be implemented with effectiveness and efficiency in mind. Application layer controls are often implemented in hardware, and they require a good amount of capacity planning because they trigger deep packet inspection and are more CPU intensive than Layer 4 controls such as access control lists (ACL).
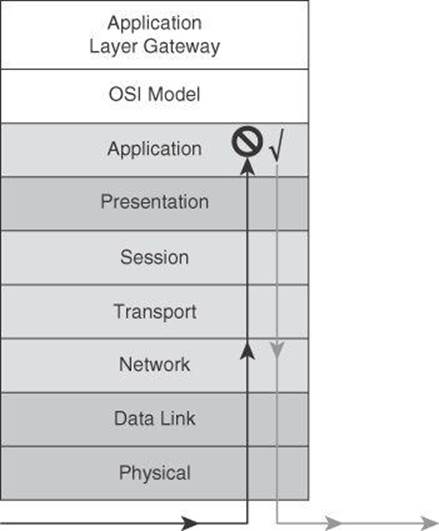
Figure 7-1. Application Layer Visibility Analyses Traffic Up to the Application Layer
Application layer visibility provides the intelligence to distinguish botnet command and control activity from otherwise innocuous web traffic, and can distinguish between valid encrypted data and data meant to obfuscate the application. Without application layer visibility, you cannot comprehensively detect, respond to, and investigate policy violations, exploits, and intrusions. Cisco IronPort Web Security Appliance (WSA) is a device that provides application layer visibility. The application layer visibility, which is the bread and butter of the IronPort WSA, can also be accomplished with Layer 7 filtering on the Cisco ASA firewalls and on Cisco IOS routers, though it necessitates more effort.
Distributed Security Intelligence
The distributed approach to gathering and providing relevant and actionable security intelligence follows the defense-in-depth guidelines of security architecture design. For threat management, this approach creates an army of sensors and threat controls that work collaboratively and automatically to provide a more effective threat detection and response mechanism. This results in higher threat coverage and greater accuracy, as new threats detected in one location are fed back into the system, making other locations know about the threat and update their detection and response capabilities to manage it.
This system is based on telemetry, collaboration, and proactive protection, where sensors in the field feed a central system that distributes the information to other sensors, as shown in Figure 7-2. This approach acts as an early warning system to prevent new attacks and automatically tune the response to current attacks. Cisco offers such systems with its AnyConnect telemetry module, which communicates with Cisco IronPort WSA. The web filtering infrastructure uses this data to strengthen its web security scanning algorithms, improve the accuracy of the URL categories and web reputation database, and ultimately provide better URL filtering rules for the organization.
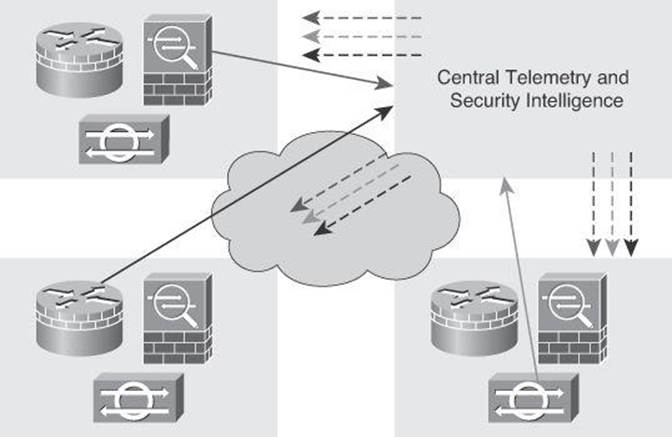
Figure 7-2. Distributed Security Intelligence Using Telemetry
Security Intelligence Analysis
The proliferation of security controls could overflow the ability of the system to gather and analyze the security intelligence information. Building an effective security intelligence analysis capability becomes a crucial component of the threat control architecture design.
Event and incident management are critical components of this strategy. Monitoring and logging are fundamental guidelines that may be already in place. Local and global correlation of the monitoring and log data becomes increasingly important, for accuracy and automation, and also for forensics and post-mortem analysis.
In Figure 7-3, multiple devices send a log entry to the syslog server, on the right, regarding the single event generated by the hacker attacking the target. All these alerts are analyzed by the central event management and correlation server, and the administrator is notified once about the issue. Without proper correlation analysis, the network administrator might have been notified by the alert from the router, by the alert from the firewall, and by the alert generated by the IPS sensor. Cisco MARS, now in end-of-life status but still supported by Cisco, was an example of such central event management and correlation system. As mentioned in Chapter 4, Cisco now refers its customers to one of its Security Information and Event Management (SIEM) ecosystem partners, such as LogLogic, Splunk, and so forth. More information about SIEM partners can be found at http://www.cisco.com/en/US/solutions/ns340/ns414/ns742/ns744/ns1090/landing_siem.html.
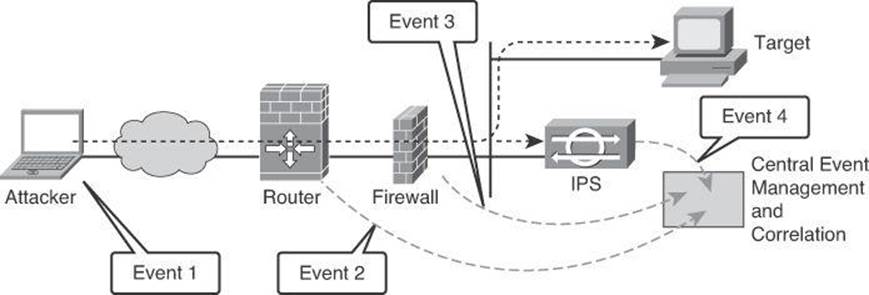
Figure 7-3. Security Information and Event Management
Integrated Threat Control Strategy
The Cisco threat control and containment solution offers comprehensive protection for your network through network-wide visibility, simplified policy control, and proactive system protection. The Cisco threat control and containment solution regulates network access, isolates infected systems, prevents intrusions, and protects critical business assets. This solution uses centralized policy, configuration, and threat event management to counteract malicious traffic, such as worms, viruses, and malware, before it affects your business.
Cisco Threat Control and Containment Categories
Threat prevention solutions have been a flagship of Cisco security for a long time. Integrated security controls found in Cisco Adaptive Security Appliance (ASA), Integrated Services Routers (ISR), and Intrusion Prevention System (IPS) sensors provide a multidimensional approach to detecting, mitigating, and responding to threats at various levels. Threat prevention mechanisms, such as application layer inspection, Modular Policy Framework (MPF), signatures, and anomaly detection and firewalling, are integrated into the fabric of the network. Flexible deployment options include standalone appliances, service modules that are embedded into routers and switches, and virtualized devices, such as Cisco ASA contexts (virtual firewalls). These mechanisms can be deployed on premises, off premises, or as part of a hybrid, managed approach using cloud services.
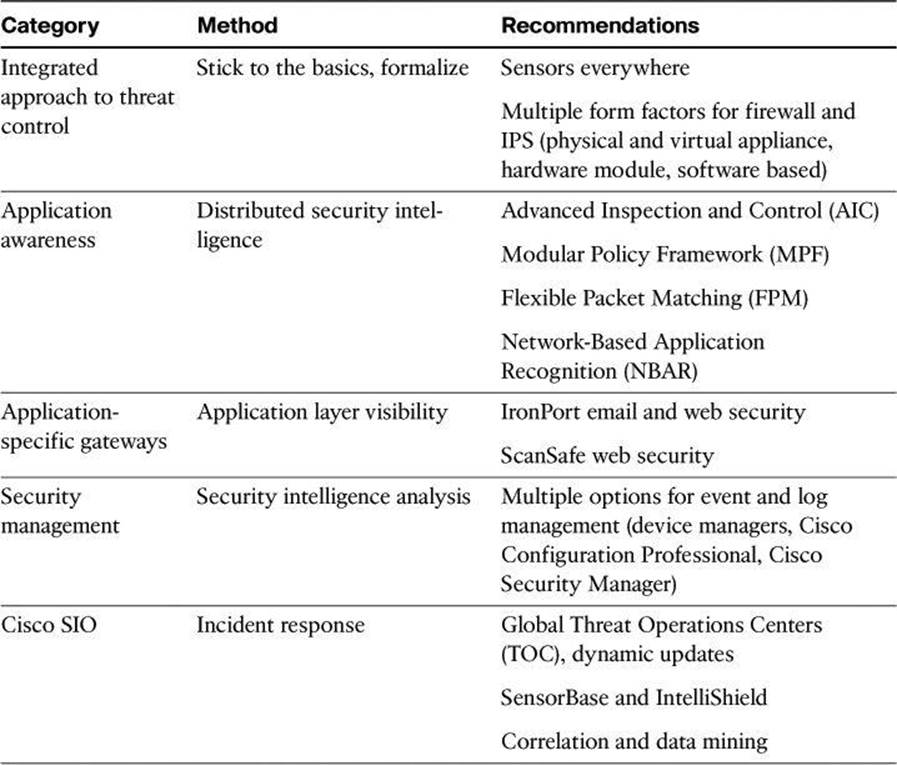
Table 7-1 provides an overview of the different technologies incorporated into the Cisco threat control and containment solution. These technologies are looked at more closely in the rest of this chapter.
Table 7-1. Cisco Threat Control and Containment
Cisco security technologies facilitate the implementation of the design guidelines previously described by incorporating the following features and technologies:
Integrated Approach to Threat Control
The network is the system that detects and prevents threats. As such, threat control is embedded and integrated in the network using multiple deployment options: appliance-based controls, hardware modules for existing network elements, software-based controls, and virtualized security elements, are all part of this strategy to prevent intrusion and control threats.
Application Awareness
Application awareness is implemented across the board in multiple network elements and security devices, such as the Zone-Based firewall that performs application layer (Layer 7) inspection and deep packet inspection. These solutions are implemented in the form of multiple application inspection mechanisms, such as, among others, the following:
• Any alphanumeric character
• Modular Policy Framework (MPF)
• Network Based Application Recognition (NBAR)
• Flexible Packet Matching (FPM)
Application-Specific Gateways
Application awareness is also implemented in the form of application-specific gateways, geared toward the inspection and analysis of traffic related to specific applications. IronPort web and email security appliances and ScanSafe web security technologies are examples of those gateways.
Security Management
A comprehensive approach to event management is available in all security management tools, with scalable features available for different scenarios. From device managers such as Cisco IPS Device Manager (IDM), to configuration builders such as Cisco Configuration Professional, to central management applications such as Cisco Security Manager, event management and correlation are a key function in Cisco security management.
Cisco Security Intelligence Operations Site
Cisco SIO is the back-end security ecosystem that detects threat activity, researches and analyzes the threats, and provides real-time updates and best practices to keep organizations informed and protected. Cisco SIO consists of three pillars:
• Threat intelligence, which is called Cisco SensorBase, shown in Figure 7-4
• The automatic and human development process, called the Threat Operations Center
• The automated and best practices content that is pushed to network elements in the form of dynamic updates
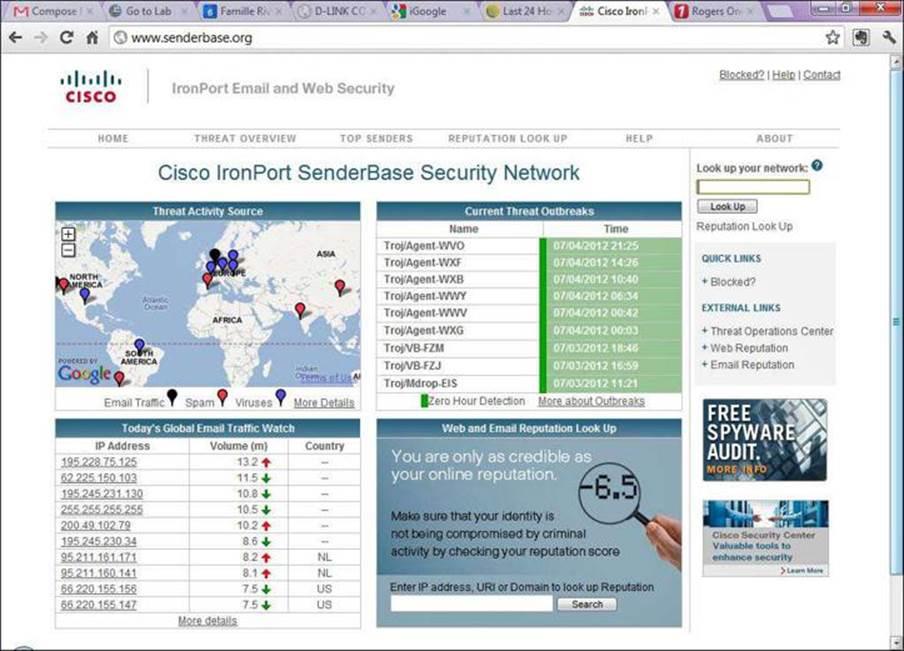
Figure 7-4. Cisco IronPort SenderBase Web Page
Cisco SIO is a security intelligence center that baselines the current state of threats on a worldwide basis and provides the network system with valuable information to detect, prevent, and react to threats. Cisco SIO acts as an early warning system by correlating threat information from the SensorBase, analyzed by the Threat Operations Center. Cisco SIO then feeds this information to enforcement elements for live threat prevention that is based on malware outbreaks, current vulnerabilities, and zero-day attacks.
More information on Cisco SIO can be found at http://tools.cisco.com/security/center/home.x and at http://www.senderbase.org.
Cisco Threat Control and Containment Solutions Fundamentals
Cisco offers multiple solutions in multiple different platforms to provide threat control and containment. For the purpose of the CCNA Security, we will focus on the most common technology used by small and medium businesses, which are Firewalling, including access-control lists, and Intrusion Prevention Systems. For a more exhaustive list of Cisco’s offerings, visit www.cisco.com.
Cisco Security Appliances
Cisco security appliances, commonly called firewalls, are integrated devices that offer a new generation of threat control mechanisms. Solutions that include firewalling services are available in multiple footprints to implement the distributed security intelligence approach to threat prevention:
• Cisco ASA: These multifunction security devices include firewalls, VPNs, IPSs, and content security technologies. They are available in multiple form factors, and benefit multiple places in the network, from the small office to the data center and service provider environment.
• Hardware modules: Designed for data center and large enterprise networks, these security modules integrate into the Catalyst 6500 switch:
• Cisco Catalyst 6500 ASA Services Module
• Cisco Catalyst 6500 Firewall Services Module (FWSM)
• Cisco IOS Firewall: Integrated in the Cisco IOS software in Integrated Services Routers and Layer 3 switches, this Cisco IOS option implements the zone-based policy firewall and allows a distributed approach to firewall services.
• Cisco Virtual Security Gateway (VSG): Designed for data centers where multitenancy and service virtualization are common, this virtual appliance integrates with commercial server virtualization and switch virtualization environments.
Note
In February 2012, Cisco announced the latest firewall OS, called Cisco ASA CX, which will bring application awareness and visibility to the traffic similarly to, but not completely the same as, how a secure web gateway would do it. Customers who wish for the full array of context awareness should still invest in a Cisco IronPort Web Security Appliance.
Cisco also announced new platforms, called the Cisco ASA 5500-X Series capable of running the Cisco ASA CX operating system. One of the many notable characteristics of the ASA 5500-X Series is its capacity to run IPS in software.
For more on Cisco ASA CX and the Cisco ASA 5500-X Series platforms, visit Cisco.com.
The different firewalls listed above implement various access control mechanisms for the new landscape of information security threats that are described in this module:
• Zone-based firewall
• ACLs
• FPM
• AIC
• MPF
• URL filtering
• User-based access control (cut-through proxy)
• Stateful failover
Cisco IPSs
Cisco IPSs are another example of integrated devices offering a new generation of threat control mechanisms. The IPS functionality is available in multiple footprints to implement the distributed security intelligence approach to threat prevention:
• Cisco IPS 4200 Series Sensors: These IPS appliances are available in multiple form factors, and benefit multiple places in the network, from the small office to the data center and service provider environment.
• Hardware modules: Integrating into ASA appliances, Catalyst 6500 switches, and ISRs, these modules embed the function of IPS sensors into the fabric of the network, and at the same time integrate with global correlation solutions such as the Cisco SIO service:
• Cisco ASA Advanced Inspection and Prevention Security Services Module (AIP-SSM) and Cisco ASA Advanced Inspection and Prevention Security Services Card (AIP-SSC)
• Cisco Intrusion Detection Services Module (IDSM-2) for Cisco Catalyst 6500
• Cisco IPS Network Module Enhanced (IPS NME) and Cisco IPS Advanced Integration Module (IPS AIM) for Cisco Integrated Services Router Generation 2 (ISR G2)
• Cisco IOS IPS: Integrated in the Cisco IOS operating system in ISRs and Layer 3 switches, this Cisco IOS option implements IPS technologies consistent with the rest of the Cisco IPS solutions.
These IPSs implement various intrusion management solutions for the new landscape of information security threats that are described in an upcoming chapter:
• Rich set of detection mechanisms
• Signatures
• Anomaly detection
• Normalization
• Correlation
• Automatic signature updates
• Multiple deployment modes
• Inline
• Promiscuous
Figure 7-5 illustrates the Cisco threat control and containment architecture for a small network scenario. Notice the distributed security intelligence approach, implemented through various threat control devices, including Cisco IOS zone-based and Cisco ASA firewalls, Cisco IOS IPS, and Cisco Security Manager. Application layer inspection, signature- and anomaly-based protection, and collaboration via the Cisco SIO Center are showcased in this scenario.
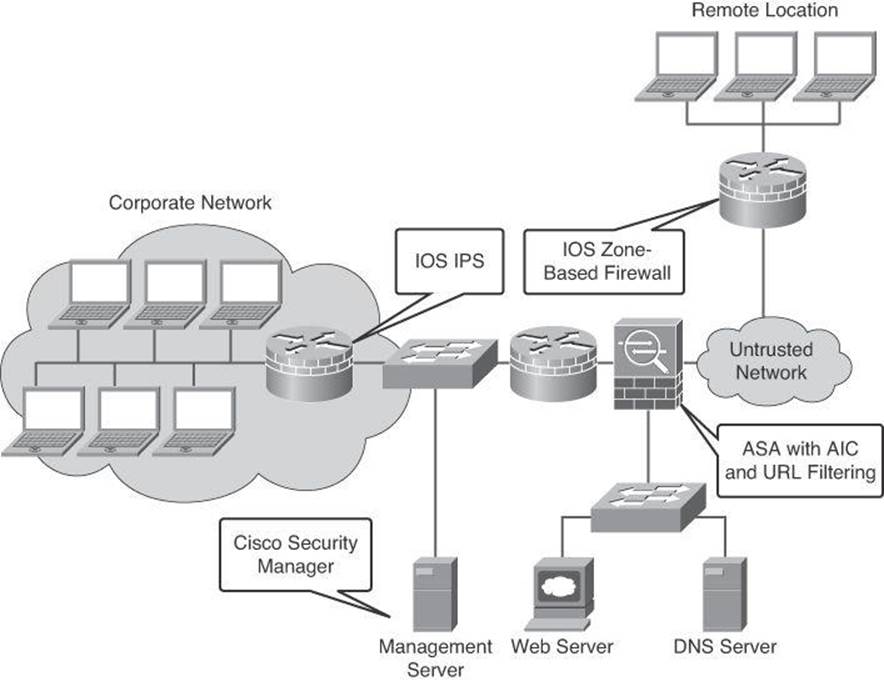
Figure 7-5. Threat Control Scenario for a Small Business
Summary
Threat vectors are stealth, targeted, aimed at the application. The motivations of attackers are increasingly based on social engineering and financial gains.
The following are the main points conveyed in this chapter:
• Threat control and containment should distribute security intelligence, improve incident analysis and correlation, and respond automatically.
• Cisco threat control and containment solutions provide multiple deployment options: appliance, hardware module, software based, and virtualized.
• Cisco threat control and containment is a solution for small, medium, and large businesses.
References
For additional information, refer to these Cisco.com resources:
“Cisco Security Intelligence Operations,” http://tools.cisco.com/security/center/home.x
“Cisco 5500 Series Adaptive Security Appliances,” http://www.cisco.com/en/US/products/ps6120/index.html
Review Questions
Use the questions here to review what you learned in this chapter. The correct answers are found in the Appendix, “Answers to Chapter Review Questions.”
1. The term “likejacking” refers to which type of threat vector?
a. Phishing
b. IPv6 Teredo tunnels
c. Social network exploits
d. Botnets
2. Which Cisco product or service provides the global correlation service?
a. IPS
b. SIO
c. Third-party SIEM systems
d. SecureX
3. Which two security appliances best fit a data center scenario where server virtualization and multitenancy are among the main architectural components?
a. FWSM
b. ASA
c. Zone-based firewall
d. VSG
4. What is meant by end-user awareness?
a. End users are consulted and made aware of the different applications tested by the organization.
b. End users are aware of the potentially harmful traffic generated by other users.
c. End users are involved in security functions that were strictly reserved to IT in the past, such as the user-acceptable policies and being conscious of potential threats.
d. End-user awareness is a network security training program developed by IT for future dissemination to end users.
5. Which of the following is seen as the best protection against zero-day attacks?
a. NBAR
b. AIC
c. SIO
d. MPF
e. FPM
f. ACL