Cyber Security Basics: Protect your organization by applying the fundamentals (2016)
Section One: Protect
“We foresee an ongoing series of low-to-moderate level cyber-attacks from a variety of sources over time, which will impose cumulative costs on US economic competitiveness and national security.”
James Clapper, Director of National Intelligence [4]
Introduction
This section discusses the various solutions, controls and processes that can be used by an information security team to help protect an organization from cyber attacks. This list is not comprehensive, nor is it meant to be. The goal is to provide a list of options whose implementation supports the foundation of an effective security program. Though there are continually new solutions being developed to combat ever-evolving threats, this section focuses on core solutions that address the majority of attacks that a typical organization regularly faces.
The following items also have a maturity level indicator, which is based on the resources and expertise required to implement the respective control, as well as how fundamental it is to an InfoSec program. If an organization is just starting to build an information security department, then level 1 items are the ones to start with. As the program improves and matures, level 2 and 3 become more appropriate.
1.1 Endpoint Protection
The days of a heterogeneous environment are gone. Endpoints come in a variety of shapes and sizes, including:
· Servers
· Desktops
· Laptops
· Mobile phones
· Tablets
Just as the form factor of endpoints can vary greatly, the list of operating systems running on these devices can include:
· Mac OS
· Android
· Chrome OS
· Apple iOS
· Windows Mobile OS
· Various distributions of Linux
Add to this the explosive growth of cloud computing and the Internet of Things (IoT), and the final result is controlled chaos. Yet all of this somehow has to work together and facilitate productivity, while doing it securely.
Though the IT landscape continues to grow more complex and fragmented, security fundamentals still apply. Protection solutions that can be installed on an endpoint include Anti-virus (AV), Host-based Intrusion Prevention Systems (HIPS), Host-based Intrusion Detection System (HIDS), and file integrity checkers (FIC). While each offers a different approach to protection in support of a defense in depth strategy, there is the challenge of having several solutions coexist peacefully on the same device. Software conflicts can cause performance degradations, errors, and other issues that can be frustrating for end users. Some compatibility issues may even cause security controls to fail to work properly, and perhaps not at all. Therefore, attention needs to be paid to the interoperability of the endpoint protection software, the operating system, and the applications that need to run. Issues like these may even affect the choice of security solutions that end up being deployed to endpoints.
The following solutions are described separately, but there are also several vendors that offer “bundled” solutions. When evaluating these products, consider everything offered by the bundle solution versus focusing on a single feature. It may prove more cost effective to select a product that offers several security controls. However, with bundled products make sure that the quality of all the features sought are at an acceptable level. The quality of a needed control should not be sacrificed for the sake of getting several at once.
An organization may also want to include free and open source products in the evaluation process. Just because a security product is paid for doesn’t mean that it is better than something available as open-source software. There may be a longer support tail for open source solutions, however, as the entity using the product may also be solely responsible for supporting, maintaining and updating it. But with what is lost in support may be made up for in flexibility, robustness (number of features) and customization options. As open source solutions often require unique employees who are able to support such products, an organization may defer to vendor-provided solutions so that they can rely on the vendor-provided support that comes with it. The cost difference, in the long-term, may be worth it.
Once security controls are installed on a device, there is still no guarantee that the software will be used nor running effectively. If the user rejects or is able to bypass the security installed on an endpoint, it’s possible that the device may actually be worse off than having no security software installed on it. Because when security software is installed on a device, that device is often put “out of mind”. The device is assumed to be fully protected by virtue of having security software installed on it. Meanwhile, if the user has disabled the protection software, or if it not running correctly, the device is still vulnerable. Trust but verify. Ensure that the security software is running correctly, that it cannot be disabled, and that it does not interfere with how the user does his or her work.
1.1.1 Configuration Management Database (CMDB)
Level 1 - The first step in protecting endpoints is to identify them. One of the most dangerous things on a network is a rogue, unmanaged device whose patch level and security posture is unknown. Maintaining an inventory of devices makes it easier to identify those that are not authorized, or are not secure enough to be on the network.
Take the time to properly discover and document all assets. These include servers, workstations, network equipment, and mobile devices. Start with the production network, but do not exclude other environments such as test, development and staging. The result is an asset database, also known as a configuration management database (CMDB). A CMDB is a centralized repository of asset information.
Creating a CMDB and process to follow to keep its information current should be one of the first steps taken before the deployment of any security solutions. Doing this will ensure that all assets are protected. To keep the inventory information current, other teams such as IT operations and networking should be required to update the database as changes occur. Asset owners should be held responsible for entering and maintaining information about the devices that they are responsible for. If changes are made to an asset, such as being decommissioned, an update to the CMDB should be done. This will help ensure that everyone has access to the latest information about what is on the network. Having current and relevant information is key to providing effective security. Creating a CMDB is the easy part. Maintaining it is the challenge.
Entries in a CMDB need a certain level of detail in order to be useful. Here is an example of the attributes each entry should have:
· Asset name
· Asset type
· Owner
· Description
· Operating system
· IP Address
A CMDB is only as good as its content. Therefore, ideally, it should be mandated that all asset owners review the CMDB on a regular basis and ensure that the information regarding assets they are responsible for is current. Part of the process for implementing new assets, or removing them from the network, should also be to update the CDMB. The effort spent maintaining asset information will prove its value both in terms of security and effective change management.
Because maintaining an asset database is fundamental to any effective information security program, it is considered a level 1 security objective.
1.1.2 Anti-Virus (AV)
Level 1 - Anti-Virus (AV) is a security solution that has one the longest histories in endpoint protection. Due to its signature-based approach of identifying malicious software, its relevance has diminished over time to the point that organizations like Netflix have discontinued its use so that resources can be focused on more effective security controls.[5]
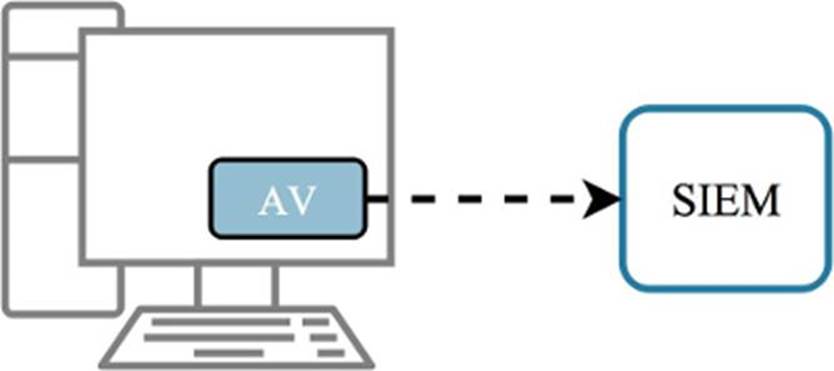
Figure 1.1: An endpoint protection agent is installed and runs on the device, with the option of sending security alerts to a centralized log repository.
The reason for the growing irrelevance of anti-virus software is that malware creators have discovered innovative ways to defeat signature-based detection by employing techniques such as polymorphism, which results in malware that is unique to each installation. The signature database used by AV can’t keep up with all of the new malware strains and permutations that are discovered daily.
Many still believe that AV still provides value as it handily detects and quarantines legacy viruses, worms and Trojans that have been plaguing PCs since before the Morris worm began defining the threat landscape almost 30 years ago.[6] These legacy threats still exist, even though not nearly as effective as their modern counterparts. For example, a maker of police bodycams was discovered to be shipping products with the Conficker-B virus pre-installed (malware which wreaked havoc in 2008.[7]) It was partially effective in spreading because newer cyber security controls do not protect against this “ancient” malware.
As long as samples from the malware museum continue to popup occasionally in the wild, it will still be some time until AV no longer has any protection value. Therefore it continues to be a fundamental component of most information security programs, and is considered a level 1 security objective.
1.1.3 Host Based Intrusion Detection System (HIDS)
Level 2 - A host based intrusion detection system (HIDS) is a software agent that runs on the device, providing alerts if threats are detected. HIDS monitors several different properties of a device, including:
· Software processes that are running
· Objects loaded into memory
· Network activity
· Changes made to the underlying operating system such as Windows registry settings or system file changes
HIDS is watching for behaviors that are suspicious, such as actions associated with previously-detected malware, or actions that are a-typical (otherwise known as anomalous behavior.) This is because the signature matching approach commonly used in AV is no longer effective. Since new malware variants and variations pop up every day (as many as 1 million per day per a 2015 study [8]), it is difficult to specify exactly what malware looks like anymore. HIDS makes an attempt to take a more heuristic approach for making detection possible.
Because of the challenge of tuning a HIDS to reduce the chance of false positives, it is considered a level 2 security objective.
1.1.4 Host Based Intrusion Prevention System (HIPS)
Level 2 - An easy way to think about host intrusion prevention system (HIPS) is as HIDS with teeth. Instead of just detecting malicious activity on a device, HIPS also has the ability to prevent that activity from taking place. HIPS offers not just a detective control, but a protection controlas well.
With the additional ability to block actions, HIPS could easily mistakenly identify benign activities as malicious and take action. These are known as false positives. Therefore, it takes a certain level of confidence in the protection software to allow it to autonomously take these sort of actions
There are many examples of legitimate changes taking place, such as the installation of patches, that were mis-identified and resulted in catastrophic events such as the Windows BSOD (blue screen of death), which quickly spread across enterprises like a cobalt fire.[9] This errant patch had to be quickly rolled back and caused Microsoft some embarrassment for having failed to test the patch more thoroughly. This also provided a valuable lesson. Best intentions aside, any change runs the risk of breaking something.
When implementing HIPS, it is recommended to run it first in detect-only mode for a training period of around 30-90 days. During this period the software will generate alerts when it detects something that it would have otherwise acted on if it were in protect mode. This way, a human can make the final decision whether or not the action should have actually been taken, and tune the product accordingly. This learning period provides the opportunity to filter out the false positives, and tune the software to the point that it is safe enough to enable its protection capabilities.
Because of the challenge of tuning a HIPS to reduce the chance of false positives, it is considered a level 2 security objective.
1.1.5 File Integrity Checker (FIC)
Level 3 - A file integrity checker (FIC) monitors specific files on a device for unauthorized changes. Critical system files, whose alteration could result in system compromise, is a good place to start. However, files change all the time on a device. The key is to determine which files are worth monitoring from a security standpoint, and making the FIC aware when authorized changes are going to take place to prevent false positives from being triggered.
Ideally, your organization has a base image of all operating systems used on the production network. This helps identify what the system files should look like. Any difference between the base image version of a file, and what resides on a device, should be investigated to rule out malicious activity. The FIC can do these comparisons.
An FIC runs on a device and takes regular (e.g. daily) fingerprints of the files being monitored. This fingerprint is often in the form of a checksum, otherwise known as a hash value. Any change in a file will result in a completely different hash value compared to the fingerprint of the file before the change.
Figure 1.1: There are several Windows 10 system files whose integrity you may want to monitor.
A checksum is the output of an algorithm called a one-way hashing function. Commonly used hashing algorithms are MD5 and SHA (the former is not as strong, and therefore should not be used, compared to the latter.) Using older or deprecated hashing functions runs the risk of not getting a truly unique hash value for each file. This makes file integrity checkers that use these suspect functions less effective.
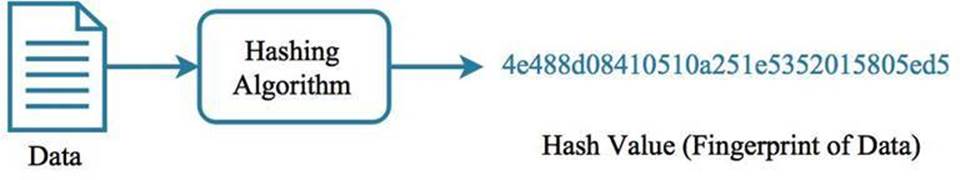
Figure 1.2: Example output of OPENSSL SHA-1 hashing function, to get the hash (or fingerprint) of the Java compiler on a Mac OS device. A file serves as input to the hashing function, and the output is the hash value or fingerprint.
Figure 1.2 shows what a FIC does on a much wider scale. The FIC will also generate alerts to appropriate personnel if file changes are detected.
Files change periodically. Systems and software get updates, and patches are installed to address security vulnerabilities. Remember: if software cannot be updated, it should not be used. The reason is that no software is 100% bug-free nor 100% secure. Eventually a problem will be found that needs to get fixed, and security vulnerabilities should be patched as quickly as possible.
When software is updated and associated files are changed as part of a planned update, the FIC should be made aware of the change ahead of time so it does not trigger any unnecessary alerts. Tight coordination is therefore required between the teams making changes and the team that maintains the FIC agents running on the endpoints. This way false positives will be reduced. Having this intra-team coordination can be a challenge that causes many organizations not to deploy a FIC, despite the security benefits it can provide. This is why it is designated as a level 2 security objective.
1.1.6 Host-Based Firewall
A host-based firewall is a software agent that runs on a device, with the goal of preventing certain (ostensibly malicious) data from being sent to or received by the device. This section will discuss two types of host firewalls: network and web browser.
1.1.6.1 Host-Based Network Firewall
Level 1 - A host-based network firewall runs on a device, with the purpose of preventing certain network-based activity from being received by the host it is running on. This type of firewall is not to be confused with a general network-based firewall, whose focus is on the entire network. The focus of a host-based network firewall is the individual device it is installed on, and these types of firewalls are bundled with most modern operating systems.
Firewalls can be set to allow traffic only from specific IP addresses and ports. A port can be referred to as a service running on a device. A web server, for example, is a service, and by default it uses port 80. By having a firewall on a device, most of the traffic inbound to the device (which includes malicious traffic) is blocked. If tuned correctly, the firewall will only allow legitimate traffic through.
When a new device gets connected to the Internet, it takes just a matter of seconds until network logs start to show evidence of scans, probes and generic attacks from IP addresses located throughout the world. To protect the device from this type of malicious activity, a firewall will block all unnecessary ports, thereby reducing the attack surface of the device.
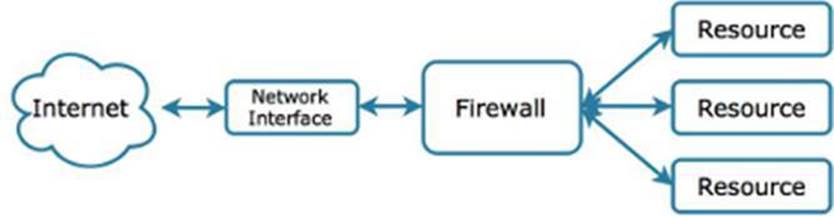
Figure 1.3: A host firewall intercepts all network traffic to and from resources on the device being protected.
The challenge of using a host-based network firewall is that it may block addresses and ports used by legitimate software on the device. Therefore, there may be some tuning required so that the balance between security and usability is assured.
Blocking unnecessary ports is fundamental to IT security, and so it is considered a level 1 security objective.
1.1.6.2 Web Browser Firewall
Level 2 - There are several web browser add-ons (also known as extensions and plug-ins) available that prevent a device from downloading malicious content embedded within a web site. These types of add-ons can be categorized as web browser firewalls. By using this type of control, malicious content such as malvertising can be blocked. Malvertising is the delivery of rogue web ads that have a malicious payload. Per a December 2015 article, Motherboard reported that “rogue ads had been diverting visitors from DailyMotion, one of the top 100 sites according to Alexa, to a malware-laden web page.”[10]
A web firewall can prevent this type of malicious payload from being executed by a user’s web browser or plug-ins it uses such as Adobe Flash (recently renamed Adobe Animate CC.)
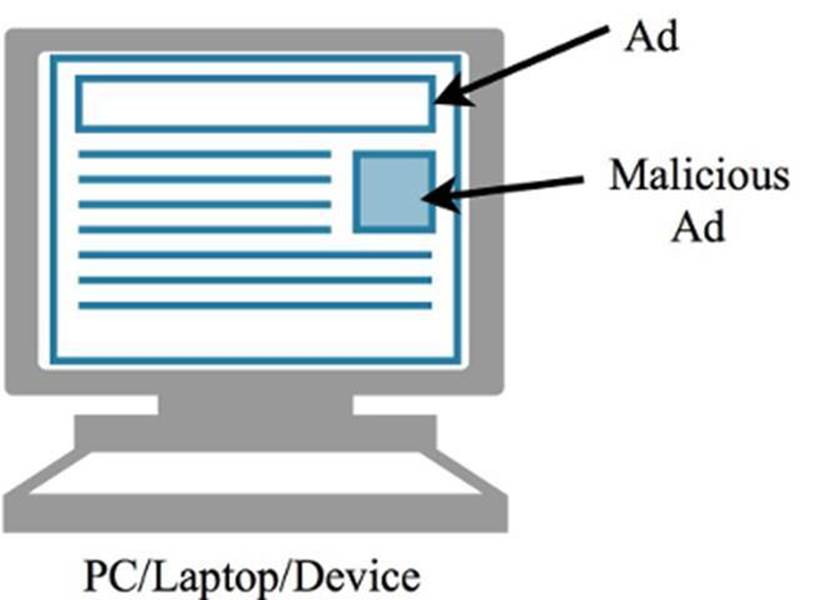
Figure 1.4: Adversaries will sometimes submit malicious ads to ad providers, which are then served to and executed by a victim’s web browser if no protection is in place.
The origin of many banner ads is not easily determined, and this gives cover for attackers to supply malicious content to otherwise legitimate ad providers. What is especially dangerous about malicious ads is that in many cases it does not require user action for the payload to be executed; the ad just has to be displayed in the browser. For this reason an organization may want an ad blocker plug-in as part of the standard software. If this is not possible, consider not running Flash by default. Ads can also be blocked by a network proxy, which is discussed later in this section.
As it can be a challenge to manage the plugins installed in web browsers on endpoint devices, this is considered a level 2 security objective.
1.1.7 Other Host-Based Security Solutions
There have been several security solutions that have been integrated into operating systems, providing new and innovative ways to protect a device from attacks. New protection mechanisms are discovered as a result of analyzing past attacks. Microsoft has received a priceless education in dealing with security issues with their software. As a result, they can be consider one of the most security aware and capability software vendors today.
The following are some of the controls that have been incorporated into many operating systems to mitigate memory-based attacks that have been seen the past.
1.1.7.1 Address Space Layout Randomization (ASLR)
Level 1 - Address Space Layout Randomization (ASLR) was developed in response to the way attackers could take advantage of how operating systems used memory. The adversary was able to determine where in memory objects were stored. The locations were the same regardless of what computer was used; the software loaded objects in memory the same way every time. This was due to a phenomenon of how software and operating systems used memory. This made the memory predictable, which in turn provided attackers the opportunity to manipulate objects in memory and perform attacks.
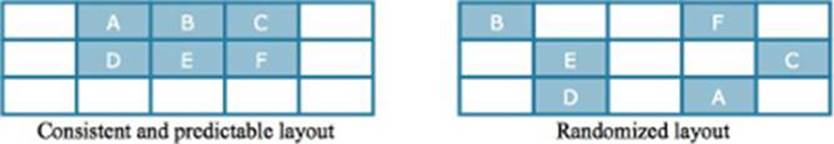
Figure 1.5: Before ASLR, software would store objects in memory in the exact same way, making it predictable and vulnerable to attack. ASLR randomizes objects in memory, making life more difficult for the attacker.
As a result of ASLR, memory locations are randomized every time the software runs, protecting endpoints from several memory-based attacks. Since it is resident in most modern operating systems, its implementation is trivial, making it a level 1 security objective.
1.1.7.2 Data Execution Prevention (DEP)
Level 1 - Data Execution Prevention (DEP) is another memory-protection mechanism focused on where in memory software is allowed to run. Memory, at a high level, is of two types: the stack and the heap. The stack is where programs commonly execute; the heap is where objects used by the program are stored.
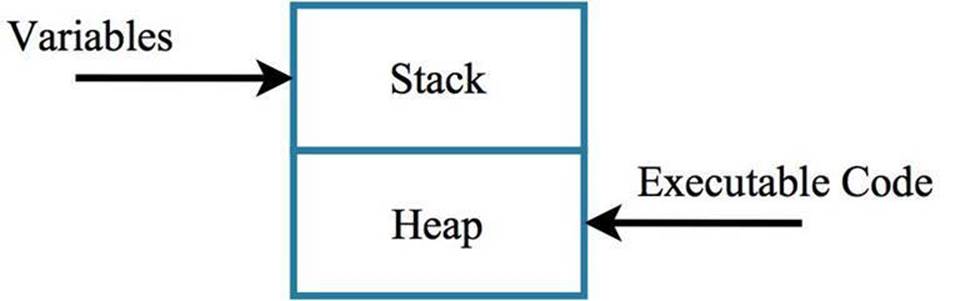
Figure 1.6: Memory at a high level is divided into the stack and the heap. Restricting where code can execute prevents certain types of memory-based attacks.
Previous to DEP, operating systems allowed software to run from any memory locations, which provided adversaries an opportunity. An attacker could add instructions to the storage part of memory (the heap), then exploit a vulnerability that would cause this code to execute. Because the heap was designed to be very accepting of any types of objects or data, malicious code could also able to be loaded (or injected) into this part of memory. Once the code was loaded, it could then be called and executed.
DEP is now integrated into many operating systems and computing devices. It runs transparently in the background, and by default, with no user interaction required. It may cause problems with the odd piece of legitimate software, but the security benefits it provides far outweigh any compatibility issues. In most cases, it still can be disabled to accommodate the fringe program that still requires the flexibility of loading executable code into the heap. Because it is integrated transparently into most modern operating systems, it is considered a level 1 security objective.
1.1.7.3 Containerization, Virtualization and Sandboxing
Level 3 - Another method for protecting a device from attacks is to run software in a container. This container is referred to as a sandbox or Virtual Machine (VM). The container is virtual, meaning it is software-based, so the protection it offers is only as good as the virtualization software.
A container allows the device to run software in a space that is isolated from the host device. Each container can have its own memory and storage that is independent of what is used and accessible by the underlying host. As a result, the operating system is not impacted if the software running inside the container (such as a web browser) becomes infected by malware.
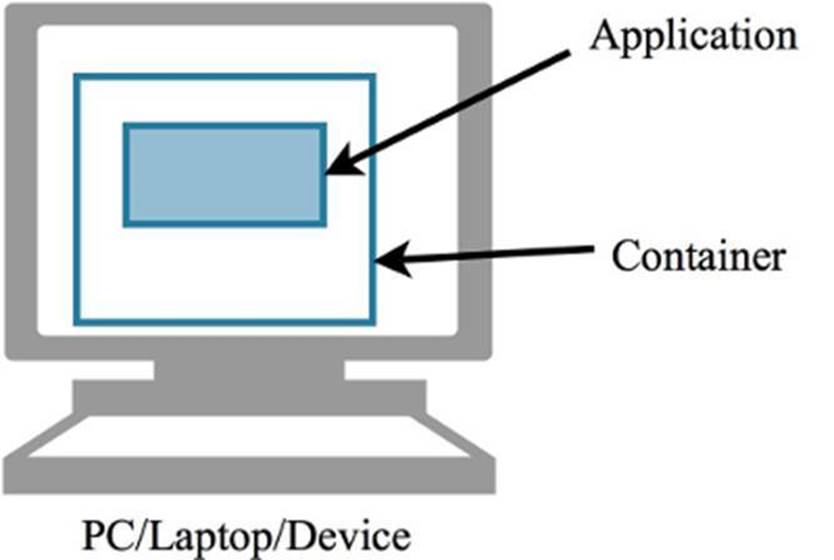
Figure 1.7: An application (guest) that runs in a container insulates the underlying operating system (host) from infection.
This approach to running programs cannot guarantee that the host is 100% insulated from what runs within the container, however. While that is the intent, weaknesses are occasionally found in virtualization software that makes these containers porous and expose the underlying system to attack.
Virtualization servers host several guest VM’s at the same time. These VMs could serve as the desktops used by employees instead of legacy thick-client desktops. A risk of using virtualization servers to host multiple VMs is that if one VM gets compromised, it is possible (if the virtualization software has a certain vulnerability) for the malware to have access to all the guest VMs running on the host.
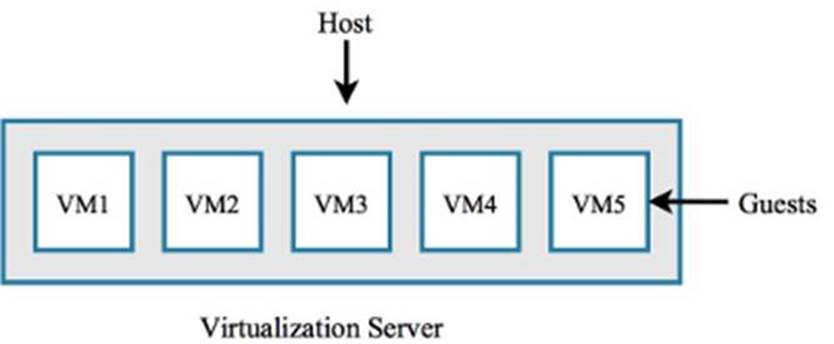
Figure 1.8: By having multiple guests hosted by a virtualization server, isolation between the VMs is possible.
Many newer operating systems automatically also use containerization (or sandboxing) natively. Newer versions of Windows, such as Windows 10, use virtual sandboxing to run programs safely, protecting the host operating system from malicious code execution. Adobe Reader (starting with version 10) launches a container for viewing PDF files (since these types of documents have for years been a popular way to deliver malicious code.) The most popular web browsers also use sandboxing to limit or defuse payloads downloaded from malicious or compromised web sites.
The risk of relying on the virtualization or sandboxing software to enforce containerization should first be understood and formally accepted. Security researcher Tom Henderson sums it up well: “Sandboxes are made of sand, not concrete.” Because of the complexity involved in securely deploying a virtualization solution, it is considered to be a level 3 security objective.
1.1.8 Digital Certificates
Digital certificate are a way to provide a digital identity of an entity. It is the digital equivalent of hand-signing paper checks. To create a digital signature, a public-private key pair first needs to be created. There are several open source and vendor tools available to do this. The private key used for creating the digital certificate needs to be protected, and the certificates created should be set such that the key is non-exportable. That means the private key cannot be extracted from the certificate. If the key can be copied, then it is difficult to verify the authenticity of anything done with the key, such as authentication or code signing.
The next step for obtaining a digital certificate is to generate a certificate request (also known as a Certificate Signing Request (CSR)). The private key is used to generate a CSR, and once created it is sent to a Certificate Authority (CA). The CA needs to be trustworthy and legitimate if you want other people, software, web browsers and operating systems to consider any certificate it creates as valid. By default, web browsers trust a slew of certificate authorities, meaning any HTTPS web site that uses a certificate signed by one of these trusted CA’s is also is considered trustworthy by proxy. Tip: Have a look at the list of CA’s that your web browser trusts by going to the browser settings; you might be surprised at some of the CA’s that are trusted by default.
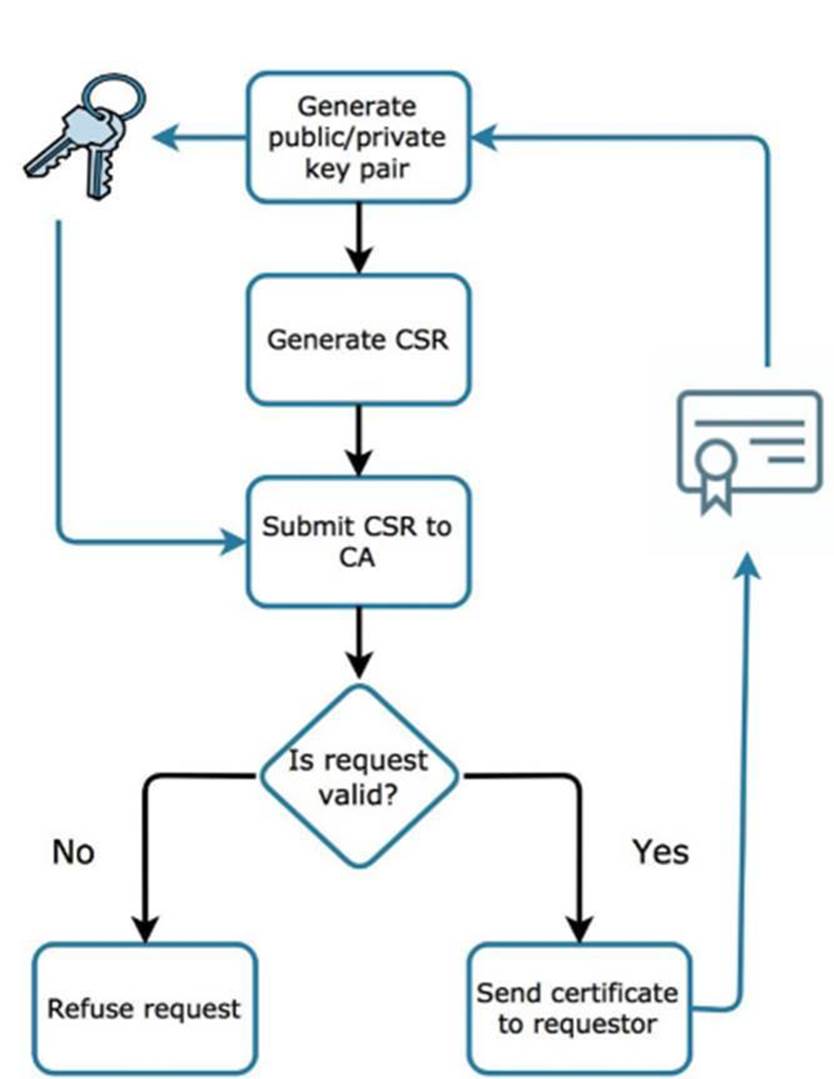
Figure 1.9: A digital certificate is created by a certificate authority in response to receiving a valid certificate signing request.
If the CSR is valid, the CA generates the digital certificate and sends it to the requestor. This certificate is now ready to use to secure web sites, sign code and emails, etc. The following are a few more topics to be familiar with when it comes to understanding digital certificates.
1.1.8.1 Authentication
A signed digital certificate can be installed on a device to allow it to authenticate and connect to a network. The protocol 802.1x is the most popular way to use this form of authentication. By using this type of authentication, an organization can limit access to the network to only those devices that have the organization’s digital certificate installed on it. This is also known as a “something you have” type of authentication.
For example, the organization’s CA can install the network certificate on authorized devices. Any device that does not have one of these certificates will not be allowed to connect. This can prevent unauthorized or “rogue” devices from gaining access to production resources.
1.1.8.2 Code Signing
Organizations should allow only approved and legitimate software to run on devices on the network. One way to verify that software is legitimate is to validate the digital certificate that was used by the author of the software to sign the code. Code signing provides proof that an authorized entity created and made modifications to the software. The legitimacy of the certificate (and therefore the signature) depends on the CA that issued the certificate. Certificates that are self-signed do not provide much value, since the author is basically vouching for her/himself.
Most operating systems now automatically enforce code signing validation of software. Applications that are not signed, or signed by an untrusted CA, will not be executed. In these cases, the operating system will request the user to explicitly allow the untrusted and unverified software to run, since this can pose a significant security risk.
1.1.8.3 Certificate Revocation List (CRL)
Software and operating systems can validate a digital certificate by checking its properties such as its expiration date. This validation process also needs to include a check to see if the certificate has been explicitly revoked. One way a certificate will be revoked is if a certificate or the key used to create it has been compromised. The check for revocation is done by automatically consulting Certificate Revocation Lists (CRL.) Therefore, to support this check, network connectivity to CRL’s, which are often hosted on remote servers, needs to be ensured.
Similar to a CRL, Microsoft operating systems use a Certificate Trust List (CTL). In September 2015, Microsoft discovered that digital certificates from a trusted vendor were leaked and used by miscreants to spoof legitimate software.[11] By having those certificates revoked, users were protected from any malware signed with those compromised certificates.
1.2 Network Protection
A network can be considered to be the circulatory system of an organization, as it provides just some of the following:
· Connectivity to printers and scanners
· Access to data repositories and cloud-based apps
· Instant messenger and chat
· Streaming music (to help us focus on work)
· Voice over IP (VoIP)
· Web browsing
Just as a network provides a conduit for legitimate activity, it is the same system that can be leveraged by adversaries to monitor activity, exfiltrate sensitive data, and install backdoors and other malware. So it goes without saying that the security of the network is paramount.
Wi-Fi may be offered by the organization to provide Internet connectivity for employee-owned mobile devices. A recommended way to provide this Wi-Fi service is to actually have two separate networks: one for production access, and one for guests and personal use. While there should be monitoring in place for the production network, you may want to forego any monitoring of the guest network. The reason for this is that there may be activity that the organization does not want to be liable for. If this network is not monitored, then this provides plausible deniability in the event that malicious, inappropriate or illegal activity is discovered to have been performed by someone utilizing this network.
Organizations are increasingly depending on cloud service providers for file and data storage, software as a service (SaaS), computational power, etc. Yet, this means using and relying on networks that are out of the organization’s direct control. Trust has to be extended to these providers. The challenge is being able to take advantage of everything the “cloud” provides while not increasing the risk to the organization, nor expanding its attack surface. The importance of performing a thorough review of agreements with cloud service providers cannot be overstated. Protections should be in place that prepare for worst-case scenarios, so that if catastrophe does strike (such as a data breach by a cloud service provider) the organization will be better protected and prepared to deal with it.
The following discusses several network-based security controls that are available, as well as different aspects of network-based protection.
1.2.1 Firewalls
A firewall is the classic example of a security device that organizations rely on for protection from network-based attacks. A firewall is commonly installed at the perimeter that separates an internal network from the Internet. Firewalls can also be installed on the internal network to provide additional protection to network segments that host sensitive resources like employee or credit card data.
The Internet perimeter is the front line, and the firewall installed at this location will routinely observe and block scans and other attacks from getting through. Firewalls, however, have evolved to do more than control the flow of individual packets. Now the term “firewall” has been extended to appliances that specifically protect databases and web applications, as well as solutions that provide several different forms of network-based protection. The following section discusses some varieties of firewalls that should be considered.
1.2.1.1 Network Firewall
Level 1 - A network firewall is used to limit access to devices, other networks, and segments of a network. It inspects the attributes of individual packets, and can analyze them in different ways. It can also operate at different network layers.
Billions and trillions of packets may traverse an organization’s network every day, and each packet has several properties and layers. The Open Systems Interconnection (OSI) model was created to provide a logical view of the different layers that make up a network packet.
|
Layer |
Description |
|
7 |
Application |
|
6 |
Presentation |
|
5 |
Session |
|
4 |
Transport |
|
3 |
Network |
|
2 |
Data Link |
|
1 |
Physical |
Table 1.1: There are seven layers to the OSI Network Model. Inspection of several layers of network packets is an example of a defense in depth strategy.
Another challenge is to not block legitimate traffic. As the primary function of a firewall is to get in the way, there will sometimes be legitimate traffic that is blocked. When one of these unintentional blocks does occur, there should be a process in place so that the issue can be researched and quickly resolved. And any changes that are made should be documented to help support and potentially roll back these changes in order to keep the network running.
Some organizations err on the side of security; some err on the side of availability. How much traffic a firewall blocks goes towards maintaining the balance of security versus usability. A network that is very secure but unusable is worthless to an organization, but the same could be said of the opposite.
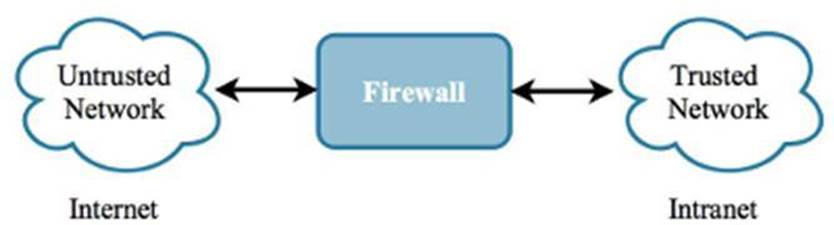
Figure 1.10: A Network Firewall can protect against scans and attacks launched from an untrusted network.
Maintaining network firewalls is one of the most technically complicated parts of an IT infrastructure. Firewalls use policies and rules to determine which packets get blocked and which ones get to go through. These policies and rules are determined by individuals and business units within an organization, and are implemented by the network operations team. The rules can quickly get very complex. Consider using a tool that provides a way to clearly manage these policies and rules, as well as graphically display the devices, networks, and the connections between them. Using a tool like this can provide documentation that is both accessible and understandable, though it goes without saying that this information should be considered sensitive (so protect it accordingly.) A network firewall is considered a fundamental part of IT security, and is considered a level 1 security objective.
1.2.1.2 Web Application Firewall
Level 3 - A web application firewall (WAF) can be used at the perimeter to protect web applications that face the Internet. A WAF is a security appliance that is focused on the uppermost layer of the network stack: layer 7, otherwise known as the application layer. This type of firewall examines all the requests that are sent to a web application, as well as the responses that the application returns. The WAF can block malicious content from coming or going, as well as sanitize the data so that it causes no harm on receipt.
A challenge to implementing a WAF is that this device first needs to “learn” the code of the web application it is protecting. Many WAFs have a learning mode that it can be put into for a few weeks or months at the beginning of an implementation. While in learning mode, the WAF observes web usage activity, and over time determines what “normal” looks like. This helps reduce the number of false positives the WAF reports. “Normal” is subjective because applications can be coded in myriad ways yet produce the same results. Without learning, some of these coding choices would be considered malicious to the WAF.
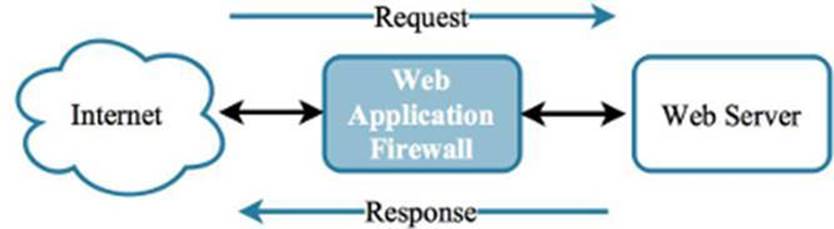
Figure 1.11: A WAF offers web-specific protection for web applications.
Another benefit of a WAF is that it can also provide virtual patching. Some applications and servers cannot be immediately patched, even in the face of zero day vulnerabilities. A WAF can prevent attackers from being able to exploit vulnerabilities before they are properly patched by blocking these attacks from ever reaching the web application.
For example, early in 2015 a critical vulnerability in the Apache Struts2 framework was discovered. This is a framework behind many Internet web sites and applications. The cause was determined to be a flaw in the underlying language: Java. A fix for Java was not planned to be released quickly. The Apache Foundation was able to respond more rapidly however, and they did so in the form of a rule that could be applied to web servers. This prevented attacks from ever reaching the Struts2 vulnerability, thereby protecting web applications that used this framework until the Java patch was made available and installed.[12] In this example the Apache web server rule is a virtual patch, which is a tactical (short-term) fix; patching Java is the strategic (long-term) fix.
Because the implementation of a WAF requires administration by someone well versed in web application development, it is considered a level 3 security objective.
1.2.1.3 Database Firewall
Level 3 - A database firewall is another type of layer 7 firewall that is tuned specifically to look at database-related syntax being sent to a database. This appliance usually sits in front of a database, so any commands sent to the database are first evaluated, at which point an alert may be generated and the query may be blocked. A database firewall can prevent attacks like SQL injection from reaching its intended target. However, before implementation a learning period is required so that the database firewall can learn what legitimate queries can be expected and should not be blocked.
A database firewall can protect a database that serves as a backend for an application. For example, an app may have a security vulnerabilities such as SQL injection, due to a lack of input validation. For vulnerable applications like this, a database firewall can be used to provide “virtual patching.” This would protect the database from receiving malicious SQL statements that are not blocked by the application in front of the database.
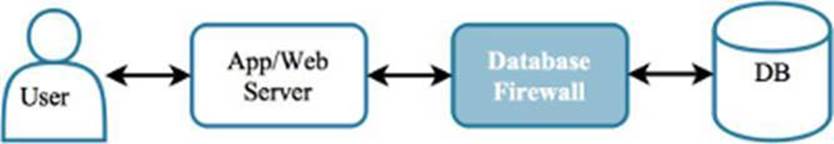
Figure 1.12: A database firewall inspects and filters commands before they reach a database.
A challenge is that structured query language (SQL) databases are being usurped by NoSQL and other non-relational databases, where the syntax is very different. Any worthy database firewall product, however, should be able to protect the latest incarnations of data repositories. As implementation of a database firewall requires someone who is very familiar with how database queries as structured, this is considered a level 3 security solution.
1.2.2 Network Intrusion Prevention System (NIPS)
Level 2 - A Network Intrusion Prevention System (NIPS) is a device that monitors network traffic very similar to how a firewall inspects network packets. In most cases, the NIPS is installed at the perimeter to protect an organization’s internal network from Internet-based attacks. An intrusion detection system can be considered the next evolution of a firewall, as it does the following:
· Uses more sophisticated methods of inspecting packets
· Examines different layers of the network packets
· Evaluates a collection of several packets to identify patterns or anomalous behavior
It can be a challenge to tune a NIPS properly so that it does not alert (or even worse, block) based on false positives. The first phase of implementation should be to put the NIPS into alert-only mode so that it can be tuned so that only meaningful alerts are generated.

Figure 1.13: A NIPS monitors and can block traffic coming from the Internet before it reaches the internal network.
The earlier version of a NIPS is a network intrusion detection system (NIDS), which only provides alerts and does not have the capability to block any network traffic. A NIDS has been replaced in most cases by a NIPS, which provides the option of actually blocking malicious traffic. As a NIPS is considered a step above a firewall, which is fundamental to a security program, and so it is considered a level 2 security objective.
1.2.4 Malware Prevention System (MPS)
Level 3 - An MPS (also known as a Malware Analysis Appliance) can be an effective way to prevent malicious applications or scripts from landing and executing on. An MPS is installed at the network perimeter and needs to have a way to intercept binaries file for inspection. One way is to have the MPS interface with an email gateway so that email attachments are stripped and fed to the MPS for inspection.
An MPS is focused on the application level of network activity, and examines file employees download during the course of the day. These files could deliberately downloaded, or accidentally (such as clicking the wrong link in an email.). Regardless of the file or its delivery method, when downloaded, the MPS makes a copy of the file and executes (or detonates) it in a container that the MPS starts up just to analyze the file. The analysis will observe and record the actions that the file performs, such as:
· Network connections
· What is loaded into memory
· Files that are accessed or changed
· Registry changes
· Processes it spawns
Based on the analysis, and comparison with signatures of other known malicious files, the MPS forms a conclusion about whether the binary has evil intent or not.
However, it is possible that the first infection may not be blocked. This is because a typical implementation of an MPS is to install it so that it is not in-line; the MPS receives a copy of the attachment while the original attachment is still delivered to its intended recipient. This is because no conclusion has been made yet about the file. If an MPS does identify the file as malicious, it is an option for the MPS to then alert the email gateway or another security appliances so that any future downloads attempts of the same file are blocked.
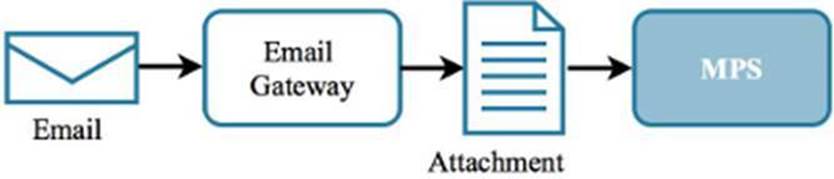
Figure 1.14: In this MPS configuration, an MPS receives a copy of binary files that are attached to emails received by the email gateway.
An MPS is a solution that should be considered only after more fundamental security controls have been implemented and have proven to be effective in contributing to the overall security of the organization. If that is the case, then an MPS makes an excellent addition to an organization’s information security arsenal. Since an MPS is appropriate for a more seasoned and well-staffed security operations team, it is considered a level 3 security solution.
1.2.5 Email Gateway
Level 2 – Email is one of the most effective ways to deliver malware. Once installed, it is possible for an adversary to obtain a foothold on the network and pivot to other endpoints, eventually finding their way to protected resources like databases, file shares and sensitive emails.
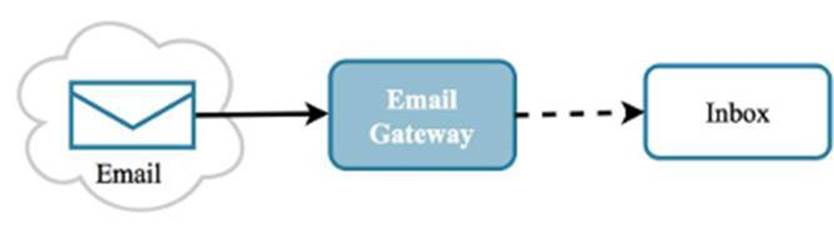
Figure 1.15: All email bound is first received by an email gateway for inspection and possible subsequent delivery.
An email gateway can be implemented in-line so that all emails have to be analyzed and determined to be safe first before being delivered to employee inboxes. It may also be able to analyze attached files, similar to how an MPS runs binaries in a dedicated container. Some versions of a gateway can also analyze and sanitize any links contained in the email body.
Given that email is the most popular way for adversaries to get malware installed on a network, an email gateway may be considered a fundamental part of an organization’s information security program. However, given its complexity and reliance on a seasoned email administrator to implement and operate it properly, it is considered a level 2 security objective.
1.4.2 Level 2
· Host Intrusion Detection System (HIDS)
· Host Intrusion Prevention System (HIPS)
· Web Browser Firewall
· Network-Based Proxy
· Network Intrusion Prevention System (NIPS)
· Email Gateway
· Internet Proxy
1.2.6 Internet Proxy
Level 2 - A network proxy is an appliance that can be installed in-line between the Internet and the internal network. All Internet-bound requests, such as visits to web pages, flow through the proxy where the request is evaluated and categorized. Some examples of these categories include:
· Controlled Substances
· Gambling
· Commerce
· Phishing
· Software Downloads
The organization sets the Internet policy, which can be to block certain categories of web sites. It is an imperfect science however, and legitimate sites will occasionally be blocked. When this happens, users should have a process to request that the site be unblocked. This process should also include a security review to determine whether or not the site is safe to be accessed.
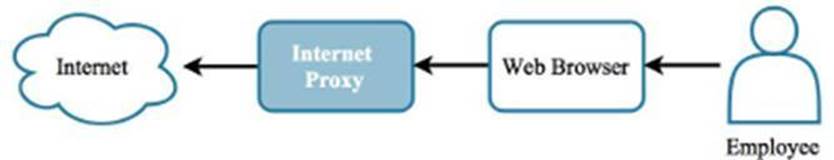
Figure 1.16: A proxy determines whether or not to let user web site requests proceed to the Internet.
Having a proxy in place to intercept web site requests also lets the security team explicitly add blocks to a policy in response to information (or “intel”) received about sites that host a malicious payload. A web proxy should be considered essential for any organization that allows Internet access from a production network.
As there is the risk of blocking legitimate sites, and the need to have staff available for adding and removing sites in a timely manner, this is considered a level 2 security objective.
1.2.7 Jump Server
Level 3 - The use of jump servers allows an organization to limit access to production systems. A jump server can also serve as the only way to provide limited access from an internal network segment to a more exposed network segment or zone, such as a DMZ. Proper implementation requires locking down the network and production systems so that the jump servers are the only interface available to access them. A jump server can provide several features, such as:
· Not granting users administrative access to production systems
· Logging commands that are executed by a user
· Limiting what commands a user can execute
A user first logs onto a jump server. Once logged on, the user can then gain access (or “jump”) to one of the production systems the jump server has access to. Since all commands issued by the user are first sent to the jump server, this server can filter commands so that only certain ones as passed to the production system.
Every command that the user executes can also be logged for analysis and generating alerts. An example of an action that may generate an alert is when a user attempts to add a new account to a production system, which could indicate a breach of policy or something malicious being attempted.
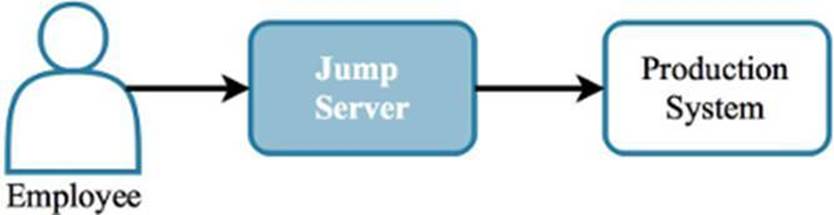
Figure 1.17: A jump server protects production systems from direct access and can log commands issued by users.
Mandating that employees access production systems only via jump servers helps limit what employees can do, and logs what actions they do (or attempt to) perform.
1.3 User Awareness and Education
Level 1 - Users are on the front line of protecting an organization. It is often not by technical means that an attacker illicitly gains sensitive info, access to systems, and footholds on a protected network. Instead, age-old methods of social engineering are often used, where the user is tricked into performing an action. People are manipulated using various techniques, often by exploiting trust and fear, so that the user does not think before acting. The goal is to get users to think first, especially when it comes to clicking links, opening attachments, or disclosing information.
Education about social engineering attacks and techniques can take several forms, including:
· Giving presentations to different groups
· mails sent by leadership
· Sharing news stories of victims that fell prey to attacks
· Inviting a law enforcement representative to provide awareness training to the company
Phishing currently is the most effective way to get malware installed on devices. The installation of malware can lead to compromise of not just a single user, but potentially of the entire organization as it propagates throughout the network. Therefore, phishing awareness training should be included in an overall security awareness program.
An effective method for teaching users how to identify phish and what to do (or not do) when a phish is encountered is to leverage a phishing awareness program. This can include actually sending a fake email to employees and taking note of who clicked a link contained therein. There are several tools available that allow you to create these types of educational phishing campaign. These tools allow you to observe and report on the results, and even provide user awareness training to those who took the bait. SANS is one such organization which offers a phishing awareness tool as part of their Securing the Human (STH) suite of their security awareness tools.[13]
Making users aware of the important role they play in protecting an organization, and equipping them with the cognitive tools needed to identify and react appropriately when receiving a social engineering attack, will significantly contribute to an organization’s overall security. As this is fundamental to any information security program of any size, it is considered a level 1 security objective.
1.4 Summary
There are many security solutions available for protecting endpoint devices, the network and end users, Using the right combination of controls that helps support the security concepts discussed in the previous section, helps reduce the risk of attack, and increases awareness of suspicious and malicious activity that may be taking place within an organization’s IT systems.
The maturity level assigned to each item represents the level of maturity an organization’s security team (or SOC) should be at to effectively implement the respective security control. It is recommended to pursue these security controls according to what is appropriate for your organization, and in the order of their maturity levels. The order of the items for each level does not represent their importance or the order in which they should be pursued.
1.4.1 Level 1
· Configuration Management Database (CMDB)
· Anti-Virus (AV)
· Host-Based Network Firewall
· Address Space Layout Randomization (ASLR)
· Data Execution Prevention (DEP)
· Network Firewall
· Security Awareness Training
1.4.2 Level 2
· Host Intrusion Detection System (HIDS)
· Host Intrusion Prevention System (HIPS)
· Web Browser Firewall
· Network Intrusion Prevention System (NIPS)
· Email Gateway
· Internet Proxy
1.4.3 Level 3
· File Integrity Checker (FIC)
· Containerization, Virtualization and Sandboxing
· Web Application Firewall (WAF)
· Database Firewall
· Malware Prevention System (MPS)
· Jump Server
1.5 Terms and Definitions
The following are the terms that were discussed in this section.
|
Term |
Definition |
|
Anomalous Behavior |
Strange or unexpected behavior that could indicate malicious activity |
|
ASLR |
Address Space Layout Randomization. This is a control implemented by PC hardware and operation systems to randomize how data objects are used memory. This mitigates certain types of memory-manipulation attacks from taking place. |
|
Attack Surface |
A description or how susceptible or exposed a target is to attack. |
|
AV |
Anti-Virus. A software agent that runs on a device, with the intent to protect it from malicious software. It is often signature-based, making it perhaps less effective than newer types of security controls. |
|
BYOD |
Bring Your Own Device. Organizations offer their employees an opportunity to use a personal device to connect to a production network. This is usually done by using containerization software on the device that provides a virtual separation of work and personal data. |
|
CA |
Certificate Authority. A trusted entity that issues certificates in response to certificate requests. |
|
Checksum |
See Hash Value. |
|
Cloud Computing |
A room full of servers somewhere on the Earth, and not floating above it. |
|
CMDB |
Configuration Management Database. A centralized repository of information about IT assets, such as computers and servers, that needs to kept current in order to be effective. |
|
Containerization |
Running applications with resources (memory, CPU, etc.) that are isolated from the underlying host operating system. |
|
CRL |
Certificate Revocation List. This is a list of digital certificates that have been revoked for various reasons, such as being no longer trusted or expired. This list is maintained and globally available. |
|
CSR |
Certificate Signing Request. A request issued to a certificate authority (CA) for a digital certificate. A certificate issued from a trusted CA should be considered more secure than a self-signed certificate. |
|
Decommission |
To securely retire a device so that it is no longer on the network and no longer in use. |
|
DEP |
Data Execution Prevention. This is a control implemented by computer hardware and operating systems to mitigate certain types of memory-manipulation attacks. |
|
Deprecated |
Something that is out of date, whose use is no longer recommended. A newer version, or its replacement, should be used instead. |
|
Detective Control |
A sensor focused on identifying certain behavior(s) taking place, at which point it can notify the user and/or security personnel. |
|
Digital Certificate |
A digital “something you have” form of authentication. |
|
DMZ |
Demilitarized zone. A segment of a network that sits between an internal (trusted) network and segment that hosts Internet-facing servers. This helps protect internal resource from Internet-based attacks. |
|
Exfiltrate |
To leak sensitive data out to the Internet or to unauthorized individuals. |
|
False Positive |
Something that is errantly considered to be negative, but after further investigation it is concluded to be benign. |
|
FIC |
File Integrity Checker. A software agent that runs on a device to help ensure the integrity of critical files. |
|
Hash Value |
The unique fingerprint of a file after running it through a one-way hashing algorithm such as SHA-256. |
|
HIDS |
Host Based Intrusion Detection System. Monitoring software that watches and issues alerts when malicious network traffic reaches the device. |
|
HIPS |
Host Based Intrusion Prevention System. Same as HIDS, but with the added benefit of being able to block traffic from reaching the device. |
|
Internet of Things (IoT) |
Devices of all shapes and sizes that are connected to the Internet. |
|
Jump Server |
Preventing direct access to servers by mandating that users log onto an intermediary server which provides limited and logged access to the target server. |
|
Malvertising |
Malicious web-based advertising such as banner ads that contain a malicious payload that infects the person viewing the ad. |
|
MD5 |
Message Digest Algorithm 5. A cryptographic hash algorithm used to verify the integrity of files and data. It is popular but no longer consider a secure option. |
|
Miscreants |
Adversaries, attackers and malicious actors. |
|
MPS |
Malware Prevention Solution (or System). An appliance or service that receives files (such as email attachments) and analyses them by running the file in a sandbox. What the file does as far as network connections, objects loaded into memory, registry changes it makes, etc. help determine whether the file is malicious or not. This is a signature-less or behavioral analysis form of malware identification. |
|
NIDS |
Network Intrusion Detection System. A system installed at the network perimeter that analyses network traffic to identify malicious traffic, and issue alerts if malicious activity is detected. |
|
NIPS |
Network Intrusion Prevention System. A system installed at the network perimeter that analyses network traffic to identify malicious traffic, and issue alerts if malicious activity is detected. It has an advantage over NIDS in that it can also block traffic that is considered malicious. |
|
OSI |
Open Systems Interconnection. A standards body whose purpose is to help standardize protocols so that they can be explained in a way that is more easily understandable. |
|
Polymorphism |
Changing the properties of an executable file (or binary) so that it evades signature-based detection. |
|
Protection Control |
A security control that blocks actions determined to be malicious from taking place. Also known as a preventative or protective control. |
|
Internet Proxy |
An appliance or service that serves as an intermediary between an end user device and the Internet. Its purpose is to restricting Internet access to only those sites that the proxy deems safe and appropriate, which can be based on the organization’s policy. |
|
SHA-1 |
Secure Hash Algorithm 1, a cryptographic hashing algorithm that can be used to verify the integrity of files and data. It is recommended over MD5. |
|
SHA-2 |
Secure Hash Algorithm 2, a newer cryptographic hashing algorithm designed by the NSA that is recommended over MD5 and SHA-1. |
|
SQL |
Structured Query Language. The syntax used by most major relational database vendors to interact with the data and structure of a database. |
|
Trojan |
Software that disguises itself as benign or beneficial, but in actuality contains a malicious payload. |
|
Virtual Patching |
Protection provided by an appliance such as a WAF that prevents attackers from exploiting vulnerabilities in an application or system before a patch is available or applied. |
|
Virus |
Malicious software with the intent to spread and infect hosts. |
|
VM |
Virtual Machine. A software-based container that runs on top of a host operating system. The container can run its own instance of software or an operating system in a way that insulates the underlying host for any infections the VM may experience. |
|
WAF |
Web Application Firewall. A security appliance that is installed in front of a web application to block malicious requests. A WAF can also provide “virtual patching” to mitigate vulnerabilities that cannot be immediately patched. |
|
Worm |
Software created with the primary intent to spread to as many hosts as possible. |
|
XSS |
Cross-Site Scripting. A type of attack that a web application may be vulnerable to due to insecure JavaScript code. |
|
Zero Day Vulnerability |
A weakness in software that is known to adversaries but not to the software manufacturer. Also known as an “O day.” |