HCISSP Study Guide (2015)
Chapter 4. Privacy and Security in Healthcare
Abstract
This chapter discusses the fundamental concepts of security and privacy and their impact on the healthcare industry. It will also review the relationship between privacy and security for healthcare organizations when managing and safeguarding healthcare information. General privacy and security principles in relation to specific healthcare industry standards will also be discussed.
Keywords
Privacy
Security
Confidentiality
Integrity
Availability
Access control
Data encryption
Data classification
Logging and monitoring
Least privilege
OECD
GAPP
PIPEDA
UK Data Protection Act
This chapter will help candidates
![]() Understand security and privacy concepts
Understand security and privacy concepts
![]() Understand the relationship between security and privacy
Understand the relationship between security and privacy
![]() Understand general privacy principles and standards
Understand general privacy principles and standards
![]() Understand sensitive data and handling implications
Understand sensitive data and handling implications
Introduction
Security Fundamentals
Confidentiality, integrity, and availability (CIA) are the foundational elements required to ensure privacy and security that users of the healthcare system deserve and expect. It is best to think of CIA as interrelated pillars that support privacy and security initiatives in healthcare. If any of the foundational elements are missing or vulnerable, privacy and security objectives within the healthcare system cannot be achieved. Confidentiality, integrity, and availability are often referred to as the CIA triad and usually represented in the model shown in Figure 4.1.
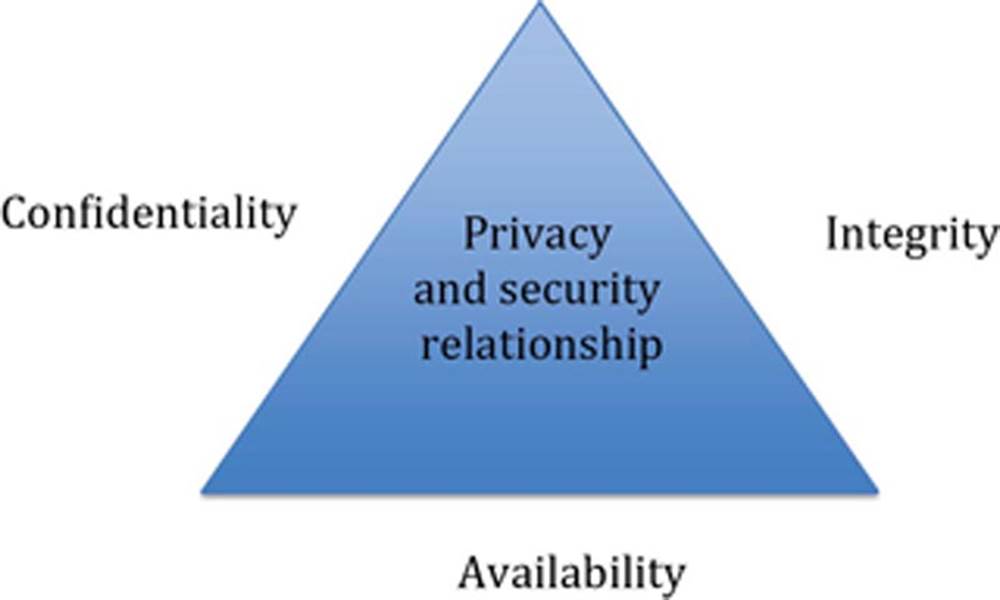
FIGURE 4.1 CIA triad.
Confidentiality
Under HIPAA, “Confidentiality means the property that data or information is not made available or disclosed to unauthorized persons or processes.” Simply put, confidentiality is about preventing unauthorized disclosure of healthcare information. Anytime sensitive healthcare information is accessed, viewed, or transmitted in an unauthorized manner, patient confidentiality is at risk.
Integrity
Integrity is formally defined by HIPAA as “Means the property that data or information have not been altered or destroyed in an unauthorized manner.” It is best to think of integrity as the reliability of information. Imagine the consequences to patient healthcare delivery if medical professionals make patient care choices based on inaccurate or unreliable data.
Availability
Availability is the third essential element to the CIA triad. Healthcare professionals require patient information systems to be there when needed. When critical healthcare systems are unavailable, quality healthcare services cannot be delivered in an efficient manner. Beyond efficiency, patient care decisions are significantly impacted when system or the information contained in those systems is unavailable. In many healthcare settings the system being down can be life-threatening rather than an inconvenience. Although HIPAA formally defines availability as “The property that data or information is accessible and useable upon demand by an authorized person,” one can see the importance of healthcare technology availability through the perspective of having the right tools to do the job. Modern healthcare has become reliant on technology as a tool for quality service delivery. Resilient healthcare systems are required to provide healthcare practitioners with the tools they need to perform their jobs on a daily basis. Just as in the past it would be unacceptable for a physician to visit a patient without his black bag and stethoscope, we cannot expect practitioners to provide services without high availability health information systems.
Security principles
One of the most effective ways to ensure CIA is to take a defense-in-depth or layered approach when addressing privacy and security issues. A tiered approach avoids a single point of failure and supports layered controls in case one of the controls is compromised or does not operate as intended.
Access Control
Access control is often the first and possibly most robust controls that can be implemented to ensure privacy and security in the healthcare environment. When you think about a typical healthcare environment and all the sensitive information present, you quickly understand the importance of limiting the access to that information to only authorized individuals who need to have access to the information in order to perform their job responsibilities and deliver healthcare services. Although similar in nature, it is important to distinguish between physical and logical access control. Since physical security is often the first line of defense we will start there. Since systems that store sensitive healthcare information are located within the physical walls of healthcare service providers, we can focus on the outside and work our way in. Considering the defense-in-depth security methodology, we are able to achieve our first layer of access control just by limiting physical access to information systems. This does not mean we do not need logical security, but rather we can gain some comfort in knowing that well-designed and properly maintained physical security access controls can deter or prevent unauthorized individuals from being able to physically access sensitive information or healthcare systems. Since we must avoid creating single points of failure and there are some threats that exist regardless of physical security controls, logical access controls are the next layer in effective security and required to support the CIA triad. Logical access controls should be developed to support the system architecture and be implemented at as many layers as possible. This typically means ensuring proper access control at both the network and system level. For example, a healthcare practitioner’s access should be controlled when he or she logs into the network and again when he or she wants to access a particular system hosted on the network. From a more practical and healthcare-focused view, organizations do not want just anyone to be able to view or access patient information. So do organizations just need to implement controls preventing only outsiders from accessing patient records? The answer is no. Just because a person is employed by a healthcare organization does not mean they should be allowed to access sensitive patient information. In fact, effective access control is based on the concept of least privilege (individuals should only be able to access the information required to perform their job – no more, no less) and we will discuss in greater detail a little later. Once a healthcare organization ultimately determines who should be able to access information, the next challenge becomes the “how.” Thinking back to our discussion on defense-in-depth, it makes sense that there is no single approach or access control to accomplish the task. In fact, the more layered the controls, the better. In order to understand how to best implement access controls, let us take a look at the three types of controls: administrative, physical, and technical.
It is best to think of these as independent but interconnected elements that work together to ensure appropriate levels of access control for healthcare organizations. Figure 4.2 shows the relationship among the control types.
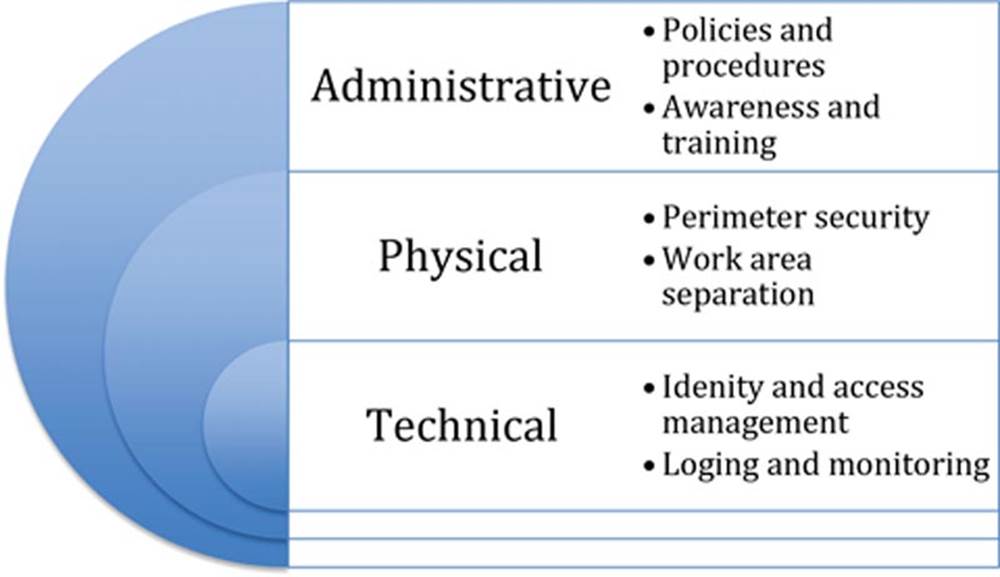
FIGURE 4.2 Relationship of control types.
Although the three categories work together and can be implemented independently, we recommend the sequence of administrative, physical, and technical and that is the order they will be discussed in this book. Administrative controls, when supported by senior leadership, set the foundation (aka “tone at the top”) for the organization’s access control objectives. These are often “soft” controls based on policies and organizational culture and regulatory requirements. Physical controls are usually the first layer of defense and often provide perimeter support for technical controls. These can range from door locks and ID badge systems to physical partitions separating employee work and patient care areas. Technical controls usually reside at the system level and are the mechanisms in place to support the organization’s privacy and security policies. A common example would be requiring a valid username and password before accessing the system.
Now that we have drawn the distinction between physical and logical access controls, we will review three common logical access control models. The three models commonly used in logical access control include discretionary access control (DAC), mandatory access control (MAC), and role-based access control (RBAC).
![]() DAC – Is a control mechanism where the user explicitly allows access to other users or programs that the user has ownership or control over.
DAC – Is a control mechanism where the user explicitly allows access to other users or programs that the user has ownership or control over.
![]() MAC – Is a control mechanism where the user permissions are explicitly controlled by the information system. The permissions are enforced by a collection of prebuilt access rules within the system. When the user is assigned permissions to a system object, the system restricts the activity of the user in accordance with the object’s permission level. For example, a user cannot share information with unauthorized users or system objects.
MAC – Is a control mechanism where the user permissions are explicitly controlled by the information system. The permissions are enforced by a collection of prebuilt access rules within the system. When the user is assigned permissions to a system object, the system restricts the activity of the user in accordance with the object’s permission level. For example, a user cannot share information with unauthorized users or system objects.
![]() RBAC – Is a control mechanism based on business-specific functions within an organization. For example, the role of “Accountant” can view accounts payable information, but the role of “Accounting Manager” can perform accounts payable transactions.
RBAC – Is a control mechanism based on business-specific functions within an organization. For example, the role of “Accountant” can view accounts payable information, but the role of “Accounting Manager” can perform accounts payable transactions.
Data Encryption
Encryption is a foundational component of healthcare security and privacy. It enables organization to achieve privacy and security objectives. Per the HIPAA Security Rule, protected health information (PHI) must be encrypted and encryption is defined as “the use of an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without use of a confidential process or key.” It is important to note that not all encryption algorithms function in the same manner and that some models and algorithms are suitable to meet specific healthcare requirements.
Although predominantly used for the protection of data, cryptography can be used for authentication. The three types of encryption algorithms include secret key (symmetric), public key (asymmetric), and hash functions.
![]() Secret or symmetric key cryptography – Utilizes one key for both encryption and decryption
Secret or symmetric key cryptography – Utilizes one key for both encryption and decryption
![]() Public or asymmetric key cryptography – Utilizes one key for encryption and a different key for decryption
Public or asymmetric key cryptography – Utilizes one key for encryption and a different key for decryption
![]() Hash functions – Are used to support integrity by converting a message into a one-way irreversible hash function
Hash functions – Are used to support integrity by converting a message into a one-way irreversible hash function
Before detailing cryptography types mentioned earlier, one must understand some foundational definitions to truly appreciate how each cryptography model functions. Ciphertext is the encrypted output from an encryption algorithm. The original unencrypted data is called plaintext. Any number of encryption algorithms can be selected by the organization to convert the plaintext into ciphertext. When the ciphertext is decrypted, the data is transformed into its original readable state, the plaintext.
Secret Key Encryption
In secret key encryption, since the same key is used to encrypt and decrypt, proper safeguarding and distribution of that key is of paramount importance. If the key is shared with unauthorized or unintended recipients at any time during the information’s life cycle, the protection of the information must be considered compromised. A compromised data protection, or encryption process that is considered to be compromised, cannot be relied on to support the confidentiality and integrity (the C and I elements of the CIA triangle) of the data being encrypted.
Public Key Encryption
Public key encryption uses two different keys. One key is used to encrypt the information and the other is used to decrypt the information. Sometimes this is referred to as asymmetric encryption because two keys are required to make the system and/or process work securely. One key is known as the public key and should be shared by the owner with anyone who will be securely communicating with the key owner. However, the owner’s secret key is not to be shared and considered a private key. If the private key is shared with unauthorized recipients, the encryption mechanisms protecting the information must be considered compromised.
Hash Functions
It is important to know that the slight technical differences that support hashing are significant enough to draw a distinction between symmetric or asymmetric cryptography and hash functions. Hashing only supports integrity and not confidentiality services. A hash function is a one-way cryptographic algorithm. The use of a one-way cryptographic algorithm means that the ciphertext cannot be decrypted to reveal the original plaintext. The algorithm is made of two parts. The first element is the original content and is called the message. After encryption, the output, or second element, is called the message digest. The message digest is a unique identifier and based on the message. It is often viewed as a digital fingerprint. If the original message were altered in anyway, then it would not match the original message digest. Table 4.1 compares the types of encryption algorithms as well as provides a common example.
Table 4.1
Common Encryption Algorithms
|
Encryption Type |
Strengths |
Weakness |
Example |
|
Symmetric |
• Faster than asymmetric systems • Difficult to break when large key size is used |
• Requires secure mechanism to deliver keys • Key management is difficult due to high volume of keys • Cannot perform nonrepudiation |
• AES • 3DES |
|
Asymmetric |
• Stronger key distribution • Improved scalability • Provides integrity, authenticity, and nonrepudiation functions |
• Slower than symmetric systems • Mathematically intense work factor |
• RSA • DSA |
|
Hash function |
• One-way efficiency • Provides file/message integrity |
• Does not support confidentiality |
• SHA 1 • MD5 |
Training and Awareness
Although training and awareness should be a cornerstone of an organization’s healthcare security program, they are often an underutilized security strategy. When managed properly, it can be a powerful tool for educating and reminding the organization’s workforce on security, privacy, and regulatory requirements. Training is a specific curriculum intended to teach individuals the specific skills needed to perform their job responsibilities.
Awareness is a more general program with a broader audience (i.e., the entire organization) intended to educate and remind employees about adhering to security and privacy initiatives to support the organization’s healthcare security, privacy, and regulatory requirements. Training and awareness are people-focused activities and therefore need to be managed differently than a specific security or privacy technology. Unlike an automated system process or configuration setting, people have (and often do have) the ability to stray from organization best practices. One of the most effective ways to overcome this challenge is to design, implement, and manage effective training and awareness programs. Our emphasis will be on security awareness and privacy programs (as these are more universal in nature and applicable to all healthcare organizations) but assume that organizations will deploy specific training programs (suited to their specific technologies and processes) under the following best practices:
![]() Training tailored to organizational-specific technologies (e.g., CCNA® certified engineers if your organization uses Cisco networking and firewall equipment)
Training tailored to organizational-specific technologies (e.g., CCNA® certified engineers if your organization uses Cisco networking and firewall equipment)
![]() Regulatory specific training for compliance personnel (e.g., HIPAA, Records Management, Safe Harbor)
Regulatory specific training for compliance personnel (e.g., HIPAA, Records Management, Safe Harbor)
NIST Special Publication 800-16 details specific recommendations for successful training and awareness programs but the following elements should be included:
![]() Clearly defined learning objectives
Clearly defined learning objectives
![]() Relevant and “user-friendly” content and delivery
Relevant and “user-friendly” content and delivery
![]() Metrics and measurements (for program delivery and continuous improvement)
Metrics and measurements (for program delivery and continuous improvement)
![]() Student evaluation and performance tracking
Student evaluation and performance tracking
![]() Implementation and tracking evidence (for regulatory compliance and audit purposes)
Implementation and tracking evidence (for regulatory compliance and audit purposes)
When healthcare organizations design, build, deploy, and manage robust training and awareness programs, they are receiving several benefits. Figure 4.3 depicts the cultural benefits of organizations adopting a strong training and awareness program. Not only are they adhering to best practices and complying with specific healthcare security and privacy requirements, but also additionally they are creating a security-aware and proactive security- and privacy-focused culture for their organization.

FIGURE 4.3 Training and awareness relationship.
Logging and Monitoring
Once an organization implements controls to safeguard healthcare information, it is essential they log and monitor the activities associated with said controls. An audit log is a system-generated chronology of events and activity associated with that system. Audit logs are typically highly configurable but most organizations focus on logging access and operational activity associated with the system. Monitoring works in conjunction with logging and is the systematic process of reviewing activity based on specific thresholds defined in the audit log configuration. HIPAA requires the following three activities associated with logging and monitoring:
|
Term |
Description |
HIPAA Reference |
|
Log-in monitoring |
Monitoring system log-in and access for discrepancies. The requirement applies to “log-in attempts” including both failed and successful log-ins |
164.308(a)(5)(ii)(C) |
|
Audit controls |
Cover audit logging and other audit trails on systems that deal with sensitive health information |
164.312(b) |
|
Information system activity review |
Regularly reviews records of information system activity such as audit logs, access reports, and security incident tracking |
164.308(a)(1)(ii)(D) |
Vulnerability Management
NIST Special Publication 800-53 Rev. 4 defines vulnerability management as “The systematic examination of an information system or product to determine the adequacy of security measures, identify security deficiencies, provide data from which to predict the effectiveness of proposed security measures, and confirm the adequacy of such measures after implementation.” As demonstrated in Figure 4.4, when performed correctly, vulnerability management is a continuous process that includes the identification and remediation of vulnerabilities.
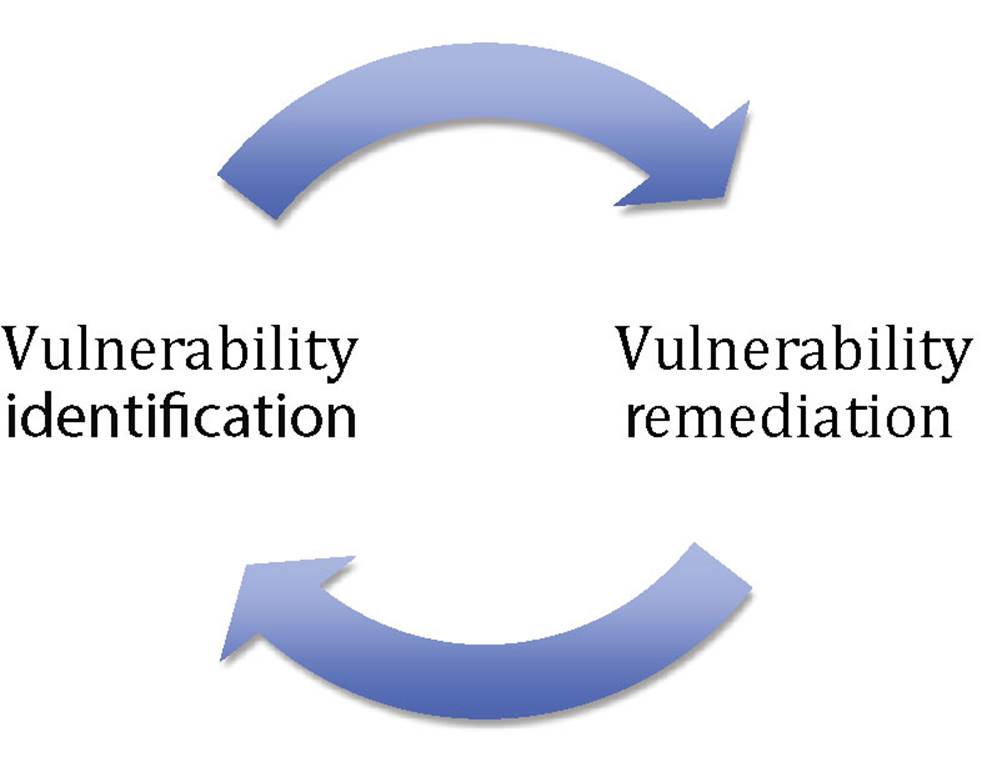
FIGURE 4.4 Vulnerability management cycle.
As part of a more comprehensive security management process HIPAA requires a systematic vulnerability management program that includes the following elements: program evaluation, security management process, risk analysis, risk management, information system activity review, incident procedures, and awareness and training.
|
Requirement |
Description |
HIPAA Reference |
|
Program evaluation |
“Perform a periodic technical and nontechnical evaluation based initially upon the standards implemented under this rule and subsequently, in response to environmental or operational changes affecting the security of electronic protected health information, that establishes the extent to which an entity’s security policies and procedures meet the requirements of this subpart.” |
(a)(8) |
|
Risk analysis and management |
• “Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity.” And • “Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level …” |
(a)(1)(ii)(A) and (a)(1)(ii)(B) |
|
System activity review |
“Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.” |
(a)(1)(ii)(D) |
|
Incident procedures |
“Implement policies and procedures to address security incidents.” |
(a)(6)(i) and (a)(6)(ii) |
|
Awareness and training |
“Implement a security awareness and training program for all members of its workforce (including management).” |
(a)(5)(i) |
Figure 4.5 shows how the five specific elements support a comprehensive vulnerability program required by HIPAA.
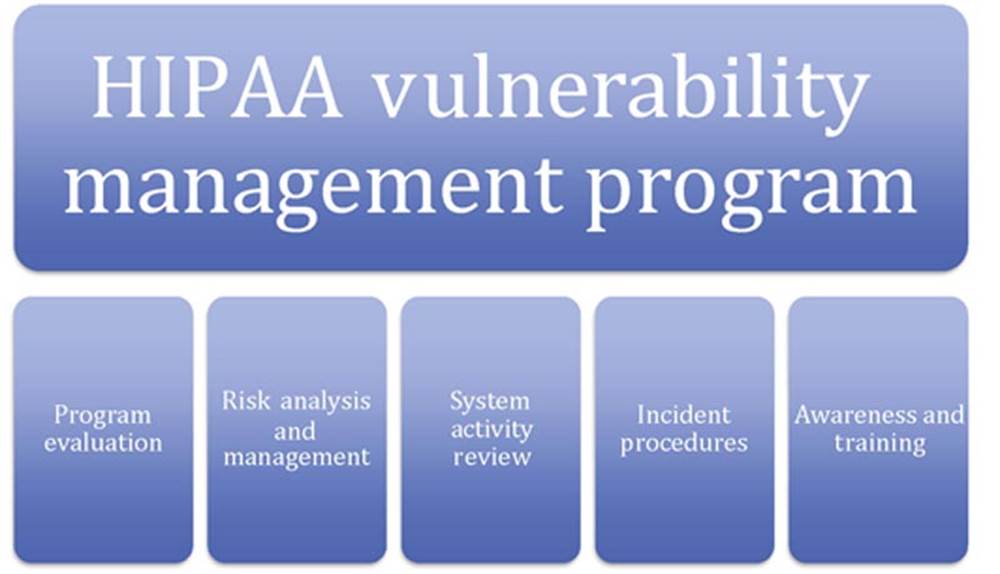
FIGURE 4.5 HIPAA vulnerability program elements.
Systems Recovery
Systems recovery and contingency planning is the series of processes and procedures that healthcare organizations implement to ensure availability (remember the availability leg of the CIA triangle) of electronic protected health information (EPHI). All healthcare organizations should develop a comprehensive business resiliency program to ensure the availability of healthcare information against natural or man-made disruptions. In addition to contingency planning being a security best practice, the HIPAA Contingency Plan Standard also addresses the importance of contingency planning through five implementation specifications. Per the HIPAA Standard [§164.308(a)(7)(ii)(A)–(E)] the five contingency plan implementation standards are a data backup plan (required), disaster recovery plan (required), emergency mode operation plan (required), testing and revision procedures (addressable), and application and data criticality analysis (addressable) and are defined as follows:
![]() Data backup plan: “Establish and implement procedures to create and maintain retrievable exact copies of electronic protected health information.”
Data backup plan: “Establish and implement procedures to create and maintain retrievable exact copies of electronic protected health information.”
![]() Disaster recovery plan: “Establish (and implement as needed) procedures to restore any loss of data.”
Disaster recovery plan: “Establish (and implement as needed) procedures to restore any loss of data.”
![]() Emergency mode operation plan: “Establish (and implement as needed) procedures to enable continuation of critical business processes for protection of the security of electronic protected health information while operating in emergency mode.”
Emergency mode operation plan: “Establish (and implement as needed) procedures to enable continuation of critical business processes for protection of the security of electronic protected health information while operating in emergency mode.”
![]() Testing and revision procedures: “Implement procedures for periodic testing and revision of contingency plans.”
Testing and revision procedures: “Implement procedures for periodic testing and revision of contingency plans.”
![]() Application and data criticality analysis: “Assess the relative criticality of specific applications and data in support of other contingency plan components.”
Application and data criticality analysis: “Assess the relative criticality of specific applications and data in support of other contingency plan components.”
Segregation of Duties
Segregation of duties mandates that sensitive job functions that, when combined, have a high potential for abuse should be performed by separate people in order to reduce that risk of abuse. This is often accomplished by having at least two individuals (one to perform and one to approve) involved to ensure a system of checks and balances. For example, if a server configuration change needs to be made to support a software installation for a developer, the developer cannot directly make that change. He or she would request the change be made, and after approval from management, a system administrator would make the changes for the developer.
Least Privilege
According to NIST Special Publication 800-12 least privilege is defined as “the security objective of granting users only those accesses they need to perform their official duties.” From a HIPAA perspective, the Privacy Rule typically requires covered entities to take reasonable actions to limit the disclosure of PHI to the least amount required to accomplish the intended task. In addition to providing users the least amount of access needed to perform their jobs, healthcare organizations also need to routinely review that privileges are still needed and appropriate for the user’s current role. In a busy healthcare organization, it is common for an employee’s job function to change and they may no longer need the same level of permissions for their new role within the organization.
Business Continuity and Disaster Recovery
Business continuity is a relatively broad concept and often means different things to different organizations. However, in its simplest form, business continuity is about ensuring an organization’s critical business functions are available and continue to operate during an incident or emergency. Each organization will need to define what critical operations are, as well as what an incident or emergency is, and business continuity and disaster recovery planning accomplish this. Business continuity planning is the process that organizations follow so they can implement policies, procedures, processes, and technology used to ensure how an organization’s business objectives will be performed after a significant disruption. It is important to note that a variety (both natural and man-made) of events (e.g., flood, terrorism) can define a significant disruption and organizations must plan accordingly. Additionally, patients have high expectations that healthcare organizations have the ability to provide critical services and patient care regardless of a significant disruption. In fact, if the event is regional or national in nature (e.g., an entire state is impacted by a pandemic), there may be an even greater expectation or need that healthcare organizations can deliver patient care services. Disaster recovery planning is similar in nature to business continuity planning and they often work in conjunction to support the healthcare organization’s short- and long-term needs when recovering from a significant and disruptive unplanned event. A useful perspective on the relationship is that business continuity is about building systems and processes that are resilient to disruptions and disaster recovery is about systems and processes that enable the organization to quickly recover from a disruption. Disaster recovery tends to focus on the short-term response after a disaster occurs. Typically it focuses on the organization’s critical systems (essential to providing healthcare services) in a timely manner (e.g., the pharmacy system needs to be available within 2 h of a disaster). Although each healthcare organization will determine its specific needs, and several factors should go into a disaster recovery planning, the following elements are essential to a comprehensive disaster recovery plan:
![]() Critical application assessment – Determining which systems are essential to the healthcare organization delivering critical services.
Critical application assessment – Determining which systems are essential to the healthcare organization delivering critical services.
![]() Backup procedures – Determining the details (e.g., who, what, when) and steps for backing up systems and data.
Backup procedures – Determining the details (e.g., who, what, when) and steps for backing up systems and data.
![]() Recovery procedures – Determining the details (e.g., who, what, when) and steps for recovering data and systems from backup after a disaster.
Recovery procedures – Determining the details (e.g., who, what, when) and steps for recovering data and systems from backup after a disaster.
![]() Implementation procedures – Determining how to best implement the selected procedures.
Implementation procedures – Determining how to best implement the selected procedures.
![]() Test procedures – Developing test procedures so that testing can be performed on a regular basis to ensure the organization is capable of recovering after a disaster.
Test procedures – Developing test procedures so that testing can be performed on a regular basis to ensure the organization is capable of recovering after a disaster.
Before an appropriate backup strategy can be selected, it is important to understand the fundamentals of backups. Essentially, backups can be managed as onsite or remote. However, most healthcare organizations will determine that a hybrid approach offers the best solution since there are both advantages and disadvantages to each strategy.
![]() Onsite backups – Allow organizations to store the data onsite, the advantage being they are readily available if needed. One disadvantage is that if the onsite location is unavailable or destroyed, so are the backup data. Another disadvantage is that the physical backup media (and information it contains) must be properly safeguarded.
Onsite backups – Allow organizations to store the data onsite, the advantage being they are readily available if needed. One disadvantage is that if the onsite location is unavailable or destroyed, so are the backup data. Another disadvantage is that the physical backup media (and information it contains) must be properly safeguarded.
![]() Remote backups – Allow organizations to store the data offsite, the advantage being that if the location is unavailable or destroyed, the backup data still exist. The disadvantage is that it can be time consuming or difficult to obtain backup data in a timely manner when they are not located onsite.
Remote backups – Allow organizations to store the data offsite, the advantage being that if the location is unavailable or destroyed, the backup data still exist. The disadvantage is that it can be time consuming or difficult to obtain backup data in a timely manner when they are not located onsite.
Another important factor when discussing backups is the frequency and specific methodology. Each method has advantages and disadvantages and most healthcare organizations select a hybrid approach to best meet their specific needs. The most common types include the following:
![]() Full backup – Includes all data and is slower to backup but faster to restore and requires the most storage space.
Full backup – Includes all data and is slower to backup but faster to restore and requires the most storage space.
![]() Incremental backup – Only includes new or modified data, is fast to backup, has a moderate restore time, and requires lower storage space.
Incremental backup – Only includes new or modified data, is fast to backup, has a moderate restore time, and requires lower storage space.
![]() Differential backup – Includes all changed data since the last full backup, has a moderate time frame to backup, and requires moderate storage space.
Differential backup – Includes all changed data since the last full backup, has a moderate time frame to backup, and requires moderate storage space.
![]() Mirrored backup – Only includes new or modified data and has the fastest backup and restore times, but requires the most storage space.
Mirrored backup – Only includes new or modified data and has the fastest backup and restore times, but requires the most storage space.
Healthcare organizations should develop a compressive program and supporting documentation to support their backup strategy. This is used to clarify expectations and execution details. It is best to answer the “five W’s plus one” (who, what, when, where, why, and how) questions when documenting the backup strategy. Since both improvements to backup technology and the substantial reduction in cost for backup technology have occurred in recent years, healthcare organizations have additional alternatives (rather than traditional tape or other storage media) to consider when developing their backup strategies. This includes alternative sites, high availability architectures and technologies, and real-time journaling. Additionally, the capabilities associated with alternate sites need to also be considered by the healthcare organization’s strategy. The three most common considerations include a hot site, cold site, and warm site.
![]() Hot sites – Duplicate the primary production site in terms of both infrastructure and data. The main advantage is that there is little to no time required to shift operations from the original production site to the alternative site. The primary disadvantage is the costs and maintenance associated with fully duplicating a production environment.
Hot sites – Duplicate the primary production site in terms of both infrastructure and data. The main advantage is that there is little to no time required to shift operations from the original production site to the alternative site. The primary disadvantage is the costs and maintenance associated with fully duplicating a production environment.
![]() Cold sites – Have the primary advantage of being low cost, since the information system hardware and backup data are not present at the cold site. The disadvantage is the time and effort required to establish a production-level environment.
Cold sites – Have the primary advantage of being low cost, since the information system hardware and backup data are not present at the cold site. The disadvantage is the time and effort required to establish a production-level environment.
![]() Warm sites – Are a hybrid alternative to hot and cold sites. The advantage is that they cost less than a hot site, but have more robust capabilities than a cold site.
Warm sites – Are a hybrid alternative to hot and cold sites. The advantage is that they cost less than a hot site, but have more robust capabilities than a cold site.
Data Retention and Destruction
Data retention and destruction policies and procedures involve the healthcare organization’s specifications for retaining and destroying data in accordance with legal, regulatory, and business requirements. The HIPAA Privacy Rule requires that covered entities apply appropriate administrative, technical, and physical safeguards to protect the privacy of PHI, in any form. This applies to the disposal of such information when the data are no longer required or a specific data retention period has expired. Additionally, the HIPAA Security Rule requires that covered entities implement policies and procedures to address the final disposition of EPHI and/or the hardware or electronic media on which it is stored, as well as to implement procedures for removal of EPHI from electronic media before the media are made available for reuse.
Since both the HIPAA Privacy and Security Rules address data retention and destruction, healthcare organizations must implement the appropriate safeguards to protect PHI and comply with HIPAA requirements.
General privacy principles
There are 12 general privacy principles we will be discussing that are applicable to the 4 commonly recognized healthcare privacy standards. The four healthcare privacy standards are:
![]() Organization for Economic Co-operation and Development (OECD) Privacy Principles
Organization for Economic Co-operation and Development (OECD) Privacy Principles
![]() Generally Accepted Privacy Principles (GAPP)
Generally Accepted Privacy Principles (GAPP)
![]() Personal Information Protection and Electronic Documents Act (PIPEDA)
Personal Information Protection and Electronic Documents Act (PIPEDA)
![]() UK Data Protection Act 1998 (DPA)
UK Data Protection Act 1998 (DPA)
We will be detailing the 4 healthcare privacy standards later in the chapter, but understanding the 12 general privacy principles provides a solid foundation and the 4 healthcare privacy standards are based on the privacy principles. Although there are slight differences between how each standard utilizes the 12 principles, the intent and overall commonality of each principle is applicable.
12 Privacy Principles
The 12 principles and their descriptions are listed as follows:
![]() Consent/Choice – Permission granted from the patient or their legal guardian to an organization to use protected health information (PHI) for lawful healthcare purposes (treatment, research, operations, etc.).
Consent/Choice – Permission granted from the patient or their legal guardian to an organization to use protected health information (PHI) for lawful healthcare purposes (treatment, research, operations, etc.).
![]() Limited Collection/Legitimate Purpose/Purpose Specification – The principle that states that the purposes for which personal data are collected should be specified not later than at the time of data collection and the subsequent use limited to the fulfillment of those purposes or such others as are not incompatible with those purposes and as are specified on each occasion of change of purpose.
Limited Collection/Legitimate Purpose/Purpose Specification – The principle that states that the purposes for which personal data are collected should be specified not later than at the time of data collection and the subsequent use limited to the fulfillment of those purposes or such others as are not incompatible with those purposes and as are specified on each occasion of change of purpose.
![]() Disclosure Limitation/Transfer to Third Parties/Trans-Border Concerns – Specifies that personal information can only be disclosed for the purposes identified under notice and consent. It may also mean that personal data be disclosed outside of jurisdictional boundaries.
Disclosure Limitation/Transfer to Third Parties/Trans-Border Concerns – Specifies that personal information can only be disclosed for the purposes identified under notice and consent. It may also mean that personal data be disclosed outside of jurisdictional boundaries.
![]() Access Limitation – This usually ensures that access to information is limited only to individuals who specifically require access. Under the DPA, it means appropriate safeguards to prevent unauthorized access to personal data.
Access Limitation – This usually ensures that access to information is limited only to individuals who specifically require access. Under the DPA, it means appropriate safeguards to prevent unauthorized access to personal data.
![]() Security – Organizations must have safeguards to protect personal information.
Security – Organizations must have safeguards to protect personal information.
![]() Accuracy, Completeness, Quality – This principle specifies that organizations in possession of personal information are responsible for ensuring its accuracy, completeness, and quality.
Accuracy, Completeness, Quality – This principle specifies that organizations in possession of personal information are responsible for ensuring its accuracy, completeness, and quality.
![]() Management, Designation of Privacy Officer, Supervisor Re-Authority, Processing Authorization, Accountability – These principles ensure that the organization has formally assigned accountability to safeguarding personal information under its control.
Management, Designation of Privacy Officer, Supervisor Re-Authority, Processing Authorization, Accountability – These principles ensure that the organization has formally assigned accountability to safeguarding personal information under its control.
![]() Transparency, Openness – Organizations must make their policies readily available to individuals and be clear on the intended use of an individual’s personal information.
Transparency, Openness – Organizations must make their policies readily available to individuals and be clear on the intended use of an individual’s personal information.
![]() Proportionality, Use and Retention, Use Limitation – This principle protects an individual’s healthcare information by restricting the use of data and ensuring that organizations destroy information when it is no longer in use.
Proportionality, Use and Retention, Use Limitation – This principle protects an individual’s healthcare information by restricting the use of data and ensuring that organizations destroy information when it is no longer in use.
![]() Access, Individual Participation –This principle states that individuals have the right to request from organizations a verification of whether or not the organization has information about them.
Access, Individual Participation –This principle states that individuals have the right to request from organizations a verification of whether or not the organization has information about them.
![]() Notice, Purpose Specification – Is a principle that ensures that organizations provide notice to individuals about the organizations’ policies and procedures regarding the collection, retention, and disclosure of data.
Notice, Purpose Specification – Is a principle that ensures that organizations provide notice to individuals about the organizations’ policies and procedures regarding the collection, retention, and disclosure of data.
![]() Additional Measures for Breach Notification – Is a principle to ensure that organizations have specific policies and procedures for notifying individuals in the event of a data breach.
Additional Measures for Breach Notification – Is a principle to ensure that organizations have specific policies and procedures for notifying individuals in the event of a data breach.
Now that we have a detailed understanding of the 12 general privacy principles we can see how they relate to the 4 specific healthcare standards listed in the following. It is important to note that since 4 different authorities issued the standards, there may be some slight differences, and in some cases not all of the 12 general privacy principles may directly apply. However, since the principles are rooted in the fundamentals of privacy, it is best to focus on the spirit or intent of the standard or law rather than the letter of the standard or law.
Data Privacy Standards
Organization for Economic Co-Operation and Development Privacy Principles
According to the OECD, their mission is to “promote policies that will improve the economic and social well-being of the world.” Although the OECD achieves their mission in many ways and provides invaluable guidance in a number of areas, our focus will be on the privacy principles. In terms of exam preparation, focusing on the 12 general privacy principles, and applying foundational privacy knowledge to the mission and organizational aspects of the OECD will suffice for exam preparation. Since OECD has an international presence, and works with organizations across the world, they can leverage the 12 privacy principles to address healthcare privacy from an international perspective.
Generally Accepted Privacy Principles
The American Institute of Certified Public Accountants and the Canadian Institute of Chartered Accountants sponsor the GAPP. Their guidance is intended to provide a framework for organizations looking to implement a privacy program. In comparison to the OECD, the GAPP has a business perspective and less of an international focus and may not address all specific local, national, or international privacy laws. However, it is still grounded in the 12 general privacy principles and enables organizations insight on how to properly safeguard healthcare information and manage effective privacy programs.
Personal Information Protection and Electronic Documents Act
The PIPEDA is the framework set forth by Canada’s Office of the Privacy Commissioner. It applies to both federal and private sector organizations and governs the collection, use, and disclosure of personal information. One of the most significant aspects of PIPEDA is that it enables individuals the right to access (and correct if necessary) their personal information if it was collected by federal and private entities. PIPEDA, as with GAPP and OECD, is based on the 12 general privacy principles discussed earlier.
UK Data Protection Act 1998
The UK Data Protection Act of 1998, commonly referred to as DPA, is an independent authority in the United Kingdom, responsible for allowing access to official information and protecting personal information. One of the ways this is accomplished is through the United Kingdom’s Information Commissioner’s Office (ICO). All organizations, unless specifically exempt, that possess and/or use personal information must register with the Commissioner’s Office. The UK DPA also uses eight data protection principles to ensure personal information is properly safeguarded. The ICO specifically states the following:
1. Personal data shall be processed fairly and lawfully and, in particular, shall not be processed unless:
a. At least one of the conditions in Schedule 2 is met, and
b. In the case of sensitive personal data, at least one of the conditions in Schedule 3 is also met.
2. Personal data shall be obtained only for one or more specified and lawful purposes, and shall not be further processed in any manner incompatible with that purpose or those purposes.
3. Personal data shall be adequate, relevant, and not excessive in relation to the purpose or purposes for which they are processed.
4. Personal data shall be accurate and, where necessary, kept up to date.
5. Personal data processed for any purpose or purposes shall not be kept for longer than is necessary for that purpose or those purposes.
6. Personal data shall be processed in accordance with the rights of data subjects under this Act.
7. Appropriate technical and organizational measures shall be taken against unauthorized or unlawful processing of personal data and against accidental loss or destruction of, or damage to, personal data.
8. Personal data shall not be transferred to a country or territory outside the European Economic Area unless that country or territory ensures an adequate level of protection for the rights and freedoms of data subjects in relation to the processing of personal data.
Another important element of the DPA to take notice of is the restrictions it holds for data transfer and use outside of the European Economic Area. Otherwise, like the other 3 privacy standards, the DPA is based on the 12 privacy principles.
Relationship between privacy and security
Although there can be some inherent conflicts between privacy and security, security is required to support privacy objectives. Therefore, there is a very close relationship and it is understood that some privacy issues (e.g., monitoring and data collection) are caused when implementing sound security practices. Most organizations will find they need to balance elements of the privacy and security relationship to properly safeguard PHI. Figure 4.6 depicts the privacy and security relationship.
FIGURE 4.6 Privacy and security relationship.
Some of the more common privacy issues impacting security include network and system monitoring, background investigations, supplier and partner relationships, and information sharing programs. Organizational privacy objectives and requirements are accomplished by the implementation of security controls. Looking back the CIA triangle, privacy is supported by the confidentiality and integrity legs of the triangle.
The disparate nature of sensitive data and handling implications
Healthcare organizations are responsible for the implementation of safeguards in order to protect sensitive patient data. Healthcare organizations and the information systems they rely on have massive amounts of data. Before the organization can select the appropriate controls and safeguards they must understand what they are trying to protect and why. Although more detailed strategies are discussed in the risk management sections of this text, data classification is one of the first steps. If you do not structure and organize the data, how can you prioritize and protect it? Furthermore, not all data and information are equal in value, so all data sets do not need to be managed, protected, and handled the same way.
Data classification schemas allow healthcare organizations to classify and label their data. These organizational-based standards and definitions allow for effective communication and understanding and enable employees to have a uniform understanding of the data and associated precautions within their organization. Although there may be slight variances and specific organizational differences in data classification models, they are based on the common principles. These typically include a hierarchical structure and clearly defined labels and definitions to ensure information is handled consistently.
Once the data are properly classified, organizations need to create detailed handling procedures that address the following data handling elements:
![]() Access – Who can access the data?
Access – Who can access the data?
![]() Use – Why is it needed? Principle of least privilege.
Use – Why is it needed? Principle of least privilege.
![]() Destruction – How is the information destroyed after acceptable use?
Destruction – How is the information destroyed after acceptable use?
Disparate data are commonly defined as data that are dissimilar in nature. This usually means differences in type, quality, format, and source. Considering the overall complexity (large number of separate and distinct organizations and systems with extensive data sharing and interdependencies) of the healthcare delivery system disparate data can be a complex challenge.
Specifically, this operating model causes the following data problems:
![]() Continuation and formation of data silos – e.g., each healthcare organization (or distinct unit within an organization) will create a separate patient record
Continuation and formation of data silos – e.g., each healthcare organization (or distinct unit within an organization) will create a separate patient record
![]() Data duplication and regeneration – e.g., separate systems (billing and pharmacy systems) containing duplicate information for the same patient
Data duplication and regeneration – e.g., separate systems (billing and pharmacy systems) containing duplicate information for the same patient
![]() Lack of standardized data formats – e.g., variance in patient record formats
Lack of standardized data formats – e.g., variance in patient record formats
In addition to making intersystem and organizational data sharing difficult, disparate data create an increased security risk. The more instances of confidential patient information, the greater the risk exposure becomes. Electronic medical records (EMRs) are intended to consolidate disparate data from all of the independent systems (e.g., pharmacy, billing, insurance) within a healthcare organization. Although this reduces many of the security concerns with disparate data referenced earlier, additional privacy and security challenges still remain. Specifically, a majority of the data types within an EMR need to be safeguarded and comply with the HIPAA Privacy Rule.
Protected Health Information
PHI is defined as any information in the medical record or designated record set that can be used to identify an individual and that was created, used, or disclosed in the course of providing a healthcare service such as diagnosis or treatment under HIPAA. The HIPAA Privacy Rule protects the 18 common identifiers listed as follows that are often associated with medical records:
1. Names
2. All geographic subdivisions smaller than a State, including street address, city, county, precinct, zip code, and their equivalent geocodes, except for the initial three digits of a zip code, if according to the current publicly available data from the Bureau of the Census: (a) the geographic unit formed by combining all zip codes with the same three initial digits contains more than 20,000 people; and (b) the initial three digits of a zip code for all such geographic units containing 20,000 or fewer people is changed to 000
3. All elements of dates (except year) for dates directly related to an individual, including birth date, admission date, discharge date, date of death; and all ages over 89 and all elements of dates (including year) indicative of such age, except that such ages and elements may be aggregated into a single category of age 90 or older
4. Phone numbers
5. Fax numbers
6. Electronic mail addresses
7. Social Security numbers
8. Medical record numbers
9. Health plan beneficiary numbers
10. Account numbers
11. Certificate/license numbers
12. Vehicle identifiers and serial numbers, including license plate numbers
13. Device identifiers and serial numbers
14. Web Universal Resource Locators (URLs)
15. Internet Protocol (IP) address numbers
16. Biometric identifiers, including fingerprints and voiceprints
17. Full face photographic images and any comparable images
18. Any other unique identifying number, characteristic, or code (note this does not mean the unique code assigned by the investigator to code the data)
The HIPAA Privacy Rule prescribes 18 identifiers that usually need to be properly safeguarded under HIPAA requirements. However, when separated (as opposed to multiple single patient identifiers in aggregate), data identifiers may not necessarily be designated as PHI. For example, a patient’s name in isolation would not be considered PHI since the name alone is not directly connected with that individual’s other PHI and the name would be considered publicly available information. Healthcare organizations need to be very cautious since data sets and the 18 protected identifiers can quickly change context, thus requiring organizations to comply with HIPAA Privacy and Security Safeguards. In the previous example, a name (not associated with any other identifiers) was considered public information and not considered to be PHI. However, that same name associated with additional healthcare data (e.g., patient treatment and billing information) would be considered PHI and would be required to be protected in accordance with the HIPAA Privacy and Security Rules. Now that we understand the relationship between data sets, PHI, and the 18 protected identifiers, we need to discuss some specific mitigation strategies to ensure HIPAA compliance. These fall under the category of data de-identification.
Data De-Identification
The HIPAA Privacy Rule contains a de-identification standard. The standard prescribes that health information is not individually identifiable if (1) it does not identify an individual and (2) the covered entity has no reasonable basis to believe it can be used to identify an individual. The HIPAA Privacy Rule continues to support this standard in sections 164.514(b) and (c) by specifying two acceptable methods for de-identification of data. These methods include Expert Determination and Safe Harbor. Expert Determination states that an organization may only determine information is not individually identifiable if:
1. A person with appropriate knowledge of and experience with generally accepted statistical and scientific principles and methods for rendering information is not individually identifiable;
2. Applying such principles and methods, it is determined that the risk is very small that the information could be used, alone or in combination with other reasonably available information, by an anticipated recipient to identify an individual who is a subject of the information; and
3. The methods and results of the analysis are documented in a way that justifies such determination.
The Safe Harbor method is the removal of certain identifiers (from the list of the 18 identifiers listed earlier) of the individual or of relatives, employers, or household members of the individual, where the covered entity does not have actual knowledge that the information could be used alone or in combination with other information to identify the individual who is the subject of the information.
Data Anonymization
Data anonymization can also be considered by covered entities that are leveraging data-driven research analysis projects (e.g., data mining, predictive analytics). However, it is important to point out the risks associated with these types of efforts. There are many tools, technologies, and methodologies that can be used to reverse engineer or de-anonymize data sets. Additionally, the manipulation and generation of new data from existing data (i.e., metadata) may require patient consent. When complying with the HIPAA Privacy Rule, it is important to note that sensitive health information falls under the Privacy Rule requirements regardless of delivery or recording formats. This means that both oral and recorded patient health information must be properly safeguarded. It is also important to note that HIPAA includes the protection of mental health data in its scope of coverage. In addition to mental health specifications, the following healthcare areas are also protected by HIPAA:
![]() Substance abuse – Substance abuse programs may not share patient information outside of the program.
Substance abuse – Substance abuse programs may not share patient information outside of the program.
![]() Pregnancy – Is not considered a preexisting condition, but all other health insurance requirements still exist.
Pregnancy – Is not considered a preexisting condition, but all other health insurance requirements still exist.
![]() HIV research data – Originally not included under HIPAA.
HIV research data – Originally not included under HIPAA.
![]() DNA – Not specifically protected, but considered to be PHI.
DNA – Not specifically protected, but considered to be PHI.
Many of the healthcare-specific services under HIPAA’s coverage are quite intuitive. However, we must not forget the services that support healthcare delivery must also be compliant with HIPAA requirements. Figure 4.7 depicts the relationship that business support functions have with HIPAA compliance. At the highest level, any business data, system, or service used to support or deliver healthcare falls under HIPAA’s regulatory authority.
FIGURE 4.7 Business support functions’ relationship with HIPAA compliance.
The following is a list of the more common business elements associated with the support or delivery of healthcare:
![]() General administrative data
General administrative data
![]() Financial/accounting data
Financial/accounting data
![]() Actuarial data
Actuarial data
Key terms
|
Access control |
Is a mechanism used to restrict access to a place or resource. It can apply to both physical and logical resources and is typically composed of administrative, technical, or physical controls |
|
Authorization |
The explicit permission from the object owner that allows a subject to access a resource |
|
Business associate |
A person who on behalf of a covered entity (or of an organized healthcare arrangement in which the covered entity participates) performs or assists in the performance of: • A function or activity involving the use or disclosure of individually identifiable health information, including claims processing or administration, data analysis, processing or administration, utilization review, quality assurance, billing, benefit management, practice management, and repricing; • Any other function or activity regulated by this subchapter; or • A person who provides legal, actuarial, accounting, consulting, data aggregation, management, administrative, accreditation, or financial services to or for such covered entity (or to or for an organized healthcare arrangement in which the covered entity participates) where the provision of the service involves the disclosure of individually identifiable health information from such covered entity (or arrangement), or from another business associate of such covered entity (or arrangement), to the person |
|
Consent |
Permission granted by the patient or the patient’s guardian to use or disclose protected health information for purposes of treatment, payment, or healthcare operations |
|
Covered entities |
Under HIPAA means: • A health plan • A healthcare clearinghouse • A healthcare provider who transmits any health information in electronic form in connection with a transaction covered under HIPAA requirements |
|
De-identified information |
Health information that does not identify an individual and with respect to which there is no reasonable basis to believe that the information can be used to identify an individual is not individually identifiable health information |
|
Disclosure |
Disclosure means the release, transfer, provision of, access to, or divulging in any other manner of information outside the entity holding the information |
|
Group Health Plan |
An employee welfare benefit plan, including insured and self-insured plans, to the extent that the plan provides medical care, including items and services paid for as medical care, to employees or their dependents directly or through insurance, reimbursement, or otherwise |
|
Healthcare operations |
Any of the following activities of the covered entity to the extent that the activities are related to covered functions: • Conducting quality assessment and improvement activities • Reviewing the competence or qualifications of healthcare professionals • Underwriting, premium rating, and other activities relating to the creation, renewal, or replacement of a contract of health insurance or health benefits • Conducting or arranging for medical review, legal services, and auditing functions • Business planning and development • Business management and general administrative activities of the entity |
|
Health information |
Any information, oral or recorded in any medium, that is created or received by a healthcare provider, health plan, public health authority, employer, life insurer, school or university, or healthcare clearinghouse; and relates to the past, present, or future physical or mental health or condition of an individual; the provision of healthcare to an individual; or the past, present, or future payment for the provision of healthcare to an individual |
|
Individual |
The person who is the subject of protected health information |
|
Individually identifiable health information |
Information that is a subset of health information, including demographic information collected from an individual, and: • Is created or received by a healthcare provider, health plan, employer, or healthcare clearinghouse; and • Relates to the past, present, or future physical or mental health or condition of an individual; the provision of healthcare to an individual; or the past, present, or future payment for the provision of healthcare to an individual; and • That identifies the individual; or • With respect to which there is a reasonable basis to believe the information can be used to identify the individual |
|
Institutional review board (IRB) |
An IRB is a board, committee, or other group formally designated by an institution to review research, involving humans as subjects. IRBs have authority to approve, require modification to, or disapprove all research activities covered by the HHS and FDA protection of human subjects regulations |
|
Limited data set |
A limited data set excludes specified direct identifiers of the individual or of relatives, employers, or household members of the individual |
|
Need-to-know |
A security principle that states a user should only be able to access the data they need to perform their job |
|
Plan administration functions |
An administration function performed by the Plan Sponsor of a Group Health Plan on behalf of the Group Health Plan and excludes functions performed by the Plan Sponsor in connection with any other benefit or benefit plan of the Plan Sponsor |
|
Protected health information |
Individually identifiable health information that is or has been electronically maintained or electronically transmitted by a covered entity, as well as such information when it takes any other form that (1) is created or received by a healthcare provider, health plan, employer, or healthcare clearinghouse; and (2) relates to the past, present, or future physical or mental health or condition of an individual, the provision of healthcare to an individual, or the past, present, or future payment for the provision of healthcare to an individual |
|
Treatment |
The provision, coordination, or management of healthcare and related services among healthcare providers or by a healthcare provider with a third party, consultation between healthcare providers regarding a patient, or the referral of a patient from one healthcare provider to another |
|
Unique user identifier |
A combination name/number assigned and maintained in security procedures for identifying and tracking individual user identity |
|
Use |
With respect to individually identifiable health information, the sharing, employment, application, utilization, examination, or analysis of such information with an entity that maintains such information |
Practice Exam
1. Which element of CIA security model is least important?
a. Availability – Data security is the primary concern; as long as the data are secure, availability does not matter.
b. Confidentiality – HIPAA already ensures patient healthcare information, so we do not have to worry about confidentiality in the CIA security model.
c. Availability – Strong access controls already ensure information is only available to authorized healthcare employees.
d. None – All elements of the CIA security model are equally important.
2. Confidentiality is best accomplished by which of the following?
a. Encryption
b. Data backup systems
c. Logical system controls that enforce data validation
d. Vulnerability management
3. The three broad types of access control are:
a. Confidentiality, integrity, availability
b. Confidential, sensitive, public
c. Administrative, physical, technical
d. Discretionary, mandatory, role-based
4. Sensitive data should be encrypted:
a. At rest
b. In transit
c. Only when leaving the organization’s network
d. Both a and b
5. Security awareness training:
a. Only needs to be given to new employees
b. Does not need to be given since healthcare employees receive this training when they receive their healthcare training and certification
c. Should be given to all employees on an annual basis
d. Only needs to be given to employees who handle PHI
6. Audit logging:
a. Only needs to be performed 1 month prior to an audit
b. Should be performed in conjunction with monitoring
c. Does not need to be performed by covered entities (only healthcare organizations)
d. Does not need to be performed by healthcare organizations (only covered entities)
7. Vulnerability management includes:
a. Identification and remediation
b. A continuous process
c. Remediation only
d. Both a and b
8. Segregation of duties:
a. Does not apply to covered entities
b. Is not required when encryption is being used
c. Is designed to reduce the risk of system abuse
d. Only applies to larger organizations since having more employees increases the risk for system abuse
9. Business continuity:
a. Only applies to covered entities since they are businesses that support healthcare organizations rather than deliver patient healthcare services
b. Is composed of many technologies and processes that support the availability leg of the CIA triangle
c. Is optional for covered entities since they do not provide direct patient care
d. None of the above
10. Data destruction includes:
a. Shredding
b. Degaussing
c. None of the above
d. Both a and b
11. OECD focuses their mission on serving:
a. The United States
b. People around the world
c. The United Kingdom
d. North America
12. GAPP applies to:
a. Federal organizations in the United States and Canada
b. The United States and Canada
c. The United States only
d. Canada only
13. PIPEDA stands for:
a. Personal Information Protection and Electronic Documents Act
b. Privacy Information Protection and Electronic Document Act
c. Personal Information Protection and Electronic Data Act
d. Privacy Information Protection and Electronic Data Act
14. The UK DPA:
a. Involves the Information Commissioner’s Office
b. Has restrictions on data transfer outside of the European Economic Area
c. Contains eight specific data protection principles
d. All of the above
15. Consent/Choice is:
a. Not important in healthcare setting since healthcare organizations need to have PHI to perform service requested by the patient
b. Should be discussed with the patient prior to delivering any services
c. Is only relevant for healthcare-related research, not traditional patient care services
d. Only applies to US entities following GAAP
16. The accuracy privacy principle:
a. Requires organizations to maintain complete and reliable PHI
b. Is applicable to GAAP
c. Is applicable to PIPEDA
d. All of the above
17. Breach notification requirements:
a. Are only important for transborder data flows
b. Do not apply if the PHI was for testing and research purposes
c. Both a and b
d. None of the above
18. The relationship between privacy and security:
a. Is symbiotic and both are relevant to safeguarding PHI
b. Is not relevant since privacy and security are two separate and distinct disciplines
c. Is not relevant since privacy is more important than security
d. Is not relevant since security is more important than privacy
19. Under the HIPAA Privacy Rule, there are:
a. 18 possible identifiers of PHI
b. 81 possible identifiers of PHI
c. 8 possible identifies of PHI
d. No specific number as it depends on the organization’s use of PHI
20. De-identification and anonymization are:
a. Synonymous
b. Two methods for preventing disclosure of PHI
c. Both a and b
d. None of the above
Practice Exam Answers
1. d
2. a
3. c
4. d
5. c
6. b
7. d
8. c
9. b
10. d
11. b
12. b
13. a
14. d
15. b
16. d
17. d
18. a
19. a
20. b
References
http://www.hhs.gov/ocr/privacy/hipaa/administrative/securityrule/index.html.
http://www.hhs.gov/ocr/privacy/hipaa/administrative/securityrule/securityrulepdf.pdf.
http://www.hhs.gov/ocr/privacy/hipaa/administrative/privacyrule/index.html.
http://www.hhs.gov/ocr/privacy/hipaa/administrative/privacyrule/privruletxt.txt.
http://www.oecd.org/internet/ieconomy/oecdguidelinesontheprotectionofprivacyandtransborderflowsofpersonaldata.htm.
http://www.aicpa.org/INTERESTAREAS/INFORMATIONTECHNOLOGY/RESOURCES/PRIVACY/GENERALLYACCEPTEDPRIVACYPRINCIPLES/Pages/default.aspx.
http://www.priv.gc.ca/leg_c/leg_c_p_e.asp.
http://www.legislation.gov.uk/ukpga/1998/29/contents.
http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf.
http://csrc.nist.gov/publications/nistpubs/800-122/sp800-122.pdf.
http://csrc.nist.gov/publications/nistpubs/800-66-Rev1/SP-800-66-Revision1.pdf.
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf.
http://csrc.nist.gov/publications/nistpubs/800-50/NIST-SP800-50.pdf.
http://csrc.nist.gov/publications/nistpubs/800-40-Ver2/SP800-40v2.pdf.
http://csrc.nist.gov/publications/nistpubs/800-34-rev1/sp800-34-rev1_errata-Nov11-2010.pdf.