Building an Information Security Awareness Program: Defending Against Social Engineering and Technical Threats, First Edition (2014)
CHAPTER 11. Creating Simulated Phishing Attacks
Valerie Thomas Securicon, Lorton, VA, USA
Abstract
Performing a simulated phishing assessment can be an intimidating process. This chapter walks through an assessment step by step to take the mystery out of the process. Various tools and techniques are discussed, enabling the reader to select the best tool and approach for their organization. Although tools and techniques are a large part of the process, other elements must be coordinated to perform a successful assessment. This chapter also discusses the planning and coordination elements of a simulated phishing assessment.
Keywords
Phishing
Simulated phishing assessment
Attacks
Coordination
Reporting
Simulated Phishing Attacks
Simulated phishing attacks are gaining popularity within organizations for many reasons. When implemented properly, simulated phishing attacks can be utilized as training tools, test resistance to attacks, and provide metrics to management. While simulated phishing attacks are useful, they can also be a bit intimidating if you haven't created one before. In this chapter we'll go through the process step by step and discuss some tools to help along the way. Beginning a simulated phishing campaign can be overwhelming at first. Keep in mind that you aren't testing everyone in your organization at once. These campaigns, or assessments, can easily be divided into small groups.
Understanding the Human Element
Phishing e-mails prey on a variety of human emotions in order to achieve the desired action [1]. Often, phishing e-mails create a sense of urgency, claiming that the recipient's account will be disabled if immediate action isn't taken. Another popular attack is the e-card e-mail. This attack indicates that someone has sent the user an e-card and they must click on the link to retrieve it. Other tactics to persuade an employee to fall prey to an attack include using their first name or sending an e-mail that appears to be from a fellow employee.
Methodology
If you wish to incorporate a simulated phishing exercise into your awareness program, here is a high-level methodology [2]:
■ Establish a baseline by testing all employees
■ Train all employees (using your technique of choice)
■ Continue to test employees
■ Educate employees with embedded or continual training
■ Report results to management
■ Make adjustments as necessary
This cycle of events may take weeks if you have a small organization or months if your organization has hundreds to thousands of employees.
Open-Source Tool, Commercial Tool, or Vendor Performed?
There are many factors to consider when selecting an assessment tool, including
■ cost
■ number of employees
■ built-in training options
■ frequency of use
■ technical requirements
■ ease of use
■ long-term metric reporting
Although all of these factors are important, the number of employees in your organization and allotted budget are normally the largest deciding factors.
Open-Source Tool
Open-sourced software/tools is “software with its source code made available and licensed with a license in which the copyright holder provides the rights to study, change and distribute the software to anyone and for any purpose.” In short, it's pretty much free. With this, there is most often no guarantee of the software and the effects it will have on your environment. Additionally, support is often limited to software/developer/user forums and limited e-mail responses. While this may seem scary reading the text alone, the majority of penetration testers, vulnerability analysts, and other technical staff in the cyber community use one or several open-source tools to get their job done. Of all the capabilities that these technical staff need, most of them are not made by for-profit companies, hence the reason to rely on the open-source community.
The most popular open-source tool for phishing campaigns is the Social-Engineer Toolkit (SET) by Dave Kennedy of TrustedSec. It is considered the “de facto” tool for social engineering (Figure 11.1). SET can be installed on a machine inside or outside of your network, depending on your social engineering scenario.
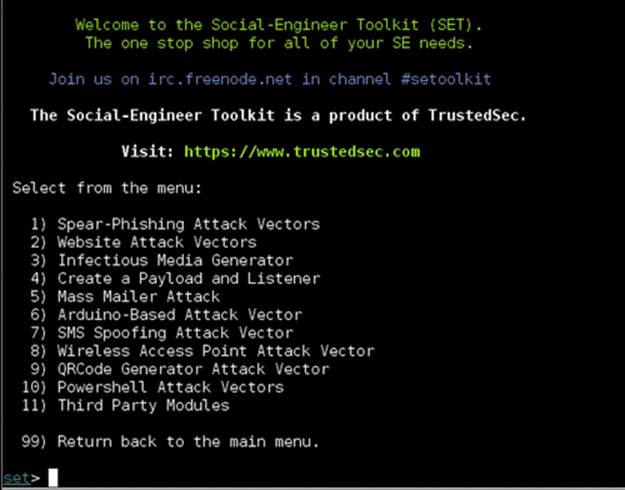
FIGURE 11.1 Main menu of the Social-Engineer Toolkit.
Pros
Aside from being free, SET offers a variety of resources for phishing campaigns including
■ the ability to clone an existing website for your landing page (page your employees will see/go to from the phishing message)
■ capturing passwords and other information entered on the landing page
■ prompting the user to run a program from the landing page
■ configuring to utilize your organization's e-mail server for ease of delivery
■ the ability to create attachments to include in e-mails
■ integrating with the Metasploit Framework for advanced testing options
Updates are released regularly and documentation is widely available to help you get started. Overall, SET is an incredibly flexible tool for developing custom phishing campaigns for the tech-savvy user.
Cons
Although SET is a powerful tool, it may not be suitable for all environments for a few reasons:
■ Must be installed on a Linux machine
■ Command-line-based
■ Requires basic knowledge of Apache web server and Metasploit Framework
■ No long-term metrics are stored in the tool itself. They must be documented from the report and saved elsewhere
■ E-mail groups are not stored in the tool and must be maintained separately
■ There is no dedicated support center for assistance
SET provides the user with many basic and advanced options for phishing campaigns. Users who are not familiar with Linux, Apache, and Metasploit Framework may find the tool difficult to use. Long-term users will need to track metrics, e-mail groups, and campaign history separately. More information on SET can be found at TrustedSec's website http://www.trustedsec.com.
Commercial Tool
If you prefer a more graphic-based tool, commercial products may be best for you. These products are mainly web-based and hosted through the vendor's infrastructure. In other words, you don't need any hardware or Linux knowledge to get started. The market for phishing campaign tools is rapidly expanding. A few of the most popular vendors are KnowBe4, PhishingBox, and PhishMe.
Pros
■ Preconfigured e-mail and landing page templates.
■ Ability to change the landing page appearance with a graphic tool instead of modifying the page source code.
■ Most products contain built-in training for employees who did not pass the assessment.
■ Products are web-based so there's no software to install.
■ Many products allow you to utilize your organization's mail server.
■ User guides and other documentation are available.
■ Support is available from the vendor for questions.
Cons
■ Subscription fees
■ Some products require a long-term contract
■ A minimum number of e-mails per year are usually required
Commercial tools also make it easy to manage multiple assessments at once. Figure 11.2 is the dashboard of PhishingBox. The dashboard highlights assessments that are in progress, scheduled, or awaiting authorization. Selecting an assessment in progress will provide you with up-to-date information of how many e-mails have been opened and more.
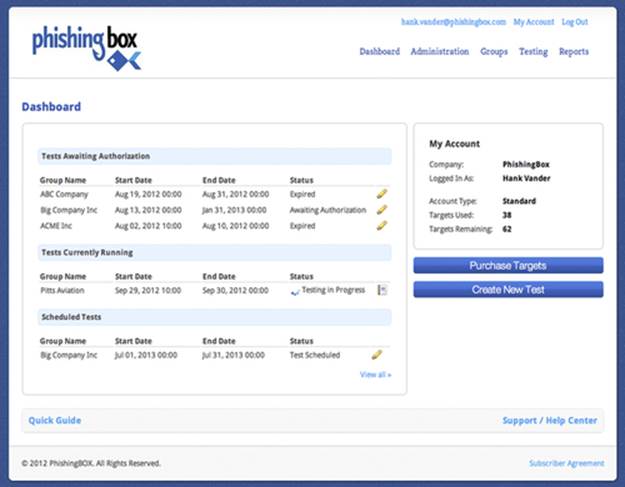
FIGURE 11.2 Dashboard Screen of PhishingBox.
The biggest hurdle to getting started with a vendor tool is the import of target e-mail addresses. Most tools require a specific format for e-mail address, name, and department. If you elect to use the vendor's e-mail servers to perform the test, some additional coordination with your e-mail team may be required in order to white list the vendor's servers for ensured mail delivery.
Selecting a Commercial Tool
In order to select the tool best suited for your organization, you should have answers (or estimates) to the following:
■ What is you annual budget?
■ How many e-mails do you want to send and how often?
■ Do you wish to include instant training material for the employees who fail the assessment?
■ Do you want to include attachments in your e-mails?
Many vendors offer free trial license and a live demo. Consider making time for the live demo. Not only does it provide you with an overview of the tool, but also it's your opportunity for questions about specific features and functionality. Evaluate a few different tools before making your selection. Some evaluation criteria to keep in mind are
■ ease of campaign creation
■ quality and quantity of e-mail and landing page templates
■ ease of modifying templates
■ ability to automatically insert first name and department into an e-mail
■ ease of creating your own e-mail and landing page
■ report generation and export options
■ long-term metric tracking
■ e-mail group management
■ ability to schedule e-mail delivery
■ available user guides and documentation
Vendor Performed
Building a phishing campaign isn't for everyone. If your budget supports a more expensive solution, hiring a vendor to perform the assessment may be for you. Almost all vendors that advertise a phishing campaign tool provide phishing assessments as a professional service. Organizations that only perform phishing assessments once or twice a year usually elect this method.
Pros
■ Easy to implement.
■ Requires no software purchase or subscription.
■ Many vendors do not require a long-term contract.
Cons
■ Most expensive solution.
■ Long-term metric tracking may not be available.
■ Dependent of vendor availability.
Although the vendor will be doing the heavy lifting on most aspects of the assessment, there are items that you as the client must provide including a list of target e-mail addresses and schedule for e-mail delivery. Most importantly, your organization must coordinate internally to prepare for the assessment to avoid confusion among the security team and other key positions in the organization.
Before You Begin
Operational coordination is essential in this process. Key people in the organization must be informed prior to performing your phishing exercise in order to prevent mistaking a phishing exercise for a real attack. Your Chief Information Security Officer (CISO) must be aware of all planned and active exercises. The manager/handler of the company's incident response team (IRT) should be informed of all exercises prior to execution. The manager may choose to inform their team in order to prevent spending time and resources investing an exercise. The manager may also choose to not inform their team in order to evaluate their response to the attack(s).
Reporting of hacks/penetrations to a company's network is a very sensitive thing. Most do not want to admit that a breach has occurred and try to keep it quiet. While this may “save face” to the company, it does not help all companies overall, as the attack data/vectors could be passed on to prevent breaches elsewhere in the industry. Final authority, unless otherwise explicitly required by law, regulation, or policy, is usually give by the company's CEO and/or board members, in collaboration with the company's legal team and public relations office. If an incident is to be reported to outside agencies, ensure that senior management is involved and that applicable laws/policies are followed.
Informing the manager of the help desk is also a good practice, as they will likely receive calls from targeted employees. While it is uncommon for the help desk manager to inform employees of a potential exercise, they can ensure that procedures for handling suspicious e-mails are up-to-date for their employees to reference. It is also important for the help desk manager to report the number of calls and e-mails received during the exercise.
Create a contact list with information for the included parties. Ensure that each main point of contact also has an alternate contact. Notifications may vary depending on the type of phishing e-mails you select. For instance, if you create an e-mail that appears to originate from human resources, then the human resources manager should be notified prior the phishing exercise. This management level notification prevents confusion and panic if employees begin contacting the originating department.
Determine Attack Objective
Simulated attacks can be as simple or complex as you'd like. They can be designed to measure many results, including
■ click only,
■ click and enter information on a landing page,
■ click and enter password on a landing page,
■ open an attachment.
If your organization hasn't conducted a simulated attack, the click only objective is a good starting point.
Select Recipients
Choosing the employees to evaluate first will help determine the type of attack you want to perform. Employees can be divided into groups for ease of administration. If your organization spans over multiple time zones, be sure to group employees in similar time zones. E-mails received during nonworking hours can be deemed suspicious. For nontechnical employees, general or company-specific types of attacks are most likely to result in clicks. For more technical employees, spear phishing attacks are more likely to result in clicks.
Select a Type of Phishing Attack
As discussed earlier, phishing e-mails utilize human emotions deceive their victims. This basically means that the sky is the limit when it comes to selecting e-mail themes.
General
General phishing attacks can be used to target anyone in the organization. These types of e-mails are a good starting point for your first few e-mails. A few themes are as follows:
■ Your package has shipped! Click here to track delivery progress.
■ Any type of charity seeking donation.
■ Someone has sent you an e-card! Click here to retrieve it.
Many of these examples can be utilized throughout the year but are ideal for holidays where cards are used, such as Valentine's Day and the months of November through December. Many purchased solutions have built-in general messages to get you started.
Company-Specific
Ethical hackers when performing a penetration test of the organization's network commonly use these types of attacks. The reasons are simple, the attacks are easy to construct and work the majority of the time. Not only do they work in penetration tests, but also they work in real-life scenarios. With minimal search time, an attacker can locate websites or affiliated partners of the company, such as
■ timekeeping software vendor or website,
■ web-based e-mail website,
■ web-based VPN website,
■ health benefits provider.
The information from these websites can be used to mimic legitimate e-mails. Additionally, the websites themselves can be duplicated to lure the employee into entering information, such as their username and password, after clicking the link in the phishing message.
Spear Phishing
According to the software company Trend Micro, 91% of cyber attacks began with a spear phishing e-mail [3]. Spear phishing e-mails target a single person or a small group within an organization. Attackers search a number of sources to deduce an employee's job function and what companies, individuals, or groups they associate with in order to create a believable attack. A spear phishing message
■ addresses the recipient by name,
■ appears to be sent by a person or vendor that the recipient is familiar with,
■ includes a proper signature block with logo and contact information,
■ often includes an infected attachment,
■ can contain a link to a website similar to the sender's (abcbank.com instead of abc-bank.com)
While other phishing e-mails are sent in large quantities, spear phishing e-mails are sent to very few employees—usually less than five. However, the extra research time usually pays off, as spear phishing messages have the highest rate of success.
Composing the E-mail
Once you've selected your target group and e-mail type, it's time to move on to creating the e-mail content. Here are some of the key elements for creating a realistic phishing message:
■ Use an attention-grabbing subject.
■ Create a sense of urgency in the message body that will motivate the recipient to take action.
■ Include logos and other applicable images.
■ Ensure the sender's name and e-mail address match the theme of your e-mail.
■ If your e-mail appears to originate from a person, include a complete signature block.
■ For e-mails that appear to be automatically generated, include a privacy statement at the end of the e-mail.
If you're using a vendor tool, you can edit the e-mail appearance in a graphic editor. Figure 11.3 is a screenshot of the composition tool by the vendor KnowBe4. This particular template includes a landing page (where the browser will go once the link has been clicked), which is displayed to the right. If you're using SET, the e-mail contents need to be plain text with appropriate HTML tags for formatting.
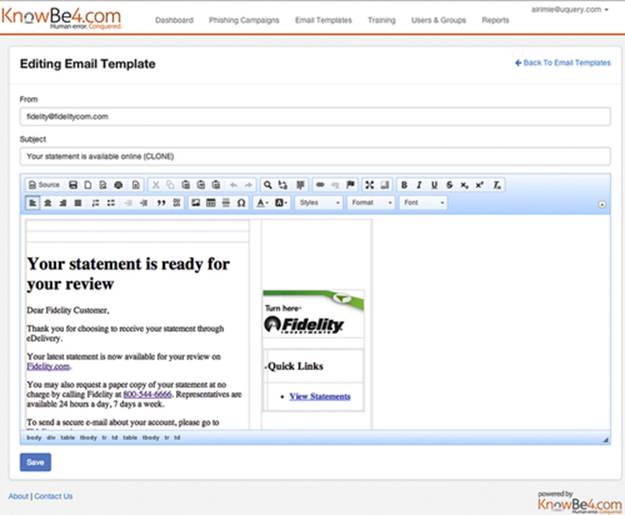
FIGURE 11.3 E-mail composition screen of KnowBe4.
Formatting the Link
Unless you are performing an attack with an attachment, your e-mail will include a link for the employee to click. The appearance of the link, or uniform resource locator (URL), plays an important role in the assessment. If the URL looks suspicious or misspelled, employees are less likely to click.
Graphic editing tools allow you to easily modify the display text of a URL so it appears as http://abc.com but once clicked goes to http://cba.com. Using this technique will educate your employees on URL modification and how to verify a link's true destination before clicking.
Creating the Landing Page
The landing page is where the employee will be directed if they click the enclosed link (Figure 11.4). If your assessment objective is to document the number of employees that clicked, this is a prime opportunity to display a message informing the employee of the simulated phishing assessment and to present training material.
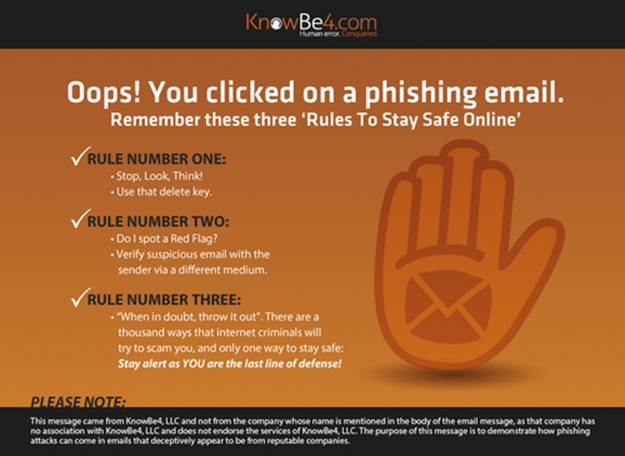
FIGURE 11.4 Basic landing page of KnowBe4.
If the attack objective is to determine if employees will click and enter information, the landing page must have areas that accept input. The most common input is an account password; however, you can customize the landing page to fit the attack objective. All commercial tools have a selection of landing pages that accept input. If you would like to use a webpage that belongs to your organization, most tools have an import feature. SET will clone a website once you have provided the URL.
Sending the E-mail
Now that you've created the list of recipients, the e-mail, and landing page, there are a few more quality control steps to take before pressing the send button:
■ Test appearance of e-mail in your e-mail client and web client (if applicable) by e-mailing the phishing e-mail to yourself.
■ Click the enclosed link to test the landing page. If your organization uses multiple browsers then test in all approved browsers.
■ Notify involved parties on the contact list as discussed earlier in the chapter. Include screenshots of the e-mail, landing page, and training page (if applicable). Also include the dates and times the e-mails will be sent.
Timing is Everything
When the e-mails are sent, they will significantly impact the results of your assessment. Ideally, the e-mails should be sent when employees are likely to be at their desks midmorning or midafternoon. Also, keep in mind what time zone your recipients are in when scheduling e-mail delivery.
Everyone needs a vacation now and again. If anyone on the contact list will be on vacation during the assessment, be sure to involve their backup contact person prior to sending any e-mails. Additionally, the personnel responsible for sending the e-mails and tracking their progress need to be available for questions. Don't start an exercise and be out of the office the next day.
Tracking Results
All tools, commercial and open source, have tracking ability to help you monitor the status of your assessment. Although individual tracking features may vary, most tools will indicate
■ if the e-mail was opened,
■ if recipients clicked the link,
■ if information was entered into the landing page,
■ if the link was clicked more than once.
Commercial tools will store the result information for each assessment for comparison reporting after additional assessments. SET does not store result information, so record will need to be tracked separately, most likely in a spreadsheet. Comparison reporting is key when reporting results to management and other involved parties to indicate the effectiveness of follow-on training.
Results tracking includes more than number of clicks. Other important results to track include
■ help desk calls reporting the e-mail,
■ e-mails received reporting the e-mail to security,
■ phone calls to security,
■ phone calls to involved departments, such as human resources
Improper reporting indicates that employees are not familiar with the procedure to follow after they've received a suspicious message. Training procedures can be adjusted to reinforce the proper procedure.
Post Assessment Follow-up
Once the assessment is complete and all results have been documented, take the time for an after action meeting with those individuals on the contact list. Discuss the results of the assessment and if there were any unexpected outcomes. Use this information to make changes to the procedure and contact list for future assessments.
Notes
[1] Open Source Software definition http://en.wikipedia.org/wiki/Open-source_software [accessed on 5.26.2014].
[2] The Seven Habits of Highly Effective Employee Phishing Training http://threatsim.com/resources/whitepaper-seven-habits-phishing [accessed on 2.12.2014].
[3] SHOCKER: Point-Of-Failure Phishing Training Does Not Work http://blog.knowbe4.com/bid/371048/SHOCKER-Point-Of-Failure-Phishing-Training-Does-Not-Work [accessed on 2.17.2014].
[4] 91% of cyber attacks begin with a spear phishing email http://news.techworld.com/security/3413574/91-of-cyberattacks-begin-with-spear-phishing-email/ [accessed on 2.17.2014].